Routing Selection Algorithm for Mobile Ad Hoc Networks Based on Neighbor Node Density
Abstract
1. Introduction
1.1. Background
1.2. Related Work
2. Notation
3. Node-Density-Based Routing Method
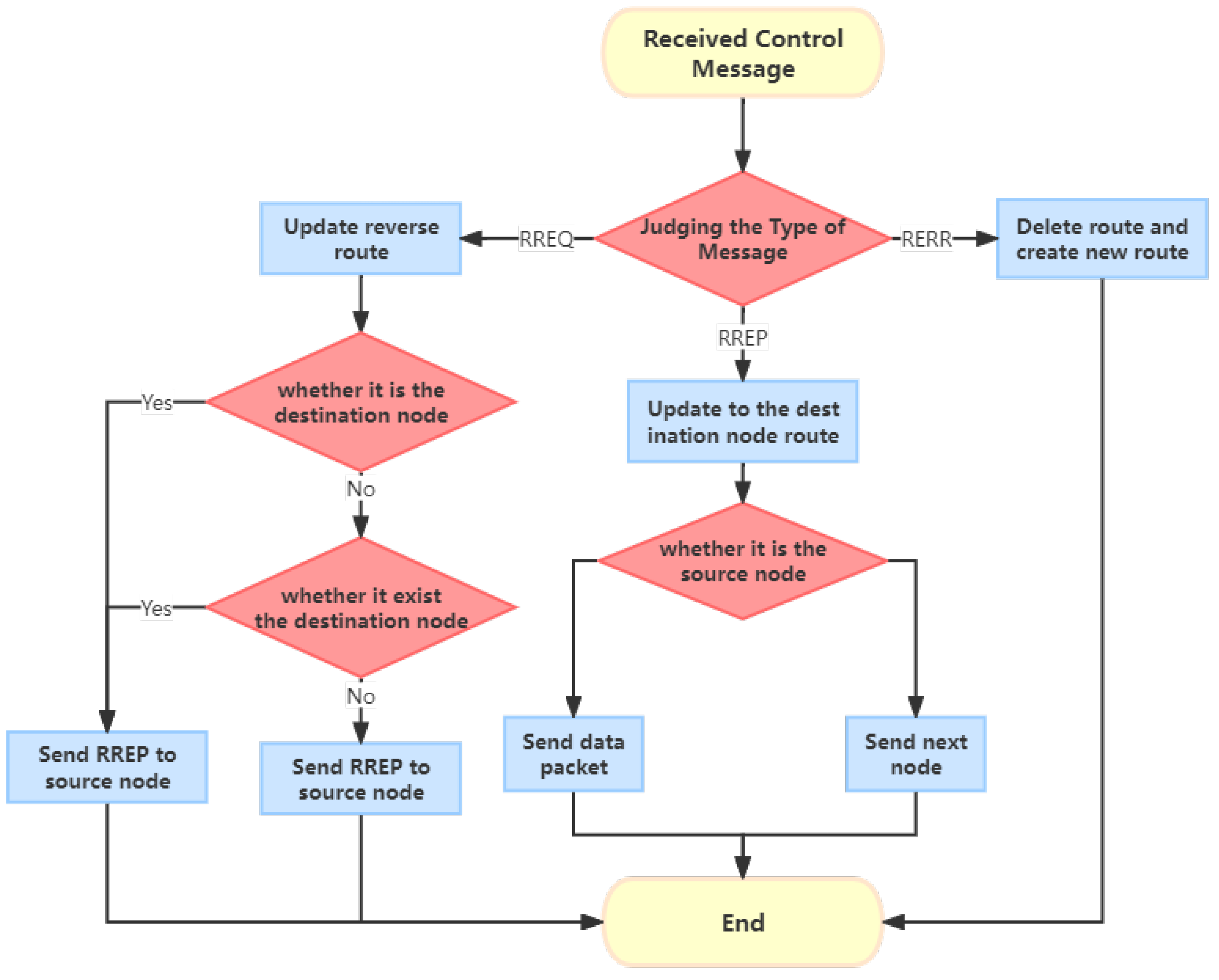
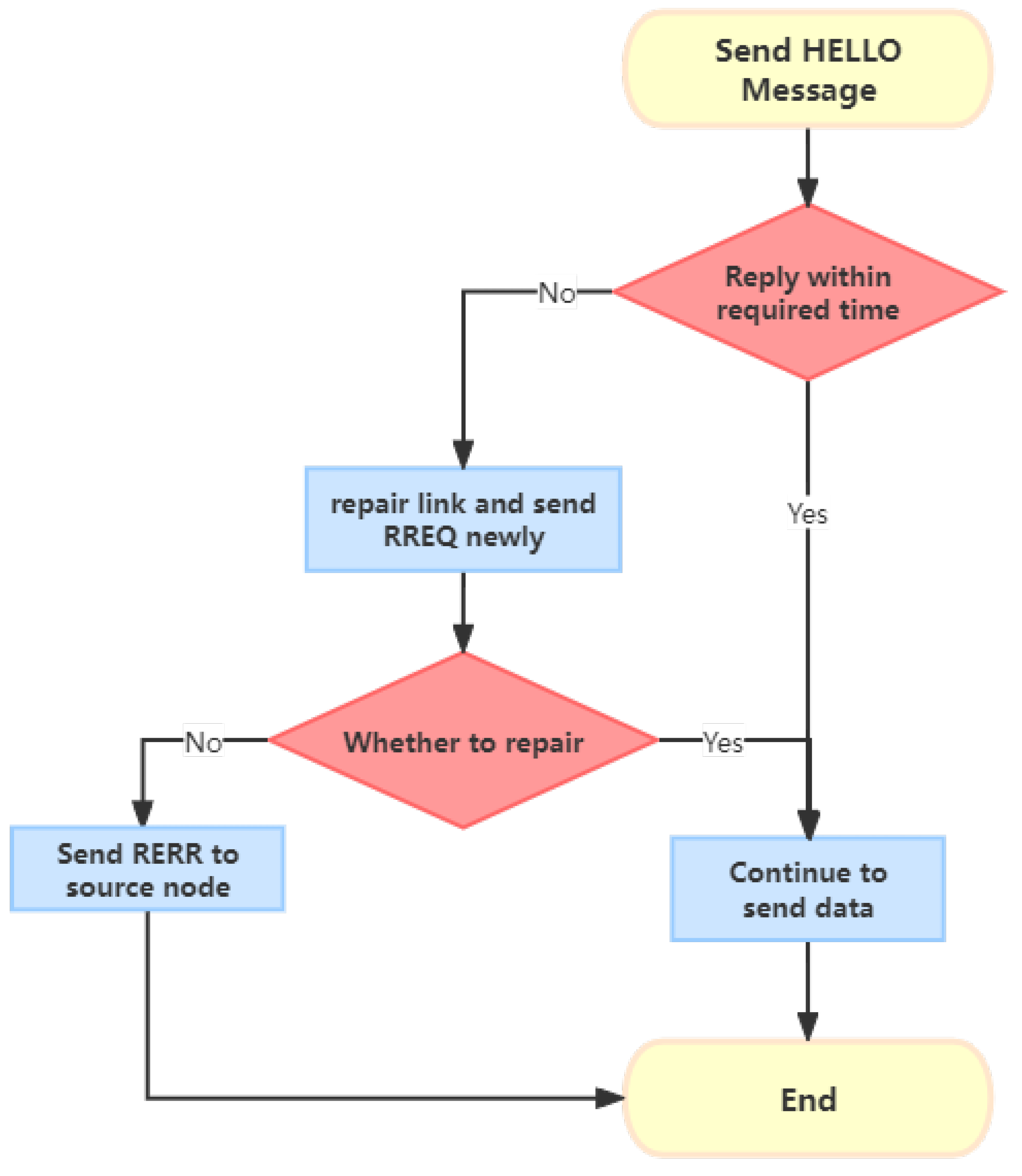
3.1. AODV
3.2. ND-AODV
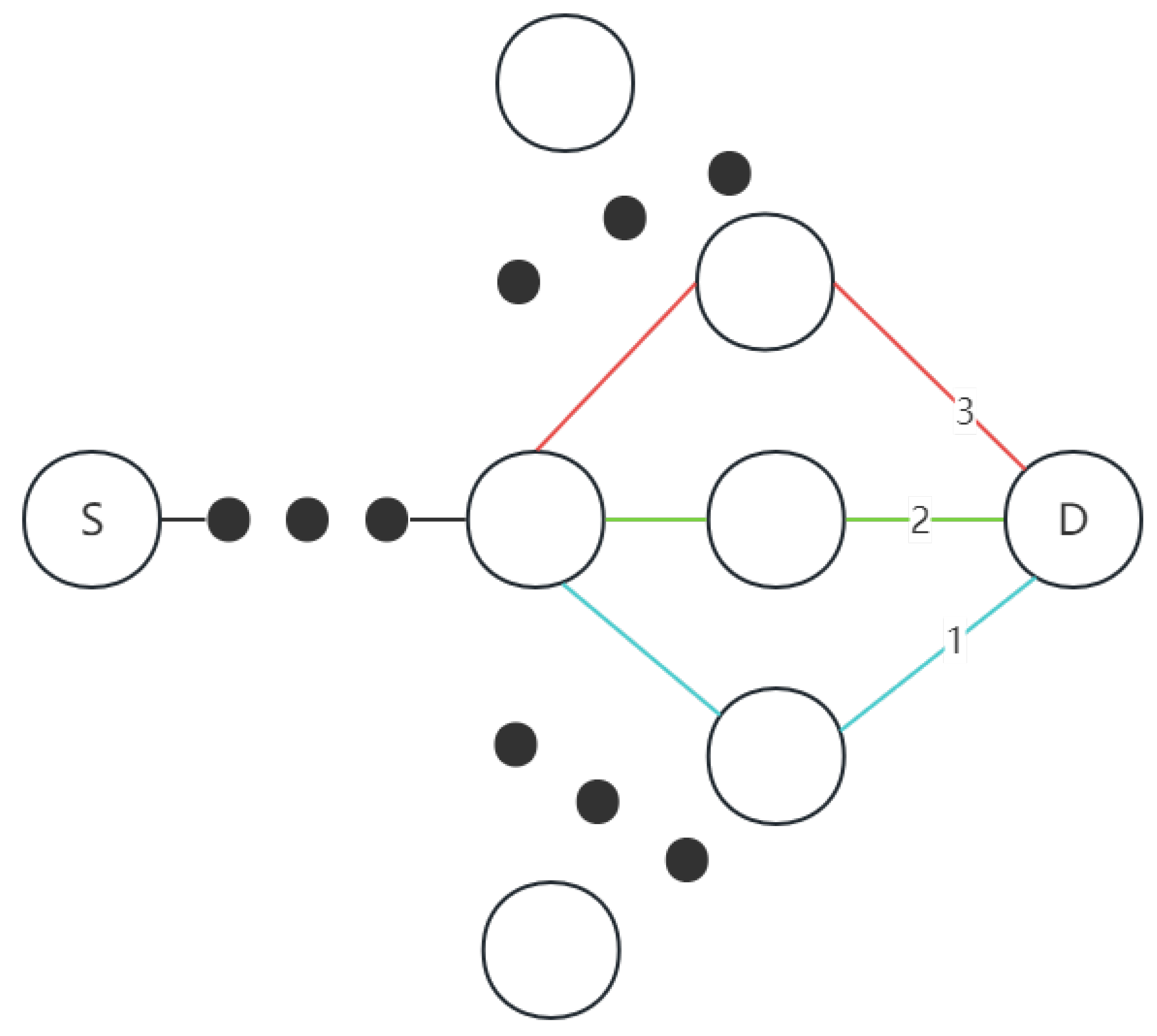
3.3. The Issues with ND-AODV
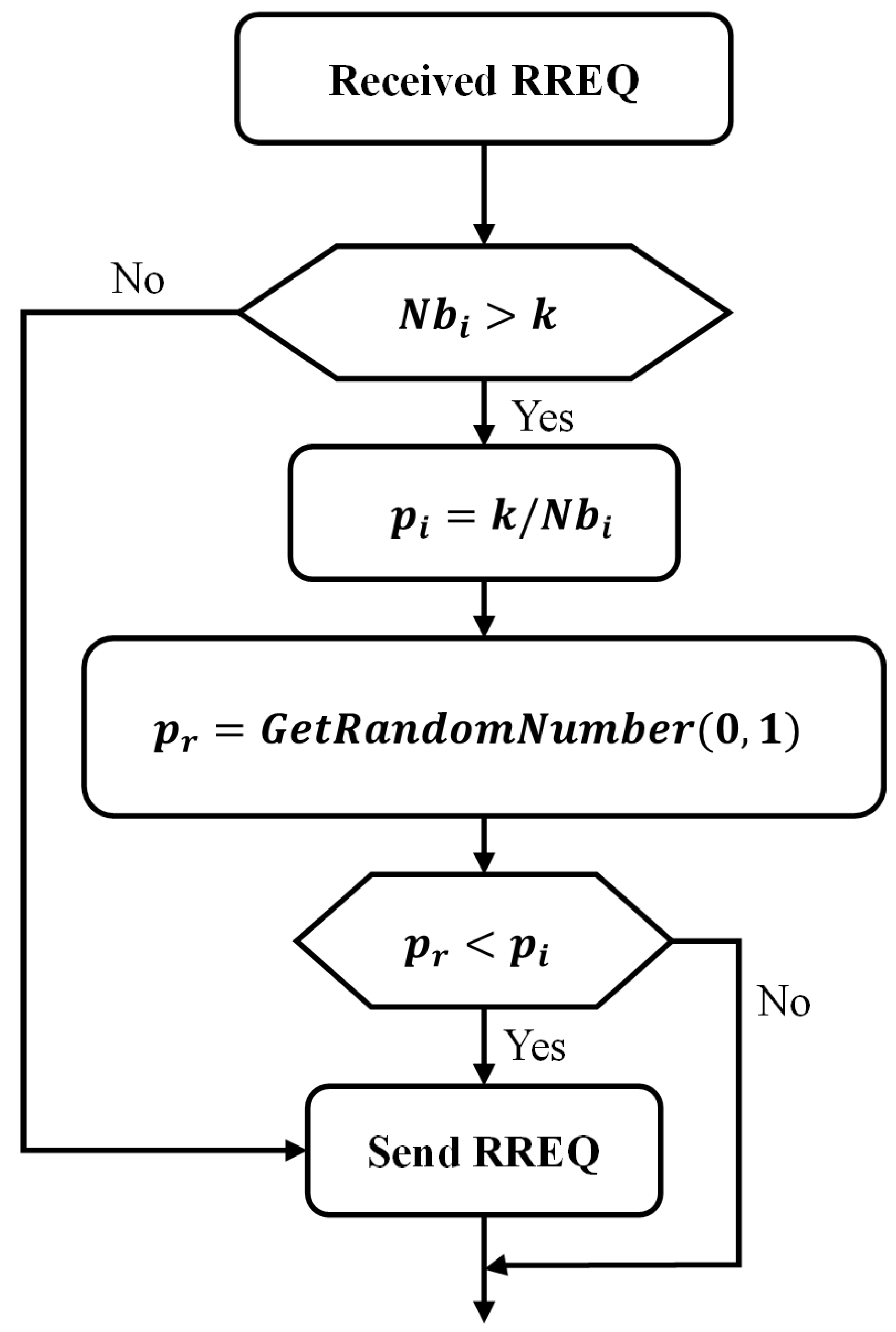
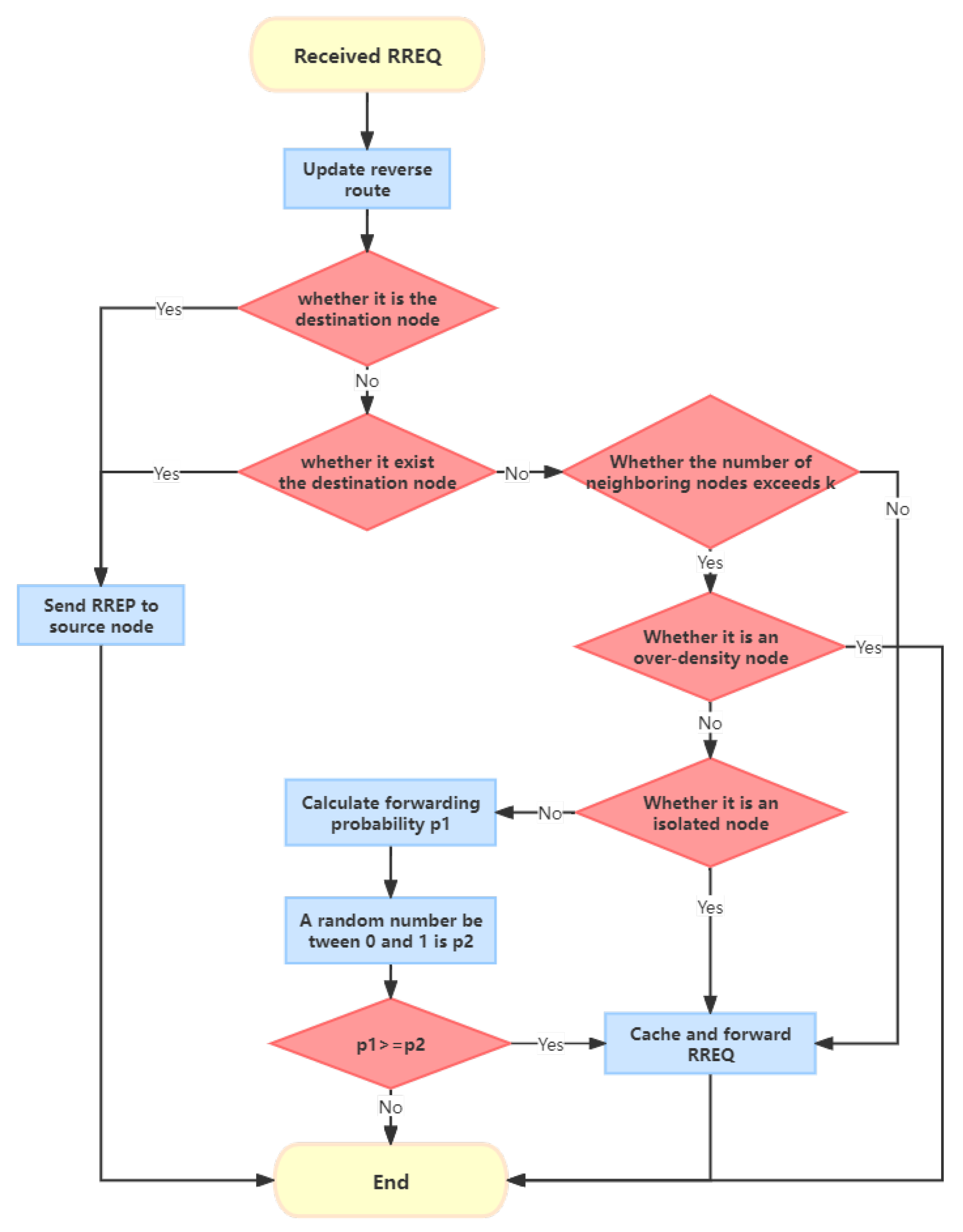
4. Proposed New Routing Method
CND-AODV
5. Simulations and Results
5.1. Simulations
5.1.1. Simulation Environment
5.1.2. Metrics
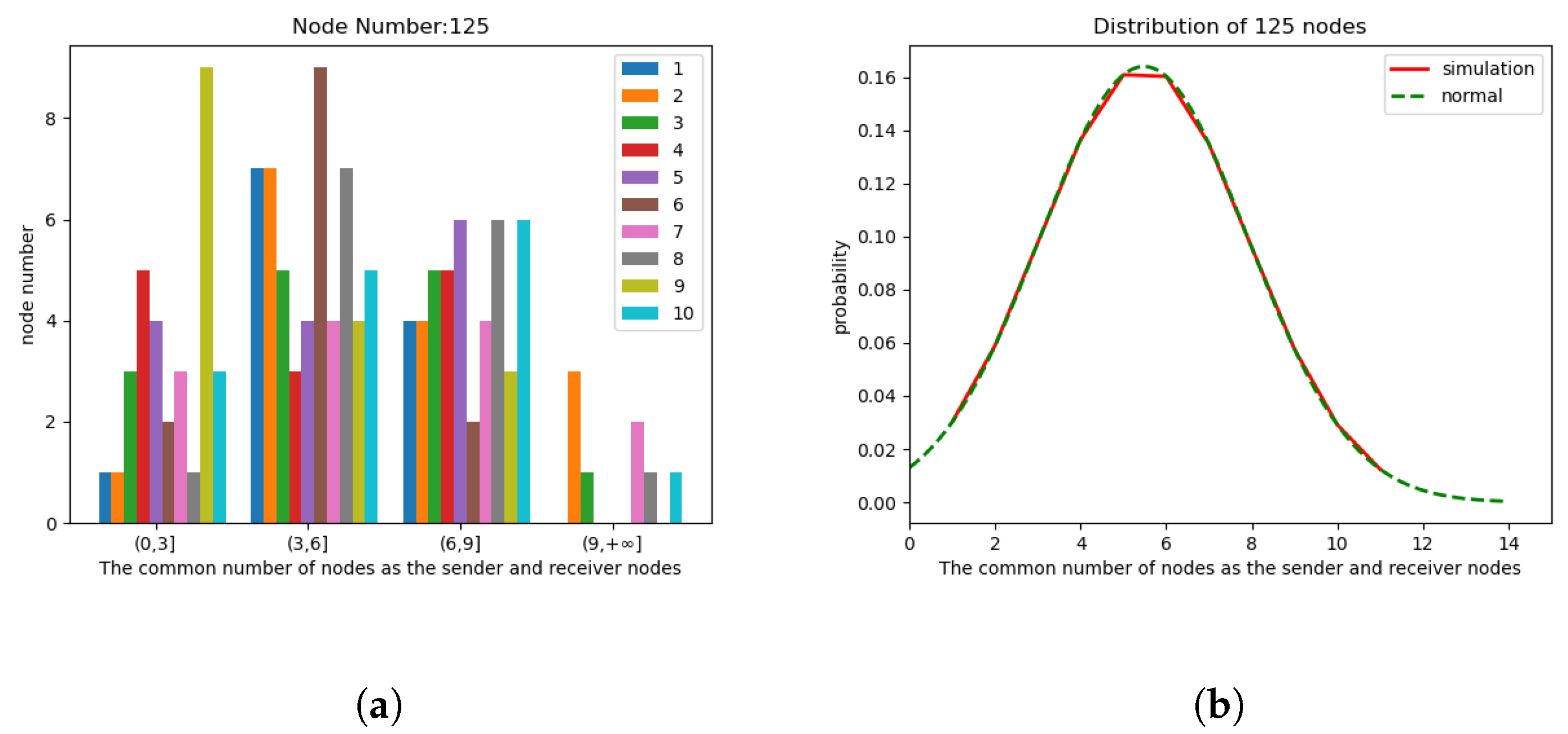
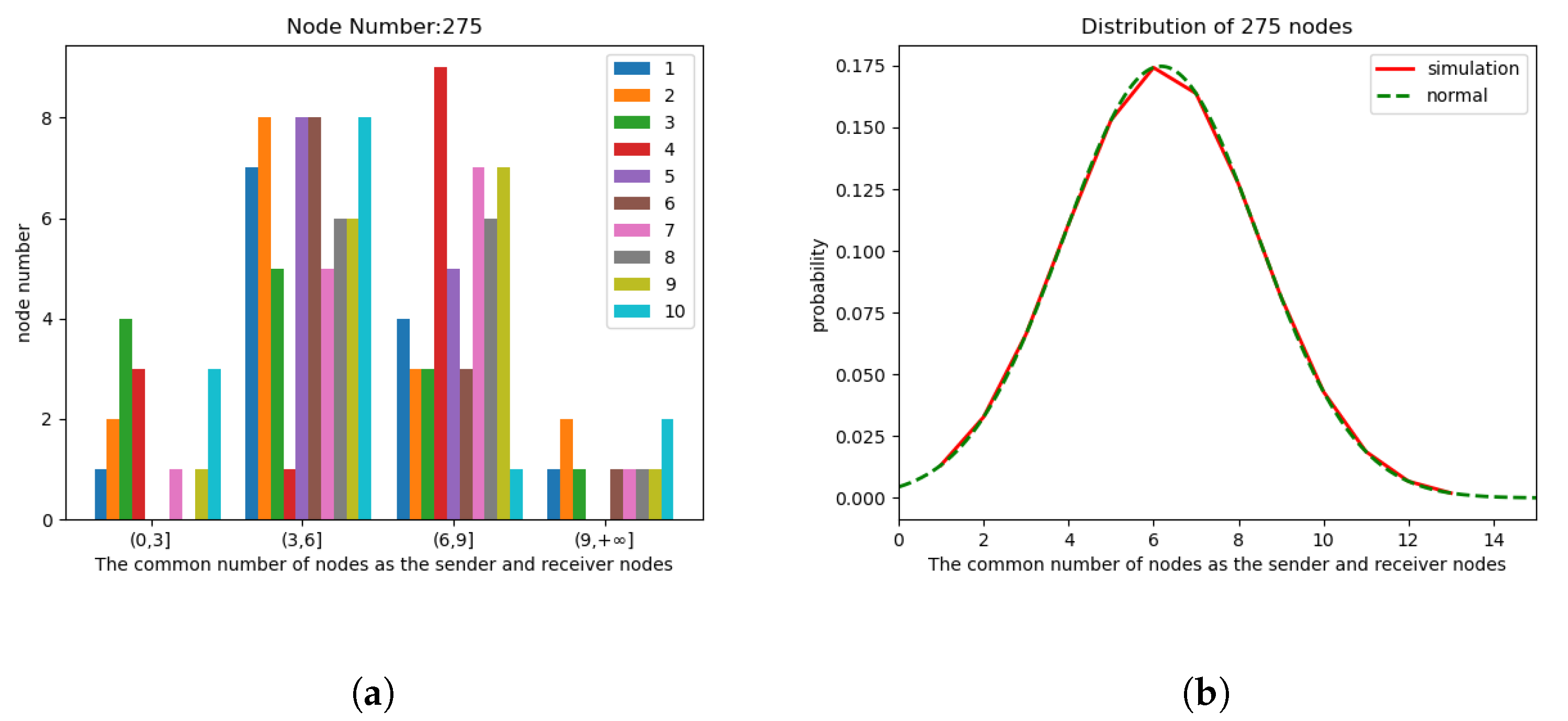
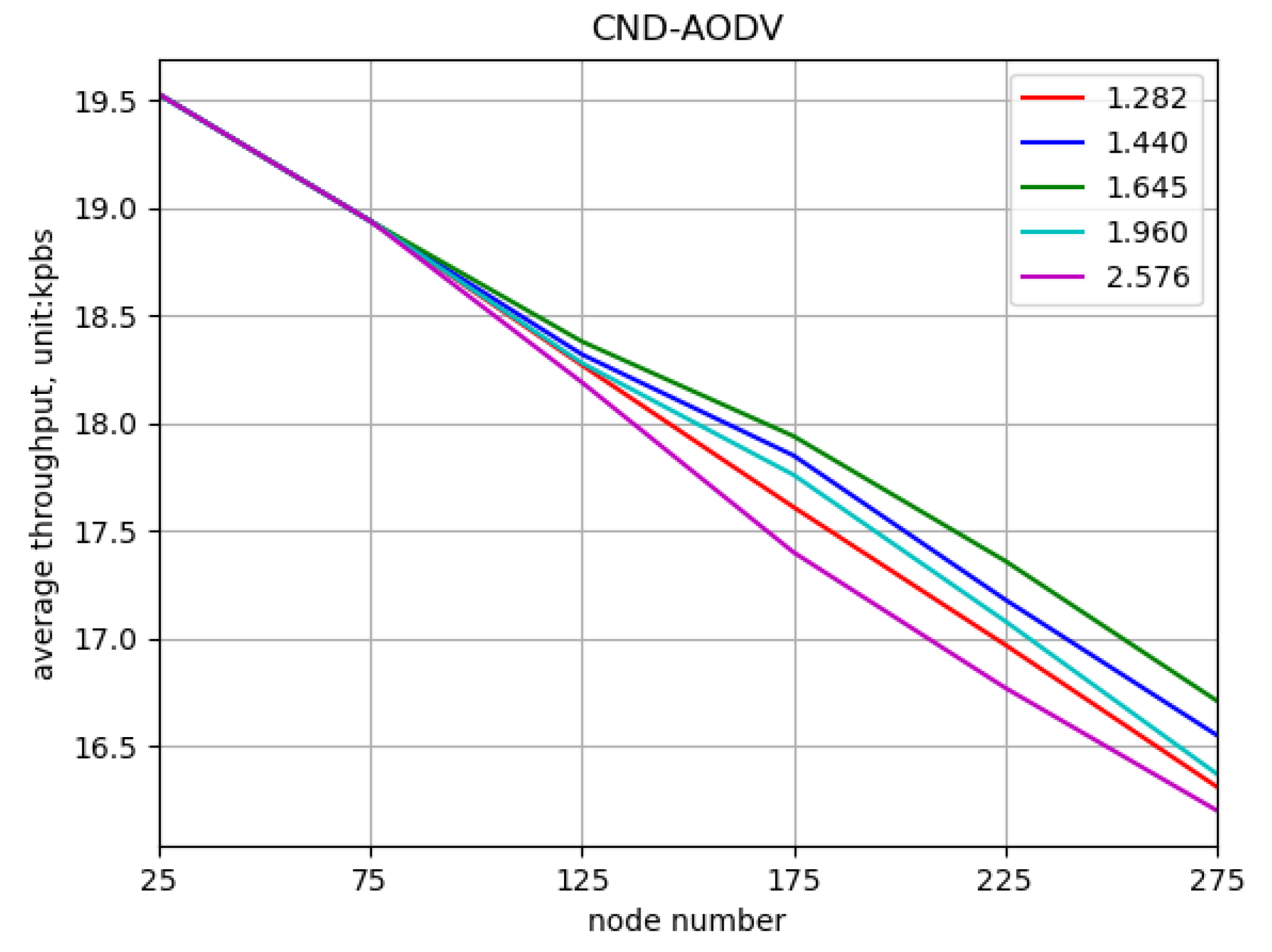
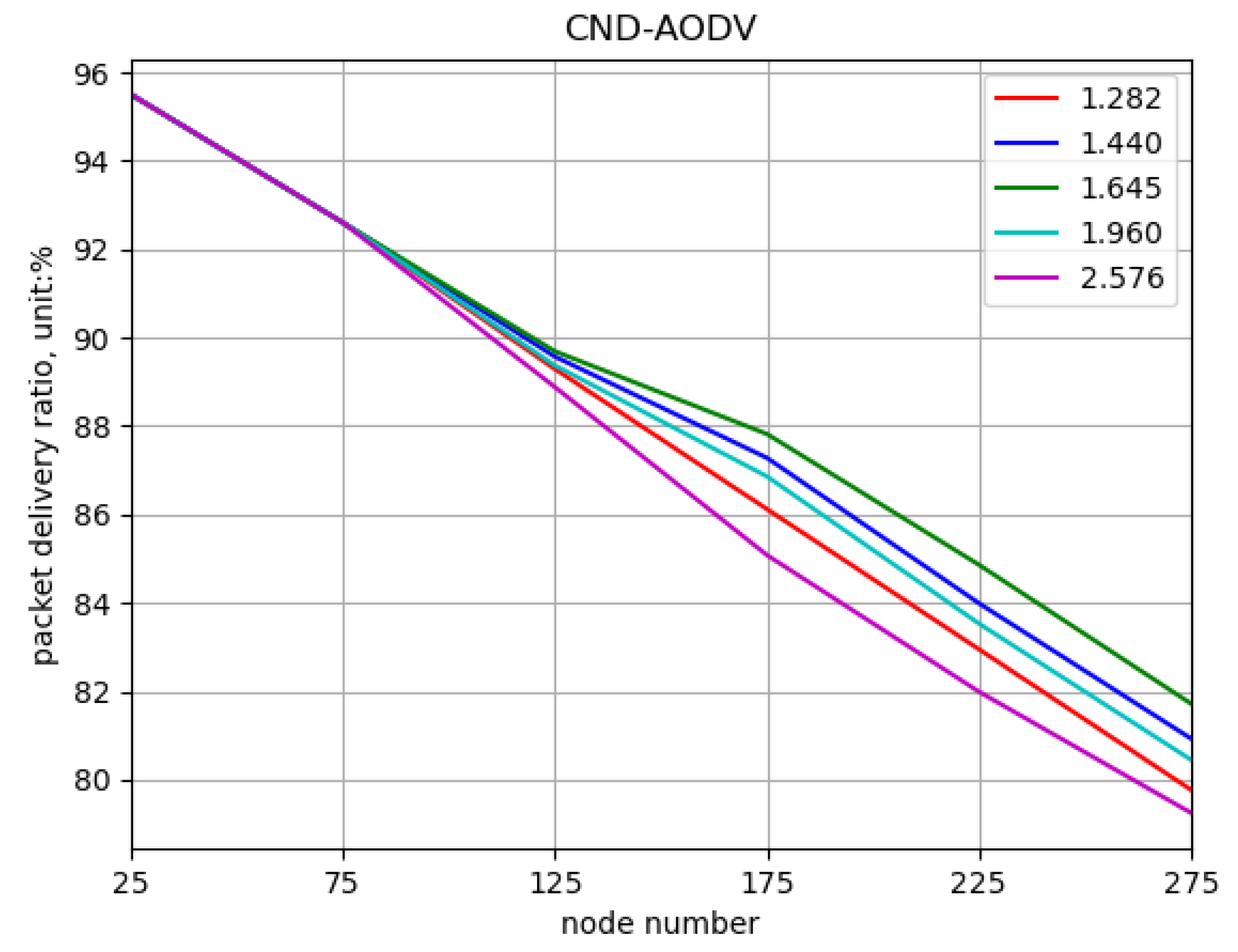
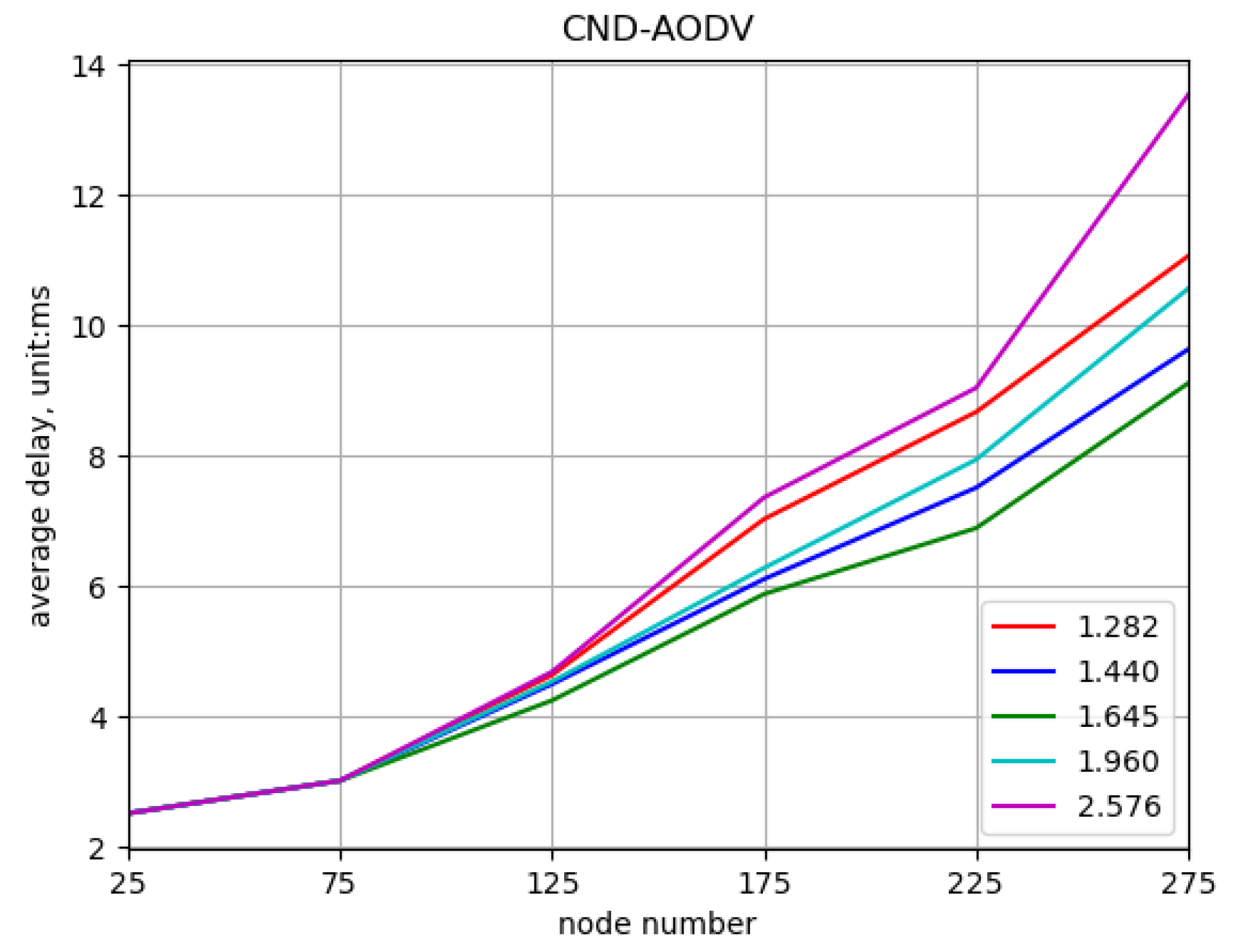
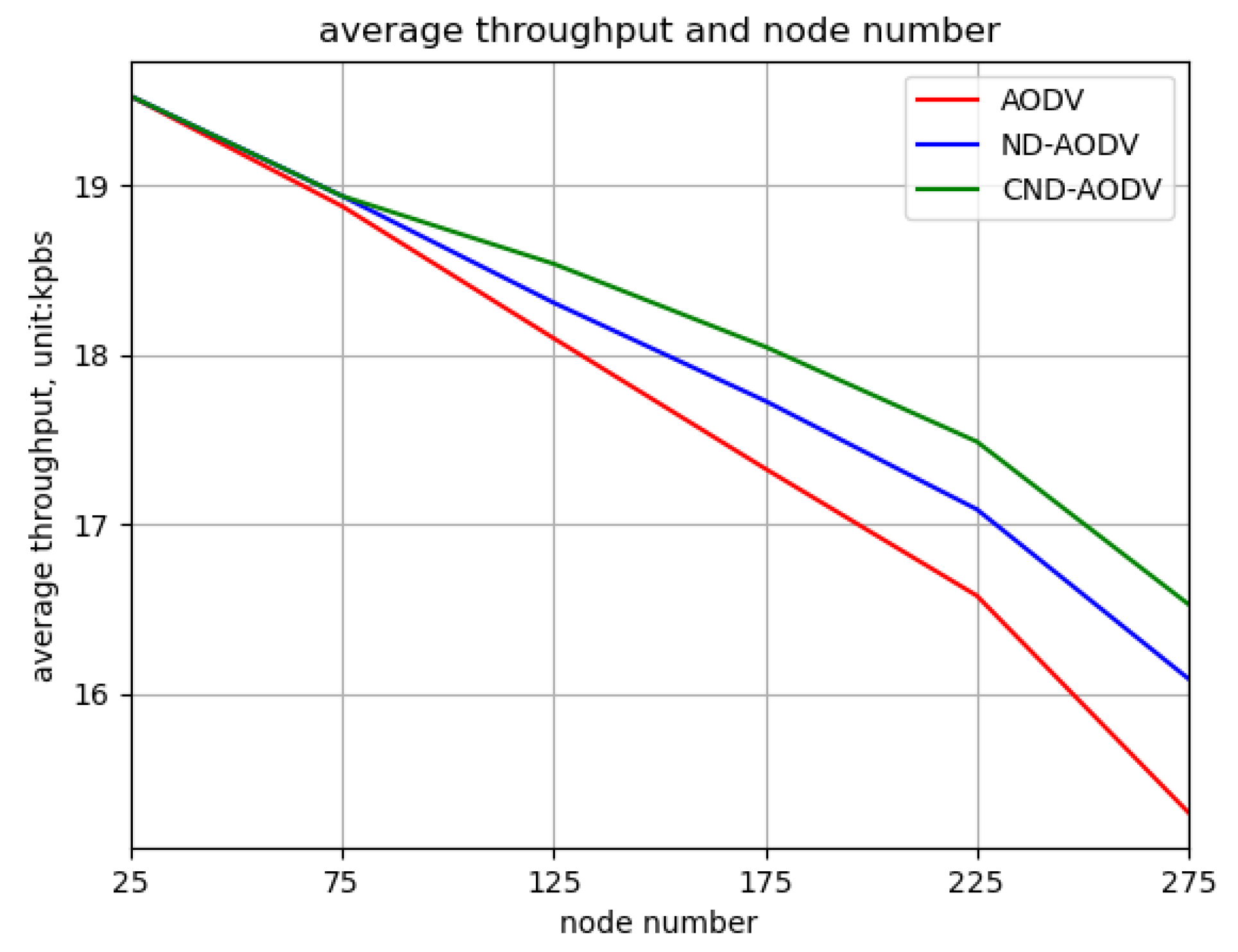
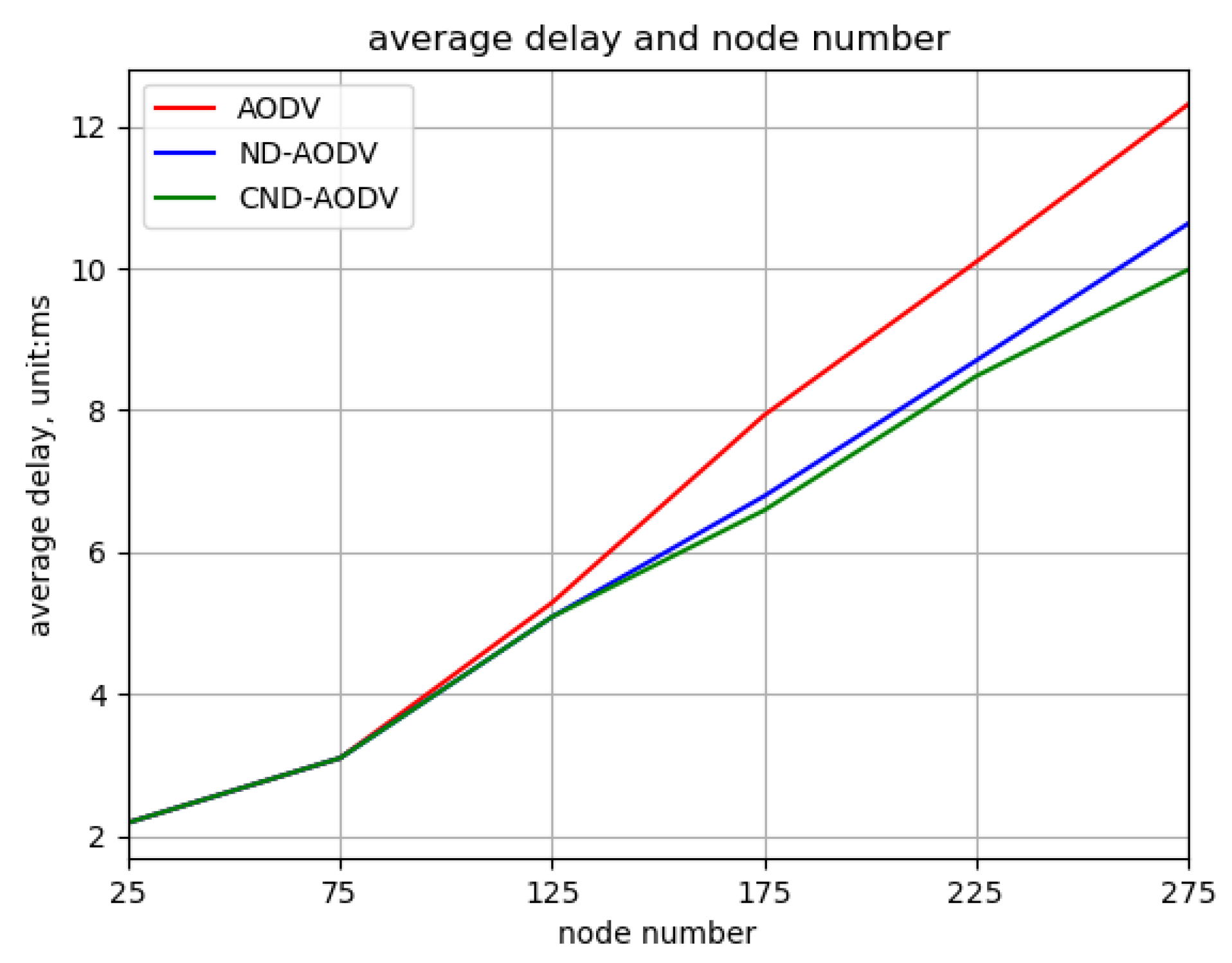
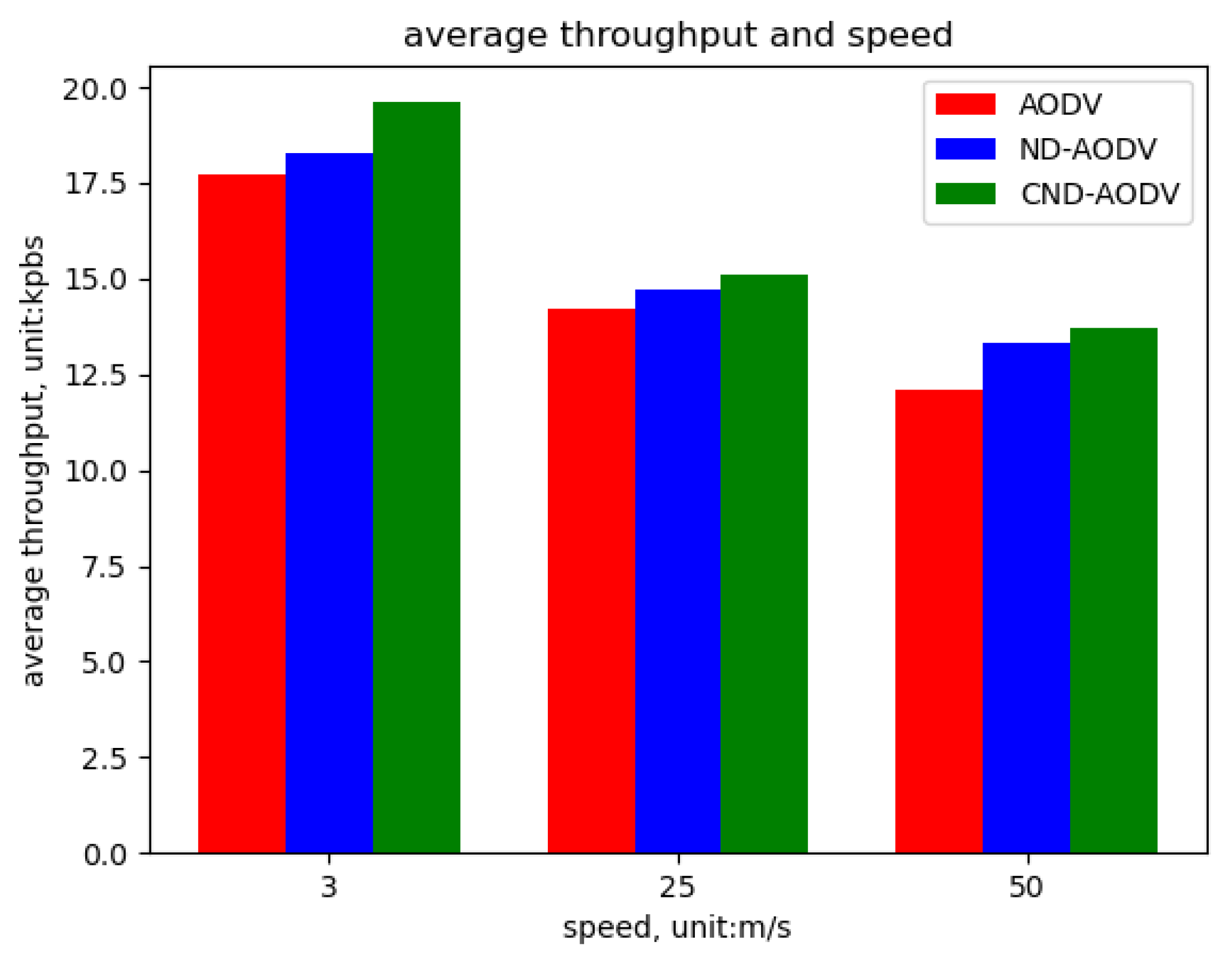
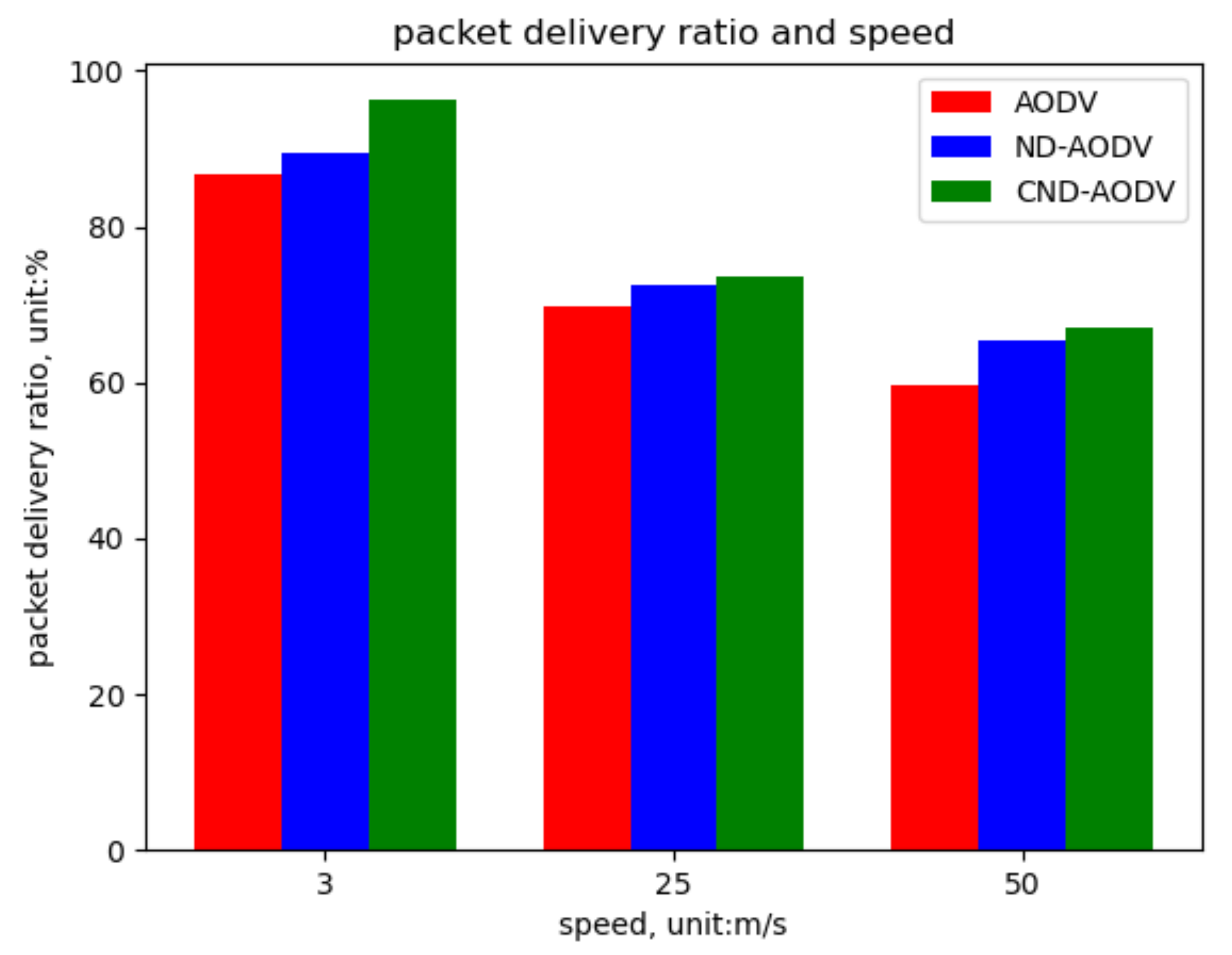
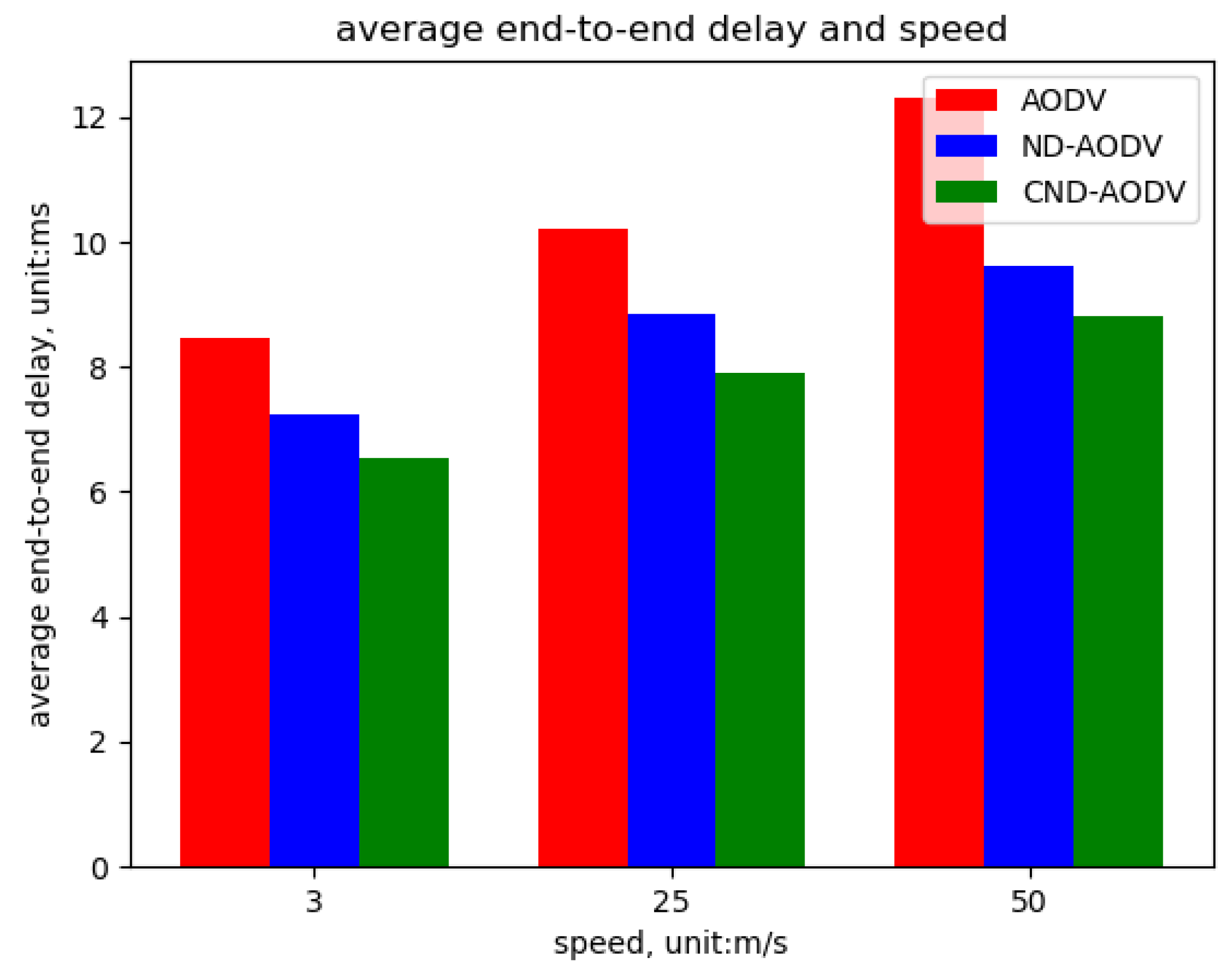
5.2. Result
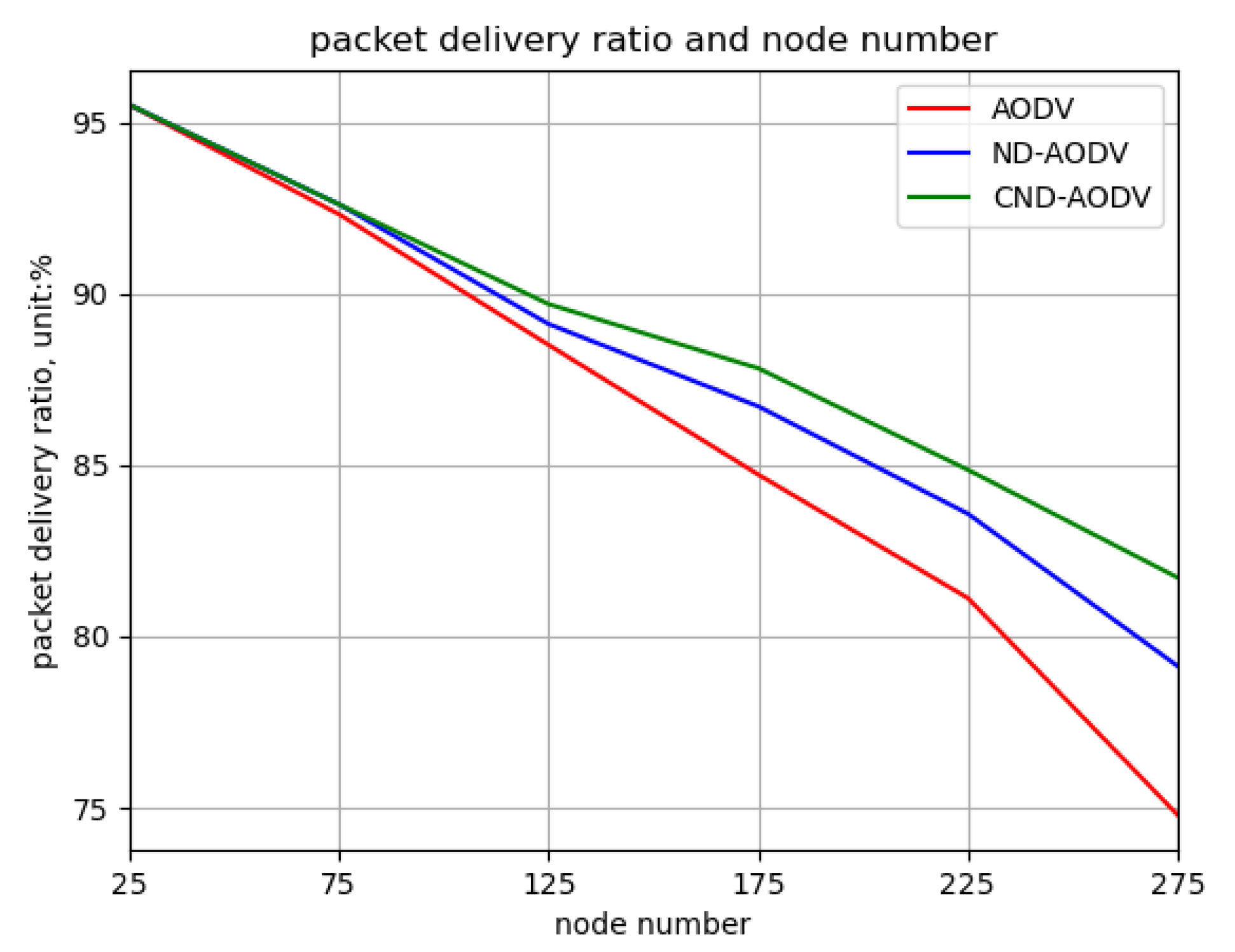
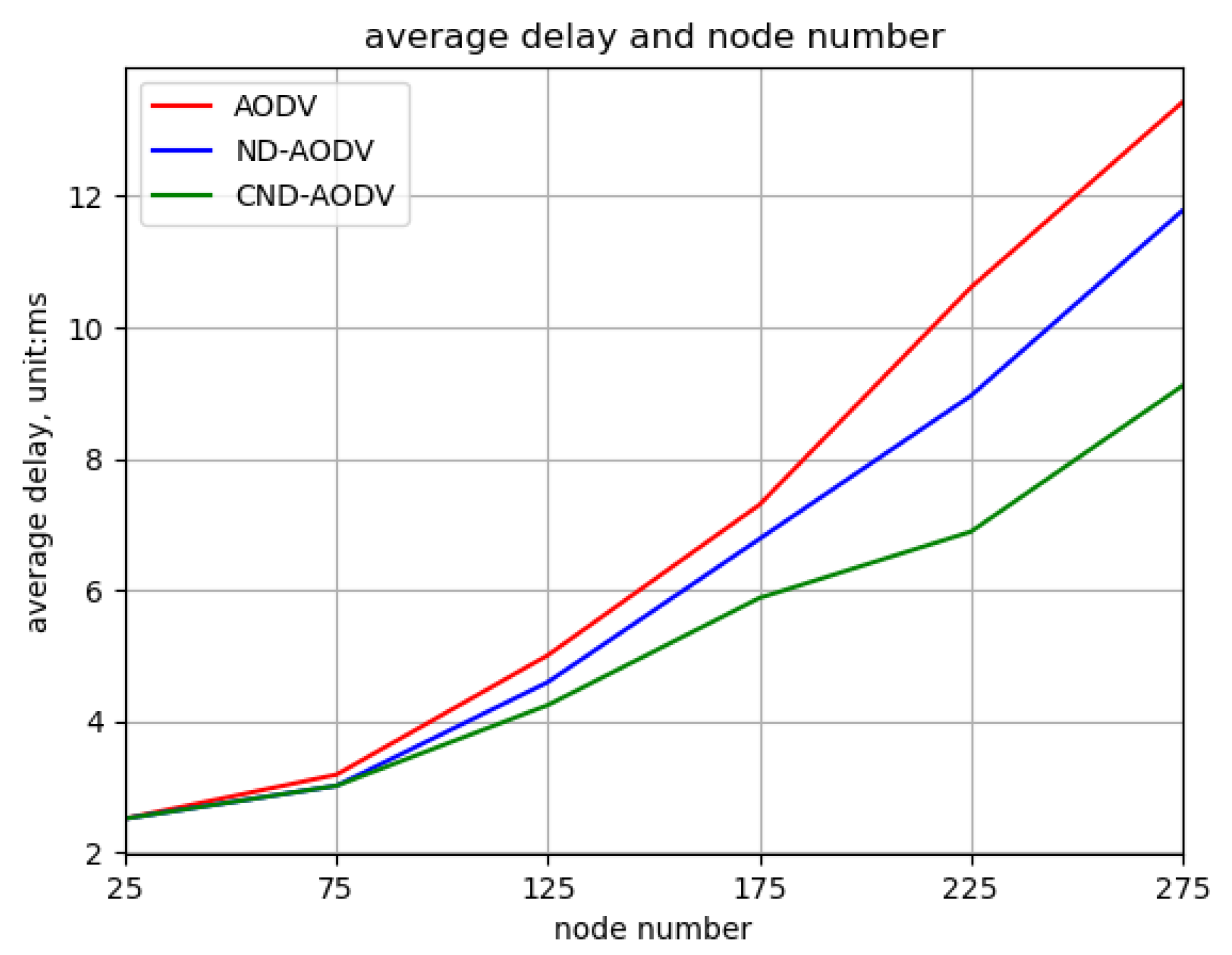
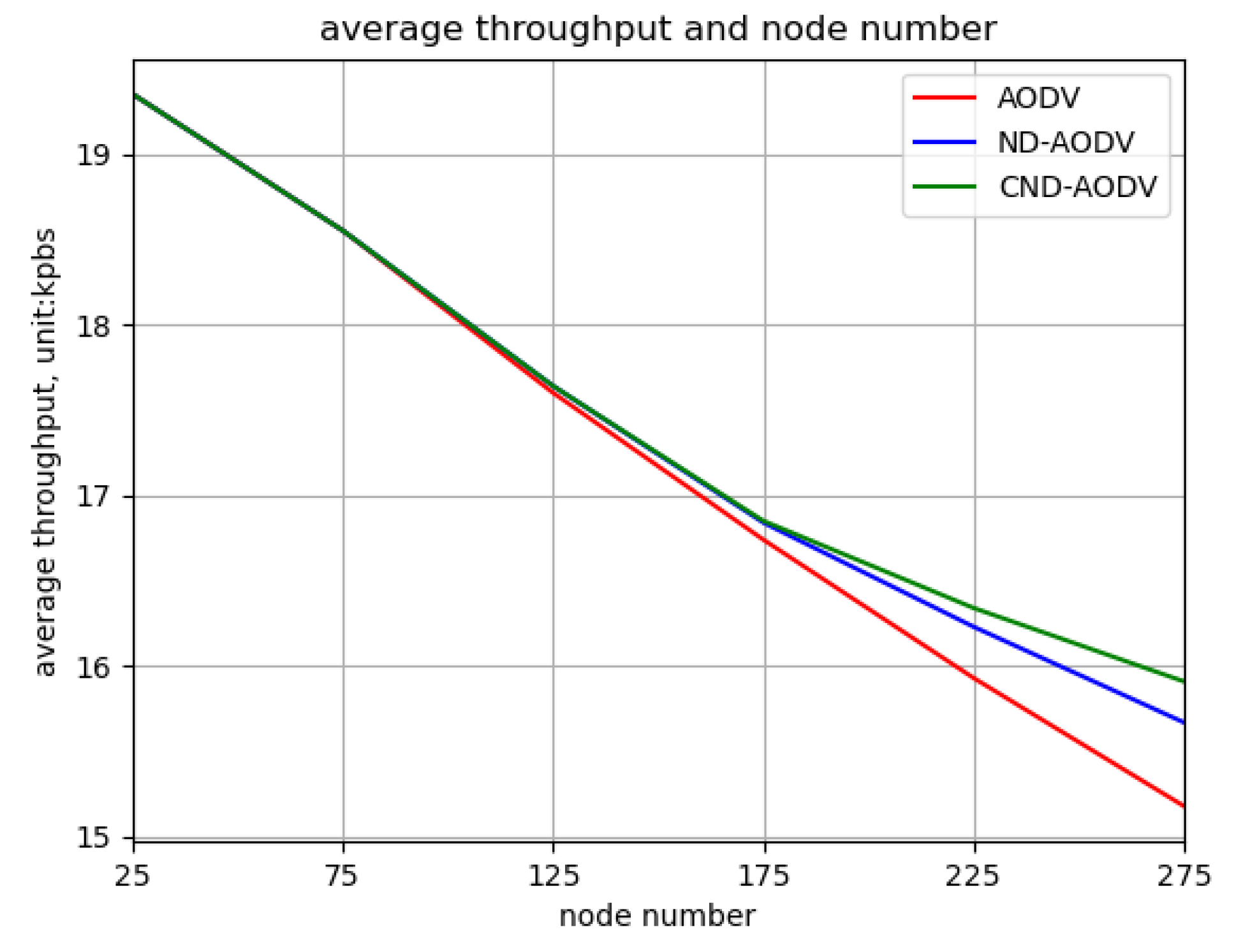
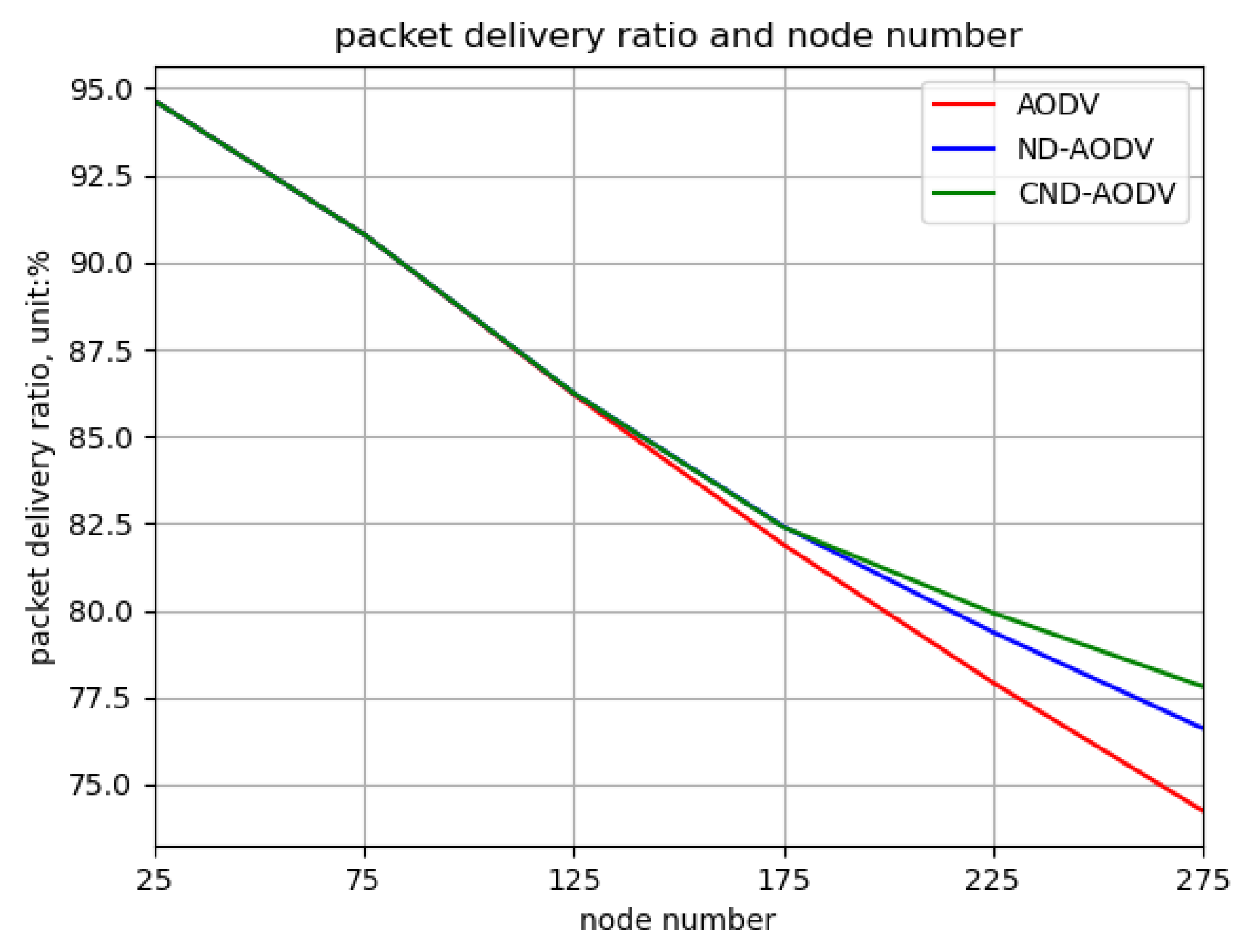
5.2.1. Environment 1
5.2.2. Environment 2
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Devi, M.; Gill, N.S. Mobile ad hoc networks and routing protocols in IoT enabled. J. Eng. Appl. Sci. 2019, 14, 802–811. [Google Scholar]
- Ahmad, I.; Ashraf, U.; Ghafoor, A. A comparative QoS survey of mobile ad hoc network routing protocols. J. Chin. Inst. Eng. 2016, 39, 585–592. [Google Scholar] [CrossRef]
- Wu, J.; Xu, T.; Zhou, T.; Chen, X.; Zhang, N.; Hu, H. Feature-based Spectrum Sensing of NOMA System for Cognitive IoT Networks. IEEE Internet Things J. 2023, 10, 801–814. [Google Scholar] [CrossRef]
- Guaya-Delgado, L.; Pallarès-Segarra, E.; Mezher, A.M.; Forne, J. A novel dynamic reputation-based source routing protocol for mobile ad hoc networks. EURASIP J. Wirel. Commun. Netw. 2019, 2019, 77. [Google Scholar] [CrossRef]
- Mobile Ad Hoc Networks (MANET). IETF Working Group. 2012. Available online: http://datatracker.ietf.org/wg/manet/charter/ (accessed on 1 July 2022).
- Sohail, M.; Wang, L. 3VSR: Three Valued Secure Routing for Vehicular Ad Hoc Networks using Sensing Logic in Adversarial Environment. Sensors 2018, 18, 856. [Google Scholar] [CrossRef]
- Malnar, M.; Jevtic, N. An improvement of AODV protocol for the overhead reduction in scalable dynamic wireless ad hoc networks. Wirel. Netw. 2022, 28, 1039–1051. [Google Scholar] [CrossRef]
- Sharma, D.K.; Patra, A.N.; Kumar, C. P-AODV: A priority based route maintenance process in mobile ad hoc networks. Wirel. Pers. Commun. 2017, 95, 4381–4402. [Google Scholar] [CrossRef]
- Bugarcic, P.D.; Malnar, M.Z.; Jevtic, N.J. Modifications of AODV protocol for VANETs: Performance analysis in NS-3 simulator. In Proceedings of the 2019 27th Telecommunications Forum (TELFOR), Belgrade, Serbia, 26–27 November 2019; pp. 1–4. [Google Scholar] [CrossRef]
- Le, T.; Rabsatt, V.; Gerla, M. Cognitive routing with the ETX metric. In Proceedings of the 2014 13th Annual Mediterranean Ad Hoc Networking Workshop (MED-HOC-NET), Piran, Slovenia, 2–4 June 2014; pp. 188–194. [Google Scholar] [CrossRef]
- Jevtic, N.J.; Malnar, M.Z. The NS-3 simulator implementation of ETX metric within AODV protocol. In Proceedings of the 2017 25th Telecommunication Forum (TELFOR), Budva, Montenegro, 28–30 June 2017; pp. 1–4. [Google Scholar] [CrossRef]
- Jevtic, N.J.; Malnar, M.Z. Novel ETX-based metrics for overhead reduction in dynamic ad hoc networks. IEEE Access 2019, 7, 116490–116504. [Google Scholar] [CrossRef]
- Suo, L.; Liu, L.; Su, Z.; Cai, S.; Han, Z.; Han, H.; Bao, F. A Reliable Low-Latency Multipath Routing Algorithm for Urban Rail Transit Ad Hoc Networks. Sensors 2023, 23, 5576. [Google Scholar] [CrossRef]
- Patel, J.; El-Ocla, H. Energy Efficient Routing Protocol in Sensor Networks Using Genetic Algorithm. Sensors 2021, 21, 7060. [Google Scholar] [CrossRef]
- Sarkar, D.; Choudhury, S.; Majumder, A. Enhanced-Ant-AODV for optimal route selection in mobile ad-hoc network. J. King Saud Univ. Comput. Inf. Sci. 2021, 33, 1186–1201. [Google Scholar] [CrossRef]
- Perkins, C.E.; Bhagwat, P. Highly dynamic destination-sequenced distance-vector routing (DSDV) for mobile computers. ACM SIGCOMM Comput. Commun. Rev. 1994, 24, 234–244. [Google Scholar] [CrossRef]
- Jacquet, P.; Muhlethaler, P.; Clausen, T.; Laouiti, A.; Qayyum, A.; Viennot, L. Optimized link state routing protocol for ad hoc networks. In Proceedings of the IEEE International Multi Topic Conference, Lahore, Pakistan, 30–30 December 2001; pp. 62–68. [Google Scholar] [CrossRef]
- Lee, S.; Belding-Royer, E.M.; Perkins, C.E. Ad hoc on-demand distance-vector routing scalability. SIGMOBILE Mob. Comput. Commun. Rev. 2002, 6, 94–95. [Google Scholar] [CrossRef]
- Saini, T.K.; Sharma, S.C. Recent advancements, review analysis, and extensions of the AODV with the illustration of the applied concept. Hoc Netw. 2020, 103, 102148. [Google Scholar] [CrossRef]
- Johnson, D.B.; Maltz, D.A.; Broch, J. DSR: The dynamic source routing protocol for multi-hop wireless ad hoc networks. Hoc Netw. 2001, 5, 139–172. Available online: https://www.cse.iitb.ac.in/~mythili/teaching/cs653_spring2014/references/dsr.pdf (accessed on 1 August 2022).
- Dimitrova, D.S.; Kaishev, V.K.; Tan, S. Computing the Kolmogorov-Smirnov distribution when the underlying CDF is purely discrete, mixed, or continuous. J. Stat. Softw. 2020, 95, 1–42. [Google Scholar] [CrossRef]
- Kolmogorov-Smirnov Test. Available online: https://en.wikipedia.org/wiki/Kolmogorov%E2%80%93Smirnov_test (accessed on 1 May 2023).
- Colan, S.D. The why and how of Z scores. J. Am. Soc. Echocardiogr. 2013, 26, 38–40. [Google Scholar] [CrossRef] [PubMed]
- NS-3. Available online: http://www.nsnam.org/ (accessed on 1 July 2022).
- Marc Greis, Tutorial on ns2. Available online: www.isi.edu/nsnam/ns/tutoria (accessed on 1 July 2022).
- Ching, T.W.; Aman, A.H.M.; Azamuddin, W.M.H.; Attarbashi, Z.S. Performance evaluation of AODV routing protocol in MANET using NS-3 simulator. In Proceedings of the 2021 3rd International Cyber Resilience Conference (CRC), Online, 29–31 January 2021; pp. 1–4. [Google Scholar] [CrossRef]
- Kurniawan, A.; Kristalina, P.; Hadi, M.Z.S. Performance analysis of routing protocols AODV, OLSR and DSDV on MANET using NS3. In Proceedings of the 2020 International Electronics Symposium (IES), Surabaya, Indonesia, 29–30 September 2020; pp. 199–206. [Google Scholar] [CrossRef]




| Number of neighbor nodes of node i | |
| Probability of the forwarding RREQ of node i | |
| Randomly generated probability, used to compare with | |
| k | Constant threshold, for congestion detection |
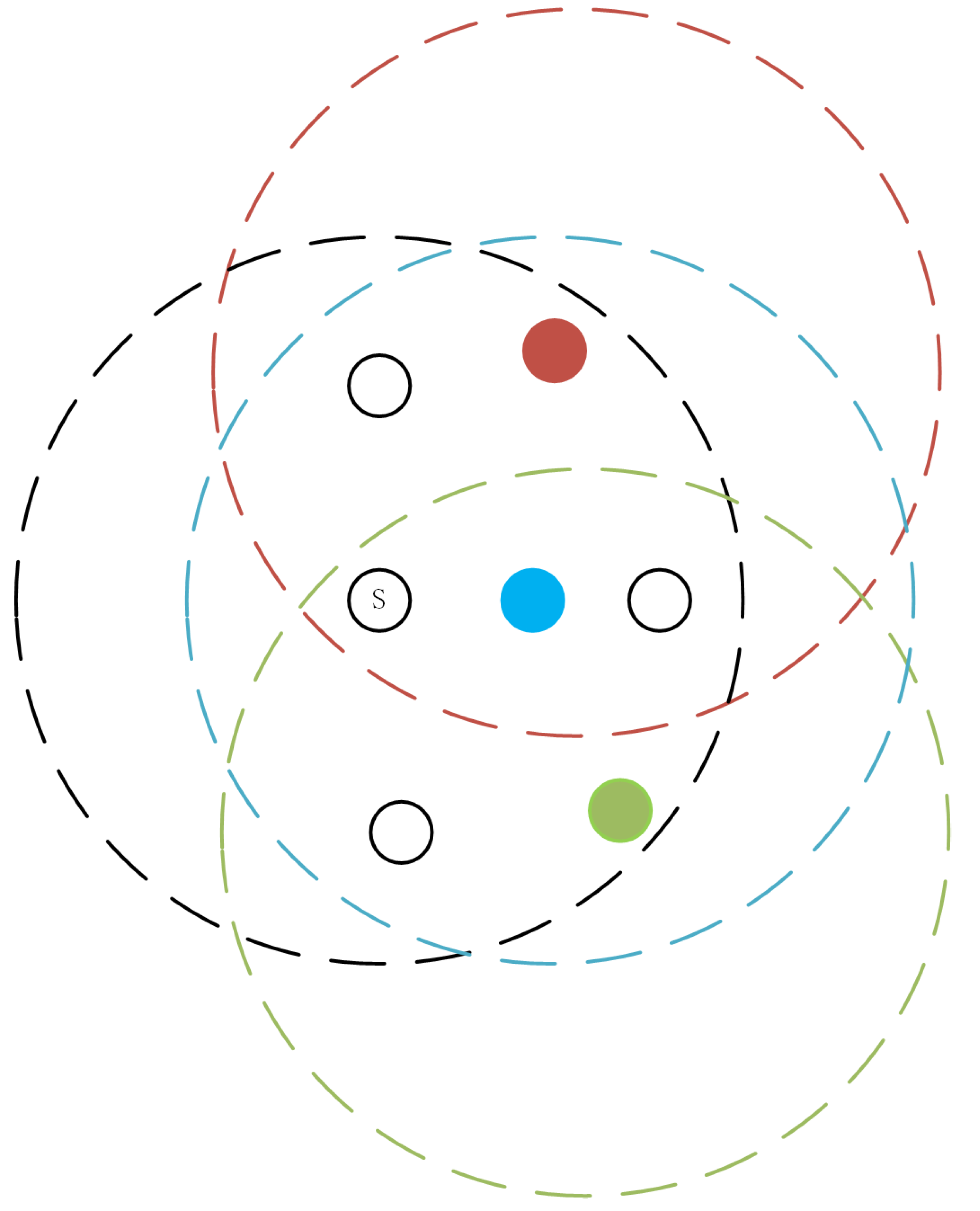
| Number of common neighbor nodes between node j and node i | |
| Mean of the number of common neighbor nodes between sender j and its neighbor nodes | |
| The set of neighbor nodes of node i | |
| Theoretical cumulative probability distribution function | |
| Empirical or observed cumulative probability distribution function | |
| D | Statistical measure for the maximum difference between two different cumulative distribution functions |
| The threshold for the maximum difference statistic of D | |
| z | The z-score, utilized as a statistical measure to assess the relative position or deviation of a data point within a dataset |
| X | The value of the data point, used to calculate z |
| Mean of the dataset, used to calculate z | |
| Standard deviation of the dataset, used to calculate z | |
| Standard deviation of the number of common neighbor nodes between sender j and its neighbor nodes |
| Threshold z | Confidence Interval |
|---|---|
| Parameter | Value |
|---|---|
| Simulation Platform | NS3.35 |
| Simulation Time | 110 s |
| Simulation Protocol | AODV, ND-AODV, and CND-AODV |
| Number of Nodes | 25, 75, 125, 175, 200, 225, 275 |
| Active Nodes | 10 |
| MAC Protocol | IEEE 802.11p |
| Simulation Area | m2 |
| Propagation Loss Model | TwoRayGroundPropagationLossModel |
| Speed of nodes | 3, 5, 25, and 50 m/s |
| Packet Size | 512b |
| Mobility Model | RandomWaypointMobilityModel |
| Transport Layer Protocol | UDP |
| Transmission Model | CBR (constant bit rate) |
| Transmission Rate | 2 Mbps |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, X.; Bian, X.; Li, M. Routing Selection Algorithm for Mobile Ad Hoc Networks Based on Neighbor Node Density. Sensors 2024, 24, 325. https://doi.org/10.3390/s24020325
Li X, Bian X, Li M. Routing Selection Algorithm for Mobile Ad Hoc Networks Based on Neighbor Node Density. Sensors. 2024; 24(2):325. https://doi.org/10.3390/s24020325
Chicago/Turabian StyleLi, Xiaolin, Xin Bian, and Mingqi Li. 2024. "Routing Selection Algorithm for Mobile Ad Hoc Networks Based on Neighbor Node Density" Sensors 24, no. 2: 325. https://doi.org/10.3390/s24020325
APA StyleLi, X., Bian, X., & Li, M. (2024). Routing Selection Algorithm for Mobile Ad Hoc Networks Based on Neighbor Node Density. Sensors, 24(2), 325. https://doi.org/10.3390/s24020325






