Abstract
Due to the need for the implementation of various IoT services, novel generation networks are often characterized by a constant requirement for their expansion and a rising number of nodes. The IoT network nodes are usually low power, so security becomes a challenging issue as conventional cryptographic techniques are hard to implement due to power and computational limitations. Besides, wireless power transfer is an appealing approach for powering IoT systems in scenarios where many nodes are placed in hardly accessible areas. Finally, due to a variety of applications, network nodes are often mobile. Motivated by these facts, in this paper, we investigate physical layer security in IoT systems powered by means of a power beacon, where a legitimate user or eavesdropper can be mobile. The closed-form approximate secrecy outage probability expressions are derived for the Nakagami-m fading environment and three scenarios of receiving node mobility, described by using a random waypoint model with mobility patterns in one, two or three dimensions. The accuracy of the obtained analytical expressions is corroborated by an independently developed simulation model.
1. Introduction
The advanced offer of the high-quality services and conditions needed for their provisioning has made interconnecting in new-generation telecommunication networks very challenging. It is well known that the Internet of Things (IoT) concept has significantly transformed everyday life by introducing various advantages in overall life quality through smart homes, smart cities, smart healthcare services, etc. [1]. Moreover, it has also made possible a huge leap in the quality of industrial process organization, making it very efficient through the minimization or exclusion of human involvement [2], which we often refer to as the Industrial IoT concept and services. Therefore, 5G and the next-generation networks that are currently in the development phase have a task to satisfy a wide set of requirements, some of which include a high level of reliability with extremely high maximal data rates, very low tolerable delay values, etc. At the same time, systems are supposed to provide an extensive network coverage area and an increased level of security [3,4].
It is important to highlight that the IoT concept also contributes to the constantly growing number of nodes and brings novel issues related to their powering, as the traditional approach is impractical when an IoT network is placed in a distant area or has no appropriate energy infrastructure. Furthermore, in many IoT scenarios, conventional battery powering is not practical due to difficulties related to changing batteries and access to numerous nodes. As a potential solution for powering, energy harvesting from existing sources, such as solar, wind, mechanical, etc., has been proposed. However, the drawback of these approaches is that they are highly dependent on weather conditions or other circumstances. Although the idea of wireless energy transfer dates back a long time, it has regained attention recently with technological advancements and maturation. Its basic advantage is that it does not depend on weather conditions, while the same approach can be used for the transmission of information and energy [5,6,7,8]. The potential for energy harvesting has been analyzed in various fading environments, including a generalized type of fading [9]. The harvesting from existing interference sources is investigated in [10], while its impact on cognitive radio systems is analyzed in [11]. In general, in the published literature, two important approaches can be distinguished: the first one corresponds to the simultaneous wireless information and power transfer (SWIPT) [12,13,14], while the other assumes that a dedicated source of power exists, which we refer to as a power beacon (PB) [15,16].
While networks with many devices enable the realization of various advanced services, ensuring security in data transmission represents a complex issue [17]. Due to the low power and limited processing capabilities of IoT devices, implementing conventional cryptographic methods is not feasible [18,19,20,21]. Physical layer security analysis has been attractive for various investigations since the pioneering work of Wyner [22]. Investigations related to covert communication with applied multi-antenna techniques for performance improvement are presented in [23,24]. However, it is important to highlight that most of the published papers are related to the analysis of systems with fixed positions of nodes. Although this analysis is very important, scenarios related to 5G and its successors often encompass cases where users are mobile, leading to both variable small-scale and large-scale fading.
1.1. Related Works
User mobility in wireless networks has a significant impact on system performance. Widely accepted models for a user’s random movement are the random direction (RD), which applies a non-uniform spatial distribution [25], and the random waypoint (RWP) model, which is based on uniform spatial distribution [26,27]. The impact of mobility on the system performance when the fading can be described with Nakagami-m distribution is provided in [28], while an analysis of the η–μ fading channels is presented in [29]. In both cases, the pattern of the user’s movement is described based on the RWP model with the movement in one, two or three dimensions. A performance analysis of a network using a power beacon powering approach and time-switching protocol with a randomly moving receiver is provided in [30]. A wirelessly powered cognitive radio system with a controlled interference level based on statistical channel state information (CSI) and a randomly moving receiver is analyzed in [16]. The RWP model is used in [31] to investigate the impact on the outage performance of unmanned aerial vehicle (UAV) communications.
However, the physical layer security of the system with a randomly moving receiver is not widely investigated. The secrecy performance of the networks over N-Nakagami fading channels has been investigated in [32], which is one of the approaches to model mobile vehicular channels. The impact of mobility on the secrecy performance of the cognitive vehicular network is presented in [33,34], but the used method does not reflect various types of movement. In [35], the impact of the receiver movement on the secrecy capacity and the secrecy outage probability is provided for the Rayleigh fading environment. Further, as wireless powering has been recognized as an important approach in enabling the necessary energy for information transmission, the secrecy performance of wirelessly powered wiretap channels was analyzed in [36]. The secrecy outage analysis of the system with power beacon and transmit antenna selection is provided in [37].
1.2. Motivation and Contribution
Wireless power transfer has attracted a lot of attention in scientific literature due to the possibility of providing a practically convenient energy supply. IoT communication networks usually consist of a set of mobile nodes, and the analysis of the impact of the nodes’ mobility is of high importance. Physical layer security is especially important for wirelessly powered networks, as conventional cryptological methods are computationally demanding and impose higher power and processing requirements. However, to the best of the authors’ knowledge, a secrecy performance analysis for the Nakagami-m fading environment with randomly moving nodes is not available in the literature, nor is an analysis of the wirelessly powered systems in these propagation conditions. Motivated by this gap, in this paper, we present the secrecy outage analysis of the IoT system that is supplied by means of a dedicated power beacon based on the time-switching (TS) protocol. We analyze the impact of mobility on the secrecy outage probability in cases when either the legitimate user or an eavesdropper is mobile, as well as when both nodes are mobile. The contributions of the paper are as follows:
- We analyze the secrecy performance of a system in which the transmitter is energy-constrained and uses a power beacon for its energy supply for various scenarios of both the legitimate receiver’s and eavesdropper’s movement patterns. For the description of receiver and eavesdropper mobility, the widely accepted RWP model is used;
- By applying the RWP movement model, we have analyzed cases where a legitimate receiver and/or eavesdropper are moving along the line, in the plane within the circle of a given radius or within the sphere, which correspond to the realistic scenarios where a legitimate receiver and eavesdropper can be positioned in various types of ground vehicles or unmanned aerial vehicles;
- The accurate approximation for the secrecy outage probability is derived in the closed form for the following cases: (1) the legitimate receiver is at the fixed position, while the eavesdropper is moving; (2) the legitimate receiver is moving in accordance with the RWP model, while the eavesdropper is at the fixed position and (3) both the legitimate receiver and eavesdropper are moving;
- The analytical approximate expressions are derived for the Nakagami-m fading propagation environment and are valid for both integer and non-integer fading parameter values;
- We have developed an independent simulation model of the described system and obtained simulation results that confirmed the high accuracy of the approximate analytical expression for the secrecy outage probability;
- Based on the developed analytical framework and simulation model, we have investigated and discussed the impact of the moving pattern, as well as system and channel parameters, on secrecy performance.
Our results can be used for the security analysis of an IoT system with a wireless power supply, positioned in inaccessible or hazardous areas, where data collecting from IoT sensors can be performed using units mounted on mobile ground or aerial vehicles [38], while communication is endangered by eavesdroppers that can also be mobile.
In the following part, we present an entire analysis in detail. In Section 2, we present the system and channel model for three analyzed scenarios of eavesdropper and legitimate receiver mobility. The secrecy performance analysis is presented in Section 3, where the derivation of novel analytical expressions is provided. The results of the numerical analysis and the corresponding discussion are presented in Section 4. Final considerations and conclusions are given in Section 5.
2. System and Channel Model
We consider an IoT system where the transmitter, which is wirelessly powered by means of a power beacon, communicates with the legitimate receiver in the presence of an eavesdropper. The wireless power transfer is performed in accordance with the TS protocol. In this concept, within each time frame of duration T, the first part equal to αT is dedicated to the power transfer, while the remaining part of the time frame, which is equal to (1 − α)T, is used for the transmission of information. The coefficient α (0 < α < 1) denotes the energy-harvesting time ratio.
The system is situated in an environment where the fading envelope of all links can be modeled by Nakagami-m distribution. The distance and the channel envelope between the power beacon and the IoT transmitter are denoted by D1 and h1, while the distance and the channel envelope between the IoT transmitter and the legitimate receiver are denoted by D2 and h2, respectively. The eavesdropper is placed at a distance D3 from the IoT transmitter, whereas the corresponding channel envelope is h3. The path loss exponents in the corresponding links are δ1, δ2 and δ3, respectively.
The signal xPB, sent from a power beacon with transmitted power PPB, is represented at the transmitter by the following equation:
where n1 is the additive white Gaussian noise (AWGN) at the transmitter, while the ratio d1 = D1/D0 represents the distance value normalized to D0 = 1 m.
As shown in Figure 1, within each time frame of duration T, the first part αT is dedicated to the energy transfer. Therefore, the harvested energy at the transmitter can be expressed by
where η (0 < η < 1) denotes the energy conversion efficiency. As the power of the IoT transmitter depends on the harvested energy and the time during which the signal is transmitted, it is given by the following equation:

Figure 1.
TS protocol for the transmission of information and energy.
Further, the signal at the legitimate receiver is given as
where n2 is the AWGN at the legitimate receiver with the average value , while d2 = D2/D0 is the distance ratio. Then, the signal-to-noise ratio (SNR) at the receiver can be expressed by the following equation:
where . By defining variables and , the SNR at the receiver can be written in the following abbreviated form:
We assume that the passive eavesdropper is positioned at the distance from the IoT transmitter, so the distance ratio is d3 = D3/D0 and the received signal at the eavesdropper is equal to
where n3 is AWGN at the eavesdropper with the average value . We assume that .
Then, the SNR at the eavesdropper can be written as
and further presented in the abbreviated form as
where .
In the scenario that we consider, the fading envelope in the channel from the PB to the transmitter follows the Nakagami-m distribution, whereas the corresponding channel power gain follows the Gamma distribution. Therefore, the fading distribution in all channels where the receiving node is a non-moving (fixed) one can be described by the following probability density function (PDF):
where and mi are Nakagami-m parameters of the channel between the PB and the transmitter (i = 1), between the IoT transmitter and the legitimate receiver (i = 2) and between the transmitter and the eavesdropper (i = 3). The mean channel power gain is , for each i = 1, 2, 3.
In the case when the receiving node is mobile, we model its movement pattern by a widely accepted RWP mobility model, where it is usually assumed that, depending on the network topology, the nodes’ positions are randomly located within the service area. In the case of a one-dimensional (1D) topology, the receiver is moving along the line with the transmitter or access point being located at the origin. In the case of two-dimensional (2D) topology, the receiver is moving within the circle in one plane, while in three-dimensional (3D) topology, it moves within a spherical space. For cases of both 2D and 3D network topologies, it is assumed that the transmitter is located at the center of the circle (or sphere) [27]. If we define distance r between the transmitter and the receiver, the corresponding distributions of nodes’ positions in the RWP model can be described by the PDF of the distance r, which is given in the following polynomial form [28,29,30]:
where D is maximal distance, while parameters n, and depend on the considered topology, as shown in Table 1.

Table 1.
Polynomial coefficients for the RWP model [28].
Due to variable distance between the transmitter and the receiver, as well as the simultaneous fading fluctuation, we have effects of both small- and large-scale fading. Therefore, the PDF of the equivalent channel power gain for the environment with Nakagami-m fading fluctuations and RWP moving receiver can be expressed in the closed form by means of incomplete gamma function of the first kind ([39], Equation (8.350.1)) and alternatively in terms of the confluent hypergeometric function 1F1(_; _; _) ([39], Equation (9.210.1)), as ([28], Equation (7)):
where j = 2, 3, is the average received power at the edge of the coverage area, while represents the maximal possible distance between the transmitter and the receiver for the given topology. For j = 2, Equation (12) corresponds to the PDF of the channel between the IoT transmitter and the moving receiver, while j = 3 corresponds to the PDF of the channel power gain between the IoT transmitter and the moving eavesdropper.
Using the transformation of the confluent hypergeometric function into Meijer G–function ([40], Equation (07.20.26.0006.01)), as
the PDF expression given in (12) can also be written in the form
Further, the corresponding cumulative distribution function (CDF) expression can be determined by integrating (14) over variable x in the range from 0 to γth [41]. By applying ([40], Equation (07.34.21.0084.01)), the final CDF expression is obtained as
3. Secrecy Performance Analysis
In the following part, we analyze the secrecy outage probability of the wirelessly powered system. To investigate the impact of the node mobility on secrecy performances, we consider scenarios where at least one of the nodes is mobile. We calculate the analytical expression for the secrecy outage that can be presented as the probability that secrecy capacity is below the predetermined limit
, as
The secrecy capacity is defined as [42]
where is the capacity of the legitimate channel, is the capacity of the eavesdropper channel, is the SNR at the receiver and is the SNR at the eavesdropper.
The capacity of the legitimate channel can be obtained as
where α is the time-splitting factor proportional to the time used for energy transfer, while the capacity of the eavesdropper channel can be achieved similarly as
Using Equations (18) and (19) and replacing them in (17), the secrecy capacity expression can be written in the following form
and can be reformulated as
Based on Equation (16) and taking into account that RS has only non-negative values, the secrecy outage probability expression can be further simplified in the following form:
which is equivalent to
Further, by using the relation and replacing it in Equation (23), the expression for the secrecy outage probability can be represented as
Due to the complex form of the joint PDF of the random variables and in the case of the Nakagami-m fading environment, wireless power transfer and the distribution of link lengths in accordance with RWP moving patterns, the expression for the secrecy outage probability cannot be determined in a mathematically closed form. However, by introducing the approximation [43]
which represents the lower performance bound, it is possible to obtain the secrecy outage probability closed-form approximation. Based on a certain expression for the lower limit, the influence of system parameters on performance can be analyzed with satisfactory accuracy.
Based on the described approach, the expression for the lower bound of the secrecy outage probability can be written in the form
where f2(γ2) and f3(γ3) are the PDFs of the channel power gain of the link from the IoT transmitter to the legitimated receiver and from the IoT transmitter to the eavesdropper node, respectively. The expression for the lower bound of the secrecy outage probability can be further written by using the definition of the CDF, in the following form:
where represents the CDF of the channel power gain in the link from the IoT transmitter to the legitimated receiver.
In the following part, we analyze the secrecy performance of a wirelessly powered IoT system, where an IoT node at a fixed position transmits information to the receiver in the presence of the passive eavesdropper for three important scenarios. In the first scenario, the legitimate receiver is mobile, while the eavesdropper is situated at a fixed position. In the second scenario, the legitimate receiver has a fixed position, whereas the eavesdropper is mobile. In the third scenario, an IoT transmitter has a fixed position, whereas both the legitimate receiver and eavesdropper represent moving nodes. For each of the described scenarios, we derive the secrecy outage probability expression.
3.1. Scenario 1: The Legitimate Receiver Is Mobile, the Eavesdropper Is Fixed-Positioned
In this scenario, due to the movement of the legitimate receiver, the distance from the fixed IoT transmitter is variable (Figure 2) and the corresponding PDF can be described with Equation (14). For the calculation of approximate expression for the secrecy outage probability defined by Equation (27), we use CDF given by Equation (15) for i = 2 and PDF given by Equation (10) for i = 3 and obtain
where , while D2,max is the maximal distance between the IoT transmitter and the legitimate receiver.
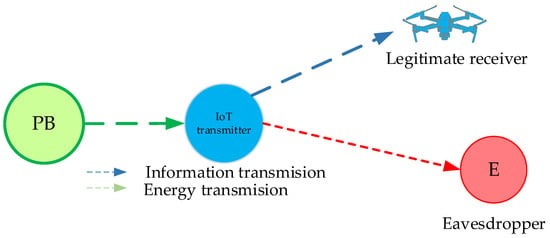
Figure 2.
System model in which the legitimate user is mobile and the eavesdropper has a fixed position.
By transforming the exponential function into the Meijer G–function ([40], Equation (01.03.26.0004.01)) as
and further by replacing in Equation (28) and using ([40], Equation (07.34.21.0011.01)), the expression (28) can be finally written in the following closed form:
3.2. Scenario 2: The Legitimate Receiver Is Fixed-Positioned, the Eavesdropper Is Mobile
In this scenario, given in Figure 3, the legitimate receiver is positioned at a fixed location, while the distance between the IoT transmitter and the eavesdropper is variable with the maximal distance . We obtain an approximate expression for secrecy outage probability by applying the PDF given by Equation (14) for the Nakagami-m fading and RWP moving node for i = 3 and the CDF for Nakagami-m fading in the link with a constant distance between the IoT transmitter and the receiver. Then, the CDF expression for the SNR in the legitimate link is presented in the form of a Meijer G–function by using the transformation of exponential into the Meijer G–function ([40], Equation (01.03.26.0004.01)), where we obtain
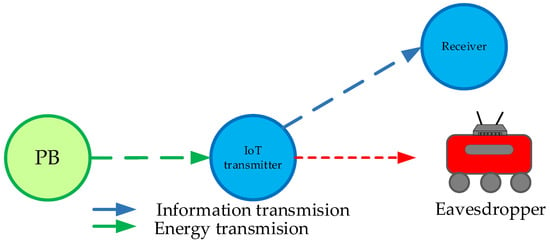
Figure 3.
System model in which the legitimate user has a fixed position and the eavesdropper is mobile.
After applying ([40], Equation (07.34.21.0084.01)), we get
Finally, the secrecy outage probability expression (27) becomes
and the final closed form is obtained by using ([40], Equation (07.34.21.0011.01)) as
3.3. Scenario 3: Both Legitimate Receiver and Eavesdropper Are Mobile
When both the legitimate receiver and eavesdropper are moving with respect to the IoT transmitter that sends information, the maximal distance from the IoT transmitter to the legitimate receiver is D2,max, while the maximal distance to the eavesdropper is D3,max. This scenario is illustrated in Figure 4. The secrecy outage probability expression is calculated by substituting the CDF expression (15) for i = 2 and the PDF expression (14) for i = 3 in Equation (27), where we obtain
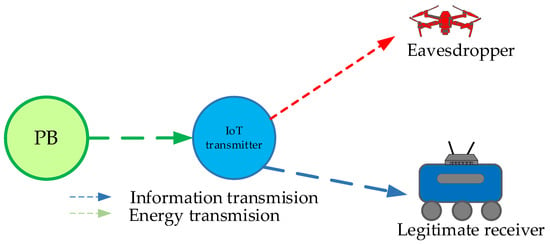
Figure 4.
System model in which both legitimate user and eavesdropper are mobile.
Further, by applying ([40], Equation (07.34.21.0011.01)), the secrecy outage probability can be expressed in the following final form:
4. Numerical Results
In this section, we provide numerical results based on the previously presented analysis. The accuracy of the derived analytical expressions is corroborated by the developed independent Monte Carlo simulation method, which is implemented in MATLAB 2023a [44]. The simulation results are calculated based on the rejection/acceptance technique described in [41], where we have generated a temporally uncorrelated time series with Nakagami-m distribution of length L = 106 samples. Combining [45,46], we have obtained a statistically accurate simulation method, valid for non-integer values of fading parameter m, which represents a special case of the more complex simulation method that we originally proposed in [47]. The numerical results are presented for various channel and system parameters. In all cases, results obtained by using developed simulation models are compared to the results obtained by approximate closed-form expressions given by Equations (30), (34) and (36).
In all simulations, the efficiency coefficient is set to η = 0.9, the data rate is RS = 1 b/s/Hz, the distance between the power beacon and the IoT transmitter is 1 m and the transmit power of the power beacon is 20 dB.
Figure 5 and Figure 6 show the secrecy outage probability for the scenario when the legitimate receiver is mobile, and its movement is modeled by the RWP model. The mean values of channel power gain are , . The Nakagami-m fading parameters in all channels are , while path loss coefficients are δ1 = δ2 = δ3 = 2.7.
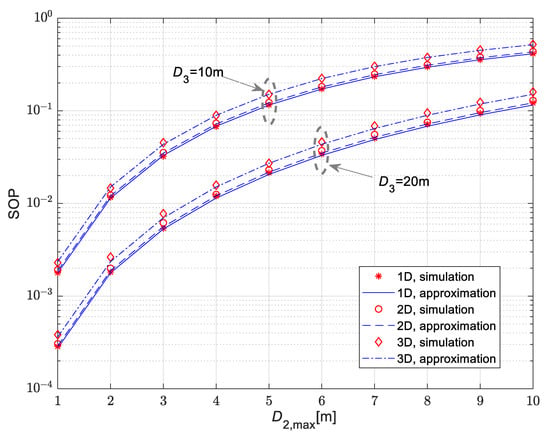
Figure 5.
Secrecy outage probability for various movement patterns of the mobile legitimate receiver for various fixed distances of eavesdropper from the IoT transmitter.
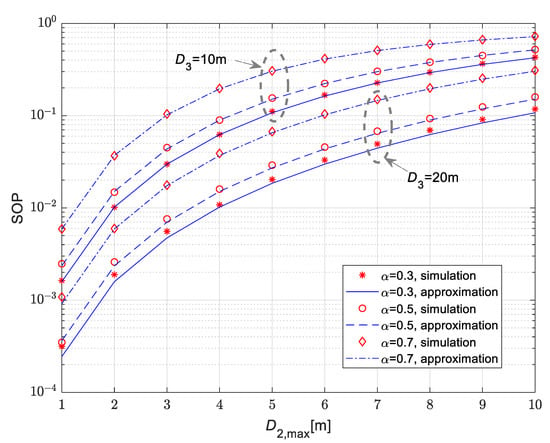
Figure 6.
Secrecy outage probability vs. maximal distance of the mobile legitimate receiver for various time-switching coefficients α.
The results in Figure 5 are presented for the time-switching coefficient equal to α = 0.5. For the movement of the legitimate receiver, the 1D, 2D and 3D patterns of the RWP model are investigated. According to the obtained results, the secrecy outage probability values are lowest in the case when the receiver is moving along the line, which corresponds to the 1D pattern, while the highest values are obtained in the case of a 3D movement pattern within the sphere of the given radius. For all considered scenarios, the secrecy outage probability increases with the rise of the maximal distance between the IoT transmitter and the legitimate user. Furthermore, the secrecy outage probability values are lower in the case when the eavesdropper is set to a larger distance from the IoT transmitter (it is smaller in the case than in the case ). The dependence of the secrecy outage probability on the time-switching coefficient α is presented in Figure 6, for the case of a mobile legitimate receiver and a fixed-position eavesdropper. In accordance with the expectations, the secrecy outage probability increases for larger values of α. Obtained results presented in both Figure 5 and Figure 6 demonstrate the accuracy of the derived approximation for secrecy outage probability given by closed-form expression (30).
In Figure 7, we present the secrecy outage probability for the scenario when the legitimate receiver is placed at the fixed position, which is equal to and . The eavesdropper is moving in accordance with the RWP model. The mean values of channel power gain are , and , while the corresponding Nakagami-m non-integer fading parameters values are , and . The path-loss coefficients have the values of , and . The time-switching coefficient is equal to α = 0.5. For all analyzed cases, secrecy outage probability is lower in the case when the legitimate receiver is placed at the fixed position with distance from the IoT transmitter than in the case when it is placed at the distance . As the eavesdropper is moving in accordance with the RWP model in 1D, 2D and 3D areas, the secrecy outage probability is highest in the case of eavesdropper movement in the 1D line and lowest in the case when it moves within the spherical 3D space. Furthermore, with the increase of the maximal distance from the IoT transmitter to the eavesdropper , the secrecy outage probability values decrease.
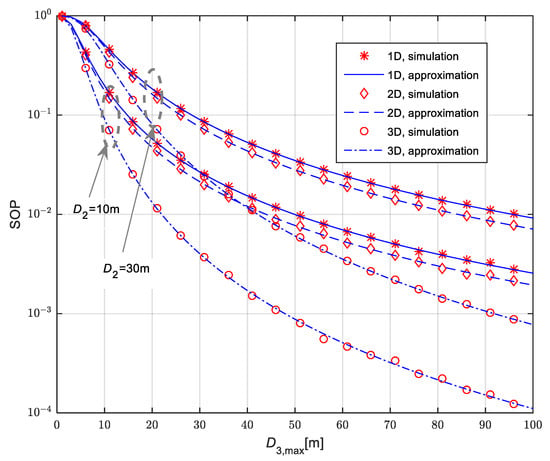
Figure 7.
Secrecy outage probability in the case of fixed legitimate receiver for various movement patterns of mobile eavesdropper.
Secrecy outage probability for the scenario when the legitimate receiver is placed at the fixed position equal to is presented in Figure 8. The eavesdropper is moving in accordance with the 3D RWP model. The mean values of channel power gain are , and . The Nakagami-m fading parameters have non-integer values equal to and , while the fading parameter in the link to the legitimate receiver is and . Secrecy performances are analyzed for three different values of path-loss coefficient in the link to the legitimate receiver equaling , and δ2 = 1.6, while
. The time-switching coefficient is equal to α = 0.5. For all analyzed cases, secrecy outage probability is lower in the case when the Nakagami-m fading parameter in the link to the legitimate receiver has higher values, i.e., fading severity is less significant. Moreover, secrecy performances are improving for lower values of path loss parameter δ2, as the path loss value is lower for the same link length and the corresponding SNR of the legitimate receiver is higher.
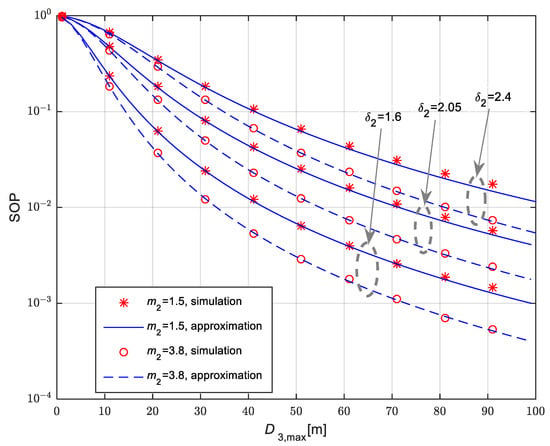
Figure 8.
Secrecy outage probability in the case of fixed legitimate receiver for 3D movement of mobile eavesdropper and various fading parameters and path loss exponent values.
In Figure 9, the dependence of the secrecy outage probability vs. fixed position D2 of the legitimate receiver is presented for the case when the eavesdropper is moving in accordance with the 3D RWP model. The mean values of channel power gain are , and , while the corresponding Nakagami-m fading parameters are . From the obtained results, it can be noticed that the secrecy outage probability increases with the rise of the fixed distance from the IoT transmitter to the legitimate receiver. Furthermore, the increase in the diameter of the 3D space, in which the eavesdropper is moving in accordance with the RWP model, leads to the decrease in secrecy outage probability values. The results are presented for different values of time-switching coefficients α of wireless power transfer. The increase of parameter α results in the increase of the secrecy outage probability. This effect is in accordance with the expectations, as the time dedicated to power transfer leads to a smaller part of each frame dedicated to information transfer and consequently to smaller secrecy capacity and increased secrecy outage probability.
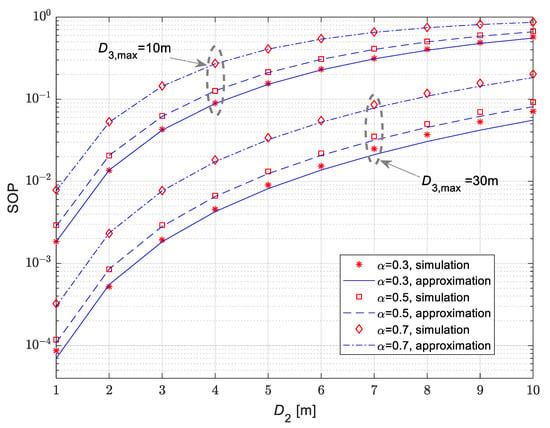
Figure 9.
Secrecy outage probability in the case of fixed legitimate receiver for various time-switching ratios for wireless power transfer.
Finally, based on the results presented in Figure 7, Figure 8 and Figure 9, it can be concluded that the approximate closed-form expression (34) accurately estimates secrecy outage probability values.
The secrecy outage probability for the case when both the legitimate receiver and eavesdropper are moving is presented in Figure 10. The Nakagami-m fading parameters take non-integer values equal to , and . Secrecy performances are analyzed for the path-loss coefficients equaling , and . For the presented results, it is assumed that both nodes are moving in a plane in accordance with a 2D pattern. The secrecy outage probability decreases with the maximal distance between the IoT transmitter and the eavesdropper . Furthermore, the analyzed performance worsens for larger values of maximal distance between IoT transmitter and legitimate receiver, as it has a higher value for than in the case when . The secrecy outage probability in this case also increases for a larger time-switching parameter α. For all analyzed cases, the results obtained by applying approximate closed-form expression (36) are in excellent agreement with the results obtained by the simulation method approach.
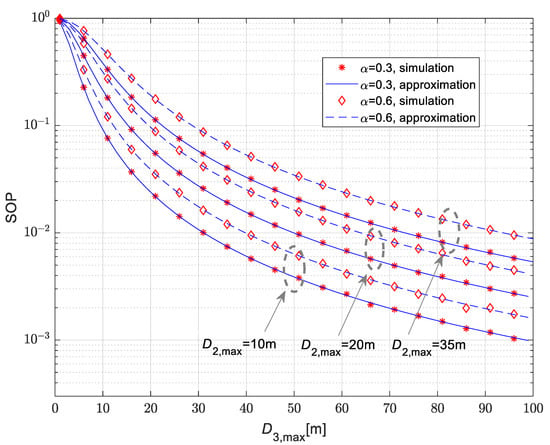
Figure 10.
Secrecy outage probability vs. maximal distance of the legitimate receiver for the scenario when both legitimate receiver and eavesdropper are mobile.
5. Conclusions
The secrecy outage performance is analyzed for the system where the IoT transmitter is energy-limited and supplied using a power beacon. The secrecy performances are analyzed for cases when either the legitimate receiver or eavesdropper is mobile and moving in accordance with the widely accepted RWP model. The accurate closed-form approximate expressions are derived for the case when the propagation environment can be modeled by Nakagami-m distribution and both integer and non-integer values of the Nakagami-m fading parameter. The closed-form approximate expressions for the secrecy outage probability are derived for the following important scenarios: (1) the legitimate receiver is fixed and the eavesdropper is mobile, (2) the legitimate receiver is mobile and the eavesdropper is fixed and (3) both the legitimate receiver and eavesdropper are mobile. The independently developed Monte Carlo simulation model corroborates the accuracy of the derived analytical expressions. The acquired numerical results show the impact of the system and channel parameters on the secrecy outage performances.
In all analyzed cases, the increase of the time-switching coefficient, which is proportional to the time dedicated to the wireless power transfer, leads to the increase in the secrecy outage probability. Further, obtained results demonstrate that secrecy performance declines with the increase of the maximal distance between the transmitter and the legitimate receiver, while improving with the rise of the maximal distance of the eavesdropper from the transmitter. On the one hand, when the eavesdropper is fixed, the best results are obtained in the case when the legitimate receiver randomly moves within the line pattern, while the worst results are obtained in the case when it moves within the sphere. On the other hand, in the case when the legitimate receiver has a fixed position, the secrecy performance improves with the increase of the number of dimensions within which the eavesdropper randomly moves.
The provided analysis presents the framework that can be useful for the design of future secure IoT systems positioned in inaccessible or hazardous areas, where data collecting from IoT sensors can be performed using units placed on mobile ground or aerial vehicles, while communication is endangered by eavesdroppers that can also be mobile. However, the analysis provided in this paper has limitations in some assumptions under which it was performed. First, although the Nakagami-m model is general and encompasses other propagation models as special cases, it does not cover all possible effects, such as shadowing. Second, multiple eavesdroppers can endanger the communication of the legitimate receiver and further degrade secrecy performances, compared to the case of a single eavesdropper. Also, ideal hardware characteristics are assumed, and characteristics deviation from the ideal ones can also degrade performances.
Finally, it is important to highlight that although the derived expression is approximate, its accuracy is demonstrated for a wide set of scenarios. Our future work will encompass the impact of shadowing on the system secrecy performances, as well as the extension to the case with multiple eavesdroppers.
Author Contributions
Conceptualization, V.B., N.K. and A.C.; methodology, V.B., N.K. and A.C.; software, N.K. and V.B.; validation, N.K., V.B. and P.I.; formal analysis, N.K., V.B. and A.C.; investigation, V.B. and N.K.; resources, V.B. and P.I; data curation, V.B.; writing—original draft preparation, V.B. and N.K.; writing—review and editing, V.B., N.K., A.C. and P.I.; visualization, V.B., N.K., A.C. and P.I.; supervision, A.C. and P.I. All authors have read and agreed to the published version of the manuscript.
Funding
This paper is partially supported by the Science Fund of the Republic of Serbia under the project “Hybrid Integrated Satellite and Terrestrial Access Network—hi-STAR” (grant no. 7750284) and by the Ministry of Science, Innovations and Technological Development of Serbia.
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
Author Nadica Kozić was employed by the Postal Savings Bank. The remaining authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
References
- Murroni, M.; Anedda, M.; Fadda, M.; Ruiu, P.; Popescu, V.; Zaharia, C.; Giusto, D. 6G—Enabling the New Smart City: A Survey. Sensors 2023, 23, 7528. [Google Scholar] [CrossRef] [PubMed]
- Sisinni, E.; Saifullah, A.; Han, S.; Jennehag, U.; Gidlund, M. Industrial Internet of Things: Challenges, Opportunities, and Directions. IEEE Trans. Ind. Inform. 2018, 14, 4724–4734. [Google Scholar] [CrossRef]
- Boualouache, A.; Brik, B.; Tang, Q.; Korba, A.A.; Cherrier, S.; Senouci, S.-M.; Pardo, E.; Ghamiri-Doudane, Y.; Langar, R.; Engel, T. 5G vehicle-to-everything at the cross-borders: Security challenges and opportunities. IEEE Internet Things Mag. 2023, 6, 114–119. [Google Scholar] [CrossRef]
- Chen, W.; Lin, X.; Lee, J.; Toskala, A.; Sun, S.; Chiasserini, C.F.; Liu, L. 5G-advanced toward 6G: Past, present, and future. IEEE J. Sel. Areas Commun. 2023, 41, 1592–1619. [Google Scholar] [CrossRef]
- Özyurt, S.; Co¸skun, A.F.; Büyükçorak, S.; Karabulut Kurt, G.; Kucur, O.A. Survey on Multiuser SWIPT Communications for 5G+. IEEE Access 2022, 10, 109814–109849. [Google Scholar] [CrossRef]
- Moloudian, G.; Hosseinifard, M.; Kumar, S.; Simorangkir, R.B.V.B.; Buckley, J.L.; Song, C.; Fantoni, G.; O’Flynn, B. RF energy harvesting techniques for battery-less wireless sensing, industry 4.0 and internet of things: A review. IEEE Sens. J. 2024, 24, 5732–5745. [Google Scholar] [CrossRef]
- Chen, W.; Tang, F.; Cui, F.; Chen, C. Research on Energy Harvesting Mechanism and Low Power Technology in Wireless Sensor Networks. Sensors 2024, 24, 47. [Google Scholar] [CrossRef]
- Zeadally, S.; Shaikh, F.K.; Talpur, A.; Sheng, Q.Z. Design architectures for energy harvesting in the Internet of Things. Renew. Sustain. Energy Rev. 2020, 128, 109901. [Google Scholar] [CrossRef]
- Blagojevic, V.M.; Cvetkovic, A.M.; Ivanis, P. Performance analysis of energy harvesting DF relay system in generalized-K fading environment. Phys. Commun. 2018, 28, 190–200. [Google Scholar] [CrossRef]
- Doan, T.X.; Hoang, T.M.; Duon, T.Q.; Ngo, H.Q. Energy Harvesting-Based D2D Communications in the Presence of Interference and Ambient RF Sources. IEEE Access 2017, 5, 5224–5234. [Google Scholar] [CrossRef]
- Kozić, N.; Blagojević, V.; Ivaniš, P. Performance Analysis of Underlay Cognitive Radio System with Self-Sustainable Relay and Statistical CSI. Sensors 2021, 21, 3727. [Google Scholar] [CrossRef] [PubMed]
- Nasir, A.A.; Zhou, X.; Durrani, S.; Kennedy, R.A. Relaying protocols for wireless energy harvesting and information processing. IEEE Trans. Wirel. Commun. 2013, 12, 3622–3636. [Google Scholar] [CrossRef]
- Ashraf, N.; Sheikh, S.A.; Khan, S.A.; Shayea, I.; Jalal, M. Simultaneous Wireless Information and Power Transfer with Cooperative Relaying for Next-Generation Wireless Networks: A Review. IEEE Access 2021, 9, 71482–71504. [Google Scholar] [CrossRef]
- Cvetković, A.; Blagojević, V.; Anastasov, J.; Pavlović, N.T.; Milošević, M. Outage Analysis of Unmanned-Aerial-Vehicle-Assisted Simultaneous Wireless Information and Power Transfer System for Industrial Emergency Applications. Sensors 2023, 23, 7779. [Google Scholar] [CrossRef] [PubMed]
- Cvetković, A.; Blagojević, V.; Manojlović, J. Capacity Analysis of Power Beacon-Assisted Industrial IoT System with UAV Data Collector. Drones 2023, 7, 146. [Google Scholar] [CrossRef]
- Kozić, N.; Blagojević, V.; Cvetković, A.; Ivaniš, P. Performance Analysis of Wirelessly Powered Cognitive Radio Network with Statistical CSI and Random Mobility. Sensors 2023, 23, 4518. [Google Scholar] [CrossRef]
- Boodai, J.; Alqahtani, A.; Frikha, M. Review of Physical Layer Security in 5G Wireless Networks. Appl. Sci. 2023, 13, 7277. [Google Scholar] [CrossRef]
- Cook, J.; Ur Rehman, S.; Khan, M.A. Security and privacy for low power iot devices on 5g and beyond networks: Challenges and future directions. IEEE Access 2023, 11, 39295–39317. [Google Scholar] [CrossRef]
- Wang, N.; Wang, P.; Alipour-Fanid, A.; Jiao, L.; Zeng, K. Physical-layer security of 5G wireless networks for IoT: Challenges and opportunities. IEEE Internet Things J. 2019, 6, 8169–8181. [Google Scholar] [CrossRef]
- Sun, L.; Du, Q. A Review of Physical Layer Security Techniques for Internet of Things: Challenges and Solutions. Entropy 2018, 20, 730. [Google Scholar] [CrossRef]
- Minh, B.V.; Nguyen, T.N.; Tu, L.T. Physical layer security in wireless sensors networks: Secrecy outage probability analysis. J. Inf. Technol. 2024, 9, 1–23. [Google Scholar] [CrossRef]
- Wyner, A.D. The wire-tap channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Ma, Y.; Ma, R.; Lin, Z.; Zhang, R.; Cai, Y.; Wu, W.; Wang, J. Improving Age of Information for Covert Communication with Time-Modulated Arrays. IEEE Internet Things J. 2025, 2, 1718–1731. [Google Scholar] [CrossRef]
- Ma, R.; Yang, W.; Guan, X.; Lu, X.; Song, Y.; Chen, D. Covert mmWave Communications with Finite Blocklength Against Spatially Random Wardens. IEEE Internet Things J. 2024, 2, 3402–3416. [Google Scholar] [CrossRef]
- Nain, P.; Towsley, D.; Lui, B.; Liu, Z. Properties of random direction models. In Proceedings of the IEEE 24th Annual Joint Conference of the IEEE Computer and Communications Societies, Miami, FL, USA, 13–17 March 2005. [Google Scholar] [CrossRef]
- Bettstetter, C.; Resta, G.; Santi, P. The node distribution of the random waypoint mobility model for wireless ad hoc networks. IEEE Trans. Mob. Comput. 2003, 2, 256–269. [Google Scholar] [CrossRef]
- Govindan, K.; Zeng, K.; Mohapatra, P. Probability density of the received power in mobile networks. IEEE Trans. Wirel. Commun. 2011, 11, 3613–3619. [Google Scholar] [CrossRef]
- Aalo, V.A.; Mukasa, C.; Efthymoglou, G.P. Effect of Mobility on the Outage and BER Performances of Digital Transmissions over Nakagami-m Fading Channels. IEEE Trans. Veh. Technol. 2016, 65, 42715–42721. [Google Scholar] [CrossRef]
- Meesa-Ard, E.; Pattaramalai, S. Evaluating the Mobility Impact on the Performance of Heterogeneous Wireless Networks Over η–μ Fading Channels. IEEE Access 2021, 9, 65017–65032. [Google Scholar] [CrossRef]
- Badarneh, O.S.; Da Costa, D.B.; Nardelli, P.H.J. Wireless-Powered Communication Networks with Random Mobility. IEEE Access 2019, 7, 166476–166492. [Google Scholar] [CrossRef]
- Khuwaja, A.A.; Chen, Y. 3D Mobility Models and Their Impact on the Outage Performance of UAV Communications. IEEE Wirel. Commun. Lett. 2024, 13, 3129–3132. [Google Scholar] [CrossRef]
- Xu, L.; Yu, X.; Wang, H.; Dong, X.; Liu, Y.; Lin, W.; Wang, X.; Wang, J. Physical layer security performance of mobile vehicular networks. Mob. Netw. Appl. 2020, 25, 643–649. [Google Scholar] [CrossRef]
- Pandey, A.; Yadav, S. Joint impact of nodes mobility and imperfect channel estimates on the secrecy performance of cognitive radio vehicular networks over Nakagami-m fading channels. IEEE Open J. Veh. Technol. 2021, 2, 289–309. [Google Scholar] [CrossRef]
- Kavaiya, S.; Patel, D.K.; Ding, Z.; Guan, Y.L.; Sun, S. Physical layer security in cognitive vehicular networks. IEEE Trans. Commun. 2020, 69, 2557–2569. [Google Scholar] [CrossRef]
- Tang, J.; Dabaghchian, M.; Zeng, K.; Wen, H. Impact of mobility on physical layer security over wireless fading channels. IEEE Trans. Wirel. Commun. 2018, 17, 7849–7864. [Google Scholar] [CrossRef]
- Jiang, X.; Zhong, C.; Chen, X.; Duong, T.Q.; Tsiftsis, T.A.; Zhang, Z. Secrecy performance of wirelessly powered wiretap channels. IEEE Trans. Commun. 2016, 64, 3858–3871. [Google Scholar] [CrossRef]
- Yan, P.; Yang, J.; Liu, M.; Sun, J.; Gui, G. Secrecy outage analysis of transmit antenna selection assisted with wireless power beacon. IEEE Trans. Veh. Technol. 2020, 69, 7473–7482. [Google Scholar] [CrossRef]
- Nguyen, M.T.; Nguyen, C.V.; Do, H.T.; Hua, H.T.; Tran, T.A.; Nguyen, A.D.; Ala, G.; Viola, F. UAV-assisted data collection in wireless sensor networks: A comprehensive survey. Electronics 2021, 21, 2603. [Google Scholar] [CrossRef]
- Gradshteyn, I.S.; Ryzhik, I.M. Table of Integrals, Series and Products, 5th ed.; Academic Press Inc.: San Diego, CA, USA, 1994. [Google Scholar]
- The Mathematical Functions Site. Available online: https://functions.wolfram.com/ (accessed on 20 December 2024).
- Papoulis, A.; Pillai, S.U. Probability Random Variables and Stochastic Processes, 4th ed.; McGraw-Hill: Boston, MA, USA, 2002. [Google Scholar]
- Elkashlan, M.; Wang, L.; Duong, T.Q.; Karagiannidis, G.K.; Nallanathan, A. On the Security of Cognitive Radio Networks. IEEE Trans. Veh. Technol. 2014, 64, 3790–3795. [Google Scholar] [CrossRef]
- Lei, H.; Gao, C.; Guo, Y.; Pan, G. On physical layer security over generalized gamma fading channels. IEEE Commun. Lett. 2015, 19, 1257–1260. [Google Scholar] [CrossRef]
- Jeruchim, M.C.; Balaban, P.; Shanmugan, K.S. Simulation of Communication Systems: Modeling, Methodology and Techniques; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2006. [Google Scholar]
- Yacoub, M.D.; Bautista, J.E.V.; Guerra de Rezende Guedes, L. On higher order statistics of the Nakagami-m distribution. IEEE Trans. Veh. Technol. 1999, 48, 790–794. [Google Scholar] [CrossRef]
- Zheng, Y.R.; Xiao, C. Simulation models with correct statistical properties for Rayleigh fading channels. IEEE Trans. Commun. 2003, 51, 920–928. [Google Scholar] [CrossRef]
- Ivaniš, P.; Milojković, J.; Blagojević, V.; Brkić, S. Capacity Analysis of Hybrid Satellite–Terrestrial Systems with Selection Relaying. Entropy 2024, 26, 419. [Google Scholar] [CrossRef] [PubMed]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).