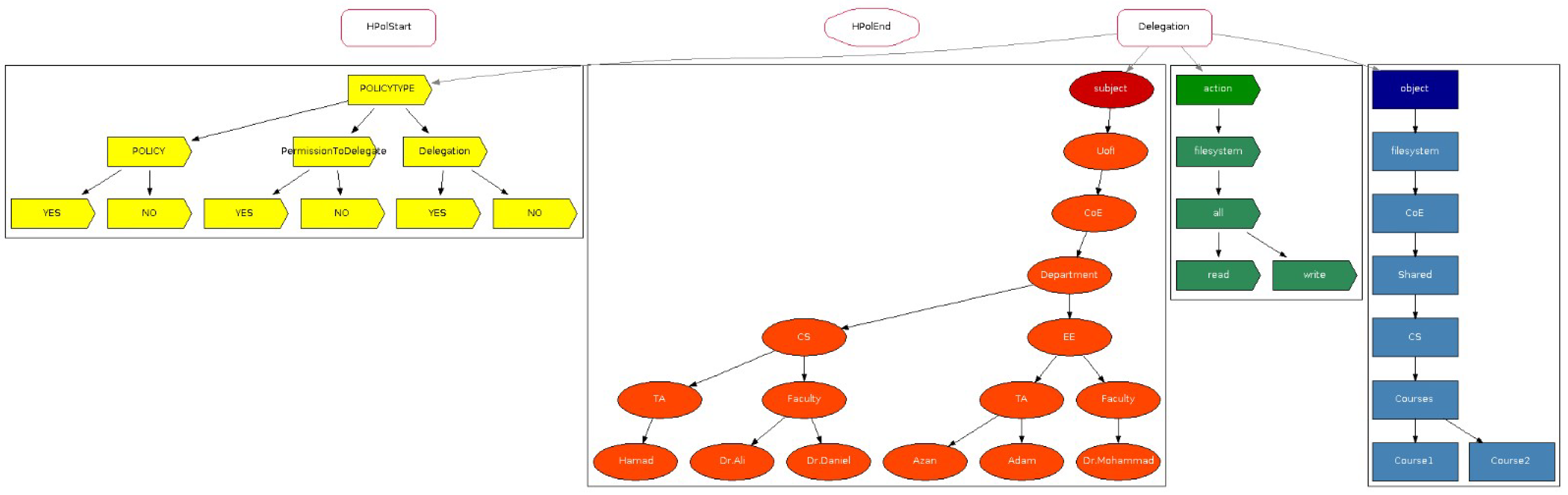
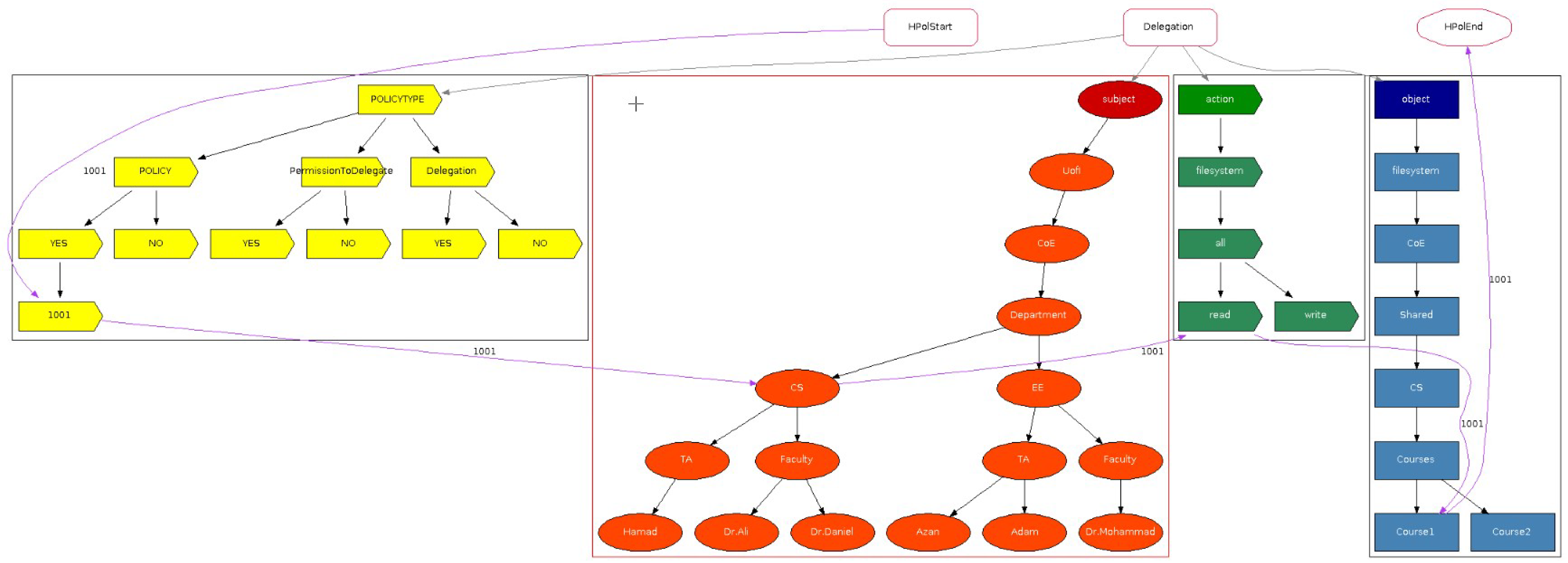
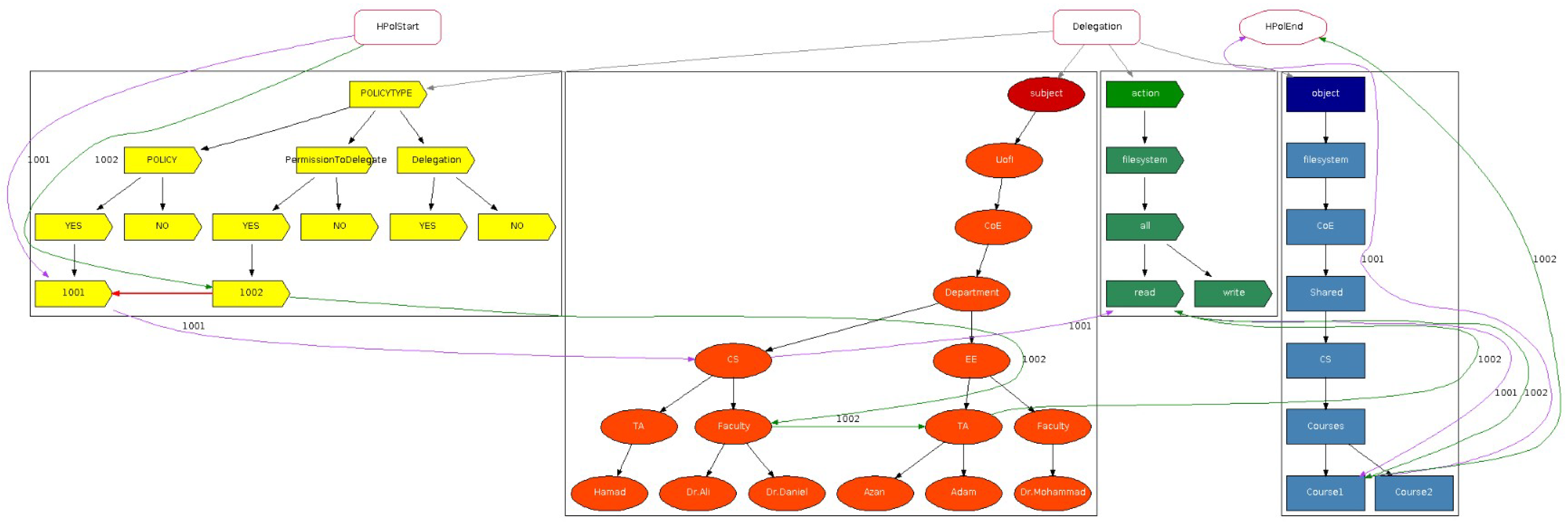
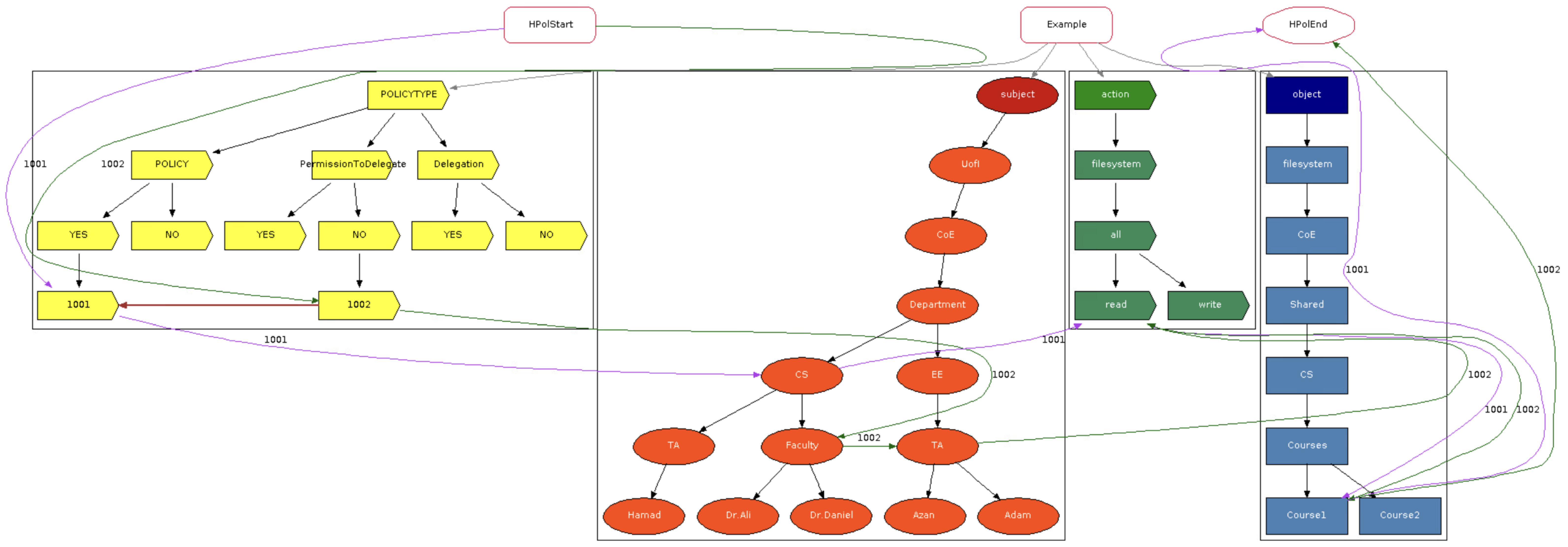
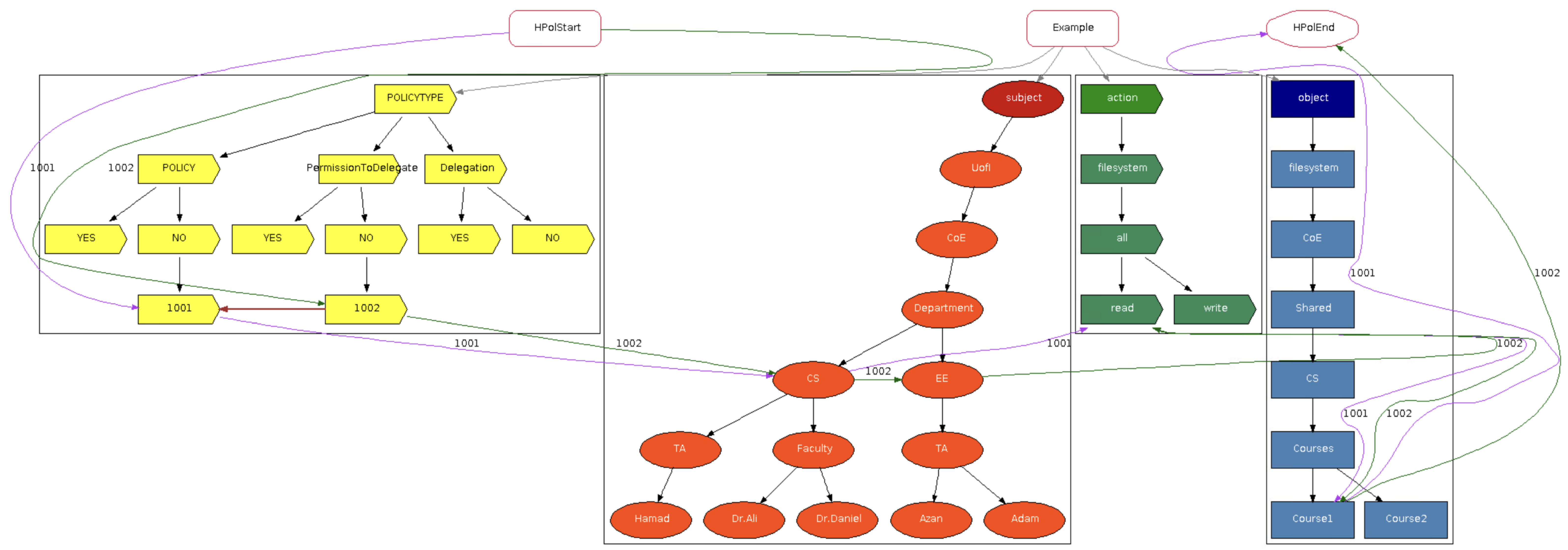
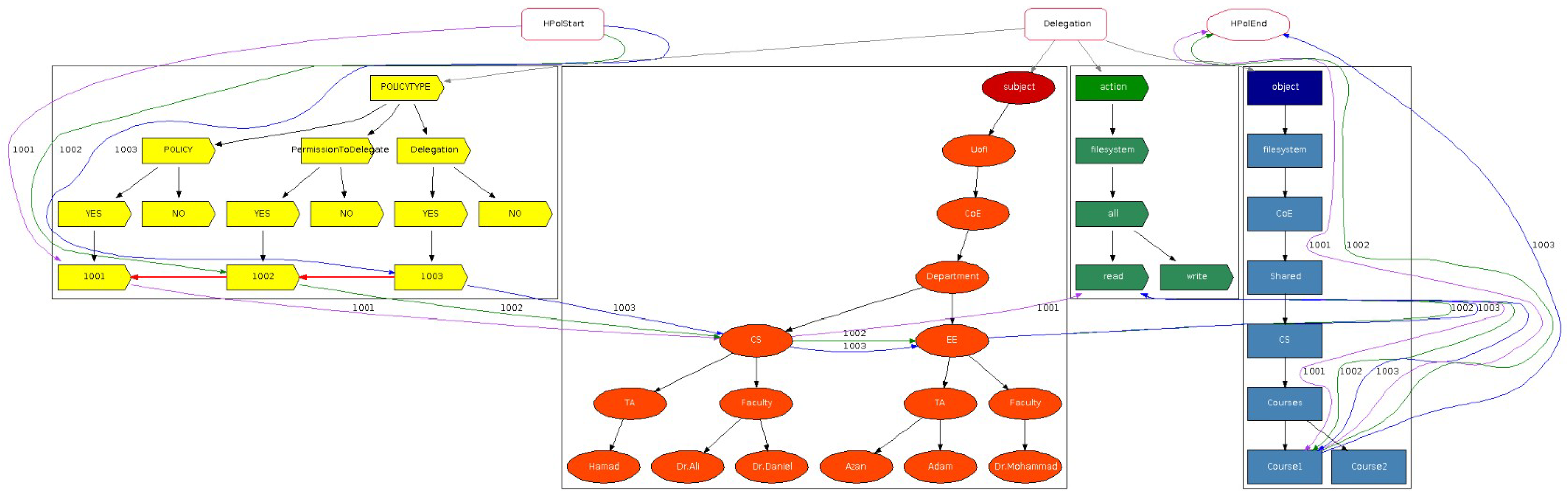
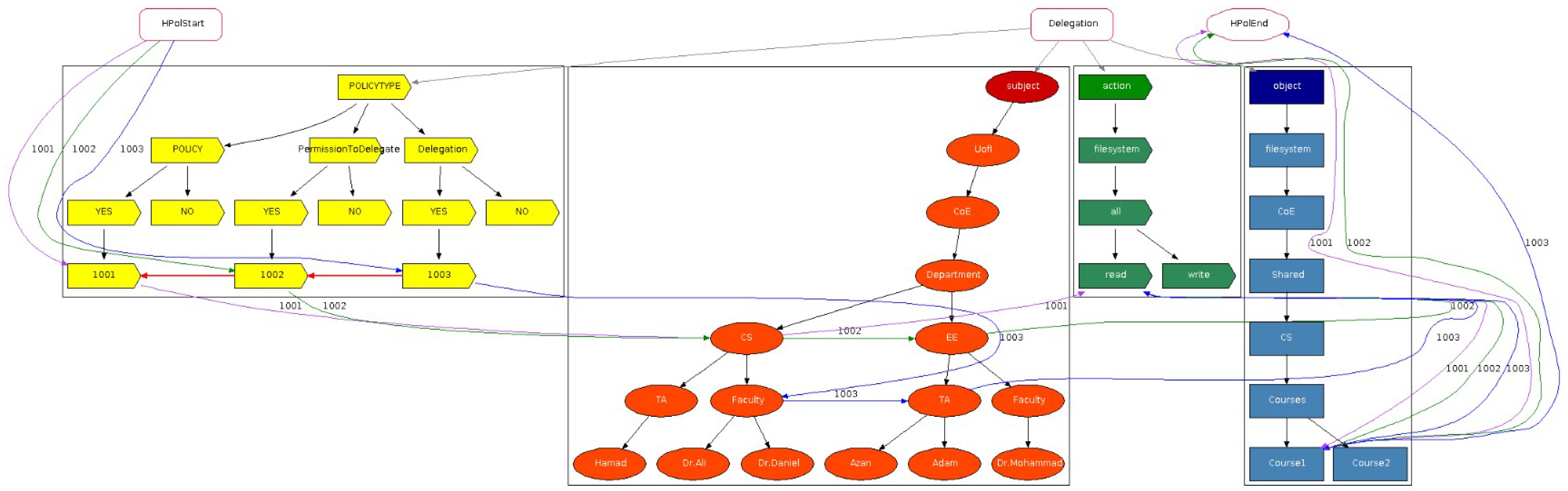
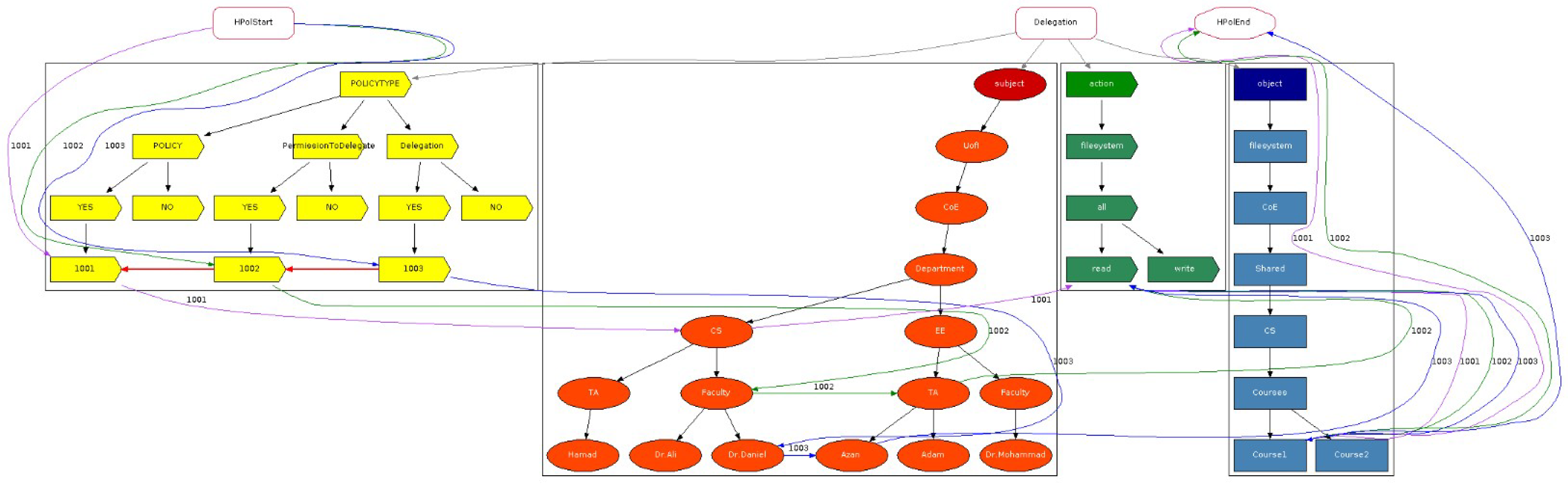
2.1. Access Control
Access control is essential for information and device security, preventing unauthorized access and regulating user privileges. This section explores various models, including attribute-based, discretionary, mandatory, and role-based access control, positive and negative policies, positive and negative permission to delegate, and positive and negative delegation.
In the field of cybersecurity, access control is playing a growing role, enabling authorized users to access system resources while blocking unauthorized access. Specifically, attribute-based access control (ABAC) and role-based access control (RBAC) stand out. ABAC relies on user and object attributes, while RBAC restricts access based on organizational roles. These models offer diverse approaches to access control.
2.2. Access Control Models
Attribute-based access control model (ABAC): ABAC is a type of system that simplifies access control by focusing on user and object attributes, environmental factors, and rules, rather than standard ownership and roles. ABAC prioritizes user identity and classifies attributes into domains, including user, object, environmental, connection, and administrative attributes, defining access requirements. Critical ABAC components include users, objects, attributes, policies, and their connections, formalized in various ABAC models. For further details about the distribution of ABAC please refer to the research conducted by [
14].
Discretionary access control (DAC): DAC functions as an access control system in which the policies governing access to secured computers, records, or resources are established by administrators or owners. These policies outline the eligibility criteria for resource access and often grant administrators the ability to limit the spread of access permissions. A common criticism of DAC models concerns the absence of centralized authority control. To learn more about DAC concepts, please refer to the [
15] survey.
Mandatory access control (MAC): MAC is a security model whereby a central entity oversees access permissions, which are determined by different security stages. Public institutions and armed forces often employ a DAC model to control their operating systems, hardware resources, and security cores. MAC can approve or disapprove access to specific computer resources based on device or user information checks. For more information, please refer to the publication by [
15].
Role-based access control (RBAC): RBAC is an alternative to DAC and MAC access controls, using a different approach to regulating access to computer resources. For additional details on RBAC systems, please see the survey reported in [
15].
2.5. Related Work
Based on our earlier analysis and research classification survey [
12] which provides a comparison of previous studies related to access control attributes, we focus on issues highlighted in the research that need to be investigated and solved with respect to the features of access control models.
Table 1 summarizes previous research based on our survey results. The survey initially identified 172 articles from the literature. After deleting duplicates, there were 137 articles left. Following relevance analysis, 39 articles were identified as relevant. Out of the 39 publications considered relevant, four were surveys and 35 were individual studies. Subsequently, an analysis of knowledge gaps was undertaken.
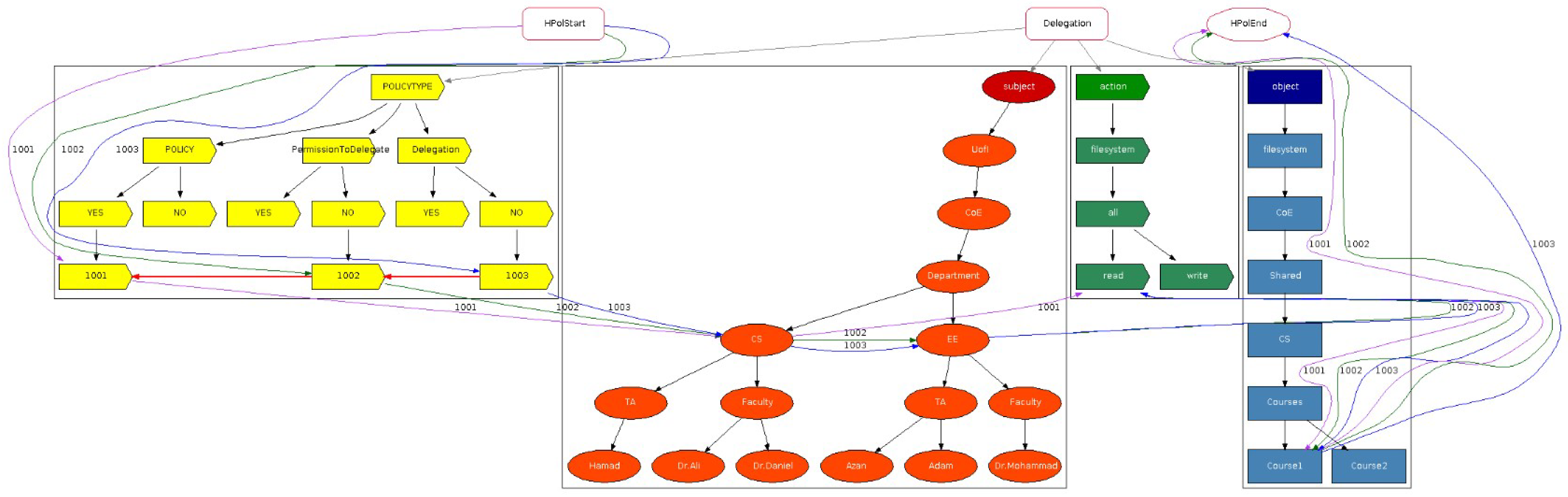
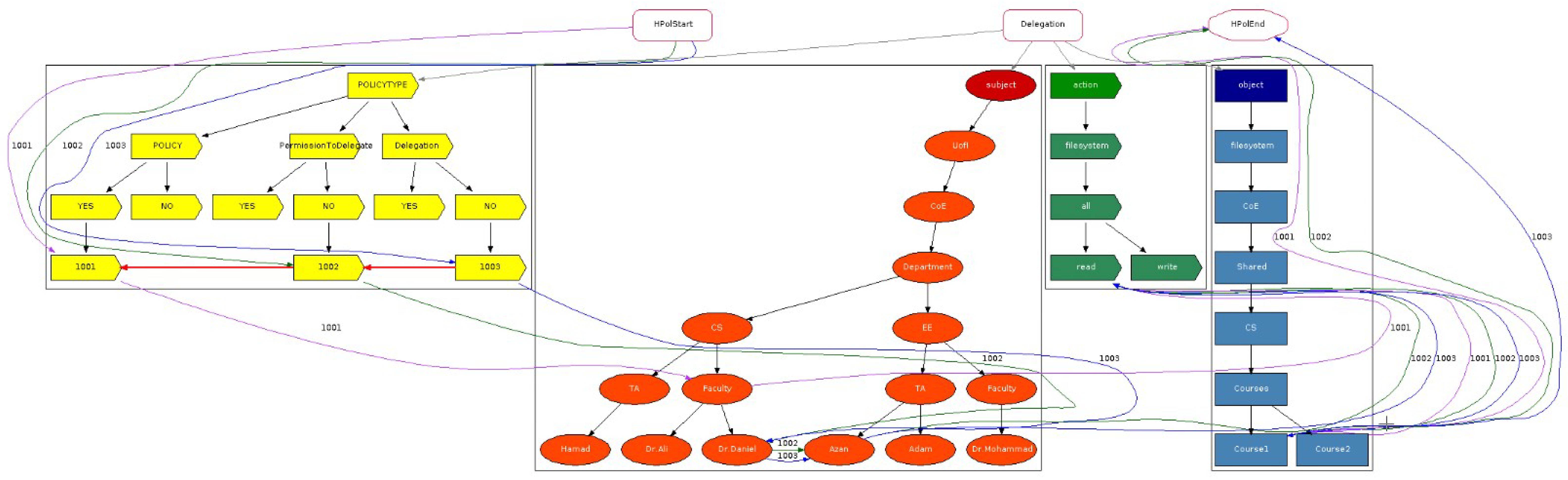
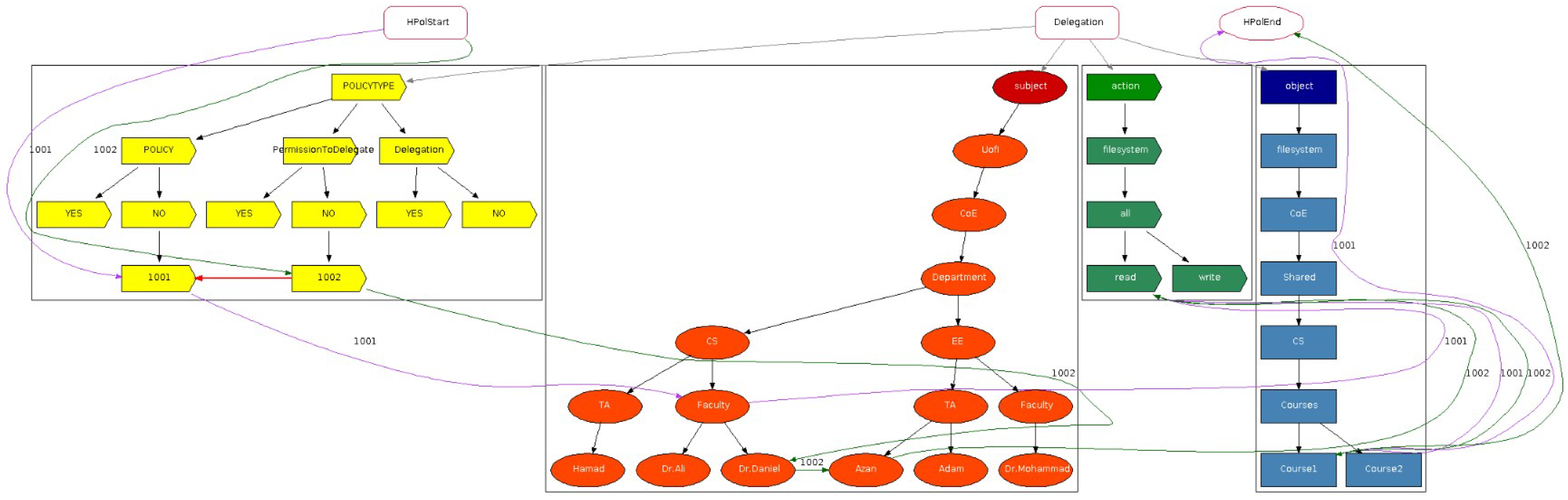
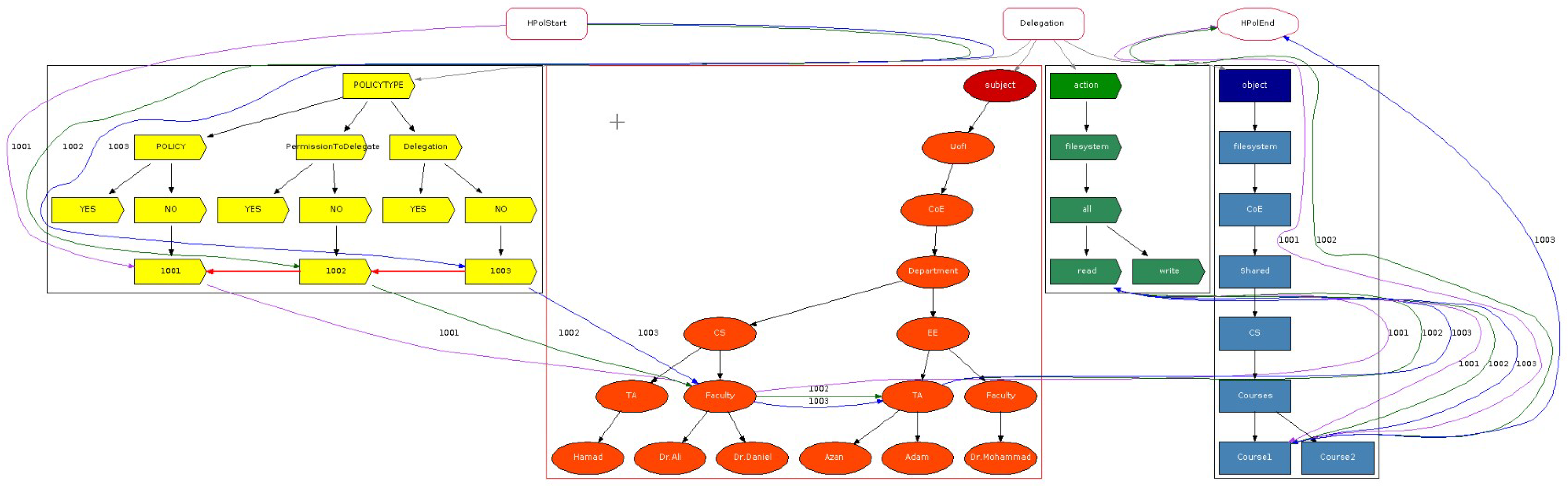
We first consider features relating to supporting positive and negative policies plus redundancy and conflict detection highlighted in our previous study [
18] (submitted under review). They represent solutions that have been successful, while the features highlighted in blue with a green check mark in
Table 1 signify current work in this article. The check marks highlighted in blue, detailed in
Section 3.3, denote support for both types of permission to delegate, and both types of delegation. Furthermore, we provide an overview of the 35 relevant articles identified in our survey [
12].
According to [
19], a delegation model based on socio-technical design, cooperation and collaboration theory best fits the needs of social networks. The model was created with ontologies and implemented with Facebook APIs. When multiple policies overlap, policy conflicts and redundant policies are identified. The authors investigate the model’s expressive power, and its acceptability with users is tested. It is additionally evaluated in terms of social validity by comparing to 27 previous delegation models based on socio-technical validity parameters derived from socially accepted principles.
Article [
20] describes a new delegation approach for extended role-based access control models, showing that it is adaptable for dealing with administration and delegation requirements in a united framework. The approach also makes it simple to express various delegation and revocation dimensions. Because the model is object-oriented, privileges are not directly adjusted; instead, objects with certain semantics can modify abilities such as permissions and constraints. Each object represents a power assignment or delegation, such as a user to a role or a user or a role to a permission. Limitations of the work include incompatibility of various types of permissions, whether positive or negative, for different types of delegation, such as positive and negative, and the conflict that exists between them.
The authors of [
21] introduced a strategy for implementing a systematic and automated technique of determining if a subject has the authority to carry out delegation in a way that does not result in conflict or separation of duties prior to system enforcement. They used the Ponder language in their project on authorization and delegation policies. Ponder authorization policies are simply access control policies that are designed to prevent unauthorized resource access. A positive permission policy defines the actions that a subject is permitted to take on target objects. Negative authorization procedures that restrict individuals’ access to specified resources are not addressed since delegation of limitations is illogical. From our perspective, both positive and negative conflict policies must be evaluated rather than solely focusing on the positive while dismissing the conflict. Furthermore, it is important to consider how both kinds of permission to delegate conflict with one other, as well as with either positive or negative policy, or with both types of delegation. It is necessary to cover both positive and negative policy, both types of delegation authorization, and both types of delegation conflict. We discuss the separation of duties conflict and the violation of the separation of duties rule further below.
To empower accurate specification and verification of such policies, Ref. [
22] proposes a model-driven engineering (MDE) approach based on UML and the Object Constraint Language (OCL). The authors begin by presenting a categorization of the different kinds of RBAC permission policies proposed in the literature. The authors propose the GemRBAC model, which is a generalized RBAC model that incorporates all of the entities needed to establish the classified policies. The model is a conceptual model that can function as a data model for data gathering and verification. The classified RBAC policies are formalized as OCL constraints on the GemRBAC model. To accommodate such operationalization, the authors utilize the Ecore version of the GemRBAC model and the OCL constraints corresponding to the categorized models publicly available online. Finally, SoD constraints are supported to avoid a mutual exclusion relation among roles, permissions, or users.
Ref. [
23] presents a comprehensive delegation method for role-based access control based on the organization-based access control (OrBAC) formalism. This includes clearly establishing delegation limitations, such as the requisite settings for the user delegating and the user receiving the delegation, role-to-role and user-to-user, to delegate a permission. The model is more adaptable, simpler to operate, and more comprehensive. Moreover, the OrBAC model offers accommodations for dealing with delegation needs without the requirement of additional elements. The OrBAC model is built around multi-granular as well as contextual licensing requirements. This allows users to specify numerous delegation characteristic features, such as permanence, totality, revocation, and so on.
Ref. [
24] presents a Cellular Automata (CA)-based conflict resolution approach for RBAC. The scalability of general computing environments requires role delegation in RBAC. This practical principle, however, can lead to conflicts during compile and operate situations. The authors propose a policy for SoD and demonstrate conflict-free role delegation. The delegation mechanism, which is based on a type of CA known as Multiple-Attractor CA (MACA), can be applied effectively as an authorizing approach in complicated automated machines within RBAC.
The authors of [
25] map RBAC onto multiple-attractor cellular automata for easy management (MACA). The restriction on SoD and role delegations can be easily addressed in MACA using pseudo-exhaustive (PE) bit patterns. The authors also demonstrate how to resolve conflicts between specified SoD constraints and delegation operations using PE-bit patterns. Because multiple subjects can grant authorizations in RBAC, administration becomes more difficult to control, and cascading and cyclic permissions may occur. As a result, the authors create an efficient mapping and delegation methodology based on MACA and utilizing PE-bit patterns. The proposed model can effectively prevent unwanted user intentions while limiting delegation time and avoiding conflicts. As a result, the authors anticipate that their mechanism will be effective for approving a technique in a difficult and complicated environment within RBAC’s automatic system.
The authors of [
26] developed an XML-based delegation and revocation (XDR) model for WISs, which supports fine-grained delegation and managed resource spreading. In addition, the proposed model allows for a variety of delegation and revocation methods, including single-step delegation, multi-step delegation, multiple delegation, partial delegation, separation of duties, and cascading revocation. A prototype was developed and tested to illustrate the potential of the proposed model.
Different models, including PBDM, RBDM0, and RDM2000, were compared and contrasted in [
27]. Total and user-to-user delegation are handled by the RBDM0 and RDM2000 models. In terms of approval administration, the PBDM model allows delegation from role-to-role and user-to-user, in addition to delegation during the role and permission phases, giving it a wide range of options. The authors included some non-support constraints, like the SoD for role-to-role delegation and user-to-user delegation, in the PBDM model. A delegation model was developed based on permission attributes, allowing system administrators to successfully handle permission phase delegation and partial delegation as well as inheritance restrictions. In future work, the model will require to be enhanced to include other delegation features, such as responsibility delegation and negative delegation.
The research study conducted by [
28] presents a logic-based framework for decentralized RBAC systems that allows for dynamic delegation. The framework provides the opportunity for an administrator to delegate responsibilities and permissions between roles. The idea of delegation trust is considered and the authors demonstrate how extended logical programming can be used to define roles and delegation responsibilities in terms of trust levels, delegation scope, role advantages and their distribution, dispute resolution, and the resolution of conflicts. Moreover, the systems proposed allow implementation of role restrictions, such as SoD, role structure, and defining the limitations of cardinality. The designed system is extensible and provides a solid platform for developing and implementing advanced role-based policies for access control within decentralized settings. Based on the administration’s delegation characteristics, the role access control is significantly enhanced. Another factor to consider is multiple delegation conflict, which can arise in either positive or negative delegation between numerous roles. Furthermore, both types of permission to delegate authority must be granted or rejected before delegation is approved between multiple roles.
In [
29], the authors discuss user-to-user delegation issues by demonstrating how delegations are implemented in the RBAC model. The model is distinguished in giving the user complete power about which authority he or she wishes to delegate, as perceived differently in relation to delegation at the role point, where all privileges of such a role have to be delegated. Furthermore, delegation and revocation are addressed, with a comprehensive set of rules for further delegations in the model for actions related to a right, as well as generic restrictions for further delegation of direct authority. Additional plans will be required to provide a more comprehensive system for managing rights.
Authorization, which is an extremely vital aspect of RBDM, can create conflict in situations where a user grants permissions to delegated users while another user grants negative permissions. The authors of Ref. [
30] propose using negative authorization in role-based group delegation to solve the conflict issue. The authors begin by presenting delegation models for granting and revocation, and then investigate the implications of negative delegation authorization on the hierarchy of roles.
Ref. [
31] presents a delegation model based on a decentralized management role graph model that supports permission to user, user-to-user, and role-to-role delegation by combining users or tasks given and defining the user role task. In the delegation model, the model is divided into two parts: a static part allows for easier administration and deployment and a dynamic part is left for future work. The authors include details regarding a member’s or team’s modifications, role hierarchy processes, and RBAC operational processes that are relevant to specific delegation issues.
Ref. [
32] considers how to clarify and enforce delegation permissions. The article describes a rule-based methodology for developing authorization policies. Using a rule-based language, the authors were able to determine and enforce permission restrictions in powerful and flexible ways. Furthermore, the rules can be used to identify potential future exceptions and handle potential conflicts. It is suggested that in large, distributed role-based systems, determining and adding complicated delegation authorization policies are difficult and time-consuming duties. Delegation is intended to meet user needs by specifying an authorization policy, whereas organizational policies can be stated to impose restrictions. The approach simplifies role administration in role-based systems through delegation.