1. Introduction
Since the first deployment of the fifth generation (5G) mobile networks in 2019, 5G has rapidly become a mainstream mobile network worldwide. According to the Global System for Mobile Communications Association (GSMA), the 5G adoption rate reached 43.1% in the United States in Q4 2022 [
1]. 5G mobile networks and telecommunication standards have been developed to meet the various demands of modern telecommunication. In particular, it is designed to support enhanced features such as Enhanced Mobile BroadBand (EMBB), Massive Machine-Type Communications (MMTC), and Ultra-Reliable and Low-Latency Communications (URLLC) [
2].
In order to ensure the seamless delivery of high-quality services to users through these three features, 5G demands heightened security compared to its predecessors in mobile networks. Therefore, the 3rd Generation Partnership Project (3GPP) consortium, which is in charge of the standardization of 5G mobile networks, has standardized an essential 5G security architecture and procedures as well as several security features [
3,
4].
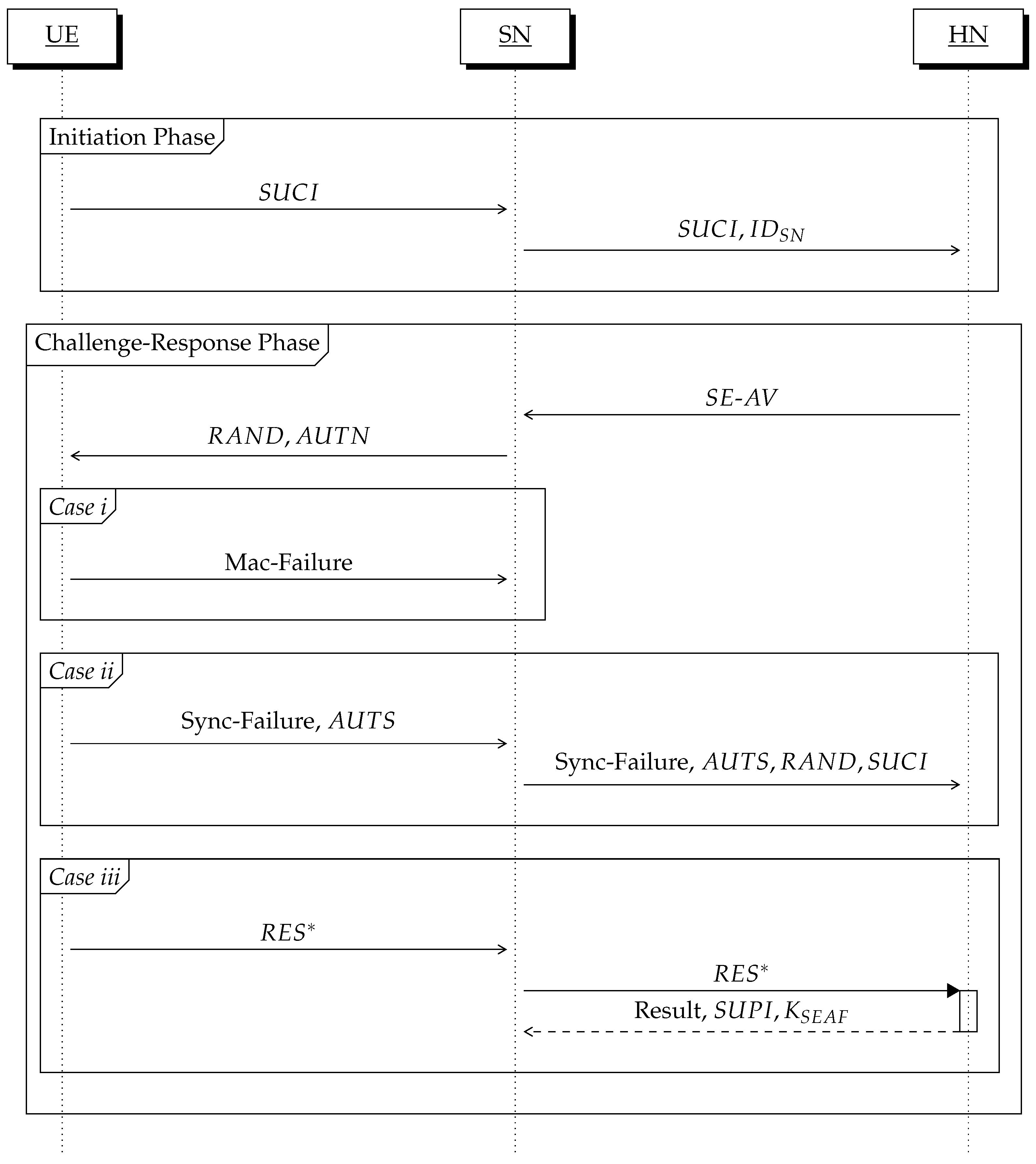
Figure 1 depicts the 3GPP 5G security architecture.
Notably, in 5G, primary authentication emerges as a cornerstone, representing the initial security checkpoint for accessing 5G network environments. For the 5G primary authentication, two protocols have been adopted as standards: 5G Authentication and Key Agreement (5G-AKA) and Improved Extensible Authentication Protocol Method for 3rd Generation Authentication and Key Agreement (EAP-AKA
) [
3,
5]. The former caters to 3GPP devices, while the latter is tailored for non-3GPP devices.
The 5G primary authentication protocols, i.e., 5G-AKA and EAP-AKA
, allow a user equipment (UE) (e.g., a mobile phone) and a home network (HN) (e.g., the network of a service provider) to authenticate each other and exchange key materials (e.g., anchor keys) to protect entire subsequent 5G communications. Note that they have been enhanced and markedly differentiated from their previous version (i.e., Evolved Packet System Authentication and Key Agreement (EPS-AKA) [
4] and Extensible Authentication Protocol Method for 3rd Generation Authentication and Key Agreement (EAP-AKA) [
6]). The most distinctive feature of those security protocols in the 5G network is using a Subscriber Concealed Identifier (SUCI) that can be explained as a Subscriber Permanent Identifier (SUPI) in the encrypted format. In the previous generation, authentication was performed by transmitting the user identification information, International Mobile Subscriber Identity (IMSI), without encryption. On the other hand, in 5G, SUPI, which is a UE’s identifier, is encrypted into SUCI using a key derived through the Elliptic Curve Integrated Encryption Scheme (ECIES) before transmission to address identifier exposure [
7,
8,
9,
10]. Despite these efforts, 5G-AKA still remains vulnerable to various types of attacks [
7,
9,
10,
11,
12,
13,
14]. Ref. [
15] described vulnerabilities for 5G-AKA through formal verification and analysis. The authors showed that there still exist attack scenarios against 5G-AKA. In addition, refs. [
10,
16] pointed out that privacy problems of users may occur since 5G-AKA is susceptible to linkability attacks. Furthermore, ref. [
17] presented shortcomings of 5G-AKA, including the lack of support for forward secrecy, also known as perfect forward secrecy.
Meanwhile, the 5G network environments face the following new challenges:
As the advancement of 5G technology and the proliferation of 5G network applications continue at a rapid pace, the emergence of new security threats and attacks becomes more pronounced, thereby necessitating the establishment of elevated security prerequisites.
Thanks to the Authentication and Key Management for Applications (AKMA) [
18], the credentials generated through 5G primary authentication can be reused for application authentication in the 5G network environments; that is, the master session key negotiated during the 5G primary authentication is applied to derive an application key that allows a UE to authenticate itself to AKMA-based applications smoothly and efficiently.
Evidently, the security robustness of the existing 5G primary authentications falls short of addressing the aforementioned concerns. As a result, it becomes imperative to bolster the security framework with robust public key-based measures and ensure the implementation of forward secrecy.
Regarding EAP-AKA
, there has been a standardization effort aimed at enhancing the protocol to incorporate support for forward secrecy (known as EAP-AKA
-FS) [
19]. On the 5G-AKA side, there are existing works proposed to support unlinkability and forward secrecy, such as [
3,
16,
17,
20,
21]. In particular, those 5G-AKA enhancements attempted to reuse the ECIES shared key, which is used to protect the UE’s identifier in the initiation phase. However, in such an approach, if an adversarial security event happens in HN, forward secrecy is not guaranteed for the session key.
In this paper, we propose a 5G-AKA-Forward Secrecy (5G-AKA-FS) protocol that supports forward secrecy and unlinkability together to solve the limitations of the existing studies and maximize the efficiency of authentication in 5G networks. The proposed protocol accomplishes forward secrecy and unlinkability by introducing an additional ECIES-based ephemeral key pair generation within HN. The main contributions of this paper are summarized as follows:
The 5G-AKA-FS protocol is designed to concurrently support forward secrecy and unlinkability.
We analyze the latest studies proposed to improve the vulnerabilities of 5G-AKA and provide a solid comparison of security attributes between our 5G-AKA-FS and the latest studies.
We conduct a rigorous security verification of the proposed protocol using formal verification (BAN Logic [
22] and ProVerif [
23]).
Performance evaluation is thoroughly carried out by measuring overhead in terms of computation and communication.
The rest of the paper is organized as follows.
Section 2 explores the existing enhancements of 5G-AKA, while
Section 3 describes the preliminaries used in this paper. Moving on to
Section 4, we present a detailed description of the proposed protocol, followed by the formal security analysis using BAN Logic and ProVerif in
Section 5. Assessing performance,
Section 6 carries out a comparative evaluation of security properties between the proposed and existing protocols, along with measured overhead. Finally,
Section 7 provides the conclusion.
2. Related Works
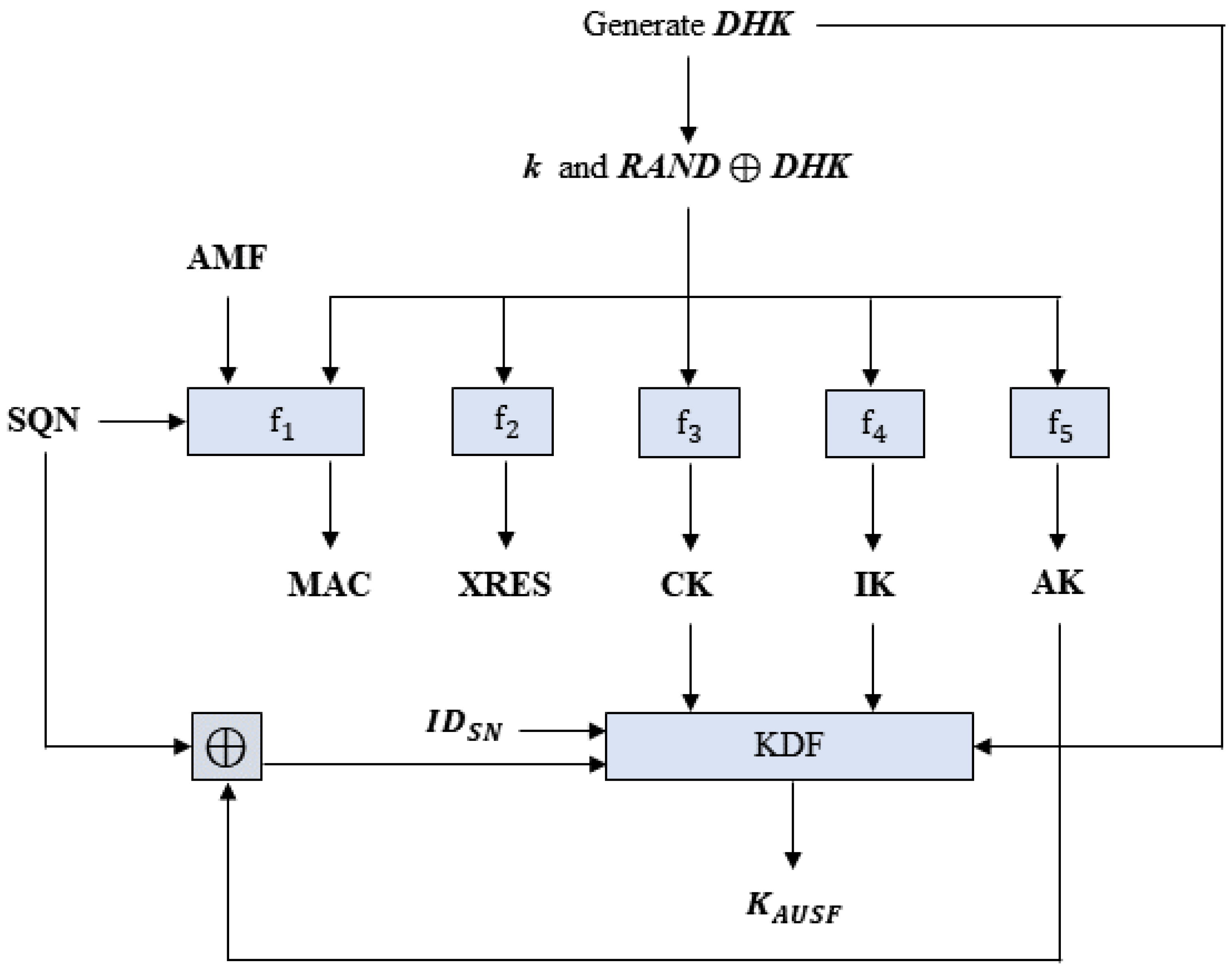
3GPP has defined two AKA protocols, namely 5G-AKA and Extensible Authentication Protocol (EAP)-AKA, for primary authentication in 5G networks. The purpose of the AKA protocols is to establish mutual authentication between the UE and the HN. In 2G to 4G networks, UE’s identifier IMSI is publicly exposed, thus resulting in privacy issues. However, in 5G-AKA, the subscriber identity information, known as SUPI, is encrypted into SUCI, which is then used for authentication while solving the privacy problem.
5G-AKA enhances authentication and key exchange in addition to introducing subscriber identity protection (e.g., SUCI) for privacy. However, as it is developed based on EPS-AKA, it inherits existing security vulnerabilities. Ref. [
15] conducted a formal verification and analysis of the 5G-AKA protocol using the Mixed Strand Space model, revealing vulnerabilities within the protocol. Their study also presented 21 attack scenarios specific to 5G-AKA and highlighted security features not supported by 5G-AKA. Furthermore, ref. [
17] identified shortcomings, such as the lack of support for forward secrecy through an analysis of 5G-AKA. In this regard, improved protocols, including [
3,
16,
17,
20,
21], have been proposed to address such vulnerabilities in 5G-AKA.
SUCI-AKA, proposed by [
20], aims to achieve forward secrecy for the anchor key
. For this goal, when generating the master session key
, the protocol reuses the shared key
, which is exchanged through ECIES to encrypt SUPI. In more details, the sequence number
is replaced with
during the generation of
. Such an approach enhances the security of the anchor and sub-session keys derived from
while still allowing the UE to verify if the received messages and their message authentication code (MAC) are fresh. However, SUCI-AKA can not support forward secrecy because the anchor key
is compromised when the long-term key
, shared between the UE and the HN, and the HN’s private key
are leaked.
5G-IPAKA, proposed by [
17], aims to provide mutual authentication between the UE and the SN, enhanced security for the anchor key and authentication vector (AV), and key confirmation. This protocol tries to provide forward secrecy by applying the ECIES secret
to generate the anchor key
, from which sub-sessions keys are then derived. Moreover, it lets the HN send
to the SN before the UE authentication. In this way, 5G-IPAKA enables the UE to authenticate the SN by verifying the SN’s message authentication code computed with
in addition to the HN. Similar to this, the UE is authenticated to the SN through its message authentication code. As a result, 5G-IPAKA achieves mutual authentication between the SN and the UE and between the HN and the UE while supporting key confirmation. However, if
and
are leaked, an attacker can reconstruct the anchor key
for malicious purposes while breaking forward secrecy. Furthermore, active attacks by malicious SNs are also possible since the HN delivers
to the SN without authenticating the UE. Finally, this protocol leads to compatibility issues with Subscriber Identity Modules (SIMs) by proposing a structure that deviates from the existing standard specification.
5GAKA-LCCO, proposed by [
21], aims to improve high communication and computation overheads as well as address SUCI replay attacks present in 5G-IPAKA. In this protocol, the SN first creates the random number and timestamp
and
, and sends to the UE these values, which are then applied to generate the key block with the long-term shared key
and the ECIES secret
. Note that the generated key block is not only used to compute the UE’s SUCI but also to authenticate the UE to the HN. Upon a receipt of the new SUCI, the HN decrypts it into the corresponding SUPI, counts on its timestamp
to validate the received
, and authenticates the UE. In such a way, the authentication process is optimized to have one round trip, reducing the computation and communication overhead. Also, the HN utilizes timestamps to prevent the SUCI replay and Denial-of-Service (DoS) attacks on itself while enhancing the security of the session keys by deriving
from
,
,
, and
. However, it should be noted that when generating
, both
and
are utilized. Therefore, if
and
are leaked, an attacker can recover
and conduct subsequent malicious attacks. Furthermore, to address SUCI replay attacks, 5GAKA-LCCO introduces freshness to SUCI by utilizing
. However, this approach requires time synchronization, which may pose challenges in situations such as roaming. Consequently, the use of
is not desirable for mobile telecommunication scenarios. Furthermore, 5GAKA-LCCO exhibits an unconventional protocol flow compared to the 5G-AKA standard, and the differences in the
can lead to compatibility issues, particularly with Legacy Universal Subscriber Identity Modules (USIMs), potentially resulting in backward compatibility problems.
5G-AKA, introduced by [
16], focuses on addressing linkability attacks by reusing the ECIES secret
, which is used to protect SUPI in the initial step. In this protocol, the HN encrypts its randomly generated number
into
with
, then sending to the UE the encrypted result instead of
along with the authentication token AUTN. At this point, it is worth noting that since the UE trusts the freshness of
, it also trusts the freshness of
. Therefore, if successfully decrypting
with
, the UE can trust the freshness of its received AUTN, thereby detecting the message replay attack prior to arriving at the
Sync_Failure while defending against the linkability attack. In spite of such a successful defense against the linkability attack, this protocol is vulnerable to active attacks by malicious SNs because it allows the HN to send
to the SN without authentication to the UE. More importantly, 5G-AKA
fails to achieve forward secrecy because the old anchor keys can be recovered if the long-term key
shared between the UE and the HN is leaked.
6. Comparative Analysis
In this section, we conduct a comparative assessment aimed at evaluating the effectiveness of the proposed protocol by considering security requirements as well as the computational and communication overheads. For a starter, six protocols are compared against six security requirements to assess the degree of security they each offer. This analysis showcases that the proposed protocol delivers robust security measures in comparison to the others.
Next, we proceed to determine the computational overhead linked to each protocol. This involves scrutinizing the amount of cryptographic operations required within each security protocol and quantifying the computational overhead through Python. We also evaluate the communication overhead by closely examining the message dimensions described in the 3GPP standard document [
3]. For that, the transmitted messages are not only inspected, but also their bit sizes are calculated to measure the communication overhead caused by each protocol.
6.1. Security Analysis
The proposed security protocol is compared to the existing protocols based on six security requirements: 5G Network and UE’s Mutual Authentication (AUTH), Secure Key Exchange (SKE), Legacy USIM Compatibility Support (LUCS), LinkaBility Attack (LBA), Active attack by Malicious SN (AMS), and Forward Secrecy for
(FS). The security requirements that each protocol satisfies are shown in
Table 4.
According to the table, all protocols satisfy the requirements for AUTH as well as SKE. However, LUCS is not supported by 5G-IPAKA and 5GAKA-LCCO. 5G-IPAKA introduces a different structure, which may result in compatibility issues. Similarly, 5GAKA-LCCO deviates from the standard by utilizing and follows an unconventional protocol flow, potentially leading to compatibility problems with previous versions, i.e., reverse compatibility problems.
LBA is an attack related to compromising a UE’s location privacy. 5GAKA-LCCO eliminates the process of synchronization failure by reducing round-trip, thus preventing LBA. In the case of 5G-AKA, is reused instead of , which enables it to confirm the freshness of and address LBA. On the other hand, 5G-AKA-FS can defend against LBA because it computes in HN and reflects this key when generating values required for authentication.
In 5G-IPAKA and 5G-AKA, active attacks by malicious SN are possible because the HN delivers to the SN without authentication of the UE. 5G-AKA, SUCI-AKA, and 5G-AKA derive the anchor key through the long-term key , so FS is not supported when is leaked. 5G-IPAKA and 5GAKA-LCCO used not only but also HN’s private key to support FS. However, if is compromised, FS for in the past is not achieved.
6.2. Overhead Analysis
To compare the trade-off between security and resource consumption, we have compared the proposed protocol computation and communication overhead. SUCI-AKA, 5G-IPAKA, 5GAKA-LCCO, and 5G-AKA′ are other protocols improvised based on 5G-AKA. However, they do not provide complete FS. EAP-TLS1.3 and EAP-AKA′-FS are both representative protocols on the mobile network field and provide complete FS. The test results provide respectful data for a trade-off between security and resource consumption.
6.2.1. Computation Overhead
Table 5 summarizes the environment used in the experiment. The computation overhead for each protocol was measured by conducting 5000 test runs using the cryptography library in Python 3.10.11.
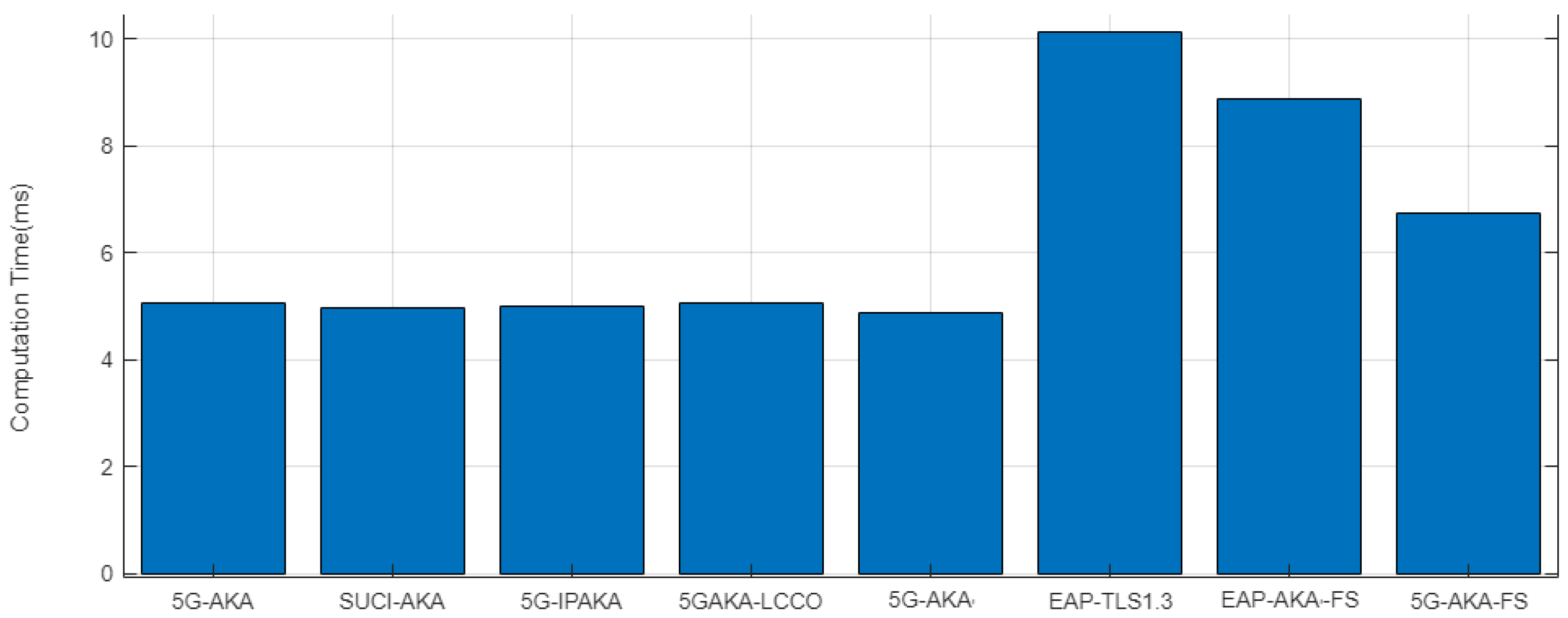
As can be seen in a test result shown in
Figure 5, 5G-AKA-related protocols have minor differences with 5G-AKA computation overhead. However, these protocols do not completely provide FS. The proposed protocol, with a computation overhead of 6.75 ms, provides FS and has resistance against LBA and AMS. Moreover, as can be seen in comparison with EAP-TLS1.3 and EAP-AKA′-FS, the increase in computation overhead for providing FS in the proposed protocol is low.
The majority of the computation overhead is incurred by ECDH (Elliptic Curve Diffie–Hellman) and digital signature. To provide FS, the protocol must generate a fresh key every session, which 5G-AKA does not do on the HN side, so an increase in overhead to provide FS on protocols is mostly caused by adding fresh ECDH in the key generation phase. In EAP-AKA′-FS, HN and UE generate fresh ECDH keys in the challenge-response phase. However, the proposed protocol, with the reuse of the fresh ECDH key generated in the initiation phase. In Step 1.1, the proposed protocol computation overhead is optimized. Moreover, unlike EAP-TLS1.3, by a succession of 5G-AKA architecture, the proposed protocol does not require a digital signature. These are the reasons the proposed protocol has lower computation overhead than EAP-TLS1.3 and EAP-AKA′-FS. Considering that our proposed protocol provides strong security, this level of computational overhead is deemed acceptable. It represents a trade-off that we are willing to accept to prioritize robust security.
6.2.2. Communication Overhead
Communication overhead refers to the total message size that needs to be transferred in the network for a specific purpose. Based on the 3GPP 33.501 specification, we have analyzed the total size of the messages that are exchanged through the primary authentication phase.
Table 6 refers to the size of the messages that consist of the 5G primary authentication phase.
The combination of upper messages concludes the total communication overhead of the 5G-AKA.
Table 7 gives the total communication overhead of 5G-AKA, improved protocols, and for practical comparison EAP-TLS1.3 and EAP-AKA′-FS.
For one protocol to offer additional security properties and inherit the structure of 5G-AKA, it is most likely to use additional messages to fulfill that purpose. As a result, 5G-AKA-FS leads to a higher communication overhead than 5G-AKA. However, as compensation for this sacrifice, i.e., additional overhead, the proposed protocol offers forward secrecy by newly generating the HN’s ephemeral ECDH public key and using it as RAND in the initialization phase. Note that in 5G-AKA RAND is a 128-bit random challenge, but in 5G-AKA-FS the RAND challenge is replaced with the HN’s ephemeral ECDH public key, which is 256-bit. This results in 5G-AKA-FS having 384-bit higher communication overhead than 5G-AKA. With only 384-bit extra messages traveling through the network, 5G-AKA-FS achieves resistance against LBA and AMS and provides FS. Among 5G-AKA-related protocols, 5G-AKA-FS is the only improvised protocol that offers all three security properties. Furthermore, despite its increase, the overhead of 5G-AKA-FS remains lower than that of the EAP-TLS-1.3 protocol and EAP-AKA′-FS. The analysis results indicate that the addition of 384 extra bits for three crucial security properties are reasonably justifiable trade-offs.