Categorizing and Harmonizing Natural, Technological, and Socio-Economic Perils Following the Catastrophe Modeling Paradigm
Abstract
1. Introduction
2. Review of Hazard Modeling Parameterization per Peril
2.1. Data
- Asteroid impacts (fireballs): The Fireballs Reported by US Government Sensors [38] dataset for the period 15 April 1988–21 August 2022, available online: https://cneos.jpl.nasa.gov/fireballs/ (accessed on 31 August 2022).
- Blackouts: Dataset of numbers of customers affected in electrical blackouts in the United States between 1984 and 2002 [39], available online: https://aaronclauset.github.io/powerlaws/data/blackouts.txt (accessed on 31 August 2022).
- Cyber-attacks: The 2005–2018 Privacy Rights Clearinghouse (PRC) catalogue [40] for category hacking/malware, available online: https://privacyrights.org/data-breaches (accessed on 31 August 2022).
- Earthquakes: The 1900–2012 International Seismological Centre-Global Earthquake Model (ISC-GEM) Global Instrumental Earthquake Catalogue [41], available online: http://www.isc.ac.uk/iscgem/ (accessed on 31 August 2022); the fault source model of the 2013 European Seismic Hazard Model (ESHM13) [42], available online: http://hazard.efehr.org/en/Documentation/specific-hazard-models/europe/overview/active-faults/ (accessed on 31 August 2022).
- Epidemics: The Global Epidemics Dataset [43], available online: https://zenodo.org/record/4626111 (accessed on 31 August 2022).
- Heatwaves: Temperature data for July 2022 in France from the Météo-France data portal [44], available online: https://donneespubliques.meteofrance.fr/donnees_libres/Txt/Synop/Archive/synop.202207.csv.gz (accessed on 31 August 2022).
- Landslides: Inventory of events triggered by the 2008 Wenchuan, China, earthquake, courtesy of Dr. G. Li and Prof. J. West [45].
- Terrorism: Dataset of the severity of terrorist attacks worldwide from 1968 to 2006, measured as the number of directly resulting deaths [39,47], available online: https://aaronclauset.github.io/powerlaws/data/terrorism.txt (accessed on 31 August 2022).
- Tropical (and extra-tropical) cyclones: The International Best Track Archive for Climate Stewardship (IBTrACS) [48], available online: https://www.ncei.noaa.gov/products/international-best-track-archive?name=ibtracs-data (accessed on 31 August 2022).
- Tsunamis: The NCEI/WDS Global Historical Tsunami Database [49], here for the selected period 1900–2022, available online: https://www.ngdc.noaa.gov/hazard/tsu_db.shtml (accessed on 31 August 2022).
- Volcanic eruptions: The global database on large magnitude explosive volcanic eruptions (LaMEVE) [50], available online: https://www2.bgs.ac.uk/vogripa/view/controller.cfc?method=lameve (accessed on 31 August 2022).
- Wildfires: The FRY global database of fire patches [51], available online: https://data.oreme.org/doi/view/0e999ffc-e220-41ac-ac85-76e92ecd0320#FRY (accessed on 31 August 2022).
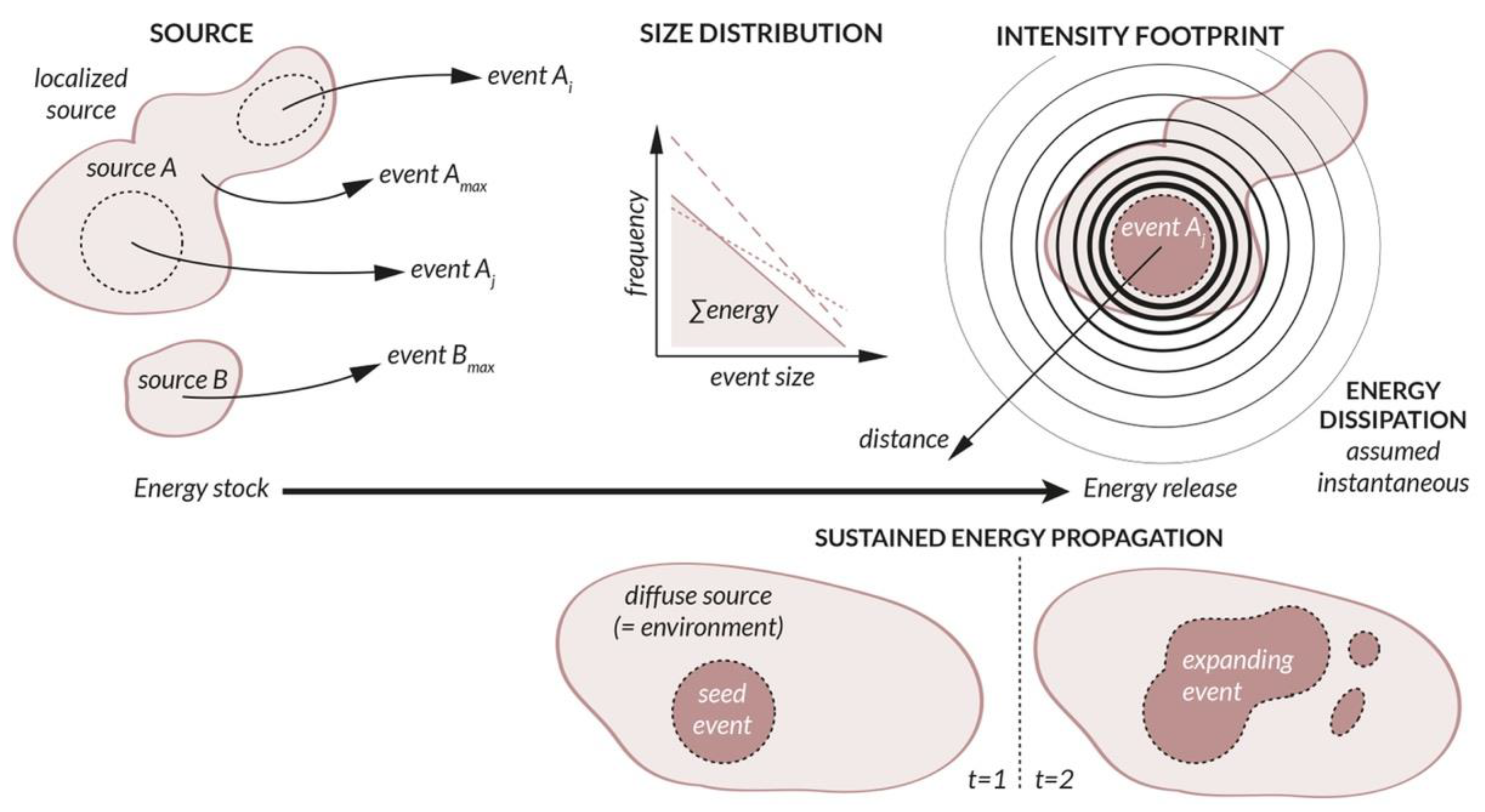
2.2. Event Source and Event Size
2.2.1. Point Source
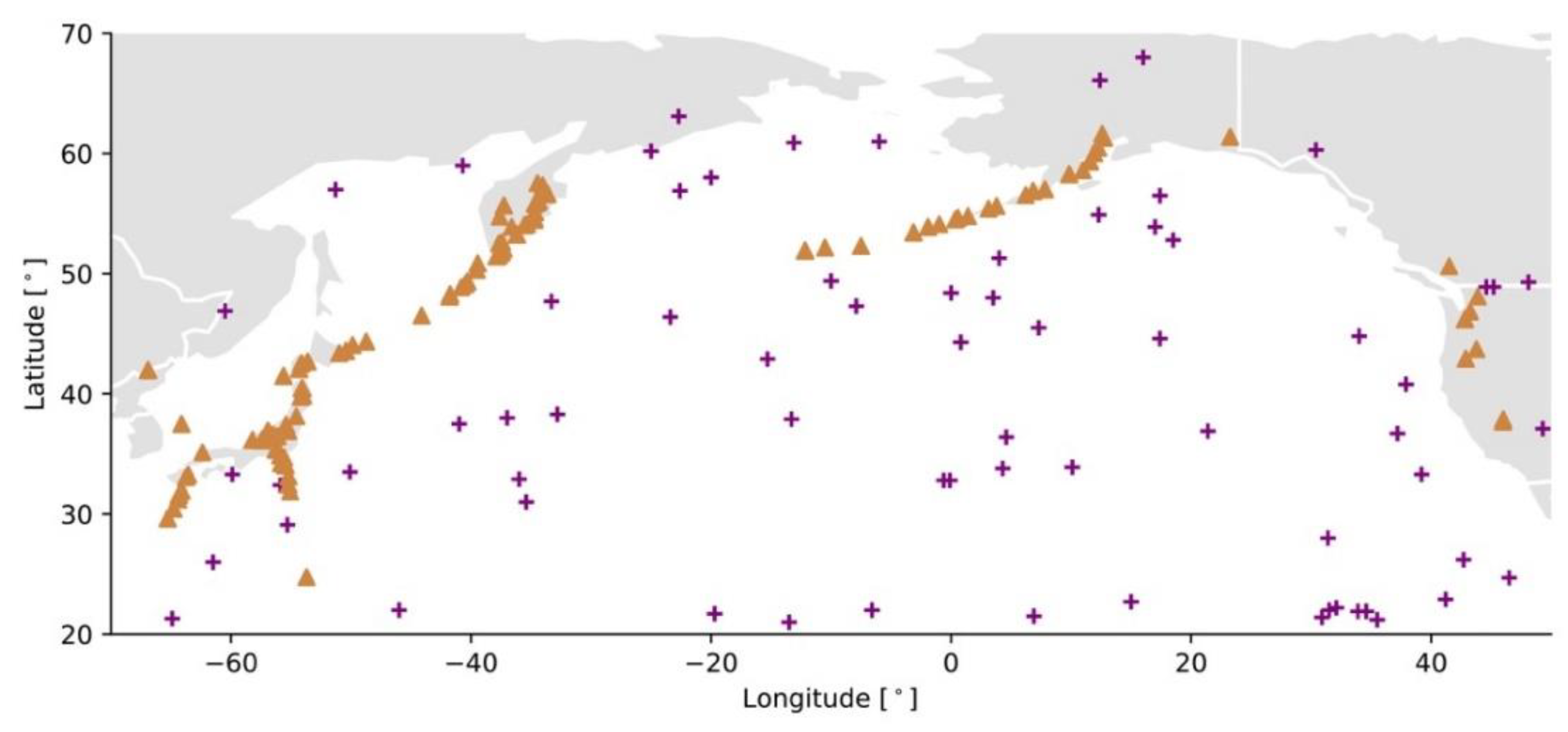
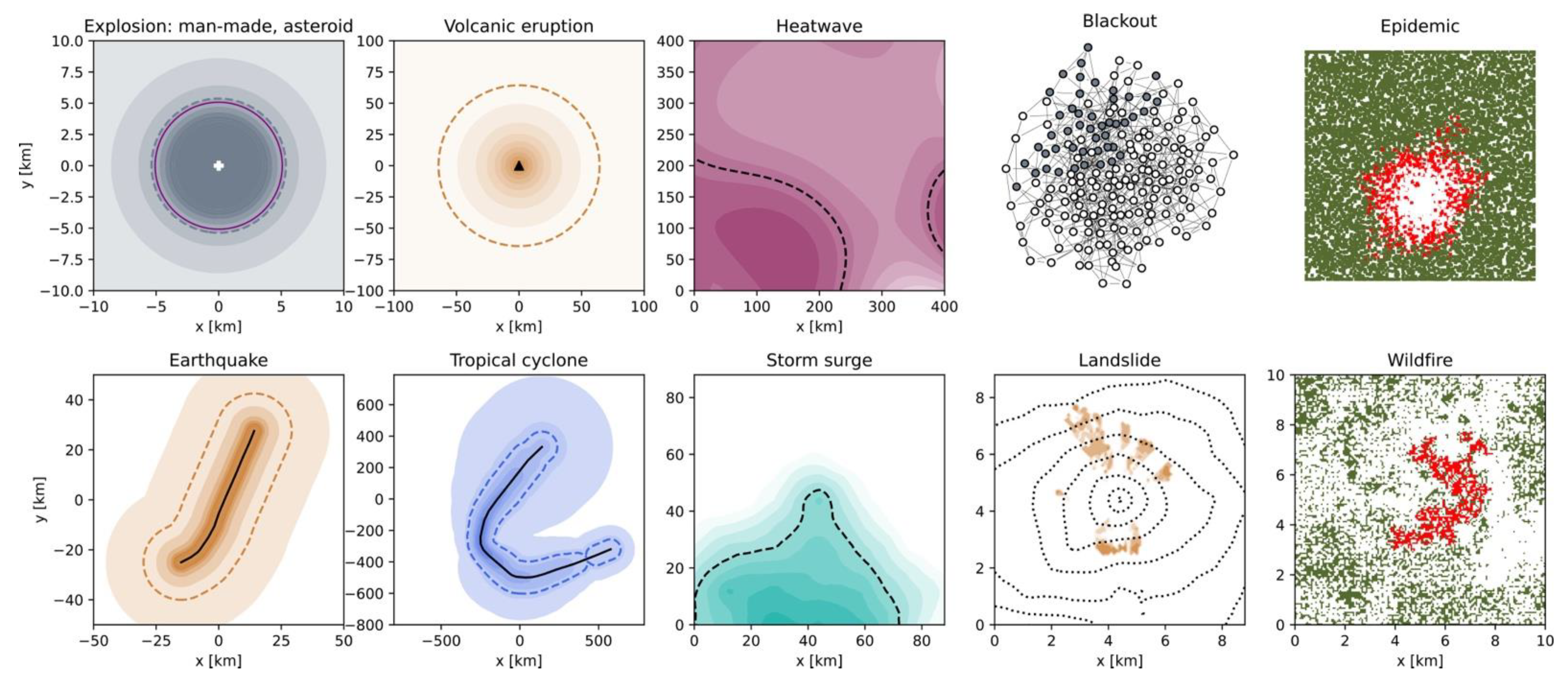
- Asteroid (or comet) impacts: The source is the impact site, which is random and uniform in space (Figure 2). The stored energy is defined by the characteristics of the impactor and the event size is directly expressed in terms of kinetic energy [J],with [kg] the mass of the body and [m/s] its velocity. The typical characteristics of the impactor are a density of 3 g/cm3 (stony asteroid), 8 g/cm3 (iron asteroid), or 0.5 g/cm3 (comet) and a velocity of 20 km/s (asteroid) or 50 km/s (comet) [52]. Equation (2) is an oversimplification of the process and does not consider atmospheric deceleration, disruption, or ablation processes, nor ground penetration [34,52,53].
- Explosions (accidental): The source is a container of explosive material. Sources of severe accidental explosions are located at industrial sites, so-called Seveso sites. The size of the event is defined by the blast energy [kJ], which is a function of the mass and chemical characteristics of the explosive substance. It is usually described in TNT mass equivalent [kg]. For a vapor cloud explosion (VCE), or fuel-air explosion, we havewhere is the explosion efficiency, or fraction of available combustion energy participating in blast wave generation, [kJ/kg] is the heat of combustion of the material, and [kg] is the mass of flammable vapor release, itself a percentage of the total mass of hazardous material. 4200 kJ/kg is the heat of combustion of TNT. For an explosion at a fuel storage site or refinery, 46.4 MJ/kg and [54,55] can be used as an example. Another type of explosion is the boiling liquid-expanding vapor explosion (BLEVE), resulting from the sudden vaporization of a liquid [56]. Related perils include fire and toxic material release [57,58].
- Explosions (armed conflicts, terrorism): The source is a bomb, whose size is known by design. For conventional blasts, Equation (3) can be used with high explosives considered as source material (e.g., TNT). For non-conventional blasts, such as a nuclear explosion, a simple equation of the yield iswhere is the total mass of the spherical bomb (core + tamper), is the difference between the expanded radius and the initial radius of the sphere, is the time required for a neutron born in a fission to subsequently strike and fission another nucleus, and is the number of neutrons liberated per fission ( for Uranium 235 and for Plutonium 239) [59]. In contrast to accidental explosions, sources of intended explosions are mobile and correlate with population density and specific (critical) infrastructure targets [26]. It can be considered a sub-peril of armed conflicts and terrorist attacks, which have a diffuse source (see Section 2.2.5). A related peril is radiation in the case of a nuclear attack.
- River floods: The source is a river system associated to a catchment basin. It can, however, be represented by (or concentrated at) a point source characterized by the peak discharge [m3/s] at a point of the river. For a small basin (1 km2), it is estimated with the Rational Formulawith the runoff coefficient (which depends on soil conditions and surface characteristics, such as asphalt versus grass), [m] the critical rainfall, the concentration time [s] (function of flow distance and terrain slope), and the catchment area [m2] [60,61]. If is defined as the duration of the rainfall event, then represents the rainfall intensity with the role of slope included in . For greater basins, non-linearities must be included, such as the topography and the non-stationary flow observed on hydrographs [60]. An empirical relationship approximating the process can otherwise be used withwhere is the expected annual peak discharge [m3/s], [km2] the catchment area, the annual average rainfall in the catchment [mm], the upstream catchment slope [m/km], and to empirical parameters [62].
- Volcanic eruptions: An active volcano transfers heat and matter from the Earth’s interior to outside the volcanic edifice. Most eruptions occur along the Ring of Fire (Figure 2). The event size is the volume of matter ejected [km3], which is also the main parameter of the Volcanic Explosivity Index (VEI) [63]. Other characteristics of the magma, such as temperature , allow the thermal energy released during the eruption to be estimated [64] (see Section 3).
2.2.2. Line Source
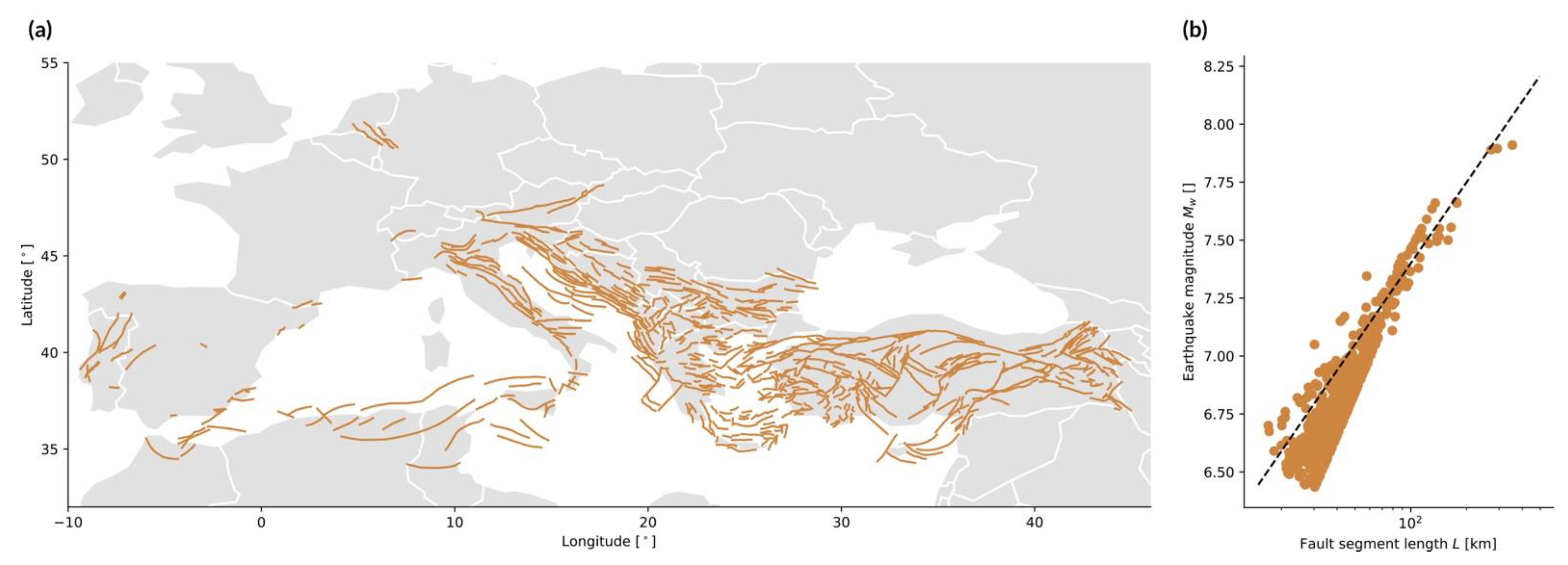
- Earthquakes: The source is a fault, i.e., a planar rock fracture which shows evidence of relative movement. There is often no need to explicitly define an area source as the line carries dip and width information (Figure 3a). The seismic energy released by an earthquake is proportional to the seismic moment [N·m], with Pa the rock shear modulus, [m2] the rupture surface area, and [m] the average displacement on the fault. The earthquake’s size is, however, commonly described in terms of moment magnitude [65]Usually, empirical relationships linking magnitude and fault geometry are used instead of the other physical characteristics of the rupture, such aswith the surface rupture length and and fitting parameters as a function of the fault mechanism (normal, reverse, or strike-slip) [66] (Figure 3b).
- Storm surges: The source is a storm, and more precisely the low-pressure region above the water mass combined with strong winds. It may be considered a line source since the event size is defined in terms of the water height along the coastline [29]. The storm surge can be related to storm maximum windspeed , for example with a polynomial function of the formwhere the empirical parameters , , and are site-specific [67]. Although the match between hurricane windspeed and storm surge height ranges is given on the Saffir–Simpson Hurricane Wind Scale, the indicator is often not sufficient for estimating the actual storm surge [68].
- Tornados: The simplified source of a tornado track is a line with no intensity variability along its length [20] (otherwise it is modelled as a track source—Section 2.2.4). The event size is defined in terms of maximum wind speed , which is the main parameter of the Enhanced Fujita Scale [69]. Additional parameters of the source, such as location, length, and width (or maximum radius), are sampled from historical data [70].
- Tsunamis (triggered by an earthquake): In this case, the source is an underwater fault line. The size of the event is commonly defined by both wave velocity and wave height at arrival on the coast, which is equivalent to the hazard intensity footprint. This applies also to tsunamis generated by other non-meteorological sources, including asteroid impacts, landslides, and volcanic eruptions. For an earthquake trigger, the initial size of the tsunami above the rupture can be estimated in terms of potential energy [J] (following the box-shaped ‘waterberg’ method) bywith kg/m3 the water density, the gravitational acceleration, the earthquake rupture length [m], the wavelength or width of the area displaced [m], and the upward rupture displacement [m] [71]. For other formulations, see [72].
2.2.3. Area Source
- Hail: The source is a convective storm, with hail as a sub-peril alongside strong winds, tornados, lightning, and heavy rain. It is described by the area in which hailstones are found, with the size of the event defined in terms of the maximum hailstone diameter [cm] [19]. Hail cells have been approximated by so-called storm boxes [19] or ellipses [74]. Their location, size, and shape are constrained by meteorological observations [74]. The temporal evolution during an event can also be considered, in which case a track source should be used [74]. Note that it is a case where event source and hazard footprint cover the same area (see Section 2.4.2).
- Urban fires and wildfires: Fires in both wildland and urban areas were originally modelled as ellipses, with the fire spread rate [m/min] defined aswith the spread rate on flat terrain and without wind as a function of the combustible characteristics (i.e., the source), the direction of maximum slope, the wind direction, the eccentricity function of windspeed and terrain slope, and an arbitrary direction [75,76]. Despite its simplicity, Equation (11) produces reasonable estimates of fire spread in a uniform environment. It is now more common to use cellular automata to model fires by considering diffuse sources instead [28] (see Section 2.2.5 and Section 2.4.3). Yet, ellipses can be used to define the seed events from which greater fires can propagate [76].
2.2.4. Track Source
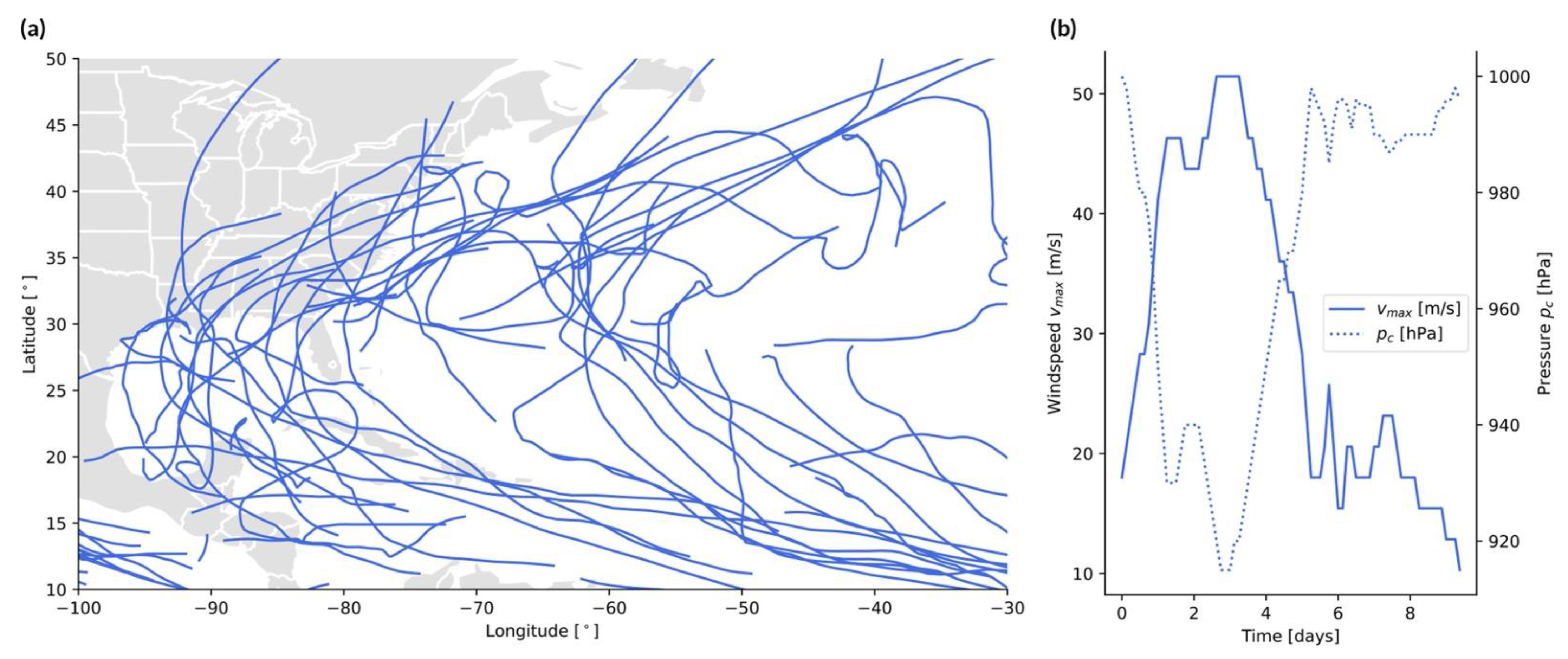
- Tropical cyclones: The source is an area of low pressure over a large water surface, which moves along a track over time . The genesis point, trajectory, and end point of the storm are stochastic and derived from past observations [77]. The event size at any given time is defined by the maximum wind speedwith [Pa] the cyclone’s central pressure, [Pa] the ambient pressure outside the cyclone, 1.15 kg/m3 the air density, the Holland parameter, and Euler’s number [78]. Notice the anticorrelation between and in Figure 4b, in agreement with Equation (12). The windspeed can then be used to estimate the event size on the Saffir–Simpson Hurricane Wind Scale. Along the track, the windspeed progressively increases, as the tropical cyclone grows, and then decreases, as the storm makes landfall, weakens, and dies off (Figure 4b). One can define the size of an individual storm in terms of total power dissipation by integrating over the wind profile along the entire track [79] (see Figure 5 and Section 3).
2.2.5. Diffuse Source
- Armed conflicts (incl. terrorism): The source is a hierarchical group of individuals, ranging from small terrorist organizations to large (trans)national armies. The size of the seed event is constrained by the funds and people power at the disposal of the attacker, as well as by the group’s network structure and utility function. The process is highly dynamic, as the various agents are mobile and opponents can allocate resources to defend against an attack [25,26]. The size of an event depends directly on the type and number of weapons. It can be a group of fighters (with firearms or non-firearms—see Section 2.4.3), conventional weapons (expressed as a TNT-equivalent, e.g., Equation (3)), or non-conventional weapons, including chemical, biological (see epidemic), radiological, nuclear (e.g., Equation (4)), and cyber- attacks. Those weapon types, which require different hazard modeling strategies, can be considered different sub-perils of an armed conflict. The event size is commonly defined in terms of the fatality count summed over all attacks taking place during the conflict ( then directly represents the human loss in the risk component of the CAT model).
- Blackouts: The source of a blackout is a current overload due to a local disturbance in the power grid. This system is composed of generator nodes (i.e., power plants), transmission nodes, and distribution nodes connected via transmission lines. A seed event can correspond to the tripping of several lines due to tree contact for example, which can be caused by lack of tree trimming or by a storm [80]. The event is only called a blackout if a relatively large number of consumers is affected by the loss of electricity. The event size can also be defined in terms of unsupplied energy [MWh]. The event size depends on how the overload propagates through the power grid through cascading failures.
- Business interruptions: The source is any business that is shut down due to direct damage by some natural or man-made event. Although a business location can be represented by a point source or extended area source, a catastrophic event consists of the aggregation of disruptions at many locations in the built environment, which may include a supply chain network in the case of contingent business interruption. The event size is directly defined in terms of revenue loss [30].
- Crop failures (due to pest): The source is a pest, such as an insect, a virus, a grazing animal, or some other invasive species that damages the crops. The size of an event depends on the complex interactions between the pest and crop growth within the crop production system where natural predators and/or pesticides may also participate [32]. Note that crop failure can also be due to climatic stress, represented by extreme temperature changes, droughts, as well as meteorological (hail), hydrological (flood), and ecological (field fire) events. In those cases, crops only represent the exposure layer of the CAT model. The event size is commonly defined in economic terms, such as farming production yield loss. However, it could, in theory, be defined by pest biomass before any consideration of crop damage.
- Cyber-attacks: The source of a cyber-attack is a malicious agent (a hacker) acting for personal gain or on behalf of a governing entity. Cyber-attacks can include theft of data or currency, ransoms, business interruption, or some other forms of system destabilization. The attack occurs, by definition, via electronic communication networks and virtual reality [21]. One particularity of cyber-attacks is that they are not geographically bound. They can cascade into greater events [22] via highly dynamic processes [21]. Their size is defined in terms of the number of data breaches in the common case of data exfiltration. However, this depends on how the initial attack propagates through the IT system. Since is often the number of actual breaches and not of attempted breaches, the event size directly reflects the loss in the risk domain after considering the level of vulnerability of the exposed system. Hazard and risk are intertwined since both the type and size of a cyber-attack depend on the attacked system. For example, a cyber-heist on a banking system is different from a distributed denial of service (DDoS) attack (with here expressed in gigabits per second [Gbps]), itself different from a cyber-attack on a power grid or other connected critical infrastructure. Many other types of events exist which could go as far as a cyber-war [22].
- Epidemics: The source of an epidemic is the first infection in the human population. This requires the pathogen and susceptible hosts to be in contact in adequate numbers. The size of an event can be the number of infections , which depends on how the epidemic propagates, as a function of the basic reproduction numberwhere is the transmission parameter, the recovery delay, and the total population. The parameters and depend on the vector, which can be a virus, bacterium, fungus, or parasite [24]. When an epidemic spreads to multiple continents, it becomes a pandemic. The total number of fatalities, which is the number of infections times the mortality rate, is the final loss. However, it may also be considered as the event size since the mortality rate also depends on the pathogen, and not only on the human vulnerability (function of age, gender, and health condition).
- Landslides: The source is the set of terrain patches with an unstable slope , which is controlled by topographic and soil characteristics. The size of the seed event can be the area [km2] or volume [km3] of each patch or set of patches. The area that is unstable is defined by a Factor of Safety () lower than 1, since it is the ratio of resisting forces to driving forces. A simple formulation iswhere [m] is the depth perpendicular to surface (or thickness) of the soil, is the gravitational acceleration, [N/m2] is the soil cohesion, [kg/m3] is the soil density, 1000 kg/m3 is the unit weight of water, is the slope angle, is the internal friction angle of the soil, and is the relative wetness representing the ratio between water column height and soil height . For additional formulations, see [81,82]. An increase of due to heavy rain further decreases , making previously stable slopes unstable [82]. is also involved in landslide triggering by earthquake ground shaking [83].
- Social unrest: The source of social unrest is the part of the population which has a high level of grievance against the governing entity [35]. The first individuals turning violent, who can be anyone in the system, can lead to a riot, i.e., an aggregate act of violence against individuals and property, which includes looting and setting fires as sub-perils [84]. The event can, however, be avoided if enough security is at the disposal of the government [35]. The dynamics is reminiscent of what can occur during an armed conflict (see above), with an extreme social unrest event potentially turning into a revolution. The event size could, in theory, be defined in terms of the number of rioters .
- Urban fires (accidental or malicious): Fire can be considered a sub-peril of industrial accidents [58], armed conflicts [85], and social unrest [84], as well as a secondary peril of earthquakes [28]. The source is some combustible material that is set alight. The event size, defined in terms of burnt area , depends on how the fire propagates in the environment, as in the case of a wildfire (see below). If an elliptical event is realistic in a uniform environment (Equation (11)), it is not in most real-world situations.
- Wildfires: The source of a wildfire has two components: a trigger for ignition and some combustible material (i.e., vegetation). The main cause of wildfires globally is anthropogenic, with fires started intentionally or accidentally. This ranges from power line ignition to arson via a forgotten cigarette butt [86]. Lightning strikes are the most important natural ignition trigger for wildfires [87]. In this case, the occurrence of a seed event depends on the continental lightning rate [flashes/min]A function of the convective cloud top height [km] and a resolution- and model-dependent scaling factor [87,88]. The size of the event, described in terms of burnt area , depends on the propagation process, a function of the characteristics of the environment, such as terrain, fuel, and meteorological conditions (see Equation (11)). Conditions are more favorable for a wildfire during a drought [89]. In the CAT modeling context, losses occur in the wildland–urban interface, defined as an area covered by more than 50% vegetation with more than one housing unit per 1.62 ha [27]. An ignition index can be calculated to map the potential size of an event as a function of dead fuel moisture, temperature, and vegetation species flammability among other parameters [90].
2.3. Event Size Distribution
2.3.1. Power-Law Distribution
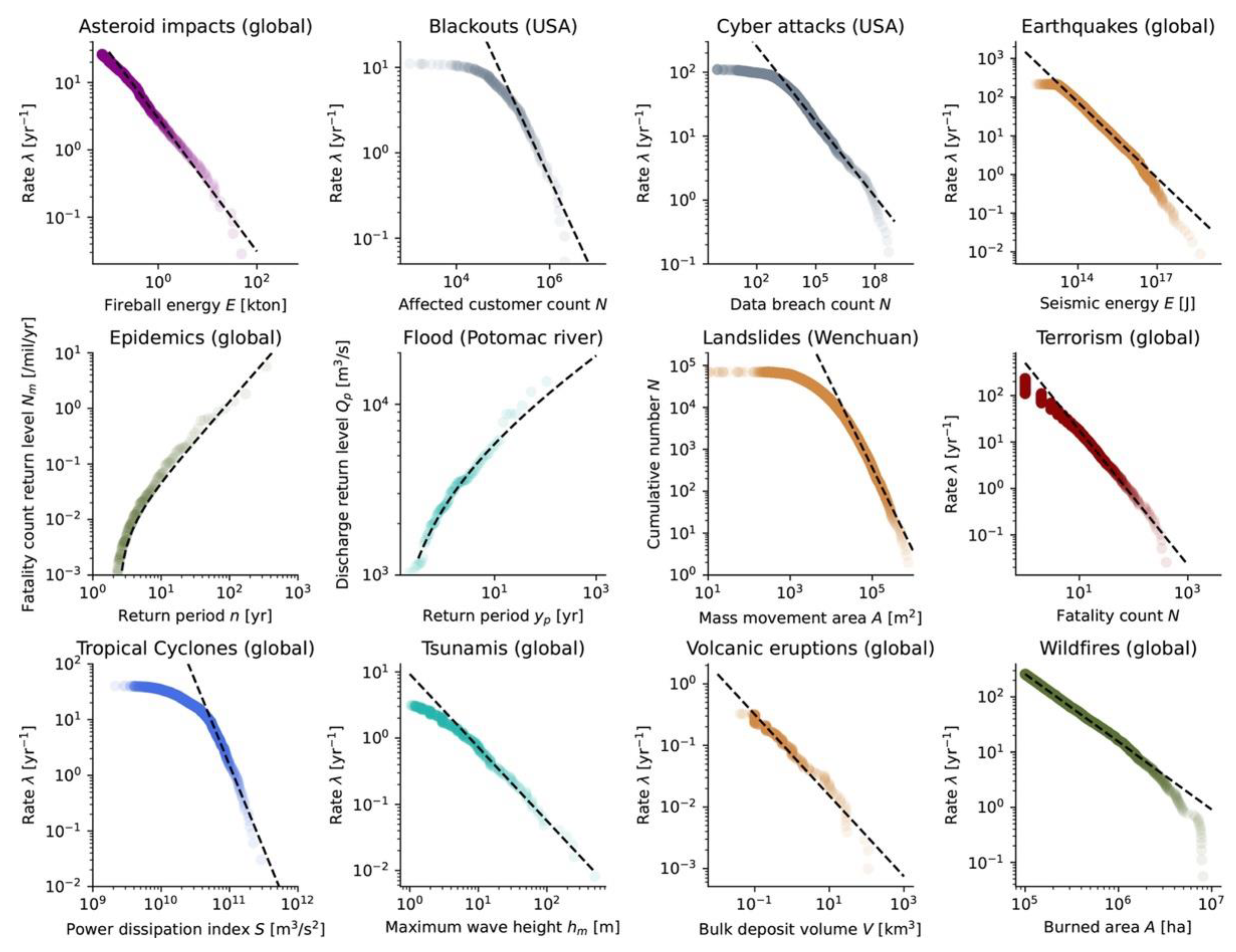
- Armed conflicts (incl. terrorism): The size distribution follows Equation (18), with as the number of fatalities [97]. In Ref. [97], a value of was obtained for various types of conflicts (war, banditry, gang warfare). In Ref. [98], a value of was obtained for interstate wars taking place between 1820 and 1997 and the 1465–1965 European great power wars. In Ref. [39], a value of was calculated for wars between 1816 and 1980. In the case of terrorism worldwide from 1968 to 2006, we obtain and (Figure 5), close to the value of found by [39,47] for the same dataset.
- Asteroid impacts: The flux of small near-Earth objects colliding with our planet follows a power-law in the form of Equation (18), with [kton] as the energy and 0.5677 and 0.90 globally [99]. In Ref. [92], a value of was obtained when including more recent data. Considering data up to 2022, we obtained 0.468 and 0.99 (Figure 5).
- Cyber-attacks: The size distribution follows Equation (18), with the number of personal identity losses or data breach volume (used as the example in this case). In Ref. [101], a value of was obtained when using data from the Open Security Foundation for the 2000–2008 period. Considering hacking events from the public dataset published by the Privacy Rights Clearinghouse [40], we obtained and for the 2005–2018 period.
- Earthquakes: Although the size distribution of earthquakes also follows a power-law in the seismic energy domain with (Equation (18), as with the and values shown in Figure 5, and with ) [102], the Gutenberg–Richter (exponential) law is used in virtually all cases [103], as a function of the magnitude . It yields a Gutenberg–Richter slope of globally [41] which is close to unity, known as the standard value for tectonic earthquakes.
- Landslides: The size distribution follows Equation (18), with [km2] the landslide area or [km3] the landslide volume. Conversion from area to volume can be performed with the empirical scaling relationship [104]. For , a review of more than 20 analyses provides [105]. For landslides triggered by the 2008 Wenchuan earthquake for instance [45], we find at the tail of the distribution (Figure 5), which is in agreement with [106] who obtained .
- Volcanic eruptions: The size distribution follows Equation (18), with [km3] as the erupted volume. Considering all volcanic eruptions which occurred after the year 1000 in the LaMEVE database [50], we obtain −1.156 and 0.66 (Figure 5). A recent review of large VEI eruptions indicates that VEI-7 events recur every 500–1000 years [108]. Our parameters lead to 300–1300 years for the range of VEI-7 events.
- Wildfires: The size distribution follows Equation (18), with [km2] as the size of the wildfire as defined by the burned area . Ref. [109] reviewed the literature and mentioned for China and the United States. Ref. [39] calculated for U.S. federal land. Ref. [92] found for fires in Angola and for fires in Canada. For the FRY catalogue [51], we obtained 8.553 and 1.23 (Figure 5).
2.3.2. Generalized Extreme Value (GEV) Distribution
- River floods: With the event size defined from the maximum discharge observed in a year of daily measurements, flood sizes are described by the GEV distribution [111,112]. Taking the Potomac River dataset [46] as a textbook example, we obtained m3/s, m3/s, and (Figure 5). A power-law behavior has also been proposed [95].
- Storms (tropical cyclones and other windstorms): Both GEV and GPD distributions have been used to describe the size distribution of storms () and related perils. Parameterizations for specific cities and coastline segments can be found in the literature [113,114,115,116]. It can be noted that defining storm size in terms of total dissipation of power yields a power-law distribution with a relatively high exponent [92]. Using such a proxy by summing over the cube of records per interval for each track duration , i.e., [m3/s2] [79,92], we obtain for global data [48] (Figure 5).
2.4. Hazard Intensity Footprint
2.4.1. Analytical Expressions of Static Event Spatial Diffusion
- Asteroid (and comet) impacts: The kinetic energy of the celestial body transforms into destructive explosive energy at impact, which is described by peak overpressure [psi]. The simplest approach consists of defining a binary intensity footprint, for instancewith the 4-psi overpressure radius [km], [Mton] the event impact energy, and [km] the burst altitude [34]. Due to lack of data for calibration, the blast footprint formula is usually calibrated to data from nuclear tests [33,52,118] (see also the comparison between Equation (28) and the industrial explosion footprint case below and in Figure 6). Damage can also occur due to thermal radiation [34].
- Earthquakes: The general formulation of a ground motion prediction equation (GMPE) iswith the earthquake magnitude and [km] the distance to the source [119,120]. The intensity is often taken as the peak ground acceleration but can also be peak ground velocity, peak ground displacement, or spectral acceleration of felt intensity [121]. One of the simplest parameterizations is , , , and , with as the PGA [g] and [km], being the distance to the surface projection of the fault rupture, and the fault depth [122] (Figure 6).
- Explosions (accidental or malicious): A simple empirical relationship linking blast overpressure [kPa] to the explosive mass [kg] iswith as the dimensional scaled distance according to Hopkinson–Cranz law and with [m] as the distance to the source [123]. This is, for example, consistent with the binary footprint model (Equation (28)) proposed for asteroid impact CAT modeling (for an impact on the ground with and 1 psi = 6.89476 kPa). This is illustrated in Figure 6. The overpressure field for very large yields is calibrated to nuclear tests [118] and therefore also applicable to the blast component of nuclear explosions.
- Tornados: The mean wind field for a stationary tornado is calculated as the sum of the tangential and radial velocities and , with both wind velocity components based on the Rankine vortex model,with the distance from the tornado origin, the maximum (tangential or radial) velocity, and the radius of the maximum (tangential or radial) velocity. An example of parameterization is m/s, m/s, and m [124]. The intensity footprint of the tornado is obtained by adding the forward motion velocity to the wind field (e.g., m/s).
- Tropical cyclones: The wind profile of a tropical cyclone can be described bywhere [km] is the distance to the cyclone center, [km] the radius of maximum winds, and [rad/s] the Coriolis parameter function of the latitude (see Equation (12) for the definition of , , , and ) [78] (Figure 6). Nowadays, more sophisticated models are preferred [125], although Equation (32) remains important in CAT modeling conditional on the proper estimation of [126].
- Volcanic eruptions: Apart from pyroclastic and lava flows, the principal hazard arises from the fall of airborne debris, ranging from blocks to ash, collectively known as tephra. The ash load is calculated by the pressure [Pa], where 900 kg/m3 is the density of dry ash and is the ash layer thickness [m]. The ash thickness can be estimated from the exponential thinning lawwhere [m] is the maximum thickness and [m] is the half-distance (Figure 6). For a circular footprint,where is the volume of tephra [127]. We remain unaware of any simple model to estimate .
2.4.2. Threshold Models of Passive Event Emergence
- Business interruptions: There exists a lower damage threshold of ~5–10% that must be breeched to result in a business interruption, and an upper threshold, often as low as 50%, to cause the facility to completely shut down for repair or demolition [30]. This depends on the hazard intensity footprint of the trigger event.
- Hail: The contour of a convective storm is estimated from meteorological indicators. A hailfall footprint (often elliptical—see Section 2.2.3) then exists if the hailstone size (often assumed uniform in space) can exceed the threshold above which damage can occur (usually 2 cm in diameter) [128]. The hazard intensity is then defined as the kinetic energy [J/m2]with the maximum hailstone diameter [mm] and empirical parameters of and in [128].
- Heatwaves: Heat stress can be quantified by the wet-bulb temperature , measured by covering a standard thermometer bulb with a wetter cloth and fully ventilating it. If exceeds a 35 °C threshold, hyperthermia follows [129]. The heat stress footprint can be derived from the temperature map (which could be considered an unbounded area source; Figure 6) with the empirical expressionwhere is the relative humidity [130].
- Storm surges: The so-called “bathtub” model defines a flooded area as all the locations below a certain elevation that are hydrologically connected to the coast, with the threshold based on the size of the storm surge event. In other words, it is a projection of a horizontal flood surface onto the topography (Figure 6). This model tends to overestimate flood extents [131]. More realistic models are based on hydrodynamics, a simplification of which are cellular automata (see Section 2.4.3). In this case, the discharge [m3/s] must be used as input, defined fromwhere [m] is the height of water above the ground, [m] the breach width, and [m/s] the velocity of the water following the weir equation [29]. The breaching of a natural or man-made defense must also be modelled, which involves defense vulnerability analysis between event size assessment and flood modeling [29].
2.4.3. Numerical Models of Dynamic Event Propagation
- Armed conflicts (ABM): A war is a cumulation of attacks and counterattacks, whose dynamics can be explained with Game Theory [36]. Although highly complex and heterogeneous in nature, some basic rules can be mentioned. The simplest model of attrition warfare is a set of ordinary differential equations (ODEs) defined aswhere is the number of soldiers in the A army, each with offensive firepower (i.e., number of enemy soldiers killed per soldier from A), and is the number of enemy soldiers in the B army, each with offensive fire power (called Lanchester equations after F.W. Lanchester’s 1916 work) [134]. Solving Equation (38) indicates that the effectiveness of an army rises proportionally to the square of the number of its soldiers, but only linearly with their fighting ability. While Equation (38) is relevant for static trench warfare (see other ODEs in [135]), agent-based models can include spatial variations of forces, decision making, and psychology [136]. Agents are then combat units with a mission and situational awareness, among other characteristics. Their possible states are alive, injured, or killed. The battlefield is the geographical lattice. However, the rules would be too numerous to list here [136,137]. A much simpler ABM for social unrest will later be provided that illustrates how different groups of individuals may act against each other [35]. The hazard footprint of an armed conflict would, in theory, be the sum of a heterogenous set of sub-footprints (e.g., explosion footprints—Equation (26), agents’ individual acts of violence—see social unrest and terrorist attack cases below, fires, etc.).
- Blackouts (CA): Cascading power failures can be modeled as a Sandpile on a network, instead of on a regular lattice. In the simplest generic configuration [138], each power line and generator have a region of safe operation, characterized by a load in a node. Links between nodes define the neighbors to which or from which a load increment is randomly transferred withwhen the power load exceeds the margin at node , then units of load are transferred (and distributed randomly) to the failed node’s neighbors :with the condition . The Sandpile network self-organizes, with cascading failures potentially leading to large-scale blackouts [138]. The footprint of the blackout is then defined as all the nodes that failed in one event (Figure 6).
- Crop failures (due to pests, ABM): Pest dynamics can be described by a set of ODEs that describes inter-species interactions. They can be multiple and play at different spatiotemporal scales in an ecosystem. The simplest model is the predator–prey Lotka–Volterra model [139,140]where is the prey density (e.g., the crops) and the predator density (e.g., the pest). Note the resemblance to the model of attrition warfare (Equation (38)). A far more complex model is the seminal ‘insect outbreak system’ of [141], which—in its simplest form—describes interactions between a pest (the spruce budworm), its predator (some birds), and the exposed vegetation (the forest). Several CA and ABM have been developed for insect pest assessment [32]. Simple agent rules can be derived from Equation (41) by, for instance, adding a spatial component, random agent movement, and a contact radius. The intensity of an event could be defined by the aggregate size of the pest on the crops, , or the direct damage, .
- Cyber-attacks (various): Cyber-catastrophes propagate via cascading effects within IT systems and networks. For data exfiltration cases, the final event size, or event footprint extent, can be defined on a data breach severity scale function of the number of lost personal records (P3, for the range 1000–10,000, to P9, for 1 billion [22]). Cyber-attacks may also cascade into critical infrastructure failures (e.g., blackout—see above) and socio-economic events [22]. Their footprints (both virtual and physical) are highly scenario-dependent. However, [22] indicated a 1.6 economic multiplier when considering loss increase due to cascades in a trading network of companies. The dynamics of a cyber-attack is mainly governed by the principle of least action, i.e., striking targets with inferior security, and follows the rules of Game Theory [22]. Various statistical models have been proposed [21,142] which are outside the scope of this paper. On the physical side, epidemic models, for example (see below), have been modified to quantify the spread of a piece of malware [143].
- Epidemics (ABM): The simplest epidemic model is the Susceptible-Infectious-Recovered (SIR) model [133]. Many more sophisticated models exist [144,145] that derive from the SIR set of ODEs:where is the susceptible stock, the infected stock, the recovered stock, and (see Section 2.2.5 and Equation (13) for the definition of and ). The controlling parameter is the basic reproduction number (Equation (13)); a feedback loop leading to an epidemic occurs for . While Equation (42) can be solved by numerical integration, agent-based models attempt to capture the real-world heterogeneous mixing of agents [146,147]. Each stock, or compartment, then represents a state. In the simplest configuration, agents move randomly and, if an infected agent is within infection range of a susceptible agent, . after (Figure 6). Such a model can incorporate local knowledge of demographic data, the healthcare system, and human contact networks [24].
- Floods (river flood, storm surge, tsunami—CA): Flood intensity usually refers to the inundation depth . Although depends on the peak discharge and the shape of the valley [148], modeling is required to properly consider the variations in topography. A simple CA can be defined with the following rules:
- Define the absolute height (or motion cost) as the sum of the altitude and water height ;
- Calculate the gradient (or weight) between the central cell and von Neumann neighbor cells (zero weight for neighbors with equal or greater );
- Discharge the central cell with (some of) the water distributed to the neighbor cells, depending on their weight.
The first discharge occurs at the source of the flood, with where is the time interval between two steps and the cell width. The motion cost can include soil characteristics, such as roughness and infiltration potential. The weights for water distribution are a function of the motion cost at the central and neighbor cells [149], which, in the simplest case, is proportional to the normalized gradients. A similar CA strategy can apply to tsunamis [150]. - Landslides (CA): The propagation of a landslide can be modelled as a Sandpile with the environment—or diffuse source—defined by the topography and the soil thickness . The simplest case consists of initiating mass movement in cells of unstable slope, which is defined by (i.e., seed event, see Equation (14)) [151]. The mass is transferred downward to the Moore neighbor of maximum gradient , so thatand with mass movement defined, for example, bywith the maximum slope angle for which . Since increases, can cross the instability threshold, hence further propagating the landslide (Figure 6). Many model variants exist [152,153,154,155]. Note that the landslide source was previously defined as diffuse instead of an area source because part of the soil outside the seed event may participate in landslide propagation (Equation (43)).
- Social unrest (ABM): A simple model of civil violence [35] consists of two types of agents: population and cops. Population agents can be in one of three states (quiet , active , or jailed ). They have a fixed degree of grievance , a fixed degree of risk aversion , and a vision radius . Cops have a vision radius . All agents are also characterized by their location . There are three rules:
- General rule: Move to an empty cell (or where someone is jailed);
- Population rule: If , become active (), otherwise stay quiet ();
- Cop rule: arrest a random active agent located within ()
where is the net risk and a threshold for rebellion.is the arrest probability, which depends on the number of cops and the number of active agents observed within (and with as a normalization constant). For each jailed agent, the jail term is random and uniform in the range , with once released. Due to the form of Equation (45), a contagion process can occur, leading to a large-scale riot [35] whose intensity could, in theory, be defined by the total number of violent individuals . The duration of the riot could be a second measure of hazard intensity. - Terrorist attacks (ABM): Large-scale terrorist attacks generally infer the use of explosives (see above). The choice of location for an attack can be explained by Game Theory, but the modeling of agents is not required. In other types of attacks, such as a group of terrorists attacking civilians with knifes, an ABM can be formulated. Ref. [156], for example, combined the effect of such an attack with the risk of stampede in a closed environment. Terrorists search targets in their radius of vision, while civilians attempt to flee with direction and speed depending on the amount of blood lost and collisions with other agents. Variants are too numerous to mention any specific model in the context of this review.
- Wildfires (incl. urban fires, CA): The so-called Forest Fire model is defined by four rules:
- An empty space fills with a tree with probability (i.e., tree growth);
- A tree ignites due to a lightning strike of probability ;
- A tree burns if at least one von Neumann neighbor is burning;
- A burning cell turns into an empty cell.
3. Peril Harmonization via the Concept of Energy Transfer
| Peril | Event Size (Section 2.2) → Intensity (Section 2.4) | Matching Energy Types |
|---|---|---|
| Armed conflicts | Various, so far aggregated in terms of loss (Equation (38)) | Various, aggregation TBD 1 |
| Asteroid impacts | Kinetic energy (Equation (2)) → overpressure (Equation (28)) | Motion → wave (air) (+radiant, thermal) |
| Blackouts | E.g., unsupplied electrical energy (Equation (40)) | Electrical (lack of) |
| Business interruption | Revenue loss | Work done (lack of) |
| Crop failures | So far in terms of farming production yield loss (Equation (41)) | Chemical (food) (lack of) |
| Cyber-attacks | E.g., number of data breaches | Stored information (lack of) |
| Earthquakes | Magnitude (Equations (7) and (8)) → PGA (Equation (29)) | Mechanical (elastic) → wave (seismic) |
| Epidemics | Infection count (Equation (42)) | TBD 1 |
| Explosions (nuclear) | Explosive yield (Equation (4)) → overpressure (Equation (30)) | Nuclear → wave (air) (+radiant, thermal) |
| Explosions (other) | TNT mass (Equation (3)) → overpressure (Equation (30)) | Chemical → wave (air) (+thermal) |
| Floods | Discharge (Equations (5) and (37)) → water depth | Motion + gravitational → gravitational (+motion) |
| Hail | Hailstone diameter → kinetic energy (Equation (35)) | Gravitational → motion |
| Heatwaves | Temperature | Thermal |
| Landslides | Area or volume → soil height | Gravitational → gravitational (+motion) |
| Social unrest | Number of violent individuals as possible proxy | Various (thermal via arson, mechanical) |
| Storms | Windspeed (Equation (12)) → Equation (32)) | Motion (+water latent heat) → motion |
| Tsunamis | Potential energy (Equation (10)) → Water height | Gravitational → wave (water) (+motion) |
| Volcanic eruptions | Erupted volume → ash depth (Equation (33)) | Thermal → gravitational (+thermal) |
| Wildfires (incl. urban) | Burnt area | Thermal (+radiant) |
4. Conclusions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A
| Symbol | Dimension | Description |
|---|---|---|
| various | Productivity parameter of the power-law | |
| [L2] | Area | |
| [1] | Power-law exponent in cumulative form () | |
| [1] | Holland parameter for tropical cyclones | |
| [1] | Empirical parameter, scaling factor | |
| [ML−1T−2] | Soil cohesion | |
| [L] | Distance | |
| [1] | Damage, e.g., mean damage ratio | |
| [1] | Euler’s number () | |
| [ML2T−2] | Energy | |
| - | Damage function | |
| - | Intensity function | |
| - | Frequency function | |
| [1] | Factor of safety for landslides | |
| [LT−2] | Gravitational acceleration ( m/s2) | |
| [L] | Height, depth | |
| various | Intensity of event | |
| [L] | Length, diameter | |
| various | Loss (e.g., economic, human) | |
| [M] | Mass | |
| [1] | Magnitude of earthquake | |
| [ML2T−2] | Seismic moment | |
| [1] | Number, count | |
| [ML−1T−2] | Pressure, overpressure | |
| [1] | Probability (non-cumulative, cumulative) | |
| [L3T−1] | Water discharge | |
| [L] | Radius, radial distance | |
| [1] | Epidemic basic reproduction number | |
| various | Size of event | |
| [T] | Time increment | |
| [Q] | Temperature | |
| [L] | Displacement | |
| [LT−1] | Velocity | |
| [L3] | Volume | |
| [L] | Width | |
| [L] | Geographical coordinates | |
| various | Random variable | |
| various | Electricity load | |
| [1] | Power-law exponent () | |
| [T−1] | Infectious disease transmission parameter | |
| [L] | Thickness | |
| [L2T−2] | Heat of combustion | |
| [T] | Return period, time interval | |
| [1] | Eccentricity | |
| [1] | in GPD | |
| [1] | Fraction, ratio | |
| various | Parameter set | |
| [T−1] | Rate of occurrence | |
| various | GEV and GPD location parameter | |
| [1] | GEV and GPD shape parameter | |
| [ML−3] | Density | |
| various | GEV and GPD scale parameter | |
| [T] | Time | |
| [1] | Angle | |
| various | Characteristics of an agent | |
| - | State of an agent | |
| various | Threshold |
| Color | Category | Perils |
|---|---|---|
| ■ | Climatological | Heatwave |
| ■/■1 | Ecological | Crop failure, epidemic, wildfire |
| ■ | Extraterrestrial | Asteroid and comet impact |
| ■ | Geophysical | Earthquake, landslide, volcanic eruption |
| ■ | Hydrological | River flood, storm surge, tsunami |
| ■ | Meteorological | Convective storm (incl. hail, tornado, lightning), (extra-)tropical cyclone, other storms |
| ■ | Socio-economic | Armed conflict, social unrest, terrorism |
| ■ | Technological | Blackout, cyber-attack, explosion, fire |
References
- Friedman, D.G. Natural Hazard Risk Assessment for an Insurance Program. Geneva Pap. Risk Insur. 1984, 9, 57–128. [Google Scholar] [CrossRef]
- Grossi, P.; Kunreuther, H.; Patel, C.C. Catastrophe Modeling: A New Approach to Managing Risk; Springer: Boston, MA, USA, 2005. [Google Scholar]
- Smolka, A. Natural disasters and the challenge of extreme events: Risk management from an insurance perspective. Phil. Trans. R. Soc. A 2006, 364, 2147–2165. [Google Scholar] [CrossRef] [PubMed]
- Mitchell-Wallace, K.; Jones, M.; Hillier, J.; Foote, M. Natural Catastrophe Risk Management and Modelling, A Practitioner’s Guide; John Wiley & Sons Ltd.: Chichester, UK, 2017. [Google Scholar]
- Crichton, D. The Risk Triangle. In Natural Disaster Management; Ingleton, J., Ed.; Tudor Rose: London, UK, 1999; pp. 102–103. [Google Scholar]
- Mailier, P.J.; Stephenson, D.B.; Ferro, C.A.T. Serial Clustering of Extratropical Cyclones. Mon. Weather Rev. 2006, 134, 2224–2240. [Google Scholar] [CrossRef]
- Matos, J.P.; Mignan, A.; Schleiss, A.J. Vulnerability of large dams considering hazard interactions, Conceptual application of the Generic Multi-Risk framework. In Proceedings of the 13th ICOLD Benchmark Workshop on the Numerical Analysis of Dams, Lausanne, Switzerland, 9–11 September 2015. [Google Scholar]
- Mignan, A.; Danciu, L.; Giardini, D. Considering large earthquake clustering in seismic risk analysis. Nat. Hazards 2018, 91, S149–S172. [Google Scholar] [CrossRef]
- Douglas, J. Physical vulnerability modelling in natural hazard risk assessment. Nat. Hazards Earth Syst. Sci. 2007, 7, 283–288. [Google Scholar] [CrossRef]
- Grünthal, G.; Thieken, A.H.; Schwarz, J.; Radtke, K.S.; Smolka, A.; Merz, B. Comparative Risk Assessments for the City of Cologne—Storms, Floods, Earthquakes. Nat. Hazards 2006, 38, 21–44. [Google Scholar] [CrossRef]
- Schneider, P.J.; Schauer, B.A. HAZUS—Its Development and Ist Future. Nat. Haz. Rev. 2006, 7, 40–44. [Google Scholar] [CrossRef]
- Schmidt, J.; Matcham, I.; Reese, S.; King, A.; Bell, R.; Henderson, R.; Smart, G.; Cousins, J.; Smith, W.; Heron, D. Quantitative multi-risk analysis for natural hazards: A framework for multi-risk modelling. Nat. Hazards 2011, 58, 1169–1192. [Google Scholar] [CrossRef]
- Cardona, O.D.; Ordaz, M.G.; Yamin, L.E.; Marulanda, M.C.; Barbat, A.H. Earthquake Loss Assessment for Integrated Disaster Risk Management. J. Earthq. Eng. 2008, 12 (Suppl. S2), 48–59. [Google Scholar] [CrossRef]
- Tseng, C.-P.; Chen, C.-W. Natural disaster management mechanisms for probabilistic earthquake loss. Nat. Hazards 2012, 60, 1055–1063. [Google Scholar] [CrossRef]
- Vickery, P.J.; Masters, F.J.; Powell, M.D.; Wadhera, D. Hurricane hazard modeling: The past, present, and future. J. Wind Eng. Ind. Aerodyn. 2009, 97, 392–405. [Google Scholar] [CrossRef]
- Aznar-Signan, G.; Bresch, D.N. CLIMADA v1: A global weather and climate risk assessment platform. Geosci. Model Dev. 2019, 12, 3085–3097. [Google Scholar] [CrossRef]
- Ermolieva, T.; Filatova, T.; Ermoliev, Y.; Obersteiner, M.; de Bruijn, K.M.; Jenken, A. Flood Catastrophe Model for Designing Optimal Flood Insurance Program: Estimating Location-Specific Premiums in the Netherlands. Risk Anal. 2017, 37, 82–98. [Google Scholar] [CrossRef]
- Palán, L.; Matyás, M.; Válková, M.; Kovacka, V.; Pazourková, E.; Puncochár, P. Accessing Insurance Flood Losses Using a Catastrophe Model and Climate Change Scenarios. Climate 2022, 10, 67. [Google Scholar] [CrossRef]
- Hohl, R.; Schiesser, H.-H.; Knepper, I. The use of weather radars to estimate hail damage to automobiles: An exploratory study in Switzerland. Atmos. Res. 2002, 61, 215–238. [Google Scholar] [CrossRef]
- Romanic, D.; Refan, M.; Wu, C.-H.; Michel, G. Oklahoma tornado risk and variability: A statistical model. Int. J. Disaster Risk Reduct. 2016, 16, 19–32. [Google Scholar] [CrossRef]
- Eling, M.; Schnell, W. What do we know about cyber risk and cyber risk insurance? J. Risk Financ. 2016, 17, 474–491. [Google Scholar] [CrossRef]
- Coburn, A.; Leverett, E.; Woo, G. Solving Cyber Risk; John Wiley & Sons: Hoboken, NJ, USA, 2019. [Google Scholar]
- Fullam, D.; Madhav, N. Quantifying Pandemic Risk. Actuar. Mag. 2015, 12, 29–34. [Google Scholar]
- Smith, D. Pandemic Risk Modelling. In The Palgrave Handbook of Unconventional Risk Transfer; Pompella, M., Scordis, N.A., Eds.; Palgrave Macmillan Cham: London, UK, 2017; pp. 463–495. [Google Scholar]
- Woo, G. Quantitative Terrorism Risk Assessment. J. Risk Financ. 2002, 4, 7–14. [Google Scholar] [CrossRef]
- Kunreuther, H.; Michel-Kerjan, E.; Porter, B. Chapter 10—Extending Catastrophe Modeling To Terrorism. In Catastrophe Modeling: A New Approach to Managing Risk; Grossi, P., Kunreuther, H., Patel, C.C., Eds.; Springer: Boston, MA, USA, 2005; pp. 209–233. [Google Scholar]
- Murnane, R.J. Catastrophe Risk Models for Wildfires in the Wildland-Urban Interface: What Insurers Need. Nat. Hazards Rev. 2006, 7, 150–156. [Google Scholar] [CrossRef]
- Lee, S.; Davidson, R.; Ohnishi, N.; Scawthorn, C. Fire Following Earthquake—Reviewing the State-of-the-Art of Modeling. Earthq. Spectra 2008, 24, 933–967. [Google Scholar] [CrossRef]
- Muir-Wood, R.; Drayton, M.; Berger, A.; Burgess, P.; Wright, T. Catastrophe loss modelling of storm-surge flood risk in eastern England. Phil. Trans. R. Soc. A 2005, 363, 1407–1422. [Google Scholar] [CrossRef] [PubMed]
- Rose, A.; Huyck, C.K. Improving Catastrophe Modeling for Business Interruption Insurance Needs. Risk Anal. 2016, 36, 1896–1915. [Google Scholar] [CrossRef] [PubMed]
- Tomlinson, C.J.; Chapman, L.; Thornes, J.E.; Baker, C.J. Including the urban heat island in spatial heat health risk assessment strategies: A case study for Birmingham, UK. Int. J. Health Geogr. 2011, 10, 42. [Google Scholar] [CrossRef]
- Tonnang, H.E.; Hervé, B.D.; Biber-Freudenberger, L.; Salifu, D.; Subramanian, S.; Ngowi, V.B.; Guimapi, R.Y.; Anani, B.; Kakmeni, F.M.; Affognon, H.; et al. Advances in crop insect modelling methods—Towards a whole system approach. Ecol. Model. 2017, 354, 88–103. [Google Scholar] [CrossRef]
- Mignan, A.; Grossi, P.; Muir-Wood, R. Risk assessment of Tunguska-type airbursts. Nat. Hazards 2011, 56, 869–880. [Google Scholar] [CrossRef][Green Version]
- Mathias, D.L.; Wheeler, L.F.; Dotson, J.L. A probabilistic asteroid impact risk model: Assessment of sub-300 m impacts. Icarus 2017, 289, 106–119. [Google Scholar] [CrossRef]
- Epstein, J.M. Modeling civil violence: An agent-based computational approach. Proc. Natl. Acad. Sci. USA 2002, 99, 7243–7250. [Google Scholar] [CrossRef]
- Kress, M. Modeling Armed Conflicts. Science 2012, 336, 865–869. [Google Scholar] [CrossRef]
- Beck, U. The Terrorist Threat, World Risk Society Revisited. Theory Cult. Soc. 2002, 19, 39–55. [Google Scholar] [CrossRef]
- Center for Near Earth Object Studies, Fireball and Bolide Data. Available online: https://cneos.jpl.nasa.gov/fireballs/ (accessed on 31 August 2022).
- Clauset, A.; Shalizi, C.R.; Newman, M.E.J. Power-Law Distributions in Empirical Data. SIAM Rev. 2009, 51, 661–703. [Google Scholar] [CrossRef]
- Privacy Rights, Data Breaches. Available online: https://privacyrights.org/data-breaches (accessed on 31 August 2022).
- Storchak, D.A.; Di Giacomo, D.; Bondár, I.; Engdahl, E.R.; Harris, J.; Lee, W.H.K.; Villasenor, A.; Bormann, P. Public Release of the ISC-GEM Global Instrumental Earthquake Catalogue (1900-2009). Seismol. Res. Lett. 2013, 84, 810–815. [Google Scholar] [CrossRef]
- Woessner, J.; The SHARE Consortium; Laurentiu, D.; Giardini, D.; Crowley, H.; Cotton, F.; Grünthal, G.; Valensise, G.; Arvidsson, R.; Basili, R.; et al. The 2013 European Seismic Hazard Model: Key components and results. Bull. Earthq. Eng. 2015, 13, 3553–3596. [Google Scholar] [CrossRef]
- Marani, M.; Katul, G.G.; Pan, W.K.; Parolari, A.J. Intensity and frequency of extreme novel epidemics. Proc. Natl. Acad. Sci. USA 2021, 118, e2105482118. [Google Scholar] [CrossRef]
- Météo-France, Données Publiques. Available online: https://donneespubliques.meteofrance.fr/ (accessed on 31 August 2022).
- Li, G.; West, A.J.; Densmore, A.L.; Jin, Z.; Parker, R.N.; Hilton, R.G. Seismic mountain building: Landslides associated with the 2008 Wenchuan earthquake in the context of a generalized model for earthquake volume balance. Geochem. Geophys. Geosyst. 2014, 15, 833–844. [Google Scholar] [CrossRef]
- Smith, J.A. Estimating the Upper Tail of Flood Frequency Distributions. Water Resour. Res. 1987, 23, 1657–1666. [Google Scholar] [CrossRef]
- Clauset, A.; Young, M.; Gleditsch, K.S. On the Frequency of Severe Terrorist Events. J. Confl. Resolut. 2007, 51, 58–87. [Google Scholar] [CrossRef]
- Knapp, K.R.; Kruk, M.C.; Levinson, D.H.; Diamond, H.J.; Neumann, C.J. The International Best Track Archive for Climate Stewardship (IBTrACS), Unifying Tropical Cyclone Data. Bull. Am. Meteo. Soc. 2010, 91, 363–376. [Google Scholar] [CrossRef]
- National Geophysical Data Center / World Data Service: NCEI/WDS Global Historical Tsunami Database. In NOAA National Centers for Environmental Information. Available online: https://www.ngdc.noaa.gov/hazard/tsu_db.shtml (accessed on 31 August 2022). [CrossRef]
- Crosweller, H.S.; Arora, B.; Brown, S.; Cottrell, E.; Deligne, N.; Guerrero, N.O.; Hobbs, L.; Kiyosugi, K.; Loughlin, S.; Lowndes, J.; et al. Global database on large magnitude explosive volcanic eruptions (LaMEVE). J. Appl. Volc. 2012, 1, 4. [Google Scholar] [CrossRef]
- Laurent, P.; Mouillot, F.; Yue, C.; Ciais, P.; Moreno, M.V.; Nogueira, J.M.P. Data Descriptor: FRY, a global database of fire patch functional traits derived from space-borne burned area products. Sci. Data 2018, 5, 180132. [Google Scholar] [CrossRef]
- Hills, J.G.; Goda, M.P. The Fragmentation of Small Asteroids in the Atmosphere. Astron. J. 1993, 105, 1114–1144. [Google Scholar] [CrossRef]
- Bland, P.A.; Artemieva, N.A. The rate of small impacts on Earth. Meteorit. Planet. Sci. 2006, 41, 607–631. [Google Scholar] [CrossRef]
- Maremonti, M.; Russo, G.; Salzano, E.; Tufano, V. Post-Accident Analysis of Vapour Cloud Explosions in Fuel Storage Areas. Trans. IChemE 1999, 77, 360–365. [Google Scholar] [CrossRef]
- Ottemöller, L.; Evers, L.G. Seismo-acoustic analysis of the Buncefield oil depot explosion in the UK, 2005 December 11. Geophys. J. Int. 2008, 172, 1123–1134. [Google Scholar] [CrossRef]
- Abbasi, T.; Abbasi, S.A. The boiling liquid expanding vapour explosion (BLEVE): Mechanism, consequence assessment, management. J. Hazard. Mater. 2007, 141, 489–519. [Google Scholar] [CrossRef]
- Alileche, N.; Cozzani, V.; Reniers, G.; Estel, L. Thresholds for domino effects and safety distances in the process industry: A review of approaches and regulations. Reliab. Eng. Syst. Saf. 2015, 143, 74–84. [Google Scholar] [CrossRef]
- Mignan, A.; Spada, M.; Burgherr, P.; Wang, Z.; Sornette, D. Dynamics of severe accidents in the oil & gas energy sector derived from the authoritative Energy-related severe accident database. PLoS ONE 2022, 17, e0263962. [Google Scholar]
- Reed, B.C. A toy model for the yield of a tamped fission bomb. Am. J. Phys. 2018, 86, 105–109. [Google Scholar] [CrossRef]
- Grimaldi, S.; Petroselli, A. Do we still need the Rational Formula? An alternative empirical procedure for peak discharge estimation in small and ungauged basins. Hydrol. Sci. J. 2015, 60, 67–77. [Google Scholar] [CrossRef]
- Gericke, O.J.; Smithers, J.C. Review of methods used to estimate catchment response time for the purpose of peak discharge estimation. Hydrol. Sci. J. 2014, 59, 1935–1971. [Google Scholar] [CrossRef]
- Meigh, J.R.; Farquharson, F.A.K.; Sutcliffe, J.V. A worldwide comparison of regional flood estimation methods and climate. Hydrol. Sci. J. 1997, 42, 225–244. [Google Scholar] [CrossRef]
- Newhall, C.G.; Self, S. The Volcanic Explosivity Index (VEI): An Estimate of Explosive Magnitude for Historical Volcanism. J. Geophys. Res. 1982, 87, 1231–1238. [Google Scholar] [CrossRef]
- Pyle, D.M. Mass and energy budgets of explosive volcanic eruptions. Geophys. Res. Lett. 1995, 22, 563–566. [Google Scholar] [CrossRef]
- Hanks, T.C.; Kanamori, H. A Moment Magnitude Scale. J. Geophys. Res. 1979, 84, 2348–2350. [Google Scholar] [CrossRef]
- Wells, D.L.; Coppersmith, K.J. New Empirical Relationships among Magnitude, Rupture Length, Rupture Width, Rupture Area, and Surface Displacement. Bull. Seismol. Soc. Am. 1994, 84, 974–1002. [Google Scholar]
- Lin, N.; Emanuel, K.A.; Smith, J.A.; Vanmarcke, E. Risk assessment of hurricane storm surge for New York City. J. Geophys. Res. 2010, 115, D18121. [Google Scholar] [CrossRef]
- Camelo, J.; Mayo, T. The lasting impacts of the Saffir-Simpson Hurricane Wind Scale on storm surge risk communication: The need for multidisciplinary research in addressing a multidisciplinary challenge. Weather Clim. Extrem. 2021, 33, 100335. [Google Scholar] [CrossRef]
- Edwards, R.; DaDue, J.G.; Ferree, J.T.; Scharfenberg, K.; Maier, C.; Coulbourne, W.L. Tornado Intensity Estimation, Past, Present, and Future. Bull. Am. Meteo. Soc. 2013, 94, 641–653. [Google Scholar] [CrossRef]
- Standohar-Alfano, C.D.; van de Lindt, J.W. Empirically Based Probabilistic Tornado Hazard Analysis of the United States Using 1973–2011 Data. Nat. Hazards Rev. 2015, 16, 04014013. [Google Scholar] [CrossRef]
- Halif, M.N.A.; Sabki, S.N. The Physics of Tsunami: Basic understanding of the Indian Ocean disaster. Am. J. Appl. Sci. 2005, 2, 1188–1193. [Google Scholar] [CrossRef]
- Ghasemi, S. Study of Tsunamis by Dimensional Analysis. Engineering 2011, 3, 905–910. [Google Scholar] [CrossRef]
- Rigby, S.E.; Lodge, T.J.; Alotaibi, S.; Barr, A.D.; Clarke, S.D.; Langdon, G.S.; Tyas, A. Preliminary yield estimation of the 2020 Beirut explosion using video footage from social media. Shock Waves 2020, 30, 671–675. [Google Scholar] [CrossRef]
- Hering, A.M.; Germann, U.; Boscacci, M.; Sénési, S. Operational nowcasting of thunderstorms in the Alps during MAP D-PHASE. In Proceedings of the 5th European Conference on Radar in Meteorology and Hydrology, Helsinki, Finland, 30 June–4 July 2008. [Google Scholar]
- Rothermal, R.C. Predicting Fire Spread in Wildland Fuels. USDA For. Serv. Res. Pap. 1972, INT-115, 1–40. [Google Scholar]
- Trunfio, G.A. Predicting Wildfire Spreading Through a Hexagonal Cellular Automata Model. In ACRI 2004, LNCS 3305; Sloot, P.M.A., Chopard, B., Hoekstra, A.G., Eds.; Springer: Berlin, Germany, 2004; pp. 385–394. [Google Scholar]
- Bloemendaal, N.; Haigh, I.D.; de Moel, H.; Muis, S.; Haarsma, R.J.; Aerts, J.C.J.H. Generation of a global synthetic tropical cyclone hazard dataset using STORM. Sci. Data 2020, 7, 40. [Google Scholar] [CrossRef]
- Holland, G.J. An Analytic Model of the Wind and Pressure Profiles in Hurricanes. Mon. Weather Rev. 1982, 108, 1212–1218. [Google Scholar] [CrossRef]
- Emanuel, K.A. The power of a hurricane: An example of reckless driving on the information superhighway. Weather 1998, 54, 107–108. [Google Scholar] [CrossRef]
- Andersson, G.; Donalek, P.; Farmer, R.; Hatziargyriou, N.; Kamwa, I.; Kundur, N.; Martins, J.; Paserba, P.; Pourbeik, J.; Sanchez-Gasca, R.; et al. Causes of the 2003 Major Grid Blackouts in North America and Europe, and Recommended Means to Improve System Dynamic Performance. IEEE Trans. Power Syst. 2005, 20, 1922–1928. [Google Scholar] [CrossRef]
- Crosta, G. Regionalization of rainfall thresholds: An aid to landslide hazard evaluation. Env. Geol. 1998, 35, 131–145. [Google Scholar] [CrossRef]
- Iverson, R.M. Landslide triggering by rain infiltration. Water Res. Res. 2000, 36, 1897–1910. [Google Scholar] [CrossRef]
- Jibson, R.W. Predicting Earthquake-Induced Landslide Displacements Using Newmark’s Sliding Block Analysis. Transp. Res. Rec. 1993, 1411, 9–17. [Google Scholar]
- McPhail, C.; Wohlstein, R.T. Individual and Collective Behaviors within Gatherings, Demonstrations, and Riots. Ann. Rev. Sociol. 1983, 9, 579–600. [Google Scholar] [CrossRef]
- Atiyeh, B.S.; Gunn, S.W.A.; Hayek, S.N. Military and civilian burn injuries during armed conflicts. Ann. Burn. Fire Disasters 2007, XX, 203–215. [Google Scholar]
- Syphard, A.D.; Keeley, J.E. Location, timing and extent of wildfire vary by cause of ignition. Int. J. Wildland Fire 2015, 24, 37–47. [Google Scholar] [CrossRef]
- Krause, A.; Kloster, S.; Wilkenskjeld, S.; Paeth, H. The sensitivity of global wildfires to simulated past, present, and future lightning frequency. J. Geophys. Res. Biogeosci. 2014, 119, 312–322. [Google Scholar] [CrossRef]
- Price, C.; Rind, D. A Simple Lightning Parameterization for Calculating Global Lightning Distributions. J. Geophys. Res. 1992, 97, 9919–9933. [Google Scholar] [CrossRef]
- Littell, J.S.; Peterson, D.L.; Riley, K.L.; Liu, Y.; Luce, C.H. A review of the relationships between drought and forest fire in the United States. Glob. Chang. Biol. 2016, 22, 2353–2369. [Google Scholar] [CrossRef]
- Molina, J.R.; Martín, T.; Silva, F.R.Y.; Herrera, M.Á. The ignition index based on flammability of vegetation improves planning in the wildland-urban interface: A case study in Southern Spain. Landsc. Urban Plan. 2017, 158, 129–138. [Google Scholar] [CrossRef]
- Newman, M.E.J. Power laws, Pareto distributions and Zipf’s law. Contemp. Phys. 2005, 46, 323–351. [Google Scholar] [CrossRef]
- Corral, Á.; González, Á. Power law size distributions in geoscience revisited. Earth Space Sci. 2019, 6, 673–697. [Google Scholar] [CrossRef]
- Coles, S. An Introduction to Statistical Modeling of Extreme Values; Springer: London, UK, 2001. [Google Scholar]
- Harris, I. Generalised Pareto methods for wind extremes. Useful tool or mathematical mirage? J. Wind Eng. 2005, 93, 341–360. [Google Scholar] [CrossRef]
- Malamud, B.D.; Turcotte, D.L. The applicability of power-law frequency statistics to floods. J. Hydro. 2006, 322, 168–180. [Google Scholar] [CrossRef]
- Chen, L.; Guo, S. Copulas and Its Applications in Hydrology and Water Resources; Springer Nature: Singapore, 2019. [Google Scholar]
- Richardson, L.F. Variation of the Frequency of Fatal Quarrels With Magnitude. J. Am. Stat. Assoc. 1948, 43, 523–546. [Google Scholar] [CrossRef]
- Cederman, L.-E. Modeling the Size of Wars: From Billiard Balls to Sandpiles. Am. Political Sci. Rev. 2003, 97, 135–150. [Google Scholar] [CrossRef]
- Brown, P.; Spalding, R.E.; ReVelle, D.O.; Tagliaferri, E.; Worden, S.P. The flux of small near-Earth objects colliding with the Earth. Nature 2002, 420, 294–296. [Google Scholar] [CrossRef]
- Dobson, I.; Carreras, B.A.; Lynch, V.E.; Newman, D.E. Complex systems analysis of series of blackouts: Cascading failure, critical points, and self-organization. Chaos 2007, 17, 026103. [Google Scholar] [CrossRef]
- Maillart, T.; Sornette, D. Heavy-tailed distribution of cyber-risks. Eur. Phys. J. B 2010, 75, 357–364. [Google Scholar] [CrossRef]
- Utsu, T. Representation and Analysis of the Earthquake Size Distribution: A Historical Review and Some New Approaches. Pure Appl. Geophys. 1999, 155, 509–535. [Google Scholar] [CrossRef]
- Gutenberg, B.; Richter, C.F. Frequency of Earthquakes in California. Bull. Seismol. Soc. Am. 1944, 34, 185–188. [Google Scholar] [CrossRef]
- Malamud, B.D.; Turcotte, D.L.; Guzzetti, F.; Reichenbach, P. Landslides, earthquakes, and erosion. Earth Planet. Sci. Lett. 2004, 229, 45–59. [Google Scholar] [CrossRef]
- Van Den Eeckhaut, M.; Poesen, J.; Govers, G.; Verstraeten, G.; Demoulin, A. Characteristics of the size distribution of recent and historical landslides in a populated hilly region. Earth Planet. Sci. Lett. 2007, 256, 588–603. [Google Scholar] [CrossRef]
- Xu, C.; Xu, X.; Yao, X.; Dai, F. Three (nearly) complete inventories of landslides triggered by the May 12, 2008 Wenchuan Mw 7.9 earthquake of China and their spatial distribution statistical analysis. Landslides 2014, 11, 441–461. [Google Scholar] [CrossRef]
- Burroughs, S.M.; Tebbens, S.F. Power-law Scaling and Probabilistic Forecasting of Tsunami Runup Heights. Pure Appl. Geophys. 2005, 162, 331–342. [Google Scholar] [CrossRef]
- Newhall, C.; Self, S.; Robock, A. Anticipating future Volcanic Explosivity Index (VEI) 7 eruptions and their chilling impacts. Geosphere 2018, 14, 572–603. [Google Scholar] [CrossRef]
- Cui, W.; Perera, A.H. What do we know about forest fire size distribution, and why is this knowledge useful for forest management? Int. J. Wildland Fire 2008, 17, 234–244. [Google Scholar] [CrossRef]
- Gilleland, E.; Katz, R.W. extRemes 2.0: An Extreme Value Analysis Package in R. J Stat. Soft. 2016, 72, 1–39. [Google Scholar] [CrossRef]
- Katz, R.W.; Parlange, M.B.; Naveau, P. Statistics of extremes in hydrology. Adv. Water Resour. 2002, 25, 1287–1304. [Google Scholar] [CrossRef]
- Morrison, J.E.; Smith, J.A. Stochastic modelling of flood peaks using the generalized extreme value distribution. Water Resour. Res. 2002, 38, 1305. [Google Scholar] [CrossRef]
- Jagger, T.H.; Elsner, J.B. Climatology Models for Extreme Hurricane Winds near the United States. J. Clim. 2006, 19, 3220–3236. [Google Scholar] [CrossRef]
- Della-Marta, P.M.; Mathis, H.; Frei, C.; Liniger, M.A.; Kleinn, J.; Appenzeller, C. The return period of wind storms over Europe. Int. J. Climatol. 2009, 29, 437–459. [Google Scholar] [CrossRef]
- Hofherr, T.; Kunz, M. Extreme wind climatology of winter storms in Germany. Clim. Res. 2010, 41, 105–123. [Google Scholar] [CrossRef][Green Version]
- Malmstadt, J.C.; Elsner, J.B.; Jagger, T.H. Risk of Strong Hurricane Winds to Florida Cities. J. Appl. Meteo. Clim. 2010, 49, 2121–2132. [Google Scholar] [CrossRef]
- Bath, M. The energies of seismic body waves and surface waves. Contr. Geophys. 1958, 1, 1–16. [Google Scholar]
- Glasstone, S.; Dolan, P.J. The Effects of Nuclear Weapons, 3rd ed.; US Department of Defense and Department of Energy: Washington, DC, USA, 1977.
- Ambraseys, N.N.; Simpson, K.A.; Bommer, J.J. Prediction of Horizontal Response Spectra in Europe. Earthq. Eng. Struct. Dyn. 1996, 25, 371–400. [Google Scholar] [CrossRef]
- Youngs, R.R.; Chiou, S.-J.; Silva, W.J.; Humphrey, J.R. Strong Ground Motion Attenuation Relationships for Subduction Zone Earthquakes. Seismol. Res. Lett. 1997, 68, 58–73. [Google Scholar] [CrossRef]
- Douglas, J.; Edwards, B. Recent and future developments in earthquake ground motion estimation. Earth-Sci. Rev. 2016, 160, 203–219. [Google Scholar] [CrossRef]
- Ambraseys, N.N.; Bommer, J.J. The attenuation of ground accelerations in Europe. Earthq. Eng. Struct. Dyn. 1991, 20, 1179–1202. [Google Scholar] [CrossRef]
- Mills, C. The design of concrete structures to resist explosions and weapon effects. In Proceedings of the 1st International Conference on Concrete for Hazard Protections, Edinburgh, UK, 27–30 September 1987. [Google Scholar]
- Holland, A.P.; Riordan, A.J.; Franklin, E.C. A Simple Model for Simulating Tornado Damage in Forests. J. App. Meteo. Climatol. 2006, 45, 1597–1611. [Google Scholar] [CrossRef]
- Willoughby, H.E.; Darling, R.W.R.; Rahn, M.E. Parametric Representation of the Primary Hurricane Vortex. Part II: A New Family of Sectionally Continuous Profiles. Mon. Weather Rev. 2006, 134, 1102–1120. [Google Scholar] [CrossRef]
- Vickery, P.J.; Wadhera, D. Statistical Models of Holland Pressure Profile Parameter and Radius to Maximum Winds of Hurricanes from Flight-Level Pressure and H*Wind Data. J. Appl. Meteo. Climatol. 2008, 47, 2497–2517. [Google Scholar] [CrossRef]
- Pyle, D.M. The Thickness, volume and grainsize of tephra fall deposits. Bull. Volcanol. 1989, 51, 1–15. [Google Scholar] [CrossRef]
- Grieser, J.; Hill, M. How to Express Hail Intensity—Modeling the Hailstone Size Distribution. J. Appl. Meteo. Climatol. 2019, 58, 2329–2345. [Google Scholar] [CrossRef]
- Sherwood, S.C.; Huber, M. An adaptability limit to climate change due to heat stress. Proc. Natl. Acad. Sci. USA 2010, 107, 9552–9555. [Google Scholar] [CrossRef]
- Stull, R. Wet-Bulb Temperature from Relative Humidity and Air Temperature. J. Appl. Meteo. Climatol. 2011, 50, 2267–2269. [Google Scholar] [CrossRef]
- Ramirez, J.A.; Lichter, M.; Coulthard, T.J.; Skinner, C. Hyper-resolution mapping of regional storm surge and tide flooding: Comparison of static and dynamic models. Nat. Hazards 2016, 82, 571–590. [Google Scholar] [CrossRef]
- Bak, P.; Tang, C.; Wiesenfeld, K. Self-Organized Criticality: An Explanation of 1/f Noise. Phys. Rev. Lett. 1987, 59, 381–384. [Google Scholar] [CrossRef]
- Kermack, W.O.; McKendrick, A.G. A Contribution to the Mathematical Theory of Epidemics. Proceed. R. Soc. A 1927, 115, 700–721. [Google Scholar]
- Kress, M. Lanchester Models for Irregular Warfare. Mathematics 2020, 8, 737. [Google Scholar] [CrossRef]
- MacKay, N.J. When Lanchester Met Richardson, the Outcome Was Stalemate: A Parable for Mathematical Models of Insurgency. In OR, Defence and Security; Forder, R.A., Ed.; Palgrave Macmillan: London, UK, 2015; pp. 124–147. [Google Scholar]
- Ilachinski, A. Irreducible Semi-Autonmous Adaptive Combat (ISAAC): An Artificial-Life Approach to Land Combat. Mil. Oper. Res. 2000, 5, 29–46. [Google Scholar] [CrossRef]
- Epstein, J.M. Agent-Based Computational Models And Generative Social Science. Complexity 1999, 4, 41–60. [Google Scholar] [CrossRef]
- Sachtjen, M.L.; Carreras, B.A.; Lynch, V.E. Disturbances in a power transmission system. Phys. Rev. E 2000, 61, 4877–4882. [Google Scholar] [CrossRef]
- Lotka, A.J. Contribution to the Theory of Periodic Reactions. J. Phys. Chem. 1910, 14, 271–274. [Google Scholar] [CrossRef]
- Volterra, V. Variations and Fluctuations of the Number of Individuals in Animal Species living together. ICES J. Mar. Sci. 1928, 3, 3–51. [Google Scholar] [CrossRef]
- Ludwig, D.; Jones, D.D.; Holling, C.S. Qualitative Analysis of Insect Outbreak Systems: The Spruce Budworm and Forest. J. Anim. Ecol. 1978, 47, 315–332. [Google Scholar] [CrossRef]
- Eling, M. Cyber risk research in business and actuarial science. Eur. Actuar. J. 2020, 10, 303–333. [Google Scholar] [CrossRef]
- Liu, W.; Zhong, S. Web malware spread modelling and optimal control strategies. Sci. Rep. 2017, 7, 42308. [Google Scholar] [CrossRef]
- Hethcore, H.W. The Mathematics of Infectious Diseases. SIAM Rev. 2000, 42, 599–653. [Google Scholar] [CrossRef]
- Wang, Z.; Broccardo, M.; Mignan, A.; Sornette, D. The dynamics of entropy in the COVID-19 outbreaks. Nonlinear Dyn. 2020, 101, 1847–1869. [Google Scholar] [CrossRef]
- Rahmandad, H.; Sterman, J. Heterogeneity and Network Structure in the Dynamics of Diffusion: Comparing Agent-Based and Differential Equation Models. Manag. Sci. 2008, 54, 998–1014. [Google Scholar] [CrossRef]
- Epstein, J.M. Modelling to contain pandemics. Nature 2009, 460, 687. [Google Scholar] [CrossRef]
- Merz, B.; Elmer, F.; Thicken, A.H. Significance of “High probability/low damage” versus “low probability/high damage” flood events. Nat. Hazards Earth Syst. Sci. 2009, 9, 1033–1046. [Google Scholar] [CrossRef]
- Issermann, M.; Chang, F.-J.; Jia, H. Efficient Urban Inundation Model for Live Flood Forecasting with Cellular Automata and Motion Cost Fields. Water 2020, 12, 1997. [Google Scholar] [CrossRef]
- Mohamed, E.S.; Rajasekaran, S. Tsunami Wave Simulation Models Based on Hexagonal Cellular Automata. WSEAS Transac. Fluid Mech. 2013, 8, 91–101. [Google Scholar]
- Piegari, E.; Cataudella, V.; Di Maio, R.; Milano, L.; Nicodemi, M. A cellular automaton for the factor of safety field in landslides modeling. Geophys. Res. Lett. 2006, 33, L01403. [Google Scholar] [CrossRef]
- Segre, E.; Deangeli, C. Cellular automaton for realistic modelling of landslides. Nonlinear Proc. Geophys. 1995, 2, 1–15. [Google Scholar] [CrossRef]
- Di Gregorio, S.; Rongo, R.; Siciliano, C.; Sorriso-Valvo, M.; Spataro, W. Mount Ontake Landslide Simulation by the Cellular Automata Model SCIDDICA-3. Phys. Chem. Earth 1999, 24, 131–137. [Google Scholar] [CrossRef]
- Guthrie, R.H.; Deadman, P.J.; Cabrera, A.R.; Evans, S.G. Exploring the magnitude-frequency distribution: A cellular automata model for landslides. Landslides 2008, 5, 151–159. [Google Scholar] [CrossRef]
- Avolio, M.V.; Di Gregorio, S.; Lupiano, V.; Mazzanti, P. SCIDDICA-SS3: A new version of cellular automata model for simulating fast moving landslides. J. Supercomput. 2013, 65, 682–696. [Google Scholar] [CrossRef]
- Lu, P.; Zhang, Z.; Li, M.; Chen, D.; Yang, H. Agent-based modeling and simulations of terrorist attacks combined with stampedes. Knowl.-Based Syst. 2020, 205, 106291. [Google Scholar] [CrossRef]
- Clarke, K.C.; Brass, J.A.; Riggan, P.J. A Cellular Automaton Model of Wildfire Propagation and Extinction. Photogramm. Eng. Remote Sens. 1994, 60, 1355–1367. [Google Scholar]
- Alexandridis, A.; Vakalis, D.; Siettos, C.I.; Bafas, G.V. A cellular automata model for forest fire spread prediction: The case of the wildfire that swept through Spetses Island in 1990. Appl. Math. Comput. 2008, 204, 191–201. [Google Scholar] [CrossRef]
- Trunfio, G.A.; D’Ambrosio, D.; Rongo, R.; Spataro, W.; Di Gregorio, S. A New Algorithm for Simulating Wildfire Spread through Cellular Automata. ACM Trans. Model. Comput. Simul. 2011, 22, 6. [Google Scholar] [CrossRef]
- Liu, Y.; Kochanski, A.; Baker, K.R.; Mell, W.; Linn, R.; Paugam, R.; Mandel, J.; Fournier, A.; Jenkins, M.A.; Goodrick, S.; et al. Fire behaviour and smoke modelling: Model improvement and measurement needs for next-generation smoke research and forecasting systems. Int. J. Wildland Fire 2019, 28, 570–588. [Google Scholar] [CrossRef]
- Fang, P.; Ye, G.; Yu, H. A parametric wind field model and its application in simulating historical typhoons in the western North Pacific Ocean. J. Wind Eng. Ind. Aerodyn. 2020, 199, 104131. [Google Scholar] [CrossRef]
- Fournier, A.; Fussell, D.; Carpenter, L. Computer Rendering of Stochastic Models. Comm. ACM 1982, 25, 371–384. [Google Scholar] [CrossRef]
- Woo, G. Calculating Catastrophe; Imperial College Press: London, UK, 2011. [Google Scholar]
- Johnston, A.C. An earthquake strength scale for the media and the public. Earthq. Volcanoes 1990, 22, 214–216. [Google Scholar]
- Malamud, B.D.; Morein, G.; Turcotte, D.L. Forest Fires: An Example of Self-Organized Critical Behavior. Science 1998, 281, 1840–1842. [Google Scholar] [CrossRef]
- Turcotte, D.L.; Malamud, B.D. Landslides, forest fires, and earthquakes: Examples of self-organized critical behavior. Physica A 2004, 340, 580–589. [Google Scholar] [CrossRef]
- Dincer, I.; Dost, S. Energy and GDP. Int. J. Energy Res. 1997, 21, 153–167. [Google Scholar] [CrossRef]
- Kreibich, H.; Piroth, K.; Seifert, I.; Maiwald, H.; Kunert, U.; Schwarz, J.; Merz, B.; Thicken, A.H. Is flow velocity a significant parameter in flood damage modelling? Nat. Hazards Earth Syst. Sci. 2009, 9, 1679–1692. [Google Scholar] [CrossRef]
- Tribus, M.; McIrvine, E.C. Energy and Information. Sci. Am. 1971, 225, 179–190. [Google Scholar] [CrossRef]
- Koski, J.V.; Maisi, V.F.; Pekola, J.P.; Averin, D.V. Experimental realization of a Szilard engine with a single electron. Proc. Natl. Acad. Sci. USA 2014, 111, 13786–13789. [Google Scholar] [CrossRef]
- Wooster, M.J.; Zhukov, B.; Oertel, D. Fire radiative energy for quantitative study of biomass burning: Derivation from the BIRD experimental satellite and comparison to MODIS fire products. Remote Sens. Environ. 2003, 86, 83–107. [Google Scholar] [CrossRef]
- Mignan, A.; Wiemer, S.; Giardini, D. The quantification of low-probability–high-consequences events: Part I. A generic multi-risk approach. Nat. Hazards 2014, 73, 1999–2022. [Google Scholar] [CrossRef]
- Mignan, A.; Wang, Z. Exploring the Space of Possibilities in Cascading Disasters with Catastrophe Dynamics. Int. J. Environ. Res. Public Health 2020, 17, 7317. [Google Scholar] [CrossRef]
- Bloemendaal, N.; de Moel, H.; Martinez, A.B.; Muis, S.; Haigh, I.D.; van der Wiel, K.; Haarsma, R.J.; Ward, P.J.; Roberts, M.J.; Dullaart, J.C.M.; et al. A globally consistent local-scale assessment of future tropical cyclone risk. Sci. Adv. 2022, 8, eabm8438. [Google Scholar] [CrossRef]
- Randers, J.; Golüke, U.; Wenstop, F.; Wenstop, S. A user-friendly earth system model of low complexity: The ESCIMO system dynamics model of global warming towards 2100. Earth Syst. Dynam. 2016, 7, 831–850. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mignan, A. Categorizing and Harmonizing Natural, Technological, and Socio-Economic Perils Following the Catastrophe Modeling Paradigm. Int. J. Environ. Res. Public Health 2022, 19, 12780. https://doi.org/10.3390/ijerph191912780
Mignan A. Categorizing and Harmonizing Natural, Technological, and Socio-Economic Perils Following the Catastrophe Modeling Paradigm. International Journal of Environmental Research and Public Health. 2022; 19(19):12780. https://doi.org/10.3390/ijerph191912780
Chicago/Turabian StyleMignan, Arnaud. 2022. "Categorizing and Harmonizing Natural, Technological, and Socio-Economic Perils Following the Catastrophe Modeling Paradigm" International Journal of Environmental Research and Public Health 19, no. 19: 12780. https://doi.org/10.3390/ijerph191912780
APA StyleMignan, A. (2022). Categorizing and Harmonizing Natural, Technological, and Socio-Economic Perils Following the Catastrophe Modeling Paradigm. International Journal of Environmental Research and Public Health, 19(19), 12780. https://doi.org/10.3390/ijerph191912780