A Survey on Secure WiFi Sensing Technology: Attacks and Defenses
Abstract
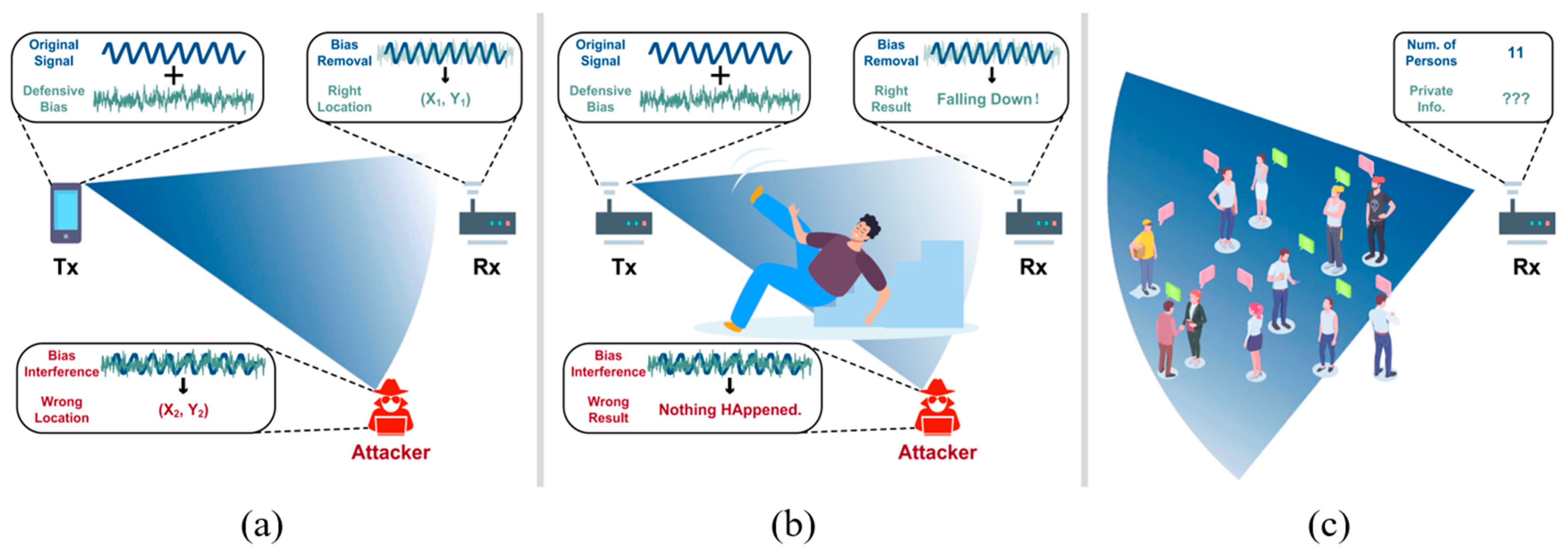
1. Introduction
- Complete picture and novel taxonomy: We present a complete picture of the literature in the area of secure WiFi sensing and propose a novel taxonomy for technologies for attack and defense of WiFi sensing, respectively, which guides the first step;
- Inclusive and up-to-date coverage: Our survey is inclusive, encompassing the latest advancements in secure WiFi sensing technologies. By integrating recent developments, we ensure that our work remains relevant and valuable to the research community;
- Comprehensive comparison and summary: We comprehensively compare and summarize existing technologies for attack and defense of WiFi sensing to provide readers with a thorough understanding of this area;
- Identification of key challenges and future directions: Our survey discusses the key challenges and future directions, which may inspire researchers and developers to carry on further research in WiFi sensing and build various applications to realize privacy-preserving, reliable, ubiquitous, and accurate WiFi sensing.
2. Background
2.1. Concept and Scope
2.2. WiFi Sensing Basics
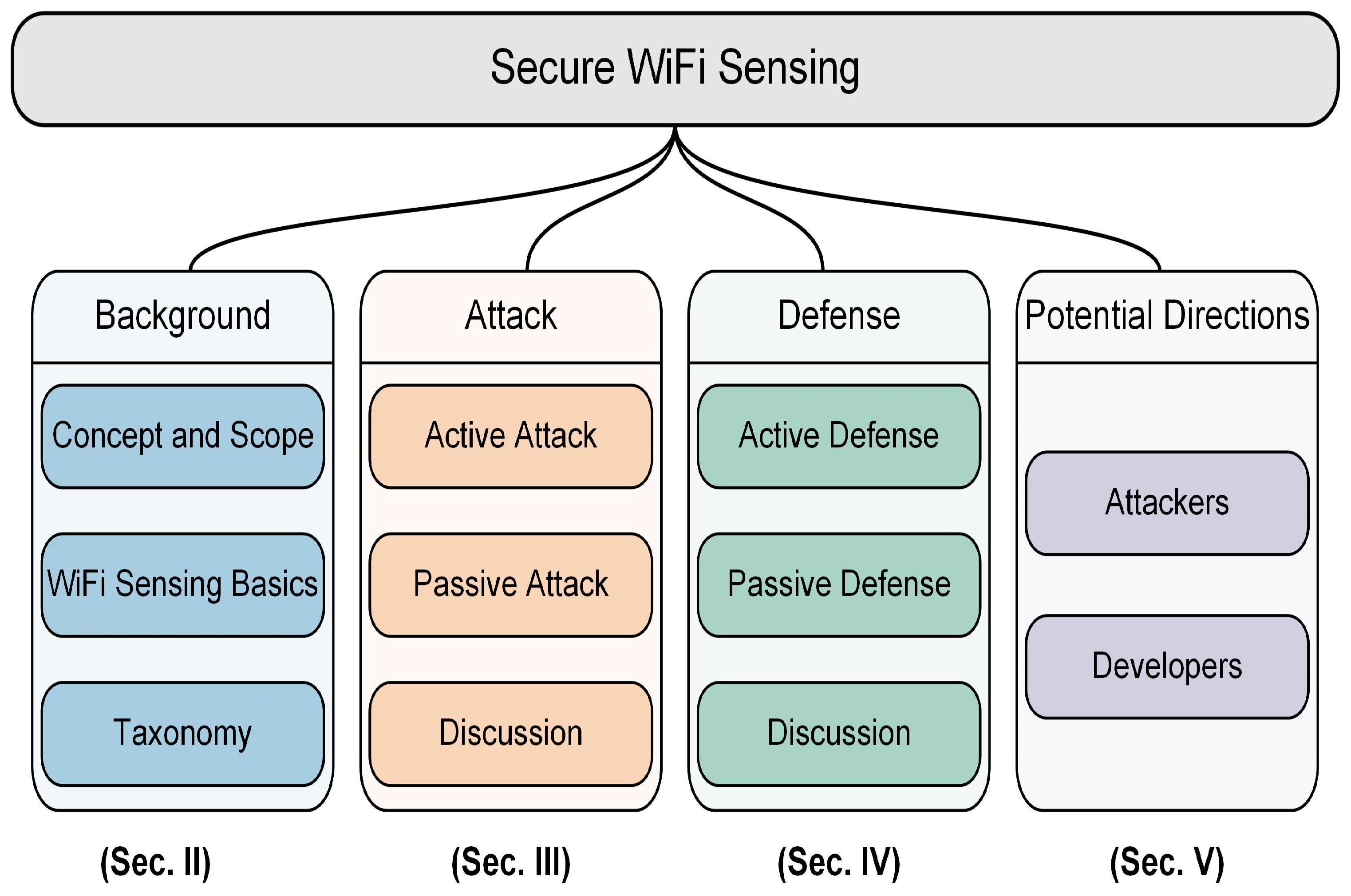
2.3. Taxonomy
- Active attack. (1) Definition: Attacks that involve direct interaction with the WiFi sensing system to alter, disrupt, or damage the wireless channel or its operations. (2) Objective: The attacker aims to interfere with the normal functioning of the sensing system, causing it to produce inaccurate or unusable results;
- Passive attack. (1) Definition: Attacks that focus on monitoring or eavesdropping on the wireless channel or sensing results without altering them. (2) Objective: The attacker aims to gather sensitive information or infer private data without being detected.
- Active defense. (1) Definition: Protective measures taken directly by the sensing target (e.g., a user, device, or system) to safeguard against attacks. (2) Objective: The target actively engages in its own protection to mitigate potential threats;
- Passive defense. (1) Definition: Protective measures adopted by external parties, such as users of the sensing data or third-party entities, to secure the sensing information. (2) Objective: These measures protect the sensing data or system without requiring direct involvement from the sensing target.
3. Attacks Against WiFi Sensing
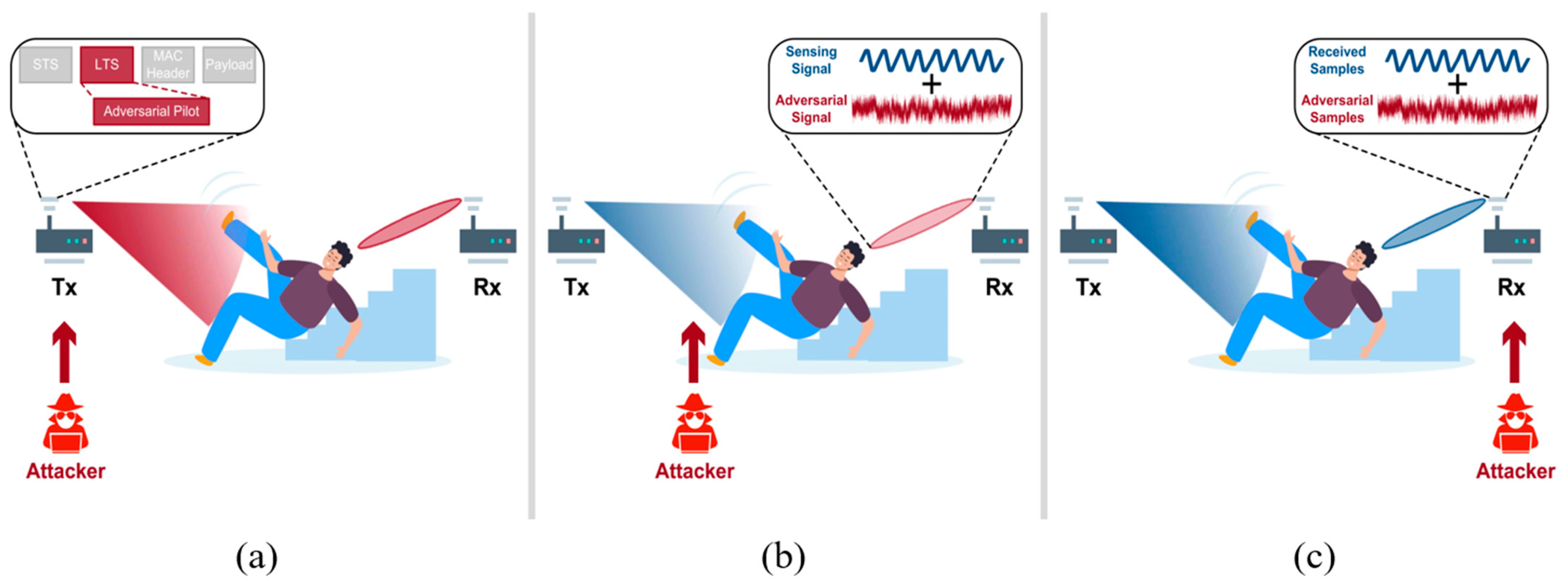
3.1. Active Attack
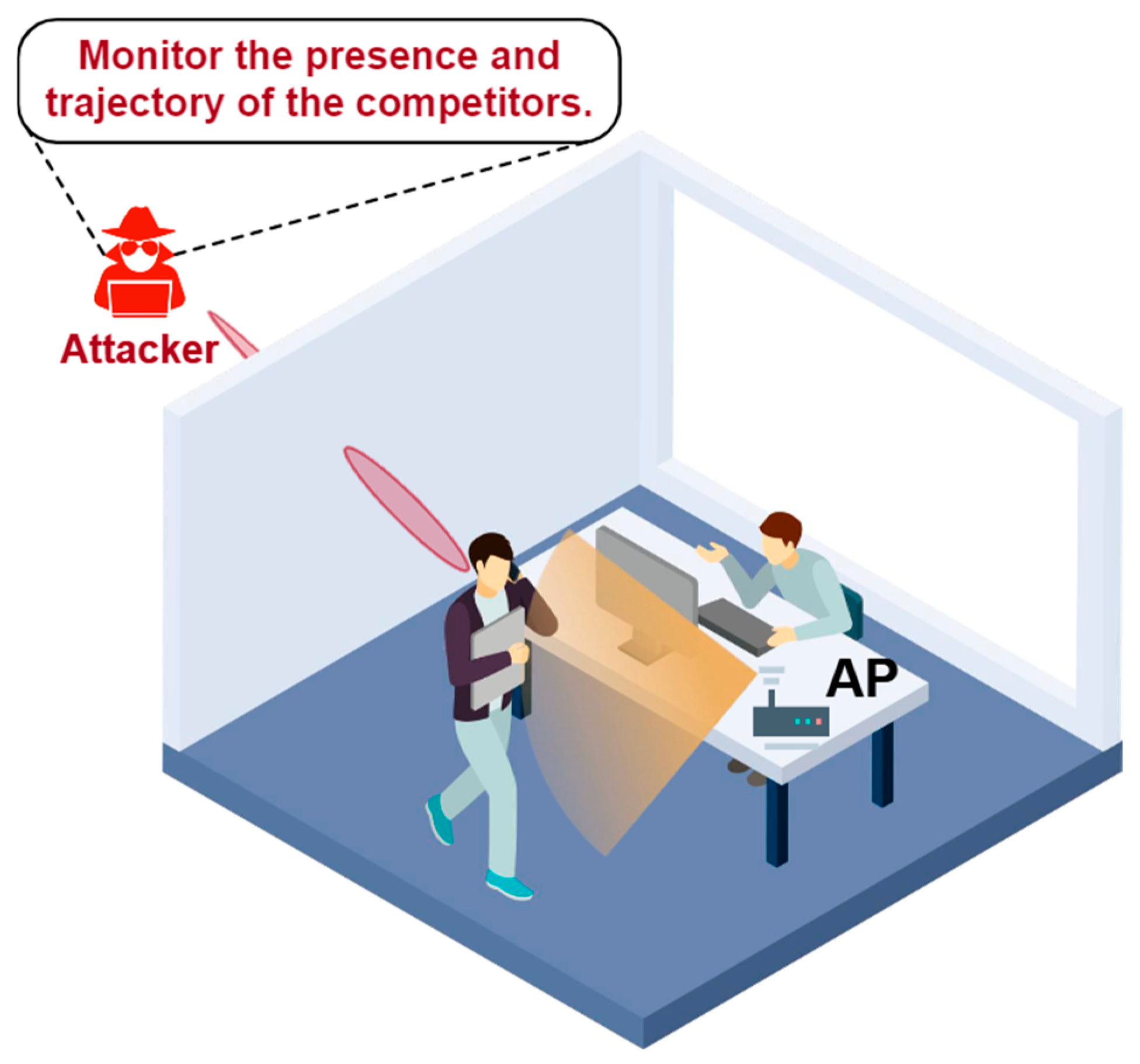
3.2. Passive Attack
3.3. Discussion
4. Defenses for WiFi Sensing
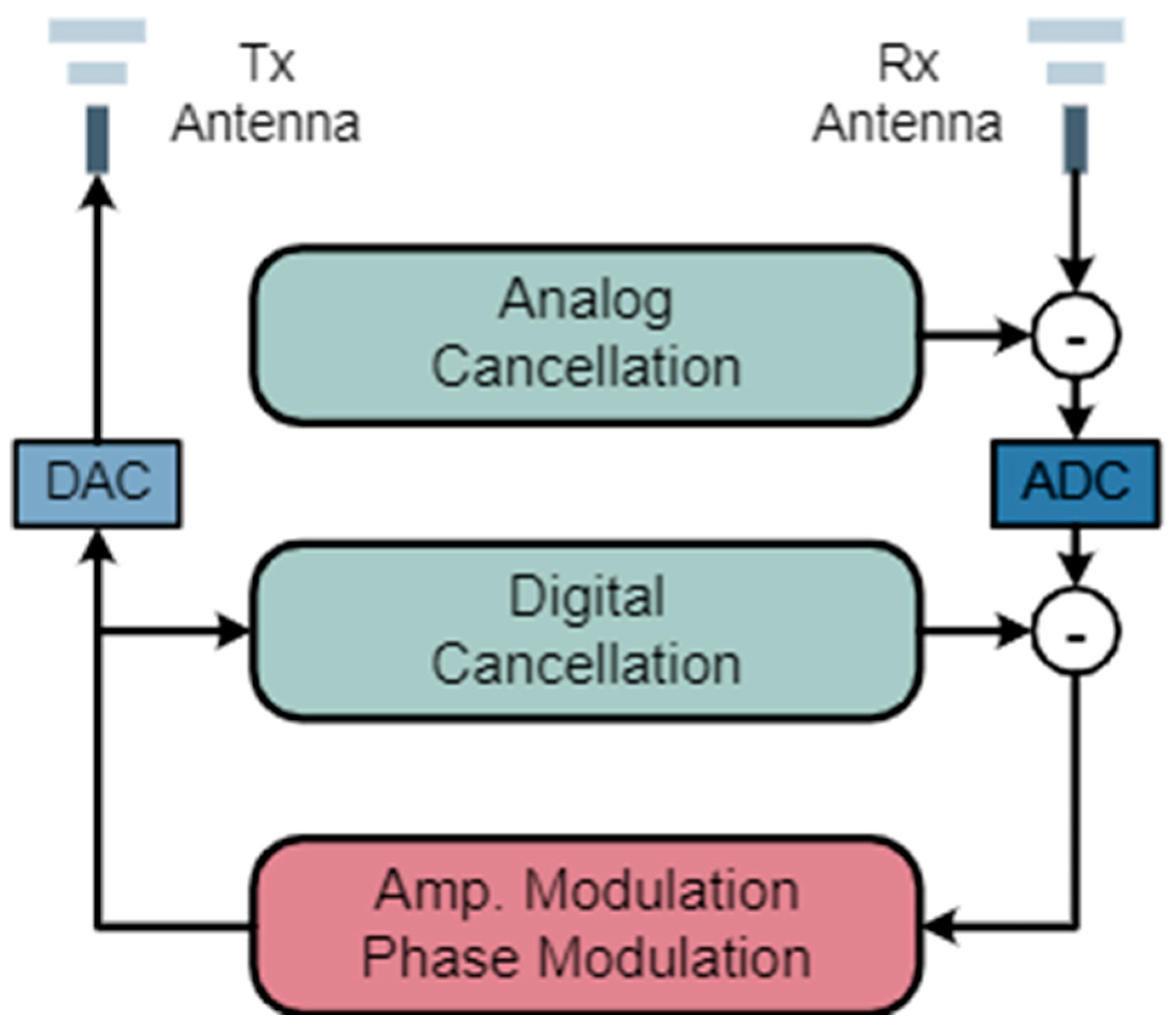
4.1. Active Defense
4.2. Passive Defense
4.3. Discussion
5. Challenges and Opportunities
5.1. Attackers
5.2. WiFi Sensing Algorithm Developers
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Liu, Y.; Dillon, T.; Yu, W.; Rahayu, W.; Mostafa, F. Missing value imputation for industrial IoT sensor data with large gaps. IEEE Internet Things J. 2020, 7, 6855–6867. [Google Scholar] [CrossRef]
- Davoli, L.; Belli, L.; Cilfone, A.; Ferrari, G. From micro to macro IoT: Challenges and solutions in the integration of IEEE 802.15. 4/802.11 and sub-GHz technologies. IEEE Internet Things J. 2017, 5, 784–793. [Google Scholar] [CrossRef]
- Chen, Y.; Guo, J.; Sun, Y.; Yao, H.; Liu, Y.; He, Y. ELASE: Enabling real-time elastic sensing resource scheduling in 5g vRAN. In Proceedings of the IEEE/ACM 32nd International Symposium on Quality of Service (IWQoS), Guangzhou, China, 19–21 June 2024. [Google Scholar]
- He, S.; Shi, K.; Liu, C.; Guo, B.; Chen, J.; Shi, Z. Collaborative sensing in internet of things: A comprehensive survey. IEEE Commun. Surv. Tutor. 2022, 24, 1435–1474. [Google Scholar] [CrossRef]
- Wu, T.; Wu, F.; Qiu, C.; Redoute, J.-M.; Yuce, M.R. A rigid-flex wearable health monitoring sensor patch for IoT-connected healthcare applications. IEEE Internet Things J. 2020, 7, 6932–6945. [Google Scholar] [CrossRef]
- Chen, C.W. Internet of video things: Next-generation IoT with visual sensors. IEEE Internet Things J. 2020, 7, 6676–6685. [Google Scholar] [CrossRef]
- Zou, Y.; Na, X.; Guo, X.; Sun, Y.; He, Y. Trident: Interference avoidance in multi-reader backscatter network via frequency-space division. In Proceedings of the IEEE INFOCOM 2024—IEEE Conference on Computer Communications, Vancouver, BC, Canada, 20–23 May 2024. [Google Scholar]
- Chen, Z.; Zhao, M.-M.; Li, M.; Xu, F.; Wu, Q.; Zhao, M.-J. Joint Location Sensing and Channel Estimation for IRS-Aided mmWave ISAC Systems. IEEE Trans. Wirel. Commun. 2024, 23, 11985–12002. [Google Scholar] [CrossRef]
- Jiao, L.; Ge, Y.; Zeng, K.; Hilburn, B. Location privacy and spectrum efficiency enhancement in spectrum sharing systems. IEEE Trans. Cogn. Commun. Netw. 2023, 9, 1472–1488. [Google Scholar] [CrossRef]
- Kotaru, M.; Joshi, K.; Bharadia, D.; Katti, S. Spotfi: Decimeter level localization using WiFi. In Proceedings of the ACM Conference on Special Interest Group on Data Communication (SIGCOMM), London, UK, 17–21 August 2015. [Google Scholar]
- Li, D.; Cao, S.; Lee, S.I.; Xiong, J. Experience: Practical problems for acoustic sensing. In Proceedings of the 28th Annual International Conference on Mobile Computing And Networking (ACM MobiCom), Sydney, Australia, 17–21 October 2022. [Google Scholar]
- Fu, Y.; Wang, S.; Zhong, L.; Chen, L.; Ren, J.; Zhang, Y. Svoice: Enabling voice communication in silence via acoustic sensing on commodity devices. In Proceedings of the 20th ACM Conference on Embedded Networked Sensor Systems (ACM SenSys), Boston, MA, USA, 6–9 November 2022. [Google Scholar]
- Siddiqi, A.A.; He, Y.; Chen, Y.; Sun, Y.; Wang, S.; Xie, Y. mmjaw: Remote jaw gesture recognition with cots mmWave radar. In Proceedings of the IEEE 30th International Conference on Parallel and Distributed Systems (ICPADS), Belgrade, Serbia, 10–14 October 2024. [Google Scholar]
- Jayawardana, D.; Liyanapathirana, R.; Zhu, X. RFID-Based Wireless Multi-Sensory System for Simultaneous Dynamic Acceleration and Strain Measurements of Civil Infrastructure. IEEE Sens. J. 2019, 19, 12389–12397. [Google Scholar] [CrossRef]
- Xie, X.; Zhang, D.; Li, Y.; Hu, Y.; Sun, Q.; Chen, Y. Robust WiFi respiration sensing in the presence of interfering individual. IEEE Trans. Mob. Comput. 2024, 23, 8447–8462. [Google Scholar] [CrossRef]
- Zeng, Y.; Wu, D.; Xiong, J.; Liu, J.; Liu, Z.; Zhang, D. Multisense: Enabling multi-person respiration sensing with commodity WiFi. Proc. ACM Interact. Mob. Wearable Ubiquitous Technol. 2020, 4, 102. [Google Scholar] [CrossRef]
- Gao, Q.; Tong, J.; Wang, J.; Ran, Z.; Pan, M. Device-free multi-person respiration monitoring using WiFi. IEEE Trans. Veh. Technol. 2020, 69, 14083–14087. [Google Scholar] [CrossRef]
- Zhang, J.; Na, X.; Xi, R.; Sun, Y.; He, Y. mmHawkeye: Passive UAV detection with a COTS mmWave radar. In Proceedings of the 20th Annual IEEE International Conference on Sensing, Communication, and Networking (SECON), Madrid, Spain, 11–14 September 2023. [Google Scholar]
- Hao, L.; Huang, B.; Jia, B.; Mao, G. DHCLoc: A device-heterogeneitytolerant and channel-adaptive passive WiFi localization method based on DNN. IEEE Internet Things J. 2021, 9, 4863–4874. [Google Scholar] [CrossRef]
- Sun, Y.; Wang, W.; Mottola, L.; Wang, R.; He, Y. Aim: Acoustic inertial measurement for indoor drone localization and tracking. In Proceedings of the 20th ACM Conference on Embedded Networked Sensor Systems (ACM SenSys), Boston, MA, USA, 6–9 November 2022. [Google Scholar]
- Alves, M.; Coelho, R.; Dranka, E. Effective Acoustic Energy Sensing Exploitation for Target Sources Localization in Urban Acoustic Scenes. IEEE Sens. Lett. 2020, 4, 1–4. [Google Scholar] [CrossRef]
- Woodford, T.; Qian, K.; Zhang, X. Metasight: High-resolution NLoS radar with efficient metasurface encoding. In Proceedings of the 21st ACM Conference on Embedded Networked Sensor Systems (ACM SenSys), Istanbul, Turkey, 12–17 November 2023. [Google Scholar]
- Nolan, J.; Qian, K.; Zhang, X. Ros: Passive smart surface for roadside-to-vehicle communication. In Proceedings of the 2021 ACM SIGCOMM 2021 Conference, Virtual Event, 23–27 August 2021. [Google Scholar]
- Sun, S.; Zhang, X.; Zheng, C.; Fu, J.; Zhao, C. Underwater Acoustical Localization of the Black Box Utilizing Single Autonomous Underwater Vehicle Based on the Second-Order Time Difference of Arrival. IEEE J. Ocean. Eng. 2020, 45, 1268–1279. [Google Scholar] [CrossRef]
- Cai, C.; Pu, H.; Ye, L.; Jiang, H.; Luo, J. Active acoustic sensing for “hearing” temperature under acoustic interference. IEEE Trans. Mob. Comput. 2021, 22, 661–673. [Google Scholar] [CrossRef]
- Ali, A.; Gonzalez-Prelcic, N.; Heath, R.W.; Ghosh, A. Leveraging sensing at the infrastructure for mmWave communication. IEEE Commun. Mag. 2020, 58, 84–89. [Google Scholar] [CrossRef]
- Sun, Y.; Wang, W.; Mottola, L.; Jia, Z.; Wang, R.; He, Y. Indoor drone localization and tracking based on acoustic inertial measurement. IEEE Trans. Mob. Comput. 2024, 23, 7537–7551. [Google Scholar] [CrossRef]
- Khalid, N.; Mirzavand, R.; Saghlatoon, H.; Honari, M.M.; Iyer, A.K.; Mousavi, P. A batteryless RFID sensor architecture with distance ambiguity resolution for smart home IoT applications. IEEE Internet Things J. 2021, 9, 2960–2972. [Google Scholar] [CrossRef]
- Zhang, X.; Li, H.-X.; Chung, H.S.-H. Setup-independent sensing architecture with multiple uhf RFID sensor tags. IEEE Internet Things J. 2021, 9, 1243–1251. [Google Scholar] [CrossRef]
- Wang, G.; Qian, C.; Cui, K.; Shi, X.; Ding, H.; Xi, W.; Zhao, J.; Han, J. A universal method to combat multipaths for RFID sensing. In Proceedings of the IEEE INFOCOM 2020—IEEE Conference on Computer Communications, Toronto, ON, Canada, 6–9 July 2020. [Google Scholar]
- Liu, J.; Chen, S.; Chen, M.; Xiao, Q.; Chen, L. Pose sensing with a single RFID tag. IEEE/ACM Trans. Netw. 2020, 28, 2023–2036. [Google Scholar] [CrossRef]
- Liu, J.; Yu, X.; Liu, X.; Chen, X.; Liu, H.; Wang, Y.; Chen, L. Time-efficient range detection in commodity RFID systems. IEEE/ACM Trans. Netw. 2022, 30, 1118–1131. [Google Scholar] [CrossRef]
- Wang, W.; He, Y.; Jin, M.; Sun, Y.; Guo, X. Meta-speaker: Acoustic source projection by exploiting air nonlinearity. In Proceedings of the 29th Annual International Conference on Mobile Computing and Networking (ACM MobiCom), Madrid, Spain, 2–6 October 2023. [Google Scholar]
- Lian, J.; Lou, J.; Chen, L.; Yuan, X. EchoSpot: Spotting your locations via acoustic sensing. Proc. ACM Interact. Mob. Wearable Ubiquitous Technol. 2021, 5, 113. [Google Scholar] [CrossRef]
- Cai, C.; Zheng, R.; Luo, J. Ubiquitous acoustic sensing on commodity IoT devices: A survey. IEEE Commun. Surv. Tutor. 2022, 24, 432–454. [Google Scholar] [CrossRef]
- Boukerche, A.; Sun, P. Design of algorithms and protocols for underwater acoustic wireless sensor networks. ACM Comput. Surv. (CSUR) 2020, 53, 134. [Google Scholar] [CrossRef]
- Wang, W.; Mottola, L.; He, Y.; Li, J.; Sun, Y.; Li, S.; Jing, H.; Wang, Y. MicNest: Long-range instant acoustic localization of drones in precise landing. In Proceedings of the 20th ACM Conference on Embedded Networked Sensor Systems (ACM SenSys), Boston, MA, USA, 6–9 November 2022. [Google Scholar]
- Xiong, J.; Jamieson, K. Arraytrack: A fine-grained indoor location system. In Proceedings of the 10th USENIX Symposium on Networked Systems Design and Implementation (NSDI), Lombard, IL, USA, 2–5 April 2013. [Google Scholar]
- Huang, Z.; Yang, P.; Zhou, C.; Wu, W.; Zhang, N. Joint Sensing and Communication for mmWave VR in Metaverse: A Meta-Learning Approach. IEEE Internet Things J. 2024, 11, 24049–24060. [Google Scholar] [CrossRef]
- Zhang, J.; Xi, R.; He, Y.; Sun, Y.; Guo, X.; Wang, W.; Na, X.; Liu, Y.; Shi, Z.; Gu, T. A survey of mmWave-based human sensing: Technology, platforms and applications. IEEE Commun. Surv. Tutor. 2023, 25, 2052–2087. [Google Scholar] [CrossRef]
- Grossi, E.; Lops, M.; Tulino, A.M.; Venturino, L. Opportunistic sensing using mmWave communication signals: A subspace approach. IEEE Trans. Wirel. Commun. 2021, 20, 4420–4434. [Google Scholar] [CrossRef]
- Zhang, X.; Li, Z.; Zhang, J. Synthesized millimeter-waves for human motion sensing. In Proceedings of the 20th ACM Conference on Embedded Networked Sensor Systems (ACM SenSys), Boston, MA, USA, 6–9 November 2022. [Google Scholar]
- Zhang, D.; Zhang, X.; Xie, Y.; Zhang, F.; Yang, H.; Zhang, D. From Single-Point to Multi-Point Reflection Modeling: Robust Vital Signs Monitoring via mmWave Sensing. IEEE Trans. Mob. Comput. 2024, 23, 14959–14974. [Google Scholar] [CrossRef]
- Yang, Z.; Zhou, Z.; Liu, Y. From RSSI to CSI: Indoor localization via channel response. ACM Comput. Surv. 2013, 46, 25. [Google Scholar] [CrossRef]
- Tan, S.; Ren, Y.; Yang, J.; Chen, Y. Commodity WiFi sensing in ten years: Status, challenges, and opportunities. IEEE Internet Things J. 2022, 9, 17832–17843. [Google Scholar] [CrossRef]
- Chen, C.; Zhou, G.; Lin, Y. Cross-domain WiFi sensing with channel state information: A survey. ACM Comput. Surv. 2023, 55, 231. [Google Scholar] [CrossRef]
- Ma, Y.; Zhou, G.; Wang, S. Wifi sensing with channel state information: A survey. ACM Comput. Surv. (CSUR) 2019, 52, 46. [Google Scholar] [CrossRef]
- He, Y.; Liu, J.; Li, M.; Yu, G.; Han, J.; Ren, K. Sencom: Integrated sensing and communication with practical WiFi. In Proceedings of the 29th Annual International Conference on Mobile Computing and Networking (ACM MobiCom), Madrid, Spain, 2–6 October 2023. [Google Scholar]
- He, Y.; Liu, J.; Li, M.; Yu, G.; Han, J. Forward-compatible integrated sensing and communication for WiFi. IEEE J. Sel. Areas Commun. 2024, 42, 2440–2456. [Google Scholar] [CrossRef]
- Lu, L.; Chen, M.; Yu, J.; Ba, Z.; Lin, F.; Han, J.; Zhu, Y.; Ren, K. An imperceptible eavesdropping attack on WiFi sensing systems. IEEE/ACM Trans. Netw. 2024, 32, 4009–4024. [Google Scholar] [CrossRef]
- Li, C.; Xu, M.; Du, Y.; Liu, L.; Shi, C.; Wang, Y.; Liu, H.; Chen, Y. Practical adversarial attack on WiFi sensing through unnoticeable communication packet perturbation. In Proceedings of the 30th Annual International Conference on Mobile Computing and Networking (ACM MobiCom), Washington, DC, USA, 30 September–4 October 2024. [Google Scholar]
- Abedi, A.; Vasisht, D. Non-cooperative Wi-Fi localization & its privacy implications. In Proceedings of the 28th Annual International Conference On Mobile Computing And Networking (ACM MobiCom), Sydney, Australia, 17–21 October 2022. [Google Scholar]
- Gjengset, J.; Xiong, J.; McPhillips, G.; Jamieson, K. Accurate indoor localization with zero start-up cost. In Proceedings of the 20th Annual International Conference on Mobile Computing and Networking (ACM MobiCom), Maui, HI, USA, 7–11 September 2014. [Google Scholar]
- Huang, P.; Zhang, X.; Yu, S.; Guo, L. Is-wars: Intelligent and stealthy adversarial attack to Wi-Fi-based human activity recognition systems. IEEE Trans. Dependable Secur. Comput. 2021, 19, 3899–3912. [Google Scholar] [CrossRef]
- Hernandez, S.M.; Bulut, E. Adversarial occupancy monitoring using one-sided through-wall WiFi sensing. In Proceedings of the ICC 2021-IEEE International Conference on Communications, Montreal, QC, Canada, 14–23 June 2021; pp. 1–6. [Google Scholar]
- Staat, P.; Mulzer, S.; Roth, S.; Moonsamy, V.; Heinrichs, M.; Kronberger, R.; Sezgin, A.; Paar, C. IRShield: A countermeasure against adversarial physical-layer wireless sensing. In Proceedings of the 2022 IEEE Symposium on Security and Privacy (IEEE S&P), San Francisco, CA, USA, 22–26 May 2022. [Google Scholar]
- Ayyalasomayajula, R.; Arun, A.; Sun, W.; Bharadia, D. Users are closer than they appear: Protecting user location from WiFi aps. In Proceedings of the 24th International Workshop on Mobile Computing Systems and Applications (ACM HotMobile), Newport Beach, CA, USA, 22–23 February 2023. [Google Scholar]
- Fang, Z.; Fu, B.; Qin, Z.; Zhang, F.; Zhang, D. PrivateBus: Privacy identification and protection in large-scale bus WiFi systems. Proc. ACM Interact. Mob. Wearable Ubiquitous Technol. 2020, 4, 9. [Google Scholar] [CrossRef]
- Konings, B.; Schaub, F.; Weber, M. PriFi beacons: Piggybacking privacy implications on WiFi beacons. In Proceedings of the 2013 ACM Conference on Pervasive and Ubiquitous Computing Adjunct Publication (ACM Ubicomp), Zurich, Switzerland, 8–12 September 2013; pp. 83–86. [Google Scholar]
- Zhou, Y.; Chen, H.; Huang, C.; Zhang, Q. WiADv: Practical and robust adversarial attack against WiFi-based gesture recognition system. Proc. ACM Interact. Mob. Wearable Ubiquitous Technol. 2022, 6, 92. [Google Scholar] [CrossRef]
- Liu, J.; He, Y.; Xiao, C.; Han, J.; Cheng, L.; Ren, K. Physical-world attack towards WiFi-based behavior recognition. In Proceedings of the IEEE INFOCOM—IEEE Conference on Computer Communications, London, UK, 2–5 May 2022; pp. 400–409. [Google Scholar]
- Song, J.; Qian, C.; Guo, Y.; Hua, K.; Yu, W. Attack evaluations of deep learning empowered WiFi sensing in IoT systems. In Proceedings of the IEEE INFOCOM—IEEE Conference on Computer Communications, Hoboken, NJ, USA, 20 May 2023; pp. 1–6. [Google Scholar]
- Liu, Z.; Xu, C.; Xie, Y.; Sie, E.; Yang, F.; Karwaski, K.; Singh, G.; Li, Z.L.; Zhou, Y.; Vasisht, D.; et al. Exploring practical vulnerabilities of machine learning-based wireless systems. In Proceedings of the 20th USENIX Symposium on Networked Systems Design and Implementation (NSDI 23), Boston, MA, USA, 17–19 April 2023; pp. 1801–1817. [Google Scholar]
- Xu, L.; Zheng, X.; Li, X.; Zhang, Y.; Liu, L.; Ma, H. WiCAM: Imperceptible adversarial attack on deep learning based WiFi sensing. In Proceedings of the 19th Annual IEEE International Conference on Sensing, Communication, and Networking (SECON), Stockholm, Sweden, 20–23 September 2022; pp. 10–18. [Google Scholar]
- Zhou, Y.; Li, C.; Chen, H.; Zhang, Q. RIStealth: Practical and covert physical-layer attack against WiFi-based intrusion detection via reconfigurable intelligent surface. In Proceedings of the 21st ACM Conference on Embedded Networked Sensor Systems (ACM SenSys), Istanbul, Turkey, 12–17 November 2023; pp. 195–208. [Google Scholar]
- Shi, Y.; Zhang, X.; Fu, L.; Zhang, H. An investigation of the private-attribute leakage in WiFi sensing. High-Confid. Comput. 2024, 4, 100209. [Google Scholar] [CrossRef]
- Lu, L.; Ba, Z.; Lin, F.; Han, J.; Ren, K. ActListener: Imperceptible activity surveillance by pervasive wireless infrastructures. In Proceedings of the IEEE 42nd International Conference on Distributed Computing Systems (ICDCS), Bologna, Italy, 10–13 July 2022; pp. 776–786. [Google Scholar]
- Cui, T.J.; Qi, M.Q.; Wan, X.; Zhao, J.; Cheng, Q. Coding metamaterials, digital metamaterials and programmable metamaterials. Light Sci. Appl. 2014, 3, e218. [Google Scholar] [CrossRef]
- Zhang, L.; Chen, X.Q.; Liu, S.; Zhang, Q.; Zhao, J.; Dai, J.Y.; Bai, G.D.; Wan, X.; Cheng, Q.; Castaldi, G.; et al. Space-time-coding digital metasurfaces. Nat. Commun. 2018, 9, 4334. [Google Scholar] [CrossRef]
- Li, L.; Cui, T.J.; Ji, W.; Liu, S.; Ding, J.; Wan, X.; Li, Y.B.; Jiang, M.; Qiu, C.-W.; Zhang, S. Electromagnetic reprogrammable coding-metasurface holograms. Nat. Commun. 2017, 8, 197. [Google Scholar] [CrossRef] [PubMed]
- Cui, T.-J.; Liu, S.; Li, L.-L. Information entropy of coding metasurface. Light Sci. Appl. 2016, 5, e16172. [Google Scholar] [CrossRef] [PubMed]
- Chen, L.; Hu, W.; Jamieson, K.; Chen, X.; Fang, D.; Gummeson, J. Pushing the physical limits of IoT devices with programmable metasurfaces. In Proceedings of the 18th USENIX Symposium on Networked Systems Design and Implementation (NSDI), Virtual Event, 12–14 April 2021. [Google Scholar]
- Li, X.; Feng, C.; Song, F.; Jiang, C.; Zhang, Y.; Li, K.; Zhang, X.; Chen, X. Protego: Securing wireless communication via programmable metasurface. In Proceedings of the 28th Annual International Conference on Mobile Computing And Networking (ACM MobiCom), Sydney, Australia, 17–21 October 2022. [Google Scholar]
- Li, X.; Feng, C.; Wang, X.; Zhang, Y.; Xie, Y.; Chen, X. RF-bouncer: A programmable dual-band metasurface for sub-6 wireless networks. In Proceedings of the 20th USENIX Symposium on Networked Systems Design and Implementation (NSDI), Boston, MA, USA, 17–19 April 2023. [Google Scholar]
- Zheng, Y.; Zhang, Y.; Qian, K.; Zhang, G.; Liu, Y.; Wu, C.; Yang, Z. Zero-effort cross-domain gesture recognition with Wi-Fi. In Proceedings of the 17th Annual International Conference on Mobile Systems, Applications, and Services (ACM MobiSys), Seoul, Republic of Korea, 17–21 June 2019. [Google Scholar]
- Guo, L.; Wang, L.; Lin, C.; Liu, J.; Lu, B.; Fang, J.; Liu, Z.; Shan, Z.; Yang, J.; Guo, S. Wiar: A public dataset for Wifi-based activity recognition. IEEE Access 2019, 7, 154935–154945. [Google Scholar] [CrossRef]
- Agyemang, J.O.; Kponyo, J.J.; Acquah, I. Lightweight Man-In-The-Middle (MITM) detection and defense algorithm for WiFi-Enabled Internet of Things (IoT) gateways. Inf. Secur. Comput. Fraud 2019, 7, 1–6. [Google Scholar]
- Martínez, J.; Durán, J.M. Software supply chain attacks, a threat to global cybersecurity: SolarWinds’ case study. Int. J. Saf. Secur. Eng. 2021, 11, 537–545. [Google Scholar] [CrossRef]
- Ge, Y.; Ching, P.C. Energy efficiency for proactive eavesdropping in cooperative cognitive radio networks. IEEE Internet Things J. 2022, 9, 13443–13457. [Google Scholar] [CrossRef]
- Zhou, S.; Zhang, W.; Peng, D.; Liu, Y.; Liao, X.; Jiang, H. Adversarial WiFi sensing for privacy preservation of human behaviors. IEEE Commun. Lett. 2019, 24, 259–263. [Google Scholar] [CrossRef]
- Li, Y.; Zhu, T. Gait-based Wi-Fi signatures for privacy-preserving. In Proceedings of the 11th ACM on Asia Conference on Computer and Communications Security (ASIA CCS), Xi’an, China, 30 May–3 June 2016; pp. 571–582. [Google Scholar]
- Zhao, P.; Liu, W.; Zhang, G.; Li, Z.; Wang, L. Preserving privacy in WiFi localization with plausible dummy locations. IEEE Trans. Veh. Technol. 2020, 69, 11909–11925. [Google Scholar] [CrossRef]
- Yang, J.; Zou, H.; Xie, L. Securesense: Defending adversarial attack for secure device-free human activity recognition. IEEE Trans. Mob. Comput. 2022, 23, 823–834. [Google Scholar] [CrossRef]
- Zhang, W.; Zhou, S.; Peng, D.; Yang, L.; Li, F.; Yin, H. Understanding and modeling of WiFi signal-based indoor privacy protection. IEEE Internet Things J. 2020, 8, 2000–2010. [Google Scholar] [CrossRef]
- Jiang, J.; Wang, J.; Liu, Y.; Chen, Y.; Liu, Y. WiCloak: Protect location privacy of WiFi devices. In Proceedings of the 23rd ACM/IEEE International Conference on Information Processing in Sensor Networks (IPSN), Hong Kong, China, 13–16 May 2024; pp. 101–112. [Google Scholar]
- Chen, Y.; Wang, W.; Zhang, Q. Privacy-preserving location authentication in WiFi with fine-grained physical layer information. In Proceedings of the 2014 IEEE Global Communications Conference, Austin, TX, USA, 8–12 December 2014; pp. 4827–4832. [Google Scholar]
- Wang, Z.; Xu, Y.; Yan, Y.; Ouyang, X.; Zhang, B. Privacy-preserving WiFi localization based on inner product encryption in a cloud environment. IEEE Internet Things J. 2024, 11, 17264–17282. [Google Scholar] [CrossRef]
- Rusca, R.; Carluccio, A.; Casetti, C.; Giaccone, P. Privacy-preserving WiFi-based crowd monitoring. Trans. Emerg. Telecommun. Technol. 2024, 35, e4956. [Google Scholar] [CrossRef]
- Hassan, M.U.; Rehmani, M.H.; Chen, J. Differential Privacy Techniques for Cyber Physical Systems: A survey. IEEE Commun. Surv. Tutor. 2019, 22, 746–789. [Google Scholar] [CrossRef]
- Zhao, C.; Zhao, S.; Zhao, M.; Chen, Z.; Gao, C.Z.; Li, H.; Tan, Y.A. Secure Multi-Party Computation: Theory, practice and applications. Inf. Sci. 2018, 476, 357–372. [Google Scholar] [CrossRef]

| Method | Category | Attack Aim | Sensing Scenario | Potential Defense |
|---|---|---|---|---|
| WiAdv [60] | Active attack | Introducing disturbance to the channel to decrease the sensing performance | Gesture recognition | Physical isolation Interference suppression |
| Liu et al. [61] | Active attack | Introducing CSI absence to decrease the sensing performance | Gesture recognition | Physical isolation Interference suppression Anomaly detection |
| Song et al. [62] | Active attack | Injecting false data to sensing datasets to decrease the sensing performance | Activity recognition | Adversarial training Anomaly detection |
| Li et al. [51] | Active attack | Manipulating WiFi preambles to decrease the sensing performance | Activity recognition User authentication | Adversarial training Anomaly detection |
| Liu et al. [63] | Active attack | Introducing disturbance to the channel to decrease the sensing performance | Location estimation | Adversarial training Anomaly detection |
| WiCAM [64] | Active attack | Introducing adversarial noise in the received signals to decrease the sensing performance | Gesture recognition Activity recognition User authentication | Adversarial training Anomaly detection |
| RIStealth [65] | Active attack | Rendering a moving individual undetectable by WiFi intrusion detection systems | Intrusion detection | Anomaly detection Device upgrade |
| IS-WARS [54] | Active attack | Injecting cross-technology signals to the channel to decrease the sensing performance | Activity recognition | Signal processing Adversarial training |
| Shi et al. [66] | Passive attack | Identifying users’ private information in sensing datasets, like height and weight | Gesture recognition Activity recognition | Data anonymization |
| Hernandez et al. [55] | Passive attack | Tracking and counting the flow of traffic throughout a building | Occupancy monitoring Crowd counting | Physical isolation Channel disturbance |
| ActListener [67] | Passive attack | Eavesdropping on user activities imperceptibly in any location of user sensing area | Activity recognition | Physical isolation Channel disturbance |
| WiPeep [52] | Passive attack | Eavesdropping locations of indoor WiFi devices | Location estimation | Randomizing ToF Fake packets detection |
| Method | Category | Defense Aim | Sensing Scenario | Targeted Attack |
|---|---|---|---|---|
| Zhou et al. [80] | Active defense | Misclassifying the private type of information while the others still are recognizable | Activity recognition | Information eavesdropping Behavioral snooping |
| Wobly [81] | Active defense | Anonymizing users’ identities when performing accurate gait authentication | Gait recognition | Information eavesdropping Behavioral snooping |
| IRShield [56] | Active defense | Obfuscating wireless channels to prevent overhearing of sensitive information | Motion detection | Information eavesdropping Behavioral snooping |
| MIRAGE [57] | Active defense | Utilizing the downlink physical layer information to defense eavesdropper | Location estimation | Information eavesdropping Location snooping |
| Zhao et al. [82] | Active defense | Creating plausible dummy locations to preserve indoor localization information | Location estimation | Information eavesdropping Location snooping |
| SecureSense [83] | Active defense | Achieving consistent predictions of WiFi sensing systems regardless of input perturbations | Activity recognition | Adversarial attack |
| Zhang et al. [84] | Active defense | Decreasing the recognition accuracy of the protected semantic significantly | User authentication Activity recognition | Information eavesdropping Identity snooping Activity snooping |
| WiCloak [85] | Active defense | Rendering location information obtained by eavesdroppers meaningless | Location estimation | Information eavesdropping Location snooping |
| PriFi [59] | Passive defense | Helping users to perceive ongoing observations from systems in the user’s current environment | \ | Information eavesdropping |
| PriLa [86] | Passive defense | Facilitating location authentication without compromising user’s location privacy | Location estimation | Information eavesdropping Location snooping |
| Wang et al. [87] | Passive defense | Protecting user’s positioning results in cloud-based indoor positioning systems | Location estimation | Information eavesdropping Location snooping |
| Rusca et al. [88] | Passive defense | Performing crowd counting and tracking within large-scale gatherings | Crowd monitoring | Information eavesdropping Crowd flow snooping |
| PrivateBus [58] | Passive defense | Protecting users from the leaked information in bus WiFi systems | Foot trace tracking Finger trace tracking | Information eavesdropping Trace snooping |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, X.; Meng, X.; Duan, H.; Hu, Z.; Wang, M. A Survey on Secure WiFi Sensing Technology: Attacks and Defenses. Sensors 2025, 25, 1913. https://doi.org/10.3390/s25061913
Liu X, Meng X, Duan H, Hu Z, Wang M. A Survey on Secure WiFi Sensing Technology: Attacks and Defenses. Sensors. 2025; 25(6):1913. https://doi.org/10.3390/s25061913
Chicago/Turabian StyleLiu, Xingyu, Xin Meng, Hancong Duan, Ze Hu, and Min Wang. 2025. "A Survey on Secure WiFi Sensing Technology: Attacks and Defenses" Sensors 25, no. 6: 1913. https://doi.org/10.3390/s25061913
APA StyleLiu, X., Meng, X., Duan, H., Hu, Z., & Wang, M. (2025). A Survey on Secure WiFi Sensing Technology: Attacks and Defenses. Sensors, 25(6), 1913. https://doi.org/10.3390/s25061913






