Abstract
The Internet of Things (IoT) and Edge Computing (EC) play an essential role in today’s communication systems, supporting diverse applications in industry, healthcare, and environmental monitoring; however, these technologies face a major challenge in accurately determining the geographic origin of sensed data, as such data are meaningful only when their source location is known. The use of Global Positioning System (GPS) is often impractical or inefficient in many environments due to limited satellite coverage, high energy consumption, and environmental interference. This paper recruits the Distance Vector-Hop (DV-Hop), Jellyfish Search (JS), and Artificial Rabbits Optimization (ARO) algorithms and presents an innovative GPS-free positioning framework for three-dimensional (3D) EC environments. In the proposed framework, the basic DV-Hop and multi-angulation algorithms are generalized for three-dimensional environments. Next, both algorithms are structurally modified and integrated in a complementary manner to balance exploration and exploitation. Furthermore, a Lévy flight-based perturbation phase and a local search mechanism are incorporated to enhance convergence speed and solution precision. To evaluate performance, sixteen 3D IoT environments with different configurations were simulated, and the results were compared with nine state-of-the-art localization algorithms using MSE, NLE, ALE, and LEV metrics. The quantitative relative improvement ratio test demonstrates that the proposed method is, on average, 39% more accurate than its competitors.
1. Introduction
Edge Computing (EC) is the most contemporary communication paradigm in today’s networks, employed in numerous fields [1]. The Internet of Things (IoT) forms the bottommost layer of EC environments, which is also called the edge layer. This layer generally comprises end-user devices, sensors, actuators, cameras, etc. In data-oriented surveillance networks, the devices of this layer collect environmental data and send them to the base stations/sinks or higher layers for further processing [2]. However, this layer’s sensors, actuators, and other equipment face the processing, storage, communication, and especially energy resource constraints [3]. Interest in the field of location-aware services in IoT, in which the geographical location of devices and their sensed data from the surroundings is crucial, is growing enormously. Detecting the location of IoT devices and their data is one of the fundamental requirements of IoT and EC networks for many wireless applications, which is known as localization/positioning [4].
Locating data, sensors, and wireless IoT devices is a challenging problem due to the dynamic and erratic nature of environments and the limited resources of devices, particularly energy limitations. Existing traditional approaches, including GPS-based methods, manual measurement methods, etc., are not appropriate for today’s dynamic large-scale networks with high data volume due to reasons such as high cost of procurement and maintenance, lack of re-access to devices, limited energy, coverage constraints, and high time consumption. Consequently, along with the development of network equipment and communication technologies, the demand for optimal positioning algorithms is felt more and more [5].
Utilizing GPS can be practical, but the accuracy of its position estimation in indoor environments, deep forests, under the sea, etc., is not satisfactory enough. Also, embedding GPS in surveillance equipment increases the cost of implementation and setup [6]. Additionally, the GPS hardware increases power consumption, which is inappropriate for power-constrained devices. As a result, researchers conducted various studies to devise alternative methods aimed at how to use the interaction and connectivity between nodes to estimate position [7].
The need for GPS-free localization arises prominently in environments where satellite signals are unavailable, attenuated, or unreliable. For instance, in underground mines, tunnels, and subterranean infrastructures, GPS signals cannot penetrate soil or rock layers, making traditional satellite-based localization infeasible. In such contexts, accurate positioning of IoT-enabled equipment, robots, and personnel faces major challenges. Similarly, disaster zones, such as collapsed buildings, forest fires, or earthquake-affected areas, often experience severe signal blockage or infrastructure damage. Deploying GPS-free IoT localization systems in these scenarios allows first responders to accurately locate trapped victims, assess structural integrity, and coordinate rescue operations in real time without relying on external satellite connectivity [8].
Furthermore, industrial and urban environments—including smart factories, large warehouses, oil refineries, and indoor logistics facilities—frequently suffer from multipath fading, electromagnetic interference, and signal occlusion caused by dense metallic structures and machinery. In these harsh or cluttered environments, GPS-based positioning can become highly inaccurate or entirely unavailable. Consequently, GPS-free localization frameworks provide a reliable alternative for maintaining continuous and precise positioning. They enable efficient asset tracking, autonomous robotic operations, and process monitoring even under severe signal distortions, thereby ensuring robust and energy-efficient operation of IoT and edge computing networks in real-world industrial and emergency scenarios [9].
The GPS-free positioning strategies are generally classified into range-based and range-free algorithms. Range-based localization algorithms require additional equipment to acquire some necessary information, such as signal strength or received angle, to estimate the position of unknown devices [10]. These methods have higher accuracy, but, due to the need for additional equipment, they are more costly. In contrast, range-free algorithms estimate the location of unknown devices by the nature of the network, the relationship between devices, the connectivity and density of the network, the number of hops, and distance calculation. Range-free algorithms have relatively lower positioning accuracy, but, due to their low cost and simplicity, they are more suitable for today’s large-scale networks [11].
Among the range-free positioning algorithms, the Distance Vector-Hop (DV-Hop) is the most optimal, simple, and widely used method for estimating the position of IoT devices in large-scale networks [12]. The DV-Hop estimates the distance through the number of hops between unknown IoT nodes and beacons. The DV-Hop returns the same distances for the nodes whose hop counts from the beacon are identical. This is due to DV-Hop’s use of the average step size, while the length of the hops in the network is disparate. Therefore, the DV-Hop estimates positions with a major error, especially in three-dimensional, large-scale environments. Accordingly, researchers have attempted in recent years to enhance DV-Hop’s accuracy by embedding other techniques in it [13].
In the hybrid methods, the combination of DV-Hop with meta-heuristic algorithms has been highly regarded, and the resulting algorithms indicated adequate performance and accuracy [14]. Metaheuristic algorithms do not demand any information about the problem [15]. As a result, these algorithms are applied to a wide range of complex real-world problems. These algorithms are also able to find a near-optimal solution for the given problem with any set of initial solutions [16]. The optimality of the final solution obtained by them can be adjusted by two parameters: the number of iterations and the number of search agents. The higher the values of these parameters are, the more optimal the final solution will be, but the execution time will also increase [17].
In this research, a new positioning algorithm named EJSARO is presented for 3D IoT networks based on the hybridization of the DV-Hop and meta-heuristic algorithms. In the first step of the proposed method, the basic VD-Hop algorithm has been extended to count hops and estimate the distance in three-dimensional environments. Next, the multi-literation method is recruited to estimate the initial positions of unknown objects using the distance and hops calculated by 3D-DV-Hop. Then, a new hybrid metaheuristic algorithm is introduced based on Jellyfish Search (JS) and Artificial Rabbits Optimization (ARO) algorithms to improve the initially estimated positions. In the proposed hybrid metaheuristic algorithm, the original ARO and JS algorithms are modified and lightened. The modified JS and ARO are then hybridized in a complementary manner. Subsequently, the outcome hybrid algorithm is enhanced by the Lévy flight function-based intermediate phase. Additionally, a new local search mechanism is provided to exploit the best area discovered by the algorithm.
To put it concisely, the main contributions and novelties of our work are as below:
- The classical DV-Hop algorithm is mathematically generalized from 2D to 3D environments, redefining hop-count computation, distance estimation, and multilateration equations.
- A new hybrid optimization algorithm combining Jellyfish Search (JS) and Artificial Rabbits Optimization (ARO) is proposed.
- Both algorithms are structurally modified: redundant mechanisms are removed, and key operators are redesigned to achieve a lighter and faster hybrid while preserving exploration–exploitation balance.
- The hybridization is complementary, not sequential—each component enhances the other’s deficiencies, which has not been performed before.
- A Lévy flight-driven motion phase is introduced to enable controlled random jumps, enhancing the ability to escape local optima and explore the search space globally.
- A counter-based local departure mechanism is introduced to detect stagnation and dynamically reinitialize stuck solutions, ensuring diversity and maintaining convergence stability. This mechanism acts as an adaptive restart process—a unique feature not seen in previous hybrid positioning algorithms.
- A greedy local search strategy is provided to improve the best-found solution iteratively by exploiting its neighborhood, increasing the precision of final position estimates.
- Sixteen diverse 3D IoT environments were designed to test the performance of the positioning methods under varying densities, scales, and anchor configurations—something rarely seen in prior 3D localization works.
- The proposed framework is evaluated against nine state-of-the-art algorithms, showing superior Mean Square Error (MSE), Node Localization Error (NLE), Average Localization Error (ALE), and Localization Error Variance (LEV) performance metrics.
The rest of this paper is organized as follows: Section 2 explores related research. Section 3 introduces the basic algorithms employed in developing the proposed algorithm. Section 4 exposes the implementation details of the proposed method and the contributions made. Section 5 provides the results of extensive experiments conducted to assess the potency of the proposed method. Eventually, Section 6 summarizes this paper and gives directions for future research.
2. Literature Review
Various studies have been conducted in the field of refining data aggregation, improving quality-of-service (QoS), reducing communication time, faster computing, achieving real-time communication, and diminishing energy consumption to augment IoT networks’ productivity. The positioning/localization problem is one of the critical challenges faced by IoT networks because, in most applications, these networks require location information. Accordingly, numerous research studies have been conducted in this orientation. For instance, Yang and Wang employed the Grey Wolf Optimizer and DV-hop algorithm and presented a new localization algorithm for WSN-based IoT networks [18]. In the proposed method, the hop counts obtained by the DV-Hop algorithm are refined by a dual communication radius. The authors claim that using a dual communication radius can enhance the hop count estimation process. In the next step, the minimum hop count between beacons is obtained by a new hop adjustment factor, which can be calculated from the average hop distance more accurately. Likewise, the hop distances between unknown IoT devices and the beacons are estimated through a weighted optimization regarding the mean square error criterion. Then, the basic GWO is improved by some modifications and used to compute the position of unknown nodes. The experimental results show that the proposed algorithm has lower localization.
Similarly, Sun and Yang employed the Black-winged Kite Algorithm (BKA) and presented a range-free positioning model for two-dimensional WSN environments [19]. In the proposed algorithm, the accuracy of the distance estimation obtained by the DV-Hop algorithm is enhanced through a new error factor. This factor refines the average hop distance calculation and reduces cumulative errors in node localization. Next, the original BKA is improved by incorporating Gaussian mutation, opposition-based learning, and an optimal individual shake strategy. These modifications augment the local optima avoidance and accelerate the convergence rate. The results of the proposed algorithm are compared with similar methods, comprising ICSFG, TSHH, RANSAC, and IAGA models. The comparison results showed that the proposed algorithm performed better than competitors in wireless sensor network localization.
Likewise, Al Janabi and Kurnaz presented a novel localization mechanism for IoT networks by integrating the Grasshopper Optimization Algorithm (GOA) with the DV-Hop algorithm [11]. The main goal of the authors in this paper was to improve localization accuracy in wireless sensor networks. In the proposed method, the hops between unknown nodes and three beacons are obtained to address scenarios with fewer than three GPS-enabled beacons. In the following, the position of objects is estimated according to the hops and calculated distances from those beacons. After that, the GOA is used to optimize the estimated positions by generating candidate solutions around the positions computed by the DV-Hop with the aim of minimizing localization error. In this regard, each position vector is considered a grasshopper in the swarm. The proposed algorithm is compared with algorithms like PSO, Firefly, and the Butterfly Optimization algorithm, and the results indicate a lower localization error.
Moreover, Singh et al. recruited the Reptile Search Algorithm and Locally Linear Embedding (LLE) algorithm and provided a new localization framework for WSN-assisted IoT networks [20]. In the proposed framework, the RSA optimizes node positions iteratively to minimize localization error in noisy/dynamic WSN environments. Then, the LLE, a manifold learning technique, reduces high-dimensional sensor data into a lower-dimensional space while preserving local node relationships. Simulation results demonstrate a reduction in localization error and computational complexity for varying sensor nodes and fixed anchor nodes. Also, the results indicate lower energy consumption in different scenarios.
In [4], Barshandeh et al. presented a new positioning system for locating objects in 3D Internet of Things networks. The proposed method is based on the Received Signal Strength Indicator (RSSI) algorithm, Slime Mold Algorithm (SMA), and Equilibrium Optimizer (EO). In the first step of the proposed algorithm, the initial position of the IoT devices is estimated by the RSSI algorithm. Then, the accuracy of the initial estimated locations is improved by the hybrid optimization algorithm. In the hybrid algorithm, the SMA algorithm is corrected and then combined with the EO algorithm through a learning mechanism. In each iteration of the algorithm, the learning strategy specifies which equation updates the solution. Additionally, a neighborhood search strategy is presented to improve the search process. To evaluate the merit of the proposed algorithm, the results obtained on fifteen 3D Internet of Things networks have been compared with the AEO, AO, EO, MRFO, SMA, WOA, PSO, and SSA algorithms. The experimental results indicate the superiority of the proposed method over competing algorithms.
In a similar research, Barshandeh et al. presented a novel localization method for two-dimensional IoT networks using the DV-Hop [5]. In this method, after obtaining the initial location of unknown network nodes, the accuracy of the initially detected locations is improved by a hybrid meta-heuristic algorithm. In the proposed hybrid meta-heuristic algorithm, the Tunicate Swarm Algorithm (TSA) is combined with Harris Hawks Optimization (HHO). Next, the resulting hybrid algorithm is improved by a new phase. The experiments conducted in this research are divided into two parts. In the first part, the efficiency of the improved hybrid optimization algorithm is evaluated using 50 benchmark functions. In the second part, the efficiency of the proposed positioning algorithm has been tested on twenty-eight Internet of Things networks. The obtained results of the proposed method are compared with the HHO, TSA, GWO, SCA, WOA, and CSA algorithms using node location error, average location error, and location error variance measures.
Also, in [21], Liu et al. presented a new localization algorithm called OTKL-BSA to estimate the location of nodes in underwater wireless sensor networks. In the OTKL-BSA, the underwater nodes are divided into two levels. Next, the clock asynchronous localization system (LS-AC) algorithm estimates the position of base layer nodes. To remove the dependence of the range-based strategy on active nodes and address the energy consumption issue, LS-AC performs state-based monitoring within the network by relying on asynchronous clocks. Also, using optimal topology and knowledge learning, a backtracking search algorithm (BSA) is introduced in this paper. The BSA has been used to eliminate the lack of dispersion of solutions and the imbalance of exploration and exploitation capabilities. In addition, the Gray Wolf Optimizer (GWO) algorithm was improved in this study by a hunting step size mechanism. To evaluate the efficiency of the OTKL-BS method, its results are compared with SLMP, MCL-MP, MP-PSO, and MGP.
Moreover, Soundararajan et al. have proposed a meta-heuristic-based positioning algorithm and a multi-hop routing method called MONL-MRPMS for Wireless Sensor Networks (WSN) [22]. The main goal of the authors in this research was to optimize energy consumption in WSN networks with a mobile sink by accurately locating network nodes. In the MONL-MRPMS algorithm, the Coyote Optimization Algorithm (COA), in which the Euclidean distance is considered as the fitness function, is used for the positioning of unknown nodes. Additionally, the Seagull Optimization Algorithm (SGO) has been used in the MONL-MRPMS to select the most optimal multi-hop routes between clusters. In the proposed method, a mobile sink is also considered, which optimizes the energy consumption in the network by adjusting the routes when the sink moves.
Additionally, Fute et al. recruited Particle Swarm Optimization (PSO) and Tabu Search (TS) and presented a hybrid positioning algorithm called FPSOTS for wireless sensor networks [23]. In FPSOTS, the PSO algorithm is improved by the strategies of the TS. In this regard, each particle in PSO uses TS to determine its best neighbor. By selecting the best neighbors, the convergence rate of the solutions towards the global optimum can be increased. In addition, the limit and performance checking procedures are added to the PSO so that only the best solutions contribute to the update of other solutions. In the FPSOTS, the initial position of unknown nodes is estimated by the received signal strength indicator (RSSI) and trilateration algorithms. In the experimental section, the results of the proposed method have been compared with the HPSOVNS, NS-IPSO, ECS-NL, and GTOA algorithms in terms of localization accuracy and convergence criteria.
Additionally, in [24], Cao et al. presented a hybrid swarm intelligence-based localization algorithm for Non-Line-of-Sight (NLoS) environments. Their proposed method recruits the Time Difference of Arrival (TDOA) and Angle of Arrival (AOA) algorithms. The TDOA and AOA are improved in this paper by the Crow Search Algorithm (CSA) and Particle Swarm Optimization (PSO). In this regard, the hybrid CSA and PSO algorithm solves the non-linear equations of the TDOA and AOA algorithms. Also, to obtain a better fitness value during the optimization process and increase the localization accuracy, the fitness function is modified based on maximum likelihood estimation. Then, an initial solution is periodically added to the population to increase the convergence of the algorithm and optimize the global search, causing a reduction in the diversity of the population. The authors have compared the results of their proposed method with the results of the Taylor, Chan, PSO, CPSO, and CSA algorithms.
Despite the progress made by existing metaheuristic-based localization algorithms, several research gaps remain unaddressed. Most current methods—such as GWO-based, SMA-based, or other single-optimizer frameworks—tend to exhibit premature convergence and limited adaptability when applied to large-scale or three-dimensional IoT environments. These algorithms, while fast in convergence, often lose population diversity during the later search phases, leading to suboptimal accuracy. While effective for exploration, these approaches often converge unstably and exploit local areas weakly, leading to inconsistent performance in diverse network conditions. Furthermore, many hybrid or improved versions of these algorithms increase computational complexity without providing consistent accuracy gains. These shortcomings highlight the need for a balanced and computationally efficient hybrid optimization strategy that can maintain diversity, avoid local stagnation, and refine position estimates precisely. To address these limitations, this study proposes the EJSARO hybrid framework, which synergistically integrates the complementary strengths of Artificial Rabbits Optimization (ARO) and Jellyfish Search (JS), augmented with Lévy-flight perturbation and a local search mechanism to enhance convergence stability and positioning accuracy in 3D IoT environments.
The above-mentioned metaheuristic-based positioning methods are compared in terms of different aspects, like initial positioner, optimizer, strengths, limitations, and published year, in Table A1.
3. Preliminaries
This section of this paper is dedicated to introducing the algorithms used in the development of the proposed method, which includes Artificial Jellyfish Search (JS), Artificial Rabbits Optimization (ARO), and Distance Vector-Hop (DV-Hop). This section also describes the network model and fitness function used in the proposed algorithm.
3.1. JS
The JS is a recently developed metaheuristic algorithm developed based on the jellyfish lifestyle in nature. Four concepts are discussed in the JS: ocean current, passive motion, active movement, and time control. This subsection briefly defines the concepts and provides their mathematical formulations; more details of the JS parts are provided in [25]. In general, jellyfish live in swarms and exhibit three movements: inside swarm movement, active motion, and passive motion. In the JS, a jellyfish swarm is generated using the chaos theory to enhance the distribution of jellyfish in the search space. Equation (1) expresses the swarm generation (initialization phase) of the JS algorithm mathematically.
where is the position of th jellyfish in the -dimensional space, contains the lower boundaries, is the upper boundaries of the problem space, and is a vector with values obtained by the Logistic chaotic map. Equation (2) presents the Logistic chaotic map.
It is noteworthy that the initial chaotic value () is between 0 and 1 and is not equal to 0, 0.25, 0.5, 0.75, or 1. Also, the is a coefficient. Figure 1 represents the distribution of the chaotic values produced by the Logistic map with and over 60 iterations.
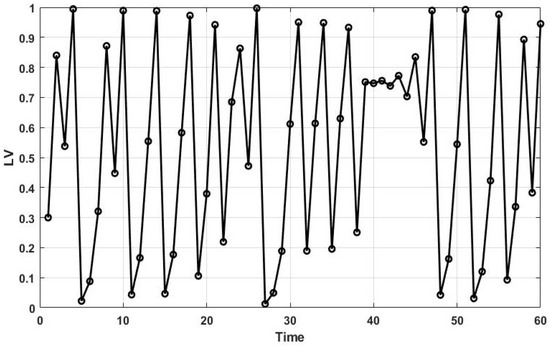
Figure 1.
The distribution of the logistic chaotic map in 60-time slots.
Once the swarm is created and the position of the jellyfish is initialized, a parameter named time control () is calculated to determine how to update the position of the jellyfish. According to the , a jellyfish decides to follow the ocean current or perform a motion within the swarm. Equation (3) presents the formula for the time control parameter.
where is the current iteration of the algorithm, is the maximum number of iterations, and is a random number in (0,1).
The ocean currents contain a significant amount of food sources that attract jellyfish. However, the amount of nutrition in the ocean current decreases over time, and the jellyfish is forced to migrate to another ocean current. The values of over 60 iterations are demonstrated in Figure 2.
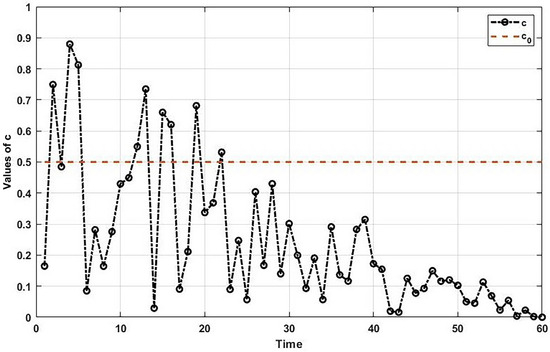
Figure 2.
Values of the time control parameter () over 60 timeslots.
Along with the time control parameter, a decision parameter named is defined in the JS, which is considered 0.5. When , the jellyfish will follow the ocean current and update its position using Equation (4).
In Equation (4), is the position of th jellyfish, is a randomly-selected number within (0,1), and is the direction of the ocean current computed as follows:
where is the jellyfish counts, is the position of the best jellyfish in the swarm, is the attraction govern factor, is the distribution coefficient, and is calculated by Equation (7).
Equation (5) can be rewritten as below:
A normal spatial distribution assumption states that jellyfish are scattered around the average position of jellyfish in the swarm. As a result, the can be redefined as follows:
where is a random number in (0,1), and is the uniform distribution, which is obtained by Equation (11).
Regarding Equations (6) and (9), the can be simplified as below:
When , the jellyfish conduct two movements within the swarm: passive and active motions. Through the passive motion, which is expressed mathematically in Equation (13), the jellyfish moves around its current position.
In Equation (13), is a parameter that specifies the movement length. With the passage of time, jellyfish perform active motion. In this motion, the jellyfish updates its position regarding the position of another jellyfish in the swarm. Each time, a jellyfish selects a random jellyfish from the current swarm as its destination. Then, the jellyfish evaluates the food resources at the destination. If the food resources in the destination point are more than in the current position, the jellyfish moves towards the destination. Otherwise, the jellyfish moves against the destination position. Equation (14) expresses the active motion of JS mathematically.
where is the position of the target jellyfish and is the food amount of the destination point. The pseudocode of the JS algorithm is presented in Algorithm 1.
| Algorithm 1. The pseudocode of JS |
| Inputs: number of search agents (), number of iterations (), initial value of chaotic map (), problem dimension (), and lower () and upper () boundaries of search space |
| Outputs: the best jellyfish () and its fitness () |
| // Swarm generation |
| while () |
| Initialize using Equation (1) |
| Calculate |
| end while |
| Find and |
| while () |
| while () |
| Compute using Equation (3) |
| if () |
| // Ocean current |
| Update using Equation (4) |
| else |
| if () |
| // Passive motion |
| Update using Equation (13) |
| else |
| // Active motion |
| Calculate by Equation (15) |
| Update using Equation (14) |
| end if |
| end if |
| Update |
| end for |
| Update and |
| end while |
| Return and |
3.2. ARO
The ARO is a new born metaheuristic optimization algorithm developed based on the survival strategies of rabbits in nature. The ARO algorithm has adequate exploration and exploitation capabilities. Hence, despite its newness, it has been applied to various problems and has manifested promising results. This subsection introduces the different parts of the ARO and their mathematical formulations; more details about its motivation are presented in [26]. In the ARO, two kinds of behaviors are considered: detour foraging and random hiding. The rabbits conduct these strategies alternately regarding the energy parameter. The strategies and energy parameters of ARO are explained in the following.
The ARO algorithm, like other meta-heuristic algorithms, begins by establishing an initial population. In the initial population, rabbits are randomly scattered in the problem space using Equation (16).
Afterward, the energy shrink parameter () is calculated for each rabbit to predict their movement strategy. When the energy of rabbits is high, they perform the detour foraging strategy. However, by reducing the energy of rabbits in later iterations, they accomplish the random hiding strategy. Equation (17) simulates the energy shrink parameter of rabbits.
where is the current iteration, in the maximum number of iterations, and is a random number in the interval of (0,1). The values of the energy shrink parameter over 60 iterations are illustrated in Figure 3.
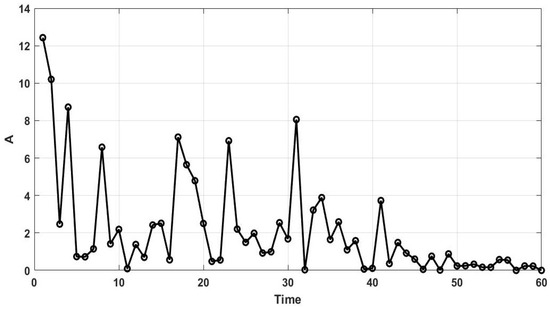
Figure 3.
Values of over 60 iterations.
Considering the values of A depicted in Figure 3, it can be observed that the energy of rabbits is high in early iterations. Therefore, the rabbits are likely to do detour foraging. As time passes, the energy of rabbits diminishes, and they prefer random hiding. To imitate this process, it is stipulated in the ARO that, when the value of A is greater than one, the rabbit performs detour foraging and updates its position by Equation (19). Through detour foraging, the rabbits explore other rabbits’ territory and prevent their territory from being detected by predators.
where is the position of the current rabbit, is the position of a randomly-selected rabbit from the search space, and . The is a random number generated with a normal distribution, , , is the dimension of the search space, is the ceiling function, , , and are random numbers between (0,1). Also, the function returns a random permutation.
Likewise, in the condition that A is less than or equal to one, the second approach, random hiding, is adopted. In nature, rabbits dig different holes in their nests to hide and avoid predators. Through random hiding, the rabbits select a random burrow to hide. Through this behavior, the position of a rabbit in the ARO is updated using Equation (27).
In Equation (27), is a random number in (0,1) and is the randomly chosen borrow around the nest. In the ARO, a burrow is obtained as follows:
where the is a burrow dug by the th rabbit, is a random within (0,1), , and is a random number acquired by the normal distribution. Algorithm 2 represents the pseudocode of the ARO algorithm.
3.3. DV-Hop
The DV-Hop is a well-known range-free positioning method, which is used in much research and real-life applications. The DV-Hop is one of the most popular positioning methods due to the simplicity of its implementation, proper execution time, no need for additional equipment, and less energy consumption [27]. This positioning algorithm estimates the position of unknown wireless objects regarding anchors (devices with prior position information) [28,29]. It is worth noting that the equations presented in the rest of this subsection are an adapted version of the basic DV-Hop for 3D environments.
| Algorithm 2. The pseudocode of ARO |
| Inputs: number of search agents (), number of iterations (), problem dimension (), and lower () and upper () boundaries of search space |
| Outputs: the best rabbit () and its fitness () |
| //Initialization |
| while () |
| Initialize by Equation (16) |
| Calculate |
| end for |
| Find and |
| while () |
| while () |
| Calculate energy shrink () by Equation (17) |
| if |
| //Detour foraging |
| Update using Equation (19) |
| else |
| //Random hiding |
| Update using Equation (27) |
| end if |
| Compute |
| end for |
| Update and |
| end while |
| Return and |
The first phase of the DV-Hop algorithm is determining the minimum number of hops between unknown devices and anchors. In this regard, each anchor broadcasts a packet containing its position information to its neighbors. This packet also includes a hop-counter field with an initial value of one. Unknown devices in the anchor’s coverage area receive this packet. After storing the anchor’s location information, these devices add one unit to the value of the hop-counter field and rebroadcast the new packet to the nearby devices. Unknown devices that have received more than one packet from one or more anchors keep only the packet with the lowest hop count and drop the remaining packets. At the end of the initial phase, all unknown devices recognize their minimum hop counts from the anchors. This process is demonstrated in Figure 4.
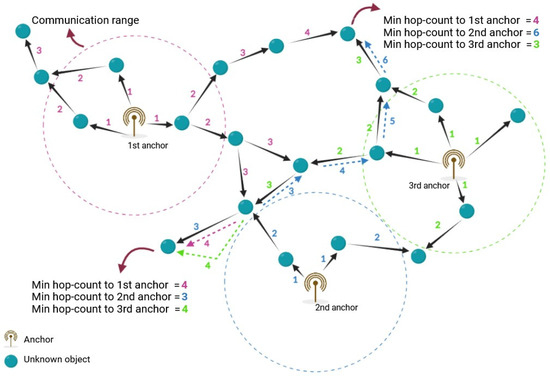
Figure 4.
Determining the hop counts in the DV-Hop.
Once the minimum hop counts from the unknown devices to the anchors are acquired, the average hop count is calculated using Equation (32) in the second phase.
In Equation (32), is the average hop count of th anchor, is the coordinate of th anchor, is the minimum hop count between th and th anchors, and is the number of deployed anchors. In the following phase, the distance of unknown objects from the anchors is computed by Equation (33), where is the distance of th unknown object from the th anchor and is the minimum number of hops between the th unknown object and th anchor.
Eventually, the position of unknown objects is estimated using the multilateration method in the fourth phase. In the Multilateration, k equations are formed as follows for each unknown wireless object. In Equation (34), is the coordinates of the th anchor, is the coordinates of the th unknown object, and is the distance between the th anchor and th unknown object. Equations formed in Equation (34) can be expanded as Equation (35). The expanded equations can also be expressed by matrix rules as Equations (36)–(40), where is the estimated position of th unknown object.
3.4. Network Model and Problem Definition
This section introduces the 3D IoT network utilized in the current paper and defines the positioning problem as an optimization problem in such networks. Like most energy-based monitoring IoT networks, wireless objects in the network adopted in the present paper are unaware of their geographic location because they are deployed randomly. These wireless objects are called unknown objects and are denoted as below:
where the is the position of th unknown object and is the number of unknown objects in the network. Unknown objects in the network can be of various types, including surveillance cameras, thermal sensors, motion sensors, humidity-measuring devices, fire detectors, etc.
Moreover, a small number of devices are deployed in the network, and their locations are specified using GPS or manual configuration. These devices are named anchors and are stated as follows:
where is the number of anchors in the network. Additionally, this paper assumes that both unknown objects and anchors in the network model are equipped with devices capable of sending and receiving data within a limited communication range.
The proposed algorithm uses the 3D-DV-Hop model to estimate the UO by the AD and Equation (37). However, the estimated positions by the 3D-DV-Hop have a significant error due to the imbalance of hop lengths in 3D networks. For precise estimations in 3D IoT networks, an enhanced hybrid meta-heuristic algorithm based on the JS and ARO algorithms is integrated with 3D-DV-HOP to diminish the Positioning Mean Square Error (PMSE). The PMSE of estimated positions is calculated using Equation (42).
where [ is the obtained coordinates of th unknown object and is the actual position of th unknown object. The proposed hybrid meta-heuristic, described in the following section, reduces the PMSE by modifying initial positions estimated by the 3D DV-Hop model.
4. Proposed Algorithm
In this paper, the DV-Hop algorithm is extended to be applicable to 3D environments. However, distance estimations between unknown IoT objects and anchors are still prone to error, as the step size is approximately determined by the distance between anchors. Also, the environmental noises and their destructive effect on the transmitted packets cause the estimated locations to contain a significant error, especially in large-scale 3D IoT networks. In this regard, several methods have been proposed to improve positioning accuracy, among which methods based on meta-heuristic algorithms demonstrated favorable results. Therefore, in this research, by taking advantage of JS and ARO algorithms, an enhanced hybrid meta-heuristic algorithm called EJSARO has been introduced and integrated with 3D DV-Hop. This section introduces the different parts of the proposed EJSARO algorithm and expresses its implementation details. A high-level representation of the proposed positioning framework is illustrated in Figure 5.
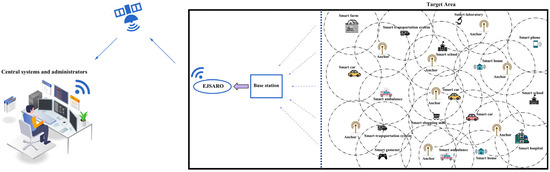
Figure 5.
An overview of the proposed positioning framework.
In the beginning, the desired target environment is investigated, and the number and type of IoT devices and anchors are specified and distributed randomly in the desired area. Next, the exact location of the anchors is determined by GPS, and the distance between them is calculated. Afterward, the number of hops between the unknown nodes and the anchors is obtained by the identification packets broadcast by the anchors. Once the hop counts between the anchors are acquired, the average hop size is computed by dividing the distance between the anchors by the hop counts between them. Then, the distance of each unknown device to the anchors is calculated by multiplying the number of hops to the anchor by the average step size. Eventually, the initial position of the unknown nodes is estimated by forming and solving Equation (34). In the following, the EJSARO rectifies the initially estimated positions and improves the location information.
In the EJSARO, the JS and ARO are hybridized, and several improvements are applied to improve searchability and local departure capability. Also, it has been made to avoid the significant increase in complexity and execution time while improving the capabilities of EJSARO. For instance, the time control parameter (Equation (3)), ocean current (Equation (4)), and passive motion (Equation (13)) are omitted from the original JS to lighten EJSARO, and the active motion (Equation (14)) is redefined as below:
Likewise, the energy shrink parameter (Equation (17)) and random hiding strategy (Equation (27)) are removed in the EJSARO, and the Detour foraging strategy (Equation (19)) is modified as follows:
Equations (43) and (44) enhance the exploitation capability of the EJSARO. In this case, the solutions are prone to becoming trapped in local optima. As a result, a local departure mechanism has been provided in EJSARO to detect and depart the solutions trapped in local optimums. In the local departure mechanism, a counter is defined for each solution. Every time the solution is updated, if the new position of the solution is better than its current position, the position of the solution is updated, and its counter is reset. Otherwise, the movement is not taken into account, and the previous position of the solution is preserved, and the counter of that solution is increased by one unit. Once the counter of a solution exceeds a predefined threshold, the position of the solution is initialized by the 3D DV-Hop algorithm.
The threshold value has a significant effect on the efficiency of the local departure mechanism and can adjust the exploration and exploitation capabilities. However, if small values are considered as the threshold, the exploration increases abnormally, and the convergence of the algorithm is weakened. Also, if large values are assigned to it, the exploitation and convergence of the algorithm are increased, but the solutions remain in the local optima for a while, or in the worst case, cannot leave the local optima. Consequently, the threshold should be adjusted carefully. After the solutions are updated, their boundaries are checked and rectified using Equation (45).
In the following, a new phase has been introduced to EJSARO to strengthen its search capabilities as much as possible. Through this phase, the position of solutions is updated using the Levy flight function as below:
where is the value produced by the Levy flight, is the normal distribution function with a standard deviation of and , and is a coefficient. Also, the is equals to 1, and the is obtained using Equation (51).
where . The local departure mechanism is also recalled in this phase after updating the solutions by the Levy flight.
As the positioning of unknown IoT objects intentionally requires exploitation, the exploitation ability has been augmented more than exploration in EJSARO. In this situation, the best solution found so far in the population has a notable impact on population guiding and the final result achieved by the algorithm. Accordingly, a local search procedure is provided in EJSARO to improve the best solution. In the local search procedure, the best solution found so far in the population is updated by Equation (52), and the greedy selection process is adopted.
where is a random number in (0,1), is the current iteration, in the maximum number of iterations, and and are randomly selected solutions from the current population. Algorithm 3 exposes the pseudocode of the proposed local search procedure in the EJSARO.
| Algorithm 3. The pseudocode of the proposed local search procedure |
| Inputs: search agents (), the best search agent (), current iteration (), maximum number of iterations (), and lower () and upper () boundaries of search space |
| Outputs: the best search agent () and its fitness () |
| for () |
| Select and randomly from the X |
| Calculate using Equation (53) |
| Obtain using Equation (52) |
| Check and rectify the using Equation (45) |
| Compute by Equation (42) |
| if |
| end if |
| end for |
| Return and |
The is a parameter that controls the local search cycle. The larger the value of φ is, the better the final solution of the algorithm will be, but the execution time will increase relatively. The value of φ is considered 5 in the EJSARO. It is also worth mentioning that, in EJSARO, solutions are initialized by Equation (40) instead of Equations (1) and (16). Algorithm 4 presents the pseudocode of the proposed EJSARO-based positioning framework.
| Algorithm 4. The pseudocode of the EJSARO |
| Inputs: number of search agents (), number of iterations (), problem dimension (), and lower () and upper () boundaries of search space |
| Outputs: the best search agent () and its fitness () |
| //Initialization |
| ; ; |
| while () |
| Initialize by Equation (39) |
| Calculate using PMSE formulated by Equation (42) |
| ; ; |
| end for |
| Find and |
| //Optimization |
| while () |
| while () |
| ; |
| if |
| //Modified Detour foraging (ARO) |
| Calculate R, Z, and L using Equations (20), (21), and (23), respectively |
| else |
| //Modified Random hiding (JS) |
| Compute using Equation (15) |
| end if |
| //Check and rectify the new solution |
| Calculate using Equation (46) |
| = |
| //Elitism (greedy selection) |
| Compute using Equation (42) |
| if |
| ; ; ; |
| else |
| end |
| if |
| ; ; |
| end |
| //Levy flight-based motion |
| Calculate using Equation (48) |
| //Check and rectify the new solution |
| = |
| //Elitism (greedy selection) |
| Compute using Equation (43) |
| if |
| ; ; ; |
| else |
| end |
| if |
| ; ; |
| end |
| //Local departure mechanism |
| if |
| Reset and reinitialize using Equation (39) |
| end |
| end for |
| //Proposed local search procedure |
| Improve using Equation (52) and the proposed local search |
| end while |
| Return and |
5. Simulation Results
To substantiate the strengths of the proposed 3D positioning framework and the effectiveness of the contributions, numerous simulations are conducted on twenty-four 3D IoT networks with varying specifications. The results are presented and discussed in the following subsections. It is noteworthy that all experiments are performed on the same system with the specifications provided in Table 1.

Table 1.
Running environment specifications.
Considering that the metaheuristic-based methods are random in nature, each positioning method was applied twenty-five times independently to the networks, and the obtained results were recorded. Then, the set of algorithm results is compared numerically and graphically by multiple criteria.
5.1. Competitors
To affirm the advantages of the proposed positioning method over the existing methods, the results obtained by the EJSARO are compared with nine similar methods. In this regard, the 3D DV-Hop algorithm is integrated with the following algorithms, which are among the most reliable, accurate, and widely used metaheuristic algorithms, and are considered competitors of the EJSARO: Artificial Ecosystem-based Optimization [30] (AEO-based DV-Hop), Aquila Optimizer [31] (AO-based DV-Hop), Artificial Rabbits Optimization [26] (ARO-based DV-Hop), Dandelion Optimizer [32] (DO-based DV-Hop), Fox Optimizer [33] (FOX-based DV-Hop), Jellyfish Search optimizer [25] (JS-based DV-Hop), Sine Cosine Algorithm [34] (SCA-based DV-Hop), Tunicate Swarm Algorithm [35] (TSA-based DV-Hop), and Whale Optimization Algorithm [36] (WOA-based DV-Hop). The parameters of these algorithms, along with their values, are listed in Table 2, which are the suggested values by their developers.

Table 2.
Parameter values of the proposed and competitor algorithms.
5.2. Evaluation Metrics
In the comparisons, the results of the EJSARO have been compared with the competitors through multiple criteria, which are defined in this subsection. For each criterion, the results of the algorithms are initially compared numerically using the statistical criteria (the best and worst achieved solutions and the average, median, and standard deviation of the set of obtained results). Next, the results are visually plotted by the box plot diagrams. In the following, the impact of the investigated characteristic of the network is evaluated through bar and line graphs. Additionally, the convergence rate of the algorithms is visually compared.
The first evaluation criterion is the Mean Squared Error (MSE) (fitness function) and is formulated by Equation (54), where is the number of unknown IoT devices, and and are the actual and estimated positions of th unknown IoT device, respectively.
The second criterion is the Node Localization Error (NLE), which measures the positioning error of every single unknown IoT object. Equation (55) expresses the mathematical formulation of the NLE.
The third evaluation criterion is Average Localization Error (ALE) presented mathematically in Equation (56), where is the communication range. Likewise, the Localization Error Variance (LEV) is considered the last evaluation criterion formulated mathematically by Equation (57).
5.3. Networks
In this paper, to rigorously evaluate the performance of the proposed framework, sixteen 3D IoT network environments were carefully designed. These networks were constructed to represent a broad spectrum of deployment scenarios to test different aspects of the proposed framework, including scalability, robustness, and localization accuracy. The design parameters—such as network area, node density, anchor count, and communication range—were varied systematically across networks. Each network configuration was developed to reflect a distinct real-world deployment scenario, ranging from compact indoor-like setups to large-scale outdoor IoT systems.
In each scenario, sensor nodes were randomly distributed within the 3D environment using a uniform random generator, ensuring diverse topological structures and avoiding any bias in position estimation. Anchor nodes were also randomly placed but kept fixed across repeated runs of the same scenario to maintain comparability of results. This randomization strategy allows the algorithm to be evaluated over multiple heterogeneous topologies, reflecting real-world IoT deployments where node positions are rarely uniform or deterministic. Table 3 presents the specifications of the IoT networks.

Table 3.
Characteristics of IoT networks.
Consequently, the experiments are organized in four scenarios; in each scenario, only one aspect of the network is variable, and the other characteristics are fixed. The following subsections provide the simulation results by scenario.
5.4. Networks with Different Deployment Area Size
This subsection presents the first set of experiments performed to evaluate the performance of the positioning algorithms. In these experiments, four three-dimensional IoT networks (Network 1 to Network 4) have been designed, and algorithms are applied to them to localize unknown objects. Networks 1 to 4 contain 200 IoT devices with unknown positions and 50 beacons with known locations. Also, the communication range (R) in these networks is set to 70 m. However, the dimensions of these networks are considered , , , and cubic meters, respectively. Table 4 provides the statistical results of the algorithms in terms of MSE (fitness value). Additionally, Figure 6 and Figure 7 illustrate the box plots of algorithm results and the best convergence of algorithms in Networks 1 to 4, respectively.

Table 4.
The statistical results of the algorithms obtained on Networks 1 to 4 regarding the MSE.
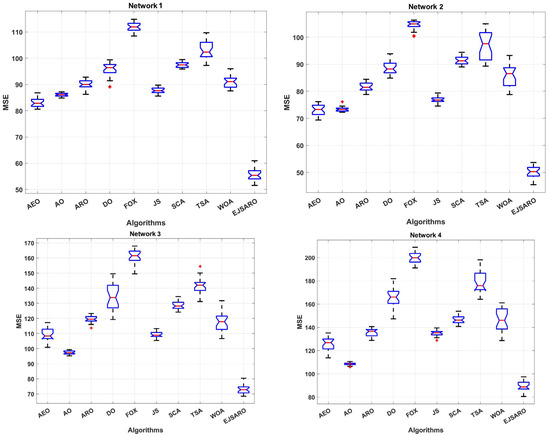
Figure 6.
The box plot diagrams of the MSE results on Networks 1 to 4 (the red points are the outliers).
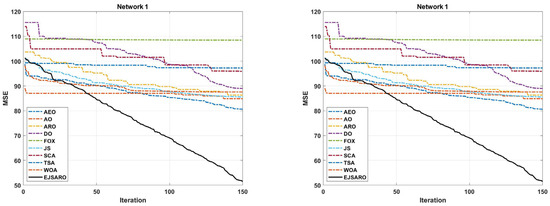
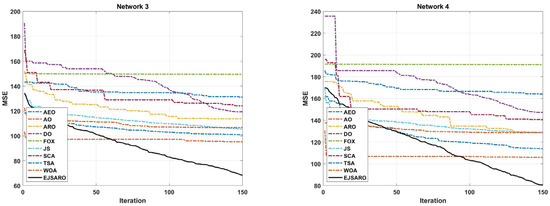
Figure 7.
The best convergence of the algorithms in Networks 1 to 4.
According to Table 4 and Figure 6, which provide the statistical and box plot diagrams of results in terms of the MSE, the EJSARO outperformed the AEO, AO, ARO, DO, FOX, JS, SCA, TSA, and WOA algorithms in Networks 1 to 4. In these networks, the best and worst predictions of the EJSARO and the average and median of the obtained solutions are better than the compared algorithms. The box plots demonstrate that the set of solutions obtained by the EJSARO is much better than the other metaheuristic-based positioning models.
It is noteworthy that the standard deviation of the EJSARO is more than competitors; nonetheless, a more accurate examination of box plots indicates that the EJSARO fluctuates in fewer MSE values. Additionally, the convergence diagrams of the algorithms, depicted in Figure 7, assert that the EJSARO reached lower MSE values in less time in Networks 1 to 4. Also, it can be concluded that the proposed model is able to obtain a continuous reduction pattern, which indicates its good performance in avoiding the local optima. Such a reduction requires high adequacy in both exploration and exploitation capabilities; in the case of a weakness in each of these two phases, the algorithm easily becomes stuck in local optimality. To provide a deeper examination, the best NLE values obtained by the algorithms are plotted in Figure 8.
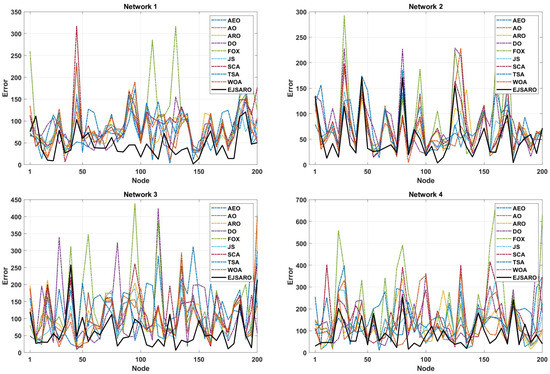
Figure 8.
The NLE of algorithms in Networks 1 to 4.
According to the NLE graphs illustrated in Figure 8, it can be observed that the proposed model has achieved a lower error rate in most of the unknown objects. Also, the NLE peaks of the EJSARO’s estimations are much lower than similar algorithms in Networks 1 to 4, which reveals the higher reliability of the EJSARO and its excellent capability in discovering the position of network objects. In the following, the best ALE values of the algorithms on Networks 1 to 4 are compared in Figure 9.
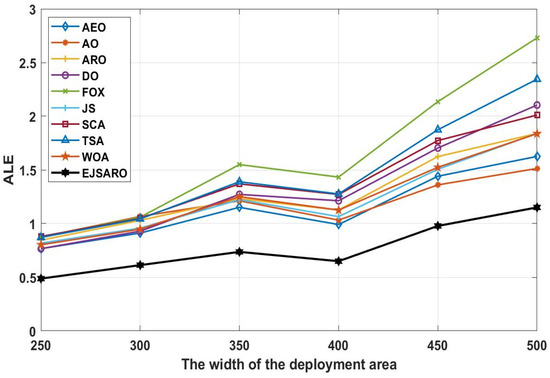
Figure 9.
The best ALE values obtained by the algorithms on Networks with different scales.
Regarding the line graphs depicted in Figure 9, it can be noticed that the proposed positioning model has achieved much better results than other compared algorithms. This good performance has remained constant even with the increase in the size of the environment. Therefore, it can be claimed that the EJSARO has been able to obtain better results than similar models in environments of different sizes. Also, in these experiments, the FOX-based localization model had the worst performance among the algorithms. Moreover, it is obvious that the ALE and positioning errors grow with an increment in the size of the environment. The best LEV graphs are illustrated in Figure 10.
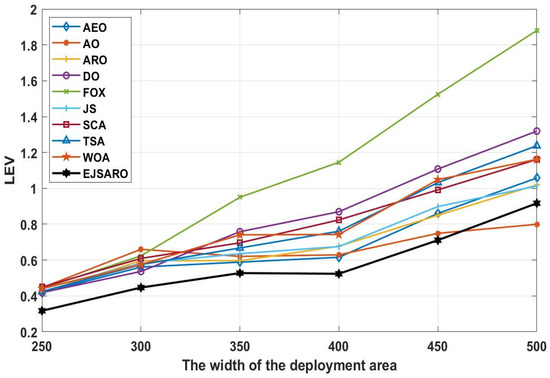
Figure 10.
The best LEV values obtained by the algorithms on Networks with different scales.
Considering the line graphs of Figure 10, it can be witnessed that the EJSARO positioning method performed well and achieved promising results. Thus, it can be asserted that the EJSARO outperformed its competitors regarding the LEV metric. However, by increasing the width of the environment to 500, the AO algorithm has been able to make a great leap and achieve better results than the compared algorithms. The most important thing is that, although the proposed model has not been able to have the best performance in a network of , it has still been able to maintain its search capabilities, which shows that the proposed algorithm has good search capabilities. Likewise, the LEV values represented in Figure 10 affirm the ALE and MSE results and indicate that the positioning error is raised by expanding the size of the target area. Regarding the numerical and visual MSE, NLE, ALE, and LEV results, it can be claimed that the EJSARO algorithm can estimate the position of IoT objects better than similar models, including AEO, AO, ARO, DO, FOX, JS, SCA, TSA, and WOA algorithms.
5.5. Networks with Different No. of IoT Devices
In the second set of experiments, the effect of the number of unknown devices on the efficiency of positioning algorithms has been investigated. In this regard, four more three-dimensional IoT networks, Networks 5 to 8, have been designed, in which 150, 200, 250, and 300 IoT devices with unknown positions are deployed. In these networks, the deployment environment is set to , and the communication range is considered 50. Likewise, 40 beacons have been placed in these networks. The statistical results of the algorithms regarding the MSE are given in Table 5. To provide a more detailed comparison, the box plot diagrams and the best convergence of the algorithms on Networks 5 to 8 are plotted in Figure 11 and Figure 12, respectively.

Table 5.
The statistical results of the algorithms obtained on Networks 5 to 8 regarding the MSE.
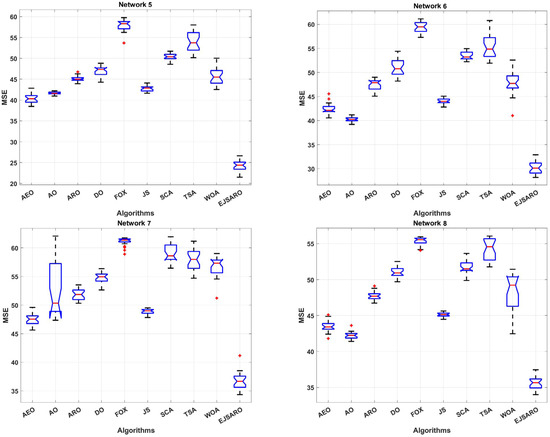
Figure 11.
The box plot diagrams of the MSE results on Networks 5 to 8 (the red points are the outliers).
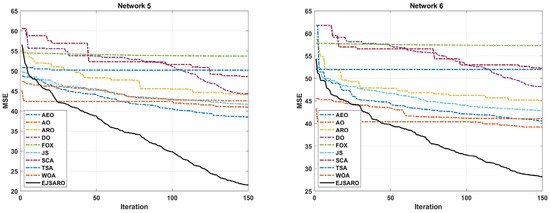
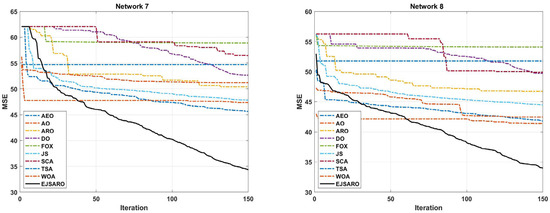
Figure 12.
The best convergence of the algorithms in Networks 5 to 8.
Regarding the numerical results of Table 5, it can be observed that the EJSARO algorithm acquired the best performance among the competitors in terms of the MSE metric. In Networks 5 to 8, the best and worst solutions and the average and median of the obtained solutions by the EJSARO are significantly better than the others. Therefore, it can be asserted that the exploration and exploitation capabilities of the EJSARO are better than the AEO, AO, ARO, DO, FOX, JS, SCA, TSA, and WOA algorithms. Regarding the standard deviation, which indicates the coherence of the set of solutions found by algorithms, other algorithms have better STD than the EJSARO. Nonetheless, by examining the box plot diagrams depicted in Figure 11, it is obvious that the set of solutions reached by the EJSARO is much better than the others and fluctuates in lower MSE values. It is worth mentioning that the AO algorithm took the second-best in most of the experiments conducted on Networks 5 to 8. Also, the box plots demonstrate that the range of solutions achieved by the EJSARO is significantly better than other compared algorithms regarding the MSE.
According to the convergence curves illustrated in Figure 12, the EJSARO has an extraordinary convergence rate compared to competing algorithms. The convergence rate of the EJSARO algorithm in Networks 5 to 8 is continuous and sharp, which exhibits its excellent exploration and exploitation capabilities and the appropriate balance between them. It is also evident that the EJSARO algorithm does not have an MSE in successive iterations, which indicates its high ability to escape and not become trapped in local optima. Therefore, it can be concluded that the proposed algorithm has performed well in generating diverse solutions, trying to escape the trap of local optimality by generating new solutions and exploring more of the problem space. In the following, the NLE results of the algorithms on Networks 5 to 8 are provided in Figure 13.
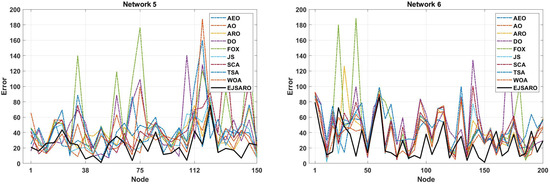
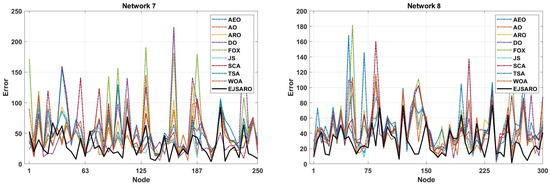
Figure 13.
The NLE of algorithms in Networks 5 to 8.
The NLE line graphs of Figure 13 manifest that the amount of positioning error in EJSARO is much lower than that of AEO, AO, ARO, DO, FOX, JS, SCA, TSA, and WOA algorithms. This means that the proposed algorithm can estimate the position of unknown network objects more accurately, which leads to a reduction in error and an increase in the accuracy of the positioning model. To examine the positioning algorithm more accurately, the best ALE values of the algorithms are presented visually in Figure 14.
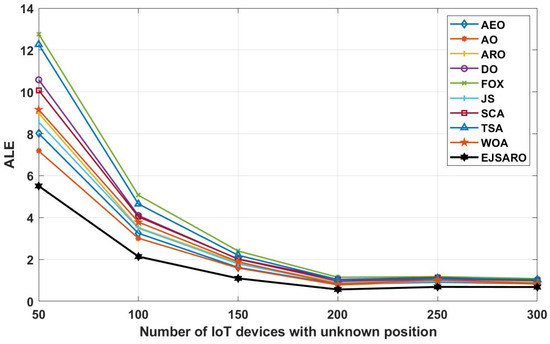
Figure 14.
The best ALE values obtained by the algorithms on Networks with different IoT devices.
The graphs of Figure 14 reveal that the proposed algorithm was able to achieve better ALE values by making more accurate estimates. Also, these graphs demonstrate that with the increase in the number of network objects, the amount of positioning error decreases, the main reason for which is the rise in the number of hops and the more accurate calculation of the average hop size. To more accurately evaluate the efficiency of the positioning algorithms and compare the set of their predictions, their results are compared in terms of the LEV, and the results of the algorithms on Networks 5 to 8 are plotted in Figure 15.
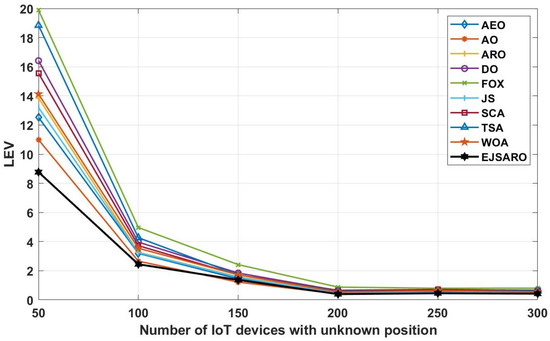
Figure 15.
The best LEV values obtained by the algorithms on Networks 5 to 8.
The curves depicted in Figure 15 indicate that the best solution obtained for Networks 5 to 8, regarding the LEV criterion, belongs to the EJSARO method, except for the network with 150 IoT devices, where the AO algorithm surpassed the competitors. Additionally, the curves illustrated in Figure 15 confirm the results of Figure 14 and assert that the positioning error decreases with the increase in the number of network objects. The main reason for reducing the error by increasing the number of network objects is the more accurate calculation of the average hop size. With the increase in the number of network objects, the objects’ minimum number of hops to the anchors/beacons is calculated more accurately, and as a result, the hop length is estimated with less error, which leads to a more accurate position estimation.
5.6. Results on Networks with Different Numbers of Anchors
This subsection discloses the results of the experiments conducted to evaluate the proficiency of the positioning algorithms in networks with different numbers of anchors/beacons. For this purpose, four 3D IoT networks (labeled Networks 9 to 12) are developed with 30, 35, 40, and 45 location-aware beacons, respectively. Then, the algorithms have been applied to estimate the position of unknown nodes. It is worth mentioning that in these networks, the deployment area is considered , the communication range is fixed to 50 m, and the number of unknown devices is set to 200. The statistical results of the algorithms in terms of MSE are presented in Table 6, box diagrams in Figure 16, and the convergence curves in Figure 17.

Table 6.
The statistical results of the algorithms on Networks 9 to 12 regarding the MSE.
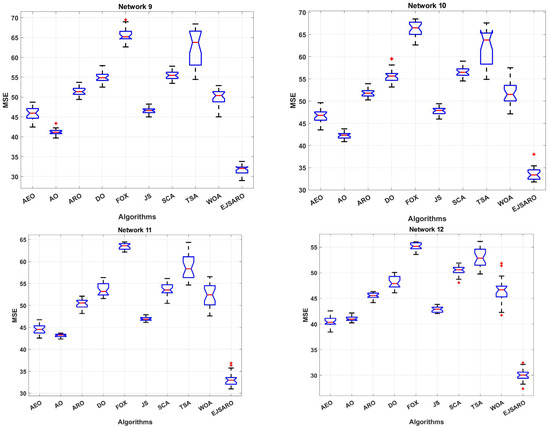
Figure 16.
The box plot diagrams of the MSE results on Networks 9 to 12 (the red points are the outliers).
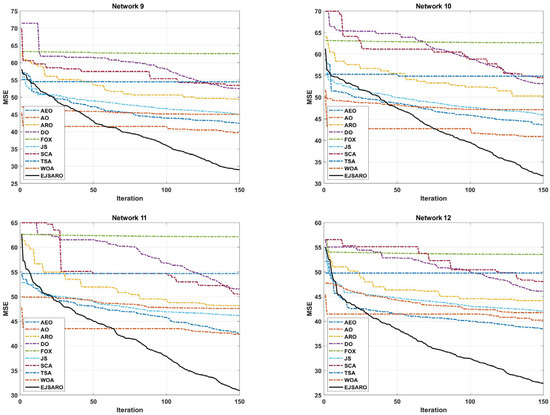
Figure 17.
The best convergence of the algorithms in Networks 9 to 12.
The statistical results of Table 6 state that the best and worst MSE values obtained by the EJSARO algorithm are better than similar algorithms, including the AEO, AO, ARO, DO, FOX, JS, SCA, TSA, and WOA algorithms. Also, these results affirm that the proposed algorithm outperforms the competing methods in terms of mean, median, and standard deviation of MSE values.
According to the box diagrams in Figure 16, it is evident that the MSE of the set of predictions made by the EJSARO algorithm is significantly better than the competing algorithms. These diagrams also show that the EJSARO can produce superior solutions in independent executions than similar algorithms, thus proving its higher reliability.
In terms of convergence rate, the curves of Figure 17 indicate that the proposed algorithm had a consistent convergence and was able to reach a more optimal solution in a shorter period of time, which is due to its high exploration and exploitation capabilities. In addition, the continuous reduction in the convergence curve of the EJSARO method demonstrates that this algorithm did not fall into the trap of local optimums or was able to get out of them in an adequate way. For a more detailed comparison of the algorithms, the NLE values are provided visually in Figure 18.
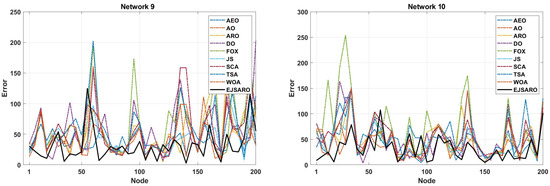
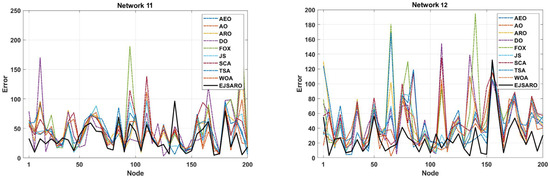
Figure 18.
The NLE of the algorithms in Networks 9 to 12.
The deep examination of NLE curves illustrated in Figure 18 indicates that the EJSARO has achieved a lower error rate in almost most of the nodes in Networks 9 to 12. In some nodes, the proposed model could not achieve a good error rate. However, considering that the EJSARO model has a good ability to cover more than 90% of the nodes in reducing the error rate, the poor performance in some nodes can be ignored. In the following, the positioning models are compared regarding the ALE, and the results are presented in Figure 19.
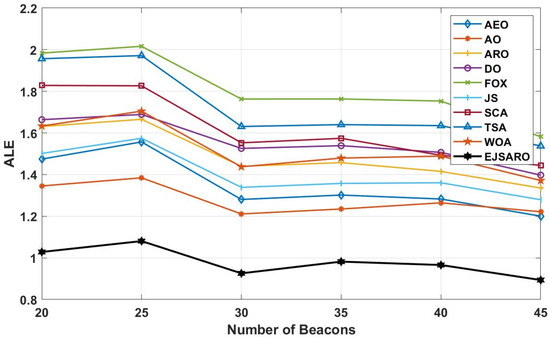
Figure 19.
The best ALE values obtained by the algorithms on Networks 9 to 12.
According to the ALE results provided in Figure 19, the proposed model has performed significantly better than other meta-heuristic-based localization models in this series of experiments conducted on Networks 9 to 12. In these networks, the AO took second place regarding the ALE evaluation metric. The huge difference between the results of the proposed algorithm and other algorithms indicates its higher capabilities in estimating the position of the network’s unknown objects in different conditions. The FOX algorithm has achieved the worst results in these networks regarding the ALE and has performed poorly compared to other positioning algorithms. Also, the curves of Figure 19 assert that the ALE values reduce by increasing the number of anchors/beacons in the networks. In the last part of the third set of experiments, Figure 20 provides the LEV results of the algorithms on Networks 9 to 12.
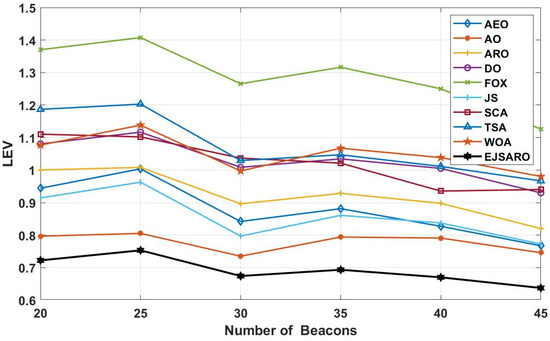
Figure 20.
The best LEV values obtained by the algorithms on Networks 9 to 12.
Considering the LEV results reported in Figure 20, the EJSARO algorithm has achieved better results than AEO, AO, ARO, DO, FOX, JS, SCA, TSA, and WOA algorithms and has surpassed them. In these networks, the worst performance is related to the FOX algorithm, which has taken last place. In these graphs, it is clear that the best predictions obtained by the EJSARO algorithm for Networks 9 to 12 are enormously better than the rest of the algorithms. In addition, these graphs reveal that with the increase in the number of anchors/beacons, the average accuracy of the models increases, the main reason for which is the generation of more equations in Equation (35), which leads to more precise initial position estimation by Equation (40).
5.7. Networks with Different Communication Range
The DV-Hop and the proposed algorithm are a range-free method and are able to locate objects with any communication range. Nonetheless, the communication range affects the hop-counting and distance estimation process. Consequently, four more three-dimensional IoT networks, in which the devices have different communication ranges, are designed in this subsection. The communication range is set to 45, 50, 55, and 60 m in Networks 13 to 16, respectively. Also, the network size, number of unknown IoT devices, and beacon count are equal to , 200, and 40, respectively. The statistical results of the positioning algorithms obtained on Network 13 to Network 16 in exposed in Table 7. Likewise, Figure 21 demonstrates the box plots of the results of algorithms, and Figure 22 compares the convergence rate of algorithms in these networks.

Table 7.
The statistical results of algorithms obtained on Networks 13 to 16 regarding the MSE.
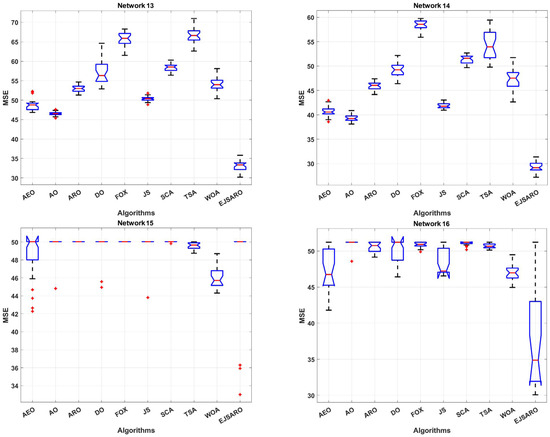
Figure 21.
The box plot diagrams of the MSE results on Networks 13 to 16 (the red points are the outliers).
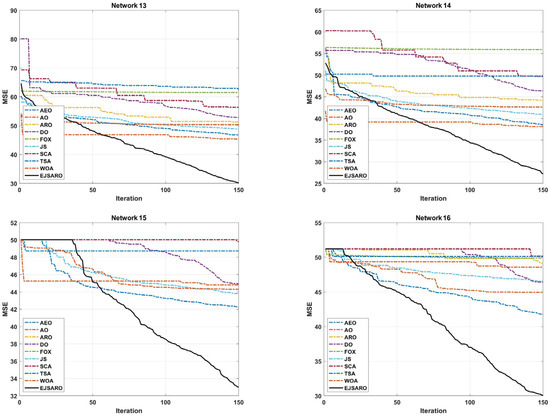
Figure 22.
The best convergence of the algorithms in Networks 13 to 16.
The statistical results of Table 7 and the box diagrams of Figure 21 express that the EJSARO algorithm outperformed its competitors in terms of best, worst, mean, median, and standard deviation of MSE and achieved better results. Additionally, the results exhibit that the set of estimations made by the EJSARO algorithm in independent executions is at much lower levels of MSE, which reveals its superiority and remarkable search capabilities. However, the worst, median, and average MSE values obtained by the WOA algorithm on Network 15 are better than other algorithms. Nevertheless, the best solution for this network is still found by the proposed method. In Network 16, the worst solution found by the WOA algorithm is better than other algorithms, but the EJSARO algorithm has surpassed its competitors in terms of statistical criteria and reached a lower MSE.
The convergence curves of Figure 22 indicate that the best solutions for Networks 13 to 16 have been found by the EJSARO. Additionally, these curves represent that the convergence rate of the proposed method is significantly better than the convergence rate of AEO, AO, ARO, DO, FOX, JS, SCA, TSA, and WOA algorithms. Consequently, it can be concluded that the EJSARO has been able to overcome its competitors and provide more optimal solutions in less time. Similarly, the NLE values of the algorithms are presented in Figure 23 to provide a more in-depth comparison.
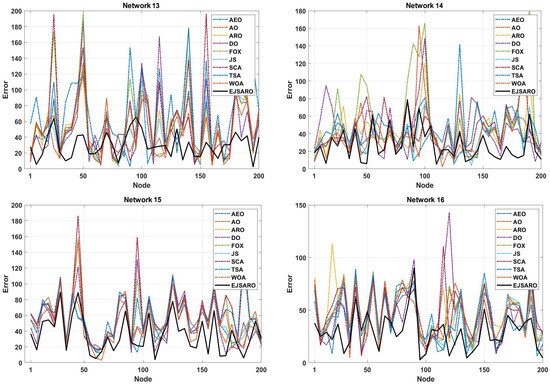
Figure 23.
The NLE of the algorithms in Networks 13 to 16.
The NLE diagrams of Figure 23 show that the localization error rate in the EJSARO method is lower than in similar algorithms. It is also clear in these graphs that the proposed method has been able to calculate the position of individual nodes more appropriately and achieve a lower average localization error. In the following, the results of the algorithms are compared by the ALE criterion to provide a more accurate evaluation; the comparison results are presented graphically in Figure 24.
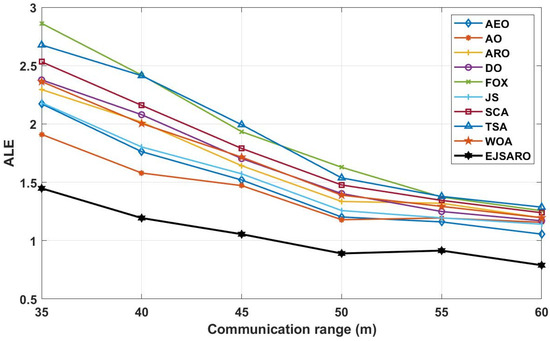
Figure 24.
The best ALE values obtained by the algorithms on Networks 13 to 16.
According to the ALE results reported in Figure 24, it is noticeable that the EJSARO method performed better than the competing algorithms and reached lower ALE values, which indicates that the proposed algorithm is capable of accurate calculation of the location of unknown objects in the network through its unique capabilities. As a result, considering that the proposed algorithm has reached the optimal results in Networks 13 to 16 regarding the ALE values, it can be claimed that the EJSARO algorithm has also surpassed its competitors. In addition, the graphs of Figure 24 reveal that the communication range has a notable impact on the efficiency of the models, and the accuracy of the models increases with the increase in the communication range. The major reason for this is to obtain the minimum hop counts more precisely by increasing the . Figure 25 also compares the results of the algorithms on Networks 13 to 16 visually regarding the LEV metric.
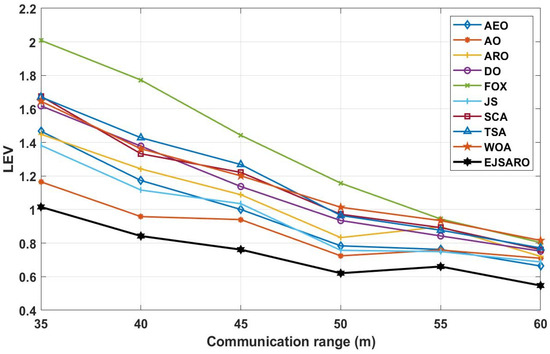
Figure 25.
The best LEV values obtained by the algorithms on Networks 13 to 16.
The diagrams in Figure 25 declare that the EJSARO has reached more optimal values regarding the LEV criteria in Networks 13 to 16 and outperformed its competitors, including AEO, AO, ARO, DO, FOX, JS, SCA, TSA, and WOA algorithms. Also, the graphs of Figure 25, in addition to indicating the superiority of EJSARO over its competitors, confirm the results of Figure 24 and reveal that the error of the models decreases with the increase in the communication range, the main reason for which was explained earlier.
5.8. Quantitative Performance Evaluation
To provide a clear and quantitative measure of the proposed framework’s effectiveness, in this subsection, a quantitative evaluation is presented to rigorously demonstrate the effectiveness of the proposed framework. To achieve this, the relative improvement of the EJSARO algorithm in comparison to competitor methods was carefully computed and analyzed. The relative improvement ratio (RI) for each comparative method is calculated as follows:
where denotes the mean square error value obtained by a baseline algorithm, and represents the corresponding result achieved by the proposed method. This ratio expresses how much EJSARO reduces the positioning error relative to each benchmark method. A higher value indicates a more significant accuracy improvement.
Table 8 presents the improvement ratios of the EJSARO over nine state-of-the-art localization algorithms across sixteen 3D IoT environments. It is noteworthy that the RI is calculated by the best MSE values obtained by the algorithms.

Table 8.
The RI values of the EJSARO over the competitors.
As can be observed from Table 8, the EJSARO consistently achieves a high positive RI value across various experimental conditions. This consistent achievement of a high positive RI value is a strong indicator of its higher accuracy in large-scale 3D localization tasks.
6. Discussion
Extensive experimentation was undertaken, focusing on a set of sixteen distinct three-dimensional IoT networks, each characterized by unique specifications and configurations. We rigorously analyzed the comprehensive collection of numerical and visual data generated by these experiments. To benchmark the performance of the proposed EJSARO method, a multitude of comparisons were performed against several state-of-the-art techniques. The comparative analysis included the assessment of algorithms such as AEO, AO, ARO, DO, FOX, JS, SCA, TSA, and WOA. The evaluation process considered a diverse range of criteria, specifically MSE (Mean Squared Error), NLE (Normalized Localization Error), ALE (Average Localization Error), and LEV (Localization Error Variance). Based on the thorough examination of both the numerical outcomes and visual representations derived from these experiments, as well as the extensive comparative studies conducted across the aforementioned evaluation metrics, a definitive conclusion can be drawn.
The higher performance of our proposed EJSARO algorithm can be attributed to the complementary hybridization of ARO and JS. In this integration, the ARO provides strong global exploration during early iterations, while the JS enhances local exploitation in later phases. Also, the Lévy flight perturbation provides occasional long and short jumps, which prevent premature convergence and local optima. Moreover, the local search phase fine-tunes the best search agent to further reduce the MSE. The combination of these mechanisms results in a strong optimization approach that is capable of optimizing the nonlinear and multimodal nature of 3D localization problems.
Furthermore, the relative improvement ratio test is conducted based on the MSE values obtained by the algorithms on sixteen 3D IoT environments. The results reveal that the proposed EJSARO algorithm achieves accuracy improvements of 30.38%, 29.78%, 38.26%, 41.78%, 50.90%, 34.98%, 43.72%, 45.54%, and 35.65% over the AEO, AO, ARO, DO, FOX, JS, SCA, TSA, and WOA algorithms, respectively. These quantitative improvements provide evidence that reveals the effectiveness of the combination of ARO, JS, Lévy flight, and the local search mechanism within the EJSARO.
In some low-complexity test environments, the WOA marginally outperformed EJSARO. This behavior is observed in test environments with smooth fitness surfaces and low-dimensional search spaces, where WOA’s encircling and spiral movements can achieve fast convergence without much need for exploration. In the more challenging 3D localization scenarios, the WOA tends to lose diversity and become trapped in local optima, whereas the EJSARO maintains high stability and accuracy due to its adaptive exploration and exploitation capabilities. Overall, the combination of JS, ARO, Lévy flight, and local search strategy enables EJSARO to deliver a consistent and significant improvement in 3D IoT localization accuracy compared to other existing metaheuristic-based positioning models.
7. Conclusions and Future Directions
The current paper proposes an innovative positioning framework named EJSARO for three-dimensional Internet of Things (3D IoT) environments. The proposed framework is range-free and requires no additional equipment, such as the Global Positioning System (GPS). In the initial step of the EJSARO, the original Distance Vector-Hop (DV-Hop) is extended to be applicable in 3D IoT networks and to count the hops between network devices. The 3D-DV-Hop is then combined with the multilateration method to estimate the initial position of unknown IoT devices. In the second phase, the Jellyfish Search (JS) and Artificial Rabbits Optimization (ARO) algorithms are modified and lightened. Following this, the modified JS and ARO are hybridized in a complementary manner. The resulting hybrid algorithm is enhanced with a Levy-flight-based intermediate phase. Since the best search agent has a remarkable impact on population guiding and the final result, a local search mechanism is also introduced to exploit the so-far found best search agent. The hybrid meta-heuristic algorithm is then employed to enhance the initially estimated positions.
To assess the potency of the EJSARO, sixteen three-dimensional IoT networks with different specifications are designed. The networks are organized into four categories regarding the varying parameters. The EJSARO is then applied to the networks to detect the position of unknown IoT devices. The results of the EJSARO are compared with the 3D-DV-Hop-based AEO, AO, ARO, DO, FOX, JS, SCA, TSA, and WOA algorithms numerically and visually in terms of Mean Squared Error (MSE), Node Localization Error (NLE), Average Localization Error (ALE), and Localization Error Variance (LEV). In performance evaluations, the results of algorithms are compared by the statistical metrics, including the best and worst achieved solutions and the average, median, and standard deviation of the obtained set of solutions. Likewise, the results are compared using the box plot diagrams and convergence rate curves. The impact of the network’s parameters is also investigated and discussed.
For future studies, the impact of other range-free or range-based methods in the initialization phase can be investigated. The proposed framework can also be adapted for mobile IoT and EC environments.
Author Contributions
Conceptualization, G.L.; data curation, H.J.; formal analysis, N.E.; investigation, H.J. and S.G.; methodology, S.B.; project administration, G.L. and N.E.; resources, S.K.; software, S.K.; supervision, S.B., G.L. and N.E.; visualization, S.K. and S.G.; writing—original draft, H.J. and S.G.; writing—review and editing, S.B. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The original contributions presented in this study are included in the article. Further inquiries can be directed to the corresponding author.
Conflicts of Interest
The authors declare no conflicts of interest.
Appendix A
The appendix compares the existing metaheuristic-based localization methods explored in Section 2. The comparison is presented in Table A1.

Table A1.
A brief comparison of existing metaheuristic-based positioning/localization methods.
Table A1.
A brief comparison of existing metaheuristic-based positioning/localization methods.
| Ref. | Optimizer | Positioner | Env. | Evaluation Metrics | Strengths | Weak Points | Year |
|---|---|---|---|---|---|---|---|
| [18] | GWO | DV-Hop | 2D IoT | Normalized average localization error |
|
| 2025 |
| [19] | BKA | DV-Hop | 2D WSN | Everage localization error Running time Convergence rate |
|
| 2025 |
| [11] | GOA | DV-Hop | 2D WSN | Localization error Runtime Convergence rate |
|
| 2024 |
| [20] | RSA | LLE | 2D IoT | Localization error Energy consumption Time |
|
| 2024 |
| [4] | SMA EO | RSSI | 3D IoT | Localization Mean square error Wilcoxon signed-rank test |
|
| 2023 |
| [5] | TSA HHO | DV-Hop | 2D IoT | Average localization error Node localization error Localization error variance |
|
| 2022 |
| [21] | GWO | Clock asynchronous localization system | 3D UWSN | Location accuracy Location coverage |
|
| |
| [22] | COA SOA | - | 2D WSN | Localization error Energy consumption |
|
| 2023 |
| [23] | PSO TS | RSSI | 2D WSN | Localization accuracy Convergence |
|
| 2023 |
| [24] | CSA PSO | TDOA AOA | NLoS | Node positioning accuracy Convergence rate |
|
| 2023 |
References
- Birhanie, H.M.; Adem, M.O. Adem, Optimized task offloading strategy in IoT edge computing network. J. King Saud Univ.-Comput. Inf. Sci. 2024, 36, 101942. [Google Scholar] [CrossRef]
- Tsai, Y.-H.; Hsu, T.-C. An Effective Deep Neural Network in Edge Computing Enabled Internet of Things for Plant Diseases Monitoring. In Proceedings of the IEEE/CVF Winter Conference on Applications of Computer Vision, Waikoloa, HI, USA, 3–8 January 2024; p. 695. [Google Scholar]
- Bey, M.; Kuila, P.; Naik, B.B.; Ghosh, S. Quantum-inspired particle swarm optimization for efficient IoT service placement in edge computing systems. Expert Syst. Appl. 2024, 236, 121270. [Google Scholar] [CrossRef]
- Barshandeh, S.; Koulaeizadeh, S.; Masdari, M.; AbdollahZadeh, B.; Ghasembaglou, M. A learning-based metaheuristic administered positioning model for 3D IoT networks. Appl. Soft Comput. 2023, 136, 110113. [Google Scholar] [CrossRef]
- Barshandeh, S.; Masdari, M.; Dhiman, G.; Hosseini, V.; Singh, K.K. A range-free localization algorithm for IoT networks. Int. J. Intell. Syst. 2022, 37, 10336–10379. [Google Scholar] [CrossRef]
- Niranjan, M.; Singh, B. RSSI-Based Hybrid Approach for Range-Free Localization Using SA-PSO Optimization. In Advances in Distributed Computing and Machine Learning, Proceedings of ICADCML 2023, Odisha, India, 15–16 January 2023; Springer: Berlin/Heidelberg, Germany, 2023; p. 487. [Google Scholar]
- Bi, J.; Zhao, M.; Yao, G.; Cao, H.; Feng, Y.; Jiang, H.; Chai, D. PSOSVRPos: WiFi indoor positioning using SVR optimized by PSO. Expert Syst. Appl. 2023, 222, 119778. [Google Scholar] [CrossRef]
- Booranawong, A.; Sengchuai, K.; Buranapanichkit, D.; Jindapetch, N.; Saito, H. RSSI-based indoor localization using multi-lateration with zone selection and virtual position-based compensation methods. IEEE Access 2021, 9, 46223–46239. [Google Scholar] [CrossRef]
- Cao, Y.; Xu, J. DV-Hop-based localization algorithm using optimum anchor nodes subsets for wireless sensor network. Ad Hoc Netw. 2023, 139, 103035. [Google Scholar] [CrossRef]
- Pourkabirian, A.; Kooshki, F.; Anisi, M.H.; Jindal, A. An accurate RSS/AoA-based localization method for internet of underwater things. Ad Hoc Netw. 2023, 145, 103177. [Google Scholar] [CrossRef]
- Janabi, S.M.A.; Kurnaz, S. A new localization mechanism in IoT using grasshopper optimization algorithm and DVHOP algorithm. Wirel. Netw. 2024, 30, 5465–5485. [Google Scholar] [CrossRef]
- Liu, W.; Li, J.; Zheng, A.; Zheng, Z.; Jiang, X.; Zhang, S. DV-Hop Algorithm Based on Multi-Objective Salp Swarm Algorithm Optimization. Sensors 2023, 23, 3698. [Google Scholar] [CrossRef]
- Wang, P.; Li, H.; Cai, X. 3D many-objective DV-hop localization model with NSGA3. Soft Comput. 2023, 28, 6171–6183. [Google Scholar] [CrossRef]
- Wu, Y.; Zhang, C.; Tong, L.; Shi, X. Location Optimization based on Improved 3D DV-HOP Algorithm in Wireless Sensor Networks. IEEE Access 2023, 11, 85525–85536. [Google Scholar] [CrossRef]
- Barshandeh, S.; Dana, R.; Eskandarian, P. A learning automata-based hybrid MPA and JS algorithm for numerical optimization problems and its application on data clustering. Knowl. Based Syst. 2022, 236, 107682. [Google Scholar] [CrossRef]
- Barshandeh, S.; Haghzadeh, M. A new hybrid chaotic atom search optimization based on tree-seed algorithm and Levy flight for solving optimization problems. Eng. Comput. 2021, 37, 3079–3122. [Google Scholar] [CrossRef]
- Barshandeh, S.; Piri, F.; Sangani, S.R. HMPA: An innovative hybrid multi-population algorithm based on artificial ecosystem-based and Harris Hawks optimization algorithms for engineering problems. Eng. Comput. 2022, 38, 1581–1625. [Google Scholar] [CrossRef]
- Yang, S.; Wang, X. Improved DV-HOP Localization Algorithm Based on Grey Wolf Optimization. Res. Sq. 2025; preprint. [Google Scholar]
- Sun, H.; Yang, S. Range-free localization algorithm based on modified distance and improved black-winged kite algorithm. Comput. Netw. 2025, 259, 111091. [Google Scholar] [CrossRef]
- Singh, H.; Yadav, P.; Rishiwal, V.; Jat, D.S.; Yadav, M.; Gnagwar, S. Reptile Search and LLE Based Node Localization in WSN-Assisted IoT. In Proceedings of the 2024 International Conference on Emerging Trends in Networks and Computer Communications (ETNCC), Windhoek, Namibia, 23–25 July 2024. [Google Scholar]
- Liu, H.; Xu, B.; Liu, B. A novel predictive localization algorithm for underwater wireless sensor networks. Wirel. Netw. 2023, 29, 303–319. [Google Scholar] [CrossRef]
- Soundararajan, S.; Kurangi, C.; Basha, A.; Uthayakumar, J.; Kalaivani, K.; Dhamodaran, M.; Shukla, N.K. Metaheuristic optimization based node localization and multihop routing scheme with mobile sink for wireless sensor networks. Wirel. Pers. Commun. 2023, 129, 2583–2605. [Google Scholar] [CrossRef]
- Fute, E.T.; Pangop, N.; Khöler, D.; Tonye, E. A new hybrid localization approach in wireless sensor networks based on particle swarm optimization and tabu search. Appl. Intell. 2023, 53, 7546–7561. [Google Scholar] [CrossRef]
- Cao, L.; Chen, H.; Chen, Y.; Yue, Y.; Zhang, X. Bio-Inspired Swarm Intelligence Optimization Algorithm-Aided Hybrid TDOA/AOA-Based Localization. Biomimetics 2023, 8, 186. [Google Scholar] [CrossRef]
- Chou, J.-S.; Truong, D.-N. A novel metaheuristic optimizer inspired by behavior of jellyfish in ocean. Appl. Math. Comput. 2021, 389, 125535. [Google Scholar] [CrossRef]
- Wang, L.; Cao, Q.; Zhang, Z.; Mirjalili, S.; Zhao, W. Artificial rabbits optimization: A new bio-inspired meta-heuristic algorithm for solving engineering optimization problems. Eng. Appl. Artif. Intell. 2022, 114, 105082. [Google Scholar] [CrossRef]
- Xue, D. Research of localization algorithm for wireless sensor network based on DV-Hop. EURASIP J. Wirel. Commun. Netw. 2019, 2019, 218. [Google Scholar] [CrossRef]
- Qiao, X.; Chang, F.; Ling, J. Improvement of Localization Algorithm for Wireless Sensor Networks Based on DV-Hop. Int. J. Online Biomed. Eng. (iJOE) 2019, 15, 53–65. [Google Scholar] [CrossRef]
- Yanfei, J.; Kexin, Z.; Liquan, Z. Improved DV-Hop Location Algorithm Based on Mobile Anchor Node and Modified Hop Count for Wireless Sensor Network. J. Electr. Comput. Eng. 2020, 2020, 9275603. [Google Scholar] [CrossRef]
- Zhao, W.; Wang, L.; Zhang, Z. Artificial ecosystem-based optimization: A novel nature-inspired meta-heuristic algorithm. Neural Comput. Appl. 2020, 32, 9383–9425. [Google Scholar] [CrossRef]
- Abualigah, L.; Yousri, D.; Elaziz, M.A.; Ewees, A.A.; Al-Qaness, M.A.; Gandomi, A.H. Aquila optimizer: A novel meta-heuristic optimization algorithm. Comput. Ind. Eng. 2021, 157, 107250. [Google Scholar] [CrossRef]
- Zhao, S.; Zhang, T.; Ma, S.; Chen, M. Dandelion Optimizer: A nature-inspired metaheuristic algorithm for engineering applications. Eng. Appl. Artif. Intell. 2022, 114, 105075. [Google Scholar] [CrossRef]
- Mohammed, H.; Rashid, T. FOX: A FOX-inspired optimization algorithm. Appl. Intell. 2023, 53, 1030–1050. [Google Scholar] [CrossRef]
- Mirjalili, S. SCA: A sine cosine algorithm for solving optimization problems. Knowl. Based Syst. 2016, 96, 120–133. [Google Scholar] [CrossRef]
- Kaur, S.; Awasthi, L.K.; Sangal, A.; Dhiman, G. Tunicate Swarm Algorithm: A new bio-inspired based metaheuristic paradigm for global optimization. Eng. Appl. Artif. Intell. 2020, 90, 103541. [Google Scholar] [CrossRef]
- Mirjalili, S.; Lewis, A. The whale optimization algorithm. Adv. Eng. Softw. 2016, 95, 51–67. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).