A Systematic Review on the Applications of Uppaal
Abstract
1. Introduction
- Presenting a systematic review of recent research works using Uppaal;
- Obtaining some quantitative information on the distribution of research papers regarding access options, scientific databases, types of papers, and geographical location;
- Analyzing the applicability and capabilities of different Uppaal versions supported by demonstrative case studies;
- Proposing practical guidelines for selecting the appropriate Uppaal version based on the application context;
- Identifying the current challenges and outlining potential future research directions and tool enhancements.
2. Background
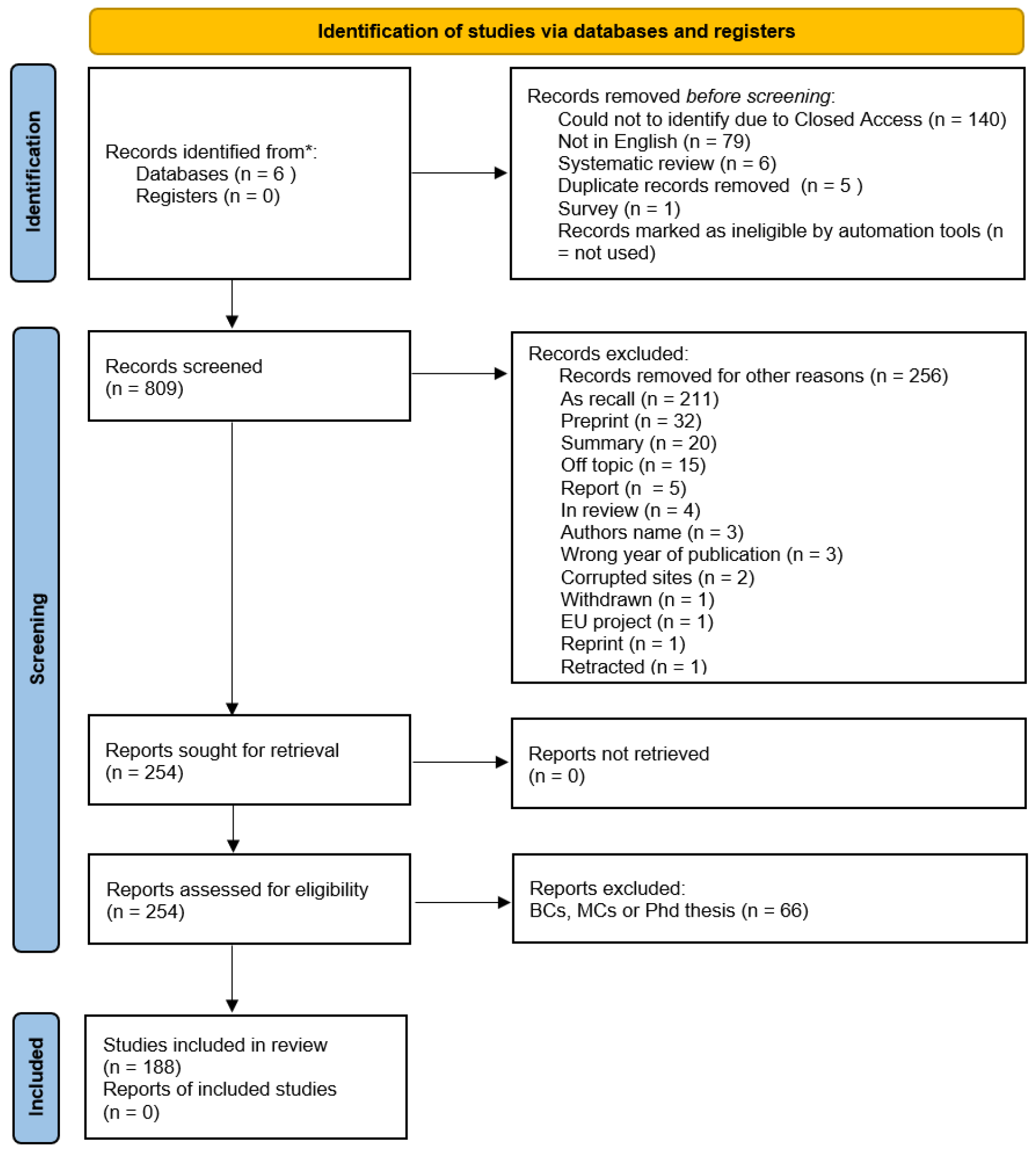
3. Research Methodology
3.1. Information Sources and Search Strategy
3.2. Research Questions
- RQ1:
- What are the application areas of the Uppaal tool?
- RQ2:
- Which version of Uppaal is used the most?
- RQ3:
- Which keywords appear the most often in the obtained papers?
- RQ4:
- What does the distribution of research papers regarding access options, scientific databases, and types of publication look like?
- RQ5:
- What does the distribution of research papers regarding geographical location look like?
3.3. Eligibility Criteria
- IC1: Papers published in 2022 and 2023.
- IC2: Research using Uppaal as the main tool.
- EC1: Papers not written in English.
- EC2: Review articles.
- EC3: Papers whose scope was to compare various tools.
- EC4: Papers that could not be evaluated due to very limited access.
3.4. Data Extraction, Storage and Analysis
4. Results
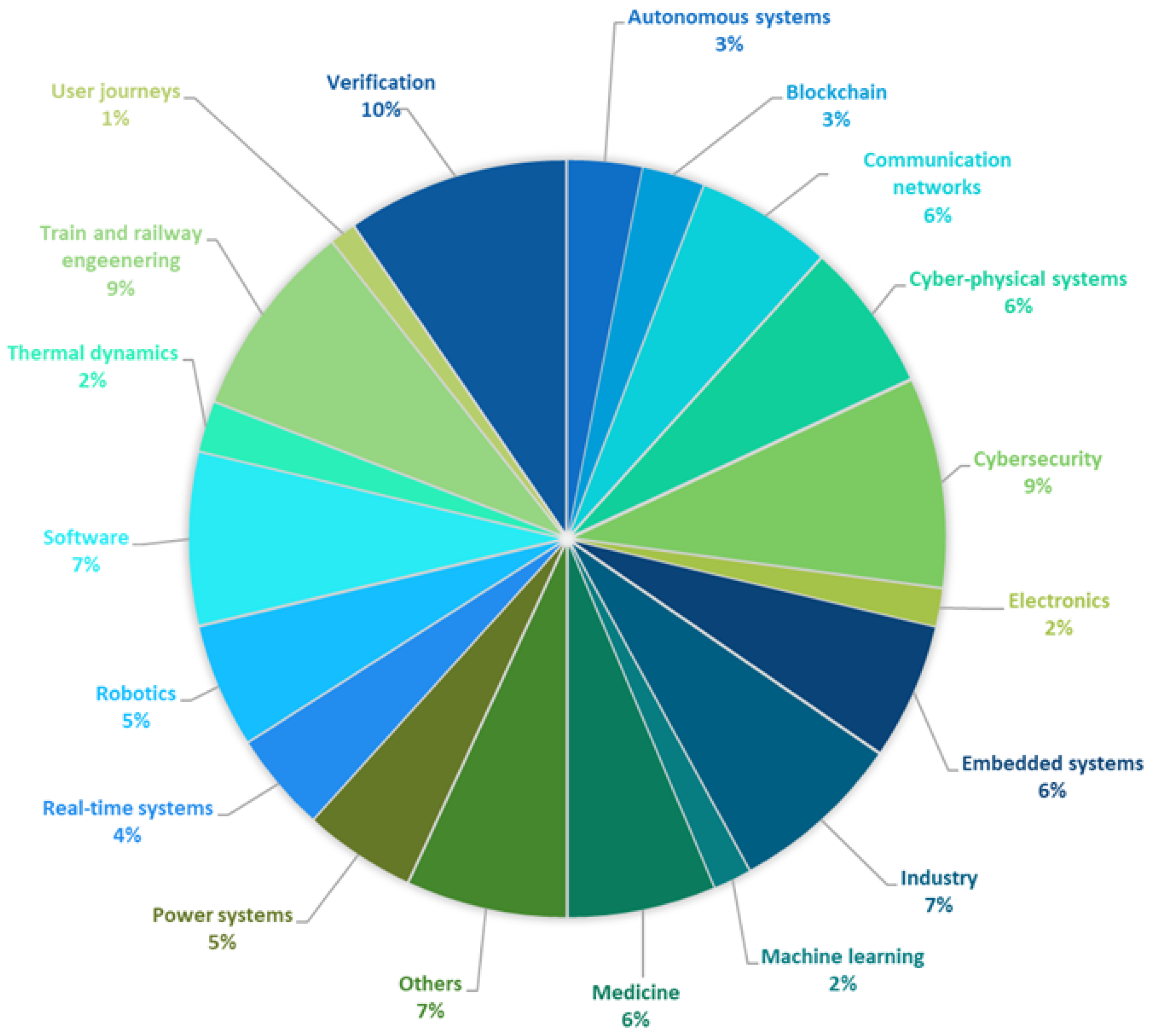
4.1. RQ1: What Are the Application Areas of the Uppaal Tool?
4.1.1. Autonomous Systems
4.1.2. Blockchain
4.1.3. Communication Networks
4.1.4. Cyber–Physical Systems
4.1.5. Cybersecurity
4.1.6. Electronics
4.1.7. Embedded Systems
4.1.8. Industry
4.1.9. Machine Learning
4.1.10. Medicine
4.1.11. Power Systems
4.1.12. Real-Time Systems
4.1.13. Robotics
4.1.14. Software
4.1.15. Thermal Dynamics
4.1.16. Train and Railway Engineering
4.1.17. User Journeys
4.1.18. Verification
4.1.19. Others
4.2. RQ2: Which Version of Uppaal Is Used the Most?
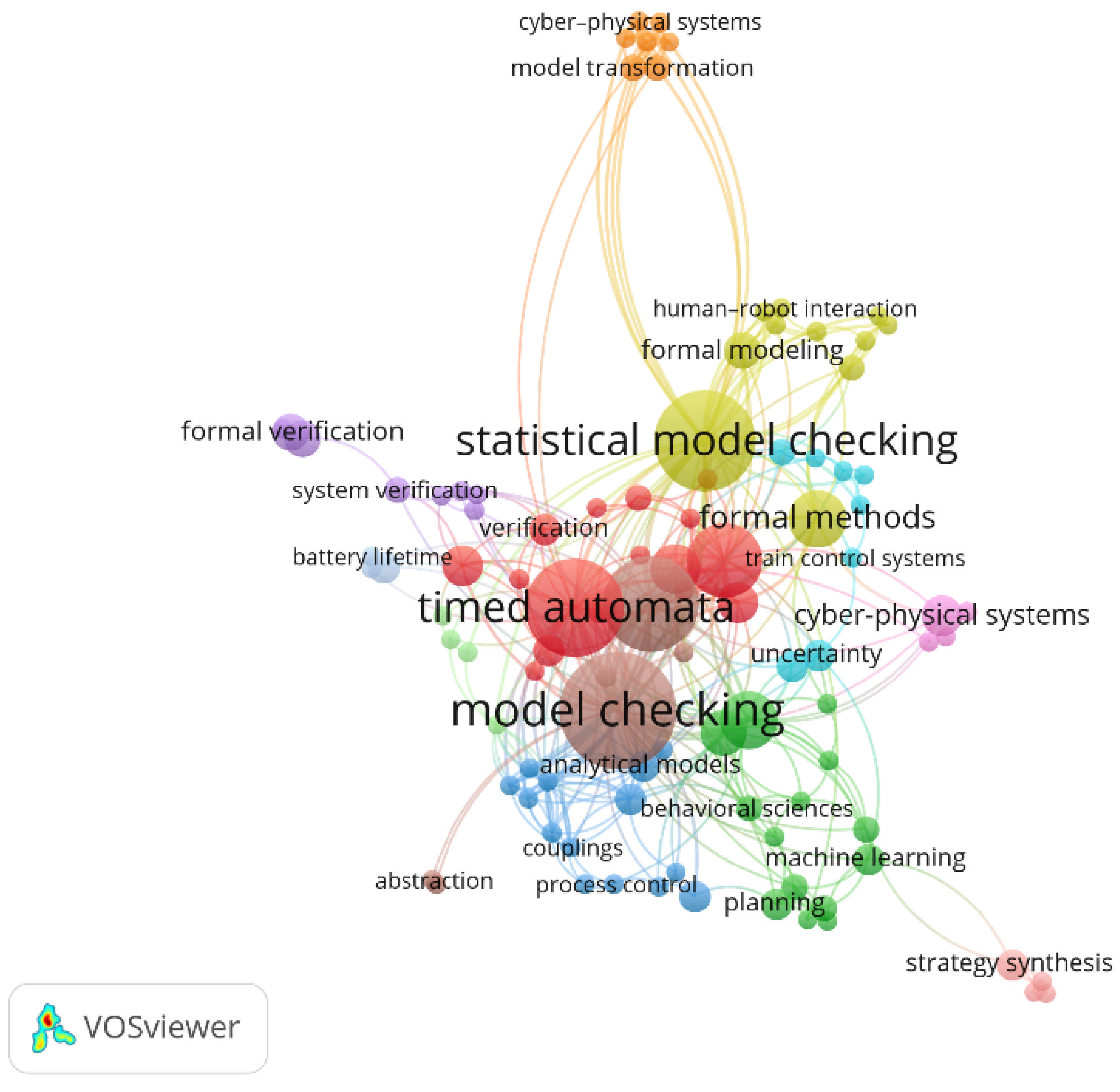
4.3. RQ3: Which Keywords Appear the Most Often in the Obtained Papers?
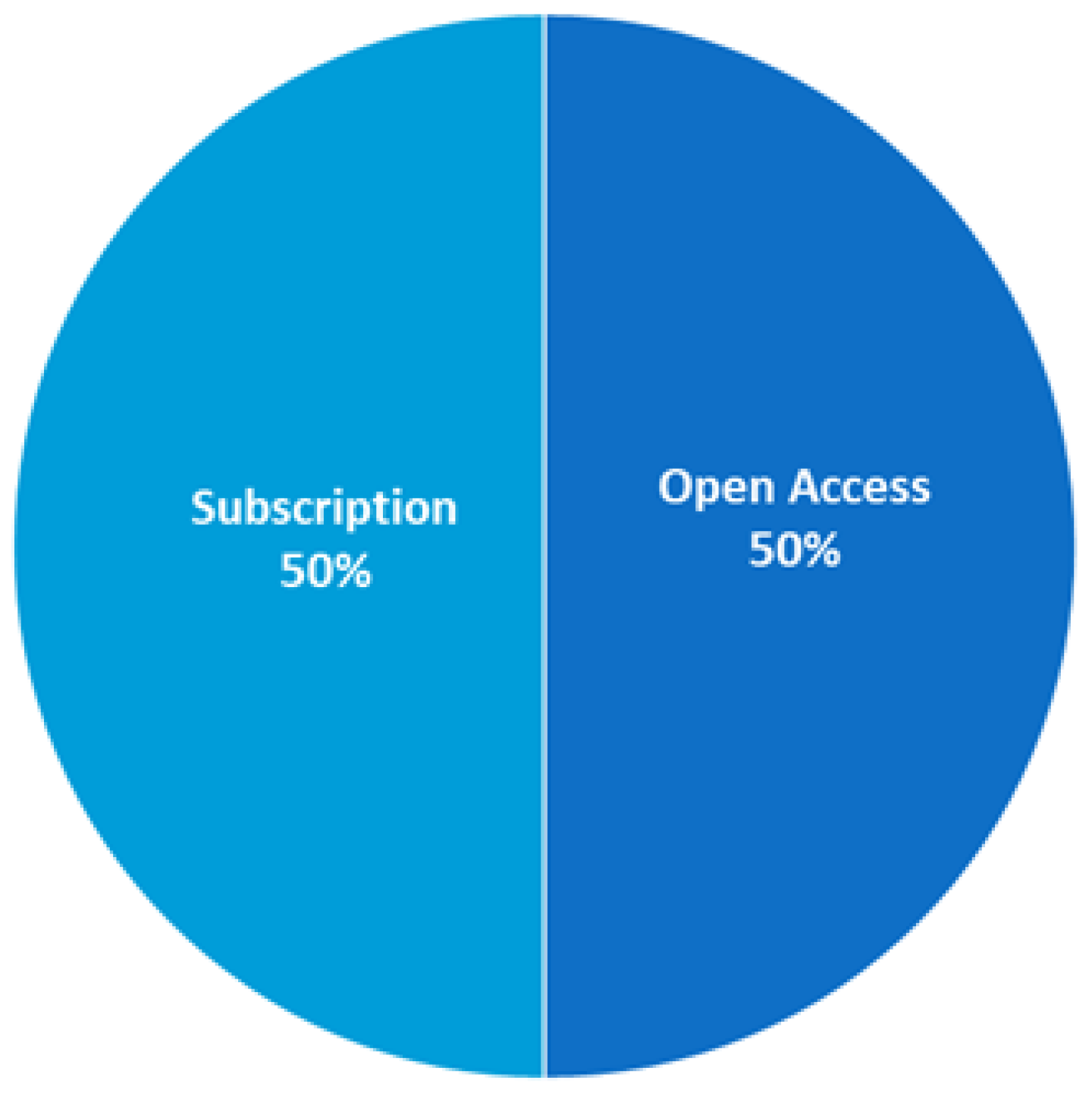
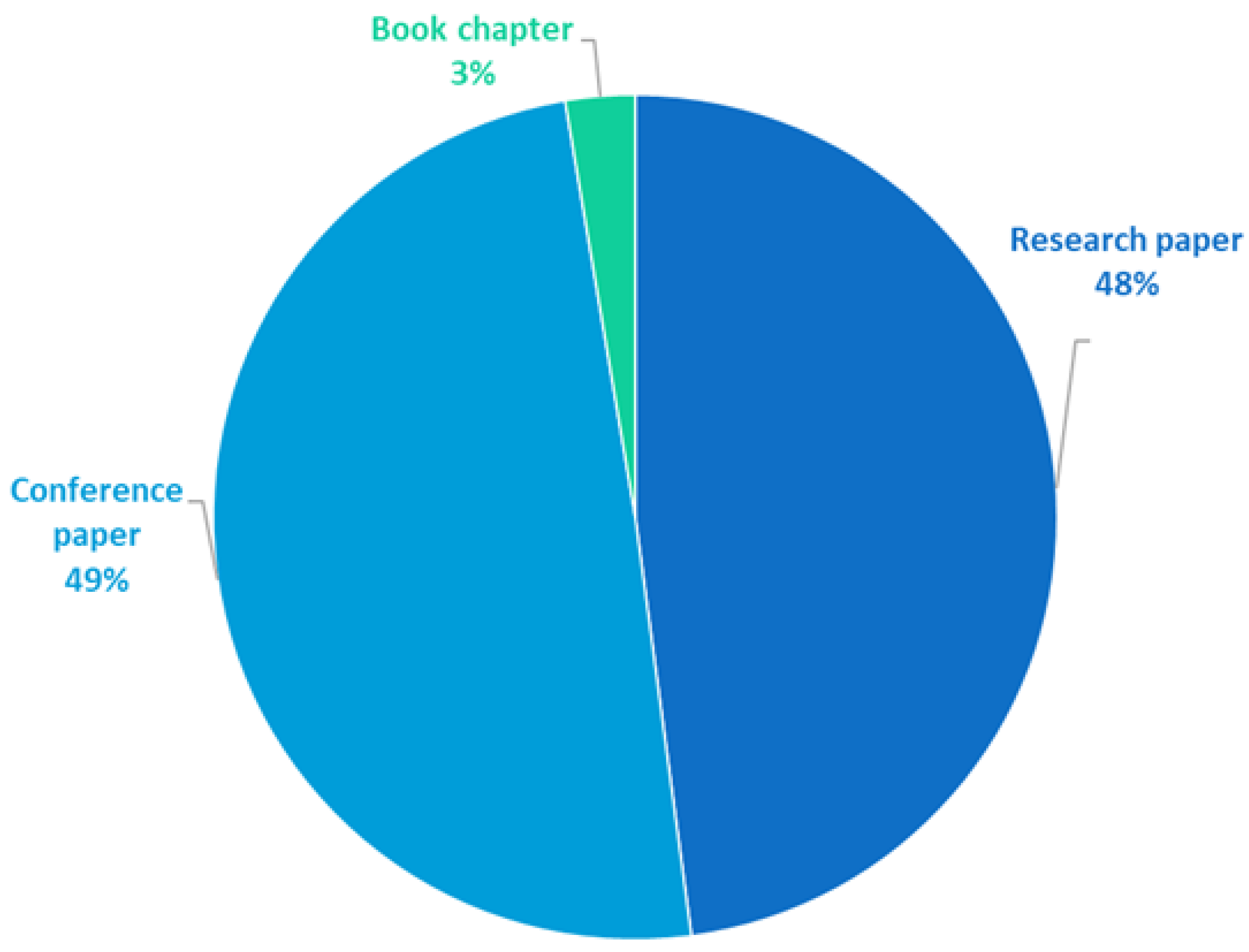
4.4. RQ4: What Does the Distribution of Research Papers Regarding Access Options, Scientific Databases, and Types of Publication Look Like?
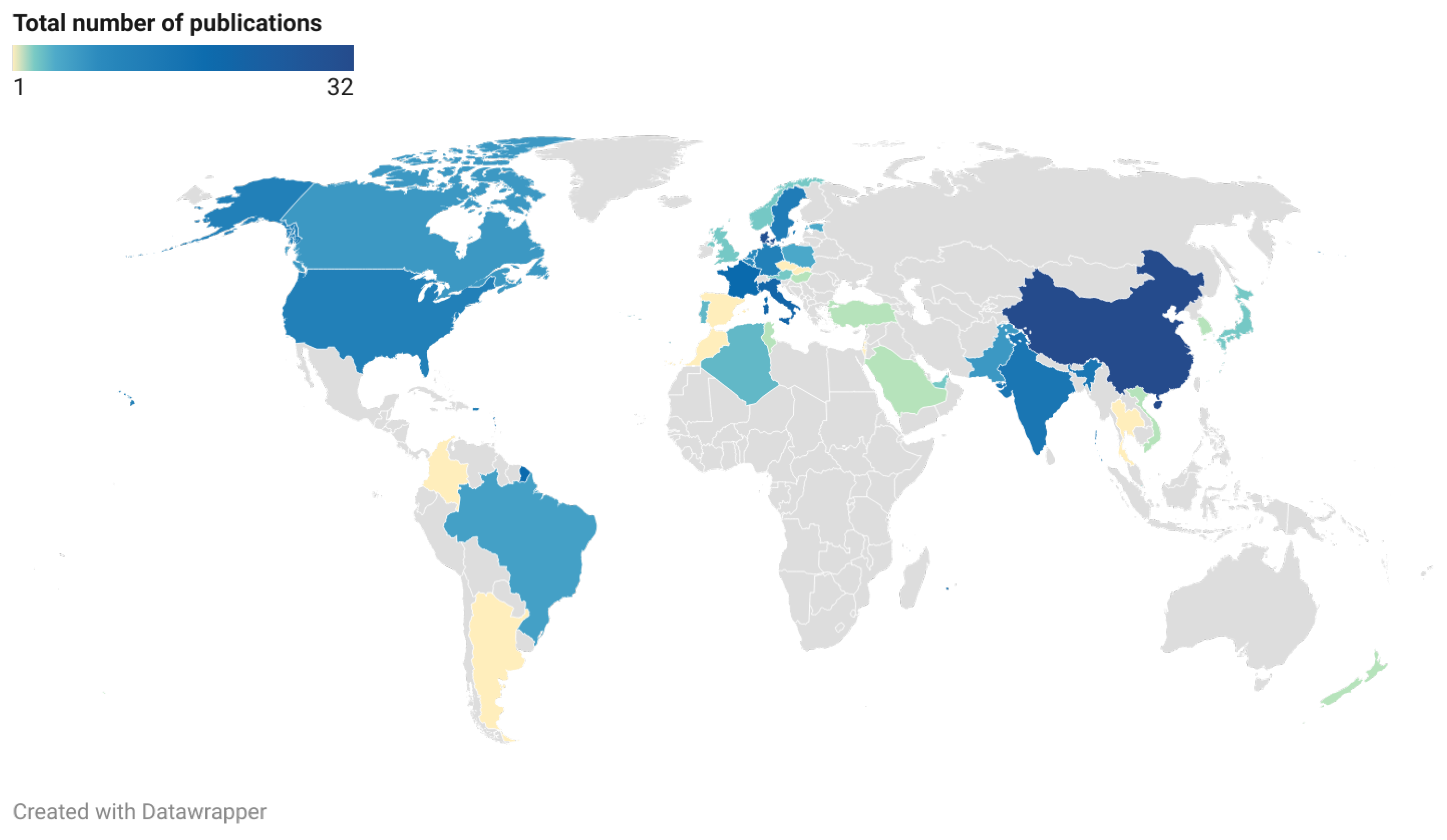
4.5. RQ5: What Does the Distribution of Research Papers Regarding Geographical Location Look Like?
5. Discussion
- Automatic and thorough verification (e.g., [74]).
5.1. A Brief Comparison with Other Mainstream Formal Validation Tools
5.2. Exploring the Applicability of Uppaal Versions
5.2.1. Classic Uppaal with Symbolic Model Checking
5.2.2. Uppaal SMC
5.2.3. Uppaal Stratego
5.2.4. Uppaal TIGA
5.2.5. Uppaal CORA
5.2.6. Guidelines for Selecting the Appropriate Uppaal Version
5.3. Open Challenges
- The authors of [28] point out a disadvantage of Uppaal SMC whereby it does not support a hierarchy of states. It is therefore necessary to construct separate templates for the parent-and-child hierarchy in the models used. Despite this fact, the authors still evaluate Uppaal SMC as a promising tool in estimating the probability of satisfying a user-specified performance query and requires much less checking time than traditional formal verification methods.
- The authors of [57] report that Uppaal Stratego solves limited types of objectives, leading it to make too strong assumptions about the problem.
- The authors of [115] point out that Uppaal SMC uses the Euler method for solving differential equations, known to be less accurate and entail larger performance overhead in comparison to analytical methods. Moreover, they note that the tool is not optimized for long-lasting simulations.
- The authors of [131] claim that Uppaal TIGA (1) cannot process parametric timed automata; (2) has no support for shared memory; and (3) requires each model to be consistent.
- The authors of [132] point out the following regarding Uppaal TIGA: (1) it can only calculate the infimum using symbolic methods; (2) its memory usage seems to be the limiting factor in applying the method to large-scale systems.
- The authors of [149] faced a problem with the machine power needed to validate the given requirements. Indeed, the verification was not completed due to the state-space problem (it crashed after 20 min on one machine, and after 4 h on the other).
- The authors of [150] indicate the following regardingUppaal: (1) it could provide a better user experience (according to chatbot developers); (2) its state machine nature limits the size of flows that can be modeled.
- The authors of [169] provide a wider discussion of Uppaal application in the railway domain. They highlight that due to the standardization of the railway process, it is challenging to determine "how to integrate tools and practices […] and how to adapt the overall workflow to accommodate innovation". Moreover, if Uppaal is meant to be introduced in current industrial processes as T2 tool (the T2 category is dedicated to tools where a fault could lead to an error in verification results), evidence should be provided by the vendors that the results produced by the tool are actually reliable, and that the tool has followed a documented process of development and maintenance. To the knowledge of the authors, this is currently lacking for Uppaal, and this could seriously hamper its adoption.
- The authors of [170] point out that railway engineers experienced some difficulties in evaluating the results; when Uppaal provided a counterexample, “it proved almost impossible […] to decipher where the error causing the requirement violation was”. The following solution to this problem is suggested: developing a backward mapping/annotating method to show the counterexample in the high-level model.
- The authors of [180] noted that system variables cannot change via external interactions with the environment, although some other model checkers enable it, but in these cases, the environment must also be modeled.
- The authors of [192] mention that the query language for requirement specification in Uppaal is less expressive than that of Timed Computation Tree Logic (TCTL), and thus, not every TCTL formula can be expressed in Uppaal. Moreover, they indicate some problems with (1) timed temporal operators; (2) the nesting of model operators; and (3) unavailability of the weak-until operator.
- The authors of [198] indicate that “the public, academic version […] is unable to exploit the computing potential of current shared-memory multi-core machines”.
- The authors of [207] state that a limitation in the area of clock synchronization algorithm verification is that Uppaal does not permit the reading of values of the clock variables.
5.4. Possible Solutions
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
References
- Woodcock, J.; Larsen, P.G.; Bicarregui, J.; Fitzgerald, J. Formal methods: Practice and experience. ACM Comput. Surv. 2009, 41. [Google Scholar] [CrossRef]
- Edmund, M.; Clarke, J.; Grumberg, O.; Peled, D.A. Model Checking; MIT Press: Cambridge, MA, USA, 1999; p. 314. [Google Scholar]
- Karmakar, R. Symbolic Model Checking: A Comprehensive Review for Critical System Design. In Proceedings of the Advances in Data and Information Sciences; Tiwari, S., Trivedi, M.C., Kolhe, M.L., Mishra, K., Singh, B.K., Eds.; Springer: Singapore, 2022; pp. 693–703. [Google Scholar]
- Legay, A.; Viswanathan, M. Statistical model checking: Challenges and perspectives. Int. J. Softw. Tools Technol. Transf. 2015, 17, 369–376. [Google Scholar] [CrossRef]
- Cimatti, A.; Clarke, E.; Giunchiglia, F.; Roveri, M. NuSMV: A new symbolic model checker. Int. J. Softw. Tools Technol. Transf. 2000, 2, 410–425. [Google Scholar] [CrossRef]
- Cavada, R.; Cimatti, A.; Dorigatti, M.; Griggio, A.; Mariotti, A.; Micheli, A.; Mover, S.; Roveri, M.; Tonetta, S. The nuXmv symbolic model checker. In Proceedings of the Computer Aided Verification: 26th International Conference, CAV 2014, Held as Part of the Vienna Summer of Logic, VSL 2014, Vienna, Austria, 18–22 July 2014; Proceedings 26. Springer: Berlin/Heidelberg, Germany, 2014; pp. 334–342. [Google Scholar]
- Holzmann, G.J. The model checker SPIN. IEEE Trans. Softw. Eng. 1997, 23, 279–295. [Google Scholar] [CrossRef]
- Kwiatkowska, M.; Norman, G.; Parker, D. PRISM: Probabilistic symbolic model checker. In Proceedings of the International Conference on Modelling Techniques and Tools for Computer Performance Evaluation, London, UK, 14–17 April 2002; Springer: Berlin/Heidelberg, Germany, 2002; pp. 200–204. [Google Scholar]
- Behrmann, G.; David, A.; Larsen, K.G. A tutorial on UPPAAL. In Formal Methods for the Design of Real-Time Systems; Springer: Berlin/Heidelberg, Germany, 2004; pp. 200–236. [Google Scholar]
- Henzinger, T.A.; Ho, P.H.; Wong-Toi, H. HyTech: A model checker for hybrid systems. In Proceedings of the Computer Aided Verification: 9th International Conference, CAV’97, Haifa, Israel, 22–25 June 1997; Proceedings 9. Springer: Berlin/Heidelberg, Germany, 1997; pp. 460–463. [Google Scholar]
- Younes, H.L. Ymer: A statistical model checker. In Proceedings of the International Conference on Computer Aided Verification, Edinburgh, UK, 6–10 July 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 429–433. [Google Scholar]
- Andrews, T.; Qadeer, S.; Rajamani, S.K.; Rehof, J.; Xie, Y. Zing: A model checker for concurrent software. In Proceedings of the Computer Aided Verification: 16th International Conference, CAV 2004, Boston, MA, USA, 13–17 July 2004; Proceedings 16. Springer: Berlin/Heidelberg, Germany, 2004; pp. 484–487. [Google Scholar]
- Shkarupylo, V.V.; Blinov, I.V.; Chemeris, A.A.; Dusheba, V.V.; Alsayaydeh, J.A.J. On Applicability of Model Checking Technique in Power Systems and Electric Power Industry. In Systems, Decision and Control in Energy III; Zaporozhets, A., Ed.; Springer International Publishing: Cham, Switzerland, 2022; pp. 3–21. [Google Scholar] [CrossRef]
- Castiglioni, V.; Lanotte, R.; Loreti, M.; Tini, S. Evaluating the Effectiveness of Digital Twins Through Statistical Model Checking with Feedback and Perturbations. In Proceedings of the Formal Methods for Industrial Critical Systems; Haxthausen, A.E., Serwe, W., Eds.; Springer: Cham, Switzerland, 2024; pp. 21–39. [Google Scholar]
- Alwhishi, G.; Bentahar, J.; Elwhishi, A.; Pedrycz, W.; Drawel, N. Multi-valued model checking IoT and intelligent systems with commitment protocols in multi-source data environments. Inf. Fusion 2024, 102, 102048. [Google Scholar] [CrossRef]
- Khan, N.; Nauman, M.; Almadhor, A.S.; Akhtar, N.; Alghuried, A.; Alhudhaif, A. Guaranteeing Correctness in Black-Box Machine Learning: A Fusion of Explainable AI and Formal Methods for Healthcare Decision-Making. IEEE Access 2024, 12, 90299–90316. [Google Scholar] [CrossRef]
- Zhou, W.; Zhao, Y.; Zhang, Y.; Wang, Y.; Yin, M. A comprehensive survey of UPPAAL-assisted formal modeling and verification. Softw. Pract. Exp. 2025, 55, 272–297. [Google Scholar] [CrossRef]
- David, A.; Larsen, K.G.; Legay, A.; Mikučionis, M.; Poulsen, D.B. Uppaal SMC tutorial. Int. J. Softw. Tools Technol. Transf. 2015, 17, 397–415. [Google Scholar] [CrossRef]
- David, A.; Jensen, P.G.; Larsen, K.G.; Mikučionis, M.; Taankvist, J.H. Uppaal stratego. In Proceedings of the Tools and Algorithms for the Construction and Analysis of Systems: 21st International Conference, TACAS 2015, Held as Part of the European Joint Conferences on Theory and Practice of Software, ETAPS 2015, London, UK, 11–18 April 2015; Proceedings 21. Springer: Berlin/Heidelberg, Germany, 2015; pp. 206–211. [Google Scholar]
- Behrmann, G.; Cougnard, A.; David, A.; Fleury, E.; Larsen, K.G.; Lime, D. UPPAAL TIGA User-Manual; Aalborg University: Aalborg, Denmark, 2007. [Google Scholar]
- Sarkis-Onofre, R.; Catalá-López, F.; Aromataris, E.; Lockwood, C. How to properly use the PRISMA Statement. Syst. Rev. 2021, 10, 1–3. [Google Scholar] [CrossRef]
- Guldstrand Larsen, K.; Lorber, F.; Nielsen, B. 20 Years of Real Real Time Model Validation. In Proceedings of the Formal Methods; Havelund, K., Peleska, J., Roscoe, B., de Vink, E., Eds.; Springer: Cham, Switzerland, 2018; pp. 22–36. [Google Scholar]
- Gu, R.; Enoiu, E. Model-Based Policy Synthesis and Test-Case Generation for Autonomous Systems. In Proceedings of the IEEE International Conference on Software Testing, Verification and Validation Workshops (ICSTW), Dublin, Ireland, 16–20 April 2023; pp. 18–27. [Google Scholar] [CrossRef]
- Huang, Z.; Li, B.; Du, D.; Li, Q. A Model Checking Based Approach to Detect Safety-Critical Adversarial Examples on Autonomous Driving Systems. In Proceedings of the International Colloquium on Theoretical Aspects of Computing; Springer: Berlin/Heidelberg, Germany, 2022; pp. 238–254. [Google Scholar]
- Hou, Z.; Wang, S.; Liu, H.; Yang, Y.; Zhang, Y. Twin Scenarios Establishment for Autonomous Vehicle Digital Twin Empowered SOTIF Assessment. IEEE Trans. Intell. Veh. 2023, 9, 1965–1976. [Google Scholar] [CrossRef]
- Wang, M.; Li, T.; Liu, J.; Dou, H.; Chen, H.; Zhang, J.; Zhang, L. Modeling and Verification of Autonomous Driving Systems under Stochastic Spatio-Temporal Constraints. In Proceedings of the International Conference on Software Engineering and Knowledge Engineering, Virtual, 1–10 July 2023; Available online: https://ksiresearch.org/seke/seke23paper/paper221.pdf (accessed on 28 May 2025).
- Wang, J.; Huang, Z.; Zhu, Y.; Shen, G. Statistical Model Checking for Stochastic and Hybrid Autonomous Driving Based on Spatio-Clock Constraints. Int. J. Softw. Eng. Knowl. Eng. 2022, 32, 553–582. [Google Scholar] [CrossRef]
- Liu, H.; Liu, J.; Sun, H.; Li, T.; Zhang, J. Uncertainty-Aware Behavior Modeling and Quantitative Safety Evaluation for Automatic Flight Control Systems. In Proceedings of the IEEE 22nd International Conference on Software Quality, Reliability and Security (QRS), Guangzhou, China, 5–9 December 2022; pp. 549–560. [Google Scholar] [CrossRef]
- Ganguly, R.; Xue, Y.; Jonckheere, A.; Ljung, P.; Schornstein, B.; Bonakdarpour, B.; Herlihy, M. Distributed runtime verification of metric temporal properties for cross-chain protocols. In Proceedings of the IEEE 42nd International Conference on Distributed Computing Systems (ICDCS), Bologna, Italy, 10–13 July 2022; IEEE: New York, NY, USA, 2022; pp. 23–33. [Google Scholar]
- Park, W.S.; Lee, H.; Choi, J.Y. Formal Modeling of Smart Contract-based Trading System. In Proceedings of the 24th International Conference on Advanced Communication Technology (ICACT), Pyeongchang, Republic of Korea, 13–16 February 2022; pp. 48–52. [Google Scholar] [CrossRef]
- Liu, Y.; Li, X.; Ma, Y. FGAC: A Fine-Grained Access Control Framework for Supply Chain Data Sharing. Systems 2022, 10, 208. [Google Scholar] [CrossRef]
- Hammami, M.A.; Lahami, M.; Maâlej, A.J. Towards a Dynamic Testing Approach for Checking the Correctness of Ethereum Smart Contracts. In Proceedings of the International Conference on Risks and Security of Internet and Systems, Sousse, Tunisia, 7–9 December 2022; Springer: Berlin/Heidelberg, Germany, 2022; pp. 85–100. [Google Scholar]
- Barati, M.; Adu-Duodu, K.; Rana, O.; Aujla, G.S.; Ranjan, R. Compliance checking of cloud providers: Design and implementation. Distrib. Ledger Technol. Res. Pract. 2023, 2, 1–20. [Google Scholar] [CrossRef]
- Kovalov, A.; Patil, G.; Bansal, V.; Gerndt, A. Model checking message delivery times in SpaceWire networks. In Proceedings of the 25th International Conference on Model Driven Engineering Languages and Systems: Companion Proceedings, Montreal, QC, Canada, 23–28 October 2022; pp. 267–275. [Google Scholar]
- Chen, N.; Zhu, H. IoT Modeling and Verification: From the CaIT Calculus to UPPAAL. IEICE Transations Inf. Syst. 2023, 106, 1507–1518. [Google Scholar] [CrossRef]
- V, G.L.; Pillai, A.S.; Raj, A. Modeling & Verification of an Adaptive IoT System using Uppaal. In Proceedings of the IEEE 3rd Global Conference for Advancement in Technology (GCAT), Bangalore, India, 7–9 October 2022; pp. 1–5. [Google Scholar] [CrossRef]
- Naeem, M.; Albano, M.; Magrin, D.; Nielsen, B.; Guldstrand, K. A Sigfox Module for the Network Simulator 3. In Proceedings of the Workshop on Ns-3, New York, NY, USA, 22–23 June 2022; WNS3 ’22. pp. 81–88. [Google Scholar] [CrossRef]
- Naeem, M.; Albano, M.; Larsen, K.G.; Nielsen, B.; Høedholt, A.; Laursen, C. Modelling and Analysis of a Sigfox-Based IoT Network Using uppaalsmc. IEEE Sens. J. 2023, 23, 10577–10587. [Google Scholar] [CrossRef]
- Jawad, A.; Newton, L.; Matrawy, A.; Jaskolka, J. A Formal Analysis of the Efficacy of Rebooting as a Countermeasure Against IoT Botnets. In Proceedings of the ICC-IEEE International Conference on Communications, Seoul, Republic of Korea, 16–20 May 2022; pp. 2206–2211. [Google Scholar] [CrossRef]
- Bezerra, W.R.; Martina, J.E.; Westphall, C.B. A Formal Verification of a Reputation Multi-Factor Authentication Mechanism for Constrained Devices and Low-Power Wide-Area Network Using Temporal Logic. Sensors 2023, 23, 6933. [Google Scholar] [CrossRef]
- Backeman, P.; Kunnappilly, A.; Seceleanu, C. Supporting 5G service orchestration with formal verification. Comput. Sci. Inf. Syst. 2023, 20, 329–357. [Google Scholar] [CrossRef]
- Roumane, A.; Kechar, B. A statistical model checking approach to analyse the random access protocol. Int. J. Wirel. Mob. Comput. 2022, 23, 338–349. [Google Scholar] [CrossRef]
- Asokan, S.; Kumar, G.S. Formal modeling of the gPTP clock synchronization algorithm in automotive ethernet. Innov. Syst. Softw. Eng. 2023, 19, 265–281. [Google Scholar] [CrossRef]
- de Moraes, R.M.; Sup, L.M.A.; Bauchspiess, A. TCP-Puerto-Londero: A New Approach for End-to-End Queue Length Control. J. Commun. Inf. Syst. 2023, 38, 105–114. [Google Scholar]
- Alshalalfah, A.L.; Mohamed, O.A.; Ouchani, S. A framework for modeling and analyzing cyber-physical systems using statistical model checking. Internet Things 2023, 22, 100732. [Google Scholar] [CrossRef]
- Kröger, J.; Fränzle, M. Updates at Runtime for Cyber Physical Systems. A Game Theoretic Approach. In Proceedings of the Software Engineering Workshops, Stuttgart, Germany, 19 February 2019; Gesellschaft für Informatik eV: Berlin, Germany, 2023. [Google Scholar]
- Anto, K.; Swain, A.; Roop, P. A novel framework for the design of resilient cyber-physical systems using control theory and formal methods. IEEE Access 2023, 11, 73556–73567. [Google Scholar] [CrossRef]
- Ghosh, P.; Karsai, G. Distributed Cyber Physical Systems Software Model Checking using Timed Automata. In Proceedings of the IEEE 26th International Symposium on Real-Time Distributed Computing (ISORC), Nashville, TN, USA, 23–25 May 2023; pp. 164–169. [Google Scholar] [CrossRef]
- Santos, A.A.; da Silva, A.F.; Pereira, F. Simulation of Cyber-Physical Intelligent Mechatronic Component Behavior Using Timed Automata Approach. In Proceedings of the International Conference Innovation in Engineering, Minho, Portugal, 28–30 June 2022; Springer: Berlin/Heidelberg, Germany, 2022; pp. 72–85. [Google Scholar]
- Hansen, S.T.; Thule, C.; Gomes, C.; van de Pol, J.; Palmieri, M.; Inci, E.O.; Madsen, F.; Alfonso, J.; Castellanos, J.A.; Rodriguez, J.M. Verification and synthesis of co-simulation algorithms subject to algebraic loops and adaptive steps. Int. J. Softw. Tools Technol. Transf. 2022, 24, 999–1024. [Google Scholar] [CrossRef]
- Miedema, L.; Grelck, C. Strategy Switching: Smart Fault-Tolerance for Weakly-Hard Resource-Constrained Real-Time Applications. In Proceedings of the International Conference on Software Engineering and Formal Methods, Berlin, Germany, 26–30 September 2022; Springer: Berlin/Heidelberg, Germany, 2022; pp. 129–145. [Google Scholar]
- Boudjadar, J.; Tomko, M. A Digital Twin Setup for Safety-aware Optimization of a Cyber-physical System. In Proceedings of the 19th International Conference on Informatics in Control, Automation and Robotics, Lisbon, Portugal, 14–16 July 2022; pp. 161–168. Available online: https://www.scitepress.org/Papers/2022/112721/112721.pdf (accessed on 28 May 2025).
- Delimpaltadakis, G.; de Albuquerque Gleizer, G.; Van Straalen, I.; Mazo, M., Jr. ETCetera: Beyond event-triggered control. In Proceedings of the 25th ACM International Conference on Hybrid Systems: Computation and Control, Milan, Italy, 4–6 May 2022; pp. 1–11. [Google Scholar]
- Lois, R.S.; Cole, D.G. Designing Secure and Resilient Cyber-Physical Systems Using Formal Models. In Proceedings of the 2022 Resilience Week (RWS), National Harbor, MD, USA, 26–29 September 2022; IEEE: New York, NY, USA, 2022; pp. 1–6. [Google Scholar]
- Ali, A.T.; Gruska, D. Dynamic attack trees methodology. In Proceedings of the Interdisciplinary Research in Technology and Management (IRTM); IEEE: New York, NY, USA, 2022; pp. 1–9. [Google Scholar]
- Ashraf, K.; Le Moullec, Y.; Pardy, T.; Rang, T. Design of Cyber Bio-analytical Physical Systems: Formal methods, architectures, and multi-system interaction strategies. Microprocess. Microsyst. 2023, 97, 104780. [Google Scholar] [CrossRef]
- Ballot, G.; Malvone, V.; Leneutre, J.; Borde, E. Reasoning about Moving Target Defense in Attack Modeling Formalisms. In Proceedings of the 9th ACM Workshop on Moving Target Defense, Los Angeles, CA, USA, 7 November 2022; pp. 55–65. [Google Scholar]
- AlQadheeb, A.; Bhattacharyya, S.; Perl, S. Enhancing cybersecurity by generating user-specific security policy through the formal modeling of user behavior. Array 2022, 14, 100146. [Google Scholar] [CrossRef]
- Sakata, K.; Fujita, S.; Sawada, K.; Iwasawa, H.; Endoh, H.; Matsumoto, N. Model verification of fallback control system under cyberattacks via UPPAAL. Adv. Robot. 2023, 37, 156–168. [Google Scholar] [CrossRef]
- Murthy, K.R.; Kumar, S.; Kumar Singh, M. Cyber Physical Systems (CPS) Security Verification Using Model Checking. In Recent Developments in Electronics and Communication Systems: Proceedings of the First International Conference on Recent Developments in Electronics and Communication Systems (RDECS-2022); IOS Press: Amsterdam, The Netherlands, 2023; Volume 32, p. 234. [Google Scholar]
- Hafeez, S.; Atif, M.; Naseer, M. Formal Specification and Verification of Distributed Denial of Service (DDoS). VAWKUM Trans. Comput. Sci. 2022, 10, 132–142. [Google Scholar] [CrossRef]
- Sakata, K.; Fujita, S.; Sawada, K. Model Verification of Resilient Third-Party Monitoring System Against Cyberattacks. In Proceedings of the 2022 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 7–9 January 2022; pp. 1–6. [Google Scholar] [CrossRef]
- Wang, Y.; Zhou, Q.; Zhang, Y.; Zhang, X.; Du, J. A formal modeling and verification scheme with an RNN-based attacker for CAN communication system Authenticity. Electronics 2022, 11, 1773. [Google Scholar] [CrossRef]
- Li, D.; Zhang, Q.; Zhao, D.; Li, L.; He, J.; Yuan, Y.; Zhao, Y. Hardware Trojan Detection Using Effective Property-Checking Method. Electronics 2022, 11, 2649. [Google Scholar] [CrossRef]
- Kumar, R.; Singh, S.; Narra, B.; Kela, R. Co-engineering Safety-Security Using Statistical Model Checking. In Proceedings of the International Conference on Formal Techniques for Distributed Objects, Components, and Systems, Lucca, Italy, 13–16 June 2022; Springer: Berlin/Heidelberg, Germany, 2022; pp. 88–92. [Google Scholar]
- Lanotte, R.; Merro, M.; Zannone, N. Impact Analysis of Coordinated Cyber-Physical Attacks via Statistical Model Checking: A Case Study. In Proceedings of the International Conference on Formal Techniques for Distributed Objects, Components, and Systems, Lisbon, Portugal, 19–23 June 2023; Springer: Berlin/Heidelberg, Germany, 2023; pp. 75–94. [Google Scholar]
- Kiviriga, A.; Larsen, K.G.; Nyman, U. Randomized reachability analysis in UPPAAL: Fast error detection in timed systems. Int. J. Softw. Tools Technol. Transf. 2022, 24, 1025–1042. [Google Scholar] [CrossRef]
- Cuartas, J.; Aranda, J.; Cordy, M.; Ortiz, J.; Perrouin, G.; Schobbens, P.Y. MUPPAAL: Reducing and Removing Equivalent and Duplicate Mutants in UPPAAL. In Proceedings of the IEEE International Conference on Software Testing, Verification and Validation Workshops (ICSTW), Dublin, Ireland, 16–20 April 2023; pp. 52–61. [Google Scholar] [CrossRef]
- Arora, S.; Hansen, R.R.; Larsen, K.G.; Legay, A.; Poulsen, D.B. Statistical model checking for probabilistic hyperproperties of real-valued signals. In Proceedings of the International Symposium on Model Checking Software; Springer: Berlin/Heidelberg, Germany, 2022; pp. 61–78. [Google Scholar]
- Oh, B.; Ahn, J.; Bae, S.; Son, M.; Lee, Y.; Kang, M.; Kim, Y. Preventing SIM Box Fraud Using Device Model Fingerprinting. In Proceedings of the NDSS Symposium, San Diego, CA, USA, 27 February–3 March 2023. [Google Scholar]
- Neupane, R.; Mehrpouyan, H. An ontology-based framework for formal verification of safety and security properties of control logics. In Proceedings of the 14th International Conference on Electronics, Computers and Artificial Intelligence (ECAI), Ploiesti, Romania, 30 June–1 July 2022; IEEE: New York, NY, USA, 2022; pp. 1–8. [Google Scholar]
- Campusano, M.; Hacks, S.; Kang, E. Towards model driven safety and security by design. In Proceedings of the International Workshops 10th QuASoQ 2022 & the 6th (SEED 2022) Co-Located with 29th APSEC22, Virtual, 6 December 2022; Series CEUR Workshop Proceedings. Volume 3330, pp. 34–41. [Google Scholar]
- Jamroga, W.; Kurpiewski, D.; Malvone, V. How to measure usable security: Natural strategies in voting protocols. J. Comput. Secur. 2022, 30, 381–409. [Google Scholar]
- Zhao, Y.; Shi, B.; Zhang, Q.; Yuan, Y.; He, J. Research on Cache Coherence Protocol Verification Method Based on Model Checking. Electronics 2023, 12, 3420. [Google Scholar] [CrossRef]
- Christensen, M.; Tzimpragos, G.; Kringen, H.; Volk, J.; Sherwood, T.; Hardekopf, B. PyLSE: A Pulse-Transfer Level Language for Superconductor Electronics. In Proceedings of the 43rd ACM SIGPLAN International Conference on Programming Language Design and Implementation, San Diego, CA, USA, 13–17 June 2022; PLDI 2022. pp. 671–686. [Google Scholar] [CrossRef]
- Beck, T.; Boniol, F.; Ermont, J.; Wartel, F.; Maillet, L. An automata-based method for interference analysis in multi-core processors. In Proceedings of the 15th Junior Researcher Workshop on Real-Time Computing (JRWRTC 2022)@ RTNS 2022, Paris, France, 7–8 June 2022; pp. 1–4. Available online: https://hal.science/hal-03857409/document (accessed on 28 May 2025).
- Ke, Y.; Xia, X. Timed Automaton-Based Quantitative Feasibility Analysis of Symmetric Cipher in Embedded RTOS: A Case Study of AES. Secur. Commun. Netw. 2022, 2022, 4118994. [Google Scholar]
- Scheipel, T.; Batista Ribeiro, L.; Sagaster, T.; Baunach, M. Smartos: An OS architecture for sustainable embedded systems. In Proceedings of the Tagungsband des FG-BS Frühjahrstreffens 2022; Gesellschaft für Informatik eV: Berlin, Germany, 2022; pp. 10–18420. [Google Scholar]
- Ribeiro, L.B.; Lorber, F.; Nyman, U.; Larsen, K.G.; Baunach, M. A Modeling Concept for Formal Verification of OS-Based Compositional Software. In Proceedings of the International Conference on Fundamental Approaches to Software Engineering, Paris, France, 22–27 April 2023; Springer: Cham, Switzerland, 2023; pp. 26–46. [Google Scholar]
- Yang, X.; Chen, X.; Wang, J. A Model Checking Based Software Requirements Specification Approach for Embedded Systems. In Proceedings of the IEEE 31st International Requirements Engineering Conference Workshops (REW), Hannover, Germany, 4–5 September 2023; IEEE: New York, NY, USA, 2023; pp. 184–191. [Google Scholar]
- Ding, G.; Liu, J. SysML Flow Model. In Proceedings of the 29th Asia-Pacific Software Engineering Conference (APSEC), Virtual, 6–9 December 2022; IEEE: New York, NY, USA, 2022; pp. 159–168. [Google Scholar]
- Jesus, V.S.d.; Lazarin, N.M.; Pantoja, C.E.; Manoel, F.C.P.B.; Alves, G.V.; Viterbo, J. A middleware for providing communicability to Embedded MAS based on the lack of connectivity. Artif. Intell. Rev. 2023, 3, 2971–3001. [Google Scholar] [CrossRef]
- Gu, R.; Jensen, P.G.; Seceleanu, C.; Enoiu, E.; Lundqvist, K. Correctness-guaranteed strategy synthesis and compression for multi-agent autonomous systems. Sci. Comput. Program. 2022, 224, 102894. [Google Scholar]
- Gu, R.; Jensen, P.G.; Poulsen, D.B.; Seceleanu, C.; Enoiu, E.; Lundqvist, K. Verifiable strategy synthesis for multiple autonomous agents: A scalable approach. Int. J. Softw. Tools Technol. Transf. 2022, 24, 395–414. [Google Scholar] [CrossRef]
- Jamroga, W.; Kim, Y. Practical Abstraction for Model Checking of Multi-Agent Systems. In Proceedings of the 20th International Conference on Principles of Knowledge Representation and Reasoning Main Track, Rhodes, Greece, 2–8 September 2023. [Google Scholar] [CrossRef]
- Yousaf, S.; Haque, H.M.U.; Atif, M.; Hashmi, M.A.; Khalid, A.; Vinh, P.C. A context-aware multi-agent reasoning based intelligent assistive formalism. Internet Things 2023, 23, 100857. [Google Scholar]
- Ribeiro, L.B.; Nagarajan, D.; Manjunath, V.; Ali Ahmad, M.T.; Baunach, M. Verifying Liveness and Real-Time of OS-Based Embedded Software. In Proceedings of the 25th Euromicro Conference on Digital System Design (DSD), Maspalomas, Spain, 31 August–2 September 2022; pp. 679–688. [Google Scholar] [CrossRef]
- Wang, J.; Wu, X.; Hou, G.; Li, P.; Gao, A.; Chen, Z.; Gao, H. Modeling and reliability verification of industrial control network protocol based on time state transition matrix. Int. J. Commun. Syst. 2022, 35, e5140. [Google Scholar] [CrossRef]
- Zhu, X. Collaborative modelling and simulation for manufacturing cost analysis. Int. J. Simul. Model. (IJSIMM) 2023, 22, 338–349. [Google Scholar] [CrossRef]
- Liu, S.; Gao, Z. Modeling and Verification of Intelligent Manufacturing Product Line System with Timed Automata. In Proceedings of the International Conference on Intelligent Manufacturing, Advanced Sensing and Big Data (IMASBD), Guilin, China, 22–24 July 2022; pp. 1–6. [Google Scholar] [CrossRef]
- Zhang, C.; Zhou, G.; Jing, Y.; Wang, R.; Chang, F. A digital twin-based automatic programming method for adaptive control of manufacturing cells. IEEE Access 2022, 10, 80784–80793. [Google Scholar]
- Ozkan, M.; Demirci, Z.; Aslan, Ö.; Yazıcı, A. Safety Verification of Multiple Industrial Robot Manipulators with Path Conflicts Using Model Checking. Machines 2023, 11, 282. [Google Scholar] [CrossRef]
- Himmiche, S.; Marangé, P.; Aubry, A.; Pétin, J.F. Robustness Evaluation Process for Scheduling under Uncertainties. Processes 2023, 11, 371. [Google Scholar] [CrossRef]
- Tahiri, I.; Philippot, A.; Carré-Ménétrier, V.; Tajer, A. A fault-tolerant and a reconfigurable control framework: Application to a real manufacturing system. Processes 2022, 10, 1266. [Google Scholar] [CrossRef]
- Siboulet, É.; Pottier, L.; Ranger, T.; Riera, B. Fresh Approaches for Structured Text Programmable Logic Controllers Programs Verification. Processes 2023, 11, 687. [Google Scholar] [CrossRef]
- Ukegbu, C.; Neupane, R.; Mehrpouyan, H. Ontology-Based Framework for Boundary Verification of Safety and Security Properties in Industrial Control Systems. In Proceedings of the 2023 European Interdisciplinary Cybersecurity Conference, Stavanger, Norway, 14–15 June 2023; EICC ’23. pp. 47–52. [Google Scholar] [CrossRef]
- Kumar, R.; Narra, B.; Kela, R.; Singh, S. AFMT: Maintaining the safety-security of industrial control systems. Comput. Ind. 2022, 136, 103584. [Google Scholar] [CrossRef]
- Larsson, J.; Enoiu, E.P. Test Generation and Mutation Analysis of Energy Consumption using UPPAAL SMC and MATS. In Proceedings of the IEEE International Conference on Software Testing, Verification and Validation Workshops (ICSTW), Dublin, Ireland, 16–20 April 2023; IEEE: New York, NY, USA, 2023; pp. 186–189. [Google Scholar]
- Jawad, A.; Jaskolka, J. Defense Models for Data Recovery in Industrial Control Systems. In Proceedings of the International Symposium on Foundations and Practice of Security, Ottawa, ON, Canada, 12–14 December 2022; Springer: Berlin/Heidelberg, Germany, 2022; pp. 271–286. Available online: https://link.springer.com/conference/fps (accessed on 28 May 2025).
- Kong, L.; Yang, Q.; Zhou, Q.; Xing, J.; Sun, X.; Zou, R. Embedding knowledge into BIM: A case study of extending BIM with firefighting plans. J. Build. Eng. 2022, 49, 103999. [Google Scholar] [CrossRef]
- Bakhshi, Z.; Rodriguez-Navas, G.; Hansson, H. Analyzing the performance of persistent storage for fault-tolerant stateful fog applications. J. Syst. Archit. 2023, 144, 103004. [Google Scholar] [CrossRef]
- Jensen, P.G.; Larsen, K.G.; Mikučionis, M. Playing Wordle with Uppaal Stratego. In A Journey from Process Algebra via Timed Automata to Model Learning: Essays Dedicated to Frits Vaandrager on the Occasion of His 60th Birthday; Springer: Berlin/Heidelberg, Germany, 2022; pp. 283–305. [Google Scholar]
- Dierl, S.; Howar, F.M.; Kauffman, S.; Kristjansen, M.; Guldstrand Larsen, K.; Lorber, F.; Mauritz, M. Learning Symbolic Timed Models from Concrete Timed Data. In Proceedings of the NASA Formal Methods Symposium, Houston, TX, USA, 16–18 May 2023; Springer: Berlin/Heidelberg, Germany, 2023; pp. 104–121. [Google Scholar]
- Quin, F.; Weyns, D.; Gheibi, O. Reducing large adaptation spaces in self-adaptive systems using classical machine learning. J. Syst. Softw. 2022, 190, 111341. [Google Scholar]
- Parveen, R.; Goveas, N. Transforming Medical Resource Utilization Process to Verifiable Timed Automata Models in Cyber-Physical Systems. In Proceedings of the International Conference on Distributed Computing and Internet Technology, Bhubaneswar, India, 19–23 January 2022; Springer: Berlin/Heidelberg, Germany, 2022; pp. 111–126. [Google Scholar]
- Baranov, E.; Bowles, J.; Given-Wilson, T.; Legay, A.; Webber, T. A Secure User-Centred Healthcare System: Design and Verification. In Proceedings of the 10th International Symposium: From Data to Models and Back, Virtual Event, 6–7 December 2021; pp. 44–60. [Google Scholar]
- Fayad, M.; Mostefaoui, A.; Chouali, S.; Benbernou, S. Toward a design model-oriented methodology to ensure QoS of a cyber-physical healthcare system. Computing 2022, 104, 1615–1641. [Google Scholar] [CrossRef]
- Baird, A.; Pinisetty, S.; Allen, N.; Patel, N.; Roop, P. Runtime Verification for Clinically Interpretable Arrhythmia Classification. In Proceedings of the 20th ACM-IEEE International Conference on Formal Methods and Models for System Design (MEMOCODE), Shanghai, China, 13–14 October 2022; IEEE: New York, NY, USA, 2022; pp. 1–10. [Google Scholar]
- Elleuch, M.; Tahar, S. Formal Analysis of an IoT-Based Healthcare Application. In Proceedings of the 2023 IEEE Symposium on Computers and Communications (ISCC), Gammarth, Tunisia, 9–12 July 2023; pp. 1–5. [Google Scholar] [CrossRef]
- Newaz, A.I.; Aris, A.; Sikder, A.K.; Uluagac, A.S. Systematic Threat Analysis of Modern Unified Healthcare Communication Systems. In Proceedings of the GLOBECOM-IEEE Global Communications Conference, Rio de Janeiro, Brazil, 4–8 December 2022; pp. 1404–1410. [Google Scholar] [CrossRef]
- Arfi, F.; Courbis, A.L.; Lambolais, T.; Bughin, F.; Hayot, M. Formal verification of a telerehabilitation system through an abstraction and refinement approach using Uppaal. IET Softw. 2023, 17, 582–599. [Google Scholar] [CrossRef]
- Nawaz, A.; Hasan, O.; Jabeen, S. Formal Verification of Deep Brain Stimulation Controllers for Parkinson’s Disease Treatment. Neural Comput. 2023, 35, 671–698. [Google Scholar] [CrossRef] [PubMed]
- Fernandes, H.R.; Gomes, G.F.; de Oliveira, A.C.P.; Campos, S.V.A. Stochastic Formal Model of PI3K/mTOR Pathway in Alzheimer’s Disease for Drug Repurposing: An Evaluation of Rapamycin, LY294002, and NVP-BEZ235. Sci. Comput. Program. 2023, 232, 103028. [Google Scholar] [CrossRef]
- Bilgram, A.; Jensen, P.G.; Jørgensen, K.Y.; Larsen, K.G.; Mikučionis, M.; Muñiz, M.; Poulsen, D.B.; Taankvist, P. An investigation of safe and near-optimal strategies for prevention of Covid-19 exposure using stochastic hybrid models and machine learning. Decis. Anal. J. 2022, 5, 100141. [Google Scholar] [CrossRef]
- Cuartas, J.; Cortés, D.; Betancourt, J.S.; Aranda, J.; García, J.I.; Valencia, A.M.; Ortiz, J. Formal Verification of a Mechanical Ventilator using UPPAAL. In Proceedings of the International Workshop on Formal Techniques for Safety-Critical Systems, Caltais, Portugal, 22 October 2023. [Google Scholar]
- Heuer, J.; Krenz-Bååth, R.; Obermaisser, R. Verifying Bio-Electronic Systems. In Proceedings of the 26th International Symposium on Design and Diagnostics of Electronic Circuits and Systems (DDECS), Tallinn, Estonia, 3–5 May 2023; IEEE: New York, NY, USA, 2023; pp. 161–166. [Google Scholar]
- Novak, M.; Grobelna, I.; Nyman, U.; Szczesniak, P.; Blaabjerg, F. Statistical Performance Verification of the FS-MPC Algorithm Applied to the Matrix Converter. In Proceedings of the International Power Electronics Conference (IPEC-Himeji 2022-ECCE Asia), Himeji, Japan, 15–19 May 2022; IEEE: New York, NY, USA, 2022; pp. 76–82. [Google Scholar]
- Mansour, A.N.A.; Grillo, S.; Ragaini, E.; Rossi, M. A Formal Approach to the Verification of Protection Systems in Low-Voltage Distribution Grids. In Proceedings of the IEEE/ACM 11th International Conference on Formal Methods in Software Engineering (FormaliSE), Melbourne, Australia, 14–15 May 2023; pp. 120–129. [Google Scholar] [CrossRef]
- Wei, L.; Miao, W.; Zeng, Z. Collaborative Modeling Power Smart IoT Entity Services based on Extended Timed Automata. In Proceedings of the EMIE The 2nd International Conference on Electronic Materials and Information Engineering, Hangzhou, China, 15–17 April 2022; pp. 1–5. [Google Scholar]
- Hmidi, Z.; Kahloul, L.; Benharzallah, S. A new Mobility and Energy Harvesting aware Medium Access Control (MEH-MAC) protocol: Modelling and performance evaluation. Ad Hoc Netw. 2023, 142, 103108. [Google Scholar] [CrossRef]
- Kristjansen, M.; Kulkarni, A.; Jensen, P.G.; Teodorescu, R.; Larsen, K.G. Dual Balancing of SoC/SoT in Smart Batteries using Reinforcement Learning in Uppaal Stratego. In Proceedings of the Annual Conference of the IEEE Industrial Electronics Society (IECON), Singapore, 16–19 October 2023. [Google Scholar]
- Soltani, R.; Volk, M.; Diamonte, L.; Lopuhaä-Zwakenberg, M.; Stoelinga, M. Optimal Spare Management via Statistical Model Checking: A Case Study in Research Reactors. In Proceedings of the International Conference on Formal Methods for Industrial Critical Systems, Antwerp, Belgium, 20–22 September 2023; Springer: Berlin/Heidelberg, Germany, 2023; pp. 205–223. [Google Scholar]
- Nagy, A.; Mansour, A.; Grillo, S.; Ragaini, E.; Rossi, M. Rigorous Automated Verification of Protection Systems in LV Distribution Grids. In Proceedings of the 2023 IEEE International Conference on Environment and Electrical Engineering and 2023 IEEE Industrial and Commercial Power Systems Europe (EEEIC/I&CPS Europe), Madrid, Spain, 6–9 June 2023; IEEE: New York, NY, USA, 2023; pp. 1–6. [Google Scholar]
- Hansen, J.; Larsen, K.G.; Cuijpers, P.J. Balancing Flexible Production and Consumption of Energy using Resource Timed Automata. In Proceedings of the 11th Mediterranean Conference on Embedded Computing (MECO), Budva, Montenegro, 7–10 June 2022; IEEE: New York, NY, USA, 2022; pp. 1–6. [Google Scholar]
- Novak, M.; Grobelna, I.; Nyman, U.M.; Szczesniak, P.; Blaabjerg, F. Modular Modeling and Statistical Validation for Grid-Connected FS-MPC-Controlled Matrix Converters. IEEE Trans. Ind. Electron. 2022, 70, 8613–8623. [Google Scholar] [CrossRef]
- Thilakasiri, T.; Becker, M. An Exact Schedulability Analysis for Global Fixed-Priority Scheduling of the AER Task Model. In Proceedings of the 28th Asia and South Pacific Design Automation Conference, Tokyo, Japan, 16–19 January 2023; pp. 326–332. [Google Scholar]
- Foughali, M.; Hladik, P.E.; Zuepke, A. Compositional Verification of Embedded Real-Time Systems. J. Syst. Archit. 2023, 142, 102928. [Google Scholar] [CrossRef]
- Zavatteri, M.; Rizzi, R.; Villa, T. Dynamic controllability of temporal networks with instantaneous reaction. Inf. Sci. 2022, 613, 932–952. [Google Scholar] [CrossRef]
- Xu, W.; Wu, X.; Zhao, Y.; Li, Y. Formal Verification and Analysis of Time-Sensitive Software-Defined Network Architecture. In Proceedings of the International Conference on Software Engineering and Knowledge Engineering, Virtual, 1–10 July 2022; pp. 369–375. Available online: https://ksiresearchorg.ipage.com/seke/seke22paper/paper094.pdf (accessed on 28 May 2025).
- An, D.; Pan, Z.; Gao, X.; Li, S.; Yin, L.; Li, T. stohMCharts: A Modeling Framework for Quantitative Performance Evaluation of Cyber-Physical-Social Systems. IEEE Access 2023, 11, 44660–44671. [Google Scholar] [CrossRef]
- Basile, D.; Beek, M.H.t.; Lazreg, S.; Cordy, M.; Legay, A. Static detection of equivalent mutants in real-time model-based mutation testing: An Empirical Evaluation. Empir. Softw. Eng. 2022, 27, 160. [Google Scholar] [CrossRef]
- Goorden, M.A.; Larsen, K.G.; Nielsen, J.E.; Nielsen, T.D.; Qian, W.; Rasmussen, M.R.; Zhao, G. Guaranteed safe controller synthesis for switched systems using analytical solutions. In Proceedings of the IEEE Conference on Control Technology and Applications (CCTA), Bridgetown, Barbados, 22 September 2023; pp. 784–790. [Google Scholar]
- Cornanguer, L.; Largouët, C.; Rozé, L.; Termier, A. TAG: Learning timed automata from logs. In Proceedings of the AAAI Conference on Artificial Intelligence, Virtual, 22 February–1 March 2022; Volume 36, pp. 3949–3958. Available online: https://ojs.aaai.org/index.php/AAAI/article/view/20311 (accessed on 28 May 2025).
- Lestingi, L.; Sbrolli, C.; Scarmozzino, P.; Romeo, G.; Bersani, M.M.; Rossi, M. Formal modeling and verification of multi-robot interactive scenarios in service settings. In Proceedings of the IEEE/ACM 10th International Conference on Formal Methods in Software Engineering, Pittsburgh, PA, USA, 18–22 May 2022; pp. 80–90. [Google Scholar]
- Lestingi, L.; Zerla, D.; Bersani, M.M.; Rossi, M. Specification, stochastic modeling and analysis of interactive service robotic applications. Robot. Auton. Syst. 2023, 163, 104387. [Google Scholar] [CrossRef]
- Foughali, M.; Zuepke, A. Formal verification of real-time autonomous robots: An interdisciplinary approach. Front. Robot. AI 2022, 9, 791757. [Google Scholar] [CrossRef] [PubMed]
- Bøgh, S.; Jensen, P.G.; Kristjansen, M.; Larsen, K.G.; Nyman, U. Distributed Fleet Management in Noisy Environments via Model-Predictive Control. In Proceedings of the International Conference on Automated Planning and Scheduling, Virtual, 13–24 June 2022; Volume 32, pp. 565–573. Available online: https://ojs.aaai.org/index.php/ICAPS/article/view/19843 (accessed on 28 May 2025).
- Praveen, A.T.; Gupta, A.; Bhattacharyya, S.; Muthalagu, R. Assuring Behavior of Multirobot Autonomous Systems With Translation From Formal Verification to ROS Simulation. IEEE Syst. J. 2022, 16, 5092–5100. [Google Scholar] [CrossRef]
- Lestingi, L.; Manglaviti, A.; Marinaro, D.; Marinello, L.; Askarpour, M.; Bersani, M.M.; Rossi, M. Analyzing the impact of human errors on interactive service robotic scenarios via formal verification. Softw. Syst. Model. 2023, 2, 473–502. [Google Scholar] [CrossRef]
- Dust, L.; Gu, R.; Seceleanu, C.; Ekström, M.; Mubeen, S. Pattern-Based Verification of ROS 2 Nodes Using UPPAAL. In Proceedings of the International Conference on Formal Methods for Industrial Critical Systems, Antwerp, Belgium, 20–22 September 2023; pp. 57–75. [Google Scholar]
- Lestingi, L.; Bersani, M.M.; Rossi, M. Model-Driven Development of Service Robot Applications Dealing With Uncertain Human Behavior. IEEE Intell. Syst. 2022, 37, 48–56. [Google Scholar] [CrossRef]
- Bersani, M.M.; Camilli, M.; Lestingi, L.; Mirandola, R.; Rossi, M.; Scandurra, P. Architecting Explainable Service Robots. In Proceedings of the European Conference on Software Architecture, Istanbul, Turkey, 18–22 September 2023; pp. 153–169. [Google Scholar] [CrossRef]
- Wang, W.; Schuppe, G.F.; Tumova, J. Decentralized Multi-agent Coordination under MITL Specifications and Communication Constraints. In Proceedings of the 31st Mediterranean Conference on Control and Automation (MED), Limassol, Cyprus, 26–29 June 2023; pp. 842–849. [Google Scholar]
- Li, R.; Yin, J.; Zhu, H.; Vinh, P.C. Verification of rabbitmq with kerberos using timed automata. Mob. Netw. Appl. 2022, 27, 2049–2067. [Google Scholar] [CrossRef]
- Wongsitthiphaithun, N.; Vatanawood, W. Transforming YAWL Workflows with Time Interval Constraints into Timed Automata. In Proceedings of the 19th International Joint Conference on Computer Science and Software Engineering (JCSSE), Bangkok, Thailand, 22–25 June 2022; pp. 1–6. [Google Scholar]
- Saadi, A.; Hammal, Y.; Oussalah, M.C. Automata-Based Approach to Manage Self-Adaptive Component-Based Architectures. Int. J. Softw. Innov. (IJSI) 2022, 10, 1–22. [Google Scholar] [CrossRef]
- Basile, D.; ter Beek, M.H. A runtime environment for contract automata. In Proceedings of the International Symposium on Formal Methods, Lübeck, Germany, 6–10 March 2023; pp. 550–567. [Google Scholar]
- Han, D.; Cai, Y.; Chen, W.; Cui, Z.; Li, A. Timed-SAS: Modeling and Analyzing the Time Behaviors of Self-Adaptive Software under Uncertainty. Appl. Sci. 2023, 13, 2018. [Google Scholar] [CrossRef]
- Atif, M.; Naseer, M.; Khan, A.S. Formal Analysis of Distributed Shared Memory Algorithms. UMT Artif. Intell. Rev. 2022, 2, 22–32. [Google Scholar] [CrossRef]
- Silva, G.R.S.; Rodrigues, G.N.; Canedo, E.D. A Modeling Strategy for the Verification of Context-Oriented Chatbot Conversational Flows via Model Checking. J. Univers. Comput. Sci. 2023, 29, 805. [Google Scholar] [CrossRef]
- Mishra, K.C.; Dutta, S. Colluder detection in SaaS cloud applications with subscription based license. Multimed. Tools Appl. 2023, 82, 12135–12149. [Google Scholar] [CrossRef]
- Goorden, M.A.; Jensen, P.G.; Larsen, K.G.; Samusev, M.; Srba, J.; Zhao, G. STOMPC: Stochastic Model-Predictive Control with Uppaal Stratego. In Proceedings of the International Symposium on Automated Technology for Verification and Analysis, Virtual Event, 25–28 October 2022; Springer: Berlin/Heidelberg, Germany, 2022; pp. 327–333. [Google Scholar]
- Kim, E.H.; Larsen, K.G.; Goorden, M.A.; Nielsen, T.D. Controlling Stormwater Detention Ponds under Partial Observability. J. Log. Algebr. Methods Program 2024, 141, 100979. [Google Scholar] [CrossRef]
- Weyns, D.; Gheibi, O.; Quin, F.; Van Der Donckt, J. Deep Learning for Effective and Efficient Reduction of Large Adaptation Spaces in Self-Adaptive Systems. ACM Trans. Auton. Adapt. Syst. 2022, 17, 1–12. [Google Scholar] [CrossRef]
- Göttmann, H.; Caesar, B.; Beers, L.; Lochau, M.; Schürr, A.; Fay, A. Precomputing Reconfiguration Strategies Based on Stochastic Timed Game Automata. In Proceedings of the 25th International Conference on Model Driven Engineering Languages and Systems, Montreal, QC, Canada, 23–28 October 2022; MODELS ’22. pp. 31–42. [Google Scholar] [CrossRef]
- Weyns, D.; Iftikhar, U.M. ActivFORMS: A formally founded model-based approach to engineer self-adaptive systems. ACM Trans. Softw. Eng. Methodol. 2023, 32, 1–48. [Google Scholar] [CrossRef]
- Fatima, K.; Sultana, S.; Abbasi, J.A.; Khalid, M.T. The Modeling and Verification of Trainify:(Tennis App). Int. J. Emerg. Multidiscip. Comput. Sci. Artif. Intell. 2022, 1, 26–34. [Google Scholar] [CrossRef]
- Hasrat, I.R.; Jensen, P.G.; Larsen, K.G.; Srba, J. End-to-end heat-pump control using continuous time stochastic modelling and Uppaal Stratego. In Proceedings of the International Symposium on Theoretical Aspects of Software Engineering, Cluj-Napoca, Romania, 8–10 July 2022; Springer: Berlin/Heidelberg, Germany, 2022; pp. 363–380. [Google Scholar]
- Albano, M.; Cibin, N.; Golmohamadi, H.; Skou, A. Probabilistic Flexoffers in residential heat pumps considering uncertain weather forecast. Energy Inform. 2022, 5, 1–19. [Google Scholar] [CrossRef]
- Hasrat, I.R.; Jensen, P.G.; Larsen, K.G.; Srba, J. A toolchain for domestic heat-pump control using Uppaal Stratego. Sci. Comput. Program. 2023, 230, 102987. [Google Scholar] [CrossRef]
- Cibin, N.; Tibo, A.; Golmohamadi, H.; Skou, A.; Albano, M. Machine learning-based algorithms to estimate thermal dynamics of residential buildings with energy flexibility. J. Build. Eng. 2023, 65, 105683. [Google Scholar] [CrossRef]
- Yang, Z.; Yuan, L.; Liu, Y. A scheme for train communication information management in onboard-centered train control system. In Proceedings of the International Conference on Frontiers of Traffic and Transportation Engineering (FTTE), Lanzhou, China, 17–19 June 2022; SPIE: Bellingham, WA, USA, 2022; Volume 12340, pp. 69–75. [Google Scholar]
- Naumann, B.; Jakobs, C.; Werner, M. Formal analysis of timeliness in the RaSTA protocol. In Proceedings of the 17th Conference on Computer Science and Intelligence Systems (FedCSIS), Sofia, Bulgaria, 4–7 September 2022; IEEE: New York, NY, USA, 2022; pp. 505–514. [Google Scholar]
- Sassi, I.; Ghazel, M.; El-Koursi, E.M. Statistical Model Checking for On-board Train Integrity Safety and Performance Analysis. In Proceedings of the European Conference on Safety and Reliability (ESREL), Dublin, Ireland, 28 August–1 September 2022; 8p. [Google Scholar]
- Lukács, G.; Bartha, T. Practical UML subset for railway engineers to support formal modeling. Trans. Motauto World 2022, 7, 56–59. [Google Scholar]
- Niu, R.; You, S. Research on run-time risk evaluation method based on operating scenario data for autonomous train. Accid. Anal. Prev. 2022, 178, 106855. [Google Scholar] [CrossRef]
- Lin, J.; Min, X. Quantitative safety analysis of train control system based on statistical model checking. Arch. Transp. 2022, 61. [Google Scholar]
- Kochan, A.; Daszczuk, W.B.; Grabski, W.; Karolak, J. Formal Verification of the European Train Control System (ETCS) for Better Energy Efficiency Using a Timed and Asynchronous Model. Energies 2023, 16, 3602. [Google Scholar] [CrossRef]
- Basile, D.; ter Beek, M.H.; Ferrari, A.; Legay, A. Exploring the ERTMS/ETCS full moving block specification: An experience with formal methods. Int. J. Softw. Tools Technol. Transf. 2022, 24, 351–370. [Google Scholar] [CrossRef]
- Lukács, G.; Bartha, T. Formal modeling and verification of the functionality of electronic urban railway control systems through a case study. Urban Rail Transit 2022, 8, 217–245. [Google Scholar] [CrossRef]
- Himrane, O.; Beugin, J.; Ghazel, M. Implementation of a Model-Oriented Approach for Supporting Safe Integration of GNSS-Based Virtual Balises in ERTMS/ETCS Level 3. IEEE Open J. Intell. Transp. Syst. 2023, 4, 294–310. [Google Scholar] [CrossRef]
- Lin, J.; Min, X.; Chai, J. Model-Based Safety Analysis of Movement Authority Scenario in TcCBTC system. In Proceedings of the Journal of Physics: Conference Series; IOP Publishing: Bristol, UK, 2022; Volume 2246, p. 012077. [Google Scholar]
- Saddem-Yagoubi, R.; Sanwal, M.U.; Libutti, S.; Benerecetti, M.; Beugin, J.; Flammini, F.; Ghazel, M.; Janssen, B.; Marrone, S.; Mogavero, F.; et al. Toward Usable Formal Models for Safety and Performance Evaluation of ERTMS/ETCS Level 3: The PERFORMINGRAIL Project. In Proceedings of the 32nd European Safety and Reliability Conference, Dublin, Ireland, 28 August–1 September 2022; 8pAvailable online: https://swepub.kb.se/bib/swepub:oai:DiVA.org:mdh-69010?tab2=abs&language=en (accessed on 28 May 2025).
- Wang, Z.; Liu, J.; Yi, L.; Wang, G. Fire Linkage Scheme Design and Modeling Verification of Urban Rail Transit. In Proceedings of the 5th International Conference on Artificial Intelligence and Big Data (ICAIBD), Chengdu, China, 27–30 May 2022; pp. 648–652. [Google Scholar] [CrossRef]
- Proença, J.; Borrami, S.; Sanchez de Nova, J.; Pereira, D.; Nandi, G.S. Verification of multiple models of a safety-critical motor controller in railway systems. In Proceedings of the International Conference on Reliability, Safety, and Security of Railway Systems, Paris, France, 1 June 2022; Springer: Berlin/Heidelberg, Germany, 2022; pp. 83–94. [Google Scholar]
- Seisenberger, M.; ter Beek, M.H.; Fan, X.; Ferrari, A.; Haxthausen, A.E.; James, P.; Lawrence, A.; Luttik, B.; van de Pol, J.; Wimmer, S. Safe and secure future AI-driven railway technologies: Challenges for formal methods in railway. In Proceedings of the International Symposium on Leveraging Applications of Formal Methods, Rhodes, Greece, 22–30 October 2022; Springer: Berlin/Heidelberg, Germany, 2022; pp. 246–268. [Google Scholar]
- Fantechi, A.; Gnesi, S.; Gori, G. Future train control systems: Challenges for dependability assessment. In Proceedings of the International Symposium on Leveraging Applications of Formal Methods, Rhodes, Greece, 22–30 October 2022; Springer: Berlin/Heidelberg, Germany, 2022; pp. 269–285. [Google Scholar]
- Kobialka, P.; Tapia Tarifa, S.L.; Bergersen, G.R.; Johnsen, E.B. Weighted games for user journeys. In Proceedings of the International Conference on Software Engineering and Formal Methods, Aveiro, Portugal, 26–30 September 2022; Springer: Berlin/Heidelberg, Germany, 2022; pp. 253–270. [Google Scholar]
- Kobialka, P.; Mannhardt, F.; Tapia Tarifa, S.L.; Johnsen, E.B. Building User Journey Games from Multi-party Event Logs. In Proceedings of the International Conference on Process Mining, Bolzano, Italy, 3 November 2022; Springer: Berlin/Heidelberg, Germany, 2022; pp. 71–83. [Google Scholar]
- Yasmine, A.; Ameur-Boulifa, R.; Guitton-Ouhamou, P.; Pacalet, R. Automatic Support for Requirements Validation. In Proceedings of the 11th Embedded Real-Time Systems Congress (ERTS’2022), Toulouse, France, 1–2 June 2022; Available online: https://telecom-paris.hal.science/hal-03689243v1/document (accessed on 28 May 2025).
- Bendík, J.; Sencan, A.; Gol, E.A.; Černá, I. Timed automata robustness analysis via model checking. Log. Methods Comput. Sci. 2022, 18. [Google Scholar] [CrossRef]
- Alam, M.T.; Halder, R.; Maiti, A. Formal Verification of Pub-Sub Blockchain Interoperability Protocol using Stochastic Timed Automata. Front. Blockchain 2023, 6, 1248962. [Google Scholar] [CrossRef]
- Bouyer, P.; Gastin, P.; Herbreteau, F.; Sankur, O.; Srivathsan, B. Zone-based verification of timed automata: Extrapolations, simulations and what next? In Proceedings of the International Conference on Formal Modeling and Analysis of Timed Systems, Warsaw, Poland, 13–15 September 2022; Springer: Berlin/Heidelberg, Germany, 2022; pp. 16–42. [Google Scholar]
- Cortellessa, V.; Pomante, L.; Stoico, V. From UML/MARTE Specifications to ESL HW/SW Co-Design: Early Functional Verification and Timing Validation. In Proceedings of the Companion of the ACM/SPEC International Conference on Performance Engineering, Coimbra, Portugal, 15–19 April 2023; pp. 373–380. [Google Scholar]
- Guin, J.; Vain, J.; Tsiopoulos, L.; Valdek, G. Temporal Multi-View Contracts Help Developing Efficient Test Models. Balt. J. Mod. Comput. 2022, 10, 710–737. Available online: https://www.bjmc.lu.lv/fileadmin/user_upload/lu_portal/projekti/bjmc/Contents/10_4_07_Guin.pdf (accessed on 28 May 2025). [CrossRef]
- Mahajan, A.; Martin, S.; Watt, S.J.; Wong, M.W.H.M. Compliance through model checking. In Proceedings of the International Workshop on AI Compliance Mechanism WAICOM, Saarbrücken, Germany, 14 December 2022; Available online: https://ink.library.smu.edu.sg/cclaw/3/ (accessed on 28 May 2025).
- Tiwari, S.; Iyer, K.; Enoiu, E.P. Combining Model-Based Testing and Automated Analysis of Behavioural Models using GraphWalker and UPPAAL. In Proceedings of the 29th Asia-Pacific Software Engineering Conference (APSEC), Tokyo, Japan, 6–9 December 2022; IEEE: New York, NY, USA, 2022; pp. 452–456. Available online: https://ieeexplore.ieee.org/abstract/document/10043283 (accessed on 28 May 2025).
- Lehmann, S.; Schupp, S. Bounded DBM-based clock state construction for timed automata in Uppaal. Int. J. Softw. Tools Technol. Transf. 2023, 25, 19–47. [Google Scholar] [CrossRef]
- Chen, H.; Su, Y.; Zhang, M.; Liu, Z.; Mi, J. Learning Assumptions for Compositional Verification of Timed Automata. In Proceedings of the International Conference on Computer Aided Verification, Paris, France, 17–22 July 2023; Springer: Berlin/Heidelberg, Germany, 2023; pp. 40–61. [Google Scholar]
- Jensen, P.G.; Kiviriga, A.; Guldstrand Larsen, K.; Nyman, U.; Mijačika, A.; Høiriis Mortensen, J. Monte Carlo Tree Search for Priced Timed Automata. In Proceedings of the International Conference on Quantitative Evaluation of Systems, Warsaw, Poland, 13–16 September 2022; Springer: Berlin/Heidelberg, Germany, 2022; pp. 381–398. [Google Scholar]
- Larsen, K.G.; Legay, A.; Mikučionis, M.; Poulsen, D.B. Importance splitting in uppaal. In Proceedings of the International Symposium on Leveraging Applications of Formal Methods, Rhodes, Greece, 22–30 October 2022; Springer: Berlin/Heidelberg, Germany, 2022; pp. 433–447. [Google Scholar]
- Vogel, T.; Carwehl, M.; Rodrigues, G.N.; Grunske, L. A property specification pattern catalog for real-time system verification with UPPAAL. Inf. Softw. Technol. 2023, 154, 107100. [Google Scholar] [CrossRef]
- Vain, J.; Tsiopoulos, L.; Kanter, G. Provably correct aspect-oriented modeling with UPPAAL timed automata. In System Assurances; Elsevier: Amsterdam, The Netherlands, 2022; pp. 447–476. [Google Scholar]
- Guin, J.; Vain, J.; Tsiopoulos, L.; Valdek, G. Temporal multi-view contracts for efficient test models. In Proceedings of the International Baltic Conference on Digital Business and Intelligent Systems, Vilnius, Lithuania, 30 June 2024; Springer: Berlin/Heidelberg, Germany, 2022; pp. 136–151. [Google Scholar]
- Johri, P.; Anand, A.; Vain, J.; Singh, J.; Quasim, M.T. System Assurances: Modeling and Management; Academic Press: Cambridge, MA, USA, 2022. [Google Scholar]
- Tigane, S.; Guerrouf, F.; Hamani, N.; Kahloul, L.; Khalgui, M.; Ali, M.A. Dynamic timed automata for reconfigurable system modeling and verification. Axioms 2023, 12, 230. [Google Scholar] [CrossRef]
- Melchert, S.B.J. Spreadsheet-based Configuration of Families of Real-Time Specifications. TiCSA, 2023; submitted to workshop. Available online: https://arxiv.org/abs/2310.20395 (accessed on 28 May 2025).
- Cicirelli, F.; Nigro, L. Analyzing stochastic reward nets by model checking and parallel simulation. Simul. Model. Pract. Theory 2022, 116, 102467. [Google Scholar] [CrossRef]
- Peres, F.; Ghazel, M. A proven translation from a UML state machine subset to timed automata. ACM Trans. Embed. Comput. Syst. 2023, 23, 1–33. [Google Scholar] [CrossRef]
- Zaman, M.; Atif, M.; Naseer, M. Formal Verification of Twin Clutch Gear Control. VAWKUM Trans. Comput. Sci. 2022, 10, 24–33. [Google Scholar] [CrossRef]
- Kitahara, Y.; Nakamura, M.; Sakakibara, K. An Investigation of Formal Verification of Control Policy of Multi-Car Elevator Systems Using Statistical Model Checking. In Proceedings of the International Conference on Machine Learning and Cybernetics (ICMLC), Tokyo, Japan, 9–11 September 2022; pp. 118–193. Available online: https://ieeexplore.ieee.org/document/9941319 (accessed on 28 May 2025).
- Palliwar, A.; Pinisetty, S. Using gossip enabled distributed circuit breaking for improving resiliency of distributed systems. In Proceedings of the IEEE 19th International Conference on Software Architecture (ICSA), Honolulu, HI, USA, 12–15 March 2022; IEEE: New York, NY, USA, 2022; pp. 13–23. [Google Scholar]
- Palliwar, A.; Pinisetty, S. Artifact for Measuring the Relative Efficacy of Gossip Enabled Distributed Circuit Breaking. In Proceedings of the 2022 IEEE 19th International Conference on Software Architecture Companion (ICSA-C), Honolulu, HI, USA, 12–15 March 2022; p. 55. [Google Scholar] [CrossRef]
- Daszczuk, W.B. Modeling and Verification of Asynchronous Systems Using Timed Integrated Model of Distributed Systems. Sensors 2022, 22, 1157. [Google Scholar] [CrossRef]
- Li, S.; Yang, Q.; Xing, J.; Chen, W.; Zou, R. A Foundation Model for Building Digital Twins: A Case Study of a Chiller. Buildings 2022, 12, 1079. [Google Scholar] [CrossRef]
- Zhang, M.; Teng, Y.; Kong, H.; Baugh, J.; Su, Y.; Mi, J.; Du, B. Automatic modelling and verification of Autosar architectures. J. Syst. Softw. 2023, 201, 111675. [Google Scholar] [CrossRef]
- Asokan, S.; Kochaleema, K.; Kumar, G.S. Formal Modelling and Verification of the Clock Synchronisation Algorithm of FlexRay. Def. Sci. J. 2023, 73, 41–50. [Google Scholar] [CrossRef]
- Bersani, M.M.; Camilli, M.; Lestingi, L.; Mirandola, R.; Rossi, M. Explainable human-machine teaming using model checking and interpretable machine learning. In Proceedings of the IEEE/ACM 11th International Conference on Formal Methods in Software Engineering (FormaliSE), Melbourne, Australia, 14–15 May 2023; IEEE: New York, NY, USA, 2023; pp. 18–28. [Google Scholar]
- Wang, X.; Guo, Y.; Lu, N.; He, P. UAV Cluster Behavior Modeling Based on Spatial-Temporal Hybrid Petri Net. Appl. Sci. 2023, 13, 762. [Google Scholar] [CrossRef]
- Cuijpers, P.J.; Hansen, J.; Larsen, K.G. Assume-Guarantee Reasoning for Additive Hybrid Behaviour. In Theories of Programming and Formal Methods: Essays Dedicated to Jifeng He on the Occasion of His 80th Birthday; Springer: Berlin/Heidelberg, Germany, 2023; pp. 297–322. [Google Scholar] [CrossRef]
- Batteux, M.; Prosvirnova, T.; Rauzy, A. A guided tour of AltaRica wizard, the AltaRica 3.0 integrated modeling environment. In Proceedings of the 32nd European Safety and Reliability Conference (ESREL 2022), Dublin, Ireland, 28 August–1 September 2022; pp. 2246–2253. Available online: https://www.rpsonline.com.sg/proceedings/esrel2022/html/copy.html (accessed on 28 May 2025).
- André, É.; Liu, S.; Liu, Y.; Choppy, C.; Sun, J.; Dong, J.S. Formalizing UML state machines for automated verification–A survey. ACM Comput. Surv. 2023, 55, 1–47. [Google Scholar] [CrossRef]



| Domain | Research Papers |
|---|---|
| Autonomous systems | [23,24,25,26,27,28] |
| Blockchain | [29,30,31,32,33] |
| Communication networks | [34,35,36,37,38,39,40,41,42,43,44] |
| Cyber–physical systems | [45,46,47,48,49,50,51,52,53,54,55,56] |
| Cybersecurity | [57,58,59,60,61,62,63,64,65,66,67,68,69,70,71,72,73] |
| Electronics | [74,75,76] |
| Embedded systems | [77,78,79,80,81,82,83,84,85,86,87] |
| Industry | [88,89,90,91,92,93,94,95,96,97,98,99,100,101] |
| Machine learning | [102,103,104] |
| Medicine | [105,106,107,108,109,110,111,112,113,114,115,116] |
| Power systems | [117,118,119,120,121,122,123,124,125] |
| Real-time systems | [126,127,128,129,130,131,132,133] |
| Robotics | [134,135,136,137,138,139,140,141,142,143] |
| Software | [144,145,146,147,148,149,150,151,152,153,154,155,156,157] |
| Thermal dynamics | [158,159,160,161] |
| Train and railway engineering | [162,163,164,165,166,167,168,169,170,171,172,173,174,175,176,177] |
| User journeys | [178,179] |
| Verification | [180,181,182,183,184,185,186,187,188,189,190,191,192,193,194,195,196,197] |
| Use Case/Domain | Recommended Version | Key Features Needed | Notes |
|---|---|---|---|
| Formal verification of real-time systems | Classic | Timed automata, reachability analysis, exhaustive model checking, safety and liveness properties | Ideal for protocol verification, embedded systems, and communication systems |
| Systems with stochastic behavior or uncertainty | SMC | Statistical model checking, probability evaluation, simulation | Suitable for energy-aware systems, battery analysis, and performance evaluation under uncertainty |
| Adaptive control in smart systems; resource-aware decision-making; energy-aware scheduling | Stratego | Strategy synthesis, cost optimization, machine learning integration | Suitable for systems requiring optimal and adaptable strategies; leverages reinforcement learning to improve control performance |
| Adversarial control; planning under uncertainty | TIGA | Timed game automata, strategy synthesis, controller generation | Useful in scheduling, autonomous systems, and human–robot interaction |
| Real-time scheduling; performance evaluation of timed systems; cost-optimal planning | CORA | Cost variables, optimal scheduling, extended priced timed automata | Ideal for scenarios where timing and resource consumption must be optimized simultaneously |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Grobelna, I.; Gajewski, K.; Karatkevich, A. A Systematic Review on the Applications of Uppaal. Sensors 2025, 25, 3484. https://doi.org/10.3390/s25113484
Grobelna I, Gajewski K, Karatkevich A. A Systematic Review on the Applications of Uppaal. Sensors. 2025; 25(11):3484. https://doi.org/10.3390/s25113484
Chicago/Turabian StyleGrobelna, Iwona, Krystian Gajewski, and Andrei Karatkevich. 2025. "A Systematic Review on the Applications of Uppaal" Sensors 25, no. 11: 3484. https://doi.org/10.3390/s25113484
APA StyleGrobelna, I., Gajewski, K., & Karatkevich, A. (2025). A Systematic Review on the Applications of Uppaal. Sensors, 25(11), 3484. https://doi.org/10.3390/s25113484








