A Zero-Knowledge Proof-Enabled Blockchain-Based Academic Record Verification System
Abstract
1. Introduction
- Credential fraud—Ensuring that issued degrees are authentic and tamper-proof.
- Data privacy—Maintaining compliance with regulations like GDPR and FERPA while securing student information.
- Global interoperability—Creating a standardized system that allows credentials to be verified seamlessly across institutions, employers, and borders.
- Scalability issues due to high gas fees and transaction costs on public blockchains.
- Lack of privacy mechanisms in existing blockchain solutions, exposing sensitive academic data.
- Interoperability barriers caused by differences in institutional infrastructure and digital identity management.
- Decentralized Identifiers (DIDs)—Establishes standardized, self-sovereign digital identities for students, facilitating global academic mobility without reliance on centralized identity systems [11].
- Dual-Blockchain Architecture (Public and Private Chains)—Separates publicly verifiable credential data from sensitive academic records, ensuring efficient, secure, and privacy-preserving transactions.
- Interplanetary File System (IPFS)—Provides secure, decentralized storage for academic documents, ensuring data integrity and tamper-proof verification in a distributed environment [12].
- zk-SNARK Encryption in zkEVM Smart Contracts—Implements privacy-preserving smart contracts, allowing credentials to be validated without exposing student information to third parties.
- Privacy-Preserving Verification via ZKPs: We incorporate Zero-Knowledge Proofs to allow institutions and employers to verify the authenticity of academic credentials without revealing sensitive student data, offering stronger privacy than any existing system.
- Support for Self-Sovereign Identity with DIDs: ZKBAR-V leverages Decentralized Identifiers (DIDs) to provide globally interoperable, self-sovereign identities that eliminate the dependency on centralized databases for student identity verification.
- Dual-Blockchain Architecture: We design a hybrid architecture that separates public and private data across two blockchains, balancing transparency (public chain) with privacy and performance (private chain).
- IPFS Integration for Secure Document Storage: Academic records are stored off-chain using IPFS, ensuring decentralized, tamper-proof, and cost-effective data management.
- zk-SNARK-Enabled Smart Contracts on zkEVM: By deploying smart contracts on a zkEVM-compatible environment, ZKBAR-V allows for on-chain credential validation while maintaining full privacy and compliance with regulations such as GDPR.
- A Unified Framework for Global Interoperability: Unlike fragmented existing systems, ZKBAR-V is designed as a comprehensive and extensible platform that facilitates international recognition and seamless verification of credentials.
2. Literature Review
Background Study
- Public Blockchain: Bitcoin is a prime example of a blockchain operating on a public network—a fully decentralized system that functions without a central governing entity. In this model, every participant can validate transactions using a consensus mechanism such as Proof of Work or Proof of Stake, which ensures network security by requiring validator nodes to verify transactions. While this system provides a highly secure and trust-based structure for transactions, it faces challenges in scalability and high operational costs due to the extensive validation process required by multiple participants [10]. Nevertheless, for applications where security and data immutability are paramount, public blockchains remain one of the most effective solutions.
- Private Blockchain: Unlike public blockchains, private blockchains operate within a restricted network while maintaining the core principles of security and immutability. However, they lack full decentralization, as control is centralized under the entity that implements and manages the system. Private blockchains are typically used at the enterprise level, where the primary focus is on data security rather than decentralization. In these networks, only a selected group of participants have permission to conduct transactions and validate data. One key advantage of private blockchains is the absence of gas fees, unlike public networks such as Ethereum. Instead, the primary costs are related to implementation and administration [33].
- The Zero-Knowledge Ethereum Virtual Machine (zkEVM) integrates Zero-Knowledge Proofs (zk-SNARKs or zk-STARKs) with smart contract execution on Ethereum-compatible networks. This technology enables transaction validation without exposing sensitive data, significantly enhancing privacy in blockchain networks. zkEVM can be deployed on both public and private networks. In public blockchains like Ethereum, it ensures transaction privacy while maintaining network security. In private environments, zkEVM provides a scalable and confidential solution for businesses requiring secure transactions. According to [9], Zero-Knowledge Proofs are essential for privacy in blockchain applications, allowing verification without disclosing underlying data. In addition, recent research highlights zkEVM’s compatibility with Solidity-based smart contracts, facilitating seamless integration across various blockchain networks while enhancing security and scalability [9,10].
- Decentralized Storage: The Interplanetary File System (IPFS) is a decentralized file storage system that operates without reliance on a central server, similar in principle to blockchain but designed for handling large volumes of data, such as files. In the IPFS, files are broken into smaller chunks and distributed across a network of computers, known as nodes. This redundancy ensures that even if some nodes go offline, the files remain accessible. Unlike traditional storage systems where files are retrieved by name or location, IPFS uses content-addressable storage. Each file is identified by a unique cryptographic hash rather than a filename. If a file is modified, its hash changes, making any tampering immediately detectable. This mechanism enables the detection and removal of corrupted files while preserving the integrity of the network [12]. A powerful use case arises when IPFS is combined with blockchain technology. Blockchain ensures transaction integrity and verification, while IPFS provides efficient decentralized storage for larger, unstructured data that blockchain alone cannot handle efficiently. This integration enhances security, scalability, and reliability while maintaining decentralized principles [12].
- Decentralized Identifiers (DIDs): Decentralized Identifiers (DIDs) were developed to address key challenges in identity registration and management, particularly the centralization of identity systems controlled by governments or traditional institutions. In centralized systems, individuals lack full control over their personal data after registration, making their information susceptible to security breaches and unauthorized access. Beyond security concerns, portability issues arise due to variations in identity formats across different countries. Some nations use distinct naming conventions or lack standardized identity numbers, making cross-border identity verification complex. Verifying identities outside the jurisdiction of the issuing government requires an in-depth understanding of each country’s registration structure, further complicating the process. To solve these challenges, the World Wide Web Consortium (W3C) formed the DID Working Group in 2017 to develop a decentralized identity standard. In 2020, they released DID v1.0, incorporating key attributes such as decentralization, user control, privacy, security, proof-based verification, discoverability, interoperability, portability, simplicity, and extensibility [11]. The ZKBAR-V framework integrates DIDs as a core component to align with BACIP principles, enhancing system interoperability through a standardized global identification system. This approach enables credential verification without relying on centralized authorities, ensuring compliance with international regulations such as GDPR, which emphasize data security and privacy.
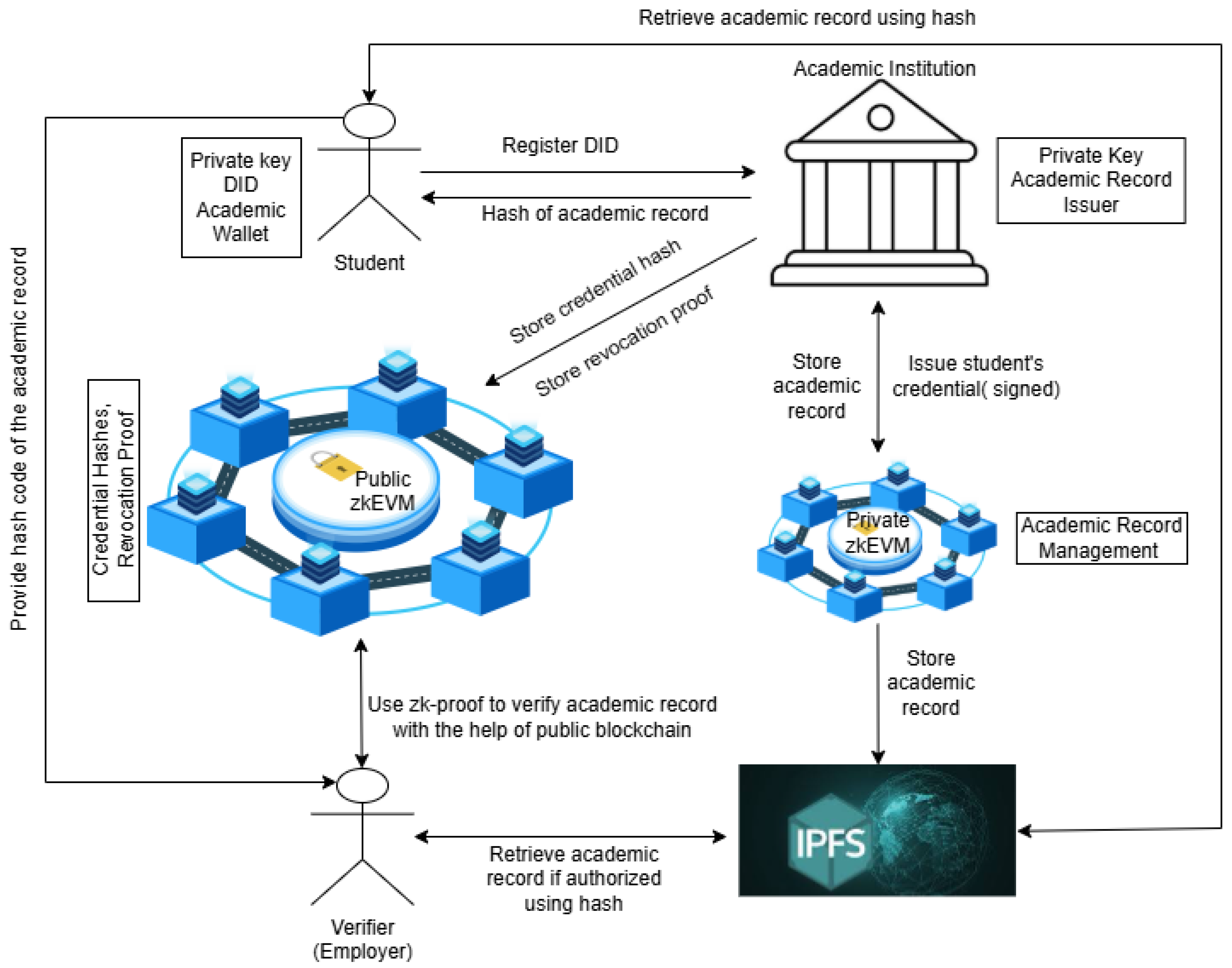
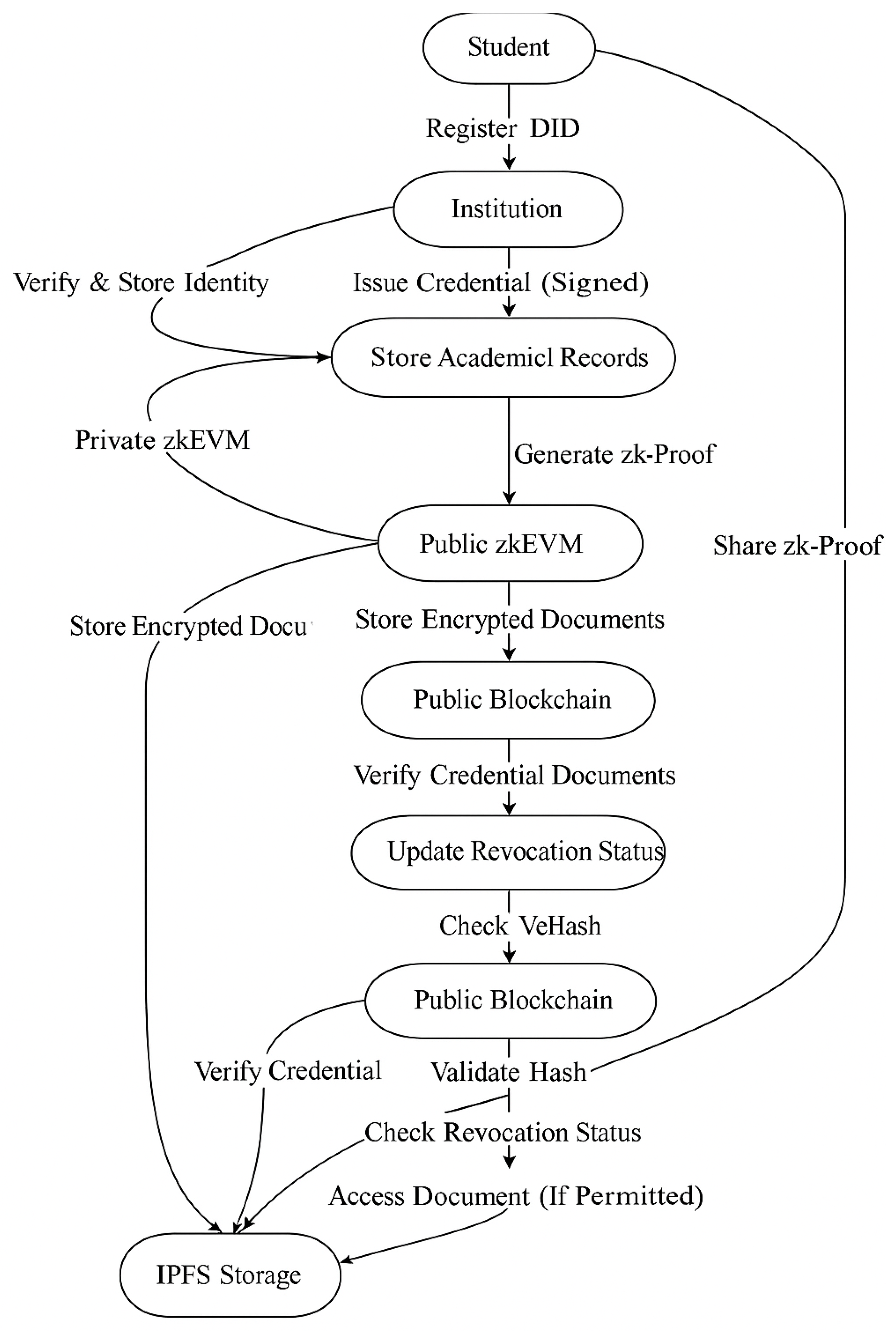
3. The Proposed Zero-Knowledge-Based Academic Record Verification System
- Private zkEVM:
- –
- This handles credential issuance and stores sensitive academic data (personally identifiable information such as social data).
- –
- The institution stores security number, passport, age, academic result, and misconducts on the private blockchain.
- –
- The institution also uses IPFS for decentralized encrypted document storage.
- Public zkEVM
- –
- Public zkEVM generates Zero-Knowledge Proofs (zk-Proofs) without exposing private data.
- –
- This processes credential verification by validating zk-Proofs.
- –
- It stores only credential hashes on the public blockchain (ensuring privacy).
- –
- It manages revocation proofs, updating the public blockchain when credentials are revoked.
3.1. System Actors and Roles
3.2. Security and Privacy Requirement
3.3. Zero-Knowledge Proof Implementation
3.4. Threat Model for the Proposed System
- D (Damage Potential)—The severity of the impact if the threat is exploited.
- R (Reproducibility)—How easily the threat can be reproduced.
- E (Exploitability)—The ease with which the threat can be exploited.
- A (Affected Users)—The number of users impacted by the threat.
- D (Discoverability)—How easy it is for an attacker to discover the vulnerability.
| Component | Threat | D | R | E | A | D | Risk Score | Severity |
|---|---|---|---|---|---|---|---|---|
| Private zkEVM | Spoofing (Unauthorized Access) | 4 | 3 | 3 | 4 | 3 | 3.4 | Low |
| Tampering (Modifying Records) | 5 | 2 | 2 | 5 | 2 | 3.2 | Low | |
| Information Disclosure | 5 | 3 | 3 | 6 | 3 | 4.0 | Medium | |
| Denial of Service (DoS) | 3 | 2 | 2 | 4 | 2 | 2.6 | Low | |
| Elevation of Privilege | 6 | 3 | 3 | 5 | 3 | 4.0 | Medium | |
| Public zkEVM | Spoofing (Impersonation) | 3 | 3 | 3 | 4 | 3 | 3.2 | Low |
| Tampering (Hash Manipulation) | 4 | 2 | 2 | 4 | 2 | 2.8 | Low | |
| Repudiation (Credential Denial) | 3 | 2 | 2 | 4 | 2 | 2.6 | Low | |
| Denial of Service (Overloading Network) | 5 | 3 | 3 | 5 | 3 | 3.8 | Medium | |
| IPFS | Tampering (Modifying Files) | 4 | 2 | 2 | 5 | 2 | 3.0 | Low |
| Information Disclosure | 6 | 3 | 3 | 6 | 3 | 4.2 | Medium | |
| Denial of Service (Access Disruption) | 4 | 3 | 3 | 4 | 3 | 3.4 | Low | |
| DID and ZKP Processes | Spoofing (Fake Identity) | 3 | 2 | 2 | 4 | 2 | 2.6 | Low |
| Information Disclosure | 5 | 3 | 3 | 6 | 3 | 4.0 | Medium | |
| Repudiation (Denying Credential Issuance) | 3 | 2 | 2 | 4 | 2 | 2.6 | Low |
4. Results and Discussion
4.1. Development and Implementation
4.2. Comparison of Component of the Proposed System with Existing Systems
4.3. Validation and Testing
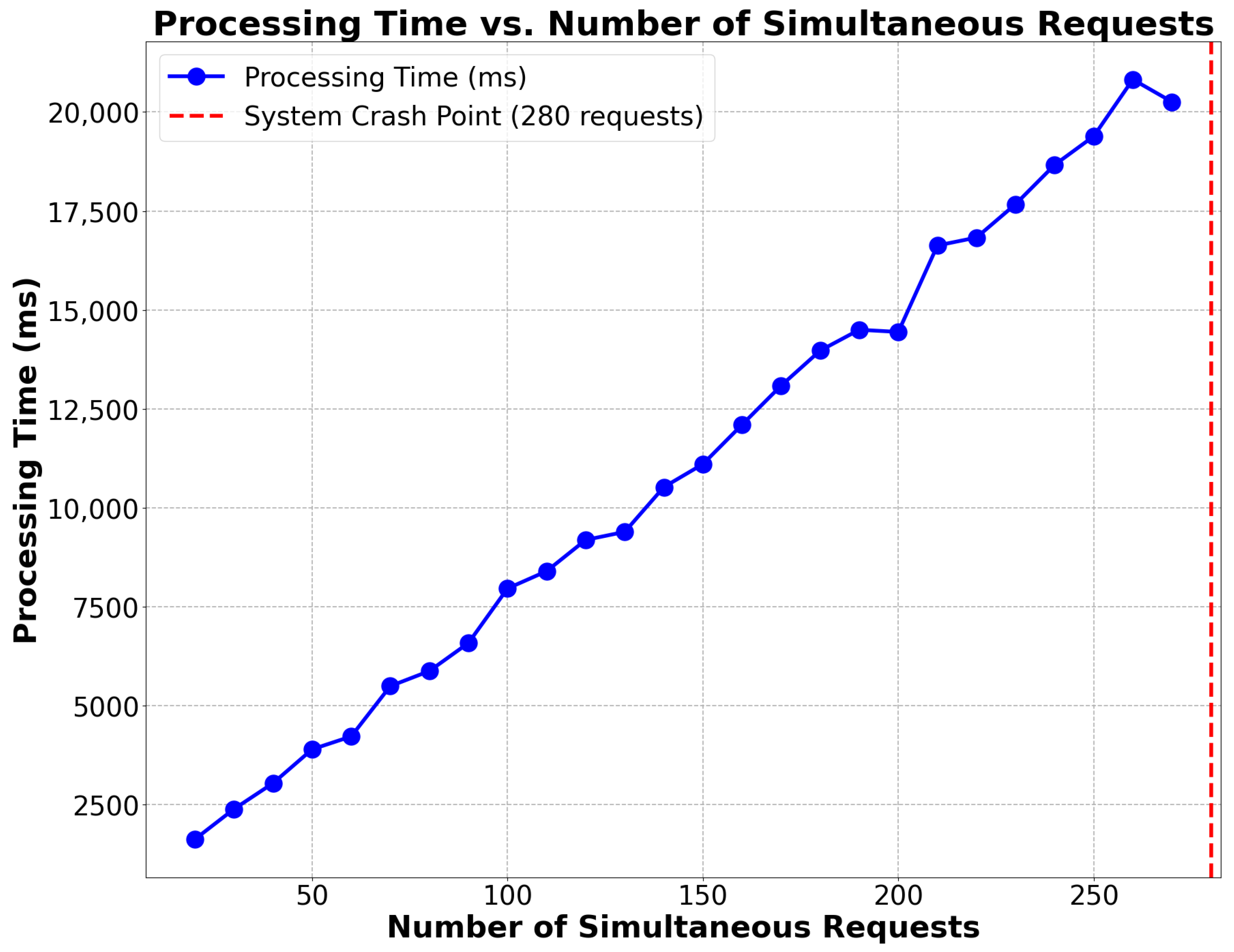
- Scalability Testing: This test was performed to determine how the system performs with increasing numbers of concurrent credential issuance/verification requests. The test started with lower loads and incrementally increased the number of concurrent requests, measuring processing time, resource utilization (CPU and memory), and response times to find a threshold, for instance, at the point where we can expect the system to slow down in terms of performance. The test helped us determine the system’s maximum capacity before a threshold is exceeded.The Scalability Testing revealed that the ZKBAR-V framework was capable of efficiently managing up to 280 concurrent credential issuance and verification requests without significant performance issues. During this load, resource utilization, including CPU and memory usage, remained within acceptable limits, and response times were consistent. However, when the load surpassed 280 concurrent requests, there was a marked increase in processing time and resource consumption, leading to noticeable delays in response times. CPU usage peaked significantly, and the system began experiencing bottlenecks, indicating that its operational capacity had been reached. These results highlight the system’s robustness at moderate traffic levels but suggest that optimizations are necessary to support higher volumes without performance degradation.Figure 4 shows a graph illustrating the relationship between the time required to process a certain number of simultaneous requests and to mark the breaking point of the system’s collapse.
- Data Integrity and Privacy Testing: The Data Integrity and Privacy Testing of academic credentials managed by the ZKBAR-V framework was carried out in a zkEVM environment. The process involved uploading a batch of academic documents to IPFS and generating their respective SHA-256 cryptographic hashes, which were then recorded in the zkEVM blockchain. In the first part of the testing, the documents were retrieved from IPFS and verified against the stored hashes. If any unauthorized changes were detected, it indicated that the system was able to prevent any tampering with documents. In the second part of the testing, the same batch of verifications was carried out, but this time using Zero-Knowledge Proofs (zk-SNARKs). Although the documents were verified, no adjacent data (including personal information) could be exposed in this part of the testing. The tests monitored both the system’s ability to maintain document integrity, as well as its ability to keep the system private at the time of credential verification.The Data Integrity and Privacy Testing on the zkEVM environment confirmed that the ZKBAR-V framework was still robust and uncompromised. The cryptographic hashes of the documents (stored on the zkEVM blockchain and linked via a hash to the data on IPFS) were tested for consistency. The system proved impervious to any kind of trickery in document updates, as all documents that were not changed produced matching hashes. Modifications to documents resulted in mismatched hashes, as did attempts to create hash collisions. All these malicious-intent scenarios were blocked at their source. Privacy tests also confirmed that the zk-SNARKs implemented in the ZKBAR-V framework were operating well and allowed the system to authenticate credentials (e.g., university qualifications) without revealing other, adjacent personal data. The zkEVM network sent out only cryptographic proofs, and the data themselves remained fully protected. This confirmed that ZKBAR-V does indeed offer a strong extra layer of privacy. The system is GDPR-compliant.
- Functional Testing: This ensured that the system functioned as a whole, meaning from end-to-end. We tested credential issuance, verification, and revocation, and how the front-end (user interface) interacted with the back-end (blockchain interactions) and IPFS. The functional testing verified that smart contracts executed as expected and that the data handling functions functioned as intended so the system would work as expected under normal usage.The integration and interplay of all the elements of the ZKBAR-V framework for Functional Testing was successful. This included the front-end, back-end, smart contracts, and integration with external systems. The system worked smoothly when issuing credentials, verifying credentials, and for revoking credentials, all performed correctly using the smart contracts in the zkEVM blockchain. The front-end was built in React.js for a smooth interaction experience for the students and institutions, and the back.js actively listens to requisite information from the front-end, communicates with the blockchain, and securely stores the documents on IPFS. Sensitive data protection: Positive results considered as sensitive information were strictly protected for all transaction cycles. Unit tests (smart contracts and API): No errors or security vulnerabilities identified. Web app: All connections with external systems by API are functional; no errors. Functional tests: Operational for all transactions, all steps, and all conditions. The system operates properly, with no errors or security vulnerabilities discovered. The system is ready for use. We can feed external systems with information and use the web app.
- Cost Efficiency Analysis: The Cost Efficiency Analysis analyzed the cost effectiveness of issuing, verifying, and revoking credentials on the public zkEVM network. It tracked gas fees and other transaction costs as part of the system’s operation in the zkEVM. It also compared the costs of deploying ZKBAR-V in the zkEVM to deploying the system on Bitcoin and Ethereum. These simulations allowed us to gauge the performance of the zkEVM relative to other blockchain networks. We identified optimizations that would minimize transaction costs for the system while keeping it economically viable for academic institutions.The analysis, based on gas prices published on 9 September 2024 (Polygon, 2024; Etherscan, 2024) [34,35], demonstrated that zkEVM Polygon consistently provided approximately 94% cost savings across all operations of issuing a credential, revoking a credential, and contract deployment when compared to Ethereum Mainnet. These findings underscore the substantial cost advantage of using zkEVM Polygon for the decentralized management of academic credentials. Figure 4 illustrates the gas consumption for the ZKBAR-V system, while Figure 5 visualizes the cost differences between both networks for credential-related transactions. Moreover, by segregating sensitive data into a private network, ZKBAR-V minimizes public transaction costs, as only necessary credential issuance and verification data incur public network fees. This dual-network approach further enhances the system’s cost efficiency.
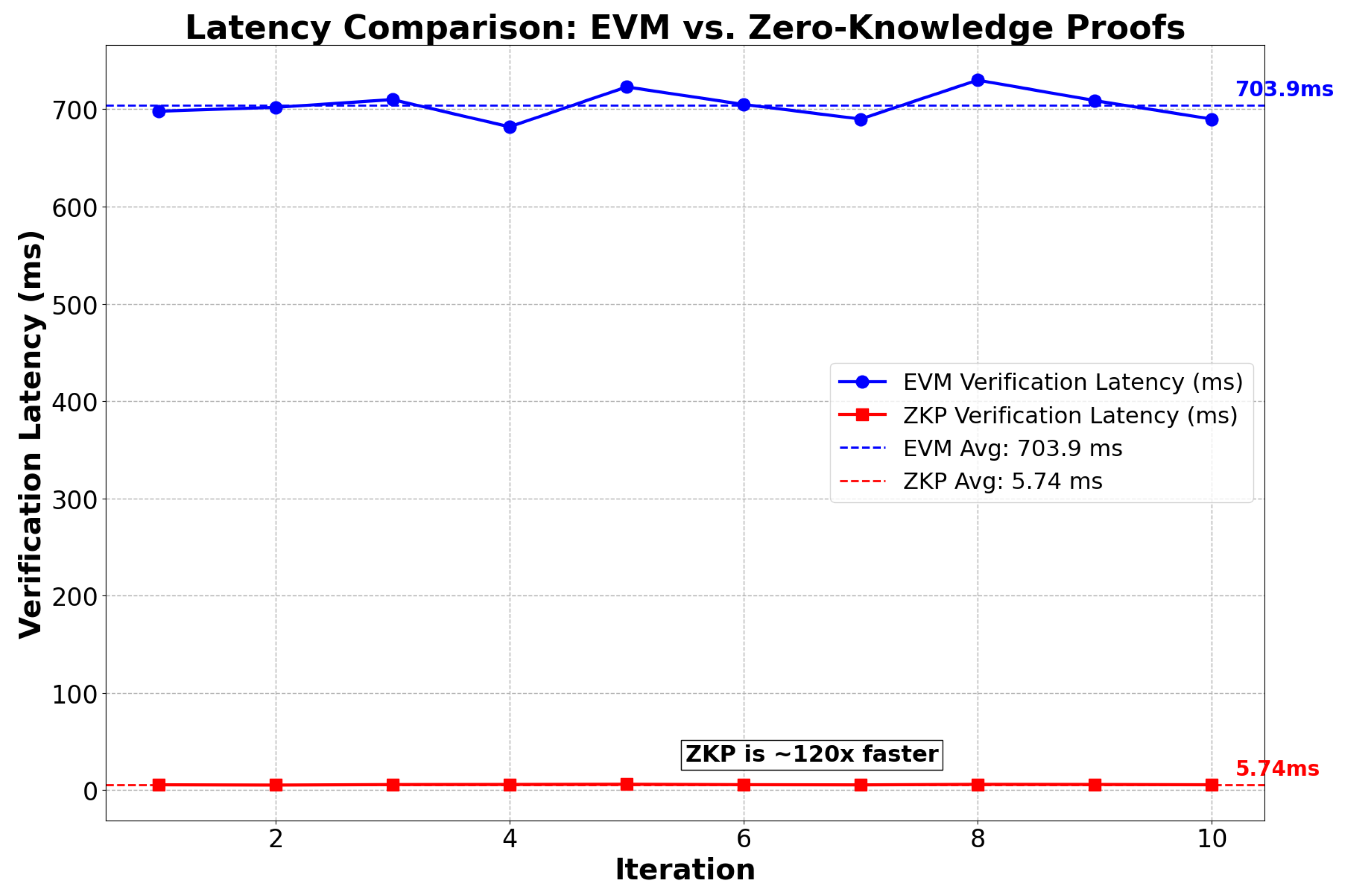
- Latency comparison between zkEVM and EVM: A verification latency comparison between Ethereum Virtual Machine (EVM) and Zero-Knowledge Proofs (ZKPs) was conducted over 10 iterations, measuring the time required to verify a transaction or computation result. The results presented in Figure 7 show that EVM has an average verification latency of 708 ms (±0.02 s), while ZKP takes only 5.8 ms (±0.001 s), meaning that ZKP is approximately 120 times faster, with significantly lower execution variability. This analysis confirms that ZKP is a more efficient solution for improving scalability and reducing costs in blockchain, as it enables fast and lightweight transaction validations without requiring full computation on every node import time.
5. Discussion
5.1. Usability of the Proposed System
5.2. Adoption Challenges
6. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Eaton, S.E.; Carmichael, J.J. Fake degrees and credential fraud, contract cheating, and paper mills: Overview and historical perspectives. In Fake Degrees and Fraudulent Credentials in Higher Education; Springer: Berlin/Heidelberg, Germany, 2023; pp. 1–22. [Google Scholar]
- Carmichael, J.J.; Eaton, S.E. Fake Degrees and Fraudulent Credentials in Higher Education: Conclusions and Future Directions. In Fake Degrees and Fraudulent Credentials in Higher Education; Springer: Berlin/Heidelberg, Germany, 2023; pp. 269–285. [Google Scholar]
- Brown, G.M. Degrees of doubt: Legitimate, real and fake qualifications in a global market. J. High. Educ. Policy Manag. 2006, 28, 71–79. [Google Scholar] [CrossRef]
- Rahman, T.; Mouno, S.I.; Raatul, A.M.; Al Azad, A.K.; Mansoor, N. Verifi-chain: A credentials verifier using blockchain and IPFS. In Proceedings of the International Conference on Information, Communication and Computing Technology; Springer: Berlin/Heidelberg, Germany, 2023; pp. 361–371. [Google Scholar]
- Blockcerts. Blockchain Credentials. 2021. Available online: https://www.blockcerts.org/ (accessed on 1 May 2025).
- Michoulis, G.; Petridou, S.; Vergidis, K. Verification of academic qualifications through ethereum blockchain: An introduction to VerDe. In Proceedings of the XIV Balkan Conference on Operational Research (BALCOR 2020), Thessaloniki, Greece, 30 September–3 October 2020; pp. 429–433. [Google Scholar]
- Ghazali, O.; Saleh, O.S. A graduation certificate verification model via utilization of the blockchain technology. J. Telecommun. Electron. Comput. Eng. (JTEC) 2018, 10, 29–34. [Google Scholar]
- Tang, Q. Towards using blockchain technology to prevent diploma fraud. IEEE Access 2021, 9, 168678–168688. [Google Scholar] [CrossRef]
- Partala, J.; Nguyen, T.H.; Pirttikangas, S. Non-interactive zero-knowledge for blockchain: A survey. IEEE Access 2020, 8, 227945–227961. [Google Scholar] [CrossRef]
- Buterin, V. A Next-Generation Smart Contract and Decentralized Application Platform. White Paper. Ethereum. Volume 3. 2–1. 2014. Available online: https://ethereum.org/en/whitepaper (accessed on 1 May 2025).
- Lin, I.C.; Yeh, I.; Chang, C.C.; Liu, J.C.; Chang, C.C. Designing a Secure and Scalable Data Sharing Mechanism Using Decentralized Identifiers (DID). CMES-Comput. Model. Eng. Sci. 2024, 141, 809. [Google Scholar] [CrossRef]
- Abed, S.I.; Albeltaji, O.S.; Alnabriss, H. Decentralized Storage Using Inter Planetary File System. In AI in Business: Opportunities and Limitations: Volume 2; Springer: Berlin/Heidelberg, Germany, 2024; pp. 221–230. [Google Scholar]
- Moya, J.A.B. Blockchain for Academic Integrity: Developing the Blockchain Academic Credential Interoperability Protocol (BACIP). arXiv 2024, arXiv:2406.15482. [Google Scholar]
- Arenas, R.; Fernandez, P. CredenceLedger: A permissioned blockchain for verifiable academic credentials. In Proceedings of the 2018 IEEE International Conference on Engineering, Technology and Innovation (ICE/ITMC), Stuttgart, Germany, 17–20 June 2018; pp. 1–6. [Google Scholar]
- Badr, A.; Rafferty, L.; Mahmoud, Q.H.; Elgazzar, K.; Hung, P.C. A permissioned blockchain-based system for verification of academic records. In Proceedings of the 2019 10th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Canary Islands, Spain, 24–26 June 2019; pp. 1–5. [Google Scholar]
- Grolleau, G.; Lakhal, T.; Mzoughi, N. An introduction to the economics of fake degrees. J. Econ. Issues 2008, 42, 673–693. [Google Scholar] [CrossRef]
- Nadeem, N.; Hayat, M.F.; Qureshi, M.A.; Majid, M.; Nadeem, M.; Janjua, J. Hybrid Blockchain-based Academic Credential Verification System (B-ACVS). Multimed. Tools Appl. 2023, 82, 43991–44019. [Google Scholar] [CrossRef]
- Capece, G.; Levialdi Ghiron, N.; Pasquale, F. Blockchain technology: Redefining trust for digital certificates. Sustainability 2020, 12, 8952. [Google Scholar] [CrossRef]
- Chakroun, B.; Keevy, J. Digital Credentialing: Implications for the Recognition of Learning Across Borders; UNESCO: Paris, France, 2018.
- Kamil, M.; Sunarya, P.A.; Muhtadi, Y.; Adianita, I.R.; Anggraeni, M. BlockCert higher education with public key infrastructure in Indonesia. In Proceedings of the 2021 9th international conference on cyber and IT service management (CITSM), Bengkulu, Indonesia, 22–23 September 2021; pp. 1–6. [Google Scholar]
- Rama Reddy, T.; Prasad Reddy, P.; Srinivas, R.; Raghavendran, C.V.; Lalitha, R.; Annapurna, B. Proposing a reliable method of securing and verifying the credentials of graduates through blockchain. EURASIP J. Inf. Secur. 2021, 2021, 7. [Google Scholar] [CrossRef]
- Alnafrah, I.; Mouselli, S. Revitalizing blockchain technology potentials for smooth academic records management and verification in low-income countries. Int. J. Educ. Dev. 2021, 85, 102460. [Google Scholar] [CrossRef]
- Baldi, M.; Chiaraluce, F.; Frontoni, E.; Gottardi, G.; Sciarroni, D.; Spalazzi, L. Certificate Validation Through Public Ledgers and Blockchains. In Proceedings of the First Italian Conference on Cybersecurity (ITASEC), Venice, Italy, 17–20 January 2017; pp. 156–165. [Google Scholar]
- Lei, A.; Cao, Y.; Bao, S.; Li, D.; Asuquo, P.; Cruickshank, H.; Sun, Z. A blockchain based certificate revocation scheme for vehicular communication systems. Future Gener. Comput. Syst. 2020, 110, 892–903. [Google Scholar] [CrossRef]
- Haveri, P.; Rashmi, U.; Narayan, D.; Nagaratna, K.; Shivaraj, K. Edublock: Securing educational documents using blockchain technology. In Proceedings of the 2020 11th International Conference on Computing, Communication and Networking Technologies (ICCCNT), Kharagpur, India, 1–3 July 2020; pp. 1–7. [Google Scholar]
- Sethia, G.; Namratha, S.; Srikanth, H.; Sreeja, C. Academic certificate validation using blockchain technology. In Proceedings of the 2022 International Conference on Trends in Quantum Computing and Emerging Business Technologies (TQCEBT), Pune, India, 13–15 October 2022; pp. 1–5. [Google Scholar]
- Shaikh, Z.A.; Khan, A.A.; Baitenova, L.; Zambinova, G.; Yegina, N.; Ivolgina, N.; Laghari, A.A.; Barykin, S.E. Blockchain hyperledger with non-linear machine learning: A novel and secure educational accreditation registration and distributed ledger preservation architecture. Appl. Sci. 2022, 12, 2534. [Google Scholar] [CrossRef]
- Chowdhary, A.; Agrawal, S.; Rudra, B. Blockchain based framework for student identity and educational certificate verification. In Proceedings of the 2021 Second International Conference on Electronics and Sustainable Communication Systems (ICESC), Coimbatore, India, 4–6 August 2021; pp. 916–921. [Google Scholar]
- Delgado-von Eitzen, C.; Anido-Rifón, L.; Fernández-Iglesias, M.J. Application of blockchain in education: GDPR-compliant and scalable certification and verification of academic information. Appl. Sci. 2021, 11, 4537. [Google Scholar] [CrossRef]
- Deenmahomed, H.A.; Didier, M.M.; Sungkur, R.K. The future of university education: Examination, transcript, and certificate system using blockchain. Comput. Appl. Eng. Educ. 2021, 29, 1234–1256. [Google Scholar] [CrossRef]
- Sharples, M.; Domingue, J. The blockchain and kudos: A distributed system for educational record, reputation and reward. In Proceedings of the Adaptive and Adaptable Learning: 11th European Conference on Technology Enhanced Learning, EC-TEL 2016 (Proceedings 11), Lyon, France, 13–16 September 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 490–496. [Google Scholar]
- Nakamoto, S.; Bitcoin, A. A Peer-to-Peer Electronic Cash System. 2008, Volume 4, p. 15. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 22 May 2025).
- Yang, R.; Wakefield, R.; Lyu, S.; Jayasuriya, S.; Han, F.; Yi, X.; Yang, X.; Amarasinghe, G.; Chen, S. Public and private blockchain in construction business process and information integration. Autom. Constr. 2020, 118, 103276. [Google Scholar] [CrossRef]
- Rana, S.K.; Rana, A.K.; Rana, S.K.; Sharma, V.; Lilhore, U.K.; Khalaf, O.I.; Galletta, A. Decentralized model to protect digital evidence via smart contracts using layer 2 polygon blockchain. IEEE Access 2023, 11, 83289–83300. [Google Scholar] [CrossRef]
- Khan, M.M.A.; Sarwar, H.M.A.; Awais, M. Gas consumption analysis of Ethereum blockchain transactions. Concurr. Comput. Pract. Exp. 2022, 34, e6679. [Google Scholar] [CrossRef]



| System/Study | ZKP | DID | Dual-Chain | IPFS | zk-SNARK or zkEVM | Prototype |
|---|---|---|---|---|---|---|
| CredenceLedger [14] | No | No | No | No | No | No |
| Badr et al. [15] | No | No | No | No | No | No |
| Gaikwad et al. [16] | No | No | No | Yes | No | No |
| B-ACVS (Nadeem et al.) [17] | No | No | No | Yes | No | Yes |
| Blockcerts (MIT) [18] | No | No | No | Yes | No | Yes |
| Sony Global Education [19] | No | No | Yes (Private Only) | No | No | Yes |
| Hyland Credentials [20] | No | Yes | No | No | No | Yes |
| University of Nicosia [31] | No | No | No | No | No | Yes |
| BACIP (Moya) [13] | No | Yes | No | No | No | Unknown |
| Baldi et al. [23] | No | No | No | No | No | Yes |
| Lei et al. [24] | No | No | No | No | No | No |
| Shaikh et al. [27] | No | No | Yes | No | No | Yes |
| Chowdhary et al. [28] | No | Yes | No | No | No | Yes |
| Delgado et al. [29] | No | Yes | No | No | No | No |
| Deenmahomed et al. [30] | No | No | No | No | No | Yes |
| Rama et al. [21] | No | No | No | Yes | No | Yes |
| VeriFi (Rahman et al.) [4] | No | No | No | Yes | No | Yes |
| Alnafrah et al. [22] | No | Yes | Yes | No | No | Yes |
| ZKBAR-V (Our Approach) | Yes | Yes | Yes | Yes | Yes | Yes |
| Actor | Role and Responsibilities |
|---|---|
| Student |
|
| Academic Institution |
|
| Verifier (Employer/University) |
|
| zkEVM Smart Contracts |
|
| Public Blockchain |
|
| Private Blockchain |
|
| IPFS (Decentralized Storage) |
|
| Requirement | Description |
|---|---|
| Data Confidentiality | Sensitive academic records are stored in a private blockchain and not exposed publicly. |
| Zero-Knowledge Verification | Credential authenticity is verified without revealing actual records. |
| Immutability and Tamper Resistance | Credential hashes stored on the public blockchain prevent modification or forgery. |
| User Control and Access | Students control who accesses their credentials using Decentralized Identifiers (DIDs) and Zero-Knowledge Proofs (zk-Proofs). |
| Decentralization and Trust Minimization | No single entity can manipulate records, ensuring trustless verification. |
| Threat Actor | Description | Potential Actions |
|---|---|---|
| Malicious Student | A dishonest student attempting to forge credentials. |
|
| Compromised Institution | A legitimate institution whose security is breached. |
|
| Unauthorized Verifier | A verifier (e.g., employer/university) that accesses credentials without consent. |
|
| External Attacker | A hacker or fraudulent entity outside the system. |
|
| STRIDE Threat | Description | Impact on the System | Mitigation Strategies |
|---|---|---|---|
| S—Spoofing | Impersonation of students, institutions, or verifiers. | Fake credentials, unauthorized access to verification. | Decentralized Identifiers (DIDs), public–private key authentication, Zero-Knowledge Proofs (zk-Proofs) for verification. |
| T—Tampering | Unauthorized modification of academic records. | Altered credentials, fake certifications. | Immutable blockchain storage, zk-SNARKs for credential verification. |
| R—Repudiation | Denying issuance or verification of credentials. | Institutions or students falsely claim actions were not performed. | Digital signatures on transactions, Zero-Knowledge Proofs (zk-Proofs) to verify transactions. |
| I—Information Disclosure | Unauthorized access to private academic data. | Privacy breaches, exposure of sensitive student records. | zkEVM smart contracts, data encryption, access control policies. |
| D—Denial of Service (DoS) | Overloading the system to disrupt credential verification. | Students or employers unable to verify credentials. | Rate-limiting, distributed storage (IPFS), and efficient blockchain queries. |
| E—Elevation of Privilege | Unauthorized access to private blockchain or issuing credentials. | A compromised institution can fraudulently issue degrees. | Permissioned private blockchain, institution key-based access control. |
| Type of Data | Storage Location | Who Can Access? |
|---|---|---|
| Credential Hashes | Public Blockchain | Verifiers (Read-Only) |
| Revocation Proofs | Public Blockchain | Verifiers (Read-Only) |
| Full Credential Details | Private Blockchain |
|
| DID (Decentralized ID) | Private Blockchain |
|
| IPFS Stored Transcripts | IPFS (Encrypted) |
|
| Components | ZKBAR-V | Hyland Credentials | B-ACVS | Sony Global Education | BCERT |
|---|---|---|---|---|---|
| GDPR | Yes | Yes | Yes | Yes | Yes |
| IPFS | Yes | No | No | No | Yes |
| Decentralized Identifiers (DIDs) | Yes | Yes | No | No | No |
| Private Blockchain (Hyperledger) | Yes | No | No | Yes | No |
| Public Blockchain (Ethereum) | Yes | Yes | Yes | No | Yes |
| Dual-Blockchain (Public zk-EVM and Private zk-EVM) | Yes | No | No | No | No |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Berrios Moya, J.A.; Ayoade, J.; Uddin, M.A. A Zero-Knowledge Proof-Enabled Blockchain-Based Academic Record Verification System. Sensors 2025, 25, 3450. https://doi.org/10.3390/s25113450
Berrios Moya JA, Ayoade J, Uddin MA. A Zero-Knowledge Proof-Enabled Blockchain-Based Academic Record Verification System. Sensors. 2025; 25(11):3450. https://doi.org/10.3390/s25113450
Chicago/Turabian StyleBerrios Moya, Juan Alamrio, John Ayoade, and Md Ashraf Uddin. 2025. "A Zero-Knowledge Proof-Enabled Blockchain-Based Academic Record Verification System" Sensors 25, no. 11: 3450. https://doi.org/10.3390/s25113450
APA StyleBerrios Moya, J. A., Ayoade, J., & Uddin, M. A. (2025). A Zero-Knowledge Proof-Enabled Blockchain-Based Academic Record Verification System. Sensors, 25(11), 3450. https://doi.org/10.3390/s25113450







