Anonymous and Efficient Chaotic Map-Based Authentication Protocol for Industrial Internet of Things
Abstract
1. Introduction
1.1. Existing Research and Motivation
1.2. Contribution
- We propose a novel chaotic map-based mutual authentication and session key agreement protocol for the IIoT environment, where independent session keys are generated between users and smart sensing devices to ensure secure communications.
- We design the proposed protocol by integrating a one-way cryptographic hash function, chaotic map, physical unclonable function (PUF), and fuzzy extractor to enhance security and functional integrity. The PUF component provides robust protection against tampering and cloning attacks on the smart sensing device.
- We conduct a formal security analysis of the protocol using the real-or-random (ROR) model to rigorously assess and ensure session key security. Additionally, we provide an informal security analysis to demonstrate resistance to a broad spectrum of attacks.
- A rigorous comparative performance evaluation was conducted to assess the security, functionality, communication overhead, and computational efficiency of the proposed protocol in relation to existing benchmarks. The study clearly demonstrates the proposed protocol’s superior efficiency and enhanced security features compared to existing protocols.
1.3. Novelty
1.4. Paper Organization
2. Background
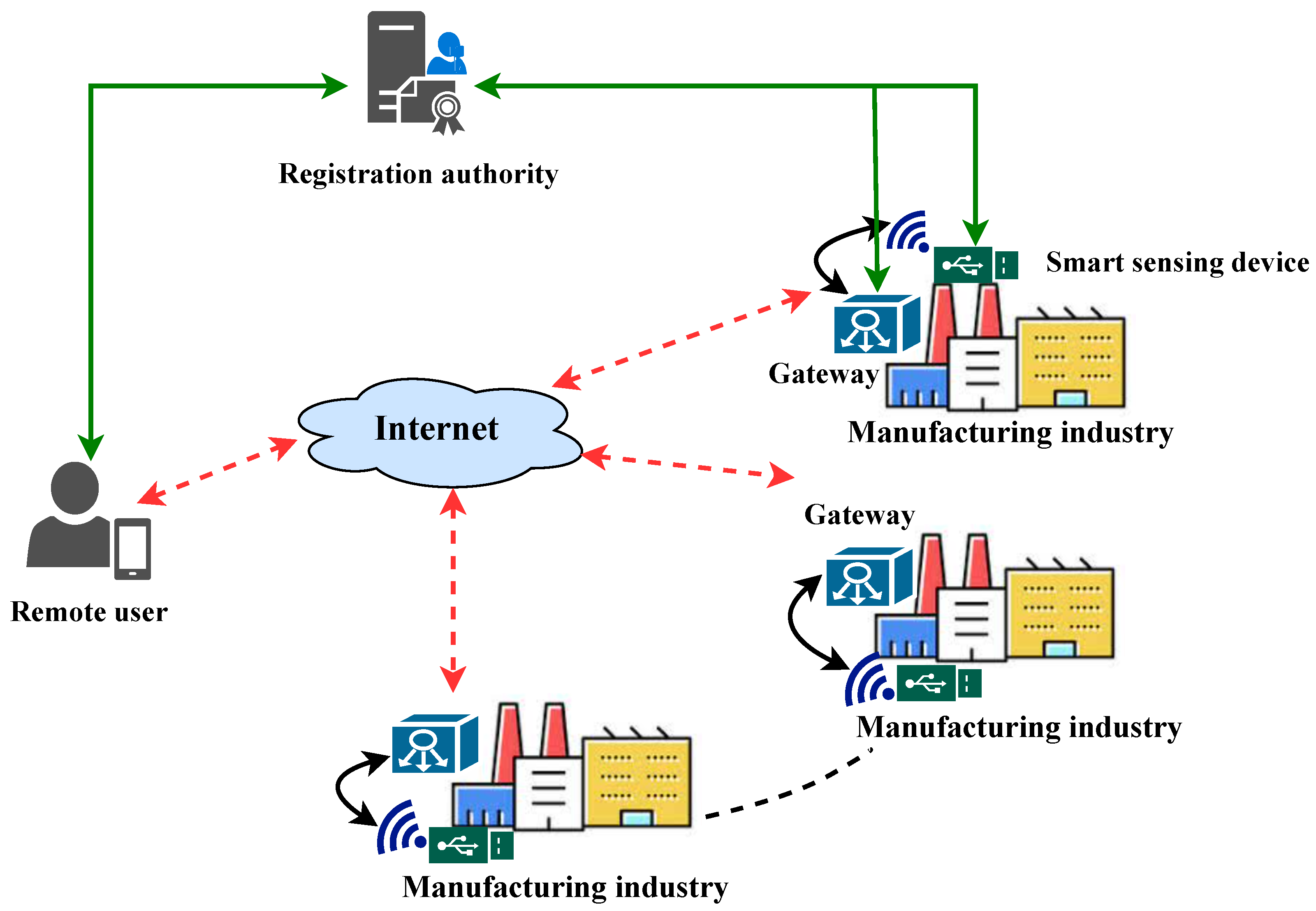
2.1. System Models
2.1.1. Authentication Model
2.1.2. Threat Model
2.2. Preliminaries
2.2.1. Physical Unclonable Function
2.2.2. Fuzzy Extractors
- Generation: Given a unique biometric or PUF measurement of entity i, the generation algorithm produces a cryptographic key and public auxiliary data .
- Reproduction: Utilizing the public auxiliary data and a noisy measurement approximating , the reproduction algorithm reconstructs the original key . For sufficiently similar input measurements (typically within a predetermined Hamming distance), will be identical to .
2.2.3. Chaotic Map
2.3. Design Objectives
- Anonymity: Protect user privacy by ensuring that their identities cannot be inferred from messages, maintaining anonymity throughout communications.
- Mutual Authentication: Verify the authenticity of users, gateways, and smart sensing devices to establish trust within the network.
- Session Key Agreement: Securely establish session keys between users and smart sensing devices, independent of the gateway, for protected communication.
- Unlinkability: Prevent the correlation of intercepted messages with specific users, preserving message anonymity.
- Forward Security: Protect the confidentiality of past communications by ensuring the compromise of current session keys does not affect the security of previous sessions.
- Resistance to Common Attacks: Strengthen the protocol’s defenses against replay, offline password guessing, and impersonation attacks to enhance overall IIoT network security.
3. The Proposed Protocol
3.1. Pre-Deployment Phase
3.1.1. GWN Registration
- Step GR-1: The RA selects a distinct and unique identity, , and a secret parameter, . These are then transmitted securely to through a secure channel.
- Step GR-2: securely stores the received parameters, , in its secure database.
3.1.2. Smart Sensing Device Registration
- Step DR-1: The RA starts the registration process by generating a unique challenge parameter, . This parameter is securely transmitted to over a secure channel.
- Step DR-2: Upon receiving from the RA, uses a to generate the response parameter . This response is then securely sent back to the RA.
- Step DR-3: The RA selects an identity and sends the pair to the appropriate gateway node through a secure channel.
- Step DR-4: Upon receiving the from the RA, generates a random number and computes . It then stores the parameters for in its database and sends back to the RA through a secure channel.
- Step DR-5: The RA finally transmits the parameters to , which then stores these parameters in its memory.
3.1.3. User Registration
- Step UR-1: User submits their registration request to the RA, along with their identity , through a secure channel.
- Step UR-2: The RA then assesses whether the request originates from a legitimate user. It computes using a hash function, where is the master secret key of the RA and is the registration timestamp. Based on the computed hash, it consults the database for the corresponding status. If the status indicates that the user is already registered (), the registration process ceases. Otherwise, the RA proceeds with registration and picks a unique temporary identity , a unique pseudo-identity , and a random number . The user’s smart card is configured with <>. The RA stores <> in its database and forwards the following parameters to the corresponding gateway node as <> via a secure channel and dispatches to .
- Step UR-3: Upon receiving <> from the RA, computes . then stores the parameters as <> in its database.
- Step UR-4: Upon receipt, inserts into a card reader, reads the biometric data , and enters their and password and picks a random number . The smart card then proceeds to compute the following:where is a fuzzy extractor generator function and is an authentication parameter. Finally, the smart card replaces the parameters <> with <> and stores <>.
3.2. Login Phase
- Step L-1: User inserts their designated smart card and subsequently enters their unique identity (), password (), and provides biometric data () via the designated sensor.
- Step L-2: Based on the provided inputs, the following computations are carried out:The is verified against as follows: If the verification fails, the login procedure is aborted. If the verification succeeds, the sign-in process is considered successful, and the following parameters are computed: .
3.3. Authentication and Key Agreement Phase
- Step A-1: generates a random nonce m and uses it to compute as a chaotic-map variable. Then, chooses and selects random nonce , and calculates . Additionally, computes . Afterward, constructs and sends it to the gateway node through an open insecure channel.
- Step A-2: Upon receiving from , searches for , which should match either or . The following computations are then performed:The calculated is checked for equality with , i.e., . If they do not match, the process is terminated. If they match, the procedure continues to the next steps.
- Step A-3: For , retrieves and selects a random nonce . The following computations are then performed:Finally, constructs as and transmits it to through an open insecure channel.
- Step A-4: Upon receiving from , retrieves and and performs the following:The resulting is compared with to verify if . If they do not match, the process is aborted. If they match, the procedure proceeds to the next step.
- Step A-5: inputs the challenge into the function to obtain a device-specific but potentially noisy response, . Due to the inherent variability of PUFs caused by environmental and hardware factors, employs a fuzzy extractor to ensure reliable key derivation. Specifically, the fuzzy extractor generates a stable and reproducible secret key and corresponding helper data , denoted as . This process ensures that even if slightly fluctuates under different conditions, the same can be reliably recovered using the helper data during key reconstruction. Next, selects a random integral string n and a random nonce , and computes the following: , , , , and , where is the generated secret session key between and . Finally, constructs as and sends it to via an open insecure channel.
- Step A-6: Upon receiving from , performs the following computations:accepts the message if holds true. Next, picks a unique temporary identity and updates the old and new temporary identities as and . Then, computes and . Finally, sends to to via an open insecure channel.
- Step A-7: Upon receiving from , computes and . accepts if holds true. Next, computes , and . Finally, stores the session key and updates the temporary identity as .
3.4. Password and Biometrics Update Phase
- Step PBU-1: The legitimate user inserts their smart card and authenticates themselves with their credentials to update their password and biometrics. The following calculations are then performed using the provided inputs:The is verified against as follows: If the verification fails, the login procedure is aborted. If the verification succeeds, can reset the password and update the biometrics data, and the following parameters are computed: .
- Step PBU-1: Next, inputs new information ( and ), and the card executes the following computations:Subsequently, the system updates the existing parameters in the smart card with the new configurations .
3.5. Smart Card Revocation
- Step SCR-1: Initially, securely transmits their identity (), credentials, and a replacement request to RA. The RA assesses these credentials and the validity of the request. Following confirmation, RA issues a replacement smart card, , a unique pseudo-identity , and a random number . Consequently, the freshly configured smart card is configured with <>. The RA stores <> in its database and forwards the following parameters to the corresponding gateway node as < > via a secure channel and dispatches to .
- Step SCR-2: Furthermore, upon receipt of the card, inserts it into a card reader and performs the same steps as outlined in Section 3.1.3 (“User Registration”). Finally, the smart card stores .
3.6. Dynamic Smart Device Addition Phase
- Step DA-1: The RA starts the registration process by generating a unique challenge parameter, . This parameter is securely transmitted to over a secure channel.
- Step DA-2: Upon receiving from the RA, uses a to generate the response parameter . This response is then securely sent back to the RA.
- Step DA-3: The RA selects an identity and sends the pair to the appropriate gateway node through a secure channel.
- Step DA-4: Upon receiving the from the RA, generates a random number and computes . It then stores the parameters for in its database and sends back to the RA through a secure channel.
- Step DA-5: The RA finally transmits the parameters to , which then stores these parameters in its memory.
4. Informal Security Analysis
4.1. Smart Sensing Device Capture Attack
4.2. Gateway Node Capture Attack
4.3. Anonymity and Untraceability
4.4. De-Synchronization Attack
4.5. Replay Attack
4.6. MitM Attack
4.7. Mutual Authentication
4.8. Session Key Security
4.9. Perfect Forward Secrecy
4.10. ESL Attack
- Scenario 1: If the attacker manages to obtain the temporary secrets , , , , and , the hash function ’s collision-resistant properties make it difficult for to derive the session key without also having access to the long-term secrets , , , , , and .
- Scenario 2: Even if gains possession of the long-term secrets , , , , , and , the absence of short-term secrets still makes it impractical for to compute the session key.
4.11. Stolen Smartcards and Privileged-Insiders Attacks
4.12. Resistance to Modeling Attacks
4.13. Impersonation Attacks
5. Formal Security Analysis
6. Performance Evaluation
6.1. Computational Overhead
6.2. Runtime Comparison
6.3. Communication Overhead
6.4. Storage Overhead
| Feature | [60] | [61] | [62] | [63] | [64] | Our |
|---|---|---|---|---|---|---|
| ✓ | × | × | × | × | ✓ | |
| ✓ | ✓ | × | ✓ | ✓ | ✓ | |
| ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
 | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| × | ✓ | ✓ | ✓ | ✓ | ✓ | |
| ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| × | × | ✓ | × | × | ✓ | |
| ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
 : Mutual authentication; : Independent session key establishment; : Perfect forward secrecy; : No clock synchronization; : ESL attack; : Stolen smartcard and privileged-insider attacks; and : Impersonation attacks; ✓: indicates feature availability; ×: indicates feature unavailability or inapplicability.
: Mutual authentication; : Independent session key establishment; : Perfect forward secrecy; : No clock synchronization; : ESL attack; : Stolen smartcard and privileged-insider attacks; and : Impersonation attacks; ✓: indicates feature availability; ×: indicates feature unavailability or inapplicability.6.5. Security and Functionality Features
 : Mutual authentication; : Independent session key establishment; : Perfect forward secrecy; : No clock synchronization; : ESL attack; : Smartcard theft and insider threats; and : Impersonation attacks. In Table 8, a check mark (✓) denotes the presence of a feature, while a cross (×) indicates its absence or inapplicability. The comparison reveals that the proposed protocol is the only one to encompass all the essential and critical security and functionality features. Conversely, the benchmark protocols show shortcomings, either missing certain features or failing to counter specific security threats.
: Mutual authentication; : Independent session key establishment; : Perfect forward secrecy; : No clock synchronization; : ESL attack; : Smartcard theft and insider threats; and : Impersonation attacks. In Table 8, a check mark (✓) denotes the presence of a feature, while a cross (×) indicates its absence or inapplicability. The comparison reveals that the proposed protocol is the only one to encompass all the essential and critical security and functionality features. Conversely, the benchmark protocols show shortcomings, either missing certain features or failing to counter specific security threats.6.6. Critical Discussion
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Kebande, V.R.; Awad, A.I. Industrial Internet of Things ecosystems security and digital forensics: Achievements, open challenges, and future directions. ACM Comput. Surv. 2024, 56, 131. [Google Scholar] [CrossRef]
- Awaisi, K.S.; Ye, Q.; Sampalli, S. A survey of industrial AIoT: Opportunities, challenges, and directions. IEEE Access 2024, 12, 96946–96996. [Google Scholar] [CrossRef]
- Nallakaruppan, M.K.; Dhanaraj, R.K.; Shukla, S.; Subbaraj, K.; Fuladi, S.; Selvarajan, S.; Alkhayyat, A.; Alturki, N. Reliable secured consumer IIoT framework with multi-layer attack interpretation and prevention. IEEE Trans. Consum. Electron. 2025, 71, 5036–5043. [Google Scholar] [CrossRef]
- Sah, D.K.; Vahabi, M.; Fotouhi, H. A comprehensive review on 5G IIoT test-beds. IEEE Trans. Consum. Electron. 2025, 71, 4139–4163. [Google Scholar] [CrossRef]
- Khan, W.Z.; Aalsalem, M.Y.; Khan, M.K. Communal acts of IoT consumers: A potential threat to security and privacy. IEEE Trans. Consum. Electron. 2019, 65, 64–72. [Google Scholar] [CrossRef]
- Sun, G.; Xu, Z.; Yu, H.; Chang, V. Dynamic network function provisioning to enable network in box for industrial applications. IEEE Trans. Ind. Inform. 2021, 17, 7155–7164. [Google Scholar] [CrossRef]
- Yu, F.; Wang, X.; Guo, R.; Ying, Z.; Cai, S.; Jin, J. Dynamical analysis, hardware implementation, and image encryption application of new 4D discrete hyperchaotic maps based on parallel and cascade memristors. Integration 2025, 104, 102475. [Google Scholar] [CrossRef]
- Sun, G.; Song, L.; Yu, H.; Chang, V.; Du, X.; Guizani, M. V2V routing in a VANET based on the autoregressive integrated moving average model. IEEE Trans. Veh. Technol. 2019, 68, 908–922. [Google Scholar] [CrossRef]
- Zhang, M.; Wei, E.; Berry, R.; Huang, J. Age-dependent differential privacy. IEEE Trans. Inf. Theory 2024, 70, 1300–1319. [Google Scholar] [CrossRef]
- Luo, T.; Zhou, Y.; He, Z.; Jiang, G.; Xu, H.; Qi, S.; Zhang, Y. StegMamba: Distortion-free immune-cover for multi-image steganography with state space model. IEEE Trans. Circuits Syst. Video Technol. 2025, 35, 4576–4591. [Google Scholar] [CrossRef]
- Han, F.; Yang, P.; Du, H.; Li, X.-Y. Accuth++: Accelerometer-based anti-spoofing voice authentication on wrist-worn wearables. IEEE Trans. Mob. Comput. 2024, 23, 5571–5588. [Google Scholar] [CrossRef]
- Hu, J.; Jiang, H.; Liu, D.; Xiao, Z.; Dustdar, S.; Liu, J. A wireless self-service system for library using commodity RFID devices. IEEE Internet Things J. 2024, 11, 4998–5010. [Google Scholar] [CrossRef]
- Xu, G.; Lei, L.; Mao, Y.; Li, Z.; Chen, X.; Zhang, K. CBRFL: A framework for committee-based Byzantine-resilient federated learning. J. Netw. Comput. Appl. 2025, 238, 104165. [Google Scholar] [CrossRef]
- Yanambaka, V.P.; Mohanty, S.P.; Kougianos, E.; Puthal, D. PMsec: Physical unclonable function-based robust and lightweight authentication in the Internet of medical things. IEEE Trans. Consum. Electron. 2019, 65, 388–397. [Google Scholar] [CrossRef]
- Ai, X.; Badshah, A.; Tu, S.; Waqas, M.; Ahmad, I. An improved ultra-lightweight anonymous authenticated key agreement protocol for wearable devices. IEEE Trans. Mob. Comput. 2025, 24, 4543–4557. [Google Scholar] [CrossRef]
- Zhou, Z.; Shojafar, M.; Alazab, M.; Abawajy, J.; Li, F. AFED-EF: An energy-efficient VM allocation algorithm for IoT applications in a cloud data center. IEEE Trans. Green Commun. Netw. 2021, 5, 658–669. [Google Scholar] [CrossRef]
- Chen, Y.; Liang, X.; Zhou, H.; Yang, X.; Wu, L.; Lv, G. GENDN: A geospatially enhanced NDN framework for location-related pub/sub services in NTN-enabled IoT. IEEE Internet Things J. 2025, 12, 8381–8393. [Google Scholar] [CrossRef]
- Xu, G.; Xu, S.; Fan, X.; Cao, Y.; Mao, Y.; Xie, Y.; Chen, X. RAT ring: Event-driven publish/subscribe communication protocol for IIoT by report and traceable ring signature. IEEE Trans. Ind. Inform. 2025, 21, 6670–6678. [Google Scholar] [CrossRef]
- Xu, Y.; Liu, Y.; Lei, M.; Gao, M.; Fang, Z.; Jiang, C. Joint pseudo-range and Doppler positioning method with LEO satellites’ signals of opportunity. Satell. Nav. 2025, 6, 10. [Google Scholar] [CrossRef]
- Ding, F.; Liu, Z.; Wang, Y.; Liu, J.; Wei, C.; Nguyen, A.; Wang, N. Intelligent event-triggered lane keeping security control for autonomous vehicle under DoS attacks. IEEE Trans. Fuzzy Syst. 2025, 33, 3595–3608. [Google Scholar] [CrossRef]
- Turkanović, M.; Brumen, B.; Hölbl, M. A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the Internet of Things notion. Ad Hoc Netw. 2014, 20, 96–112. [Google Scholar] [CrossRef]
- Tai, W.-L.; Chang, Y.-F.; Li, W.-H. An IoT notion-based authentication and key agreement scheme ensuring user anonymity for heterogeneous ad hoc wireless sensor networks. J. Inf. Secur. Appl. 2017, 34, 133–141. [Google Scholar] [CrossRef]
- Chen, Y.; Yin, F.; Hu, S.; Sun, L.; Li, Y.; Xing, B.; Chen, L.; Guo, B. ECC-based authenticated key agreement protocol for industrial control system. IEEE Internet Things J. 2022, 10, 4688–4697. [Google Scholar] [CrossRef]
- Shuai, M.; Xiong, L.; Wang, C.; Yu, N. A secure authentication scheme with forward secrecy for industrial Internet of Things using Rabin cryptosystem. Comput. Commun. 2020, 160, 215–227. [Google Scholar] [CrossRef]
- Gong, B.; Wu, Y.; Badshah, A.; Waqas, M. Privacy-preserving and traceable certificateless anonymous mutual authentication scheme for IoT. IEEE Trans. Dependable Secur. Comput. 2025, 22, 7508–7520. [Google Scholar] [CrossRef]
- Zeng, D.; Badshah, A.; Tu, S.; Waqas, M.; Han, Z. A security-enhanced ultra-lightweight and anonymous user authentication protocol for telehealthcare information systems. IEEE Trans. Mob. Comput. 2025, 24, 4529–4542. [Google Scholar] [CrossRef]
- Hammad, M.; Badshah, A.; Almeer, M.A.; Waqas, M.; Song, H.H.; Chen, S.; Han, Z. Lightweight and robust key agreement for securing IIoT-driven flexible manufacturing systems. IEEE Internet Things J. 2025, 12, 17197–17209. [Google Scholar] [CrossRef]
- Zhai, Z.; Liu, J.; Liu, X.; Mao, Y.; Zhang, X.; Ma, J.; Jin, C. A lightweight authentication method for Industrial Internet of Things based on blockchain and Chebyshev chaotic maps. Future Internet 2025, 17, 338. [Google Scholar] [CrossRef]
- Aman, M.N.; Basheer, M.H.; Sikdar, B. A lightweight protocol for secure data provenance in the Internet of Things using wireless fingerprints. IEEE Syst. J. 2021, 15, 2948–2958. [Google Scholar] [CrossRef]
- Modarres, A.M.A.; Sarbishaei, G. An improved lightweight two-factor authentication protocol for IoT applications. IEEE Trans. Ind. Inform. 2023, 19, 6588–6598. [Google Scholar] [CrossRef]
- Rafique, F.; Obaidat, M.S.; Mahmood, K.; Ayub, M.F.; Ferzund, J.; Chaudhry, S.A. An efficient and provably secure certificateless protocol for industrial Internet of Things. IEEE Trans. Ind. Inform. 2022, 18, 8039–8046. [Google Scholar] [CrossRef]
- Yi, F.; Zhang, L.; Xu, L.; Yang, S.; Lu, Y.; Zhao, D. WSNEAP: An efficient authentication protocol for IIoT-oriented wireless sensor networks. Sensors 2022, 22, 7413. [Google Scholar] [CrossRef]
- Eldefrawy, M.H.; Ferrari, N.; Gidlund, M. Dynamic user authentication protocol for industrial IoT without timestamping. In Proceedings of the 2019 15th IEEE International Workshop on Factory Communication Systems (WFCS), Sundsvall, Sweden, 27–29 May 2019; pp. 1–7. [Google Scholar]
- Harishma, B.; Patranabis, S.; Chatterjee, U.; Mukhopadhyay, D. POSTER: Authenticated key-exchange protocol for heterogeneous CPS. In Proceedings of the 2018 Asia Conference on Computer and Communications Security, Incheon, Republic of Korea, 4–8 June 2018; pp. 849–851. [Google Scholar]
- Mutlaq, K.A.-A.; Nyangaresi, V.O.; Omar, M.A.; Abduljabbar, Z.A. Symmetric key based scheme for verification token generation in Internet of Things communication environment. In Proceedings of the EAI International Conference on Applied Cryptography in Computer and Communications, Virtual Event, 14–15 May 2022; pp. 46–64. [Google Scholar]
- Chen, Y.; Martínez, J.-F.; Castillejo, P.; López, L. A privacy protection user authentication and key agreement scheme tailored for the Internet of Things environment: PriAuth. Wirel. Commun. Mob. Comput. 2017, 2017, 5290579. [Google Scholar] [CrossRef]
- Patel, C.; Doshi, N. Cryptanalysis of ECC-based key agreement scheme for generic IoT network model. In Proceedings of the 2019 10th International Conference on Computing, Communication and Networking Technologies (ICCCNT), Kanpur, India, 6–8 July 2019; pp. 1–7. [Google Scholar]
- Chen, P.; Song, Y.; Xia, Y. Adaptively diagnosing system faults in microservice architecture: An autonomous predictive model construction framework. Future Gener. Comput. Syst. 2025, 177, 108256. [Google Scholar] [CrossRef]
- Jiang, H.; Ye, L.; Hu, J.; Chen, X.; Chen, S.; Zhang, W.; Yang, K. WarmGait: Thermal array-based gait recognition for privacy-preserving person re-ID. IEEE Trans. Mob. Comput. 2025, 1–14. [Google Scholar] [CrossRef]
- Luo, H.; Li, Q.; Cheng, H.; Li, W.; Sun, W.; Zhao, W.; Liu, Z. A2Tformer: Addressing temporal bias and non-stationarity in transformer-based IoT time series classification. IEEE Internet Things J. 2025, 12, 42198–42213. [Google Scholar] [CrossRef]
- Zhang, K.; Wang, H.; Chen, M.; Chen, X.; Liu, L.; Geng, Q.; Zhou, Y. Leveraging machine learning to proactively identify phishing campaigns before they strike. J. Big Data 2025, 12, 124. [Google Scholar] [CrossRef]
- Xu, G.; Wang, L.; Chen, S.; Zhu, L.; Guizani, M.; Shi, L. MPAEE: A multi-path adaptive energy-efficient routing scheme for low earth orbit-based industrial Internet of Things. IEEE Internet Things J. 2025, 12, 34793–34805. [Google Scholar] [CrossRef]
- Sun, Q.; Jian, X.; Han, C.; Li, Y. An improved opportunistic localization algorithm using LEO signals based on PSODC. IEEE Trans. Instrum. Meas. 2025, 74, 8512110. [Google Scholar] [CrossRef]
- Liu, X.; Zhao, L.; Jin, J. A noise-tolerant fuzzy-type zeroing neural network for robust synchronization of chaotic systems. Concurr. Comput. Pract. Exp. 2024, 36, e8218. [Google Scholar] [CrossRef]
- Shen, X.; Li, L.; Ma, Y.; Xu, S.; Liu, J.; Yang, Z.; Shi, Y. VLCIM: A vision-language cyclic interaction model for industrial defect detection. IEEE Trans. Instrum. Meas. 2025, 74, 2538713. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Guo, X.; Zhang, J.; Meng, X.; Li, Z.; Wen, X.; Girard, P.; Liang, B.; Yan, A. HALTRAV: Design of a high-performance and area-efficient latch with triple-node-upset recovery and algorithm-based verifications. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2024, 44, 2367–2377. [Google Scholar] [CrossRef]
- Canetti, R.; Krawczyk, H. Universally composable notions of key exchange and secure channels. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Amsterdam, The Netherlands, 28 April–2 May 2002; pp. 337–351. [Google Scholar]
- Yang, J.; Liu, Y.; Wang, W.; Wu, H.; Chen, Z.; Ma, X. PATNAS: A path-based training-free neural architecture search. IEEE Trans. Pattern Anal. Mach. Intell. 2024, 47, 1484–1500. [Google Scholar] [CrossRef]
- Zhao, Z.; Li, X.; Luan, B.; Jiang, W.; Gao, W.; Neelakandan, S. Secure Internet of Things using a novel Brooks–Iyengar quantum Byzantine agreement-centered blockchain networking model in smart healthcare. Inf. Sci. 2023, 629, 440–455. [Google Scholar] [CrossRef]
- Herder, C.; Yu, M.-D.; Koushanfar, F.; Devadas, S. Physical unclonable functions and applications: A tutorial. Proc. IEEE 2014, 102, 1126–1141. [Google Scholar] [CrossRef]
- Zhou, Z.; Abawajy, J.; Chowdhury, M.; Hu, Z.; Li, K.; Cheng, H.; Alelaiwi, A.A.; Li, F. Minimizing SLA violation and power consumption in cloud data centers using adaptive energy-aware algorithms. Future Gener. Comput. Syst. 2018, 86, 836–850. [Google Scholar] [CrossRef]
- Delvaux, J.; Gu, D.; Verbauwhede, I.; Hiller, M.; Yu, M.-D. Efficient fuzzy extraction of PUF-induced secrets: Theory and applications. In Cryptographic Hardware and Embedded Systems—CHES 2016; Gierlichs, B., Poschmann, A.Y., Eds.; Springer: Berlin/Heidelberg, Germany, 2016; pp. 412–431. [Google Scholar]
- Lee, T.-F. Efficient three-party authenticated key agreements based on Chebyshev chaotic map-based Diffie–Hellman assumption. Nonlinear Dyn. 2015, 81, 2071–2078. [Google Scholar] [CrossRef]
- Wu, Z.Y.; Ismail, M.; Zhang, J.; Zhang, J. Tidal-like concept drift in RIS-covered buildings: When programmable wireless environments meet human behaviors. IEEE Wireless Commun. 2025, 1–8. [Google Scholar] [CrossRef]
- Zhang, K.; Zheng, B.; Xue, J.; Zhou, Y. Explainable and trust-aware AI-driven network slicing framework for 6G IoT using deep learning. IEEE Internet Things J. 2025. [Google Scholar] [CrossRef]
- Bergamo, P.; D’Arco, P.; De Santis, A.; Kocarev, L. Security of public-key cryptosystems based on Chebyshev polynomials. IEEE Trans. Circuits Syst. I Regul. Pap. 2005, 52, 1382–1393. [Google Scholar] [CrossRef]
- Yoshioka, D. Security of public-key cryptosystems based on Chebyshev polynomials over Z/pkZ. IEEE Trans. Circuits Syst. II Express Briefs 2020, 67, 2204–2208. [Google Scholar]
- Xiao, L.; Zhao, L.; Jin, J. Preset-time convergence fuzzy zeroing neural network for chaotic system synchronization: FPGA validation and secure communication applications. Sensors 2025, 25, 5394. [Google Scholar] [CrossRef]
- Hammad, M.; Badshah, A.; Abbas, G.; Alasmary, H.; Waqas, M.; Khan, W.A. A provable secure and efficient authentication framework for smart manufacturing industry. IEEE Access 2023, 11, 67626–67639. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Alazab, M. Designing authenticated key management scheme in 6G-enabled network in a box deployed for industrial applications. IEEE Trans. Ind. Inform. 2021, 17, 7174–7184. [Google Scholar] [CrossRef]
- Yang, Z.; He, J.; Tian, Y.; Zhou, J. Faster authenticated key agreement with perfect forward secrecy for industrial Internet-of-Things. IEEE Trans. Ind. Inform. 2020, 16, 6584–6596. [Google Scholar] [CrossRef]
- Sutrala, A.K.; Obaidat, M.S.; Saha, S.; Das, A.K.; Alazab, M.; Park, Y. Authenticated key agreement scheme with user anonymity and untraceability for 5G-enabled softwarized industrial cyber-physical systems. IEEE Trans. Intell. Transp. Syst. 2022, 23, 2316–2330. [Google Scholar] [CrossRef]
- Srinivas, J.; Das, A.K.; Wazid, M.; Kumar, N. Anonymous lightweight chaotic map-based authenticated key agreement protocol for industrial Internet of Things. IEEE Trans. Dependable Secur. Comput. 2020, 17, 1133–1146. [Google Scholar] [CrossRef]


| Protocol | Cryptographic Primitives | Descriptions | Limitations |
|---|---|---|---|
| Turkanović et al. [21] | • Cryptographic hash function | • Lightweight • Dynamic addition of sensor nodes • Free password update | • No PUF-based physical security provided • Strict clock synchronization required • Anonymity not provided • No resistance to sensor capture attacks |
| Chen et al. [23] | • Cryptographic hash function • Elliptic curve cryptography | • Supporting node revocation • No strict clock synchronization | • No PUF-based physical security provided • Excessive system overhead • Lack of perfect forward secrecy • No resistance to ephemeral secret leakage attacks |
| Shuai et al. [24] | • Cryptographic hash function • Rabin cryptosystem | • Free password update • Dynamic addition of sensor nodes | • No PUF-based physical security provided • Strict clock synchronization required • No resistance to offline guessing and user impersonation attacks • No resistance to privileged insider and eavesdropping attacks • No resistance to stolen smart-card attacks |
| Zhai et al. [28] | • Cryptographic hash function • Chaotic Map | • Lightweight • Supporting cross-domain authentication | • No PUF-based physical security provided • Strict clock synchronization required • Lack of anonymity and untraceability |
| Aman et al. [29] | • Cryptographic hash function • PUF | • Lightweight • Providing PUF-based physical security • No strict clock synchronization | • No resistance to replay and non-invasive physical attacks • The neglect of PUF noise impact |
| Rafique et al. [31] | • Cryptographic hash function • AES symmetric encryption/decryption | • Lightweight | • No PUF-based physical security provided • No resistance to smart-card and device theft attacks • Strict clock synchronization required |
| Eldefrawy et al. [33] | • Cryptographic hash function | • Lightweight • Free password update • Dynamic addition/revocation of sensor nodes • No strict clock synchronization | • No PUF-based physical security provided • Lack of mutual authentication |
| Harishma et al. [34] | • Cryptographic hash function • Identity-based encryption • PUF | • Providing PUF-based physical security • No strict clock synchronization | • No resistance to ephemeral secret leakage attacks |
| Chen et al. [36] | • Cryptographic hash function • Elliptic curve cryptography | • Lightweight | • No PUF-based physical security provided • No resistance to insider and node-capturing attacks • Strict clock synchronization required • Lack of untraceability |
| Symbol | Definition |
|---|---|
| kth GWN | |
| Secret parameter of | |
| Identity of | |
| jth smart sensing deivce | |
| Challenge component for | |
| Response component for | |
| Secret parameter bound to | |
| Cryptographic key and auxiliary data of | |
| ith user | |
| Identity and password of | |
| Biometric template of | |
| Cryptographic key and auxiliary data of | |
| Smart card of and its number of | |
| Secret parameter bound to | |
| Pseudo-identity of | |
| Physical unclonable function associated with | |
| The trusted registration authority | |
| Smart card number | |
| Session key | |
| Temporary identity of | |
| The Old/new temporary identitity | |
| Secret key of | |
| Cryptographic hash function | |
| Fuzzy extractor generation function | |
| Fuzzy extractor reproduction function |
| Query | Functionality |
|---|---|
| This query allows the adversary to passively observe and collect messages exchanged among and , facilitating the evaluation of forward secrecy. | |
| This query enables the simulation of active attacks, such as impersonation and replay. The adversary sends a message to and receives the corresponding response. | |
| Upon executing this query, the adversary obtains complete access to the credentials stored on the compromised smart card belonging to the legitimate registered user . | |
| This query discloses the actual session key if has been accepted. | |
| This query returns the real session key when , or a random string of the same length when . If can consistently guess the value of b correctly, it signifies a successful compromise of the session key’s semantic security. |
| Operation | Platform-I | Platform-II |
|---|---|---|
| Hash function () | 0.007 ms | 0.001 ms |
| ECC point multiplication () | 6.549 ms | 0.846 ms |
| ECC point addition () | 0.273 ms | 0.002 ms |
| Physical unclonable function () | 0.5 s | – |
| Fuzzy extractor () | 6.549 ms | 0.846 ms |
| Chaotic map () | 0.102 ms | 0.019 ms |
| Protocol | User | GWN / Server | Smart Sensing Device | Total Overhead |
|---|---|---|---|---|
| Hammad et al. [60] | ||||
| Wazid et al. [61] | ||||
| Yang et al. [62] | ||||
| Sutrala et al. [63] | ||||
| Srinivas et al. [64] | ||||
| Our Proposed |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zeng, D.; Badshah, A.; Tu, S.; Ai, X.; Alasmary, H.; Waqas, M.; Khan, M.T. Anonymous and Efficient Chaotic Map-Based Authentication Protocol for Industrial Internet of Things. Sensors 2025, 25, 7676. https://doi.org/10.3390/s25247676
Zeng D, Badshah A, Tu S, Ai X, Alasmary H, Waqas M, Khan MT. Anonymous and Efficient Chaotic Map-Based Authentication Protocol for Industrial Internet of Things. Sensors. 2025; 25(24):7676. https://doi.org/10.3390/s25247676
Chicago/Turabian StyleZeng, Dake, Akhtar Badshah, Shanshan Tu, Xin Ai, Hisham Alasmary, Muhammad Waqas, and Muhammad Taimoor Khan. 2025. "Anonymous and Efficient Chaotic Map-Based Authentication Protocol for Industrial Internet of Things" Sensors 25, no. 24: 7676. https://doi.org/10.3390/s25247676
APA StyleZeng, D., Badshah, A., Tu, S., Ai, X., Alasmary, H., Waqas, M., & Khan, M. T. (2025). Anonymous and Efficient Chaotic Map-Based Authentication Protocol for Industrial Internet of Things. Sensors, 25(24), 7676. https://doi.org/10.3390/s25247676






