Securing UAV Flying Ad Hoc Wireless Networks: Authentication Development for Robust Communications †
Abstract
1. Introduction
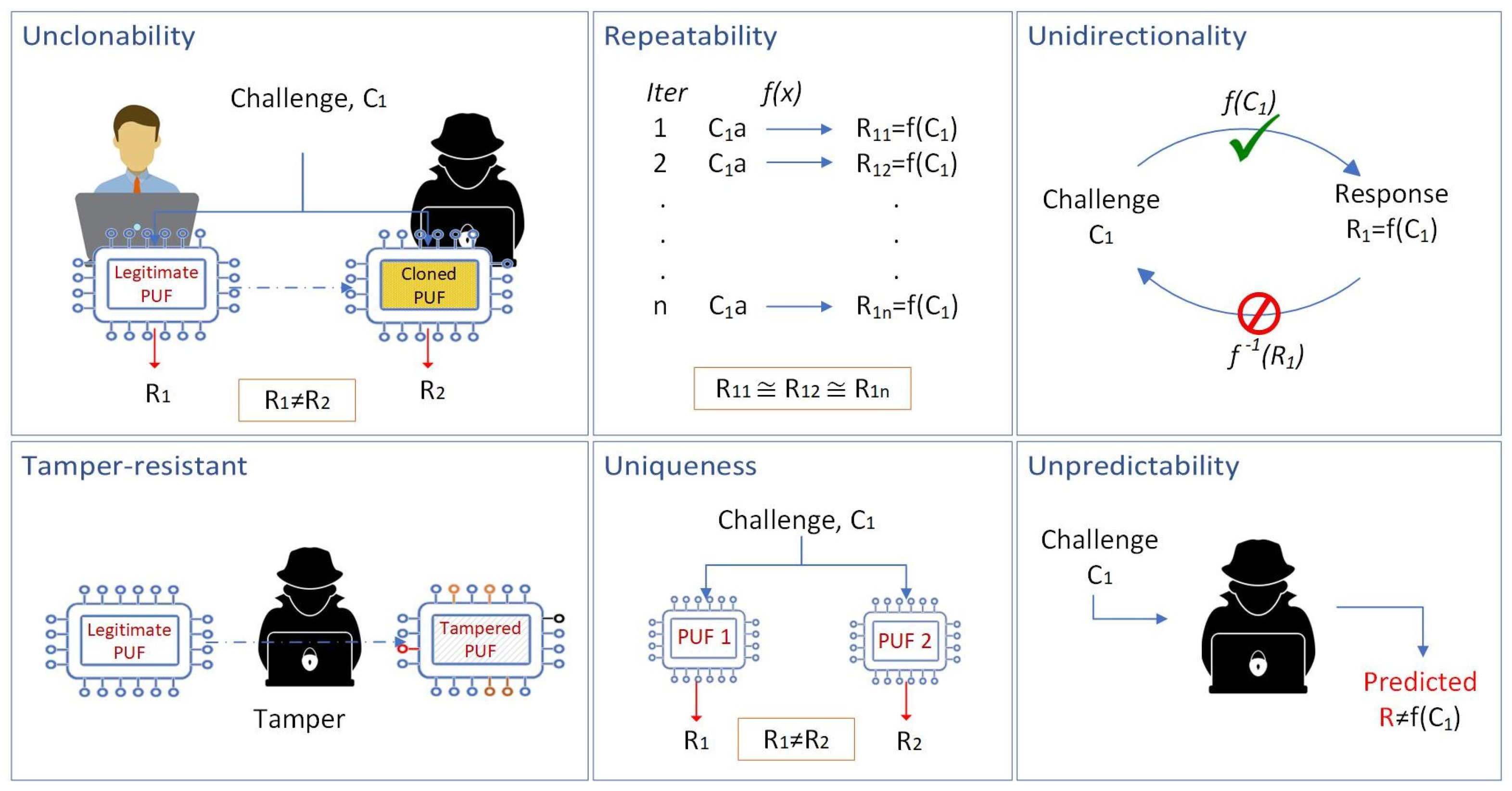
1.1. Physical Unclonable Functions
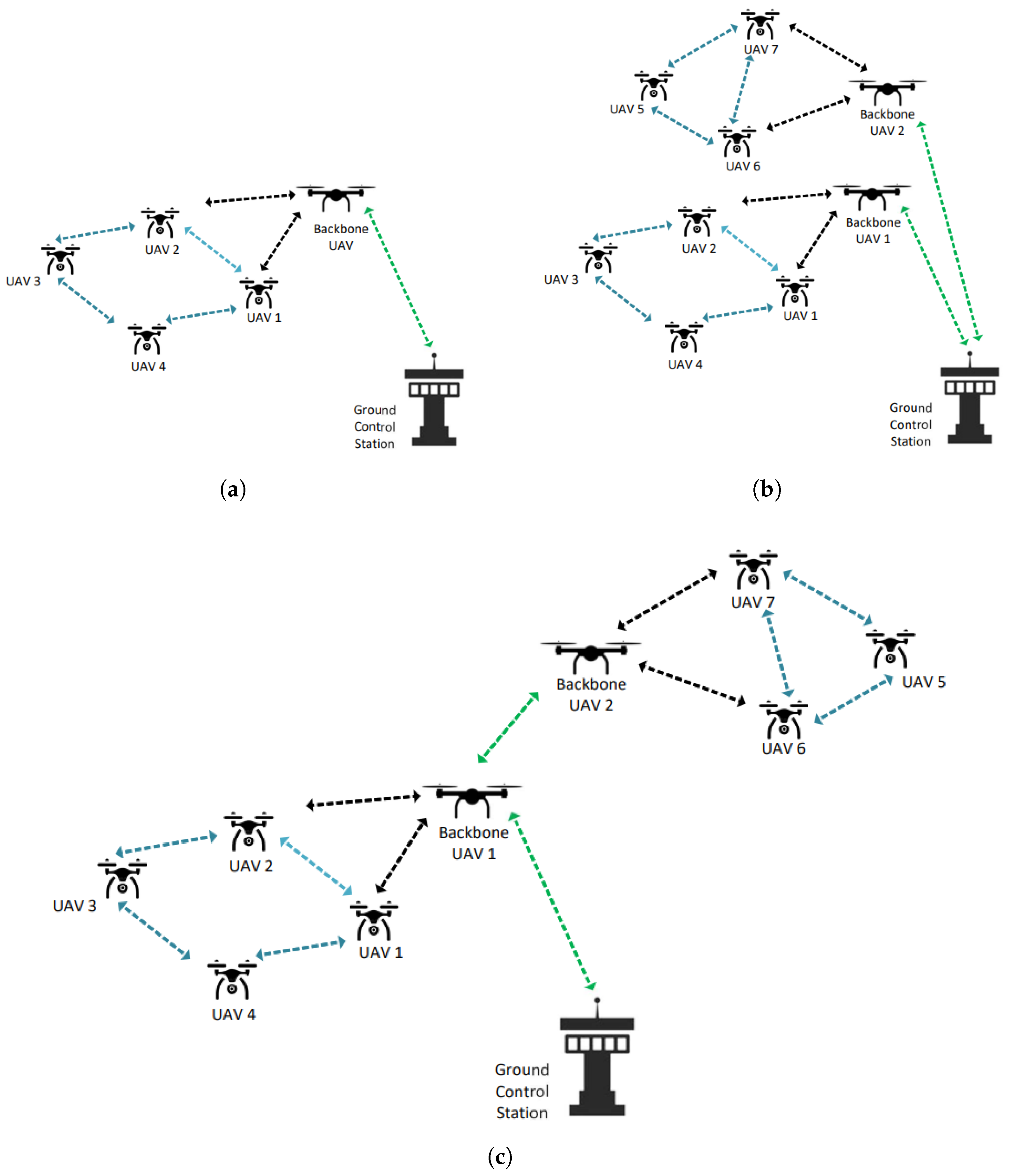
1.2. Flying Ad Hoc Networks
- A novel mutual authentication protocol is introduced to enable a secure link between a UAV and the ground station utilizing Physical Unclonable Functions, without requiring any secret information to be stored on the UAV.
- A comprehensive solution is provided for securing Flying Ad Hoc Networks. By integrating PUFs, the communication channels between UAVs and ground stations are secured against unauthorized access, and network resilience to various cyber threats is enhanced.
- The proposed protocol is thoroughly analyzed regarding its security properties through formal verification methods and cryptanalysis. This detailed analysis demonstrates the protocol’s effectiveness in protecting UAV networks from a wide range of cyber attacks, setting a new benchmark for secure communication in UAV operations.
2. Related Work
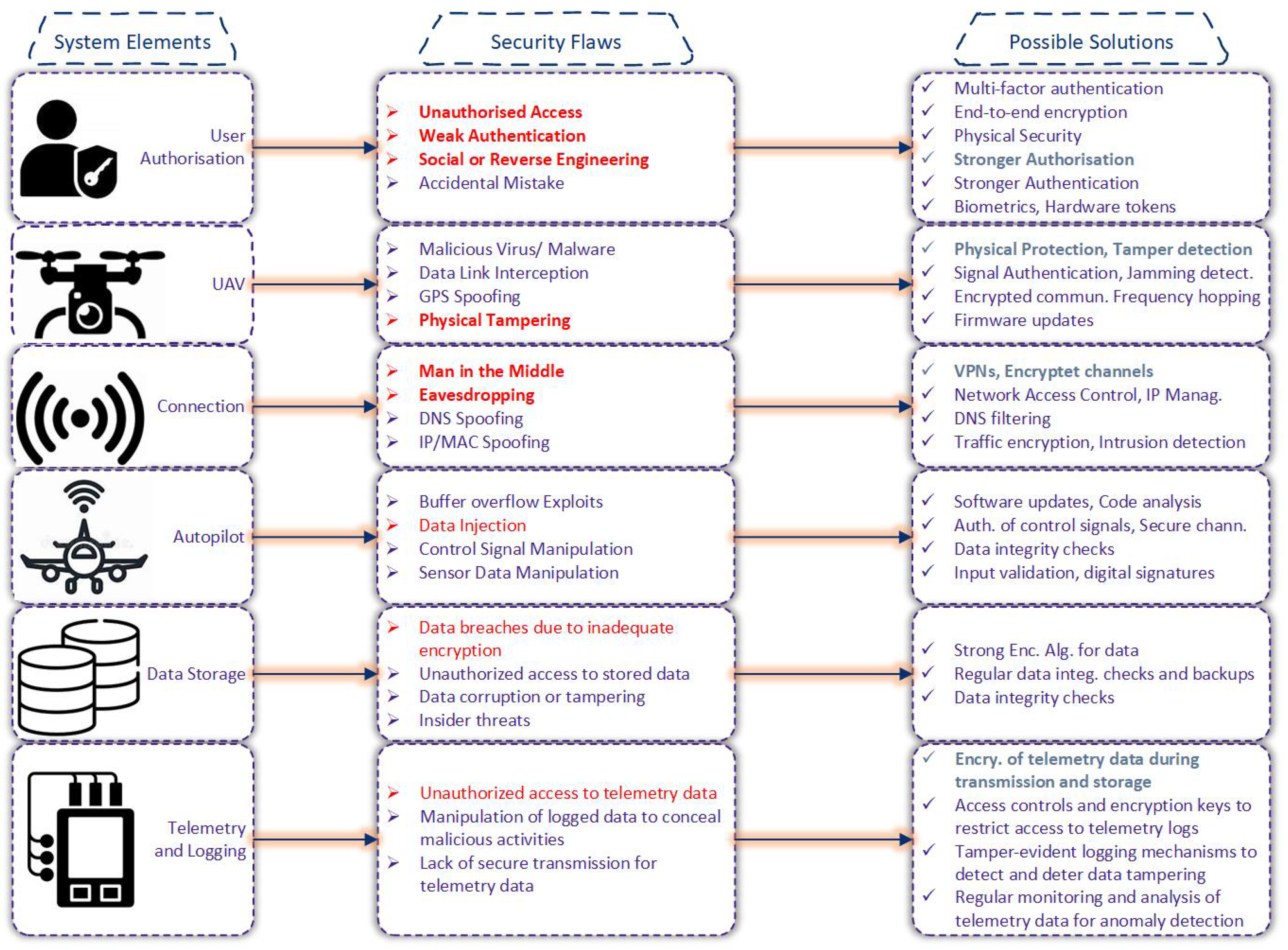
Common UAV Cyber Attacks
3. Security Objectives and System Model
3.1. Threat Model
- Eavesdropping: An Adv can intercept and listen to all unencrypted communications across the network. This allows the adversary to gather information about the communication protocol, message contents, and network topology.
- Message Modification and Injection: An Adv can intercept, delete, modify, and insert messages in public communication channels. This capability includes the ability to create spoofed messages to impersonate a legitimate UAV or ground station.
- Replay Attacks: An Adv can store intercepted messages and replay them at a later time, potentially bypassing nonces or other security mechanisms used to prevent duplication.
- Man-in-the-Middle Attacks: Advs can position themselves between two legitimate communication parties and alter the communication stream, potentially compromising the integrity and confidentiality of the data.
- Device Capture and Tampering: An Adv can physically capture a legitimate UAV and attempt to extract sensitive information from its memory, including encryption keys, mission data, and authentication credentials.
- Cloning Attack: After capturing a UAV, an Adv may attempt to create a clone of the device by extracting its memory contents, allowing the adversary to masquerade as the legitimate UAV.
3.2. Design Goals
3.3. System Model
4. The Proposed Scheme
4.1. UAV Registration Stage
4.1.1. Initial Registration
4.1.2. Data Storage and Handling
4.1.3. Resilience Against Desynchronization Attacks
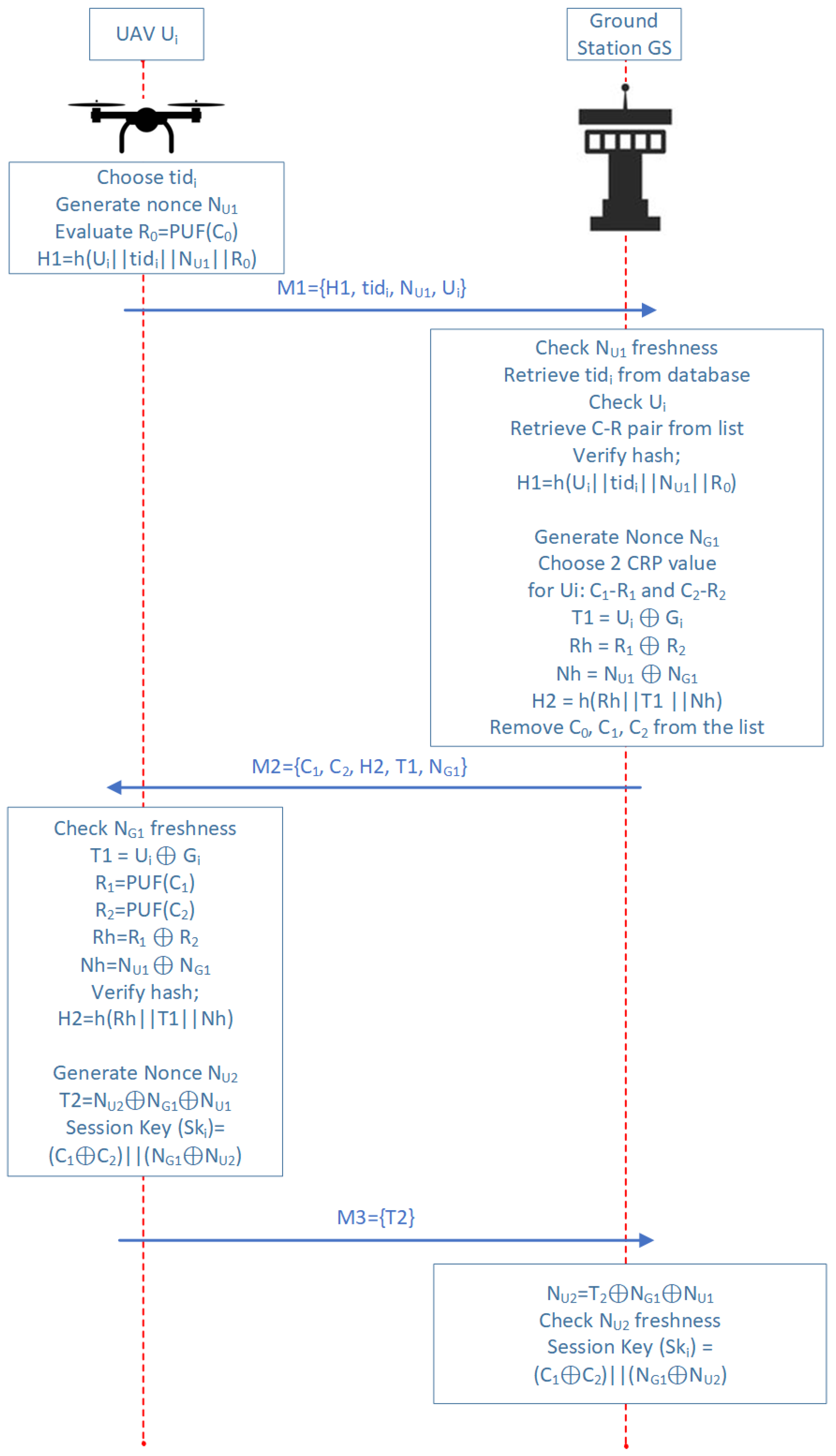
4.2. UAV-GS Authentication Phase
- To send the initial authentication message, the UAV generates the first response by using the stored challenge .
- The UAV sends the message = (,) to the ground station. This message includes the temporary identifier , a random nonce , and a hash = h (‖‖‖), where is the response generated in step 1.
- Upon receiving , the ground station checks its database for any entry corresponding to the received temporary id, . It also verifies the freshness of the nonce to ensure it has not been used in previous authentication sessions. If these conditions are satisfied, ’s authentication request proceeds; if not, the request is disregarded. Following successful verification of the hash , the GS searches for the appropriate challenge–response pair (C,R) in its database. It then generates a new nonce and selects two unused challenge–response pairs from the database for subsequent steps in the authentication process.
- The GS then sends = (,,,,) to
- The UAV checks the freshness of the incoming nonce and retrieves the ground station’s identity () using from the incoming message, along with its own identifier .
- 6.
- 7.
- Consequently, the mutual authentication between the UAV and the GS is successfully completed. Following this, all subsequent communications are secured through encryption utilizing the session key Ski, which has been established to ensure data integrity and confidentiality.
- 8.
- As outlined in the equation below, to preserve user anonymity throughout the authentication process, both the UAV and the GS generate a new temporary identifier, , for the UAV. This identifier will be used in future authentications to ensure anonymity.
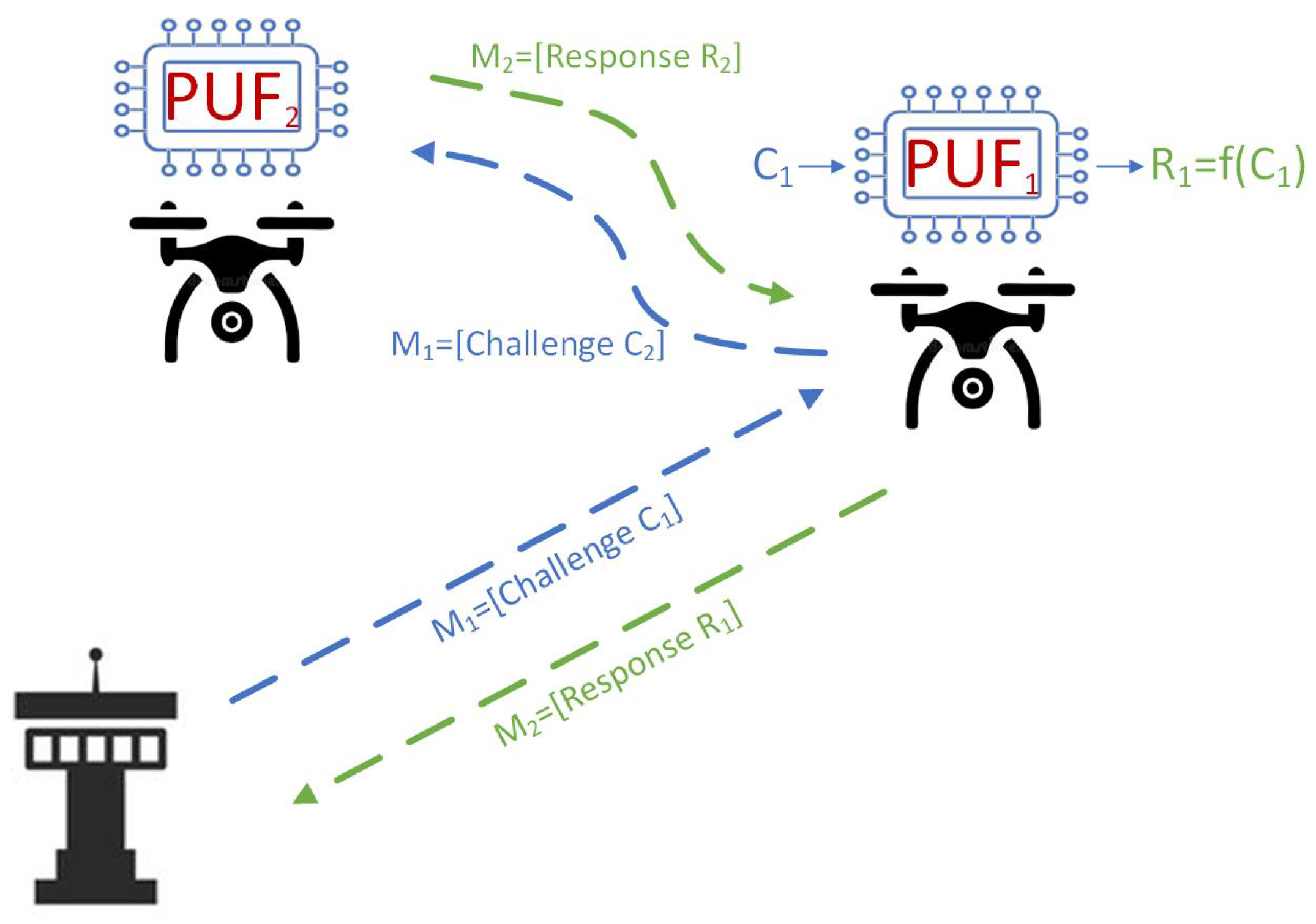
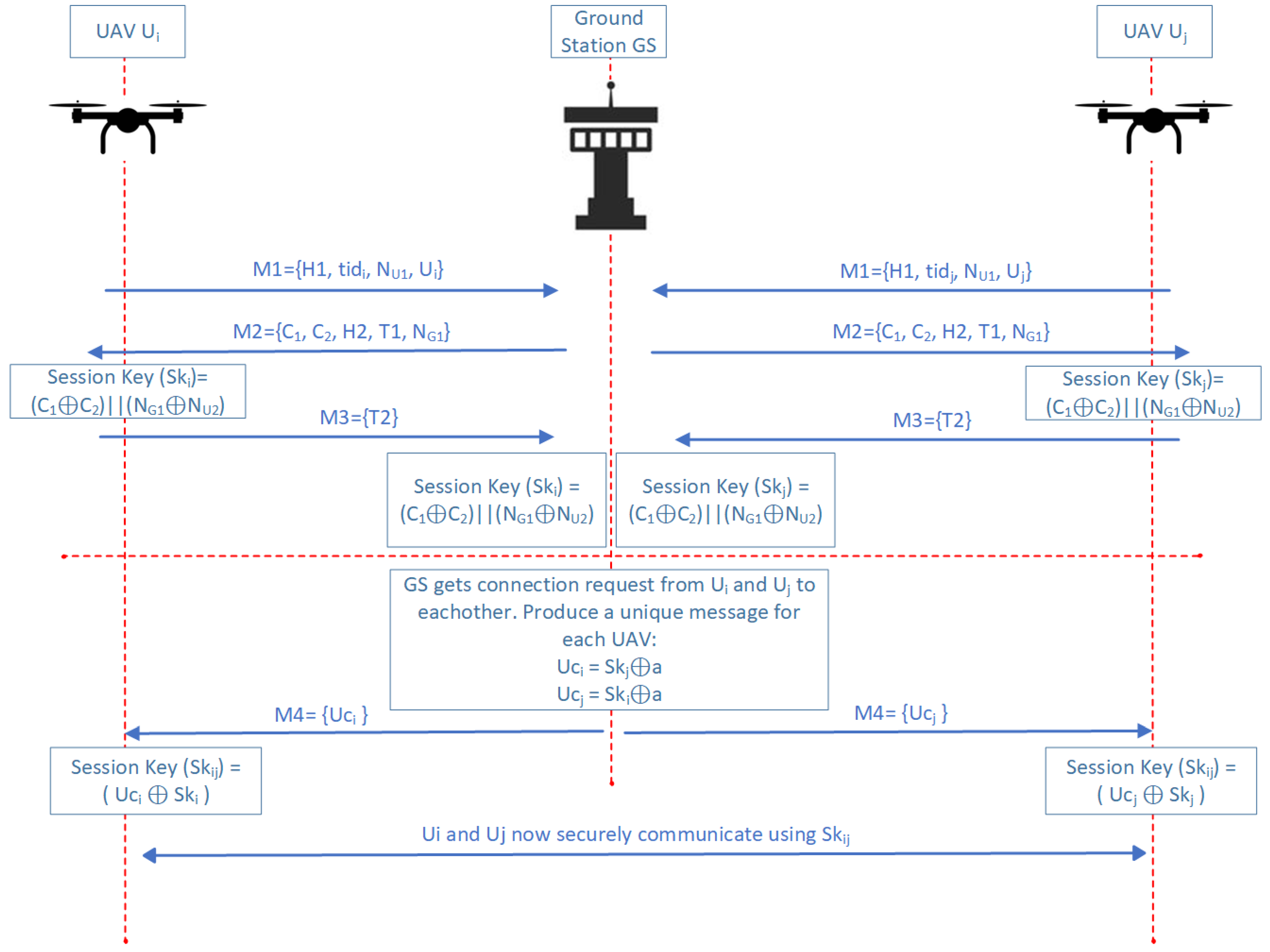
4.3. UAV-UAV Authentication Phase
- Session Key Establishment:
- establishes a session key with .
- establishes a session key with .
- Generation of Unique Message for UAVs:
- computes the and messages for UAVs.
- Distribution of Shared Session Key:
- securely transmits to .
- securely transmits to .
- Secure Communication:
- and obtain for their secure communication.
5. Security Analysis
5.1. Formal Proof
- #(X)
- Represents the belief that X is fresh.
- A|~P
- “Believes” operator—if , then A believes the proposition P is true.
- A|⇒M
- “Sends” operator—if , then A sends message M.
- K(A,B)
- Symbol that A and B share a secure key (or that A believes the key is known only to A and B).
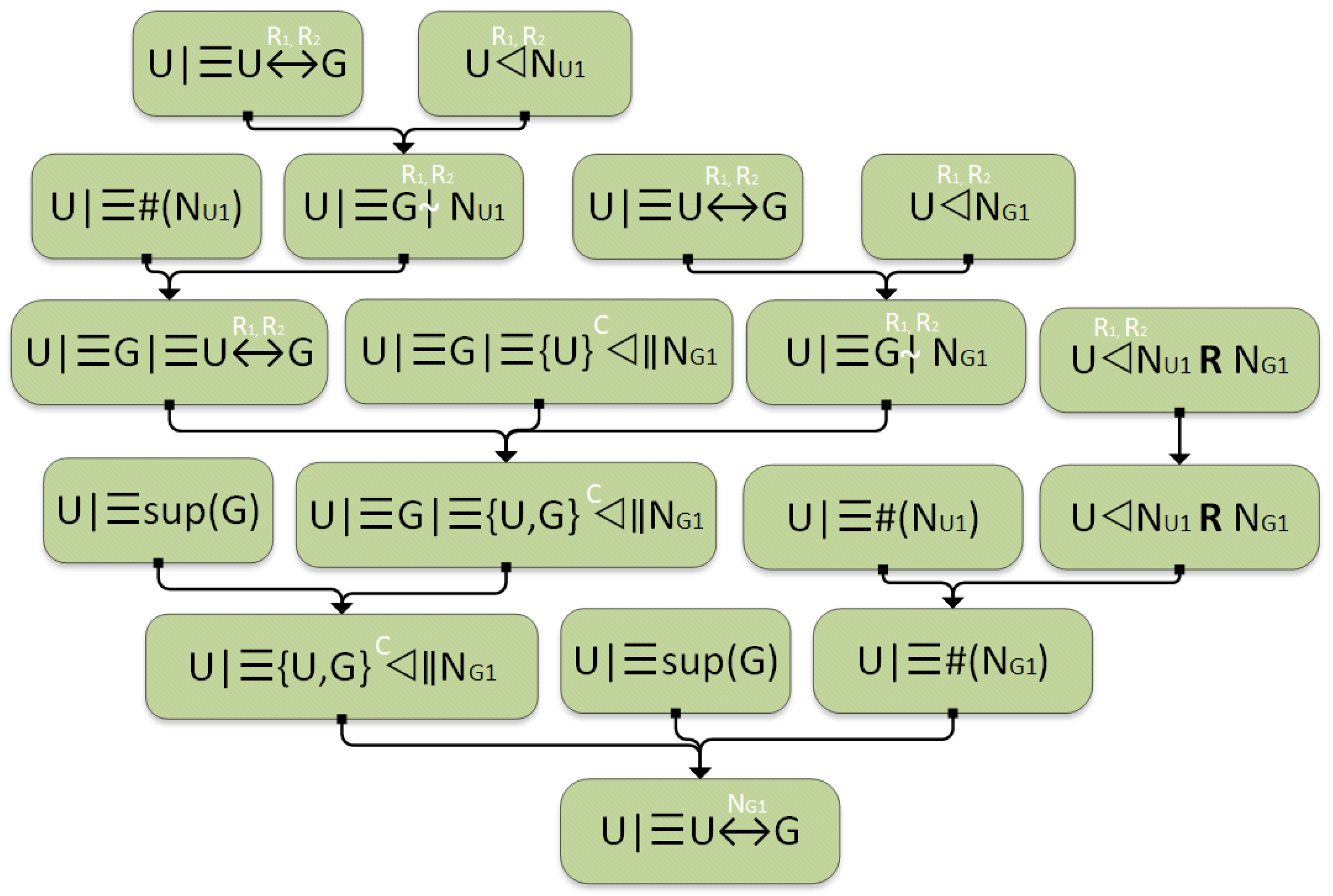
5.1.1. Authentication Rule
- The GS receives message :
- The GS checks the freshness of :
- The GS verifies the hash using :
- The GS sends message :
- The UAV receives message :
- The UAV checks the freshness of :
- The UAV verifies the hash :
Applying Authentication Rule
5.1.2. Nonce Verification Rule
- The UAV generates :
- The GS checks freshness:
- The GS generates :
- The UAV checks freshness:
Applying Nonce Verification Rule
5.1.3. Confidentiality Rule
- The UAV calculates :
- The UAV sends to the GS:
- The GS calculates the same :
5.1.4. Super-Principal Rule
- The UAV believes that the session key is secure between the UAV and GS:
- The GS believes that the session key is secure between the UAV and GS:
5.1.5. Freshness Rule
- The UAV generates nonce :
- The GS checks the freshness of :
- The GS generates nonce :
- The UAV checks the freshness of :
Applying Freshness Rule
5.1.6. Good-Key Rule
- The UAV believes that the session key is secure between the UAV and GS:
- The GS believes that the session key is secure between the UAV and GS:
- Authentication: Both UAV and GS authenticate each other using fresh nonces and challenge–response pairs.
- Nonce Verification: Both nonces and are verified to be fresh, ensuring no replay attacks.
- Confidentiality: The session key is established securely, known only to the UAV and GS.
- Super-Principal Rule: The GS is trusted by the UAV to maintain secure challenge–response pairs and identities.
- Freshness Rule: The freshness of nonces ensures the authenticity and timeliness of the messages.
- Good-Key Rule: The session key is a good key for secure communication between the UAV and GS.
5.2. Cryptanalysis
- [C5]
- Resistance to known attacks:
- [C7]
- Provision of key agreement:
- [C8]
- No clock synchronization:
- [C10]
- Mutual authentication:
- [C11]
- User anonymity:
- [C12]
- Forward secrecy:
Attack Scenarios
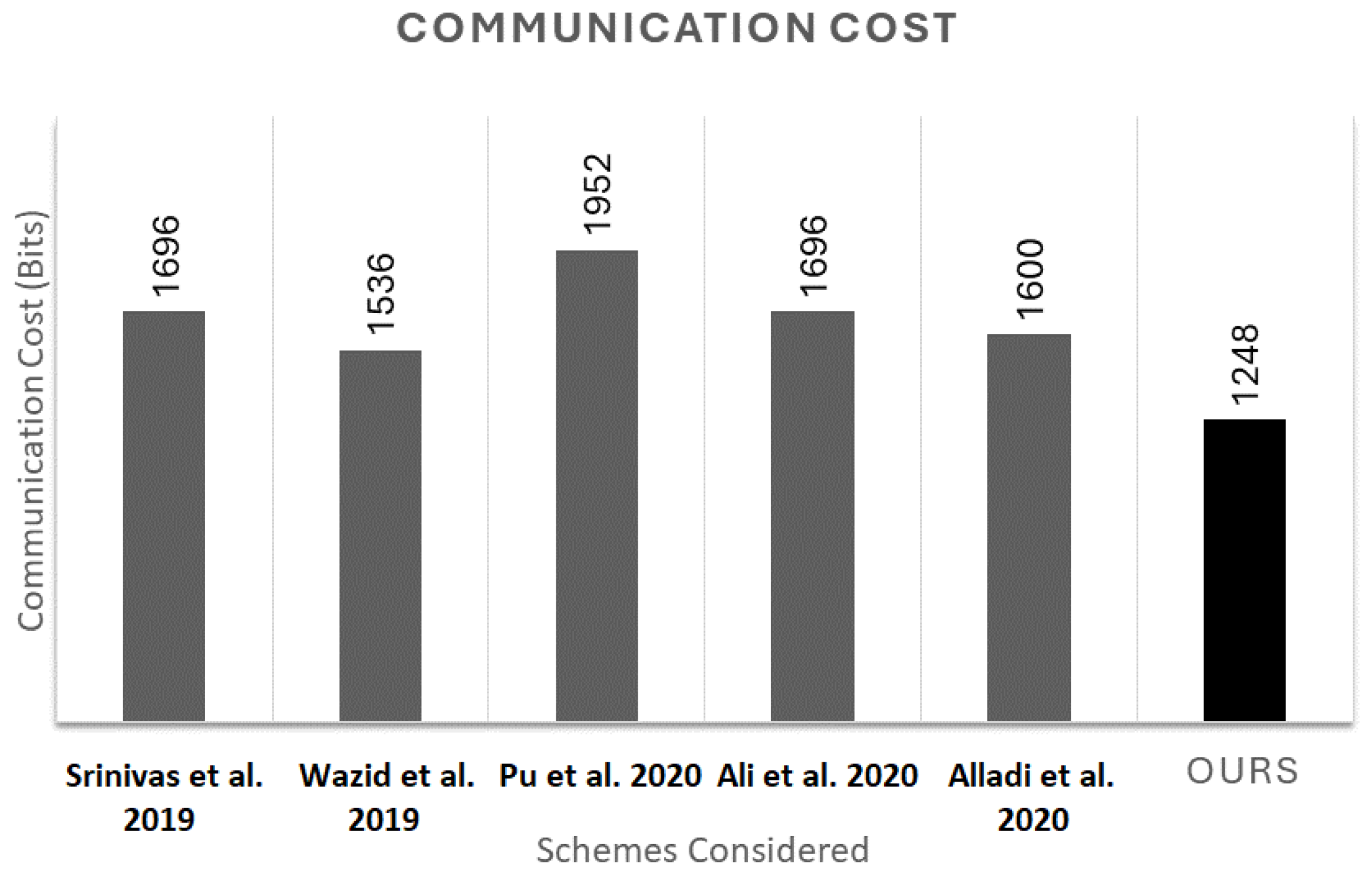
6. Results and Discussion
6.1. Security Comparison
6.2. Performance Comparison
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| PUF | Physical Unclonable Function |
| UAV | Unmanned Aerial Vehicle |
| GS | Ground station |
| FANET | Flying Ad Hoc Network |
| VANET | Vehicular Ad Hoc Network |
References
- Tan, Y.; Wang, J.; Liu, J.; Kato, N. Blockchain-Assisted Distributed and Lightweight Authentication Service for Industrial Unmanned Aerial Vehicles. IEEE Internet Things J. 2022, 9, 16928–16940. [Google Scholar] [CrossRef]
- Valavanis, K.P.; Vachtsevanos, G.J. Handbook of Unmanned Aerial Vehicles; Springer: Berlin/Heidelberg, Germany, 2015; Volume 1. [Google Scholar]
- Fraser, B.; Al-Rubaye, S.; Aslam, S.; Tsourdos, A. Enhancing the Security of Unmanned Aerial Systems using Digital-Twin Technology and Intrusion Detection. In Proceedings of the 2021 IEEE/AIAA 40th Digital Avionics Systems Conference (DASC), San Antonio, TX, USA, 3–7 October 2021; pp. 1–10. [Google Scholar] [CrossRef]
- Aloseel, A.; Al-Rubaye, S.; Zolatas, A.; Shaw, C. Attack-Detection Architectural Framework Based on Anomalous Patterns of System Performance and Resource Utilization—Part II. IEEE Access 2021, 9, 87611–87629. [Google Scholar] [CrossRef]
- Saleem, Z.; Firdous, U.; Afzal, M.K.; Ali, A.; Iqbal, M.; Al-Fuqaha, A.; Al-Rubaye, S. Blockchain-Based Privacy Preservation Using Steganography in Drone-Enabled VANETs. In Proceedings of the GLOBECOM 2023–2023 IEEE Global Communications Conference, Kuala Lumpur, Malaysia, 4–8 December 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 6862–6867. [Google Scholar] [CrossRef]
- Pu, C.; Wall, A.; Choo, K.K.; Ahmed, I.; Lim, S. A Lightweight and Privacy-Preserving Mutual Authentication and Key Agreement Protocol for Internet of Drones Environment. IEEE Internet Things J. 2022, 9, 9918–9933. [Google Scholar] [CrossRef]
- Chao, H.; Cao, Y.; Chen, Y. Autopilots for Small Fixed-Wing Unmanned Air Vehicles: A Survey. In Proceedings of the 2007 International Conference on Mechatronics and Automation, Harbin, China, 5–8 August 2007; pp. 3144–3149. [Google Scholar] [CrossRef]
- Morse, B.; Engh, C.; Goodrich, M. UAV video coverage quality maps and prioritized indexing for wilderness search and rescue. In Proceedings of the 2010 5th ACM/IEEE International Conference on Human-Robot Interaction (HRI), Osaka, Japan, 2–5 March 2010; pp. 227–234. [Google Scholar] [CrossRef][Green Version]
- Bekmezci, I.; Sahingoz, O.; Temel, Ş. Flying ad-hoc networks (FANETs): A survey. Ad Hoc Netw. 2013, 11, 1254–1270. [Google Scholar] [CrossRef]
- Mousa, M.; Al-Rubaye, S.; Inalhan, G. Unmanned Aerial Vehicle Positioning using 5G New Radio Technology in Urban Environment. In Proceedings of the 2023 IEEE/AIAA 42nd Digital Avionics Systems Conference (DASC), Barcelona, Spain, 1–5 October 2023. [Google Scholar] [CrossRef]
- To, L.; Bati, A.; Hilliard, D. Radar Cross Section measurements of small Unmanned Air Vehicle Systems in non-cooperative field environments. In Proceedings of the 2009 3rd European Conference on Antennas and Propagation, Berlin, Germany, 23–27 March 2009; pp. 3637–3641. [Google Scholar]
- Khan, M.A.; Safi, A.; Qureshi, I.M.; Khan, I.U. Flying ad-hoc networks (FANETs): A review of communication architectures, and routing protocols. In Proceedings of the 2017 First International Conference on Latest trends in Electrical Engineering and Computing Technologies (INTELLECT), Karachi, Pakistan, 15–16 November 2017; pp. 1–9. [Google Scholar] [CrossRef]
- Sen, M.A.; Al-Rubaye, S.; Tsourdos, A. Developing Secure Hardware for UAV Authorisation Using Lightweight Authentication. In Proceedings of the 2023 IEEE/AIAA 42nd Digital Avionics Systems Conference (DASC), Barcelona, Spain, 1–5 October 2023. [Google Scholar] [CrossRef]
- Alladi, T.; Naren, N.; Bansal, G.; Chamola, V.; Guizani, M. SecAuthUAV: A Novel Authentication Scheme for UAV-Ground Station and UAV-UAV Communication. IEEE Trans. Veh. Technol. 2020, 69, 15068–15077. [Google Scholar] [CrossRef]
- Tian, C.; Jiang, Q.; Li, T.; Zhang, J.; Xi, N.; Ma, J. Reliable PUF-based mutual authentication protocol for UAVs towards multi-domain environment. Comput. Netw. 2022, 218, 109421. [Google Scholar] [CrossRef]
- Zhang, L.; Xu, J.; Obaidat, M.S.; Li, X.; Vijayakumar, P. A PUF-based lightweight authentication and key agreement protocol for smart UAV networks. IET Commun. 2022, 16, 1142–1159. [Google Scholar] [CrossRef]
- Aysu, A.; Gulcan, E.; Moriyama, D.; Schaumont, P.; Yung, M. End-To-End Design of a PUF-Based Privacy Preserving Authentication Protocol. In Proceedings of the Cryptographic Hardware and Embedded Systems—CHES 2015, Saint-Malo, France, 13–16 September 2015; Güneysu, T., Handschuh, H., Eds.; Springer: Berlin/Heidelberg, Germany, 2015; pp. 556–576. [Google Scholar]
- Hooper, M.; Tian, Y.; Zhou, R.; Cao, B.; Lauf, A.; Watkins, L.; Robinson, W.; Alexis, W. Securing Commercial WiFi-Based UAVs From Common Security Attacks. In Proceedings of the MILCOM 2016-2016 IEEE Military Communications Conference, Baltimore, MD, USA, 1–3 November 2016. [Google Scholar] [CrossRef]
- Blazy, O.; Bonnefoi, P.F.; Conchon, E.; Sauveron, D.; Akram, R.N.; Markantonakis, K.; Mayes, K.; Chaumette, S. An Efficient Protocol for UAS Security. In Proceedings of the 2017 Integrated Communications, Navigation and Surveillance Conference (ICNS), Herndon, VA, USA, 18–20 April 2017; pp. 1–21. [Google Scholar] [CrossRef]
- Alladi, T.; Chamola, V.; Sikdar, B.; Choo, K.K.R. Consumer IoT: Security Vulnerability Case Studies and Solutions. IEEE Consum. Electron. Mag. 2019, 9, 17–25. [Google Scholar] [CrossRef]
- Abdallah, A.; Ali, M.Z.; Mišić, J.; Mišić, V.B. Efficient Security Scheme for Disaster Surveillance UAV Communication Networks. Information 2019, 10, 43. [Google Scholar] [CrossRef]
- Semal, B.; Markantonakis, K.; Akram, R.N. A Certificateless Group Authenticated Key Agreement Protocol for Secure Communication in Untrusted UAV Networks. In Proceedings of the 2018 IEEE/AIAA 37th Digital Avionics Systems Conference (DASC), London, UK, 23–27 September 2018; pp. 1–8. [Google Scholar] [CrossRef]
- Kumar, G.; Singh, B.; Kumar, N.; Chamola, V. CB-CAS: Certificate-Based Efficient Signature Scheme With Compact Aggregation for Industrial Internet of Things Environment. IEEE Internet Things J. 2019, 7, 2563–2572. [Google Scholar] [CrossRef]
- Chatterjee, B.; Das, D.; Maity, S.; Sen, S. RF-PUF: Enhancing IoT security through authentication of wireless nodes using in-situ machine learning. IEEE Internet Things J. 2018, 6, 388–398. [Google Scholar] [CrossRef]
- Choi, D.; Seo, S.H.; Oh, Y.S.; Kang, Y. Two-Factor Fuzzy Commitment for Unmanned IoT Devices Security. IEEE Internet Things J. 2018, 6, 335–348. [Google Scholar] [CrossRef]
- Alladi, T.; Chamola, V.; Zeadally, S. Industrial Control Systems: Cyberattack Trends and Countermeasures. Comput. Commun. 2020, 155, 1–8. [Google Scholar] [CrossRef]
- Chen, B.; Willems, F. Secret Key Generation Over Biased Physical Unclonable Functions With Polar Codes. IEEE Internet Things J. 2018, 6, 435–445. [Google Scholar] [CrossRef]
- Pu, C.; Li, Y. Lightweight Authentication Protocol for Unmanned Aerial Vehicles Using Physical Unclonable Function and Chaotic System. In Proceedings of the 2020 IEEE International Symposium on Local and Metropolitan Area Networks (LANMAN), Orlando, FL, USA, 13–15 July 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Lee, S.; Jang, B.C.; Kim, M.; Lim, S.H.; Ko, E.; Kim, H.H.; Yoo, H. Machine Learning Attacks-Resistant Security by Mixed-Assembled Layers-Inserted Graphene Physically Unclonable Function. Adv. Sci. 2023, 10, 2302604. [Google Scholar] [CrossRef]
- Huang, Z.; Lin, Y.; Zeng, F.; Bian, J.; Yang, Z.; Liang, H.; Lu, Y.; Yao, L.; Wen, X.; Ni, T. PFO PUF: A Lightweight Parallel Feed Obfuscation PUF Resistant to Machine Learning Attacks. In Proceedings of the 2024 IEEE International Test Conference in Asia (ITC-Asia), Changsha, China, 18–20 August 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Karmakar, R.; Kaddoum, G.; Akhrif, O. A PUF and Fuzzy Extractor-Based UAV-Ground Station and UAV-UAV Authentication Mechanism With Intelligent Adaptation of Secure Sessions. IEEE Trans. Mob. Comput. 2024, 23, 3858–3875. [Google Scholar] [CrossRef]
- Tanveer, M.; Aldosary, A.; Khokhar, S.U.D.; Das, A.K.; Aldossari, S.A.; Chaudhry, S.A. PAF-IoD: PUF-Enabled Authentication Framework for the Internet of Drones. IEEE Trans. Veh. Technol. 2024, 73, 9560–9574. [Google Scholar] [CrossRef]
- Nair, A.S.; Thampi, S.M.; Jafeel, V. A post-quantum secure PUF based cross-domain authentication mechanism for Internet of drones. Veh. Commun. 2024, 47, 100780. [Google Scholar] [CrossRef]
- Chen, L.; Zhu, Y.; Liu, S.; Yu, H.; Zhang, B. PUF-based dynamic secret-key strategy with hierarchical blockchain for UAV swarm authentication. Comput. Commun. 2024, 218, 31–43. [Google Scholar] [CrossRef]
- Kerns, A.J.; Shepard, D.P.; Bhatti, J.A.; Humphreys, T.E. Unmanned Aircraft Capture and Control Via GPS Spoofing. J. Field Robot. 2014, 31, 617–636. [Google Scholar] [CrossRef]
- Soreanu, P.; Volkovich, V.; Barzily, Z.; Golani, M.; Volkovich, Z. Mitigating jamming attacks in wireless sensor networks: An energy-efficient method in a mobile jammer environment. Int. J. Pure Appl. Math. 2009, 56, 533–550. [Google Scholar]
- Khattab, S.; Mosse, D.; Melhem, R. Jamming Mitigation in Multi-Radio Wireless Networks: Reactive or Proactive. In Proceedings of the SecureComm ’08: Proceedings of the 4th International Conference on Security and Privacy in Communication Netowrks, Istanbul, Turkey, 22–25 September 2008. [Google Scholar] [CrossRef]
- Tan, H.; Zheng, W.; Vijayakumar, P. Secure and Efficient Authenticated Key Management Scheme for UAV-Assisted Infrastructure-Less IoVs. IEEE Trans. Intell. Transp. Syst. 2023, 24, 6389–6400. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A.C.C. On the security of public key protocols. In Proceedings of the 22nd Annual Symposium on Foundations of Computer Science (SFCS), Washington, DC, USA, 28–30 October 1981; pp. 350–357. [Google Scholar]
- Mao, W.; Boyd, C. Towards formal analysis of security protocols. In Proceedings of the [1993] Proceedings Computer Security Foundations Workshop VI, Franconia, NH, USA, 15–17 June 1993; pp. 147–158. [Google Scholar] [CrossRef]
- Wang, D.; Wang, P. Two Birds with One Stone: Two-Factor Authentication with Security Beyond Conventional Bound. IEEE Trans. Dependable Secur. Comput. 2018, 15, 708–722. [Google Scholar] [CrossRef]
- Wang, D.; Li, W.; Wang, P. Measuring Two-Factor Authentication Schemes for Real-Time Data Access in Industrial Wireless Sensor Networks. IEEE Trans. Ind. Inform. 2018, 14, 4081–4092. [Google Scholar] [CrossRef]
- Roy, S.; Das, A.K.; Chatterjee, S.; Kumar, N.; Chattopadhyay, S.; Rodrigues, J.J.P.C. Provably Secure Fine-Grained Data Access Control Over Multiple Cloud Servers in Mobile Cloud Computing Based Healthcare Applications. IEEE Trans. Ind. Inform. 2019, 15, 457–468. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Vasilakos, A.V.; Rodrigues, J.J.P.C. Design and Analysis of Secure Lightweight Remote User Authentication and Key Agreement Scheme in Internet of Drones Deployment. IEEE Internet Things J. 2019, 6, 3572–3584. [Google Scholar] [CrossRef]
- Srinivas, J.; Das, A.K.; Kumar, N.; Rodrigues, J.J.P.C. TCALAS: Temporal Credential-Based Anonymous Lightweight Authentication Scheme for Internet of Drones Environment. IEEE Trans. Veh. Technol. 2019, 68, 6903–6916. [Google Scholar] [CrossRef]
- Ali, Z.; Chaudhry, S.A.; Ramzan, M.S.; Al-Turjman, F. Securing Smart City Surveillance: A Lightweight Authentication Mechanism for Unmanned Vehicles. IEEE Access 2020, 8, 43711–43724. [Google Scholar] [CrossRef]
- Zhao, X.; Zhao, Q.; Liu, Y.; Zhang, F. An Ultracompact Switching-Voltage-Based Fully Reconfigurable RRAM PUF With Low Native Instability. IEEE Trans. Electron Devices 2020, 67, 3010–3013. [Google Scholar] [CrossRef]
| Notation | Meaning |
|---|---|
| Ui | ID of UAV |
| Tidi | Temporary ID of UAV |
| GS | Ground station |
| Gi | ID of ground station |
| NUi | Random nonce produced by UAV |
| NGi | Random nonce produced by GS |
| Ci | challenge parameter of PUF |
| Ri | response parameter of PUF |
| Hash function | |
| ⊕ | XOR operation |
| ∥ | Concatenation |
| Ski | Session key between UAV and GS |
| Skij | Session key between and |
| a | 192-bit random number |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sen, M.A.; Al-Rubaye, S.; Tsourdos, A. Securing UAV Flying Ad Hoc Wireless Networks: Authentication Development for Robust Communications. Sensors 2025, 25, 1194. https://doi.org/10.3390/s25041194
Sen MA, Al-Rubaye S, Tsourdos A. Securing UAV Flying Ad Hoc Wireless Networks: Authentication Development for Robust Communications. Sensors. 2025; 25(4):1194. https://doi.org/10.3390/s25041194
Chicago/Turabian StyleSen, Muhammet A., Saba Al-Rubaye, and Antonios Tsourdos. 2025. "Securing UAV Flying Ad Hoc Wireless Networks: Authentication Development for Robust Communications" Sensors 25, no. 4: 1194. https://doi.org/10.3390/s25041194
APA StyleSen, M. A., Al-Rubaye, S., & Tsourdos, A. (2025). Securing UAV Flying Ad Hoc Wireless Networks: Authentication Development for Robust Communications. Sensors, 25(4), 1194. https://doi.org/10.3390/s25041194