Blockchain-Based Information Security Protection Mechanism for the Traceability of Intellectual Property Transactions
Abstract
1. Introduction
- Enhanced legal compliance: The PROV data model is used to build an information traceability chain that complies with W3C standards, embedding blockchain timestamps to meet the legal requirements for the determination of the “time of first publication” and mapping the data of the entire life cycle of intellectual property rights creation, transaction, and use into judicially admissible elements of evidence.
- Dynamic trust mechanism: design a BLS threshold signature scheme based on the dynamic DKG protocol, enabling multiparty collaborative verification by creators, trading platforms, regulatory agencies, etc., and the signature threshold can be dynamically adjusted with the trading scenario.
- Chain verification structure: innovatively embedding the signature hash value of the previous stage into the subsequent verification link, forming an inseparable chain structure of traceable evidence, preventing man-in-the-middle attacks and timestamp forgeries.
2. Related Work
2.1. Blockchain Traceability Technology Evolution
- The maturity of cross-chain technology: e.g., Ref. [3] adopts the super ledger Fabric multi-channel architecture to realize the data isolation and collaboration of different business sectors.
- On-chain and off-chain collaborative storage: Ref. [4] reduces on-chain storage pressure while ensuring data trustworthiness through a hybrid storage scheme of IPFS and blockchain.
2.2. Technical Bottlenecks in Intellectual Property Traceability
3. Blockchain-Based Intellectual Property Traceability Information Protection Scheme
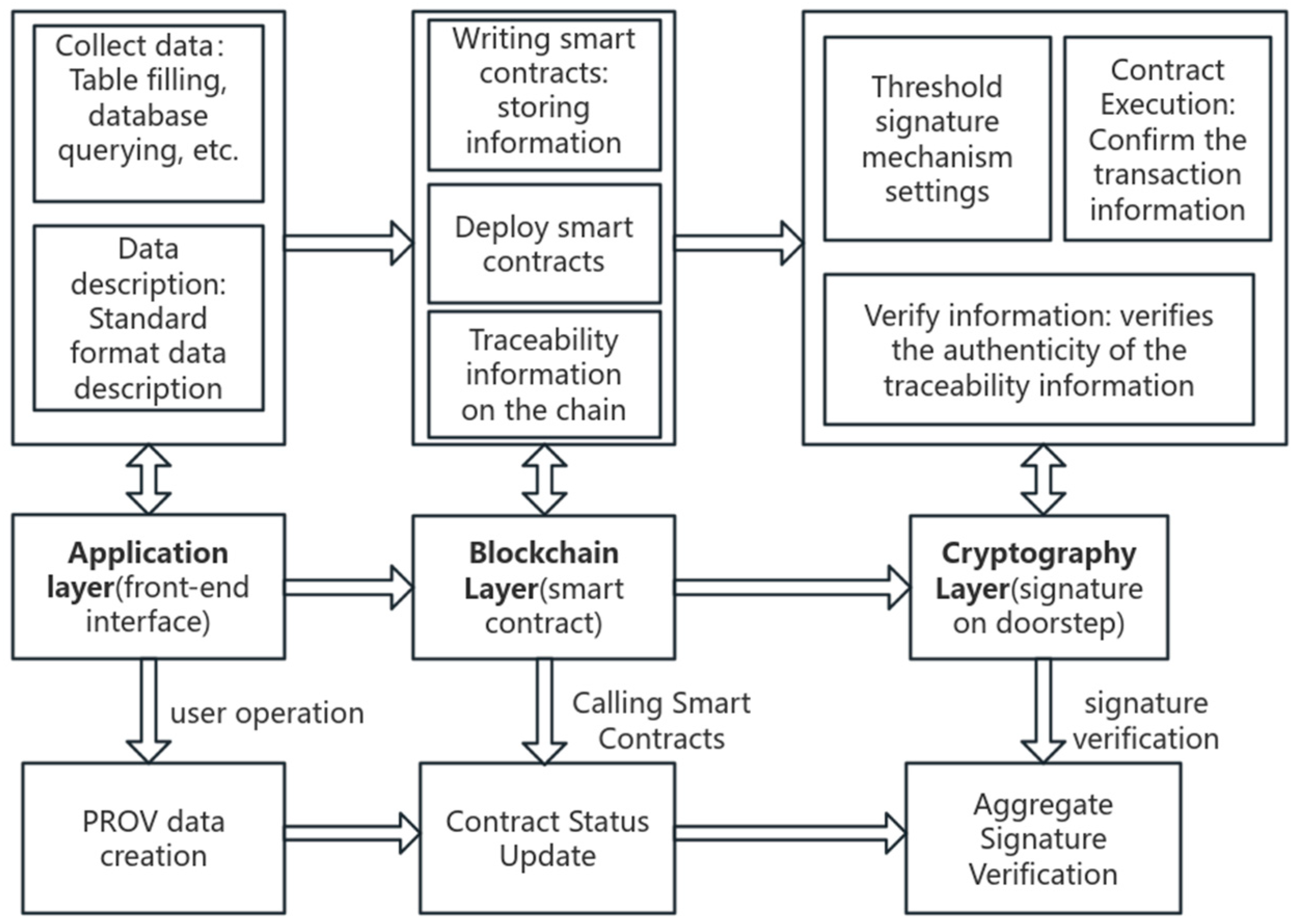
3.1. General Structure
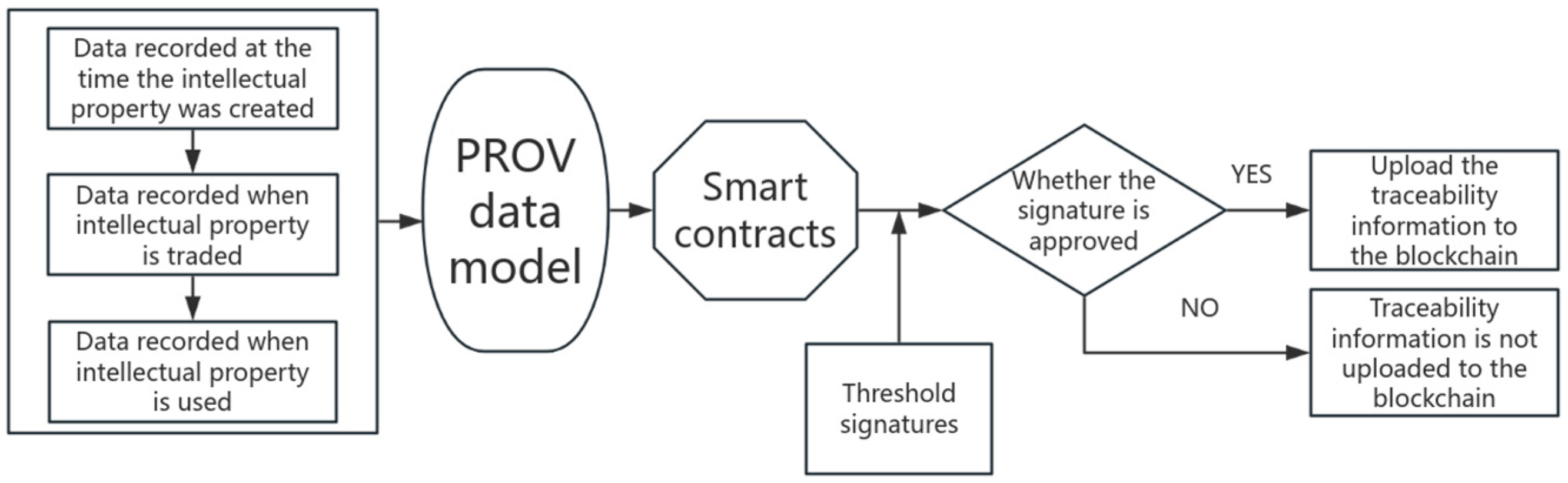
3.2. Collection and Description of Traceability Information of Intellectual Property Transactions
- Title creation stage:
- (1)
- Record the creator’s identifying information, time of creation, and place of creation;
- (2)
- Confirmation of the act of creation by means of electronic signatures, etc., and generation of related metadata.
- (3)
- Utilizing the PROV model, in which prov: Entity represents the created work, prov: Activity represents the creation behavior, and prov: Agent represents the creator.
- The stage of property rights transactions:
- (1)
- Record information on transactions such as the purchase, sale, authorization, and licensing of intellectual property.
- (2)
- Include information such as the time of the transaction, the counterparty, and the price of the transaction.
- (3)
- In PROV, prov: Entity denotes the intellectual property of the transaction, prov: Activity denotes the transaction behavior, and prov: Agent denotes the counterparty.
- Property use stage:
- (1)
- Record the actual use of intellectual property rights, including the party that uses it, when it is used, and how it is used.
- (2)
- In PROV, prov: Entity denotes the intellectual property being used, prov: Activity denotes the usage behavior, and prov: Agent denotes the user.
3.3. Traceability Information Encapsulation Smart Contract
3.4. Authentication of Traceability Information Based on Threshold Signatures and Timestamps
3.4.1. System Initialization
- (1)
- Define parameters
- (2)
- Role identification
3.4.2. Distributed Key Generation
3.4.3. Threshold Signature Generation
- (1)
- PROV message construction
- (2)
- Partial signature generation
- (3)
- Signature aggregation
3.4.4. Signature Verification
3.4.5. Threat Model Assumptions and Defense Strategies
- Witch Attack: The attacker forges multiple false identities (nodes) to participate in the system in an attempt to control the network or the signature process.
- 2.
- Data forgery: Attackers tamper with PROV data, such as artwork metadata and transaction records.
- 3.
- Collusion attack: Some nodes collude in an attempt to forge signatures or tamper with data.
- 4.
- Smart contract vulnerability: Unauthorized operations using contract code vulnerabilities.
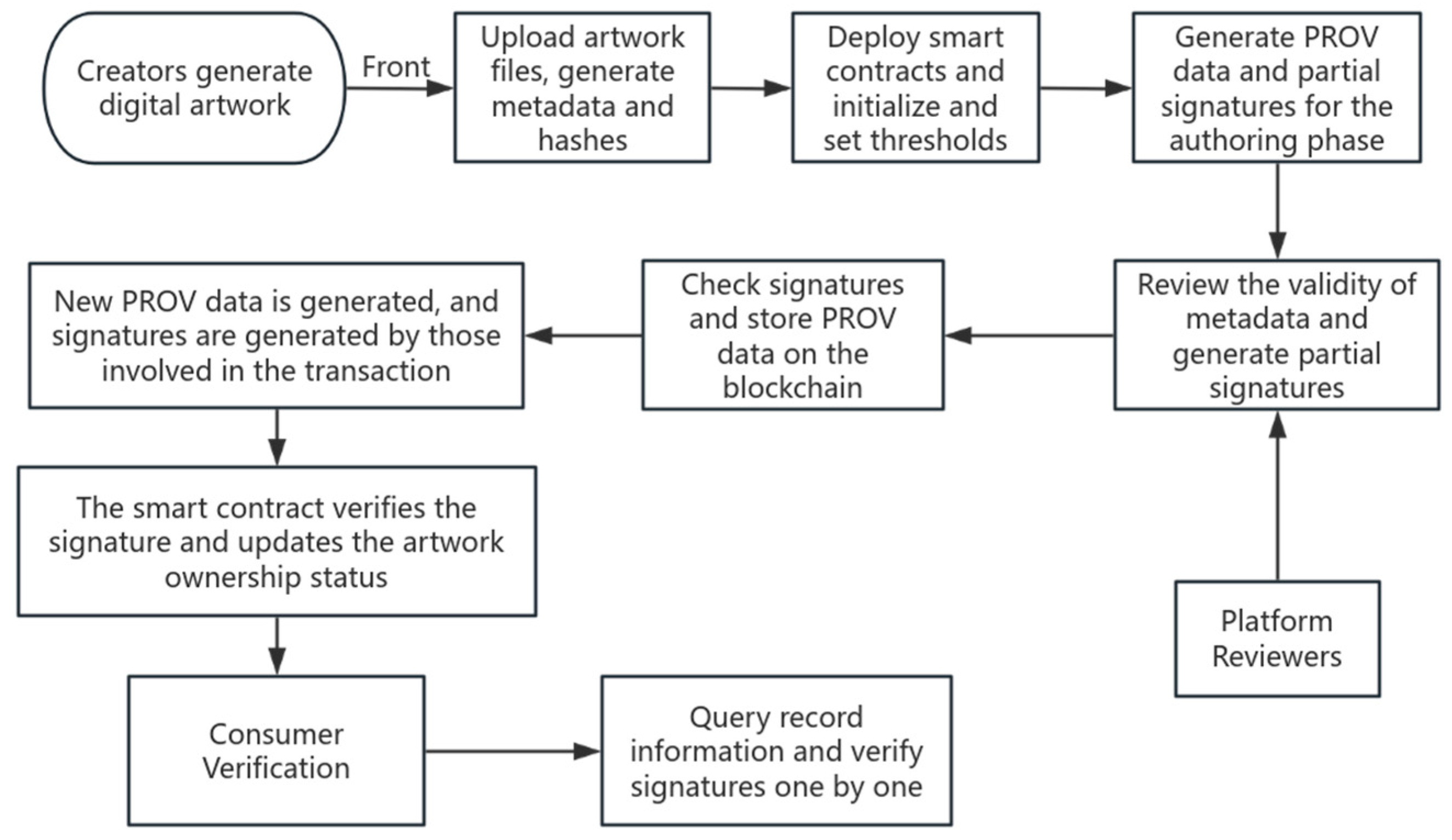
4. Experimental Analysis
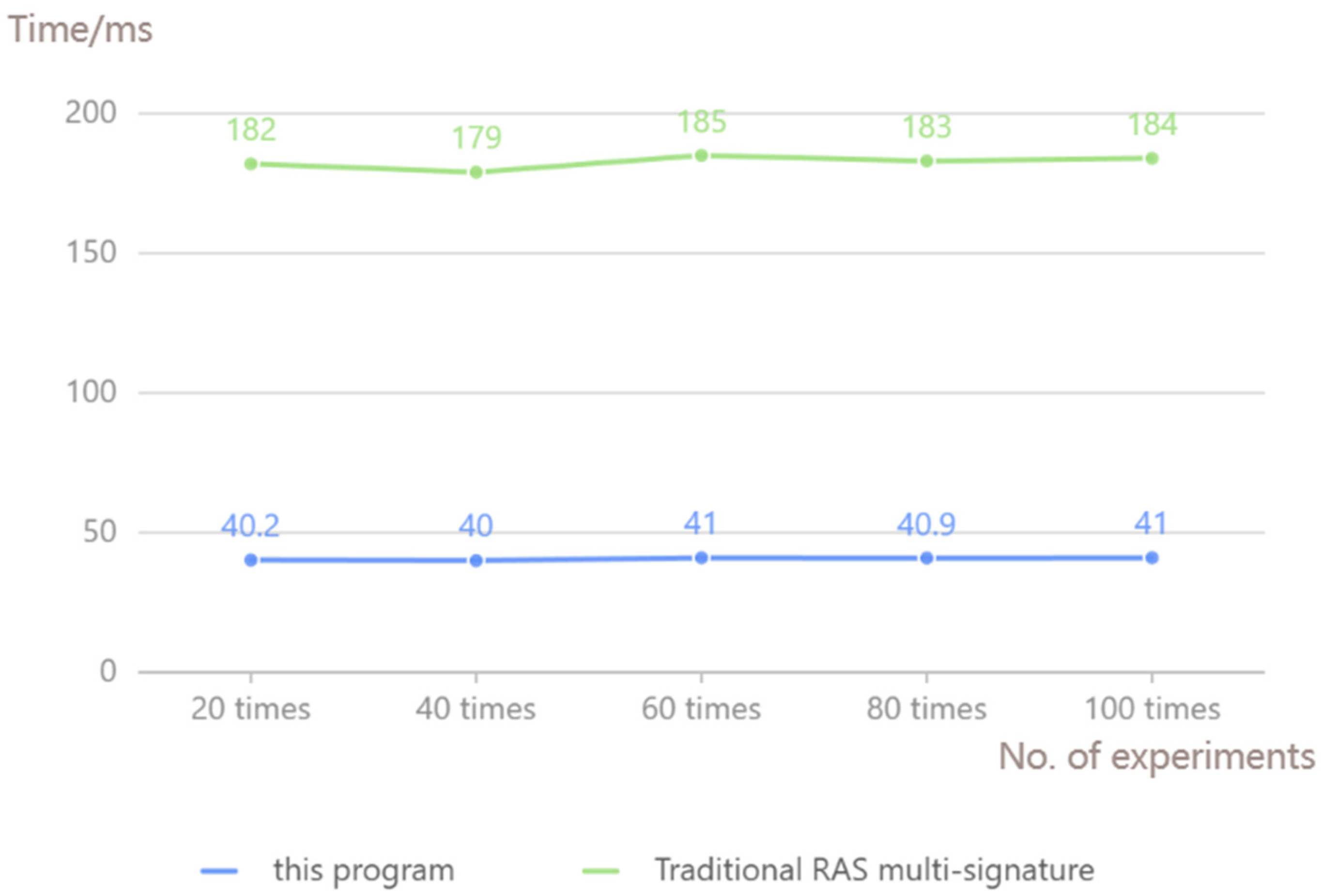
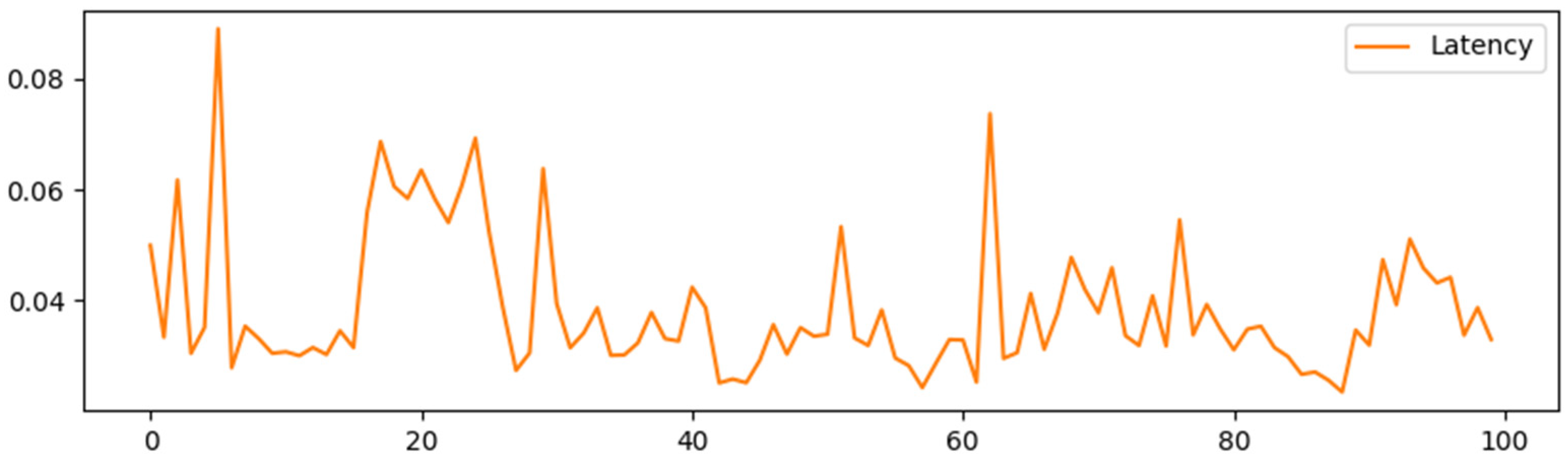
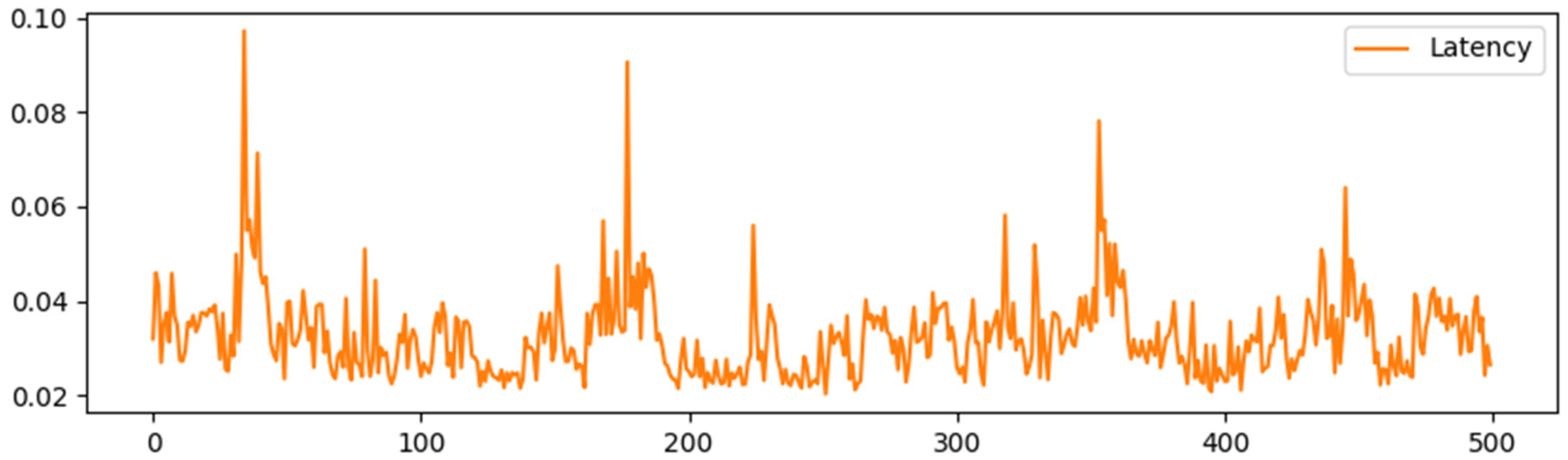
4.1. Performance Analysis
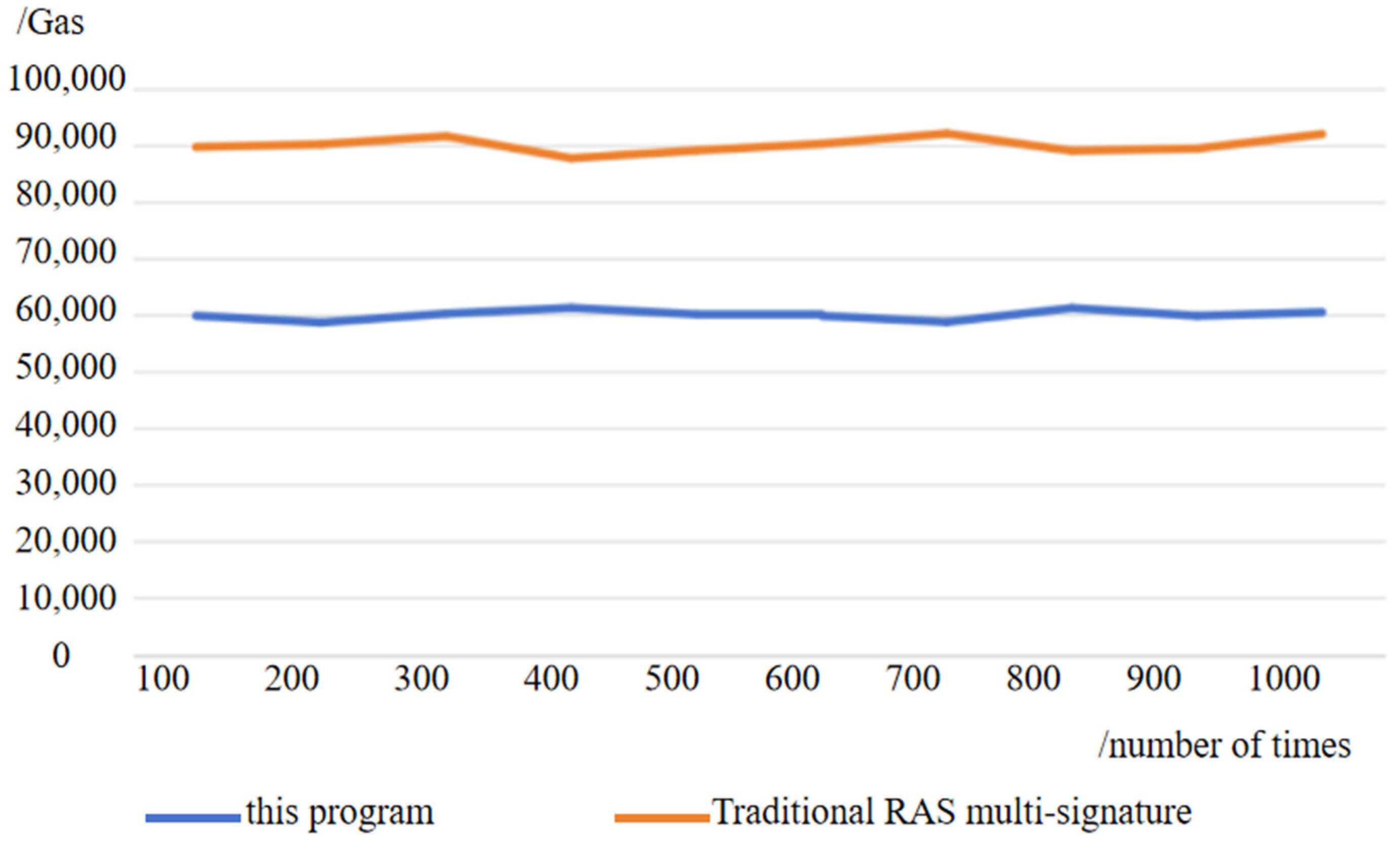
4.2. Comparison of Traceability Information Protection Programs
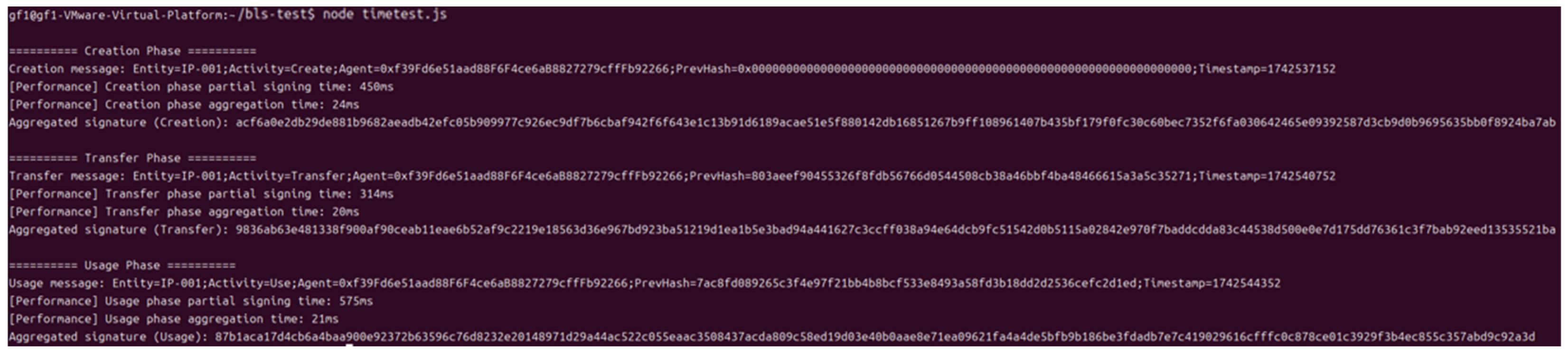
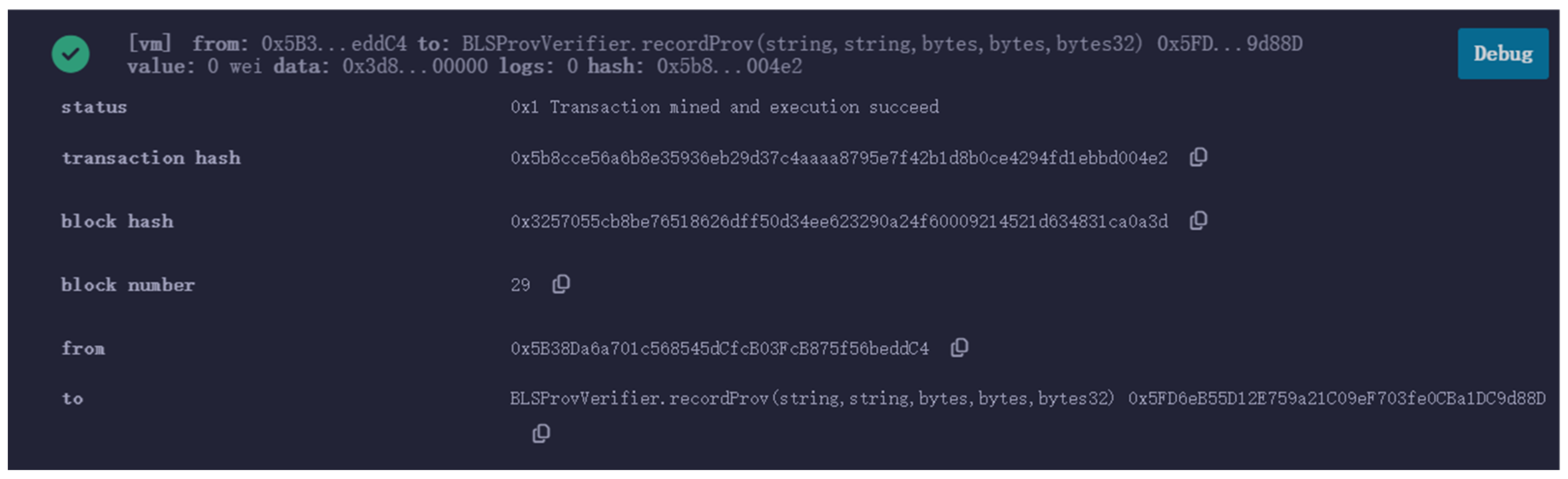
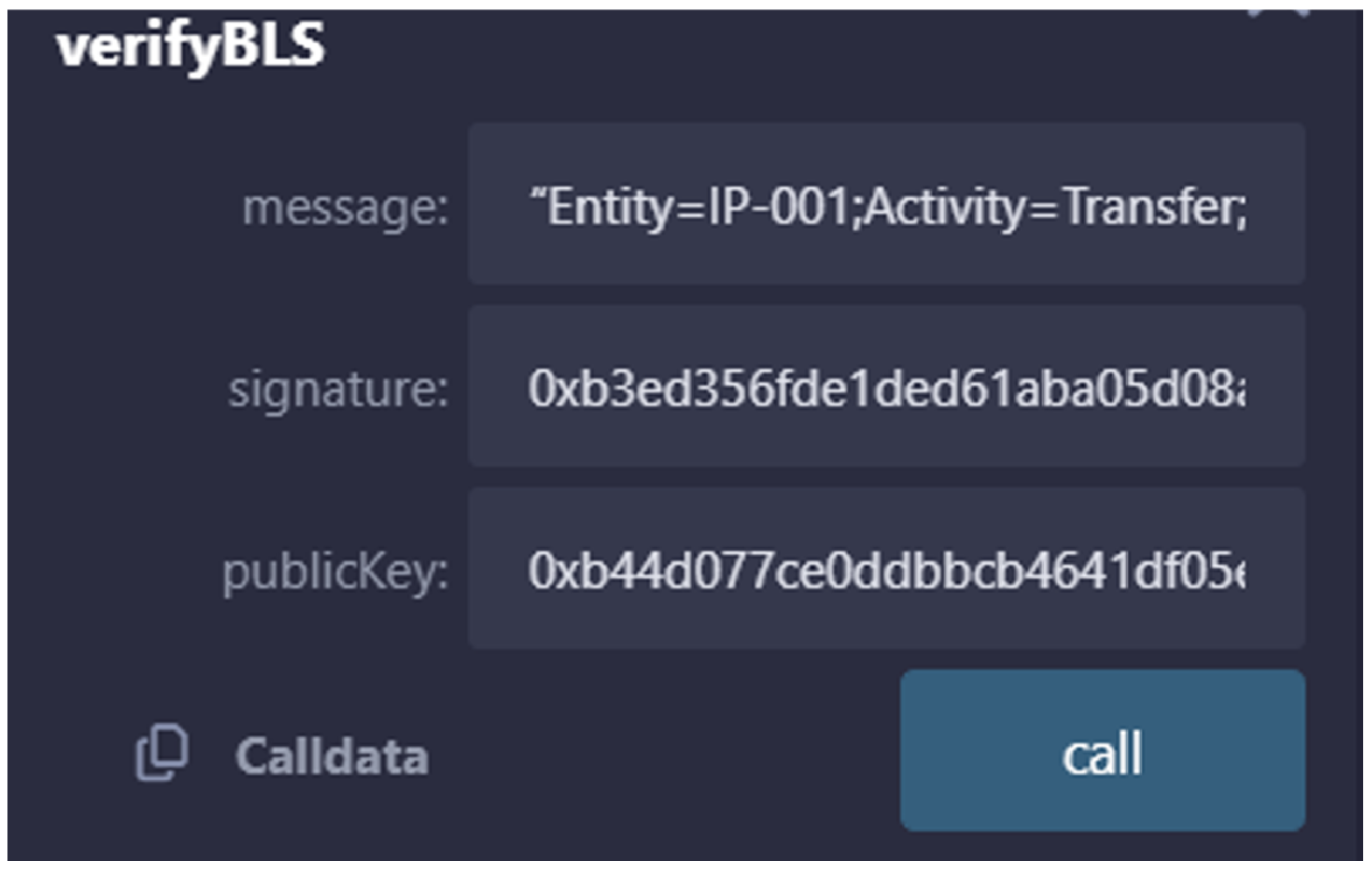
4.3. Experimental Tests
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Yu, J.; Zhang, X. Blockchain technology and the modernization of intellectual property rights registration system. Intellect. Prop. 2020, 8, 59–67. [Google Scholar] [CrossRef]
- Zhu, C.; Xu, D.; Ren, N.; Cui, H.; Zhao, Y. Blockchain combined with digital watermarking for geographic data transaction deposit and copyright protection model. J. Surv. Mapp. 2021, 50, 1694–1704. [Google Scholar]
- Xu, J.; Cui, H.; Jiang, C.; Jiang, Y. Research on multi-blockchain management and cross-chain query method for power user information. Electr. Meas. Instrum. 2024, 61, 32–38. [Google Scholar] [CrossRef]
- Liu, X.; Hu, X.; Xu, G.; Chen, X. Inadvertent transmission protocol for blockchain data confidential query. Comput. Eng. 2022, 48, 13–20. [Google Scholar] [CrossRef]
- Wu, Q.; Hu, W. Design of mobile authentication protocol based on SM2 algorithm and blockchain. J. Netw. Inf. Secur. 2018, 4, 60–65. [Google Scholar]
- Fan, S.; Song, B.; Dong, X.; Han, T. Research and design of drug traceability tracking program based on blockchain. J. Chengdu Inf. Eng. Univ. 2019, 34, 267–273. [Google Scholar] [CrossRef]
- Feng, G.; Hu, J.; Chen, M. Research and realization of aquatic products trading traceability system based on blockchain. Fish. Mod. 2022, 49, 44–60+71. [Google Scholar] [CrossRef]
- Liu, P.; Deng, C.; Wang, D. Research on Power Supply Traceability Mode Based on Blockchain. In Proceedings of the 2022 2nd International Conference on Computer Science and Blockchain (CCSB), Wuhan, China, 28–30 October 2022; pp. 58–61. [Google Scholar] [CrossRef]
- Hou, D.; Zhang, Y.; Li, S.; Tian, D. Aeronautical equipment quality traceability system based on blockchain technology. J. Nanjing Univ. Aeronaut. Astronaut. 2024, 56, 731–740. [Google Scholar] [CrossRef]
- Feng, Z.; Du, B.; Yu, Z.; Mou, S. Research on blockchain-driven input strategy of new energy vehicle power battery recycling and traceability technology. China Manag. Sci. 2024, 1–14. [Google Scholar] [CrossRef]
- Chen, S.; Zhou, L.; Fan, Z. Research on the construction of agricultural product quality and safety traceability platform based on blockchain technology. In Proceedings of the 2021 International Conference on Computer, Blockchain and Financial Development (CBFD), Nanjing, China, 23–25 April 2021; pp. 319–323. [Google Scholar] [CrossRef]
- Zhang, J.; Tang, H.; Liu, X. Research on multi-chain traceability system of agricultural products based on blockchain and IPFS. Chin. J. Agric. Mech. Chem. 2024, 45, 127–134. [Google Scholar] [CrossRef]
- Liu, H.; Dong, J.; Ge, S. Traceability System for Rare Chinese Herbal Medicines Based on Blockchain Structure. In Proceedings of the 2021 3rd International Conference on Artificial Intelligence and Advanced Manufacture (AIAM), Manchester, UK, 23–25 October 2021; pp. 382–385. [Google Scholar] [CrossRef]
- Guo, S. Blockchain-based traceability system for trading pre-made food products. In Proceedings of the 2022 2nd International Conference on Computer Science and Blockchain (CCSB), Wuhan, China, 28–30 October 2022; pp. 7–10. [Google Scholar] [CrossRef]
- Sun, Y.; Zhang, F.; Xia, W.; Chen, Y. Application Research on Blockchain-based Steel Structure Traceability Management. In Proceedings of the 2020 2nd International Conference on Machine Learning, Big Data and Business Intelligence (MLBDBI), Taiyuan, China, 23–25 October 2020; pp. 1–4. [Google Scholar] [CrossRef]
- Zhang, Y.; Jin, M.; Zheng, G.; Li, H. Design and Application of Product Traceability Blockchain-based Platform. In Proceedings of the 2020 3rd International Conference on Smart BlockChain (SmartBlock), Zhengzhou, China, 23–25 October 2020; pp. 125–131. [Google Scholar] [CrossRef]
- Rao, K.S.; Vanathi, A.; Andiran, V. Using Blockchain Technology to Improve Drug Traceability in the Healthcare Supply Chain. In Proceedings of the 2023 3rd International Conference on Innovative Mechanisms for Industry Applications (ICIMIA), Bengaluru, India, 21–23 December 2023; pp. 217–223. [Google Scholar] [CrossRef]
- Liu, S.; Liu, C.; Zhang, R.; Wang, J. Research on organic rice traceability based on blockchain smart contract. Chin. J. Agric. Mech. Chem. 2024, 45, 217–222+251. [Google Scholar] [CrossRef]
- Boldyreva, A. Threshold Signatures, Multisignatures and Blind Signatures Based on the Gap-Diffie-Hellman-Group Signature Scheme. In Public Key Cryptography—PKC 2003; Springer: Berlin/Heidelberg, Germany, 2003. [Google Scholar]
- Zhang, L.; Chen, D.; Zhang, E.; Jiang, S.; Li, G. Design and realization of tea traceability information supervision system based on blockchain multi-chain architecture. Chin. J. Agric. Mech. Chem. 2025, 46, 171–177. [Google Scholar] [CrossRef]
- Huang, R.; Yang, W.; Song, Z. A trusted distributed industrial data governance scheme based on blockchain. J. Zhejiang Univ. (Eng. Ed.) 2025, 59, 269–277. [Google Scholar] [CrossRef]


| Intellectual Property Transaction Information | PROV Data Model Elements | Corresponding Description |
|---|---|---|
| Intellectual property entities (e.g., patents, copyrights, etc.) | Entity | Intellectual property rights themselves are represented in the PROV model as entities. For example, information such as the number, description, time of creation, and holder of a patent can be considered as entities. |
| IP creators (creators, inventors) and IP holders (e.g., companies or individuals) | Agent | The creator or inventor of intellectual property is the agent who performs the creation activity and participates in the process of generating intellectual property as the relevant agent. The holder of the intellectual property rights acts as an agent in the transaction and may be an individual, a business, or another organization. |
| Creation, trade, and use | Activity | Describes the flow of activities of IP entities in different scenarios, including the creation of property rights, the trading of property rights, and the use of property rights. |
| Parties to the transaction (e.g., buyer, seller, agent) | Agent | In an IP transaction, buyers, sellers, agents, etc. can act as agents, executing the transaction activities and associating with the corresponding IP entities. |
| Role | Duty | Trust Assumptions |
|---|---|---|
| Creator | Generate digital artwork metadata to initiate the initial signature process. | Assume a trusted entity, but use authentication (such as a digital certificate) to prevent identity forgery. |
| Validators | Participate in distributed key generation (DKG); validate and sign transactions or usage records. | The nodes may be partially Byzantine (malicious), but the total number does not exceed the threshold t − 1 |
| Platform Auditor | Review the legitimacy of metadata (e.g., copyright ownership, content compliance) and participate in multi-party signatures. | It needs to be elected through an on-chain governance mechanism, assuming that its behavior is subject to economic staking (such as staking). |
| Buyers or consumers | Buy or use digital artwork, verify historical signatures, and initiate transaction signatures. | It is possible that a rational attacker (attempting to tamper with ownership) relies on cryptography to constrain its behavior. |
| Auditors | Independently verify PROV chain integrity and detect anomalous behavior. | There is no need to hold a key, only need to read the on-chain data, assuming that it has compliance review capabilities. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, Z.; Feng, W.; Huang, M.; Feng, S.; Mo, S.; Li, Y. Blockchain-Based Information Security Protection Mechanism for the Traceability of Intellectual Property Transactions. Sensors 2025, 25, 3064. https://doi.org/10.3390/s25103064
Wang Z, Feng W, Huang M, Feng S, Mo S, Li Y. Blockchain-Based Information Security Protection Mechanism for the Traceability of Intellectual Property Transactions. Sensors. 2025; 25(10):3064. https://doi.org/10.3390/s25103064
Chicago/Turabian StyleWang, Zheng, Wenlong Feng, Mengxing Huang, Siling Feng, Shilong Mo, and Yunhong Li. 2025. "Blockchain-Based Information Security Protection Mechanism for the Traceability of Intellectual Property Transactions" Sensors 25, no. 10: 3064. https://doi.org/10.3390/s25103064
APA StyleWang, Z., Feng, W., Huang, M., Feng, S., Mo, S., & Li, Y. (2025). Blockchain-Based Information Security Protection Mechanism for the Traceability of Intellectual Property Transactions. Sensors, 25(10), 3064. https://doi.org/10.3390/s25103064





