Abstract
Particle Swarm Optimization (PSO) has been widely employed to optimize the deployment of Unmanned Aerial Vehicles (UAVs) in various scenarios, particularly because of its efficiency in handling both single and multi-objective optimization problems. In this paper, a framework for optimizing the deployment of edge-enabled UAVs using Pareto-PSO is proposed for data collection scenarios in which UAVs operate autonomously and execute onboard distributed multi-objective PSO to maximize the total non-overlapping coverage area while minimizing latency and energy consumption. Performance evaluation is conducted using key indicators, including convergence time, throughput, and total non-overlapping coverage area across bandwidth and swarm-size sweeps. Simulation results demonstrate that the Pareto-PSO consistently attains the highest throughput and the largest coverage envelope, while exhibiting moderate and scalable convergence times. These results highlight the advantage of treating the objectives as a vector-valued objective in Pareto-PSO for real-time, scalable, and energy-aware edge-UAV deployment in dynamic Internet of Flying Things environments.
1. Introduction
The Internet of Flying Things (IoFT) represents a multi-layered network architecture that integrates Unmanned Aerial Vehicles (UAVs), commonly known as drones, as the primary physical entities in Flying Ad Hoc Network (FANET) environments, in conjunction with Internet of Things (IoT) technology [1]. This integration facilitates real-time data exchange, autonomous coordination, and effective management of low-altitude airspace [2].
Given their versatile functionalities and rapid deployment, UAVs are increasingly used to collect real-time data from hard-to-reach locations. A prominent application is providing wireless coverage to distributed ground users (GUs), where UAVs can be deployed as flying base stations (FBSs), cellular base stations, or Wi-Fi access points to extend connectivity in areas lacking traditional communication infrastructure [3,4,5].
UAV deployment refers to positioning and operating UAVs for specific tasks across a wide range of civil and military application domains [6]. After disasters, UAVs can serve as mobile communication systems to connect GUs and survivors [7], acting as first-response platforms that support rescue efforts [8]. Furthermore, UAVs can act as a platform for the delivery of commercial services to consumers [9]. In surveillance and monitoring missions, effective UAV deployment plays a crucial role in facilitating data collection and improving the quality of coverage for the targeted areas of interest [10]. In addition, within network reconstruction scenarios, UAVs can function as aerial relays to re-establish wireless links and reconnect isolated ground networks, particularly in disaster situations where fixed ad hoc networks have been severely compromised [11].
By positioning edge servers closer to the users, Mobile Edge Computing (MEC) reduces network congestion that often occurs with traditional cloud-based systems. This local processing leads to accelerated data processing that minimizes delays, leading to better performance and better Quality of Service (QoS), especially in tasks requiring real-time responses [2], collecting data missions, emergency communication, and rescue operations.
In the Internet of Drones (IoD), edge computing technology enhances the capabilities of both fog and cloud computing to support real-time IoT applications. By processing a portion of UAV data locally on edge IoD devices, the edge layer reduces the computing load without relying on fog or cloud interventions. This shift toward edge-based data processing and storage promotes significant latency improvements [12]. UAVs can be considered as edge nodes capable of offering computing services to GUs, with the aim of minimizing the average task response time by jointly optimizing UAV deployment and computation offloading [3].
Optimizing UAV deployment is a key area of ongoing research [13]. Deployment studies typically prioritize latency, coverage, and energy consumption, especially under rapid deployment and real-time decision making. These objectives directly shape network efficiency, responsiveness, and sustainability. Latency governs end-to-end data transfer and processing speed; coverage defines the served area; and energy consumption critically determines UAV operational lifetime [13]. Therefore, it is crucial to reduce peak energy consumption before service commencement [5]. Additional metrics (e.g., QoS variants, link reliability, security) are important but often increase model complexity. In mission-critical contexts, prioritizing latency, coverage, and energy preserves tractability for timely decisions.
For instance, the Particle Swarm Optimization (PSO) algorithm is a lightweight metaheuristic noted for rapid convergence, efficient search, and adaptability; it effectively handles landscapes with multiple local optima [14].
To adopt a consistent and effective metric for multi-objective edge-UAV deployment based on the well-known PSO metaheuristic, this paper proposes and implements a Pareto-PSO framework for edge-UAV deployment and compares it against two PSO-based scalarization baselines. These include the following:
- Pareto-PSO with external archive:treats the objectives as a vector and maintains an external Pareto archive of non-dominated solutions to approximate the Pareto front.
- Weighted-sum PSO: scalarizes the multi-objective problem using predefined weights to optimize a single composite objective.
- Epsilon-constrained PSO: rotates the primary objective by optimizing one objective while imposing the remaining objectives as constraints.
The combination of scalarization and vector-based approaches has been rarely examined in prior work, and our comparison of Pareto-PSO with PSO-based scalarization baselines shows that fitness function design—scalar versus vector—materially affects the performance of distributed PSO deployment strategies in data collection and emergency response missions. These results guide the selection of methods that achieve real-time, scalable, and efficient deployment trade-offs for edge-UAVs operating in dynamic environments. Because distributed algorithms operate solely on locally available data, they enable informed decision making with minimal information exchange, thereby reducing communication overhead and latency [4]. This rationale motivates distributing the PSO metaheuristic across the edge-UAV swarm.
Furthermore, in this paper, we aim to identify the strengths, limitations, and performance characteristics of using scalarization techniques to convert a multi-objective edge-UAV deployment optimization problem into a single-objective one. In addition, our goal is also to use a vectorization technique that combines multiple objectives directly. The goal is to assess how scalarization compares to directly handling the problem as a vector of multiple objective functions, particularly in terms of convergence speed, throughput, and coverage efficiency. The evaluation is based on a scenario in which a swarm of edge-UAVs are deployed over an area of interest to gather and receive various types of information, such as recorded videos, voice messages, or text messages, from distributed GUs and then offload the collected data to a fog computing node. In this work, resilience refers to the framework’s algorithmic robustness and adaptability to user mobility and dynamic edge network conditions, rather than explicit tolerance to UAV or communication failures.
The remainder of this paper is organized as follows. Section 2 reviews the related work. Section 3 presents the basic concepts and techniques used. Section 4 describes the proposed system model and details the problem formulation. Section 5 presents and discusses the simulation results and performance evaluation. Section 6 concludes the paper and discusses future research directions.
2. Related Work
Many meta-heuristics and techniques have been implemented for single-objective optimization and even for multi-objective optimization in UAV deployment, such as Genetic Algorithm (GA), PSO, Ant Colony Optimization (ACO), and Evolutionary algorithms, among others.
In this section, we cover two subsections. The first subsection presents an overview of the proposed and designed UAV deployment algorithms to address the specific application challenges that arise when positioning and operating UAVs for different tasks, including overcoming technical UAV constraints such as energy consumption and resource limitations, along with practical complexities of real-world deployments such as cost effectiveness in dynamic and often unpredictable environments. The second subsection then discusses studies that investigate the use of the PSO algorithm to optimize the UAV deployment problem.
2.1. Overview of UAV Deployment Algorithms
Fan et al. [6] aimed to reduce the probability of UAV detection by adversary systems during real-time monitoring missions in tactical battlefield scenarios, allowing UAVs to identify potential targets. They proposed a Distributed Virtual Force Motion Control Algorithm (DVFMC) to achieve this goal. The algorithm operates without requiring global information and relies on local coverage of the path-demand area. MATLAB simulations validated the efficiency of the proposed method in reducing the probability of detection. The resulting UAV network was proved to be effective for real-time operation with high reliability, making it well suited for battlefield monitoring applications.
Rhodes et al. [7] present an advanced UAV deployment approach for autonomous gas source search and localization in unknown GPS-denied environments. Their system leverages a UAV platform that integrates the Dual Control for Exploitation and Exploration (DCEE) utility function with a Rapidly exploring Random Tree (RRT)-based path planning algorithm. This combination is central to the UAV deployment strategy, enabling the UAV to autonomously map its environment, avoid obstacles, and make real-time decisions about where to sample next. The proposed approach ensures that UAVs can explore unknown environments safely, efficiently, and intelligently, dynamically adapting their deployment to maximize the effectiveness of the search and estimation process, thereby addressing real-world challenges in hazardous source locations.
Huang and Savkin [10] proposed a reactive, decentralized, and collision-free 3D deployment algorithm for surveillance and monitoring applications. The algorithm aims to maximize the quality of coverage (QoC) of targets by deploying UAVs in a continuous 3D space and navigating each UAV based on local measurements rather than global information. MATLAB simulations demonstrate the effectiveness of the algorithm in achieving the desired coverage performance.
Liu et al. [15] proposed two centralized UAV deployment algorithms. The first algorithm, UAV Deployment Algorithm Degree and Distance (UDA-DD), uses the distance between the base stations and the user devices, along with the user degree, as metrics to build and update service connections. In contrast, the second algorithm, UAV Deployment Algorithm Degree (UDA-DS), focuses on maintaining the QoS between base stations and user devices based on the user degree and SINR between users and base stations. Both algorithms seek to formulate the full communication coverage problem with objectives such as minimizing the number of UAVs deployed, ensuring the quality of service, and guaranteeing network robustness. However, both algorithms differ in how they provide coverage in two scenarios. The first scenario addresses the absence of terrestrial static base stations, while the second considers situations where static base stations exist but fail to deliver sufficient communication coverage to all users. Simulations were performed using MATLAB R2015b, and the results demonstrated that both UDA-DD and UDA-DS improved the QoS and ensured robust network performance during UAV deployment. However, since these approaches are centralized, they may not be suitable for large-scale or dynamic environments.
In [16], Trotta et al. propose a distributed framework for an aerial mesh deployment system named the aErial Local Positioning System for Emergency (ELAPSE), where UAVs are used as mobile base stations. The authors deployed these UAVs to provide emergency services, maintain coverage, establish connectivity between isolated rescue teams, and assist affected individuals in areas lacking infrastructure. The UAV swarm operates without relying on Global Positioning System (GPS) signals; instead, it uses a combination of local and cooperative positioning techniques. The results of OMNeT++ simulations demonstrate the effectiveness of the proposed framework.
Lee and Friderikos [17] investigated the use of UAVs as FBSs that can be associated with different macro-base stations to address trajectory optimization in multi-cell wireless networks. The proposed UAV deployment algorithm, based on Mixed Integer Linear Programming (MILP), introduces a novel optimization framework that determines the optimal trajectory of FBSs to minimize the Total Travel Time (TTT) while serving GUs across multiple cells.
In [18], Miao et al. explored the use of UAVs as MEC nodes to improve the computing and storage capacity of the IoT industry and smart city applications during natural disasters. They propose a UAV deployment method called Ground-Air Controlled Global and Local Path Planning for UAV Swarm-MEC Offloading Strategy (GAGLPP), which aims to achieve three objectives: maximize offloading services, minimize path length, and maximize energy efficiency. The experimental results validate the effectiveness of the GAGLPP strategy.
In [19], Huang and Savkin investigated the deployment of UAV-mounted base stations after disasters or during temporary events to provide optimal coverage for a set of GUs. Their algorithm aims to minimize the distance between UAVs and GUs while also maintaining connectivity with fixed base stations. UAVs are deployed at different altitudes to serve GUs, ensuring strong signal quality in both Line-Of-Sight (LOS) and Non-Line-Of-Sight (NLOS) conditions. The proposed decentralized deployment algorithm assumes direct air-to-ground LOS communication, allowing each UAV to determine its movement based solely on local information.
Zhang et al. [20] introduce a novel deep reinforcement learning (DRL) framework to optimize the deployment of tethered UAVs in millimeter-Wave (mmWave) Integrated Access and Backhaul (IAB) networks, with a particular focus on dense urban environments. The proposed approach, based on the TD3-MB algorithm, jointly addresses three main objectives: minimizing the number of required UAVs and terrestrial base stations, optimizing the hovering positions of UAVs, and configuring the multi-hop backhauling topology. The deployment problem is formulated as a constrained optimization task, where the goal is to reduce the overall deployment cost while ensuring that all client nodes are connected to the network core and meet strict quality-of-service requirements. By modeling the environment as a Markov Decision Process, and by applying a non-cumulative reward criterion via the max-Bellman optimality equation, the framework effectively learns optimal deployment and routing strategies. The study demonstrates that this method adapts efficiently to complex urban scenarios with varying blockage densities, as validated through case studies in cities in Asia, Europe, and North America. The results highlight the framework’s ability to overcome key challenges such as line-of-sight constraints, deployment cost, power limitations, and scalability, ultimately enabling robust and cost-effective UAV-based network deployments in practical settings.
Qi et al. [21] propose an optimization strategy that addresses the problem of minimizing the latency among multi-rotor surveillance UAVs involved in video transmission to a relay UAV for maritime search and rescue operations. The problem is decomposed into three sub-problems: (i) offloading decision optimization, (ii) relay UAV position optimization, and (iii) association optimization between surveillance UAVs and targets. The proposed approach effectively reduces the maximum latency and balances the delay across all surveillance UAVs, enabling faster and more fair rescue decision making. However, the study assumes known target locations and static environmental conditions, and its computational complexity may limit scalability for large-scale or highly dynamic scenarios.
Table 1 provides a comprehensive overview of some of the latest and significant studies on UAV deployment algorithms, evaluating them according to three essential criteria: the type of UAV system used, the primary application objective, and the architectural approach to decision making and information usage. The criteria are described as follows:
- The first criterion considers the type of UAV; for instance, some works focus on deploying single UAVs as flying base stations (FBSs) or relay nodes, emphasizing areas such as coverage maximization and seamless backhaul integration. In contrast, other studies leverage UAV swarms to achieve robust mesh networking or adopt UAV-based mobile edge computing (MEC) architectures to support distributed, real-time data processing in dynamic industrial environments.
- The second criterion focuses on the application objective of each deployment algorithm, as presented in the respective studies. Beyond technical specifications, the table highlights how each algorithm’s objective is tailored to specific operational contexts. Coverage-focused algorithms are particularly relevant for disaster response and rural connectivity, where rapid deployment and reliable service are priorities. Meanwhile, connectivity-driven approaches address the complexities of maintaining robust inter-UAV links in challenging or contested environments. The inclusion of MEC-oriented algorithms underscores the growing importance of computational offloading at the network edge.
- The third criterion is an assessment of the algorithmic architecture: whether control is centralized, or distributed, and whether deployment decisions are based on global or local information.

Table 1.
Comparison of UAV deployment algorithms.
Table 1.
Comparison of UAV deployment algorithms.
| Paper | Method | UAV as | Objective | Architecture | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| FBS | Swarm | MEC | Connectivity | Coverage | Computation | Optimal Path | Centralized | Distributed | Local Info | Global Info | ||
| Fan et al. [6] | DVFMC | ✓ | ✓ | ✓ | ✓ | ✓ | ||||||
| Huang and Savkin [10] | GPS-Free Decentralized Flocking | ✓ | ✓ | ✓ | ✓ | ✓ | ||||||
| Lui et al. [15] | UDA-DD and UDA-DS | ✓ | ✓ | ✓ | ||||||||
| Trotta et al. [16] | ELAPSE | ✓ | ✓ | ✓ | ✓ | |||||||
| Lee and Friderikos [17] | GAGLPP | ✓ | ✓ | |||||||||
| Miao et al. [18] | Deep RL-based swarm path planning | ✓ | ✓ | |||||||||
| Huang and Savkin [19] | Reactive Collision Free 3D | ✓ | ✓ | ✓ | ✓ | ✓ | ||||||
2.2. Literature Review on UAV Deployment Based on PSO Meta-Heuristic
Chen et al. [3] proposed a hybrid PSO-based method called the PSO-Genetic Algorithm-Greedy (PSO-GA-G) to jointly optimize UAV deployment and computation offloading in multi-UAV-enabled MEC systems. The method adopts a two-layer solution: The outer layer combines PSO and GA to determine optimal UAV positions, while the inner layer uses a greedy algorithm to decide which tasks received from mobile devices should be offloaded. The approach aims to minimize the average task response time in a dynamic environment but faces constraints on computational complexity, especially with GA, real-world modeling, and energy awareness.
In [4], Hydher et al. focused on optimizing UAV deployment in disaster-affected areas to maximize spectral efficiency while minimizing energy consumption. The problem was divided into two sub-problems: (i) horizontal placement and user assignment and (ii) altitude optimization. For the former, they applied K-means clustering combined with the stable marriage algorithm. For altitude optimization, they proposed two methods: a basic exhaustive search and a more efficient PSO meta-heuristic. The proposed approach enabled significant energy savings and achieves higher spectral efficiency, especially in dense networks. However, the study assumed static user locations and centralized control, which can limit its adaptability and practicality in highly dynamic or large-scale disaster scenarios.
Lin et al. [13] proposed an enhanced optimization algorithm called Double Self-Limiting PSO (DSLPSO), which is designed to improve UAV energy efficiency in data collection missions for IoT scenarios. The algorithm focuses on determining the optimal number and locations of UAV stopping points, minimizing the total energy consumption of both the UAV and IoT devices. By planning more energy-efficient trajectories, DSLPSO extends mission duration and outperforms existing algorithms in terms of energy savings and adaptability to varying mission sizes. Notably, the method introduces Self-Limiting Radius and Multiple Simulated Annealing (SLRMSA) mechanisms to balance global and local search capabilities. However, the study is limited by its focus on single-UAV scenarios, fixed flight altitude, and idealized simulation environments, which may affect scalability and practical deployment in more complex settings.
Liu et al. [14] proposed a hybrid approach named Tent-PSO that combines the standard PSO technique with tent chaotic mapping to optimize drone paths. The approach aims to maximize throughput, increase user coverage, maintain link quality, and enhance global search efficiency in real-time, with drones deployed as communication relays to provide reliable connectivity for mobile GUs. By replacing random initialization of the positions of particles with tent mapping, the algorithm prevents particles from inefficient exploration and reduces the risk of getting trapped in local optima. The Tent-PSO approach is difficult to apply practically, since its outcomes rely heavily on the parameters that are chosen, and it does not evaluate real-life scenarios.
Abdel-Razeq et al. [22] investigated the joint optimization of 3D UAV deployment and a transmit power allocation strategy for a UAV-enabled uplink Non-Orthogonal Multiple Access (UL-NOMA) network, aiming to maximize the ergodic sum rate. For the UAV deployment stage, they applied the PSO meta-heuristic to determine the optimal 3D positioning of UAVs. The objective is to minimize the aggregate path loss between UAVs and GUs, thus ensuring efficient data collection. The study assumes perfect channel conditions and disregards guards user movement, UAV energy limits, and signal processing errors. Because it streamlines user pairing and leaves out important issues in large, real-world networks, its conclusions might not be immediately applicable to actual implementation.
In [23], Xuefeng Chen et al. proposed a hybrid intelligent coverage algorithm called the PSO–Virtual Repulsive Force Firefly Algorithm (PSO-VRFFA) to optimize UAV-mounted base stations. In this approach, the PSO algorithm serves as the general framework (for a global search, by exploring the search space for promising UAV positions), while the VFA component phase fine-tunes UAV locations to maximize user coverage and minimize overlap between UAVs. Although PSO-VFA achieves improved user coverage and faster convergence, it is constrained in terms of scalability and practical applicability in a large, dynamic, or resource-constrained environment.
Rasouli [24] aimed to use the PSO algorithm to determine the optimal placement of drones deployed as aerial base stations in crowded user environments. The objective is to maximize user coverage using the minimum number of drones while considering energy consumption as a constraint. The study demonstrates that the PSO-based approach enables the rapid and flexible deployment of UAVs, improves energy efficiency and ensures stable and reliable connections for users. However, it is limited by its reliance on an idealized simulation environment with randomly distributed users and fixed altitudes, which may not fully represent real-world conditions or address additional practical concerns such as backhaul connectivity and experimental validation.
Ibraiwish et al. [25] proposed a framework to optimize the trajectories of visible light communication-enabled UAVs by formulating a Multi-objective Optimization Problem (MOP) that jointly maximizes the user sum rate and rate fairness while minimizing UAV power consumption. The optimization is performed using the PSO algorithm with enhanced particle initialization. The advantages of the proposed method are its ability to dynamically adapt UAV trajectories to user mobility, achieve significant improvements in sum rate and user coverage, and explicitly account for the dominant energy cost of UAV propulsion. However, the study is limited by its reliance on predetermined user mobility patterns, simplified (obstacle-free) simulation environments, and potential scalability challenges as the number of UAVs and users increases.
Li et al. [26] proposed a Multi-Objective Particle Swarm Optimization (MOPSO) framework for the deployment of UAVs in multi-hop Flying Ad Hoc Networks (FANETs), supporting emergency vehicular communications. Their method formulates UAV placement as a multi-objective optimization problem that simultaneously minimizes deployment cost, networking time, and hop count, facilitating rapid and reliable relay construction between stranded vehicles and infrastructure. Utilizing terrain-aware simulations incorporating obstacles and realistic environmental factors, the MOPSO algorithm effectively identifies relay node positions that maintain stable inter-UAV links while operating within the communication range. The optimizer employs Pareto dominance principles to generate a diverse set of trade-off solutions representing different balances among conflicting objectives. A key innovation is the adoption of a branching-node selection strategy, which strategically reduces overall deployment time and cost, particularly in asymmetric network topologies. Although the approach exhibits strong adaptability to dynamic real-world conditions, the authors note that performance may be sensitive in scenarios with uniform target distributions, and underlying assumptions such as simplified channel and mobility models may restrict direct applicability to highly complex environments.
Table 2 presents a comparison between the related works listed in Section 2.2; it details UAV deployment based on the PSO meta-heuristic and compares them to our proposed PSO usage approach. This comparison is based on the following three criteria:
- The first criterion considers the most common optimization objectives; it includes maximizing user coverage, as well as minimizing energy consumption while maximizing energy efficiency during missions or minimizing latency.
- The second criterion focuses on how the PSO algorithm is used, whether it is implemented as a standard approach or in variants for the UAV deployment scenario.
- The third criterion considers the UAV type involved; most studies deploy rotary-wing UAVs as aerial base stations or relays, and some are deployed with specialized roles such as flying access points or UAV-enabled mobile edge computing systems (serving as edge servers).
- Most of the works in this table prefer to solve objectives either in (i) sequential, separate stages by using different techniques for different sub-problems or (ii) aggregate multiple objectives into a single function for standard PSO optimization. A truly simultaneous multi-objective optimization with PSO is only seen in the work of Ibraiwish et al. [25] and in the work of Li et al. [26]. Our work proposes a true multi-objective PSO framework, including Pareto-PSO in a distributed manner, allowing simultaneous optimization of coverage, latency, and energy for edge-UAV network.

Table 2.
Comparison of UAV deployment works based on PSO meta-heuristic.
Table 2.
Comparison of UAV deployment works based on PSO meta-heuristic.
| Paper | Objectives | Method | UAV Types | Objectives Handling Strategy | |||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Energy | Coverage | Latency | Throughput | PSO | PSO-Combined | MEC | AP | BS | Relay | ||
| [3] | ✓ | ✓ | ✓ | Sequential: deployment PSO+GA, offloading greedy | |||||||
| [4] | ✓ | ✓ | ✓ | Two-stage pipeline: placement via K-means/stable marriage, altitude via standard PSO | |||||||
| [13] | ✓ | ✓ | Single-objective (energy-focused) | ||||||||
| [14] | ✓ | ✓ | ✓ | ✓ | Single-objective (combined metric of multiple goals) | ||||||
| [22] | ✓ | ✓ | ✓ | Single-objective (maximize ergodic sum rate) | |||||||
| [23] | ✓ | ✓ | ✓ | Single-objective (maximize coverage, minimize overlap via weighted sum) | |||||||
| [24] | ✓ | ✓ | ✓ | ✓ | Single-objective (coverage primary, energy as constraint) | ||||||
| [25] | ✓ | ✓ | ✓ | Multi-objective Pareto dominance (simultaneous) | |||||||
| [26] | ✓ | ✓ | ✓ | ✓ | Multi-objective optimization (Pareto-based deployment) | ||||||
| Our Work | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | Multi-objective distributed optimization (all objectives jointly optimized) | ||||
3. Basic Concepts
This section aims to provide the fundamental concepts underlying the techniques employed in our study, providing a clear foundation for understanding the proposed approach prior to the implementation details. Understanding these concepts provides clarity on how each technique contributes to solving the edge-UAV deployment problem proposed in this paper.
3.1. Particle Swarm Optimization (PSO) Meta-Heuristic for UAV Deployment
PSO is a population-based meta-heuristic inspired by the social behavior of flocking birds or schooling fish. The optimization of UAV deployment based on the standard PSO meta-heuristic is modeled as a swarm of particles, where each particle represents a potential UAV deployment solution [23]. To search for the optimal solution, each particle updates its position and velocity in the solution space based on its own historical best position (pbest) and the global best position identified by the swarm (gbest) [27].
where i denotes the particle index, f represents the fitness function, t is the current iteration number, is the total number of particles, and P indicates the position of the particle. The position P and velocity V of the particles are updated by the following equations [27]:
where is the inertia weight used to balance global exploration and local exploitation; and are uniformly distributed random variables within the range ; and and are positive constants known as “acceleration coefficients”.
3.2. The Weighted-Sum Method
The Weighted-sum method is one of the most widely used scalarization techniques [5]. It transforms a MOP into a set of single-objective problems by assigning a specific weight to each objective (by varying the importance of objectives, we build a set of single-objective optimization subproblems), allowing them to be aggregated into a single scalar value.
where , , …, and represent the objectives to be optimized, and are weighting coefficients that control the importance given to each objective.
Normalization of Terms
The objective values in our paper (minimizing latency, maximizing coverage, and minimizing energy consumption) have different units and magnitudes. To ensure that all objectives are comparable and consistently directed toward minimization, we follow the standard optimization practice of reversing the sign of maximization objectives, as described by [28]: Any maximization problem can be transformed into a minimization problem by replacing the objective with . Thus, the coverage metric is converted to a minimization objective simply by using the following:
3.3. The Epsilon-Constrained Method
The Epsilon constraint method is a mathematical programming technique that transforms a Multi-objective Optimization Problem (MOP) into a series of single-objective constrained problems. As a scalarization approach, it generates one Pareto front point at a time by optimizing one objective while treating the others as constraints [29]. The method typically assumes that all objective functions are to be minimized, as shown below:
where and S define the feasible region, which is defined by a set of equality and/or inequality constraints. The vector of upper bounds, , specifies the maximum value for each objective function.
3.4. The Pareto Front in a Multi-Objective Optimization Problem (MOP)
Multi-objective optimization is the process of simultaneously optimizing two or more objectives subject to certain constraints [30]. The process involves the simultaneous optimization of multiple objective functions that may conflict with each other, all within specified criteria. Due to the conflicting nature of these objectives and their associated constraints, determining an optimal set of solutions presents a significant challenge. A solution is deemed Pareto optimal when there is no other feasible solution that can enhance one objective without compromising at least one of the other objectives [31]. A MOP is formulated as follows in the study [30]:
where is a feasible nonempty set, and f is a vector-valued function composed of p () real-valued functions. In Figure 1, all points in the dataset represent feasible solutions obtained for objective functions 1 and 2. When considering points A, B, and C with the objective of minimizing both objectives, the following observations can be made:
- Point A dominates point B in objective 1 and point C in both objectives.
- Point B dominates point A in objective 2 and also dominates point C in both objectives.
- Point C is dominated by both points A and B in both objectives.
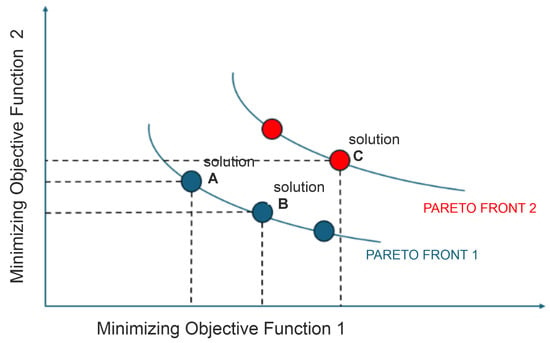
Figure 1.
The set of objective space solutions for objective functions f1 and f2 along with A, B, and C solutions.
Figure 1.
The set of objective space solutions for objective functions f1 and f2 along with A, B, and C solutions.
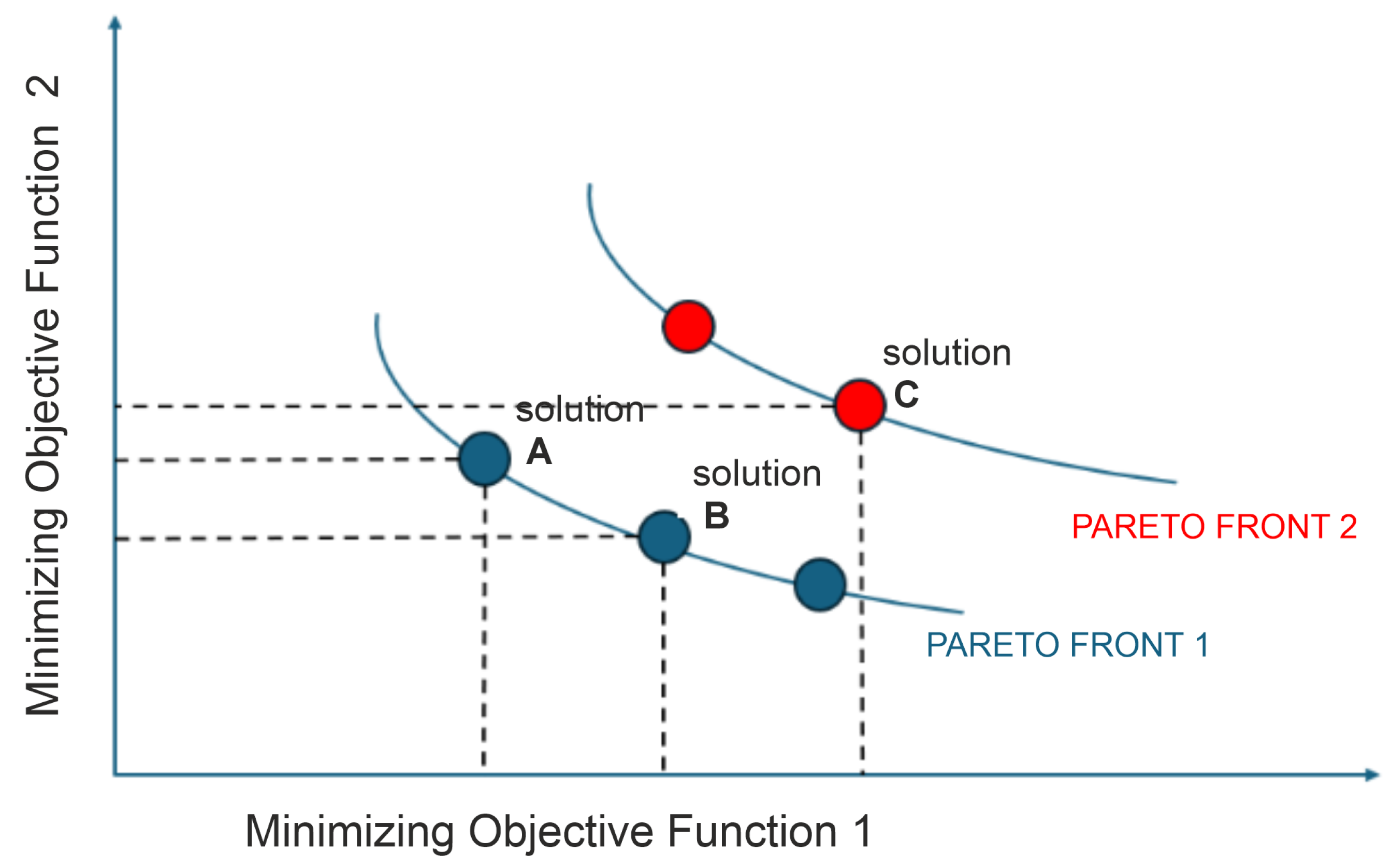
In this scenario, points A and B are non-dominated by each other and by any other solution, which categorizes them as belonging to the same Pareto front (PF1). On the other hand, point C is dominated by both A and B, placing it in the subsequent Pareto front (PF2).
To allocate all individuals to distinct Pareto fronts, the process starts by identifying all non-dominated solutions (PF1) within the complete set of solutions X. The remaining set is then analyzed to determine the subsequent set of non-dominated solutions as PF2. This process is repeated iteratively until all solutions have been assigned to a Pareto front [31].
4. System Model and Problem Formulation
Figure 2 illustrates the communication architecture used for data reception and transmission. We consider a set N = {1, 2, 3, …, n} of UAVs equipped with edge computing capabilities, providing data collection services to a set M = {1, 2, 3, …, m} of GUs, distributed over a 500 m × 500 m geographical area. Vector Si = {, , , …, } represents the size of the data received from the GUs by edge-UAVi. We propose the following scenario:
- Edge-UAVs fly over the area of interest, providing connectivity to GU devices.
- GU devices upload their data, such as text messages, GPS positions, videos, and audio files.
- Each edge-UAV waits until it has received all assigned data and then retransmits it to a fog node for further processing.
- The new optimized position of each edge-UAV is computed using the PSO algorithm, which aims to optimize three objectives: maximizing the total non-overlapping coverage area, minimizing latency, and minimizing energy consumption.
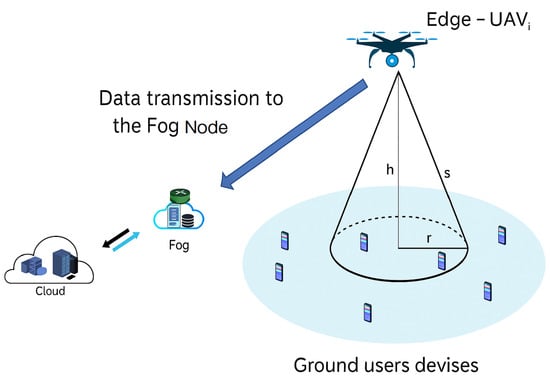
Figure 2.
Communication architecture.
Figure 2.
Communication architecture.
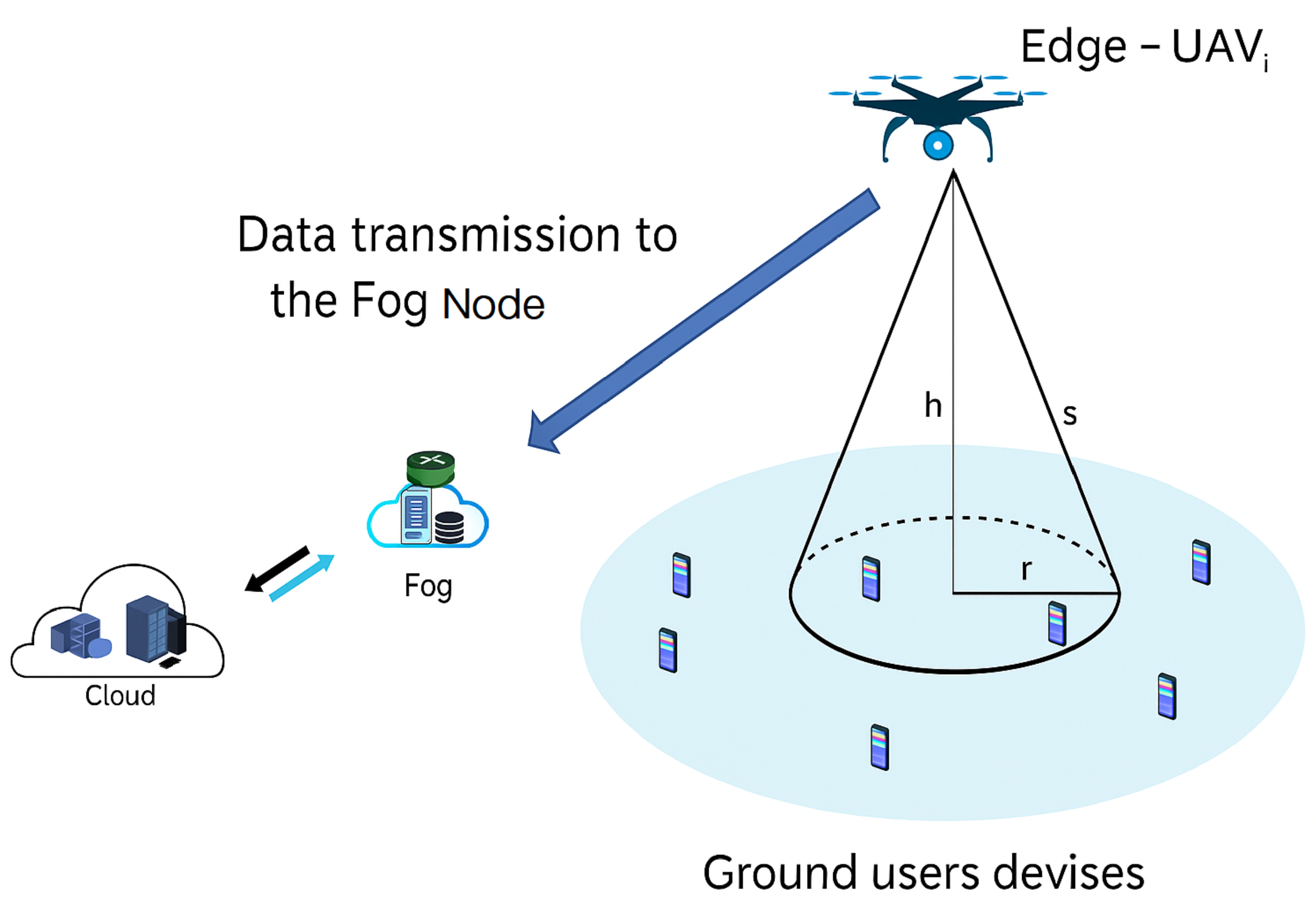
4.1. Latency Model
In wireless communication, path loss is always present [23]. In our model, the overall path loss occurs in two stages: from GUs to edge-UAVi and from edge-UAVi to the fog node. The proposed system model is constructed based on the approach described in [27]. Each edge-UAVi receives data from several GUs and then forwards them to a shared fog node. For the reception stage, from ground users (GUs) to edge-UAVs, the communication model incorporates realistic path loss including both line-of-sight (LoS) and non-line-of-sight (NLoS) conditions probabilistically, as is consistent with standards such as 3GPP. Importantly, fading and shadowing effects are integrated to capture small- and large-scale channel variations. The achievable transmission rate is determined based on the Signal-to-Interference-plus-Noise Ratio (SINR), which includes interference arising from concurrent transmissions of other edge-UAVs. Similarly, for the transmission stage from edge-UAVs to the fog node, the same comprehensive path loss model is adopted, incorporating fading, shadowing, and interference effects akin to those considered in the GUs-to-UAV links. This unified approach enhances the accuracy and consistency of channel modeling across both communication stages. Consequently, the total delay experienced by an edge-UAV comprises these two principal components:
- Reception latency (Trecv): the time required for edge-UAVi to receive data from its associated GUs.
- Offloading latency (Toffload): the time needed to transmit the received data from edge-UAVi to the fog node.
In our latency model, we assume that edge-UAVs are equipped with a single radio interface, and data reception from GUs is performed sequentially. This serial reception mechanism reflects the practical limitations of UAV hardware and aligns with the rapid deployment objectives as access point UAVs, where implementing complex parallel reception schemes such as OFDMA may be constrained by size, power, and real-time processing capabilities. While parallel reception is common in modern UAV communication systems, and can help at reducing latency by supporting simultaneous multi-user transmissions, our adoption of sequential reception allows for analytical tractability and a clear characterization of worst-case latency accumulation. In particular, serial reception ensures that the total reception latency is determined by the slowest user transmission, as is consistent with Equation (13). Therefore, the total latency for edge-UAVi is given by Equation (9).
The power received on edge-UAVi from GUj is given by
where is the received power at edge-UAVi from GUj, and is the transmission power of GUj. G denotes the total antenna gain (in dB), which includes the gains of both the transmitting antenna (Tx) in the ground device and the receiving antenna (Rx) in edge-UAVi. is the wavelength of the transmitted signal, given by , where c is the speed of light, and is the carrier frequency. F models the small-scale fading effect, commonly assumed Rayleigh-distributed representing multipath fluctuations, while S accounts for large-scale shadowing, modeled as a log-normal random variable reflecting slow environment changes such as obstacles. is the distance between edge-UAVi and GUj, and represents the path loss under LoS or NLoS conditions, respectively.
4.1.1. Reception Latency ()
As already defined, reception latency represents the time required for edge-UAVi to receive data from its associated GUs. The SINR at edge-UAVi for user j is calculated using the following equation:
where is the received signal power from . is the noise power spectral density, I is the aggregate interference power from other concurrent transmission, and B is the system bandwidth. Based on this, the maximum transmission data rate () from GUj to edge-UAVi can be expressed by the following equation:
The reception latency is determined by Equation (13), which clearly indicates that the system performance depends on the slowest data reception among all GUs.
In this context, denotes the size of the data received from GUj by edge-UAVi, and represents the transmission data rate between GUj and edge-UAVi.
4.1.2. Offloading Latency ()
Once edge-UAVi has received all data, it offloads them to the fog node. The transmission rate from edge-UAVi to the fog node is given by Equation (16).
This equation represents the power received at the receiver fog node from the transmitter edge-UAVi while considering the path loss due to the environment under line-of-sight (LoS) or non-line-of-sight (NLoS) conditions. Here, G represents the combined antenna gain of the transmitter and receiver, is the wavelength of the transmitted signal (in meters), and represents the distance between edge-UAVi and the fog node (in meters). F and S represent small-scale Rayleigh fading and large-scale log-normal shadowing random variables, respectively. The corresponding SINR at the fog node is expressed as
where is the received power from edge-UAV i at the fog node, denotes the interference power at the fog node from other UAVs, is the noise power spectral density, and B is the bandwidth. Now, the offloading data rate is given by the following equation:
while the offloading latency is given by
4.1.3. Total Latency
The total latency is calculated by Equation (18):
Algorithm 1 presents the pseudo-code for calculating the Total_Latencyi associated with edge-UAVi. The algorithm is structured into three main parts; the reception latency calculation part measures how long it takes for edge-UAVi to receive data from all connected GUs, where the maximum latency (the slowest) among all users determine the completion time. The second part is the calculation of offloading latency, where the time required for edge-UAVi to offload all received data to a nearby fog node. The third part is the final aggregation part, where the total latency is the sum of the two latencies.
| Algorithm 1 Latency calculation. |
|
4.2. Energy Consumption Model
In this subsection, we introduce our energy consumption model for edge-UAVs, taking into consideration four main operations: communication, computation, hovering, and traveling. In general, the total energy consumption is calculated by adding the energy expended during data reception and transmission, local processing (PSO computation), hovering, and movement from a position to the new position.
4.2.1. Energy Consumption for Data Reception and Transmission
The energy consumed during data reception and transmission depends on the transmission power of the communication system and the duration of these activities. Each edge-UAV handles communication in two phases: it receives data from ground devices during the first phase and then transmits the collected data to the fog node during the second phase, as described in [32]. We assume that each GU transmits D units of data to edge-UAVi, and the time required to complete this transmission is given by , where is the data rate. Since the energy consumed by edge-UAVi during reception is negligible (ignoring reception energy is a common and justified simplification in typical UAV data collection modeling, because the transmission workload is handled mainly by GUs), it can be ignored. Therefore, this assumption is supported by prior work such as [33], which explicitly neglects UAV communication energy including reception due to its relatively small magnitude compared to propulsion energy. The energy consumption of edge-UAVs is primarily considered during the data transmission phase to the fog node (data offloading) and can be modeled as in [32]:
where is a constant power consumption of the communication module given by 0.5 watts in the simulation (assumed for a quadrotor UAV around 2.5–3 kg), is the amount of data offloaded by edge-UAVi to the fog node, and is the transmission rate between edge-UAVi and the fog node.
4.2.2. Computational Energy
The energy required to execute the PSO algorithm to determine the next position is governed by the computational load and the power consumption of the onboard processor.
In Equation (20), represents the processor power consumption (in watts), and represents the time taken by each edge-UAV to run its own PSO runtime measured via tic/toc (in seconds).
4.2.3. Traveling Energy
The traveling energy includes only the time required to move from the current position to the newly calculated position, as defined in Equation (21):
4.2.4. Hovering Energy
In the context of UAV-assisted edge computing, hovering time refers to the total duration during which an Unmanned Aerial Vehicle (UAV) remains stationary in the air over a designated area to perform data-related operations. In our energy model, this includes the time spent with the edge-UAV for data reception from GUs, data transmission (offloading) to a fog node, and local computation. Formally, the hovering time for edge-UAVi can be expressed as the sum of the communication and computation durations:
The hovering energy for edge-UAVi is defined by Equation (22).
where represents the power required for hovering (in watts), and is the hovering time (in seconds).
4.2.5. Total Energy Consumption
By adding all components, the total energy consumption for the mission is given by
In our context, each term corresponds to the energy consumed during hovering, communication, computation, and movement phases, respectively. Algorithm 2 presents the pseudo-code used to calculate the energy consumption of each edge-UAV.
| Algorithm 2 Energy consumption calculation. |
|
4.3. Coverage Model
The coverage model evaluates how effectively edge-UAVs cover the target area while minimizing overlapping coverage. The objective is to maximize the total non-overlapping coverage area, thereby ensuring efficient spatial utilization and reducing redundancy.
In our deployment scenario, the coverage area is determined by the union of the coverage disks provided by all edge-UAVs. When multiple edge-UAVs operate in close proximity, their coverage regions can overlap, which can lead to an overestimation of the total covered area if not treated carefully. To ensure accurate estimation, we adopt the inclusion–exclusion principle that systematically accounts for pairwise, triple, and higher-order overlaps. Let denote the coverage area of edge-UAVi, defined as a disk of radius centered at the edge-UAV’s ground projection. The total coverage area of N edge-UAVs is given by the following union:
Applying the inclusion–exclusion formula, we expand the union as follows:
Here, we have the following:
- -
- represents the area covered by edge-UAV i;
- -
- is the intersection area between edge-UAV i and edge-UAV j;
- -
- Higher-order intersections , and others, capture regions simultaneously covered by three or more edge-UAVs.
Algorithm 3 illustrates how to compute the total non-overlapping coverage area of multiple edge-UAVs. In practice, we implement the inclusion–exclusion principle up to triple overlaps (pairwise and triple intersections), which provides an accurate and computationally tractable estimate of the non-overlapping coverage.
| Algorithm 3 Non-overlapping coverage calculation. |
|
4.4. Integration of PSO-Based Methods with Our Proposed Models
In this section, the integration of our suggested Pareto-PSO for edge-UAV deployment is explained by contrasting it with two alternative PSO methods: Epsilon-constrained PSO and Weighted-sum PSO. These approaches vary in their strategies for computing the fitness function when dealing with numerous objectives. The are defined as follows:
- Epsilon-constrained PSO: In this implementation of the PSO meta-heuristic, we use a rotating primary objective while treating the other two objectives as constraints. We are interested in the first case of considering the maximization of the coverage area as the main objective to optimize and the minimization of both latency and energy consumption as constraints. Then, we switch to the other objectives by role. By doing this, we generate a series of single-objective optimization subproblems. In the basic concept of the Epsilon-constrained PSO method, we can sweep the epsilon value for each primary objective to increase the Pareto front of optimal solutions. In this study, a single value is used for each constraint to maintain a consistent computational framework across compared methods. The goal is to evaluate convergence and relative performance rather than to construct the complete Pareto front. The selected thresholds are empirically determined to reflect realistic and feasible operating conditions. A penalty is used to prevent the optimizer from favoring solutions that seem good in other objectives but violate practical constraints. Then, the PSO meta-heuristic is applied to the obtained fitness functions. Algorithm 4 illustrates how the Epsilon-constrained PSO handles and evaluates the fitness function by rotating the primary objectives.
| Algorithm 4 Fitness function definition for Epsilon-constrained PSO. |
|
- Weighted-sum PSO: In this implementation, an aggregate fitness is formed by assigning equal weights to the three objectives—maximizing coverage and minimizing latency and energy—thereby treating their importance as equal. In the Weighted-sum PSO implementation, equal weights (0.33, 0.33, 0.33) are assigned to the latency, energy, and coverage objectives to establish a balanced and unbiased baseline. The intention is to compare scalarization and Pareto-based strategies under uniform importance rather than to perform sensitivity analysis on weight tuning. The PSO metaheuristic is then applied to this scalarized objective. Algorithm 5 details how the Weighted-sum PSO evaluates a multi-objective formulation via scalarization.
| Algorithm 5 Fitness function definition for Weighted-sum PSO. |
|
- Pareto-PSO: In this implementation, the fitness is vector-valued and evaluated by Algorithm 6, combining latency, coverage, and energy so they are optimized simultaneously. Each edge-UAV independently executes a Pareto-PSO-based multi-objective routine on its dynamically assigned subset of GUs, yielding a decentralized, parallel set of optimizations rather than a single centralized swarm optimization. Each UAV produces a three-dimensional fitness vector (latency, coverage, energy) over its local service area.
| Algorithm 6 Fitness function definition for Pareto-PSO. |
|
Algorithm 7 implements a decentralized Pareto-based Particle Swarm Optimization (Pareto-PSO) for edge-UAV deployment. Each UAV executes an independent, locally informed PSO process in parallel with other UAVs. Although the architecture follows a decentralized and communication-light structure, it does not yet incorporate inter-UAV cooperation mechanisms typically seen in fully distributed systems. Therefore, the proposed framework is better characterized as a parallel decentralized optimization scheme rather than a fully cooperative distributed one. For each UAV, a local swarm of particles is initialized around its starting location, and each particle encodes a candidate 3D position. Fitness evaluation is performed using a vector of the three objectives. To guide particle movement, an archive of non-dominated solutions is maintained for each UAV. Leaders are selected via crowding distance: a leader is sampled from archive members with the largest crowding distance (least crowded region) to promote diversity; ties are broken at random, and boundary members retain maximal distance. Particle velocities and positions are then updated using classical cognitive and social terms, with fitness always treated as a vector, ensuring true Pareto dominance. Each UAV continues this local optimization until convergence, outputting its best position and associated fitness.
Crucially, our model incorporates user mobility by updating user positions at each iteration of the optimization. After UAVs reposition and users move, a dynamic user association is performed, where each user is attributed to the UAV providing the highest SINR, with explicit consideration of inter-UAV interference. This reassociation occurs iteratively in tandem with UAV position updates, ensuring users are consistently connected to the UAV offering the optimal link quality at each step. This adaptive mechanism helps mitigate the natural trade-off between maximizing coverage and minimizing latency by preventing users from being persistently served by UAVs with poor channel conditions or at long distances.
Once all UAVs converge, the selected positions are collected into bestPosMat. Total non-overlapping coverage is obtained by forming the union of coverage maps derived from bestPosMat, avoiding double counting. Global throughput is then computed once from bestPosMat under dynamic user association, where each user is attributed to the UAV providing the highest SINR while explicitly accounting for inter-UAV interference. In parallel, per-UAV archives are concatenated into a global swarm archive that approximates the system-level Pareto front with non-dominated solutions only and supports system-wide decision making. For each composition of UAV positions drawn from these archives, the aggregated non-overlapping coverage and total network latency are evaluated using dynamic user association and SINR-based reassignment, with interference explicitly considered. This post-processing step constructs a comprehensive set of multi-objective deployment scenarios, spanning a range of coverage and latency trade-offs.
| Algorithm 7 Decentralized Pareto-PSO for edge-UAV deployment. |
|
5. Performance Evaluation
To evaluate the performance of our proposed Pareto-PSO in comparison with other UAV deployment methods, we performed several simulations using MATLAB R2016a. The simulation parameters, selected after a series of experimental tests, are presented in Table 3. Our simulation parameters were chosen to reflect realistic UAV-assisted edge computing scenarios. Each UAV covered a circular area of radius m and operates in a 500 m-by-500 m square environment. The noise power spectral density was set to watts, while the transmission bandwidth B was explored at four levels, from 200 kHz up to 40 MHz. We studied networks with 5 to 25 edge-UAVs (numUAVs) and 50 to 250 GUs (numUsers). Each simulation used 12 particles over 50 iterations to optimize deployment. The system constraints included a maximum energy consumption of joules, a minimum coverage area of m2, and a latency threshold of s. Realistic power values were used for transmission ( W), processing ( W), travel ( W), and hovering ( W). The baseline PSO and Weighted-sum PSO parameters reported in Table 3 (, inertia , learning coefficients ) were chosen for two reasons: (1) they represent balanced trade-offs (equal weighting) suitable for rapid-deployment scenarios where no single objective should dominate initial decisions, and (2) the PSO coefficients follow widely accepted settings from the PSO literature that provide good convergence and maintain a balance between exploration and exploitation in swarm intelligence studies. The optimization framework utilizes a particle swarm algorithm with 12 particles and 50 iterations to maximize coverage, minimize latency, and optimize energy consumption while adhering to practical operational constraints. Our proposed Pareto-PSO for edge-UAV deployment was compared with two PSO-based methods—Weighted-sum PSO and Epsilon-constrained PSO—according to their achieved throughput, coverage area, and computational convergence time. This setup provides a clear and reproducible means to benchmark the impact of different multi-objective decision-making methods on the performance and efficiency of a UAV-based edge network.

Table 3.
Simulation parameters.
The simulation parameters were chosen according to standard UAV communication models and previous works [1,2,3,4,5,6,7,8,9,10].
Experimental Results
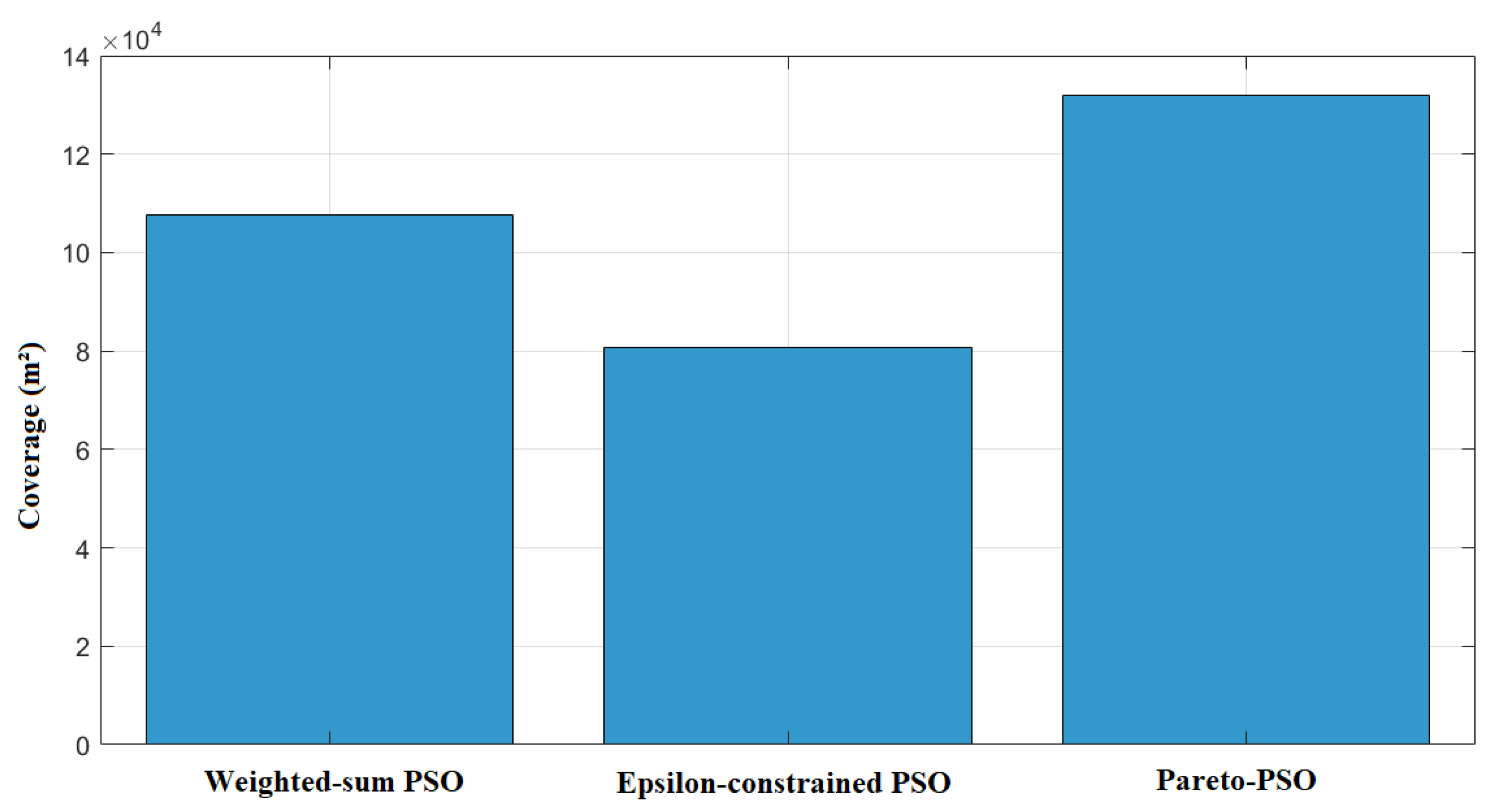
Figure 3 contrasts the total non-overlapping coverage areas attained by the three optimization strategies. Pareto-PSO achieved the largest covered footprint at approximately 131,862 m2, indicating that the search successfully identified frontier configurations that extend spatial reach while remaining acceptable on the accompanying objectives. Weighted-sum PSO followed with about 107,511 m2, which is consistent with scalarization that can approximate a coverage-oriented solution when the weighting scheme affords sufficient emphasis to the area component yet still moderates extremes due to the composite objective. Epsilon-constrained PSO yielded the smallest coverage at roughly 80,637 m2 under the reported thresholds, reflecting the restrictive effect of feasibility limits: when stringent latency or energy bounds are enforced, the feasible region excludes some coverage-maximizing placements, thereby reducing aggregate served area.
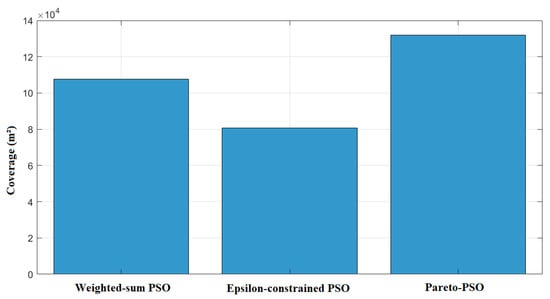
Figure 3.
Coverage comparison of our proposed Pareto-PSO, Weighted-sum PSO, and Epsilon-constrained PSO.
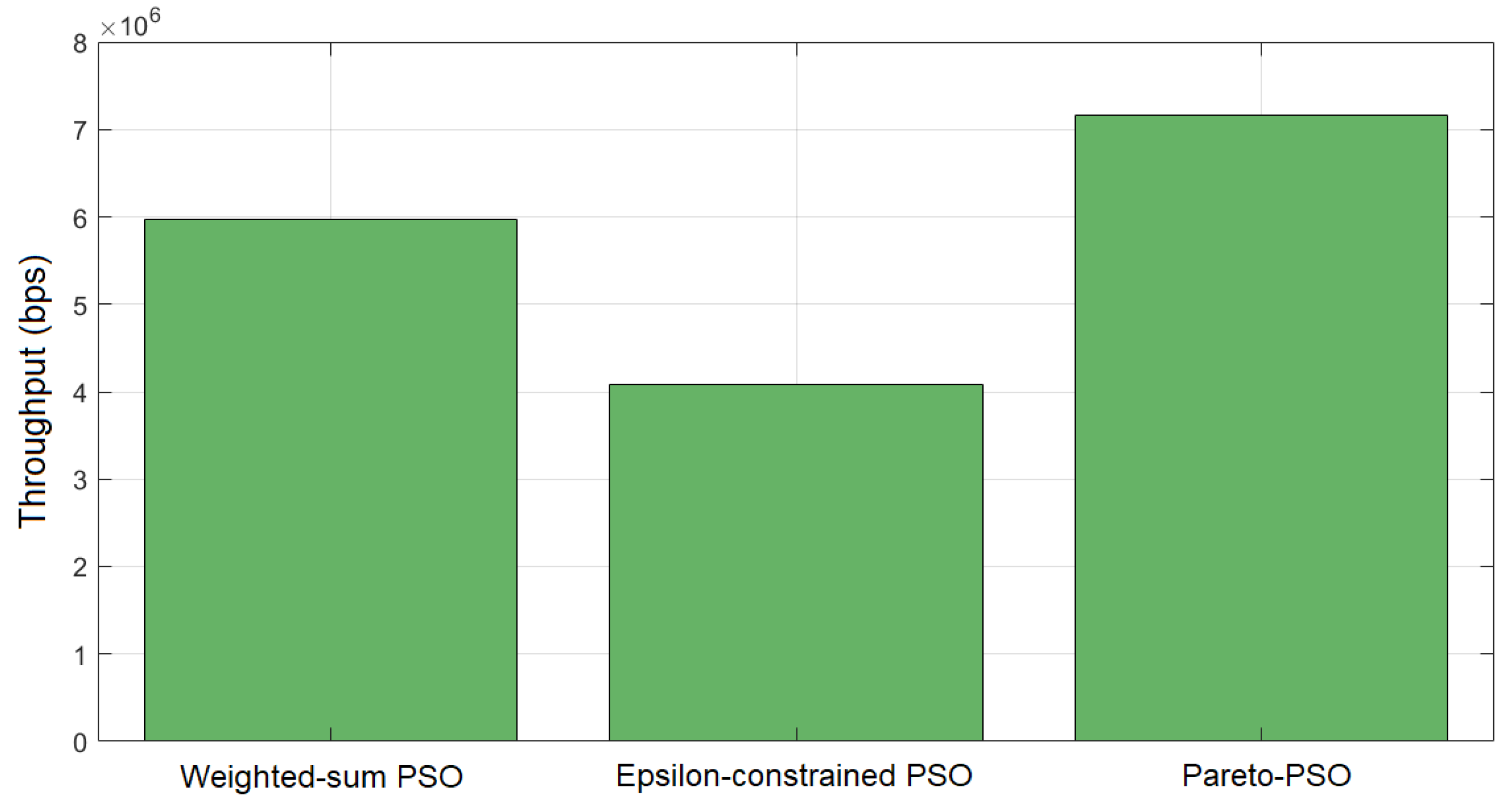
In terms of throughput, Figure 4 reports the aggregate throughput achieved by each method. Pareto-PSO attained the highest rate, approximately 7.16 Mb/s (megabits per second), which is consistent with selecting a non-dominated solution located near the rate-optimal edge of the frontier. Weighted-sum PSO reached about 5.97 Mb/s, reflecting the expected attenuation caused by simultaneous optimization of competing objectives under fixed weights; unless the scalarization heavily privileges throughput, the best scalar solution typically falls short of the extreme. Epsilon-constrained PSO returned the lowest throughput, around 4.08 Mb/s, which accords with feasibility-driven optimization: tighter bounds on latency and/or energy reduce access to high-throughput configurations, yielding compliant but less rate-intensive deployments.
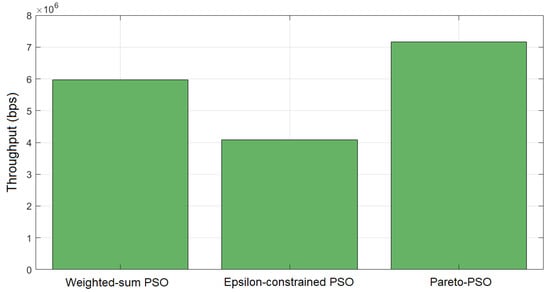
Figure 4.
Throughput comparison of our proposed Pareto-PSO, Weighted-sum PSO, and Epsilon-constrained PSO.
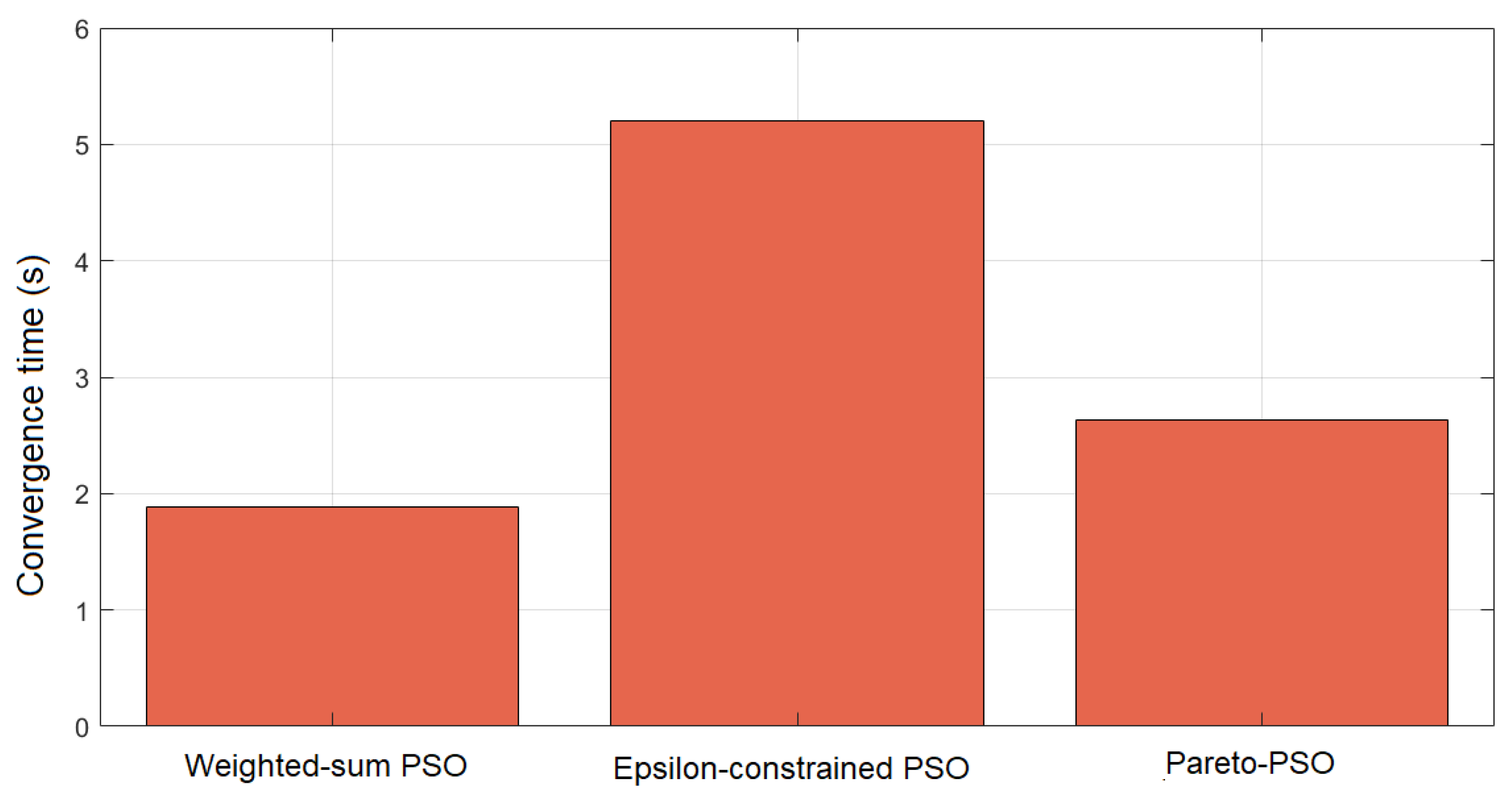
Figure 5 compares the convergence times across the three strategies for edge-UAV deployment. Weighted-sum PSO attained the shortest runtime at 1.769 s, underscoring the efficiency of scalarization. By reducing multiple objectives into a single scalar, the search becomes concentrated, decision overhead diminishes, and the swarm stabilizes rapidly. Pareto-PSO recorded an intermediate time of 2.600 s, which is consistent with the modest but necessary overhead of maintaining a non-dominated archive. Nevertheless, the archive’s elite solutions provide strong guidance, allowing the swarm to balance exploration and exploitation while converging within a reasonable time frame. The Epsilon-constrained PSO required the longest convergence time (5.134 s), reflecting the computational burden of feasibility screening and penalty enforcement. Each iteration must filter infeasible solutions and reorient the swarm toward admissible regions, increasing the evaluations needed before stabilization. While slower, this ensures strict compliance with system constraints.
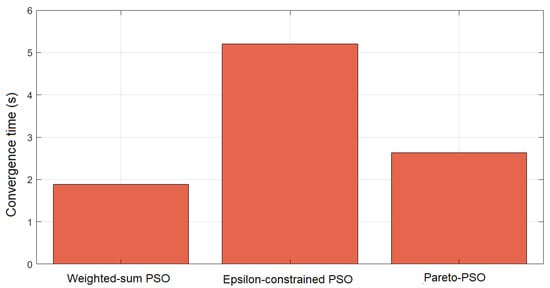
Figure 5.
Comparison of convergence times for the proposed Pareto-based PSO, the Weighted-Sum PSO, and the Epsilon-Constrained PSO.
The comparative results in Table 4 provide valuable insight into the behavior of Weighted-sum PSO (W_PSO), Epsilon-constrained PSO (Eps_PSO), and Pareto-PSO (P_PSO) under identical deployment conditions. The comparative results in these ten independent runs reveal clear performance distinctions among our proposed Pareto-PSO with the other PSO-based optimization methods for edge-UAV deployment. Regarding coverage, Pareto-PSO consistently achieved the highest values, ranking first in 10 out of 10 runs. This demonstrates its superiority in expanding non-overlapping UAV coverage and ensuring broader service areas. Weighted-sum PSO also performed competitively, with several runs showing near parity with Pareto-PSO (e.g., Runs 2 and 10), highlighting its stability in preserving spatial reach. In contrast, Epsilon-constrained PSO systematically yielded the lowest coverage values, which reflects its conservative optimization approach under strict feasibility constraints. The trade-off becomes more apparent when throughput is analyzed. Pareto-PSO clearly dominated this metric across 9 out of 10 runs, with values reaching up to (Run 6), thereby confirming its effectiveness in directing UAVs toward high-demand regions and maximizing data transmission rates. Weighted-sum PSO maintained intermediate throughput levels, averaging around , while Epsilon-constrained PSO lagged behind, rarely exceeding . These observations confirm that Pareto-PSO prioritizes throughput maximization without sacrificing robustness in convergence. Overall, the evidence indicates that Pareto PSO offers the best compromise, combining high coverage, superior throughput, and moderate convergence times. Weighted-sum PSO remains attractive when speed is critical but sacrifices optimality, whereas Epsilon-constraint PSO provides strict feasibility but at the cost of both performance and efficiency. Finally, the convergence time reveals another layer of differentiation. Weighted-sum PSO proved to be the fastest across nearly all runs, with an average convergence time of ∼1.2 s, reflecting its computational simplicity and speed. Pareto-PSO, though slightly slower (∼1.7 s on average), yielded a difference that is not significant, and it still achieved a very satisfactory time and a balanced trade-off by exploring a wider solution space while still converging much faster than Epsilon-constrained PSO. The latter remained the slowest, requiring more than 3 s in all runs due to its constraint-handling overhead. These findings align with the theoretical expectation that Pareto-based optimization methods excel at balancing multiple objectives simultaneously, producing superior throughput and competitive coverage, while maintaining reasonable computational efficiency compared to more rigid approaches.

Table 4.
Performance comparison of Weighted-sum PSO, Epsilon-constraint PSO, and Pareto-based PSO across 10 runs.
To assess robustness, we computed 95% confidence intervals (CIs) for the coverage, throughput, and convergence time across ten runs. Table 5 shows that Pareto-PSO clearly dominated by achieving both the highest coverage and the highest throughput ( Mb/s, CI ), with consistent improvements over Weighted-sum and Epsilon-constrained PSO. Although Weighted-sum PSO converged faster, its coverage and throughput remained significantly lower. These results confirm that Pareto-PSO provides the most effective trade-off, ensuring superior coverage and reliable data-rate performance.

Table 5.
Mean and 95% confidence intervals (CIs) for coverage, throughput, and convergence time over 10 runs.
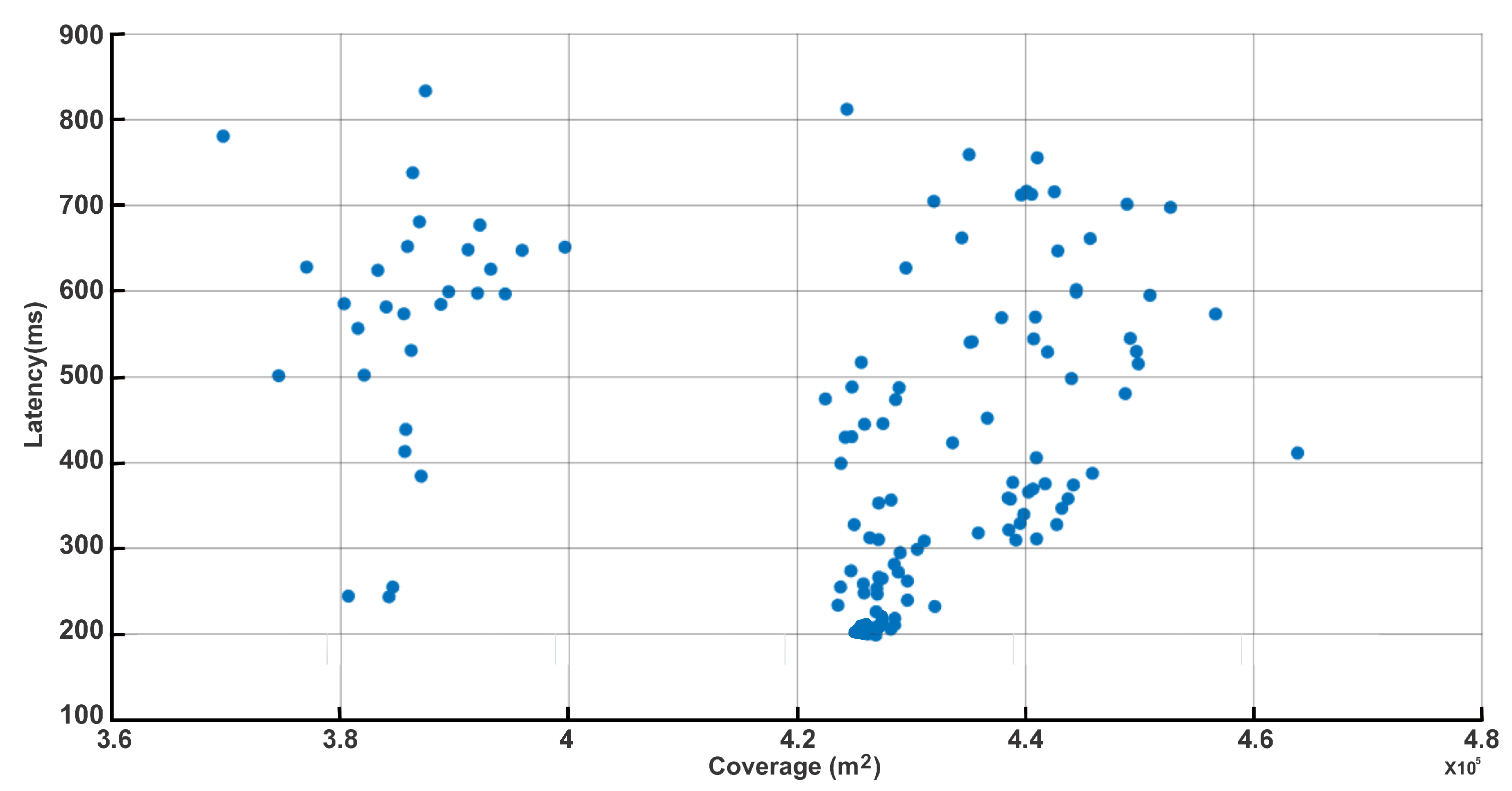
The resulting Pareto front, shown in Figure 6, presents a robust and quantitative portrayal of the fundamental trade-off achieved by our decentralized edge-UAV swarm optimization. This front reveals a spectrum of optimal solutions in which maximizing coverage ( to ) necessarily incurs higher latency values, sometimes reaching 800 ms, as UAVs must disperse to serve a wider area—thereby increasing communication distances and path delays. At the opposite end, deployments clustering UAVs nearer to user hotspots yield much lower latencies (as low as 200 ms) but must sacrifice total coverage. Crucially, the spread and diversity of the Pareto front vividly demonstrate that our algorithm effectively discovers a broad set of non-dominated trade-offs, capturing realistic system-level deployment scenarios aligned with practical needs and constraints. This diversity—distinct clusters and wide latency range—directly validates the flexibility and adaptability of our approach, letting system designers select deployments perfectly matched to specific operational priorities, whether for rapid response or maximal user reach. By presenting only non-dominated, genuinely optimal points, Figure 6 and Table 6 provide transparent, actionable guidance for UAV swarm planning and directly address the reviewer’s request for rigorous multi-objective analysis. The strength of the methodology is further highlighted by the absence of redundant or inferior configurations, ensuring every point on the front reflects a true performance compromise suitable for practical implementation.
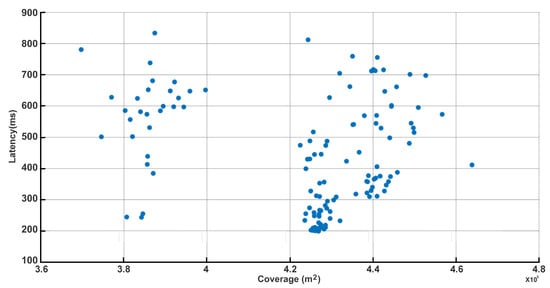
Figure 6.
Pareto trade-off: coverage vs. latency.

Table 6.
Pareto set of non-dominated solution coverage and latency results at the swarm-level.
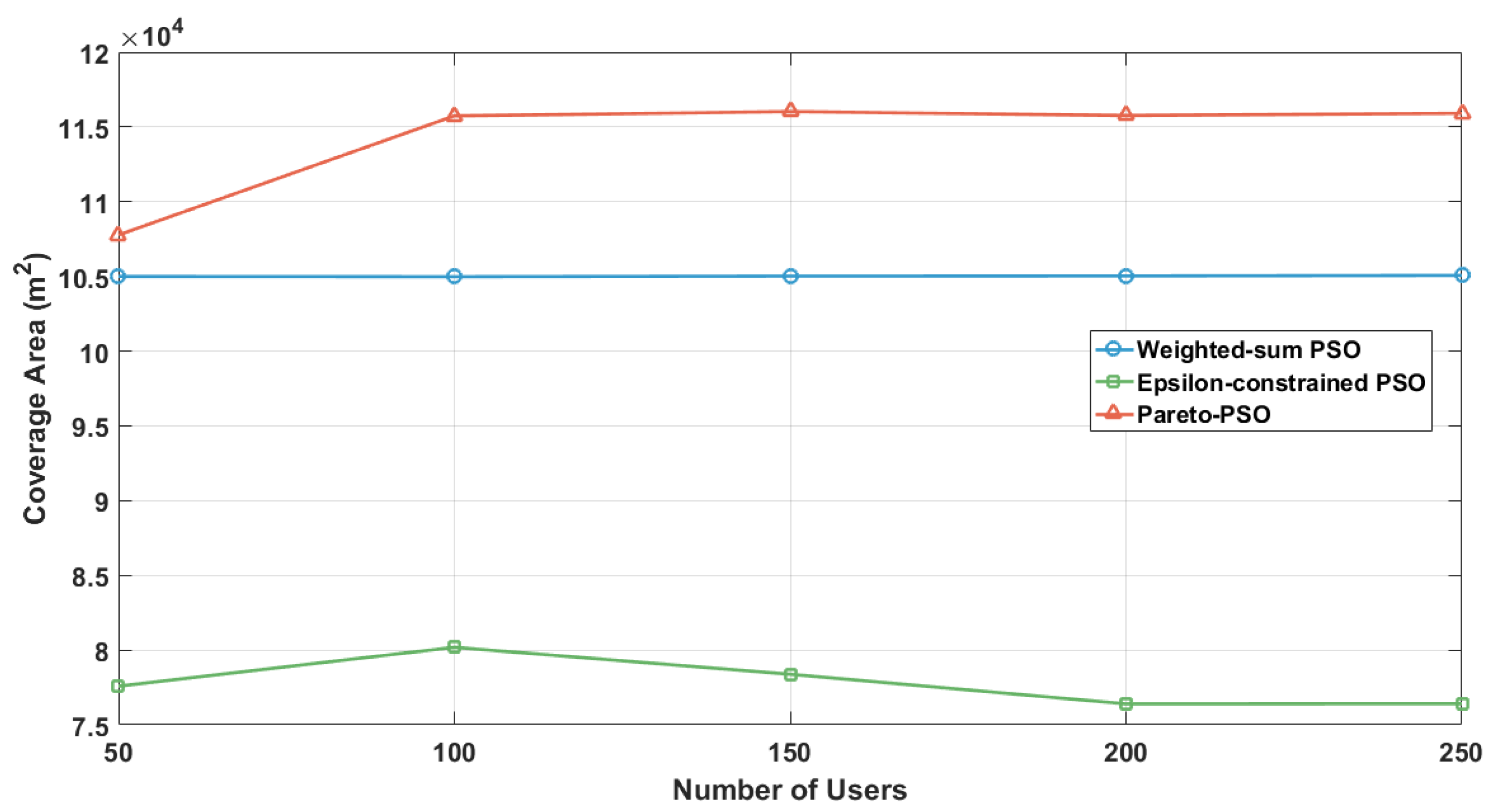
Figure 7 examines the evolution of non-overlapping coverage as the user density increased across the three multi-objective strategies: Weighted-sum PSO, Epsilon-constrained PSO, and Pareto-PSO. The trajectories reveal a consistent hierarchy: Pareto-PSO achieved the largest coverage envelope at all load levels, increasing from approximately at 50 users to about between 100 and 250 users. In contrast, the Weighted-sum PSO curve remained nearly flat at around , while the Epsilon-constrained PSO started lower (about at 50 users), showed a temporary improvement at 100 users, but then declined to approximately by 200–250 users. Overall, the results suggest that Pareto-PSO delivers the most robust coverage under varying demand, Weighted-sum PSO provides stable but less adaptive performance, and Epsilon-constrained PSO requires density-aware tuning of its feasibility schedule to mitigate coverage erosion as user density grows.
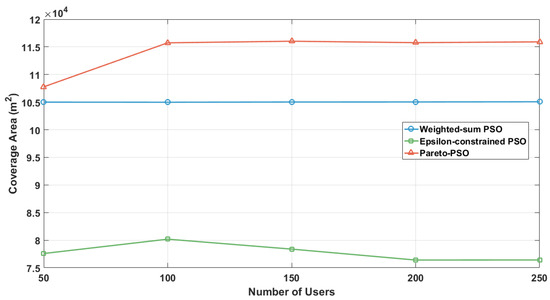
Figure 7.
Users number influence on coverage area.
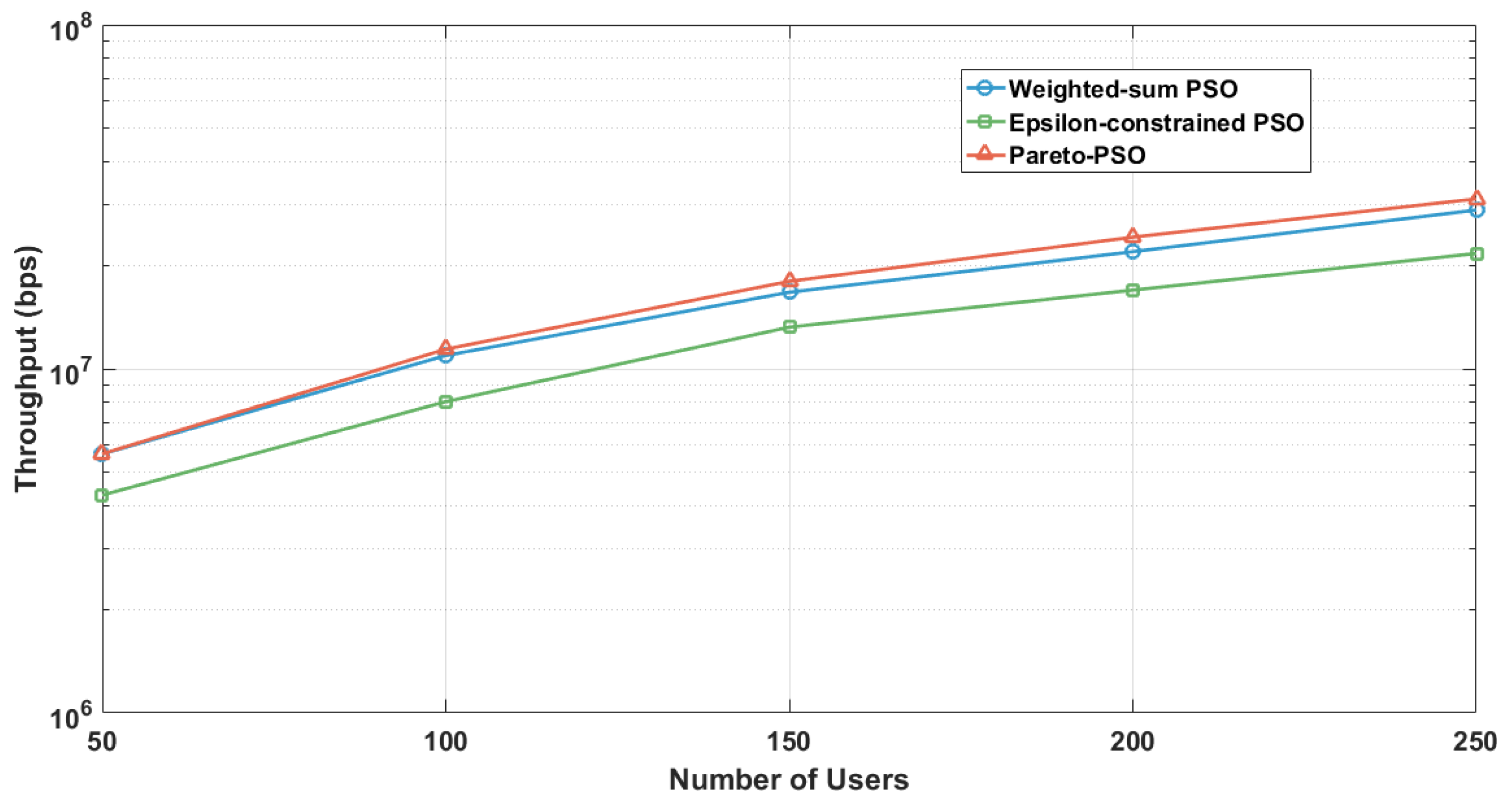
Figure 8 presents the aggregate throughput as a function of user density across the three optimization strategies under the edge-UAV deployment scenario for data collection. Pareto-PSO consistently defined the upper performance envelope, increasing from approximately 5–6 Mb/s at 50 users to about 35–40 Mb/s at 250 users. Weighted-sum PSO closely paralleled this trend but remained marginally lower at all densities (e.g., 11–12 Mb/s versus 12–13 Mb/s at 100 users and roughly 30–35 Mb/s versus 35–40 Mb/s at 250 users). In contrast, Epsilon-constrained PSO exhibited steady improvement yet remained consistently below the other methods (e.g., 7–8 Mb/s at 100 users and 20–25 Mb/s at 250 users), reflecting the restrictive influence of feasibility enforcement at higher loads. Overall, these findings underscore that Pareto-PSO’s ability to preserve a diverse non-dominated set facilitates the rediscovery of high-throughput layouts under varying interference.
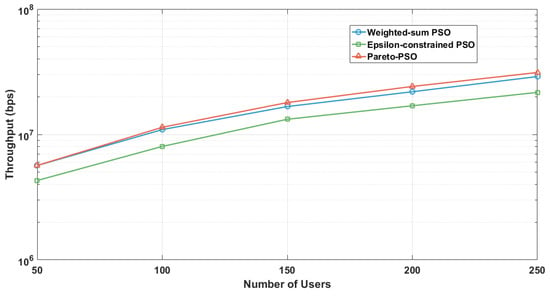
Figure 8.
Users number influence on throughput.
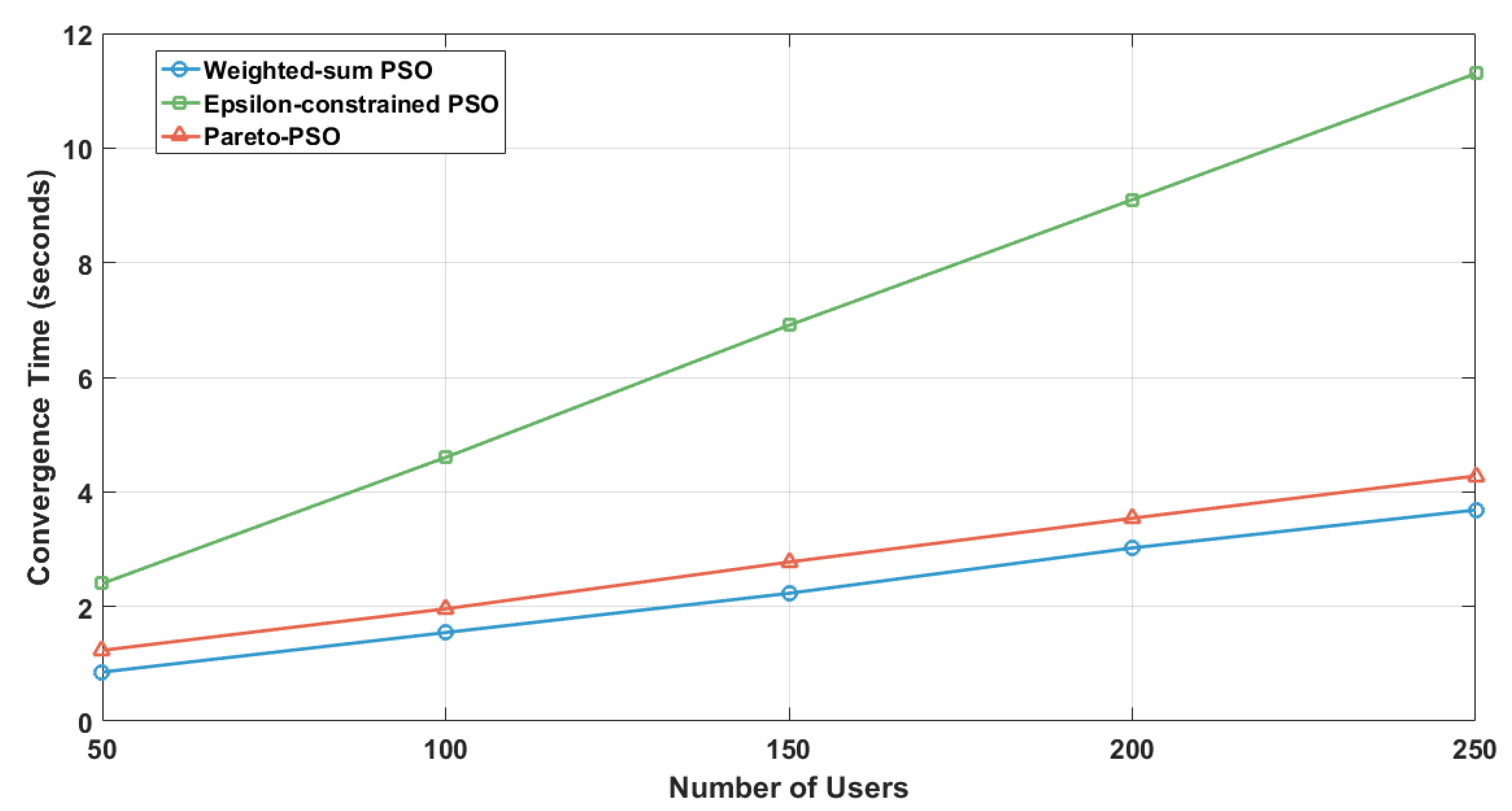
Figure 9 illustrates convergence time as a function of user density for the three optimization strategies. Weighted-sum PSO achieved the fastest convergence, starting at under 1 s with 50 users and rising gradually to about 4 s at 250 users. Pareto-PSO required slightly more time, beginning near 1.2 s and increasing steadily to approximately 4.5 s by 250 users, reflecting the additional computational effort of maintaining and updating a Pareto front. In contrast, Epsilon-constrained PSO showed the slowest performance, with convergence times escalating from around 2.5 s at 50 users to over 11 s at 250 users, indicating that its feasibility checks and repair mechanisms introduce significant overhead as load grows.
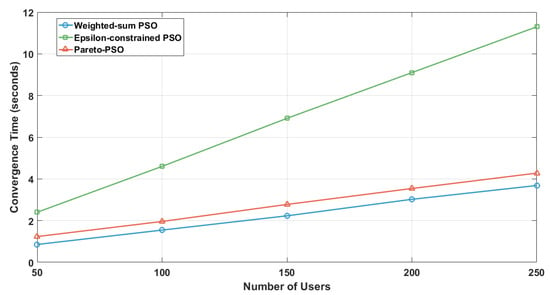
Figure 9.
Users number influence on convergence time.
Taken together, these results highlight a trade-off between solution quality and computational efficiency. Weighted-sum PSO converges quickly but risks reduced adaptability, Pareto-PSO balances slightly higher computational cost with robust adaptability and superior coverage/throughput performance, and Epsilon-constrained PSO, while theoretically precise in enforcing feasibility, suffers from substantial computational overhead under higher user densities.
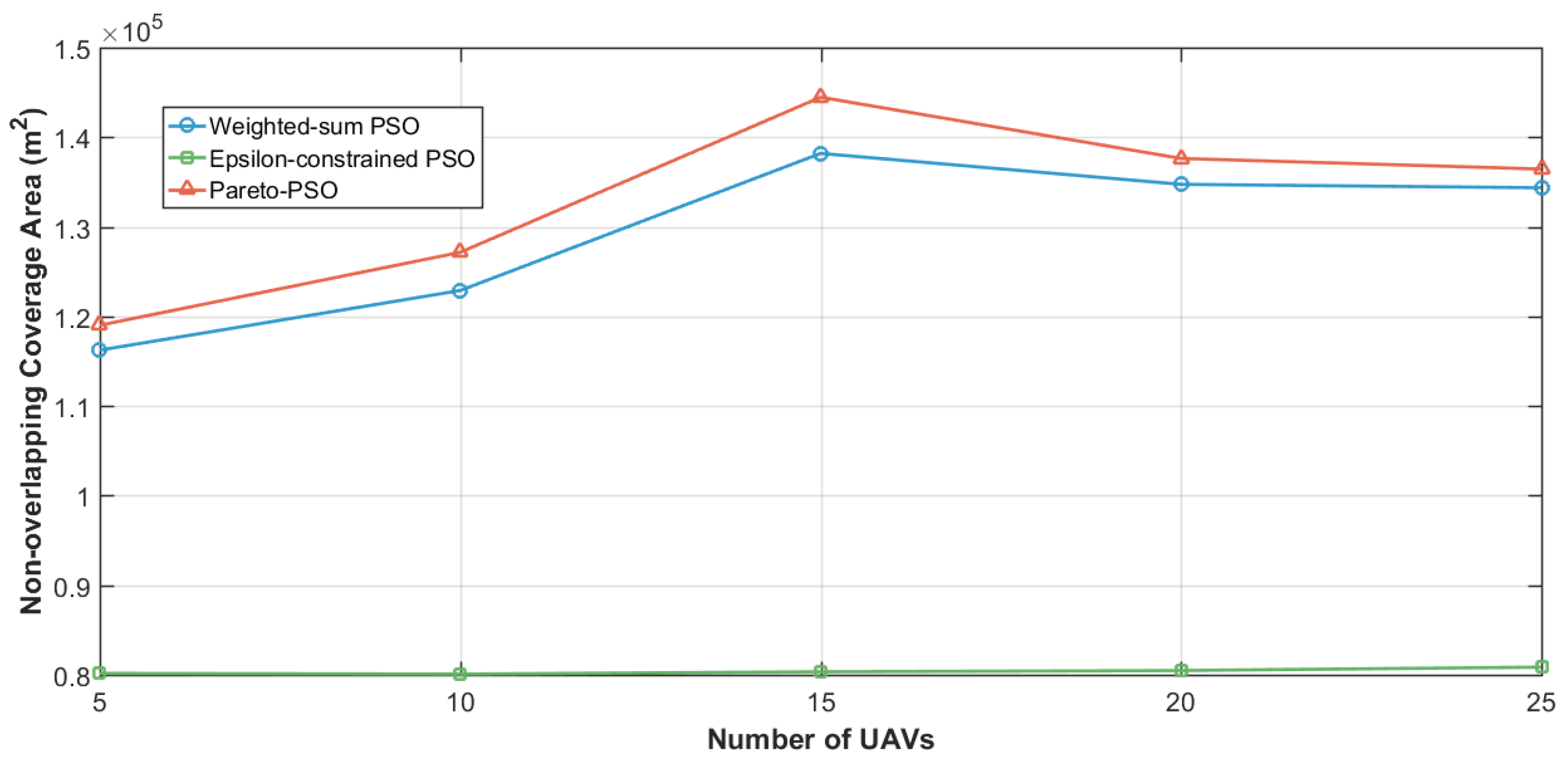
Figure 10 illustrates the scalability of non-overlapping coverage as the swarm size increased from 5 to 25 edge-UAVs. Both Pareto-PSO and Weighted-sum PSO exhibited strong coverage expansion up to around 15 UAVs, achieving peak values of approximately and , respectively. Beyond this point, coverage slightly declined due to overlapping service regions and interference effects at higher densities. By contrast, Epsilon-constrained PSO remained nearly flat around across all swarm sizes. Overall, the results confirm that Pareto-PSO consistently discovers the largest non-overlapping coverage envelope.
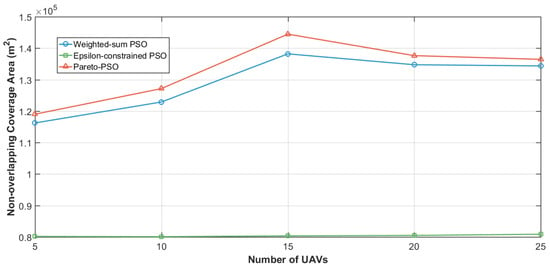
Figure 10.
Edge-UAVs number influence on non-overlapping coverage area.
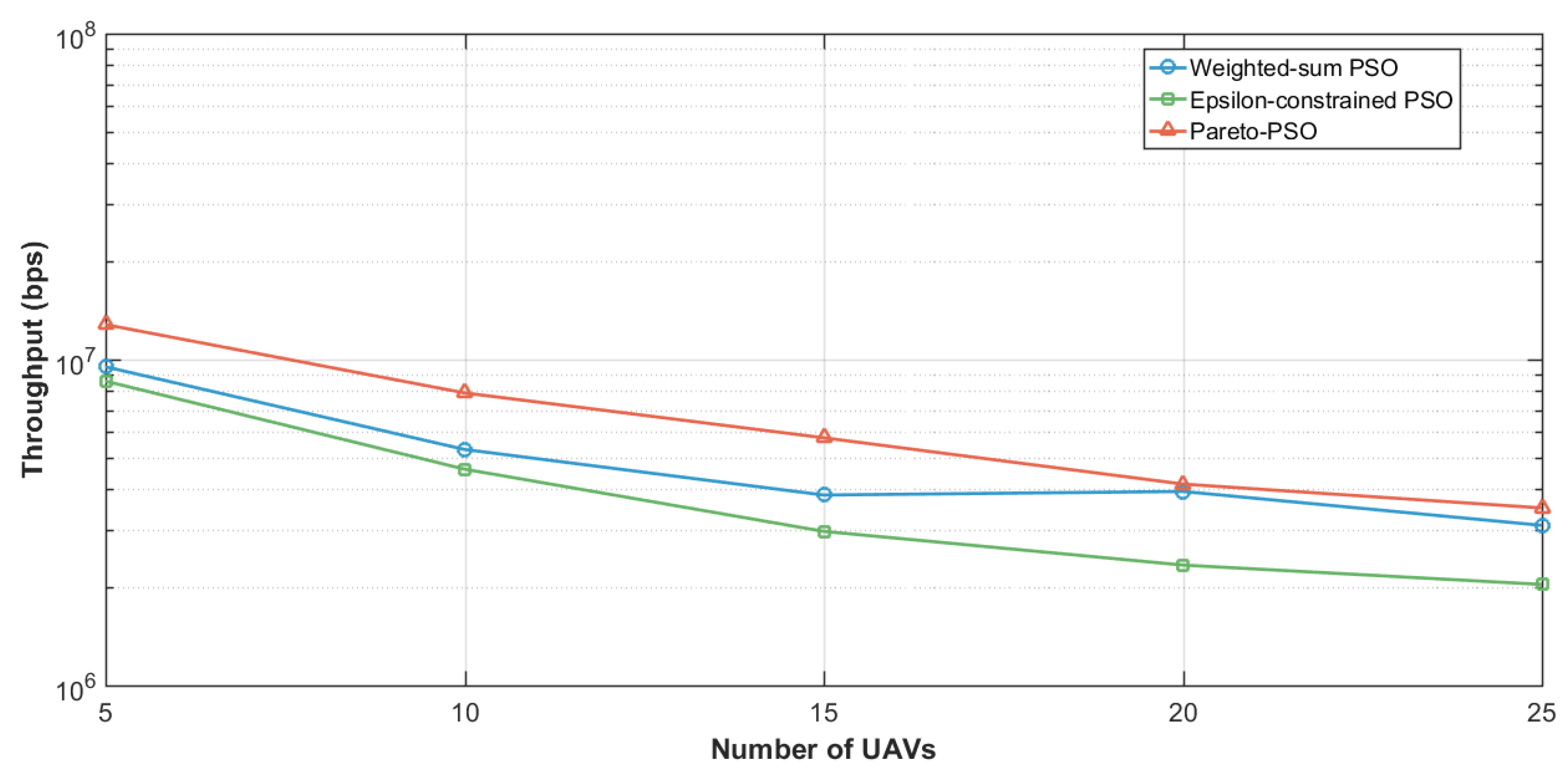
Figure 11 analyzes the total network throughput as the number of edge-UAVs deployed increased, comparing the performance of Weighted-PSO, Epsilon-constrained PSO, and Pareto-PSO. The results demonstrate that aggregate throughput declines as the number of UAVs increases, reflecting the adverse impact of inter-UAV interference and bandwidth partitioning at higher swarm densities. At five UAVs, all strategies achieved relatively high rates, with Pareto-PSO clearly leading, followed closely by Weighted-sum PSO, while Epsilon-constrained PSO trailed behind. As the swarm size scaled to 10–25 UAVs, the throughput decreased almost monotonically across all approaches, indicating that additional UAVs introduce co-channel contention and resource splitting that reduce the achievable SINR and, consequently, the overall throughput. Despite this decline, Pareto-PSO consistently outperformed the other methods, suggesting that its non-dominated search mechanism reliably identifies deployment geometries and power–altitude trade-offs that mitigate interference effects. In contrast, the Epsilon-constrained PSO remained the lowest performer throughout.
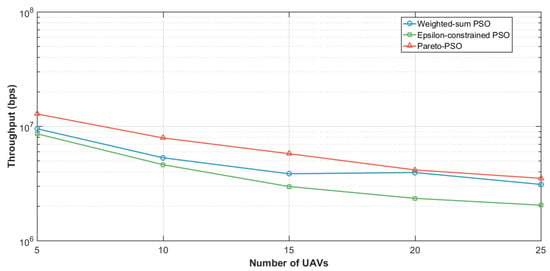
Figure 11.
Edge-UAVs number influence on throughput (log Scale Y-Axis).
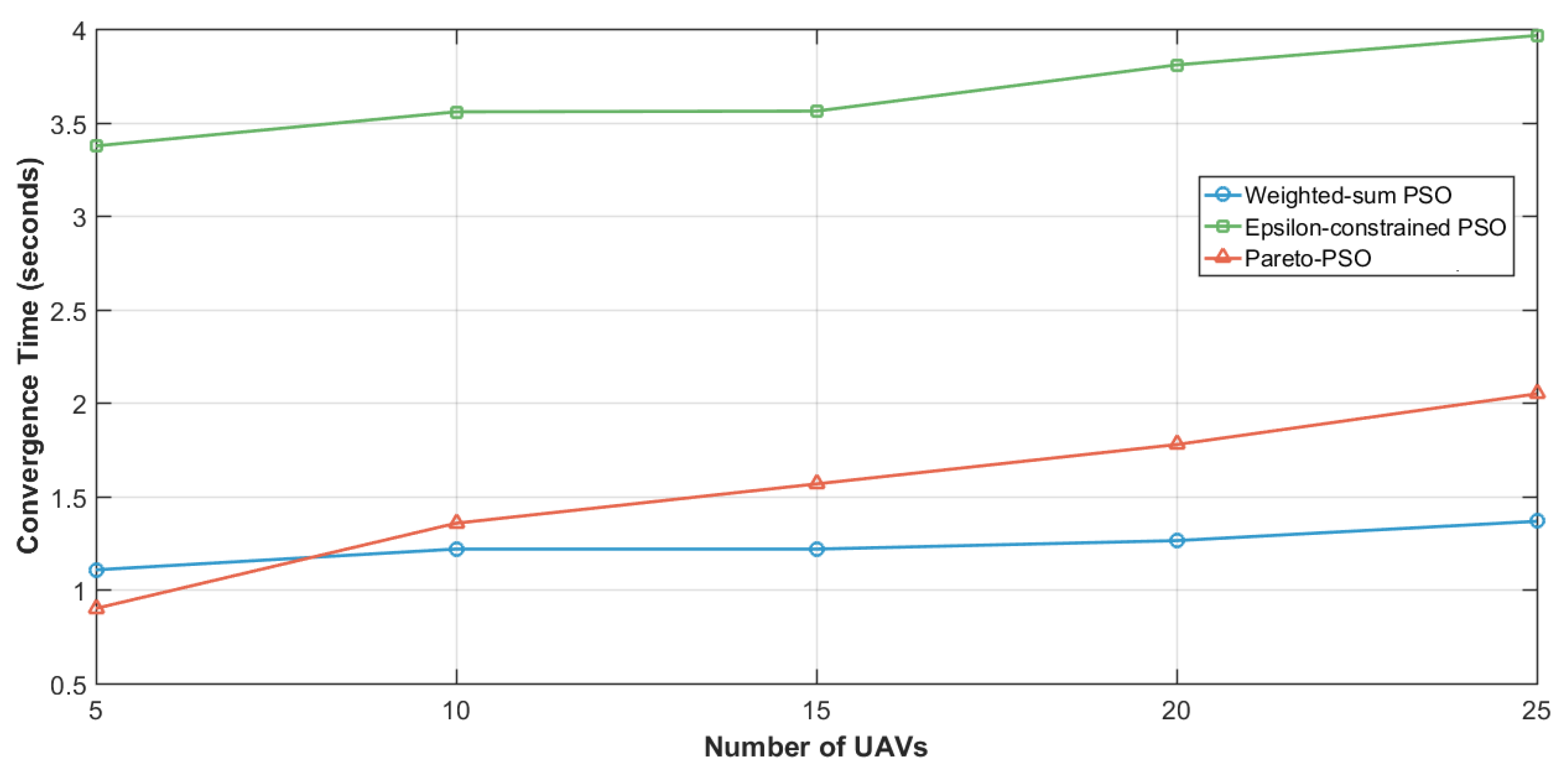
Figure 12 quantifies the scalability of convergence time as the number of UAVs increased from 5 to 25. The Weighted-sum PSO exhibited the lowest sensitivity to swarm size, with its runtime increasing only slightly from about 1.1 s at 5 UAVs to around 1.35 s at 25 UAVs. Pareto-PSO showed a moderate growth trend, rising from roughly 0.9 s at 5 UAVs to just above 2.0 s at 25 UAVs, reflecting the added computational cost of archive maintenance and leader selection as dimensionality expands. By contrast, the Epsilon-constrained PSO consistently reported the highest runtimes, ranging from about 3.35 s at 5 UAVs to nearly 4.0 s at 25 UAVs. Although Pareto-PSO requires slightly higher convergence time compared to Weighted-sum PSO, the difference is not significant, and it still achieves convergence within a very satisfactory time frame. This indicates that Pareto-PSO maintains both robustness and efficiency while providing a richer set of trade-off solutions.
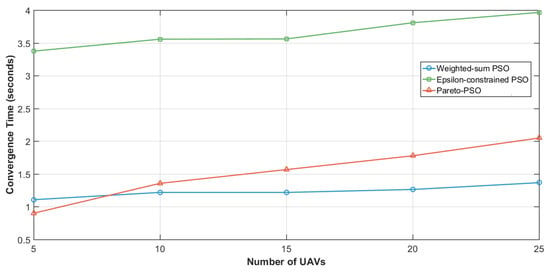
Figure 12.
Edge-UAVs number influence on convergence time.
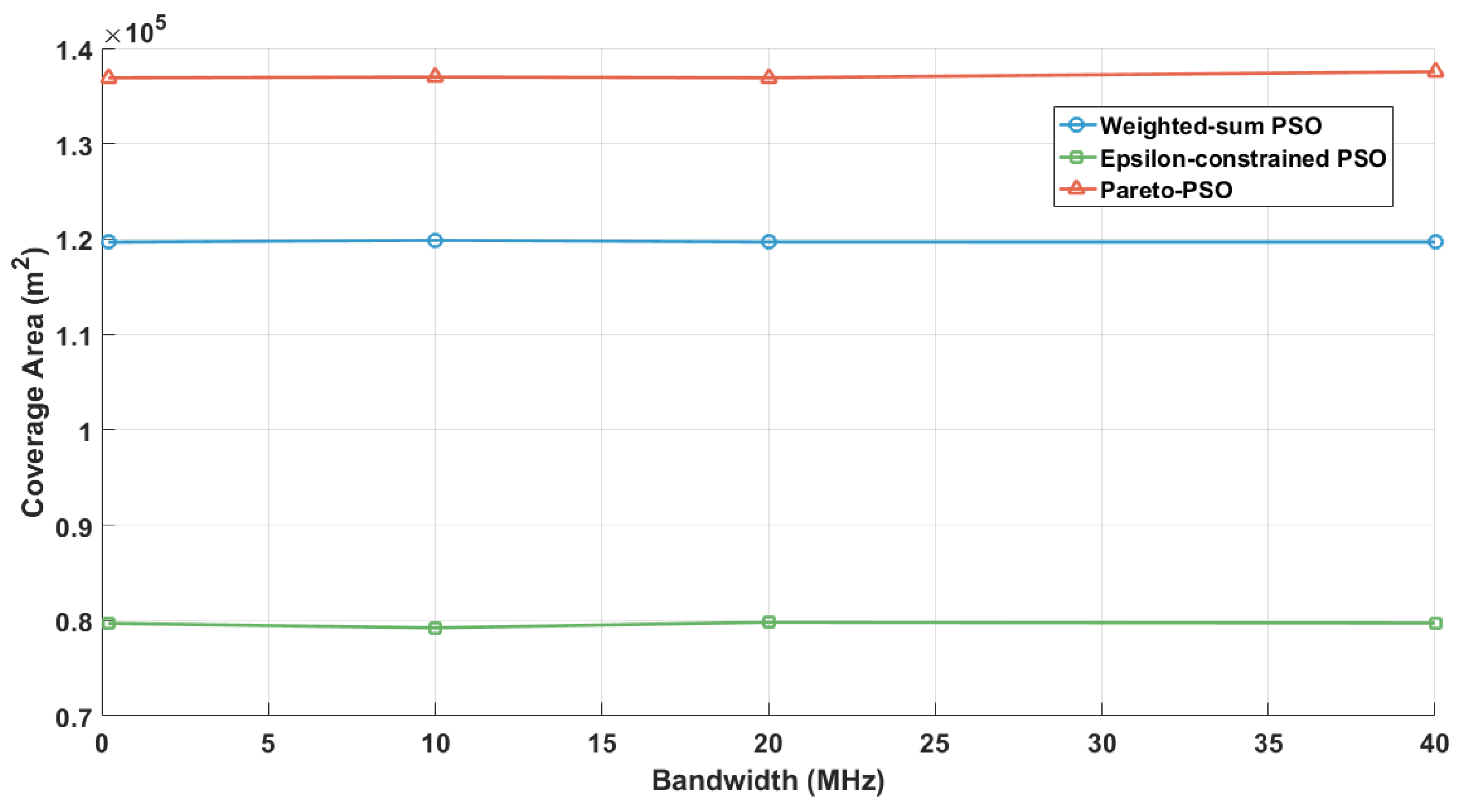
Figure 13 examines the impact of system bandwidth on the achievable non-overlapping coverage for the three optimization strategies. Across the examined range (200 kHz–40 MHz), all curves are nearly flat. This indicates that coverage in the studied system is determined by UAV geometry and line-of-sight conditions rather than spectral width. Among the strategies, Pareto-PSO achieved the highest coverage (≈), Weighted-sum PSO performed slightly lower (≈), and Epsilon-constrained PSO remained significantly smaller (≈). The flat trend across all curves confirms that bandwidth allocation affects throughput but does not expand the physical coverage footprint. Thus, improving coverage should rely on UAV deployment policies such as placement, altitude optimization, and interference management, while bandwidth should be tuned primarily for data rate objectives.
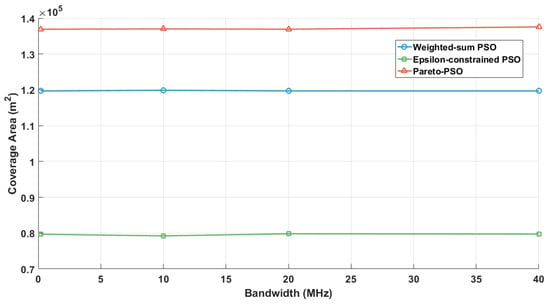
Figure 13.
Bandwidth influence on coverage area.
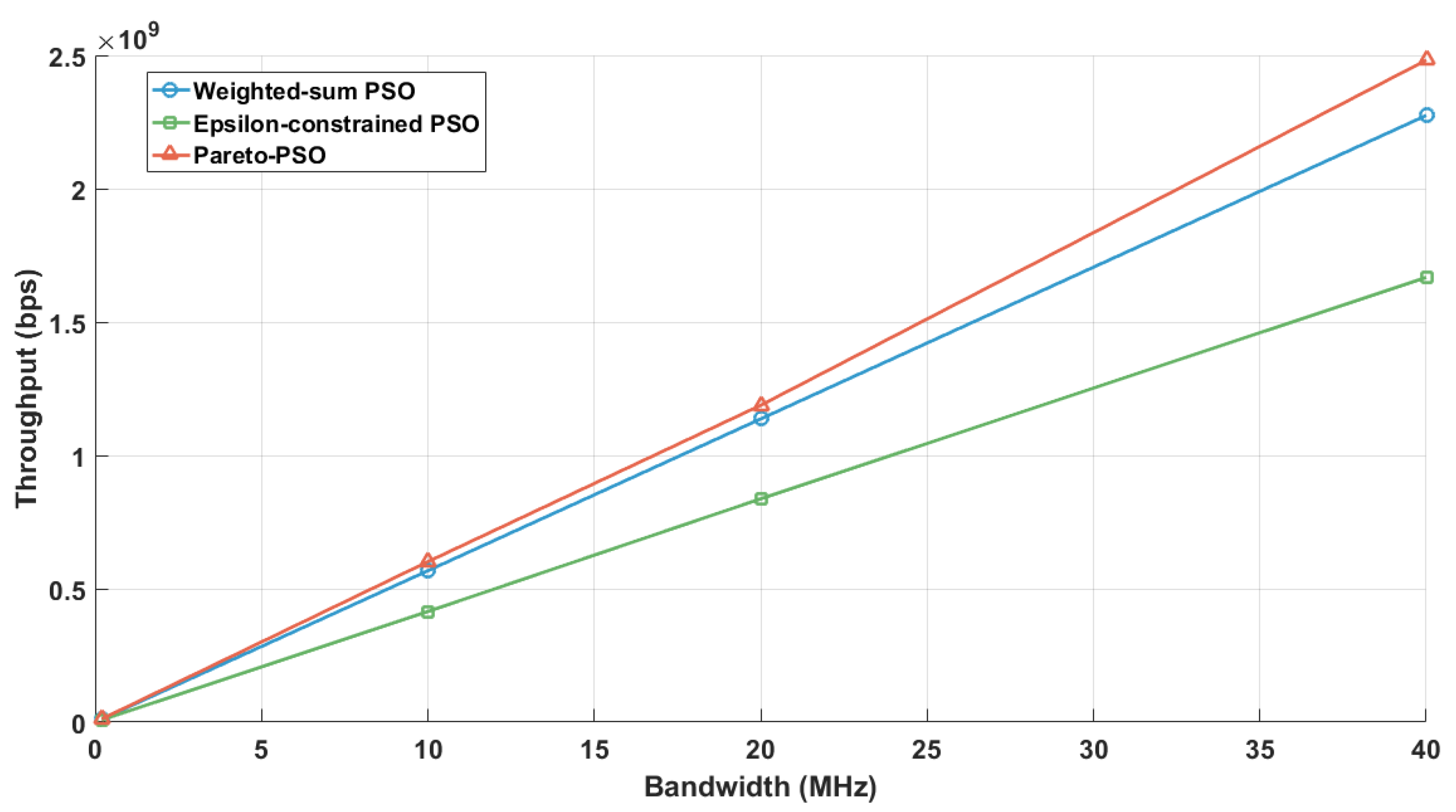
Figure 14 depicts a near-linear scaling of the aggregate throughput with bandwidth from 10 to 40 MHz, which is a behavior consistent with a capacity increasing proportionally to the system bandwidth under approximately stable SINR conditions. Pareto-PSO consistently formed the upper envelope, demonstrating superior SINR exploitation and spectrum efficiency. Weighted-sum PSO tracked closely but remained below due to scalarization trade-offs, while Epsilon-constrained PSO lagged, as its feasibility limits restrict aggressive rate maximization. Overall, Pareto-PSO delivered the highest throughput across all bandwidths and achieved steeper scaling, making it the most effective strategy when spectrum expansion is key.
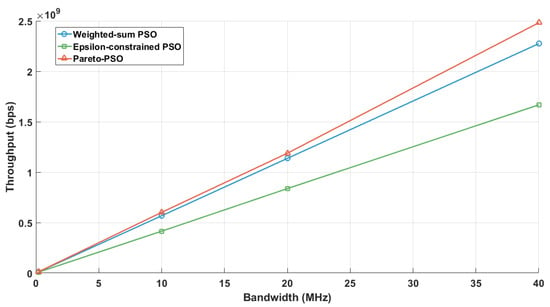
Figure 14.
Bandwidth influence on throughput.
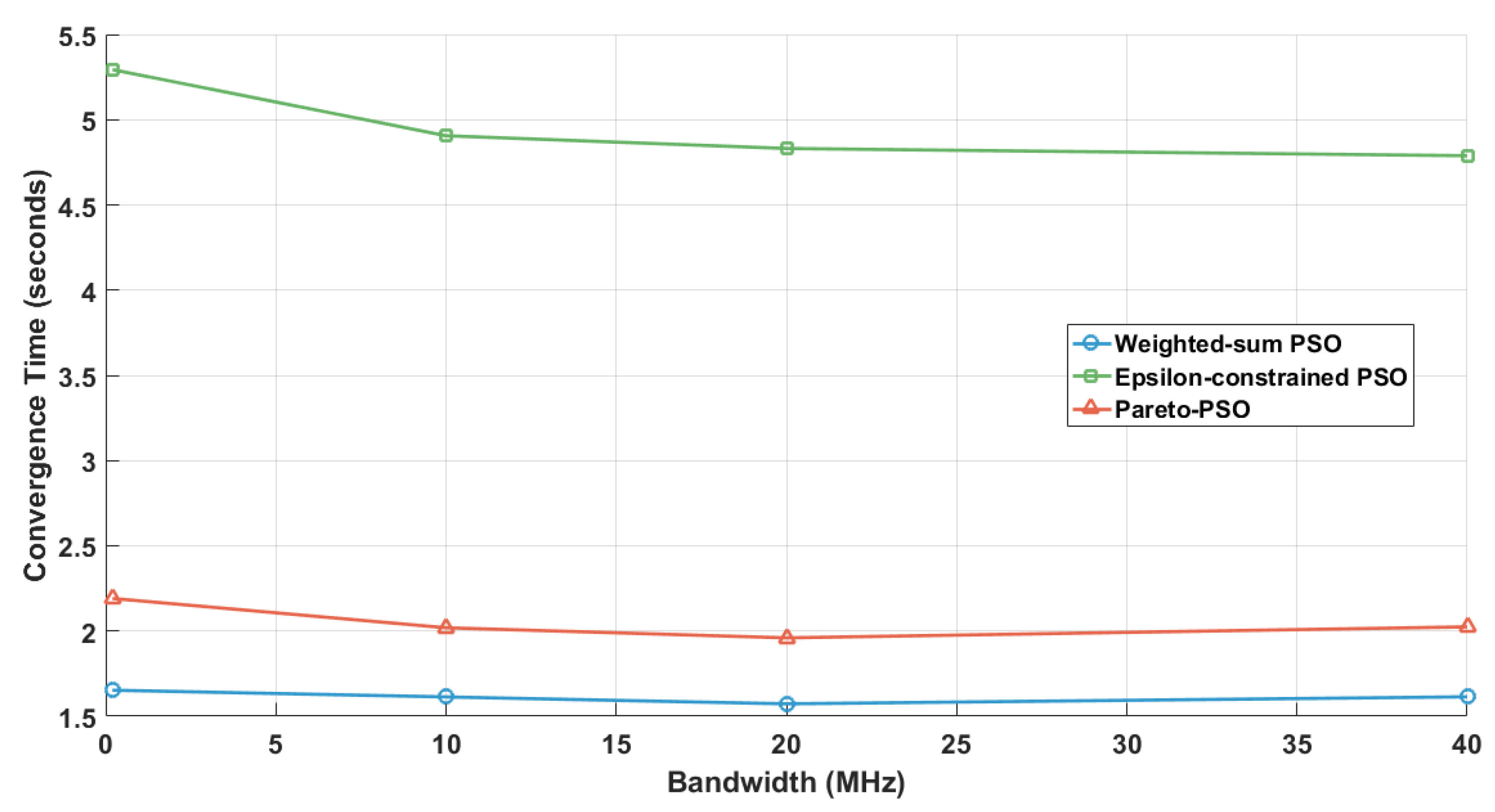
Figure 15 examines solver runtime as a function of bandwidth across 200 kHz–40 MHz, while the number of edge-UAVs was fixed at five, and number of GUs was fixed at 200. Weighted-sum PSO was the fastest and nearly bandwidth-insensitive, fluctuating around 1.6 s, which is consistent with scalar optimization’s minimal overhead. Pareto-PSO showed a shallow U-shape: its runtime decreased from about 2.2 s at 0 MHz to 2.0 s near 20 MHz and then stabilized slightly above 2.0 s, reflecting smoother rate feedback balanced by archive management costs. Epsilon-constrained PSO recorded the highest runtimes but declined from 5.3 s to 4.8 s, indicating that higher bandwidth relaxes feasibility pressure and reduces search effort.
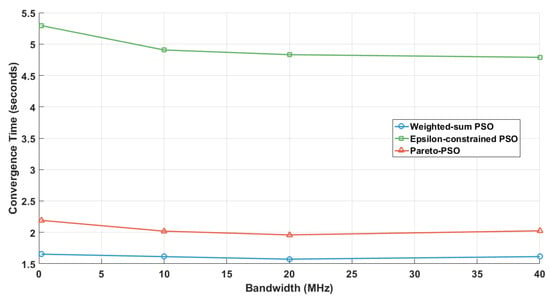
Figure 15.
Bandwidth influence on convergence time.
6. Conclusions and Future Work
In this paper, we proposed the use of Pareto-based PSO to optimize edge-UAV deployment in the Internet of Flying Things (IoFT). This study demonstrated that the governing factor in edge-UAV deployment performance is the way multiple objectives are mapped into the optimization landscape. By preserving coverage, latency, and energy as a vector of concurrent, non-commensurate objectives, the Pareto-based PSO constructs and maintains a rich frontier that consistently delivers the largest non-overlapping coverage envelope and the highest aggregate throughput across bandwidth levels while sustaining scalable—though moderate—convergence times as swarm size grows. In contrast, fixed scalarization in the Weighted-sum PSO collapses the frontier into a single surrogate objective: this ensures the fastest runtime but systematically tempers extreme gains in coverage and rate whenever the weights diverge from the local frontier geometry. The Epsilon-constrained PSO guarantees explicit feasibility, yet its penalty-driven updates and screening overhead slow convergence and restrict the exploration of aggressively rate-maximizing placements, resulting in weaker throughput. Collectively, these findings confirm that vectorization transforms the optimizer into a frontier builder and selector—retaining decision flexibility for latency-sensitive and energy-aware IoFT deployments—whereas scalarization limits the search to single-point compromises. Consequently, Pareto-PSO emerged as the most effective and reliable strategy for real-time multi-objective edge-UAV deployment, striking a practical balance between throughput leadership, coverage maximization, and acceptable computational cost.
As future work, we aim to compare our proposed Pareto-PSO approach with other multi-objective optimization meta-heuristics, such as genetic algorithms for edge-UAV deployment in IoFT. We will also focus on extending the current decentralized framework into a cooperative distributed model, enabling UAVs to exchange partial solutions and collectively refine global decisions in real time. Future extensions will incorporate resilience tests against UAV loss, link degradation, and environmental perturbations to further validate system reliability. We intend to extend the proposed framework by integrating modern parallel access techniques such as Orthogonal Frequency Division Multiple Access (OFDMA) and other advanced resource allocation mechanisms. These enhancements will allow the model to better capture concurrent data receptions, reduce latency estimates, and improve the framework’s alignment with current UAV communication standards. Incorporating these techniques will also enable a more comprehensive evaluation of network throughput and interference interactions in multi-UAV environments. We will explore the effect of varying weight configurations in the Weighted-sum PSO to evaluate sensitivity and robustness across different priority scenarios, enabling a fairer and more comprehensive comparison of scalarized versus Pareto-based methods. Finally, we will also extend the -constrained PSO implementation by sweeping multiple values to generate a richer Pareto front, allowing us to assess the trade-offs between coverage, latency, and energy consumption.
Author Contributions
Conceptualization, S.Z. (Sabrina Zerrougui) and S.Z. (Sofiane Zaidi); methodology, S.Z. (Sabrina Zerrougui); software, C.T.C.; validation, S.Z. (Sabrina Zerrougui), S.Z. (Sofiane Zaidi), and C.T.C.; formal analysis, S.Z. (Sabrina Zerrougui); investigation, S.Z. (Sofiane Zaidi); resources, C.T.C.; data curation, C.T.C.; writing—original draft preparation, S.Z. (Sabrina Zerrougui) and S.Z. (Sofiane Zaidi); writing—review and editing, C.T.C.; visualization, C.T.C.; supervision, S.Z. (Sofiane Zaidi); project administration, S.Z. (Sofiane Zaidi); funding acquisition, C.T.C. All authors have read and agreed to the published version of the manuscript.
Funding
This work was partially funded by the EU project REMARKABLE (Grant agreement ID: 101086387), under the program HORIZON-MSCA-2021-SE-01-01, by the project CIPROM/2023/29, which is funded by “Direcció General de Ciència i Investigació”, Generalitat Valenciana, Spain, by R&D project PID2021-122580NB-I00, from MICIU/AEI/10.13039/501100011033, and “ERDF A way of making Europe”.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The dataset can be made available upon request to the authors.
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| PSO | Particle Swarm Optimization |
| UAV | Unmanned Aerial Vehicle |
| IoFT | Internet of Flying Things |
| FANET | Flying Ad Hoc Network |
| IoT | Internet of Things |
| GU | Ground User |
| FBS | Flying Base Station |
| MEC | Mobile Edge Computing |
| QoS | Quality of Service |
| IoD | Internet of Drones |
| GA | Genetic Algorithm |
| ACO | Ant Colony Optimization |
| UDA-DD | UAV Deployment Algorithm Degree and Distance |
| UDA-DS | UAV Deployment Algorithm Degree and Signal-to-Interference-plus-Noise Ratio |
| DVFMC | Distributed Virtual Force Motion Control |
| ELAPSE | aErial Local Positioning System for Emergency |
| GPS | Global Positioning System |
| MILP | Mixed Integer Linear Programming |
| TTT | Total Travel Time |
| GAGLPP | Ground–Air-Controlled Global and Local Path Planning |
| LOS | Line-Of-Sight |
| NLOS | Non-Line-Of-Sight |
| QoC | Quality of Coverage |
| DRL | Deep Reinforcement Learning |
| SINR | Signal to Interference plus Noise Ratio |
| mmWave | millimeter-Wave |
| IAB | Integrated Access and Backhaul |
| DCEE | Dual Control for Exploitation and Exploration |
| RRT | Rapidly exploring Random Tree |
| UL-NOMA | UAV-enabled upLink Non-Orthogonal Multiple Access |
| PSO-VRFFA | Particle Swarm Optimization–Virtual Repulsive Force Firefly Algorithm |
| PSO-GA-G | Particle Swarm Optimization-Genetic Algorithm-Greedy |
| MOP | Multi-objective Optimization Problem |
| DSLPSO | Double Self-Limiting Particle Swarm Optimization |
| SLRMSA | Self-Limiting Radius and Multiple Simulated Annealing |
| PF | Pareto Front |
| MOPSO | Multi-Objective Particle Swarm Optimization |
References
- Zaidi, S.; Atiquzzaman, M.; Calafate, C.T. Internet of flying things (IoFT): A survey. Comput. Commun. 2021, 165, 53–74. [Google Scholar] [CrossRef]
- Ogab, M.; Zaidi, S.; Bourouis, A.; Calafate, C.T. Machine Learning-Based Intrusion Detection Systems for the Internet of Drones: A Systematic Literature Review. IEEE Access 2025, 13, 96681–96714. [Google Scholar] [CrossRef]
- Chen, Z.; Zheng, H.; Zhang, J.; Zheng, X.; Rong, C. Joint computation offloading and deployment optimization in multi-UAV-enabled MEC systems. Peer-to-Peer Netw. Appl. 2022, 15, 194–205. [Google Scholar] [CrossRef]
- Hydher, H.; Jayakody, D.N.K.; Hemachandra, K.T.; Samarasinghe, T. Intelligent UAV Deployment for a Disaster-Resilient Wireless Network. Sensors 2020, 20, 6140. [Google Scholar] [CrossRef] [PubMed]
- Zhang, X.; Xiang, X.; Lu, S.; Zhou, Y.; Sun, S. Evolutionary Optimization of Drone-Swarm Deployment for Wireless Coverage. Drones 2022, 7, 8. [Google Scholar] [CrossRef]
- Fan, J.; Zhang, L.; Shen, G.; Li, Z.; Cao, P.; Lei, L. A self-deployment algorithm for flying Ad Hoc networks (FANETs) towards low probability of detection coverage in directional antennas. In Proceedings of the 2020 IEEE 20th International Conference on Communication Technology (ICCT), Nanning, China, 28–31 October 2020; pp. 898–902. [Google Scholar]
- Rhodes, C.; Liu, C.; Chen, W.-H. Autonomous source term estimation in unknown environments: From a dual control concept to UAV deployment. IEEE Robot. Autom. Lett. 2022, 7, 2274–2281. [Google Scholar] [CrossRef]
- Parvaresh, N.; Kulhandjian, M.; Kulhandjian, H.; D’Amours, C.; Kantarci, B. A tutorial on AI-powered 3D deployment of drone base stations: State of the art, applications and challenges. Veh. Commun. 2022, 36, 100474. [Google Scholar] [CrossRef]
- Alkouz, B.; Shahzaad, B.; Bouguettaya, A. Service-based drone delivery. In Proceedings of the 2021 IEEE 7th International Conference on Collaboration and Internet Computing (CIC), Philadelphia, PA, USA, 29 November–1 December 2021; pp. 68–76. [Google Scholar]
- Huang, H.; Savkin, A.V. An algorithm of reactive collision free 3-D deployment of networked unmanned aerial vehicles for surveillance and monitoring. IEEE Trans. Ind. Inform. 2019, 16, 132–140. [Google Scholar] [CrossRef]
- Park, S.-Y.; Shin, C.S.; Jeong, D.; Lee, H. DroneNetX: Network reconstruction through connectivity probing and relay deployment by multiple UAVs in ad hoc networks. IEEE Trans. Veh. Technol. 2018, 67, 11192–11207. [Google Scholar] [CrossRef]
- Attalah, M.A.; Zaidi, S.; Mellal, N.; Calafate, C.T. Task-Offloading Optimization Using a Genetic Algorithm in Hybrid Fog Computing for the Internet of Drones. Sensors 2025, 25, 1383. [Google Scholar] [CrossRef]
- Lin, L.; Wang, Z.; Tian, L.; Wu, J.; Wu, W. A PSO-based energy-efficient data collection optimization algorithm for UAV mission planning. PLoS ONE 2024, 19, e0297066. [Google Scholar] [CrossRef] [PubMed]
- Liu, S.; Zhou, W.; Qin, M.; Peng, X. Tent–PSO-based unmanned aerial vehicle path planning for cooperative relay networks in dynamic user environments. Sensors 2025, 25, 2005. [Google Scholar] [CrossRef] [PubMed]
- Liu, X.; Wang, X.; Huang, M.; Jia, J.; Bartolini, N.; Li, Q.; Zhao, D. Deployment of UAV-BSs for on-demand full communication coverage. Ad Hoc Netw. 2023, 140, 103047. [Google Scholar] [CrossRef]
- Trotta, A.; Montecchiari, L.; Di Felice, M.; Bononi, L. A GPS-free flocking model for aerial mesh deployments in disaster-recovery scenarios. IEEE Access 2020, 8, 91558–91573. [Google Scholar] [CrossRef]
- Lee, J.; Friderikos, V. Multiple UAVs trajectory optimization in multicell networks with adjustable overlapping coverage. IEEE Internet Things J. 2023, 10, 9122–9135. [Google Scholar] [CrossRef]
- Miao, Y.; Hwang, K.; Wu, D.; Hao, Y.; Chen, M. Drone swarm path planning for mobile edge computing in industrial internet of things. IEEE Trans. Ind. Inform. 2022, 19, 6836–6848. [Google Scholar] [CrossRef]
- Huang, H.; Savkin, A.V. Deployment of heterogeneous UAV base stations for optimal quality of coverage. IEEE Internet Things J. 2022, 9, 16429–16437. [Google Scholar] [CrossRef]
- Zhang, Y.; Kishk, M.A.; Alouini, M.-S. Deployment optimization of tethered drone-assisted integrated access and backhaul networks. IEEE Trans. Wirel. Commun. 2024, 23, 2668–2680. [Google Scholar] [CrossRef]
- Qi, S.; Lin, B.; Deng, Y.; Chen, X.; Fang, Y. Minimizing Maximum Latency of Task Offloading for Multi-UAV-Assisted Maritime Search and Rescue. IEEE Trans. Veh. Technol. 2024, 73, 13625–13638. [Google Scholar] [CrossRef]
- Abdel-Razeq, S.; Shakhatreh, H.; Alenezi, A.; Sawalmeh, A.; Anan, M.; Almutiry, M. PSO-based UAV deployment and dynamic power allocation for UAV-enabled uplink NOMA network. Wirel. Commun. Mob. Comput. 2021, 2021, 2722887. [Google Scholar] [CrossRef]
- Chen, X.; Tang, W.; Yang, X.; Zhou, L.; Li, L. PSO-VFA: A hybrid intelligent algorithm for coverage optimization of UAV-mounted base stations. J. Internet Technol. 2022, 23, 487–495. [Google Scholar] [CrossRef]
- Rasouli, F. Algorithm PSO for Maximum Coverage of Users Using Drones to Find Optimal Points for Deployment. Comput. Algorithms Numer. Dimens. 2024, 3, 150–157. [Google Scholar]
- Ibraiwish, H.; Eltokhey, M.W.; Alouini, M.-S. Energy efficient deployment of VLC-enabled UAV using particle swarm optimization. IEEE Open J. Commun. Soc. 2023, 5, 553–565. [Google Scholar] [CrossRef]
- Li, H.; Hao, X.; Wen, J.; Liu, F.; Zhang, Y. Multi-Objective Deployment of UAVs for Multi-Hop FANET: UAV-Assisted Emergency Vehicular Network. Drones 2024, 8, 262. [Google Scholar] [CrossRef]
- Zaidi, S.; Attalah, M.A.; Khamer, L.; Calafate, C.T. Task Offloading Optimization Using PSO in Fog Computing for the Internet of Drones. Drones 2024, 9, 23. [Google Scholar] [CrossRef]
- Nocedal, J.; Wright, S.J. Numerical Optimization; Springer: New York, NY, USA, 2006. [Google Scholar]
- Becerra, R.L.; Coello Coello, C.A. Epsilon-Constraint with an Efficient Cultured Differential Evolution. In Proceedings of the 9th Annual Conference Companion on Genetic and Evolutionary Computation, London, UK, 7–11 July 2007; pp. 2787–2794. [Google Scholar]
- Khorram, E.; Khaledian, K.; Khaledyan, M. A numerical method for constructing the Pareto front of multi-objective optimization problems. J. Comput. Appl. Math. 2014, 261, 158–171. [Google Scholar] [CrossRef]
- Kesireddy, A.; Medrano, F.A. Elite multi-criteria decision making—Pareto front optimization in multi-objective optimization. Algorithms 2024, 17, 206. [Google Scholar] [CrossRef]
- Zhang, X.; Wang, A.; Sun, G.; Liu, L.; Zhang, J. UAV Deployment Optimization in UAV-Assisted Wireless Communications. arXiv 2024, arXiv:2403.15411. [Google Scholar] [CrossRef]
- Nemer, I.A.; Sheltami, T.R.; Belhaiza, S.; Mahmoud, A.S. Energy-Efficient UAV Movement Control for Fair Communication Coverage: A Deep Reinforcement Learning Approach. Sensors 2022, 22, 1919. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).