1. Introduction
With the wide application of machine learning and network technology, the power system has been rapidly developed, forming the idea of the smart grid consisting of multilayer smart sensors. Smart grids leverage and aggregate information collected by sensors to assist in making power management decisions [
1,
2]. As a new generation of power systems, the smart grid provides users with stable and reliable power services and achieves efficient operation and intelligent management [
3,
4]. However, since electric power information is relevant to user privacy, data communication among various sensors and the power service center leads to significant security concerns [
5].
To achieve efficient communication while guaranteeing data privacy in smart grid systems, existing secure data communication protocols [
6,
7] combine asymmetric and symmetric encryption algorithms. With the high efficiency of symmetric encryption methods [
8,
9], sensitive electric data is masked by a predetermined symmetric secret key, which is only accessed by authorized groups. Due to the security of asymmetric encryption methods [
10], a pair of asymmetric secret keys is utilized to share the symmetric secret key in a smart grid system.
Recently, identity-based encryption is one of the most effective asymmetric encryption methods for authentication among dynamic hierarchical sensor groups [
11]. Specifically, the identity-based encryption method utilizes identity information to guarantee that only authorized users can obtain valuable information from ciphertext. Gupta et al. [
12] propose an efficient identity-based protocol for authentication in transport systems. Zhao et al. [
13] further introduce an identity-based broadcast signcryption scheme in the Internet of Vehicles. Shen et al. [
14] focus on security enhancement and present an identity-based higncryption protocol. Particularly, for hierarchical architecture scenario applications, Pavithran et al. [
15] propose a blockchain-aided protocol to utilize hierarchical identity-based encryption in the Internet of Things systems and Badar et al. [
16] propose an identity-based authentication protocol using the physical unclonable function, particularly for smart grid scenarios.
However, these data encryption methods involve complex computations, such as pairing and modular inversion operations. In practice, smart sensors deployed on the terminal side have limited computing resources, while data communication and collaborative analysis require real-time feedback. To match the requirements of real-time grid data processing, developing a secure data communication protocol with efficiency improvement has become a hot topic.
Additionally, the dynamic sensor group leads to a huge cost for secret group key updates [
17], particularly in smart grid scenarios. On the one hand, the dense update frequency of the sensor group has a significant impact on the performance of the smart grid system. On the other hand, the change of group members causes forward and backward security concerns for the secret group key.
Based on the analysis above, this paper proposes an identity-based efficient secure data communication protocol for hierarchical sensor groups in smart grid systems. The main contributions of this paper can be summarized in three aspects:
We propose a novel secure data communication protocol for sensor groups in the smart grid system, leveraging the symmetric encryption method to transmit obscured data and the identity-based encryption method to share group secret keys. Identities of authorized users are encoded by Bloom filter, and a cloud-aided pre-verification procedure is introduced. Efficient authentication is achieved by searching the pre-calculated authentication array table in the cloud server.
A dynamic update mechanism of the group secret key is designed corresponding with the proposed protocol for lower resource costs in smart grid scenarios. When the sensor group is changed, the proposed mechanism utilizes lightweight operations to implement dynamic updates of the group secret key, which guarantees forward and backward security for the smart grid system.
Theoretical analysis demonstrates that our protocol achieves forward and backward security of a dynamic sensor group and has the capability to resist the replay attack and impersonation attack. Experimental evaluation indicates that our protocol performs better than the state-of-the-art protocols. Specifically, for computation cost, the proposed protocol is 73.94% superior to others on average in the authentication process, 37.77% in the encryption process, and 55.75% in the decryption process. For communication cost, the proposed protocol is 79.98% superior to others on average in the authentication process.
The remainder of this paper is organized as follows: The subsequent section presents current research work relevant to this study.
Section 3 introduces the system model. The definition related to this study is detailed in
Section 4.
Section 5 introduces the specific content of this protocol.
Section 6 is the security analysis of this protocol, and
Section 7 introduces performance analysis. The concluding section encapsulates the research presented in this paper.
2. Related Works
2.1. Broadcast Encryption Algorithm
Broadcast encryption was first proposed in 1993 [
18]. Recently, Boneh et al. [
19] proposed a broadcast encryption scheme using bilinear mapping. The private key and ciphertext of the scheme reached the constant level, which supports the anti-collusion attack and proves that the broadcaster could no longer be a trusted authority but any legitimate user. However, the number of users for this solution has been set at the beginning of the solution, and subsequent users cannot be added. Lewko et al. [
20] proposed a broadcast encryption scheme that supports the user’s cancellation and non-monotonic mechanism, making the application of broadcast encryption more flexible. However, although the above scheme and subsequent schemes [
21,
22] realize the advantages of multiple users sharing the same message, they cannot achieve good access control. Kumar [
23] et al. proposed a broadcast encryption technology based on threshold and wildcard. This technique uses hidden access policies to provide security for sensitive data broadcast over insecure channels. In addition, for any number of attributes, the technology realizes the fixed-length ciphertext, which greatly reduces the communication overhead and computational complexity. However, the proposed scheme does not consider the direct withdrawal of users and the dynamic addition of users in the system.
2.2. Authentication Protocol
Wazid et al. [
24] proposed a three-factor authentication protocol for remote users in a smart grid environment based on renewable energy. The protocol uses one-way hash functions, bitwise OR operations, and ECC operations to achieve lightweight encryption. The protocol supports the dynamic addition of smart sensors, flexibility of password and biometric updates, user anonymity, and non-traceability. Mahmood et al. [
25] proposed a lightweight authentication protocol based on ECC, which used ProVerif, an automatic verification tool, to analyze its own security, and adopted Burrows–Abadi–Needham (BAN) logic to prove the completeness and completeness of the protocol. The downside is that the protocol does not support the anonymity of smart sensors. Kumar et al. [
26] proposed a lightweight authentication and key agreement protocol that achieves anonymity, integrity, and security based on ECC, symmetric encryption, hash functions, and message authentication codes. Wang et al. [
27] proposed a mutual authentication protocol based on edge computing in a smart grid system, which supports efficient conditional anonymity and key management based on blockchain technology. The proposed protocol ensures mutual authentication and anti-replay attacks and supports efficient key renewal and revocation to achieve conditional anonymity with lower computing and communication costs.
2.3. Key Updating Protocol
Group multicast effectively improves the efficiency of group communication. How to generate and update multicast keys efficiently has important practicality and wide application prospects in the smart grid. At present, a large number of group key generation and updating protocols have been proposed, which can be divided into three categories: key updating protocol based on binary key tree, key updating protocol based on multi-fork key tree, and key updating protocol based on polynomial. Lin et al. [
28] proposed an M-fork tree key management and digital signature protocol based on elliptic curves. At the time of transmission, the protocol provides several flexible and scalable schemes to manage security issues that dynamically adapt the framework to the rapidly changing IoV topology, speeding up the time to synchronize system key reconstruction and reducing the number of stages to resynchronize system keys. Tan et al. [
29] proposed a dynamic key management scheme based on attribute-based encryption. In the vehicular ad hoc network, identity authentication plays an important role in privacy protection. This protocol guarantees non-repudiation and authenticity properties while achieving efficient vehicular communications.
3. System Model
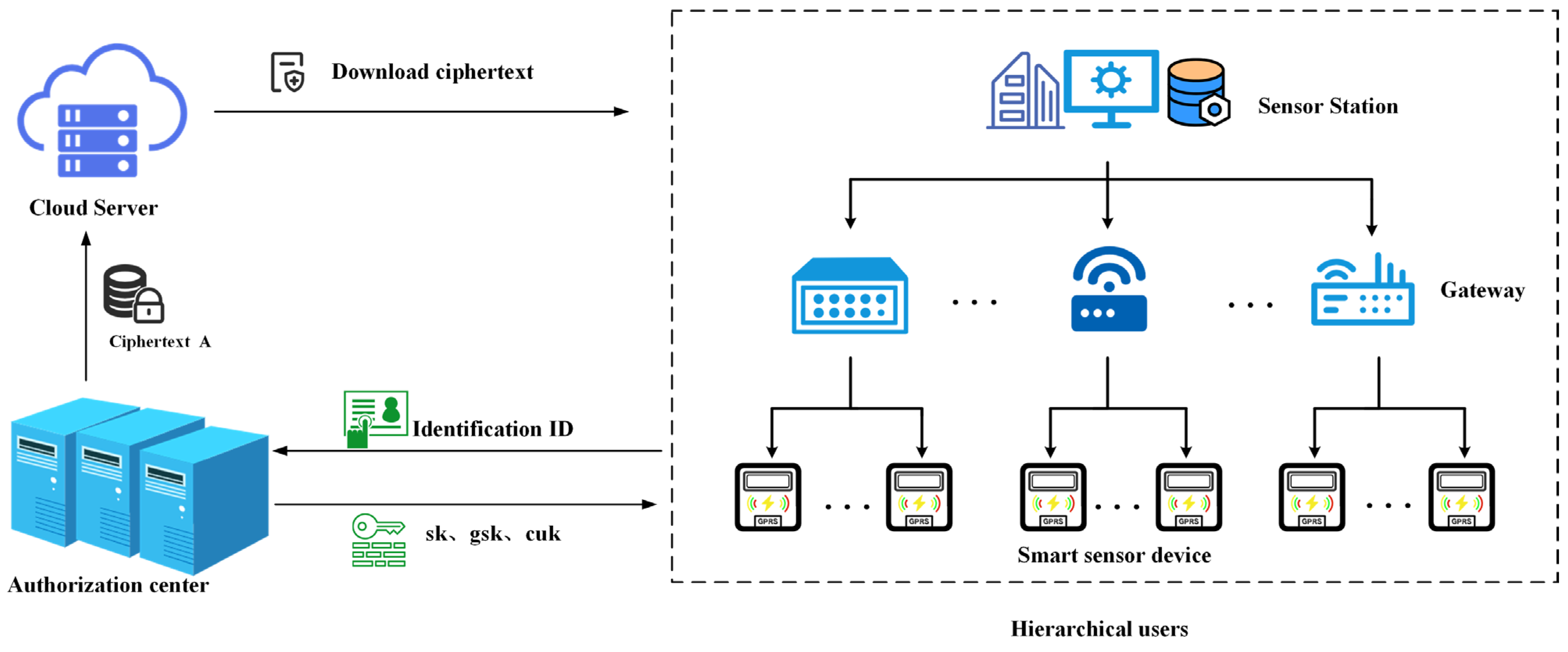
As shown in
Figure 1, the system model consists of three entities: cloud server, authorization center, and smart sensor devices.
Cloud server: As one of the components of the power service center, the cloud server has sufficient computing resources and storage capacity. It is responsible for storing ciphertext and performing pre-authentication operations for device access requests. Additionally, the cloud server takes responsibility for removing inactive devices that have not established a connection beyond a predefined threshold, thereby effectively eliminating broken-down devices.
Authorization center: The authorization center is a trusted entity that is responsible for generating system parameters, public and private key pairs, user keys, and session keys based on the identity of the smart device. The authorization center sends them to the smart device. In addition, the authorization center is responsible for the plaintext encryption to generate the ciphertext and send it to the cloud server. Additionally, the authorization center conducts regular checks for the cloud server, implementing maintenance procedures or server replacement when an abnormal status is detected.
Smart sensor device: The smart sensor devices consist of a master station system, gateway devices, and smart sensors. The smart sensor device has limited computing power and storage capabilities, and every device has a public–private key pair, a user key, and a session key. The smart sensor devices use the session key to communicate with the power service center and decrypt the ciphertext using their private keys.
4. Definition
4.1. Bloom Filter
A Bloom filter is a random data structure with high special efficiency. The set
is encoded in an array of
bits and the Bloom filter determines whether an element x belongs to the set S. The steps to build the (w, m, k, H) Bloom filter BFS for set S are as follows. First, the set of hash functions
is selected, where the hash functions
are independent of each other and have the range
. All bits of BFS are then set to 0 initially. Finally, for all
and
, let
. However, the Bloom filter may misjudge when determining whether the element belongs to the set S by mistaking
for
. When it is necessary to determine whether the element
belongs to the set
, simply compute
and check
whether all values are 1. If the result is not all 1,
, otherwise
. The maximum error rate is
where
and
is a negligible function of
.
4.2. Identity-Based Public Key Encryption Algorithm
The identity-based cryptosystem makes use of the bilinear property of elliptic curves, and bilinear pairing is established by the relation between cyclic subgroups of elliptic curves and multiplicative cyclic subgroups of extended domains. When the difficulty of the extended domain discrete logarithm problem is similar to that of the elliptic curve discrete logarithm problem, an efficient and secure identity-based cryptosystem can be constructed. The identity-based data encryption algorithm is defined as follows:
P1 is set as the generator of the elliptic curve addition cyclic group G1, and P2 is the generator of the elliptic curve addition cyclic group G2. H (·) stands for hash function; Enc (·) and Dec (·), respectively, correspond to the operation modes of encryption and decryption. KDF (·) is a function involved in the key derivation process; MAC (·) is the authentication message code that carries the key in the authentication process; e (·) is a bilinear pair.
The cryptographic function takes the bit string and an integer and outputs an integer . The cryptographic function takes the bit string and an integer and outputs an integer . The key generation center randomly selects as mater secret key, and computes in as mater public key. The encryption master key pair is . The key generation center is kept secret at ke and publicly available at Ppub. The key generation center chooses and exposes the one-byte private key to generate the function identifier . The identity of the user A is , and generates A’s private key . The key generation center first computes in the bounded domain . If , the system needs to re-generate the master private key, compute and expose the master public key, and update the existing user’s private key; otherwise, calculate , then calculate .
Assume that user A encrypts plaintext and sends it to user B, A computes element of the group , and then randomly selects , and computes . A calculates . According to the classification of encryption, there are two ways to encrypt plaintext to generate : stream cipher and block cipher . A computes , and finally obtains the ciphertext
After receiving the ciphertext, user B calculates , . According to the classification of encryption, there are two ways to decrypt ciphertext to generate : stream cipher and block cipher ). Finally, B computes . If , output , otherwise an error is reported.
5. Protocol
This protocol mainly includes six steps, which are system initialization, key generation, data encryption, user authentication, data decryption, and dynamic updating of terminal devices. The following is the specific interaction process.
5.1. System Initialization
Given security parameter , the authorization center (CA) selects a particular elliptic curve and a point of large prime order on an elliptic curve on a finite field, selects as addition cyclic groups of prime , and selects a multiplicative cyclic group of primes . Select Bloom filter’s bit array size and k hash functions which map every identity in the user’s set to . Generally, hash functions are used to calculate the elements in the authorized user set, and the obtained results are modulo m, and the Bloom filter’s pre-authentication array table A is obtained and stored in the server.
5.2. Key Generation
CA selects a number at random as system master key , and the corresponding system master public key is disclosed. CA selects and exposes the private key generating function identifier hid, which is represented by a single byte. AC computes over a finite field. If , calculate the user’s private key , and the corresponding user’s public key is . If , the system master key and public key need to be recalculated. CA randomly selects , timestamp , the system master public key , the system private key , and user identification to generate the user key . In addition, generates a random number for every smart sensor device to generate session key .
Broadcast key generation: For every smart sensor or gateway device, CA generates the broadcast key through the master public key , the master private key and of all devices, where n represents the last layer, and m represents the last smart sensor device at the last layer. CA selects at random to generate the broadcast session key .
Multicast key generation: When the power service center wants to multicast with the subset of users, the user key and the hash value of user identities are calculated as the multicast key:
where
is the current timestamp,
and
indicate the user key and identity of the user set, respectively. CA randomly selects grand to generate the multicast session key
.
5.3. Data Encryption
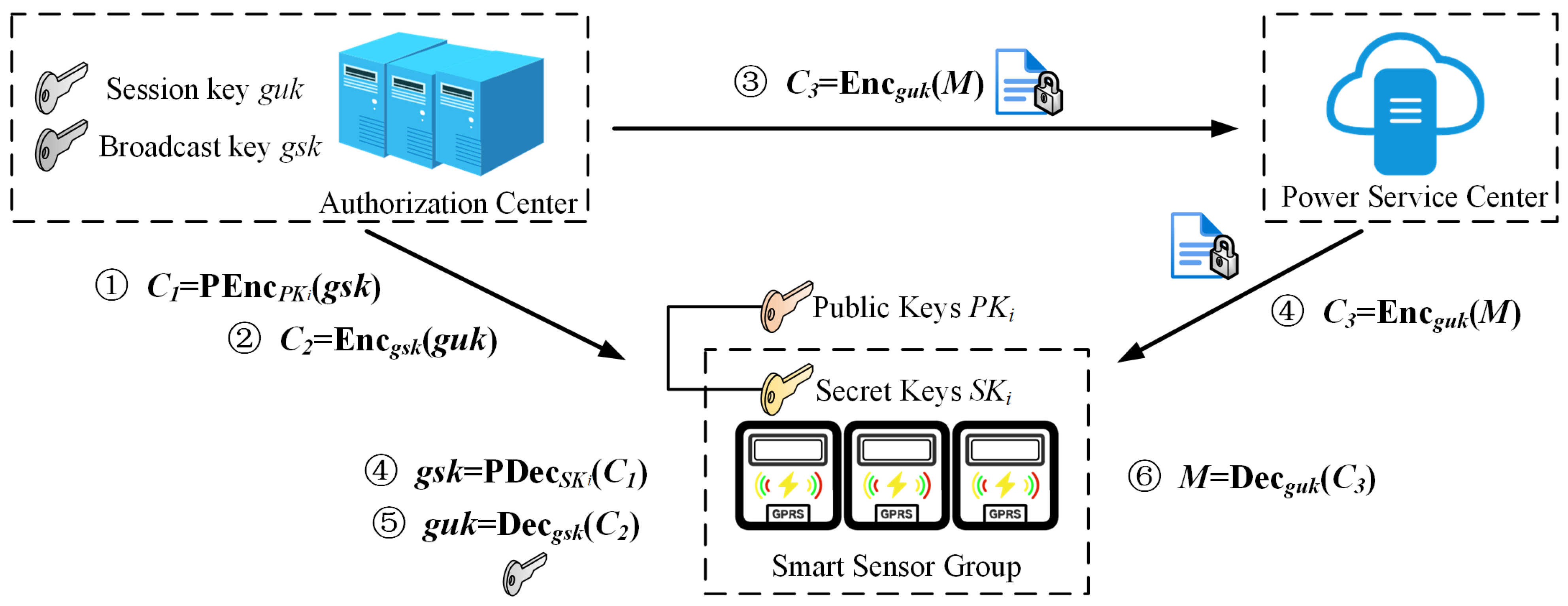
(a) Unicast encryption: As shown in
Figure 2, CA uses the user’s public key
to encrypt the user key to obtain
, and then uses the unicast key to encrypt the session key to obtain
, and finally uses the session key to encrypt the plaintext
to obtain
, where
represents identity based public key encryption algorithm, and
represents any symmetric encryption algorithm.
(b) Broadcast encryption: As shown in
Figure 3, CA uses the user’s public key
to encrypt the broadcast key to obtain
, and then uses the broadcast key to encrypt the broadcast session key to obtain
, and finally uses the broadcast session key to encrypt the plaintext
to obtain
.
(c) Multicast encryption: As shown in
Figure 4, CA uses the user’s public key
to encrypt the multicast key to obtain
, and then uses the multicast key to encrypt the multicast session key to obtain
, and finally uses the multicast session key to encrypt the plaintext
to obtain
.
5.4. User Authentications
If the user wants to make a data access request to the power service center, it first verifies the legitimacy of the identity. As shown in
Figure 5, user authentications include pre-authentication and main authentication. The specific process is as follows.
Pre-authentication: The power service center uses the hash function disclosed by CA in the initialization stage to hash the user identity and obtain the pre-authentication array generated by the Bloom filter. The power service center pre-verifies the user identity: If , the user passes the authentication and obtains the pre-authentication certification. The power service center calculates .
Main authentication: After passing the pre-authentication, the user uses his private key and the system master public key to calculate the shared key
, and calculates
Then, the user sends to the power service center. The power service center receives at moment and firstly checks whether the time interval between and meets , where represents the transmission delay. If the timestamp falls within the accepted time window, the power service center calculates , if , then it proves that the user has the correct certification and public and private key pair, and the user successfully passes the authentication.
5.5. Data Decryption
(a) Unicast decryption: As shown in
Figure 2, the smart sensor device uses its private key
to calculate
, decrypts the unicast key, then the session key
by using the user key, and finally decrypts the plaintext
by using the session key.
(b) Broadcast decryption: As shown in
Figure 3, the smart sensor device uses its own private key
to calculate
to obtain the user’s broadcast key, and then the broadcast session key is obtained by using the broadcast key. Finally, the plaintext
is decrypted by using the broadcast session key.
(c) Multicast decryption: As shown in
Figure 4, the smart sensor device uses its own private key
to calculate
to obtain the user’s multicast key, and then multicast session key
is obtained by using the multicast key. Finally, the plaintext
is decrypted by using the multicast session key.
5.6. Dynamic Updating of Terminal Devices
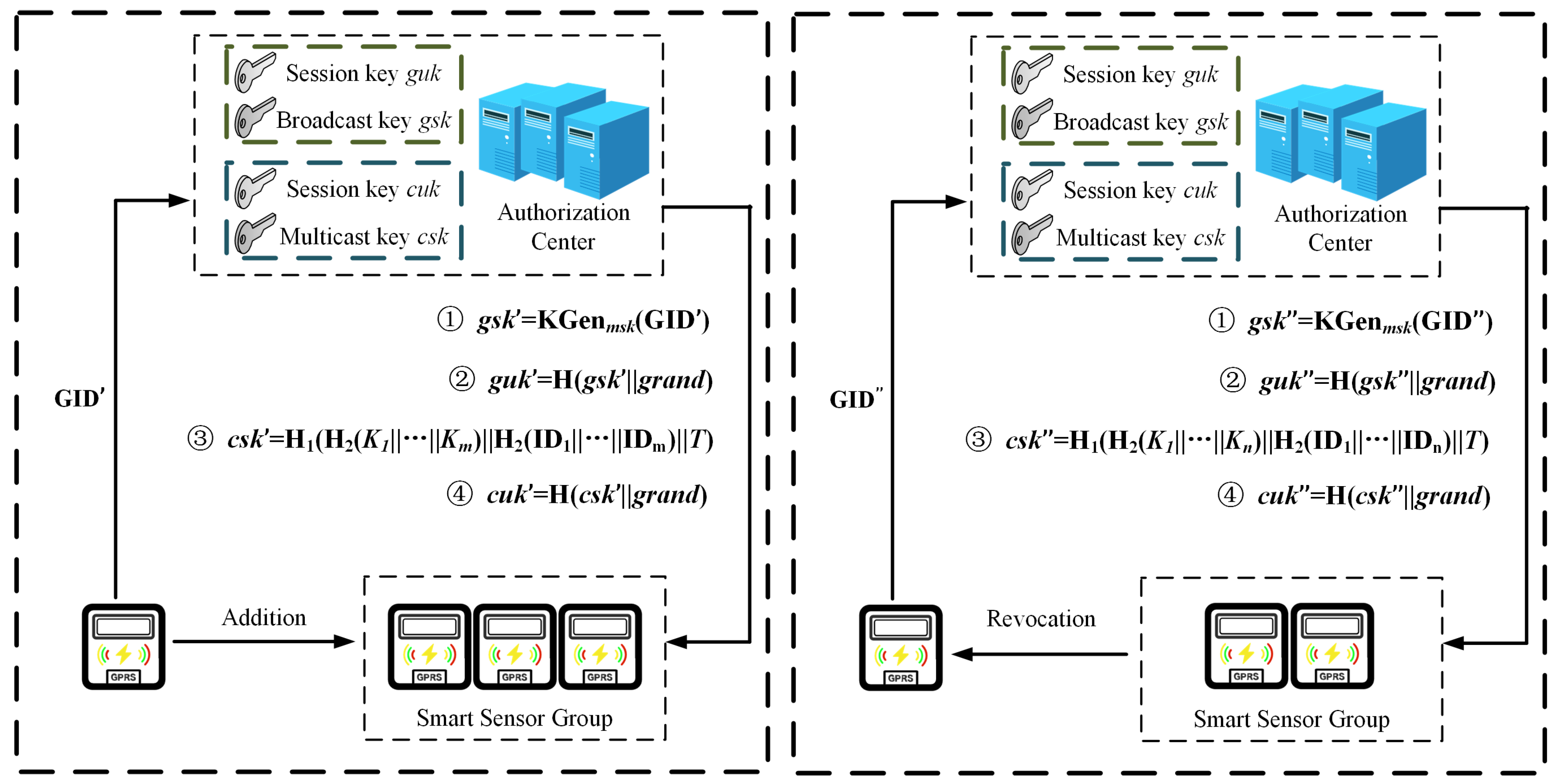
5.6.1. Smart Sensor Device Addition
As shown in
Figure 6, when a new user is added to the system, the system generates the public and private keys pair and user key and updates the broadcast key, broadcast session key, multicast key, and multicast session key. The public key, private key, and user key follow the steps for key generation.
(a) Updating the broadcast key and broadcast session key: CA generates the broadcast key using the master public key , master private key , and identity of the existing device . AC selects at random to generate the broadcast session key .
(b) Updating the multicast key and multicast session key: When the power service center wants to multicast with a subset of users containing new users, it firstly recalculates the hash value of the user keys and identities for users: , where indicates the current timestamp, and indicates the user keys and identities of users, respectively. CA randomly selects to generate the multicast session key .
5.6.2. Smart Sensor Device Revocation
As shown in
Figure 6, when a smart sensor device is revoked, its public key, private key, and authentication certification will expire, and it can no longer be used for data access.
(a) Updating the broadcast key and broadcast session key: When a smart device is removed, the broadcast key needs to be recalculated. According to the key generation algorithm, the broadcast key is recalculated, and then the broadcast session key is generated.
(b) Updating the multicast key and multicast session key: When a smart device is removed, the multicast key needs to be recalculated. According to the key generation algorithm, the multicast key is recalculated, and then the multicast session key is generated.
(c) Smart sensor device migration: When a subset of user devices is migrated from one gateway to another gateway device, CA needs to recalculate the hash values of the user keys and identities for all nodes on the path from this subset of users to the root node, and then obtain a new multicast key , which is based on the current new timestamp . is broadcast to users in this subset with the previous multicast session key, and upon receiving the message, users decrypt and update the multicast session key .
5.7. Fault Recovery
The cloud server maintains an active device list and monitors connection intervals for all client devices. For any device with > , where denotes the maximum allowable inactive duration, the cloud server automatically revokes its authentication credentials and removes from .
Similarly, the CA implements regular check with period . At each interval, CA sends status requests to cloud server, analyzes status feedback, and repairs or replaces broken-down cloud devices. A failure log matrix is held by CA for post-incident analysis.
6. Security Analysis
This section formally analyzes the security properties of the proposed protocol. The security relies on the hardness of the elliptic curve discrete logarithm problem (ECDLP), the computational Diffie–Hellman (CDH) problem on elliptic curves, and the security of the underlying identity-based encryption (IBE) scheme () and symmetric encryption scheme (). The hash functions are assumed to be cryptographically secure (e.g., behaving as random oracles).
6.1. Forward Security
Theorem 1. Forward security ensures that a smart sensor device (with identity ), once revoked from a group at time , cannot decrypt messages intended for the group after . This means cannot obtain any newly generated group keys (e.g., , ) or session keys (e.g., , ).
Proof. Consider the broadcast key . When is revoked, a new broadcast key is generated by CA using where represents the identities of the remaining authorized devices. This is then used to derive a new broadcast session key The plaintext is encrypted as The key is distributed to authorized users by encrypting it with their respective public keys (derived from ) using the IBE scheme: .
Since is revoked, its identity is not part of , and CA will not provide with Even if possesses its old private key it cannot decrypt for any (assuming ) to obtain , due to the security of the IBE scheme. Without , cannot compute via (as is fresh and is one-way). Therefore, cannot decrypt .
The argument for the multicast key is similar. When is revoked from a multicast group, a new is computed based on the remaining members’ keys and identities, and a new timestamp. This is distributed encrypted with the previous multicast session key Since is no longer part of the group, it will not receive this update, or if it does, the subsequent session key will be derived from which it cannot obtain if is re-encrypted using IBE for the new group. If is broadcast using the old , then the subsequent derived from and a new will be unknown to . The core idea is that new keys are generated that does not have the components to derive or decrypt.
Thus, the protocol ensures forward security provided the IBE scheme is secure and hash functions are one-way. An adversary controlling cannot gain access to future group communications. □
6.2. Backward Security
Theorem 2. Backward security ensures that a newly added smart sensor device (with identity ) at time cannot decrypt messages encrypted for the group before its addition.
Proof. Before joins, group communications use keys like (and ) or (and ). These keys were generated based on the identities and keys of members existing before . For instance, , where .
When joins, it receives its own private key , user key , and session key . However, does not receive past group keys like or . The IBE-encrypted was distributed only to members of . Since was not in , cannot be used to decrypt ciphertexts containing .
The user keys are unique to each user and timestamp. A new user cannot derive past user keys of other members due to the one-way nature of and the secrecy of and other users’. Similarly, past multicast keys depend on keys and identities of the old group and an old timestamp, which cannot reconstruct.
Therefore, cannot access messages encrypted prior to it joining the group, ensuring backward security. This relies on the IBE security and the one-way property of hash functions. □
6.3. Replay Attack Resistance
Theorem 3. The protocol resists replay attacks during user authentication. The user sends and to the power service center. .
Proof. The power service center (server) receives at its current time It first verifies the freshness of the by checking if , where is a predefined small interval for network delay.
If an adversary intercepts a valid and replays it at a significantly later time , then The server will detect this stale timestamp and reject the message.
If the adversary attempts to use a fresh with the old , the server will compute (where ). Since and is collision-resistant, will not be equal to (except with negligible probability). Thus, the authentication will fail.
To successfully replay with a fresh timestamp , the adversary would need to compute a new . This requires knowledge of . Since the user’s private key is secret, and computing without is hard (related to the CDH problem, given and ), the adversary cannot forge a valid .
The inclusion of a fresh timestamp in the hash computation for and the server’s freshness check effectively prevent replay attacks. □
6.4. Impersonation Attack Resistance
Theorem 4. An adversary attempts to impersonate a legitimate smart sensor device (with identity and private key ) to the power service center.
Proof. To impersonate , the adversary must successfully complete the authentication process. This involves computing , where . The adversary knows , , and . The system master key and user private key are secret.
The private key is computed as , where . Thus, .
An adversary faces the following difficulties:
Deriving from : This is the ECDLP, which is assumed to be hard.
Deriving from : This is also the ECDLP.
Computing directly from and without knowing or : This is computationally equivalent to solving the CDH problem (given , compute ). While is not exactly , computing without is infeasible.
The pre-authentication step using the Bloom filter adds another layer. If the adversary’s chosen (or forged) identity is not in the authorized set encoded in the Bloom filter on the server, , and pre-authentication fails. Even if a Bloom filter collision occurs for a random (with small probability ), the subsequent main authentication requiring will fail.
Since the adversary cannot compute or without breaking underlying hard problems (ECDLP or CDH), it cannot generate a valid message. Therefore, the protocol is resistant to impersonation attacks. □
7. Performance Analysis
7.1. Theoretical Analysis
This section will be analyzed in terms of computational cost and communication cost. In computational cost analysis, we focus only on the bilinear pairing, multiplication, hashing, and modular inverse algorithms performed by every device, and ignore other lightweight operations. We represent as a bilinear pairing operation, as a multiplication operation, as a hash operation, and as a modular power operation. In the registration phase, the power service center generates the unicast key for every smart grid device, which requires three multiplications, three hashes, and one modular power, namely . The power service center needs operations to generate the broadcast key, and operations to generate the multicast key. In the encryption phase, unicast encryption, broadcast encryption, and multicast encryption all require one asymmetric encryption operation and two symmetric encryption operations. In the authentication phase, CA authenticates user identity by one multiplication and one hash. In communication cost analysis, CA generates the private key, session key, broadcast key, broadcast session key, multicast key, and multicast session key for the user. Their key’s bit length is . During data access, the user downloads the ciphertext from the power service center. We will ignore other transmitted data.
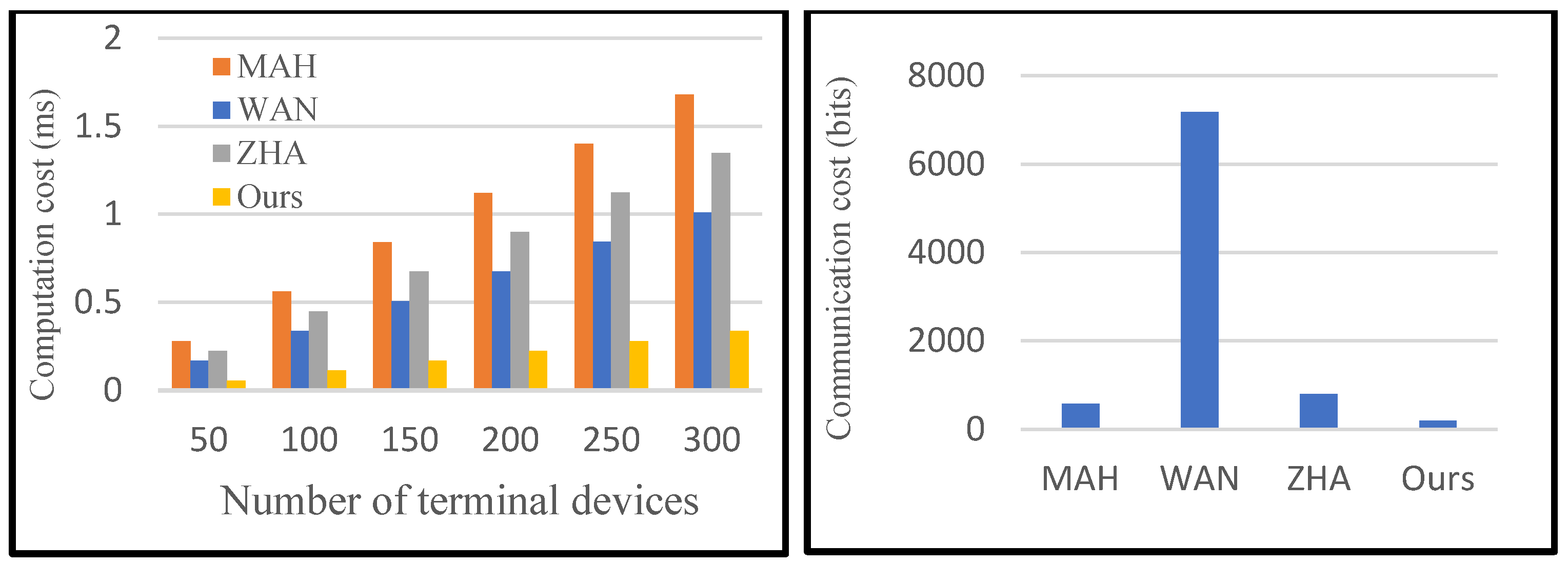
Table 1 shows the cost comparison of the certification process between the proposed protocol and the protocols of MAH [
26], WAN [
28], and ZHA [
14]. In our protocol, CA requires one multiplication and one hash operation to verify the validity of the terminal device. Therefore, the time consumed by CA authentication increases linearly with the increasing number of terminal devices. As shown in
Table 2, the cost of the proposed protocol is lower than other protocols, both in terms of computation cost and communication cost. MAH protocol has the highest computational cost, and WAN protocol has the highest communication cost.
Table 2 shows the cost comparison of encryption and decryption between the proposed protocol and the protocols of CHE [
22], ACH [
23], and KUM [
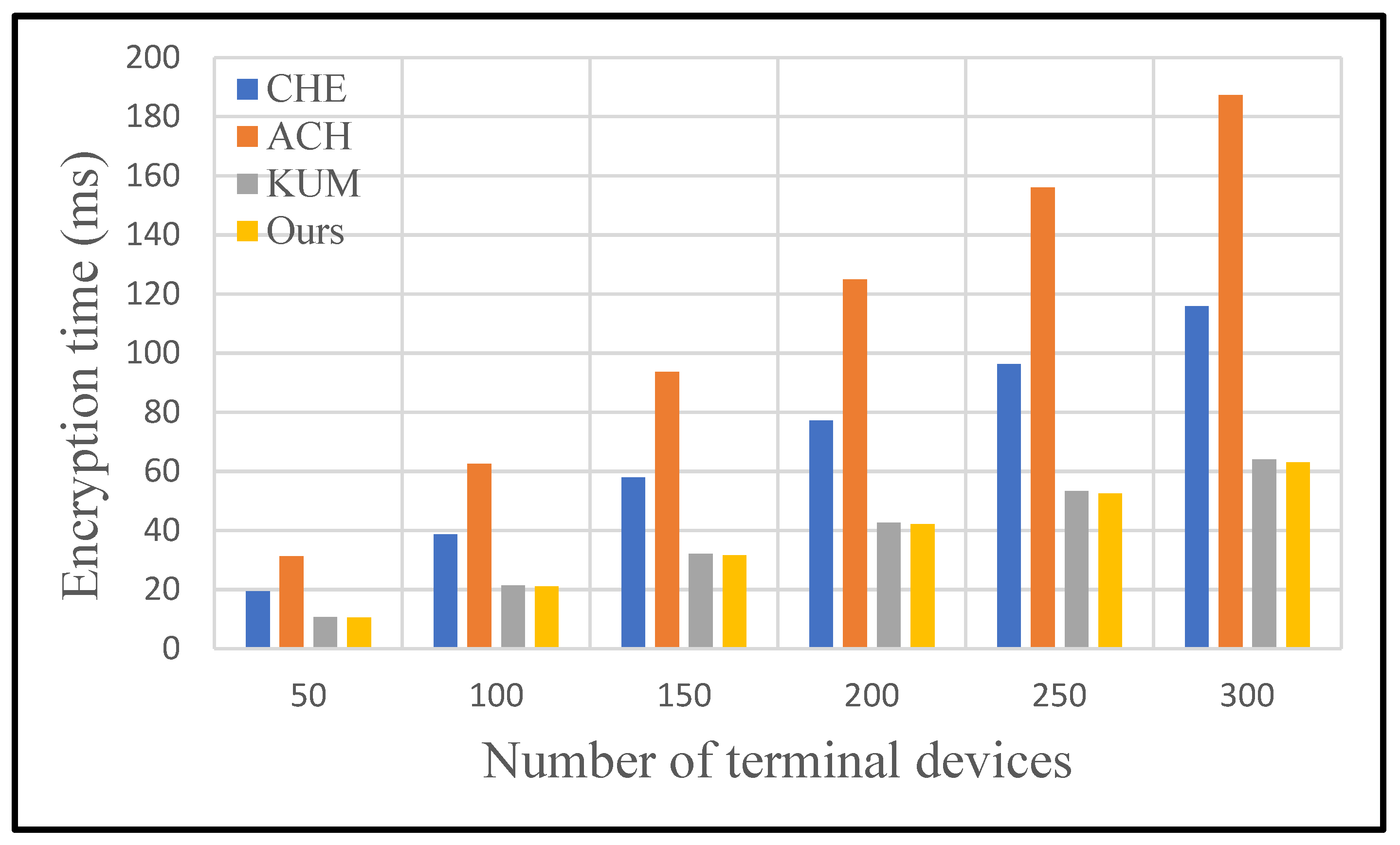
27]. The protocol of CHE and KUM has low encryption costs but requires a lot of bilinear pairing operations in the key generation and decryption stage, which is not suitable for resource-limited terminal devices in smart grids. In the decryption cost, the proposed protocol has a lower cost.
7.2. Experimental Analysis
In this section, we conduct some experiments to prove that the protocol we designed is efficient. We compare the proposed scheme with the schemes in CHE, ACH, and KUM in terms of encryption cost and decryption cost.
In our experiments, we used a computer with an Intel (R) Core (TM) i9-10920X CPU @ 3.50 GHz to simulate the CA in the design system. The cloud server was deployed on a 1-core, 2 GB RAM virtual machine with a high-I/O 40 GB system disk. We employ real-world smart grid terminal devices to evaluate the proposed protocol. Specifically, converged terminals use SCM701 MCUs with 4 GB ROM and 1 GB RAM, load control terminals leverage AT91SAM9G25-CU MCUs with 256 MB ROM and 64 MB RAM, and multi-function terminals integrate i.MX6 Dual-Core MCUs with 4 GB ROM and 512 MB RAM. In the experiment, the C++ programming language is used to implement the designed protocol, and the PBC library is used to multiply and modular exponents of elliptic curves. The hash function in our experiment is SHA-256. All tests were conducted under Ubuntu 20.0, while network conditions were emulated using Linux Traffic Control to impose 100 Mbps bandwidth and 50 ms latency constraints. These configurations are identical to smart grid environments, thereby demonstrating the scheme’s effectiveness in real-world scenarios.
As shown in
Figure 7, both the computation and communication costs of the proposed protocol are less than other authentication protocols. Since the Bloom filter is introduced to encode the identities of smart sensor devices, the proposed protocol reduces the computation and communication cost of the certification phase. Detailed experimental results are shown in
Table 3 and
Table 4. With the increasing number of terminal devices, the advantage of our protocol becomes more obvious. Specifically, the proposed protocol is 73.94% superior to others on average in terms of computation and 79.98% in terms of communication.
Figure 8 and
Figure 9 show comparisons of data encryption and decryption costs for each scheme with the increasing number of terminal devices. The proposed scheme is obviously superior to other schemes in terms of encryption and decryption cost. Detailed experimental results are shown in
Table 5 and
Table 6. Specifically, the running time of unicast encryption and multicast encryption increases linearly with the increase in terminal devices. Broadcast encryption does not consume excessive uptime due to changes in the number of devices. No matter how many devices are added, broadcast encryption is calculated only once using the device’s identity.
For the encryption process, the proposed protocol performs best among the four secure data communication protocols. KUM protocol also performs well with the increasing number of smart sensor devices, followed by CHE protocol, while ACH protocol showcases the worst performance. Specifically, the proposed protocol is 37.77% superior to others on average in terms of encryption cost.
For the decryption process, the proposed protocol is the most efficient protocol among the four secure data communication protocols as well. Particularly, the KUM protocol and CHE protocol demonstrate similar performance on efficiency in the decryption phase, which significantly falls behind our protocol. In terms of decryption efficiency, the ACH protocol is the worst protocol as well. Specifically, the proposed protocol is 55.75% superior to others on average in terms of decryption cost.
According to the evaluations above, our protocol showcases comprehensive advantages in the secure data communication process. The proposed protocol obviously demonstrates the best performance on authentication, encryption, and decryption progress. In conclusion, the proposed protocol provides an effective and efficient solution for secure data communication in smart grid scenarios.
8. Conclusions
In this paper, we propose a novel secure data communication protocol for sensor groups in the smart grid system. The proposed protocol leverages the symmetric encryption method to transmit obscured data and utilizes the identity-based encryption method to share group secret keys. To improve communication efficiency, the identities of authorized users are encoded by the Bloom filter, and a cloud-aided pre-verification procedure is introduced. Correspondingly, a novel dynamic update mechanism of the group secret key is designed in smart grid scenarios. When the sensor group is changed, the proposed mechanism utilizes lightweight operations to implement dynamic updates of the group secret key. Theoretical analysis demonstrates that our protocol achieves forward and backward security of a dynamic sensor group and has the capability to resist the replay attack and impersonation attack. Experimental evaluation indicates that our protocol performs better than the state-of-the-art protocols. Specifically, for computation cost, the proposed protocol is 73.94% superior to others on average in the authentication process, 37.77% in the encryption process, and 55.75% in the decryption process. For communication cost, the proposed protocol is 79.98% superior to others on average in the authentication process.
Author Contributions
Conceptualization, Y.F.; methodology, Y.F. and B.X.; software, Y.C.; validation, Y.C.; formal analysis, Y.S.; writing—original draft preparation, Y.F.; writing—review and editing, Y.L.; visualization, Y.F.; supervision, B.X.; funding acquisition, Y.F. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by a grant from the National Key Research and Development Program of China (No. 2022YFB2402900) Key Techniques of Adaptive Grid Integration and Active Synchronization for Extremely High Penetration Distributed Photovoltaic Power Generation and Science and Technology Project of State Grid Corporation of China under grant 52060023001T (Key Techniques of Adaptive Grid Integration and Active Synchronization for Extremely High Penetration Distributed Photovoltaic Power Generation).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The raw data supporting the conclusions of this article will be made available by the authors on request.
Acknowledgments
The authors acknowledge Wenting Wang and Sun Li for their assistance in this study.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Fang, X.; Misra, S.; Xue, G.; Yang, D. Smart grid—The new and improved power grid: A survey. IEEE Commun. Surv. Tutor. 2011, 14, 944–980. [Google Scholar] [CrossRef]
- Gungor, V.C.; Sahin, D.; Kocak, T.; Ergut, S.; Buccella, C. Smart grid technologies: Communication technologies and standards. IEEE Trans. Ind. Inform. 2011, 7, 529–539. [Google Scholar] [CrossRef]
- Liu, Z.; Cao, Z.; Dong, X.; Zhao, X.; Liu, T.; Bao, H.; Shen, H. EPMDA-FED: Efficient and Privacy-Preserving Multidimensional Data Aggregation Scheme with Fast Error Detection in Smart Grid. IEEE Internet Things J. 2022, 9, 6922–6933. [Google Scholar] [CrossRef]
- Zhang, X.; You, L.; Hu, G. An Efficient and Robust Multidimensional Data Aggregation Scheme for Smart Grid Based on Blockchain. IEEE Trans. Netw. Serv. Manag. 2022, 19, 3949–3959. [Google Scholar] [CrossRef]
- Zuo, X.; Li, L.; Peng, H.; Luo, S.; Yang, Y. Privacy-Preserving Multidimensional Data Aggregation Scheme Without Trusted Authority in Smart Grid. IEEE Syst. J. 2021, 15, 395–406. [Google Scholar] [CrossRef]
- Halak, B.; Yilmaz, Y.; Shiu, D. Comparative analysis of energy costs of asymmetric vs. symmetric encryption-based security applications. IEEE Access 2022, 10, 76707–76719. [Google Scholar] [CrossRef]
- Patgiri, R.; Muppalaneni, N.B. Stealth: A highly secured end-to-end symmetric communication protocol. In Proceedings of the International Symposium on Networks, Computers and Communication, Shenzhen, China, 19–22 July 2022; pp. 1–8. [Google Scholar]
- Gadhiya, N.; Tailor, S.; Degadwala, S. A review on different level data encryption through a compression techniques. In Proceedings of the International Conference on Inventive Computation Technologies, Lalitpur, Nepal, 24–26 April 2024; pp. 1378–1381. [Google Scholar]
- Jimale, M.A.; Z’ABa, M.R.; Kiah, L.B.M.; Idris, M.Y.I.; Jamil, N.; Mohamad, M.S.; Rohmad, M.S. Authenticated encryption schemes: A systematic review. IEEE Access 2022, 10, 14739–14766. [Google Scholar] [CrossRef]
- Shen, Y.; Sun, Z.; Zhou, T. Survey on asymmetric cryptography algorithms. In Proceedings of the International Conference on Electronic Information Engineering and Computer Science, Changchun, China, 23–26 September 2021; pp. 464–469. [Google Scholar]
- Al-Shareeda, M.A.; Anbar, M.; Manickam, S.; Khalil, A.; Hasbullah, I.H. Security and privacy schemes in vehicular ad-hoc network with identity-based cryptography approach: A survey. IEEE Access 2021, 9, 121522–121531. [Google Scholar] [CrossRef]
- Gupta, B.B.; Gaurav, A.; Hsu, C.-H.; Jiao, B. Identity-based authentication mechanism for secure information sharing in the maritime transport system. IEEE Trans. Intell. Transp. Syst. 2021, 24, 2422–2430. [Google Scholar] [CrossRef]
- Zhao, Y.; Wang, Y.; Liang, Y.; Yu, H.; Ren, Y. Identity-based broadcast signcryption scheme for vehicular platoon communication. IEEE Trans. Ind. Inform. 2022, 19, 7814–7824. [Google Scholar] [CrossRef]
- Shen, S.; Wang, H.; Zhao, Y. Identity-based authenticated encryption with identity confidentiality. Theor. Comput. Sci. 2022, 901, 1–18. [Google Scholar] [CrossRef]
- Pavithran, D.; Al-Karaki, J.N.; Shaalan, K. Edge-based blockchain architecture for event-driven IoT using hierarchical identity based encryption. Inf. Process. Manag. 2021, 58, 102528. [Google Scholar] [CrossRef]
- Badar, H.M.S.; Qadri, S.; Shamshad, S.; Ayub, M.F.; Mahmood, K.; Kumar, N. An identity based authentication protocol for smart grid environment using physical uncloneable function. IEEE Trans. Smart Grid 2021, 12, 4426–4434. [Google Scholar] [CrossRef]
- Samiullah, F.; Gan, M.-L.; Akleylek, S.; Aun, Y. Group key management in internet of things: A systematic literature review. IEEE Access 2023, 11, 77464–77491. [Google Scholar] [CrossRef]
- Fiat, A.; Naor, M. Broadcast encryption. In Advances in Cryptology—CRYPTO’93: 13th Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 1994; pp. 480–491. [Google Scholar]
- Boneh, D.; Gentry, C.; Waters, B. Collusion resistant broadcast encryption with short ciphertexts and private keys. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 2005; pp. 258–275. [Google Scholar]
- Lewko, A.; Sahai, A.; Waters, B. Revocation systems with very small private keys. In Proceedings of the IEEE Symposium on Security and Privacy, Oakland, CA, USA, 16–19 May 2010; pp. 273–285. [Google Scholar]
- Chen, L.; Li, J.; Zhang, Y. Adaptively secure efficient broadcast encryption with constant-size secret key and ciphertext. Soft Comput. 2020, 24, 4589–4606. [Google Scholar] [CrossRef]
- Acharya, K. Secure and efficient public key multi-channel broadcast encryption schemes. J. Inf. Secur. Appl. 2020, 51, 102436. [Google Scholar] [CrossRef]
- Sravan Kumar, G.; Sri Krishna, A. Privacy sustaining constant length ciphertext-policy attribute-based broadcast encryption. In Soft Computing and Signal Processing; Springer: Singapore, 2019; pp. 313–324. [Google Scholar]
- Wazid, M.; Das, A.K.; Kumar, N.; Rodrigues, J.J.P.C. Secure three-factor user authentication scheme for renewable-energy-based smart grid environment. IEEE Trans. Ind. Inform. 2017, 13, 3144–3153. [Google Scholar] [CrossRef]
- Mahmood, K.; Chaudhry, S.A.; Naqvi, H.; Kumari, S.; Li, X.; Sangaiah, A.K. An elliptic curve cryptography based lightweight authentication scheme for smart grid communication. Future Gener. Comput. Syst. 2018, 81, 557–565. [Google Scholar] [CrossRef]
- Kumar, P.; Gurtov, A.; Sain, M.; Martin, A.; Ha, P.H. Lightweight authentication and key agreement for smart metering in smart energy networks. IEEE Trans. Smart Grid 2018, 10, 4349–4359. [Google Scholar] [CrossRef]
- Wang, J.; Wu, L.; Choo, K.-K.R.; He, D. Blockchain-based anonymous authentication with key management for smart grid edge computing infrastructure. IEEE Trans. Ind. Inform. 2019, 16, 1984–1992. [Google Scholar] [CrossRef]
- Lin, H.Y.; Hsieh, M.Y. A dynamic key management and secure data transfer based on m-tree structure with multi-level security framework for Internet of vehicles. Connect. Sci. 2022, 34, 1089–1118. [Google Scholar] [CrossRef]
- Tan, H.; Zheng, W.; Guan, Y.; Lu, R. A privacy-preserving attribute-based authenticated key management scheme for accountable vehicular communications. IEEE Trans. Veh. Technol. 2022, 72, 3622–3635. [Google Scholar] [CrossRef]
| Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).