Machine Learning and Deep Learning Techniques for Internet of Things Network Anomaly Detection—Current Research Trends
Abstract
1. Introduction
2. Survey Methodology
3. Machine Learning—IoT Network Anomaly Detection
3.1. Anomaly Detection
3.2. Attack-Based Anomaly Detection
| Ref. | Problem Addressed | Dataset | Proposed Solution | Results Obtained | Advantages | Disadvantages | Year |
|---|---|---|---|---|---|---|---|
| [47] | Anomaly detection in the IoT using ML | Time-series data, NSL-KDD | Compared several ML classifiers, such as KNN and DTs | DTs and Linear Discriminant Analysis achieved 80% accuracy with non-time-series data | Both time-series data and non-time-series data used | Small dataset size | 2018 |
| [48] | Detecting anomalies and attacks in IoT networks | Dataset from Kaggle | Compared different ML models in predicting attacks and anomalies on IoT systems | RF and ANN outperformed DT with 99.4% accuracy | Model better and faster than other techniques | Dataset limitations and computational complexity | 2019 |
| [49] | Identifying attacks and anomalies in IoT systems | DS2OS | Proposed a new method for missing data values, and evaluated its effectiveness on real datasets | The accuracy rate was 99.43% with RT and 99.4% with DT in detecting anomalies | Managed missing data values, reduced dataset dimensionality | Needs testing with more datasets | 2020 |
| [50] | Identifying anomalies in the IoT using ML | IoT-23 | Investigated ML models, compared algorithms, and assessed their performance using metrics | RF outperformed others with an accuracy rate of 99.9% | Accurately identified anomalies in network traffic | Needs testing with more datasets other than IoT-23 | 2020 |
| [32] | ML-based anomaly detection | - | Proposed combining supervised and unsupervised algorithms | Showcased different ML models, datasets, and applications | A broad overview of all related topics | In-depth research is needed | 2021 |
| [39] | ML-based anomaly detection IoT networks | DAD and UNSW-NB15 | Used five shallow ML models (NB, LR, AB, RF, and SVM) with the DAD dataset | RF and AB achieved a mean accuracy of 0.9998 | Dataset validated in detecting anomalies with ML | Needs varied datasets and testing with different ML models | 2021 |
| [51] | Anomaly detection in indoor Wi-Fi and IoT devices | UCI Wi-Fi indoor localization dataset | Evaluated ML models and proposed ensemble learning for improved accuracy | Ensemble learning strategy with RF achieved an accuracy of 98% | Precise anomaly detection method for indoor IoT devices | Needs more training data and testing with more ML algorithms | 2021 |
| [52] | Using ML-based models to detect anomalies in the IoT | ToN-IoT and BoT-IoT | Proposed a Hadoop-based framework using KNN, SVM, and NB ML classifiers | Accuracy was 90% with ToN-IoT and 99% with BoT-IoT | High accuracy and low false positive rates | Needs testing with larger datasets and more complex ML algorithms | 2021 |
| [53] | ML-based anomaly detection in the IoT | DS2OS | Assessed memory usage, execution time, and detection accuracy for LR, DT, RF, and GBM | GBM and RF achieved 99.99% accuracy, outperforming others | Minimizes detection error rates and execution time | Requires extensive training data | 2022 |
| [54] | ML-based techniques to identify power consumption anomalies | Private data | Employed ML-based techniques—VAR, Prophet, and LightGBM | LightGBM had the best accuracy with an MAE of 0.282046 | Can help in smart home automation and power system maintenance | Needs more testing with large data | 2022 |
| [55] | Detecting label noise in IDSs with ML models | - | Proposed new framework using Decision Trees and active learning to detect label noise | Reduced noise by 98% | An explainable AI approach that detects a high % of noise | Only achieves binary classification, and uses a limited dataset | 2022 |
| [56] | Identifying anomalous activity in IoT systems with ML | IoT-23 | Evaluated Gradient-Boosting and Extreme Gradient-Boosting (XGBoost) techniques using the IoT-23 dataset | XGBoost had a high accuracy rate of 99.98% | XGBoost can increase IoT system security | Needs more testing on larger and real-world datasets | 2022 |
| [57] | Network intrusions and cyberattacks in the IoT with ML | KDDcup99 | Used BT ML model to test anomalies and compared it to other models (KNN, NN, SVM, etc.) | Model accuracy was 99.79% | Distinguished between 22 different anomalous behaviors | Performed poorly during testing | 2023 |
| [58] | Detecting anomalies and maintaining user privacy with ML | Real-life traffic data from IoT device networks | Proposed an ML model using KNN, LR, and MLP that identifies IoT devices and detects anomalies | Accuracy of 99.5% was achieved with KNN while keeping the device anonymous | Ensures the privacy of users while accurately detecting anomalies | Needs more testing on datasets and in varied networks | 2023 |
| [59] | Anomaly detection in the IoT with ML | CoAP-IoT | Introduced a new CoAP-IoT dataset and validated it using supervised learning | RF, SVM, and DT performed best, with a mean accuracy of 0.9 | Created a new dataset and validated it | Needs more testing using various datasets and real-world IoT systems | 2023 |
| [60] | ML-based IDSs in the IoT | Bot-IoT, MedBIoT, and MQTT-IoT-IDS2020 | Introduced a lightweight framework by testing it with DT, RF, KNN, and XGB ML models | Achieved high classification accuracy with an F1 score of 0.99 across all datasets | Lightweight and efficient, which is suitable for IoT applications | The ML model used does not apply to all IoT sensors | 2023 |
| Ref. | Problem Addressed | Dataset | Proposed Solution | Results Obtained | Advantages | Disadvantages | Year |
|---|---|---|---|---|---|---|---|
| [61] | DDoS attacks in the IoT | PCAP data | Used ML classifiers QDA, SVM, KNN, NV, DT, and RF | DPAE outperformed other models | SDN-based categorizer | Legit traffic misclassified and delays in detection | 2018 |
| [62] | Detecting DDoS attacks in the IoT | Regular DDoS attack traffic data | Five ML classifiers tested with datasets—NN, DT, RF, SVM, KNN | Classifiers achieved an accuracy of more than 0.99. NN achieved the best overall | Accuracy in detecting DDoS attacks | No real-world dataset used | 2018 |
| [63] | DDoS in IIoT scenarios | UNSW NB15 | Proposed federated learning to detect DDoS in the IIoT | Low mitigation response time with high mitigation accuracy | High accuracy and low response time | Needs more tests to implement in real-world IIoT settings | 2020 |
| [64] | Network security in IoT systems | NSL-KDD | Proposed a two-stage hybrid using ML algorithms and a genetic algorithm | Ensemble classifier performed better with 99.8% accuracy | Can reduce cyberattacks and improve security | Needs more testing on actual IoT networks | 2021 |
| [65] | Malicious bot-IoT traffic in IoT networks | Bot-IoT | Proposed a novel metric called CorrAUC based on the AUC metric | The model was effective and achieved 96% accuracy | High accuracy in detecting malicious traffic | Not scalable and needs more training data | 2021 |
| [66] | Identifying intrusions in network activity | CSE-CIC-IDS2018 | Used DT, EF, KNN, and GNB ML models | RF scored the highest F1 score of 89.5% with a precision of 99.3% | Early detection of malicious attacks; efficient and accurate | Needs better parameters and a wider dataset range | 2022 |
| [67] | IoT malware identification | IoT-23, LITNET-2020, and NetML-2020 | Used both ML and DL algorithms on datasets to detect malware on datasets | RF achieved the highest accuracy score of 96% | Exhibits high accuracy in classifying malware | Management of large datasets | 2022 |
| [68] | Mitigating IoT-Botnet attacks using NIDS for the IoT | CICIoT2023 | Proposed solution with ML models to detect Botnet attacks | DT was most accurate with a 99.17% score, followed by RF and KNN | A wide-ranging dataset was used | Computationally complex | 2023 |
| [42] | Detecting DDoS attacks in SDN IoT | Private data | NB, DT, SVM model classifiers used to test attacks in the IoT | DT achieved 98.1% accuracy, outperforming other models | Reduces the impact of DDoS attacks | Enhanced the system | 2023 |
| [69] | Detecting cyberattacks in Industrial IoT (IIoT) scenarios with hybrid ML models | DS2OS | Proposed framework combines different ML models to form an HML | The models scored an accuracy of 99.8% in detecting abnormal traffic | Use of a comprehensive dataset and high accuracy of detection | The framework is computationally heavy | 2023 |
| [70] | Using ML models to prevent security threats in the IoT | - | Proposed the DT model to classify abnormal data | Successful in detecting and classifying abnormal data | Works in maintaining security | No specific accuracy or performance rates are mentioned in the paper | 2023 |
| [71] | Cyberattacks and IDSs in IoT networks | IoT-23 and IoT Network Intrusion | Compared different ML models—RF, DT, NB, MLP, and KNN | RF and DT performed best with an accuracy of 99.9% each | Highly accurate in classifying malicious activity | Needs larger datasets and improved accuracy of the models | 2023 |
| [72] | Detecting DoS attacks with datasets | IoTID20 | Features selected via a GA and CFS trained with KNN, DT, RF, SVM classifiers | DT and RF achieved 100% accuracy with the GA | Used recent and real-time data | Lack of scalability | 2024 |
| [73] | Detecting attacks using ML | Smart Home Testbed, UNSW-NB15, CIFAR-10, Kitsune, Bot-IoT, NSL-KDD | Used NV, RF, DT, and SVM models to detect adversary attacks in the IoT | RF showed the most resilience- accuracy dropped only 21% | Showed innovative detection methods | Lack of a balanced dataset | 2024 |
| [74] | Detection of malware in the IoT | UNSW-NB15 | Used ML models—LR, KNN, DT, ET, RF, and MLP | ET achieved 99.98% accuracy | Used large and diverse dataset | Difficult to detect a zero-day attack | 2024 |
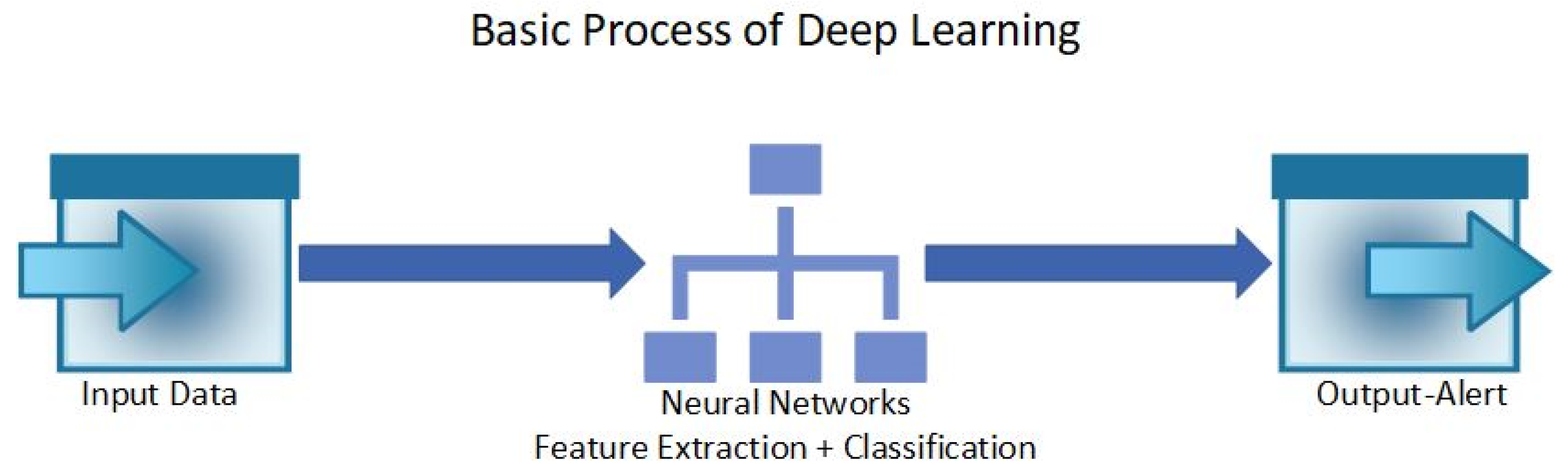
4. Deep Learning—IoT Network Anomaly Detection
4.1. Anomaly Detection
4.2. Attack-Based Anomaly Detection
| Ref. | Problem Addressed | Dataset | Proposed Solution | Results Obtained | Advantages | Disadvantages | Year |
|---|---|---|---|---|---|---|---|
| [81] | DL-based anomaly detection in smart cities | KDD CUP 99 | Deep mitigation learning proposed | The model achieved 99.78% accuracy and outperformed BP and ELM | Can enhance security in urban areas | Classification accuracy reduced during compression | 2019 |
| [82] | DL-based anomaly detection | BoT-IoT | VCDL model proposed | Achieved 99.7% accuracy | Outperformed other models | Class imbalance issues | 2020 |
| [36] | DL-based IDSs in IoT networks | UNSW—NB15, NSL-KDD, UNB ISCX 2012, and KDD CUP 99 | Surveys various DL models in studies—DNN, CNN, RNN, FNN, and more | DNN, FNN, and RNN performed best with 99.7% accuracy | Showcased several DL model results on various datasets | Further study is needed to explore more DL models with other datasets | 2021 |
| [83] | DL-based IDSs | UNSW-15 | DL-based CNN-LSTM model proposed | Achieved an accuracy of 98.43% across all domains | Detected anomalies in resource-constrained domains | Needs more research with more varied datasets | 2021 |
| [84] | Real-time anomaly detection in time-series data | NAB and the Yahoo Webscope | PDAD-SID model proposed to detect anomalies | Outperformed other models like LSTM with an AUC score of 92.6% | Can be applied to various Industry 4.0 applications | Needs testing with more complex time-series data types | 2021 |
| [85] | DL-based anomaly detection in the IoT | BoT-IoT, MQTT-IoT-IDS2020, IoT-23, IoT-DS-1, and IoT-DS-2 | CNN1D, CNN2D, and CNN3D models proposed | All models achieved an accuracy >99% for all datasets | Proposed DL models outperformed other models | Limited datasets and lack of actual testing | 2022 |
| [86] | DL-based IDSs | NSL-KDD and UNSW-NB15 | CNN models proposed to detect anomalies in datasets | The model achieved an average of 99% accuracy on both datasets | Efficient in finding anomalies in IoT networks | Needs more testing with larger and real datasets | 2022 |
| [87] | Heterogeneity of traffic in IoT devices | CIC-IDS2017 and CIC-IDS2018 | Semi-supervised method proposed called SS-Deep-ID | Achieved an accuracy >99% with the datasets | Integrated into fog-enabled IoT networks | Computational overhead is significant | 2022 |
| [88] | SDN and DL for IDSs in IoT | CSE-CIC-IDS2018 | SDN architecture IDSIoT-SDL used with the LSTM DL model | The model had an accuracy of 99.05% and 212 true negatives | High accuracy and low false positive rates | Needs testing with DL models and in real environments | 2022 |
| [76] | DL-enabled anomaly identification | DS2OS | DNN DL-based model proposed | Achieved an accuracy of 99.8% | Accurate and efficient anomaly detection | Needs testing with more datasets and real-world situations | 2022 |
| [89] | Anomaly detection in smart cities | ToN-IoT Telemetry | Compared DL and ML-based models with the dataset | The voting classifier with SMOTE achieved 99.7% accuracy | Compared to many learning models | Needs more testing with more varied datasets | 2022 |
| [90] | False alert detection in IDSs in the IoT | Traffic log | Combined ML and DNN to detect false alerts | DNN with RF had an accuracy of 96.7%, which was higher than other ML models | Used real alert records from traffic log data | Needs testing with more datasets and comparison to other models | 2022 |
| [91] | IDSs in the IIoT | WUSTL-IIOT-2021 | Used DL models with network flow data for an IDS | Achieved a 99% accuracy rating | Successful in handling class imbalance in the dataset | Needs more testing with more varied datasets | 2023 |
| [92] | DL-based IDSs in the IIoT | WUSTL-IIOT-2021 | DL models applied to the dataset to detect anomalies | DeepIIoT achieved >99% accuracy | Higher accuracy than others in the IIoT | Better classification of anomalies could be achieved | 2023 |
| [93] | Interpreting DL decisions with IDSs in the IoT | CICIDS2017 and NSL-KDD | CNN models and a hybrid CNN model with LSTM and Autoencoder | LSTM with 1D-CNN showed 98.02% accuracy with CICIDS2017 | Thorough study of CNNs and other DL-models | Needs more varied datasets, model optimization | 2023 |
| [94] | Detect anomalies in IoT data using DL techniques | SWaT (Secure Water Treatment) | Compared TCN, LSTM, BI-LSTM, and CuDNN-LSTM on SWaT | The average RMSE of CuDNN-LSTM was 0.042, with more time, and TCN was 0.161, with less time | Effective in detecting anomalies | Needs testing with different datasets | 2023 |
| [95] | Anomaly detection in IDSs with DL | ToN_IoT | Implemented deep SHAP with the CNN model | Achieved accuracy of 99.15% and F1 score of 98.83% | Increased accuracy and F1 score than previous SHAP | SHAP is computationally heavy and costly | 2023 |
| [96] | Anomaly detection with DL and ML | UNSW-NB15 | Proposed two-tier classification with GBC and CNNs | Achieved an accuracy of 99.85% | Employs ML and DL collaboration | Needs further validation in a real-world setting | 2023 |
| [97] | Anomaly detection by federated DL | UNSW-NB15 | FDQN used on the dataset to detect anomalies | Performed better in resource usage and detection accuracy | Scalable, versatile, and outperformed other models | The exact values of metrics are not mentioned | 2023 |
| [98] | IDSs in the IoT in Industry 4.0 applications | KDD99 | Combined a CNN with LSTM to form C2-LSTM | Achieved high accuracy, precision, recall, and AUC score | Extracted temporal and spatial features separately | An old dataset was used. Testing is needed with a newer dataset | 2023 |
| [99] | IDSs in the IoT with DL-based models | ToN_IoT, CICIDS2017, and SWaT | Proposed a stacking ensemble of DL models named DIS-IoT | Accuracy score with ToN_IoT was 99.6%, with CICIDS2017 was 98.7%, and with SWaT was 99.7% | Outperformed other models in all metrics | Needs testing with real IoT devices | 2024 |
| Ref. | Problem Addressed | Dataset | Proposed Solution | Results Obtained | Advantages | Disadvantages | Year |
|---|---|---|---|---|---|---|---|
| [100] | DL-based cyberattack detection | NSL-KDD | DNN proposed | Accuracy score of 99.2% with a two-class model | Improved detection of cyberattacks | Longer training time and needs a large dataset | 2018 |
| [101] | IDSs for attack detection | KDD99 | RBM employed for detection | A precision rate of 94% was achieved | The ability of DL models to detect an attack | Comprehensive results not mentioned | 2018 |
| [102] | Detecting malicious activity in the IoT with DL | UNSW-NB15 and NSL-KDD99 | Four DL models were used—CNN, DNN, MLP, and Autoencoder | DNN outperformed others with an accuracy of 99.24% | High accuracy and F1 results achieved | Complex model and computationally heavy | 2019 |
| [103] | Botnet and phishing attacks in the IoT | PhishTan, OpenPhish, Curlie | LSTM neural network proposed | Accuracy with botnet attack was 94.8%; accuracy with phishing was 94.3% | Integrated CNN and LSTM models | Complex to implement in a real environment | 2020 |
| [104] | Identifying attacks in the IoT | IoT-23 | Hybrid DL model of CNN and LSTM | Achieved a detection accuracy of 96% | Improved accuracy and efficiency | Needs testing with more datasets | 2021 |
| [105] | Detecting DDoS and DoS attacks in the IoT | Collected data and N-BaIoT | DeL-IoT deep ensemble learning model | Outperformed ML methods with a 99.8% detection rate | Provides accuracy and scalability | More tests are needed with varied datasets | 2021 |
| [106] | Brute-force attacks in the IoT | MQTT-IoT-IDS2020 | Featured bi-flow and uni-flow DL-based models | The bi-flow feature had 99.6% accuracy and the uni-flow feature had 99.7% accuracy | High accuracy in detection | Needs more datasets for testing | 2023 |
| [107] | Cyberattacks and device profiling in the IoT | Edge-IIoTset | DTL model with a CNN, GA, and aggregation ensemble | Achieved 100% accuracy and detected various cyberattacks | Incorporated a realistic dataset | Needs more research for scalability and real-time detection | 2023 |
| [108] | Detecting cyberattacks with DL | CIC IoT 2022 | FFNN, LSTM, and RandNN were used to test the dataset | Accuracy score of FFNN was 99.93%, of LSTM was 99.7%, of was RandNN 96.42% | Versatile extraction and classification features | Optimization needed with more diverse datasets | 2023 |
5. Research Summary
6. Research Gaps
7. Areas for Improvement
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Malhotra, P.; Singh, Y.; Anand, P.; Bangotra, D.K.; Singh, P.K.; Hong, W.C. Internet of things: Evolution, concerns and security challenges. Sensors 2021, 21, 1809. [Google Scholar] [CrossRef]
- Touqeer, H.; Zaman, S.; Amin, R.; Hussain, M.; Al-Turjman, F.; Bilal, M. Smart home security: Challenges, issues, and solutions at different IoT layers. J. Supercomput. 2021, 77, 14053–14089. [Google Scholar] [CrossRef]
- Bikos, A.N.; Kumar, S.A.P. Securing Digital Ledger Technologies-Enabled IoT Devices: Taxonomy, Challenges, and Solutions. IEEE Access 2022, 10, 46238–46254. [Google Scholar] [CrossRef]
- Berger, C.; Eichhammer, P.; Reiser, H.P.; Domaschka, J.; Hauck, F.J.; Habiger, G. A Survey on Resilience in the IoT: Taxonomy, Classification, and Discussion of Resilience Mechanisms. ACM Comput. Surv. 2022, 54, 147. [Google Scholar] [CrossRef]
- Yousef, Z.; Barhoumi, H.G.W. Four-layer Architecture for IoT Security in Fog Network. In Proceedings of the 2023 10th International Conference on Internet of Things: Systems, Management and Security, IOTSMS 2023, San Antonio, TX, USA, 23–25 October 2023; pp. 59–65. [Google Scholar] [CrossRef]
- Cviti, I.; Perakovi, D.; Periša, M.; Stojanovi, M.D. Novel classification of IoT devices based on traffic flow features. J. Organ. End User Comput. 2021, 33, 1–20. [Google Scholar] [CrossRef]
- Gupta, A.; Fernando, X.; Das, O. Reliability and Availability Modeling Techniques in 6G IoT Networks: A Taxonomy and Survey. In Proceedings of the 2021 International Wireless Communications and Mobile Computing, IWCMC 2021, Harbin, China, 28 June 2021–2 July 2021; pp. 586–591. [Google Scholar] [CrossRef]
- Goudarzi, M.; Palaniswami, M.; Buyya, R. Scheduling IoT Applications in Edge and Fog Computing Environments: A Taxonomy and Future Directions. ACM Comput. Surv. 2022, 55, 152. [Google Scholar] [CrossRef]
- Hameed, A.; Alomary, A. Security Issues in IoT: A Survey. In Proceedings of the 2019 International Conference on Innovation and Intelligence for Informatics, Computing, and Technologies (3ICT), Sakhier, Bahrain, 22–23 September 2019. [Google Scholar]
- Mann, P.; Tyagi, N.; Gautam, S.; Rana, A. Classification of Various Types of Attacks in IoT Environment. In Proceedings of the 12th International Conference on Computational Intelligence and Communication Networks, Bhimtal, India, 25–26 September 2020. [Google Scholar] [CrossRef]
- Stephenson, S.; Almansoori, M.; Emami-Naeini, P.; Chatterjee, R. ‘It’s the Equivalent of Feeling Like You’re in Jail’: Lessons from Firsthand and Secondhand Accounts of IoT-Enabled Intimate Partner Abuse. In Proceedings of the 32nd USENIX Security Symposium (USENIX Security 23), Anaheim, CA, USA, 9–11 August 2023. [Google Scholar]
- Khan, M.A.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Ahmed, H.I.; Nasr, A.A.; Abdel-Mageid, S.; Aslan, H.K. A survey of IoT security threats and defenses. Int. J. Adv. Comput. Res. 2019, 9, 325–350. [Google Scholar] [CrossRef]
- Bellman, C.; van Oorschot, P.C. Analysis, Implications, and Challenges of an Evolving Consumer IoT Security Landscape. In Proceedings of the 2019 17th International Conference on Privacy, Security, and Trust (PST), Fredericton, NB, Canada, 26–28 August 2019. [Google Scholar]
- Ioannou, C.; Vassiliou, V. Classifying security attacks in IoT networks using supervised learning. In Proceedings of the 15th Annual International Conference on Distributed Computing in Sensor Systems, DCOSS 2019, Santorini, Greece, 29–31 May 2019; pp. 652–658. [Google Scholar] [CrossRef]
- Aljemy, K.; Alanazi, M.; Alsofiry, M.; Baig, A. Improving IoT security using blockchain. In Proceedings of the 2019 IEEE 10th GCC Conference and Exhibition, GCC 2019, Kuwait, Kuwait, 19–23 April 2019. [Google Scholar] [CrossRef]
- Khanam, S.; Ahmedy, I.B.; Idris, M.Y.I.; Jaward, M.H.; Sabri, A.Q.B.M. A Survey of Security Challenges, Attacks Taxonomy and Advanced Countermeasures in the Internet of Things. IEEE Access 2020, 8, 219709–219743. [Google Scholar] [CrossRef]
- Iqbal, W.; Abbas, H.; Daneshmand, M.; Rauf, B.; Bangash, Y.A. An In-Depth Analysis of IoT Security Requirements, Challenges, and Their Countermeasures via Software-Defined Security. IEEE Internet Things J. 2020, 7, 10250–10276. [Google Scholar] [CrossRef]
- Detres, W.; Chowdhury, M.M.; Rifat, N. IoT Security and Privacy. In Proceedings of the IEEE International Conference on Electro Information Technology, Mankato, MN, USA, 19–21 May 2022; pp. 498–503. [Google Scholar] [CrossRef]
- Gautam, K.K.S.; Kumar, R.; Yadav, R.; Sharma, P. Investigation of the Internet of Things (IoT) Security and Privacy Issues. In Proceedings of the 5th International Conference on Inventive Research in Computing Applications, ICIRCA 2023, Coimbatore, India, 3–5 August 2023; pp. 1489–1494. [Google Scholar] [CrossRef]
- Victor, P.; Lashkari, A.H.; Lu, R.; Sasi, T.; Xiong, P.; Iqbal, S. IoT malware: An attribute-based taxonomy, detection mechanisms, and challenges. Peer Peer Netw. Appl. 2023, 16, 1380–1431. [Google Scholar] [CrossRef] [PubMed]
- Alhowaide, A.; Alsmadi, I.; Tang, J. Ensemble Detection Model for IoT IDS. Internet Things 2021, 16, 100435. [Google Scholar] [CrossRef]
- Albulayhi, K.; Smadi, A.A.; Sheldon, F.T.; Abercrombie, R.K. Iot intrusion detection taxonomy, reference architecture, and analyses. Sensors 2021, 21, 6432. [Google Scholar] [CrossRef] [PubMed]
- Hanif, S.; Ilyas, T.; Zeeshan, M. Intrusion Detection In IoT Using Artificial Neural Networks On UNSW-15 Dataset. In Proceedings of the 2019 IEEE 16th International Conference on Smart Cities: Improving Quality of Life Using ICT & IoT and AI (HONET-ICT), Charlotte, NC, USA, 6–9 October 2019. [Google Scholar]
- DeMedeiros, K.; Hendawi, A.; Alvarez, M. A Survey of AI-Based Anomaly Detection in IoT and Sensor Networks. Sensors 2023, 23, 1352. [Google Scholar] [CrossRef]
- Sheikh, T.U.; Rahman, H.; Al-Qahtani, H.S.; Hazra, T.K.; Sheikh, N.U. Countermeasure of Attack Vectors using Signature-Based IDS in IoT Environments. In Proceedings of the 2019 IEEE 10th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Vancouver, BC, Canada, 17–19 October 2019; pp. 1130–1136. [Google Scholar]
- Hoang, T.M.; Pham, T.A.; Do, V.V.; Nguyen, V.N.; Nguyen, M.H. A Lightweight DNN-based IDS for Detecting IoT Cyberattacks in Edge Computing. In Proceedings of the International Conference on Advanced Technologies for Communications, Ha Noi, Vietnam, 20–22 October 2022; pp. 136–140. [Google Scholar] [CrossRef]
- Cook, A.A.; Misirli, G.; Fan, Z. Anomaly Detection for IoT Time-Series Data: A Survey. IEEE Internet Things J. 2020, 7, 6481–6494. [Google Scholar] [CrossRef]
- Otoum, S.; Guizani, N.; Mouftah, H. Federated Reinforcement Learning-Supported IDS for IoT-steered Healthcare Systems. In Proceedings of the IEEE International Conference on Communications, Montreal, QC, Canada, 14–23 June 2021. [Google Scholar] [CrossRef]
- Stach, T.; Kinkel, Y.; Constapel, M.; Burmeister, H.C. Maritime Anomaly Detection for Vessel Traffic Services: A Survey. J. Mar. Sci. Eng. 2023, 11, 1174. [Google Scholar] [CrossRef]
- Prasad, N.R.; Mantr, D. Smart LSTM-based IDS for Heterogeneous loT (HetloT). In Proceedings of the 2022 25th International Symposium on Wireless Personal Multimedia Communications (WPMC), Herning, Denmark, 30 October 2022–2 November 2022; pp. 23–28. [Google Scholar]
- Diro, A.; Chilamkurti, N.; Nguyen, V.D.; Heyne, W. A comprehensive study of anomaly detection schemes in iot networks using machine learning algorithms. Sensors 2021, 21, 8320. [Google Scholar] [CrossRef]
- Wu, J.; Wang, Y.; Xie, B.; Li, S.; Dai, H.; Ye, K.; Xu, C. Joint Semantic Transfer Network for IoT Intrusion Detection. IEEE Internet Things J. 2023, 10, 3368–3383. [Google Scholar] [CrossRef]
- Hussain, A.; Sharif, H.; Rehman, F.; Kirn, H.; Sadiq, A.; Khan, M.S.; Riaz, A.; Ali, C.N.; Chandio, A.H. A Systematic Review of Intrusion Detection Systems in the Internet of Things Using ML and DL. In Proceedings of the 2023 4th International Conference on Computing, Mathematics, and Engineering Technologies: Sustainable Technologies for Socio-Economic Development, iCoMET 2023, Sukkur, Pakistan, 17–18 March 2023. [Google Scholar] [CrossRef]
- Mazhar, N.; Salleh, R.; Zeeshan, M.; Hameed, M.M.; Khan, N. R-IDPS: Real-time SDN based IDPS system for IoT security. In Proceedings of the HONET 2021—IEEE 18th International Conference on Smart Communities: Improving Quality of Life Using ICT, IoT and AI, Karachi, Pakistan, 11–13 October 2021; pp. 71–76. [Google Scholar] [CrossRef]
- Slevi, S.T.; Visalakshi, P. A survey on Deep Learning based Intrusion Detection Systems on Internet of Things. In Proceedings of the 5th International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud), I-SMAC 2021, Palladam, India, 11–13 November 2021; pp. 1488–1496. [Google Scholar] [CrossRef]
- Ishaque, M.; Johar, M.G.M.; Khatibi, A.; Yamin, M. Hybrid deep learning based intrusion detection system using Modified Chicken Swarm Optimization algorithm. ARPN J. Eng. Appl. Sci. 2023, 18, 1707–1718. [Google Scholar] [CrossRef]
- Ahmad, I.; Al Qahtani, H.S. A comparative analysis of gradient boosting, random forest and deep neural networks in the intrusion detection system. ARPN J. Eng. Appl. Sci. 2023, 18, 1707–1718. [Google Scholar]
- Vigoya, L.; Fernandez, D.; Carneiro, V.; Nóvoa, F.J. IoT dataset validation using machine learning techniques for traffic anomaly detection. Electronics 2021, 10, 2857. [Google Scholar] [CrossRef]
- Sudharsan, B.; Breslin, J.G.; Ali, M.I. Edge2Train: A framework to train machine learning models (SVMs) on resource-constrained IoT edge devices. In Proceedings of the ACM International Conference Proceeding Series, Association for Computing Machinery, Malmö, Sweden, 6–9 October 2020. [Google Scholar] [CrossRef]
- Qian, B.; Su, J.; Wen, Z.; Jha, D.N.; Li, Y.; Guan, Y.; Puthal, D.; James, P.; Yang, R.; Zomaya, A.Y.; et al. Orchestrating the Development Lifecycle of Machine Learning-based IoT Applications: A Taxonomy and Survey. ACM Comput. Surv. 2020, 53, 82. [Google Scholar] [CrossRef]
- Bhayo, J.; Shah, S.A.; Hameed, S.; Ahmed, A.; Nasir, J.; Draheim, D. Towards a machine learning-based framework for DDOS attack detection in software-defined IoT (SD-IoT) networks. Eng. Appl. Artif. Intell. 2023, 123, 106432. [Google Scholar] [CrossRef]
- Mohanta, B.K.; Jena, D.; Satapathy, U.; Patnaik, S. Survey on IoT security: Challenges and solution using machine learning, artificial intelligence, and blockchain technology. Internet Things 2020, 11, 100227. [Google Scholar] [CrossRef]
- Ahmed, K.I.; Tahir, M.; Habaebi, M.H.; Lau, S.L.; Ahad, A. Machine learning for authentication and authorization in iot: Taxonomy, challenges and future research direction. Sensors 2021, 21, 5122. [Google Scholar] [CrossRef] [PubMed]
- Bharathi, M.; Geetha, K.; Mani, P.K.; Vijayakumar, G.N.S.; Srinivasan, K.; Kumar, K.R. AI and IoT-based Electric Vehicle Monitoring System. In Proceedings of the 6th International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud), I-SMAC 2022—Proceedings, Dharan, Nepal, 10–12 November 2022; pp. 722–727. [Google Scholar] [CrossRef]
- Alsharif, M.; Rawat, D.B. Machine Learning Enabled Intrusion Detection for Edge Devices in the Internet of Things. In Proceedings of the 2023 IEEE 13th Annual Computing and Communication Workshop and Conference, CCWC 2023, Las Vegas, NV, USA, 8–11 March 2023; pp. 361–367. [Google Scholar] [CrossRef]
- Brady, S.; Magoni, D.; Murphy, J.; Assem, H.; Portillo-Dominguez, A.O. Analysis of Machine Learning Techniques for Anomaly Detection in the Internet of Things. In Proceedings of the 2018 IEEE Latin American Conference on Computational Intelligence (LA-CCI), Gudalajara, Mexico, 7–9 November 2018. [Google Scholar]
- Hasan, M.; Islam, M.M.; Zarif, M.I.I.; Hashem, M. Attack and anomaly detection in IoT sensors in IoT sites using machine learning approaches. Internet Things 2019, 7, 100059. [Google Scholar] [CrossRef]
- Vangipuram, R.; Gunupudi, R.K.; Puligadda, V.K.; Vinjamuri, J. A machine learning approach for imputation and anomaly detection in IoT environment. Expert Syst. 2020, 37, e12556. [Google Scholar] [CrossRef]
- Stoian, N.-A. Machine Learning for Anomaly Detection in IoT Networks: Malware Analysis on the IoT-23 Data Set. Bachelor’s Thesis, University of Twente, Enschede, The Netherlands, 2020. [Google Scholar]
- Vidya, M.S.; Sakthidharan, G.R. Accurate Anomaly Detection using various Machine Learning methods for IoT devices in Indoor Environment. In Proceedings of the 5th International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud), I-SMAC 2021, Palladam, India, 11–13 November 2021; pp. 308–316. [Google Scholar] [CrossRef]
- Thaseen, I.S.; Mohanraj, V.; Ramachandran, S.; Sanapala, K.; Yeo, S.S. A Hadoop based framework integrating machine learning classifiers for anomaly detection in the internet of things. Electronics 2021, 10, 1955. [Google Scholar] [CrossRef]
- Wu, X.W.; Cao, Y.; Dankwa, R. Accuracy vs Efficiency: Machine Learning Enabled Anomaly Detection on the Internet of Things. In Proceedings of the 2022 IEEE International Conference on Internet of Things and Intelligence Systems, IoTaIS 2022, Bali, Indonesia, 24–26 November 2022; pp. 245–251. [Google Scholar] [CrossRef]
- Malki, A.; Atlam, E.S.; Gad, I. Machine learning approach of detecting anomalies and forecasting time-series of IoT devices. Alex. Eng. J. 2022, 61, 8973–8986. [Google Scholar] [CrossRef]
- Abrishami, M.; Dadkhah, S.; Neto, E.C.P.; Xiong, P.; Iqbal, S.; Ray, S.; Ghorbani, A.A. Label Noise Detection in IoT Security based on Decision Tree and Active Learning. In Proceedings of the IEEE 19th International Conference on Smart Communities: Improving Quality of Life Using ICT, IoT and AI, HONET 2022, Marietta, GA, USA, 19–21 December 2022; pp. 46–53. [Google Scholar] [CrossRef]
- Balega, M.; Farag, W.; Ezekiel, S.; Wu, X.W.; Deak, A.; Good, Z. IoT Anomaly Detection Using a Multitude of Machine Learning Algorithms. In Proceedings of the Applied Imagery Pattern Recognition Workshop, Washington, DC, USA, 11–13 October 2022. [Google Scholar] [CrossRef]
- Xu, H.; Sun, Z.; Cao, Y.; Bilal, H. A data-driven approach for intrusion and anomaly detection using automated machine learning for the Internet of Things. Soft Comput. 2023, 27, 14469–14481. [Google Scholar] [CrossRef]
- Portela, A.L.; Menezes, R.A.; Costa, W.L.; Silveira, M.M.; Bittecnourt, L.F.; Gomes, R.L. Detection of IoT Devices and Network Anomalies based on Anonymized Network Traffic. In Proceedings of the IEEE/IFIP Network Operations and Management Symposium 2023, NOMS 2023, Miami, FL, USA, 8–12 May 2023. [Google Scholar] [CrossRef]
- Vigoya, L.; Pardal, A.; Fernandez, D.; Carneiro, V. Application of Machine Learning Algorithms for the Validation of a New CoAP-IoT Anomaly Detection Dataset. Appl. Sci. 2023, 13, 4482. [Google Scholar] [CrossRef]
- He, M.; Huang, Y.; Wang, X.; Wei, P.; Wang, X. A lightweight and efficient IoT intrusion detection method based on feature grouping. IEEE Internet Things J. 2023, 11, 2935–2949. [Google Scholar] [CrossRef]
- Bakker, J.N.; Ng, B.; Seah, W.K.G. Can Machine Learning Techniques be effectively used in real networks against DDoS attacks? In Proceedings of the 2018 27th International Conference on Computer Communication and Networks (ICCCN), Hangzhou, China, 30 July 2018–2 August 2018. [Google Scholar]
- Doshi, R.; Apthorpe, N.; Feamster, N. Machine learning DDoS detection for consumer Internet of things devices. In Proceedings of the 2018 IEEE Symposium on Security and Privacy Workshops, SPW 2018, San Francisco, CA, USA, 24 May 2018; pp. 29–35. [Google Scholar] [CrossRef]
- Li, J.; Lyu, L.; Liu, X.; Zhang, X.; Lyu, X. FLEAM: A Federated Learning Empowered Architecture to Mitigate DDoS in Industrial IoT. IEEE Trans. Ind. Inform. 2021, 18, 4059–4068. [Google Scholar] [CrossRef]
- Saba, T.; Sadad, T.; Rehman, A.; Mehmood, Z.; Javaid, Q. Intrusion Detection System through Advance Machine Learning for the Internet of Things Networks. IT Prof. 2021, 23, 58–64. [Google Scholar] [CrossRef]
- Shafiq, M.; Tian, Z.; Bashir, A.K.; Du, X.; Guizani, M. CorrAUC: A Malicious Bot-IoT Traffic Detection Method in IoT Network Using Machine-Learning Techniques. IEEE Internet Things J. 2021, 8, 3242–3254. [Google Scholar] [CrossRef]
- Guarino, I.; Bovenzi, G.; Di Monda, D.; Aceto, G.; Ciuonzo, D.; Pescape, A. On the use of Machine Learning Approaches for the Early Classification in Network Intrusion Detection. In Proceedings of the 2022 IEEE International Symposium on Measurements and Networking, M and N 2022—Proceedings, Padua, Italy, 18–20 July 2022. [Google Scholar] [CrossRef]
- Maran, P.; Yap, T.T.V.; Chin, J.J.; Ng, H.; Goh, V.T.; Kuek, T.Y. Comparison of Machine Learning Models for IoT Malware Classification. In Proceedings of the International Conference on Computer, Information Technology and Intelligent Computing (CITIC 2022), Online, 25–27 July 2022; pp. 15–28. [Google Scholar] [CrossRef]
- Raju, V.S.A.; Suma, B. Network Intrusion Detection for IoT-Botnet Attacks Using ML Algorithms. In Proceedings of the 2023 7th International Conference on Computation System and Information Technology for Sustainable Solutions (CSITSS), Bangalore, India, 2–4 November 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Jayesh, T.P.; Pandiaraj, K.; Paul, A.; Chandran, R.R.; Menon, P.P. A Hybrid Machine Learning Approach to Anomaly Detection in Industrial IoT. In Proceedings of the 2023 3rd International Conference on Advances in Computing, Communication, Embedded and Secure Systems, Kalady, India, 18–20 May 2023; pp. 32–36. [Google Scholar] [CrossRef]
- Al Sukhni, B.; Mohanta, B.K.; Dehury, M.K.; Tripathy, A.K. A Novel Approach for Detecting and Preventing Security attacks using Machine Learning in IoT. In Proceedings of the 2023 14th International Conference on Computing Communication and Networking Technologies, ICCCNT 2023, Delhi, India, 6–8 July 2023. [Google Scholar] [CrossRef]
- Kumari, P.; Mangat, V.; Singh, A. Comparative Analysis of State-of-the-Art Attack Detection Models. In Proceedings of the 2023 14th International Conference on Computing Communication and Networking Technologies, ICCCNT 2023, Delhi, India, 6–8 July 2023. [Google Scholar] [CrossRef]
- Altulaihan, E.; Almaiah, M.A.; Aljughaiman, A. Anomaly Detection IDS for Detecting DoS Attacks in IoT Networks Based on Machine Learning Algorithms. Sensors 2024, 24, 713. [Google Scholar] [CrossRef] [PubMed]
- Khazane, H.; Ridouani, M.; Salahdine, F.; Kaabouch, N. A Holistic Review of Machine Learning Adversarial Attacks in IoT Networks. Future Internet 2024, 16, 32. [Google Scholar] [CrossRef]
- Azeem, M.; Khan, D.; Iftikhar, S.; Bawazeer, S.; Alzahrani, M. Analyzing and comparing the effectiveness of malware detection: A study of machine learning approaches. Heliyon 2024, 10, e23574. [Google Scholar] [CrossRef] [PubMed]
- Yue, Y.; Li, S.; Legg, P.; Li, F. Deep Learning-Based Security Behaviour Analysis in IoT Environments: A Survey. Secur. Commun. Netw. 2021, 2021, 8873195. [Google Scholar] [CrossRef]
- Abusitta, A.; de Carvalho, G.H.S.; Wahab, O.A.; Halabi, T.; Fung, B.C.M.; Al Mamoori, S. Deep learning-enabled anomaly detection for IoT systems. Internet Things 2023, 21, 100656. [Google Scholar] [CrossRef]
- Ahmad, R.; Alsmadi, I.; Alhamdani, W.; Tawalbeh, L. A comprehensive deep learning benchmark for IoT IDS. Comput. Secur. 2022, 114, 102588. [Google Scholar] [CrossRef]
- Gutal, A.; Bhamare, T.; Mayekar, A.; Deshmukh, P. Automation of Society Security Using Deep Learning and IoT. In Proceedings of the 5th International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud), I-SMAC 2021, Palladam, India, 11–13 November 2021; pp. 96–102. [Google Scholar] [CrossRef]
- Alagheband, M.R.; Mashatan, A. Advanced digital signatures for preserving privacy and trust management in hierarchical heterogeneous IoT: Taxonomy, capabilities, and objectives. Internet Things 2022, 18, 100492. [Google Scholar] [CrossRef]
- Achir, M.; Abdelli, A.; Mokdad, L.; Benothman, J. Service discovery and selection in IoT: A survey and a taxonomy. J. Netw. Comput. Appl. 2022, 200, 103331. [Google Scholar] [CrossRef]
- Li, D.; Deng, L.; Lee, M.; Wang, H. IoT data feature extraction and intrusion detection system for smart cities based on deep migration learning. Int. J. Inf. Manag. 2019, 49, 533–545. [Google Scholar] [CrossRef]
- NG, B.A.; Selvakumar, S. Anomaly detection framework for Internet of things traffic using vector convolutional deep learning approach in fog environment. Future Gener. Comput. Syst. 2020, 113, 255–265. [Google Scholar] [CrossRef]
- Dhillon, H.; Haque, A. Towards Network Traffic Monitoring Using Deep Transfer Learning. In Proceedings of the 2020 IEEE 19th International Conference on Trust, Security, and Privacy in Computing and Communications (TrustCom), Guangzhou, China, 29 December 2020–1 January 2021. [Google Scholar] [CrossRef]
- Raeiszadeh, M.; Saleem, A.; Ebrahimzadeh, A.; Glitho, R.H.; Eker, J.; Mini, R.A.F. A Deep Learning Approach for Real-Time Application-Level Anomaly Detection in IoT Data Streaming. In Proceedings of the IEEE Consumer Communications and Networking Conference, CCNC, Las Vegas, NV, USA, 8–11 January 2023; pp. 449–454. [Google Scholar] [CrossRef]
- Ullah, I.; Mahmoud, Q.H. Design and Development of a Deep Learning-Based Model for Anomaly Detection in IoT Networks. IEEE Access 2021, 9, 103906–103926. [Google Scholar] [CrossRef]
- Varalakshmi, S.; Premnath, S.P.; Yogalakshmi, V.; Vijayalakshmi, P.; Kavitha, V.R.; Vimalarani, G. Design of IoT Network using Deep Learning-based Model for Anomaly Detection. In Proceedings of the 5th International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud), I-SMAC 2021, Palladam, India, 11–13 November 2021; pp. 216–220. [Google Scholar] [CrossRef]
- Abdel-Basset, M.; Hawash, H.; Chakrabortty, R.K.; Ryan, M.J. Semi-Supervised Spatiotemporal Deep Learning for Intrusions Detection in IoT Networks. IEEE Internet Things J. 2021, 8, 12251–12265. [Google Scholar] [CrossRef]
- Wani, A.; Revathi, S.; Khaliq, R. SDN-based intrusion detection system for IoT using deep learning classifier (IDSIoT-SDL). CAAI Trans. Intell. Technol. 2021, 6, 281–290. [Google Scholar] [CrossRef]
- Saba, T.; Khan, A.R.; Sadad, T.; Hong, S.P. Securing the IoT System of Smart City against Cyber Threats Using Deep Learning. Discret. Dyn. Nat. Soc. 2022, 2022, 1241122. [Google Scholar] [CrossRef]
- Li, S.; Qin, D.; Wu, X.; Li, J.; Li, B.; Han, W. False Alert Detection Based on Deep Learning and Machine Learning. Int. J. Semant. Web. Inf. Syst. 2022, 18, 1–21. [Google Scholar] [CrossRef]
- Alani, M.M.; Damiani, E.; Ghosh, U. DeepIIoT: An Explainable Deep Learning Based Intrusion Detection System for Industrial IoT. In Proceedings of the 2022 IEEE 42nd International Conference on Distributed Computing Systems Workshops, ICDCSW 2022, Bologna, Italy, 10 July 2022; pp. 169–174. [Google Scholar] [CrossRef]
- Mohammadpour, L.; Ling, T.C.; Liew, C.S.; Aryanfar, A. A Survey of CNN-Based Network Intrusion Detection. Appl. Sci. 2022, 12, 8162. [Google Scholar] [CrossRef]
- Roy, S.; Li, J.; Pandey, V.; Bai, Y. An Explainable Deep Neural Framework for Trustworthy Network Intrusion Detection. In Proceedings of the 2022 10th IEEE International Conference on Mobile Cloud Computing, Services, and Engineering, MobileCloud 2022, San Francisco, CA, USA, 15–18 August 2022; pp. 25–30. [Google Scholar] [CrossRef]
- Gopali, S.; Namin, A.S. Deep Learning-Based Time-Series Analysis for Detecting Anomalies in the Internet of Things. Electronics 2022, 11, 3205. [Google Scholar] [CrossRef]
- Oseni, A.; Moustafa, N.; Creech, G.; Sohrabi, N.; Strelzoff, A.; Tari, Z.; Linkov, I. An Explainable Deep Learning Framework for Resilient Intrusion Detection in IoT-Enabled Transportation Networks. IEEE Trans. Intell. Transp. Syst. 2023, 24, 1000–1014. [Google Scholar] [CrossRef]
- Hamdan, M.; Eldhai, A.M.; Abdelsalam, S.; Ullah, K.; Bashir, A.K.; Marsono, M.; Kon, F.; Batista, D.M. A Two-Tier Anomaly-based Intrusion Detection Approach for IoT-Enabled Smart Cities. In Proceedings of the IEEE INFOCOM 2023—Conference on Computer Communications Workshops, INFOCOM WKSHPS 2023, Hoboken, NJ, USA, 20 May 2023. [Google Scholar] [CrossRef]
- Al-Naday, M.; Reed, M.; Dobre, V.; Toor, S.; Volckaert, B.; De Turck, F. Service-based Federated Deep Reinforcement Learning for Anomaly Detection in Fog Ecosystems. In Proceedings of the 26th Conference on Innovation in Clouds, Internet and Networks, ICIN 2023, Paris, France, 6–9 March 2023; pp. 121–128. [Google Scholar] [CrossRef]
- Li, C.; Fu, Y.; Zhang, R.; Liang, H.; Wang, C.; Li, J. An Anomaly Detection Approach Based on Integrated LSTM for IoT Big Data. Secur. Commun. Netw. 2023, 2023, 8903980. [Google Scholar] [CrossRef]
- Lazzarini, R.; Tianfield, H.; Charissis, V. A stacking ensemble of deep learning models for IoT intrusion detection. Knowl. Based Syst. 2023, 279, 110941. [Google Scholar] [CrossRef]
- Diro, A.A.; Chilamkurti, N. Distributed attack detection scheme using deep learning approach for Internet of Things. Future Gener. Comput. Syst. 2018, 82, 761–768. [Google Scholar] [CrossRef]
- Dawoud, A.; Shahristani, S.; Raun, C. Deep learning and software-defined networks: Towards secure IoT architecture. Internet Things 2018, 3–4, 82–89. [Google Scholar] [CrossRef]
- Nagisetty, A.; Gupta, G.P. Framework for Detection of Malicious Activities in IoT Networks using Keras Deep Learning Library. In Proceedings of the Third International Conference on Computing Methodologies and Communication (ICCMC 2019), Erode, India, 27–29 March 2019. [Google Scholar] [CrossRef]
- De La Torre Parra, G.; Rad, P.; Choo, K.K.R.; Beebe, N. Detecting Internet of Things attacks using distributed deep learning. J. Netw. Comput. Appl. 2020, 163, 102662. [Google Scholar] [CrossRef]
- Sahu, A.K.; Sharma, S.; Tanveer, M.; Raja, R. Internet of Things attack detection using hybrid Deep Learning Model. Comput. Commun. 2021, 176, 146–154. [Google Scholar] [CrossRef]
- Tsogbaatar, E.; Bhuyan, M.H.; Taenaka, Y.; Fall, D.; Gonchigsumlaa, K.; Elmroth, E.; Kadobayashi, Y. DeL-IoT: A deep ensemble learning approach to uncover anomalies in IoT. Internet Things 2021, 14, 100391. [Google Scholar] [CrossRef]
- Otoom, A.F.; Eleisah, W.; Abdallah, E.E. Deep Learning for Accurate Detection of Brute Force attacks on IoT Networks. Procedia Comput. Sci. 2023, 220, 291–298. [Google Scholar] [CrossRef]
- Latif, S.; Boulila, W.; Koubaa, A.; Zou, Z.; Ahmad, J. DTL-IDS: An optimized Intrusion Detection Framework using Deep Transfer Learning and Genetic Algorithm. J. Netw. Comput. Appl. 2024, 221, 103784. [Google Scholar] [CrossRef]
- Bakhsh, S.A.; Khan, M.A.; Ahmed, F.; Alshehri, M.S.; Ali, H.; Ahmad, J. Enhancing IoT network security through deep learning-powered Intrusion Detection System. Internet Things 2023, 2023, 100936. [Google Scholar] [CrossRef]


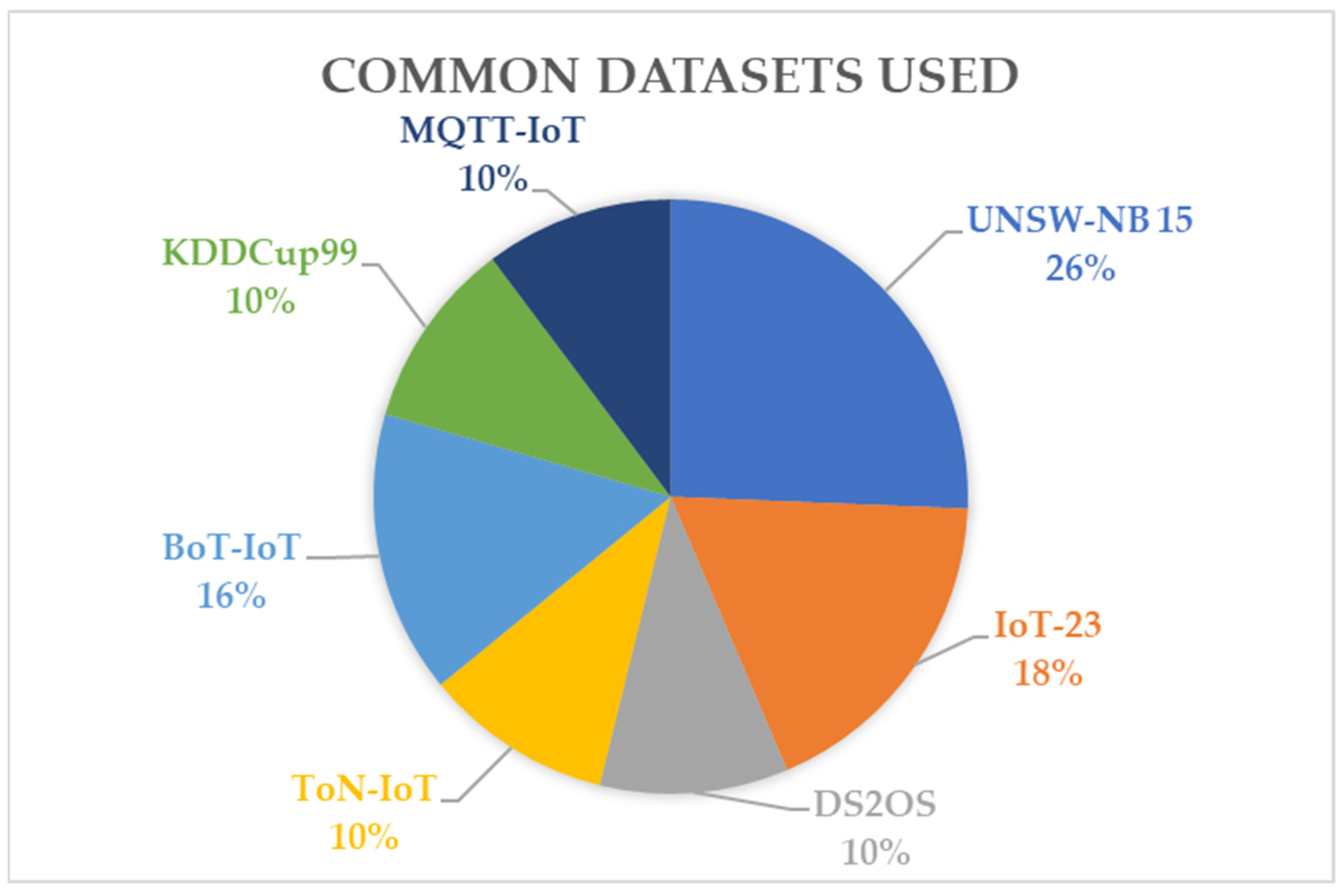
| Reference | Attacks |
|---|---|
| [12] | Spoofing, Sleep deprivation, Replay, Session hijacking |
| [13] | Spyware, Trojans, Sinkhole, Spoofing, Jamming, Tag cloning, Physical tampering |
| [14] | DDoS, Botnets, Falsified sensor data, Attacks on cloud services, Physical tampering |
| [15] | DDoS, Man-in-the-Middle, Spoofing, Physical tampering, Data breach, Malware, Ransomware |
| [16] | DDoS, Man-in-the-Middle, Malware, Ransomware, Physical tampering, Data breach, Spoofing |
| [17] | Physical damage, Exhaustion attacks, Cryptanalysis, Side-channel information, Man-in-the-Middle, DoS/DDoS, Message forging |
| [18] | Physical, Malware, DoS, Man-in-the-Middle, Replication, Spoofing, Injection, Social engineering |
| [19] | DoS, Man-in-the-Middle, Malware, Physical, Password |
| [20] | DoS, Man-in-the-Middle, Physical, Malware, Botnet, Spoofing, Eavesdropping |
| [21] | DDoS, Ransomware, Industrial spying, Click fraud |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rafique, S.H.; Abdallah, A.; Musa, N.S.; Murugan, T. Machine Learning and Deep Learning Techniques for Internet of Things Network Anomaly Detection—Current Research Trends. Sensors 2024, 24, 1968. https://doi.org/10.3390/s24061968
Rafique SH, Abdallah A, Musa NS, Murugan T. Machine Learning and Deep Learning Techniques for Internet of Things Network Anomaly Detection—Current Research Trends. Sensors. 2024; 24(6):1968. https://doi.org/10.3390/s24061968
Chicago/Turabian StyleRafique, Saida Hafsa, Amira Abdallah, Nura Shifa Musa, and Thangavel Murugan. 2024. "Machine Learning and Deep Learning Techniques for Internet of Things Network Anomaly Detection—Current Research Trends" Sensors 24, no. 6: 1968. https://doi.org/10.3390/s24061968
APA StyleRafique, S. H., Abdallah, A., Musa, N. S., & Murugan, T. (2024). Machine Learning and Deep Learning Techniques for Internet of Things Network Anomaly Detection—Current Research Trends. Sensors, 24(6), 1968. https://doi.org/10.3390/s24061968





