A Fuzzy-Based Relay Security Algorithm for Wireless Sensor Networks
Abstract
1. Introduction
2. Related Works
2.1. Fuzzy-Based Relay Selection Algorithm
- Step 1:
- Defining the input and output variables and giving the domain of membership functions.
- Step 2:
- Defining the membership functions as the fuzzy processing program, and then outputting the input value with a different membership degree [0, 1].
- Step 3:
- Designing a fuzzy rules base. Based on experience or expert knowledge, designers use the semantic transform of “IF X1 is A AND X2 is B, THEN Y is C” to create a fuzzy rule base that will become the core of the fuzzy inference engine.
- Step 4:
- Fuzzification inference: The results are derived from an interactive fuzzy operation control rule base.
- Step 5:
- Defuzzification: It achieved an output value from aggregated results using the membership degrees.
2.2. Yang’s Fuzzy Inference Method
- Step 1:
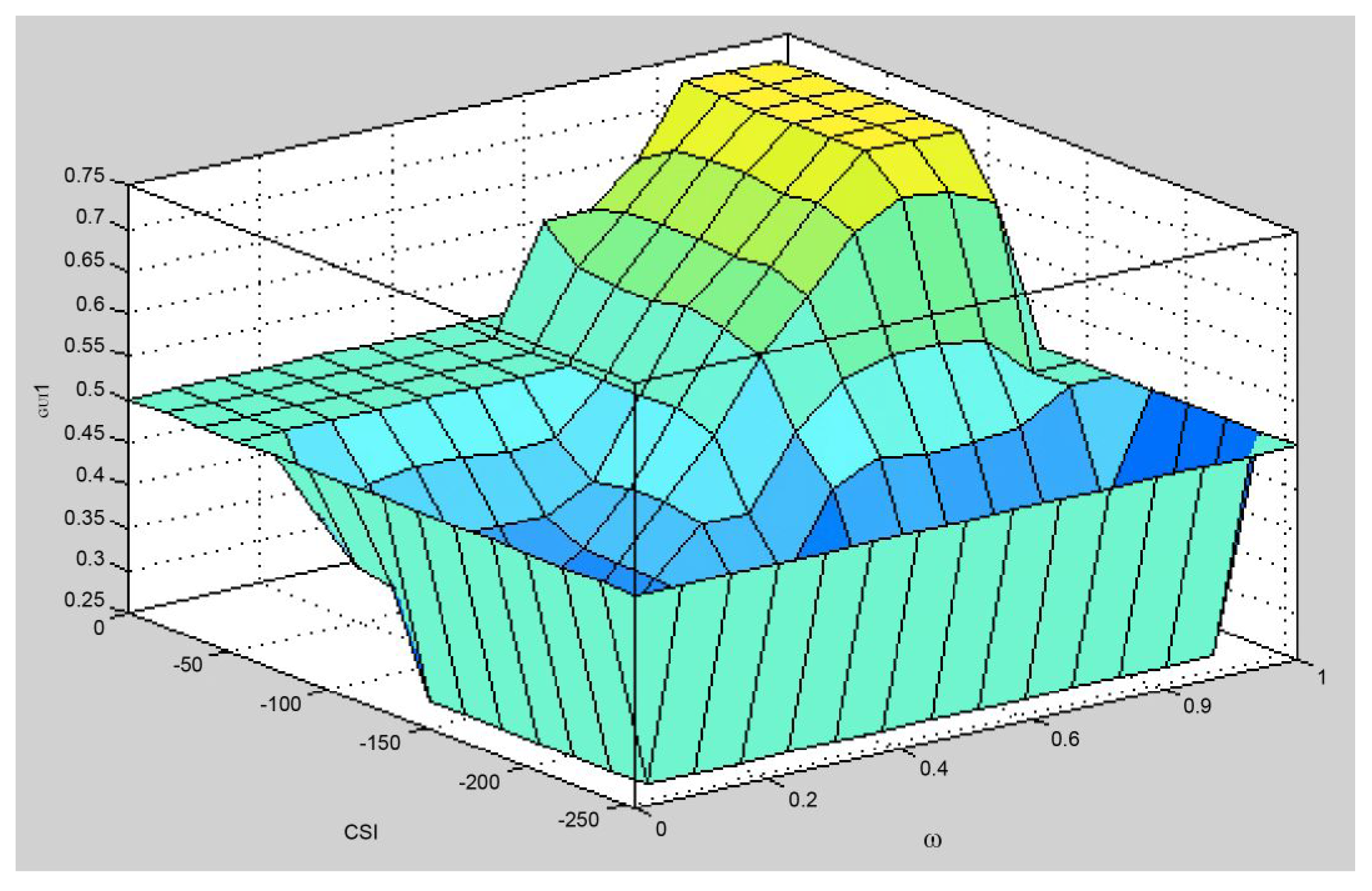
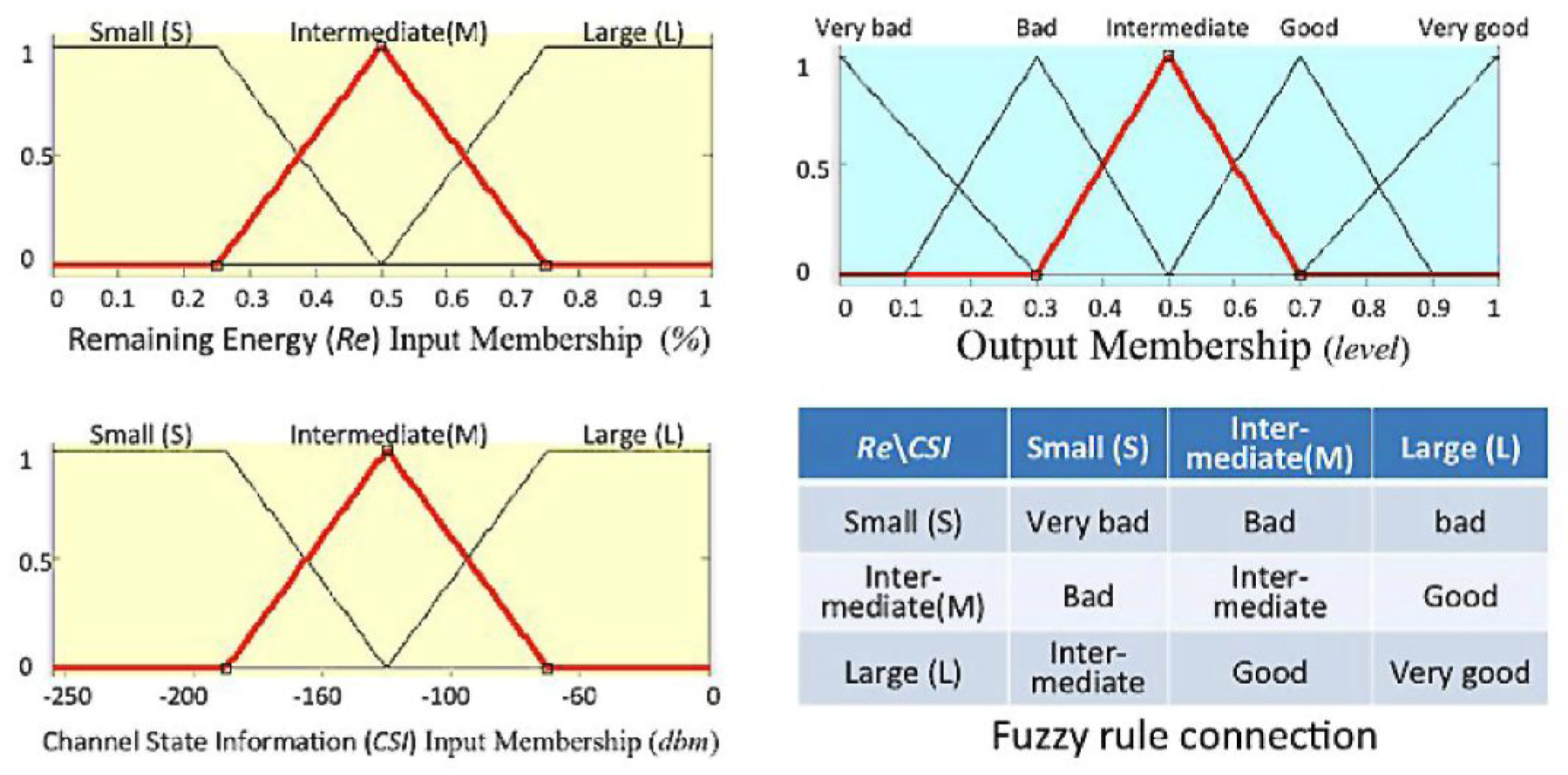
- Establishing membership degree matrix of input variables (Re: Remaining power; CSI: Communication State Information). Formula (1) is an example of a five-input matrix of candidate nodes:
- Step 2:
- Formula (2) assigns the output weights for adjustment.
- Step 3:
- Use the operation of to calculate the output result by in Formula (3). The output node of 0.85 is determined as a relay node. Yang used a sorting algorithm as its selection mechanism when the result has the same output value.
2.3. Brante’s Fuzzy Inference Method
3. Research Methods
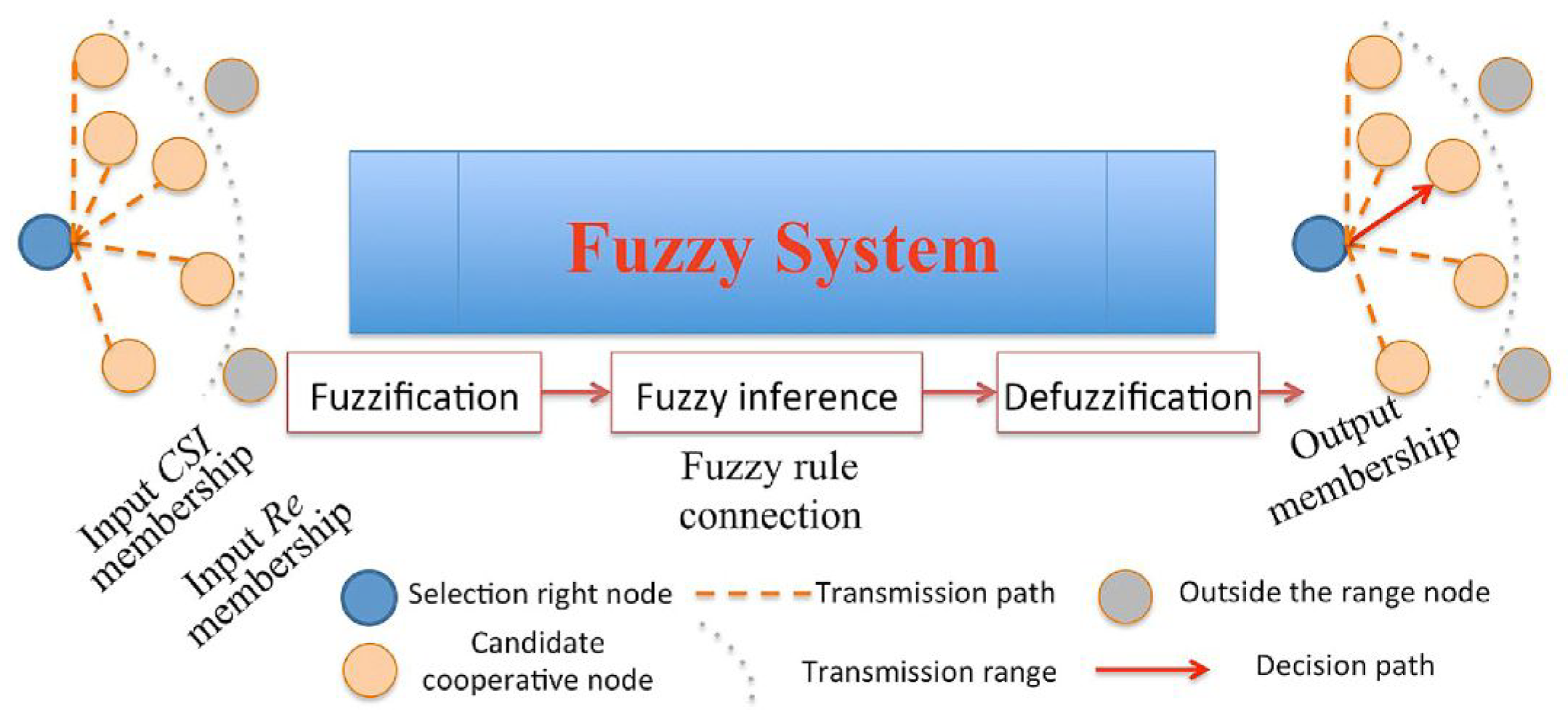
3.1. Relay Selection Algorithm in a Fuzzy System
3.2. Tabu Algorithm
- Step 1:
- Enter the values of the parameters and conditions.
- Step 2:
- Randomly select any one group of the starting solutions.
- Step 3:
- Construct a candidate list for selecting the best solution from the neighborhood.
- Step 4:
- Before performing Step 5, first examine the Tabu list to filter the selected moves; only allow moves that are not in the Tabu list or are in compliance with the principle of opening the Tabu list. If not in line with the principle of opening the Tabu list, return to Step 3 and select sub-optimal solutions to view.
- Step 5:
- Be moving.
- Step 6:
- To record moving steps to the Tabu list, and according to the first in, first out (FIFO) method, the oldest records are removed in order to maintain the length of the Tabu list.
- Step 7:
- Calculate the objective function and compare the current best solution and the recorded optimal solution. If the current optimal solution is superior, go to Step 3; otherwise, go to Step 9. The score of the objective function is returned to the Tabu search algorithm to determine whether to update the best solution or perform a new move. The objective of its design is to minimize network damage, such as energy consumption.
- Step 8:
- Update the best solution to the current recorded optimal solution.
- Step 9:
- Determine the termination conditions for default; if it meets these conditions, go to the end step. On the contrary, return to Step 3.
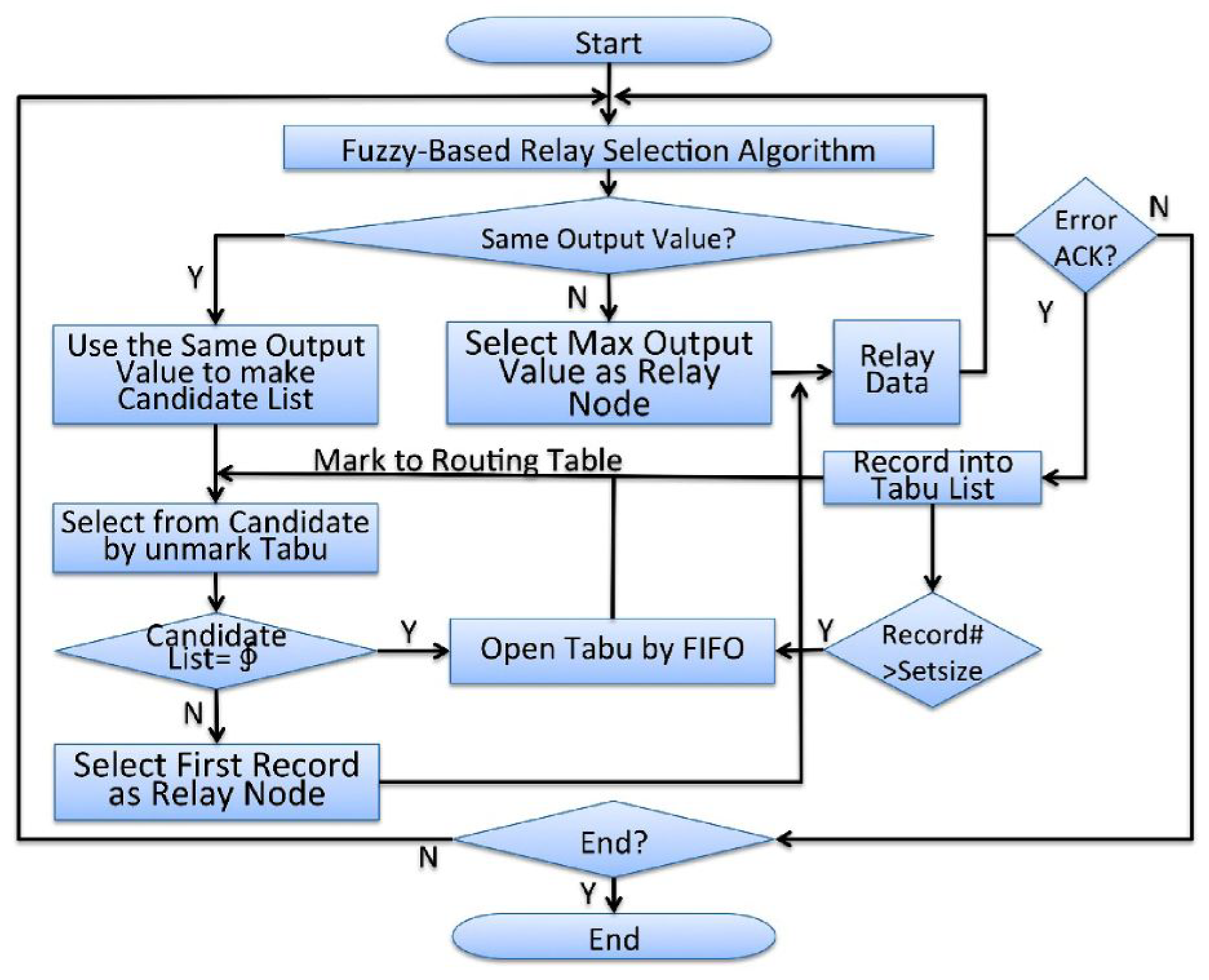
3.3. The Proposed FTRS Algorithm
- Fuzzy logic for multi-criteria decision-making (evaluating residual energy, link quality, etc.);
- Tabu search with a short-term memory (Tabu list) to handle cases where multiple nodes receive the same fuzzy score.
- Procedure 1:
- The fuzzy relay safety-selection algorithm is used to judge whether it generates using the case of the same output value first. If not, the first output node will be transferred directly as a relay partner.
- Procedure 2:
- If it has the same output value, it is filtered from the routing table for a no Tabu flag record as the candidate node list. The Tabu flag is marked on a routing table when it is recorded in the transmissible failed Tabu list.
- Procedure 3:
- If the candidate list is not empty, it uses the first record for the relay node to transmit the information directly. If the candidate list is empty, it starts the opening Tabu list and clears the Tabu flag in the routing table using the first-in, first-out method. Another timing procedure is used to start the opening Tabu list when the number of Tabu lists exceeds a preset value, which avoids routing table lists, including all of the Tabu lists. Then, the algorithm will never escape the release of nodes as a relay node for choosing.
4. Performance Analysis
4.1. Analysis of Electricity Consumption
4.2. Analysis of Memory Storage Space
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Tian, F.; Xue, H.; Fu, G.; Liu, G. SDN-based Privacy Protection Model for IoT Node Awareness. Int. J. Netw. Secur. 2024, 26, 840–850. [Google Scholar]
- Zhang, L. Support Verifiable IoT Perception Layer Information Search and Encryption Algorithms. Int. J. Netw. Secur. 2024, 26, 1053–1062. [Google Scholar]
- Luo, R.C.; Chen, O. Mobile Sensor Node Deployment and Asynchronous Power Management for Wireless Sensor Networks. IEEE Trans. Ind. Electron. 2012, 59, 2377–2385. [Google Scholar] [CrossRef]
- Zheng, K.; Fu, J.; Liu, X. Relay Selection and Deployment for NOMA-Enabled Multi-AAV-Assisted WSN. IEEE Sens. 2025, 25, 16235–16249. [Google Scholar] [CrossRef]
- Duan, H. DV-Hop Localization in Wireless Sensor Networks Based on Hybrid Firefly Particle Swarm Optimization. Int. J. Netw. Secur. 2025, 27, 35–45. [Google Scholar]
- Shen, Y. The Problem of Extreme Value Falling into Local Optimal Solution in Anomaly Detection in Wireless Sensor Networks. Int. J. Netw. Secur. 2025, 27, 323–329. [Google Scholar]
- Brante, G.; Kakitani, M.T.; Souza, R.D. Energy efficiency analysis of some cooperative and non-cooperative transmission schemes in wireless sensor networks. IEEE Trans. Commun. 2011, 59, 2671–2677. [Google Scholar] [CrossRef]
- Zhou, Z.; Zhou, S.; Cui, J.H.; Cui, S. Energy-efficient cooperative communication based on power control and selective single-relay in wireless sensor networks. IEEE Trans. Wirel. Commun. 2008, 7, 3066–3078. [Google Scholar] [CrossRef]
- Song, Z. Intrusion Detection Method for Wireless Sensor Network Based on Residual Convolutional Neural Networks Under Cloud Computing Environment and Its Application in Management. Int. J. Netw. Secur. 2025, 27, 510–519. [Google Scholar]
- Feng, T.H.; Shih, N.Y.; Hwang, M.S. Safety Relay Selection Algorithms Based On Fuzzy Relationship For Wireless Sensor Networks. J. Supercomput. 2018, 75, 4601–4616. [Google Scholar] [CrossRef]
- Feng, T.H.; Shih, N.Y.; Hwang, M.S. A Safety Review on Fuzzy-based Relay Selection in Wireless Sensor Networks. Int. J. Netw. Secur. 2015, 17, 712–721. [Google Scholar]
- Yang, W.; Cai, Y.; Xu, Y. An Energy-Aware Relay Selection Algorithm Based On Fuzzy Comprehensive Evaluation. In Proceedings of the International Conference of Networks Security, Wireless Communications and Trusted Computing, Wuhan, China, 25–26 April 2009; pp. 144–146. [Google Scholar]
- Brante, G.; Peron, G.d.S.; Souza, R.D.; Abrão, T. Distributed Fuzzy Logic-Based Relay Selection Algorithm for Cooperative Wireless Sensor Networks. IEEE Sens. 2013, 13, 4375–4386. [Google Scholar] [CrossRef]
- Mao, L.; Zhang, Y. Secure Localization Method in WSN Based on Improved MCL Algorithm. Int. J. Netw. Secur. 2024, 26, 740–750. [Google Scholar]
- Lu, Y.C.; Hwang, M.S. A Cryptographic Key Generation Scheme without a Trusted Third Party for Access Control in Multilevel Wireless Sensor Networks. Int. J. Netw. Secur. 2022, 24, 959–964. [Google Scholar]
- Li, W.T.; Feng, T.H.; Hwang, M.S. Distributed Detecting Node Replication Attacks in Wireless Sensor Networks: A Survey. Int. J. Netw. Secur. 2014, 16, 323–330. [Google Scholar]
- Madhavi, S.; Praveen, R.; Jagatheswari, S.; Nivitha, K. Hybrid ELECTRE and Bipolar Fuzzy PROMOTHEE-based Packet Dropping Malicious Node Mitigation Technique for Improving QoS in WSNs. Int. J. Commun. Syst. 2025, 38, e5974. [Google Scholar] [CrossRef]
- Glover, F.E.A. Genetic Algorithms and Tabu Search hybrids for optimization. Comput. Ops. Res. 1995, 22, 111–134. [Google Scholar] [CrossRef]
- Gao, Y.; Zhang, F. Multi-Copy Relay Node Selection Strategy Based on Reinforcement Learning. Sensors 2023, 23, 6131. [Google Scholar] [CrossRef] [PubMed]
- Yang, P.; Kuang, W.; Wang, S. Relay Selection for Dual-Hop Cooperative Ambient Backscatter Communication Systems. Sensors 2023, 23, 5791. [Google Scholar] [CrossRef] [PubMed]
- Liu, J.; Hao, Z.; Wang, J.; Zhang, X. Abnormal Traffic Detection Scheme Based on RBF Fuzzy Neural Network and Attention Mechanism in Robot Environment. Int. J. Netw. Secur. 2023, 25, 1018–1024. [Google Scholar]
- Yuan, Y.; Gu, Y.; Zhang, Z. Public Data Integrity Auditing Scheme Based on Fuzzy Identity for Cloud Storage System. Int. J. Netw. Secur. 2023, 25, 609–619. [Google Scholar]
- IEEE 802.15.4; IEEE Standard for Low-Rate Wireless Personal Area Networks (WPANs). IEEE: Piscataway, NJ, USA, 2015.


| Operational Unit | Power Consumption |
|---|---|
| Transmitter electronics () | 25 mA |
| Receiver electronics () | 27 mA |
| Cycle electronics () | 0.6 μA |
| Yang’s | Brante’s | Safety | |||
|---|---|---|---|---|---|
| Differentiate | Sorting | Randomly | Selection | ||
| Instruction | Complexity | Cycles | Method [12] | Method [7] | Mechanism |
| Random | O(n) | 4 | 1 × 4 = 4 | ||
| If … then | O(n) | 3 | 4 × 4 = 16 | ||
| Reading records | O(n) | 5 | 1 × 5 = 5 | 1 × 5 = 5 | 4 × 4 = 16 |
| Sorting records | O(n × log n) | 5 | 1 × 5 = 5 | 1 × 5 = 5 | 1 × 5 = 5 |
| Filtering records | O(n) | 4 | 1 × 4 = 4 | ||
| Deleted records | O(n) | 4 | 1 × 4 = 4 | ||
| Writing records | O(n) | 4 | 1 × 4 = 4 | 1 × 4 = 4 | 4 × 4 = 16 |
| Marked Records | O(n) | 3 | 1 × 3 = 3 | ||
| Removed marks | O(n) | 3 | 1 × 3 = 3 | ||
| Total | 14 | 18 | 67 | ||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, N.-I.; Feng, T.-H.; Hwang, M.-S. A Fuzzy-Based Relay Security Algorithm for Wireless Sensor Networks. Sensors 2025, 25, 4422. https://doi.org/10.3390/s25144422
Wu N-I, Feng T-H, Hwang M-S. A Fuzzy-Based Relay Security Algorithm for Wireless Sensor Networks. Sensors. 2025; 25(14):4422. https://doi.org/10.3390/s25144422
Chicago/Turabian StyleWu, Nan-I, Tung-Huang Feng, and Min-Shiang Hwang. 2025. "A Fuzzy-Based Relay Security Algorithm for Wireless Sensor Networks" Sensors 25, no. 14: 4422. https://doi.org/10.3390/s25144422
APA StyleWu, N.-I., Feng, T.-H., & Hwang, M.-S. (2025). A Fuzzy-Based Relay Security Algorithm for Wireless Sensor Networks. Sensors, 25(14), 4422. https://doi.org/10.3390/s25144422









