1. Introduction
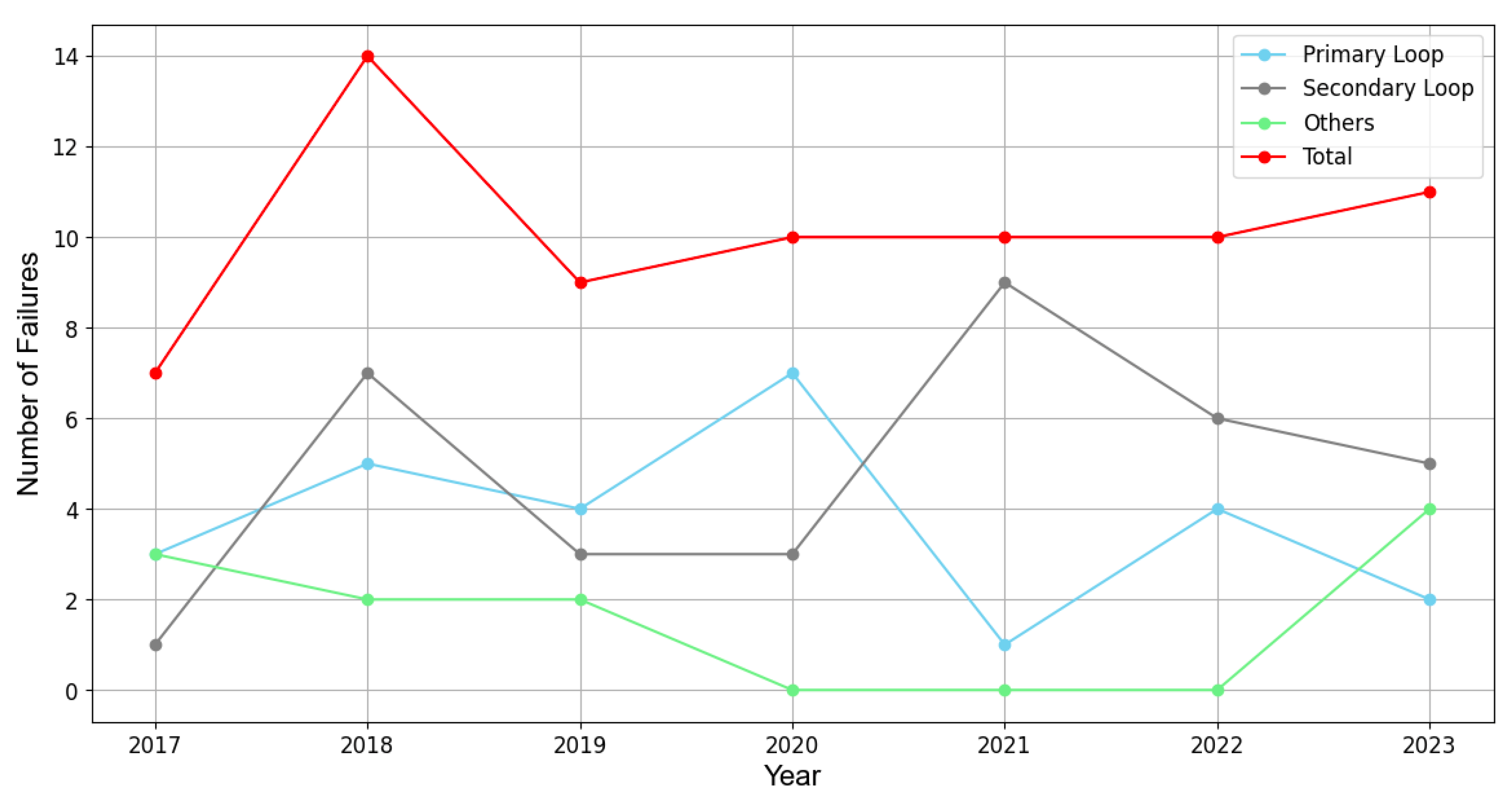
Figure 1 illustrates the chronological progression of nuclear power plant (NPP) failures from 2017 to 2023 in South Korea [
1]. It is observed that the total number of failures (represented by red dots) incurred from different sources shows a notable increase over time. With regard to managing NPPs, the advent of remote wireless diagnosis systems marks a pivotal shift towards enhancing human safety and operational efficiency. These systems are indispensable in addressing the challenges posed by aging infrastructure, where mechanical failures and radiation leakage risks are exacerbated by material degradation in high-temperature and radiation-exposed environments. This paradigm shift focuses attention on the necessity for secure and reliable communication networks, particularly tailored to the unique conditions prevailing within NPPs. Prominent applicable wireless technologies include Bluetooth, Zigbee, Wi-Fi, LoRa, WirelessHART, Terahertz, infrared (IR) communication, and more [
2]. Among these technologies, IR, the electromagnetic spectrum of which falls between the red end of visible light and microwaves, offers distinct advantages in the context of monitoring nuclear steam supply systems [
3]. While traditional wireless technologies offer a broad spectrum of solutions, the peculiar requirements of NPP environments—characterized by stringent regulatory standards and the critical need for minimal electromagnetic interference—demand a more focused approach. The hazard detection system using sensor networks in NPPs requires the minimum power possible to collect periodic data from thousands of sensors. In addition to this unusual type of sensor network environment, the system should comply with the regulations for radio-frequency interference (RFI) and electromagnetic interference (EMI) restrictions [
4]. IR communication, with its inherent advantages of low power consumption and reduced electromagnetic interference, offers a compelling solution for such specialized applications. Taking that into consideration, the role of IR communication emerges as exceptionally significant.
However, the application of IR communication in NPPs is not without its challenges. The primary concern revolves around securing data transmission, considering the severe consequences of cyber-attacks on such vital infrastructure. Cyber-attacks, such as the Nordex wind turbine system shutdown in Germany in 2022, the Ukrainian power grid hack in 2015, and the Stuxnet worm in Iran, illustrate the potential threat of security breaches that can lead to unexpected termination of processes, malicious stealing of resources, and drastic damage to power-generating machines [
5,
6]. Recent incidents of cyber-attacks on power facilities globally accentuate the vulnerability of energy systems to security breaches, thereby amplifying the need for robust security measures. In light of this, our study presents an advanced encryption method specifically designed for IR sensor networks within NPP loops responsible for transferring heat and steam.
To address these challenges, this paper proposes a novel encryption strategy that employs a custom-designed S-box to secure data transmission from IR sensors to gateway nodes within NPPs. This strategy is developed to meet the unique security requirements of NPP operational loops, focusing on minimizing power consumption while maximizing data protection against cyber threats. By implementing this targeted encryption approach, we aim to enhance the security framework for IR communication in NPPs, ensuring the integrity and reliability of critical data transmission. This effort is expected to serve as a model for implementing similar security measures across various critical infrastructure sectors, thereby advancing the conversation on cybersecurity strategies in the face of growing digital threats.
2. Infrared Communication
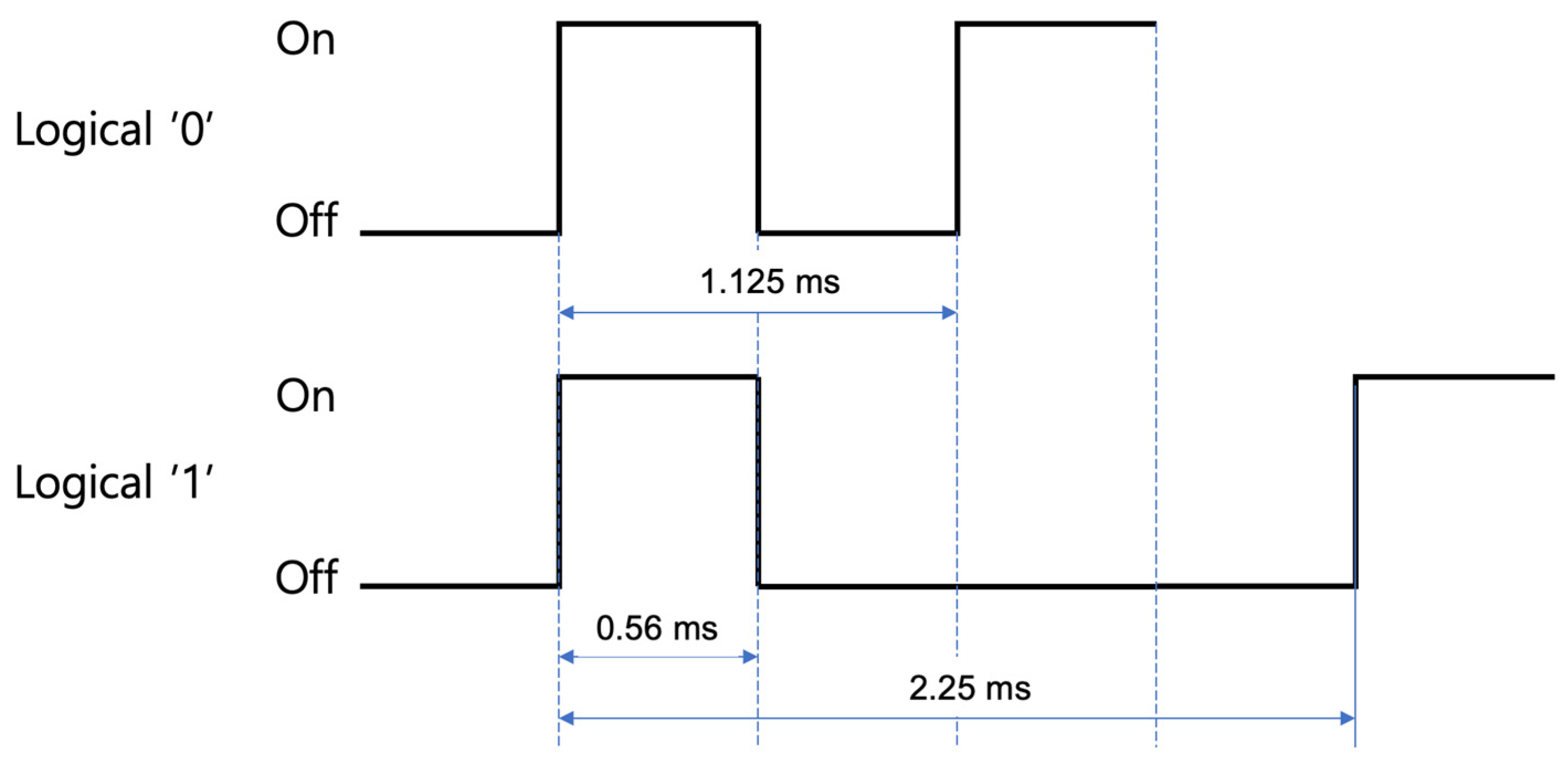
The most commonly used protocol in IR communication is the NEC protocol, which is regarded as the de facto standard for IR data transactions [
7]. NEC, a leading electronics company, has contributed significantly to establishing this protocol. In the NEC protocol, bit pattern encoding is governed by the spacing between pulses, with each bit’s representation being composed of a combination of pulse and space. The pulse operates at a 38 kHz frequency, leading to a fundamental period of 0.56 ms. A logical ‘1’—indicating a True condition—is represented by a structured sequence: pulse followed by long (three consecutive) spaces. This sequence occupies a total duration of 2.25 ms, as depicted in
Figure 2. Conversely, a logical ‘0’, signifying a False condition, is denoted by a sequence of pulse followed by short (one single) space, resulting in an overall period of 1.125 ms, also illustrated in
Figure 2.
When the message transmission starts, the following protocol is executed in order to establish the communication (see
Figure 3). First, a 9 ms leading pulse burst is transmitted, followed by 4.5 ms space, then comes the next 8-bit slave device address for 27 ms duration, followed by its complemented values during 27 ms, then the 8-bit command (data) followed by the same length of duplicated values in complementary forms during 27 ms. The communication ends with the final 562.5 ms pulse. As shown in
Figure 3, the data are transmitted in the order of least significant bits (LSBs) through most significant bits (MSBs).
4. Evaluations
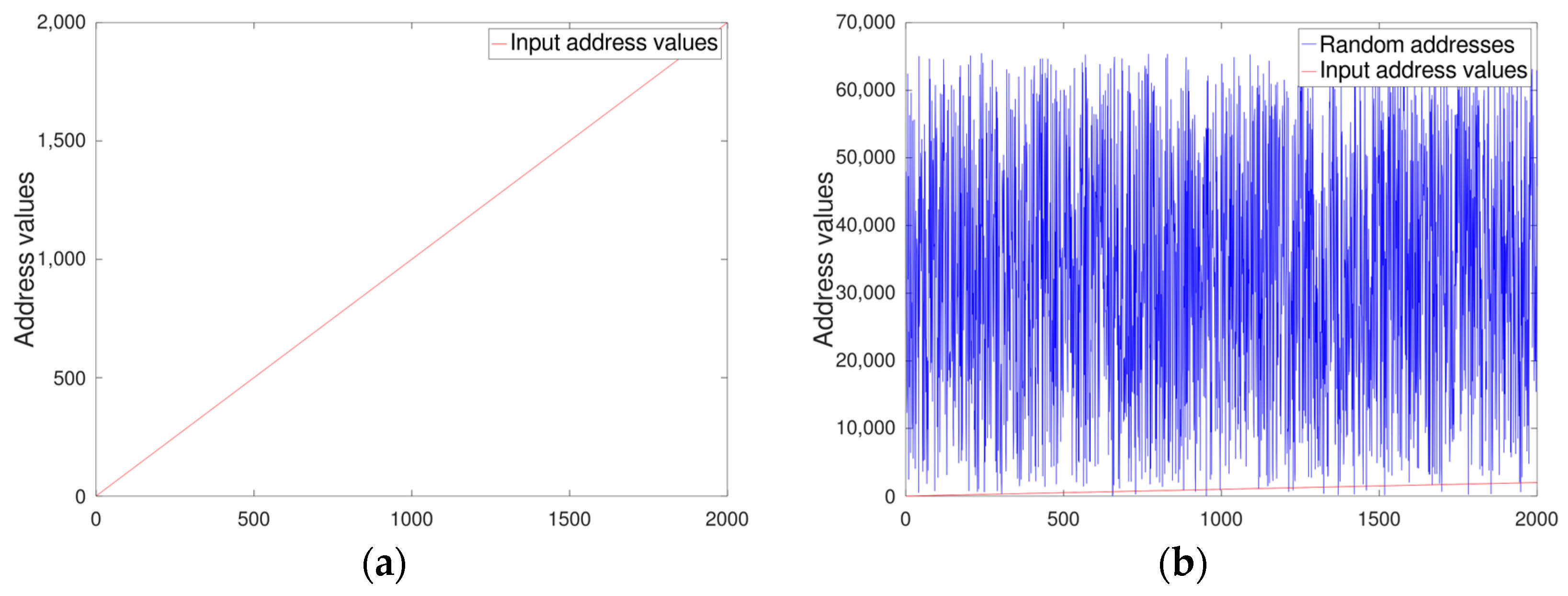
Figure 8 shows the hypothetically expected outcome of our proposed random address generator. In this figure, we used the randi() function from the Octave tool library to obtain randomness while applying linearly incrementing 2000 test address values ranging from 0 to 1999. In
Figure 8, the left-hand side figure depicts the straight line representing the linear address values. The right-hand side figure compares the linear values with the generated random values for clarity. We measured the strength of randomness by counting the number of duplicated address values. Since the randi() function generates different random numbers each time it is called, we repeated the process of generating 2000 random addresses 2000 times to ensure accuracy and consistency. The mean number of redundant address values was 30.492, and although the exact value is trivial, we can regard the number as greater than 30.
In the experiment, the original dataset comprises 2000 NIC address samples, each represented as a 24-bit integer. These integers represent a wide range of values, indicating a diverse dataset suitable for evaluating four proposed algorithm variations. Specifically, the dataset spans from a minimum value of 11,257 to a maximum of 16,758,366, with an average value of approximately 8,405,759.82. This broad distribution of values provides a robust basis for assessing the effectiveness and security of the proposed encryption techniques, ensuring a comprehensive evaluation across a variety of data characteristics.
To assess the cryptographic strength of the proposed algorithms, an entropy analysis was conducted on the datasets generated by each algorithm. Entropy, a statistical measure of randomness that quantifies the uncertainty involved in predicting the value of a random variable, serves as a fundamental metric in evaluating the effectiveness and security of cryptographic systems. A higher entropy value indicates a higher level of unpredictability and randomness, thereby implying stronger encryption.
The entropy H of a dataset can be calculated using Formula (3):
where
p(
xi) is the probability of occurrence of each unique value
xi in the dataset. This method involves counting the occurrences of each unique encrypted value, calculating the probability of each unique value, and then applying the entropy formula to compute the overall entropy of the dataset [
22].
4.1. XOR-AES Variation
Our first encrypted dataset ra_dec_XOR_AES exhibits a broad range of values, from a minimum of 5 to a maximum of 65,503, with an average value calculated at 32,783.60. This distribution suggests a uniform dispersion of encrypted values within the feasible range of 16-bit integers, which potentially indicates a level of randomness and unpredictability in the encrypted data. The comprehensive span of values, nearing the limits of the 16-bit integer capacity, hints at a deliberate utilization of the available numeric space, possibly contributing to the cryptographic strength of the algorithm. The mean value, closely aligning with the midpoint of the 16-bit integer range, further supports the hypothesis of an evenly distributed output, a desirable characteristic in encryption to mitigate patterns or biases that could be exploited for cryptanalysis. The entropy analysis of the ra_dec_XOR_AES encryption algorithm revealed an entropy value of 10.9368 bits. This indicates a high degree of randomness within the encrypted outputs, showcasing the algorithm’s effective obfuscation capabilities. The relatively high entropy value suggests that the ra_dec_XOR_AES algorithm provides robust security features, minimizing potential vulnerabilities to pattern-based attacks and enhancing the unpredictability of the encrypted data.
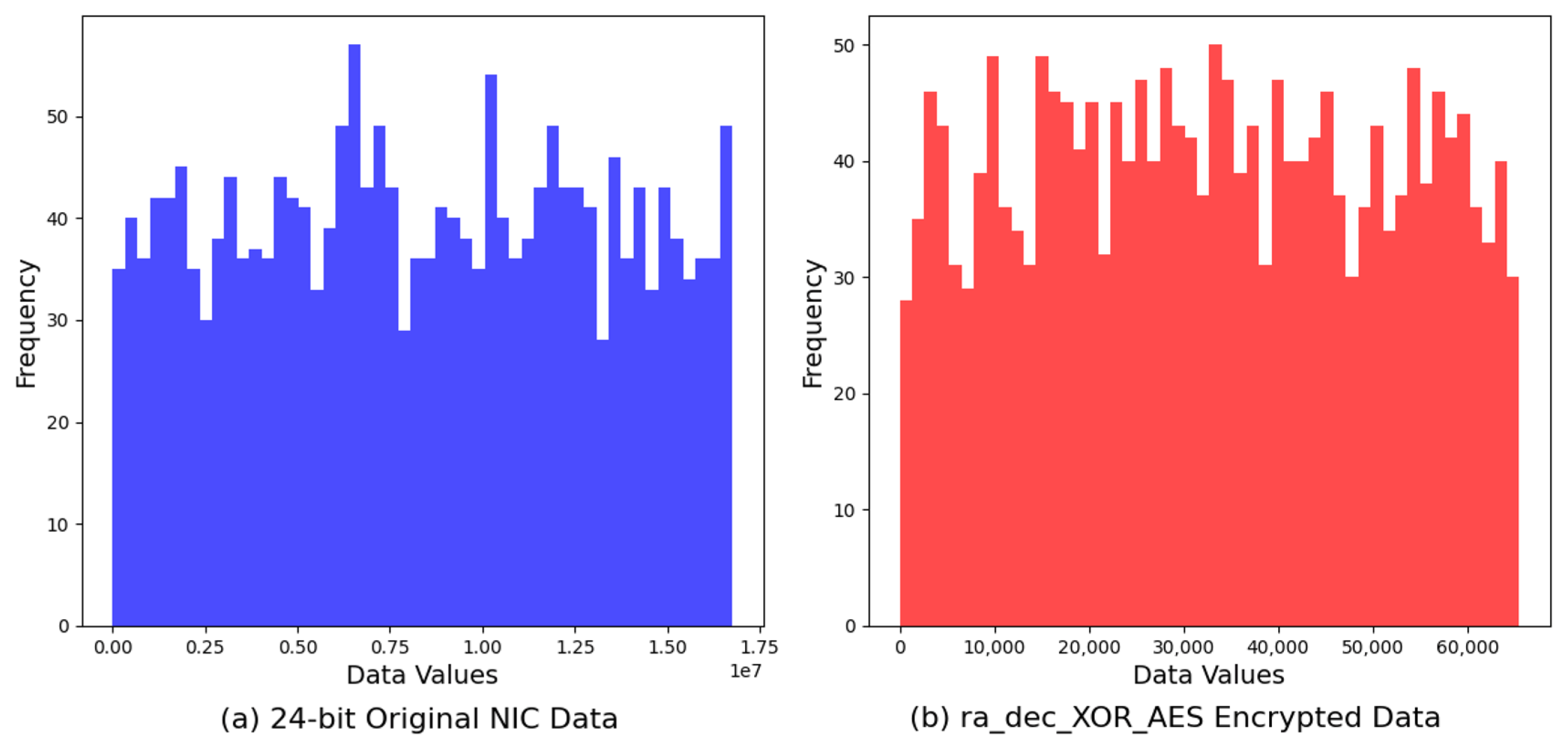
For visualization, we compared the histogram of the original 24-bit NIC data against that of the encrypted output generated by the
ra_dec_XOR_AES algorithm.
Figure 9 reveals the effectiveness of the encryption process in obfuscating the original dataset’s distribution. The original data’s histogram, characterized by its distinct pattern and distribution, contrasts sharply with the more uniform and dispersed histogram of the encrypted data. This transformation highlights the
ra_dec_XOR_AES algorithm’s capability to enhance data security by significantly increasing randomness and reducing predictability.
4.2. XOR-CCM Variation
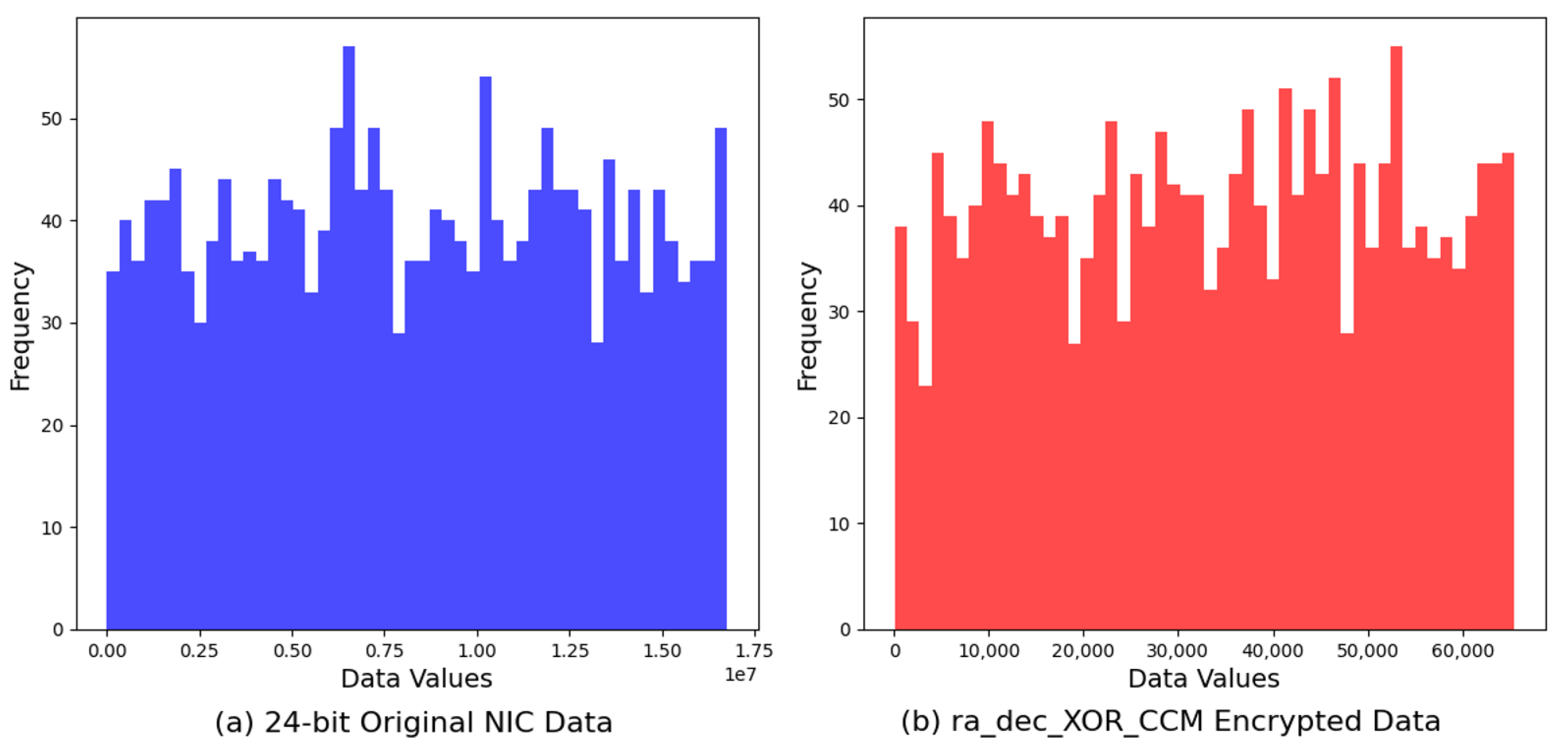
ra_dec_XOR_CCM reveals from a minimum of 52 to a maximum of 65,511, with the mean value situated at 33,444.17. This range of values demonstrates the algorithm’s proficient employment of the 16-bit numeric field, ensuring comprehensive coverage that approaches the upper limits of possible values. The distribution pattern of the ra_dec_XOR_CCM dataset signifies a commendable degree of randomness, with the encrypted values spreading across the vast majority of the available space. This dispersion is indicative of the algorithm’s strategic encryption methodology, aimed at maximizing the unpredictability of the output. The average value, slightly elevated towards the upper end of the range, suggests a nuanced approach in the encryption process, potentially contributing to a higher level of security against cryptographic breaches. Furthermore, the close proximity of the maximum value to the theoretical limit of 16-bit integers underscores the algorithm’s ability to exploit the numeric space fully, enhancing the encrypted data’s resistance to pattern recognition and cryptanalytic attacks. The balanced and widespread distribution of values across the spectrum echoes the algorithm’s effectiveness in obfuscating the original data’s characteristics, a crucial aspect in maintaining data confidentiality. The entropy value associated with the ra_dec_XOR_CCM encryption algorithm was determined to be 10.9348 bits. This demonstrates the algorithm’s proficiency in ensuring a high level of randomness in its encrypted outputs, closely rivaling the performance of the ra_dec_hash_CCM algorithm. The ra_dec_XOR_CCM algorithm’s encryption outputs are characterized by a strong dispersal of values, indicating a robust defense mechanism against cryptographic breaches through pattern detection.
Further, the comparison between the original data and the
ra_dec_XOR_CCM encrypted output through their histograms provides insight into the encryption’s impact on data randomness. The
ra_dec_XOR_CCM algorithm alters the data distribution to achieve a more homogeneous spread of values, as opposed to the original data’s clustered distribution. This analysis accentuates the algorithm’s success in augmenting data unpredictability, a crucial attribute in safeguarding information from unauthorized access and analysis (
Figure 10).
4.3. Hash-AES Variation
The third, ra_dec_hash_AES, showed a notable range of values, extending from a minimum of 60 to a maximum of 65,510, with an average value intricately positioned at 32,430.66. This distribution pattern underscores a well-distributed span of encrypted values, suggesting an effective dispersion across the entire 16-bit numeric spectrum. The examination of this dataset highlights the algorithm’s capability to exploit the available numeric space efficiently, thereby potentially enhancing the cryptographic strength through the promotion of randomness and unpredictability within the encrypted outputs. The proximity of the average value to the midpoint of the 16-bit range, coupled with the broad spread of values, supports the premise of an equitable and uniform distribution. For the ra_dec_hash_AES encryption algorithm, the computed entropy was 10.9288 bits. While this value reflects a substantial level of data randomness, it is marginally lower compared to the ra_dec_XOR_AES algorithm. This slight difference in entropy indicates a nuanced variation in the algorithm’s ability to distribute encrypted values across the available data space, which may influence the algorithm’s resistance to cryptanalytic attacks, albeit to a minor extent.
The analysis of our examination extends to the
ra_dec_hash_AES encrypted data, compared alongside the original dataset’s histogram. The graphical representation illustrates a marked transformation in data distribution, from the original’s specific patterns to a flattened, more evenly spread distribution in the encrypted output. This comparison underscores the
ra_dec_hash_AES algorithm’s proficiency in diluting original data characteristics, thereby fortifying the encryption strength against statistical analysis and pattern recognition (
Figure 11).
4.4. Hash-CCM Variation
The final dataset, ra_dec_hash_CCM, exhibited a value range from a minimum of 3 to a maximum of 65,386, with the average encrypted value calculated to be 33,221.89. This analysis underscores the algorithm’s effective utilization of the 16-bit integer space, highlighting a substantial dispersion of values that encompasses nearly the entire potential range. The distribution characteristics observed in the ra_dec_hash_CCM dataset indicate a balanced and widespread allocation of encrypted values, suggesting a strategic approach to maximize randomness and reduce predictability within the encrypted data. Notably, the slight shift in the average value towards the higher end of the range, compared to previous algorithms analyzed, may reflect the algorithm’s unique encryption mechanism or data transformation strategy, which in turn could influence its resilience to cryptographic analysis. This dataset’s broad span of values and the near-central positioning of the average value illustrate the algorithm’s capacity to generate encrypted data that is evenly distributed across the available numeric spectrum. The ra_dec_hash_CCM encryption algorithm exhibited the highest entropy value among the evaluated algorithms, at 10.9438 bits. This superior entropy level underscores the algorithm’s exceptional performance in generating encrypted outputs with maximum randomness. Such a high degree of unpredictability significantly contributes to the algorithm’s cryptographic strength, providing enhanced security against attempts to decipher or predict the encrypted data.
Lastly, the
ra_dec_hash_CCM algorithm’s encrypted data, when compared to the original, demonstrates a notable increase in distribution uniformity. The encrypted data’s histogram showcases a broad spread across the value range, diverging from the original data’s concentrated peaks. This evident dispersion serves as a testament to the
ra_dec_hash_CCM algorithm’s effectiveness in obscuring data patterns, thereby elevating the security level and complicating potential decryption efforts without the key (
Figure 12).
Lastly, the ra_dec_hash_CCM algorithm’s encrypted data, when compared to the original, demonstrate a notable increase in distribution uniformity. The encrypted data’s histogram showcases a broad spread across the value range, diverging from the original data’s concentrated peaks. This evident dispersion serves as a testament to the ra_dec_hash_CCM algorithm’s effectiveness in obscuring data patterns, thereby elevating the security level and complicating potential decryption efforts without the key.
5. Discussion
In our comprehensive evaluation of encryption algorithms, we analyzed the entropy values alongside the incidence of duplicated addresses produced by each algorithm. This analysis aimed to assess the randomness and uniqueness of the encrypted outputs, which are crucial for the overall security and integrity of the encrypted data. To calculate the entropy of each encryption algorithm’s output, we utilized the Shannon entropy formula, which is a measure of the unpredictability or randomness in a set of data. Specifically, the entropy was computed using the formula , as shown in Formula (3). This method provided a quantitative assessment of the data complexity and unpredictability, with higher entropy values indicating greater randomness and, thus, stronger encryption.
Furthermore, we explored the relationship of our entropy calculation methodology with standards set forth by notable organizations such as the National Institute of Standards and Technology (NIST) and the Bundesamt für Sicherheit in der Informationstechnik (BSI) [
23]. Both institutions emphasize the importance of entropy in assessing the strength of cryptographic systems. While our study did not directly apply the specific guidelines or methodologies recommended by NIST or BSI, our approach to entropy measurement aligns with the fundamental principles highlighted by these bodies. They advocate for the quantification of randomness as a critical factor in evaluating the security properties of encryption algorithms. By adhering to the universal principles of entropy calculation, our analysis ensures that the evaluation of encryption algorithms is grounded in well-established cryptographic standards.
The entropy values and the number of duplicated addresses indicative of each algorithm’s performance are shown in
Table 2.
Our entropy analysis revealed that the Hash-CCM algorithm exhibited the highest entropy value at 10.9438 bits, indicating superior randomness in its encryption process compared to the other algorithms. High entropy is indicative of a robust encryption mechanism, as it reflects the unpredictability and complexity of the encrypted data. Furthermore, the number of duplicated addresses serves as an indicator of the uniqueness of the encrypted outputs. A lower incidence of duplicates suggests that the algorithm is more effective in generating distinct encrypted values, thus enhancing the security against potential cryptographic attacks. In this context, the Hash-CCM algorithm demonstrated the lowest number of duplicated addresses, with only 22 occurrences, underscoring its exceptional ability to maintain data uniqueness. Conversely, the Hash-AES algorithm, while still ensuring a high degree of security with an entropy value of 10.9288 bits, showed the highest number of duplicated addresses at 37. This suggests that, despite its effectiveness in randomizing data, there may be a slight reduction in the uniqueness of its outputs compared to Hash-CCM. The XOR-based algorithms, XOR-AES and XOR-CCM, displayed closely related entropy values and numbers of duplicated addresses, positioning them as reliable options for secure data encryption. However, they did not achieve the same level of performance in terms of both randomness and uniqueness as observed in the Hash-CCM algorithm.
Building upon the foundational analysis of entropy and duplicated address incidences, our further investigation through bit pattern change and correlation analyses has introduced new dimensions to our evaluation, particularly highlighting the efficacy of the Hash-CCM algorithm when combined with a self-reconfiguring approach and the CCM S-box. This combination not only adheres to the principles of robust encryption by enhancing data randomness and minimizing predictability but also surpasses the performance achieved with the conventional AES S-box usage.
The bit pattern change analysis, detailing the average frequency of bit alterations across the encryption process, and the correlation analysis, quantifying the degree of linear relationship between original and encrypted datasets, collectively affirm the superior encryption quality of Hash-CCM. These analyses demonstrate that Hash-CCM, especially when employing a self-reconfiguring system alongside the CCM S-box, introduces a higher level of data obfuscation compared to its counterparts. This assertion is backed by the statistical evidence presented earlier, where Hash-CCM not only yielded the highest entropy but also exhibited the lowest incidence of duplicated addresses, thus asserting its dominance in producing unique and unpredictable encrypted outputs.
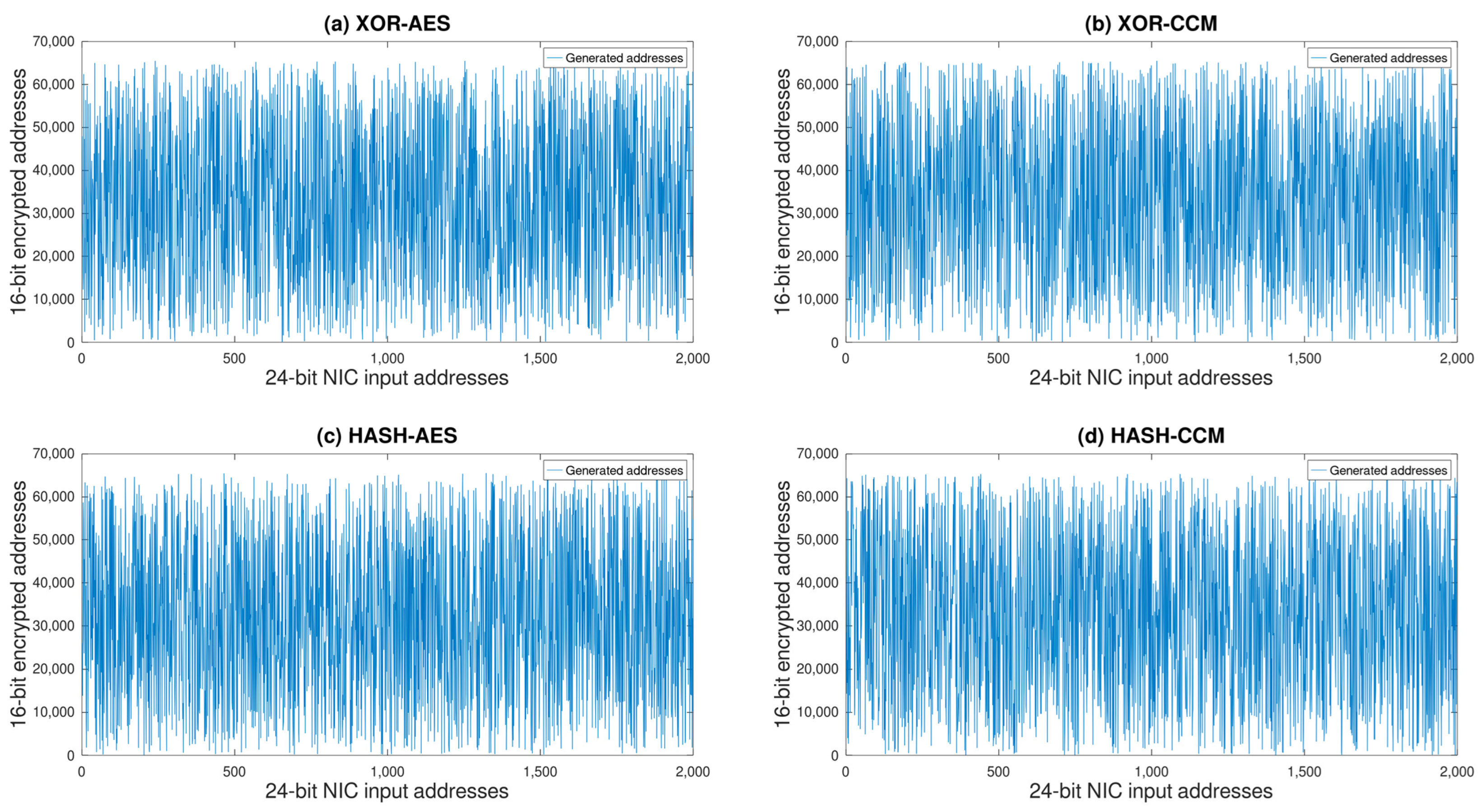
Figure 13 presents the distribution of 16-bit values generated by the encryption of 2000 samples of 24-bit NIC addresses using four distinct encryption algorithms: (a) XOR-AES, (b) XOR-CCM, (c) Hash-AES, and (d) Hash-CCM. Each subplot illustrates the variation in encrypted outputs, providing a visual representation of the algorithms’ effectiveness in producing a wide spread of values across the 16-bit space.
Upon thorough examination, which includes assessments of entropy values, incidences of duplicated addresses, bit pattern change frequencies, and correlation analyses, it is clear that the adoption of self-reconfiguring mechanisms alongside the CCM S-box in the Hash-CCM encryption algorithm surpasses the conventional cryptographic security benchmarks, notably outperforming the traditional AES S-box approach. This innovative approach makes Hash-CCM an exemplary model for encryption methodologies, particularly critical for enhancing IR communication security in specialized environments like remote diagnostics of NPPs.
The findings of our research emphasize the significance of evolving encryption strategies to strengthen communication security within critical infrastructure settings. The superior performance of Hash-CCM, characterized by its high entropy values, minimal duplicated addresses, significant bit pattern changes, and negligible correlation with the original data, renders it an optimal solution for securing IR communications. Such communications are vital for the remote monitoring and diagnostics of nuclear facilities, where data integrity and security cannot be compromised.