1. Introduction
The threat of personal data exposure through unauthorized access has never been as imminent as it is in recent times [
1]. Systems need different types of authentication to increase security, and traditional forms of authentication, such as PINs and passwords, tend to be vulnerable to forgery or easily stolen. Due to the growing number of security vulnerabilities, the need for better and safer authentication has gained more importance than ever before. Authentication is a means of verifying an identity that is claimed by utilizing different types of assets or data [
2]. These authentication techniques utilize an array of user attributes, including possession (something the individual owns, e.g., a digital certificate, smart card, portable device, etc.), knowledge (something the individual knows, such as a password), or inherent traits (something the individual has, i.e., biometrics such as fingerprints, facial, or voice recognition). Biometric features, which are characterized by “something the user is”, play a very important role in modern authentication systems. Commercially available biometric features include physical aspects such as fingerprints, facial characteristics, iris scans, and palm vein patterns, as well as behavioral aspects like keystroke patterns, signature analysis, and voice recognition [
3]. In this context, brain signals, classified as a subset of behavioral features, have gained interest due to their distinct advantages, particularly their concealed yet dependable nature [
4]. Brain activities are unique in the way they closely correlate with an individual´s mental state, actions, and cognitive conditions [
5]. These signals unveil both psychological and behavioral characteristics. The remarkable attributes of brain activities are their state-dependent dynamic behavior and their distinctive resistance to spoofing attacks, including attempts to imitate or forge a user [
6]. Brain activity can be measured by an “electroencephalogram” (EEG), a technology involving the placement of electrodes on the scalp to record electrical signals [
7]. These signals are produced by the synaptic activation of a group of neurons. In recent years, EEG signal analysis has gained attention because of its informative content, and it has played a pivotal role in several research fields, such as medicine, biometrics, and many other research fields [
8]. By capitalizing on the distinct advantages of brain signals, [
9] enhanced security and privacy measures in biometric authentication systems. EEG-based user authentication aligns with the principles of EEG-based biometrics, utilizing the unique nature of brain signals to verify the identity of users [
10]. By analyzing the distinctive EEG patterns, it ensures that only authorized users can access the system. Moreover, EEG-based user authentication contributes to improving user privacy, thereby introducing an extra layer of confidentiality [
11], addressing security concerns while maintaining user-friendly and scalable authentication procedures that manage growing user bases without compromising performance and security. Furthermore, EEG-based user authentication, which relies on the behavioral and psychological traits of users, offers robust protection against spoofing attacks and attempts to impersonate individuals [
12]. These attributes make it a promising and secure option for modern authentication systems [
13]. EEG-based user authentication not only combines the unique attributes of brain activity but also aligns with the evolving landscape of biometric authentication for enhanced security and user privacy. This research seeks to address significant challenges in the field of EEG-based user authentication. These challenges include comprehensiveness, user-friendliness, and the preservation of user confidentiality in real-time EEG-based authentication scenarios. In response to these challenges, it also introduces an innovative and comprehensive EEG-based user authentication scheme based on deep neural network techniques. The key contributions of the proposed study are as follows:
A unique approach for user identification and authentication by integrating selected features obtained through mutual information analysis. Specifically, it highlights the utilization of power spectral density (PSD) values, enhancing its ability to extract relevant and discriminative features, making it more significant for user recognition purposes compared to conventional methods.
A comprehensive architecture for EEG-based user identification and authentication, enabling the verification of newly enrolled users even without their EEG data during the initial training phase. This adaptability allows the system to effectively scale and accommodate a growing user base.
An approach that emphasizes utilizing selected features instead of directly storing or processing raw EEG data, significantly enhancing privacy by eliminating the need to retain sensitive raw EEG data that contain crucial information essential for analysis and interpretation.
A novel approach for EEG-based user authentication, which involves the calculation of predicted labels from classified EEG data segments. The final decision depends on the probability of the majority predicted label, with a predefined threshold used to ensure the authentication of genuine users and imposters.
The rest of this paper is organized as follows.
Section 2 discusses the challenges in the field of EEG-based user authentication and their implications in detail.
Section 2 also illustrates the current and previous common EEG-based authentication techniques using various machine learning and deep learning models. The problem statement for EEG-based user identification and authentication tasks, the architecture utilized in this research, and the representation of EEG data segments used as input, along with preprocessing and feature extraction using the mutual information of selected features, are discussed and explained in
Section 3. Furthermore, the core of the proposed user authentication scheme is detailed in the subsection on probability assessment, while the verification process is described in the subsection on the validation procedure. The tests, experiments, and results are analyzed and presented in
Section 4, with an emphasis on user identification and authentication in particular.
Section 5 concludes with a comparative discussion highlighting the novelty of the proposed scheme in relation to state-of-the-art works, and the conclusions are drawn in
Section 6.
2. Related Works
EEG-based user authentication presents several significant challenges that must be addressed for practical and real-time applications. One main challenge is designing a procedure that effectively identifies and authenticates users through their EEG patterns [
14]. Current systems employ a variety of techniques, as explored in [
15], but they often face issues like overfitting due to the high number of learnable parameters relative to the available training data [
16,
17]. Although the effectiveness of these models has increased, overfitting remains a frequent problem since there are many more learnable parameters than there are available training data. In general, EEG-based user authentication is considered a classification problem, in which EEG signals from a group of users are utilized to train a classification model. During the EEG recording, the signals are subjected to preprocessing, and then a set of distinctive features is extracted [
18]. Subsequently, a classifier is trained using these extracted features, which is employed to perform two main functions: user identification and user authentication. In user identification, the classifier is used to determine the identity from a given set of EEG records, while in user authentication, the classifier verifies whether two EEG records belong to the same user. In this study, the primary focus is on EEG-based user authentication, incorporating both user identification and verification. It is important to emphasize that for a classifier to work effectively, the user needs to replicate the same task they performed during the initial recording.
Generally, EEG-based biometric systems rely on shallow classifiers, like linear discriminant analysis [
19], support vector machine [
20], etc. However, in recent years, deep learning models [
21] have shown promising results in terms of accuracy and enhanced authentication. Although these classifiers have achieved better accuracy in EEG-based biometric applications, they still face a critical challenge known as “comprehensiveness”. This challenge refers to the requirement that the authentication factor should be applicable to every individual, not just those included in the training dataset [
22]. Current EEG-based authentication systems are limited, as they can only identify or authenticate users included in the initial training dataset. When a new user needs to register, their EEG data must be added, and the classifier retrained. This approach is impractical for real-time applications and suits systems with a predefined, limited user set. However, unlike traditional models, neural networks can accommodate new data without retraining from scratch. Few studies have explored techniques in EEG-based recognition that allow the inclusion of new users without requiring complete retraining of the model. In [
23], the author proposed a transfer learning technique to adapt an existing model for new users, but it struggled with accommodating large sets of new users. An EEG feature extractor model proposed in [
24] used deep learning for feature extraction, but instead of using extracted feature vectors directly, it employed them in a fully connected neural network, making it similar to a classification model. Addressing this challenge of scalability is crucial for practical, real-time EEG-based user authentication.
Another significant challenge of EEG-based user authentication is the number of electrodes required. The authors of [
25] used two electrodes for user authentication. To achieve better accuracy with fewer electrodes, the authors of [
26] proposed a user authentication method. In [
27], the number of electrodes employed was 33, significantly more than the number commonly found in most commercial EEG headsets. Some methods assume EEG data are sampled with up to 64 channels [
28], which is typically found in advanced medical devices. However, using many electrodes presents challenges in data acquisition and reduces user satisfaction. For practical use, a user authentication system should rely on a limited number of electrodes. The most important challenge in the methods proposed is the lack of attention to user privacy [
29]. EEG-based user authentication typically compares two EEG samples to verify whether they belong to the same person. However, storing EEG data for each user can expose sensitive information, such as gender, age, medical status, and other data [
30]. Methods should adopt a password-based approach, where the server stores a value instead of the actual data, preserving privacy while verifying the identity. Currently, only a small fraction of techniques offer such privacy-preserving capabilities. In this research study, the main focus is on addressing various challenges related to EEG-based user authentication by employing an FFNN to accurately authenticate users [
31] through the analysis of EEG signals. The aim of this study is to enhance the practical applicability of user authentication systems by proposing a method that maintains high accuracy and efficiency compared to state-of-the-art approaches. Furthermore, it is expected to extend the system’s usability to individuals who are not part of the training database by utilizing a multi-class classification technique to distinguish users based on their unique EEG patterns, making comprehensive EEG-based user authentication more achievable while preserving user privacy.
Developing an effective EEG-based recognition technique starts with extracting relevant features from raw EEG data. Since EEG signals are complex and unstructured, it is crucial to extract distinctive features before training machine learning models. The choice of feature extraction methods significantly affects the accuracy of the user identification and authentication system. Several well-established techniques are employed for EEG feature extraction, including the autoregressive model [
32] for capturing temporal dependencies, power spectral density [
33] for frequency-based analysis, wavelet transform [
34] for transient and frequency-specific information, principal component analysis [
35] for reducing the complexity of EEG data while retaining relevant information, time-domain features [
36] for statistical information about the EEG signals, and the Fourier transform [
37] for analyzing signals in the frequency domain. Once these distinguishing features are extracted from the EEG data, the user identification and authentication processes can typically advance through different approaches.
The “feature-based approach” involves extracting relevant features from EEG data. For example, Alsumari et al. [
38] designed an EEG-based recognition system based on a one-dimensional temporal domain representation of EEG data. Wilaiprasitporn et al. [
39] proposed an EEG-based biometric system for identifying users by extracting 15 statistical features using neighborhood component analysis. Białas et al. [
40] proposed an EEG-based authentication system combining signal analysis and user image verification, integrating a random forest (RF) classifier with a mobile app, achieving 83% classification accuracy. With respect to the algorithms used for EEG-based user identification and authentication, the most commonly used one is SVM. Leon et al. [
41] enhanced the validation of BCI using SSVEP for multi-class classification. Schons et al. [
42] developed an EEG-based biometric system using a CNN with 64-channel inputs and data augmentation, achieving 99% accuracy for 109 users. However, it relies on 12-second EEG segments, which is not ideal for real-time applications. An innovative EEG authentication framework was introduced by Bingkun et al. [
43] for end-to-end user verification using a CNN on two public datasets, demonstrating promising results. However, the small sample size for channel selection and the lack of evaluation factors pose challenges to the scalability of the system. Debie et al. [
44] used an EEG fusion method with a CNN to improve user authentication, demonstrating better performance and reliability under cross-sectional conditions compared to single-protocol models. Maiorana et al. [
45] used hidden Markov models for EEG-based user recognition, spanning six trials and two sessions per subject over three years. While the study addressed longevity factors, it lacked detailed feature selection criteria and did not explore EEG signal stability beyond this period. Kim et al. [
46] used local function networks (FNs) for EEG-based user authentication, focusing on quadrantal FNs under different resting conditions. While showing promising results, their approach also used t-SNE for visualization, which has limitations such as sensitivity to hyperparameters, poor scalability, and interpretability problems. The feature extraction method plays a vital role in the effectiveness of EEG-based user authentication. For example, using machine learning models and methods for capturing meaningful information from the EEG signals to identify and authenticate users accurately is essential.
MLP neural networks [
47] are ideal for EEG-based user authentication due to their ability to automatically identify relevant features from raw EEG data, eliminating the need for manual feature extraction and simplifying the authentication process. The built-in feature extraction capability simplifies the whole authentication process, increasing its effectiveness and reducing the complexity of system design. MLP neural networks have achieved notable success in EEG-based user authentication. Waili et al. [
48] proposed an MLP network using Daubechies (d8) wavelet for feature extraction, achieving 73.65% accuracy in biometric recognition. However, the choice of filter parameters and their impact on EEG signal quality were not discussed. Haukipuro et al. [
49] used a single-electrode EEG device for mobile authentication, performing multi-step processing with 27 users in a real-life scenario, achieving 85.30% accuracy. However, the authentication error increased when new users were added, indicating potential limitations in the feature space or user overlap. Using auditory stimuli at rest for EEG-based authentication was presented in [
50], with three classifiers utilized (MLP, KNN, and XGBoost), achieving an accuracy of 69% based on the auditory stimulus. Despite the low accuracy, the study lacked details on the sample size, user demographics, and auditory stimuli used for authentication. Liew et al. [
51] proposed an incremental fuzzy-rough nearest neighborhood (IncFRNN) technique for biometric authentication using visual evoked potentials from 37 users, achieving 87% accuracy. However, the validation process to reduce overfitting was not clearly explained. EEG-based biometric authentication was performed using eye-blinking signals [
52], with stationary wavelet transforms and independent component analysis (SWT+ICA) for preprocessing. An artificial neural network (ANN) achieved 81% accuracy, but the study omitted details on the feature extraction and fusion techniques used. The reviewed papers listed in
Table 1 focused mostly on EEG-based user identification rather than user authentication. Although several machine learning and deep learning models have been employed for EEG-based authentication, integrating multi-factor authentication (MFA) methods could further enhance the security and robustness of these systems. For example, Theodoropoulos et al. [
53] and P.D. et al. [
54] demonstrated how integrating OTPs and cryptographic techniques with multi-factor frameworks can strengthen authentication mechanisms in various applications. Similarly, Cheng et al. [
55] showcased the effectiveness of hybrid EEG and eye movement-based authentication systems, achieving superior accuracy and reliability compared to single-modality approaches, which highlights the potential of combining physiological and cryptographic factors for more secure hybrid EEG-based authentication systems.
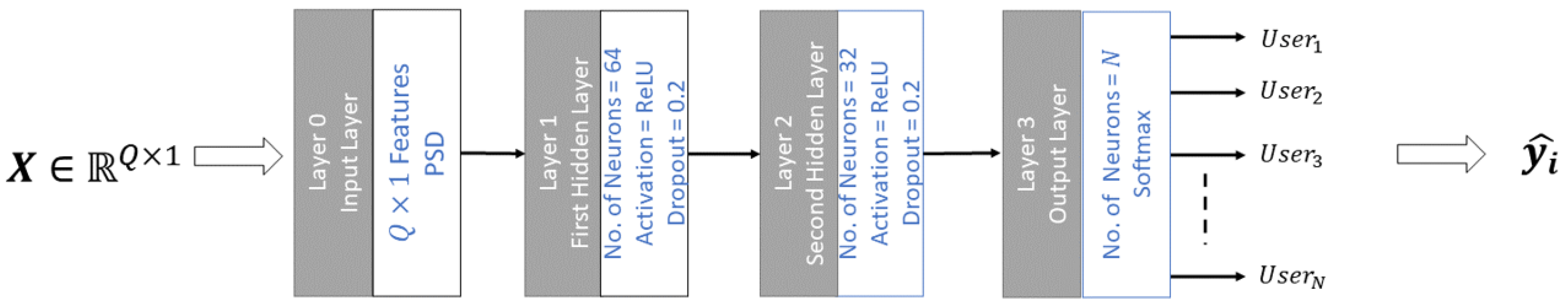
The proposed user authentication approach is a promising method that focuses on power spectral density (PSD) for extracting features from five frequency bands: alpha, beta, theta, gamma, and delta. This feature extraction utilizes mutual information (MI) and employs a feedforward neural network (FFNN) for classification. Notably, the use of the P300 speller paradigm with a reduced number of channels (only eight channels) distinguishes this approach from others. The proposed method not only achieves improved accuracy but also simplifies EEG-based user identification and authentication by performing a probability assessment based on predicted labels to accurately differentiate between genuine users and impostors.
5. Discussion and Comparative Analysis with Related Studies
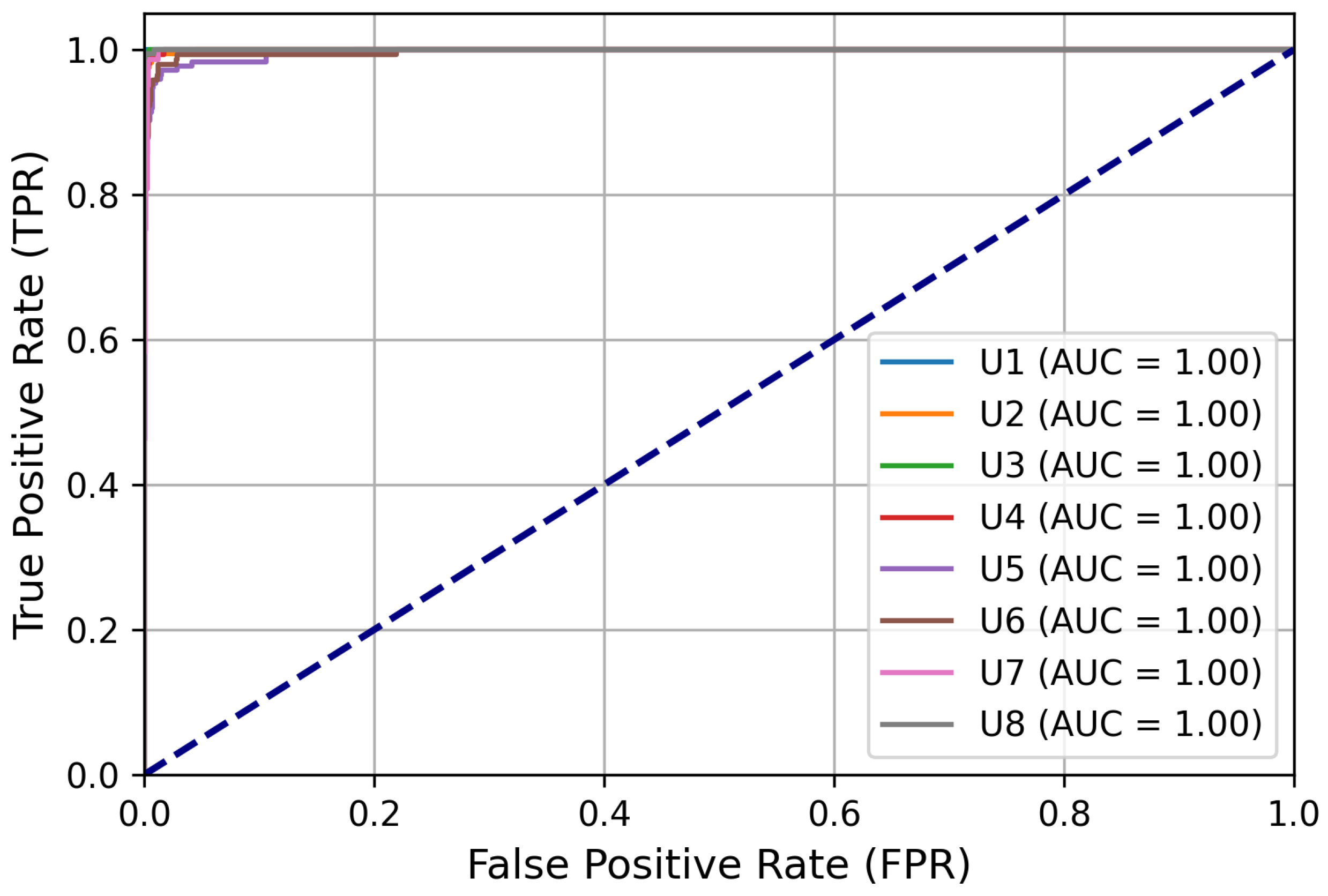
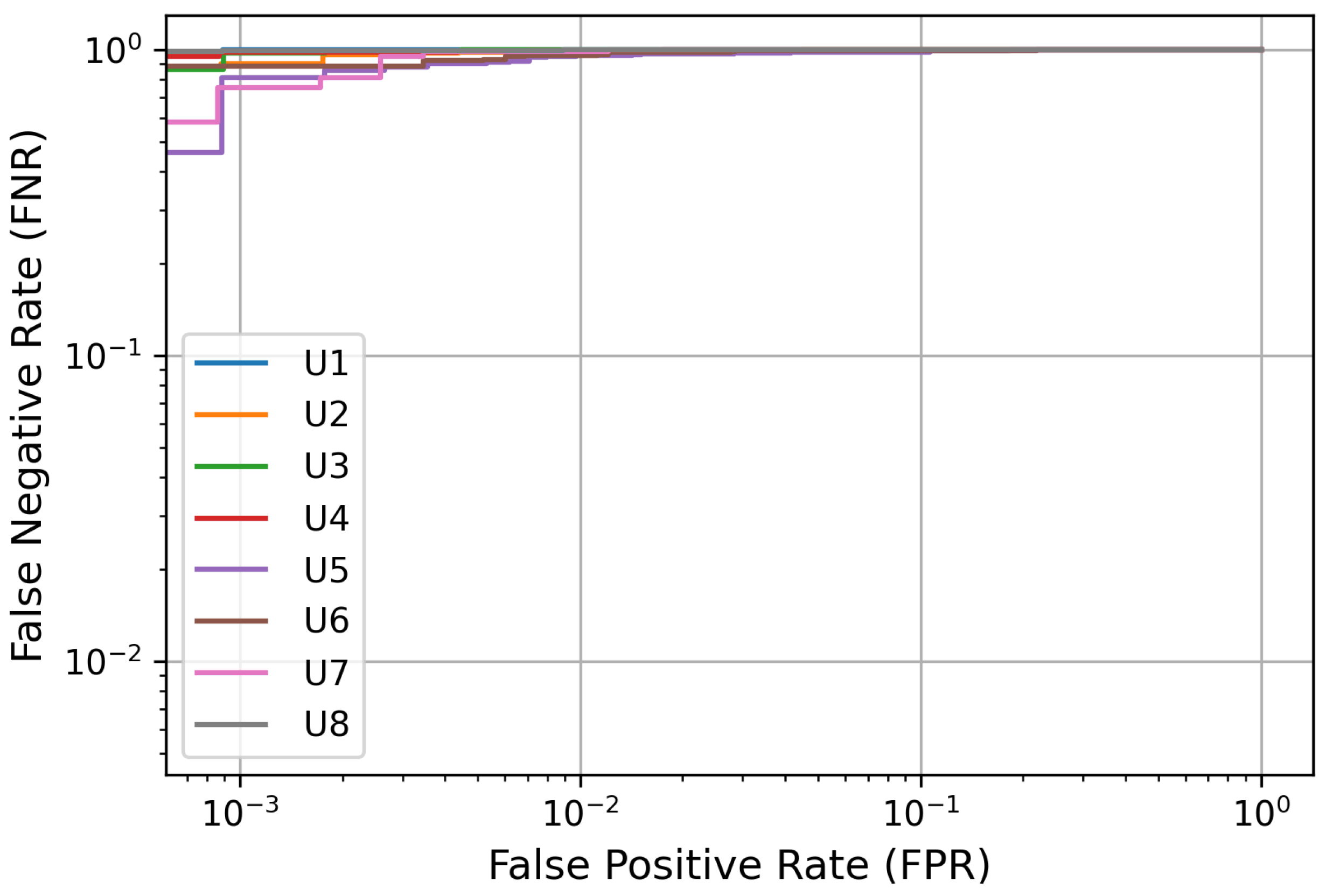
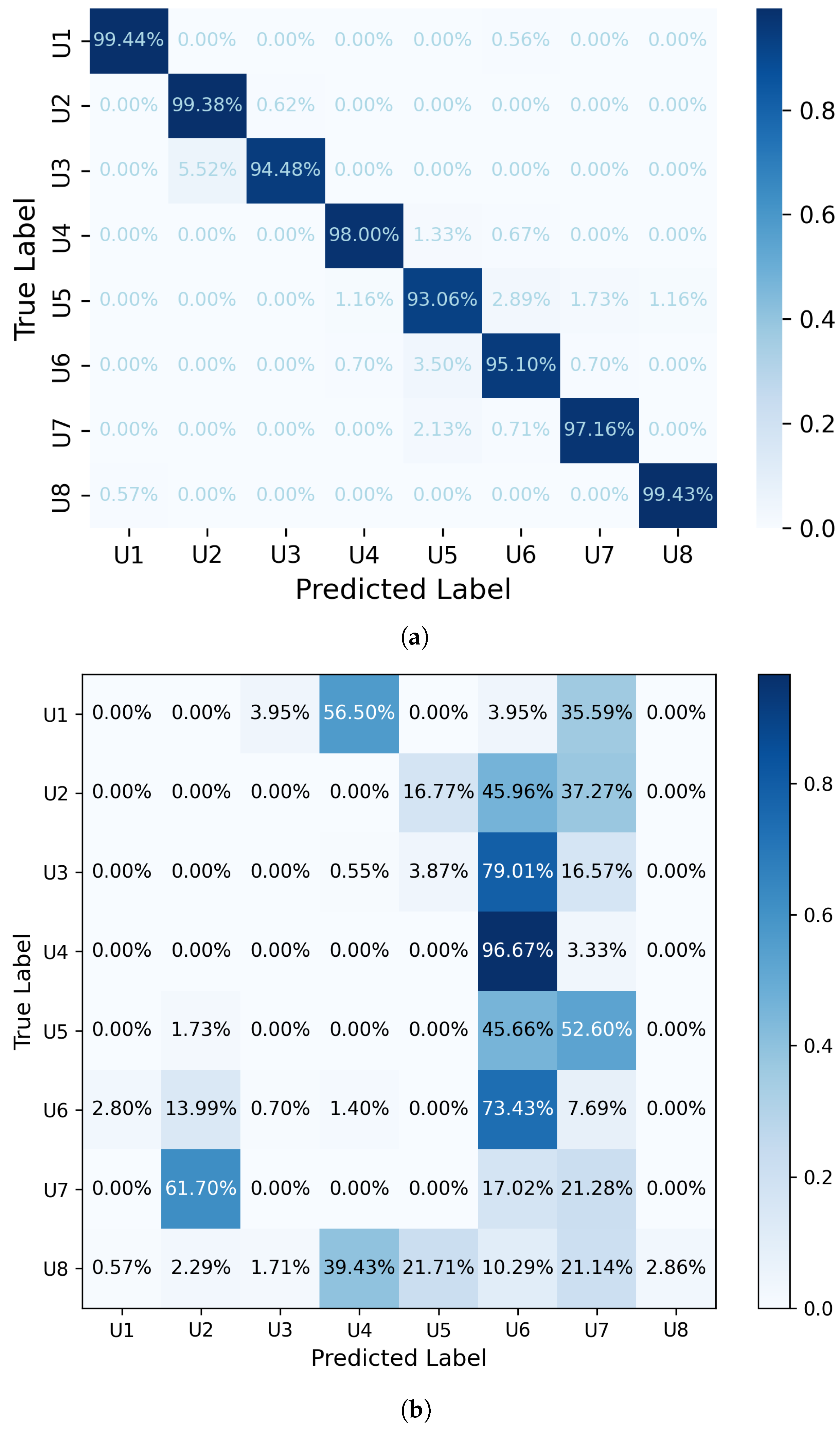
The proposed feedforward neural network (FFNN) significantly improves EEG-based user identification and authentication, demonstrating a marked enhancement in accuracy compared to previous studies. Specifically, when compared to the study by Waili et al. [
47], which used a more limited dataset (six users and 19 channels) and employed wavelet decomposition on alpha and beta bands, the proposed method shows a substantial improvement in user recognition accuracy. While Waili et al. achieved 73% accuracy using multi-layer perceptron (MLP) neural networks, the FFNN in this study achieved 97% accuracy, which is a notable advancement.
Table 6 provides an overview of current EEG-based user authentication techniques that utilize neural networks across various datasets, along with a comparative analysis highlighting the advancements and distinctions of the proposed method.
One of the key differences between the proposed approach and prior research lies in the number of EEG channels used. As noted, the use of a single channel for EEG-based authentication, such as in [
52], inherently limits accuracy due to the reduced feature complexity across users and tasks. In contrast, our approach utilizes a reduced channel configuration of eight channels, which strikes a balance between practical feasibility and high performance. This approach enhances generalizability to unseen data, which is crucial for real-time applications where computational efficiency is important. The scalability of the system, while still leveraging the minimal channel setup, significantly reinforces security protocols, making it more suitable for real-time applications compared to studies that rely on larger numbers of channels, such as the 64 channels used by Liew et al. [
51].
The comparison with studies like Liew et al. [
51], which used 64 channels and advanced feature extraction techniques like cross-correlation and coherence, highlights a trade-off between accuracy and practicality. While their method achieved 87% accuracy, it is less feasible for real-time applications, where a large number of channels may not be practical due to data privacy concerns and computational requirements. The proposed study circumvents these challenges by focusing on optimizing feature selection using mutual information analysis and selected features, particularly in the power spectral density (PSD) domain, to enhance feature discriminability without relying on a vast array of channels.
Moreover, Bhateja et al. [
52] highlighted the limitations of using signal fusion in single-channel EEG mixed with Electrooculography (EOG) signals, which could impose further constraints on authentication accuracy. In contrast, the proposed method emphasizes feature extraction and selection over signal fusion, which not only improves accuracy but also addresses privacy concerns by minimizing the direct processing of raw EEG data. By reducing the number of channels and focusing on relevant features, the method provides a more efficient, practical, and privacy-preserving solution for EEG-based user authentication.
Despite the promising results, several limitations and factors must be considered when interpreting these findings. First, the dataset used in this study, while consisting of eight users and eight channels, may not fully represent the variability seen in larger, more diverse populations. The small user pool limits the study’s ability to generalize to a broader population, especially in more heterogeneous environments or in real-world scenarios. Additionally, the reliance on a specific set of features, such as those derived from PSD, may not capture all relevant aspects of the EEG signal, particularly in more complex tasks or individuals with significantly different brainwave patterns.
Furthermore, model assumptions may not apply to other datasets or tasks, such as the suitability of FFNNs for feature extraction. Models like EEGNet, which is designed for EEG analysis and efficiently captures spatial and temporal data using depthwise and separable convolutions, could be used in future research. Performance may be further improved by hybrid strategies that combine EEGNet with conventional feature extraction. In addition, by extending methods or adding domain-specific knowledge, biases in feature selection from mutual information analysis could be minimized. Evaluating models such as EEGNet on a variety of tasks could enhance their classification accuracy and robustness.
In summary, the proposed EEG-based user authentication system demonstrates improved performance compared to existing methods by optimizing the trade-off between accuracy, efficiency, and practicality. While the approach offers several advantages in terms of scalability, real-time application suitability, and privacy preservation, further exploration of model assumptions, dataset constraints, and feature selection biases is necessary to improve generalizability and performance. Continued development in these areas could lead to even more reliable and secure EEG-based authentication systems, paving the way for real-world deployment in high-security applications.
6. Conclusions and Future Work
This study addresses the practical challenges in EEG-based user authentication, such as comprehensiveness and privacy. To achieve this objective, an EEG-based user identification and authentication scheme is proposed that utilizes a feedforward neural network (FFNN) to extract relevant features from EEG signals. The system then verifies the user’s claimed identity by comparing the similarities between the stored data and the selected EEG features. Privacy preservation is ensured through multiple mechanisms: (1) only the extracted features, not the raw EEG data, are stored, thus preventing any reconstruction of the original EEG signals; (2) all stored data are obscured, preventing the detection of any specific individual; and (3) robust encryption techniques are applied to secure both the stored features and transmitted data, preventing unauthorized access. Furthermore, the proposed method eliminates the possibility of users accessing their own EEG data, thereby further safeguarding privacy. Another advantage of this approach is its comprehensiveness, as it can be used for all users, including those who are not part of the training database. This method demonstrates ease of use and can operate with a smaller number of channels. Consequently, the results show an accuracy of 97%, which is superior to that of other related studies.
While this research demonstrates the potential of EEG-based user authentication, addressing data privacy and model robustness remains essential. Robustness can be evaluated through adversarial attack simulations to assess the system’s resilience against malicious attempts. Enhancing feature extraction methods may improve the system’s ability to capture subtle user-specific patterns, while more sophisticated machine learning architectures can better exploit the spatial and temporal dependencies in EEG data. Exploring transfer learning, real-time implementation, and integrating user feedback and interaction are critical steps toward practical deployment. Furthermore, evaluating the system across diverse datasets and exploring its potential for secure access to data centers, where critical data and servers are kept, as well as bank vaults, will enhance its broader applicability and impact. These advancements will contribute to the development of secure, reliable, and broadly applicable EEG-based user authentication systems.