1. Introduction
Blockchain technology, as a distributed ledger system, provides a revolutionary solution for decentralized transaction verification and data storage [
1,
2,
3,
4,
5,
6], such as dynamic sharding schemes like DBShard [
7] and DRLBShard [
8]. These existing solutions mainly focus on adjusting the size and number of shards to optimize system performance, which may not be suitable for resource-constrained IoT blockchain networks. Therefore, how to effectively improve the throughput and security performance of IoT blockchain sharding systems has become a key research issue.
To improve system throughput and efficiency, transactions in sharding blockchains are processed by multiple committees in parallel. However, at the beginning of each epoch, nodes take time to form committees, and the imbalance in latency between committees increases the transaction confirmation time, thereby reducing blockchain throughput. Therefore, it is necessary to investigate how to efficiently schedule committees to reduce transaction waiting time and improve system performance [
9]. In addition, in dynamic IoT environments, the system faces a number of challenges that can impact the stability of committees and the overall performance of the system. For example, joining and leaving of nodes, fluctuations in transmission latency, and attacks by malicious nodes can lead to changes in committee members, which impacts the stability of the system [
10]. Existing sharding protocols generally perform well in static network environments, but are relatively poorly adapted to dynamic changes, which may lead to performance fluctuations and security risks. Therefore, establishing effective scheduling committees to optimize system performance and ensure security in dynamic environments becomes a feasible way to address these challenges.
In this paper, a committee utility optimization scheduling algorithm (CSA) is proposed for IoT blockchain sharding. The CSA algorithm can dynamically adapt to the changes of the committees in real time, autonomously select the optimal committee, and quickly adjust the scheduling strategy when the committee members change. This ensures high throughput and stability in dynamic environments. In addition, CSA offers low latency, high real-time performance, and robust security against attacks such as Sybil and eclipse attacks. The proposed optimization algorithm not only solves the problem of inefficient scheduling in IoT blockchain systems, but also enhances the robustness of the system to handle dynamic node changes, network latency fluctuations, and various security challenges. Specifically, the contributions of this paper are described as follows.
We propose an IoT blockchain Committee Scheduling Algorithm (CSA), which enables the system to prioritize committees with strong processing capabilities and low latency, thereby enhancing system efficiency and reducing transaction latency.
CSA improves the committee scheduling optimization framework by incorporating transaction fees as a metric, making the system’s utility considerations more comprehensive and optimized. By designing a well-structured Markov chain state space and transition probability matrix, it achieves iterative optimization among feasible solutions, ultimately selecting the best committee scheduling scheme, thus addressing the inefficiency issues in IoT blockchain systems.
CSA adopts Kullback–Leibler (KL) divergence to analyze performance disturbances, replacing the traditional total variation distance, thus providing a more precise method for measuring distribution deviations and offering a solid theoretical foundation for disturbance analysis in complex systems. The committee scheduling optimization framework effectively handles uncertainties such as dynamic node changes and network latency fluctuations in IoT environments, and can mitigate security threats like Sybil and eclipse attacks, thereby enhancing the system’s security.
The remainder of this paper is organized as follows:
Section 2 reviews related work on blockchain sharding and IoT blockchain technologies.
Section 3 presents the proposed CSA, including problem definition, technical details, algorithm implementation, and convergence analysis.
Section 4 offers a theoretical analysis and performance evaluation. Finally,
Section 5 summarizes the paper and discusses future research directions.
2. Related Work
Blockchain sharding technology, with its characteristics of scalability, decentralization, security, and anonymity, makes it a promising solution to address the challenges in the Internet of Things (IoT). Many representative sharding blockchain protocols have been proposed [
11,
12,
13]. For example, Zamani et al. [
14] proposed RapidChain, a fault-tolerant sharding protocol for permissionless blockchains. RapidChain leverages efficient cross-shard verification methods to improve throughput, and eliminates the need for flood broadcasting messages. To improve the efficiency of cross-shard transactions, Amiri et al. [
15] introduced SharPer, a permissioned blockchain system that improves scalability by reallocating different data shards to different network clusters. Wang et al. [
16] proposed a blockchain sharding scheme—Node Rating Sharding (NRS). This approach evaluates and selects nodes with high reputation for shard participation, thereby improving system security and shard resilience while reducing threats from nodes with low reputation. Nguyen et al. [
17] introduced OptChain, a new shard placement approach aimed at reducing the number of cross-shard transactions. Similarly, Dang et al. [
18] developed a generic distributed transaction protocol for blockchain sharding, which improves the efficiency of shard generation by utilizing Elastico.
Regarding IoT blockchain systems, scholars have recently proposed several methods and projects. For example, Aptos adopted a new consensus protocol that optimizes the throughput and scalability of a sharding network, with a focus on improving cross-chain performance and security [
19]. Sui used the Narwhal consensus mechanism to improve system throughput and parallel processing of transactions, especially for IoT applications with low-latency requirements [
20]. Linera employed a hybrid protocol combining asynchronous and synchronous consensus that optimizes the integration of sharding and blockchain and improves system efficiency [
21]. Fuel utilized parallel execution technology to reduce transaction latency and enhance throughput, making it an ideal solution for IoT networks with high-performance requirements [
22]. Wang et al. [
23] proposed TransShard, a transaction-aware sharding scheme that dynamically adjusts the sharding strategy according to the transaction characteristics of account-based blockchains, thus improving the transaction efficiency and system throughput. Wei et al. [
24] presented FCDSB, a fog computing network architecture based on dynamic blockchain sharding.FCDSB is designed for consumer electronics in the Artificial Intelligence of Things (AIoT) to optimize the allocation of computing resources and enhance security. Li et al. [
25] proposed a dynamic blockchain sharding scheme based on graph partitioning, and they optimized load balancing and cross-shard communication efficiency using the graph partitioning methods. Regarding the storage issue, Peng et al. [
26] presented a clustering-based collaborative storage scheme for blockchain applications in IoT systems. This scheme optimizes storage allocation among nodes and improves the storage efficiency and scalability of the blockchain network. Additionally, Li et al. [
27] proposed a secure and efficient blockchain sharding scheme by combining hybrid consensus mechanisms and dynamic management, which effectively enhances the security and fault tolerance of the system. Furthermore, Hu et al. [
28] introduced LMChain, an efficient load-migratable beacon-based sharding blockchain system, which further improves the scalability and efficiency of IoT blockchain systems through dynamic load migration and beacon-based sharding mechanisms.
In IoT environments, scholars have proposed an innovative dynamic and adaptive sharding framework, called SmartChain [
29], specifically designed to overcome the inherent challenges of dynamism and heterogeneity in IoT blockchain systems. SmartChain dynamically selects the number of shards, partition structures, and leader selection modes to achieve high throughput and low security risks. To address the problem of limited scalability of IoT frameworks, Wu et al. [
30] proposed a novel blockchain-integrated sharding algorithm by analysing transaction records of frequently interacting sender–receiver pairs. Furthermore, considering the uniqueness of IoT environments, Xi et al. [
31] proposed HMMDShard, a dynamic blockchain sharding scheme based on hidden Markov models (HMMs). HMMDShard achieves adaptive dynamic incremental updates of blockchain shards by integrating HMMs, effectively reducing cross-shard transactions across all shards. Aiming at storage and computation issues in IoT environments, Pan et al. [
32] proposed HyperChain, a dynamic state sharding protocol that supports smart contract execution, which achieves low cross-shard communication and good scalability. This scheme optimizes the efficiency of cross-shard communication through intelligent sharding strategies, enhancing the overall performance of the blockchain. Based on the above analysis, most solutions focus on shard generation, optimization of cross-shard transactions, and improving system throughput and security. However, there is still room for further improvements in enhancing overall system efficiency, addressing challenges in dynamic IoT environments, and improving cross-shard communication efficiency.
In summary, we have summarized typical related works in
Table 1. To address the issue of unbalanced two-phase latency caused by member committees in IoT environments and to accelerate the process of performing final consensus in the final committee, we propose our algorithm, CSA. This algorithm aims to improve block generation efficiency and the overall throughput of the blockchain system while enhancing system security.
3. CSA Algorithm
In this study, we formalize the trade-off relationships among transaction throughput, cumulative transaction waiting time, and transaction fees into a utility maximization problem and propose a committee scheduling algorithm to solve it. This section introduces the proposed method and provides an analysis from the perspectives of problem definition, Markov chain design, and the CSA.
3.1. Algorithm Framework
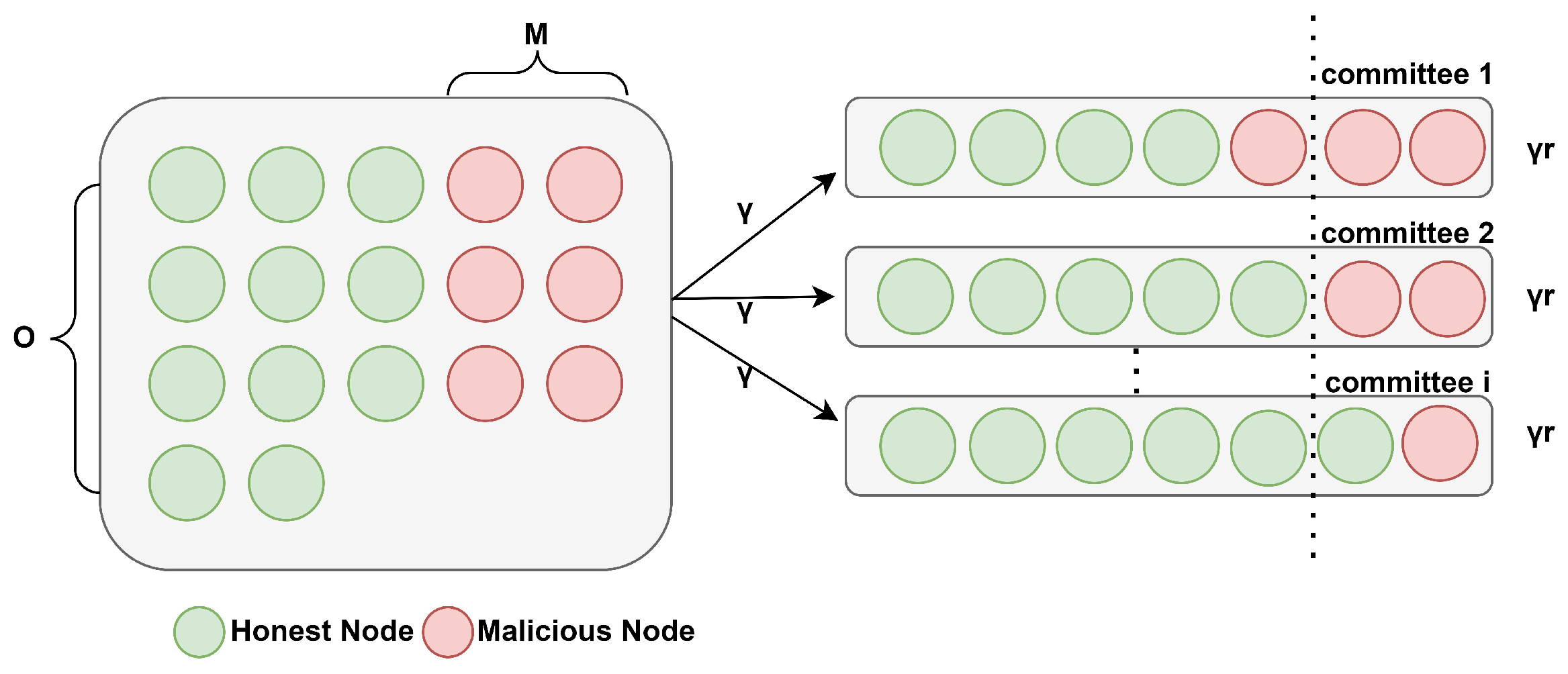
The algorithm framework is shown in
Figure 1. The first part is the construction of committees before the algorithm implementation and the two-stage latency of the committees. In this part, committees are formed through a proof-of-work-based election mechanism, which causes the committee formation latency. This is followed by the internal consensus phase within the committee, known as consensus latency. Then, committees are selected as feasible solutions. To make the problem clearer and solvable, we use Log-Sum-Exp approximation (see
Section 3.2) to simplify the problem. Next, using the iterative optimization idea based on the Markov chain (see
Section 3.3), feasible solutions are continuously iterated and optimized to select the optimal solution based on the transition probability matrix. The specific process of the algorithm (see
Section 3.4) includes the algorithm flow and the derivation of the algorithm’s convergence. Finally, the best committee combination selected is submitted to the final committee, forming the final block.
The committee scheduling problem is modeled in a blockchain sharding system, which operates within epochs . The committees are divided into member committees and the final committee. The final committee is responsible for generating the final block on the root chain, while the other committees are referred to as member committees. The shards generated by the member committees are represented by the set . A binary variable is defined to indicate whether committee is allowed to participate in the final consensus phase of period . The total two-phase latency set of each member committee is represented by , while the number of transactions in each committee is denoted by . Additionally, is introduced to represent the given deadline (DDL) used to evaluate the shards received in epoch j.
When the transaction capacity of the final block is constrained, a predefined DDL should be minimized to expedite the generation process of the final block. In the experiments, the DDL is defined as a fixed proportion of the time taken by the member committees to submit their shards to the designated committee. Consequently, the DDL is defined as
, which can be calculated as the sum of the time from the committee formation phase to the specified DDL. Furthermore, the cumulative time
for all transactions encapsulated in each shard
can be computed.
The objectives of the problem are to (1) maximize the total number of transactions processed by the final committee, (2) reduce the overall cumulative time for these transactions, and (3) increase the transaction fees collected by the committees. The first objective aligns with improving the throughput of the main chain, the second relates to enhancing the timeliness of transactions distributed across allowed shards, and the third focuses on optimizing the committees’ efficiency and boosting the blockchain network’s appeal. As a result, the following utility maximization problem is established:
The constraints are as follows:
In the objective function MUCom, and are adjustable weights that measure the preference for the total number of allowed transactions (TXs) and transaction fees. Constraint (3) specifies that the number of selected member committees in each epoch must be greater than the predefined minimum . In constraint (4), represents the capacity of transactions that can be packaged into the final block during each epoch. Therefore, constraint (4) ensures that the capacity limit of the final block is maintained in every epoch .
3.2. Log-Sum-Exp Approximation
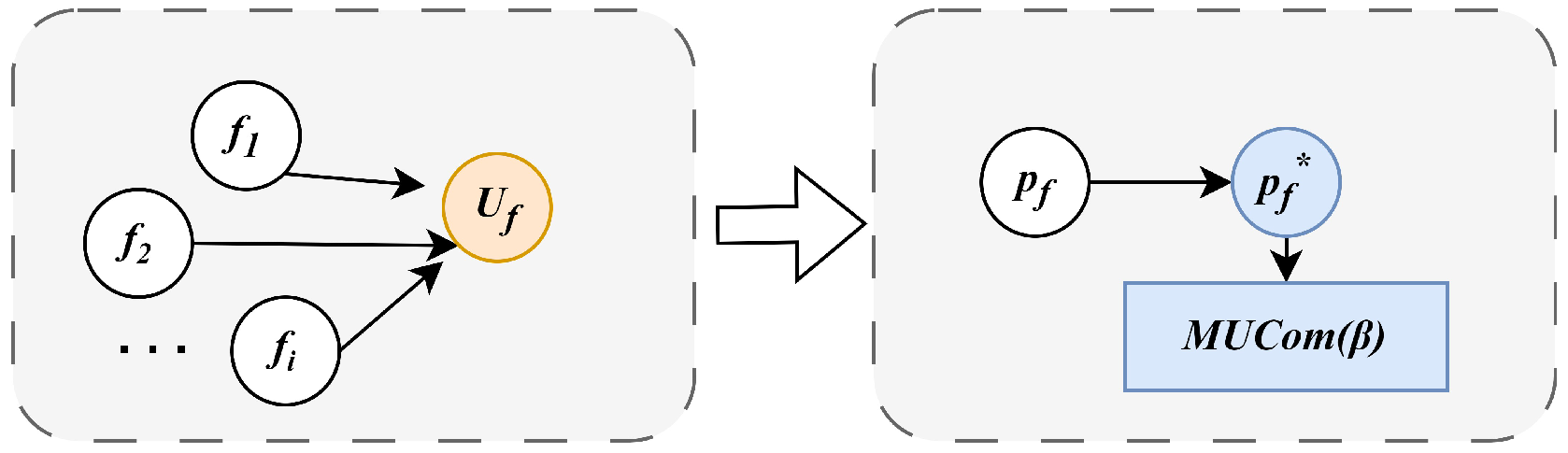
Using the log-sum-exp approximation, the optimal solution to the original problem is represented as a probability distribution, enabling the algorithm to probabilistically identify near-optimal solutions. As shown in
Figure 2, let
f denote a feasible solution to the target problem, where each feasible solution is associated with a probability
, indicating the likelihood of the system selecting
f. This approach defines the problem, approximated by the log-sum-exp technique, as the
problem [
33], where
is a positive scalar that governs the approximation accuracy. The set of approximations of all feasible solutions is regarded as the state space of the Markov chain, and the design of an effective transition probability matrix helps to obtain the optimal solution.
3.3. Markov Chain Design
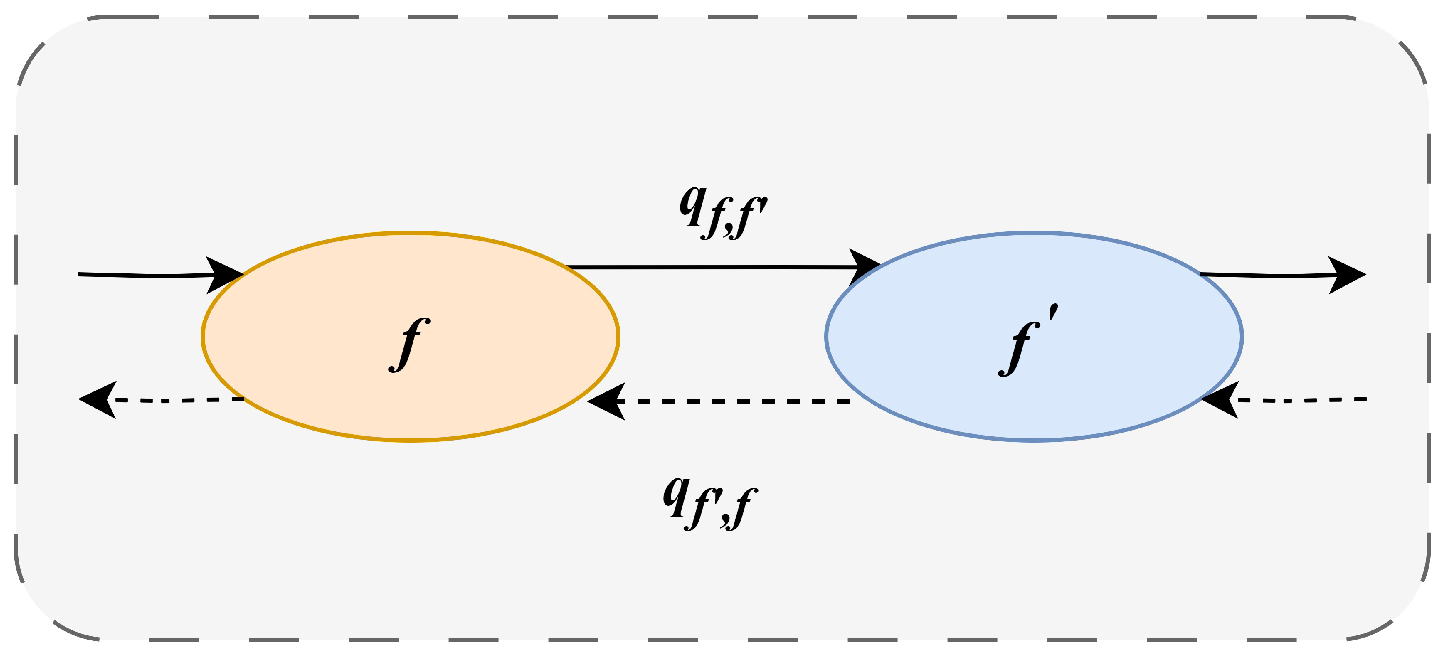
To address the iterative transitions between different committee state sets, a Markov chain-based state transition algorithm is used to optimise the scheduling problem of committees in a sharded blockchain system. Specifically, at each time interval, the system selects the next state according to state transition rules, forming a Markov chain that converges to the optimal solution. In the model, the scheduling scheme for each committee is represented as a state
f, and the entire state space consists of all possible combinations of committee schedules. For each pair of adjacent states
, a transition probability
is defined, which is linked to the utility difference between the two states. In the Markov chain, all states are mutually reachable, and for every pair of adjacent states
, the detailed balance equation
[
34,
35] must hold.
Initially, the transition rate between two solutions
f and
is set to zero until they simultaneously satisfy the following two conditions: (a):
. (b):
, where
i represents the shard responsible for the transition
. In other words, transitions between states do not occur until specific conditions are met, after which state transitions are allowed. This controlled transition ensures local changes in the system rather than large-scale adjustments, which will help the system to remain stable and gradually converge to the optimal solution in the dynamically changing environment of large-scale IoT nodes. The state transitions are shown in
Figure 3. The state transition probabilities for the required Markov chain are designed as follows:
With this design, the system gradually reaches high-utility states, achieving higher efficiency in committee scheduling and transaction verification, while reducing latency and optimizing overall performance. The transition probabilities are designed to gradually approach the optimal state, thereby reducing the latency in committee scheduling and mitigating performance perturbations within the system. Let
represent the optimal solution to the
problem. By solving the Karush–Kuhn–Tucker (KKT) conditions [
36] for
, the steady-state probability for each solution
can be derived as follows:
Due to the iterative nature of the system, state transitions in the designed Markov space correspond to the replacement of member committee sets. Therefore, during the implementation of Markov chain, if the state transitions are trained to converge to the desired steady-state distribution , the system will achieve near-optimal performance. This Markov chain is designed to deviate from time reversibility. Such an approximation algorithm can converge to the globally optimal state relatively quickly. In addition, by adjusting the design of the state transition probabilities, the algorithm ensures that the system maintains robust performance in the presence of dynamic events such as committee members joining or leaving, thus realizing adaptive scheduling adjustments.
Theoretically, the designed Markov chain has good convergence and its mixing time
[
35] is proportional to the complexity of the system’s states, as shown below.
Meanwhile, by adjusting the parameters of the transition probabilities, the algorithm can effectively control the system’s convergence speed and its adaptability in dynamic environments. Experimental results also show that the Markov chain algorithm exhibits strong adaptability and optimization performance in solving complex committee scheduling problems.
3.4. CSA: Committee Utility Optimization Scheduling Algorithm
This section first describes the implementation of the CSA, including the solution construction, algorithm iteration, and real-time monitoring process. Then, the convergence and complexity of the algorithm are discussed.
3.4.1. Algorithm Implementation
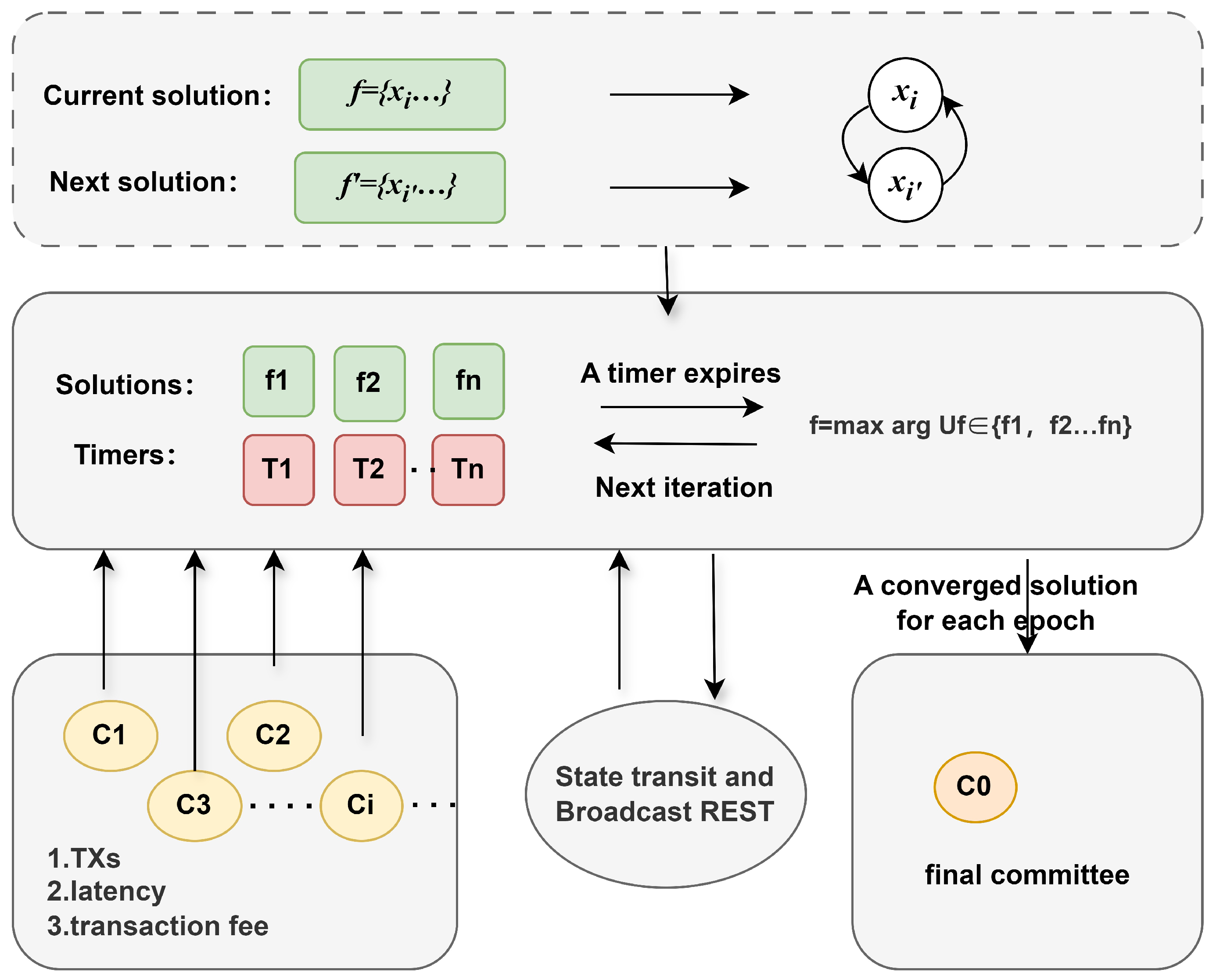
An implementation of the proposed CSA based on Markov chain theory with a well-designed transition-rate matrix is presented in Algorithm 1. CSA is designed to schedule blockchain committees to achieve the optimal solution f. In Lines 1 through 2, it first checks whether the number of committees exceeds the minimum threshold and whether the total number of transactions received exceeds the capacity C. If these conditions are satisfied, the event monitoring process is initiated for the current epoch. Then, in Lines 3 through 7, the algorithm generates possible committee combinations by iteratively constructing the initial solution set while ensuring that the constraints are satisfied.
During each iteration, the algorithm randomly selects two committees
i and
from the current state, setting
and
, respectively. It calculates the current system utility
and the hypothetical utility
, then uses these values to generate a timer
for continuous monitoring.
Figure 4 shows the execution process of the algorithm, where the algorithm runs on multiple independent parallel threads. Each thread executes a set of feasible solutions
and timers
. All parallel threads communicate with the committees in real time, exchanging a limited set of messages such as reset signals and the current system utility.
When a committee joins or leaves, the algorithm dynamically updates the committee set , resets the initial solution set , and reinitialises the timer . When a timer expires, the algorithm exchanges the corresponding committee states and sends a RESET signal to notify other nodes to recalibrate. In addition, the algorithm supports responding to RESET signals by recalculating the timer and adjusting the states accordingly.
The algorithm terminates under two conditions: (1) when the system states converge and the system satisfies the capacity constraint
C, the solution with the highest utility is chosen as the final solution
f; (2) when the number of final committees exceeds the maximum threshold
, the algorithm stops monitoring new incoming committees. Through this process, the algorithm achieves optimal committee scheduling even in dynamic environments.
| Algorithm 1: Committee Scheduling Algorithm |
![Sensors 25 01648 i001]() |
3.4.2. Algorithm Convergence
The time required for the Markov chain to reach convergence can be quantified using the concept of mixing time [
35]. Let
be the probability distribution over all states in the solution space
at time
t, where the initial state is
f, and let
be the static distribution probability of the designed Markov chain. The mixing time can then be defined using the Kullback–Leibler (KL) divergence as follows:
In this context,
denotes the allowable deviation between the converged solution and the optimal solution, while
represents the KL divergence, which quantifies the discrepancy between two probability distributions. For each epoch
, the cardinality of the feasible solution space can be expressed as follows:
The maximum number of transition options is
. The iterative convergence of the proposed algorithm leads to the following conclusions: For a given set of committees, let
and
. With
, the Markov chain has the following constraints on the mixing time
in each epoch [
35,
37]:
As increases, the convergence time has an upper bound. It also grows exponentially with and logarithmically with . Thus, the pursuit of smaller performance loss (i.e., smaller ) leads to a higher upper bound on the convergence time and vice versa. Additionally, as the number of transactions increases, the algorithm needs to process more transactions and dynamic events, which increases the computational overhead. The convergence time also increases as the solution space becomes more complex, with state transitions growing more complex as grows. Therefore, while the algorithm performs well in the simulation experiment, the convergence time still increases significantly as the scale grows.
Next, we analyze the computational complexity of the algorithm. The maximum number of transition options between states is . Although the computation of each individual transition probability is , the overall complexity is , since the transition space is , and each state can transition with other states. The space complexity is primarily determined by the space required to store the state space and the transition probability matrix. Since the size of the state space is , the space required to store the state and transition matrix is . We further explore the trade-off between the optimal solution loss (expressed as ), and the mixing time for different values of . As approaches infinity, the optimal solution loss decreases asymptotically to zero. However, the upper bound of the mixing time grows exponentially at the rate of and diverges to infinity. Consequently, while a larger is effective in minimizing the loss of the solution, it greatly affects the convergence speed, highlighting the important balance between solution accuracy and computational efficiency.
5. Conclusions
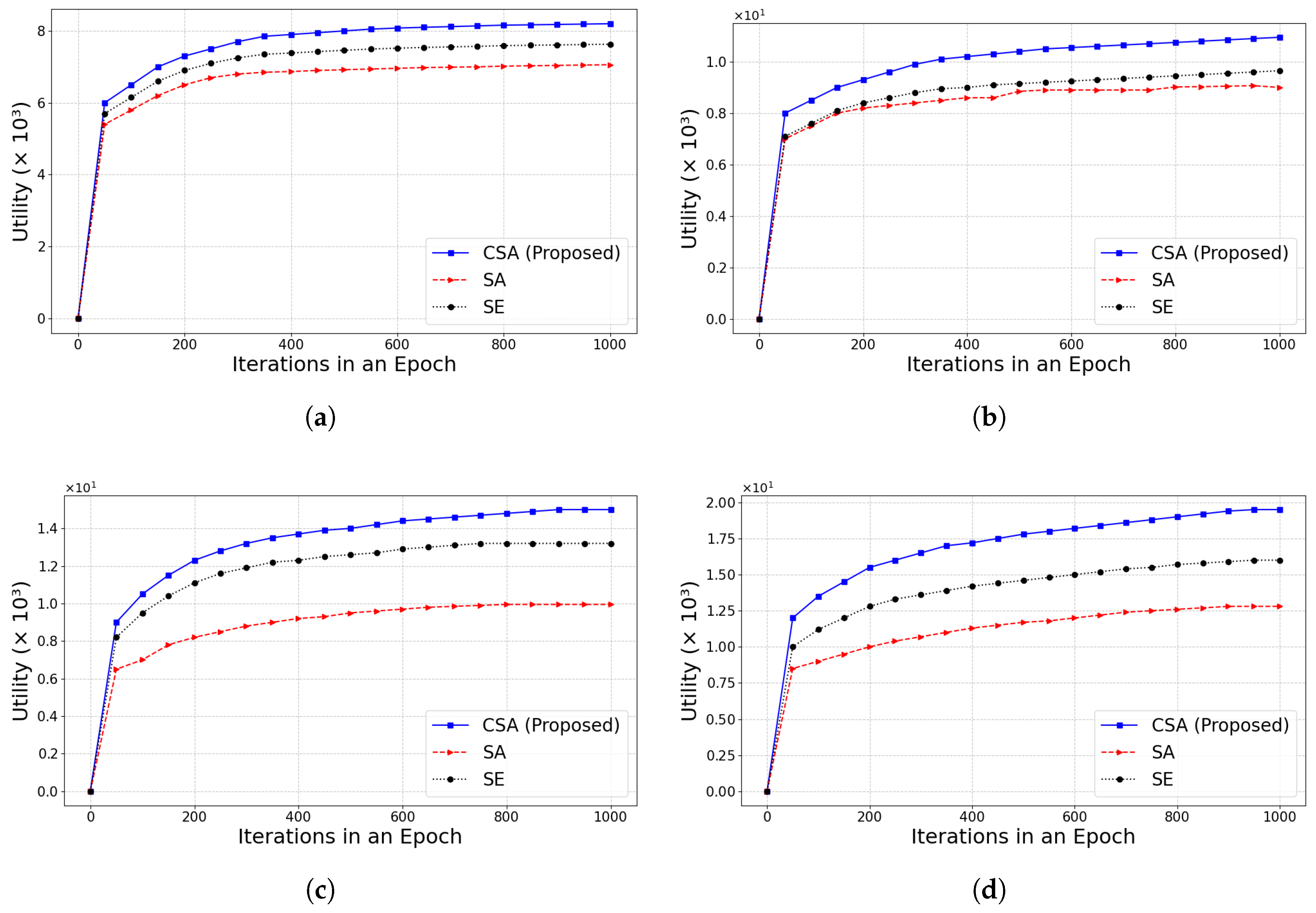
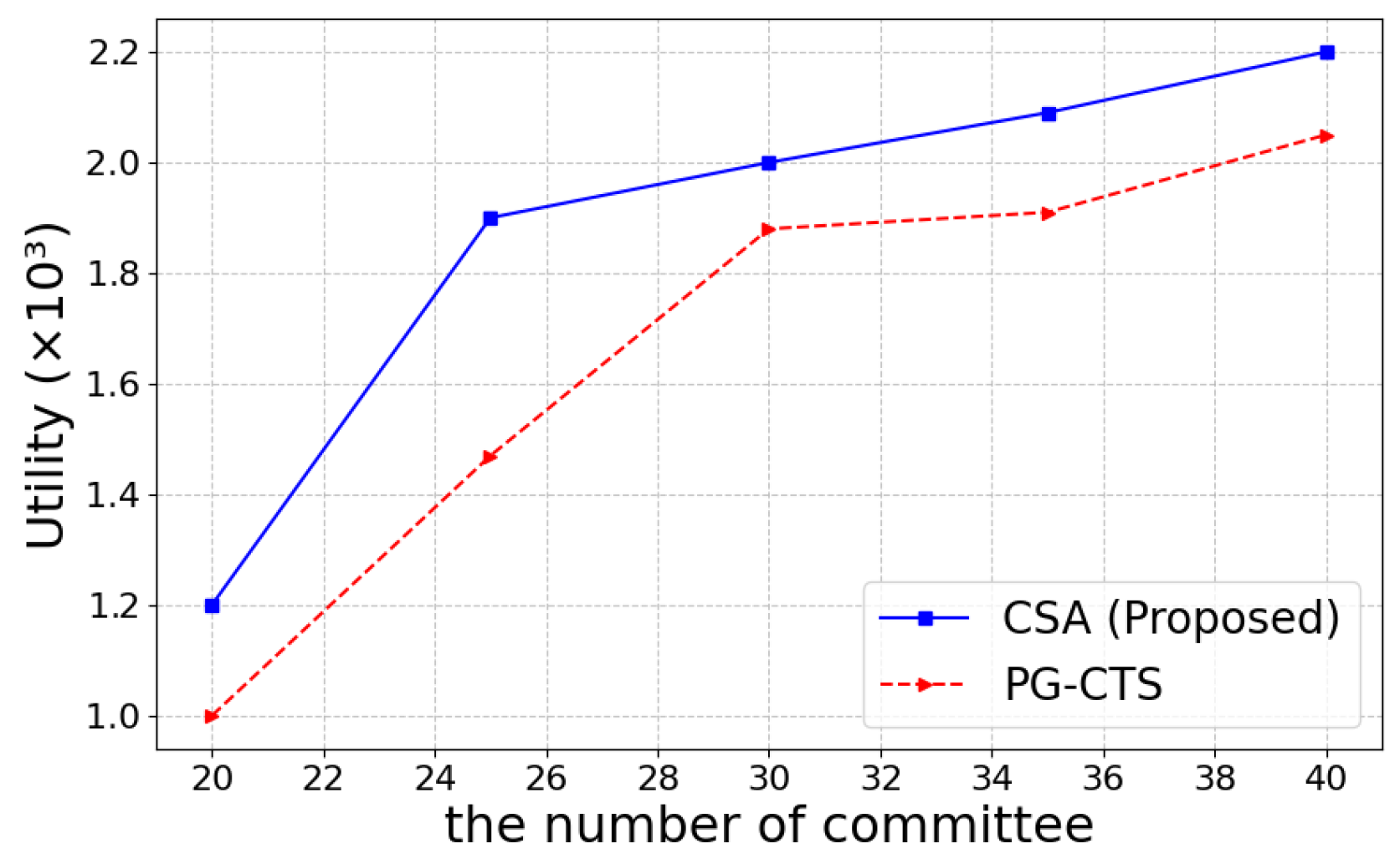
In this paper, we propose an IoT blockchain sharding committee utility optimization scheduling algorithm, called CSA. CSA balances transaction number, cumulative latency, and transaction fees for each epoch, and it addresses these trade-offs using approximation techniques and Markov chain iterative optimization. Theoretical properties of the proposed algorithm, such as convergence time bounds and performance fluctuations caused by committee failures, are critically analyzed. Additionally, a security analysis is performed to evaluate the impact of malicious attacks, such as Sybil and eclipse attacks, on committee failures. Finally, the algorithm’s ability to handle dynamic member committee leaving and joining is also demonstrated.
As blockchain technology continues to evolve and expand into new application domains, future work could explore the scalability of optimization algorithms in large-scale IoT networks and investigate advanced defense mechanisms against emerging attacks. There is also a need to study how to improve the efficiency of the committee selection process in a real-time dynamic environment. The above will be the focus of future research and development to come up with more reliable, secure, and scalable blockchain solutions to meet the demands of IoT.