Toward Efficient Health Data Identification and Classification in IoMT-Based Systems
Abstract
1. Introduction
- Conducting a review of existing methods in IoMT data identification and classification highlighting critical gaps in data privacy efficiency that motivate our approach.
- Proposing SDAIPA (SDAIA-HIPAA) framework with two core components:
- Standard Data Identification—Our model introduces a single and comprehensive data identification list to eliminates inconsistencies in detecting regulated data, ensuring compliance efficiency and interoperability across heterogeneous systems.
- Robust Data Classification—We design a hybrid sensitivity classification model that integrates quantitative privacy risk assessment in align with HIPPA and SDAIA regulations to granular IoMT health data protection.
2. Related Work
2.1. Health Insurance Portability and Accountability Act (HIPAA)
2.2. The Saudi Data and AI Authority (SDAIA)
- Public: Data that is freely available to the public and does not require any restrictions. This might include general information about the government, public services, or weather data.
- Confidential: Data that is intended for use within the Saudi government or its affiliated organizations. This might include internal documents, reports, or operational data.
- Secret: Data that is subject to access controls and requires specific authorization to view or use. This might include sensitive government information, personal data, or confidential business data.
- Top secret: Data that is highly sensitive and requires strict security measures to protect it from unauthorized access. This might include national security secrets, critical infrastructure data, or highly confidential government information.
2.3. IoMT Data Identification and Classification
3. SDAIPA (SDAIA-HIPAA) Identification and Classification Model
3.1. SDAIPA Data Identification
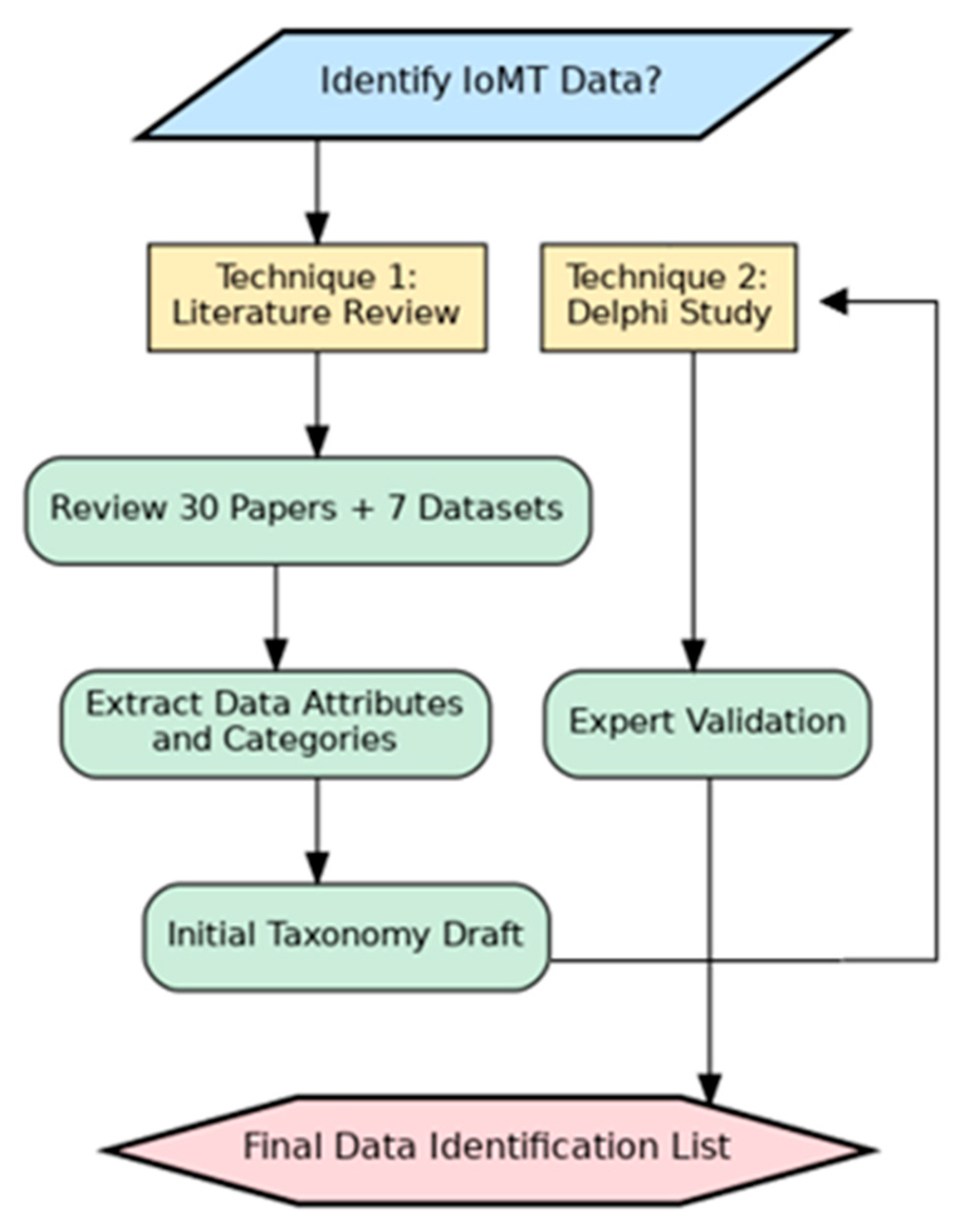
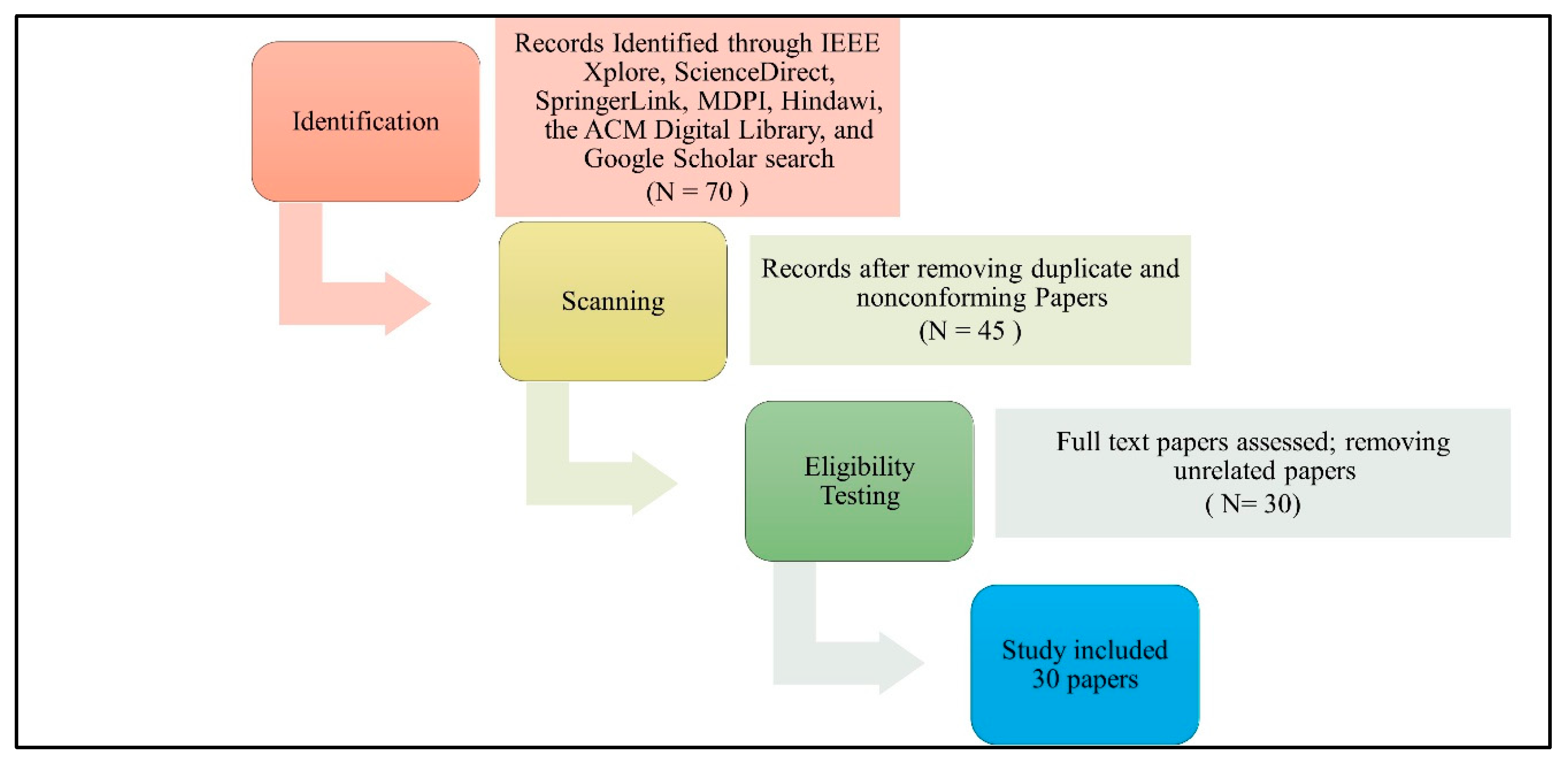
3.1.1. Methodology
Scientific Papers
IoMT Datasets
3.1.2. Finding
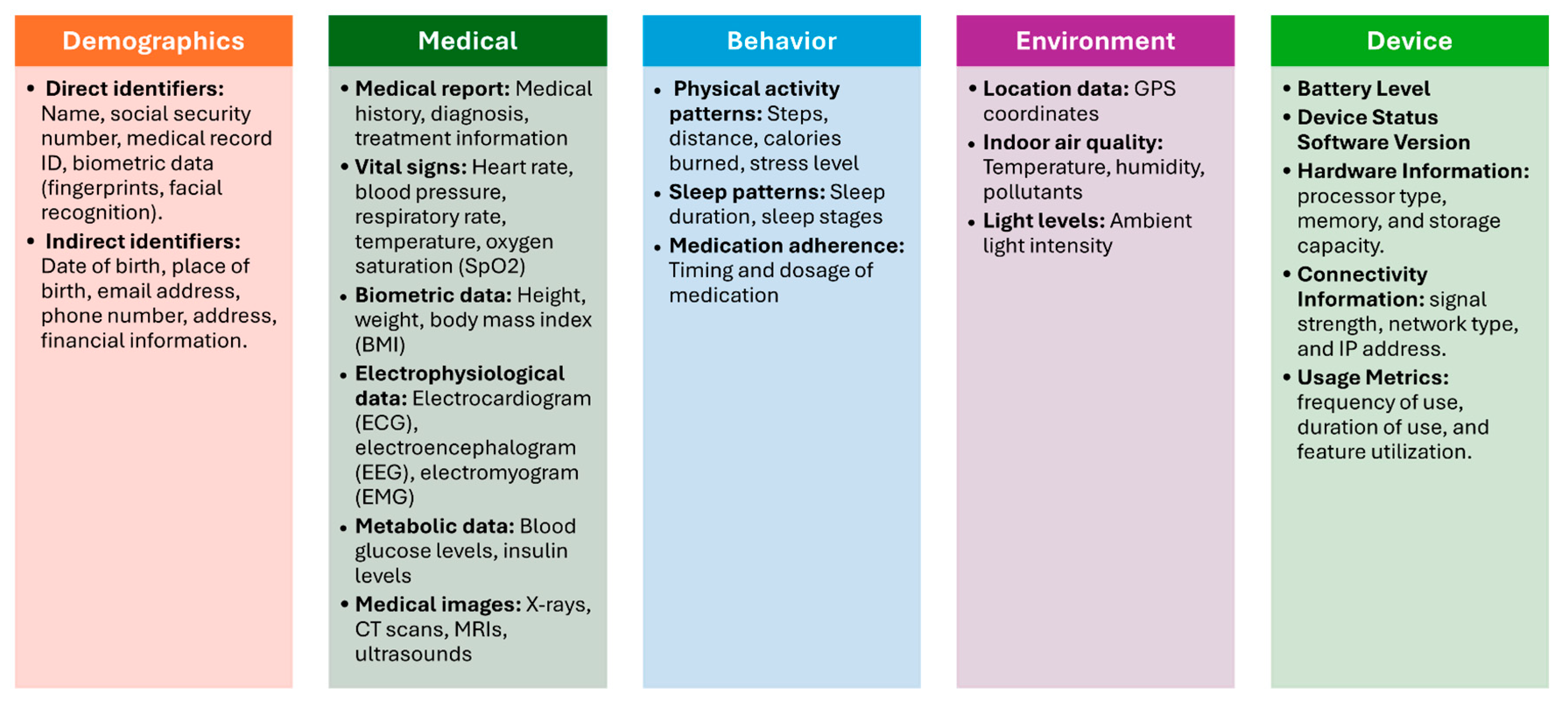
- Demographic Data: This refers to personal information about patients, such as age, gender, name and contact information [29,33,34]. The demographic data will be divided into two main types [35]: direct identifiers and indirect identifiers. Direct identifiers are any data elements that directly and uniquely identify an individual such as name and ID. Indirect patient identifiers are data elements that, while not directly identifying an individual, can be combined with other information to uniquely identify them such as date of birth.
- Medical Data: This encompasses a wide range of health-related information, including medical history, diagnoses, symptoms, medications, allergies, vital signs, and lab results [25,26,27,29,30,31,33,34,36,37,38]. IoMT devices collect and store medical data to enable remote monitoring, early detection of health issues, and personalized treatment plans.
3.1.3. Validation
- Assess the accuracy and comprehensiveness of the identified data elements.
- Validate the relevance of the data elements to the overarching goals and objectives of IoMT research and practice.
- Identify any additional data elements that may be critical for advancing the field of IoMT.
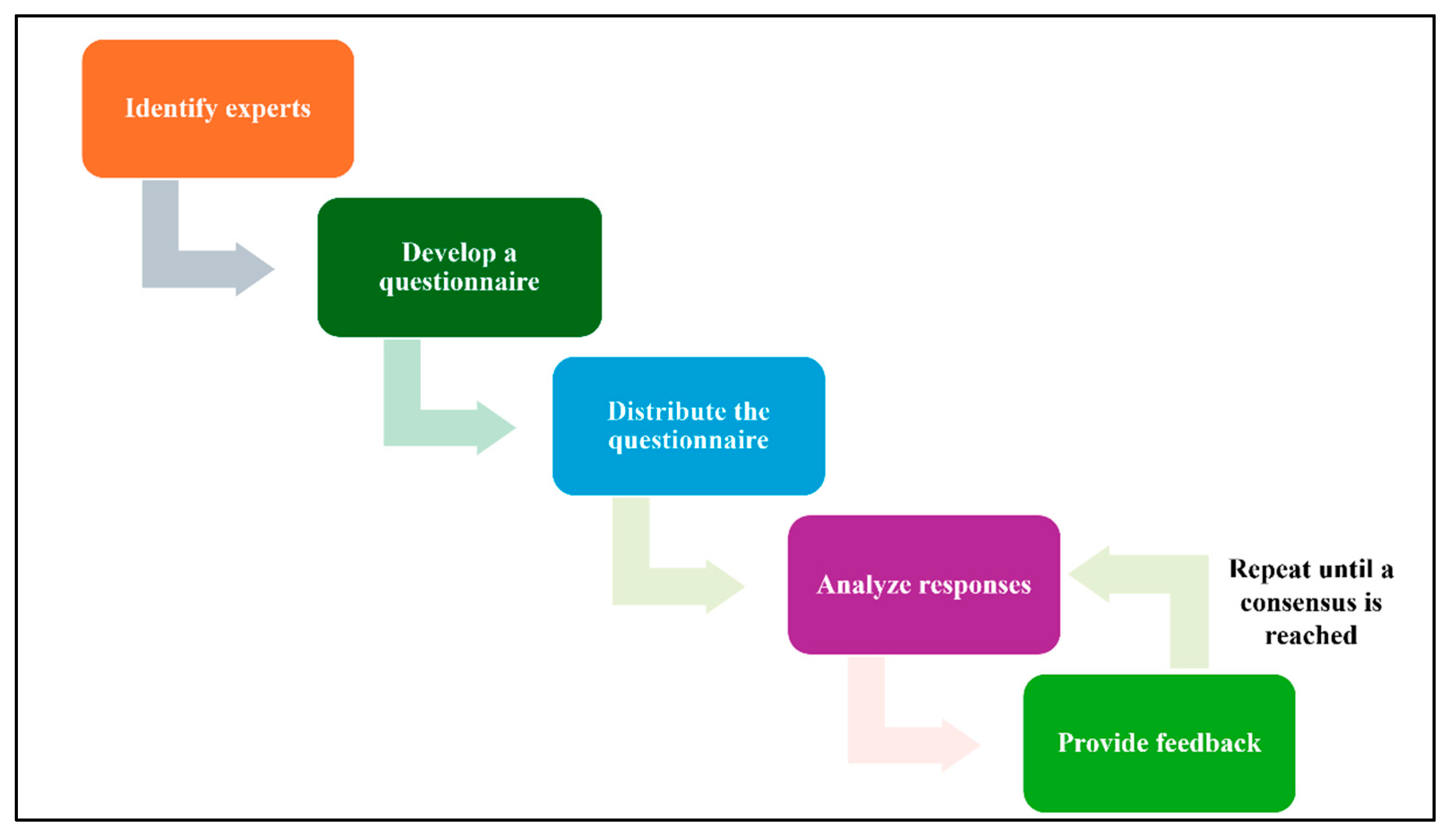
- Identify experts: Select a group of experts who have knowledge and experience in the relevant field.
- Develop a questionnaire: Create a questionnaire that includes clear and concise questions about the topic being studied.
- Distribute the questionnaire: Send the questionnaire to the experts and request their responses.
- Analyze responses: Summarize the experts’ responses and identify any areas of agreement or disagreement.
- Provide feedback: Share the summary of responses with the experts and allow them to revise their opinions based on the feedback from others.
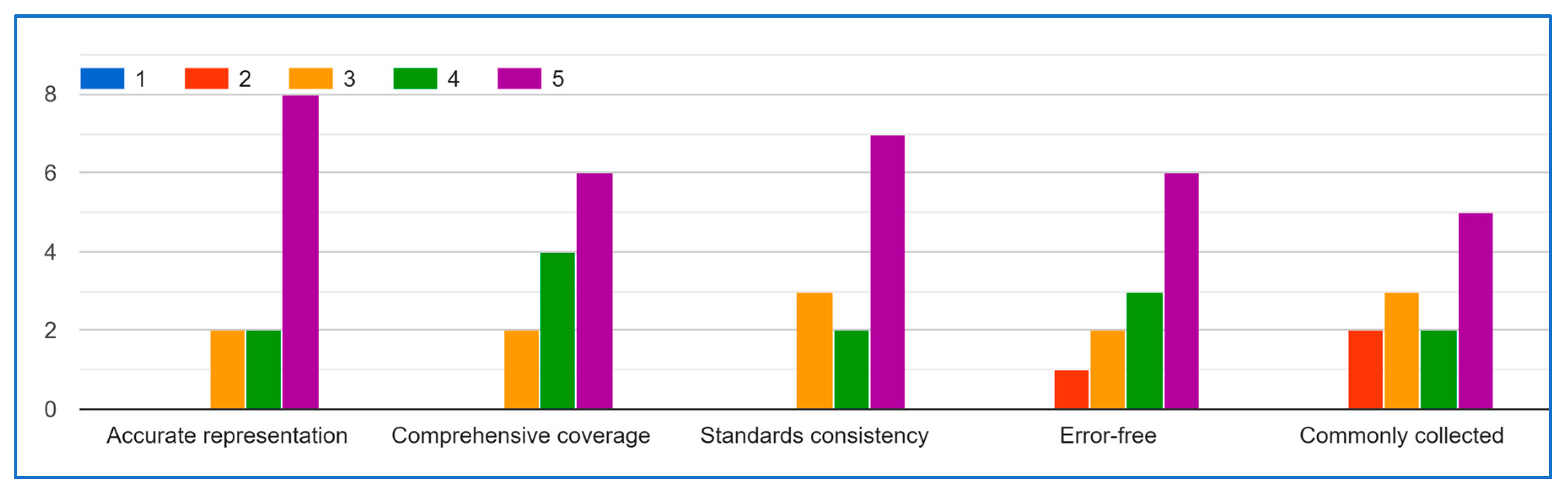
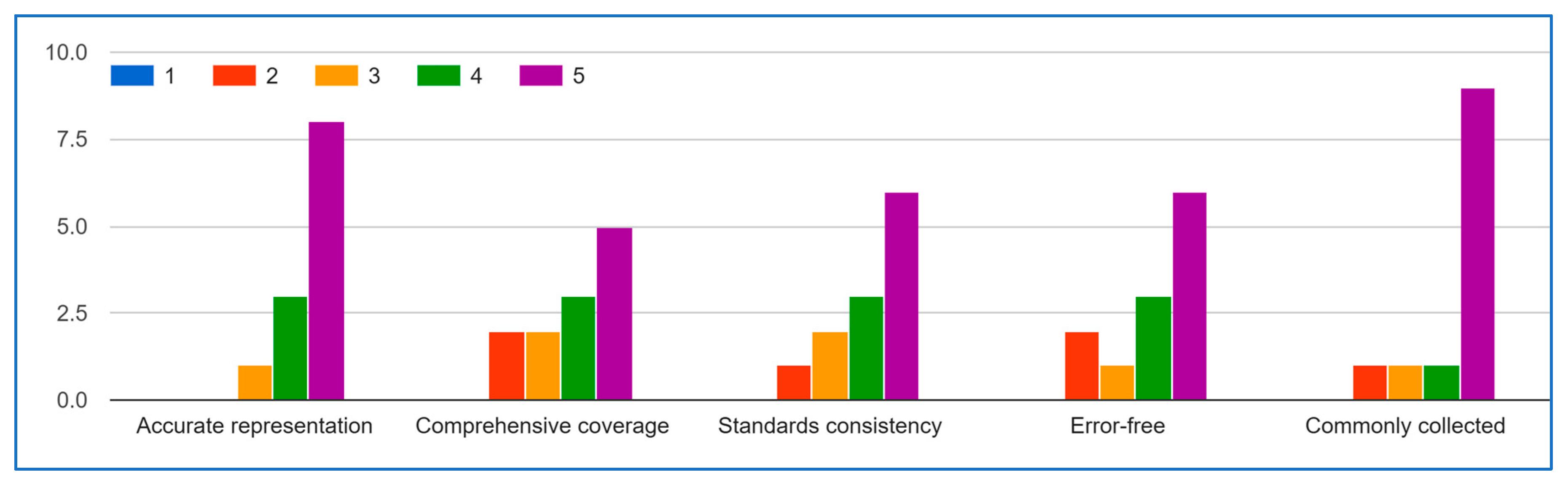
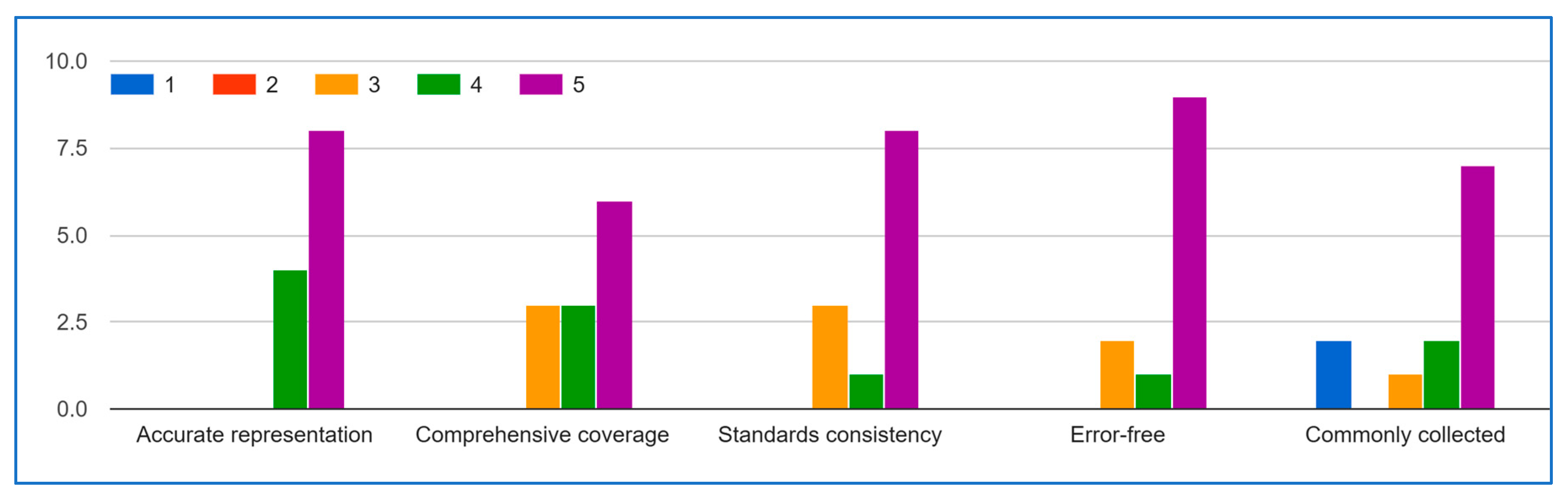
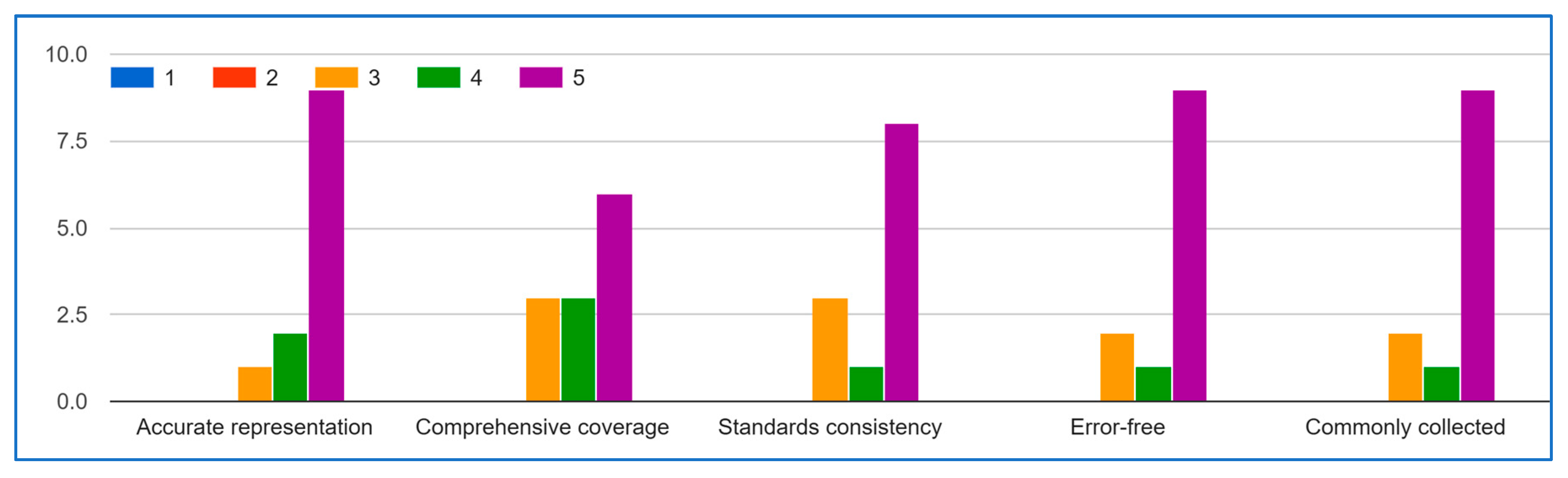
- Repeat steps 4 and 5: Continue this process of iteration and feedback until a consensus is reached. Figure 4 illustrates the Delphi method steps.
Delphi Method (Round 1)
- Does the data list accurately represent the IoMT captured data?
- Is the data list comprehensive, capturing all relevant aspects of the IOMT data?
- Is the data list consistent with existing IoMT guidelines?
- Is the data list free from errors and inconsistencies?
- Is the data list commonly or frequently collected in IOMT activities?
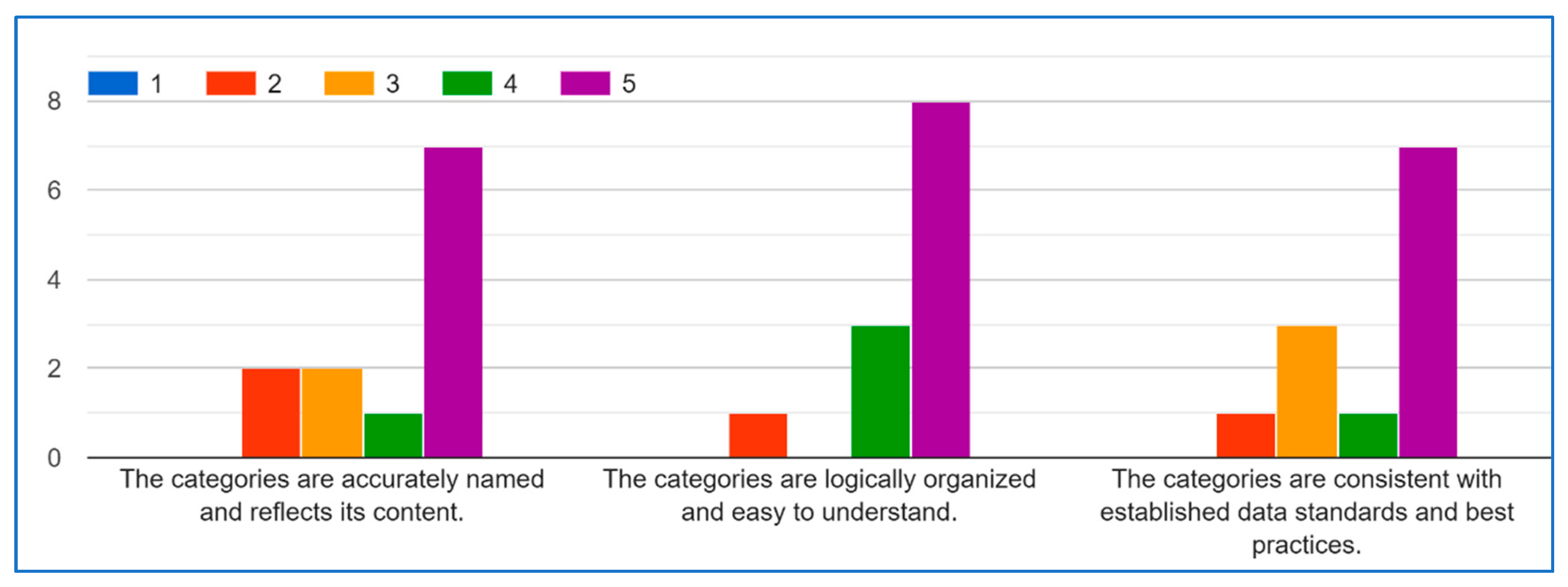
- Are the categories accurately named and reflect their content?
- Are the categories logically organized and easy to understand?
- Are the categories consistent with established data standards and best practices?
Delphi Method (Round 2)
3.2. SDAIPA Data Classification
3.2.1. Methodology
- Sensitivity level: the level of the data type based on the suggested sensitivity impact matrix.
- Uniqueness: the scored assessment of individual identifiability for the data type based on HIPAA and SDAIA.
- Harm potential: the scored assessment of potential for adverse consequences for the data type based on HIPAA and SDAIA.
3.2.2. Finding
3.2.3. Validation
4. Practical Considerations
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| FDA | Food and Drug Administration |
| GDPR | General Data Protection Regulation |
| HIPAA | The Health Insurance Portability and Accountability Act |
| HL7 | Health Level Seven |
| IOT | Internet of Things |
| IOMT | Internet of Medical Thing |
| IOS | The International Organization for Standardization |
| NDMO | National Data Management Office |
| OECD | The Organisation for Economic Co-operation and Development |
| PHI | Protected Health Information |
| SDAIA | The Saudi Data and AI Authority |
| WHO | The World Health Organization |
Appendix A

Appendix B
| Data Type | Uniqueness (1–5) | Harm Potential (1–5) | Total Risk | Sensitivity Level |
|---|---|---|---|---|
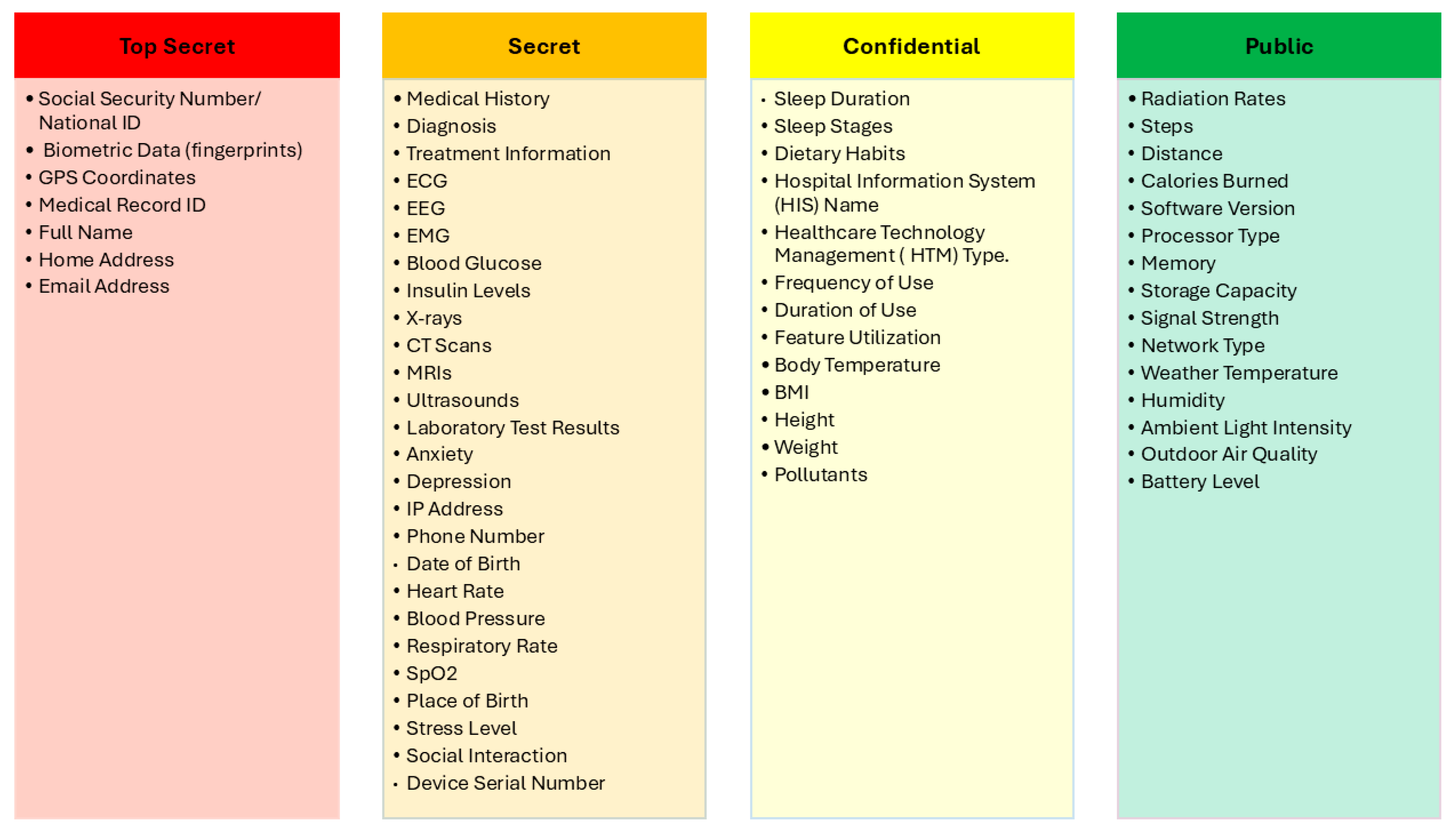
| Social Security Number/National ID | 5 | 5 | 5 | Top Secret |
| Biometric Data (fingerprints) | 5 | 5 | 5 | Top Secret |
| GPS Coordinates | 5 | 5 | 5 | Top Secret |
| Medical Record ID | 5 | 4 | 4.6 | Top Secret |
| Medical History | 4 | 5 | 4.4 | Secret |
| Diagnosis | 4 | 5 | 4.4 | Secret |
| Treatment Information | 4 | 5 | 4.4 | Secret |
| ECG | 4 | 5 | 4.4 | Secret |
| EEG | 4 | 5 | 4.4 | Secret |
| EMG | 4 | 5 | 4.4 | Secret |
| Blood Glucose | 4 | 5 | 4.4 | Secret |
| Insulin Levels | 4 | 5 | 4.4 | Secret |
| X-rays | 4 | 5 | 4.4 | Secret |
| CT Scans | 4 | 5 | 4.4 | Secret |
| MRIs | 4 | 5 | 4.4 | Secret |
| Ultrasounds | 4 | 5 | 4.4 | Secret |
| Laboratory Test Results | 4 | 5 | 4.4 | Secret |
| Anxiety | 4 | 5 | 4.4 | Secret |
| Depression | 4 | 5 | 4.4 | Secret |
| Address | 5 | 4 | 4.4 | Secret |
| Phone Number | 5 | 4 | 4.4 | Secret |
| Name | 5 | 3 | 4.2 | Secret |
| Date of Birth | 4 | 3 | 3.6 | Confidential |
| Email Address | 4 | 3 | 3.6 | Confidential |
| Serial Number | 4 | 3 | 3.6 | Confidential |
| Heart Rate | 3 | 4 | 3.4 | Confidential |
| Blood Pressure | 3 | 4 | 3.4 | Confidential |
| Respiratory Rate | 3 | 4 | 3.4 | Confidential |
| SpO2 | 3 | 4 | 3.4 | Confidential |
| Stress Level | 3 | 4 | 3.4 | Confidential |
| Place of Birth | 3 | 3 | 3 | Confidential |
| Sleep Duration | 3 | 3 | 3 | Confidential |
| Sleep Stages | 3 | 3 | 3 | Confidential |
| Dietary Habits | 3 | 3 | 3 | Confidential |
| Social Interaction | 3 | 3 | 3 | Confidential |
| HIS | 3 | 3 | 3 | Confidential |
| HTM | 3 | 3 | 3 | Confidential |
| Frequency of Use | 3 | 3 | 3 | Confidential |
| Duration of Use | 3 | 3 | 3 | Confidential |
| Feature Utilization | 3 | 3 | 3 | Confidential |
| Temperature | 2 | 3 | 2.4 | Public |
| BMI | 2 | 3 | 2.4 | Public |
| Radiation Rates | 2 | 3 | 2.4 | Public |
| Height | 2 | 2 | 2 | Public |
| Weight | 2 | 2 | 2 | Public |
| Steps | 2 | 2 | 2 | Public |
| Distance | 2 | 2 | 2 | Public |
| Calories Burned | 2 | 2 | 2 | Public |
| Pollutants | 2 | 2 | 2 | Public |
| Software Version | 2 | 2 | 2 | Public |
| Processor Type | 2 | 2 | 2 | Public |
| Memory | 2 | 2 | 2 | Public |
| Storage Capacity | 2 | 2 | 2 | Public |
| Signal Strength | 2 | 2 | 2 | Public |
| Network Type | 2 | 2 | 2 | Public |
| Temperature | 1 | 1 | 1 | Public |
| Humidity | 1 | 1 | 1 | Public |
| Ambient Light Intensity | 1 | 1 | 1 | Public |
| Outdoor Air Quality | 1 | 1 | 1 | Public |
| Battery Level | 1 | 1 | 1 | Public |
References
- Global Smart Healthcare Market—Industry Trends and Forecast to 2029. 2022. Available online: https://www.databridgemarketresearch.com/reports/global-smart-healthcare-market (accessed on 23 July 2025).
- Juniper Research. Smart Hospital Market Value to Reach $59 Billion Globally by 2026. Available online: https://www.juniperresearch.com/press/smart-hospital-market-value-to-reach-59-billion/ (accessed on 6 August 2024).
- Medical Device Cybersecurity Regional Preparedness Response Playbook. 2022. Available online: https://www.mitre.org/sites/default/files/2022-11/pr-2022-3616-medical-device-cybersecurity-regional-preparedness-response-companion-guide.pdf (accessed on 23 May 2025).
- Vaiyapuri, T.; Binbusayyis, A.; Varadarajan, V. Security, Privacy and Trust in IOMT Enabled Smart Healthcare System: A Systematic Review of current and Future Trends. Int. J. Adv. Comput. Sci. Appl. 2021, 12, 731–737. [Google Scholar] [CrossRef]
- World Health Organization (WHO). Privacy Policy. Available online: https://www.who.int/about/policies/privacy (accessed on 11 May 2025).
- SDAIA. Personal Data Protection Law. 2023. Available online: https://sdaia.gov.sa/en/SDAIA/about/Documents/Personal%20Data%20English%20V2-23April2023-%20Reviewed-.pdf (accessed on 23 June 2025).
- Gordon, A. Classification, 2nd ed.; Taylor & Francis: London, UK, 1999. [Google Scholar]
- McCullagh, K. Data Sensitivity: Proposals for Resolving the Conundrum. J. Int. Com. Law Tech. 2007, 2, 190–201. [Google Scholar]
- Cullagh, K.M. Data sensitivity: Resolving the conundrum. In Proceedings of the Sensitive data: Perceptions and implications, CLS Seminar, London, UK, 16 April 2007. [Google Scholar]
- U.S. Department Health and Human Services. Health Information Privacy. Available online: https://www.hhs.gov/hipaa/index.html (accessed on 6 February 2025).
- ISO. ISO—Health Informatics. Available online: https://www.iso.org/sectors/health/health-informatics (accessed on 19 August 2025).
- Health Level Seven International—Homepage|HL7 International. Available online: https://www.hl7.org/.
- National Data Governance Interim Regulations. Available online: https://sdaia.gov.sa/ndmo/Files/PoliciesEn.pdf (accessed on 24 December 2024).
- Edemekong, P.F.; Annamaraju, P.; Afzal, M.; Haydel, M.J. Health Insurance Portability and Accountability Act (HIPAA) Compliance; StatPearls: Treasure Island, FL, USA, 2024. [Google Scholar]
- Isola, S.; Khalili, Y.A. Protected Health Information. StatPearls: Treasure Island, FL, USA, 2023. [Google Scholar]
- Berkeley, U. Human Research Protection Program|UC Berkeley. Available online: https://cphs.berkeley.edu/hipaa/hipaa18.html (accessed on 19 August 2025).
- About SDAIA|Data & AI. Available online: https://sdaia.gov.sa/en/SDAIA/about/Pages/About.aspx (accessed on 19 August 2025).
- About National Data Management Office (NDMO). Available online: https://sdaia.gov.sa/en/Sectors/NDMO/Pages/default.aspx (accessed on 19 August 2025).
- Saha, S.; Mallick, S.; Neogy, S. Privacy-Preserving Healthcare Data Modeling Based on Sensitivity and Utility. SN Comput. Sci. 2022, 3, 1–13. [Google Scholar] [CrossRef]
- Kalyani, G.; Chaudhari, S. An efficient approach for enhancing security in Internet of Things using the optimum authentication key. Int. J. Comput. Appl. 2019, 42, 306–314. [Google Scholar] [CrossRef]
- Katarahweire, M.; Bainomugisha, E.; Mughal, K.A. Data Classification for Secure Mobile Health Data Collection Systems. Dev. Eng. 2020, 5, 100054. [Google Scholar] [CrossRef]
- Srivastava, R.; Kumar, S.; Kumar, B. 7-Classification model of machine learning for medical data analysis. In Statistical Modeling in Machine Learning; Elsevier: Amsterdam, The Netherlands, 2023; pp. 111–132. [Google Scholar]
- Mahalakshmi, R.; Lalithamani, N. Optimizing IoMT network performance using gateway placement. Simul. Model. Pr. Theory 2025, 143, 103164. [Google Scholar] [CrossRef]
- Awad, F.H.; Hamad, M.M.; Alzubaidi, L. Robust Classification and Detection of Big Medical Data Using Advanced Parallel K-Means Clustering, YOLOv4, and Logistic Regression. Life 2023, 13, 691. [Google Scholar] [CrossRef] [PubMed]
- BPCO Dataset Based GANS for IOMT. 2021. Available online: https://www.kaggle.com/datasets/cnrieiit/bpco-dataset-based-gans-for-iomt (accessed on 29 July 2025).
- Elderly Fall Prediction and Detection. 2022. Available online: https://www.kaggle.com/datasets/laavanya/elderly-fall-prediction-and-detection (accessed on 23 June 2025).
- Human Stress Detection in and Through Sleep. 2022. Available online: https://www.kaggle.com/datasets/laavanya/human-stress-detection-in-and-through-sleep (accessed on 15 July 2025).
- IoT Healthcare Security Dataset. 2023. Available online: https://www.kaggle.com/datasets/faisalmalik/iot-healthcare-security-dataset (accessed on 1 July 2025).
- Maternal Health Risk Data. 2021. Available online: https://www.kaggle.com/datasets/csafrit2/maternal-health-risk-data (accessed on 23 May 2025).
- Patient Temperature and Pulse Rate. 2021. Available online: https://www.kaggle.com/datasets/meghagoriya/patient-temperature-and-pulse-rate (accessed on 23 July 2025).
- Stress-Lysis. 2023. Available online: https://www.kaggle.com/datasets/jeyasrisenthil/input-data (accessed on 15 May 2025).
- Concept Dictionary Basics—Documentation—OpenMRS Wiki. Available online: https://openmrs.atlassian.net/wiki/spaces/docs/pages/25475255/Concept+Dictionary+Basics#Introduction (accessed on 19 August 2025).
- Mendhe, N.M.; D, S.; M, R.S. Artificial intelligence-based Web-Centric e-health monitoring system. In Proceedings of the 2022 International Conference on Innovative Computing, Intelligent Communication and Smart Electrical Systems (ICSES), Chennai, India, 15–16 July 2022; pp. 1–5. [Google Scholar]
- Wani, R.U.Z.; Thabit, F.; Can, O. Security and privacy challenges, issues, and enhancing techniques for Internet of Medical Things: A systematic review. Secur. Priv. 2024, 7, e409. [Google Scholar] [CrossRef]
- Hrynaszkiewicz, I.; Norton, M.L.; Vickers, A.J.; Altman, D.G. Preparing raw clinical data for publication: Guidance for journal editors, authors, and peer reviewers. BMJ 2010, 340, c181. [Google Scholar] [CrossRef]
- Geetha, N.; Sankar, A. An intelligent IoT-Based health monitoring system for tribal people. In Incorporating the Internet of Things in Healthcare Applications and Wearable Devices; IGI Global Scientific Publishing: Hershey, PA, USA, 2019; pp. 137–149. [Google Scholar] [CrossRef]
- Manoj, G.; Divya, P.S.; Barath, S.R.; Santhiyagu, I.J. Mathematical modeling of IOT-Based health monitoring System. In Internet of Things; Springer Nature: London, UK, 2021; pp. 211–233. [Google Scholar]
- Saini, D.; Garg, N.; Sharma, N.; Hingonia, M.; Jain, M. IoT Based Health Monitoring System. Int. J. Res. Appl. Sci. Eng. Technol. 2024, 12, 4365–4372. [Google Scholar] [CrossRef]
- Ozsahin, D.U.; Duwa, B.B.; Idoko, J.B.; Rwiyereka, A.; Ishimwe, D.; Hassan, S.; Ozsahin, I. Internet of things-based patient well-being monitoring system. In Practical Design and Applications of Medical Devices; Elsevier: Amsterdam, The Netherlands, 2024; pp. 23–38. [Google Scholar]
- Raj, S.S.; Madiajagan, M. Parallel machine learning and deep learning approaches for internet of medical things (IoMT). In Intelligent IoT Systems in Personalized Health Care; Elsevier: Amsterdam, The Netherlands, 2021; pp. 89–103. [Google Scholar]
- Winnie, Y.; E, U.; Ajay, D.M. Enhancing data security in IoT healthcare services using FOG computing. In Proceedings of the 2018 International Conference on Recent Trends in Advance Computing (ICRTAC), Chennai, India, 10–11 September 2018; pp. 200–205. [Google Scholar]
- Rajasekaran, M.; Yassine, A.; Hossain, M.S.; Alhamid, M.F.; Guizani, M. Autonomous monitoring in healthcare environment: Reward-based energy charging mechanism for IoMT wireless sensing nodes. Futur. Gener. Comput. Syst. 2019, 98, 565–576. [Google Scholar] [CrossRef]
- Liu, S.; Xu, H.; Zang, R. An improved anonymous authentication scheme for internet of medical things based on elliptic curve cryptography. In Proceedings of the 2023 5th International Conference on Natural Language Processing (ICNLP), Guangzhou, China, 24–26 March 2023. [Google Scholar]
- Ayoub, S.-A.; Ali, A.-G.M.; Narhimene, B. Enhanced Intrusion Detection system for remote healthcare. In Advances in Computing Systems and Applications; Proceedings of the 5th Conference on Computing Systems and Applications 2022, Algiers, Algeria, 17–18 May 2022; Springer: Berlin, German, 2022; pp. 323–333. [Google Scholar]
- Linstone, H.A.; Turoff, M. The Delphi Method—Techniques and Applications; Addison-Wesley Pub. Co.: Boston, MA, USA, 2002. [Google Scholar]
- Garfinkel, S.L. De-Identification of Personal Information; NISTIR 8053; NIST: Gaithersburg, MA, USA, 2015.
- U.S Department of Health and Human Services. Guidance Regarding Methods for De-Identification of Protected Health Information in Accordance with the Health Insurance Portability and Accountability Act (HIPAA) Privacy Rule. Available online: https://www.hhs.gov/hipaa/for-professionals/special-topics/de-identification/index.html#determination (accessed on 4 February 2025).
- McCallister, E.; Grance, T.; Scarfone, K. Guide to Protecting the Confidentiality of Personally Identifiable Information (PII); NIST Special Publication 800-122; NIST: Gaithersburg, MA, USA, 2010. Available online: https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-122.pdf (accessed on 19 August 2025).
- Sweeney, L.; Yoo, J.S.; Perovich, L.; Boronow, K.E.; Brown, P.; Brody, J.G. Re-identification Risks in HIPAA Safe Harbor Data: A study of data from one environmental health study. Technol Sci. 2017, 2017, 2017082801. [Google Scholar] [PubMed]
- ARX Aerospace & Defense. ARX Aerospace & Defense—ARX Aerospace & Defense Provides Specialized Training Programs in Aerospace and Defense Disciplines. Available online: https://arx.sa/.
- Presidio. Available online: https://www.presidio.com/.
- Art. 9 GDPR—Processing of Special Categories of Personal Data—General Data Protection Regulation (GDPR). Available online: https://gdpr-info.eu/art-9-gdpr/ (accessed on 23 June 2025).
- Dhiab, Y.B.; Aoueileyine, M.O.-E.; Bouallegue, R. Context-Aware Adaptive Security Framework for IoT-Based patient monitoring systems. In Proceedings of the 39th International Conference on Advanced Information Networking and Applications, Barcelona, Spain, 9–11 April 2025; pp. 105–116. [Google Scholar]
- Inshi, S.; Chowdhury, R.; Ould-Slimane, H.; Talhi, C. Secure Adaptive Context-Aware ABE for Smart Environments. IoT 2023, 4, 112–130. [Google Scholar] [CrossRef]
- Ben Othman, S.; Getahun, M. Leveraging blockchain and IoMT for secure and interoperable electronic health records. Sci. Rep. 2025, 15, 12358. [Google Scholar] [CrossRef] [PubMed]
- Leung Mak, H.W. From COVID-19 Pandemic of Five Selected East Asian Cities to Assessment of Data Openness and Integration for Future City Development; No. 2; The University of Hong Kong: Hong Kong, China, September 2021. [Google Scholar]
- Conduah, A.K.; Ofoe, S.; Siaw-Marfo, D. Data privacy in healthcare: Global challenges and solutions. Digit. Health 2025, 11. [Google Scholar] [CrossRef] [PubMed]


| Ref. | Approach | Data Categories | Strengths | Limitations/Gaps |
|---|---|---|---|---|
| Saha et al. [19] | Metric Sensitivity Score + Decision tree | Sensitive vs. Non-sensitive | Balances privacy and utility | Binary classification only; limited to attribute-level sensitivity |
| Kalyani & Chaudhari [20] | Deep Learning Neural Network (DNN) | Sensitive vs. Non-sensitive | Scalable, improves encryption | Binary classification; lacks IoMT context |
| Katarahweire et al. [21] | Expert-driven (case studies, interviews) | Public, Confidential, Critical | Practical, context-aware classification | Limited to MHDCSs; lacks automation and IoMT validation |
| Dataset Name | Purpose | Size | Number of Columns |
|---|---|---|---|
| BPCO Dataset (GANs for IoMT) [25] | Generate synthetic COPD patient data for IoMT research | 4.2 MB | 13 |
| Elderly Fall Prediction & Detection [26] | Detect/prevent falls in elderly using IoT sensors | 28.5 MB | 7 |
| Human Stress Detection in Sleep [27] | Classify stress levels during sleep via wearables | 1.2 MB | 9 |
| IoT Healthcare Security Dataset [28] | Anomaly detection in medical IoT devices | 87.3 MB | 32 |
| Maternal Health Risk Data [29] | Predict pregnancy-related risks (e.g., preeclampsia) | 0.8 MB | 7 |
| Patient Temperature & Pulse Rate [30] | Monitor vital signs for early warning systems | 3.1 MB | 3 |
| Stress-Lysis (Stress Level Detection) [31] | Predict stress levels (low/medium/high) from physiological signals | 0.03 MB | 4 |
| Expert # | Years of Experience | Institution Type |
|---|---|---|
| 1 | 8 | Medical Devices Company |
| 2 | 7 | Hospital |
| 3 | 10 | Government |
| 4 | 3 | Medical Devices Company |
| 5 | 9 | Hospital |
| 6 | 12 | Hospital |
| 7 | 1 | Medical Research Center |
| 8 | 4 | Medical Devices Company |
| 9 | 8 | Government |
| 10 | 7 | University |
| 11 | 7 | Government |
| 12 | 5 | Medical Devices Company |
| # | Comment | Response |
|---|---|---|
| 1 | You should not consider the gander in demographic, also the SN in device | The list was refined with gender removed from demographics and device serial number clarified under device-related attributes |
| 2 | Passport number, Driver’s license number, Genetic information (e.g., DNA sequences), Health insurance ID, Full face photos and comparable images, Vehicle identification numbers (VIN), Gender, Race/Ethnicity, Marital status, educational background (e.g., school attended), Employment information (e.g., occupation, job title), Geolocation data, religious affiliation | After some research, it was clear that this information cannot be collected by IoMT devices. It can be added manually to the patient’s record. |
| 3 | Gender is not included. I think financial data is not relevant and not usually captured by IoMT. | The list was refined based on expert feedback, with gender removed from demographics |
| # | Comment | Response |
|---|---|---|
| 1 | Laboratory test results: blood tests, genetic tests, medication records, allergies, immunization records, surgical history, mental health data, physical activity data, sleep patterns, nutrition and diet information, rehabilitation progress, prosthetic and assistive device data, drug and alcohol use, pregnancy and fertility data, microbiome data. | The list was refined to include additional laboratory and clinical data types |
| 2 | You can add nutrients and minerals | Same as Blood test |
| 3 | Missing other diagnoses instruments data like data collected in laboratory tests (blood chemistry, hormones, bathology, Microbiology) | The list was refined to include additional laboratory and clinical data types |
| # | Comment | Response |
|---|---|---|
| 1 | An additional info can be collected such as dietary habits and social interaction (mental health). | The list was refined to incorporate mental health |
| 2 | You can add physiological disorders such as anxiety, and depression. Those can even affect organic diseases. | The list was refined to incorporate anxiety and depression |
| 3 | medication adherence for example should be written by the physician | The list was refined with medication adherence removed from behavior |
| # | Comment | Response |
|---|---|---|
| 1 | Outdoor air quality: pollution levels (e.g., PM2.5, CO2, ozone), noise levels, weather conditions (e.g., precipitation, wind speed, UV index), radiation exposure, soil quality, water quality (e.g., pH, contaminants), proximity to green spaces, allergens in the environment, electromagnetic field (EMF) exposure, barometric pressure, carbon monoxide levels, ventilation quality, hazardous material presence (e.g., chemicals, asbestos). | The list was expanded to explicitly include the suggested environmental attributes, ensuring broader coverage of factors such as radiation exposure, pollutants, and hazardous materials |
| 2 | Some patients, such as Cancer patients, get exposed to radiation, so it is important to include radiation exposure within the environmental section. | Radiation exposure was added |
| # | Comment | Response |
|---|---|---|
| 1 | HIS applicable, serial number, MAC addresses. The medical devices need to have a property number “the device belongs to the hospital” and an HTM number “the device belongs to the healthcare technology management department ‘HTM’ or you can say the Biomes in the institution. | The list was refined to include serial number, MAC address, property number, and HTM identifiers as device attributes, ensuring proper traceability and management within healthcare institutions. |
| 2 | Device temperature, charging status, device uptime, operating system version, firmware version, peripheral connectivity (e.g., Bluetooth, USB), sensor data (e.g., accelerometer, gyroscope), app permissions, app performance metrics, error logs, device location history, encryption status, data transfer rates, security features (e.g., firewall, antivirus status), available updates, backup status, device manufacturer and model, device warranty information, screen resolution, touch sensitivity, camera specifications. | They are considered as device status information |
| 3 | Any error of defect should be shown on screen especially the critical care devices | The list was revised to include error and defect reporting as an attribute, with emphasis on visibility for critical care devices. The list has been updated |
| # | Comment | Response |
|---|---|---|
| 1 | The demographics terminology generally means the medical information not the personal information. You can use (PID: patient identification) | The category terminology was revised by replacing “Demographics” with “Patient Identification (PID)” to align with expert clarification |
| 2 | Behaviour category needs more investigation. It is not clear if environment is what is surrounding the patient or the medical device? | The definition of behavior data is updated to reflect that (Both are in the same place since these devices are wearable.) |
| Classification | Potential Adverse Impact Level | Score Range (Sensitivity Level) |
|---|---|---|
| Top secret (TS) | High (Catastrophic harm) | 4.6–5.0 |
| Secret (S) | Medium (Severe harm) | 3.7–4.5 |
| Confidential (C) | Low (Moderate harm) | 2.5–3.6 |
| Public (P) | None (Minimal/no harm) | ≤2.49 |
| Score | Definition |
|---|---|
| 1 | Non-identifying; common to a population. |
| 2 | Low uniqueness; requires combination with other data to identify an individual. |
| 3 | Moderate uniqueness; may identify an individual in a small group. |
| 4 | High uniqueness; identifies individuals in a small group. |
| 5 | Globally unique; directly identifies an individual. |
| Score | Definition |
|---|---|
| 1 | No realistic harm; No impact to individuals or operations |
| 2 | Minor inconvenience; Temporary annoyance or minimal privacy impact |
| 3 | Significant privacy invasion; Identity theft risk, personal embarrassment |
| 4 | Serious consequences; Financial loss, discrimination, reputational damage |
| 5 | Life-altering/criminal impact; Blackmail, life-threatening discrimination, legal violations |
| Attribute | Uniqueness | Harm Potential | Score (60/40) | Score (55/45) | Score (65/35) | Classification |
|---|---|---|---|---|---|---|
| GPS Coordinates | 5 | 5 | 5.0 | 5.0 | 5.0 | Top Secret |
| Medical History | 4 | 5 | 4.4 | 4.45 | 4.35 | Secret |
| Heart Rate | 3 | 4 | 3.4 | 3.45 | 3.35 | Confidential |
| Device ID | 1 | 1 | 1 | 1 | 1 | Public |
| Data Type | Uniqueness (1–5) | Expert Scoring | Justification | Harm Potential (1–5) | Expert Scoring | Justification |
|---|---|---|---|---|---|---|
| Social Security Number/National ID | 5 | Correct | 5 | Correct | ||
| Biometric Data (fingerprints) | 5 | Correct | 5 | Correct | ||
| Medical Record ID | 5 | Correct | 4 | 5 | HIPAA PHI | |
| Full Name | 5 | Correct | 3 | 5 | ||
| Home/Mailing Address | 4 | 5 | Refer to an individual | 4 | 5 | can help identify the individual |
| Phone Number | 4 | Refer to an individual | 3 | 5 | HIPAA PHI | |
| Date of Birth | 4 | Correct | 3 | 5 | HIPAA PHI | |
| Email Address | 4 | 5 | unique | 3 | 5 | HIPAA PHI |
| Place of Birth | 3 | 4 | Refer to group of people | 3 | 4 | HIPAA PHI |
| Data Type | Uniqueness (1–5) | Expert Scoring | Justification | Harm Potential (1–5) | Expert Scoring | Justification |
|---|---|---|---|---|---|---|
| Heart Rate | 3 | 4 | 4 | 5 | ||
| Blood Pressure | 3 | 4 | 4 | 5 | ||
| Respiratory Rate | 3 | 4 | 4 | 5 | ||
| SpO2 | 3 | 4 | 4 | 5 | ||
| Medical History | 4 | Correct | 5 | Correct | ||
| Diagnosis | 4 | Correct | 5 | Correct | ||
| Treatment Information | 4 | Correct | 5 | Correct | ||
| ECG | 4 | Correct | 5 | Correct | ||
| EEG | 4 | Correct | 5 | Correct | ||
| EMG | 4 | Correct | 5 | Correct | ||
| Blood Glucose | 4 | Correct | 5 | Correct | ||
| Insulin Levels | 4 | Correct | 5 | Correct | ||
| X-ray imagines | 4 | Correct | 5 | Correct | ||
| CT Scan images | 4 | Correct | 5 | Correct | ||
| MRI images | 4 | Correct | 5 | Correct | ||
| Ultrasound images | 4 | Correct | 5 | Correct | ||
| Laboratory Test Results | 4 | Correct | 5 | Correct | ||
| Body Temperature | 2 | 3 | May identify an individual in a small group. | 3 | Correct | |
| BMI | 2 | 3 | May identify an individual in a small group. | 3 | 4 | may be exploited to discriminate against the individual |
| Height | 2 | 3 | May identify an individual in a small group. | 2 | 3 | may be exploited to discriminate against the individual |
| Weight | 2 | 3 | May identify an individual in a small group. | 2 | 3 | may be exploited to discriminate against the individual |
| Data Type | Uniqueness (1–5) | Expert Scoring | Justification | Harm Potential (1–5) | Expert Scoring | Justification |
|---|---|---|---|---|---|---|
| Anxiety | 4 | Correct | 5 | Correct | ||
| Depression Level | 4 | Correct | 5 | Correct | ||
| Stress Level | 3 | Correct | 4 | 5 | may be exploited to discriminate against the individual | |
| Sleep Duration | 3 | Correct | 3 | 4 | may be exploited to discriminate against the individual | |
| Sleep Stages | 3 | Correct | 3 | 4 | may be exploited to discriminate against the individual | |
| Dietary Habits | 3 | Correct | 3 | 4 | may be exploited to discriminate against the individual | |
| Social Interaction | 3 | 4 | specific to an individual | 3 | 5 | may be exploited to discriminate against the individual |
| Steps | 2 | Correct | 2 | Correct | ||
| Distance | 2 | Correct | 2 | Correct | ||
| Calories Burned | 2 | Correct | 2 | Correct |
| Data Type | Uniqueness (1–5) | Expert Scoring | Justification | Harm Potential (1–5) | Expert Scoring | Justification |
|---|---|---|---|---|---|---|
| GPS Coordinates | 5 | Correct | 5 | Correct | ||
| Environment Radiation Rates | 2 | Correct | 3 | Correct | ||
| Weather Temperature | 1 | Correct | 1 | Correct | ||
| Weather Humidity | 1 | Correct | 1 | 2 | physical attacks | |
| Ambient Light Intensity | 1 | Correct | 1 | 2 | physical attacks | |
| Outdoor Air Quality | 1 | Correct | 1 | 2 | physical attacks | |
| Pollutants | 2 | Correct | 2 | 4 | This can be used to kill them |
| Data Type | Uniqueness (1–5) | Expert Scoring | Justification | Harm Potential (1–5) | Expert Scoring | Justification |
|---|---|---|---|---|---|---|
| Device Serial Number | 5 | Correct | 3 | 4 | Device attack | |
| Hospital Information System (HIS) Name | 3 | Correct | 3 | Correct | ||
| Healthcare Technology Management (HTM) Type | 3 | Correct | 3 | Correct | ||
| Frequency of device Usage | 3 | Correct | 3 | Correct | ||
| Duration of device Usage | 3 | Correct | 3 | Correct | ||
| Feature Utilization | 3 | Correct | 3 | Correct | ||
| Software Version | 2 | 1 | No realistic harm | 2 | 4 | Software attack |
| Processor Type | 2 | 1 | No realistic harm | 2 | 3 | Many attacks |
| Device Memory | 2 | 1 | No realistic harm | 2 | 3 | memory attacks |
| Storage Capacity | 2 | 1 | No realistic harm | 2 | 3 | overflow attacks) |
| Signal Strength | 2 | 1 | No realistic harm | 2 | 3 | WLAN attacks |
| Network Type | 2 | 1 | No realistic harm | 2 | 3 | wireless attacks |
| Device Battery Level | 1 | Correct | 1 | 2 | physical attacks |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alsadhan, A.; Alhogail, A.; Alsalamah, H.A. Toward Efficient Health Data Identification and Classification in IoMT-Based Systems. Sensors 2025, 25, 5966. https://doi.org/10.3390/s25195966
Alsadhan A, Alhogail A, Alsalamah HA. Toward Efficient Health Data Identification and Classification in IoMT-Based Systems. Sensors. 2025; 25(19):5966. https://doi.org/10.3390/s25195966
Chicago/Turabian StyleAlsadhan, Afnan, Areej Alhogail, and Hessah A. Alsalamah. 2025. "Toward Efficient Health Data Identification and Classification in IoMT-Based Systems" Sensors 25, no. 19: 5966. https://doi.org/10.3390/s25195966
APA StyleAlsadhan, A., Alhogail, A., & Alsalamah, H. A. (2025). Toward Efficient Health Data Identification and Classification in IoMT-Based Systems. Sensors, 25(19), 5966. https://doi.org/10.3390/s25195966





