Exploring the Potential of Microservices in Internet of Things: A Systematic Review of Security and Prospects
Abstract
1. Introduction
- Identifying Key Security Challenges: analyzing how microservices address security challenges in IoT systems.
- Assessing Current Solutions: evaluating the effectiveness of existing microservice-based solutions in enhancing IoT security.
- Highlighting Research Trends: using bibliometric analysis to uncover trends, popular research topics, and influential papers in this domain.
- Proposing Future Directions: suggesting potential areas for future research based on identified gaps and trends.
2. Research Protocol
- Population (refers to the group or system being studied): IoT systems;
- Intervention (refers to the specific procedure or action being investigated): microservices for IoT;
- Comparisons (involve the alternative conditions or groups against which the intervention is evaluated): standard IoT architectures (including other software architectures)
- Outcomes (refer to the specific effects or results that the study aims to measure): the security benefits of adopting microservices in IoT systems
- Study design (refers to the type and methodology of studies included in the review): focus on studies that provide solutions, methodologies, security mechanisms, or other procedures to handle microservice-based IoT systems.
2.1. Research Questions
2.2. Search Techniques
- Venue-based search;
- Query-based search;
- Snowballing.
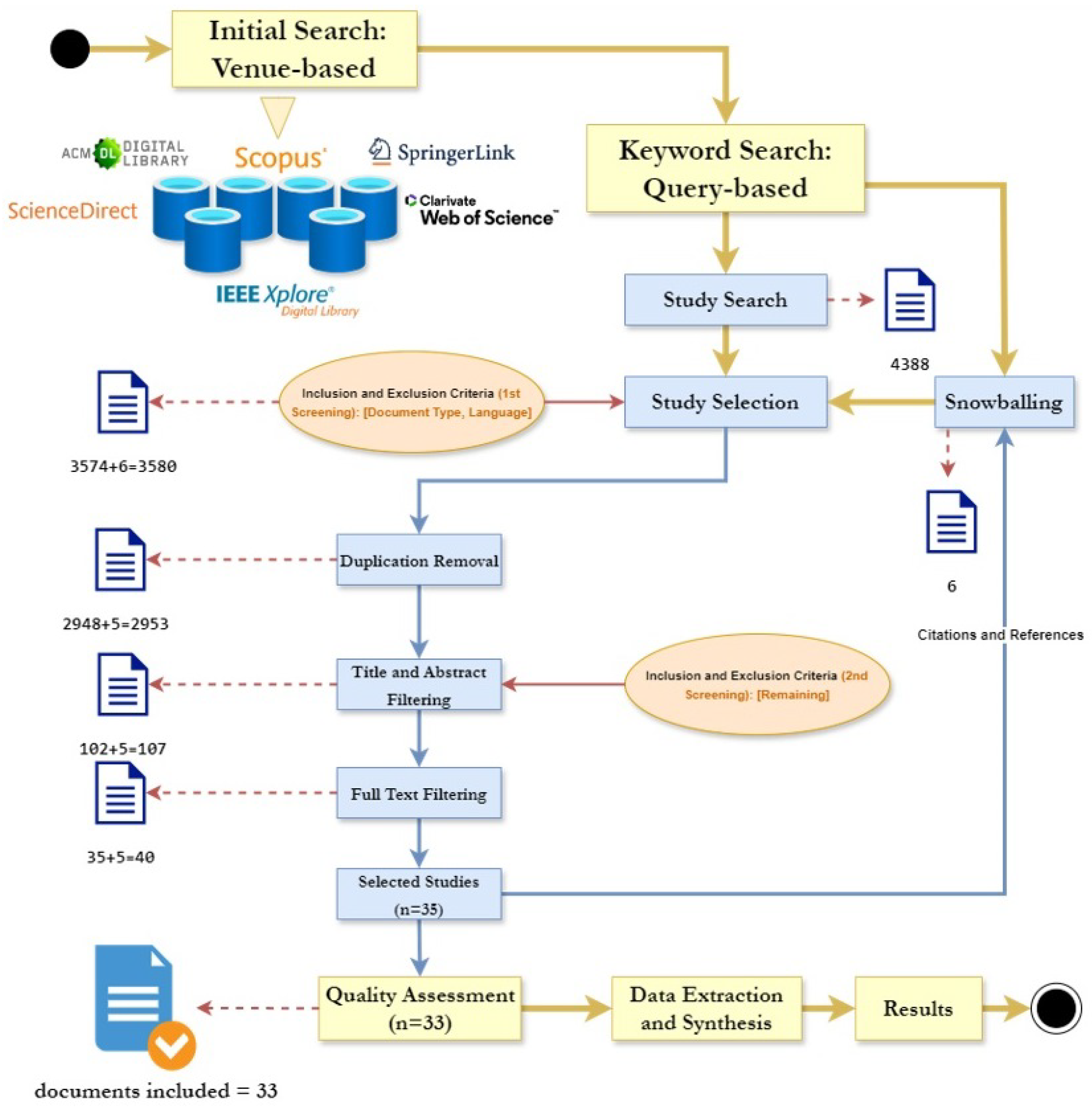
2.3. Search Process
2.3.1. Methodology
2.3.2. Time Frame and Keywords
2.3.3. Search Results
2.3.4. Studies Selection
- Studies related to microservice-based IoT systems;
- Studies whose primary focus is security aspects of microservice-based IoT systems;
- Studies that provide solutions, methodologies, security mechanisms, or other procedures to handle microservice-based IoT systems;
- Studies written in English, French, or Arabic.
- Short studies (less than 5 pages for academic literature);
- Secondary or tertiary studies (such as literature reviews, surveys, and others) *;
- Tutorial papers and editorials;
- Grey literature;
- Studies without full text available;
- Studies that do not link microservices and IoT;
- Not accessed electronically.
2.3.5. Selection Process
2.3.6. Quality Assessment
2.3.7. Data Extraction Form
3. Results and Analysis
3.1. Quality Assessment Results
3.2. Results Discussion
3.3. Number of Publications per Year (RQ1)
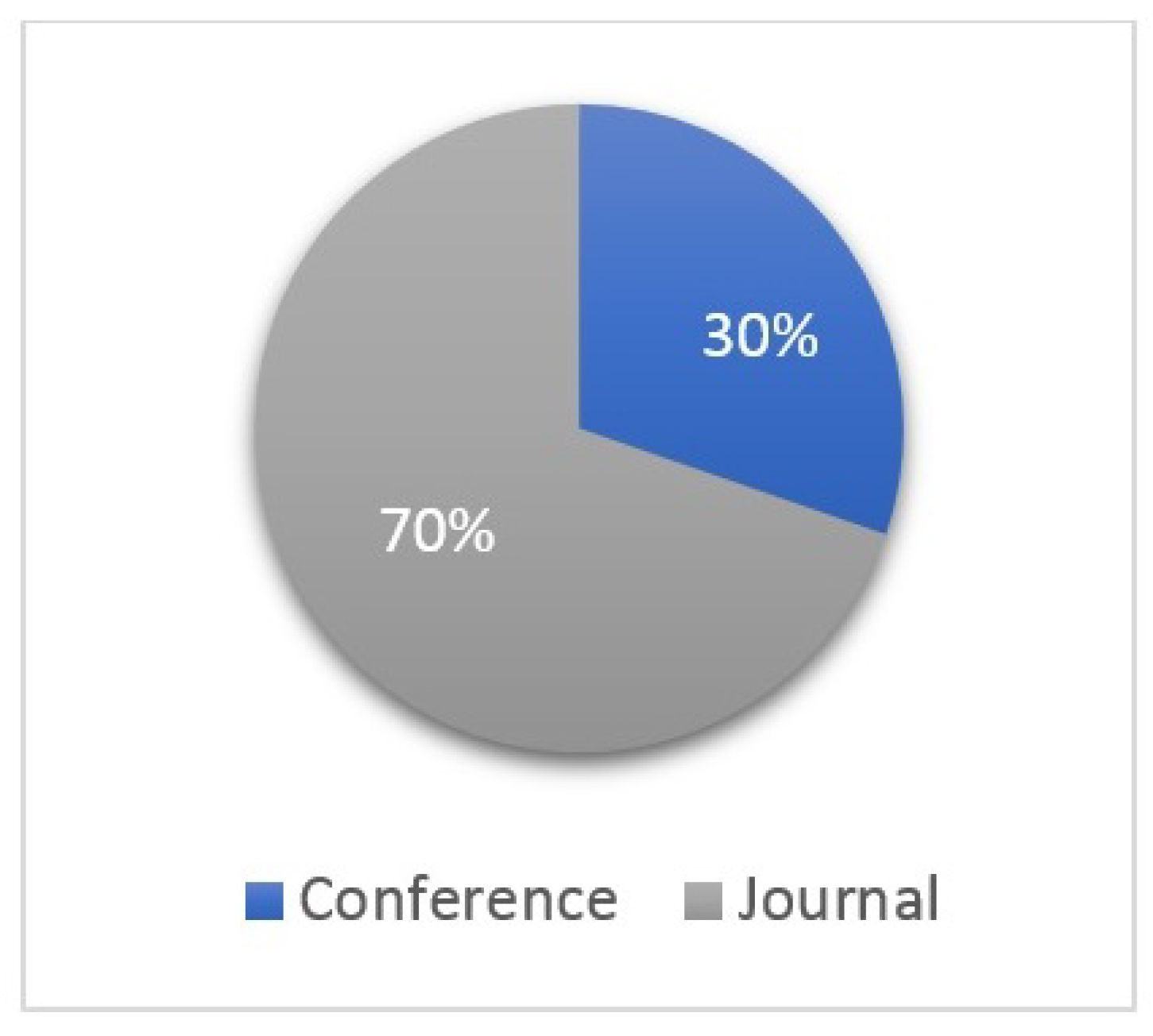
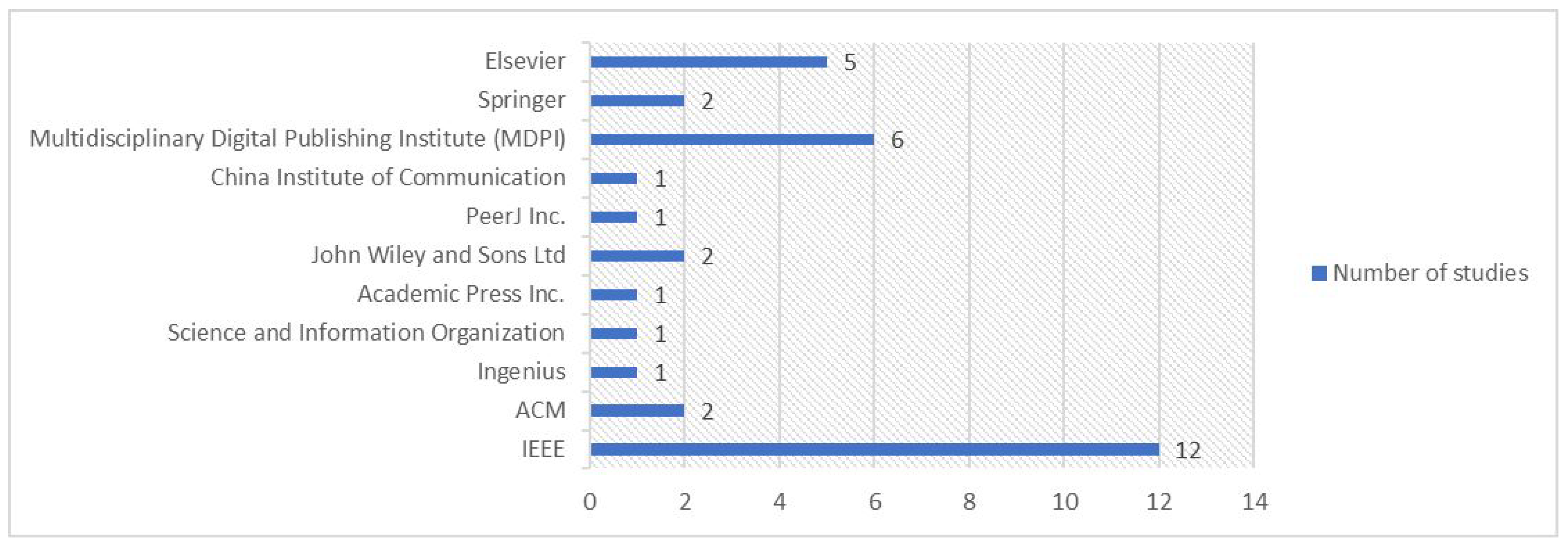
3.4. Primary Publication Outlets (RQ2)
3.5. Benefits of MSA in IoT (RQ3)
- Flexibility and Scalability: Microservices enable the ability to scale specific parts of the application as needed, making it possible to execute services on resource-constrained devices and efficiently manage resources.
- Technology Heterogeneity: Microservices allow different parts of the application to be implemented with diverse technologies, providing flexibility and adaptability in the IoT ecosystem.
- Interoperability and Enhanced Performance: Microservices facilitate seamless integration of diverse devices and services, fostering interoperability within IoT ecosystems. This architecture not only streamlines communication between components but also enhances performance by allowing independent scaling of services. As a result, microservices empower IoT applications to respond swiftly and effectively to user needs, ultimately improving system reliability and responsiveness.
- Continuous and Easy Deployment: MSA promotes continuous deployment practices, allowing for rapid updates, bug fixes, and feature enhancements, leading to more agile and responsive IoT applications.
- Resource-Constrained Device Support: MSA’s flexibility allows specific microservices to run on resource-limited IoT devices, enhancing the capability of IoT systems in various deployment scenarios.
- Agile Development Process Owing to MSA’s Modular Design: With microservices, IoT applications benefit from an agile and flexible development process, allowing rapid deployment and adaptation to changing requirements.
- Resource Optimization and Management: With MSA, resources can be allocated and managed more effectively, resulting in optimized performance and reduced wastage of computing resources.
- Real-time Data Processing: Automated microservices frameworks enable real-time processing of big data, improving fog resiliency and ensuring high-quality service delivery in IoT-Fog-Cloud ecosystems.
- Fault Tolerance and Anomaly Detection: In MSA, failures in one microservice do not affect the entire application, as each service operates independently, leading to improved fault isolation and system resilience.
- Secure Authentication and Authorization: Microservices architectures offer efficient authentication and authorization mechanisms, safeguarding IoT applications against unauthorized access and ensuring reliable user management.
- Privacy and Data Protection: Microservices architectures ensure secure communication channels, data encryption, and access control mechanisms, enhancing privacy and safeguarding against data breaches.
- Enhanced Security: Integrating other technologies like Blockchain technology into microservices architecture provides decentralized data management and robust security mechanisms, ensuring data integrity and access control in IoT applications.
3.6. Key MSA IoT Challenges (RQ4)
3.7. Security Risks in MSA IoT (RQ5)
3.8. Performance Implications (RQ6)
- Scalability: Microservices offer the advantage of scalability, allowing individual components to scale independently based on demand. However, improper scaling strategies or excessive communication overhead between microservices can impact performance. Ensuring effective load balancing and efficient communication mechanisms is crucial to maintaining optimal performance.
- Latency: Communication between microservices may introduce additional latency compared to monolithic architectures (P9 [30], P12 [33] and P28 [49]). Each request may need to traverse multiple services, potentially leading to increased network latency and response times. Proper design and optimization techniques, such as caching, asynchronous messaging, and event-driven architectures, can mitigate latency issues.
- Network Overhead: Microservices communicate with each other over the network, leading to increased network traffic (P12 [33] and P28 [49]). This can cause network congestion and affect performance, particularly in resource-constrained IoT environments. Careful consideration of network protocols, data compression techniques, and efficient message-passing mechanisms can help manage network overhead.
- Service Discovery: In a microservice architecture, services need to discover and communicate with each other dynamically. This introduces additional overhead for service discovery mechanisms, such as service registries or DNS resolution. The efficiency and performance of service discovery mechanisms can impact the overall system performance.
- Resource Utilization: Microservices require additional resources, such as memory, CPU, and storage, compared to a monolithic architecture (P31 [52] and P28 [49]). The increased resource utilization can impact the performance of the underlying infrastructure, particularly in resource-constrained IoT devices. Proper resource management and optimization techniques are essential to ensure efficient resource utilization.
- Complexity: Microservices introduce additional complexity in terms of managing and coordinating multiple services. The increased complexity can affect performance due to additional processing overhead and potential bottlenecks. Proper design and monitoring practices, along with effective management of dependencies, can help mitigate the impact of complexity on performance.
3.9. Practical Aspects of Implementing Microservices in IoT Systems (RQ7)
- Best Practice #1: System Decomposition and Security Considerations
- Description: Breaking down large systems into smaller units of work (P25 [46]) and differentiating between various types of services (e.g., business services and infrastructure services).
- Implementation Guidance:
- -
- Decomposing large, monolithic systems into individual microservices based on shared functionality, business logic, or domain boundaries, with Domain-Driven Design (DDD) helping to identify logical boundaries.
- -
- Using a zero-trust architecture by implementing strong authentication and authorization for each service and enforcing security policies at the service mesh level, ensuring secure communication.
- -
- Incorporating defense-in-depth by applying multiple layers of security, such as network- and service-level firewalls, and encrypting data both at rest and in transit.
- Best Practice #2: Access Control and Identity Management
- Description: Using identity providers to create and manage access tokens, enabling permission, profile, and credential management.
- Implementation Guidance:
- -
- Granting limited access to external clients through firewalls and managing microservice access rights.
- -
- Delegating authentication (P24 [45]) to a single point and utilizing OAuth2 for lightweight identity infrastructure:
- (a)
- Delegated Authentication: OAuth2 allows microservices to offload authentication to a centralized identity provider. This reduces overhead by avoiding repetitive authentication processes in each microservice, which is especially beneficial in environments where resources are limited.
- (b)
- Token-Based Authorization: Once authenticated, the identity provider issues access tokens, which are short-lived and lightweight. These tokens are then used by the services to manage secure communication and resource access. Tokens ensure that services can authenticate and authorize requests without relying on resource-heavy identity checks, thus maintaining system efficiency.
- (c)
- For scalability, integrating rate limiting (restricting the number of requests a user or service can make in a time frame) and token expiration to prevent system overload, and centralizing access control through API gateways.
- Best Practice #3: Scaling and Service Distribution
- Description: Microservice architectures inherently allow horizontal scaling by replicating services to handle increased workloads.
- Implementation Guidance:
- -
- Utilizing container orchestration platforms like Kubernetes or Docker Swarm for automated scaling, allowing services to adjust based on metrics such as CPU usage or memory consumption.
- -
- Applying horizontal pod autoscalers to dynamically manage scaling and distributing traffic evenly with load balancers across service instances.
- -
- Ensuring redundancy and fault tolerance by distributing services across nodes or clusters.
- -
- Implementing throttling (limiting the rate of request processing) and rate limiting at the API gateway level to prevent high traffic from overwhelming individual services.
- Best Practice #4: Autonomous Development and Topology Mapping
- Description:
- -
- Addressing new demands with individual microservices to maintain autonomous development.
- -
- Facilitating mapping service (P20 [41]) requests to microservice topologies to prevent rough dependencies and enhance scalability.
- Implementation Guidance:
- -
- Developing, deploying, and scaling microservices independently through CI/CD pipelines, ensuring continuous integration and delivery.
- -
- Using service topology maps to visualize and organize relationships between services. Tools like service mesh can help map dependencies and communication paths, preventing bottlenecks and ensuring scalability.
- Best Practice #5: Accountability and Certificate-based Security
- Description: Establishing tracking measures for actions and adopting certificate-based solutions (P27 [48]) for IoT service authentication and integrity.
- Implementation Guidance:
- -
- Implementing certificate-based authentication with mutual TLS (mTLS) for secure service communication, ensuring each service verifies the identity of others.
- -
- Managing digital certificates through Public Key Infrastructure (PKI), with certificate authorities automating certificate issuance and renewal.
- -
- Logging all service interactions and activities using auditing tools to track and trace responsibility across services.
- Best Practice #6: Reusability, Safety, and Multi-microservice Requirements
- Description: Reusing microservices across systems to improve efficiency and safety, especially in complex IoT environments.
- Implementation Guidance:
- -
- Designing microservices with modularity to ensure reusability across various applications or domains, adhering to SOLID principles (e.g., the single responsibility principle), which promotes clean and maintainable code.
- -
- Avoiding dependencies between multiple microservices for single functionalities, which can lead to complex orchestration. Using event-driven architectures (e.g., Apache Kafka or RabbitMQ) to decouple services and enable asynchronous, safe communication.
- Best Practice #7: Layer Segmentation and Security Scenarios
- Description: Segmenting the IoT system into local (edge) and centralized (cloud) layers to improve security and performance.
- Implementation Guidance:
- -
- Using edge computing for real-time data processing in local layers and offloading long-term storage and analytics to the cloud, ensuring performance and efficiency.
- -
- Implementing specific security measures at each layer, such as using edge computing gateways for localized processing and securing data transmission to the cloud with end-to-end encryption (e.g., TLS 1.3).
- -
- Applying role-based access control (RBAC) at each layer to ensure only authorized entities can access sensitive data.
- Best Practice #8: Efficient Service Aggregation
- Description: Using API gateways as single-entry points for aggregating microservices.
- Implementation Guidance:
- -
- Deploying API gateways to handle incoming requests, routing them to appropriate microservices, and managing security features like rate limiting, caching, and request/response transformations.
- -
- For fine-grained requests (requests for specific, smaller pieces of data), using API gateways that support GraphQL or gRPC, which allow clients to specify the exact data they need. Coarse-grained requests (larger, bulkier requests) can be aggregated efficiently, as well, to reduce response times and improve system performance.
3.10. Future Directions for Research (RQ8)
3.10.1. Limited Emphasis on Standard Security Measures
3.10.2. Inadequate Attention to Microservice-Based Security in IoT: Dominance of Machine Learning Approaches
3.10.3. Insufficiency of Security Patterns for Microservice-Based IoT Systems
3.10.4. Integrating Blockchain and AI/Machine Learning Solutions
3.10.5. Energy Efficiency and Sustainability
3.10.6. 5G/6G Technologies for Resource Allocation
3.10.7. Distributed Learning and Security-by-Design
3.10.8. Advancing Security Monitoring Techniques for Microservice-Based IoT Systems
3.10.9. Exploring Quantum Computing for IoT Security
3.11. Summary of Key Findings and Implications
- Theoretical Implications: the findings contribute to the growing body of knowledge on microservices and IoT, providing a detailed understanding of the benefits, challenges, and best practices.
- Practical Implications: practitioners can leverage these insights to improve the design, implementation, and management of IoT systems, leading to more robust and efficient solutions.
- Policy Implications: policymakers and industry leaders can use these findings to develop standards and guidelines that promote the secure and efficient adoption of microservices in IoT environments.
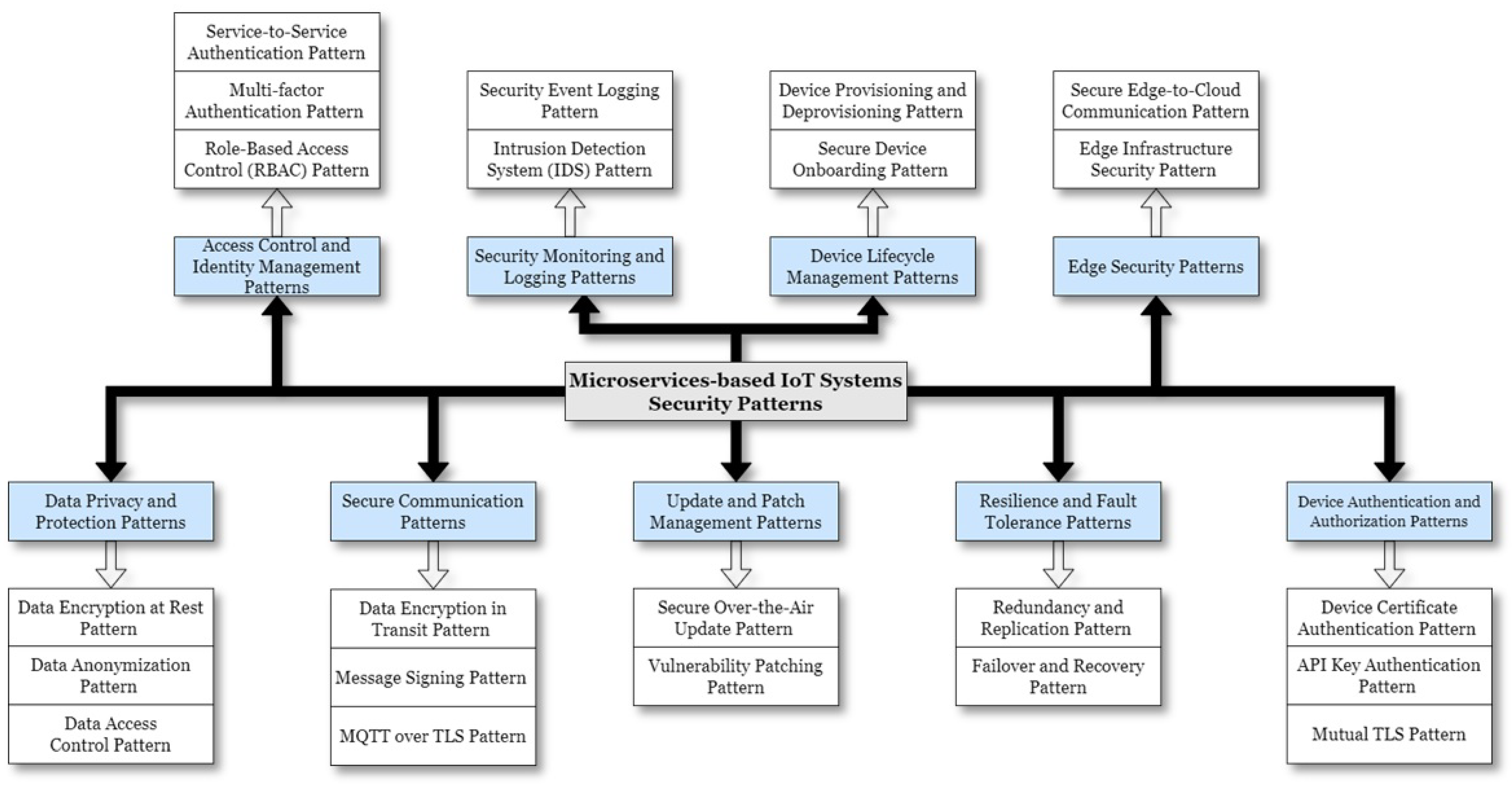
4. Microservice-Based IoT Systems Security Pattern Taxonomy
- Device Authentication and Authorization Patterns: These patterns focus on authenticating and authorizing IoT devices before allowing them to interact with microservices. Techniques like device certificates, API keys, and mutual TLS can be included.
- Secure Communication Patterns: These patterns address securing communication between IoT devices and microservices to prevent data interception and tampering. Examples include encryption of data in transit, message signing, and secure protocols like MQTT over TLS.
- Data Privacy and Protection Patterns: These patterns involve safeguarding sensitive data collected and processed by IoT devices and microservices. Techniques like data encryption, data anonymization, and data access controls can be included.
- Edge Security Patterns: These patterns deal with securing edge devices and gateways in IoT systems, where data are processed and filtered before being sent to the cloud. This includes securing the edge infrastructure and ensuring secure communication between edge devices and microservices.
- Access Control and Identity Management Patterns: These patterns address managing user and service identities, access control policies, and authentication mechanisms in MSA-based IoT systems.
- Resilience and Fault Tolerance Patterns: These patterns focus on building resilient IoT systems that can withstand potential security incidents and recover from failures.
- Security Monitoring and Logging Patterns: These patterns involve implementing monitoring and logging mechanisms to detect and respond to security threats and incidents in MSA-based IoT systems.
- Update and Patch Management Patterns: These patterns deal with managing software updates and security patches for IoT devices and microservices to ensure they are protected against known vulnerabilities.
- Device Life-cycle Management Patterns: These patterns address the secure onboarding, provisioning, and decommissioning of IoT devices within the microservices architecture.
5. Threats to Validity
5.1. Selection Bias
5.2. Quality Assessment
5.3. Scope and Generalizability
5.4. Reporting and Language Bias
5.5. Time Frame Limitation
5.6. Systematic Errors
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Chou, T. Precision—Principles, Practices and Solutions for the Internet of Things; McGraw Hill: New York, NY, USA, 2017. [Google Scholar]
- Al-Qaseemi, S.A.; Almulhim, H.A.; Almulhim, M.F.; Chaudhry, S.R. IoT architecture challenges and issues: Lack of standardization. In Proceedings of the 2016 Future Technologies Conference (FTC), San Francisco, CA, USA, 6–7 December 2016; IEEE: New York, NY, USA, 2016; pp. 731–738. [Google Scholar] [CrossRef]
- Mouha, R.A.R.A. Internet of Things (IoT). JDAIP 2021, 9, 77. [Google Scholar] [CrossRef]
- Zhang, Z.K.; Cho, M.C.Y.; Wang, C.W.; Hsu, C.W.; Chen, C.K.; Shieh, S. IoT Security: Ongoing Challenges and Research Opportunities. In Proceedings of the 2014 IEEE 7th International Conference on Service-Oriented Computing and Applications, Matsue, Japan, 17–19 November 2014; IEEE: New York, NY, USA, 2014; pp. 230–234. [Google Scholar] [CrossRef]
- Banu, N.M.; Sujatha, C. IoT architecture a comparative study. Int. J. Pur. Appl. Math. 2017, 117, 45–49. [Google Scholar]
- Bouaouad, A.E.; Cherradi, A.; Assoul, S.; Souissi, N. The key layers of IoT architecture. In Proceedings of the 2020 5th International Conference on Cloud Computing and Artificial Intelligence: Technologies and Applications (CloudTech), Marrakesh, Morocco, 24–26 November 2020; IEEE: New York, NY, USA, 2020; pp. 1–4. [Google Scholar] [CrossRef]
- Akhdar, A.E.; Baidada, C.; Kartit, A. Study of Cyber Threats in IoT Systems. In Proceedings of the Data Analytics and Management; Swaroop, A., Polkowski, Z., Correia, S.D., Virdee, E.B., Eds.; in Lecture Notes in Networks and Systems; Springer Nature: Singapore, 2024; pp. 329–344. [Google Scholar] [CrossRef]
- Sill, A. The Design and Architecture of Microservices. IEEE Cloud Comput. 2016, 3, 76–80. [Google Scholar] [CrossRef]
- El Khalyly, B.; Belangour, A.; Banane, M.; Erraissi, A. A comparative study of microservices-based IoT platforms. Int. J. Adv. Comput. Sci. Appl. (IJACSA) 2020, 11, 389–398. [Google Scholar] [CrossRef]
- Alshuqayran, N.; Ali, N.; Evans, R. A systematic mapping study in microservice architecture. In Proceedings of the 2016 IEEE 9th International Conference on Service-Oriented Computing and Applications (SOCA), Macau, China, 4–6 November 2016; IEEE: New York, NY, USA, 2016; pp. 44–51. [Google Scholar]
- Pereira-Vale, A.; Fernandez, E.B.; Monge, R.; Astudillo, H.; Márquez, G. Security in microservice-based systems: A Multivocal literature review. Comput. Secur. 2021, 103, 102200. [Google Scholar] [CrossRef]
- Hannousse, A.; Yahiouche, S. Securing microservices and microservice architectures: A systematic mapping study. Comput. Sci. Rev. 2021, 41, 100415. [Google Scholar] [CrossRef]
- Razzaq, A. A Systematic Review on Software Architectures for IoT Systems and Future Direction to the Adoption of Microservices Architecture. SN Comput. Sci. 2020, 1, 350. [Google Scholar] [CrossRef]
- Lee, J.Y.; Lee, J. Current Research Trends in IoT Security: A Systematic Mapping Study. Mob. Inf. Syst. 2021, 2021, 8847099. [Google Scholar] [CrossRef]
- Driss, M.; Hasan, D.; Boulila, W.; Ahmad, J. Microservices in IoT Security: Current Solutions, Research Challenges, and Future Directions. Procedia Comput. Sci. 2021, 192, 2385. [Google Scholar] [CrossRef]
- Siddiqui, H.; Khendek, F.; Toeroe, M. Microservices based architectures for IoT systems—State-of-the-art review. Internet Things 2023, 23, 100854. [Google Scholar] [CrossRef]
- Methley, A.M.; Campbell, S.; Chew-Graham, C.; McNally, R.; Cheraghi-Sohi, S. PICO, PICOS and SPIDER: A comparison study of specificity and sensitivity in three search tools for qualitative systematic reviews. BMC Health Serv. Res. 2014, 14, 579. [Google Scholar] [CrossRef] [PubMed]
- Wohlin, C. Guidelines for snowballing in systematic literature studies and a replication in software engineering. In Proceedings of the 18th International Conference on Evaluation and Assessment in Software Engineering, London UK, 13–14 May 2014; ACM: New York, NY, USA, 2014; pp. 1–10. [Google Scholar] [CrossRef]
- Kitchenham, B. Procedures for performing systematic reviews. Keele UK Keele Univ. 2004, 33, 1–26. [Google Scholar]
- Kusumaningsih, D. Mendeley as a reference management and citation generator for academic articles. In Proceedings of the International Conference on Applied Science and Engineering (ICASE 2018), Sukoharjo, Indonesia, 6–7 October 2018; Atlantis Press: Amsterdam, The Netherlands, 2018; pp. 81–83. [Google Scholar]
- Innovation, V.H. Covidence—Better Systematic Review Management; Veritas Health Innovation: Melbourne, Australia, 2018. [Google Scholar]
- Liu, Q.; Chen, L.; Jiang, H.; Wu, J.; Wang, T.; Peng, T.; Wang, G. A collaborative deep learning microservice for backdoor defenses in Industrial IoT networks. Ad Hoc Netw. 2022, 124, 102727. [Google Scholar] [CrossRef]
- Chegini, H.; Mahanti, A. A Framework of Automation on Context-Aware Internet of Things (IoT) Systems. In Proceedings of the 12th IEEE/ACM International Conference on Utility and Cloud Computing Companion, Auckland, New Zealand, 2–5 December 2019; Association for Computing Machinery: New York, NY, USA, 2019; Volume 162, pp. 157–162. [Google Scholar] [CrossRef]
- Jita, H.; Pieterse, V. Framework to Apply the Internet of Things for Medical Care in a Home Environment. In Proceedings of the 2018 International Conference on Cloud Computing and Internet of Things, Singapore, 29–31 October 2018; Association for Computing Machinery: New York, NY, USA, 2018; Volume 54, pp. 45–54. [Google Scholar] [CrossRef]
- Sodhro, A.H.; Lakhan, A.; Pirbhulal, S.; Groenli, T.M.; Abie, H. A Lightweight Security Scheme for Failure Detection in Microservices IoT-Edge Networks. In Lecture Notes in Electrical Engineering; Springer: Berlin, Germany, 2022; pp. 397–409. [Google Scholar] [CrossRef]
- Power, A.; Kotonya, G. A Microservices Architecture for Reactive and Proactive Fault Tolerance in IoT Systems. In Proceedings of the 2018 IEEE 19th International Symposium on A World of Wireless, Mobile and Multimedia Networks (WoWMoM), Chania, Greece, 12–15 June 2018; IEEE: New York, NY, USA, 2018; pp. 588–599. [Google Scholar] [CrossRef]
- Santana, C.; Andrade, L.; Mello, B.; Batista, E.; Sampaio, J.V.; Prazeres, C. A Reliable Architecture Based on Reactive Microservices for IoT Applications. In Proceedings of the 25th Brazillian Symposium on Multimedia and the Web, Rio de Janeiro, Brazil, 29 October–1 November 2019; Association for Computing Machinery: New York, NY, USA, 2019; Volume 19, pp. 15–19. [Google Scholar] [CrossRef]
- Lu, D.; Huang, D.; Walenstein, A.; Medhi, D. A Secure Microservice Framework for IoT. In Proceedings of the 2017 IEEE Symposium on Service-Oriented System Engineering (SOSE), San Francisco, CA, USA, 6–9 April 2017; pp. 9–18. [Google Scholar] [CrossRef]
- Pahl, M.O.; Aubet, F.X. All Eyes on You: Distributed Multi-Dimensional IoT Microservice Anomaly Detection. In Proceedings of the 14th International Conference on Network and Service Management, CNSM 2018 and Workshops, 1st International Workshop on High-Precision Networks Operations and Control, HiPNet 2018 and 1st Workshop on Segment Routing and Service Function Chaining, Rome, Italy, 5–9 November 2018; SR+SFC 2018. pp. 72–80. [Google Scholar]
- Alshudukhi, K.S.; Khemakhem, M.A.; Eassa, F.E.; Jambi, K.M. An Interoperable Blockchain Security Frameworks Based on Microservices and Smart Contract in IoT Environment. Electronics 2023, 12, 776. [Google Scholar] [CrossRef]
- Sun, L.; Li, Y.; Memon, R.A. An open IoT framework based on microservices architecture. China Commun. 2017, 14, 154–162. [Google Scholar] [CrossRef]
- Whaiduzzaman, M.; Mahi, M.J.N.; Barros, A.; Khalil, M.I.; Fidge, C.; Buyya, R. BFIM: Performance Measurement of a Blockchain Based Hierarchical Tree Layered Fog-IoT Microservice Architecture. IEEE Access 2021, 9, 106655–106674. [Google Scholar] [CrossRef]
- Xu, R.; Nikouei, S.Y.; Chen, Y.; Blasch, E.; Aved, A. BlendMAS: A blockchain-enabled decentralized microservices architecture for smart public safety, presented at the Proceedings - 2019 2nd IEEE International Conference on Blockchain. Blockchain 2019, 2019, 564–571. [Google Scholar] [CrossRef]
- Nguyen, L.T.T.; Ha, S.X.; Le, T.H.; Luong, H.H.; Vo, K.H.; Nguyen, K.H.T.; Nguyen, A.T.; Dao, T.A.; Nguyen, H.V.K. BMDD: A novel approach for IoT platform (broker-less and microservice architecture, decentralized identity, and dynamic transmission messages). PeerJ Comput. Sci. 2022, 8, e950. [Google Scholar] [CrossRef]
- Bracke, V.; Sebrechts, M.; Moons, B.; Hoebeke, J.; Turck, F.D.; Volckaert, B. Design and evaluation of a scalable Internet of Things backend for smart ports. Softw.-Pract. Exp. 2021, 51, 1557–1579. [Google Scholar] [CrossRef]
- Aydin, S.; Aydin, M.N. Design and implementation of a smart beehive and its monitoring system using microservices in the context of IoT and open data. Comput. Electron. Agric. 2022, 196, 106897. [Google Scholar] [CrossRef]
- Díaz-Sánchez, D.; Marín-Lopez, A.; Almenarez Mendoza, F.; Arias Cabarcos, P. DNS/DANE collision-based distributed and dynamic authentication for microservices in IoT. Sensors 2019, 19, 3292. [Google Scholar] [CrossRef] [PubMed]
- Santana, C.; Andrade, L.; Delicato, F.C.; Prazeres, C. Increasing the availability of IoT applications with reactive microservices. SOCA 2021, 15, 109–126. [Google Scholar] [CrossRef]
- Maroof, U.; Shaghaghi, A.; Michelin, R.; Jha, S. iRECOVer: Patch your IoT on-the-fly. Future Gener. Comput. Syst. 2022, 132, 178–193. [Google Scholar] [CrossRef]
- Maia, R.F.; Lurbe, C.B.; Baniya, A.A.; Hornbuckle, J. IRRISENS: An IoT Platform Based on Microservices Applied in Commercial-Scale Crops Working in a Multi-Cloud Environment. Sensors 2020, 20, 7163. [Google Scholar] [CrossRef]
- Rath, C.K.; Mandal, A.K.; Sarkar, A. Microservice based scalable IoT architecture for device interoperability. Comput. Stand. Interfaces 2023, 84, 103697. [Google Scholar] [CrossRef]
- Ying, F.; Zhao, S.; Deng, H. Microservice Security Framework for IoT by Mimic Defense Mechanism. Sensors 2022, 22, 2418. [Google Scholar] [CrossRef]
- Benayache, A.; Bilami, A.; Barkat, S.; Lorenz, P.; Taleb, H. MsM: A microservice middleware for smart WSN-based IoT application. J. Netw. Comput. Appl. 2019, 144, 138–154. [Google Scholar] [CrossRef]
- Rakesh, N. Performance analysis of anomaly detection of different IoT datasets using cloud micro services. In Proceedings of the 2016 International Conference on Inventive Computation Technologies (ICICT), Coimbatore, India, 26–27 August 2016; pp. 1–5. [Google Scholar] [CrossRef]
- Ordonez-Camacho, D. Reducing the IoT security breach with a microservice architecture based on TLS and OAuth2. Ingenius 2020, 25, 94–103. [Google Scholar] [CrossRef]
- Aldea, C.L.; Bocu, R.; Vasilescu, A. Relevant Cybersecurity Aspects of IoT Microservices Architectures Deployed over Next-Generation Mobile Networks. Sensors 2023, 23, 189. [Google Scholar] [CrossRef]
- Jin, W.; Xu, R.; You, T.; Hong, Y.G.; Kim, D. Secure edge computing management based on independent microservices providers for gateway-centric IoT networks. IEEE Access 2020, 8, 187975–187990. [Google Scholar] [CrossRef]
- Pahl, M.O.; Donini, L. Securing IoT microservices with certificates, presented at the IEEE/IFIP Network Operations and Management Symposium: Cognitive Management in a Cyber World. NOMS 2018, 2018, 1–5. [Google Scholar] [CrossRef]
- Ghosh, A.; Mukherjee, A.; Misra, S. SEGA: Secured Edge Gateway Microservices Architecture for IIoT-Based Machine Monitoring. IEEE Trans. Ind. Inform. 2022, 18, 1949–1956. [Google Scholar] [CrossRef]
- Nguyen, L.T.T.; Nguyen, N.N.P.; Nguyen, T.A.; Vo, H.K.; Luong, H.H.; Dao, T.A.; Nguyen, K.H.T.; Ha, X.S. SIP-MBA: A Secure IoT Platform with Brokerless and Micro-service Architecture. Int. J. Adv. Comput. Sci. Appl. 2021, 12. [Google Scholar] [CrossRef]
- Taneja, M.; Jalodia, N.; Byabazaire, J.; Davy, A.; Olariu, C. SmartHerd management: A microservices-based fog computing–assisted IoT platform towards data-driven smart dairy farming. Software Pract. Exp. 2019, 49, 1055–1078. [Google Scholar] [CrossRef] [PubMed]
- Alanezi, K.; Mishra, S. Utilizing Microservices Architecture for Enhanced Service Sharing in IoT Edge Environments. IEEE Access 2022, 10, 90034–90044. [Google Scholar] [CrossRef]
- Ouyang, R.; Wang, J.; Xu, H.; Chen, S.; Xiong, X.; Tolba, A.; Zhang, X. A Microservice and Serverless Architecture for Secure IoT System. Sensors 2023, 23, 4868. [Google Scholar] [CrossRef]
- Atitallah, S.B.; Driss, M.; Ghezala, H.B. Revolutionizing Disease Diagnosis: A Microservices-Based Architecture for Privacy-Preserving and Efficient IoT Data Analytics Using Federated Learning. Procedia Comput. Sci. 2023, 225, 3322–3331. [Google Scholar] [CrossRef]
- Zhang, X.; Liang, J.; Lu, Y.; Zhang, P.; Bi, Y. Differentiated Security Requirements: An Exploration of Microservice Placement Algorithms in Internet of Vehicles. Electronics 2024, 13, 1597. [Google Scholar] [CrossRef]
- Wohlin, C.; Runeson, P.; Höst, M.; Ohlsson, M.C.; Regnell, B.; Wesslén, A. Experimentation in Software Engineering; Springer Science & Business Media: Berlin, Germany, 2012. [Google Scholar]
- Kuhrmann, M.; Fernández, D.M.; Daneva, M. On the pragmatic design of literature studies in software engineering: An experience-based guideline. Empir. Softw. Eng. 2017, 22, 2852–2891. [Google Scholar] [CrossRef]
- Petticrew, M.; Roberts, H. Systematic Reviews in the Social Sciences: A Practical Guide; John Wiley & Sons: Hoboken, NJ, USA, 2008. [Google Scholar]
- University of Hawai. Systematic Review Toolbox: Quality Assessment. Available online: https://hslib.jabsom.hawaii.edu/systematicreview/qualityassessment (accessed on 21 July 2024).
- Young, J.M.; Solomon, M.J. How to critically appraise an article. Nat. Rev. Gastroenterol. Hepatol. 2009, 6, 82–91. [Google Scholar] [CrossRef]
- Petersen, K.; Vakkalanka, S.; Kuzniarz, L. Guidelines for conducting systematic mapping studies in software engineering: An update. Inf. Softw. Technol. 2015, 64, 1. [Google Scholar] [CrossRef]



| Keywords String | Database | Queries |
|---|---|---|
| • Microservices, micro-services, MSA. • Internet of Things, IoT, smart devices. • Security, secure, intrusion, vulnerabilities. | WoS | TS = (“microservices” OR “micro-services” OR “MSA”) AND TS = (“Internet of Things” OR “IoT” OR “smart devices”) AND TS = (“security” OR “secure” OR “intrusion” OR “vulnerabilities”) AND PY = (2010–2024)Results: 136 |
| TS = ((“microservices” OR “micro-services” OR “MSA”) NEAR/100 (“Internet of Things” OR “IoT” OR “smart devices”) NEAR/100 (“security” OR “secure” OR “intrusion” OR “vulnerabilities”)) AND PY = (2010–2024)Results: 78 | ||
| TS = ((“microservices” OR “micro-services” OR “MSA”) NEAR/50 (“Internet of Things” OR “IoT” OR “smart devices”) NEAR/50 (“security” OR “secure” OR “intrusion” OR “vulnerabilities”)) AND PY = (2010–2024)Results: 55 | ||
| Other Repositories | (“microservices” OR “micro-services” OR “MSA”) AND (“Internet of Things” OR “IoT” OR “smart devices”) AND (“security*” OR “intrusion” OR “vulnerabilities*”) |
| Repository | Search Results |
|---|---|
| WoS | 55 |
| Scopus | 205 |
| ScienceDirect | 1273 |
| SpringerLink | 1786 |
| ACM | 722 |
| IEEE | 347 |
| Total | 4388 |
| Quality Assessment Criteria | ID | Question | Weight | Score Legend |
|---|---|---|---|---|
| Research Question and Objectives | C1.1 | Are the objectives of the study well -stated and aligned with its research question? | 3 | - 1 (yes) - 0 (no) |
| C1.2 | Is the research question clearly defined and relevant to IoT microservice security? | 3 | ||
| Study Design, Methodology, and Evaluation | C2.1 | Are the methods and techniques used to investigate IoT microservice security clearly described? | 2 | - 1 (Clear description) - 0.5 (Mostly clear description with minor gaps) -0 (Unclear description) |
| C2.2 | Are the evaluation metrics and performance measures appropriate for assessing the effectiveness and efficiency of the proposed solutions? | 2 | -1 (Appropriate) - 0.5 (Some appropriate metrics, but room for improvement) - 0 (Inappropriate/NA) | |
| C2.3 | Does the study employ an appropriate research design for investigating IoT microservice security aspects, such as experimental studies or case studies? | 3 | - 1 (yes) - 0 (no) | |
| Results and Findings | C3.1 | Do the findings provide meaningful insights into the security issues, vulnerabilities, or threats in IoT microservice? | 3 | - 1 (Meaningful insights) - 0.5 (Findings provide meaningful insights, but some areas lack depth) - 0 (Lack of meaningful insights) |
| Analysis and Discussion | C4.1 | Does the study clearly address any specific security issues in IoT microservice systems? | 2 | - 1 (yes) - 0 (no) |
| C4.2 | Are the limitations of the proposed approaches or studies discussed? | 1 | - 1 (Limitations discussed) - 0.5 (Some limitations discussed, but not comprehensively) - 0 (Limitations not discussed) | |
| Practical Applicability | C5.1 | Are the proposed security mechanisms or approaches feasible and applicable in real -world IoT deployments according to the authors? | 3 | - 1 (yes) - 0 (no) |
| C5.2 | Does the study provide practical recommendations or guidelines for securing IoT microservices? | 2 | - 1 (Detailed and validated solution) - 0.5 (Overview of solution or framework) - 0 (No clear solutions) | |
| Citation and Quality of References | C6.1 | Has the study been cited by other articles? | 2 | - 1 (yes) - 0 (no) |
| C6.2 | Has the study been published in ranked journals or conference proceedings? | 2 | - JRC for journals: - 1 (Q1 or Q2) - 0.5 (Q3 or Q4) - 0 (not ranked) |
| ID | Data Field | Description | RQ |
|---|---|---|---|
| 1 | PID | Paper ID + Title + First author’s name. | |
| 2 | Year | Year of published paper. | |
| 3 | Type of publication | Conference, journal, workshop. | |
| 4 | Study field | Agriculture, smart city, computer science, other. | |
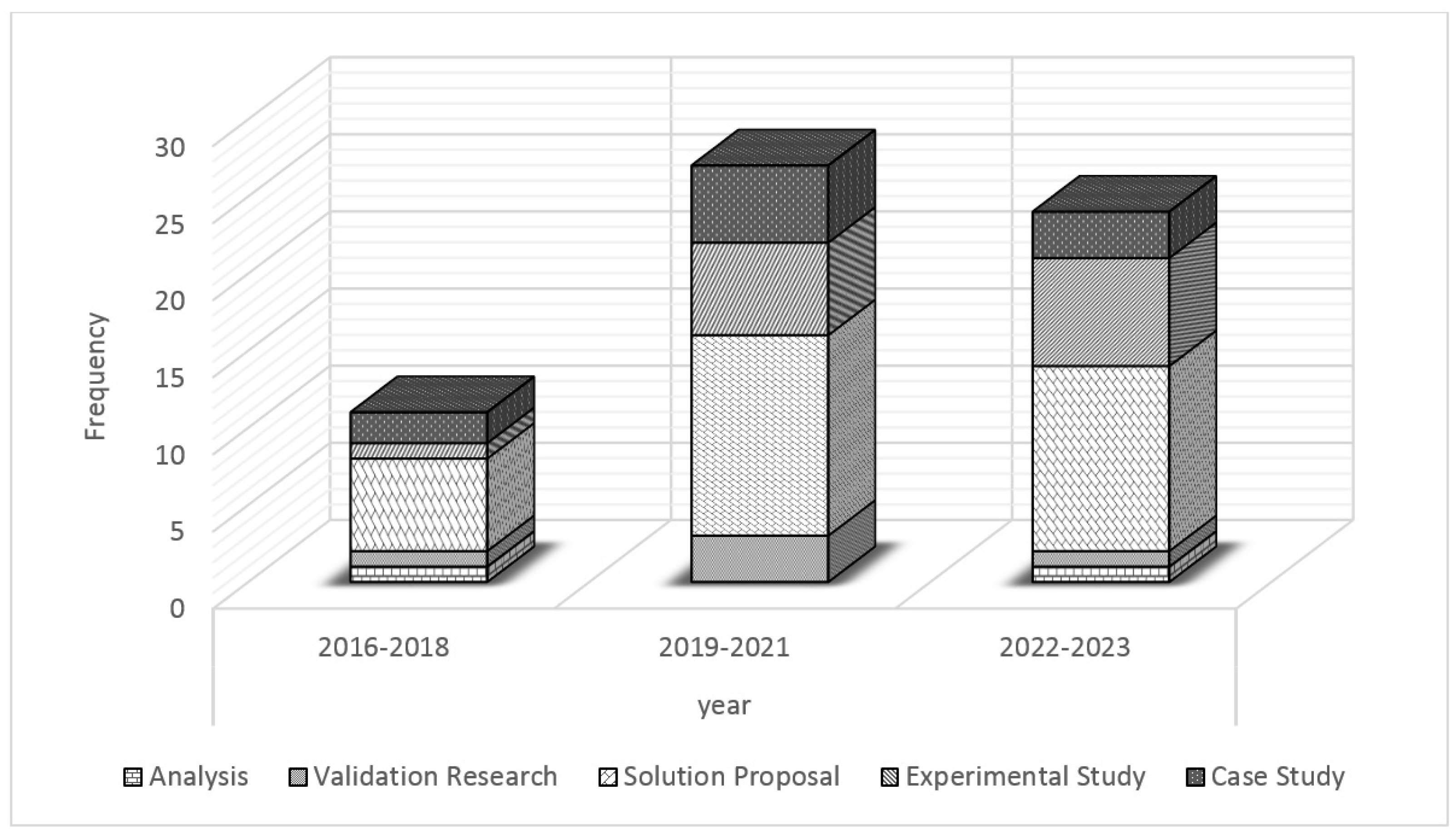
| 5 | Study design | Case study, experimental study, solution proposal, analysis, validation research, other. | |
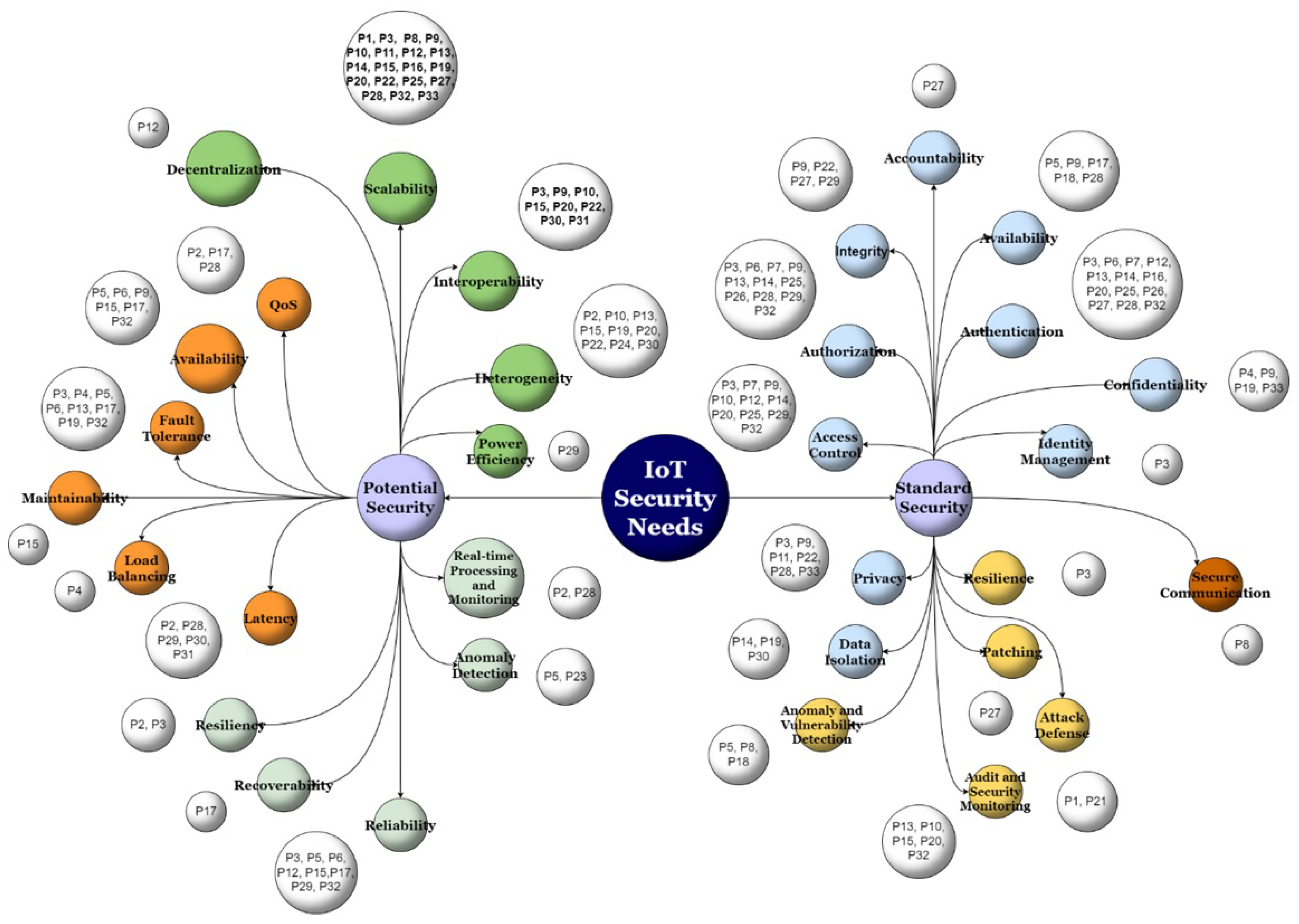
| 5 | Security aspects | Security aspects addressed: potential security, standard security, both. | |
| 6 | Solution type | General measures, methodology, architecture, framework, algorithm, application, tool, other. | |
| 7 | Security mechanisms | Security mechanisms proposed or used. Whether the study is coupled with blockchain, machine learning, or other technologies. | |
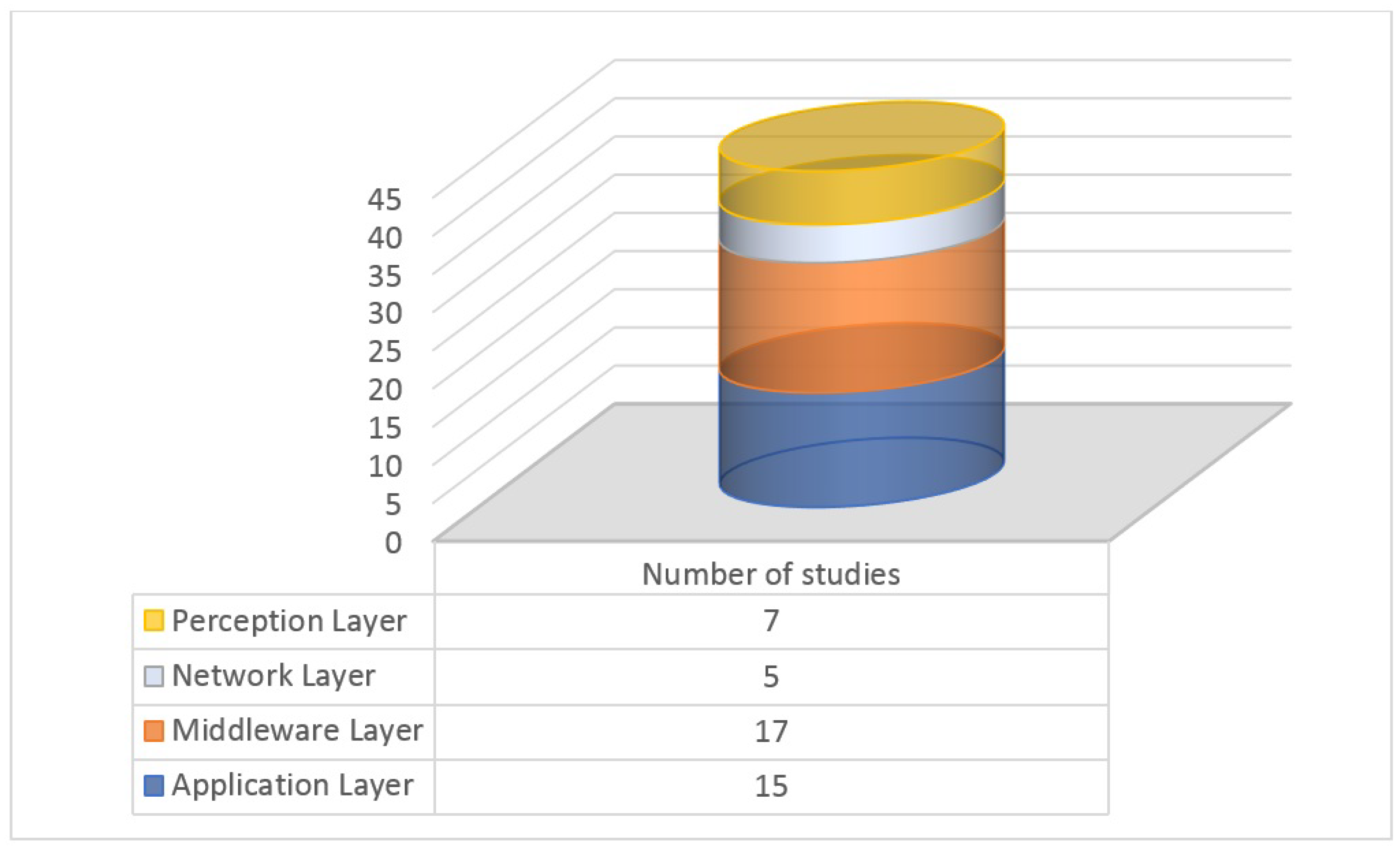
| 8 | Applicability level | Architectural level where the security mechanisms are applied. | |
| 9 | Benefits of MSA in IoT | Benefits of adopting microservices in IoT, particularly in terms of security. | RQ3 |
| 10 | Key MSA IoT challenges | Possible challenges could include issues related to performance, security, interoperability, complexity, or resource constraints. | RQ4 |
| 11 | Security risks in MSA IoT | Potential security risks associated with using microservices in IoT systems. | RQ5 |
| 12 | Performance implications | Performance implications of using microservices in IoT systems. | RQ6 |
| 13 | Best practices | Practical aspects of implementing microservices in IoT systems. | RQ7 |
| 14 | Future directions for research | Most promising future directions for research in the area of microservices adoption in IoT systems. | RQ8 |
| PID | Reference | Type | Publisher/Conference | Year | Score |
|---|---|---|---|---|---|
| P1 | [22] | Journal paper | Elsevier | 2022 | 25 |
| P2 | [23] | Conference paper | IEEE/ACM | 2019 | 14.5 |
| P3 | [24] | Conference paper | IEEE | 2018 | 21 |
| P4 | [25] | Conference paper | Springer | 2022 | 20 |
| P5 | [26] | Conference paper | IEEE | 2018 | 26 |
| P6 | [27] | Conference paper | ACM | 2019 | 16 |
| P7 | [28] | Conference paper | IEEE | 2017 | 17 |
| P8 | [29] | Conference paper | IEEE | 2018 | 26 |
| P9 | [30] | Journal paper | MDPI | 2023 | 25 |
| P10 | [31] | Journal paper | China Institute of Communication | 2017 | 18 |
| P11 | [32] | Journal paper | IEEE | 2021 | 26 |
| P12 | [33] | Conference paper | IEEE | 2019 | 19.5 |
| P13 | [34] | Journal paper | PeerJ Inc. | 2022 | 22.5 |
| P14 | [35] | Journal paper | John Wiley and Sons Ltd | 2021 | 14.5 |
| P15 | [36] | Journal paper | Elsevier | 2022 | 22.5 |
| P16 | [37] | Journal paper | MDPI | 2019 | 26 |
| P17 | [38] | Journal paper | Springer | 2020 | 21.5 |
| P18 | [39] | Journal paper | Elsevier | 2022 | 26 |
| P19 | [40] | Journal paper | MDPI | 2020 | 24 |
| P20 | [41] | Journal paper | Elsevier | 2023 | 17 |
| P21 | [42] | Journal paper | MDPI | 2022 | 27 |
| P22 | [43] | Journal paper | Academic Press Inc. | 2019 | 15.5 |
| P23 | [44] | Conference paper | IEEE | 2016 | 19.5 |
| P24 | [45] | Journal paper | Ingenius | 2021 | 21.5 |
| P25 | [46] | Journal paper | MDPI | 2023 | 21.5 |
| P26 | [47] | Journal paper | IEEE | 2020 | 21.5 |
| P27 | [48] | Conference paper | IEEE | 2018 | 24 |
| P28 | [49] | Journal paper | IEEE | 2022 | 21 |
| P29 | [50] | Journal paper | Science and Information Organization | 2021 | 14 |
| P30 | [51] | Journal paper | John Wiley and Sons Ltd | 2019 | 17.5 |
| P31 | [52] | Journal paper | IEEE | 2022 | 15.5 |
| P32 | [53] | Journal paper | MDPI | 2023 | 23.5 |
| P33 | [54] | Journal paper | Elsevier | 2023 | 20.5 |
| Field | Number of Studies |
|---|---|
| Computing models (cloud, edge, fog) | 9 |
| IoT Security | 7 |
| Industrial Internet of Things (IIoT) | 2 |
| Smart IoT | 5 |
| Agriculture | 3 |
| Communication infrastructures | 1 |
| Healthcare | 4 |
| General/Agnostic | 2 |
| Security Mechanisms | Examples | PID |
|---|---|---|
| MSA coupled with Deep Learning and Machine Learning for Security | STRIP-based backdoor detection; CycleGAN-based trigger identification; Unlearning-based model mitigation. | P1 |
| The first microservice utilizes complex event processing for real-time data stream analysis; the second employs machine learning for proactive fault tolerance. | P5 | |
| Anomaly Detection model; Data-Centric Discovery. | P8 | |
| MSA coupled with Blockchain for Security | Dynamic Service Replacement and Isolation Mechanism; Smart contracts. | P3 |
| Tamper-proof resistant scheme; Blockchain-based data verification; System schedulability. | P11 | |
| Security Policy; Smart contracts; Decentralized Security Microservices. | P12 | |
| Decentralized authentication; Role-Based access control (RBAC) model; Dynamic message transmission mechanism. | P13 | |
| Anomaly Detection and Monitoring | Fault-tolerant Microservices framework for real-time data stream analysis and proactive fault mitigation. | P5 |
| Automated anomalous behavior detection in surveillance videos. | P23 | |
| Log monitoring | P32 | |
| Encryption techniques | Encryption–Decryption (RSA, DES, and AES) and dynamic service interaction to address privacy concerns. | P22 |
| Modified Fully Homomorphism Encryption. | P4 | |
| Secure Boot and Flash Encryption; AES Key Management. | P28 | |
| AWS Key Management Service (asymmetric encryption) | P32 | |
| TLS Encryption. | P24 | |
| Containerization and technological independence | Docker Containerization; Lightweight container-based virtualization architecture for IoT service coordination. | P7, P9, P28, P30, P31 |
| API Security | REST API Security; API Gateways; Protocol Conversion; Traffic Restriction. | P7, P8, P15, P25, P32 |
| Edge Gateways | Security and isolated edge gateways; Edge Gateway Replication. | P26, P28 |
| Authentication and Authorization | IAM; Single Sign-On and Federation; Access Control Policies; Mutual Authentication Credentials, OAuth2 access tokens. | P3, P10, P14, P15, P18, P24, P25, P26, P32 |
| Certificates and Signatures | PKI certificates. | P24 |
| Certificate pinning; Chameleon signatures. | P16 | |
| Security certificate. | P19 | |
| X.509 version 3 certificates; Fully distributed certificate revocation; Short certificate lifetimes; and Automated certificate renewal. | P27 | |
| Patch Management | Firmware Updates; Patch Management. | P20 |
| Load Balance | Load balancer for each microservice; Workload assignment strategy. | P4, P28 |
| MSA IoT Challenge | Brief | Proposed Solutions | PID |
|---|---|---|---|
| Secure data distribution | With the vast amount of data generated and exchanged within IoT systems, ensuring data privacy, confidentiality, and integrity becomes paramount. Microservice-based applications must verify the authenticity of each service involved in communication to prevent malicious misuse by hackers. Robust authorization and access control mechanisms are necessary to address security requirements in heterogeneous environments. | Implementing end-to-end encryption, using protocols such as TLS, ensures data confidentiality during transmission. Additionally, adopting robust access control mechanisms like OAuth2 and Zero Trust security models can enhance authentication and authorization processes. Identity management frameworks like OAuth2 can also be integrated to handle authorization securely and efficiently. | P20, P24, P32 |
| Secure Integration of Resource-Constrained IoT Devices in MSA | The challenge lies in ensuring that the applications can run efficiently and effectively on resource-limited IoT devices while maintaining desired levels of performance, functionality, and security. | To address this, lightweight security protocols such as Datagram Transport Layer Security (DTLS) can be employed. Additionally, edge computing can be leveraged to offload resource-intensive tasks to nearby devices or servers, reducing the computational burden on resource-constrained devices. Microservices can be designed to operate in low-power modes, minimizing the energy consumption of IoT devices. | P8, P4 |
| Discovery and scheduling of services | Microservice-based applications are composed of fine-grained, distributed, and independent entities. Ensuring smooth operations and effective utilization of resources requires dynamically identifying and allocating services based on demand, availability, and priority. This challenge involves managing the dynamic nature of Microservices Architecture in IoT settings, taking into account factors like limited computational resources, intermittent connectivity, and constrained devices. | Service orchestration tools, such as Kubernetes, can dynamically manage microservices, ensuring proper load balancing and resource allocation based on service demand. Service mesh architectures can also be used to enhance communication between microservices by automating discovery and providing traffic management. | P20, P16 |
| Dynamic Configuration and Interface Flexibility | Adopting Microservices Architecture (MSA) for IoT solutions requires dynamically configuring and defining interfaces between modules. The heterogeneous nature of IoT ecosystems demands flexible module interactions, and using well-defined service interfaces is essential. However, current practices lack standardized methods for this purpose, necessitating innovative approaches to streamline interactions effectively. | Employing containerization technologies like Docker can help in standardizing microservice interfaces and promoting portability across different IoT environments. Additionally, adopting APIs and using open standards such as REST or gRPC for communication ensures flexibility and simplifies the process of integrating diverse modules in IoT ecosystems. | P18 |
| Heterogeneity in Firmware Extraction for IoT Devices | IoT devices are highly diverse and heterogeneous, often featuring a wide range of architectures, protocols, and applications. Manually extracting firmware from such a large variety of available binary firmware becomes a labor-intensive and time-consuming task. This scalability issue can impede the efficient assessment of security vulnerabilities and updates for a vast number of IoT devices. | Automated tools for firmware extraction and analysis can speed up the process. Standardizing the firmware formats used by IoT devices can also reduce the complexity of this challenge. IoT-specific solutions like MUD (Manufacturer Usage Description) can be employed to standardize behavior expectations. | |
| Comprehensive Vulnerability Detection for Diverse IoT Deployments | In the MSA IoT ecosystem, detecting vulnerabilities comprehensively across the diverse range of deployed IoT devices poses a challenge. Many existing detection techniques focus on specific types of vulnerabilities, limiting their effectiveness in covering the full spectrum of potential threats in IoT systems with a blend of different protocols, architectures, and applications. Developing holistic and adaptable vulnerability detection methods becomes essential to ensure the security of diverse IoT deployments. | Comprehensive security platforms like Microsoft Azure Security Center or AWS IoT Device Defender provide real-time vulnerability assessments across a variety of IoT architectures. Machine learning models can also be trained to detect patterns of anomalous behavior, improving the detection of unknown vulnerabilities across diverse deployments. | |
| Achieving Seamless Integration in IoT with Microservices | The smart domain of IoT comprises various software and platforms collecting and processing data, requiring effective coordination and communication to fully leverage the benefits of Microservices Architecture. | Using middleware platforms or IoT gateways that act as intermediaries between different systems can simplify integration. Standards like MQTT (Message Queuing Telemetry Transport) can be utilized for efficient messaging between IoT devices and microservices, ensuring smooth data exchange. | P9 |
| Management Complexity | The increased number of microservices can lead to management complexity, making it challenging to maintain a consistent and robust security posture across the entire system | Implementing service orchestration frameworks such as Kubernetes or using microservices management platforms can automate much of the complexity involved in managing large numbers of microservices. These tools also provide features for monitoring, scaling, and securing microservices, reducing the overall management burden. | Self-Suggested |
| Security Risks in MSA IoT | Brief | PID |
|---|---|---|
| Container Vulnerabilities | Microservices are often deployed within containers, such as Docker containers, but inadequate security measures or mismanaged configurations can lead to exploitable vulnerabilities. Outdated or unpatched container images may contain known vulnerabilities, posing risks to the microservices and enabling unauthorized access. Using Docker to orchestrate the cloud environment exposes various security risks, including internally deployed malicious applications, infected containers, and malevolent or semi-honest hosts. These risks emphasize the importance of implementing robust security measures to protect the integrity and safety of the containerized microservices in the cloud. | P21 |
| Risk of Performance Bottleneck | As the number of microservices increases, the complexity of coordinating and orchestrating them grows. If not carefully designed and optimized, the communication and data exchange between microservices might become inefficient, resulting in increased latency and reduced responsiveness. Performance bottlenecks may occur due to issues like high network traffic, resource contention, or inefficient data transfers between microservices. Such bottlenecks can negatively impact the real-time processing capabilities of the IoT system and degrade its overall performance. | P12 |
| Distributed Data Sharing/API Vulnerabilities | Each microservice typically has its own set of APIs that allow data exchange and communication with other services. If not appropriately secured, these APIs could become entry points for attackers to exploit and compromise the overall system’s security.Exposing APIs without proper authentication and access controls might enable unauthorized access to sensitive data or functionalities. Additionally, insufficient data validation and input sanitization in microservices’ APIs can lead to security vulnerabilities like injection attacks or data breaches. The distributed nature of microservices can make it challenging to maintain consistent and robust security measures across the entire system. | P12, P21 |
| Distributed Denial of Service (DDoS) Attacks | Microservice architectures distribute functionality across multiple services, making them more susceptible to DDoS attacks. If a specific microservice is overwhelmed with malicious requests, it can impact the availability and performance of the entire IoT system, potentially causing service disruptions or outages | P7 |
| Insecure Communication | Microservices typically communicate with each other over networks, making them susceptible to security vulnerabilities. If proper encryption and authentication measures are not implemented, sensitive data transmitted between microservices can be intercepted or tampered with, leading to data breaches or unauthorized access | Self-Suggested |
| Insider Threats | Microservices are typically developed and maintained by different teams or individuals. This distributed ownership introduces the risk of insider threats, where a malicious or compromised insider can exploit vulnerabilities or gain unauthorized access to sensitive data across multiple microservices. | |
| Software Vulnerabilities | Microservices may rely on third-party software libraries, and if these libraries have known vulnerabilities, they can be exploited by attackers to compromise the entire system. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
El Akhdar, A.; Baidada, C.; Kartit, A.; Hanine, M.; García, C.O.; Lara, R.G.; Ashraf, I. Exploring the Potential of Microservices in Internet of Things: A Systematic Review of Security and Prospects. Sensors 2024, 24, 6771. https://doi.org/10.3390/s24206771
El Akhdar A, Baidada C, Kartit A, Hanine M, García CO, Lara RG, Ashraf I. Exploring the Potential of Microservices in Internet of Things: A Systematic Review of Security and Prospects. Sensors. 2024; 24(20):6771. https://doi.org/10.3390/s24206771
Chicago/Turabian StyleEl Akhdar, Abir, Chafik Baidada, Ali Kartit, Mohamed Hanine, Carlos Osorio García, Roberto Garcia Lara, and Imran Ashraf. 2024. "Exploring the Potential of Microservices in Internet of Things: A Systematic Review of Security and Prospects" Sensors 24, no. 20: 6771. https://doi.org/10.3390/s24206771
APA StyleEl Akhdar, A., Baidada, C., Kartit, A., Hanine, M., García, C. O., Lara, R. G., & Ashraf, I. (2024). Exploring the Potential of Microservices in Internet of Things: A Systematic Review of Security and Prospects. Sensors, 24(20), 6771. https://doi.org/10.3390/s24206771








