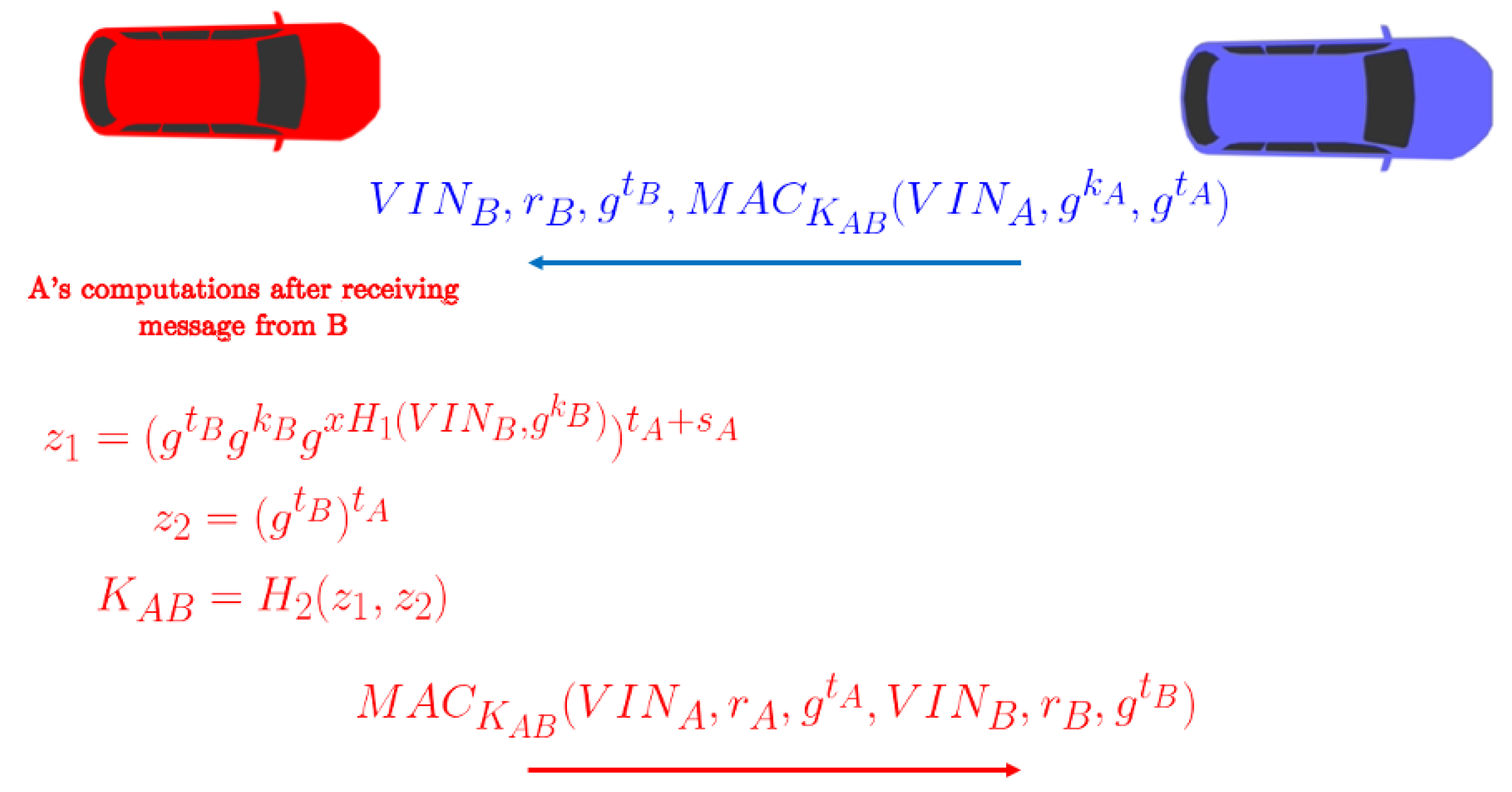1. Introduction
Modern-day vehicles are no longer composed of just hydraulic and mechanical components; they are increasingly becoming closer to robots (“computers with wheels”). Technologies such as Advanced Driver Assistance Systems (ADASs) [
1] and external connectivity improve driver and passenger experience, and can also enable autonomous driving and smart traffic management. In this sense, one can consider cars as hyper-sensorized and connected platforms, with three goals for people transportation: no accidents, no pollution, and no traffic jams.
To realize these goals, three core elements—connectivity, safety, and security—are indispensable for the development and deployment of autonomous vehicles. In particular, vehicular communication entails a major revolution, since information exchange among vehicles (V2V communications), with infrastructure (V2I) (vehicle to infrastructure), or in general with other agents in traffic (V2X), could help to prevent the 1.35 million deaths caused by car accidents worldwide [
2] and reduce the nearly 7 million deaths caused by pollution [
3].
However, the car industry needs to guarantee the security of these communications to prevent their misuse. Misidentifying vehicles can lead to faulty driving decisions, resulting in avoidable safety risks and potential accidents. The aim of this paper was to design and evaluate a secure communication protocol for vehicular networks that replaces traditional PKI-based schemes with identity-based cryptographic mechanisms, using the Vehicle Identification Number (VIN) as a unique identifier. The main contributions of this research to the body of knowledge on V2V communication include a generic IB communication protocol, the use of the VIN as a secure and practical identifier for dynamic key generation in vehicular networks, a real-world prototype implementation demonstrating the feasibility of the proposed approach in a conventional vehicle, and an analysis of performance metrics that highlights the impact of hardware processing capabilities on encryption and decryption operations. In vehicular communications, we can highlight the following standards: IEEE 802.11p [
4], ETSI TS 102 637 [
5], ETSI EN 302 665 [
6], ISO 21217:2014 [
7], IEEE 1609.2 [
8], IEEE 1609.3 [
9], SAE J2735 [
10], ISO 15118 [
11], 5G V2X [
12], ITU-T Y.2060 [
13], and ISO 26262 [
14]. All of these standards show us how V2X communications should function, offering different technical solutions. In these standards and other proposals, various methods are used, such as identification via IP addresses, ICCID (Integrated Circuit Card Identifier), random numbers, license plate readings [
15], etc. In contrast, our contribution allows vehicles to be identified by their VIN, which is the simplest and most natural form of identification. The use of cryptography in these communication protocols enables authentication, which generates trust, enables confidential communication, and prevents the exchanged information from being modified. Some traditional V2X security protocols proposed decentralizing the Certificate Authority’s (CA) tasks to reduce the communication and computation overhead, as well as the dependence on a centralized CA in PKI-based solutions.
Identity-based cryptography, introduced by Shamir [
16], is an alternative to public key cryptography that avoids the use of certificates and the management and updating of Certificate Revocation Lists (CRLs). In this case, arbitrary strings, called identities, can play the role of public keys. These must unequivocally identify users, such as email addresses or social security numbers in the personal communication setting. In the vehicular communication context, the VIN, which uniquely identifies vehicles, serves as an ideal candidate for such identifiers.
In this scenario, anyone can derive the public key of a user from his identity, and his private key is computed by a Key Generation Center (KGC) from the user’s identity and the KGC’s master secret key. In the context of vehicles, this process could be performed by the international normalization bodies in charge of issuing the World Manufacturer Identifiers (WMIs) of traditional frame numbers.
Moreover, when compared to credential management systems, identity-based cryptography avoids handling and securely storing multiple credentials, since key generation is inherently tied to the identities from which the keys are derived. This makes cryptographic schemes easier to integrate and improves scalability for systems with a large number of users, as in the case of vehicles. Privacy-friendly credential management systems also usually involve multiple steps for exchanging, verifying, and validating credentials, which can introduce delays or complexities in the authentication process.
Several identity-based cryptosystems have been proposed, including encryption, digital signature, and key establishment protocols. One can highlight the schemes by A. Shamir [
16], D.Boneh and Franklin [
17], C. Gentry and A. Silverberg [
18], R. Sakai, K. Ohgishi and M. Kasahara [
19], and C. Boyd and K. R. Choo [
20]. Most of these make use of pairings (bilinear maps) [
21], while some avoid their use to obtain more efficient protocols [
22] or so that they can resist quantum attacks [
23]. For our real test, we selected D. Fiore et al.’s [
22] protocol, which can be applied over any cyclic group of prime order, and for which the Diffie–Hellman problem is intractable (no known efficient algorithm can solve it). This protocol is extremely efficient and only requires one round of communication with short messages, which makes it suitable for this application.
There are several applications for the proposed communication protocol called “V2V Secure communication protocol based on digital VIN number” and its generalization to V2X communications, such as the following:
Digital documentation: This could allow us to authenticate a vehicle with law enforcement authorities. With a slight modification, new functionalities could be added, such as recording vehicle history, including data related to the vehicle’s repairs, owners, and technical reports.
Tolls: The car could communicate with infrastructure without requiring any more specific hardware, making payments easier. This would be a universal system for identifying the vehicle and communicating the necessary information independently of the highway controller (the payment process is outside of the scope of this paper).
Payment method: Unequivocal identification can allow vehicles to serve as payment gateways, making applications possible in places such as gas stations, fast food kiosks, etc. The integrated On Board Unit (OBU) could have a graphic console, adapted to the navigator screen, so that these kinds of transactions could be accepted.
V2X Identification: The information coded in the VIN provides details about a vehicle’s features. Therefore, its identification against other components is very useful for information exchange. This has multiple applications: determining the length of a vehicle, locating a pedestrian, creating digital signage, providing traffic jam solutions, etc.
Repair workshops: Currently, the reception process at repair workshops is often tedious because a lot of time is required to make a repair order. This period could be shortened with our communication system, since cars would be able to very quickly send the owners’ details and information about failures or servicing to the workshop’s admission area.
Gas stations: The system could avoid accidental fuel refills and allow a much faster payment.
The manuscript is organized in the following way:
Section 2 presents a review of the state of the art in secure V2V communication protocols, highlighting the most relevant approaches and their limitations.
Section 3 describes the proposed protocol in detail, specifically designed to ensure secure communication between vehicles using identity-based cryptography.
Section 4 and
Section 5 present the experimental validation, evaluating the feasibility and effectiveness of the protocol.
Section 6 summarizes the main findings of the work, emphasizing the practical utility of the developed protocol. Finally,
Section 7 discusses potential future research directions aimed at improving and extending the proposed system.
2. Related Work
As with any other type of computer system, being able to identify users is essential to develop applications that require authentication systems. In this sense, V2X applications are no exception.
Vehicular communication can be classified into two types: internal, which includes transmissions among different Electronic Control Units (ECUs), usually based on the CAN Bus (Controller Area Network) protocol [
24], and external, known as V2X (vehicle-to-everything) [
25], which links vehicles to the environment through radio frequencies, WiFi, or 5G connections and which is mainly defined by the IEEE 802.11P [
26] and 5G [
27] standards. V2X communications are usually classified as follows [
28]:
V2V: connections among vehicles, in order to, for example, avoid collisions; vehicles can share position and speed data to interact and be able to react faster than the driver.
V2P (vehicle-to-pedestrian): connections between vehicles, pedestrians, or riders for detection, alert notification, and accident prevention.
V2I: connections between vehicles and road infrastructures to manage the priority and timing of traffic signs, optimizing the traffic.
V2N (Vehicle-to-network): connections between vehicles and the cloud to route traffic, to develop real-time traffic management, Beyond the Visual Line Of Sight (BVLOS) warnings, etc.
V2H (Vehicle-to-home): connections between vehicles and homes to implement, for example, door opening once the car is parked.
Security and privacy issues in vehicular networks have been extensively reported in the literature. Secure communication is essential for the adoption of V2X technologies, since it is required to ensure the safety and security of future connected and autonomous cars.
To carry out a complete assessment of the state of the art in V2X communications, we have organized this section into an analysis of technologies for the secure identification of vehicles, an analysis of communication standards (mainly based on WiFi and 5G), and an examination of V2V secure communication protocols.
2.1. Vehicle Identification
Vehicle identification is an essential phase in ITSs (Intelligent Traffic Systems), and so there have been many studies on the topic. Some of them rely on car license plate recognition, which was developed in 1976 at the Police Scientific Development Branch (PSDB) in the UK [
29].
Johnson and Bird [
30] proposed knowledge-guided boundary following and template matching for automatic vehicle identification. In 1990, Lotufo, Morgan, and Johnson [
31] proposed automatic number plate recognition with optical character recognition techniques. Later, Fahmy [
32] proposed Bidirectional Associative Memory (BAM) neural networks for number plate reading. In 2010, Changshui et al. [
33] showed how an identification system could be used to analyze vehicle handling and stability, and subsequently, Jeevagan et al. [
34] proposed the development of vehicle identification using Radio Frequency Identification (RFID).
Later, in 2018, Satsangi et al. [
15] compared thresholding optical character recognition (OCR) and machine learning approaches for license plate recognition, and in 2019 [
35], Kohli and Sharma studied the possibility of identifying vehicles through GSM (Global System for Mobile Communications) signals.
The use of the VIN and identity-based cryptography in car-related communication has already been proposed by Groza et al. in 2020 [
36], but our work goes one step further by using this concept in a digital version.
In 2023, ref. [
37] proposed a solution involving density-based traffic management using Arduino, a GSM module, and RFID. Also in 2023, ref. [
38] proposed a cooperative method to identify vehicles in autonomous driving using registration numbers (VRNs). Currently, blockchain technology is also being used for vehicle identification. For instance, the proposal in [
39] illustrated how its use facilitates identification through the various physical forms of vehicles. The issue of vehicle identification was also present in [
40], who explained how to create an efficient authenticated key agreement scheme, titled STCLA, designed for fog-based IoV, adopting certificateless cryptography. It is also worth highlighting that the latest studies on vehicle recognition using license plates with the Yolo V8 algorithm achieved an overall recognition accuracy of 98.05 percent [
41]. Our study shows that the identification of vehicles can be achieved in different ways, including identification through their license plate, through an RFID device, or even through their form, but no article has yet shown the possibility of identifying vehicles by the chassis number in digital format, in
Table 1 we can see a classification.
2.2. WiFi vs. 5G Communications
After having studied vehicular connections, we can describe them as emerging networks whose principal technologies are WiFi and 5G. In this section, we will review their main characteristics, together with their advantages and disadvantages.
WiFi under the 802.11P standard, also known as WAVE (Wireless Access for the Vehicular Environment), has the key features shown in
Table 2. It represents a positive development with respect to the IEEE 802.11A standard, since it has physical and MAC (Media Access Control) improvements. Their importance lies in the fact that they serve as the basis for direct V2V communications.
This kind of communication is known as DSRC (Dedicated Short Range Communication) and is ideal for providing real-time support to cooperative systems [
42].
5G or Cellular C-V2X is a communication technology with a shorter range that employs current mobile phone coverage using license specter networks. It connects large spaces and can be used for V2I services that require less latency (Technology 3G and 4G LTE Release 14). The new 5G (3GPP Release 16) will be the key enabler for V2X, with three main features: ubiquitous connectivity for large sets of users, very low latency, and high-speed Gigabit connection. Its principal characteristics are presented in
Table 3.
The WiFi 802.11P DSRC and 5G C-V2X standards are supported by large committees. The best way to increase road safety and decrease road fatalities is not to choose one standard, but to use a hybrid communication approach in which WiFi [5.9 GHz] and 5G [3.x GHz] technologies work together.
2.3. V2V Secure Communication Protocols Using Identity-Based Cryptography
Nowadays, countless applications, papers, patents, and research studies exist related to vehicular communications, but none of them have used the VIN in digital format as a car identifier. We will summarize the main results in this field.
V2V communication is an emerging technology that helps nearby moving vehicles communicate with each other. In this way, Vibin et al. [
42] presented the design and development of a V2V communication system that collects vehicle-related data and transmits it over WiFi to the vehicles in its vicinity.
New car equipment applications like longitudinal and lateral vehicle following control systems that use radar can help to reduce traffic jams. For instance, Wei et al. [
43] proposed a method to calculate the trajectory of the preceding vehicle based on its historical movement data transmitted among vehicles.
Car manufacturers, insurance companies, workshops, and telecommunications operators, etc., are aware that, in the near future, new connectivity services will create new models of business. A good example is the car manufacturing company SEAT, which has created a strategy for urban mobility called SEAT CODE [
44].
Zhao et al. [
45] presented a system to create car platooning by adjusting their distance according to traffic using an ECAN module to communicate with the CAN bus. Hwang et al. [
46] described a new method that responds with the necessary ECUs for a specific V2V message. None of these developments were carried out from the perspective of cybersecurity. Identity-based (IB) cryptography has previously been used for V2V communications [
47]. Andreica and Groza [
48] identified vehicles and used this identification number to bootstrap security based on identity-based cryptographic schemes. They also introduced the use of license plates as a means to identify vehicles by applying identity-based schemes [
48]. In the VANETs (Vehicle Ad hoc Networks) setting [
47], Shuhaimi and Juhana [
47] studied IB schemes in order to provide security and privacy for VANETs. In other situations where privacy is required, other proposals using pseudonyms (random identifiers) [
49] or group signatures have been used [
50]. In 2025 N. Gopinath, K. L. Narayanan, S. Sageengrana, and M. Meenaksh studied a hybrid authentication architecture for VANETs combining certificate-based and identity-based cryptography with machine-learning-based attack detection, achieving significant improvements in latency, scalability, and detection accuracy [
51]. However, most of these proposals did not specify which information is used for the identity.
In some proposals, the authors specified the identity used. For example, in [
48], license plates were used as identities. They are first recognized by smartphone cameras located in the vehicles. However, the string that is usually used for vehicle identification is the Vehicle Identification Number, since it is unique, while the license plate number can change if the vehicle is reregistered, for example, in a different country. This identity was used by Groza et al. [
36] for car access control with a smartphone. However, they recognized the VIN using a smartphone and did not use its digital version.
3. Identity-Based V2V Secure Communication Protocol
As previously discussed, it is necessary to design and implement a secure communication protocol, where communications can be performed in a limited time. Latency and computing capacity restrictions make traditional approaches ineffective; thus, we propose a protocol that uses the identities of vehicles.
In this section, we propose a generic communication protocol between two vehicles which guarantees confidentiality, authentication, and integrity. This protocol builds on a one-round two-party Identity-Based Key Establishment Scheme and an AEAD (authenticated encryption with associated data) scheme [
52], and uses the Digital Vehicle Identification Number as the identity. The protocol begins with the establishment of a session key using a one-round key exchange scheme based on identity-based authentication, followed by an AEAD scheme for message exchange between the vehicles.
There is a preliminary setup phase where the system’s public parameters and the private key of the KGC are established. The authority responsible for this management calculates each vehicle’s private key, based on its VIN and secret information, and provide this to the vehicle.
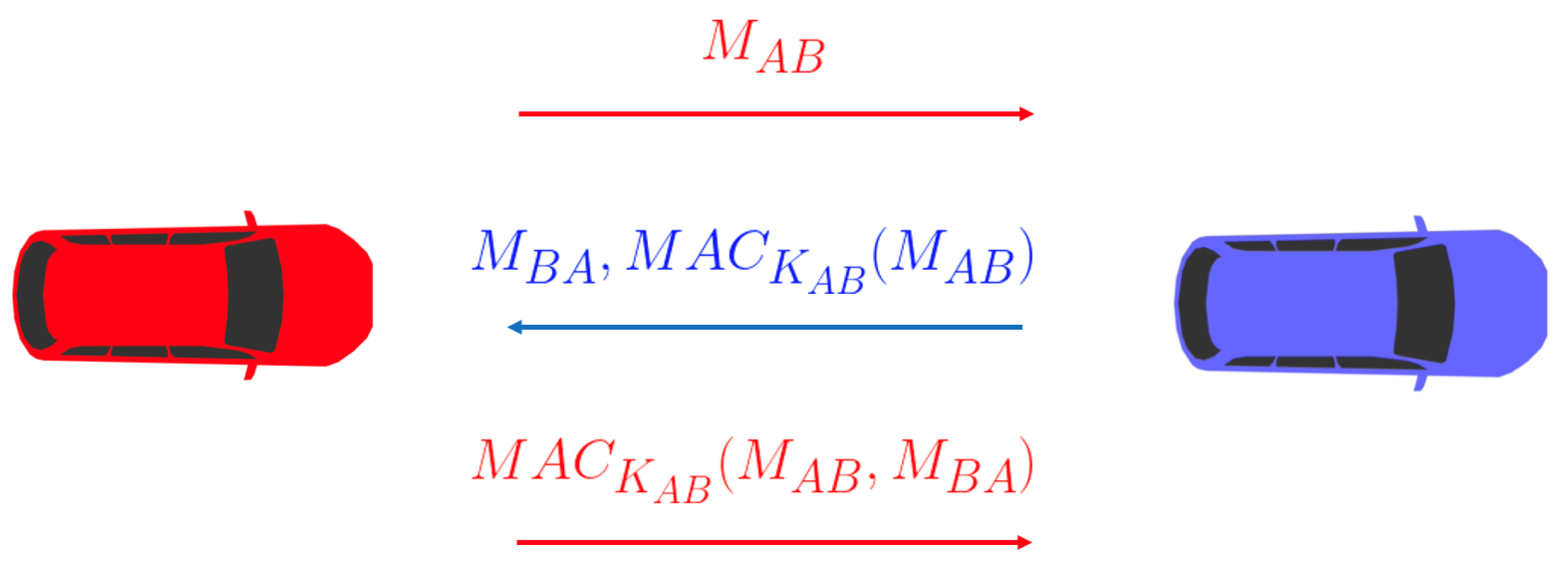
Subsequently, message exchange between the two vehicles occurs, with authentication based on their digital VINs. Vehicle B adds a Message Authentication Code (MAC) to the message sent, calculated using the shared key generated from the message sent by vehicle A. The exchange concludes with vehicle A sending an MAC, calculated using all exchanged messages, to vehicle B as a key confirmation. Once the vehicles have shared the common key, they can begin exchanging information using an authenticated encryption scheme.
3.1. The Digital Vehicle Identification Number
The VIN is the usual way to uniquely identify a vehicle for administrative purposes. It is equivalent to a passport or national ID numbers for people.
In its current format, the VIN comprises 17 characters and was standardized in 1983 by ISO 3779 [
53], which defines its structure as showed in
Figure 1. There are some differences between the European and American formats, and the characters can be either numbers or letters (except for I, O, Q, and Ñ). The VIN has to be easily readable and located in a safe, tamper-proof place. It is usually located under the hood or inside the vehicle, directly engraved in the frame.
Although there are many options for identifying vehicles, the main approach is obtaining the VIN directly from the car’s documents or from the vehicle frame; the problem with this method is that it is very slow and not a digital solution. It is employed, for instance, in workshops and technical inspections. Another way to achieve this is by reading the number plate, with the problematic aspect of relying on number plates, which can be changed or altered. This is used in public parking areas and by traffic control cameras. Moreover, RFID systems can automate identification when vehicles pass through tolls, but they cannot identify the car, they only identity an RFID system. Recent work has proposed a CNN-based approach combining data augmentation and multi-task learning for efficient and accurate vehicle model identification in forensic contexts, improving upon traditional manual methods. [
55].
A digital version of the VIN has recently been proposed [
56]. In this patent claim, this digital VIN can be accessed through the OBD2 (On-Board Diagnostics 2) diagnosis socket, mandatorily present in vehicles under the SAE J1979 standard [
57] and its European counterpart, the ISO 15031 [
58].
The OBD2 standard can provide us with this number using a simple and universal instruction PID 0x02 issued to any vehicle. This instruction returns the VIN extracted from the ECU in hex format.
3.2. Cryptographic Tools
To build our V2V secure communication protocol, we make use of different cryptographic tools, both symmetric and asymmetric. In this section, we describe their main features regarding security.
3.2.1. Message Authentication Codes
Integrity and authentication are essential cryptographic goals. To achieve them with symmetric cryptography tools, one can make use of Message Authentication Codes (MACs).
To achieve this, when party A sends a message to party B, A appends to the message an authentication tag, computed by the MAC algorithm as a function of the message and the shared secret key. Party B, when receiving this information, recomputes the authentication tag in the received message using the MAC with the shared key and checks whether the obtained value is equal to the received tag. In this case, one can see that the message has not been altered and has been sent by a party knowing the shared secret key.
Some efficient constructions of message authentication schemes are based on cryptographic hash functions and derive their security from these. We use the HMAC (Hash-based Message Authentication Code) construction, with the SHA-256 hash function [
59].
3.2.2. Authenticated Encryption with Associated Data
AEAD is a symmetric tool that provides both confidentiality and authentication for the encrypted text, and also allows us to check the integrity and authentication of additional associated data that are sent in the clear. It was introduced by Rogaway [
60].
It can be built by combining MACs and symmetric ciphers, using block cipher modes of operation. There are dedicated algorithms for this task.
In our proof of concept, we use AES-256 (Advanced Encryption Standard) with the Galois Counter Mode (AEAD_AES_256_GCM), because AES provides faster performance, lower resource usage, and high efficiency.
3.2.3. Identity-Based Key Establishment Scheme
Key establishment schemes allow two or more users to agree on a common key that can afterwards be used in a symmetric key algorithm. These protocols are usually interactive, and each round of messages that are sent at the same time is called a round.
A desired security requirement is that the protocol is authenticated; i.e., the users are sure about who they are agreeing the key with. For this, a Public Key Infrastructure might be needed, with its corresponding shortcomings.
To avoid such disadvantages, an identity-based approach can be used, where users only need to know their counterpart’s identity to establish a key in an authenticated manner. The KGC is in charge of creating the private keys corresponding to the identities and sending them to the users.
An instance of the protocol is called a session, which has different variables associated with it, indicating, for example, the session state, the peers, whether the session has aborted, the session identifier, etc.
The adversary controls all the communication and can insert, delay, modify, or intercept the messages exchanged. Moreover, it has access to different information, such as the private keys of users, session keys, or the ephemeral information of the session. A party is said to be corrupted if the adversary has obtained its private key, all its session states, and all session keys currently stored, and is controlled by the adversary.
Definition 1. An identity-based key-agreement protocol is said to be secure if, for any probabilistic polynomial time adversary , the following holds:
If two parties not corrupted by the adversary complete matching sessions, then they will compute the same session key with overwhelming probability;
The probability that guesses the correct bit b when it is provided either with a random session key (if the randomly chosen bit is 1) or with the real session key (if the randomly chosen bit is 0) is at most plus a negligible function on the security parameter.
We refer to [
22] for a more formal description of the security model.
In our proof of concept, we use the protocol of Fiore et al. [
22]. A description can be found in
Appendix A.
3.3. Secure V2V Communication Protocol
In this section, we propose a secure communication protocol. It builds on a one-round two-party Identity-Based Key Establishment Scheme, so that two vehicles can agree on a key to be used afterwards with an AEAD scheme [
52].
Before the exchange of messages, there is a setup phase, where public parameters and the master secret key of the Key Generation Center (KGC) are established. The KGC, to create a private key for a vehicle, takes its
and the master secret key to compute
. The KGC sends each vehicle its private key, as shown in
Figure 2.
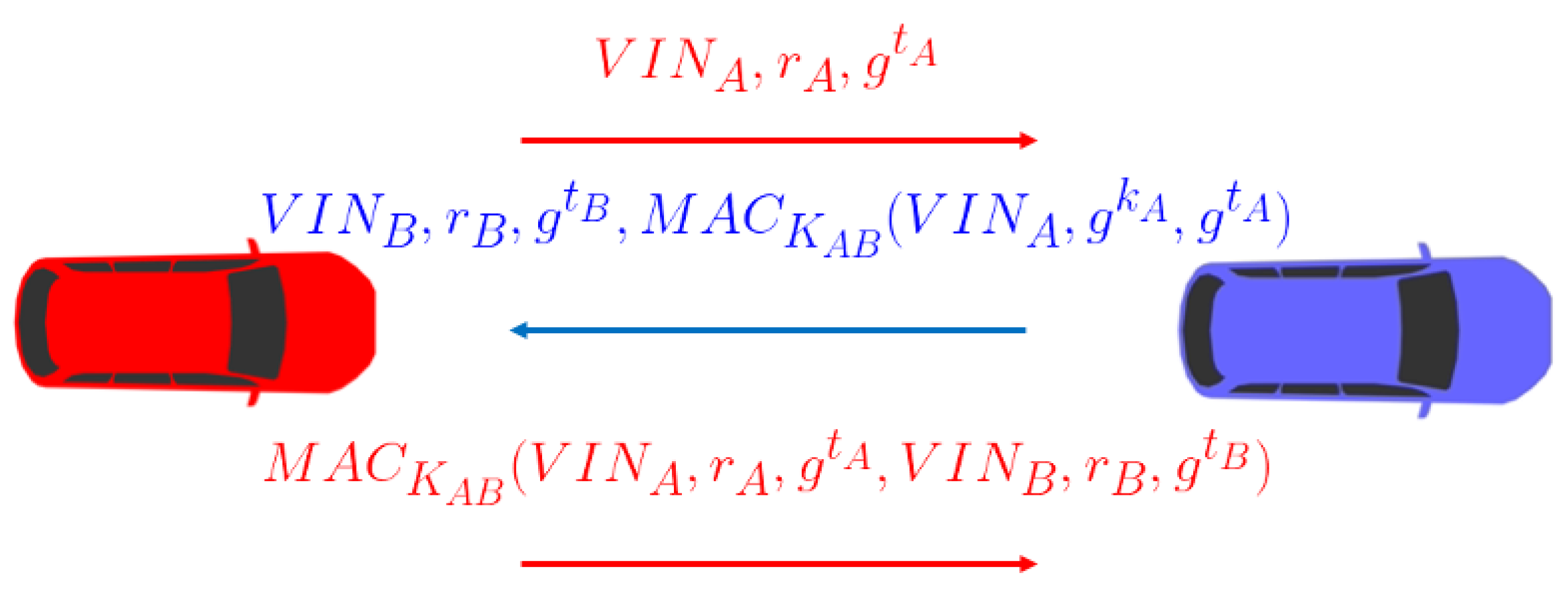
Afterwards, both vehicles exchange messages, authenticated based on the digital VIN, and moreover, they compute the tag generated by the MAC in the message sent by vehicle
B and the common key established with vehicle
A. The communication ends with vehicle
A sending a tag from all the messages exchanged with the common key established, acting as key confirmation. The protocol is sketched in
Figure 3.
Once the vehicles have shared a common key, they use an AEAD scheme to securely communicate.
This protocol is secure for any secure one-round two-party Identity-Based Key Establishment Scheme.
Theorem 1. Let be a one-round two-party Identity-Based Key Establishment Scheme which is secure in the sense of Definition 1; then, the proposed communication protocol provides confidentiality, integrity, and authentication.
In our proof-of-concept implementation, to instantiate the proposed protocol, we used the IB key establishment scheme by Fiore and Gennaro [
22], which is secure under the
Strong Diffie–Hellman Assumption. A description of the protocol can be found in
Appendix A, and we used HMAC-SHA256.
The proposed protocol inherits the security from Fiore and Gennaro’s construction, and therefore, its security relies on the strong Diffie–Hellman assumption in the Random Oracle Model (see [
22] for the security proof). This protocol is very efficient, since it does not make use of bilinear maps, which makes it suitable for this scenario. The vehicle private keys generated by the KGC are shown in
Figure 4.
The communication flow of the protocol instantiated with Fiore and Gennaro’s IB Key Establishment Scheme using the VIN as identity can be seen in
Figure 5.
Moreover,
Figure 6 and
Figure 7 show the intermediate computations performed by vehicles
B and
A, respectively, after receiving the other vehicle’s message.
Subsequently, we use the established key for an AEAD. In particular, we use AES-256 with the Galois Counter Mode (AEAD AES 256 GCM).
We decided to use AEAD since it combines both encryption and authentication in a single, efficient operation, which makes it a strong choice for secure communication and data protection.
In particular, we chose AES-256 with the Galois Counter Mode, since it provides faster performance, lower resource usage, high efficiency, and strong security. AES is the current standard for block ciphers and has been widely analyzed and used over many years. Moreover, AES-GCM is widely supported in both hardware and software implementations, making it a highly accessible choice. In addition, modern processors have built-in support for AES operations, which further boosts the speed of AES-GCM.
4. Proof of Concept
The general aims of the built PoC were as follows:
- 1.
To demonstrate that the VINs of the two cars can be read through their own CAN Bus.
- 2.
To validate that it is possible to create a secure WiFi communication between both cars, using the proposed protocol based on Identity-Based Cryptography, described in
Section 3.3.
- 3.
To measure the processing time needed to send a message or to establish a common key and exchange a message using an AEAD in two different scenarios.
To summarize, the PoC demonstrated that the digital VIN is a secure and viable way to identify vehicles and showed two different applications. It was very important to know the processing time, since many uses require a near-real-time communication system. We show that the solution proposed is viable and that we could characterize its main quantitative metrics, to measure and quantify its computational performance.
The analysis of the logs obtained in the PoC enabled us to define the specific hardware needed to comply with latency requirements. It was important to assess how vehicle speed would affect the proposed system.
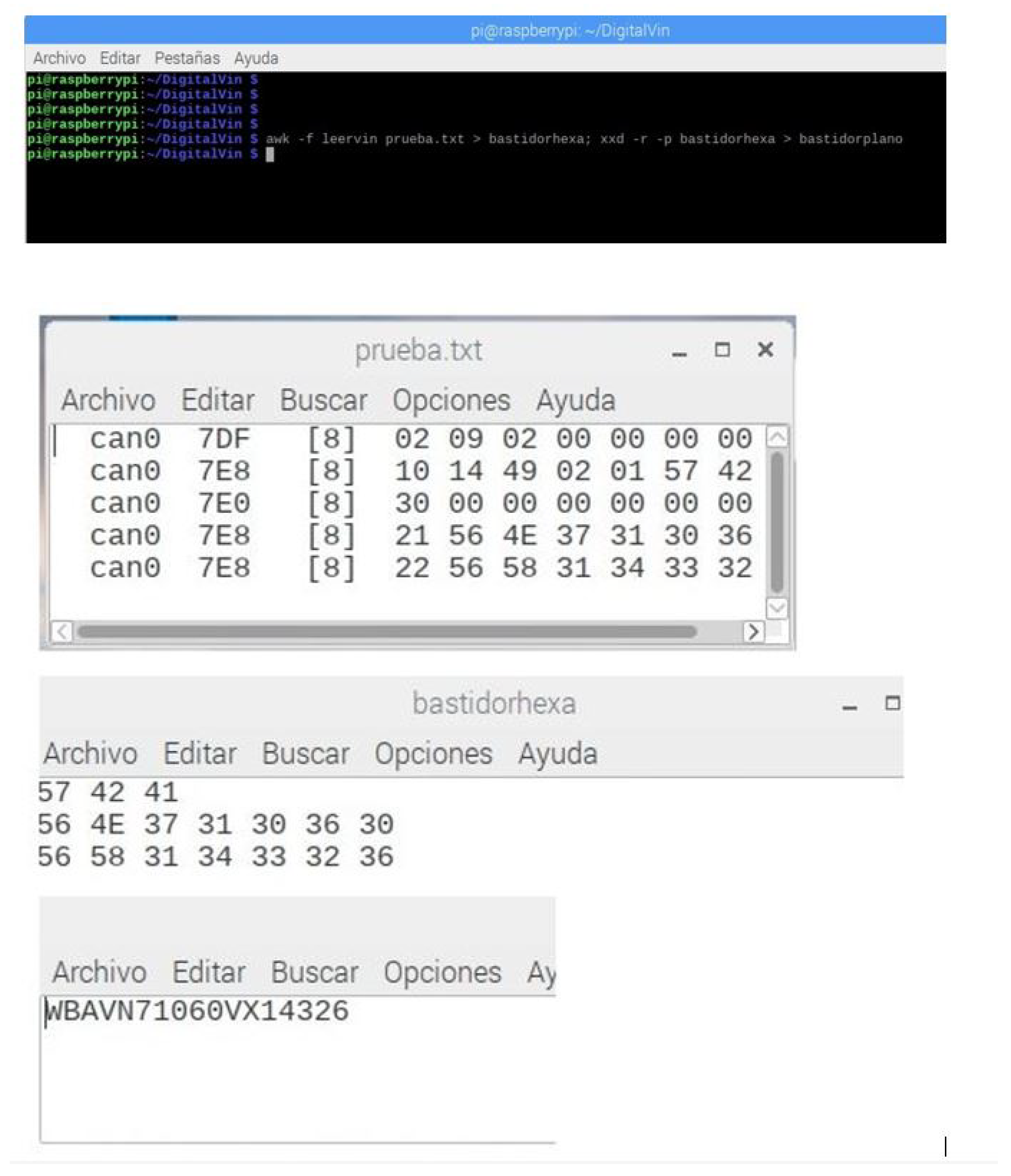
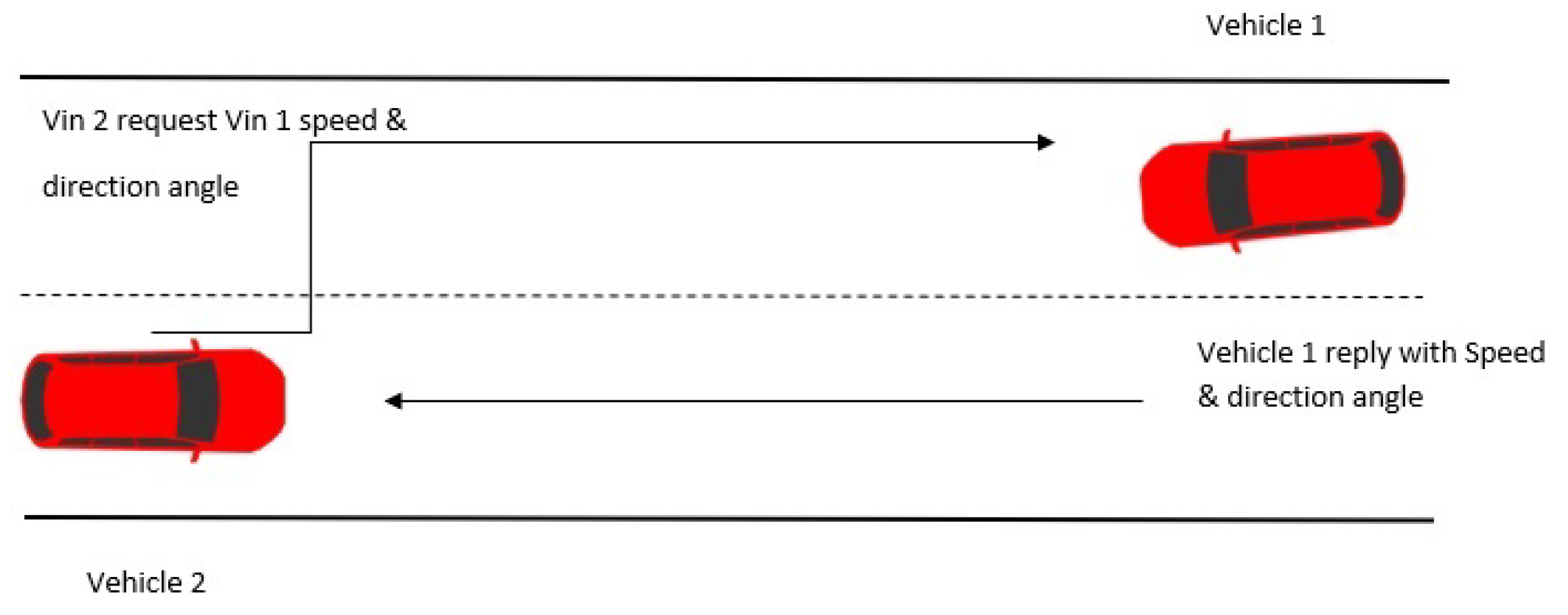
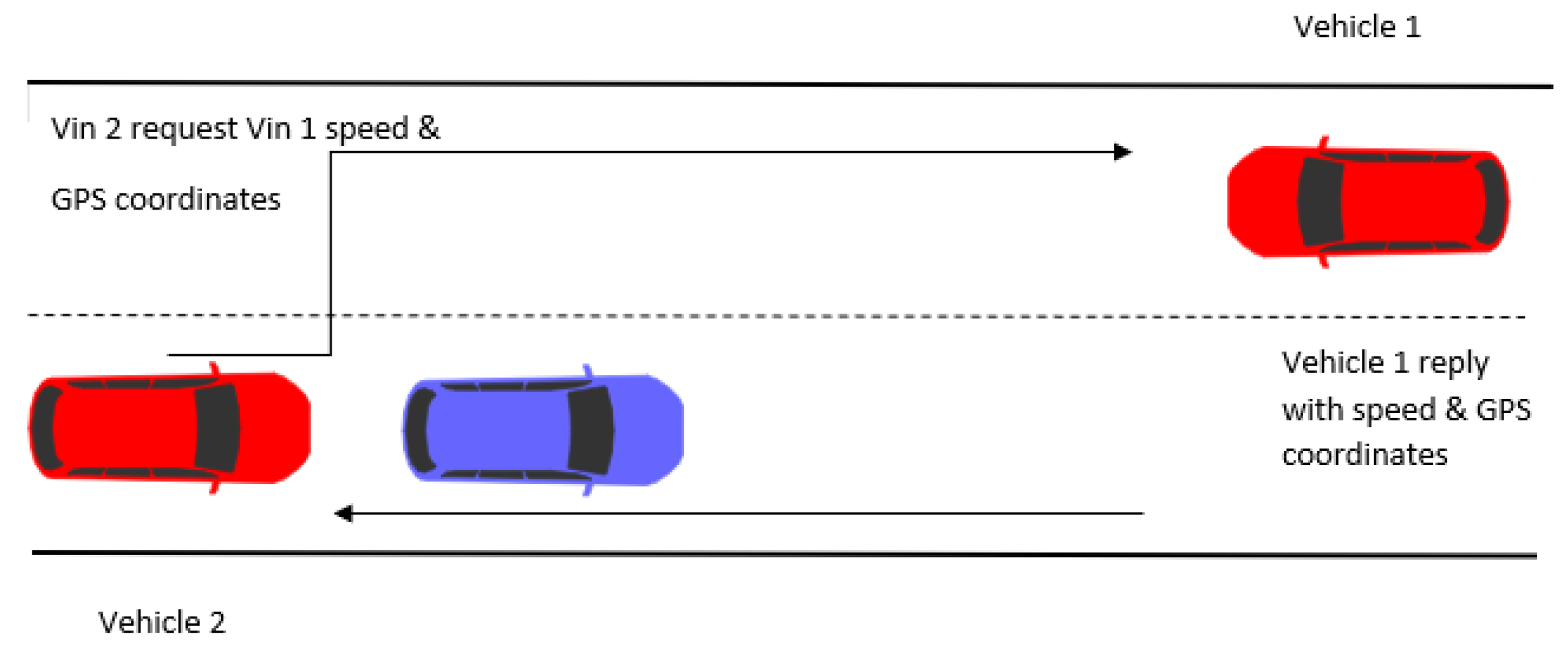
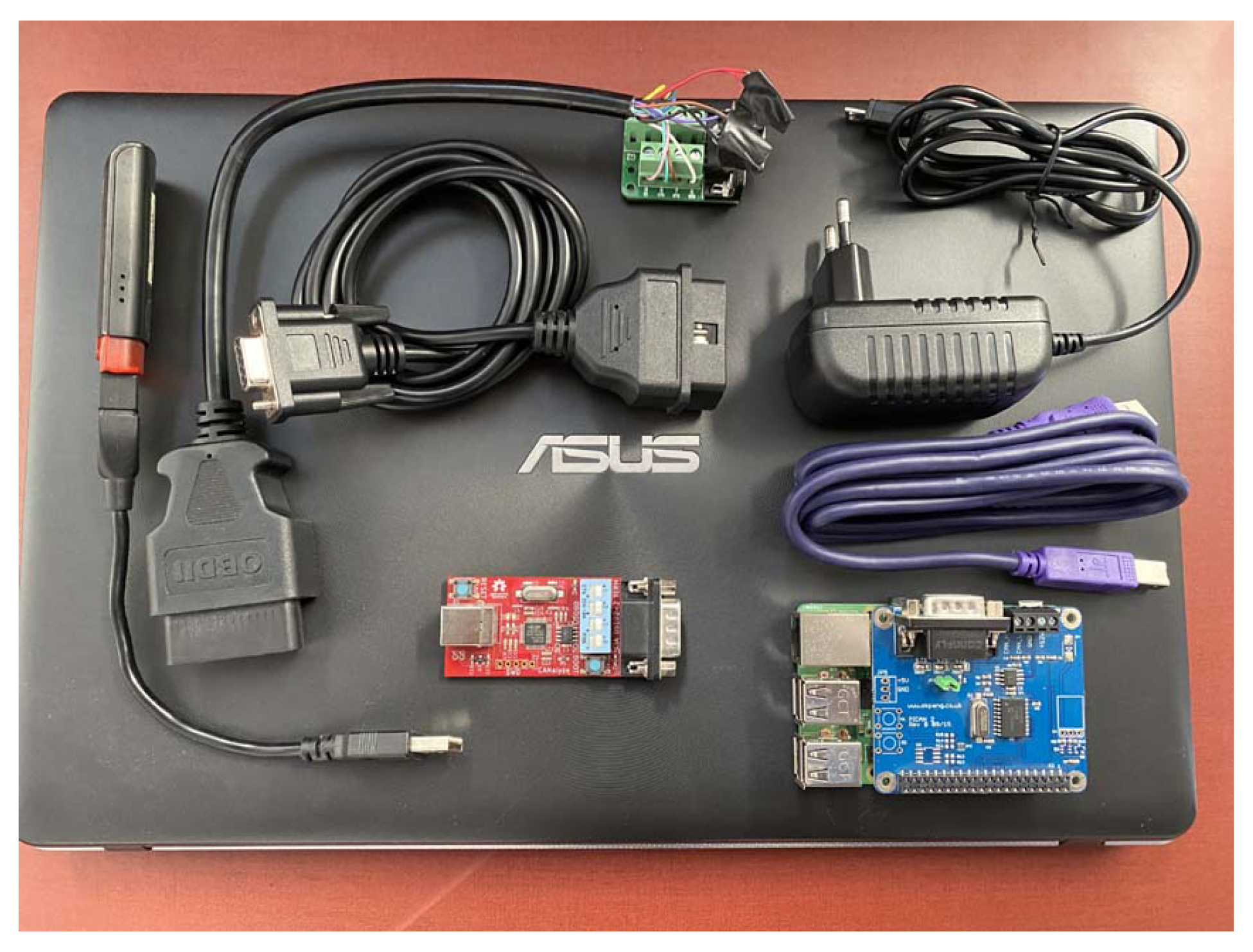
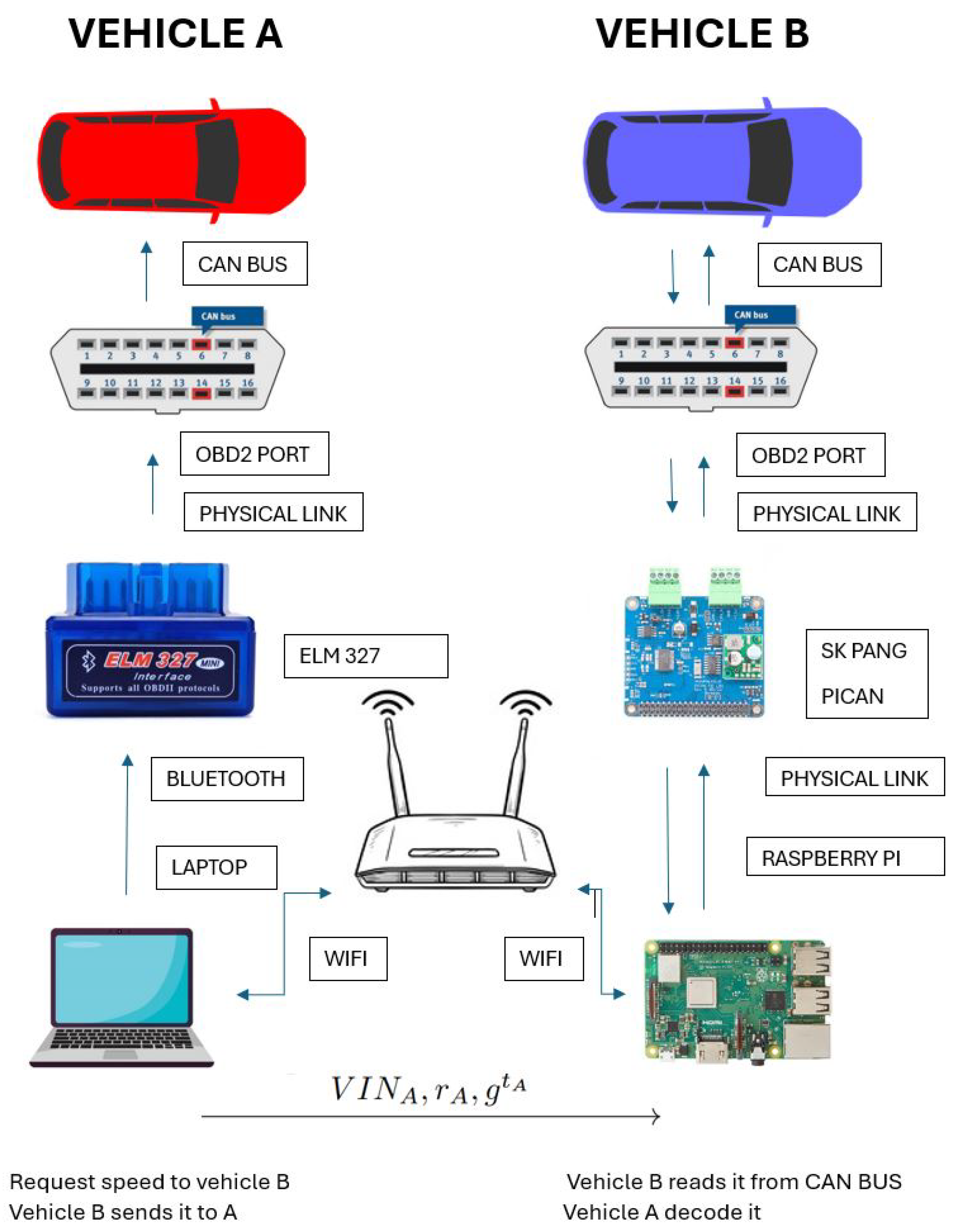
A prototype was implemented and tested in a real scenario. The goal of the prototype was to show that data can be sent from the CAN bus of the first vehicle to the second vehicle. To ensure secure transmission, we needed to obtain VINs through the OBD2 diagnostic port to use them as identifiers.
The method was as follows: First, once the setting is configured (all elements are in the same WiFi network) and we have connected all the elements, the VINs of both cars are read. This can be accomplished by sending the PIDs (Parameter IDs), which are codes used to request data from a vehicle, used as a diagnostic tool. In
Table A1, we can see the PIDs needed to obtain the VIN. Afterwards, we establish an encrypted connection using the VINs obtained by implementing the IB-based scheme described in
Figure 6 and
Figure 7. This protocol generates a common key that must then be used for the AEAD. Finally, speed or GPS details can be requested and sent between both cars.