Task Offloading Algorithm for Multiple Unmanned Aerial Vehicles Based on Temporal Graph
Abstract
1. Introduction
- We establish an optimization problem aimed at minimizing the total task completion time for UAV swarms. To model this problem, we introduce a temporal graph to simulate service nodes and task sequences in computing networks. When manually constructing timestamps on the edges of a temporal graph, we determine the offset based on the proximity index ranking of conflicts at each service node and set the basic quantity based on path hops. The temporal sequence represented by the timestamps reveals the execution order among tasks.
- We transform the optimization problem into a connectivity issue in graph theory from a graph-theoretical perspective to reduce unnecessary waiting and computation resource allocation risks. Then, using total traversal time as a metric, we find the fastest temporal graph path for each UAV within the temporal graph and assign the set of service nodes included in the path to form an exclusive service network for UAV.
- We propose a two-stage matching algorithm for the task offloading strategy problem. Given the UAV service network and tasks to offload, we establish the bilateral supply–demand relationship between tasks and the service network based on task classification and dependencies. We complete the overall matching considering the actual service node locations, service node status, task types, and task offloading demands.
- We evaluate the proposed task offloading algorithm based on the exchange matching algorithm through experimental simulation. The results show that this algorithm excels in optimizing the total task completion time for a swarm of UAVs, validating its effectiveness.
2. Related Work
2.1. UAV-Based Task Offloading and Edge Integration
2.2. Task Heterogeneity and Collaborative Execution
2.3. Task Dependency-Aware Offloading
2.4. Graph-Based Modeling for Task Offloading
| Reference | Multiple UAVs-MEC | Task Completion Time | Task Classification | Task Dependency | Graph Theory |
|---|---|---|---|---|---|
| Wang et al. [7] | ✗ | ✔ | ✗ | ✗ | ✗ |
| Kang et al. [8] | ✗ | ✔ | ✗ | ✗ | ✗ |
| Sun et al. [10] | ✔ | ✔ | ✗ | ✗ | ✗ |
| Akter et al. [11] | ✔ | ✔ | ✗ | ✗ | ✗ |
| Huang et al. [12] | ✗ | ✗ | ✔ | ✗ | ✗ |
| Li et al. [13] | ✔ | ✔ | ✗ | ✗ | ✗ |
| Qi et al. [15] | ✗ | ✗ | ✗ | ✔ | ✗ |
| Fu et al. [16] | ✗ | ✔ | ✗ | ✗ | ✗ |
| Yang et al. [20] | ✗ | ✔ | ✗ | ✗ | ✔ |
| Cai et al. [23] | ✗ | ✔ | ✗ | ✔ | ✔ |
| Our paper | ✔ | ✔ | ✔ | ✔ | ✔ |
3. System Model
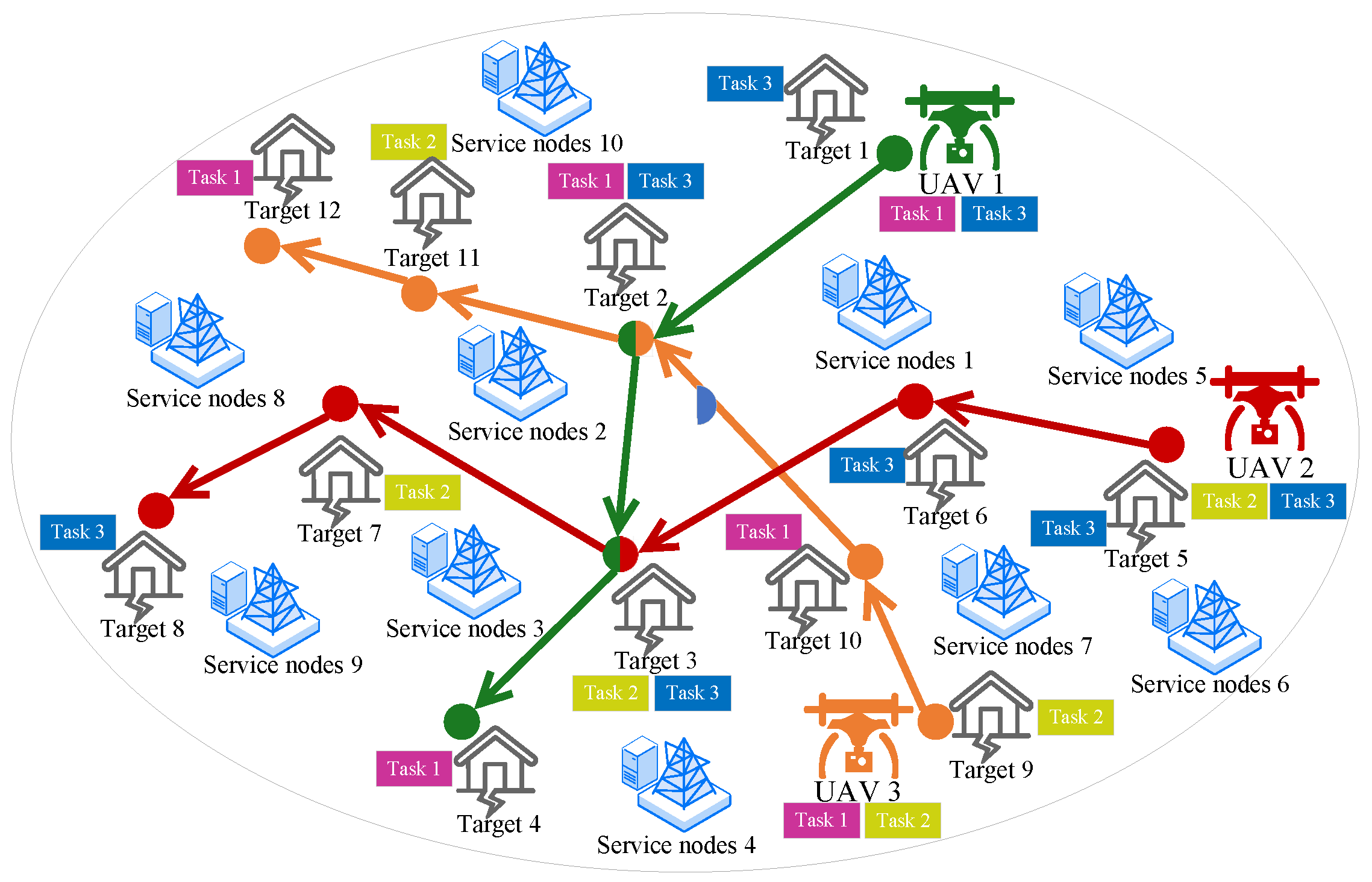
3.1. System Description
3.2. Task Offloading Model
3.3. Optimization Problem
4. Task Offloading Algorithm Based on Temporal Graph
4.1. Methodology
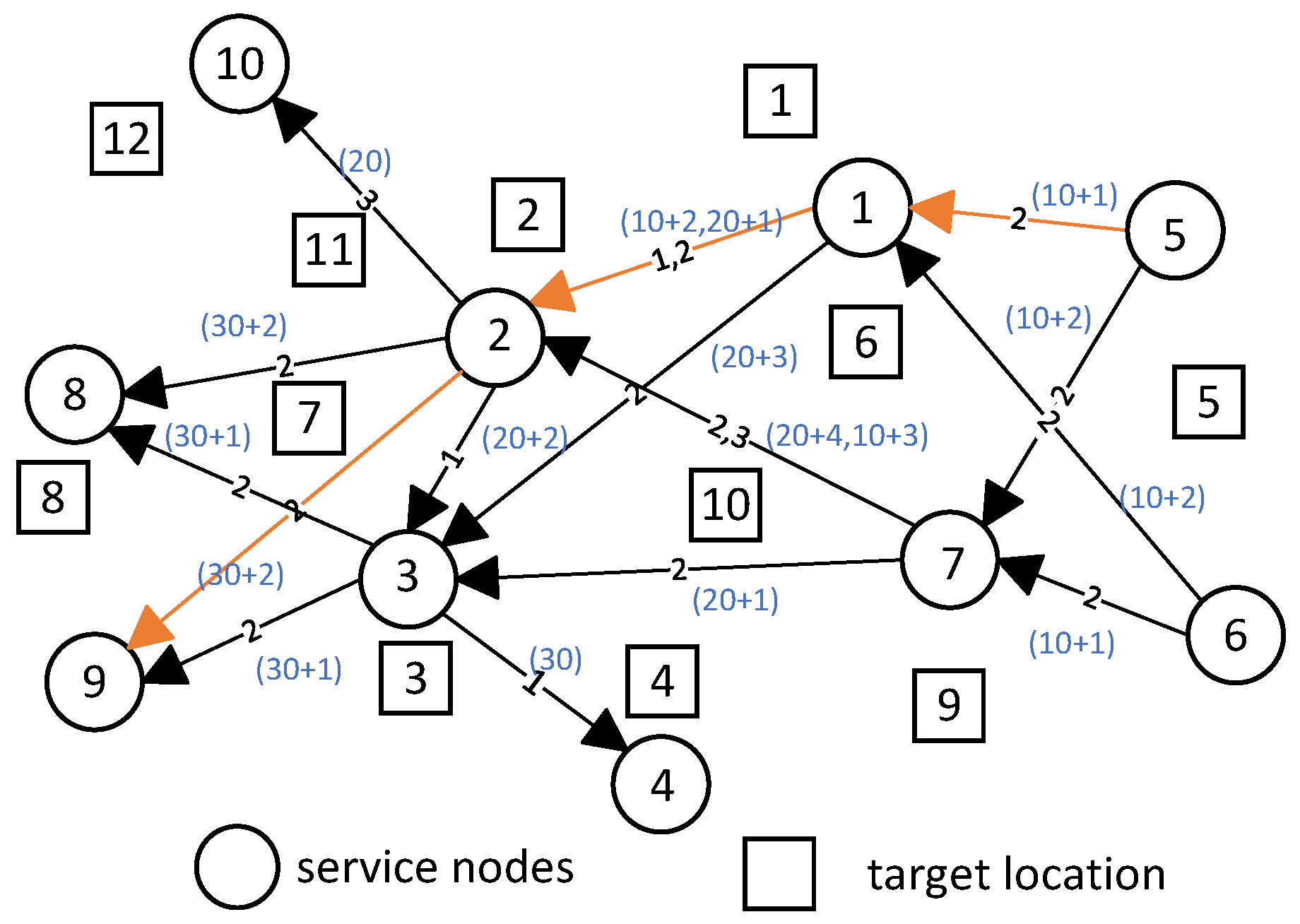
4.1.1. Establish the Temporal Graph
- The basic quantity of timestamp for edge is 10, and the offset is 1. Thus, the timestamp for edge is represented as .
- The basic quantity of timestamp for edge is the sum of the previous edge’s basic quantity, 10, and an increment of 10, resulting in 20. The offset is 1. Therefore, the timestamp for edge is represented as .
4.1.2. Establish Exclusive Service Network
4.1.3. Search Task Offloading Strategies
4.2. Algorithm Description
| Algorithm 1 Two-stage Matching Algorithm (2-stage MA) based Temporal Graph |
|
4.2.1. Establish the Temporal Graph
- Identify nodes with multiple incoming edges: When a service node has multiple incoming edges, it may need to provide computational services for multiple demands, indicating potential competition for access.
- Traverse these nodes and identify any existing conflicts. Sort these conflicts by proximity index to determine the timestamp offsets: For example, at service node 2, edge has two labels (1 and 2), and edge also has two labels (2 and 3). There are four conflict situations in total. Calculate the proximity index for each of these conflicts and sort them from smallest to largest as follows: label 2 of , label 1 of , label 3 of , and label 2 of . Therefore, their timestamp offsets are respectively 1, 2, 3, and 4. The smaller the proximity index, the higher the priority of resolving that conflict, and hence the smaller the timestamp offset.
- Identify the service nodes near each UAV’s first location point and set the corresponding outgoing edge basic quantity to 1: For instance, for UAV 2, the service nodes near its first location point are 5 and 6. Thus, the basic quantity of timestamps for these edges (labeled 2) should be set to 1. Specifically, this includes label 2 of , label 2 of , label 2 of , and label 2 of .
- Traverse the directed paths in the temporal graph based on edge labels and determine the basic quantity of timestamps for each edge: For example, considering the directed path , the basic quantities of timestamps on these edges are respectively 10, 20, and 30. Each edge’s basic quantity increases by 10 from the previous one, ensuring that the timestamps in the temporal graph path do not decrease.
4.2.2. Establish Exclusive Service Network
- Traverse each UAV’s temporal graph path based on the labels in the temporal graph.
- For a particular temporal graph path, identify as the set of service nodes near its first location point and as the set of service nodes near its last location point.
- Find the shortest path from any service node to any service node , and calculate the total traversal time for this path.
- Select the temporal graph path with the smallest total traversal time among all paths as the execution path for the UAV.
4.3. Complexity Analysis
- Temporal Graph Construction (lines 1–9): In this step, we need to compute the pairwise proximity between service nodes, form a candidate edge set, sort edges by proximity, and build graph adjacency structures. Pairwise proximity computation is . Sort E edges is (if ). Insert edge is . So, the time complexity is (if ), the space complexity is .
- Phase 1: Task → Temporal Path Matching (lines 10–18): In this step, for each task, we need to evaluate Q candidate temporal paths to select the optimal or feasible one. For D tasks, checking Q paths, each of average length L, the time complexity is (if (constant-time path evaluation), this reduces to ). Furthermore, if the algorithm needs to enumerate all simple paths in the graph, Q may grow exponentially (depending on the graph structure), making this step a bottleneck. In practice, an upper bound is often imposed on Q (for example, only taking the shortest paths), in which case Q can be treated as polynomial or constant to ensure scalability.
- Phase 2: Temporal Path → Service Node Matching (lines 17–25): In this step, for each path, we need to check available service nodes for feasibility and assign accordingly. For Q paths, each checked against S nodes, the time complexity is . Path-to-node mapping and resource status tracking require , which is the space complexity.
- Objective Evaluation and Finalization (lines 26–37): In this step, we need to compute each UAV’s completion time, take the maximum, and check optional conflict and output. The time complexity is (if ).
5. Simulation and Analysis
5.1. Parameter Settings
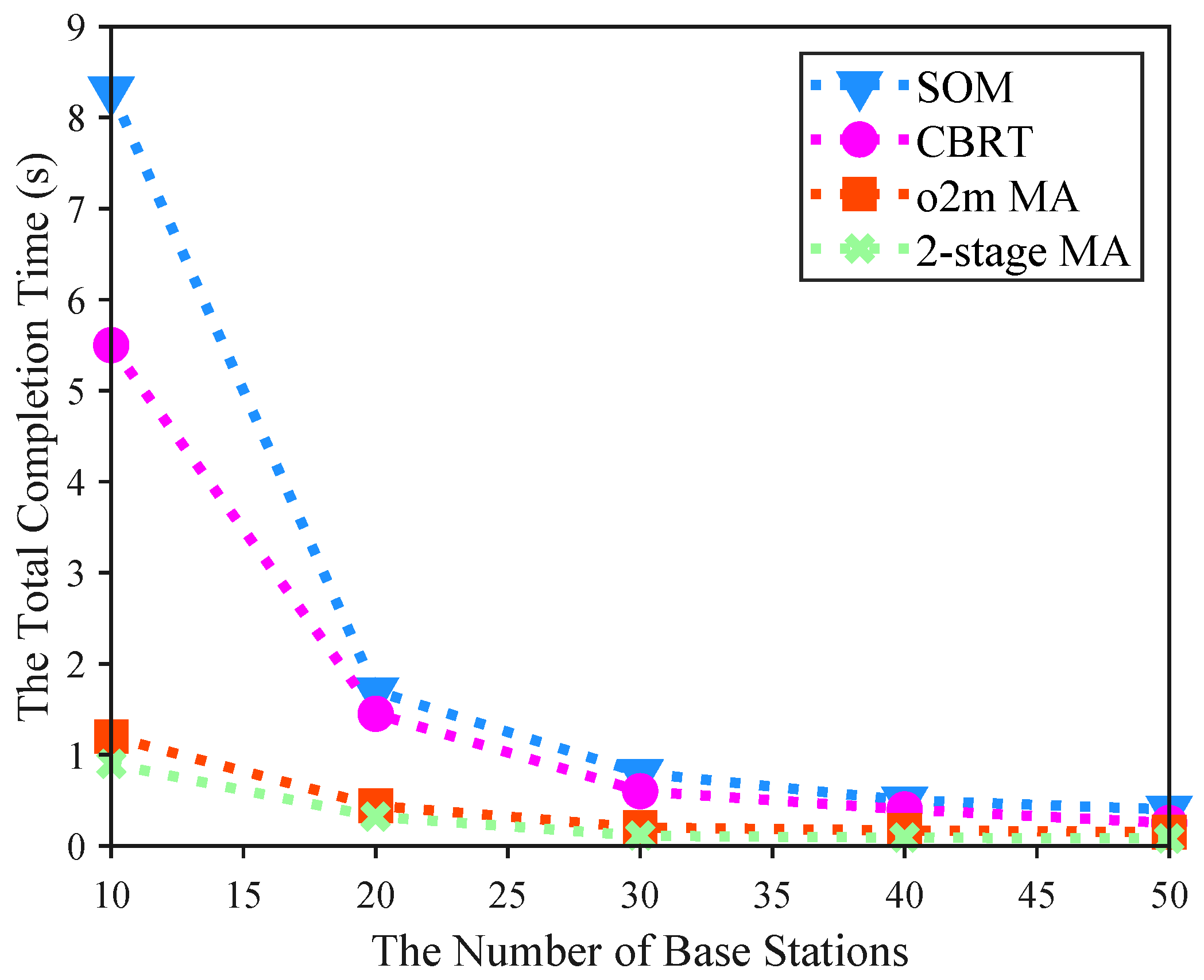
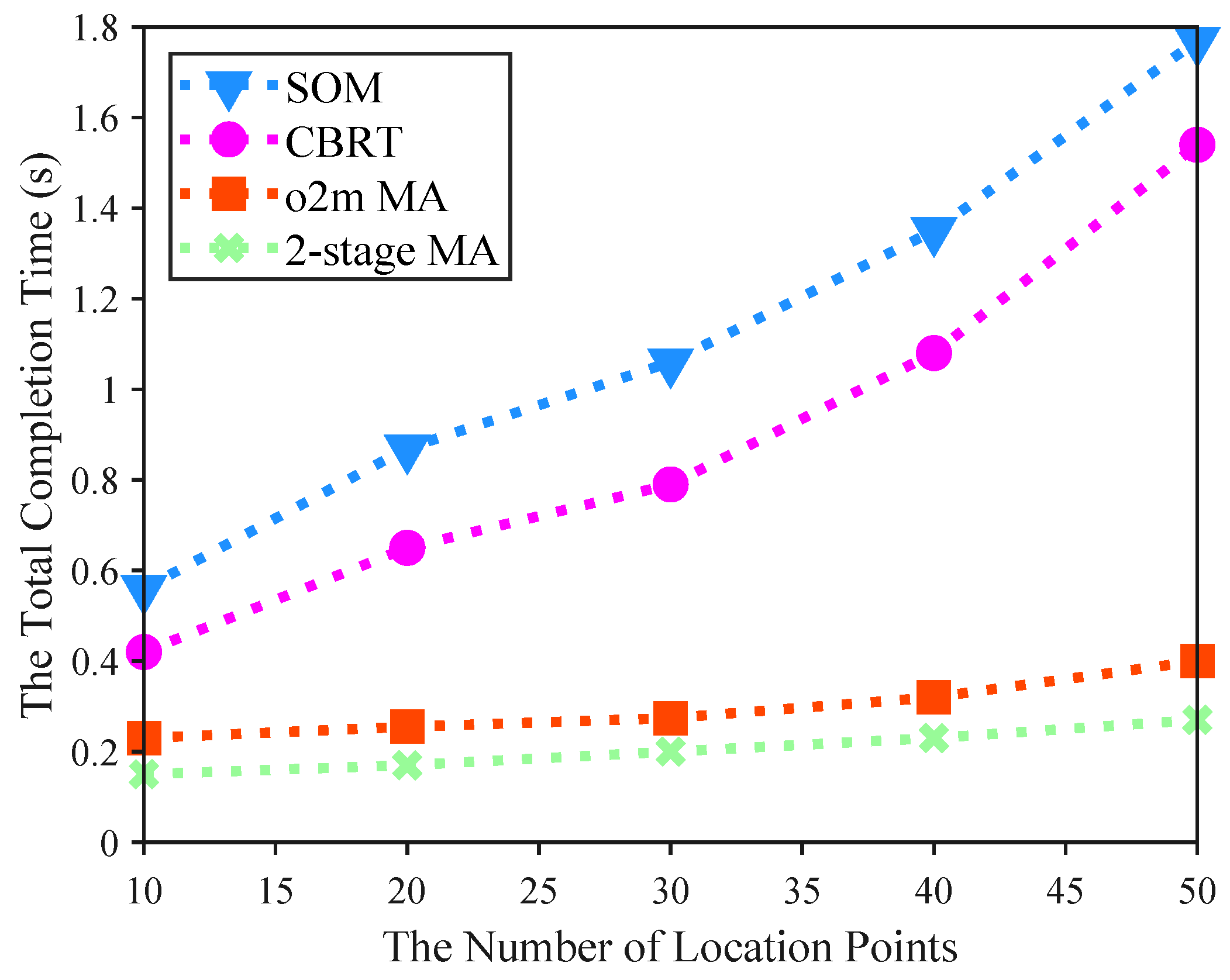
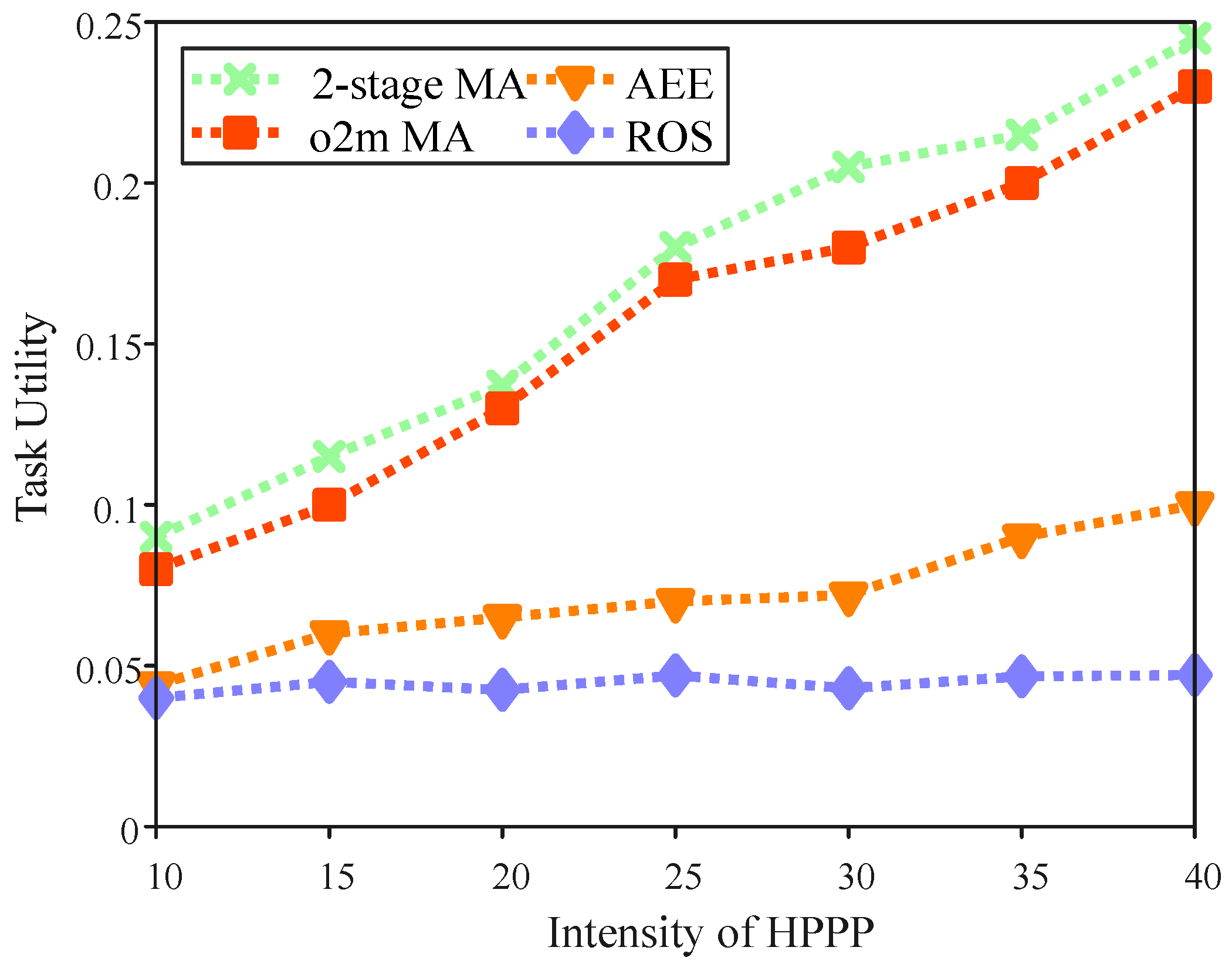
5.2. Performance Analysis
6. Conclusions
7. Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Wei, J.; Chen, M.; Wang, L.; Ren, P.; Lei, Y.; Qu, Y.; Jiang, Q.; Dong, X.; Wu, W.; Wang, Q.; et al. Status, challenges and trends of data-intensive supercomputing. CCF Trans. High Perform. Comput. 2022, 4, 211–230. [Google Scholar] [CrossRef]
- Zhang, X.; Debroy, S. Resource management in mobile edge computing: A comprehensive survey. ACM Comput. Surv. 2023, 55, 291. [Google Scholar] [CrossRef]
- Yang, P.; Xiao, Y.; Xiao, M.; Li, S. 6G wireless communications: Vision and potential techniques. IEEE Netw. 2019, 33, 70–75. [Google Scholar] [CrossRef]
- Djigal, H.; Xu, J.; Liu, L.; Zhang, Y. Machine and deep learning for resource allocation in multi-access edge computing: A survey. IEEE Commun. Surv. Tutor. 2022, 24, 2449–2494. [Google Scholar] [CrossRef]
- Chen, X.; Mao, Y.; Wang, H.; Xu, Y.; Li, D.; Liu, S.; Zhao, X. Data-driven task offloading method for resource-constrained terminals via unified resource model. IEEE Internet Things J. 2023, 10, 9703–9715. [Google Scholar] [CrossRef]
- Zhang, T.; Xu, Y.; Loo, J.; Yang, D.; Xiao, L. Joint computation and communication design for UAV-assisted mobile edge computing in IoT. IEEE Trans. Ind. Inform. 2019, 16, 5505–5516. [Google Scholar] [CrossRef]
- Wang, Y.; Chen, W.; Luan, T.H.; Su, Z.; Xu, Q.; Li, R.; Chen, N. Task offloading for post-disaster rescue in unmanned aerial vehicles networks. IEEE ACM Trans. Netw. 2022, 30, 1525–1539. [Google Scholar] [CrossRef]
- Kang, H.; Chang, X.; Mišić, J.; Mišić, V.B.; Fan, J.; Liu, Y. Cooperative UAV resource allocation and task offloading in hierarchical aerial computing systems: A MAPPO-based approach. IEEE Internet Things J. 2023, 10, 10497–10509. [Google Scholar] [CrossRef]
- Qin, L.; Zheng, Y.; Gao, Y. Enhancing UAV-based edge computing: A study on nonhovering operations and two-stage optimization strategies. Appl. Intell. 2024, 54, 10780–10801. [Google Scholar] [CrossRef]
- Sun, G.; Wang, Y.; Sun, Z.; Wu, Q.; Kang, J.; Niyato, D.; Leung, V.C.M. Multi-objective Optimization for Multi-UAV-assisted Mobile Edge Computing. IEEE Trans. Mob. Comput. 2024, 23, 14803–14820. [Google Scholar] [CrossRef]
- Akter, S.; Kim, D.Y.; Yoon, S. Task offloading in multi-access edge computing enabled UAV-aided emergency response operations. IEEE Access 2023, 11, 23167–23188. [Google Scholar] [CrossRef]
- Huang, L.; Qu, H.; Zuo, L. Multi-type UAVs cooperative task allocation under resource constraints. IEEE Access 2018, 6, 17841–17850. [Google Scholar] [CrossRef]
- Li, J.; Yi, C.; Chen, J.; Shi, Y.; Zhang, T.; Li, X.; Wang, R.; Zhu, K. A Reinforcement Learning-Based Stochastic Game for Energy-Efficient UAV Swarm-Assisted MEC With Dynamic Clustering and Scheduling. IEEE Trans. Green Commun. Netw. 2024, 9, 255–270. [Google Scholar] [CrossRef]
- Luan, H.; Xu, Y.; Liu, D.; Du, Z.; Qian, H.; Liu, X.; Tong, X. Energy efficient task cooperation for multi-UAV networks: A coalition formation game approach. IEEE Access 2020, 8, 149372–149384. [Google Scholar] [CrossRef]
- Qi, N.; Huang, Z.; Zhou, F.; Shi, Q.; Wu, Q.; Xiao, M. A task-driven sequential overlapping coalition formation game for resource allocation in heterogeneous UAV networks. IEEE Trans. Mob. Comput. 2022, 22, 4439–4455. [Google Scholar] [CrossRef]
- Fu, X.; Feng, P.; Gao, X. Swarm UAVs task and resource dynamic assignment algorithm based on task sequence mechanism. IEEE Access 2019, 7, 41090–41100. [Google Scholar] [CrossRef]
- Mao, Y.; You, C.; Zhang, J.; Huang, K.; Letaief, K.B. A survey on mobile edge computing: The communication perspective. IEEE Commun. Surv. Tutor. 2017, 19, 2322–2358. [Google Scholar] [CrossRef]
- Zhao, G.; Xu, H.; Zhao, Y.; Qiao, C.; Huang, L. Offloading tasks with dependency and service caching in mobile edge computing. IEEE Trans. Parallel Distrib. Syst. 2021, 32, 2777–2792. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, S.; Zhao, Q.; Du, S.; Zhou, A.; Ma, X.; Yang, F. Dependency-aware task scheduling in vehicular edge computing. IEEE Internet Things J. 2020, 7, 4961–4971. [Google Scholar] [CrossRef]
- Yang, Y.; Shi, Y.; Yi, C.; Cai, J.; Kang, J.; Niyato, D.; Shen, X. Dynamic human digital twin deployment at the edge for task execution: A two-timescale accuracy-aware online optimization. IEEE Trans. Mob. Comput. 2024, 23, 12262–12279. [Google Scholar] [CrossRef]
- Holme, P.; Saramäki, J. Temporal networks. Phys. Rep. 2012, 519, 97–125. [Google Scholar] [CrossRef]
- Li, Y.; Li, J.; Lv, Z.; Li, H.; Wang, Y.; Xu, Z. GASTO: A fast adaptive graph learning framework for edge computing empowered task offloading. IEEE Trans. Netw. Serv. Manag. 2023, 20, 932–944. [Google Scholar] [CrossRef]
- Cai, J.; Zhu, X.; Ackah, A.E. Mobility-aware task offloading scheme for 6G networks with temporal graph and graph matching. IEEE Internet Things J. 2024, 11, 20840–20852. [Google Scholar] [CrossRef]
- Yan, X.; Zhang, X.; Zeng, K.; Bai, F.; Shen, T.; Cao, B. Multi-Endpoint DAG-Driven Joint Partitioning-Offloading and Scheduling Optimization for DNN Inference. IEEE Internet Things J. 2025, 12, 41087–41102. [Google Scholar] [CrossRef]
- Chen, W.; Su, Z.; Xu, Q.; Luan, T.H.; Li, R. VFC-based cooperative UAV computation task offloading for post-disaster rescue. In Proceedings of the IEEE INFOCOM 2020-IEEE Conference on Computer Communications, Toronto, ON, Canada, 6–9 July 2020; pp. 228–236. [Google Scholar]
- Tran, T.X.; Pompili, D. Joint task offloading and resource allocation for multi-server mobile-edge computing networks. IEEE Trans. Veh. Technol. 2018, 68, 856–868. [Google Scholar] [CrossRef]
- Al-Hourani, A.; Keepan, S.; Lardner, S. Optimal LAP altitude for maximum coverage. IEEE Wirel. Commun. Lett. 2014, 3, 569–572. [Google Scholar] [CrossRef]
- Kempe, D.; Kleinberg, J.; Kumar, A. Connectivity and inference problems for temporal networks. In Proceedings of the Thirty-Second Annual ACM Symposium on Theory of Computing, Portland, OR, USA, 21–23 May 2020; pp. 504–513. [Google Scholar]
- Klobas, N.; Mertzios, G.B.; Molter, H.; Niedermeier, R.; Zschoche, P. Interference-free walks in time: Temporally disjoint paths. Auton. Agents-Multi-Agent Syst. 2023, 37, 1. [Google Scholar] [CrossRef]
- Ibiapina, A.; Lopes, R.; Marino, A.; Silva, A. Menger’s theorem for temporal paths (not walks). arXiv 2022, arXiv:2206.15251. [Google Scholar]
- Cheng, J.; Yang, P.; Navaie, K.; Ni, Q.; Yang, H. A low-latency interference coordinated routing for wireless multi-hop networks. IEEE Sens. J. 2021, 21, 8679–8690. [Google Scholar] [CrossRef]
- Hosseinzadeh, M.M.; Cannataro, M.; Guzzi, P.H.; Dondi, R. Temporal networks in biology and medicine: A survey on models, algorithms, and tools. Netw. Model. Anal. Health Inform. Bioinform. 2023, 12, 10. [Google Scholar] [CrossRef]
- Gu, B.; Zhou, Z.; Mumtaz, S.; Frascolla, V.; Bashir, A.K. Context-aware task offloading for multi-access edge computing: Matching with externalities. In Proceedings of the 2018 IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar]
- Xia, B.; Li, C.; Zhou, Z.; Liu, J. Research on deployment method of service function chain based on network function virtualization in distribution communication network. In Proceedings of the 2023 IEEE 6th Information Technology, Networking, Electronic and Automation Control Conference (ITNEC), Chongqing, China, 24–26 February 2023; Volume 6, pp. 1410–1414. [Google Scholar]



| Symbol | Meaning | Symbol | Meaning |
|---|---|---|---|
| Set of tasks | Set of UAVs | ||
| Location set of targets | Set of time slots | ||
| Set of service nodes | Set of routes for all UAVs | ||
| Set of tasks collected by all UAVs | Tasks of type | ||
| Length of time slot | The computational resources required for the task | ||
| The input data volume of the task | Directed acyclic graph | ||
| The set of subtasks | Dependencies between subtasks | ||
| Data volume transferred between two subtasks | The maximum cache capacity of the UAV | ||
| R | The communication rate | g | The channel gain |
| d | The distance between UAV and service node | Path loss | |
| The connection probability of link | Task weights |
| Parameters | Value | Parameters | Value |
|---|---|---|---|
| M | [3, 6] | 100 mW | |
| mW | [5, 10] MHz | ||
| [1, 5] GHz | (9.61, 0.61) | ||
| [500, 800] KB | [100, 300] MHz |
| Backhaul Latency (ms) | Interference Level | Task Completion Time (s) | System Efficiency (%) |
|---|---|---|---|
| 50 | Low | 0.131 | 98.13 |
| 50 | High | 0.168 | 85.25 |
| 100 | Low | 0.263 | 95.89 |
| 100 | High | 0.614 | 82.46 |
| 200 | Low | 0.797 | 97.20 |
| 200 | High | 1.312 | 88.34 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhao, L.; Zhu, X.; Cai, J. Task Offloading Algorithm for Multiple Unmanned Aerial Vehicles Based on Temporal Graph. Sensors 2025, 25, 6759. https://doi.org/10.3390/s25216759
Zhao L, Zhu X, Cai J. Task Offloading Algorithm for Multiple Unmanned Aerial Vehicles Based on Temporal Graph. Sensors. 2025; 25(21):6759. https://doi.org/10.3390/s25216759
Chicago/Turabian StyleZhao, Lingyu, Xiaorong Zhu, and Jianhong Cai. 2025. "Task Offloading Algorithm for Multiple Unmanned Aerial Vehicles Based on Temporal Graph" Sensors 25, no. 21: 6759. https://doi.org/10.3390/s25216759
APA StyleZhao, L., Zhu, X., & Cai, J. (2025). Task Offloading Algorithm for Multiple Unmanned Aerial Vehicles Based on Temporal Graph. Sensors, 25(21), 6759. https://doi.org/10.3390/s25216759






