An Edge-Computing-Based Integrated Framework for Network Traffic Analysis and Intrusion Detection to Enhance Cyber–Physical System Security in Industrial IoT
Abstract
1. Introduction
- We propose a comprehensive framework that integrates network traffic analysis, clustering, intrusion detection, and edge computing to address the complexity and security challenges of cyber–physical system security in industrial IoT.
- We employ k-means and DBSCAN clustering methods to effectively segment network traffic and, therefore, detect different traffic scenarios in IIoT networks as well as potential discrepancies.
- We implement and compare three machine-learning models (KNN, RF, and LR) to detect intrusions and found the models performing well with a high accuracy to differentiate between benign and malicious traffic.
- We provide the practical mechanism of incorporating edge computing within the proposed framework.
- We provide recommendations regarding clustering and machine-learning approaches that are suitable for practical implementation in actual industrial IoT environments.
2. Related Work
3. System Design and Model
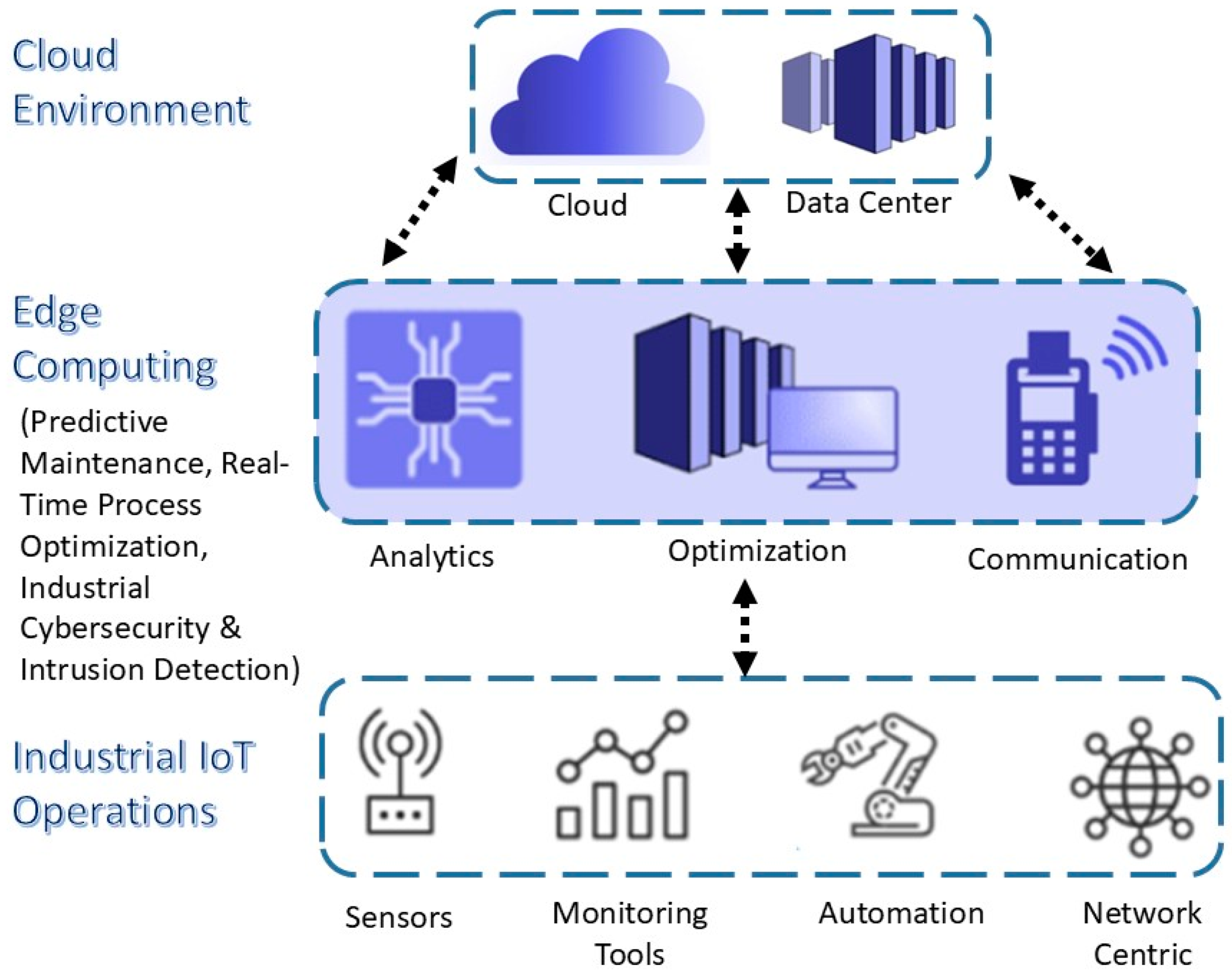
3.1. Implementation of Edge Computing in the Proposed Framework
3.2. Algorithm for Edge-Computing-Based Integrated Framework for Network Traffic Analysis and Intrusion Detection for CPSs in IIoT
| Algorithm 1: Edge-Computing-Based Integrated Framework for Network Traffic Analysis and Intrusion Detection for CPSs in IIoT |
|
4. Performance Evaluation
4.1. Evaluation Metrics
- True Positive (TP): the number of correctly identified positive instances;
- True Negative (TN): the number of correctly identified negative instances;
- False Positive (FP): the number of incorrectly identified positive instances;
- False Negative (FN): the number of incorrectly identified negative instances.
4.2. Dataset
4.3. Experimental Design
4.4. Results and Discussion
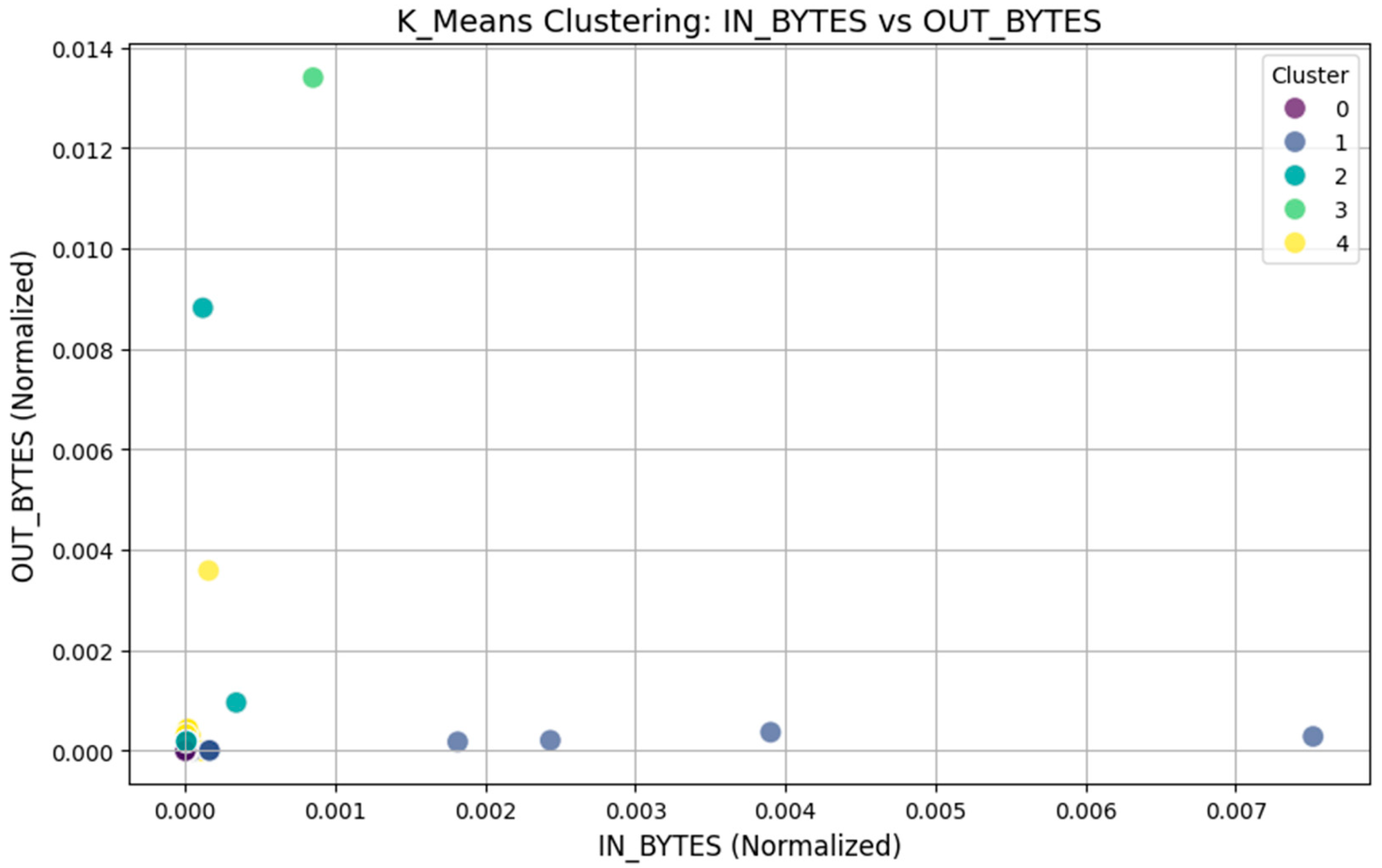
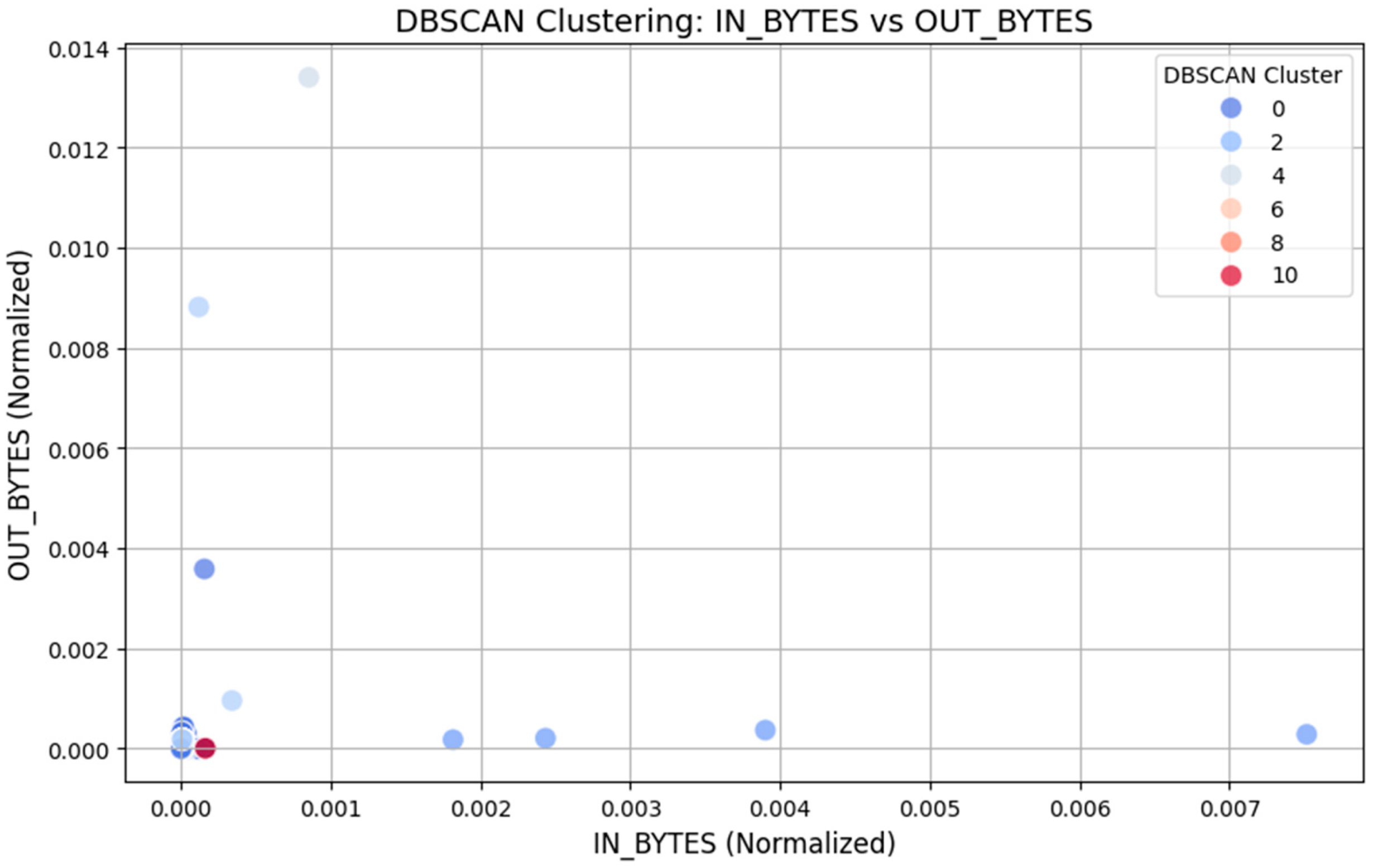
4.4.1. Network Traffic Analysis
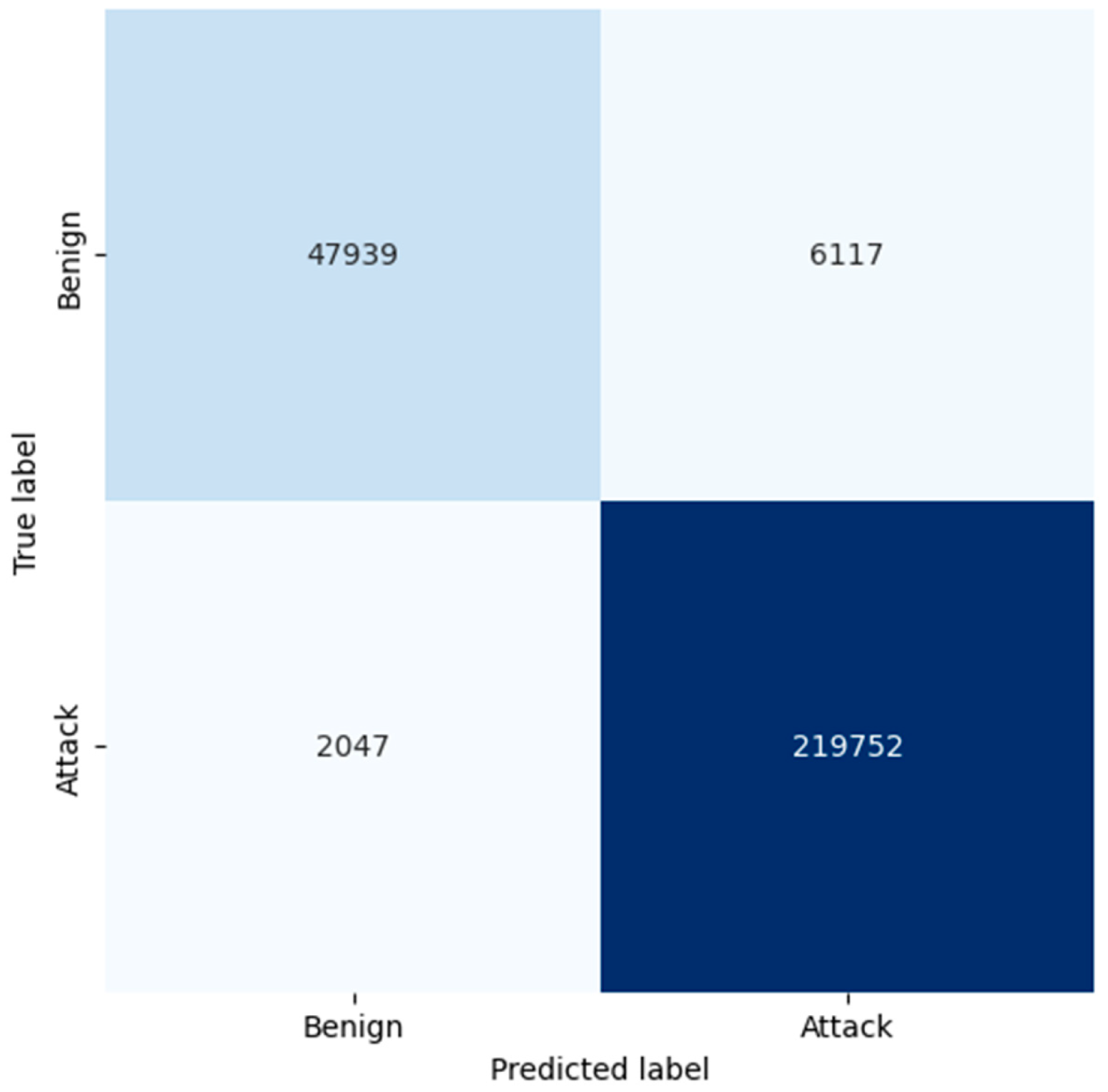
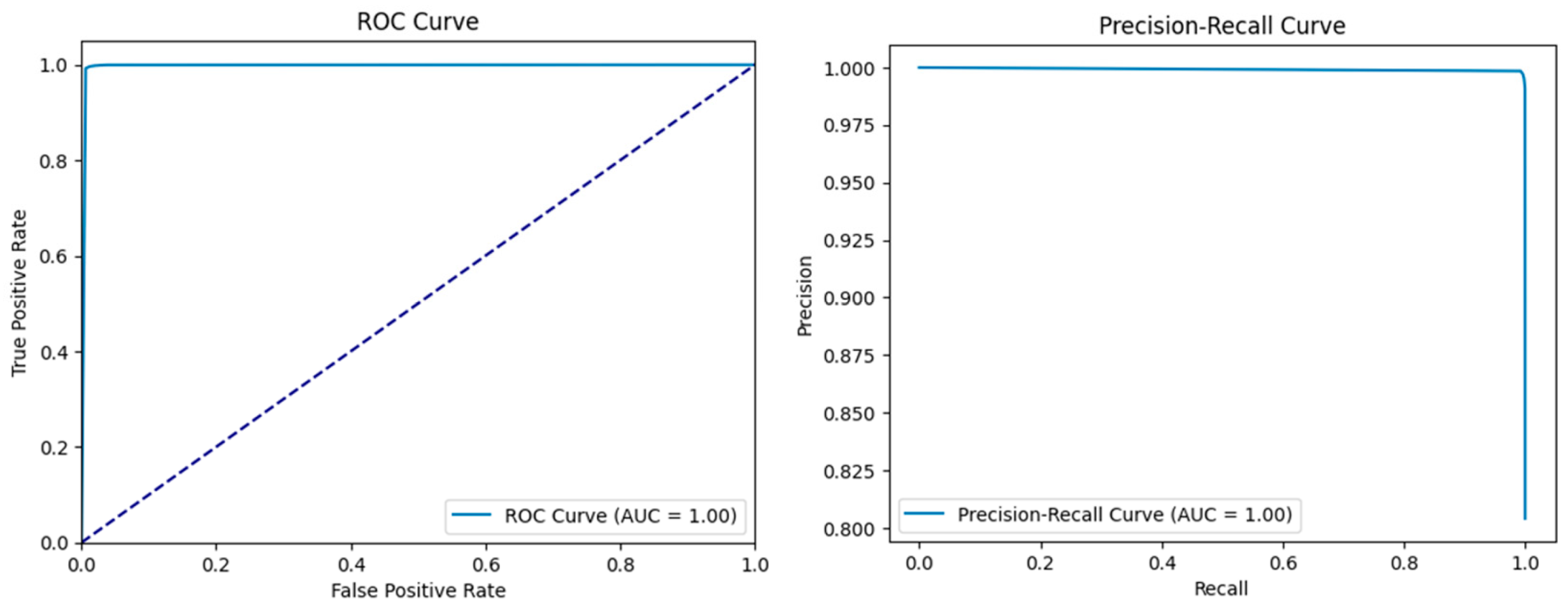
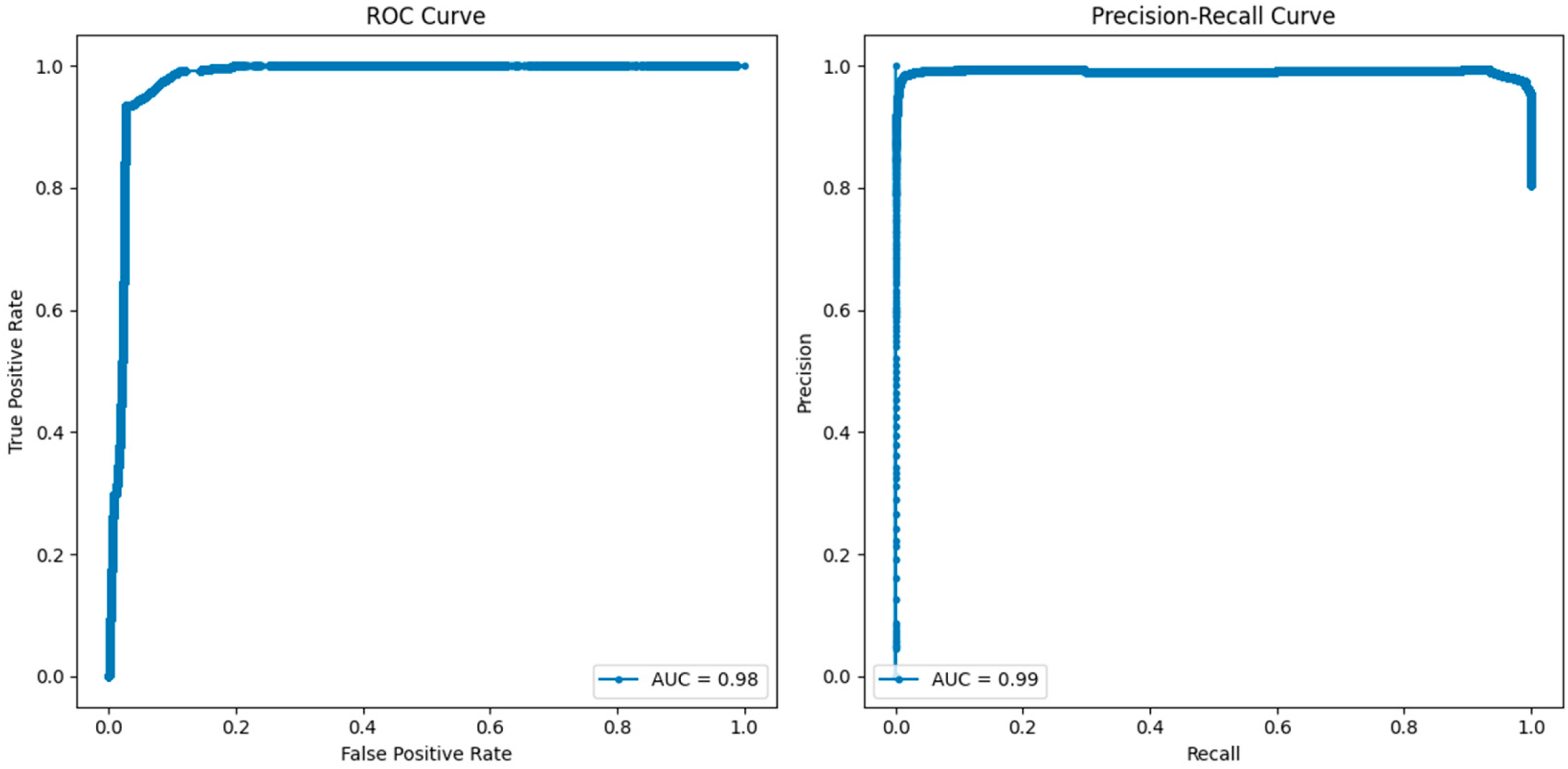
4.4.2. Intrusion Detection System
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Fernández-Caramés, T.M.; Fraga-Lamas, P. Use Case Based Blended Teaching of IIoT Cybersecurity in the Industry 4.0 Era. Appl. Sci. 2020, 10, 5607. [Google Scholar] [CrossRef]
- Zhu, E.; Wang, H.; Zhang, Y.; Zhang, K.; Liu, C. PHEE: Identifying influential nodes in social networks with a phased evaluation-enhanced search. Neurocomputing 2024, 572, 127195. [Google Scholar] [CrossRef]
- Peng, K.; Zhao, B.; Bilal, M.; Xu, X.; Nayyar, A. QoS-Aware Cloud-Edge Collaborative Micro-Service Scheduling in the IIoT. Hum.-Centric Comput. Inf. Sci. 2023, 13. [Google Scholar] [CrossRef]
- Zhang, G.; Wei, X.; Tan, X.; Han, Z.; Zhang, G. AoI Minimization Based on Deep Reinforcement Learning and Matching Game for IoT Information Collection in SAGIN. IEEE Trans. Commun. 2025. early access. [Google Scholar] [CrossRef]
- Qiao, Y.; Lü, J.; Wang, T.; Liu, K.; Zhang, B.; Snoussi, H. A Multihead Attention Self-Supervised Representation Model for Industrial Sensors Anomaly Detection. IEEE Trans. Ind. Inform. 2024, 20, 2190–2199. [Google Scholar] [CrossRef]
- Peter, O.; Pradhan, A.; Mbohwa, C. Industrial internet of things (IIoT): Opportunities, challenges, and requirements in manufacturing businesses in emerging economies. Procedia Comput. Sci. 2023, 217, 856–865. [Google Scholar] [CrossRef]
- Alotaibi, B. A Survey on Industrial Internet of Things Security: Requirements, Attacks, AI-Based Solutions, and Edge Computing Opportunities. Sensors 2023, 23, 7470. [Google Scholar] [CrossRef]
- Diène, B.; Rodrigues, J.J.P.C.; Diallo, O.; Ndoye, E.H.M.; Korotaev, V.V. Data management techniques for Internet of Things. Mech. Syst. Signal Process. 2020, 138, 106564. [Google Scholar] [CrossRef]
- Javed, A.; Robert, J.; Heljanko, K.; Främling, K. IoTEF: A Federated Edge-Cloud Architecture for Fault-Tolerant IoT Applications. J. Grid Comput. 2020, 18, 57–80. [Google Scholar] [CrossRef]
- Hajda, J.; Jakuszewski, R.; Ogonowski, S. Security Challenges in Industry 4.0 PLC Systems. Appl. Sci. 2021, 11, 9785. [Google Scholar] [CrossRef]
- Liu, Y.; Li, W.; Dong, X.; Ren, Z. Resilient Formation Tracking for Networked Swarm Systems Under Malicious Data Deception Attacks. Int. J. Robust Nonlinear Control 2024, 35, 2043–2052. [Google Scholar] [CrossRef]
- Li, C.; He, A.; Liu, G.; Wen, Y.; Chronopoulos, A.T.; Giannakos, A. RFL-APIA: A Comprehensive Framework for Mitigating Poisoning Attacks and Promoting Model Aggregation in IIoT Federated Learning. IEEE Trans. Ind. Inform. 2024, 20, 12935–12944. [Google Scholar] [CrossRef]
- Abosuliman, S.S. Deep learning techniques for securing cyber-physical systems in supply chain 4.0. Comput. Electr. Eng. 2023, 107, 108637. [Google Scholar] [CrossRef]
- Wang, E.; Yang, Y.; Wu, J.; Liu, W.; Wang, X. An Efficient Prediction-Based User Recruitment for Mobile Crowdsensing. IEEE Trans. Mob. Comput. 2018, 17, 16–28. [Google Scholar] [CrossRef]
- Jiang, H.; Ji, P.; Zhang, T.; Cao, H.; Liu, D. Two-Factor Authentication for Keyless Entry System via Finger-Induced Vibrations. IEEE Trans. Mob. Comput. 2024, 23, 9708–9720. [Google Scholar] [CrossRef]
- Alguliyev, R.; Imamverdiyev, Y.; Sukhostat, L. Cyber-physical systems and their security issues. Comput. Ind. 2018, 100, 212–223. [Google Scholar] [CrossRef]
- Al-Quayed, F.; Ahmad, Z.; Humayun, M. A Situation Based Predictive Approach for Cybersecurity Intrusion Detection and Prevention Using Machine Learning and Deep Learning Algorithms in Wireless Sensor Networks of Industry 4.0. IEEE Access 2024, 12, 34800–34819. [Google Scholar] [CrossRef]
- Zhou, W.; Xia, C.; Wang, T.; Liang, X.; Lin, W.; Li, X.; Zhang, S. HIDIM: A novel framework of network intrusion detection for hierarchical dependency and class imbalance. Comput. Secur. 2025, 148, 104155. [Google Scholar] [CrossRef]
- Li, T.; Kouyoumdjieva, S.T.; Karlsson, G.; Hui, P. Data collection and node counting by opportunistic communication. In Proceedings of the 2019 IFIP Networking Conference (IFIP Networking), Warsaw, Poland, 20–22 May 2019; pp. 1–9. [Google Scholar]
- Goldstein, A.; Johanndeiter, T.; Frank, U. Business Process Runtime Models: Towards Bridging the Gap Between Design, Enactment, and Evaluation of Business Processes; Springer: Berlin/Heidelberg, Germany, 2019; Volume 17, ISBN 1025701803742. [Google Scholar]
- Nankya, M.; Chataut, R.; Akl, R. Securing Industrial Control Systems: Components, Cyber Threats, and Machine Learning-Driven Defense Strategies. Sensors 2023, 23, 8840. [Google Scholar] [CrossRef]
- Umran, S.M.; Lu, S.; Abduljabbar, Z.A.; Zhu, J.; Wu, J. Secure Data of Industrial Internet of Things in a Cement Factory Based on a Blockchain Technology. Appl. Sci. 2021, 11, 6376. [Google Scholar] [CrossRef]
- Zhang, X.; Hou, D.; Xiong, Z.; Liu, Y.; Wang, S.; Li, Y. EALLR: Energy-Aware Low-Latency Routing Data Driven Model in Mobile Edge Computing. IEEE Trans. Consum. Electron. 2024. early access. [Google Scholar] [CrossRef]
- Li, X.; Liu, Y.; Ji, H.; Zhang, H.; Leung, V.C.M. Optimizing resources allocation for fog computing-based internet of things networks. IEEE Access 2019, 7, 64907–64922. [Google Scholar] [CrossRef]
- Sun, G.; Liao, D.; Zhao, D.; Xu, Z.; Yu, H. Live Migration for Multiple Correlated Virtual Machines in Cloud-Based Data Centers. IEEE Trans. Serv. Comput. 2018, 11, 279–291. [Google Scholar] [CrossRef]
- Algarni, A.; Acarer, T.; Ahmad, Z. An Edge Computing-Based Preventive Framework With Machine Learning- Integration for Anomaly Detection and Risk Management in Maritime Wireless Communications. IEEE Access 2024, 12, 53646–53663. [Google Scholar] [CrossRef]
- Cao, K.; Hu, S.; Shi, Y.; Colombo, A.; Karnouskos, S.; Li, X. A Survey on Edge and Edge-Cloud Computing Assisted Cyber-Physical Systems. IEEE Trans. Ind. Inform. 2021, 17, 7806–7819. [Google Scholar] [CrossRef]
- Sun, G.; Wang, Z.; Su, H.; Yu, H.; Lei, B.; Guizani, M. Profit Maximization of Independent Task Offloading in MEC-Enabled 5G Internet of Vehicles. IEEE Trans. Intell. Transp. Syst. 2024, 25, 16449–16461. [Google Scholar] [CrossRef]
- Safa, N.S.; Maple, C.; Furnell, S.; Azad, M.A.; Perera, C.; Dabbagh, M.; Sookhak, M. Deterrence and prevention-based model to mitigate information security insider threats in organisations. Futur. Gener. Comput. Syst. 2019, 97, 587–597. [Google Scholar] [CrossRef]
- Babar, M.; Khan, M.S.; Habib, U.; Shah, B.; Ali, F.; Song, D. Scalable Edge Computing for IoT and Multimedia Applications Using Machine Learning. Hum.-Centric Comput. Inf. Sci. 2021, 11, 41. [Google Scholar] [CrossRef]
- Ma, Y.; Ma, R.; Lin, Z.; Zhang, R.; Cai, Y.; Wu, W.; Wang, J. Improving Age of Information for Covert Communication With Time-Modulated Arrays. IEEE Internet Things J. 2025, 12, 1718–1731. [Google Scholar] [CrossRef]
- Yao, C.; Yang, Y.; Yin, K.; Yang, J. Traffic Anomaly Detection in Wireless Sensor Networks Based on Principal Component Analysis and Deep Convolution Neural Network. IEEE Access 2022, 10, 103136–103149. [Google Scholar] [CrossRef]
- Lin, W.; Xia, C.; Wang, T.; Zhao, Y.; Xi, L.; Zhang, S. Input and Output Matter: Malicious Traffic Detection with Explainability. IEEE Netw. 2024, 39, 259–267. [Google Scholar] [CrossRef]
- Shah, K.; Patel, H.; Sanghvi, D.; Shah, M. A Comparative Analysis of Logistic Regression, Random Forest and KNN Models for the Text Classification. Augment. Hum. Res. 2020, 5, 12. [Google Scholar] [CrossRef]
- Peppes, N.; Daskalakis, E.; Alexakis, T.; Adamopoulou, E.; Demestichas, K. Performance of Machine Learning-Based Multi-Model Voting Ensemble Methods for Network Threat Detection in Agriculture 4.0. Sensors 2021, 21, 7475. [Google Scholar] [CrossRef]
- Venkatesan, V.K.; Ramakrishna, M.T.; Izonin, I.; Tkachenko, R.; Havryliuk, M. Efficient Data Preprocessing with Ensemble Machine Learning Technique for the Early Detection of Chronic Kidney Disease. Appl. Sci. 2023, 13, 2885. [Google Scholar] [CrossRef]
- Farnaaz, N.; Jabbar, M.A. Random Forest Modeling for Network Intrusion Detection System. Procedia Comput. Sci. 2016, 89, 213–217. [Google Scholar] [CrossRef]
- Alrashdi, I.; Alqazzaz, A.; Aloufi, E.; Alharthi, R.; Zohdy, M.; Ming, H. AD-IoT: Anomaly detection of IoT cyberattacks in smart city using machine learning. In Proceedings of the 2019 IEEE 9th Annual Computing and Communication Workshop and Conference, CCWC 2019, Las Vegas, NV, USA, 7–9 January 2019; pp. 305–310. [Google Scholar]
- Mozaffaree Pour, N.; Oja, T. Prediction Power of Logistic Regression (LR) and Multi-Layer Perceptron (MLP) Models in Exploring Driving Forces of Urban Expansion to Be Sustainable in Estonia. Sustainability 2021, 14, 160. [Google Scholar] [CrossRef]
- Muthuramalingam, S.; Bharathi, A.; Rakesh Kumar, S.; Gayathri, N.; Sathiyaraj, R.; Balamurugan, B. Iot based intelligent transportation system (iot-its) for global perspective: A case study. In Internet of Things and Big Data Analytics for Smart Generation; Springer: Cham, Switzerland, 2019; pp. 279–300. [Google Scholar]
- Kumar, A. Cybersecurity Threat Detection using Machine Learning and Network Analysis. J. Artif. Intell. Gen. Sci. 2024, 1, 124–131. [Google Scholar] [CrossRef]
- Sangaiah, A.K.; Javadpour, A.; Pinto, P. Towards data security assessments using an IDS security model for cyber-physical smart cities. Inf. Sci. 2023, 648, 119530. [Google Scholar] [CrossRef]
- Ni, C.; Li, S.C. Machine learning enabled Industrial IoT Security: Challenges, Trends and Solutions. J. Ind. Inf. Integr. 2024, 38, 100549. [Google Scholar] [CrossRef]
- Wisdom, D.D.; Vincent, O.R.; Igulu, K.; Hyacinth, E.A.; Christian, A.U.; Oduntan, O.E.; Hauni, A.G. Industrial IoT Security Infrastructures and Threats. In Communication Technologies and Security Challenges in IoT: Present and Future; Springer: Singapore, 2024; pp. 369–402. [Google Scholar]
- Yafooz, W.M.S.; Bakar, Z.B.A.; Fahad, S.K.A. Business Intelligence Through Big Data Analytics, Data Mining and Machine Learning. In Data Management, Analytics and Innovation, Proceedings of ICDMAI 2019, Kuala Lumpur, Malaysia, 18–20 January 2019; Springer: Singapore, 2020; Volume 1016, pp. 217–230. [Google Scholar]
- Kumari, A.; Patel, R.K.; Sukharamwala, U.C.; Tanwar, S.; Raboaca, M.S.; Saad, A.; Tolba, A. AI-Empowered Attack Detection and Prevention Scheme for Smart Grid System. Mathematics 2022, 10, 2852. [Google Scholar] [CrossRef]
- Balaji, B.S.; Paja, W.; Antonijevic, M.; Stoean, C.; Bacanin, N.; Zivkovic, M. IoT Integrated Edge Platform for Secure Industrial Application with Deep Learning. Hum.-Centric Comput. Inf. Sci. 2023, 13. [Google Scholar] [CrossRef]
- Kaggle. NF-ToN-IoT-V2. Available online: https://www.kaggle.com/datasets/dhoogla/nftoniotv2/data (accessed on 16 August 2024).
- Singh, V.; Gupta, I.; Jana, P.K. A novel cost-efficient approach for deadline-constrained workflow scheduling by dynamic provisioning of resources. Future Gener. Comput. Syst. 2018, 79, 95–110. [Google Scholar] [CrossRef]
- Matni, N.; Moraes, J.; Oliveira, H.; Rosário, D.; Cerqueira, E. Lorawan gateway placement model for dynamic internet of things scenarios. Sensors 2020, 20, 4336. [Google Scholar] [CrossRef]
- Deng, D. DBSCAN Clustering Algorithm Based on Density. In Proceedings of the 2020 7th International Forum on Electrical Engineering and Automation (IFEEA), Hefei, China, 25–27 September 2020; pp. 949–953. [Google Scholar]




| Reference | Focused Area | Machine Learning Techniques | Features | Dataset | Key Contributions |
|---|---|---|---|---|---|
| [13] | Anomaly detection in CPS for Supply Chain 4.0 | PCA-BSO feature selection + ML models | Network traffic anomalies | Real-world traffic data from a semiconductor factory | PCA-BSO used to select significant features, improving classification accuracy |
| [16] | Security issues in cyber–physical systems (CPSs) | Review-based work | CPS security threats and attack types | Review-based work | Categorizes CPS security threats and describes philosophical challenges |
| [27] | Edge computing integration in CPS | Review-based work | QoS optimization in CPS | Review-based work | Edge–cloud computing and QoS challenges in CPSs |
| [41] | Machine-learning-based cybersecurity analysis | Network IDS and Host IDS | Attack pattern analysis, adversarial ML vulnerabilities | KDDCup99, NSL-KDD, UNSW-NB15, WSN-DS, CICIDS 2017 | Explores robustness of IDSs against adversarial ML attacks |
| [42] | IDS in Edge Intelligence for Smart Cities | Linear Correlation Feature Selection, INTERACT, MLP | Feature extraction and selection for attack prediction | KDDCup99 | Hybrid feature selection and ML for improved intrusion detection |
| Proposed Framework | Network traffic analysis and intrusion detection in IIoT CPS using edge computing | k-means, DBSCAN, KNN, RF, LR | Network traffic behavior, anomaly detection, supervised learning for intrusion detection | NF-ToN-IoT-V2 (real-world industrial IoT dataset) | Integrates clustering and ML models with edge computing for real-time and scalable intrusion detection |
| Cluster | Number of Instances |
|---|---|
| Cluster 4 | 2089 |
| Cluster 0 | 1808 |
| Cluster 1 | 624 |
| Cluster 2 | 393 |
| Cluster 3 | 86 |
| Class | Precision | Recall | F1 Score | Accuracy | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| KNN | RF | LR | KNN | RF | LR | KNN | RF | LR | KNN | RF | LR | |
| Benign (0) | 0.99 | 1.00 | 0.96 | 0.98 | 0.98 | 0.89 | 0.99 | 0.99 | 0.92 | 0.99 | 0.99 | 0.97 |
| Attack (1) | 1.00 | 0.99 | 0.97 | 1.00 | 1.00 | 0.99 | 1.00 | 1.00 | 0.98 | |||
| Macro average | 0.99 | 1.00 | 0.97 | 0.99 | 0.99 | 0.94 | 0.99 | 0.99 | 0.95 | |||
| Weighted average | 0.99 | 0.99 | 0.97 | 0.99 | 0.99 | 0.97 | 0.99 | 0.99 | 0.97 | |||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhukabayeva, T.; Ahmad, Z.; Adamova, A.; Karabayev, N.; Abdildayeva, A. An Edge-Computing-Based Integrated Framework for Network Traffic Analysis and Intrusion Detection to Enhance Cyber–Physical System Security in Industrial IoT. Sensors 2025, 25, 2395. https://doi.org/10.3390/s25082395
Zhukabayeva T, Ahmad Z, Adamova A, Karabayev N, Abdildayeva A. An Edge-Computing-Based Integrated Framework for Network Traffic Analysis and Intrusion Detection to Enhance Cyber–Physical System Security in Industrial IoT. Sensors. 2025; 25(8):2395. https://doi.org/10.3390/s25082395
Chicago/Turabian StyleZhukabayeva, Tamara, Zulfiqar Ahmad, Aigul Adamova, Nurdaulet Karabayev, and Assel Abdildayeva. 2025. "An Edge-Computing-Based Integrated Framework for Network Traffic Analysis and Intrusion Detection to Enhance Cyber–Physical System Security in Industrial IoT" Sensors 25, no. 8: 2395. https://doi.org/10.3390/s25082395
APA StyleZhukabayeva, T., Ahmad, Z., Adamova, A., Karabayev, N., & Abdildayeva, A. (2025). An Edge-Computing-Based Integrated Framework for Network Traffic Analysis and Intrusion Detection to Enhance Cyber–Physical System Security in Industrial IoT. Sensors, 25(8), 2395. https://doi.org/10.3390/s25082395










