ANN-Based Intelligent Secure Routing Protocol in Vehicular Ad Hoc Networks (VANETs) Using Enhanced AODV
Abstract
1. Introduction
1.1. Navigating Vehicular Ad Hoc Networks
1.2. Clustering Strategies in Vehicular Ad Hoc Networks
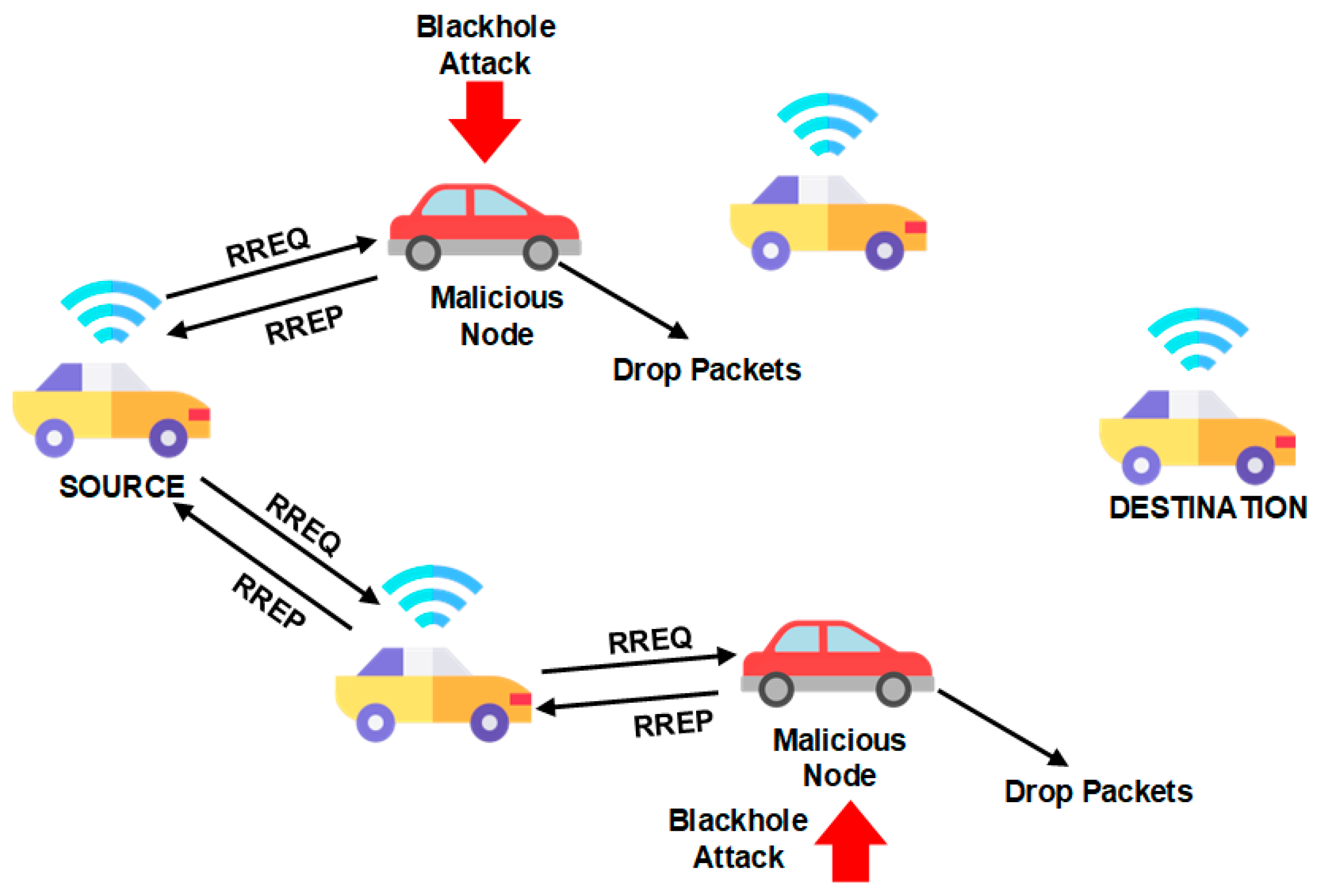
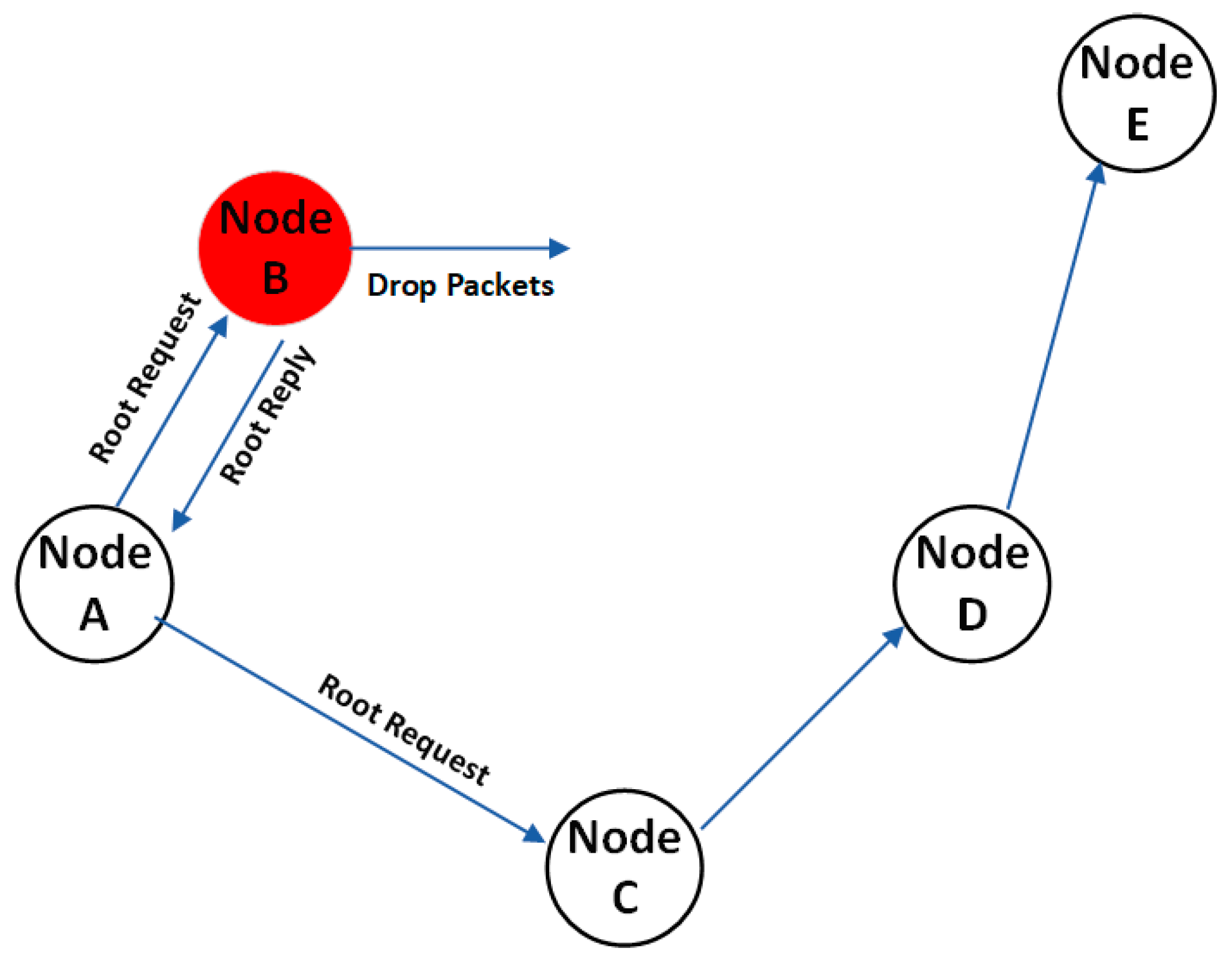
1.3. Cyber Attack Scenarios in VANET

1.4. Machine Learning in VANET Routing Prediction
1.5. Research Motivation
- The development of a cluster-based routing technique to facilitate the efficient delivery of content.
- The detection of malicious nodes in VANET through the application of deep learning.
- The establishment of optimal pathways to ensure the efficient delivery of data to their intended destinations.
1.6. Problem Statement
1.7. Research Contributions
- An innovative, secure routing protocol was introduced to combat black hole attacks within VANETs. This protocol is designed to optimize the allocation of tasks by selecting the most secure and efficient path for data transmission.
- Integrating a cluster-based routing technique facilitates the streamlined delivery of content to the target vehicle following a meticulous verification process based on the vehicle’s past performance, utilizing ANNs.
- Establishing clusters through a meticulously designed algorithm incorporating security considerations further bolsters the dependability of the hop count in the network.
- The deployment of ANN techniques to identify and combat black hole attacks and secure routing within VANETs. This approach leverages knowledge and related skills to pinpoint routing paths between source and destination nodes accurately.
- Implementing an authentication-based method for efficient content delivery ensures secure analysis and path prediction. This is achieved by utilizing a modified AODV algorithm, which effectively predicts the route after securing the network using an ANN-based machine learning (ML) algorithm.
- Section 2 explores related work focused on secure routing within VANETs, shedding light on previously adopted methodologies. Various established secure routing solutions are presented alongside examining multiple clustering techniques. Towards the conclusion of this section, diverse machine-learning methods for detecting malicious nodes are scrutinized.
- Section 3 intricately expounds upon the proposed solution framework and model diagram. Secure routing is realized through a cluster-based machine learning model and a modified AODV algorithm. This section elucidates the proposed solution by incorporating diverse flowcharts and model diagrams, ensuring a lucid comprehension of the methodology.
- Section 4 involves simulating our techniques within a suitable simulation environment, utilizing the NS-2 simulator and Python for machine learning. Existing datasets are harnessed for model training, and this section offers a comprehensive description of the experimental setup and various components of the experiments.
- Lastly, Section 5 concludes the paper, and potential avenues for future research are delineated.
2. Literature Review
2.1. Effectual Routing Strategies
2.2. Machine Learning-Based Approaches for the Identification of Malicious Nodes
3. Intelligent Cluster-Based Routing Approach
3.1. Routing Attack Scenario
3.2. The Optimal and Secure Route Minimizing Communication Latency to the Fullest Extent
3.3. Intelligent Path Prediction
- Enhanced route discovery: Modified AODVs employ advanced algorithms to optimize the route discovery process. It uses techniques like improved route request broadcasting and route reply propagation. This enhancement reduces the time taken to establish a route.
- Classification parameter: The modifications introduce a classification parameter that helps categorize routes based on their stability and reliability. This parameter is used to select the most suitable route for data transmission.
- Dynamic route maintenance: Modified AODVs adapt to network changes more efficiently. It incorporates mechanisms for monitoring the stability of routes and triggers route updates when necessary. This ensures that the protocol can quickly react to link failures and changes in network topology.
- Load balancing: The modified version is designed to distribute traffic evenly across available routes, preventing congestion and improving overall network performance. This is achieved through route selection algorithms that consider the current network load.
- Improved scalability: The modifications address scalability concerns by optimizing the route table management. It can handle a larger number of nodes in the network without a significant increase in control overhead.
- The main advantage of this AODV modification is that it enhances the proposed system’s performance. Reduced latency: The improved route discovery and maintenance mechanisms reduce the latency in establishing and maintaining routes. This is crucial for real-time applications like video streaming and online gaming.
- Enhanced reliability: The classification parameter helps select more reliable and stable routes, reducing packet losses and improving communication quality.
- Adaptability: The protocol can quickly adapt to changes in the network, such as node mobility or link failures, making it suitable for dynamic ad hoc networks.
- Efficient Resource Utilization: Load balancing and scalability improvements ensure that network resources are utilized efficiently, leading to better network performance and longevity.
- Improved quality of service support: The modifications enhance the support for quality of service (QoS) by allowing for a better selection of routes based on specific application requirements.
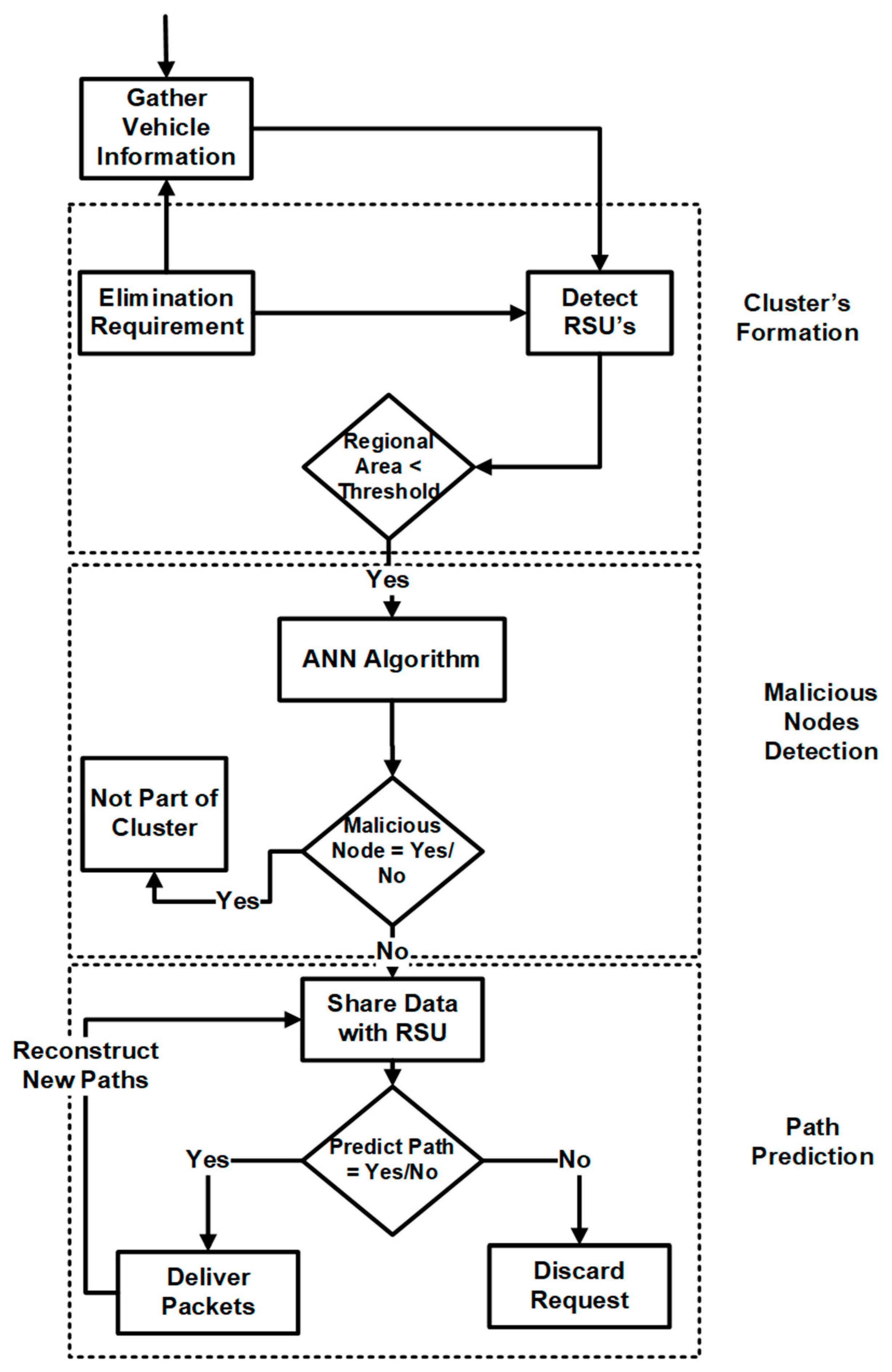
3.4. Cluster Formation
| Algorithm 1. Cluster formation |
| Input: Output: Cluster, Number of Clusters |
Steps:
|
| Algorithm 2. Black hole attack detection through deep learning |
| Input: Output: |
| STEPS: TRAINING MODEL OF MACHINE LEARNING
|
- Initially, a vehicular node broadcasts a timestamp (ML parameter) to RSU. Then, RSU checks the speed of node i-e. If it is less than the speed threshold, it is considered eligible for permanent connection with RSU; if it is greater than the threshold, it forms a temporary connection with RSU, then the direction of the node is checked.
- After that, all the ML parameters are applied for malicious node detection. The node’s packet delivery and packet drop information, i.e., the node’s previous behavior, is taken from the previous RSU.
- After verifying present and previous behavior through the deep learning classifier ANN, the node is declared secure and becomes part of the secure cluster.
3.5. Path Prediction
- Route Request Mode: In this mode, a request for a route is disseminated to all neighboring nodes, persisting until it ultimately arrives at the intended destination.
- Route Reply Mode: In this mode, each neighboring node that can potentially offer a route to the destination responds by providing the route information to the source node. The source node then forwards the message via the route characterized by the most prominent sequence number.
- Route Maintenance Phase: This phase comes into play when a route fails to transmit a message to the destination.
3.5.1. Route Request and Route Reply
3.5.2. Route Maintenance
| Algorithm 3. Path prediction using modified AODV |
| Input Output: Predicted path, targeted path |
|
4. Performance Evaluation
4.1. Simulation Scenario
4.2. Dataset and Evaluation Results
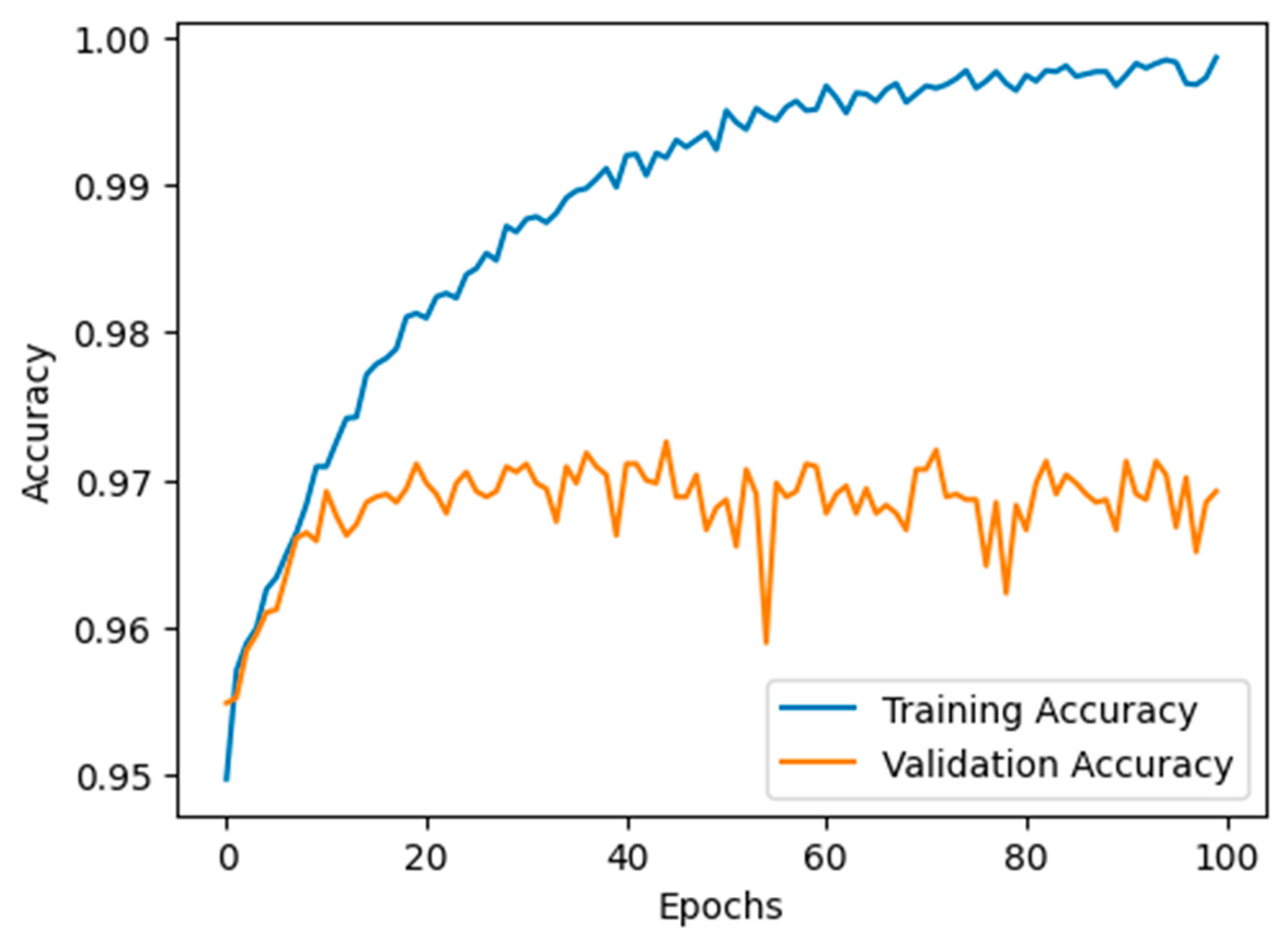
4.3. Model Accuracy
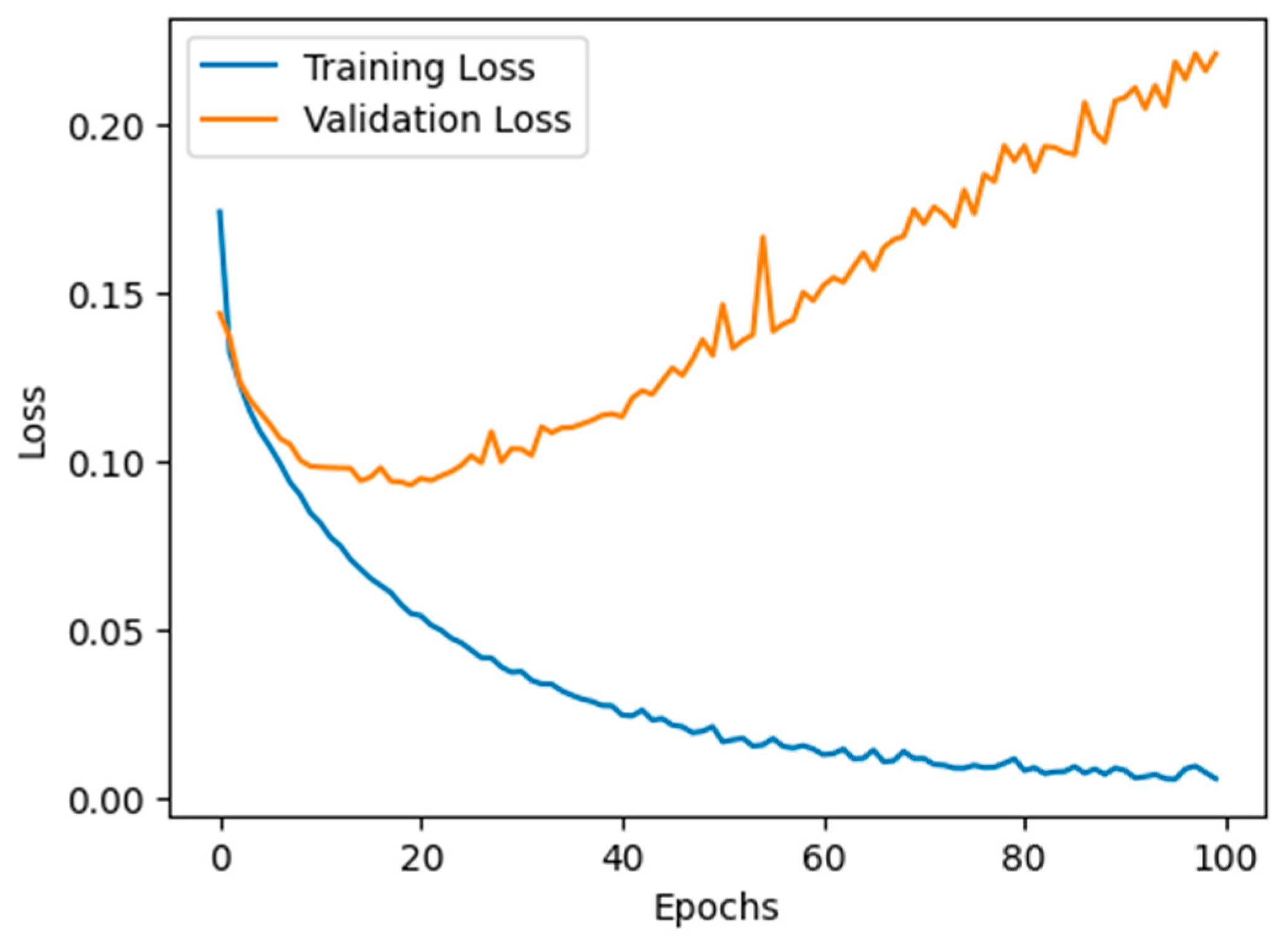
4.4. Model Loss
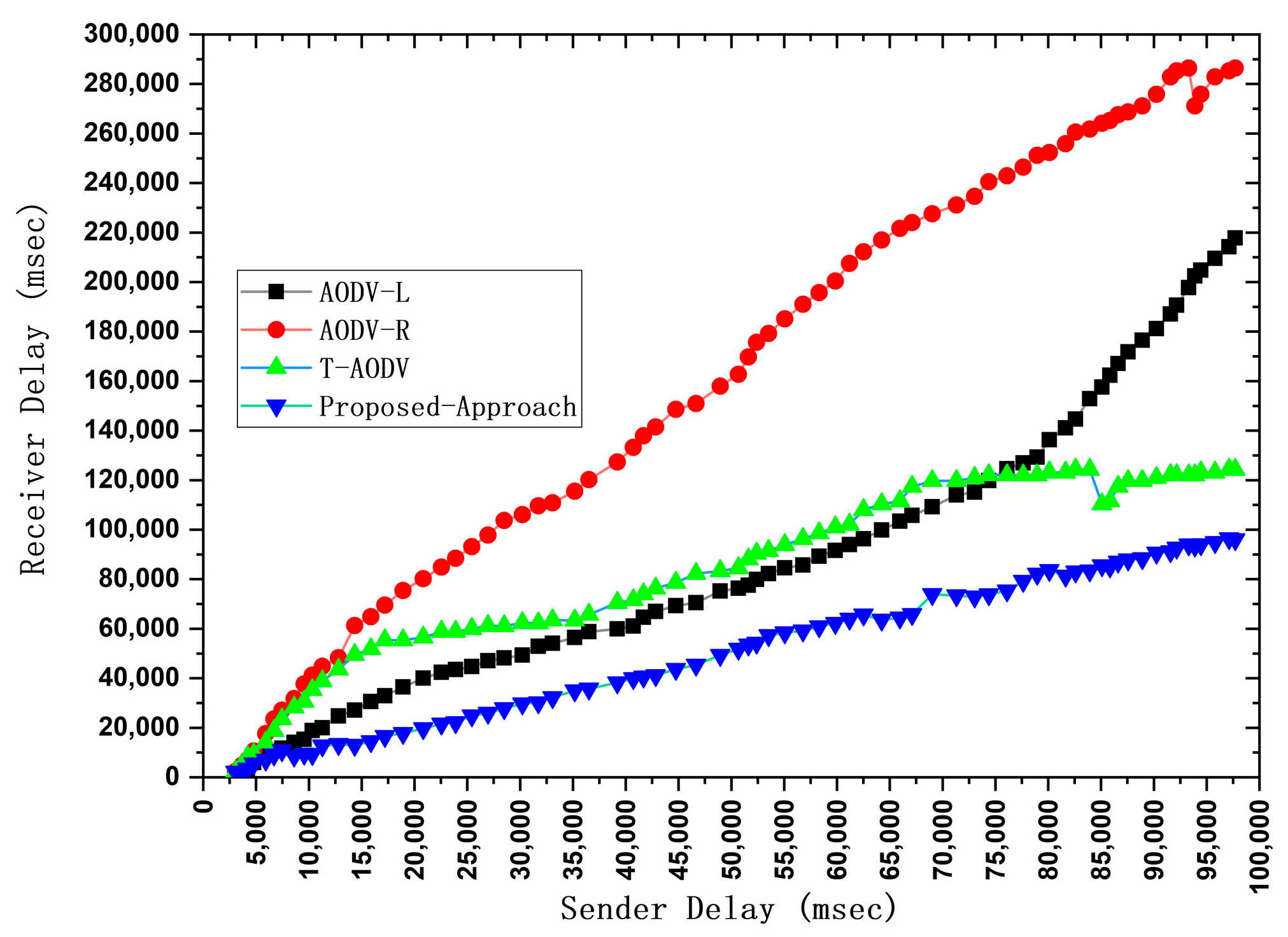
4.5. End-to-End Delay
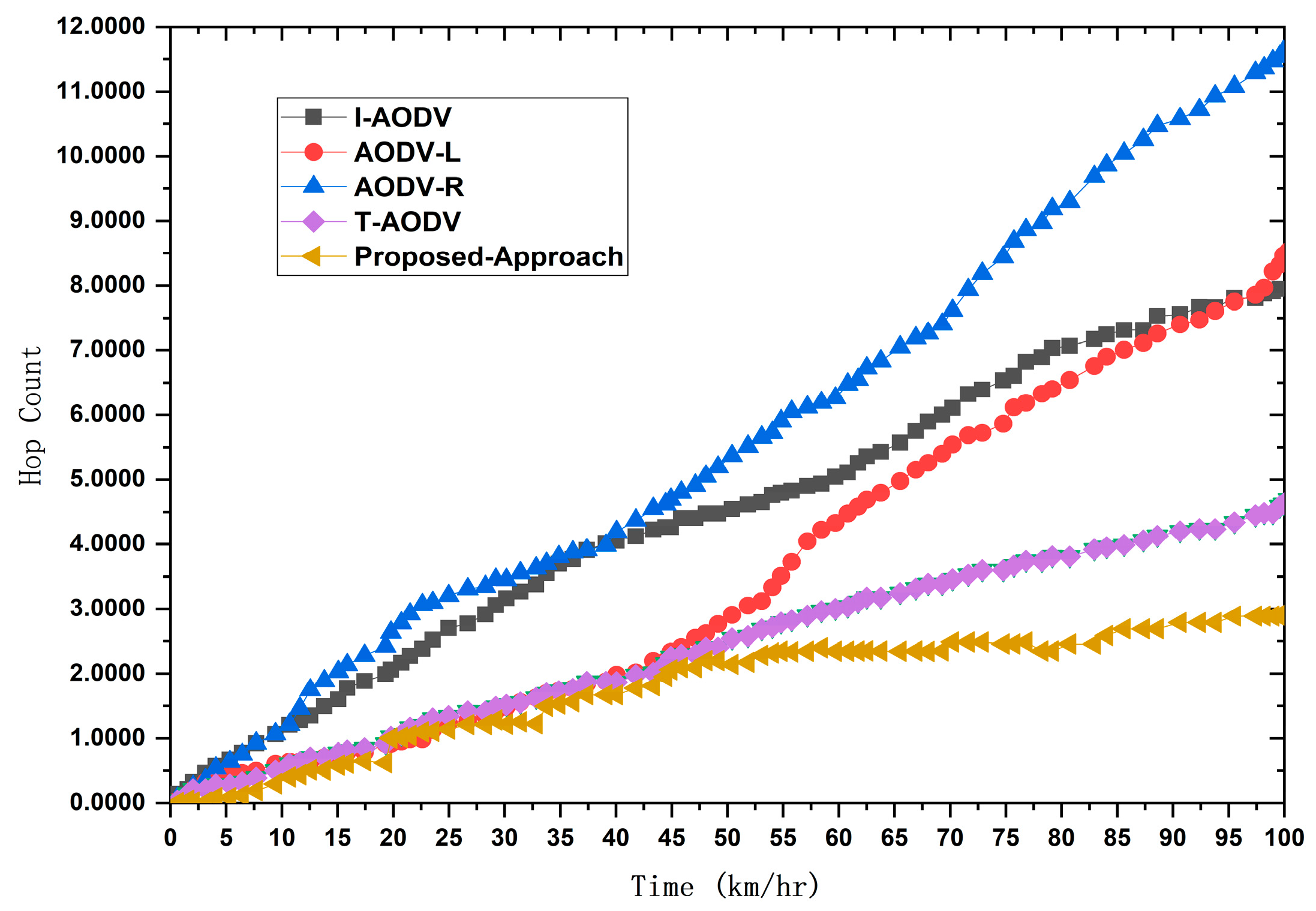
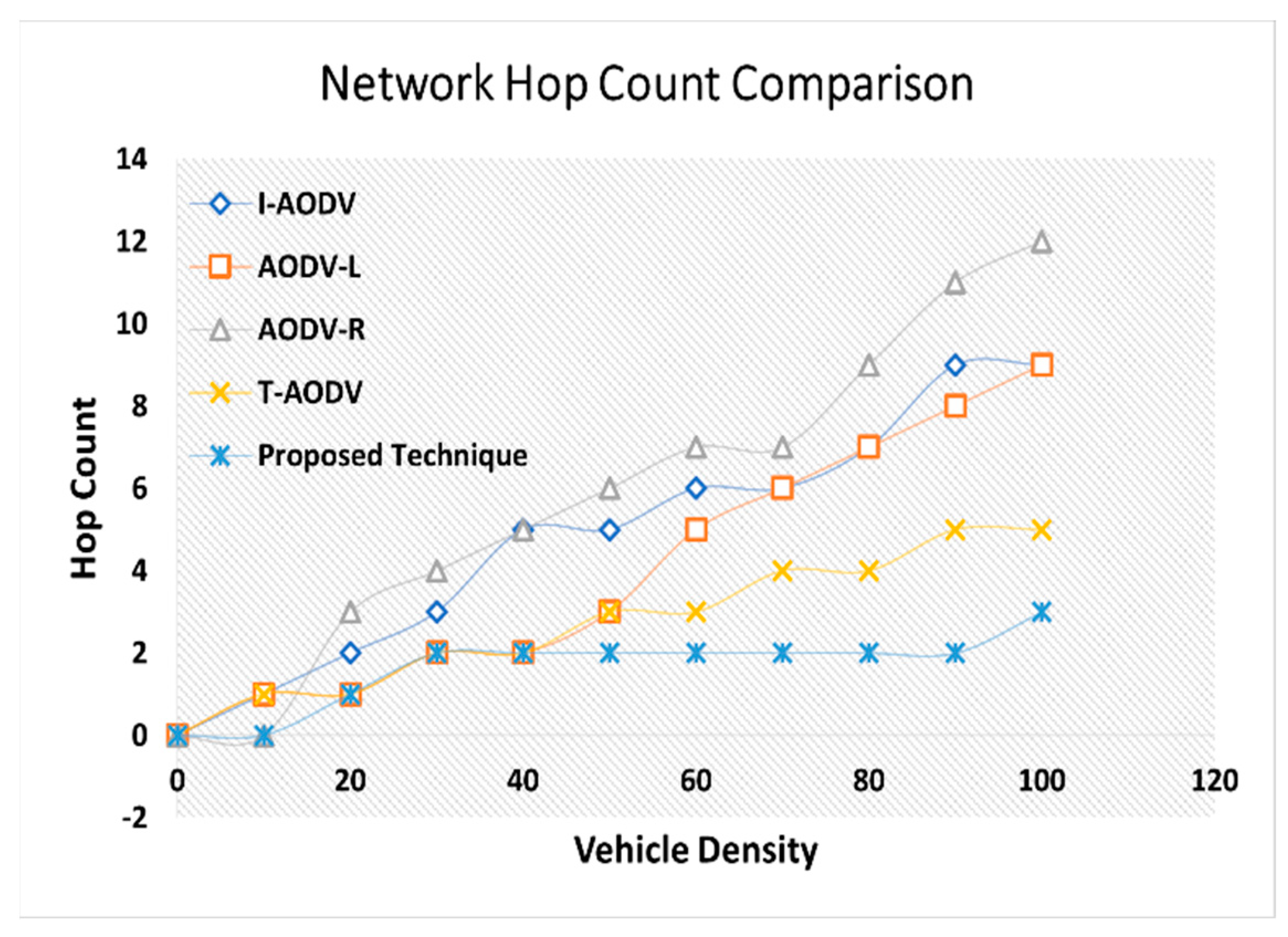
4.6. Average Hop Count
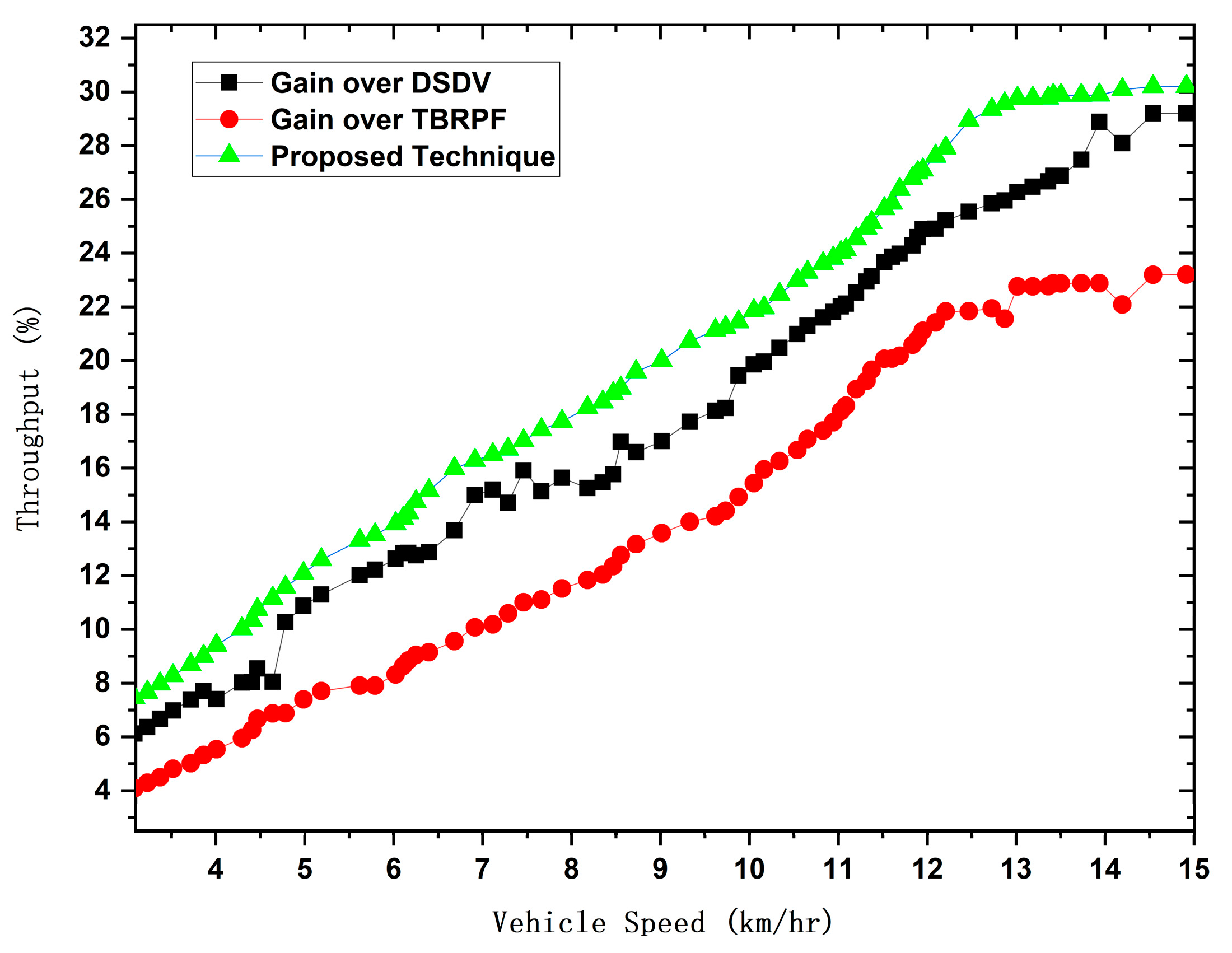
4.7. Average Hop Count/Throughout
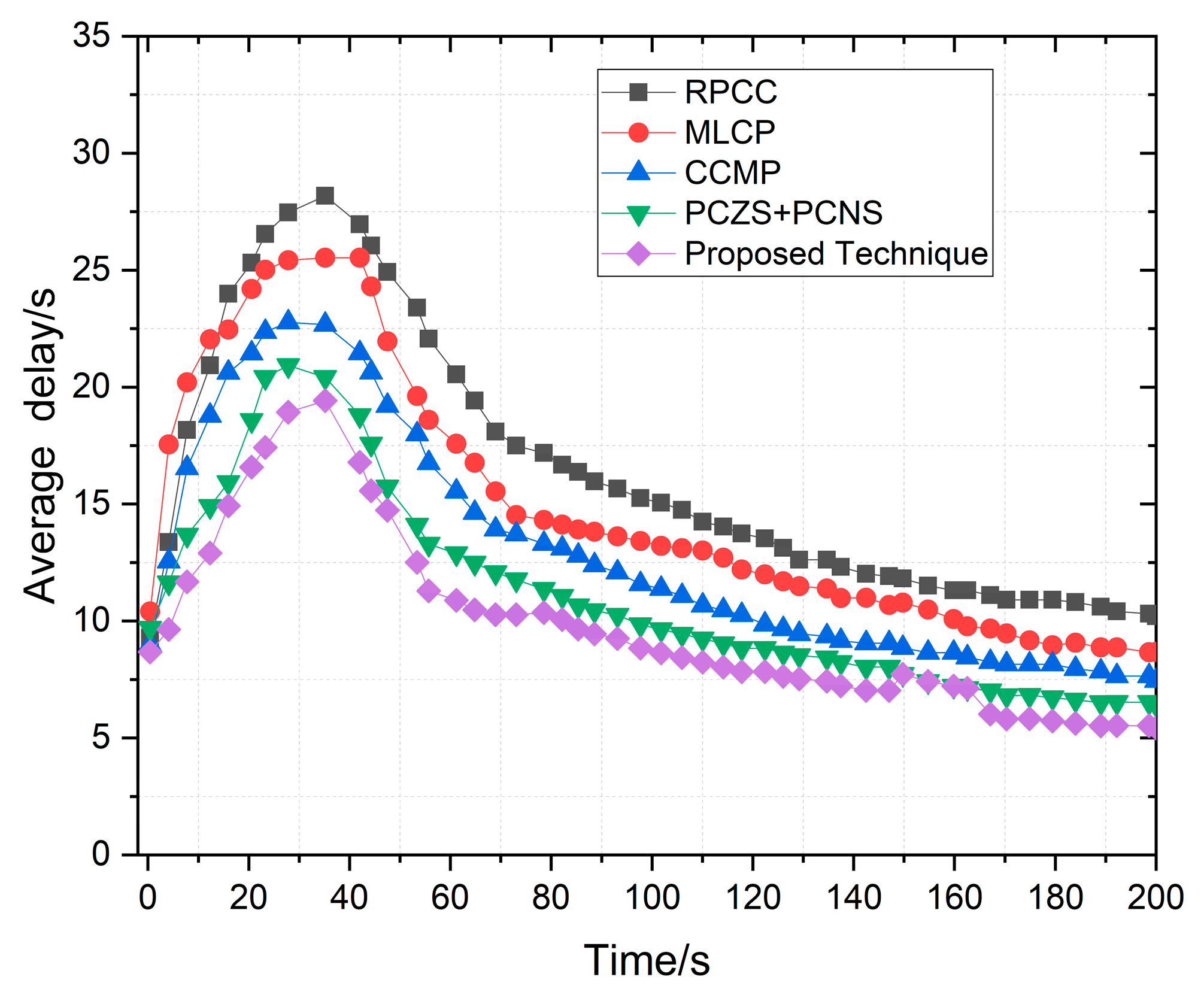
4.8. Average Delay
5. Conclusions, Limitations, and Future Directions
- This study was confined to identifying black hole attacks within the VANET environment.
- It is worth noting that neural networks are susceptible to adversarial attacks, which can potentially induce erroneous results within the network. This vulnerability becomes particularly pronounced in vehicular ad hoc networks, where malicious nodes can readily manipulate data.
- Detecting black hole attacks primarily centers on routing aspects but is delimited to the research dimensions concerning network load balancing and its intricacies.
- While proficient in identifying the shortest, most secure, and efficient routes from source to destination nodes, the research was limited to facilitating confidential communications exclusively among vehicles engaged in specialized convoy operations, which have implications for national security.
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Azzoug, Y.; Boukra, A. Improved junction-based routing for VANETs using a Bio-inspired route stability approach. Ad Hoc Netw. 2024, 153, 103346. [Google Scholar] [CrossRef]
- Ali, A.; Iqbal, M.M.; Jabbar, S.; Asghar, M.N.; Raza, U.; Al-Turjman, F. VABLOCK: A blockchain-based secure communication in V2V network using icn network support technology. Microprocess. Microsyst. 2022, 93, 104569. [Google Scholar] [CrossRef]
- Azam, F.; Sunil, K.; Yadav, N.P.; Sanjeevikumar, P.; Ramesh, C.B. A comprehensive review of authentication schemes in vehicular ad-hoc network. IEEE Access 2021, 9, 31309–31321. [Google Scholar] [CrossRef]
- Kumar, A.; Vijayakumar, V.; Abhishek, K.; Pankaj, D.; Surendra, S.C.; Ambeth Kumar, V.D.; Bijaya, K.P.; Kalyana, C.V. Black hole attack detection in vehicular ad-hoc network using secure AODV routing algorithm. Microprocess. Microsyst. 2021, 80, 103352. [Google Scholar] [CrossRef]
- IEEE 1471-2000; IEEE Recommended Practice for Architectural Description for Software-Intensive Systems. IEEE: Piscataway, NJ, USA, 2023. Available online: https://standards.ieee.org/ieee/1471/2187 (accessed on 18 December 2023).
- ISO/IEC/IEEE 42010:2022; Software, Systems and Enterprise Architecture Description. IEEE: Piscataway, NJ, USA, 2022. Available online: https://www.iso.org/standard/74393.html (accessed on 18 December 2023).
- Kannan, S.; Gaurav, D.; Yuvaraj, N.; Ashutosh, S.; Sachi, N.M.; Mukesh, S.; Udayakumar, E.; Hamidreza, G.; Alia, A.; Mehdi, G. Ubiquitous vehicular ad-hoc network computing using deep neural network with iot-based bat agents for traffic management. Electronics 2021, 10, 785. [Google Scholar] [CrossRef]
- Günay, F.B.; Ercüment, Ö.; Tuğrul, Ç.Y.; Sinan, H.; Atta ur Rehman, K. Vehicular ad hoc network (VANET) localization techniques: A survey. Arch. Comput. Methods Eng. 2021, 28, 3001–3033. [Google Scholar] [CrossRef]
- Ali, A.; Muhammad, M.I.; Harun, J.; Habib, A.; Ammar, M.; Meryem, A.; Maha, M.A. Multilevel central trust management approach for task scheduling on IoT-based mobile cloud computing. Sensors 2021, 22, 108. [Google Scholar] [CrossRef]
- Shahwani, H.; Syed, A.S.; Muhammad, A.; Muhammad, A.; Jaehoon, P.J.; Jitae, S. A comprehensive survey on data dissemination in Vehicular Ad Hoc Networks. Veh. Commun. 2022, 34, 100420. [Google Scholar] [CrossRef]
- Aung, N.; Sahraoui, D.; Liming, C.; Wenyin, Z.; Abderrahmane, L.; Huansheng, N. VeSoNet: Traffic-aware content caching for vehicular social networks based on path planning and deep reinforcement learning. arXiv 2021, arXiv:2111.05567. [Google Scholar]
- Jamil, F.; Harun, J.; Abid, A. Spoofing Attack Mitigation in Address Resolution Protocol (ARP) and DDoS in Software-Defined Networking. J. Inf. Secur. Cybercrimes Res. 2022. Available online: https://repository.nauss.edu.sa/handle/123456789/67196 (accessed on 18 December 2023). [CrossRef]
- Agarwal, V.; Sachin, S.; Piyush, A. IoT based smart transport management and vehicle-to-vehicle communication system. In Computer Networks, Big Data and IoT: Proceedings of ICCBI 2020; Springer: Singapore, 2021; pp. 709–716. [Google Scholar]
- Husnain, G.; Anwar, S.; Sikander, G.; Ali, A.; Lim, S. A bio-inspired cluster optimization schema for efficient routing in vehicular ad hoc networks (VANETs). Energies 2023, 16, 1456. [Google Scholar] [CrossRef]
- Rana, K.H.; Vishnu, S.; Gagan, T. Fuzzy logic-based multi-hop directional location routing in vehicular ad-hoc network. Wirel. Pers. Commun. 2021, 121, 831–855. [Google Scholar] [CrossRef]
- Ahmad, S.; Salman, K.; Faisal, J.; Faiza, Q.; Abid, A.; DoHyeun, K. Design of a general complex problem-solving architecture based on task management and predictive optimization. Int. J. Distrib. Sens. Netw. 2022, 18, 15501329221107868. [Google Scholar] [CrossRef]
- He, C.; Guanqiao, Q.; Liang, Y.; Shouming, W. A two-level communication routing algorithm based on vehicle attribute information for vehicular ad hoc network. Wirel. Commun. Mob. Comput. 2021, 2021, 6692741. [Google Scholar] [CrossRef]
- Rashid, S.A.; Lukman, A.; Mustafa, M.H.; Sameer, A. Prediction based efficient multi-hop clustering approach with adaptive relay node selection for VANET. J. Commun. 2020, 15, 332–344. [Google Scholar] [CrossRef]
- Senouci, O.; Harous, S.; Aliouat, Z. Survey on vehicular ad hoc networks clustering algorithms: Overview, taxonomy, challenges, and open research issues. Int. J. Commun. Syst. 2020, 33, e4402. [Google Scholar] [CrossRef]
- Elhoseny, M.; Shankar, K. Energy efficient optimal routing for communication in VANETs via clustering model. In Emerging Technologies for Connected Internet of Vehicles and Intelligent Transportation System Networks: Emerging Technologies for Connected and Smart Vehicles; Springer: Berlin/Heidelberg, Germany, 2020; pp. 1–14. [Google Scholar]
- Bensalah, F.; Najib, E.; Youssef, B. SDNStat-Sec: A statistical defense mechanism against DDoS attacks in SDN-based VANET. In Advances on Smart and Soft Computing: Proceedings of ICACIn 2020; Springer: Singapore, 2021; pp. 527–540. [Google Scholar]
- Khan, S.; Ishita, S.; Mazzamal, A.; Muhammad, Z.K.; Shahzad, K. Security challenges of location privacy in VANETs and state-of-the-art solutions: A survey. Future Internet 2021, 13, 96. [Google Scholar] [CrossRef]
- Sharma, S.; Ajay, K.; Suhaib, A.; Surbhi, S. A detailed tutorial survey on VANETs: Emerging architectures, applications, security issues, and solutions. Int. J. Commun. Syst. 2021, 34, e4905. [Google Scholar] [CrossRef]
- Ali, A.; Jamil, F.; Whangbo, T.; Ahmad, S. AI-Enabled Cybernetic Analytics of Security Modles for Smart Serious Games-Based Mobile Operating Systems. In Proceedings of the 9th International Conference on Artificial Intelligence and Applications (AIAP 2022), Vancouver, BC, Canada, 26–27 February 2022. [Google Scholar]
- Monfared, S.K.; Shokrollahi, S. DARVAN: A fully decentralized anonymous and reliable routing for VANets. Comput. Netw. 2023, 223, 109561. [Google Scholar] [CrossRef]
- Balan, K.; Abdulrazak, L.F.; Khan, A.S.; Julaihi, A.A.; Tarmizi, S.; Pillay, K.S.; Sallehudin, H. RSSI and public key infrastructure based secure communication in autonomous vehicular networks. Int. J. Adv. Comput. Sci. Appl. 2018, 9, 1047–1106. [Google Scholar] [CrossRef]
- George, S.; Santra, A.K. Traffic prediction using multifaceted techniques: A survey. Wirel. Pers. Commun. 2020, 115, 1047–1106. [Google Scholar] [CrossRef]
- Fatemidokht, H.; Marjan, K.R. QMM-VANET: An efficient clustering algorithm based on QoS and monitoring of malicious vehicles in vehicular ad hoc networks. J. Syst. Softw. 2020, 165, 110561. [Google Scholar] [CrossRef]
- Kandali, K.; Hamid, B. An Efficient Routing Protocol Using an Improved Distance-Based Broadcasting and Fuzzy Logic System for VANET. Int. J. Intell. Eng. Syst. 2020, 13, 6. [Google Scholar] [CrossRef]
- Cao, Z.; Zujie, F.; Jaesoo, K. Intersection-based routing with fuzzy multi-factor decision for VANETs. Appl. Sci. 2021, 11, 7304. [Google Scholar] [CrossRef]
- Sadakale, R.; Ramesh, N.V.K.; Rajendrakumar, P. TAD-HOC routing protocol for efficient VANET and infrastructure-oriented communication network. J. Eng. 2020, 2020, 8505280. [Google Scholar] [CrossRef]
- Ragavi, B.; Saranya, S.; Pavithra, L.; Mohanapriya, G.; Nandhini, V.; Dhaarani, S. TROPHY: Efficient greedy transmission of data packet using trophy (TAD-hoc) protocol along with greedy algorithm in VANET. In Proceedings of the 2021 Third International Conference on Intelligent Communication Technologies and Virtual Mobile Networks (ICICV), Tirunelveli, India, 4–6 February 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 23–28. [Google Scholar]
- Kaur, G.; Kakkar, D. Hybrid optimization enabled trust-based secure routing with deep learning-based attack detection in VANET. Ad Hoc Netw. 2022, 136, 102961. [Google Scholar] [CrossRef]
- Kazi, A.K.; Shariq, M.K. DyTE: An effective routing protocol for VANET in urban scenarios. Eng. Technol. Appl. Sci. Res. 2021, 11, 6979–6985. [Google Scholar] [CrossRef]
- Acharya, A.; Oluoch, J. A Dual Approach for Preventing Blackhole Attacks in Vehicular Ad Hoc Networks Using Statistical Techniques and Supervised Machine Learning. In Proceedings of the 2021 IEEE International Conference on Electro Information Technology (EIT), Mt. Pleasant, MI, USA, 14–15 May 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 230–235. [Google Scholar]
- Ghaleb, F.A.; Zainal, A.; Rassam, M.A.; Mohammed, F. An effective misbehavior detection model using artificial neural network for vehicular ad hoc network applications. In Proceedings of the 2017 IEEE conference on application, information and network security (AINS), Miri, Malaysia, 13–14 November 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 13–18. [Google Scholar]
- Lai, W.K.; Mei-Tso, L.; Yu-Hsuan, Y. A machine learning system for routing decision-making in urban vehicular ad hoc networks. Int. J. Distrib. Sens. Netw. 2015, 11, 374391. [Google Scholar] [CrossRef]
- Wang, B.; Xu, K.; Zheng, S.; Zhou, H.; Liu, Y. A deep learning-based intelligent receiver for improving the reliability of the MIMO wireless communication system. IEEE Trans. Reliab. 2022, 71, 1104–1115. [Google Scholar] [CrossRef]
- Kurtkoti, M.; Premananda, B.; Vishwavardhan Reddy, K. Performance Analysis of Machine Learning Algorithms in Detecting and Mitigating Black and Gray Hole Attacks. In Innovative Data Communication Technologies and Application: Proceedings of ICIDCA 2021; Springer: Berlin/Heidelberg, Germany, 2022; pp. 945–961. [Google Scholar]
- Kandali, K.; Bennis, L.; El Bannay, O.; Bennis, H. An intelligent machine learning based routing scheme for VANET. IEEE Access 2022, 10, 74318–74333. [Google Scholar] [CrossRef]
- Jyothi, N.; Patil, R. A Black Widow Optimization-Based Neuro-Fuzzy Model for Designing an Efficient Cluster Routing Protocol in a VANET Environment. Int. J. Fuzzy Syst. Appl. (IJFSA) 2022, 11, 1–19. [Google Scholar] [CrossRef]
- Al-Ahwal, A.; Mahmoud, R.A. Performance Evaluation and Discrimination of AODV and AOMDV VANET Routing Protocols Based on RRSE Technique. Wirel. Pers. Commun. 2023, 128, 321–344. [Google Scholar] [CrossRef]
- Kien, P.T.; Seok, H.J. Multi-level cluster-based hierarchical protocol for ad hoc mobile networks. In Proceedings of the 2008 International Conference on Computer and Electrical Engineering, Phuket, Thailand, 20–22 December 2008; IEEE: Piscataway, NJ, USA, 2008; pp. 901–905. [Google Scholar]
- Padmavathi, G.; Subashini, P.; Aruna, M.D.D. CCMP-AES Model with DSR routing protocol to secure Link layer and Network layer in Mobile Adhoc Networks. Int. J. Comput. Sci. Eng. 2010, 2, 1524–1531. [Google Scholar]
- Zhang, X.; Shi, S.; Qian, C. Webflow: Scalable and decentralized routing for payment channel networks with high resource utilization. arXiv 2021, arXiv:2109.11665. [Google Scholar]





| Destination IP | Next Hop | Hop Count | Vehicle Information | RSU’s | ANN Algorithm Parameters | Malicious Node | RSU based Decision | Route Request | Route Reply | Sequence Number | Classification | Packets Delivered | Shortest Path (Yes/No) |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 192.168.1.100 | 192.168.1.105 | 2 | Vehicle 1 (Sedan) | RSU1, RSU3 | Learning Rate: 0.01 | No | Yes | 4 | 2 | 1234 | High | 1000 | Yes |
| 192.168.1.201 | 192.168.1.202 | 1 | Vehicle 2 (Truck) | RSU2, RSU4 | Learning Rate: 0.02 | Yes | No | 3 | 1 | 5678 | Medium | 800 | No |
| 192.168.1.305 | 192.168.1.308 | 3 | Vehicle 3 (Motorcycle) | RSU1, RSU2 | Learning Rate: 0.01 | No | Yes | 5 | 3 | 9876 | Low | 1200 | Yes |
| 192.168.1.410 | 192.168.1.412 | 2 | Vehicle 4 (Bus) | RSU3, RSU4 | Learning Rate: 0.03 | No | Yes | 2 | 1 | 3456 | High | 900 | No |
| 192.168.1.501 | 192.168.1.504 | 1 | Vehicle 5 (Sports Car) | RSU1, RSU2 | Learning Rate: 0.02 | No | No | 6 | 4 | 6543 | Medium | 1500 | Yes |
| 192.168.1.610 | 192.168.1.611 | 1 | Vehicle 6 (Van) | RSU3, RSU4 | Learning Rate: 0.01 | No | Yes | 4 | 2 | 7890 | Low | 1100 | No |
| 192.168.1.701 | 192.168.1.703 | 3 | Vehicle 7 (Electric Car) | RSU1, RSU2 | Learning Rate: 0.02 | Yes | No | 2 | 2 | 4321 | High | 1700 | Yes |
| 192.168.1.810 | 192.168.1.815 | 2 | Vehicle 8 (SUV) | RSU1, RSU3 | Learning Rate: 0.03 | No | Yes | 3 | 3 | 8765 | Medium | 950 | Yes |
| 192.168.1.910 | 192.168.1.912 | 1 | Vehicle 9 (Compact Car) | RSU2, RSU4 | Learning Rate: 0.01 | No | No | 4 | 2 | 2345 | Low | 1300 | No |
| 192.168.1.1000 | 192.168.1.1003 | 3 | Vehicle 10 (Tractor) | RSU1, RSU2 | Learning Rate: 0.02 | No | Yes | 5 | 4 | 5670 | High | 1600 | Yes |
| Parameters | Values |
|---|---|
| Simulator | SUMO 1.19 + NS-3.0 |
| Network Area Range | 2500 m × 2500 m |
| Vehicle Drive Time | 200 s |
| Total Simulation Time | 1000 s |
| Nodes Density | 100, 150, 200, 250, 300, 350, 400. |
| Wireless Protocol | 802.11 b |
| TransmissionRange Among Vehicles | 1500 m |
| Number of Vehicles | 200 |
| Road Conditions | Two Way Highly Road |
| Number of RSUs | 30 |
| RSU Wireless Area | 250 m |
| RSU Broadcast Time Interval | 50 s |
| Network Connectivity | 5G |
| Parameters | Values |
|---|---|
| Dense (Dense) | (None, 14) |
| Dense_1 (Dense) | (None, 64) |
| Dense_2 (Dense) | (None, 64) |
| Dense_3 (Dense) | (None, 64) |
| Dense_4 (Dense) | (None, 1) |
| Classification Class | Precision | Recall | F1 Score | Accuracy |
|---|---|---|---|---|
| 0 | 0.97 | 0.99 | 0.98 | 0.97 |
| 1 | 0.98 | 0.98 | 0.98 | 0.98 |
| Average | 0.975 | 0.985 | 0.98 | 0.975 |
| Vehicle Speed (m/s) | Simulation End Time |
|---|---|
| 15 | 56 |
| 14 | 57 |
| 13 | 59 |
| 12 | 61 |
| 11 | 64 |
| 10 | 67 |
| 9 | 70 |
| 8 | 75 |
| 7 | 80 |
| 6 | 88 |
| 5 | 99 |
| 4 | 115 |
| 3 | 141 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
ul Hassan, M.; Al-Awady, A.A.; Ali, A.; Sifatullah; Akram, M.; Iqbal, M.M.; Khan, J.; Abdelrahman Ali, Y.A. ANN-Based Intelligent Secure Routing Protocol in Vehicular Ad Hoc Networks (VANETs) Using Enhanced AODV. Sensors 2024, 24, 818. https://doi.org/10.3390/s24030818
ul Hassan M, Al-Awady AA, Ali A, Sifatullah, Akram M, Iqbal MM, Khan J, Abdelrahman Ali YA. ANN-Based Intelligent Secure Routing Protocol in Vehicular Ad Hoc Networks (VANETs) Using Enhanced AODV. Sensors. 2024; 24(3):818. https://doi.org/10.3390/s24030818
Chicago/Turabian Styleul Hassan, Mahmood, Amin A. Al-Awady, Abid Ali, Sifatullah, Muhammad Akram, Muhammad Munwar Iqbal, Jahangir Khan, and Yahya Ali Abdelrahman Ali. 2024. "ANN-Based Intelligent Secure Routing Protocol in Vehicular Ad Hoc Networks (VANETs) Using Enhanced AODV" Sensors 24, no. 3: 818. https://doi.org/10.3390/s24030818
APA Styleul Hassan, M., Al-Awady, A. A., Ali, A., Sifatullah, Akram, M., Iqbal, M. M., Khan, J., & Abdelrahman Ali, Y. A. (2024). ANN-Based Intelligent Secure Routing Protocol in Vehicular Ad Hoc Networks (VANETs) Using Enhanced AODV. Sensors, 24(3), 818. https://doi.org/10.3390/s24030818







