Trust-Based Optimized Reporting for Detection and Prevention of Black Hole Attacks in Low-Power and Lossy Green IoT Networks
Abstract
1. Introduction
- The development of a novel trust-based Optimized Reporting Module (ORM) that alleviates the burden from the root node, preventing it from being a single point of failure. In the proposed scheme, the root node only receives the trust value of a node when action is required, rather than receiving trust values whenever they are calculated.
- Reduction of the overhead cost associated with sending trust values of a specific node to the root within a fixed time span.
- Implementation of RPL’s optimized routing algorithm to enhance network efficiency by mitigating latency, reducing overall transmission load, and lowering the burden on the root node.
2. Related Work
3. Classification of Attacks on RPL-Based IoT
3.1. Wireless Sensor Network-Inherited Attacks
3.1.1. Black Hole Attacks
3.1.2. Sinkhole Attacks
3.1.3. Wormhole Attacks
3.1.4. Sybil Attacks
3.1.5. Hello Flood Attacks
3.2. RPL-Specific Attacks
3.2.1. Rank Attacks
3.2.2. Version Attacks
3.2.3. Neighbor Attacks
3.2.4. Replay Attacks
4. Proposed Trust-Based Optimized Reporting Scheme
4.1. Fundamental Concepts in Trust Management
- Network Structure: We consider an IoT network where all nodes can communicate and exchange information with each other. The network primarily consists of two types of nodes: GMN and GLN. GMNs are entities within the network seeking to establish trust, while GLNs play a crucial role in trust management. GLNs collect the computed trust scores for each GMN and decide whether specific GMNs are trustworthy to be a part of the network. In the proposed model, we represent each communication request as a “task” in the subsequent text.
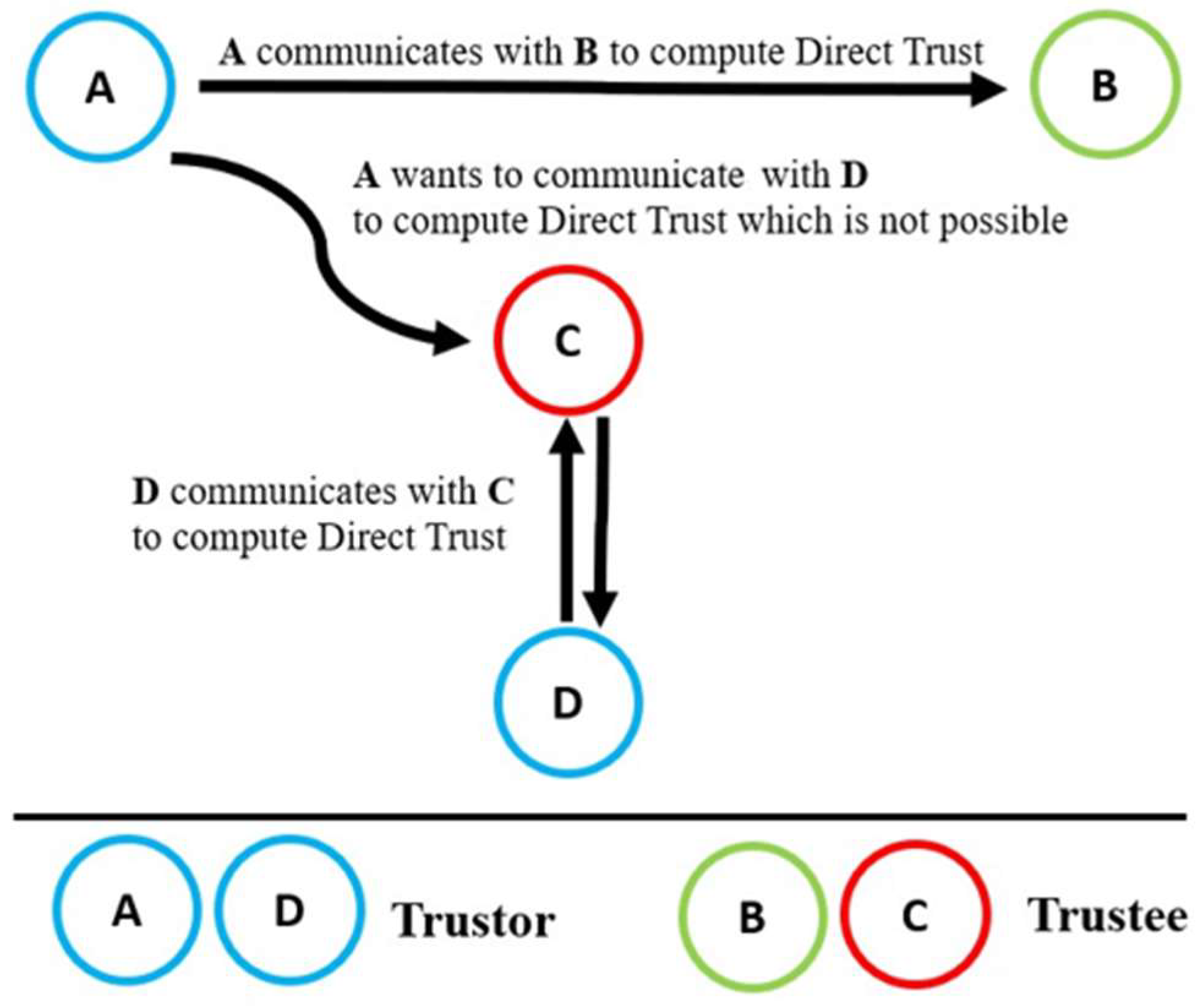
- Trustor: This refers to entities within the network that seek to evaluate and establish trust in other network participants, including GMNs and GLNs. In our context, Trustors are nodes or devices within the IoT network that engage in the process of trust calculation for both GMNs and GLNs.
- Trustee: This represents the entities being evaluated for trustworthiness, including both GMNs and GLNs. Trustees may be individual nodes, devices, or even entire subsystems in the IoT network. Understanding the characteristics and behaviors of Trustees is crucial for effective trust evaluation and management.
- Recommenders: These act as intermediaries that contribute to the trust evaluation process for both GMNs and GLNs. These entities provide valuable insights and recommendations based on their observations of Trustors and Trustees, thereby enhancing the robustness of trust calculations with the network.
4.2. Trust Calculation Mechanism
4.2.1. Notations and Their Meanings
- Energy (: This represents the residual energy of a specific node to participate in communication in the network. It is calculated by subtracting the current energy from the initial energy.
- Unselfishness (: This indicates how much a node has responded to transmission requests from neighboring nodes. It involves the trust value for energy and the number of successful communications.
- Honesty (: This assesses the node’s trustworthiness based on the number of completed transmissions.
- Dishonesty (: This assesses the node’s trust based on the number of unsuccessful transmissions.
- Forgetting curve: This is a mechanism that prioritizes recent behavior over older feedback in trust evaluation.
- Similarity (: This measures the variation among the feedback propagated by the recommenders.
- : a node’s initial energy.
- : a node’s current energy.
- : the direct trust of a node.
- : the indirect trust of a node.
- : the number of successful tasks. In this paper, we represent each communication request as a “task”.
- : the number of unsuccessful tasks.
- : a set of honest feedback.
- : a set of dishonest feedback.
- : the current trust value.
- : the initial trust value.
4.2.2. Direct Trust
| Algorithm 1: Computing Direct Trust |
| input: Trust values of , , , output: Direct Trust if Target node is an immediate neighbor node then if Trust value does not exist for Target node then else end if end if |
4.2.3. Indirect Trust
| Algorithm 2: Computing Indirect Trust |
| input: Trust values of , , output: Indirect Trust if Target node is an immediate neighbor node then if Trust value does not exist for Target node then else end if end if |
4.2.4. Forgetting Curve
| Algorithm 3: Forgetting Curve |
| input: t—Direct trust or Indirect trust values, c—, n— output: Setting the priority of recent test scores function if then end if if then end if return |
4.3. Trust Propagation
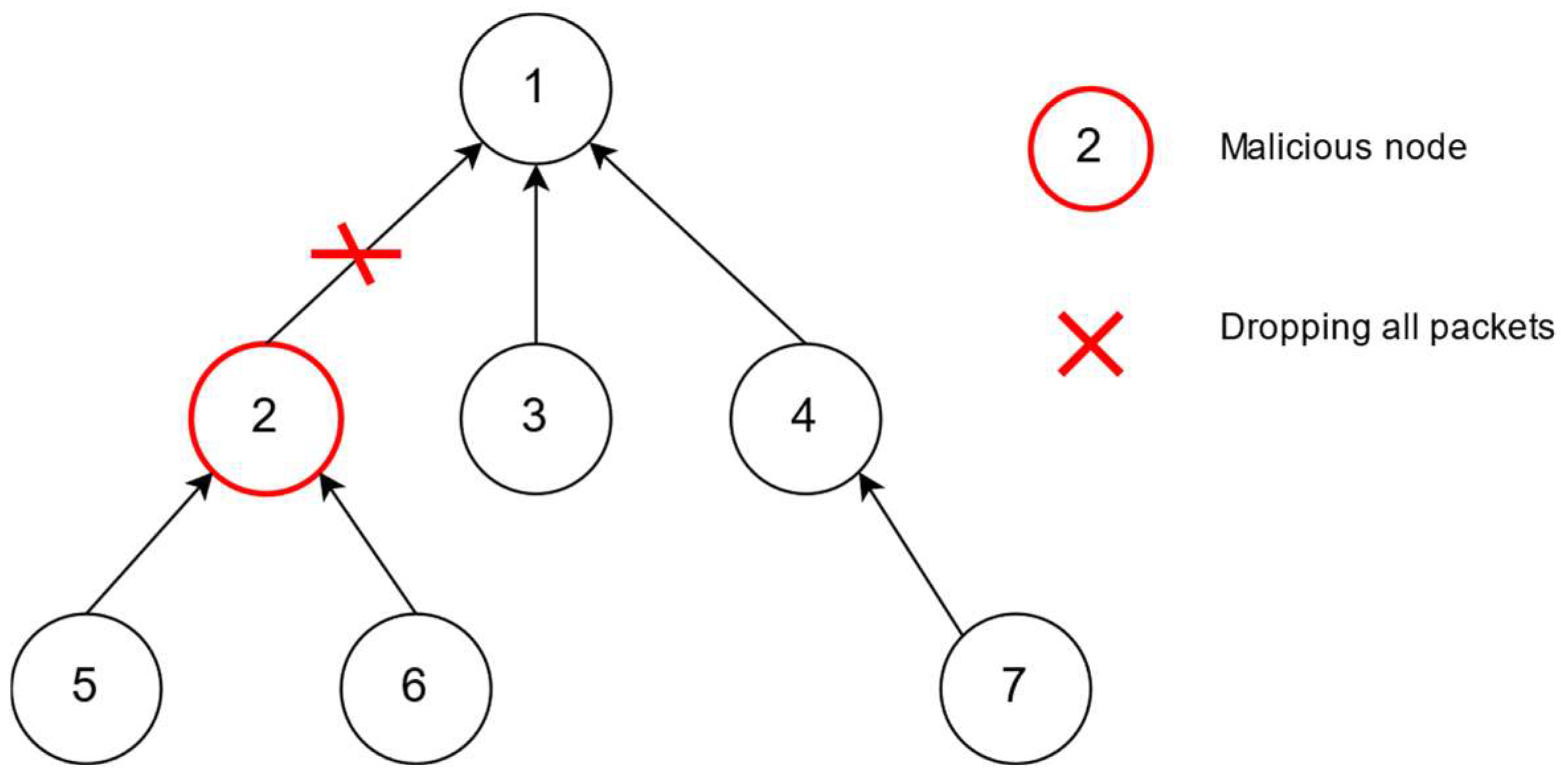
4.3.1. Delta-Based Isolation Strategy
4.3.2. Cost Optimization through Delta-Based Strategy
4.3.3. Root Node Overhead Reduction
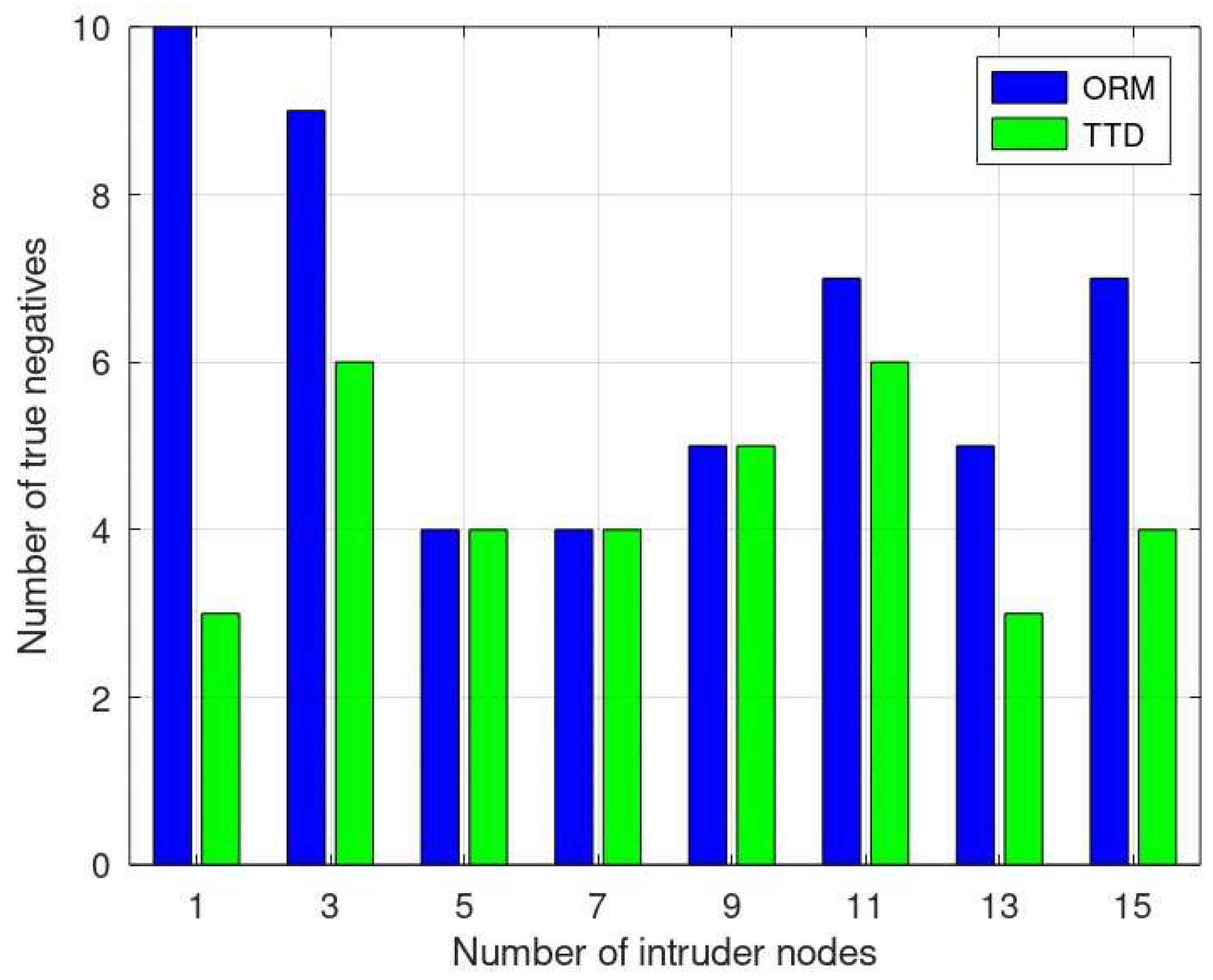
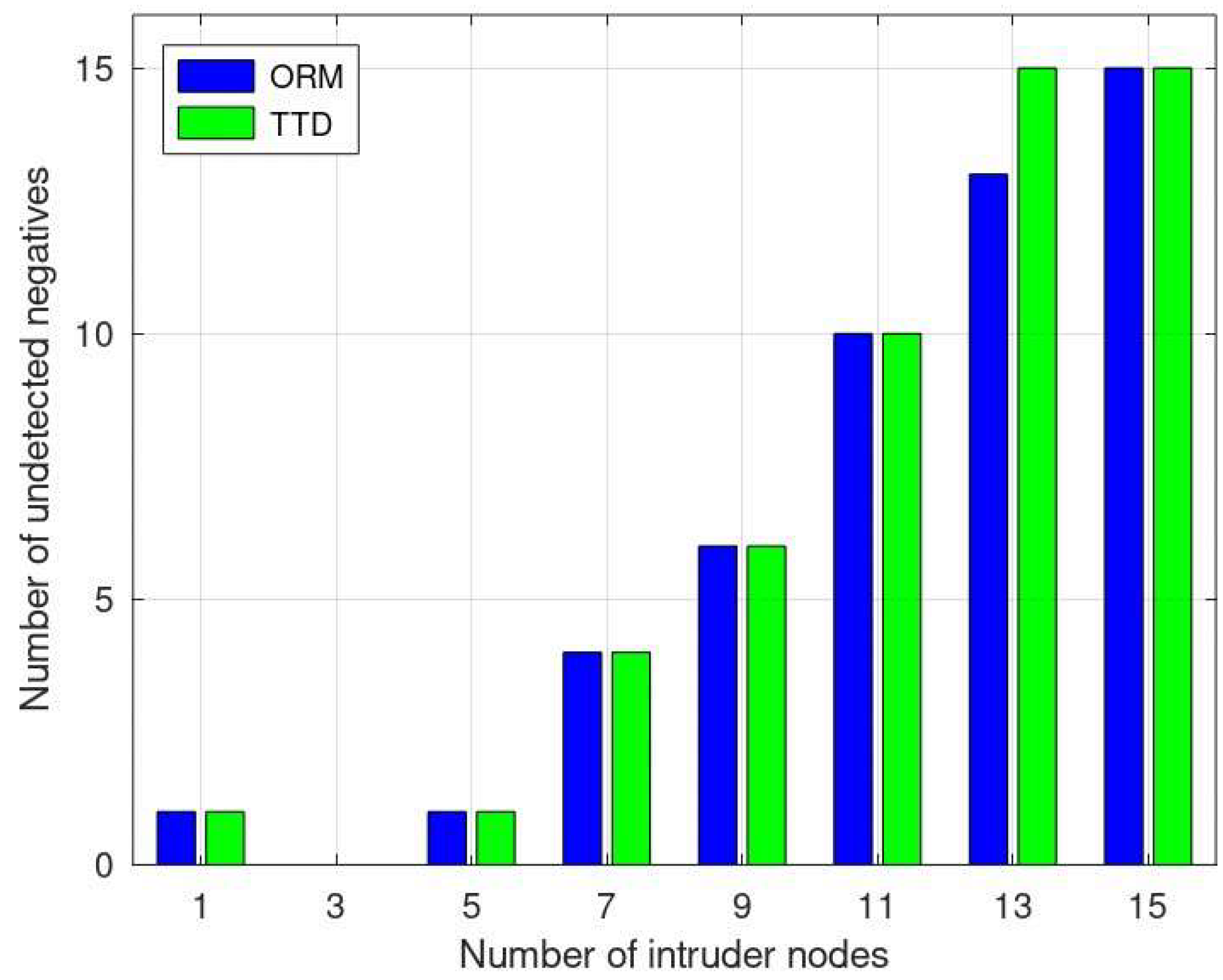
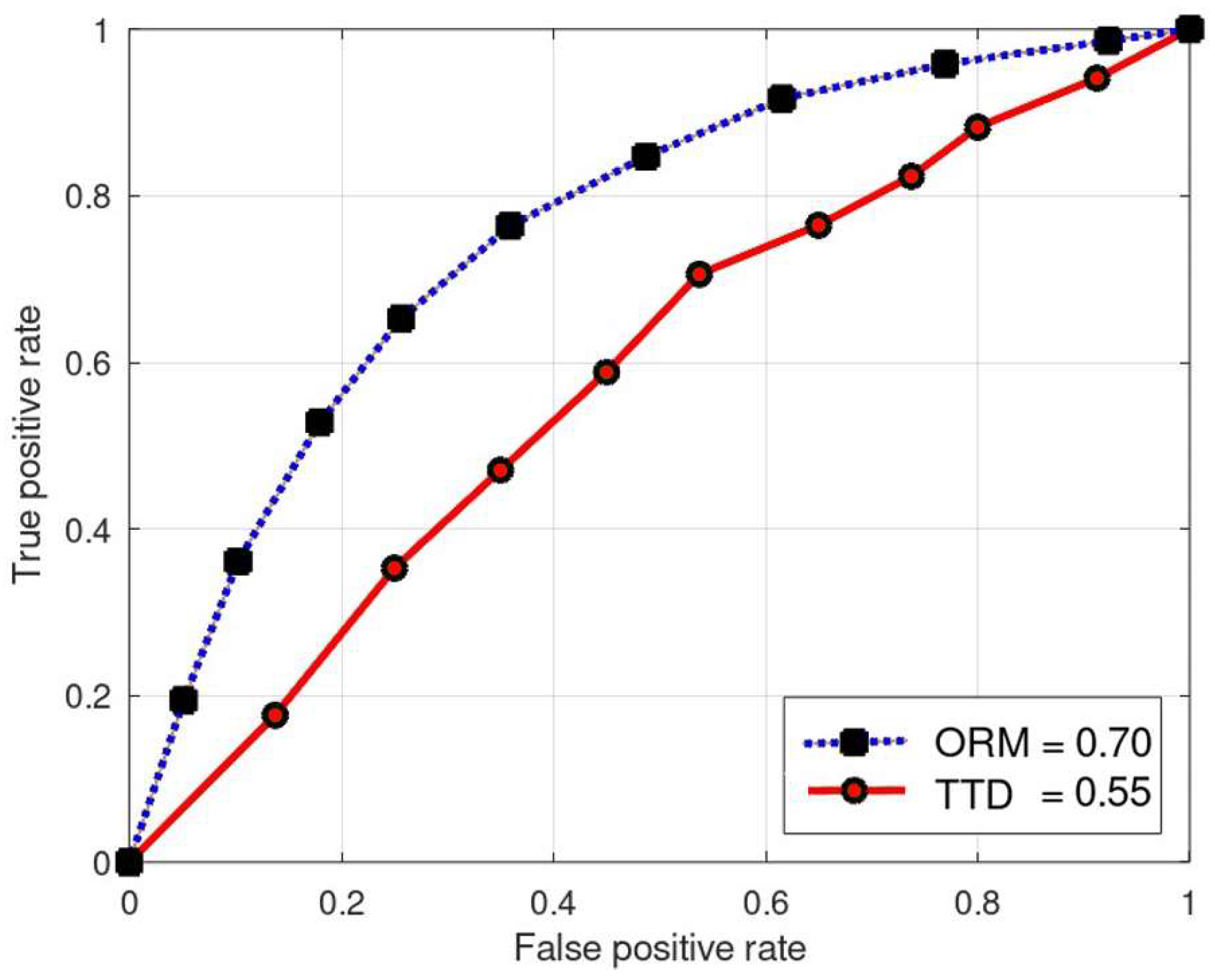
5. Simulation and Results
5.1. Performance Metrics
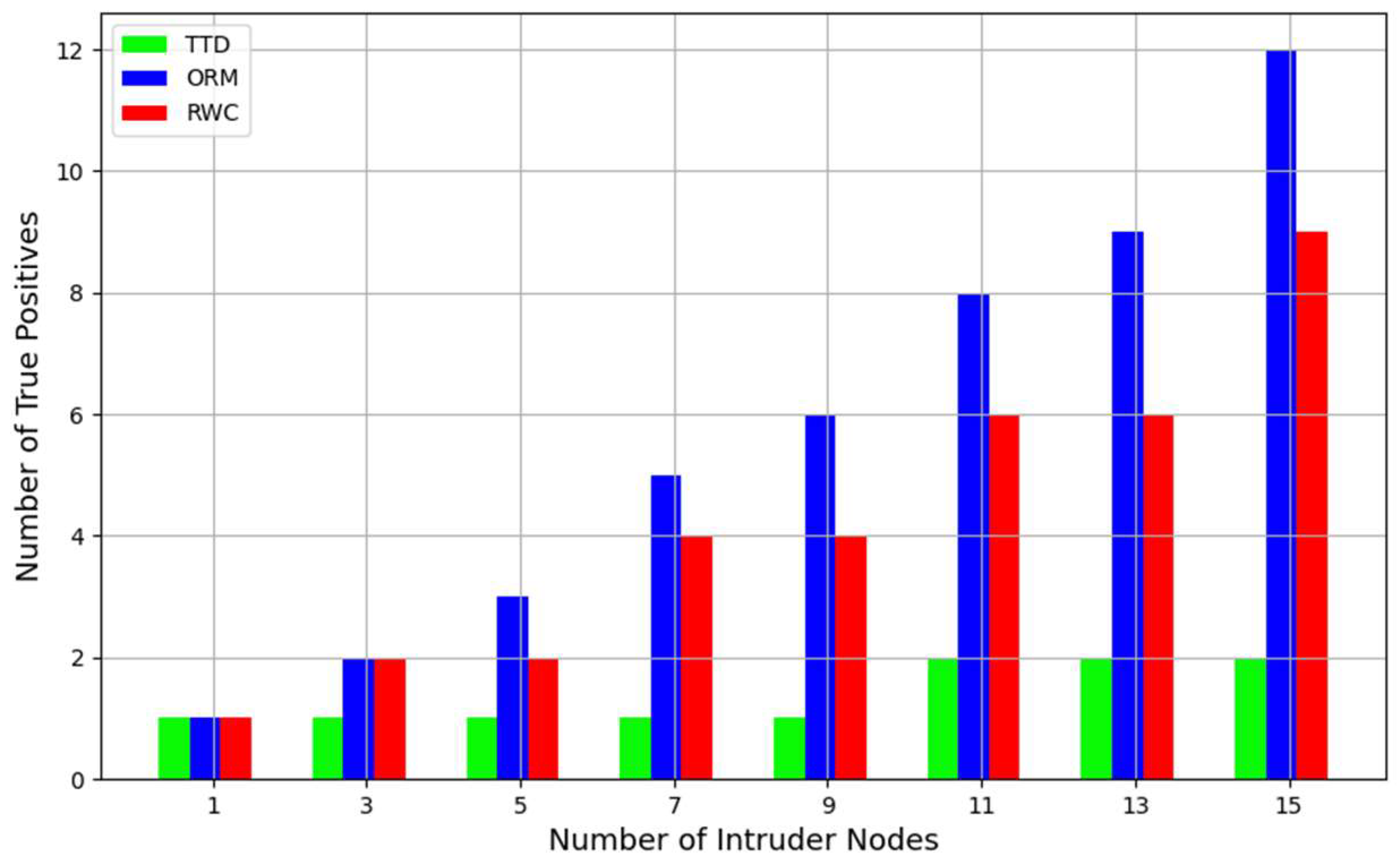
- True Positive (TP): the number of intruder nodes correctly recognized as malicious by the detection system.
- True Negative (TN): the number of benign nodes correctly identified as non-intruders by the detection system.
- False Negative (FN): the number of malicious nodes mistakenly categorized as benign by the detection system.
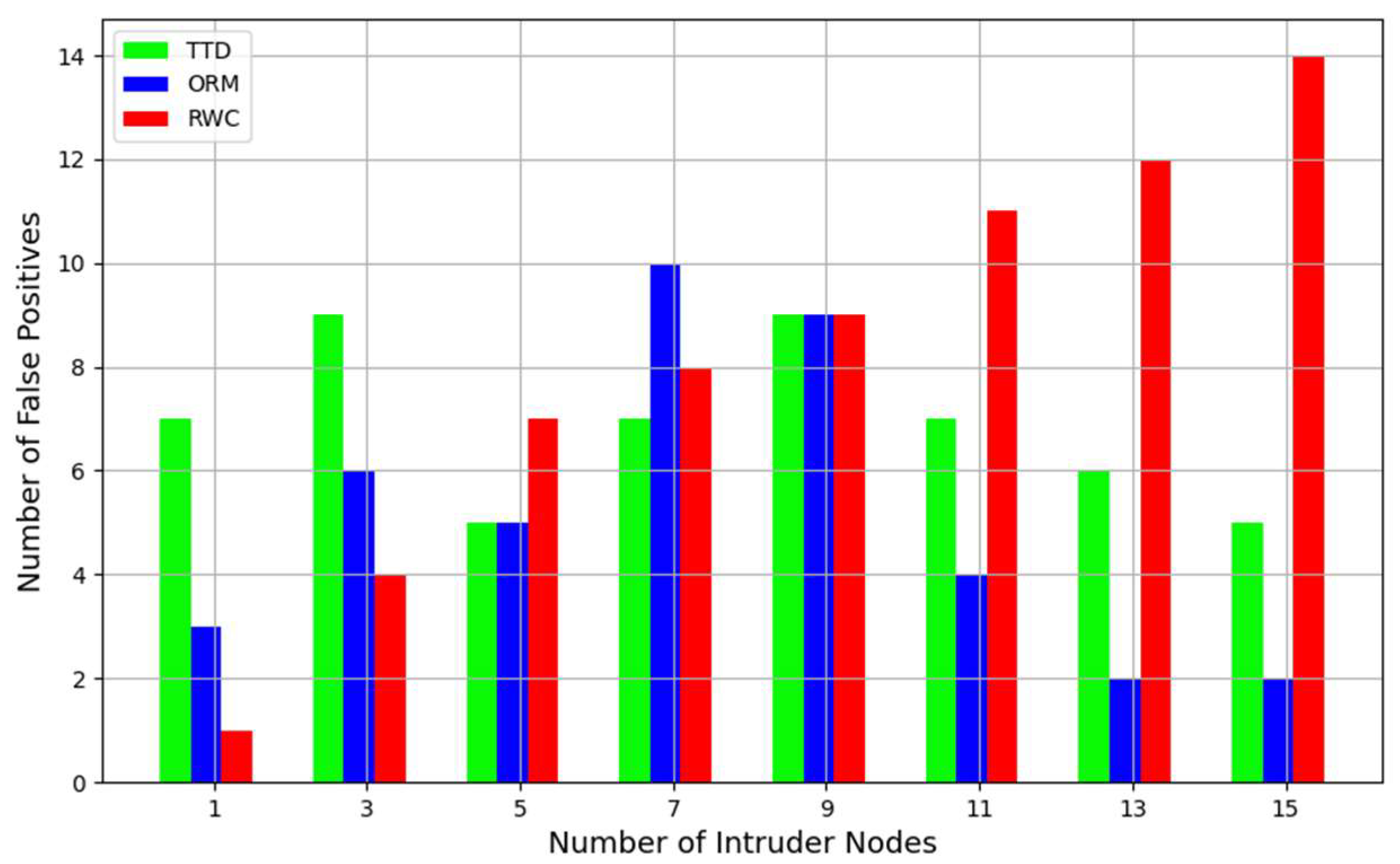
- False Positive (FP): the number of benign nodes mistakenly classified as malicious by the detection system.
- True Positive Rate (TPR): also known as sensitivity, this represents the proportion of actual positive instances (intruder nodes) that are correctly identified by the system.
- False Positive Rate (FPR): the proportion of actual negative instances (benign nodes) that are incorrectly identified as positive (misclassified as intruders).
- True Negative Rate (TNR): also known as specificity, this signifies the proportion of actual negative instances (benign nodes) that are correctly identified by the system.
- Receiver Operator Characteristic (ROC) Curve: The ROC curve is a graphical representation that illustrates the trade-off between TPR and FPR at various thresholds. It helps evaluate the performance of a classification model across different operating points.
5.2. Results
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Sahay, R.; Geethakumari, G.; Mitra, B.; Thejas, V. Exponential Smoothing based Approach for Detection of Blackhole Attacks in IoT. In Proceedings of the 2018 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), Indore, India, 16–19 December 2018. [Google Scholar]
- Ji, B.; Zhang, X.; Mumtaz, S.; Han, C.; Li, C.; Wen, H.; Wang, D. Survey on the Internet of Vehicles: Network Architectures and Applications. IEEE Commun. Stand. Mag. 2020, 4, 34–41. [Google Scholar] [CrossRef]
- Almalki, F.; Alsamhi, S.; Sahal, R.; Hassan, J.; Hawbani, A. Green IoT for Eco-Friendly and Sustainable Smart Cities: Future Directions and Opportunities. Mob. Netw. Appl. 2023, 28, 178–202. [Google Scholar] [CrossRef]
- Maple, C. Security and privacy in the internet of things. J. Cyber Policy 2017, 2, 155–184. [Google Scholar] [CrossRef]
- Airehrour, D.; Gutierrez, J.; Ray, S.K. A testbed implementation of a trust-aware RPL routing protocol. in protocol. In Proceedings of the 27th International Telecommunication Networks and Applications Conference, Melbourne, VIC, Australia, 22–24 November 2017. [Google Scholar]
- Patrick, J.; Jacinto, J.; Limjoco, W.J.; Rhodette, J. IPv6 routing protocol for low-power and lossy networks implementation in network simulator-3. In Proceedings of the TENCON 2017: IEEE Region 10 Conference (TENCON), Penang Island, Malaysia, 5–8 November 2017. [Google Scholar]
- Tim, W.; Thubert, P.; Brandt, A.; Hui, J.; Kelsey, R.; Levis, P.; Pister, K.; Struik, R.; Vasseur, P.; Alexander, R. RPL: IPv6 Routing Protocol for Low-Power and Lossy Networks; Internet Engineering Task Force (IETF): Wilmington, DE, USA, 2012. [Google Scholar]
- Airehrour, D.; Gutierrez, J.; Ray, S.K. Securing RPL routing protocol from blackhole attacks using a trust-based mechanism. In Proceedings of the 26th International Telecommunication Networks and Applications Conference (ITNAC), Dunedin, New Zealand, 7–9 December 2016. [Google Scholar]
- Wallgren, L.; Raza, S.; Voigt, T. Routing Attacks and Countermeasures in the RPL-Based Internet of Things. Int. J. Distrib. Sens. Netw. 2013, 2013, 1–11. [Google Scholar] [CrossRef]
- Raoof, A.; Matrawy, A.; Lung, C.-H. Routing Attacks and Mitigation Methods for RPL Based Internet of Things. IEEE Commun. Surv. Tutor. 2019, 21, 1582–1606. [Google Scholar] [CrossRef]
- Jiang, J.; Liu, Y.; Dezfouli, B. A Root-based Defense Mechanism against RPL Blackhole Attacks in Internet of Things Networks. In Proceedings of the APSIPA Annual Summit and Conference 2018, Honolulu, HI, USA, 12–15 November 2018. [Google Scholar]
- Sharma, D.K.; Dhurandher, S.K.; Kumaram, S.; Datta, K.G.; Kumar, P. Mitigation of black hole attacks in 6LoWPAN RPL-based Wireless sensor network for cyber physical systems. Comput. Commun. 2022, 189, 182–192. [Google Scholar] [CrossRef]
- Mekkaoui, K.; Teggar, H. Mitigation of Smart Black Hole Attacks Using Universal Sink Detection Method in Graph Theory. Available online: https://europepmc.org/article/ppr/ppr591885 (accessed on 6 March 2024).
- Javed, M.; Tariq, N.; Ashraf, M.; Khan, F.A.; Asim, M.; Imran, M. Securing Smart Healthcare Cyber-Physical Systems against Blackhole and Greyhole Attacks Using a Blockchain-Enabled Gini Index Framework. Sensors 2023, 23, 9372. [Google Scholar] [CrossRef]
- Alwis, C.D.; Porambage, P.; Dev, K.; Gadekallu, T.R.; Liyanage, M. A Survey on Network Slicing Security: Attacks, Challenges, Solutions and Research Directions. IEEE Commun. Surv. Tutor. 2023, 3, 1–23. [Google Scholar] [CrossRef]
- Wen, J.; Yang, J.; Wang, T.; Li, Y.; Lv, Z. Energy-efficient task allocation for reliable parallel computation of cluster-based wireless sensor network in edge computing. Digit. Commun. Netw. 2023, 9, 473–482. [Google Scholar] [CrossRef]
- Javaid, N. A Secure and Efficient Trust Model for Wireless Sensor IoTs Using Blockchain. IEEE Access 2022, 10, 4568–4579. [Google Scholar] [CrossRef]
- Ahmed, F.; Ko, Y.-B. Mitigation of black hole attacks in Routing Protocol for Low Power and Lossy Networks. Secur. Commun. Netw. 2016, 9, 5143–5154. [Google Scholar] [CrossRef]
- Kumar, A.; Kumar, R. A Robust Trust Model for Wireless Sensor Networks. In Proceedings of the 2018 5th IEEE Uttar Pradesh Section International Conference on Electrical, Electronics and Computer Engineering (UPCON), Gorakhpur, India, 2–4 November 2018. [Google Scholar]
- Yan, S.L.; Yu, W.; Han, Z. Information theoretic framework of trust modeling and evaluation for ad hoc networks. IEEE J. Sel. Areas Commun. 2006, 24, 305–317. [Google Scholar]
- Zhang, J.; Chen, C.; Cohen, R. A Scalable and Effective Trust-Based Framework for Vehicular Ad-Hoc Networks. J. Wirel. Mob. Netw. Ubiquitous Comput. Dependable Appl. 2010, 1, 3–15. [Google Scholar]
- Ahmed, S.; Tepe, K. Misbehaviour detection in vehicular networks using logistic trust. In Proceedings of the IEEE Wireless Communications and Networking Conference, Doha, Qatar, 3–6 April 2016. [Google Scholar]
- Wang, H.; Jiang, J.; Li, W. A Dynamic Trust Model Based on Time Decay Factor. In Proceedings of the IEEE SmartWorld, Ubiquitous Intelligence & Computing, Advanced & Trusted Computing, Guangzhou, China, 8–12 October 2018. [Google Scholar]
- Qu, C.; Ju, L.; Jia, Z.; Xu, H.; Zheng, L. Light-Weight Trust-Based On-Demand Multipath Routing Protocol for Mobile Ad Hoc Networks. In Proceedings of the 2013 12th IEEE International Conference on Trust, Security and Privacy in Computing and Communications, Melbourne, VIC, Australia, 16–18 July 2013. [Google Scholar]
- Lahbib, A.; Toumi, K.; Elleuch, S.; Laouiti, A.; Martin, S. Link reliable and trust aware RPL routing protocol for Internet of Things. In Proceedings of the IEEE 16th International Symposium on Network Computing and Applications (NCA), Cambridge, MA, USA, 30 October–1 November 2017. [Google Scholar]
- Ahmed, S.; Tepe, K. Evaluating trust models for improved event learning in VANETs. In Proceedings of the IEEE 30th Canadian Conference on Electrical and Computer Engineering (CCECE), Windsor, ON, Canada, 30 April–3 May 2017. [Google Scholar]
- Guo, J.; Ma, J.; Wan, T. A Mutual Evaluation Based Trust Management Method for Wireless Sensor Networks. Chin. J. Electron. 2017, 26, 407–415. [Google Scholar] [CrossRef]
- Bhargava, A.; Verma, S.; Kumar, B.; Tomar, G. Computational trust model for Internet of Vehicles. In Proceedings of the 2017 Conference on Information and Communication Technology (CICT), Gwalior, India, 3–5 November 2017. [Google Scholar]
- Otoum, S.; Kantarci, B.; Mouftah, H. Hierarchical trust-based black-hole detection in WSN-based smart grid monitoring. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017. [Google Scholar]
- Wu, D.; Wu, J.; Wang, R. An Energy-efficient and Trust-based Formation Algorithm for Cooperative Vehicle Platooning. In Proceedings of the 2019 International Conference on Computing, Networking and Communications (ICNC), Honolulu, HI, USA, 18–21 February 2019. [Google Scholar]
- Khan, Z.A.; Herrmann, P. A Trust Based Distributed Intrusion Detection Mechanism for Internet of Things. In Proceedings of the IEEE 31st International Conference on Advanced Information Networking and Applications (AINA), Taipei, Taiwan, 27–29 March 2017. [Google Scholar]
- Zawaideh, F.; Salamah, M.; Al-Bahadili, H. A fair trust-based malicious node detection and isolation scheme for WSNs. Int. J. Commun. Syst. 2018, 32, 78–85. [Google Scholar]
- Mehta, R.; Parmar, M. Trust based mechanism for Securing IoT Routing Protocol RPL against Wormhole & Grayhole Attacks. In Proceedings of the 3rd International Conference for Convergence in Technology (I2CT), Pune, India, 6–7 April 2018. [Google Scholar]
- Tandon, A.; Srivastava, P. Trust-based Enhanced Secure Routing against Rank and Sybil Attacks in IoT. In Proceedings of the Twelfth International Conference on Contemporary Computing (IC3), Noida, India, 8–10 August 2019. [Google Scholar]
- Mathew, M.; Gayathri, I.; Raj, A. An efficient distributed TCNPR method for wireless sensor networks. In Proceedings of the International Conference on Energy, Communication, Data Analytics and Soft Computing (ICECDS), Chennai, India, 1–2 April 2017. [Google Scholar]
- Basan, A.; Basan, E.; Makarevich, O. A Trust Evaluation Method for Active Attack Counteraction in Wireless Sensor Networks. In Proceedings of the 2017 International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery (CyberC), Nanjing, China, 12–14 October 2017. [Google Scholar]
- Maidhili, S.; Gushwal, K. Intrusion Detection and Prevention Based on State Context and Hierarchical Trust in Wireless Sensor Networks. In Proceedings of the International Conference on Computer Communication and Informatics (ICCCI), Coimbatore, India, 4–6 January 2018. [Google Scholar]
- Azzedin, F. Mitigating Denial of Service Attacks in RPL-Based IoT Environments: Trust-Based Approach. IEEE Access 2023, 11, 129077–129089. [Google Scholar] [CrossRef]
- Al-Sarawi, S.; Anbar, M.; Alabsi, B.A.; Aladaileh, M.A.; Ahmed, S.D. Passive Rule-Based Approach to Detect Sinkhole Attack in RPL-Based Internet of Things Networks. IEEE Access 2023, 11, 94081–94093. [Google Scholar] [CrossRef]
- Tong, F.; Chen, C.; Pan, J. A Novel Detection and Localization Scheme for Wormhole Attack in Internet of Things. IEEE Internet Things J. 2023, 11, 7141–7152. [Google Scholar] [CrossRef]
- Zhang, K.; Liang, X.; Lu, R.; Shen, X. Sybil Attacks and Their Defenses in the Internet of Things. IEEE Internet Things J. 2014, 2014, 372–383. [Google Scholar] [CrossRef]
- Boudouaia, M.A.; Ali-Pacha, A.; Abouaissa, A.; Lorenz, P. Security against Rank Attack in RPL Protocol. IEEE Netw. 2020, 34, 133–139. [Google Scholar] [CrossRef]
- Sharma, G.; Grover, J.; Verma, A. Performance evaluation of mobile RPL-based IoT networks under version number attack. Comput. Commun. 2023, 197, 12–22. [Google Scholar] [CrossRef]
- Sahay, R.; Geethakumari, G.; Mitra, B. Mitigating the worst parent attack in RPL based internet of things. Clust. Comput. 2022, 25, 1303–1320. [Google Scholar] [CrossRef]
- Raoof, A.; Matrawy, A.; Lung, C.-H. Enhancing Routing Security in IoT: Performance Evaluation of RPL’s Secure Mode Under Attacks. IEEE Internet Things J. 2020, 7, 11536–11546. [Google Scholar] [CrossRef]



Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khan, M.A.; Rais, R.N.B.; Khalid, O.; Ahmad, S. Trust-Based Optimized Reporting for Detection and Prevention of Black Hole Attacks in Low-Power and Lossy Green IoT Networks. Sensors 2024, 24, 1775. https://doi.org/10.3390/s24061775
Khan MA, Rais RNB, Khalid O, Ahmad S. Trust-Based Optimized Reporting for Detection and Prevention of Black Hole Attacks in Low-Power and Lossy Green IoT Networks. Sensors. 2024; 24(6):1775. https://doi.org/10.3390/s24061775
Chicago/Turabian StyleKhan, Muhammad Ali, Rao Naveed Bin Rais, Osman Khalid, and Sanan Ahmad. 2024. "Trust-Based Optimized Reporting for Detection and Prevention of Black Hole Attacks in Low-Power and Lossy Green IoT Networks" Sensors 24, no. 6: 1775. https://doi.org/10.3390/s24061775
APA StyleKhan, M. A., Rais, R. N. B., Khalid, O., & Ahmad, S. (2024). Trust-Based Optimized Reporting for Detection and Prevention of Black Hole Attacks in Low-Power and Lossy Green IoT Networks. Sensors, 24(6), 1775. https://doi.org/10.3390/s24061775







