Abstract
This paper studies extremely large-scale multiple-input multiple-output (XL-MIMO)-empowered integrated sensing and secure communication systems, where both the radar targets and the communication user are located within the near-field region of the transmitter. The radar targets, being untrusted entities, have the potential to intercept the confidential messages intended for the communication user. In this context, we investigate the near-field beam-focusing design, aiming to maximize the achievable secrecy rate for the communication user while satisfying the transmit beampattern gain requirements for the radar targets. We address the corresponding globally optimal non-convex optimization problem by employing a semidefinite relaxation-based two-stage procedure. Additionally, we provide a sub-optimal solution to reduce complexity. Numerical results demonstrate that beam focusing enables the attainment of a positive secrecy rate, even when the radar targets and communication user align along the same angle direction.
1. Introduction
Integrated sensing and communication (ISAC) has emerged as a significant advancement in upcoming wireless systems [1,2]. These systems enable the dual use of hardware platforms and limited spectrum/power resources for both communication and sensing tasks [3]. One of the most promising areas of ISAC application is in vehicular ad hoc networks (VANETs), which are at the forefront of the evolution of connected and autonomous vehicles [4]. In VANETs, vehicles communicate with each other and possibly with infrastructure components, such as traffic signals or roadside units. These communications can be used for sharing traffic conditions, alerting nearby vehicles of emergency braking, or even for cooperative driving in the future [5]. With the increasing complexity and density of modern traffic systems, vehicles also need advanced sensing capabilities for safety and navigation purposes. By integrating ISAC into VANETs, vehicles can dynamically optimize resources, streamline hardware, and enhance safety through real-time communication of sensed data, ensuring efficient and adaptive network performance [6,7].
Currently, ISAC systems allow the reuse of information-bearing signals for radar sensing [2]. While this dual operation improves spectrum efficiency and reduces the cost of systems, it introduces potential risks of information leakage. This becomes particularly concerning when sensing targets, being untrusted entities, might intercept these confidential signals [8]. To address this issue, physical layer security techniques have been integrated into ISAC systems to ensure communication security [9,10,11]. In [9], the authors examine an ISAC scenario consisting of one communication user and one untrusted target, potentially an eavesdropper, and they design the transmit covariance matrices to maximize the achievable secrecy rate. In [10], the authors jointly optimize the transmit information and sensing beamforming, aiming to minimize the beampattern matching error for sensing while ensuring the minimum secrecy rate requirement. Meanwhile, in [11], optimization-based beamforming designs are presented, focusing on the security of information transmissions within ISAC systems.
It should be noted that all the aforementioned papers on secrecy ISAC address the far-field scenario, where both radar targets and communication users reside within the far-field region of the transmitter. Motivated by the great success of multiple-input multiple-output (MIMO) technology in 4G and 5G [12,13], in future 6G networks, extremely large-scale (XL)-MIMO is envisioned to be utilized. XL-MIMO, deploying hundreds, or even thousands, of antenna elements at base stations or reflecting elements at reconfigurable intelligent surfaces, can significantly improve performance, such as spectral efficiency [14]. The envisioned deployment of XL-MIMO in future 6G networks will likely lead to wireless operations in the radiating near-field (Fresnel) region, in contrast to conventional wireless systems, which typically operate in the far-field region [15]. Thus, there will be a shift in 6G: radar targets and communication users may predominantly operate within the near-field region of the transmitter [16]. While far-field propagation assumes a planar wavefront, the near-field region is characterized by a spherical wavefront. This unique near-field waveform propagation characteristic paves the way for the beam focusing technique, as detailed in [17,18], offering a notable boost in secrecy communication performance by mitigating information leakage. Nevertheless, this promising avenue has garnered limited attention in the current secrecy ISAC literature.
Motivated by the preceding discussion, in this paper, we explore the near-field beam-focusing design for secrecy ISAC systems. Here, one transmitter equipped with an extremely large-scale antenna array senses multiple radar targets and communicates with a single communication user concurrently. Both the radar targets and the communication users are situated within the near-field region of the transmitter. These radar targets, being untrusted, might eavesdrop on the confidential messages intended for the communication user. In this context, we investigate the near-field beam-focusing design to characterize the trade-off between radar sensing and secure communication. The main contributions of this paper are summarized below:
- To the best of the authors’ knowledge, this work represents the first study of the near-field secrecy ISAC scenario, with a focus on revealing the benefits of near-field operation for secure communication. To achieve this, we formulate a near-field secrecy beam-focusing problem to maximize the secrecy rate for the communication user while meeting the transmit beampattern gain requirement for each radar target. The considered problem is new and has not been previously studied in either the conventional far-field or near-field contexts.
- While the formulated problem is non-convex, we achieve a global optimum solution by employing a two-stage procedure based on semidefinite relaxation (SDR). Additionally, we propose a novel low-complexity sub-optimal beam-focusing design tailored for this new problem.
- Finally, we provide numerical results to validate the effectiveness of our proposed secrecy beam-focusing designs. Notably, our proposed beam-focusing designs enable a positive secrecy rate even when the radar targets and communication user align along the same angle direction, which is unattainable with far-field beam steering. Additionally, we illustrate the performance trade-off between radar sensing and secrecy communication in near-field ISAC systems.
The remainder of this paper is organized as follows: Section 2 introduces the system model and problem formulation for near-field secrecy ISAC systems. Section 3 presents the development of an optimal solution and a sub-optimal, lower-complexity alternative. In Section 4, we provide extensive simulation results to validate our designs and illustrate the trade-offs involved. Finally, Section 5 concludes the paper with a summary of our findings and potential future research directions.
Let boldface lower-case and upper-case letters denote vectors and matrices, respectively. Use for the norm, for the transpose, for the Hermitian transpose, for the null space of a matrix, and to represent complex numbers.
2. System Model and Problem Formulation
Consider a near-field secrecy ISAC system, as illustrated in Figure 1. Here, one transmitter equipped with an extremely large-scale uniform linear array (ULA) of N antenna elements serves a single-antenna communication user and simultaneously senses L potential targets. Both the radar targets and the communication user are situated within the near-field region of the transmitter. These radar targets, being untrusted, might eavesdrop on the confidential messages intended for the communication user. With an inter-element spacing of d, the total antenna array aperture is . The boundary separating the near-field and far-field regions, known as either the Fraunhofer or Rayleigh distance, is defined as [19]. As the antenna count N increases, can extend over several hundred meters, encompassing numerous communication users and sensing targets. Given these considerations, research on near-field ISAC systems becomes increasingly crucial.
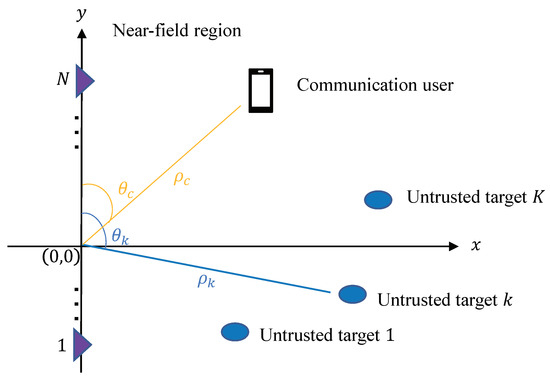
Figure 1.
Illustration of near-field secrecy ISAC systems, consisting of one extremely large-scale antenna array that senses potential radar targets and serves communication users simultaneously.
2.1. Near-Field Channel Model
The ULA of the transmitter is positioned along the y-axis. The Cartesian coordinate of the nth antenna element is represented as , with . The communication user is located at , with and denoting the distance and angle between the communication user and the array center, respectively. Let denote the distance between the nth antenna element of the transmitter and the communication user. Denote c and as the light speed and the carrier, respectively. Then, the near-field channel between the transmitter and the communication user is given by
where , and denotes the steering vector, given by
Let and denote the distance and angle between the lth untrusted radar target and the array center, respectively. The corresponding near-field channel between the transmitter and the lth untrusted radar target is given by
where , and the steering vector , given by
2.2. Signal Model
The transmitter uses beam focusing to transmit a combined signal for both communication and radar-sensing tasks. Represented by , the baseband signal at the transmitter is given by
where is the beam-focusing vector for the communication user, with s being the information-bearing signal. On the other hand, is the dedicated radar signal with zero mean, and its covariance matrix is denoted as .
According to (1) and (3), the received signal at the communication user can be written as , where denotes the additive noise at the communication user, with zero mean and variance of . Thus, the signal-to-interference-plus-noise ratio (SINR) at the communication user is expressed as
In the near-field ISAC scenarios, both communication and radar signals can contribute to radar-sensing tasks. Consequently, the transmit beampattern gain at the lth radar target is defined as [20]
The radar targets are untrusted nodes, which potentially intercept the confidential messages intended for the communication user. The SINR at the lth target is given by
2.3. Problem Formulation
We are interested in characterizing the performance trade-off between radar sensing and secrecy communication. Specifically, we aim to maximize the secrecy rate of the communication user while satisfying the transmit beampattern gains for radar targets, by jointly optimizing the beam-focusing vector and the radar covariance matrix . Mathematically, the problem of interest is formulated as
where denotes the transmit beampattern gain threshold for the lth radar target, and is the transmit power at the transmitter.
3. Proposed Solution
In this section, we first propose a two-stage optimization approach to solve the non-convex problem (8) globally optimally in Section 3.1. Then, in Section 3.2, we develop a low-complexity sub-optimal solution.
3.1. Optimal Solution
In this subsection, we present an SDR-based two-stage procedure to achieve the optimal solution for (8). This is accomplished by decomposing (8) into two sub-problems. First, by introducing a variable , we reformulate (8) as
Similar to [21], it can be proven that there always exists a for which problem (9) shares the same optimal solution as problem (8). To be specific, let denote the optimal value of (9) for a given . Consequently, the optimal value of (8) is equivalent to the following problem:
Based on the above discussion, we conclude that problem (8) can be solved through a two-step process. Firstly, we solve (9) to obtain the optimal value for any given . Secondly, we solve (10) to find the optimal by conducting a one-dimensional search over the parameter space. Consequently, we next focus on solving (9).
Problem (9) is still non-convex. Next, we apply the SDR technique to solve (9) globally optimally. To this end, by defining and ignoring the non-convex rank-one constraint on , we recast (9) as
where , , and .
Problem (11) is non-convex due to the non-concave nature of its objective function. Nevertheless, we can effectively address this by employing the Charnes–Cooper transformation [22], which allows us to equivalently reformulate (11) as
Problem (12) is convex, and thus, it can be solved directly using existing solvers such as CVX [23].
Let represent the optimal solution to (12). It can be readily demonstrated that and are the optimal solution to (11). If , the relaxation of the rank-one constraint in (11) does not impact its optimality. We now present a theorem affirming that we can always construct an optimal solution to (12) with a rank-one matrix .
Theorem 1.
Proof of Theorem 1.
The Lagrangian of problem (12) is given by
where is a matrix Lagrange multiplier associated with the constraint ; , , and are, respectively, defined as
where , , , and represent the Lagrange multipliers corresponding to the first through fourth constraints in (12), respectively.
Given (13), the relevant Karush–Kuhn–Tucker (KKT) conditions for the proof are formulated as
where , denote the optimal Lagrange multipliers for the dual problem of (12), and the resulting and are and . Here, (17b) is obtained from the complementary slackness condition.
Define . Then, we have
Based on (18b), the columns of must lie in the null space of when . Define . If , we can conclude that . In this case, we have when .
We next discuss the case of . In this case, let denote the orthonormal basis of the null space of , i.e., . Let , denote the mth column of . For each , it follows
From (20), we conclude that . Thus, we have
If , we have . This means can be expressed as . However, since , in this case, the achievable secrecy rate is equal to zero. Thus, we obtain . As a result, the optimal can be expressed as
where and . is an extra dimension of orthonormal basis, which lies in the null space of and is orthogonal to the span of , i.e., and .
3.2. ZF-Based Sub-Optimal Solution
In this subsection, we propose a sub-optimal solution based on zero-forcing (ZF) for problem (8), which exhibits a significantly lower computational complexity compared to the optimal solution. This sub-optimal approach involves aligning the information beam with the null space of the radar target’s channel to prevent any information leakage to potential eavesdroppers, as expressed by . Simultaneously, the radar signal is constrained to lie within the null space of the communication user, specified as , ensuring that it does not interfere with the communication user.
Define . Denote its singular value decomposition as , where and are unitary matrices, is a diagonal matrix, and are the first L and the last right singular vectors of . In order to guarantee , the ZF-based has the following form:
where denotes the transmit power of the information beam, and is an arbitrary complex vector of unit norm. To maximize the secrecy rate, should match the equivalent channel , and thus .
According to (26), the achievable secrecy rate becomes
To maximize the secrecy rate in (27), we need to minimize the power consumption required to ensure the radar-sensing task. Consequently, we can obtain the optimal radar-sensing covariance matrix by solving the following problem:
4. Simulation Results and Discussion
In this section, we showcase numerical results to validate our secure beam-focusing design in the context of near-field ISAC systems. Our system setup involves a transmitter with a ULA of antennas, operating at GHz. The Rayleigh distance for this setup is m. We position the communication user at meters on the x-axis. All receivers are assumed to have an identical noise power of dBm.
We first show the capabilities of beam focusing for ensuring secure communication. For our demonstration, we consider that a single radar target, which can potentially act as an eavesdropper, is positioned at meters. This location coincides with the angular direction of the communication user. Figure 2a,b show the normalized signal power of the communication signal and radar signal at each point of the near-field -plane, respectively, given the transmit power dB and the transmit beampattern gain threshold . Both the communication signal beam and radar signal covariance matrix are obtained by solving problem (8) based on the given user locations and the predefined threshold values. From Figure 2a, we observe that most of the energy from the communication beam is concentrated around the communication user. This results in minimal information leakage to the radar target. In contrast, Figure 2b shows that the energy from the radar covariance matrix predominantly focuses on the radar target, ensuring limited interference to the communication user. Analyzing both Figure 2a,b, we conclude that our proposed secure beam focusing is adept at facilitating secure communication even when the radar targets and communication user occupy the same angular position—a feat not feasible with traditional far-field beam steering.
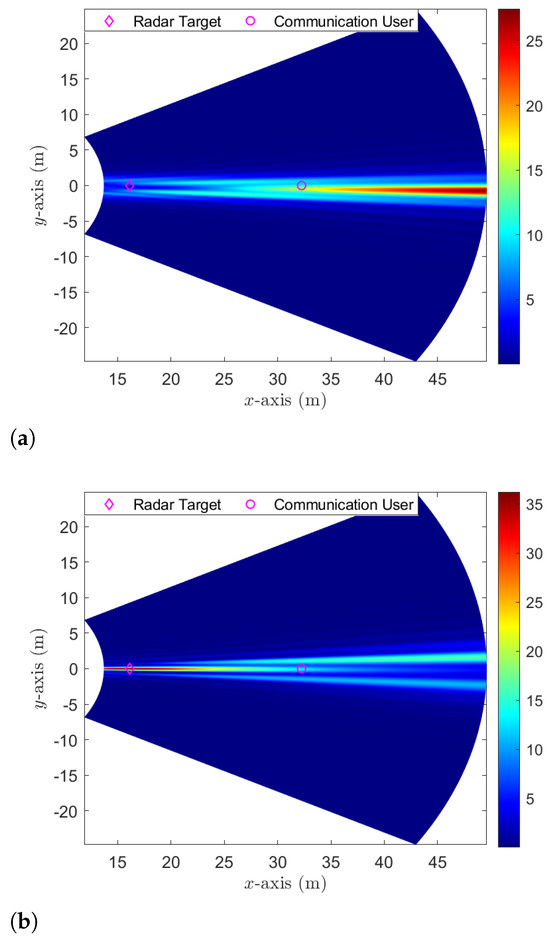
Figure 2.
The normalized signal power of communication and radar signals. (a) Communication signal; (b) radar signal.
Figure 3 depicts the trade-off between the achievable secrecy rate and the transmit beampattern gain, as evaluated using both the optimal and sub-optimal solutions. The simulation settings are consistent with those used in Figure 2. It is observed that, as the target beampattern gain requirement rises, the achievable secrecy rate declines sharply. This decline occurs because with a fixed and limited total transmit power, dedicating more power to radar sensing reduces the power available for secure communication. This observation indicates that careful design of the secure beam-focusing scheme is crucial for balancing these two performances. Additionally, the optimal solution consistently surpasses the sub-optimal solution regarding the trade-off between secrecy rate and target beampattern gain. This superior performance stems from the more comprehensive and precise optimization techniques used in deriving the optimal solution, albeit at the cost of increased computational complexity. As anticipated, increasing the transmit budget enhances either the secrecy rate or the target beampattern gain.
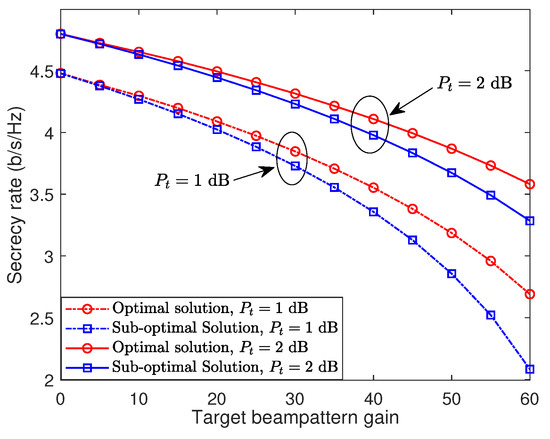
Figure 3.
Trade-off between the secrecy rate and the transmit beampattern gain.
Figure 4 effectively illustrates the relationship between the achievable secrecy rate and transmit power, evaluated using both the optimal and sub-optimal near-field solutions, along with the far-field beam steering solution. The far-field beam steering solution is derived by substituting the precise near-field channel model with a standard far-field channel model, thereby neglecting the effects of the near-field. The simulation settings are consistent with those used in Figure 2. Figure 4 shows that the secrecy rates achievable by both the optimal and sub-optimal near-field solutions increase as the transmit power increases. In contrast, the achievable rate of the far-field beam steering remains consistently at zero. This is due to the untrusted radar target, potentially an eavesdropper, sharing an identical angular direction with the communication user, coupled with a relatively smaller distance from the transmitter. Consequently, this potential eavesdropper experiences superior channel conditions compared to the legitimate communication user. Under these circumstances, far-field beam steering fails to differentiate between the untrusted radar target and legitimate communication users, resulting in a zero secrecy rate. Conversely, near-field solutions yield positive secrecy rates, thanks to the beam-focusing capability in the near-field, which proficiently distinguishes users in both angular and distance dimensions.
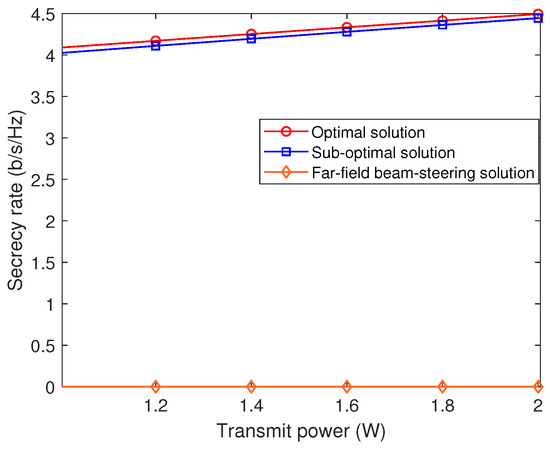
Figure 4.
Secrecy rate versus the transmit power.
Finally, we study a general scenario with varying numbers of radar targets randomly positioned on the near-field -plane. Figure 5 shows a plot of the achievable secrecy rate against the number of radar targets L, with a consistent radar target threshold . We successively add radar targets to the near-field -plane. As seen in Figure 5, the achievable secrecy rate for both optimal and sub-optimal solutions consistently decreases as the number of radar targets grows. This is because, as the quantity of radar targets rises, so does the likelihood of intercepted communications, consequently leading to a reduced achievable secrecy rate. Additionally, a higher transmit power can improve the secrecy rate for a given radar target count.
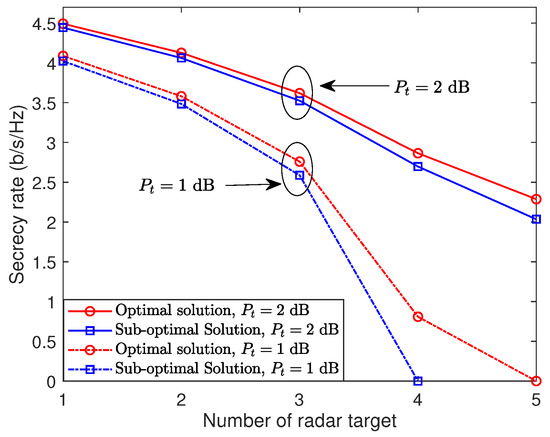
Figure 5.
Secrecy rate versus the number of radar targets.
5. Conclusions
This paper addresses beam-focusing design in near-field ISAC systems using XL-MIMO, focusing on maximizing the secrecy rate while meeting radar target requirements. It introduces both globally optimal and practical low-complexity sub-optimal solutions, catering to different computational capacities. Our numerical results demonstrate the efficacy of these solutions, notably achieving positive secrecy rates in challenging scenarios where the radar targets and communication user are positioned at identical angles. This study thus marks a significant advancement in secure communication within near-field ISAC environments, showcasing the potential of XL-MIMO in overcoming traditional security challenges.
One interesting extension of this paper is to use the Cramér–Rao bound (CRB) to evaluate the estimation accuracy. In such a case, the beam-focusing vectors and the radar covariance matrix should be jointly optimized to minimize the CRB. Furthermore, the beam-focusing design can also be extended to the robust beam-focusing case, where perfect channel state information is not necessary. Additionally, while our proposed algorithms have been effectively validated through simulations, we recognize the need for their verification through practical measurements in future research. This step is crucial for a comprehensive assessment of their real-world applicability and performance.
Author Contributions
Conceptualization, P.S. and H.D.; methodology, P.S.; software, P.S.; validation, P.S., H.D. and B.W.; formal analysis, P.S.; investigation, P.S.; resources, P.S.; data curation, P.S.; writing—original draft preparation, P.S.; writing—review and editing, H.D. and B.W.; visualization, P.S.; supervision, H.D. and B.W.; project administration, B.W.; funding acquisition, B.W. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the Open Foundation of National Railway Intelligence Transportation System Engineering Technology Research Center under grant No. RITS2021KF02 and the National Natural Science Foundation of China under grant No. 61971238.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data is contained within the article.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Liu, X.; Huang, T.; Shlezinger, N.; Liu, Y.; Zhou, J.; Eldar, Y.C. Joint transmit beamforming for multiuser MIMO communications and MIMO radar. IEEE Trans. Signal Process. 2020, 68, 3929–3944. [Google Scholar] [CrossRef]
- Liu, F.; Cui, Y.; Masouros, C.; Xu, J.; Han, T.X.; Eldar, Y.C.; Buzzi, S. Integrated sensing and communications: Toward dual-functional wireless networks for 6G and beyond. IEEE J. Sel. Areas Commun. 2022, 40, 1728–1767. [Google Scholar] [CrossRef]
- Liu, A.; Huang, Z.; Li, M.; Wan, Y.; Li, W.; Han, T.; Liu, C.; Du, R.; Tan, D.; Lu, J.; et al. A survey on fundamental limits of integrated sensing and communication. IEEE Commun. Surv. Tutor. 2022, 24, 994–1034. [Google Scholar] [CrossRef]
- Sheikh, M.S.; Liang, J.; Wang, W. A survey of security services, attacks, and applications for vehicular ad hoc networks (VANETs). Sensors 2019, 19, 3589. [Google Scholar] [CrossRef]
- Hartenstein, H.; Laberteaux, L.P. A tutorial survey on vehicular ad hoc networks. IEEE Commun. Mag. 2008, 46, 164–171. [Google Scholar] [CrossRef]
- Wu, Q.; Wang, S.; Ge, H.; Fan, P.; Fan, Q.; Letaief, K.B. Delay-sensitive task offloading in vehicular fog computing-assisted platoons. arXiv 2023, arXiv:2309.10234. [Google Scholar] [CrossRef]
- Wu, Q.; Zhao, Y.; Fan, Q.; Fan, P.; Wang, J.; Zhang, C. Mobility-aware cooperative caching in vehicular edge computing based on asynchronous federated and deep reinforcement learning. IEEE J. Sel. Top. Signal Process. 2022, 17, 66–81. [Google Scholar] [CrossRef]
- Wei, Z.; Liu, F.; Masouros, C.; Su, N.; Petropulu, A.P. Toward multi-functional 6G wireless networks: Integrating sensing, communication, and security. IEEE Commun. Mag. 2022, 60, 65–71. [Google Scholar] [CrossRef]
- Deligiannis, A.; Daniyan, A.; Lambotharan, S.; Chambers, J.A. Secrecy rate optimizations for MIMO communication radar. IEEE Trans. Aerosp. Electron. Syst. 2018, 54, 2481–2492. [Google Scholar] [CrossRef]
- Ren, Z.; Qiu, L.; Xu, J. Optimal transmit beamforming for secrecy integrated sensing and communication. In Proceedings of the ICC 2022-IEEE International Conference on Communications, Seoul, Republic of Korea, 16–20 May 2022; pp. 5555–5560. [Google Scholar]
- Su, N.; Liu, F.; Masouros, C. Secure Radar-Communication Systems With Malicious Targets: Integrating Radar, Communications and Jamming Functionalities. IEEE Trans. Wirel. Commun. 2021, 20, 83–95. [Google Scholar] [CrossRef]
- Naser, M.; Alsabah, M.; Mahmmod, B.; Noordin, N.; Abdulhussain, S.; Baker, T. Downlink training design for FDD massive MIMO systems in the presence of colored noise. Electronics 2020, 9, 2155. [Google Scholar] [CrossRef]
- Alsabah, M.; Naser, M.; Mahmmod, B.; Noordin, N.; Abdulhussain, S. Sum rate maximization versus MSE minimization in FDD massive MIMO systems with short coherence time. IEEE Access 2021, 9, 108793–108808. [Google Scholar] [CrossRef]
- Zhang, X.; Wang, Z.; Zhang, H.; Yang, L. Near-field channel estimation for extremely large-scale array communications: A model-based deep learning approach. IEEE Commun. Lett. 2023, 27, 1155–1159. [Google Scholar] [CrossRef]
- Zhang, X.; Zhang, H.; Zhang, J.; Li, C.; Huang, Y.; Yang, L. Codebook Design for Extremely Large-Scale MIMO Systems: Near-field and Far-field. arXiv 2021, arXiv:2109.10143. [Google Scholar] [CrossRef]
- Wang, Z.; Mu, X.; Liu, Y. Near-field integrated sensing and communications. IEEE Commun. Lett. 2023, 27, 2048–2052. [Google Scholar] [CrossRef]
- Zhang, H.; Shlezinger, N.; Guidi, F.; Dardari, D.; Eldar, Y.C. 6G Wireless Communications: From Far-Field Beam Steering to Near-Field Beam Focusing. IEEE Commun. Mag. 2023, 61, 72–77. [Google Scholar] [CrossRef]
- Zhang, H.; Shlezinger, N.; Guidi, F.; Dardari, D.; Imani, M.F.; Eldar, Y.C. Beam focusing for near-field multiuser MIMO communications. IEEE Trans. Wirel. Commun. 2022, 21, 7476–7490. [Google Scholar] [CrossRef]
- Guerra, A.; Guidi, F.; Dardari, D.; Djurić, P.M. Near-field tracking with large antenna arrays: Fundamental limits and practical algorithms. IEEE Trans. Signal Process. 2021, 69, 5723–5738. [Google Scholar] [CrossRef]
- Hua, H.; Xu, J.; Han, T.X. Optimal transmit beamforming for integrated sensing and communication. IEEE Trans. Veh. Technol. 2023, 72, 10588–10603. [Google Scholar] [CrossRef]
- Zhang, H.; Huang, Y.; Li, C.; Yang, L. Secure beamforming design for SWIPT in MISO broadcast channel with confidential messages and external eavesdroppers. IEEE Trans. Wirel. Commun. 2016, 15, 7807–7819. [Google Scholar] [CrossRef]
- Chang, T.-H.; Hsin, C.-W.; Ma, W.-K.; Chi, C.-Y. A linear fractional semidefinite relaxation approach to maximum-likelihood detection of higher-order QAM OSTBC in unknown channels. IEEE Trans. Signal Process. 2009, 58, 2315–2326. [Google Scholar] [CrossRef][Green Version]
- Grant, M.; Boyd, S. CVX: Matlab Software for Disciplined Convex Programming, Version 2.1. 2014. Available online: http://cvxr.com/cvx/ (accessed on 25 December 2023).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).