UHF RFID Sensing for Dynamic Tag Detection and Behavior Recognition: A Multi-Feature Analysis and Dual-Path Residual Network Approach
Abstract
1. Introduction
- We develop a diversity suppression model to reduce interference with the signal from tag and human characteristics.
- We construct a 3D feature space incorporating the IQR temporal fluctuation index, cumulative phase difference, and tag-state evaluation metrics, combined with an improved isolation forest algorithm, to achieve precise dynamic tag detection.
- We develop a behavior recognition model to segment behavior streams and use Doppler frequency analysis to identify specific behavior characteristics and changes. We also construct a time-frequency map based on wavelet transform to illustrate energy changes in behavior and propose a dual-path residual network to recognize behaviors such as taking away, putting back, picking up, and putting back.
- We develop an optimization engine for marketing strategies in a retail scenario to convert behavior recognition results into actionable business decisions.
2. Related Work
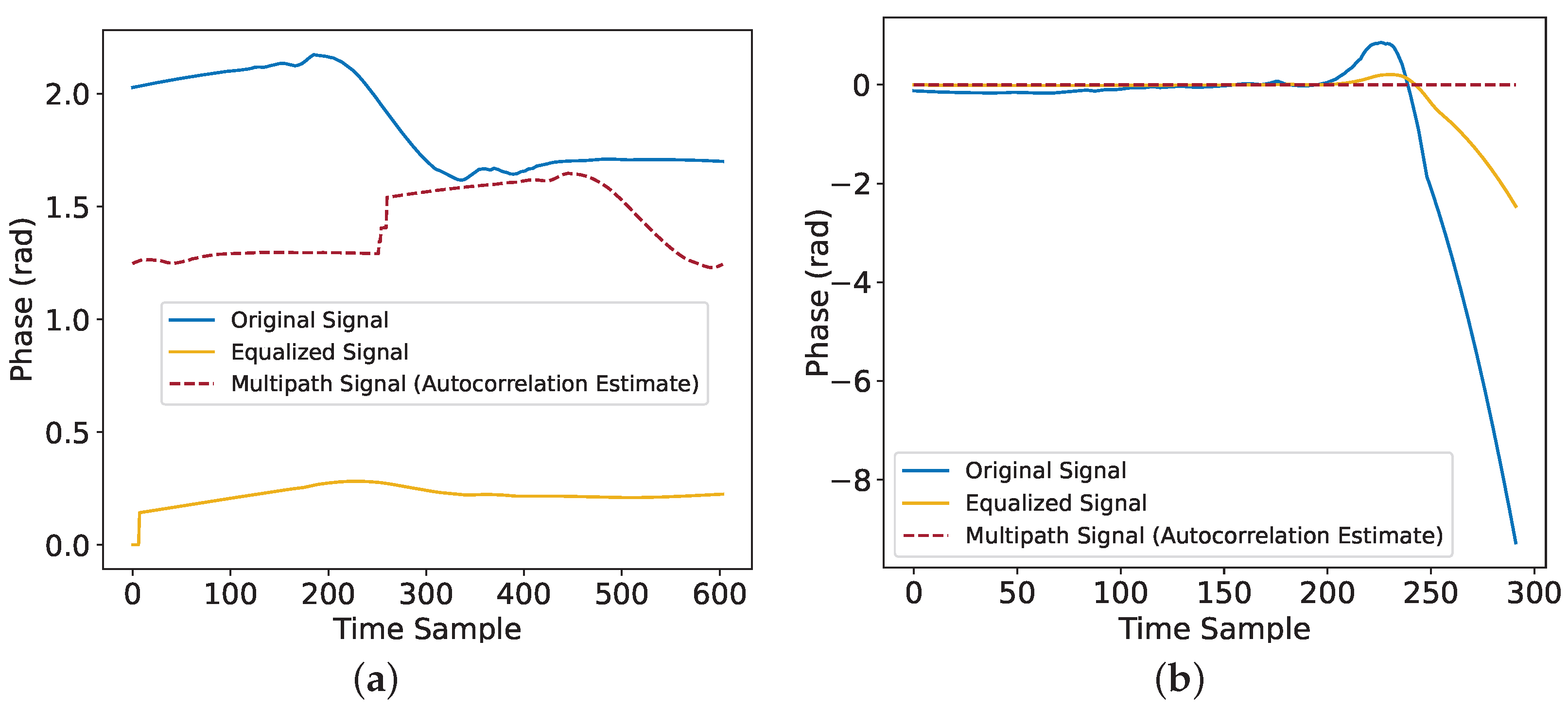
2.1. Autocorrelation Method to Mitigate Multipath Effects
2.2. Behavior Recognition Based on Doppler Frequency Shift
2.3. Behavior Recognition Based on Deep Learning
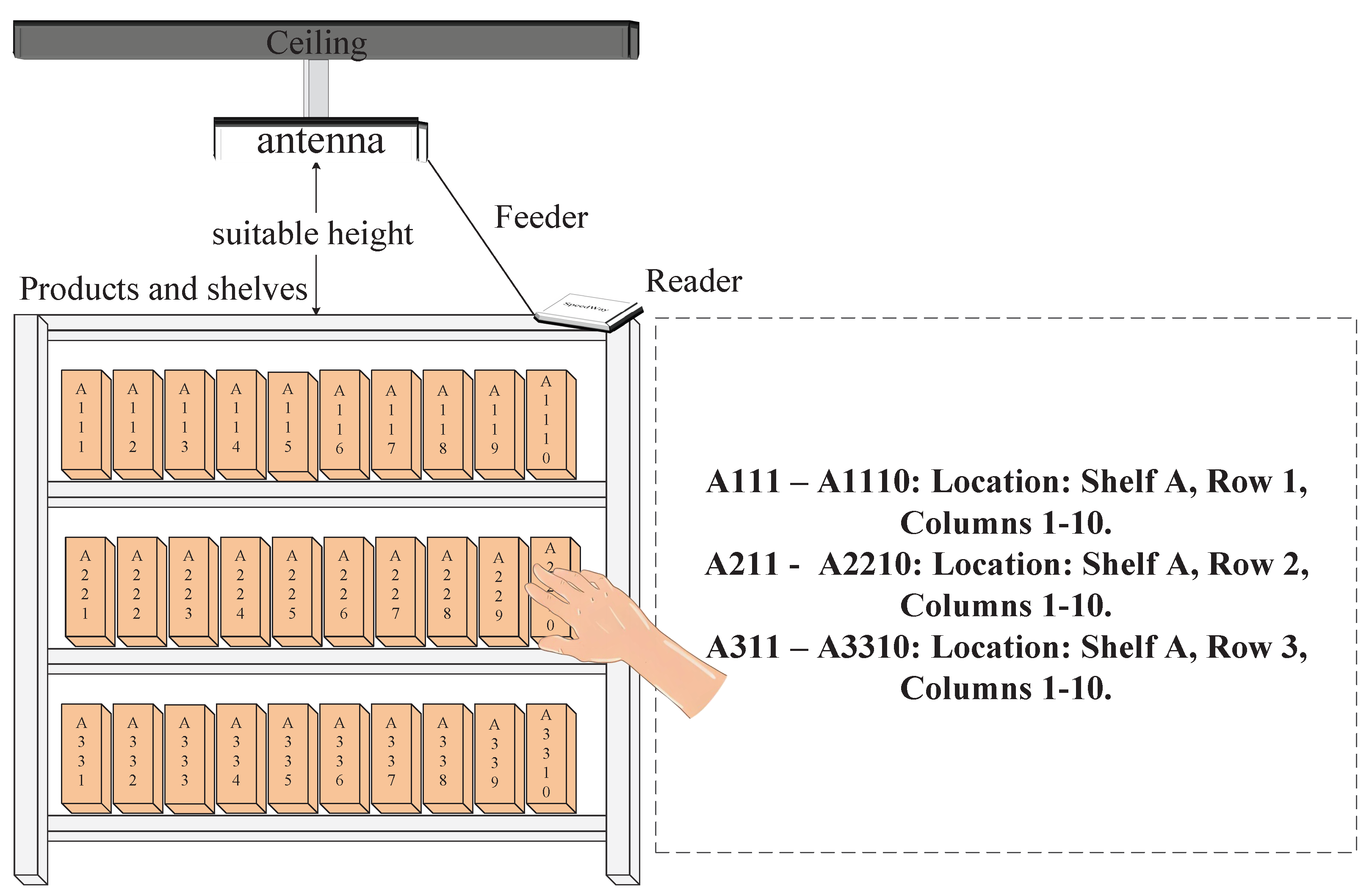
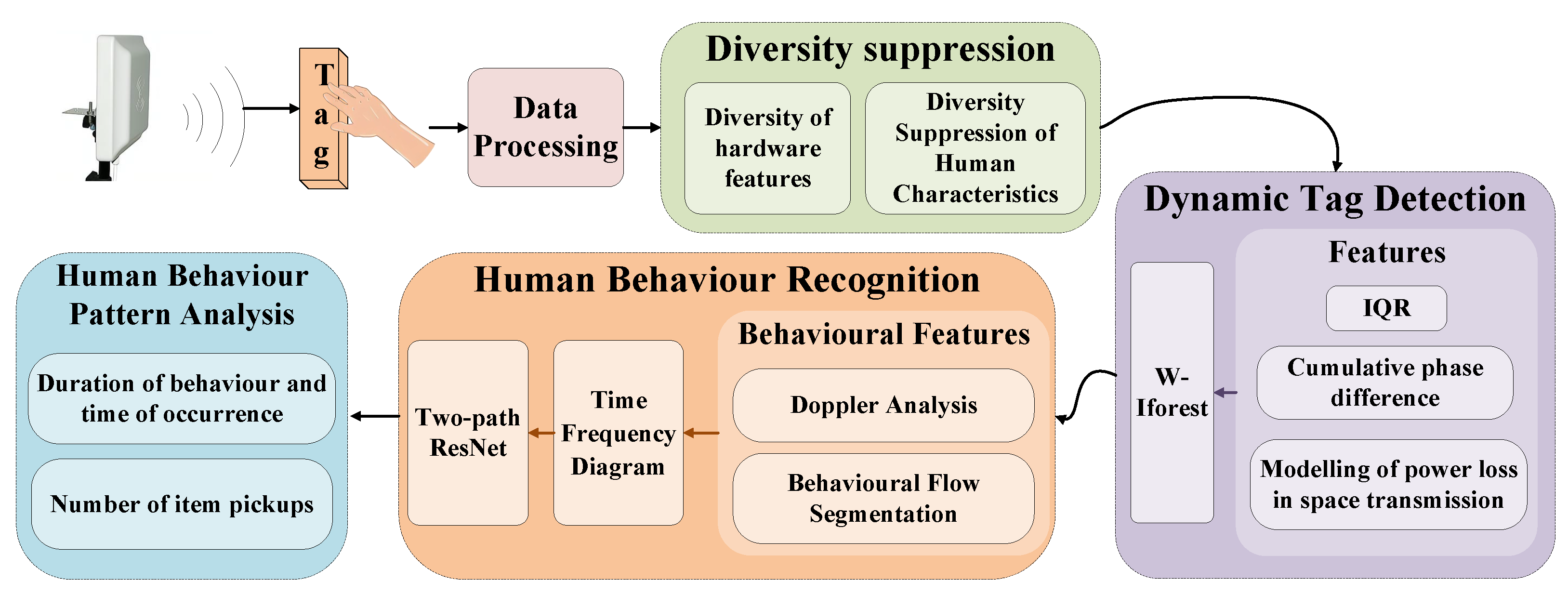
3. System Overview
- (1)
- Preprocessing of labeled data using phase unwrapping and smoothing filtering;
- (2)
- Diversity suppression to effectively reduce tag hardware characteristics and environmental and human interference;
- (3)
- Dynamic tag detection, using a three-dimensional feature matrix containing IQR time-domain fluctuations, cumulative phase difference phase-domain dynamics, and tag-state evaluation indicators, combined with an improved isolation forest algorithm for dynamic tag detection;
- (4)
- Behavior recognition utilizing Doppler frequency to analyze behavior characteristics, combined with wavelet transform to generate time-frequency maps of behavior energy features and a dual-path residual network for behavior classification;
- (5)
- Analysis of key indicators, such as the number of times tags are picked up or put back and the duration of behavior, to analyze human behavior patterns.
4. System Design
4.1. Data Preprocessing
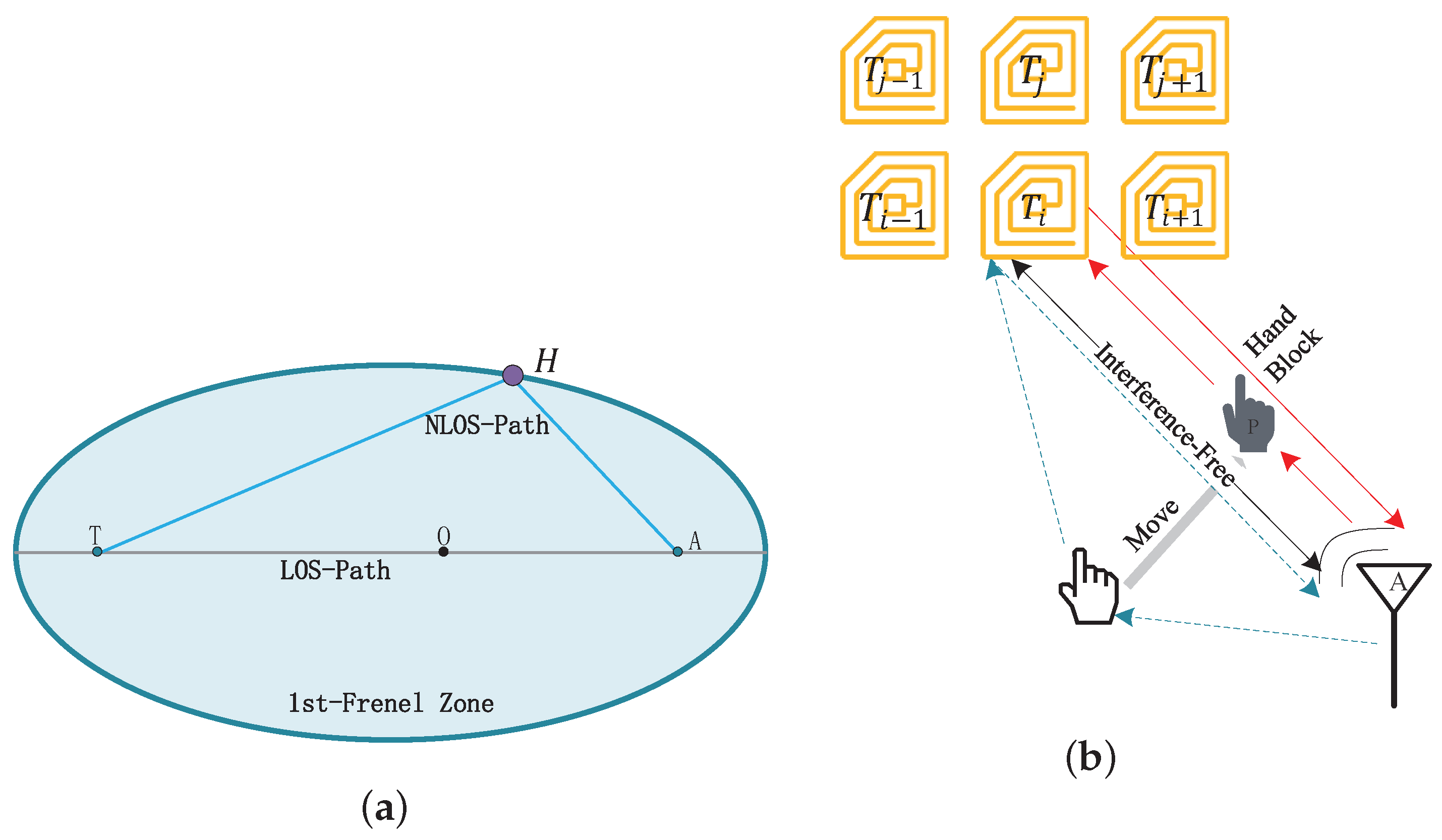
4.2. Feature Diversity Suppression
4.2.1. Tag Hardware Feature Suppression
4.2.2. Suppression of Human Characteristics
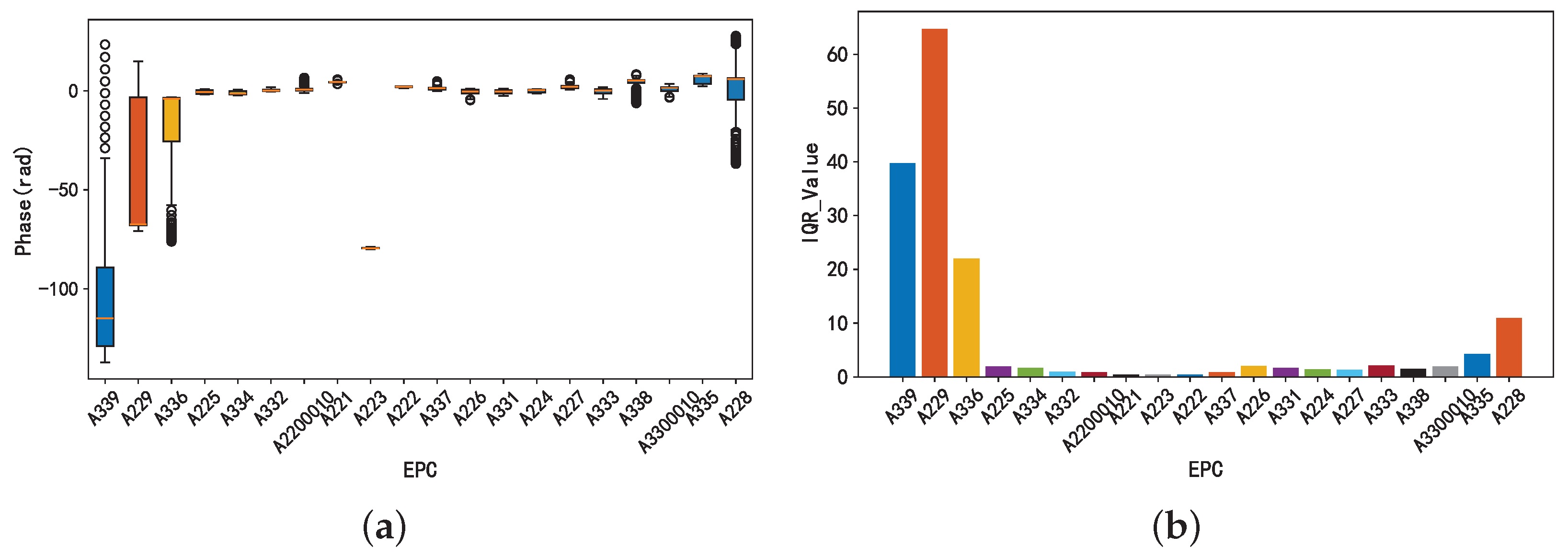
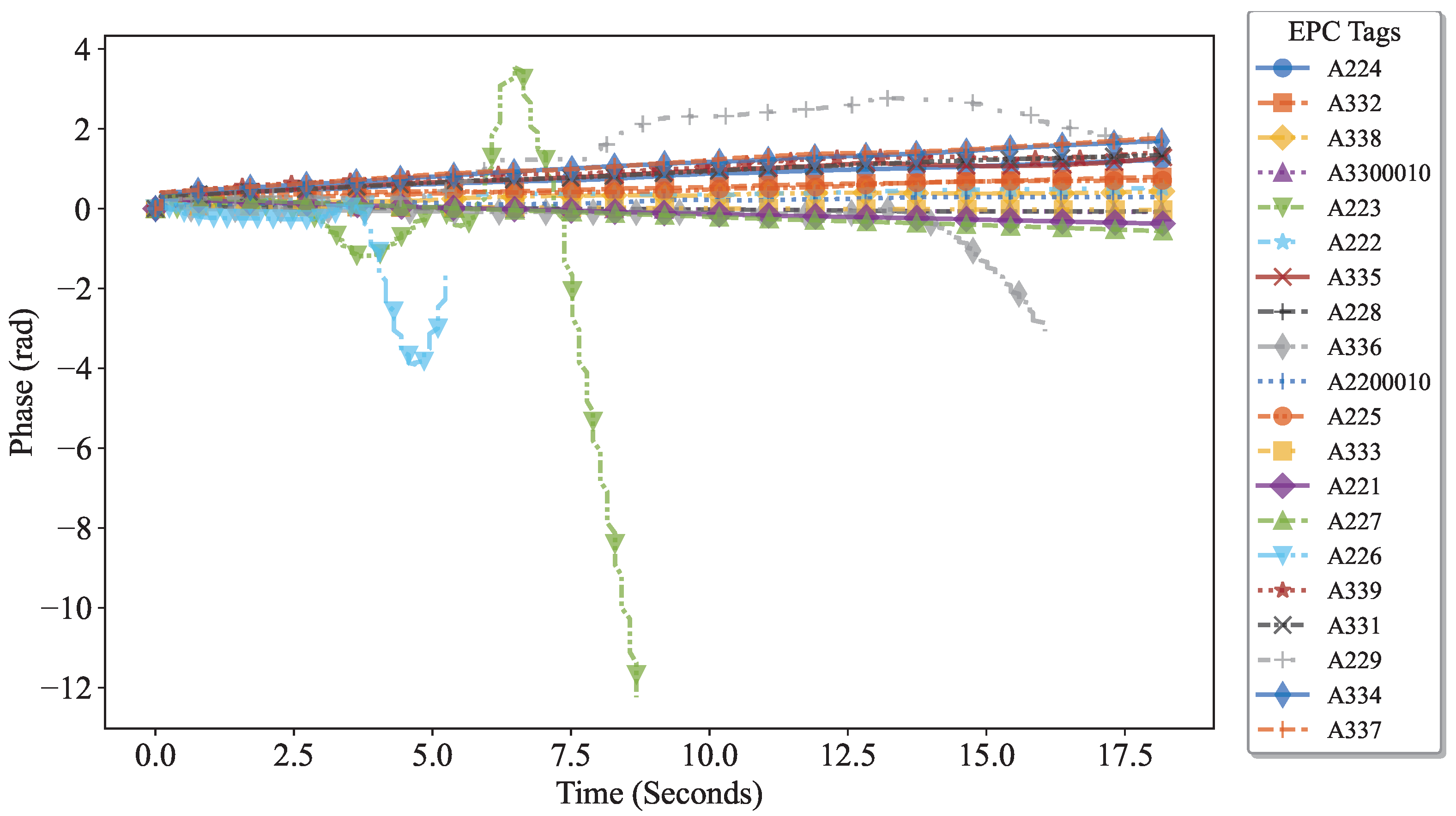
4.3. Dynamic Tag Detection
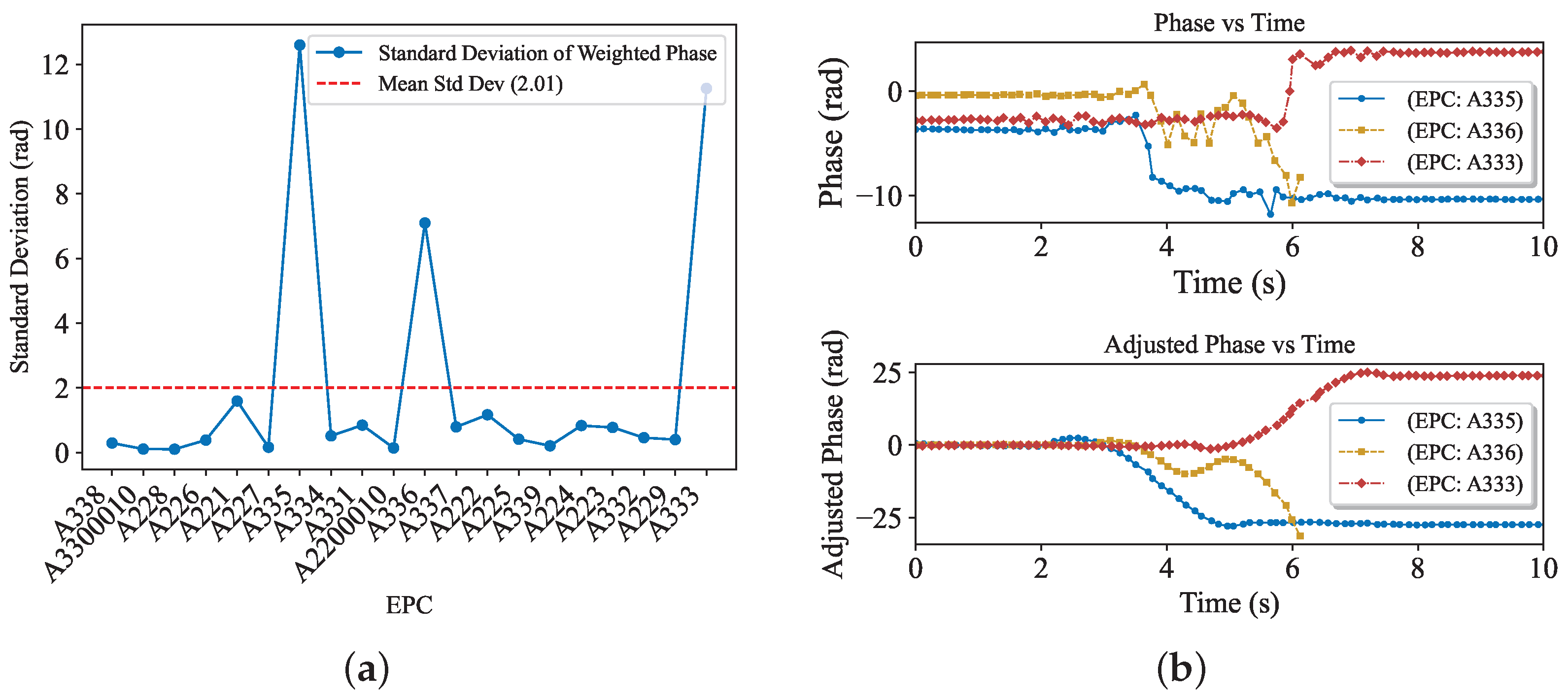
4.3.1. Volatility Analysis
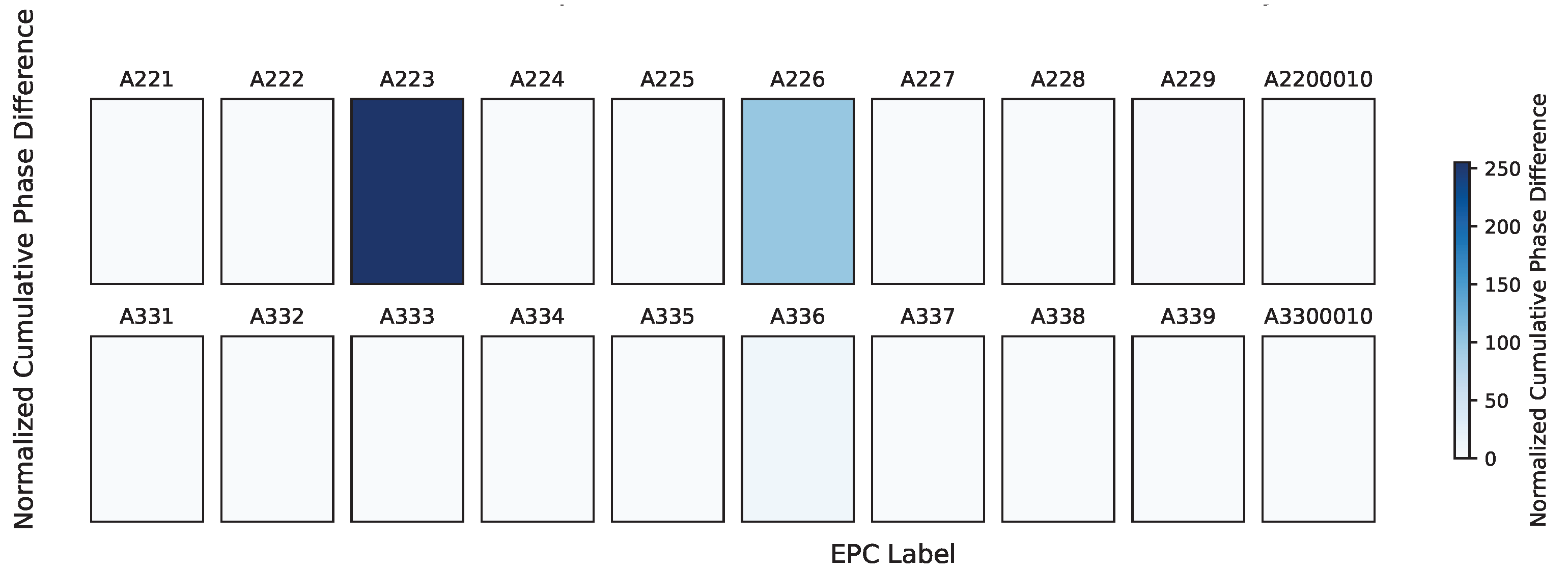
4.3.2. Phase Characteristic Analysis
4.3.3. Analysis of the Human Body’s Impact on Signal Characteristics
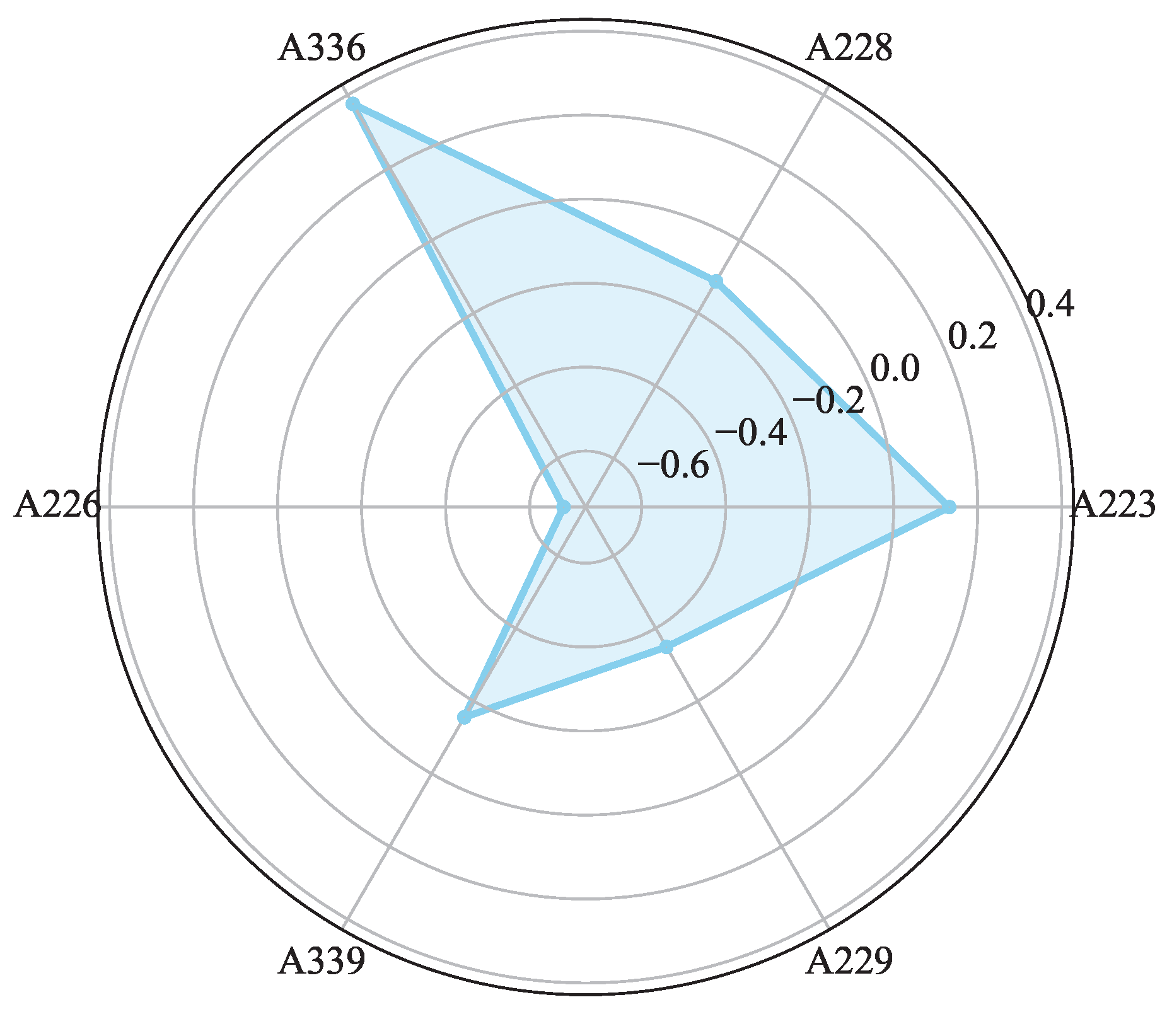
4.3.4. Dynamic Tag Detection
| Algorithm 1: Weighted Isolation Forest (W-IF). |
|
4.4. Behavioral Recognition Model
4.4.1. Behavioral Analysis
4.4.2. CWT-Frequency Analysis of Behavioral Characteristics
4.4.3. Behavior Recognition Model Based on Dual-Path Residual Network
5. System Implementation and Evaluation
5.1. Human Behavior Pattern Analysis
5.2. Experimental Evaluation
5.2.1. Experimental Setup
5.2.2. Evaluation of Experimental Results
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Nikpour, B.; Sinodinos, D.; Armanfard, N. Deep Reinforcement Learning in Human Activity Recognition: A Survey and Outlook. IEEE Trans. Neural Netw. Learn. Syst. 2025, 36, 4267–4278. [Google Scholar] [CrossRef]
- Hussain, Z.; Sheng, Q.Z.; Zhang, W.E. A review and categorization of techniques on device-free human activity recognition. J. Netw. Comput. Appl. 2020, 167, 102738. [Google Scholar] [CrossRef]
- Lara, O.D.; Labrador, M.A. A Survey on Human Activity Recognition using Wearable Sensors. IEEE Commun. Surv. Tutor. 2013, 15, 1192–1209. [Google Scholar] [CrossRef]
- Padilla-Lopez, J.R.; Chaaraoui, A.A.; Florez-Revuelta, F. Visual Privacy Protection Methods: A Survey. Expert Syst. Appl. 2015, 42, 4177–4195. [Google Scholar] [CrossRef]
- Han, J.; Qian, C.; Wang, X.; Ma, D.; Zhao, J.; Xi, W.; Wang, Z. Twins: Device-free Object Tracking using Passive Tags. IEEE/ACM Trans. Netw. 2016, 24, 1605–1617. [Google Scholar] [CrossRef]
- Zou, Y.; Xiao, J.; Han, J.; Wu, K.; Li, Y.; Ni, L.M. GRfid: A Device-Free RFID-Based Gesture Recognition System. IEEE Trans. Mob. Comput. 2017, 16, 381–393. [Google Scholar] [CrossRef]
- Yao, L.; Sheng, Q.Z.; Ruan, W.; Li, X.; Wang, S.; Yang, Z. Unobtrusive Posture Recognition via Online Learning of Multi-dimensional RFID Received Signal Strength. In Proceedings of the International Conference on Parallel and Distributed Systems, Melbourne, VIC, Australia, 14–17 December 2015; pp. 1–6. [Google Scholar] [CrossRef]
- Ruan, W.; Ruan, W.; Sheng, Q.Z.; Yao, L.; Li, X.; Falkner, N.J.; Yang, L. Device-Free Human Localization and Tracking with UHF Passive RFID Tags: A Data-Driven Approach. J. Netw. Comput. Appl. 2018, 104, 78–96. [Google Scholar] [CrossRef]
- Ma, X.J.; Ji, Q.R.; Li, L.Y.; Zhao, Y.; Liu, B.Y.; Chen, F. A low-cost device-free activity recognition method. J. Northwest Univ. (Nat. Sci. Ed.) 2018, 48, 1–10. [Google Scholar] [CrossRef]
- Zhu, S.; Lv, H.; Huang, W. RF-AcSense: Device-Free Activity Localization and Recognition via Passive RFID Tag Array. In Proceedings of the 49th IEEE Conference on Local Computer Networks (LCN), Normandy, France, 8–10 October 2024; pp. 1–9. [Google Scholar] [CrossRef]
- Golipoor, S.; Sigg, S. RFID-based Human Activity Recognition Using Multimodal Convolutional Neural Networks. In Proceedings of the 29th IEEE International Conference on Emerging Technologies and Factory Automation (ETFA), Padova, Italy, 10–13 September 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Liu, M.; Chen, Y.; Zheng, H.; Huang, L.; Zhao, K.; Zhao, Y. Skeleton-Based Human Activities Fine-grained Recognition with RFID Technology. In Proceedings of the 2024 9th International Conference on Signal and Image Processing (ICSIP), Nanjing, China, 12–14 July 2024; pp. 6–12. [Google Scholar] [CrossRef]
- Shangguan, L.; Zhou, Z.; Zheng, X.; Yang, L.; Liu, Y.; Han, J. ShopMiner: Mining Customer Shopping Behavior in Physical Clothing Stores with COTS RFID Devices. In Proceedings of the 13th ACM Conference on Embedded Networked Sensor Systems, Seoul, Republic of Korea, 1–4 November 2015; pp. 1–12. [Google Scholar] [CrossRef]
- Zhang, Z.; Law, C.L.; Gunawan, E. Multipath Mitigation Technique Based on Partial Autocorrelation Function. Wirel. Pers. Commun. 2007, 41, 145–154. [Google Scholar] [CrossRef]
- Xiong, W.; Tian, Y.; Dai, X.; Zhang, Q.; Liang, Y.; Ruan, X. Analysis of Multi-GNSS Multipath for Parameter-Unified Autocorrelation-Based Mitigation and the Impact of Constellation Shifts. Remote Sens. 2024, 16, 4009. [Google Scholar] [CrossRef]
- Zhang, J.; Yu, J.; Ma, Y.; Liang, X. RF-RES: Respiration Monitoring with COTS RFID Tags by Dopplershift. IEEE Sens. J. 2021, 21, 24844–24854. [Google Scholar] [CrossRef]
- Chen, Y.; Yu, J.; Kong, L.; Zhu, Y.; Tang, F. Sensing Human Gait for Environment-Independent User Authentication Using Commodity RFID Devices. IEEE Trans. Mob. Comput. 2024, 23, 6304–6317. [Google Scholar] [CrossRef]
- Huang, K.; Ma, Y.; Chu, Y.; Wang, Z. Tag-Fall: A Doppler Shift-Based Fall Detection Method Using RFID Passive Tags. IEEE J. Radio Freq. Identif. 2024, 8, 252–261. [Google Scholar] [CrossRef]
- Ding, H.; Shangguan, L.; Yang, Z.; Han, J.; Zhou, Z.; Yang, P.; Zhao, J. FEMO: A Platform for Free-weight Exercise Monitoring with RFIDs. In Proceedings of the 13th ACM Conference on Embedded Networked Sensor Systems, Seoul, Republic of Korea, 1–4 November 2015; pp. 83–190. [Google Scholar] [CrossRef]
- Han, J.; Ding, H.; Qian, C.; Xi, W.; Wang, Z.; Jiang, Z.; Zhao, J. CBID: A Customer Behavior Identification System Using Passive Tags. IEEE/Acm Trans. Netw. 2016, 24, 2885–2898. [Google Scholar] [CrossRef]
- Zheng, H.; Chen, Y.; Li, Y.; Wang, Z.; Chen, J.; Zhu, X. High-Accuracy and Fine-Granularity Human Activity Recognition Method Based on Body RFID Skeleton. IEEE Trans. Consum. Electron. 2024, 70, 1040–1051. [Google Scholar] [CrossRef]
- Liu, W.; Wang, J.; Li, B.; Wang, L. Enabling Fine-Grained Shopping Behavior Information Acquisition with Dual-RFID-Tags. IEEE Trans. Mob. Comput. 2020, 7, 7539–7549. [Google Scholar] [CrossRef]
- Chen, Z.; Yang, M.; Hou, X.; Yang, L.; Dong, W.; Yu, B.; Wang, Q. RFID-Based Indoor Human Behavior Recognition Using SATCN: A Self-Attention Enhanced Temporal Convolutional Network. In Proceedings of the 2024 27th International Conference on Computer Supported Cooperative Work in Design (CSCWD), Tianjin, China, 8–10 May 2024; pp. 2852–2857. [Google Scholar] [CrossRef]
- Huang, W.; Liu, Y.; Zhu, S.; Wang, S.; Zhang, Y. TSCNN: A 3D Convolutional Activity Recognition Network Based on RFID RSSI. In Proceedings of the 2020 International Joint Conference on Neural Networks (IJCNN), Glasgow, UK, 19–24 July 2020; pp. 1–8. [Google Scholar] [CrossRef]
- Zhao, C.; Wang, L.; Xiong, F.; Chen, S.; Su, J.; Xu, H. RFID-Based Human Action Recognition Through Spatiotemporal Graph Convolutional Neural Network. IEEE Internet Things J. 2023, 10, 19898–19912. [Google Scholar] [CrossRef]
- Ali, K.; Liu, A.X.; Chai, E.; Sundaresan, K. Monitoring Browsing Behavior of Customers in Retail Stores via RFID Imaging. IEEE Trans. Mob. Comput. 2022, 21, 1034–1048. [Google Scholar] [CrossRef]
- Ding, S.; Chen, Z.; Zheng, T.; Luo, J. RF-Net: A Unified Meta-learning Framework for RF-enabled One-shot Human Activity Recognition. In Proceedings of the 18th ACM Conference on Embedded Networked Sensor Systems, ACM, Virtual Event, 16–19 November 2021; pp. 1–14. [Google Scholar] [CrossRef]
- Khean, V.; Kim, C.; Ryu, S.; Khan, A.; Hong, M.K.; Kim, E.Y.; Kim, J.; Nam, Y. Human Interaction Recognition in Surveillance Videos Using Hybrid Deep Learning and Machine Learning Models. Comput. Mater. Contin. 2024, 81, 773. [Google Scholar] [CrossRef]
- Wu, H.; Tao, B.; Gong, Z.; Yin, Z.; Ding, H. A Fast UHF RFID Localization Method Using Unwrapped Phase-Position Model. IEEE Trans. Autom. Sci. Eng. 2019, 16, 1698–1707. [Google Scholar] [CrossRef]
- Maguire, Y.; Pappu, R. An optimal Q-algorithm for the ISO 18000-6C RFID protocol. IEEE Trans. Autom. Sci. Eng. 2009, 6, 16–24. [Google Scholar] [CrossRef]


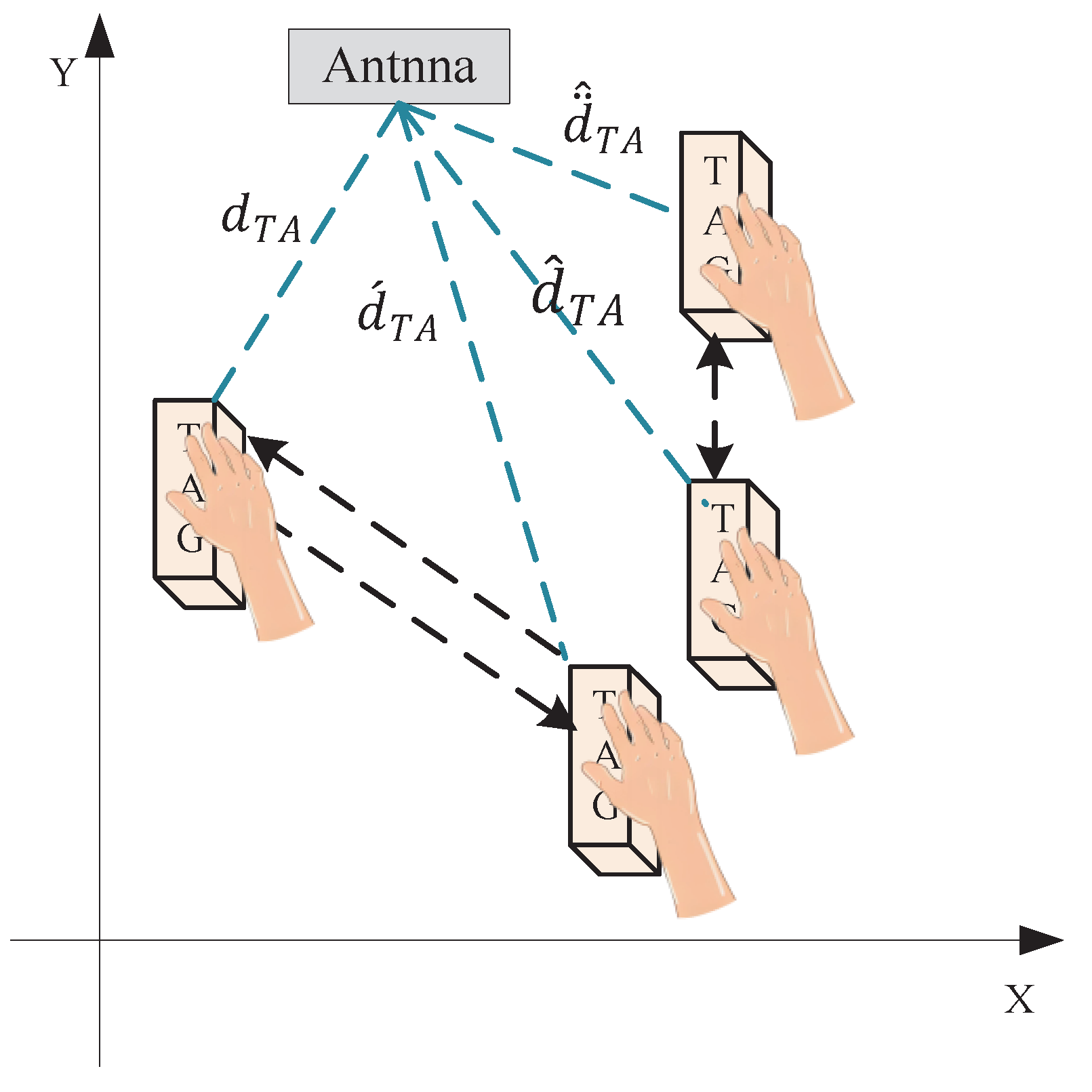
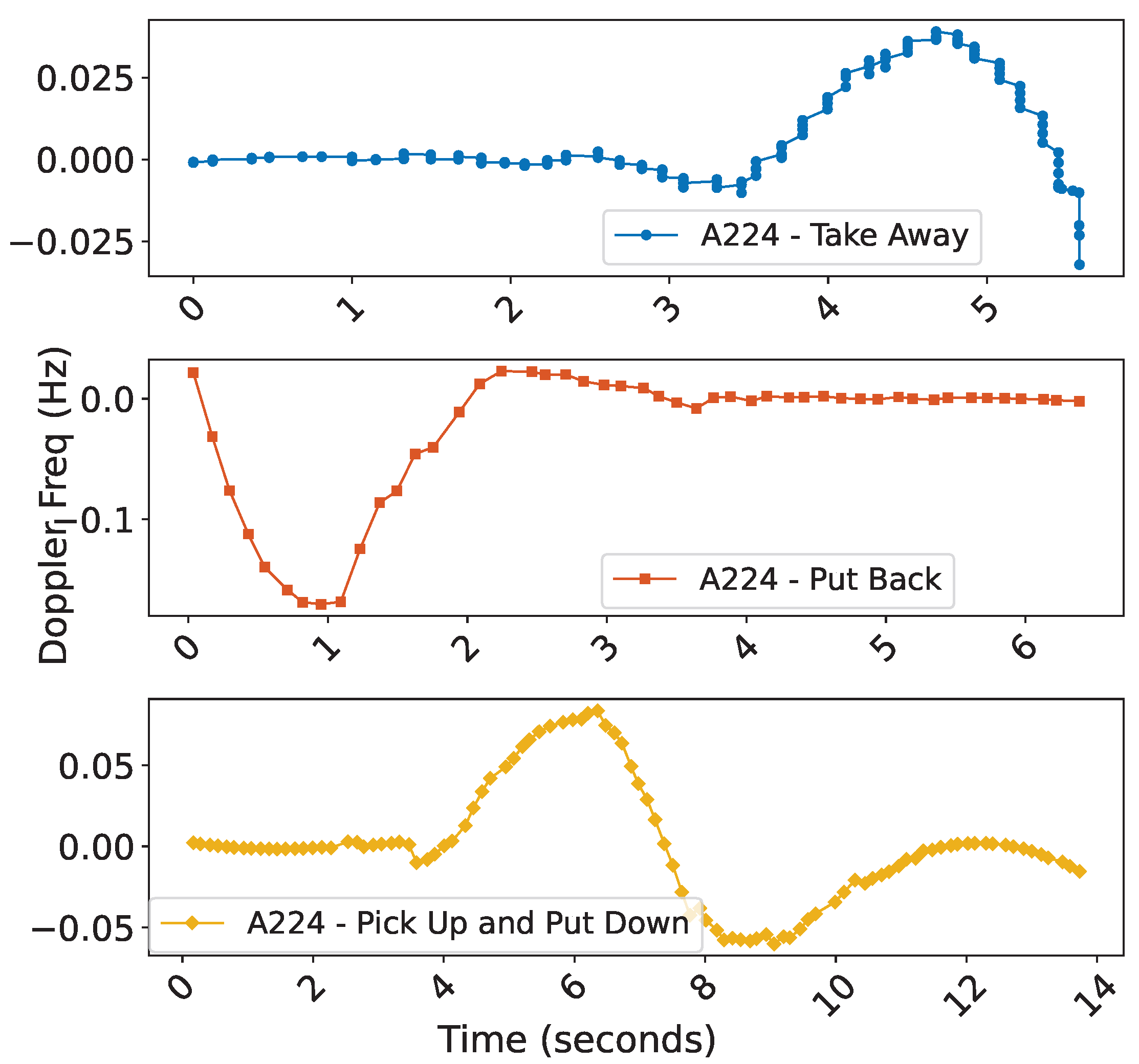
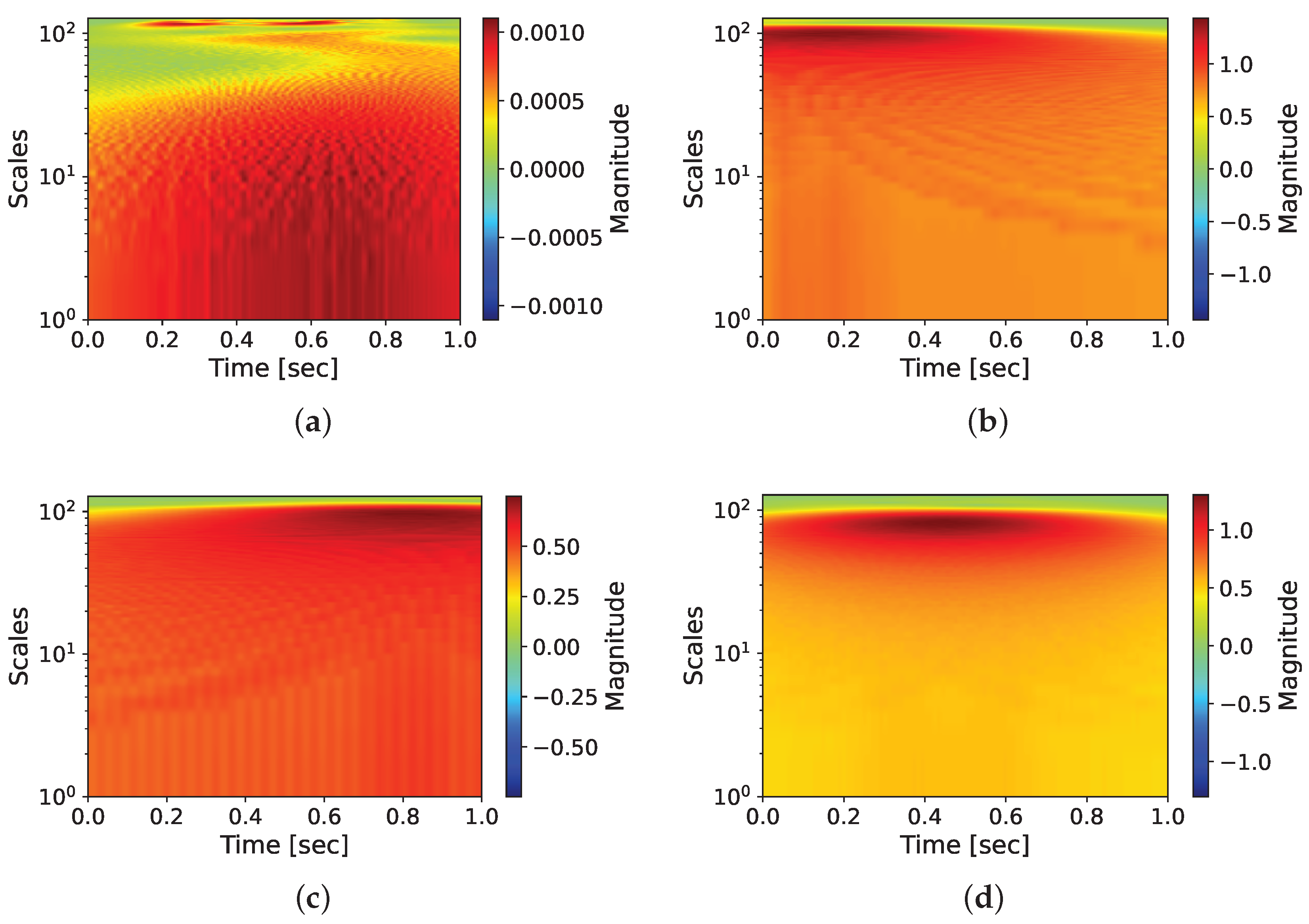
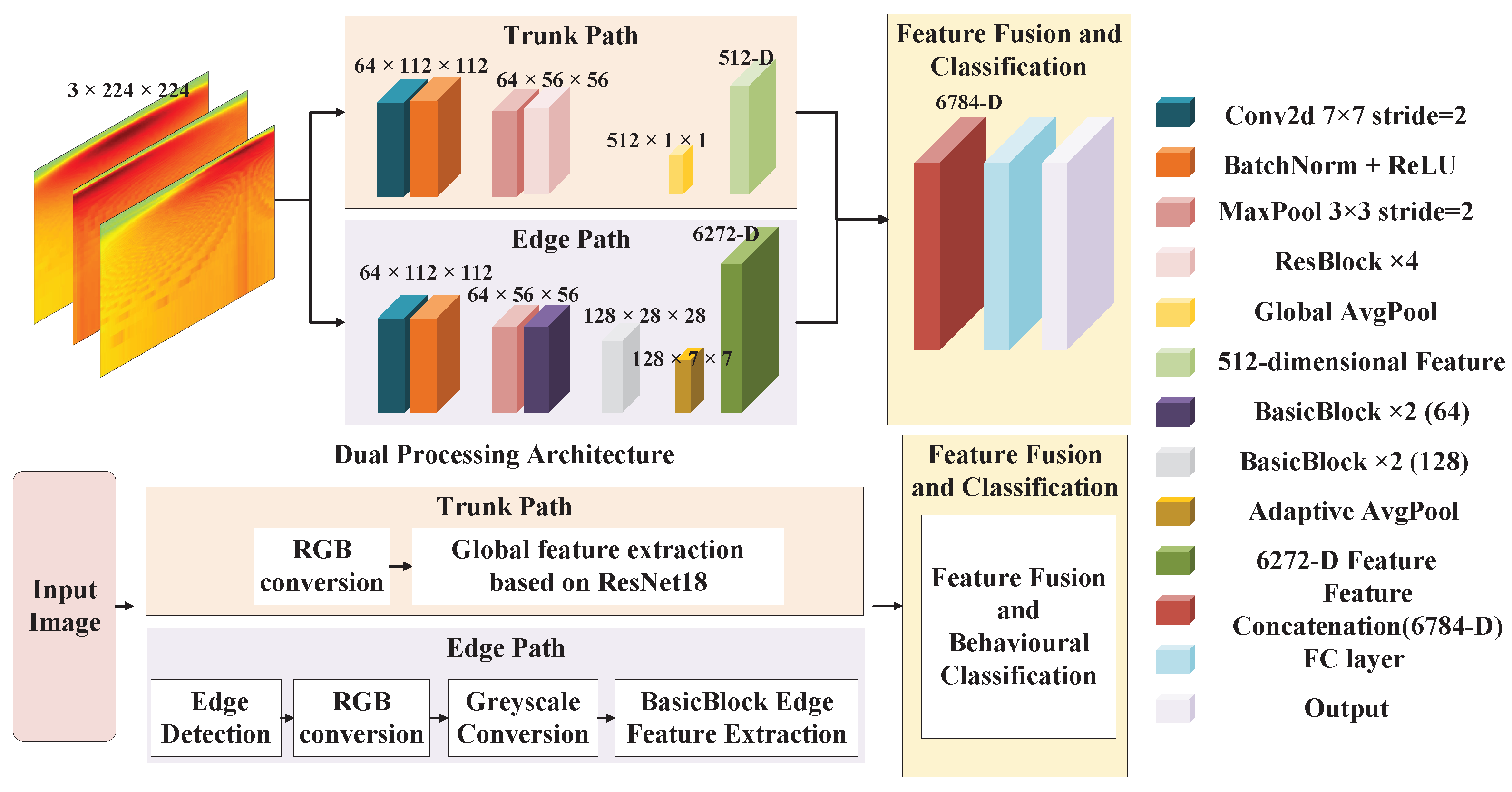
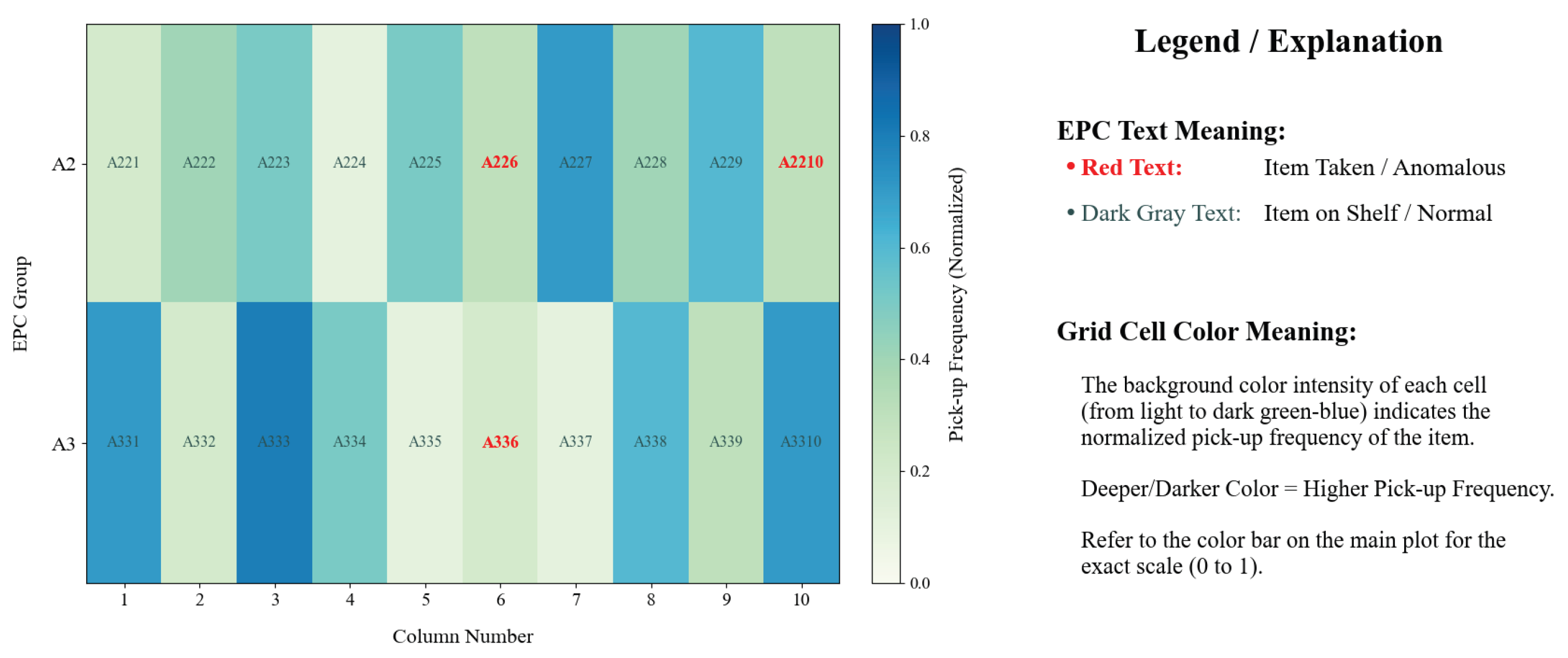
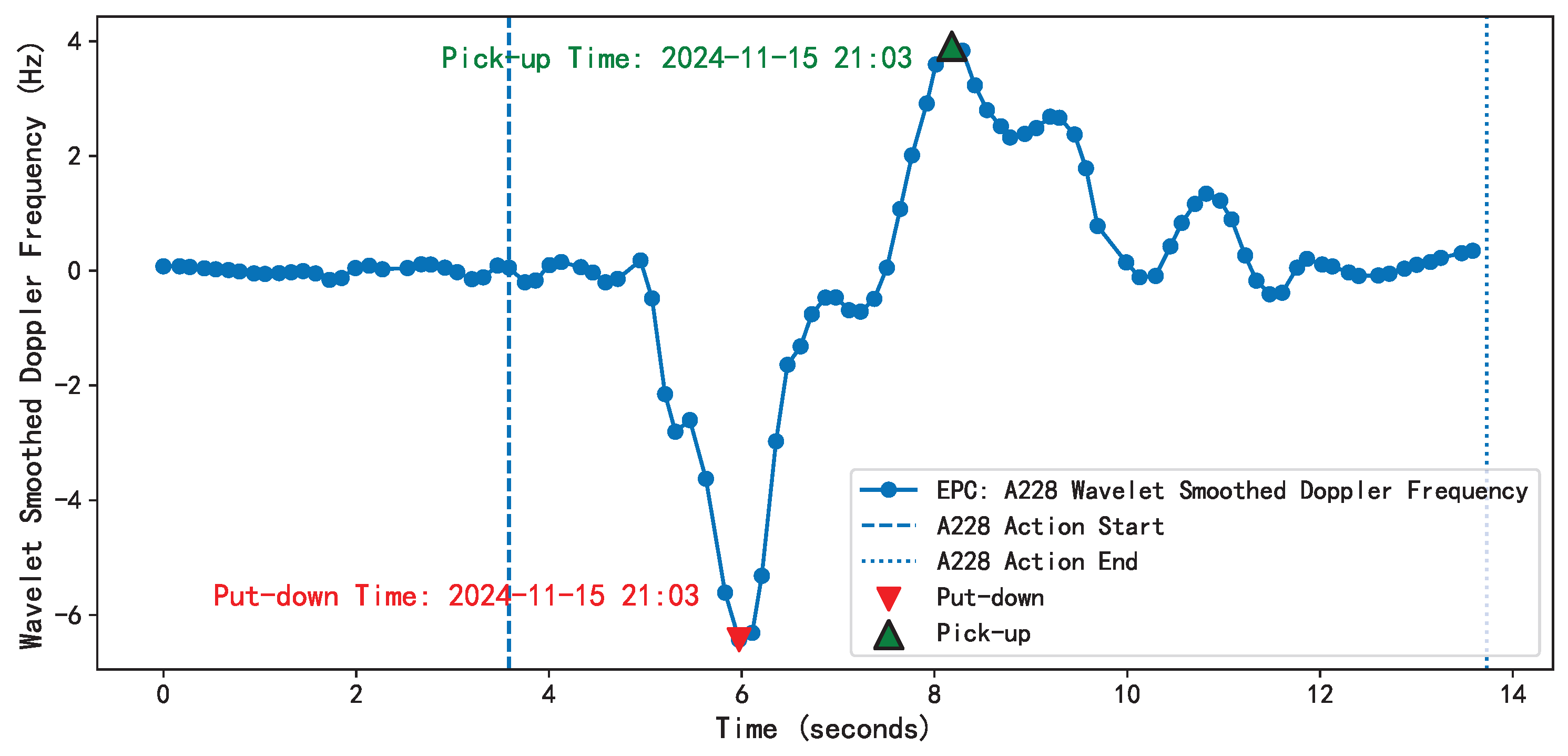

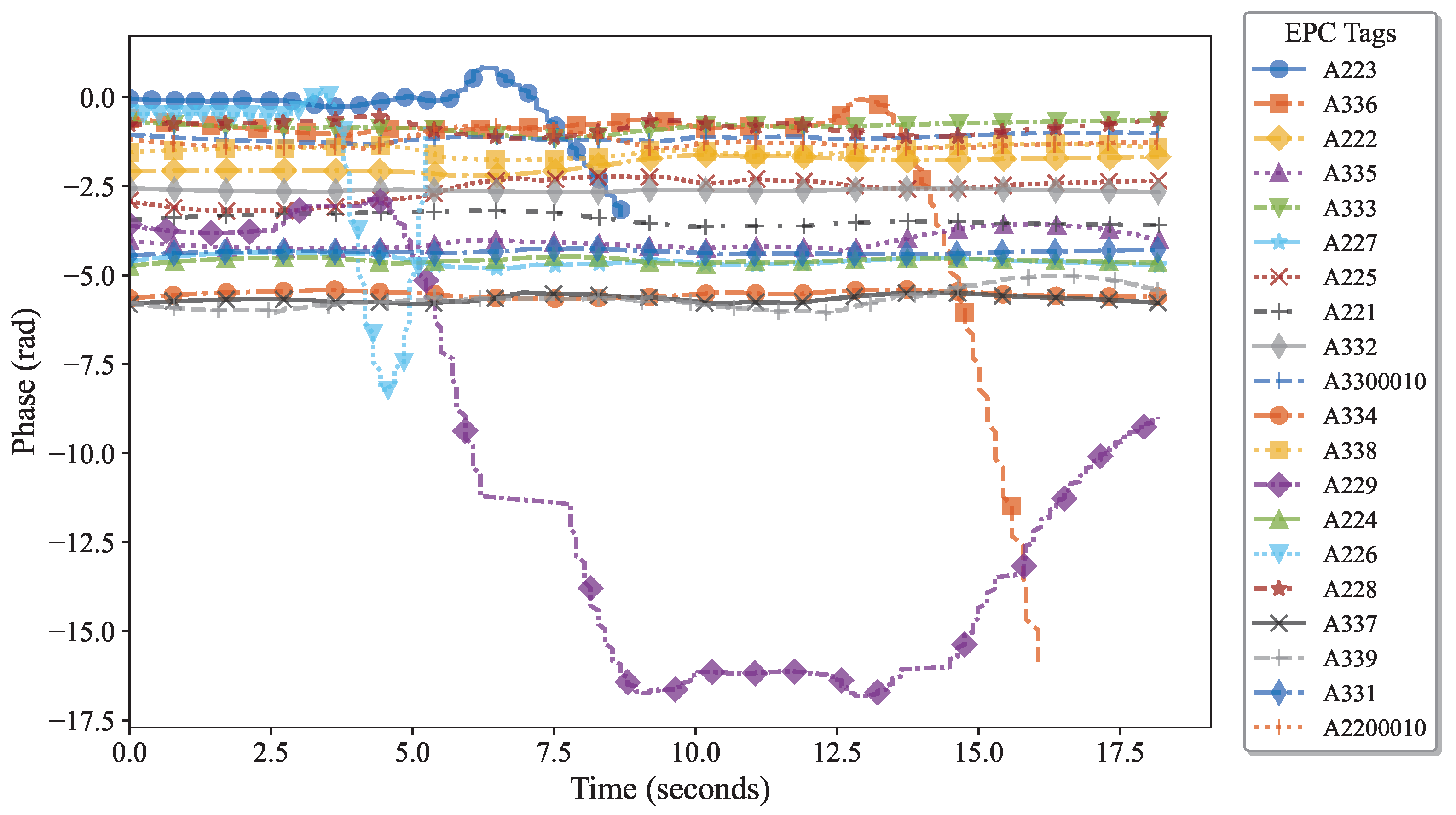
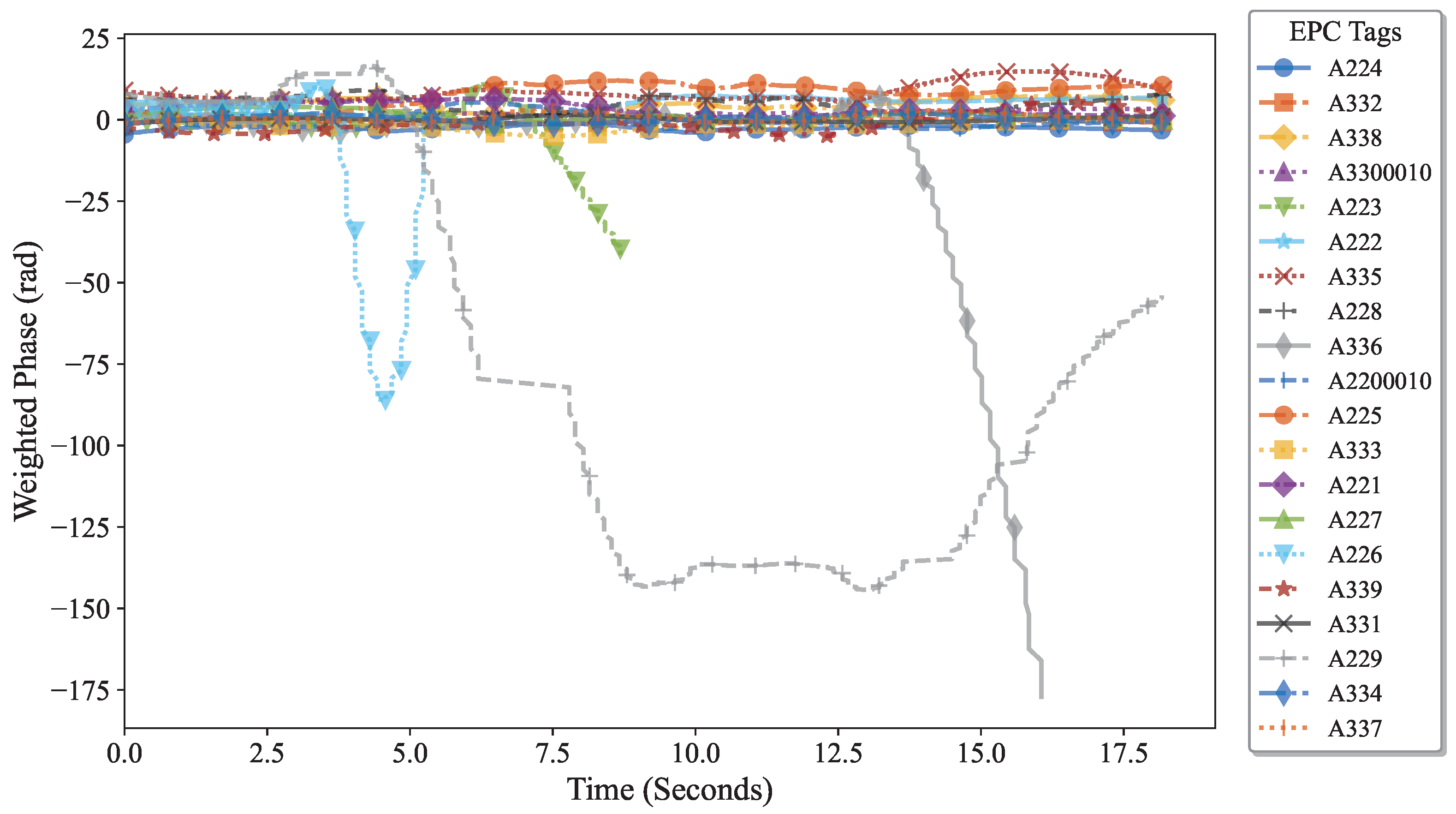

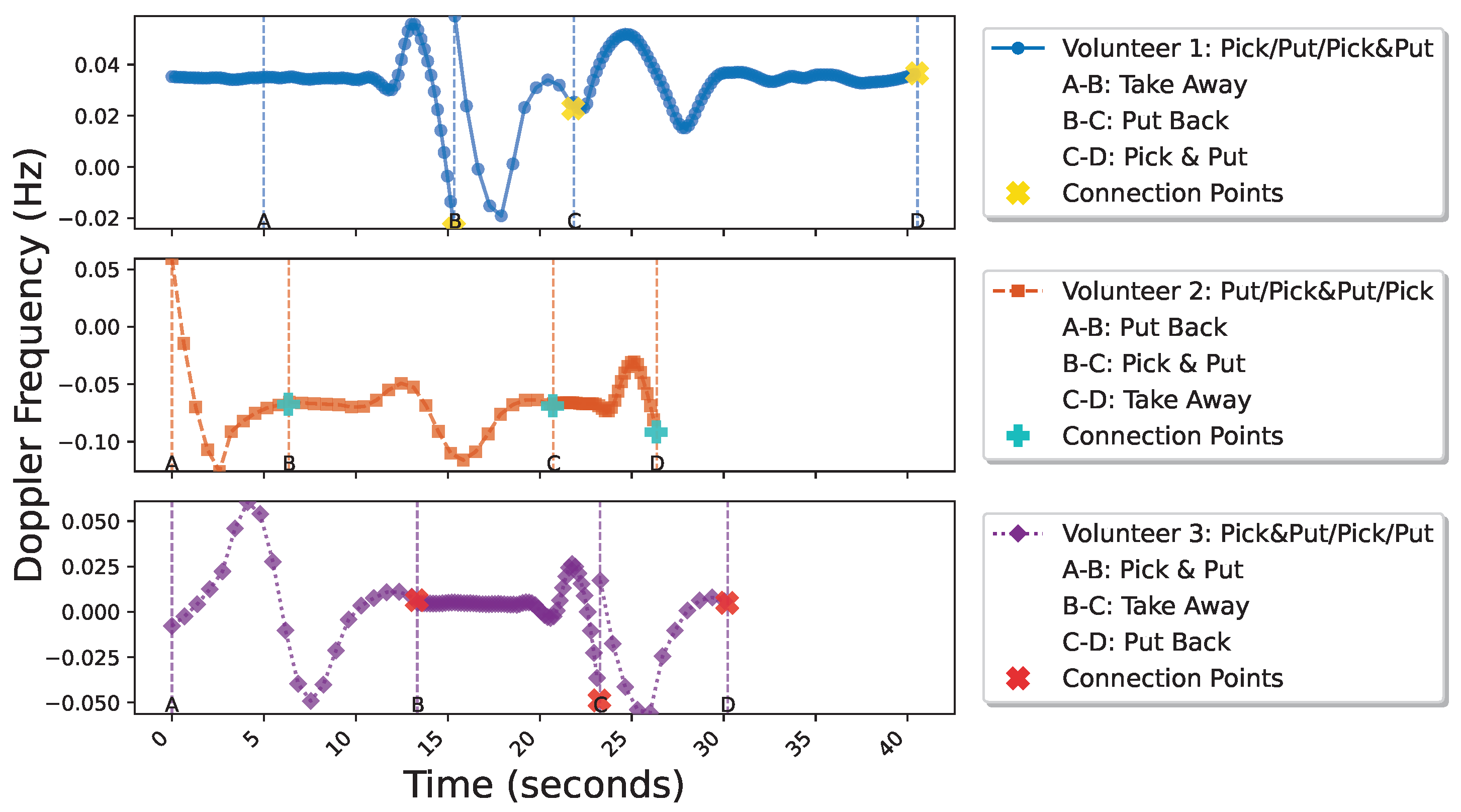


| Split Interval | Behavior |
|---|---|
| A–B | Take away |
| B–C | Put back |
| C–D | Pick up and put down |
| Product | January | February | March | April | May | June |
|---|---|---|---|---|---|---|
| Thermos cup | 480 | 450 | 380 | 250 | 180 | 150 |
| Glass cup | 250 | 260 | 280 | 320 | 380 | 420 |
| Towel | 300 | 310 | 320 | 350 | 380 | 450 |
| Umbrella | 100 | 150 | 350 | 380 | 300 | 250 |
| Flip-flops | 50 | 80 | 150 | 300 | 450 | 550 |
| Cotton slippers | 500 | 400 | 200 | 80 | 30 | 10 |
| Shirt | 350 | 380 | 450 | 520 | 600 | 650 |
| Parameter | Value |
|---|---|
| Reader Type | Impinj Speedway |
| Tag Type | AZ-9662 |
| Tag Size | 70 mm × 17 mm |
| Protocol | ISO-18000-6C [30] |
| Reader Read Power | 26 dBm |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, H.; Liu, X.; Liu, L.; Qin, B.; Pan, R.; Pang, S. UHF RFID Sensing for Dynamic Tag Detection and Behavior Recognition: A Multi-Feature Analysis and Dual-Path Residual Network Approach. Sensors 2025, 25, 5540. https://doi.org/10.3390/s25175540
Wang H, Liu X, Liu L, Qin B, Pan R, Pang S. UHF RFID Sensing for Dynamic Tag Detection and Behavior Recognition: A Multi-Feature Analysis and Dual-Path Residual Network Approach. Sensors. 2025; 25(17):5540. https://doi.org/10.3390/s25175540
Chicago/Turabian StyleWang, Honggang, Xinyi Liu, Lei Liu, Bo Qin, Ruoyu Pan, and Shengli Pang. 2025. "UHF RFID Sensing for Dynamic Tag Detection and Behavior Recognition: A Multi-Feature Analysis and Dual-Path Residual Network Approach" Sensors 25, no. 17: 5540. https://doi.org/10.3390/s25175540
APA StyleWang, H., Liu, X., Liu, L., Qin, B., Pan, R., & Pang, S. (2025). UHF RFID Sensing for Dynamic Tag Detection and Behavior Recognition: A Multi-Feature Analysis and Dual-Path Residual Network Approach. Sensors, 25(17), 5540. https://doi.org/10.3390/s25175540






