Smartphone Addiction and Cybercrime Victimization in the Context of Lifestyles Routine Activities and Self-Control Theories: The User’s Dual Vulnerability Model of Cybercrime Victimization
Abstract
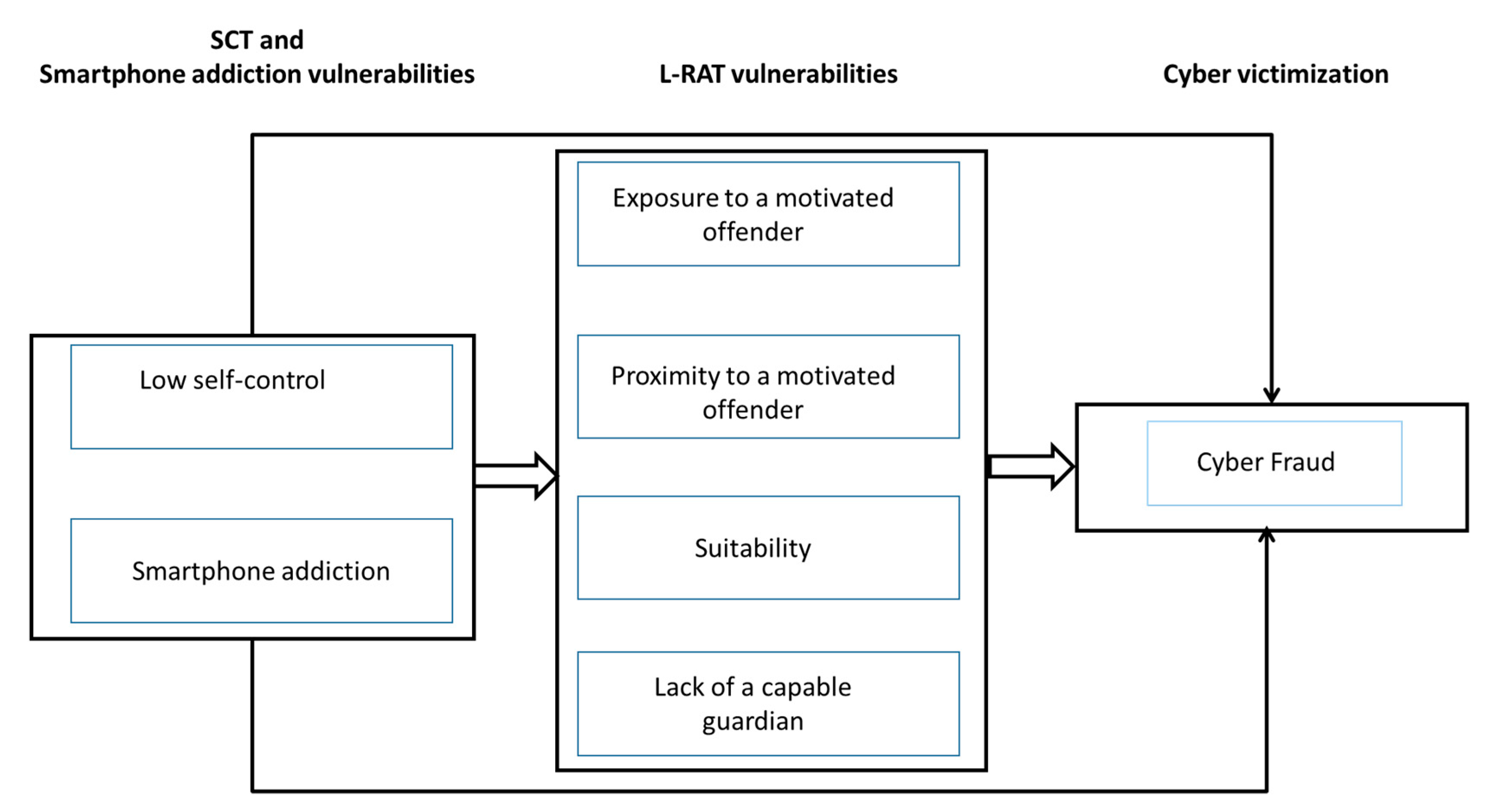
1. Introduction
Literature Review
2. Materials and Methods
2.1. Participants
2.2. Materials
2.2.1. Dependent Variable
2.2.2. Covariates
2.2.3. Control Variables
2.2.4. Statistical Analyses
3. Results
4. Discussion
Strengths and Limitations
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Becker, G.S. Crime and punishment: An economic approach. In Economic Analysis of the Law; Blackwell Publishing Ltd.: Oxford, UK, 2007; pp. 255–265. [Google Scholar]
- Cohen, L.E.; Felson, M. Social change and crime rate trends: A routine activity approach. Am. Sociol. Rev. 1979, 44, 588–608. [Google Scholar] [CrossRef]
- Cohen, L.E.; Kluegel, J.R.; Land, K.C. Social inequality and predatory criminal victimization: An exposition and test of a formal theory. Am. Sociol. Rev. 1981, 46, 505–524. [Google Scholar] [CrossRef]
- Hindelang, M.J.; Gottfredson, M.R.; Garofalo, J. Victims of Personal Crime: An. Empirical Foundation for a Theory of Personal Victimization; Ballinger: Cambridge, MA, USA, 1978. [Google Scholar]
- Gottfredson, M.R.; Hirschi, T. A General Theory of Crime; Stanford University Press: Palo Alto, CA, USA, 1990. [Google Scholar]
- Schreck, C.J. Criminal victimization and low self-control: An extension and test of a general theory of crime. Justice Q. 1999, 16, 633–654. [Google Scholar] [CrossRef]
- Pratt, T.C.; Turanovic, J.J.; Fox, K.A.; Wright, K.A. Self-control and victimization: A meta-analysis: Self-control and victimization. Criminology 2014, 52, 87–116. [Google Scholar] [CrossRef]
- Akdemir, N.; Lawless, C.J. Exploring the human factor in cyber-enabled and cyber-dependent crime victimisation: A lifestyle routine activities approach. Internet Res. 2020, 30, 1665–1687. [Google Scholar] [CrossRef]
- Whitty, M.T. Predicting susceptibility to cyber-fraud victimhood. J. Financ Crime 2019, 26, 277–292. [Google Scholar] [CrossRef]
- Wilcox, P.; Cullen, F.T. Situational opportunity theories of crime. Annu. Rev. Criminol. 2018, 1, 123–148. [Google Scholar] [CrossRef]
- Busch, P.A.; McCarthy, S. Antecedents and consequences of problematic smartphone use: A systematic literature review of an emerging research area. Comput. Human. Behav. 2021, 114, 106414. [Google Scholar] [CrossRef]
- Al-Kandari, Y.Y.; Al-Sejari, M.M. Social isolation, social support and their relationship with smartphone addiction. Inf. Commun. Soc. 2020, 1–19. [Google Scholar] [CrossRef]
- Lapierre, M.A.; Zhao, P. Smartphones and social support: Longitudinal associations between smartphone use and types of support. Soc. Sci. Comput. Rev. 2021. [Google Scholar] [CrossRef]
- Williams, M.L. Guardians upon high: An application of routine activities theory to online identity theft in Europe at the country and individual level. Br. J. Criminol. 2016, 56, 21–48. [Google Scholar] [CrossRef]
- Reyns, B.W.; Henson, B. The thief with a thousand faces and the victim with none: Identifying determinants for online identity theft victimization with routine activity theory. Int. J. Offender Ther. Comp. Criminol. 2016, 60, 1119–1139. [Google Scholar] [CrossRef] [PubMed]
- Wilson, S.J.; Maclean, R.R. Associations between self-control and dimensions of nicotine dependence: A preliminary report. Addict. Behav. 2013, 38, 1812–1815. [Google Scholar] [CrossRef] [PubMed]
- Herrero, J.; Urueña, A.; Torres, A.; Hidalgo, A. Socially connected but still isolated: Smartphone addiction decreases social support over time. Soc. Sci. Comput. Rev. 2019, 37, 73–88. [Google Scholar] [CrossRef]
- Herrero, J.; Torres, A.; Vivas, P.; Urueña, A. Smartphone addiction and social support: A three-year longitudinal study. Interv Psicosoc. 2019, 28, 111–118. [Google Scholar] [CrossRef]
- Herrero, J.; Urueña, A.; Torres, A.; Hidalgo, A. Smartphone addiction: Psychosocial correlates, risky attitudes, and smartphone harm. J. Risk Res. 2017, 22, 1–12. [Google Scholar] [CrossRef]
- Urueña López, A.; Mateo, F.; Navío-Marco, J.; Martínez-Martínez, J.M.; Gómez-Sanchís, J.; Vila-Francés, J.; Serrano-López, A. Analysis of computer user behavior, security incidents and fraud using Self-Organizing Maps. Comput. Secur. 2019, 83, 38–51. [Google Scholar] [CrossRef]
- Van de Weijer, S.G.A.; Leukfeldt, E.R. Big five personality traits of cybercrime victims. Cyberpsychol. Behav. Soc. Netw. 2017, 20, 407–412. [Google Scholar] [CrossRef] [PubMed]
- Jensen-Campbell, L.A.; Knack, J.M.; Waldrip, A.M.; Campbell, S.D. Do Big Five personality traits associated with self-control influence the regulation of anger and aggression? J. Res. Pers. 2007, 41, 403–424. [Google Scholar] [CrossRef]
- Rammstedt, B.; John, O.P. Measuring personality in one minute or less: A 10-item short version of the Big Five Inventory in English and German. J. Res. Pers. 2007, 41, 203–212. [Google Scholar] [CrossRef]
- Zhang, G.; Chen, X.; Xiao, L.; Li, Y.; Li, B.; Yan, Z.; Guo, L.; Rost, D.H. The relationship between Big Five and self-control in boxers: A mediating model. Front. Psychol. 2019, 10, 1690. [Google Scholar] [CrossRef] [PubMed]
- Bian, M.; Leung, L. Linking loneliness, shyness, smartphone addiction symptoms, and patterns of smartphone use to social capital. Soc. Sci. Comput. Rev. 2015, 33, 61–79. [Google Scholar] [CrossRef]
- Young, K.S. Internet addiction: The emergence of a new clinical disorder. Cyberpsychol. Behav. 1998, 1, 237–244. [Google Scholar] [CrossRef]
- Strahan, R.; Gerbasi, K.C. Short, homogeneous versions of the marlow-crowne social desirability scale. J. Clin. Psychol. 1972, 28, 191–193. [Google Scholar] [CrossRef]
- Crowne, D.P.; Marlowe, D. A new scale of social desirability independent of psychopathology. J. Consult. Psychol. 1960, 24, 349–354. [Google Scholar] [CrossRef] [PubMed]
- Bentler, P.M. EQS 6 Structural Equations Program Manual; Multivariate Software, Inc.: Encino, CA, USA, 2006. [Google Scholar]
- Preacher, K.J.; Kelley, K. Effect size measures for mediation models: Quantitative strategies for communicating indirect effects. Psychol. Methods 2011, 16, 93–115. [Google Scholar] [CrossRef] [PubMed]
- Muthén, L.K.; Muthén, B.O. Mplus User’s Guide, 8th ed.; Muthén & Muthén: Los Angeles, CA, USA, 1998. [Google Scholar]
- Kim, J.; Hong, H.; Lee, J.; Hyun, M.-H. Effects of time perspective and self-control on procrastination and Internet addiction. J. Behav. Addict. 2017, 6, 229–236. [Google Scholar] [CrossRef] [PubMed]
- Burt, C.H. Self-control and crime: Beyond gottfredson & hirschi’s theory. Annu. Rev. Criminol. 2020, 3, 43–73. [Google Scholar] [CrossRef]
- Maloney, P.W.; Grawitch, M.J.; Barber, L.K. The multi-factor structure of the brief self-control scale: Discriminant validity of restraint and impulsivity. J. Res. Pers. 2012, 46, 111–115. [Google Scholar] [CrossRef]
- Perrone, D.; Sullivan, C.J.; Pratt, T.C.; Margaryan, S. Parental efficacy, self-control, and delinquency: A test of a general theory of crime on a nationally representative sample of youth. Int. J. Offender Ther. Comp. Criminol. 2004, 48, 298–312. [Google Scholar] [CrossRef] [PubMed]
- Piquero, A.R.; MacIntosh, R.; Hickman, M. Does self-control affect survey response? Applying exploratory, confirmatory, and item response theory analysis to Grasmick et al.’s self-control scale. Criminology 2000, 38, 897–930. [Google Scholar] [CrossRef]
- Guerra, C.; Ingram, J.R. Assessing the relationship between lifestyle routine activities theory and online victimization using panel data. Deviant. Behav. 2020, 1–17. [Google Scholar] [CrossRef]
- Copersino, M.L. Cognitive mechanisms and therapeutic targets of addiction. Curr. Opin. Behav. Sci. 2017, 13, 91–98. [Google Scholar] [CrossRef] [PubMed]
- Nigg, J.T. Annual Research Review: On the relations among self-regulation, self-control, executive functioning, effortful control, cognitive control, impulsivity, risk-taking, and inhibition for developmental psychopathology. J. Child. Psychol. Psychiatry 2017, 58, 361–383. [Google Scholar] [CrossRef] [PubMed]
- Stautz, K.; Zupan, Z.; Field, M.; Marteau, T.M. Does self-control modify the impact of interventions to change alcohol, tobacco, and food consumption? A systematic review. Health Psychol. Rev. 2018, 12, 157–178. [Google Scholar] [CrossRef] [PubMed]
- Herrero, J.; Torres, A.; Vivas, P.; Arenas, A.; Urueña, A. Examining the empirical links between digital social pressure, personality, psychological distress, social support, users’ residential living conditions, and smartphone addiction. Soc. Sci. Comput. Rev. 2021. [Google Scholar] [CrossRef]
| Cyber Fraud | ||||
|---|---|---|---|---|
| Variables | Direct Effects (Odds Ratio) 1 | Direct Effects (Stand. Coefficient) 1 | Indirect Effects | Total Effects |
| L-RAT | ||||
| Exposure | 1.12 [1.01, 1.25] | 0.06 [0.01, 0.10] | - | 0.06 [0.01, 0.10] |
| Proximity | 1.42 [1.29, 1.57] | 0.17 [0.12, 21] | - | 0.17 [0.12, 21] |
| Suitability | 1.34 [1.21, 1.47] | 0.15 [0.10, 0.20] | - | 0.15 [0.10, 0.20] |
| Guardian | 0.88 [0.80, 0.98] | −0.07 [−0.13, −0.01] | - | −0.07 [−0.13, −0.01] |
| SCT2 Agreeableness Conscientiousness | 0.80 [0.67, 0.95] 0.67 [0.57, 0.78] | −0.08 [−0.14, −0.02] −0.15 [−0.21, −0.10] | 0.01 [0.00, 0.02] −0.01 [−0.02, 0.00] | −0.07 [−0.13, −0.01] −0.16 [−0.22, −0.11] |
| Smartphone addiction2 | 1.20 [1.16, 1.26] | 0.20[0.16, 0.25] | 0.05 [0.04, 0.07] | 0.25 [0.22, 0.30] |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Herrero, J.; Torres, A.; Vivas, P.; Hidalgo, A.; Rodríguez, F.J.; Urueña, A. Smartphone Addiction and Cybercrime Victimization in the Context of Lifestyles Routine Activities and Self-Control Theories: The User’s Dual Vulnerability Model of Cybercrime Victimization. Int. J. Environ. Res. Public Health 2021, 18, 3763. https://doi.org/10.3390/ijerph18073763
Herrero J, Torres A, Vivas P, Hidalgo A, Rodríguez FJ, Urueña A. Smartphone Addiction and Cybercrime Victimization in the Context of Lifestyles Routine Activities and Self-Control Theories: The User’s Dual Vulnerability Model of Cybercrime Victimization. International Journal of Environmental Research and Public Health. 2021; 18(7):3763. https://doi.org/10.3390/ijerph18073763
Chicago/Turabian StyleHerrero, Juan, Andrea Torres, Pep Vivas, Antonio Hidalgo, Francisco J. Rodríguez, and Alberto Urueña. 2021. "Smartphone Addiction and Cybercrime Victimization in the Context of Lifestyles Routine Activities and Self-Control Theories: The User’s Dual Vulnerability Model of Cybercrime Victimization" International Journal of Environmental Research and Public Health 18, no. 7: 3763. https://doi.org/10.3390/ijerph18073763
APA StyleHerrero, J., Torres, A., Vivas, P., Hidalgo, A., Rodríguez, F. J., & Urueña, A. (2021). Smartphone Addiction and Cybercrime Victimization in the Context of Lifestyles Routine Activities and Self-Control Theories: The User’s Dual Vulnerability Model of Cybercrime Victimization. International Journal of Environmental Research and Public Health, 18(7), 3763. https://doi.org/10.3390/ijerph18073763






