Revisiting Wireless Cyberattacks on Vehicles
Abstract
1. Introduction
2. Radio-Frequency Tools
2.1. Hardware
- HackRF One [23] (versions r1 through r10), from Great Scott Gadgets, is a half-duplex transceiver that operates at frequencies from 1 MHz to 6 GHz and can reach a rate of 20 million samples per second. With HackRF One and the appropriate software, the real-time frequency spectrum can be visualized. Moreover, it allows us to capture and replay signals.
- There is another device from Great Scott Gadgets, known as YARD Stick One [24], that accepts different types of digital modulations (ASK/OOK, GFSK, 2FSK, 4FSK, MSK) and rates of up to 500 kbps. This gadget can be used to capture and decode signals, and to generate synthetic signals from binary information.
- Proxmark 3 RDV4 [25] is a tool designed mainly for RFID analysis and research. It allows for testing, sniffing, replaying, and cloning devices such as RFID tags or Mifare Classic cards. Proxmark can be used to analyze immobilizers, which usually work as an RFID device. It can also be used to assess vehicles that have a PKES system to lock/unlock the car and even to start the engine, such as Tesla.
2.2. Software
- To interact with a HackRF One gadget, GNU Radio Companion [26] is a good option, which is a project that provides a graphical programming environment based on signal processing blocks for interacting with software-defined radio (SDR) devices.
- GQRX [27] is a program based on GNU Radio Companion that displays the frequency spectrum in a waterfall model and is able to apply signal processing to received radio signals. It can be used to identify the working frequency of a given key fob with HackRF One.
- inspectrum [28] is software that displays the power of a signal in time and frequency. It is used to analyze signal capture files and extract their characteristics and even encoded symbols as bits.
- Universal Radio Hacker [29] is a project that encompasses the previous functionalities: it can be used to send and receive radio signals, but also to analyze their encoded information.
- rfcat [30] (version 2.0.1) is a Python 3 library dedicated to the use of YARD Stick One.
3. State of the Art
3.1. Remote Keyless Entry
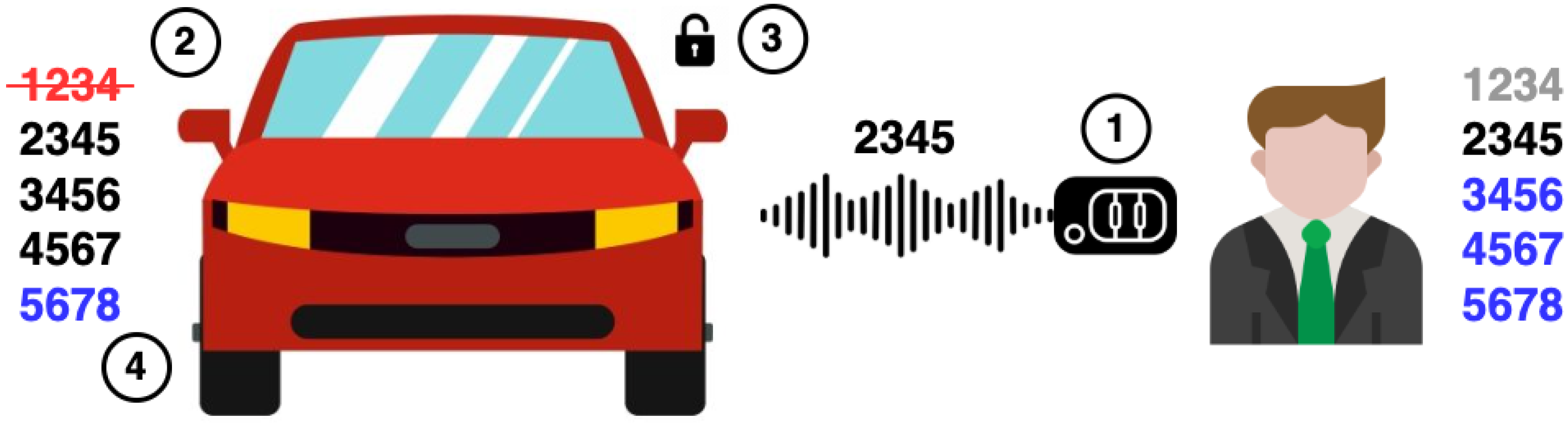
3.1.1. Replay Attacks
3.1.2. RollJam Attack
3.1.3. RollBack Attack
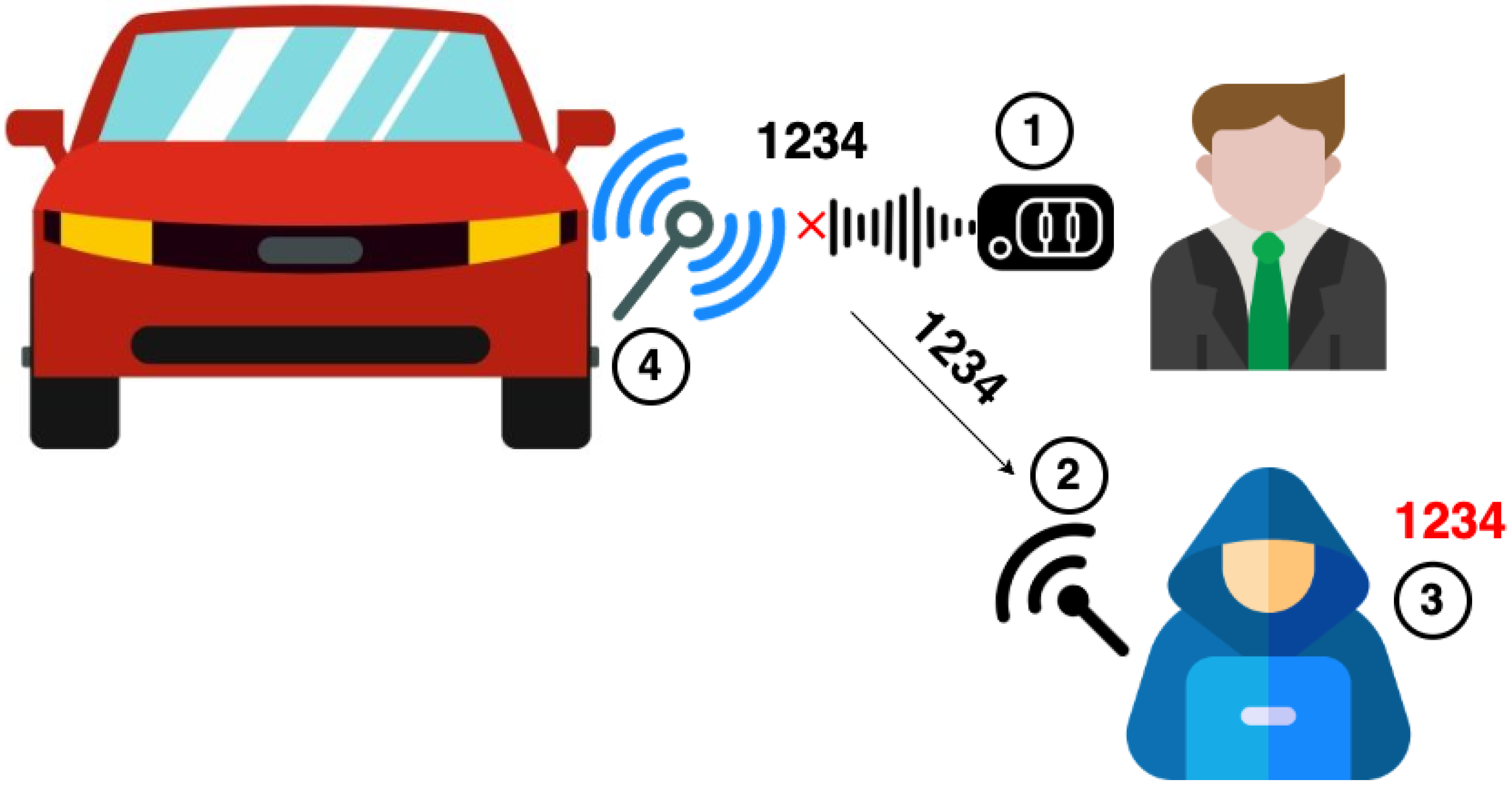
3.2. Passive Keyless Entry and Start
Relay Attacks
3.3. Immobilizer
3.4. Tire-Pressure Monitoring System
- It can be used to track a certain vehicle, because it is an automatic protocol and difficult to deactivate.
- TPMS signals can be easily jammed or spoofed, because they use radio-frequency communications. It could lead to false dashboard warnings.
3.5. Bluetooth
3.6. Global Positioning System
4. Research Gaps
- Risk assessment: The risks and impact of automobiles need to be measured. On the one hand, new regulations force manufacturers to pass cybersecurity tests [3]. On the other hand, insurance companies must take this variable into account when defining the policy. Although risk assessment in the automotive sector is very complex, some approximations using well-known frameworks can be found in [64].
- Supply chain: The automotive industry employs a complex supply chain to source the components that are used to build new vehicles, provide services and perform repairs. This supply chain poses a huge risk to the industry, since each connected endpoint is a vulnerability waiting to happen [65]. It is a fact that the security of individual components does not ensure the security of the whole system.
- Reverse engineering: Vehicle manufacturers will never publicly disclose any source code or detailed specification for the products they build. For this reason, researchers must utilize their reverse-engineering skills to extract ECUs firmware and analyze compiled artifacts from closed-source microprocessors, for example. Others might want to analyze radio signals or discover logic bugs in state-machine systems.
- Cryptography: On the one hand, there are protocols like RKE, PKES, and TPMS that still lack robustness. Modern cryptographic schemes must be considered, such as lightweight cryptography [66]. On the other hand, for devices that have no strict computational power limitation, post-quantum algorithms are preferred to prevent traditional algorithms to be broken with quantum computers.
- Mitigations: While there is research about vulnerabilities and methods to compromise vehicular technologies, there must also be research about how to defend from these techniques and protect the affected systems.
- Software security: Modern cars are equipped with many features that improve the user experience and comfort. However, these new systems integrated in the car, such as operating systems or web browsers, must be analyzed. Manufacturers should follow best practices and continuous integration with quality assurance to prevent bugs and errors in their codebase.
- V2X communications: With the advances on technology, image processing, robotics and artificial intelligence, there habe been a lot of studies on autonomous vehicles. These vehicles must communicate with each other (V2V) and with other entities (V2X). Standards are still being designed [67]. As a result, there is a need to protect these communications from the design phase, because they can be critical for human safety. Modern post-quantum cryptographic protocols are taken into consideration for this application, as shown in [68,69,70].
- Digital twins: Digital twins are a cutting-edge approach to enhance vehicle security by creating virtual replicas of automotive systems and simulation environments [71]. In this context, security and privacy issues can be analyzed using a digital twin rather than a real vehicle [72]. This can help finding vulnerabilities and testing communication protocols [73], or even charging protocols for electric vehicles [74].
- Artificial Intelligence and Machine Learning: AI can improve threat and anomaly detection, and intrusion prevention in connected and autonomous vehicles [75]. Machine learning models can analyze vast amounts of real-time data to identify potential attacks before they cause any damage. Although training these models requires large, diverse datasets, AI can also generate synthetic data, which enables researchers to create simulation environments for a wide range of cyberattacks and rare threat scenarios [76]. Simulations allow for the continuous testing and validation of security measures in a controlled environment. This approach accelerates the development of automotive cybersecurity and ensures safety in future intelligent transportation systems.
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- UNECE. UN Regulation No. 155—Cyber Security and Cyber Security Management System; UNECE: Geneva, Switzerland, 2021. [Google Scholar]
- UNECE. UN Regulation No. 156—Software Update and Software Update Management System; UNECE: Geneva, Switzerland, 2021. [Google Scholar]
- Girdhar, M.; Hong, J.; Moore, J. Cybersecurity of Autonomous Vehicles: A Systematic Literature Review of Adversarial Attacks and Defense Models. IEEE Open J. Veh. Technol. 2023, 4, 417–437. [Google Scholar] [CrossRef]
- Car Hacking Village. Available online: https://www.carhackingvillage.com (accessed on 22 January 2025).
- Enabling Positive Security Solutions for the Automotive Market. Available online: https://asrg.io (accessed on 22 January 2025).
- Driving Automotive Cybersecurity Forward. Available online: https://vicone.com (accessed on 22 January 2025).
- Pwn2Own Automotive. Available online: https://vicone.com/pwn2own-automotive (accessed on 22 January 2025).
- Valasek, C.; Miller, C. A Survey of Remote Automotive Attack Surfaces; Technical Report; IOActive: Seattle, WA, USA, 2018. [Google Scholar]
- Black Hat USA 2015: The Full Story of How That Jeep Was Hacked. Available online: https://www.kaspersky.com/blog/blackhat-jeep-cherokee-hack-explained/9493/ (accessed on 18 May 2023).
- Miller, D.C.; Valasek, C. Remote Exploitation of an Unaltered Passenger Vehicle; Technical Report; IOActive: Seattle, WA, USA, 2015. [Google Scholar]
- Kamkar, S. Drive It Like You Hacked It: New Attacks and Tools to Wirelessly Steal Cars. DEF CON 23. Available online: https://defcon.org/html/defcon-23/dc-23-speakers.html#Kamkar (accessed on 22 December 2024).
- Valdes-Dapena, P. Some Auto Insurers Are Refusing to Cover Certain Hyundai and Kia Models. Available online: https://edition.cnn.com/2023/01/27/business/progressive-state-farm-hyundai-kia/index.html (accessed on 22 January 2025).
- Pavel Zhovner, A.Z.; Nadyrshin, R. Our Response to the Canadian Government. Available online: https://blog.flipper.net/response-to-canadian-government/ (accessed on 22 January 2025).
- Singh Rathore, R.; Hewage, C.; Kaiwartya, O.; Lloret, J. In-Vehicle Communication Cyber Security: Challenges and Solutions. Sensors 2022, 22, 6679. [Google Scholar] [CrossRef]
- Bozdal, M.; Samie, M.; Jennions, I. A Survey on CAN Bus Protocol: Attacks, Challenges, and Potential Solutions. In Proceedings of the 2018 International Conference on Computing, Electronics & Communications Engineering (iCCECE), Southend, UK, 16–17 August 2018; pp. 201–205. [Google Scholar] [CrossRef]
- Wu, W.; Li, R.; Xie, G.; An, J.; Bai, Y.; Zhou, J.; Li, K. A Survey of Intrusion Detection for In-Vehicle Networks. IEEE Trans. Intell. Transp. Syst. 2020, 21, 919–933. [Google Scholar] [CrossRef]
- Young, C.; Zambreno, J.; Olufowobi, H.; Bloom, G. Survey of Automotive Controller Area Network Intrusion Detection Systems. IEEE Des. Test 2019, 36, 48–55. [Google Scholar] [CrossRef]
- Tindell, K. CAN Injection: Keyless Car Theft. Available online: https://kentindell.github.io/2023/04/03/can-injection/ (accessed on 1 February 2025).
- Palmer, Z. Thieves Are Now Stealing Cars via a Headlight ‘CAN Injection’. Available online: https://www.autoblog.com/carbuying/vehicle-headlight-can-bus-injection-theft-method-update (accessed on 1 February 2025).
- Chowdhury, A.; Karmakar, G.; Kamruzzaman, J.; Jolfaei, A.; Das, R. Attacks on Self-Driving Cars and Their Countermeasures: A Survey. IEEE Access 2020, 8, 207308–207342. [Google Scholar] [CrossRef]
- Sun, X.; Yu, F.R.; Zhang, P. A Survey on Cyber-Security of Connected and Autonomous Vehicles (CAVs). IEEE Trans. Intell. Transp. Syst. 2022, 23, 6240–6259. [Google Scholar] [CrossRef]
- Yoshizawa, T.; Preneel, B. Survey of Security Aspect of V2X Standards and Related Issues. In Proceedings of the 2019 IEEE Conference on Standards for Communications and Networking (CSCN), Virtual, 15–17 December 2019; pp. 1–5. [Google Scholar] [CrossRef]
- HackRF One. Available online: https://greatscottgadgets.com/hackrf/one/ (accessed on 2 July 2022).
- YARD Stick One. Available online: https://greatscottgadgets.com/yardstickone/ (accessed on 2 July 2022).
- Proxmark 3 RDV4. Available online: https://proxmark.com/proxmark-3-hardware/proxmark-3-rdv4 (accessed on 22 January 2025).
- About GNU Radio. Available online: https://www.gnuradio.org/about/ (accessed on 2 July 2022).
- OZ9AEC, A.C. Gqrx SDR—Open Source Software Defined Radio by Alexandru Csete OZ9AEC. Available online: https://gqrx.dk/ (accessed on 22 January 2025).
- Miek/Inspectrum: Radio Signal Analyzer. Available online: https://github.com/miek/inspectrum (accessed on 22 January 2025).
- Pohl, J.; Noack, A. Universal Radio Hacker: A Suite for Analyzing and Attacking Stateful Wireless Protocols. In Proceedings of the 12th USENIX Workshop on Offensive Technologies (WOOT 18), Baltimore, MD, USA, 13–14 August 2018. [Google Scholar]
- Rfcat. Available online: https://github.com/atlas0fd00m/rfcat (accessed on 22 January 2025).
- Ibrahim, O.A.; Hussain, A.M.; Oligeri, G.; Di Pietro, R. Key is in the Air: Hacking Remote Keyless Entry Systems. In Security and Safety Interplay of Intelligent Software Systems; Hamid, B., Gallina, B., Shabtai, A., Elovici, Y., Garcia-Alfaro, J., Eds.; Springer: Cham, Switzerland, 2019; pp. 125–132. [Google Scholar]
- Ghanem, A.; AlTawy, R. Garage Door Openers: A Rolling Code Protocol Case Study. In Proceedings of the 2022 19th Annual International Conference on Privacy, Security & Trust (PST), Fredericton, NB, Canada, 22–24 August 2022; pp. 1–6. [Google Scholar] [CrossRef]
- Ossmann, M. Rapid Radio Reversing. Available online: https://www.blackhat.com/docs/asia-16/materials/asia-16-Ossmann-Rapid-Radio-Reversing-wp.pdf (accessed on 22 January 2025).
- Kendil, S.A. Reverse Engineering a Car Key Fob Signal (Part 1). Available online: https://0x44.cc/radio/2024/03/13/reversing-a-car-key-fob-signal.html (accessed on 2 February 2025).
- Enderlein, R.R. KeeLoq; Technical Report; École Polytechnique Fédérale de Lausanne: Lausanne, Switzerland, 2010. [Google Scholar]
- Verdult, R.; Garcia, F.D.; Balasch, J. Gone in 360 Seconds: Hijacking with Hitag2. In Proceedings of the 21st USENIX Security Symposium (USENIX Security 12), Bellevue, WA, USA, 8–10 August 2012; pp. 237–252. [Google Scholar]
- Hicks, C.; Garcia, F.D.; Oswald, D. Dismantling the AUT64 Automotive Cipher. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2018, 2, 46–69. [Google Scholar] [CrossRef]
- Moradi, A.; Kasper, T. A new remote keyless entry system resistant to power analysis attacks. In Proceedings of the 2009 7th International Conference on Information, Communications and Signal Processing (ICICS), Macau, China, 8–10 December 2009; pp. 1–6. [Google Scholar] [CrossRef]
- Erazo, D. Breaking Learning Codes. Available online: https://media.defcon.org/DEF%20CON%2032/DEF%20CON%2032%20villages/DEF%20CON%2032%20-%20Car%20Hacking%20Village%20-%20Danilo%20Erazo%20-%20How%20I%20discovered%20and%20hacked%20Learning%20Codes%20of%20the%20key%20job%20of%20a%20car%20assembled%20in%20my%20country.pdf (accessed on 22 January 2025).
- van de Beek, S.; Leferink, F. Vulnerability of Remote Keyless-Entry Systems Against Pulsed Electromagnetic Interference and Possible Improvements. IEEE Trans. Electromagn. Compat. 2016, 58, 1259–1265. [Google Scholar] [CrossRef]
- Glocker, T.; Mantere, T.; Elmusrati, M. A protocol for a secure remote keyless entry system applicable in vehicles using symmetric-key cryptography. In Proceedings of the 2017 8th International Conference on Information and Communication Systems (ICICS), Irbid, Jordan, 4–6 April 2017; pp. 310–315. [Google Scholar] [CrossRef]
- Parameswarath, R.P.; Sikdar, B. An Authentication Mechanism for Remote Keyless Entry Systems in Cars to Prevent Replay and RollJam Attacks. In Proceedings of the 2022 IEEE Intelligent Vehicles Symposium (IV), Aachen, Germany, 5–9 June 2022; pp. 1725–1730. [Google Scholar] [CrossRef]
- Csikor, L.; Lim, H.W.; Wong, J.W.; Ramesh, S.; Parameswarath, R.P.; Chan, M.C. RollBack: A New Time-Agnostic Replay Attack Against the Automotive Remote Keyless Entry Systems. ACM Trans. Cyber-Phys. Syst. 2022, 8, 1–25. [Google Scholar] [CrossRef]
- Joo, K.; Choi, W.; Lee, D.H. Hold the Door! Fingerprinting Your Car Key to Prevent Keyless Entry Car Theft. In Proceedings of the 2020 Network and Distributed System Security Symposium, San Diego, CA, USA, 23–26 February 2020. [Google Scholar] [CrossRef]
- Alrabady, A.; Mahmud, S. Some attacks against vehicles’ passive entry security systems and their solutions. IEEE Trans. Veh. Technol. 2003, 52, 431–439. [Google Scholar] [CrossRef]
- Francillon, A.; Danev, B.; Capkun, S. Relay Attacks on Passive Keyless Entry and Start Systems in Modern Cars. In Proceedings of the Network and Distributed System Security Symposium (NDSS), San Diego, CA, USA, 6–9 February 2011; Eidgenössische Technische Hochschule Zürich, Department of Computer Science: Zürich, Switzerland, 2011. [Google Scholar] [CrossRef]
- Wang, J.; Lounis, K.; Zulkernine, M. CSKES: A Context-Based Secure Keyless Entry System. In Proceedings of the 2019 IEEE 43rd Annual Computer Software and Applications Conference (COMPSAC), Milwaukee, WI, USA, 15–19 July 2019; Volume 1, pp. 817–822. [Google Scholar] [CrossRef]
- Greene, K.; Rodgers, D.; Dykhuizen, H.; McNeil, K.; Niyaz, Q.; Shamaileh, K.A. Timestamp-based Defense Mechanism Against Replay Attack in Remote Keyless Entry Systems. In Proceedings of the 2020 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 4–6 January 2020; pp. 1–4. [Google Scholar] [CrossRef]
- Wouters, L.; Herrewegen, J.V.d.; Garcia, F.D.; Oswald, D.; Gierlichs, B.; Preneel, B. Dismantling DST80-based Immobiliser Systems. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2020, 2, 99–127. [Google Scholar] [CrossRef]
- Verdult, R.; Garcia, F.D.; Ege, B. Dismantling Megamos Crypto: Wirelessly Lockpicking a Vehicle Immobilizer. In Proceedings of the Supplement to the Proceedings of 22nd USENIX Security Symposium (Supplement to USENIX Security 15), Washington, DC, USA, 14–17 August 2015; pp. 703–718. [Google Scholar]
- Garcia, F.D.; Oswald, D.; Kasper, T.; Pavlidès, P. Lock It and Still Lose It—On the (in)Security of Automotive Remote Keyless Entry Systems. In Proceedings of the 25th USENIX Conference on Security Symposium, Austin, TX, USA, 10–12 August 2016; pp. 929–944. [Google Scholar]
- Benadjila, R.; Renard, M.; Lopes-Esteves, J.; Kasmi, C. One Car, Two Frames: Attacks on Hitag-2 Remote Keyless Entry Systems Revisited. In Proceedings of the 11th USENIX Conference on Offensive Technologies, Vancouver, BC, Canada, 14–15 August 2017. [Google Scholar]
- Immler, V. Breaking Hitag 2 Revisited. In Proceedings of the Second International Conference on Security, Privacy, and Applied Cryptography Engineering, Berlin/Heidelberg, Germany, 9–12 December 2012; pp. 126–143. [Google Scholar] [CrossRef]
- Verstegen, A.; Verdult, R.; Bokslag, W. Hitag 2 Hell –Brutally Optimizing Guess-and-Determine Attacks. In Proceedings of the 12th USENIX Workshop on Offensive Technologies (WOOT 18), Baltimore, MD, USA, 13–14 August 2018. [Google Scholar]
- Wouters, L.; Marin, E.; Ashur, T.; Gierlichs, B.; Preneel, B. Fast, furious and insecure: Passive keyless entry and start systems in modern supercars. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2019, 2019, 66–85. [Google Scholar] [CrossRef]
- Rouf, I.; Miller, R.; Mustafa, H.; Taylor, T.; Oh, S.; Xu, W.; Gruteser, M.; Trappe, W.; Seskar, I. Security and Privacy Vulnerabilities of In-Car Wireless Networks: A Tire Pressure Monitoring System Case Study. In Proceedings of the 19th USENIX Conference on Security, Denver, CO, USA, 11–13 August 2010; p. 21. [Google Scholar]
- Checkoway, S.; McCoy, D.; Kantor, B.; Anderson, D.; Shacham, H.; Savage, S.; Koscher, K.; Czeskis, A.; Roesner, F.; Kohno, T. Comprehensive Experimental Analyses of Automotive Attack Surfaces. In Proceedings of the 20th USENIX Security Symposium (USENIX Security 11), San Francisco, CA, USA, 8–12 August 2011. [Google Scholar]
- Pham, M.; Xiong, K. A survey on security attacks and defense techniques for connected and autonomous vehicles. Comput. Secur. 2021, 109, 102269. [Google Scholar] [CrossRef]
- Woo, S.; Jo, H.J.; Lee, D.H. A Practical Wireless Attack on the Connected Car and Security Protocol for In-Vehicle CAN. IEEE Trans. Intell. Transp. Syst. 2015, 16, 993–1006. [Google Scholar] [CrossRef]
- Wouters, L.; Gierlichs, B.; Preneel, B. My other car is your car: Compromising the Tesla Model X keyless entry system. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2021, 2021, 149–172. [Google Scholar] [CrossRef]
- Symeonidis, I.; Mustafa, M.A.; Preneel, B. Keyless car sharing system: A security and privacy analysis. In Proceedings of the 2016 IEEE International Smart Cities Conference (ISC2), Trento, Italy, 12–15 September 2016; pp. 1–7. [Google Scholar] [CrossRef]
- Philipsen, S.G.; Andersen, B.; Singh, B. Threats and Attacks to Modern Vehicles. In Proceedings of the 2021 IEEE International Conference on Internet of Things and Intelligence Systems (IoTaIS), Bandung, Indonesia, 23–24 November 2021; pp. 22–27. [Google Scholar] [CrossRef]
- Ferreira, R.; Gaspar, J.; Souto, N.; Sebastião, P. Effective GPS Jamming Techniques for UAVs Using Low-Cost SDR Platforms. In Proceedings of the 2018 Global Wireless Summit (GWS), Chiang Rai, Thailand, 25–28 November 2018; pp. 27–32. [Google Scholar] [CrossRef]
- Wang, Y.; Wang, Y.; Qin, H.; Ji, H.; Zhang, Y.; Wang, J. A Systematic Risk Assessment Framework of Automotive Cybersecurity. Automot. Innov. 2021, 4, 253–261. [Google Scholar] [CrossRef]
- Davies, N. The Top 8 Cybersecurity Threats Facing the Automotive Industry Heading into 2023. Available online: https://cybersecurity.att.com/blogs/security-essentials/the-top-8-cybersecurity-threats-facing-the-automotive-industry-heading-into-2023 (accessed on 20 May 2024).
- Lightweight Cryptography. Available online: https://www.nist.gov/programs-projects/lightweight-cryptography (accessed on 16 May 2024).
- C-V2X Explained. Available online: https://5gaa.org/c-v2x-explained (accessed on 22 January 2025).
- Yoshizawa, T.; Preneel, B. Post-Quantum Impacts on V2X Certificates—Already at The End of The Road. In Proceedings of the 2023 IEEE 97th Vehicular Technology Conference (VTC2023-Spring), Florence, Italy, 20–23 June 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Abdel Hakeem, S.A.; Kim, H. Authentication and encryption protocol with revocation and reputation management for enhancing 5G-V2X security. J. King Saud Univ.-Comput. Inf. Sci. 2023, 35, 101638. [Google Scholar] [CrossRef]
- Lonc, B.; Aubry, A.; Bakhti, H.; Christofi, M.; Mehrez, H.A. Feasibility and Benchmarking of Post-Quantum Cryptography in the Cooperative ITS Ecosystem. In Proceedings of the 2023 IEEE Vehicular Networking Conference (VNC), Istanbul, Turkey, 26–28 April 2023; pp. 215–222. [Google Scholar] [CrossRef]
- Hu, Z.; Lou, S.; Xing, Y.; Wang, X.; Cao, D.; Lv, C. Review and Perspectives on Driver Digital Twin and Its Enabling Technologies for Intelligent Vehicles. IEEE Trans. Intell. Veh. 2022, 7, 417–440. [Google Scholar] [CrossRef]
- Ali, W.A.; Fanti, M.P.; Roccotelli, M.; Ranieri, L. A Review of Digital Twin Technology for Electric and Autonomous Vehicles. Appl. Sci. 2023, 13, 5871. [Google Scholar] [CrossRef]
- He, C.; Luan, T.H.; Lu, R.; Su, Z.; Dong, M. Security and Privacy in Vehicular Digital Twin Networks: Challenges and Solutions. IEEE Wirel. Commun. 2023, 30, 154–160. [Google Scholar] [CrossRef]
- Bhatti, G.; Mohan, H.; Raja Singh, R. Towards the future of smart electric vehicles: Digital twin technology. Renew. Sustain. Energy Rev. 2021, 141, 110801. [Google Scholar] [CrossRef]
- Li, T.; Shang, M.; Wang, S.; Stern, R. Detecting Subtle Cyberattacks on Adaptive Cruise Control Vehicles: A Machine Learning Approach. IEEE Open J. Intell. Transp. Syst. 2025, 6, 11–23. [Google Scholar] [CrossRef]
- Li, T.; Rosenblad, B.; Wang, S.; Shang, M.; Stern, R. Exploring Energy Impacts of Cyberattacks on Adaptive Cruise Control Vehicles. In Proceedings of the 2023 IEEE Intelligent Vehicles Symposium (IV), Anchorage, AK, USA, 4–7 June 2023; pp. 1–6. [Google Scholar] [CrossRef]


Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gesteira-Miñarro, R.; López, G.; Palacios, R. Revisiting Wireless Cyberattacks on Vehicles. Sensors 2025, 25, 2605. https://doi.org/10.3390/s25082605
Gesteira-Miñarro R, López G, Palacios R. Revisiting Wireless Cyberattacks on Vehicles. Sensors. 2025; 25(8):2605. https://doi.org/10.3390/s25082605
Chicago/Turabian StyleGesteira-Miñarro, Roberto, Gregorio López, and Rafael Palacios. 2025. "Revisiting Wireless Cyberattacks on Vehicles" Sensors 25, no. 8: 2605. https://doi.org/10.3390/s25082605
APA StyleGesteira-Miñarro, R., López, G., & Palacios, R. (2025). Revisiting Wireless Cyberattacks on Vehicles. Sensors, 25(8), 2605. https://doi.org/10.3390/s25082605





