A Systematic Literature Review on Machine Learning and Deep Learning Approaches for Detecting DDoS Attacks in Software-Defined Networking
Abstract
1. Introduction
1.1. Motivation behind This SLR
1.2. Related Works
1.3. Contributions and Organization of SLR
- Provides a solid background of the SDN architecture, underlines the forwarding process, and illustrates examples of SDN DDoS attacks.
- Presents theoretical background and practical steps that could be a reference or guideline for the research community to conduct SLR in any field.
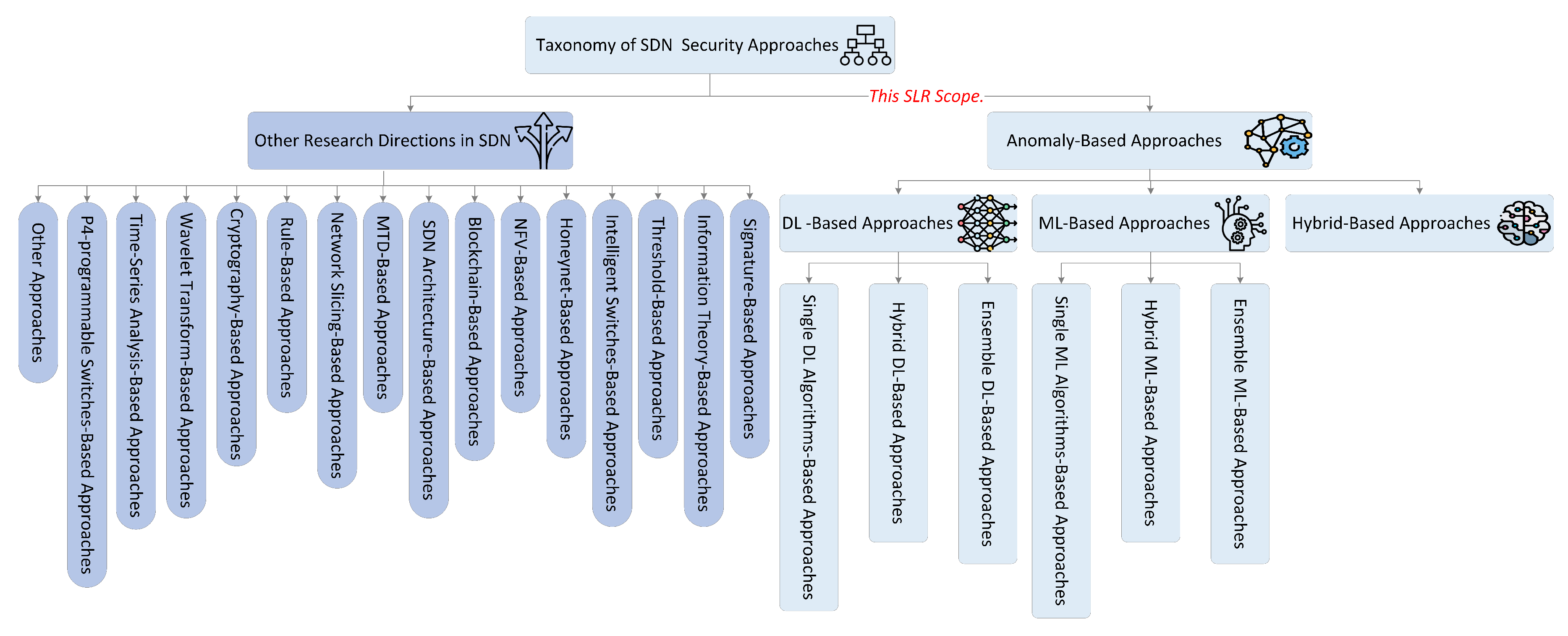
- Presents new taxonomy of current research directions of state-of-the-art approaches for detecting DDoS attacks in the SDN network.
- A comprehensive review through critical analysis of 70 studies published from 2014 to 2022 on the existing literature of ML, DL, and hybrid approaches (incorporating both ML and DL) for detecting and mitigating DDoS attacks in SDN networks. It also underlines their limitations and highlights potential research gaps.
- Provides a critical analysis of the evaluation metrics, network simulators, hacking tools, experimental platforms, traffic analyzers, and up-to-date datasets used in the existing literature or studies related to detecting and mitigating SDN DDoS attacks.
- A list of challenges, open issues, and future research directions as a roadmap for researchers working on SDN DDoS attack detection approaches are given.
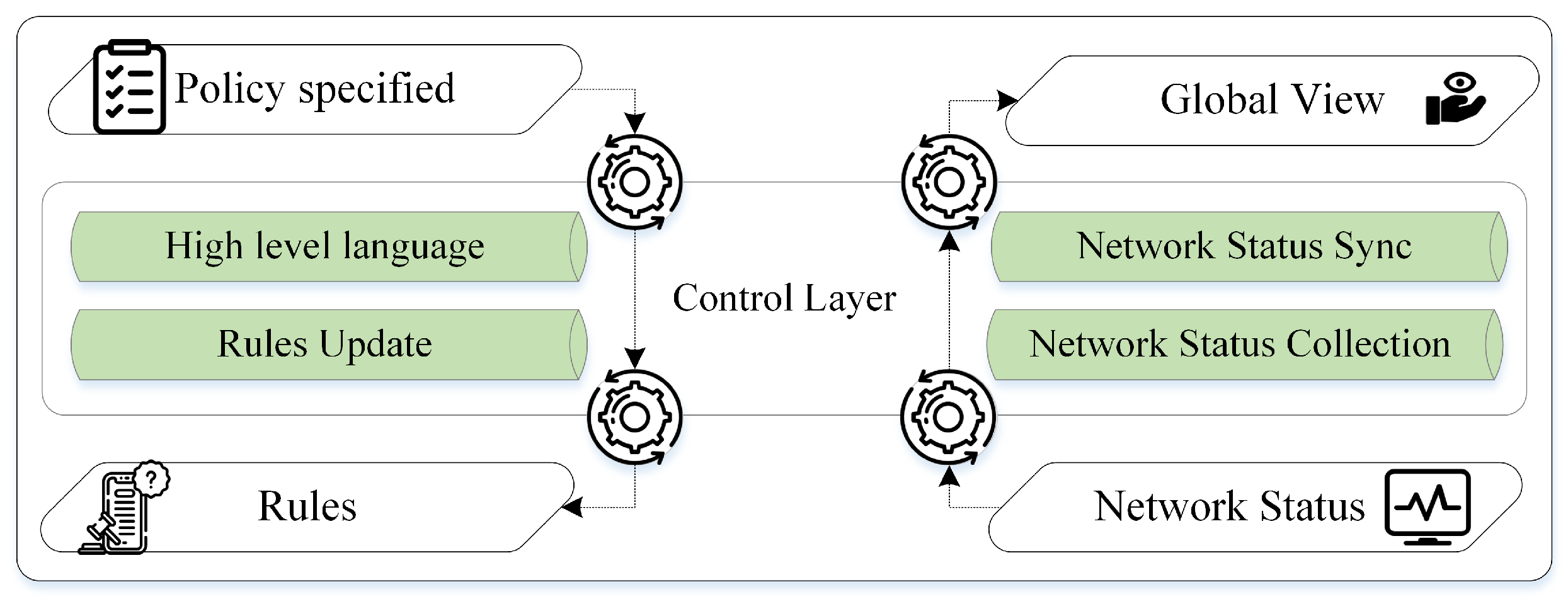
2. Background
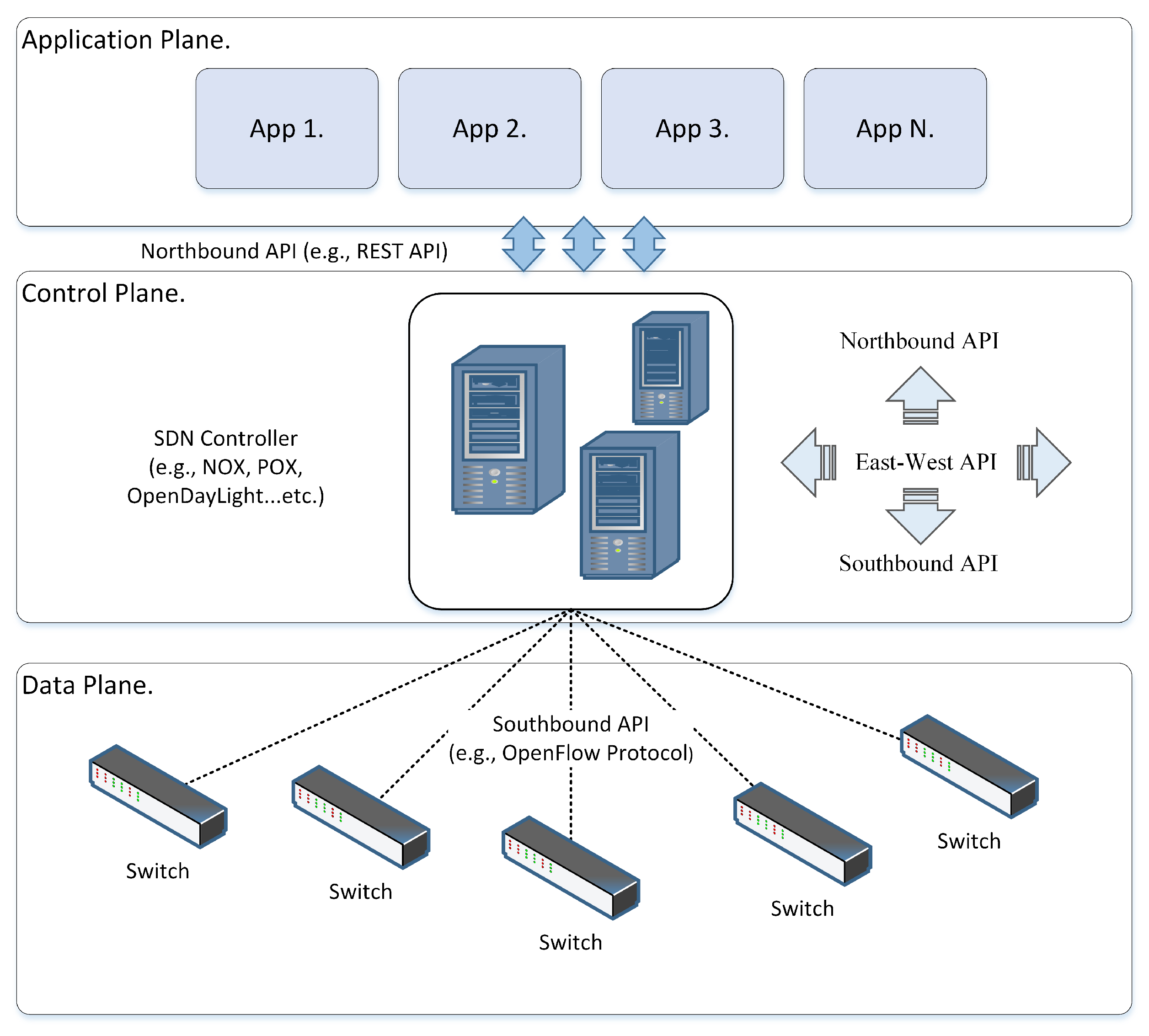
2.1. Architecture Model of SDN
2.1.1. Application Plane
2.1.2. Northbound API
2.1.3. Control Plane
2.1.4. Southbound API
2.1.5. Data Plane
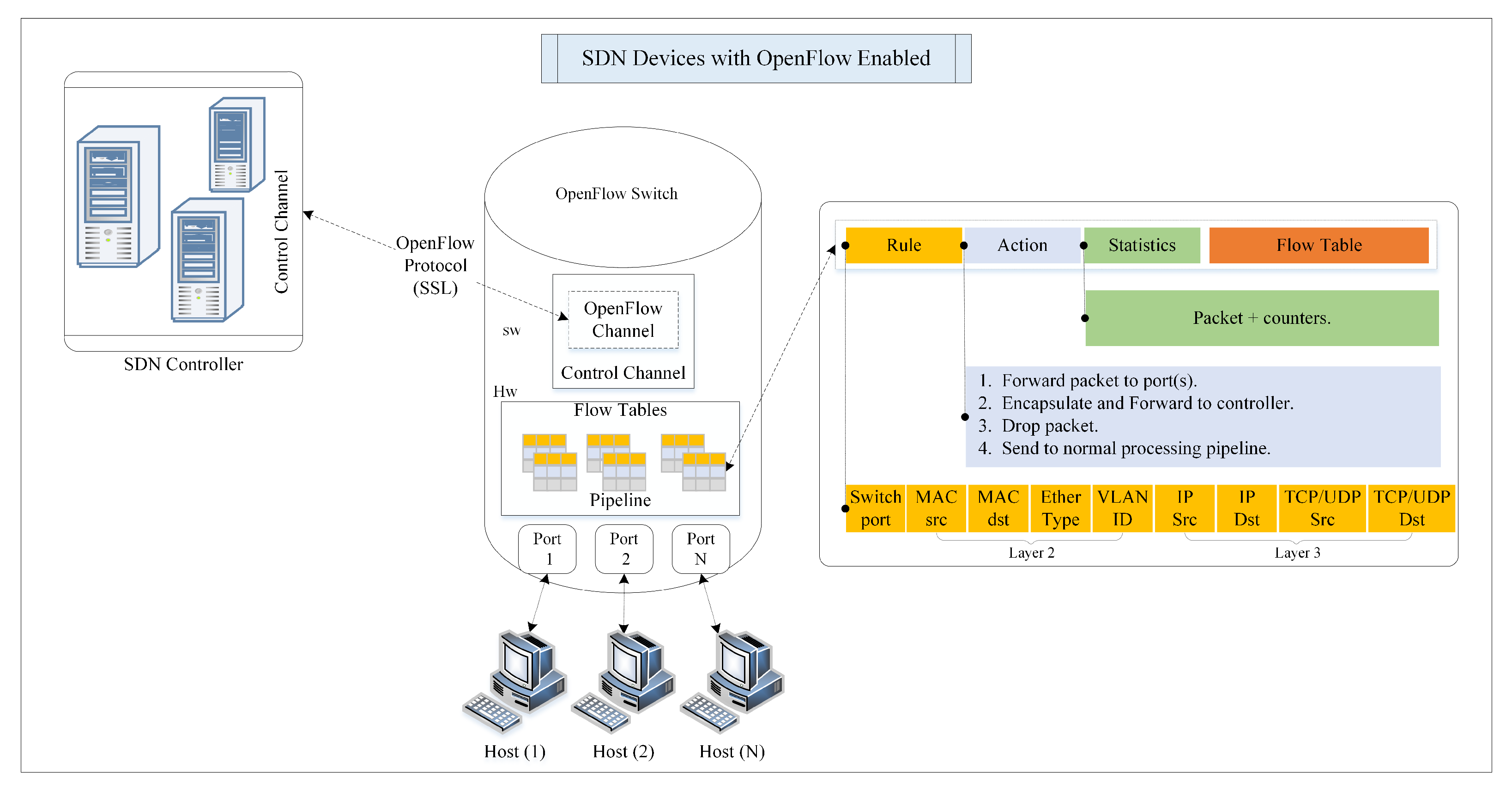
2.2. OpenFlow Forwarding Process
- To deliver a packet to destination host “B”, source host “A” sends a packet to the SDN switch through port 1.
- Upon receiving the packet, the switch performs a lookup in its flow tables. Suppose there is a match, then the switch will execute the instructions associated with the specific flow entry. Otherwise, the default OpenFlow switch specification (preinstalled OpenFlow rules) states that the packet must be forwarded to the SDN controller over the OpenFlow (southbound API) secure channel using a Packet-In message. The Packet-In message may include the complete packet or just a segment. In another case, the switch buffers the entire packet, and the Packet-In message contains a buffer ID of the packet [39].
- The controller receives a Packet-In message from the switch. Typically, two things can happen here. First, the controller examines the packet header and checks whether it needs to send a Packet-Out message or not. If it does, include the reference buffer ID in the Packet-In message and the instruction for action to be performed (e.g., forward to the destination or drop the packet). Second, the controller might also send a flow modification message (Flow-Mod message) to the switch to install a new flow entry rule in the flow table to handle a similar subsequent flow in the future [31,39].
- The switch receives the Packet-Out message from the controller, updates the flow table with a new flow entry, and then forwards the packet to the destination host “B”.
- Finally, the destination host “B” receives the packet from source host “A”. When host “B” sends a return packet to host “A”, the reverse path of this communication follows the same steps.
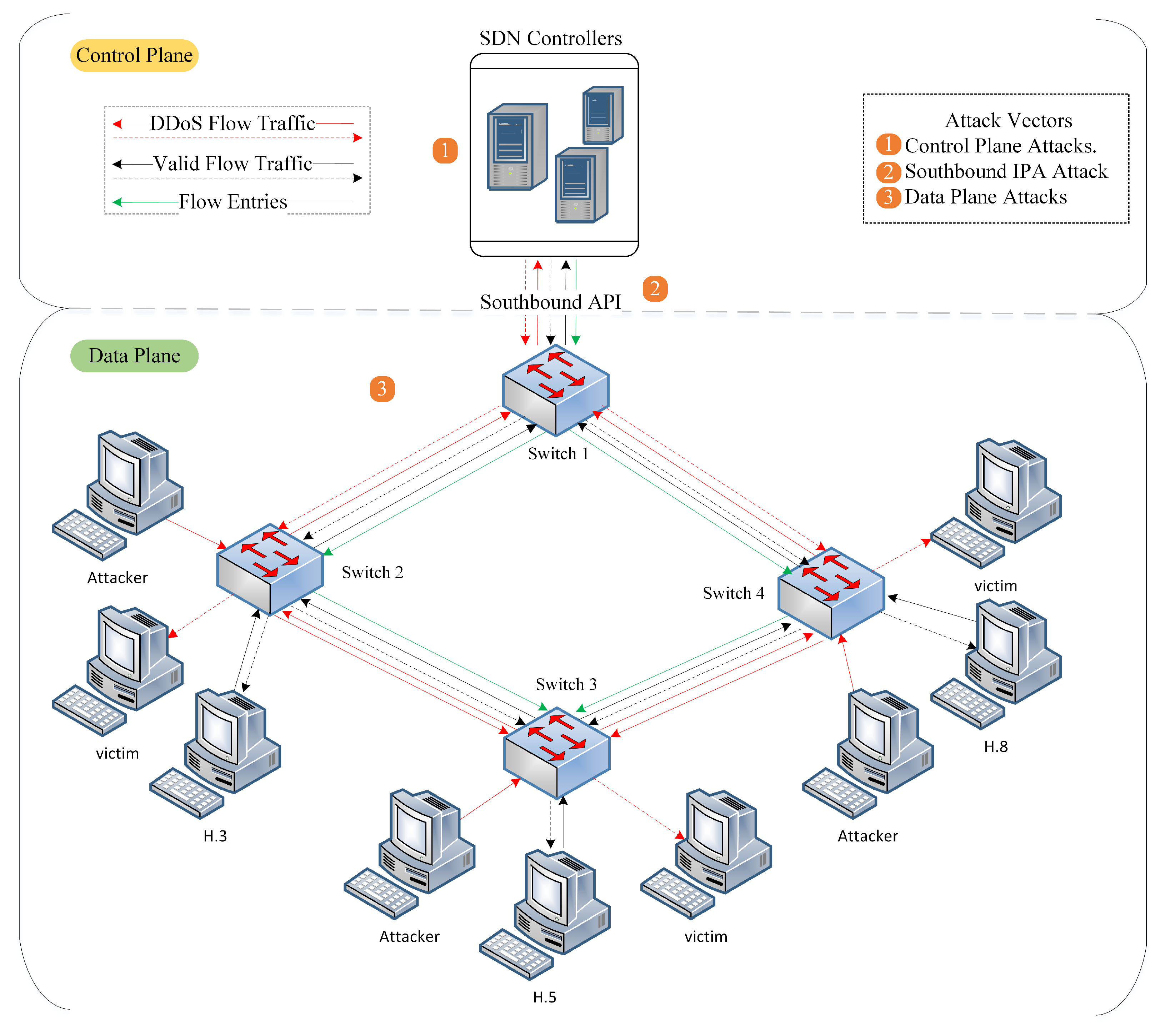
2.3. DDoS Attacks against SDN Network
2.4. ML and DL-Based Approaches
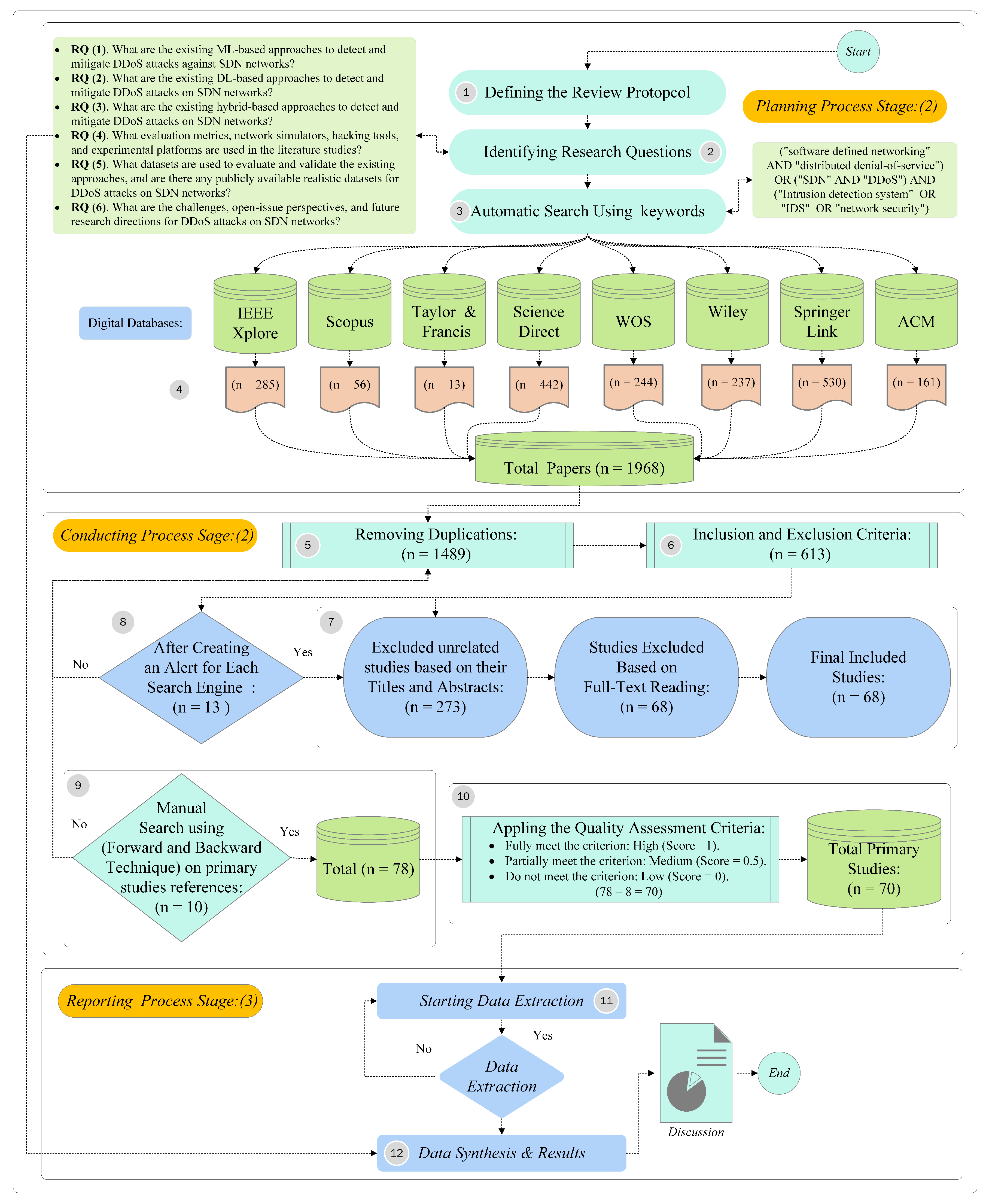
3. Research Methodology
3.1. Defining the Review Protocol
3.2. Defining Research Questions (RQ)
- RQ(1). What are the existing ML-based approaches to detect and mitigate DDoS attacks against SDN networks?
- RQ(2). What are the existing DL-based approaches to detect and mitigate DDoS attacks on SDN networks?
- RQ(3). What are the existing hybrid-based approaches to detect and mitigate DDoS attacks on SDN networks?
- RQ(4). What evaluation metrics, network simulators, hacking tools, and experimental platforms are used in the literature studies?
- RQ(5). What datasets are used to evaluate and validate the existing approaches, and are there any publicly available realistic datasets for DDoS attacks on SDN networks?
- RQ(6). What are the challenges, open-issue perspectives, and future research directions for DDoS attacks on SDN networks?
3.3. Inclusion and Exclusion Criteria Terms
- (i)
- Title and abstract stage: this stage excluded the irrelevant studies based on title and abstract. Next, the studies that meet at least some criteria terms in Table 2 are selected and passed to the next stage for further processing.
- (ii)
- Full-text reading stage: this stage excluded the studies based on full-text or partial reading if they did not meet the criteria terms in Table 2.
- (iii)
- Final selection stage: This stage applies the criteria terms in Table 2 for final selection and excludes studies that do not match any of the following criteria.
- -
- The research study must be relevant and related to the research questions.
- -
- The research study discusses the comprehensive solution ML, DL, and hybrid-based approaches to detect and mitigate DDoS attacks on SDN networks.
- -
- The research study provides a sufficient volume of technical implementation and methodology information.
- -
- The research study presents an adequate description of the obtained results.
3.4. Search Plan
3.5. Research Study Selection Procedure
3.6. Quality Assessment (QA) Criteria
3.7. Data Extraction and Data Synthesis
4. SLR Results
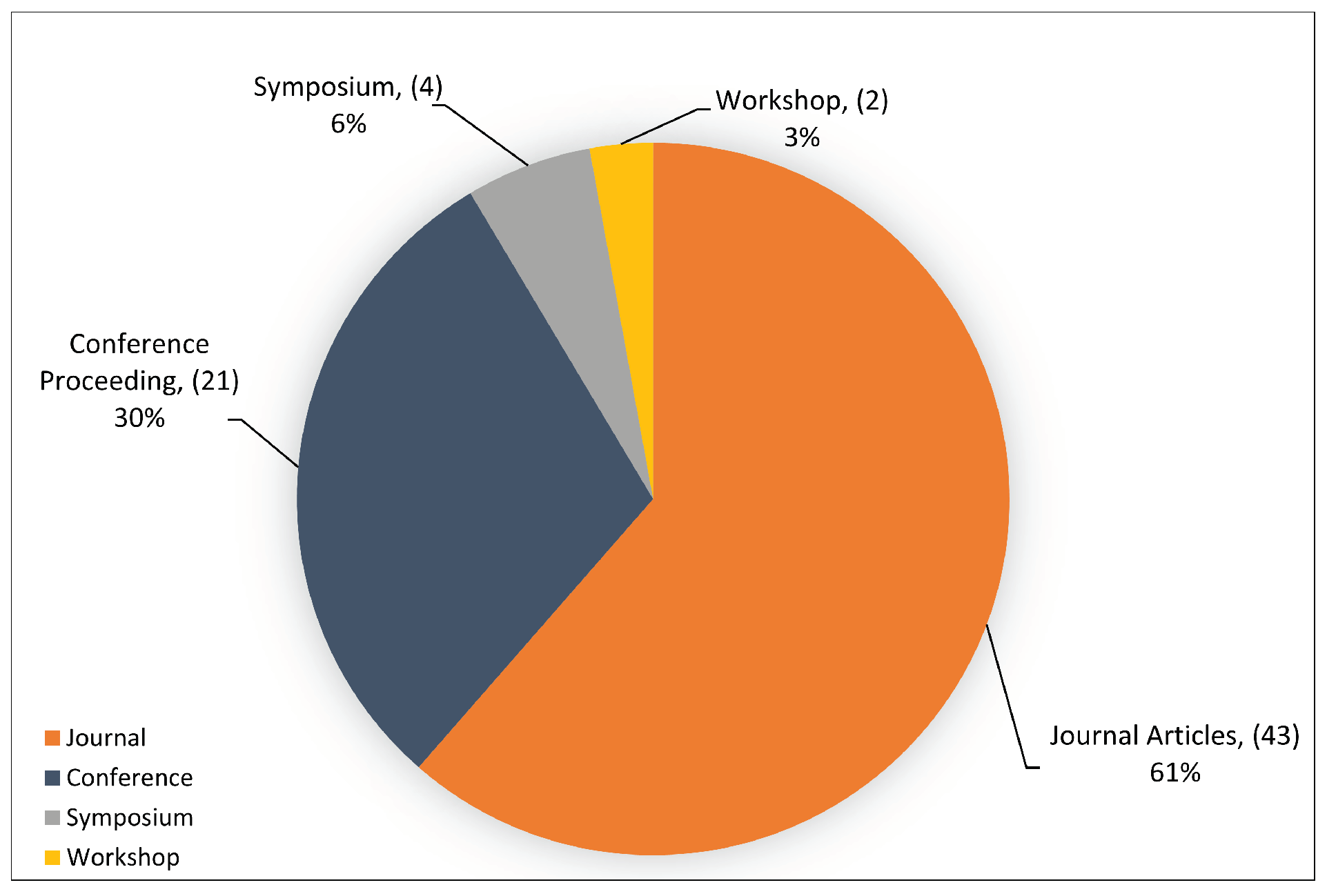
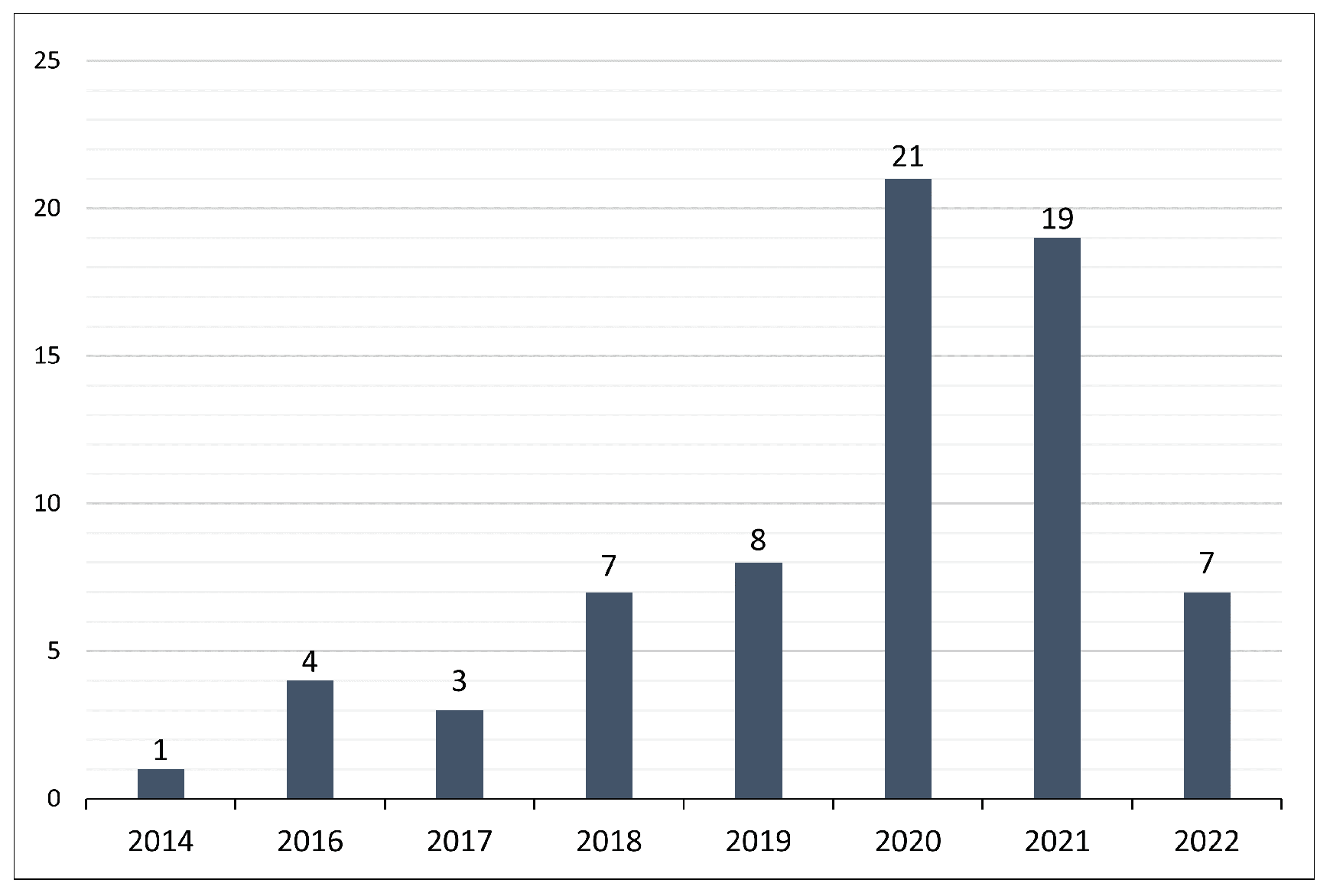
4.1. Sources and Year of Publication
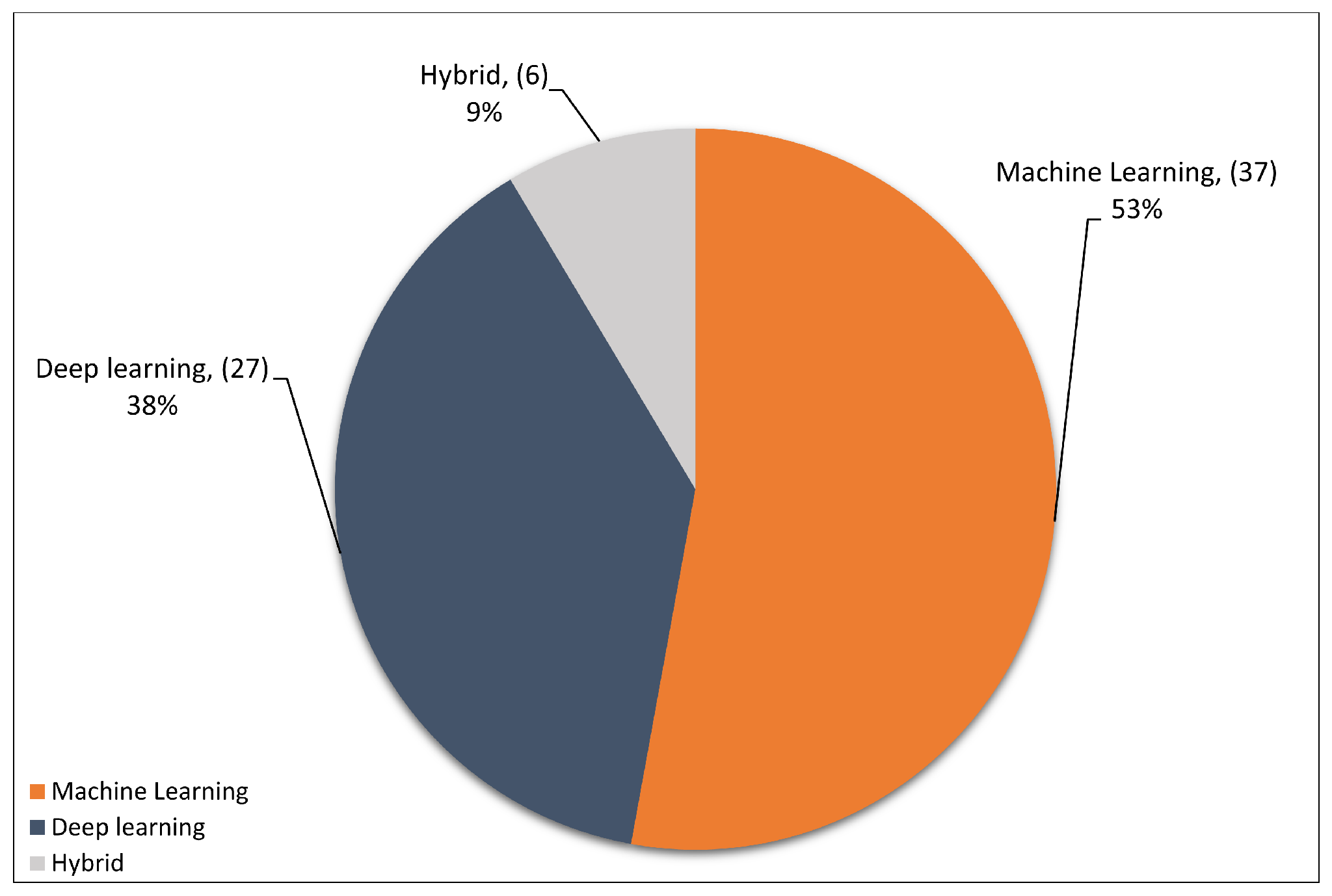
4.2. Primary Studies’ Methods
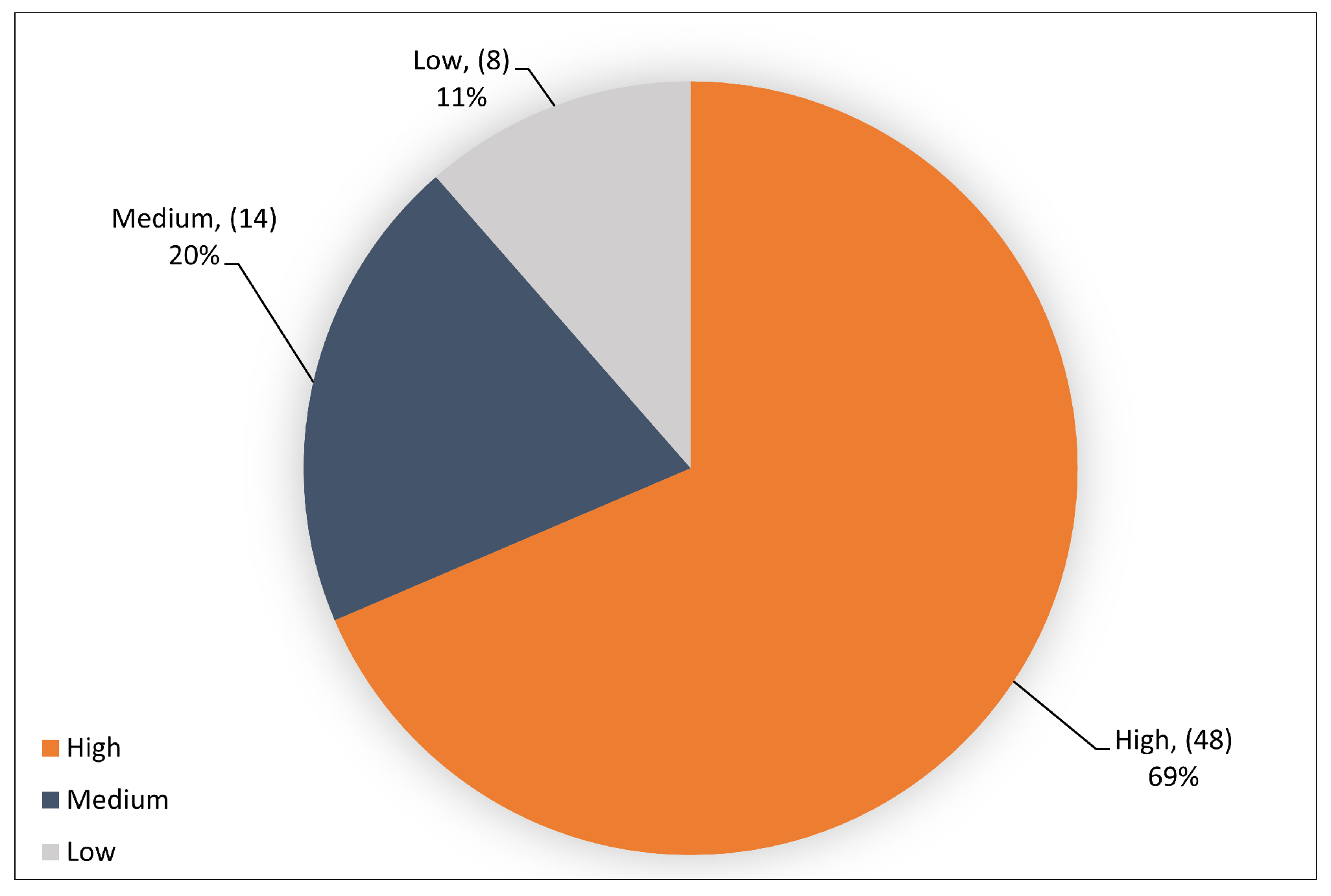
4.3. Quality Assessment Results
5. Research Questions Results and Discussion
5.1. RQ(1). What Are the Existing ML-Based Approaches to Detect and Mitigate DDoS Attacks against SDN Networks?
5.1.1. Ensemble ML Approaches
5.1.2. Hybrid ML Approaches
5.1.3. Single ML Approaches
5.2. RQ(2). What Are the Existing DL-Based Approaches to Detect and Mitigate DDoS Attacks on SDN Networks?
5.2.1. Ensemble DL Approaches
5.2.2. Hybrid DL Approaches
5.2.3. Single DL Approaches
5.3. RQ(3). What Are the Existing Hybrid-Based Approaches to Detect and Mitigate DDoS Attacks on SDN Networks?
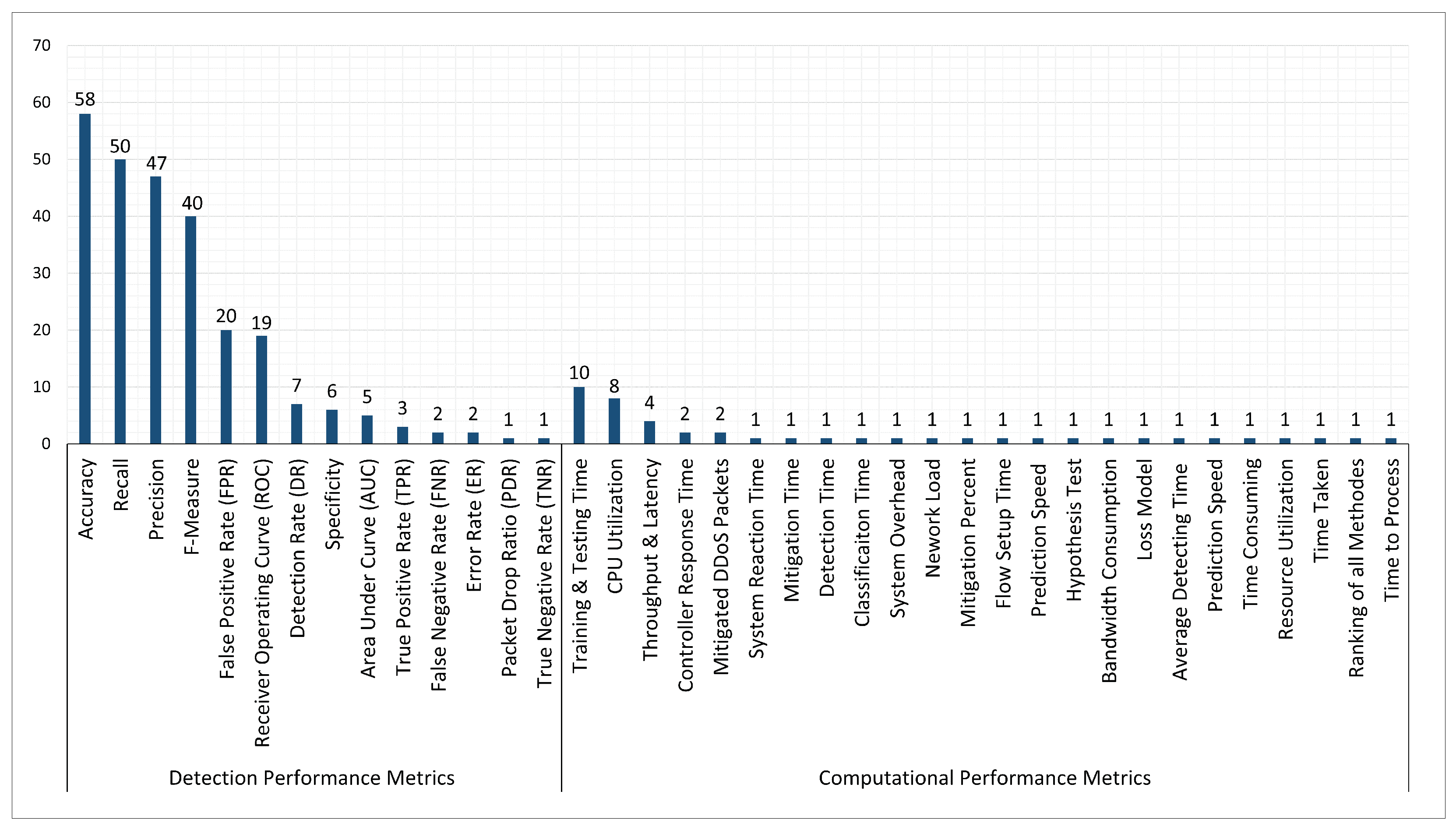
5.4. RQ(4). What Evaluation Metrics, Network Simulators, Hacking Tools, and Experimental Platforms Are Used in the Studies?
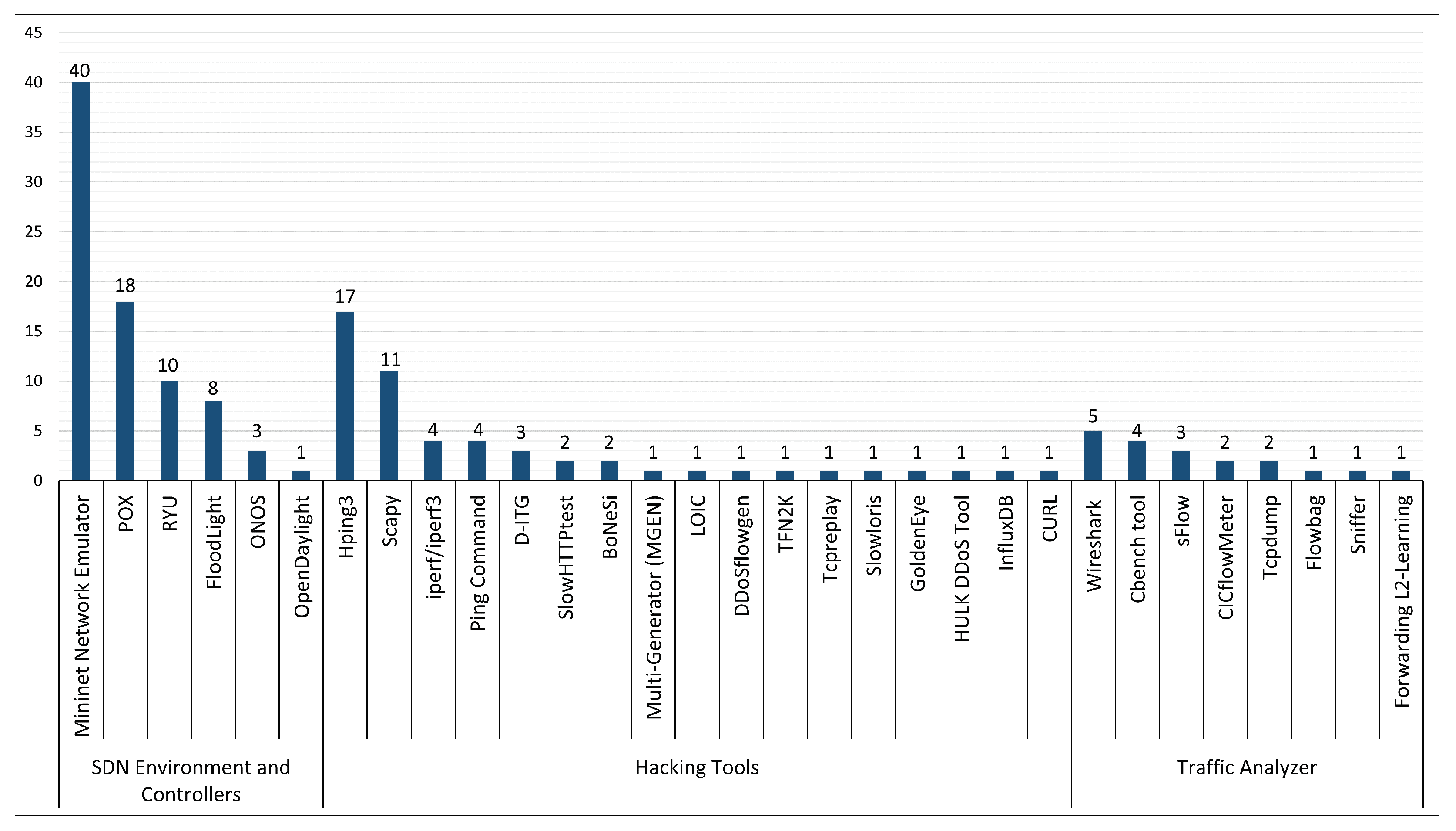
5.4.1. Network Simulator and Tools
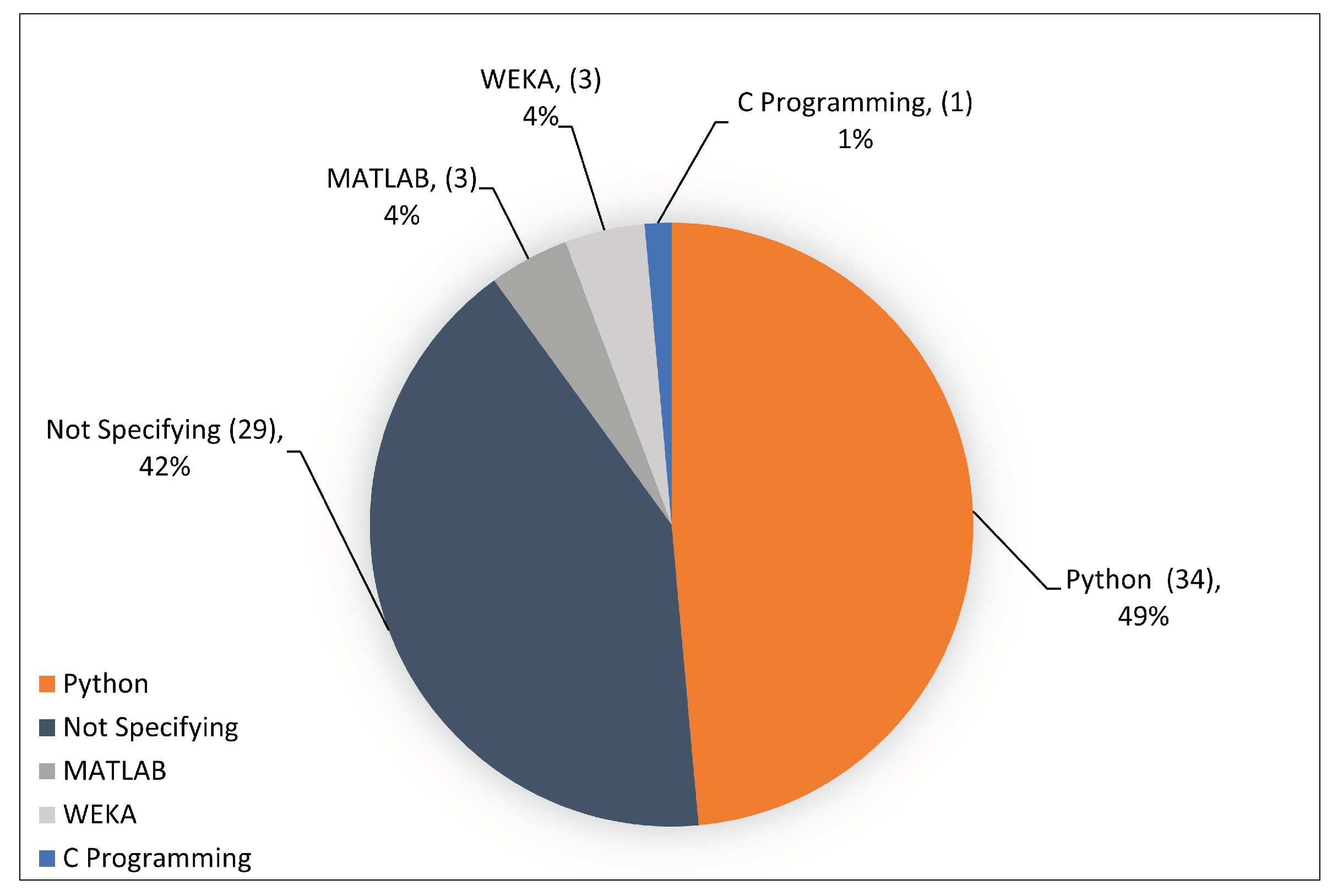
5.4.2. Experimental Platforms
5.4.3. Evaluation Metrics
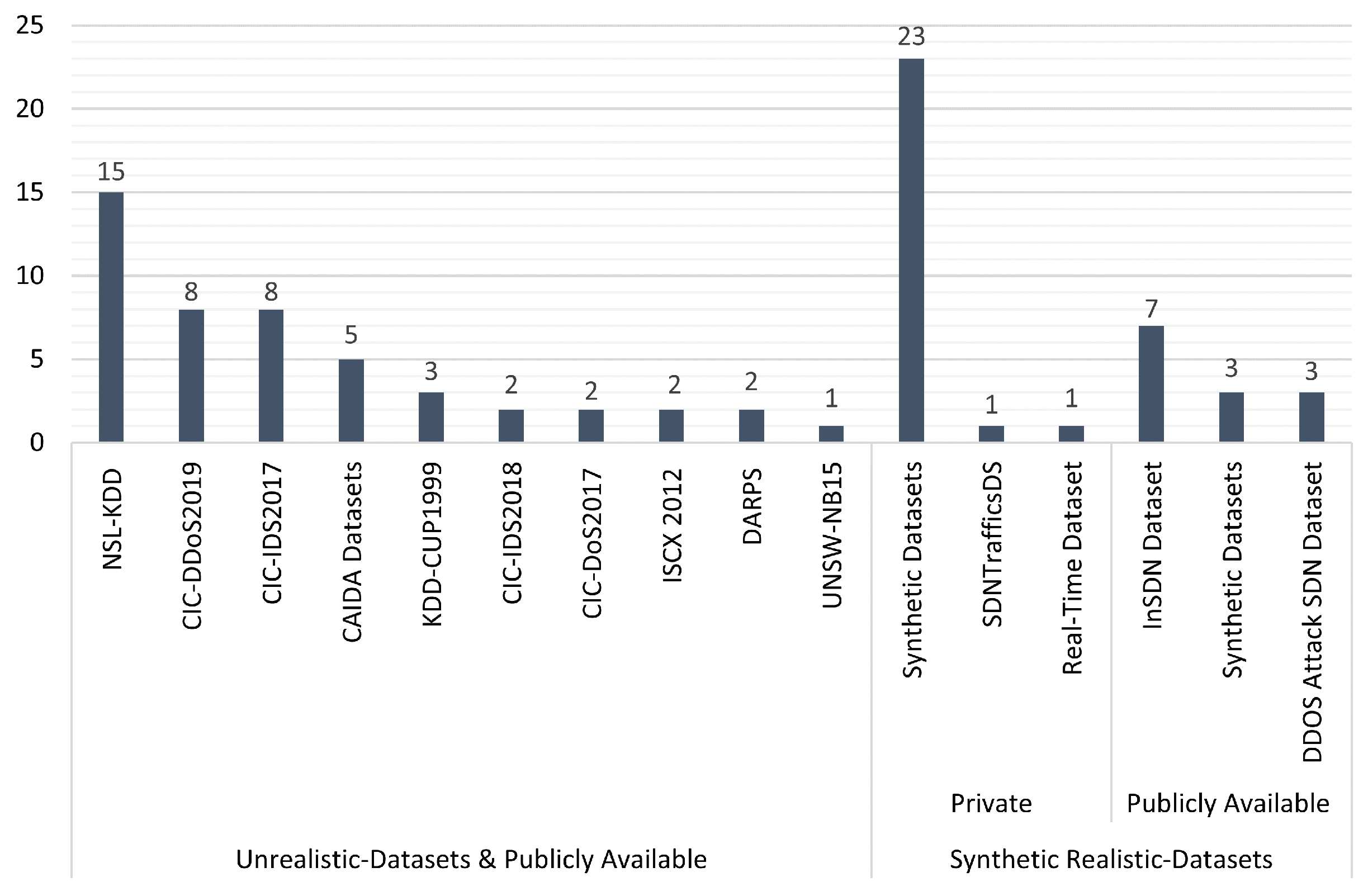
5.5. RQ(5). What Datasets Are Used to Evaluate and Validate the Existing Approaches, and Are There Any Publicly Available Realistic Datasets for DDoS Attacks on SDN Networks?
5.6. RQ(6). What Are the Challenges, Open-Issue Perspectives, and Future Research Directions for DDoS Attacks on SDN Networks?
5.6.1. Security Challenges
- DDoS attacks against SDN controllers: This SLR argues that DDoS attacks against SDN controllers can be classified as “global impact” attacks since they could cause the failure of the entire network. Many approaches, such as [63,67,80,102,104,112,113,120], are designed to detect DDoS attacks on SDN controllers since the controller is an essential component of the SDN network, providing critical functionality and network management authority. It is responsible for coordinating and managing network traffic flows, implementing network configuration, and installing forwarding rules on the data plane devices. Consequently, it becomes an enticing target for attackers to attempt DDoS attacks. Thus, DDoS attacks against SDN controllers remain an open security challenge that needs consideration.
- Availability of realistic datasets: This SLR notes that most researchers used self-generated datasets using different hacking tools, network simulators, and various experimental platforms. At the same time, few researchers still rely on the existing unrealistic benchmark datasets, such as NSL-KDD, CIC-DDoS2019, and KDD-CUP1999, to train and evaluate their approaches, even though the datasets do not reflect the characteristics of an SDN network environment and do not represent flow-based SDN architecture adequately. Finally, some researchers contribute realistic synthetic datasets by publicly making them available [126,130,131]. The variety of datasets utilized results in the research community finding it challenging to compare their works with others [129]. Therefore, the availability of a realistic SDN dataset remains an open research challenge that needs addressing.
- Distributed SDN controllers: This SLR remarked that the security approaches proposed in most literature studies are based on a topology with a single network controller, such as [69,75,77,86,113]. However, this topology is vulnerable to single points of failure in the case of DDoS attacks. In contrast, a network with distributed controllers in a flat or hierarchical design is much more efficient in load distribution, consistency, and scalability. In addition, as the severity of DDoS attacks increases, these distributed controllers can maintain network efficiency whenever the central controller becomes a bottleneck. They can reduce the impact of DDoS attacks and communication overhead, eliminate single points of failure, and ease the load balancer’s traffic flow among multiple controllers. Therefore, the operation of distributed SDN controllers remains an open security challenge that needs further investigation.
- High-rate and low-rate DDoS attacks: This SLR highlights that most approaches in literature studies detect and mitigate high-rate DDoS attacks with high accuracy and a low false-positive rate. High-rate DDoS attacks are easy to predict due to a noticeable increase in the attack traffic volume in the flow. However, in recent years, a different type of DDoS attack has surfaced, known as low-rate or stealthy attacks, which are very challenging to detect and mitigate with high detection accuracy and low false-positive rates due to the similarity of attack traffic flow with legitimate network traffic flow. Some studies, such as [74,86], try to detect low-rate DDoS attacks, but only achieve low performance. Therefore, detecting and mitigating low-rate DDoS attacks with high accuracy and a low false-positive rate remains an open research challenge that needs addressing.
- Deployment of detection approaches: This SLR found that most literature studies deployed their approaches at the SDN controller, such as [82,91,102,103,104,106,111]. The main reason is that the forwarding switches send normal and abnormal traffic flows to the controller for attack detection or requesting new forwarding rules. Furthermore, the controller needs to regularly collect and monitor the network flow statistics, which could add communication overhead and interrupt the detection process. Typically, the SDN architecture experience overload while detecting and mitigating SDN DDoS attacks; therefore, an efficient approach must be implemented outside the SDN controller to address these challenges and reduce the controller’s overhead. If implemented this way, the proposed approach for detecting and mitigating SDN DDoS attacks must cooperate with the controller and the data plane switches.
- Prevention approach for DDoS attacks: This SLR demonstrated that most literature studies, such as [59,66,70,74,75,76,77,81,84,90,92,95,106,109,112,113,114,118,126] focus on detection and mitigation instead of prevention of SDN DDoS attacks. There is a lack of approaches concerning prevention besides the detection and mitigation approaches. Preventing DDoS attacks protects the SDN network’s functionality from deteriorating, which is more urgent than detecting and mitigating them by stopping their propagation into the network and consuming its resources. Therefore, DDoS attacks’ prevention, detection, and mitigation are still an open research challenge that needs addressing.
- Feature-selection techniques and hyper-parameter tuning: This SLR highlights that most literature studies, such as [61,67,77,87,95,97,102,109,122,125,127] use various feature selection techniques to select the most relevant network traffic features. A thorough feature selection process significantly enhances the ML-DL approach’s performance. Thus, feature selection techniques warrant further investigation using other strategies that could further improve ML and DL-based approaches. In addition, it is essential to hyper-tune the ML and DL models to obtain the best parameters for practical training and avoid negative impacts. Through hyper-parameters, the ML and DL models perform well when the hyper-parameters are tuned or optimized. Therefore, the feasibility of incorporating novel feature selection techniques and hyper-parameters to improve ML-DL-based detection, mitigation, or prevention of SDN DDoS attacks remains an open research challenge that needs addressing.
5.6.2. Future Research Directions
- Towards DL-based approaches: This SLR studied and analyzed the three most popular approaches (i.e., ML, DL, and hybrid) to detect and mitigate SDN DDoS attacks. However, the trend is shifting towards the DL-based approach according to the amount of interest it has generated within the research community in recent years. The most crucial benefit of DL over classic ML is higher performance in analyzing massive datasets. Moreover, several technologies, such as cloud computing and IoT systems, have adopted SDN technology to handle enormous amounts of data that needs to be processed [132]. Hence, DL-based approaches and techniques naturally fit into SDN and emerging technologies since their computational architecture already includes many processing layers that can train data at different grades of complexity. Therefore, the outcomes or new findings in DL-based research have a promising future for incorporation into SDN security approaches.
- Towards P4-programmed switches: We noticed from the literature reviewed that all researchers used default OpenFlow-enabled switches in their studies, except for [65], who employed programmable switches to work with a dynamic and flexible network. Utilizing P4-programmed switches within the SDN architecture could lower the controller’s overhead in case of DDoS attacks. Therefore, it is one of the promising future research directions for SDN network security defense approaches.
6. Conclusions and Limitations
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A. Quality Assessment (QA) Criterion
| Ref. | Study ID | Design | Conduct | Analysis | Conclusion | Total Score | QA Studies Level | |||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | High | Medium | Low | |||
| [59] | S1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1.5 | 8.5 | ✓ | ✗ | ✗ |
| [60] | S2 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0 | 6 | ✓ | ✗ | ✗ |
| [61] | S3 | 0.5 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0 | 5.5 | ✗ | ✓ | ✗ |
| [62] | S4 | 0.5 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0.5 | 0 | 5 | ✗ | ✓ | ✗ |
| [63] | S5 | 1 | 1 | 1 | 1 | 0.5 | 1 | 1 | 1 | 0.5 | 8 | ✓ | ✗ | ✗ |
| [64] | S6 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0.5 | 0 | 5.5 | ✗ | ✓ | ✗ |
| [65] | S7 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0.5 | 6.5 | ✓ | ✗ | ✗ |
| [66] | S8 | 1 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 7 | ✓ | ✗ | ✗ |
| [67] | S9 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0.5 | 6.5 | ✓ | ✗ | ✗ |
| [68] | S10 | 1 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 7 | ✓ | ✗ | ✗ |
| [69] | S11 | 1 | 1 | 1 | 1 | 0.5 | 1 | 1 | 0.5 | 0.5 | 7.5 | ✓ | ✗ | ✗ |
| [70] | S12 | 1 | 1 | 1 | 1 | 1 | 0.5 | 1 | 0.5 | 0.5 | 7.5 | ✓ | ✗ | ✗ |
| [71] | S13 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0 | 0 | 5.5 | ✗ | ✓ | ✗ |
| [72] | S14 | 0.5 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0 | 0 | 4.5 | ✗ | ✗ | ✓ |
| [73] | S15 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0.5 | 6.5 | ✓ | ✗ | ✗ |
| [74] | S16 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 1 | 0.5 | 0.5 | 7 | ✓ | ✗ | ✗ |
| [75] | S17 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0.5 | 6.5 | ✓ | ✗ | ✗ |
| [76] | S18 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 1 | 0.5 | 0.5 | 7 | ✓ | ✗ | ✗ |
| [77] | S19 | 1 | 1 | 1 | 1 | 0.5 | 1 | 1 | 0.5 | 0.5 | 7.5 | ✓ | ✗ | ✗ |
| [78] | S20 | 0.5 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0 | 0 | 4.5 | ✗ | ✗ | ✓ |
| [79] | S21 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 8 | ✓ | ✗ | ✗ |
| [80] | S22 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0.5 | 6.5 | ✓ | ✗ | ✗ |
| [81] | S23 | 0.5 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0 | 5.5 | ✗ | ✓ | ✗ |
| [82] | S24 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 8 | ✓ | ✗ | ✗ |
| [83] | S25 | 0.5 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0.5 | 0 | 5 | ✗ | ✓ | ✗ |
| [84] | S26 | 0.5 | 0.5 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0.5 | 0 | 4.5 | ✗ | ✗ | ✓ |
| [85] | S27 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0 | 6 | ✓ | ✗ | ✗ |
| [86] | S28 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 1 | 7 | ✓ | ✗ | ✗ |
| [87] | S29 | 1 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 7 | ✓ | ✗ | ✗ |
| [88] | S30 | 0.5 | 1 | 1 | 0 | 0.5 | 0.5 | 0.5 | 0 | 0 | 4 | ✗ | ✗ | ✓ |
| [89] | S31 | 1 | 1 | 1 | 1 | 0.5 | 1 | 1 | 0.5 | 0.5 | 7.5 | ✓ | ✗ | ✗ |
| [90] | S32 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 1 | 1 | 0.5 | 7.5 | ✓ | ✗ | ✗ |
| [91] | S33 | 1 | 1 | 1 | 1 | 0.5 | 1 | 1 | 0.5 | 0 | 7 | ✓ | ✗ | ✗ |
| [92] | S34 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0.5 | 6.5 | ✓ | ✗ | ✗ |
| [93] | S35 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0 | 0 | 5.5 | ✗ | ✓ | ✗ |
| [94] | S36 | 1 | 1 | 1 | 1 | 0.5 | 1 | 1 | 0.5 | 1 | 8 | ✓ | ✗ | ✗ |
| [95] | S37 | 1 | 1 | 1 | 1 | 0.5 | 1 | 1 | 0.5 | 1 | 8 | ✓ | ✗ | ✗ |
| [96] | S38 | 1 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 7 | ✓ | ✗ | ✗ |
| [97] | S39 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0.5 | 0 | 5.5 | ✗ | ✓ | ✗ |
| [98] | S40 | 0.5 | 1 | 1 | 0.5 | 0.5 | 1 | 1 | 0 | 0 | 4.5 | ✗ | ✗ | ✓ |
| [99] | S41 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0.5 | 6.5 | ✓ | ✗ | ✗ |
| [100] | S42 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 1 | 1 | 0.5 | 7.5 | ✓ | ✗ | ✗ |
| [101] | S43 | 0.5 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0 | 5.5 | ✗ | ✓ | ✗ |
| [102] | S44 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0 | 0 | 5.5 | ✗ | ✓ | ✗ |
| [103] | S45 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0.5 | 6.5 | ✓ | ✗ | ✗ |
| [104] | S46 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0.5 | 0.5 | 6 | ✓ | ✗ | ✗ |
| [105] | S47 | 1 | 1 | 1 | 1 | 0.5 | 1 | 0.5 | 0.5 | 0.5 | 7 | ✓ | ✗ | ✗ |
| [106] | S48 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 1 | 0 | 6.5 | ✓ | ✗ | ✗ |
| [107] | S49 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0.5 | 6.5 | ✓ | ✗ | ✗ |
| [108] | S50 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0.5 | 6.5 | ✓ | ✗ | ✗ |
| [109] | S51 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 8 | ✓ | ✗ | ✗ |
| [110] | S52 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0.5 | 6.5 | ✓ | ✗ | ✗ |
| [111] | S53 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 8 | ✓ | ✗ | ✗ |
| [112] | S54 | 1 | 1 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 7.5 | ✓ | ✗ | ✗ |
| [113] | S55 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 8 | ✓ | ✗ | ✗ |
| [114] | S56 | 0.5 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0 | 0 | 4.5 | ✗ | ✗ | ✓ |
| [115] | S57 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0.5 | 6.5 | ✓ | ✗ | ✗ |
| [116] | S58 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0 | 6 | ✓ | ✗ | ✗ |
| [117] | S59 | 0.5 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0 | 0 | 4.5 | ✗ | ✗ | ✓ |
| [118] | S60 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0 | 0 | 5.5 | ✗ | ✓ | ✗ |
| [119] | S61 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0 | 6 | ✓ | ✗ | ✗ |
| [120] | S62 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0.5 | 6.5 | ✓ | ✗ | ✗ |
| [121] | S63 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0.5 | 0 | 5.5 | ✗ | ✓ | ✗ |
| [122] | S64 | 0.5 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0 | 0 | 4.5 | ✗ | ✗ | ✓ |
| [123] | S65 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 9 | ✓ | ✗ | ✗ |
| [124] | S66 | 1 | 1 | 1 | 1 | 0.5 | 1 | 1 | 0.5 | 0.5 | 7.5 | ✓ | ✗ | ✗ |
| [125] | S67 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0 | 0.5 | 5.5 | ✗ | ✓ | ✗ |
| [126] | S68 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0.5 | 6.5 | ✓ | ✗ | ✗ |
| [127] | S69 | 1 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 7 | ✓ | ✗ | ✗ |
| [128] | S70 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0 | 0 | 5.5 | ✗ | ✓ | ✗ |
References
- Singh, M.P.; Bhandari, A. New-flow based DDoS attacks in SDN: Taxonomy, rationales, and research challenges. Comput. Commun. 2020, 154, 509–527. [Google Scholar] [CrossRef]
- Al-Amiedy, T.A.; Anbar, M.; Belaton, B.; Bahashwan, A.A.; Hasbullah, I.H.; Aladaileh, M.A.; Mukhaini, G.A. A systematic literature review on attacks defense mechanisms in RPL-based 6LoWPAN of Internet of Things. Internet Things 2023, 22, 100741. [Google Scholar] [CrossRef]
- Casado, M.; Garfinkel, T.; Akella, A.; Freedman, M.J.; Boneh, D.; McKeown, N.; Shenker, S. SANE: A Protection Architecture for Enterprise Networks. In Proceedings of the 15th USENIX Security Symposium, Vancouver, BC, Canada, 31 July–4 August 2006; Volume 49, pp. 137–151. [Google Scholar]
- Scott-Hayward, S.; Natarajan, S.; Sezer, S. A Survey of Security in Software Defined Networks. IEEE Commun. Surv. Tutor. 2016, 18, 623–654. [Google Scholar] [CrossRef]
- McKeown, N.; Anderson, T.; Balakrishnan, H.; Parulkar, G.; Peterson, L.; Rexford, J.; Shenker, S.; Turner, J. OpenFlow: Enabling Innovation in Campus Networks. ACM SIGCOMM Comput. Commun. Rev. 2008, 38, 69–74. [Google Scholar] [CrossRef]
- Cui, J.; Wang, M.; Luo, Y.; Zhong, H. DDoS detection and defense mechanism based on cognitive-inspired computing in SDN. Future Gener. Comput. Syst. 2019, 97, 275–283. [Google Scholar] [CrossRef]
- Nygren, A.; Pfaff, B.; Lantz, B.; Heller, B.; Barker, C.; Beckmann, C.; Cohn, D.; Malek, D.; Talayco, D.; Erickson, D.; et al. Openflow Switch Specification Version 1.5. 1; Open Networking Foundation: Palo Alto, CA, USA, 2015. [Google Scholar]
- Singh, J.; Sunny, B. Detection and mitigation of DDoS attacks in SDN: A comprehensive review, research challenges and future directions. Comput. Sci. Rev. 2020, 37, 100279. [Google Scholar] [CrossRef]
- Aladaileh, M.A.; Anbar, M.; Hintaw, A.J.; Hasbullah, I.H.; Bahashwan, A.A.; Al-Amiedy, T.A.; Ibrahim, D.R. Effectiveness of an Entropy-Based Approach for Detecting Low-and High-Rate DDoS Attacks against the SDN Controller: Experimental Analysis. Appl. Sci. 2023, 13, 775. [Google Scholar] [CrossRef]
- Kaur, S.; Kumar, K.; Aggarwal, N.; Singh, G. A comprehensive survey of DDoS defense solutions in SDN: Taxonomy, research challenges, and future directions. Comput. Secur. 2021, 110, 102423. [Google Scholar] [CrossRef]
- Dalmazo, B.L.; Marques, J.A.; Costa, L.R.; Bonfim, M.S.; Carvalho, R.N.; da Silva, A.S.; Fernandes, S.; Bordim, J.L.; Alchieri, E.; Schaeffer-Filho, A.; et al. A systematic review on distributed denial of service attack defense mechanisms in programmable networks. Int. J. Netw. Manag. 2021, 31, e2163. [Google Scholar] [CrossRef]
- Alashhab, A.A.; Zahid, M.S.M.; Azim, M.A.; Daha, M.Y.; Isyaku, B.; Ali, S. A Survey of Low Rate DDoS Detection Techniques Based on Machine Learning in Software-Defined Networks. Symmetry 2022, 14, 1563. [Google Scholar] [CrossRef]
- Alhijawi, B.; Almajali, S.; Elgala, H.; Bany Salameh, H.; Ayyash, M. A survey on DoS/DDoS mitigation techniques in SDNs: Classification, comparison, solutions, testing tools and datasets. Comput. Electr. Eng. 2022, 99, 107706. [Google Scholar] [CrossRef]
- Ali, T.E.; Chong, Y.W.; Manickam, S. Machine Learning Techniques to Detect a DDoS Attack in SDN: A Systematic Review. Appl. Sci. 2023, 13, 3183. [Google Scholar] [CrossRef]
- Al-Mashhadi, S.; Anbar, M.; Jalal, R.A.; Al-Ani, A. Design of cloud computing load balance system based on SDN technology. In Proceedings of the Computational Science and Technology 2019 (ICCST2019), Kota Kinabalu, Malaysia, 29–30 August 2019; pp. 123–133. [Google Scholar] [CrossRef]
- Bahashwan, A.A.; Anbar, M.; Abdullah, N. New architecture design of cloud computing using software defined networking and network function virtualization technology. In Proceedings of the International Conference of Reliable Information and Communication Technology, Johor, Malaysia, 22–23 September 2019; pp. 705–713. [Google Scholar] [CrossRef]
- Kreutz, D.; Ramos, F.M.; Verissimo, P.E.; Rothenberg, C.E.; Azodolmolky, S.; Uhlig, S. Software-defined networking: A comprehensive survey. Proc. IEEE 2015, 103, 14–76. [Google Scholar] [CrossRef]
- Cui, Y.; Qian, Q.; Guo, C.; Shen, G.; Tian, Y.; Xing, H.; Yan, L. Towards DDoS detection mechanisms in software-defined networking. J. Netw. Comput. Appl. 2021, 190, 103156. [Google Scholar] [CrossRef]
- Paliwal, M.; Shrimankar, D.; Tembhurne, O. Controllers in SDN: A review report. IEEE Access 2018, 6, 36256–36270. [Google Scholar] [CrossRef]
- Richardson, L.; Ruby, S. RESTful Web Services; O’Reilly Media, Inc.: Sebastopol, CA, USA, 2008. [Google Scholar]
- POX. Installing POX—POX Manual Current Documentation. 2008. Available online: https://noxrepo.github.io/pox-doc/html/ (accessed on 26 July 2022).
- Gude, N.; Koponen, T.; Pettit, J.; Pfaff, B.; Casado, M.; McKeown, N.; Shenker, S. NOX: Towards an operating system for networks. ACM SIGCOMM Comput. Commun. Rev. 2008, 38, 105–110. [Google Scholar] [CrossRef]
- Floodlight. Floodlight Controller—Confluence. 2018. Available online: https://floodlight.atlassian.net/wiki/spaces/floodlightcontroller/overview (accessed on 26 July 2022).
- OpenDaylight. Home—OpenDaylight platform (ODL). Available online: https://www.opendaylight.org/ (accessed on 26 July 2022).
- Xia, W.; Wen, Y.; Foh, C.H.; Niyato, D.; Xie, H. A survey on software-defined networking. IEEE Commun. Surv. Tutor. 2015, 17, 27–51. [Google Scholar] [CrossRef]
- Aladaileh, M.A.; Anbar, M.; Hasbullah, I.H.; Sanjalawe, Y.K. Information theory-based approaches to detect DDoS attacks on software-defined networking controller a review. Int. J. Educ. Inf. Technol. 2021, 15, 83–94. [Google Scholar] [CrossRef]
- Jarraya, Y.; Madi, T.; Debbabi, M. A survey and a layered taxonomy of software-defined networking. IEEE Commun. Surv. Tutor. 2014, 16, 1955–1980. [Google Scholar] [CrossRef]
- Mousavi, S.M.; Marc, S. Early detection of DDoS attacks against SDN controllers. In Proceedings of the 2015 International Conference on Computing, Networking and Communications (ICNC), Garden Grove, CA, USA, 16–19 February 2015; pp. 77–81. [Google Scholar] [CrossRef]
- ur Rasool, R.; Wang, H.; Ashraf, U.; Ahmed, K.; Anwar, Z.; Rafique, W. A survey of link flooding attacks in software defined network ecosystems. J. Netw. Comput. Appl. 2020, 172, 102803. [Google Scholar] [CrossRef]
- Berde, P.; Gerola, M.; Hart, J.; Higuchi, Y.; Kobayashi, M.; Koide, T.; Lantz, B.; O’Connor, B.; Radoslavov, P.; Snow, W.; et al. ONOS: Towards an Open, Distributed SDN OS. In Proceedings of the Third Workshop on Hot Topics in Software Defined Networking, Chicago, IL, USA, 22 August 2014; pp. 1–6. [Google Scholar] [CrossRef]
- Latif, Z.; Sharif, K.; Li, F.; Karim, M.M.; Biswas, S.; Wang, Y. A comprehensive survey of interface protocols for software defined networks. J. Netw. Comput. Appl. 2020, 156, 102563. [Google Scholar] [CrossRef]
- Pfaff, B.; Davie, B. The Open Vswitch Database Management Protocol. Technical Report, RFC 7047. Available online: http://www.ietf.org/rfc/rfc7047.txt (accessed on 11 August 2022).
- Bianchi, G.; Bonola, M.; Capone, A.; Cascone, C. Openstate: Programming platform-independent stateful openflow applications inside the switch. ACM SIGCOMM Comput. Commun. Rev. 2014, 44, 44–51. [Google Scholar] [CrossRef]
- Smith, M.; Dvorkin, M.; Laribi, Y.; Pandey, V.; Garg, P.; Weidenbacher, N. OpFlex Control Protocol. Technical Report, IETF Internet Draft. Available online: https://datatracker.ietf.org/doc/draft-smith-opflex/03/ (accessed on 26 August 2022).
- Zubaydi, H.D.; Anbar, M.; Wey, C.Y. Review on detection techniques against DDoS attacks on a software-defined networking controller. In Proceedings of the 2017 Palestinian International Conference on Information and Communication Technology (PICICT), Gaza, Palestine, 8–9 May 2017; pp. 10–16. [Google Scholar] [CrossRef]
- Li, Q.; Liu, Y.; Zhu, Z.; Li, H.; Jiang, Y. BOND: Flexible failure recovery in software defined networks. Comput. Netw. 2019, 149, 1–12. [Google Scholar] [CrossRef]
- Al-Ani, A.; Anbar, M.; Laghari, S.A.; Al-Ani, A.K. Mechanism to prevent the abuse of IPv6 fragmentation in OpenFlow networks. PLoS ONE 2020, 15. [Google Scholar] [CrossRef]
- Wazirali, R.; Ahmad, R.; Alhiyari, S. SDN-openflow topology discovery: An overview of performance issues. Appl. Sci. 2021, 11, 6999. [Google Scholar] [CrossRef]
- Klein, D.; Jarschel, M. An OpenFlow extension for the OMNeT++ INET framework. In Proceedings of the 6th International ICST Conference on Simulation Tools and Techniques, Cannes, France, 5 March 2013; pp. 322–329. [Google Scholar]
- Benton, K.; Camp, L.J.; Small, C. OpenFlow Vulnerability Assessment. In Proceedings of the Second ACM SIGCOMM Workshop on Hot Topics in Software Defined Networking, Hong Kong, China, 16 August 2013; pp. 151–152. [Google Scholar] [CrossRef]
- Aladaileh, M.A.; Anbar, M.; Hasbullah, I.H.; Chong, Y.W.; Sanjalawe, Y.K. Detection techniques of distributed denial of service attacks on software-defined networking controller—A review. IEEE Access 2020, 8, 143985–143995. [Google Scholar] [CrossRef]
- Valdovinos, I.A.; Pérez-Díaz, J.A.; Choo, K.K.R.; Botero, J.F. Emerging DDoS attack detection and mitigation strategies in software-defined networks: Taxonomy, challenges and future directions. J. Netw. Comput. Appl. 2021, 187, 103093. [Google Scholar] [CrossRef]
- Yan, Q.; Yu, F.R.; Gong, Q.; Li, J. Software-Defined Networking (SDN) and Distributed Denial of Service (DDoS) Attacks in Cloud Computing Environments: A Survey, Some Research Issues, and Challenges. IEEE Commun. Surv. Tutor. 2015, 18, 602–622. [Google Scholar] [CrossRef]
- Aladaileh, M.A.; Anbar, M.; Iznan, H. Hasbullah, A.A.B.; Al-Sarawn, S. Dynamic Threshold-Based Approach to Detect Low-Rate DDoS Attacks on Software-Defined Networking Controller. Comput. Mater. Contin. 2022, 73, 1403–1416. [Google Scholar] [CrossRef]
- Aladaileh, M.A.; Anbar, M.; Hintaw, A.J.; Hasbullah, I.H.; Bahashwan, A.A.; Al-Sarawi, S. Renyi Joint Entropy-Based Dynamic Threshold Approach to Detect DDoS Attacks against SDN Controller with Various Traffic Rates. Appl. Sci. 2022, 12, 6127. [Google Scholar] [CrossRef]
- Mousavi, S.M.; St-Hilaire, M. Early detection of DDoS attacks against software defined network controllers. J. Netw. Syst. Manag. 2018, 26, 573–591. [Google Scholar] [CrossRef]
- Bahashwan, A.A.; Anbar, M.; Hanshi, S.M. Overview of IPv6 based DDoS and DoS attacks detection mechanisms. In Proceedings of the Advances in Cyber Security: First International Conference, ACeS 2019, Penang, Malaysia, 30 July–1 August 2019; pp. 153–167. [Google Scholar]
- Ahmed, M.; Shatabda, S.; Islam, A.K.M.; Robin, M.; Islam, T. Intrusion Detection System in Software-Defined Networks Using Machine Learning and Deep Learning Techniques—A Comprehensive Survey. TechRxiv, 2021; 1–44. [Google Scholar] [CrossRef]
- Ahmad, Z.; Shahid Khan, A.; Wai Shiang, C.; Abdullah, J.; Ahmad, F. Network intrusion detection system: A systematic study of machine learning and deep learning approaches. Trans. Emerg. Telecommun. Technol. 2021, 32, e4150. [Google Scholar] [CrossRef]
- Liu, H.; Lang, B. Machine Learning and Deep Learning Methods for Intrusion Detection Systems: A Survey. Appl. Sci. 2019, 9, 4396. [Google Scholar] [CrossRef]
- Elejla, O.E.; Anbar, M.; Hamouda, S.; Faisal, S.; Bahashwan, A.A.; Hasbullah, I.H. Deep-Learning-Based Approach to Detect ICMPv6 Flooding DDoS Attacks on IPv6 Networks. Appl. Sci. 2022, 12, 6150. [Google Scholar] [CrossRef]
- Kitchenham, B. Procedures for Performing Systematic Reviews. Keele 2004, 33, 1–26. [Google Scholar]
- Kitchenham, B.; Pearl Brereton, O.; Budgen, D.; Turner, M.; Bailey, J.; Linkman, S. Systematic literature reviews in software engineering—A systematic literature review. Inf. Softw. Technol. 2009, 51, 7–15. [Google Scholar] [CrossRef]
- Busalim, A.H.; Hussin, A.R.C. Understanding social commerce: A systematic literature review and directions for further research. Int. J. Inf. Manag. 2016, 36, 1075–1088. [Google Scholar] [CrossRef]
- Brereton, P.; Kitchenham, B.A.; Budgen, D.; Turner, M.; Khalil, M. Lessons from applying the systematic literature review process within the software engineering domain. J. Syst. Softw. 2007, 80, 571–583. [Google Scholar] [CrossRef]
- Kitchenham, B.; Charters, S.M. Guidelines for Performing Systematic Literature Reviews in Software Engineering; Technical Report, ver. 2.3; Keele University: Keele, UK, 2007. [Google Scholar]
- Baabad, A.; Zulzalil, H.B.; Hassan, S.; Baharom, S.B. Software Architecture Degradation in Open Source Software: A Systematic Literature Review. IEEE Access 2020, 8, 173681–173709. [Google Scholar] [CrossRef]
- Binbeshr, F.; Kiah, M.M.; Por, L.Y.; Zaidan, A.A. A systematic review of PIN-entry methods resistant to shoulder-surfing attacks. Comput. Secur. 2021, 101, 102116. [Google Scholar] [CrossRef]
- Maheshwari, A.; Mehraj, B.; Khan, M.S.; Idrisi, M.S. An optimized weighted voting based ensemble model for DDoS attack detection and mitigation in SDN environment. Microprocess. Microsyst. 2022, 89, 104412. [Google Scholar] [CrossRef]
- Swami, R.; Dave, M.; Ranga, V. Voting-based intrusion detection framework for securing software-defined networks. Concurr. Comput. Pract. Exp. 2020, 32, e5927. [Google Scholar] [CrossRef]
- Firdaus, D.; Munadi, R.; Purwanto, Y. DDoS Attack Detection in Software Defined Network using Ensemble K-means++ and Random Forest. In Proceedings of the 2020 3rd International Seminar on Research of Information Technology and Intelligent Systems (ISRITI), Yogyakarta, Indonesia, 10–11 December 2020; pp. 164–169. [Google Scholar] [CrossRef]
- Deepa, V.; Sudar, K.M.; Deepalakshmi, P. Design of Ensemble Learning Methods for DDoS Detection in SDN Environment. In Proceedings of the 2019 International Conference on Vision Towards Emerging Trends in Communication and Networking (ViTECoN), Vellore, India, 30–31 March 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Ahuja, N.; Singal, G.; Mukhopadhyay, D.; Kumar, N. Automated DDOS attack detection in software defined networking. J. Netw. Comput. Appl. 2021, 187, 103108. [Google Scholar] [CrossRef]
- Phan, T.V.; Bao, N.K.; Park, M. A Novel Hybrid Flow-Based Handler with DDoS Attacks in Software-Defined Networking. In Proceedings of the 2016 Intl IEEE Conferences on Ubiquitous Intelligence & Computing, Advanced and Trusted Computing, Scalable Computing and Communications, Cloud and Big Data Computing, Internet of People, and Smart World Congress (UIC/ATC/ScalCom/CBDCom/IoP/SmartWorld), Toulouse, France, 18–21 July 2016; pp. 350–357. [Google Scholar] [CrossRef]
- Musumeci, F.; Fidanci, A.C.; Paolucci, F.; Cugini, F.; Tornatore, M. Machine-Learning-enabled DDoS Attacks Detection in P4 Programmable Networks. J. Netw. Syst. Manag. 2022, 30, 1–27. [Google Scholar] [CrossRef]
- Nadeem, M.W.; Goh, H.G.; Ponnusamy, V.; Aun, Y. DDoS Detection in SDN using Machine Learning Techniques. Comput. Mater. Contin. 2022, 71, 771–789. [Google Scholar] [CrossRef]
- Swami, R.; Dave, M.; Ranga, V. Detection and Analysis of TCP-SYN DDoS Attack in Software-Defined Networking. Wirel. Pers. Commun. 2021, 118, 2295–2317. [Google Scholar] [CrossRef]
- Tonkal, O.; Polat, H.; Başaran, E.; Cömert, Z.; Kocaoğlu, R. Machine Learning Approach Equipped with Neighbourhood Component Analysis for DDoS Attack Detection in Software-Defined Networking. Electronics 2021, 10, 1227. [Google Scholar] [CrossRef]
- Sangodoyin, A.O.; Akinsolu, M.O.; Pillai, P.; Grout, V. Detection and Classification of DDoS Flooding Attacks on Software-Defined Networks: A Case Study for the Application of Machine Learning. IEEE Access 2021, 9, 122495–122508. [Google Scholar] [CrossRef]
- Sahoo, K.S.; Tripathy, B.K.; Naik, K.; Ramasubbareddy, S.; Balusamy, B.; Khari, M.; Burgos, D. An Evolutionary SVM Model for DDOS Attack Detection in Software Defined Networks. IEEE Access 2020, 8, 132502–132513. [Google Scholar] [CrossRef]
- Alamri, H.A.; Thayananthan, V. Analysis of Machine Learning for Securing Software-Defined Networking. Procedia Comput. Sci. 2021, 194, 229–236. [Google Scholar] [CrossRef]
- Sudar, K.; Beulah, M.; Deepalakshmi, P.; Nagaraj, P.; Chinnasamy, P. Detection of Distributed Denial of Service Attacks in SDN using Machine Learning Techniques. In Proceedings of the 2021 International Conference on Computer Communication and Informatics (ICCCI), Coimbatore, India, 27–29 January 2021; pp. 1–5. [Google Scholar] [CrossRef]
- Polat, H.; Polat, O.; Cetin, A. Detecting DDoS Attacks in Software-Defined Networks Through Feature Selection Methods and Machine Learning Models. Sustainability 2020, 12, 1035. [Google Scholar] [CrossRef]
- Pérez-Díaz, J.A.; Valdovinos, I.A.; Choo, K.K.R.; Zhu, D. A Flexible SDN-Based Architecture for Identifying and Mitigating Low-Rate DDoS Attacks Using Machine Learning. IEEE Access 2020, 8, 155859–155872. [Google Scholar] [CrossRef]
- Tan, L.; Pan, Y.; Wu, J.; Zhou, J.; Jiang, H.; Deng, Y. A New Framework for DDoS Attack Detection and Defense in SDN Environment. IEEE Access 2020, 8, 161908–161919. [Google Scholar] [CrossRef]
- Alamri, H.A.; Thayananthan, V. Bandwidth Control Mechanism and Extreme Gradient Boosting Algorithm for Protecting Software-Defined Networks Against DDoS Attacks. IEEE Access 2020, 8, 194269–194288. [Google Scholar] [CrossRef]
- Scaranti, G.F.; Carvalho, L.F.; Barbon, S.; Proença, M.L. Artificial Immune Systems and Fuzzy Logic to Detect Flooding Attacks in Software-Defined Networks. IEEE Access 2020, 8, 100172–100184. [Google Scholar] [CrossRef]
- Ahmad, A.; Harjula, E.; Ylianttila, M.; Ahmad, I. Evaluation of Machine Learning Techniques for Security in SDN. In Proceedings of the 2020 IEEE Globecom Workshops, Taipei, Taiwan, 7–11 December 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Satheesh, N.; Rathnamma, M.; Rajeshkumar, G.; Sagar, P.V.; Dadheech, P.; Dogiwal, S.; Velayutham, P.; Sengan, S. Flow-based anomaly intrusion detection using machine learning model with software defined networking for OpenFlow network. Microprocess. Microsyst. 2020, 79, 103285. [Google Scholar] [CrossRef]
- Santos, R.; Souza, D.; Santo, W.; Ribeiro, A.; Moreno, E. Machine Learning Algorithms to Detect DDoS Attacks in SDN. Concurr. Comput. Pract. Exp. 2020, 32, e5402. [Google Scholar] [CrossRef]
- Alshamrani, A.; Chowdhary, A.; Pisharody, S.; Lu, D.; Huang, D. A Defense System for Defeating DDoS Attacks in SDN Based Networks. In Proceedings of the 15th ACM International Symposium on Mobility Management and Wireless Access, Miami, FL, USA, 21–25 November 2017; pp. 83–92. [Google Scholar] [CrossRef]
- De Assis, M.V.; Novaes, M.P.; Zerbini, C.B.; Carvalho, L.F.; Abrãao, T.; Proença, M.L. Fast Defense System Against Attacks in Software Defined Networks. IEEE Access 2018, 6, 69620–69639. [Google Scholar] [CrossRef]
- Sahoo, K.S.; Iqbal, A.; Maiti, P.; Sahoo, B. A Machine Learning Approach for Predicting DDoS Traffic in Software Defined Networks. In Proceedings of the 2018 International Conference on Information Technology (ICIT), Bhubaneswar, India, 19–21 December 2018; pp. 199–203. [Google Scholar] [CrossRef]
- Nurwarsito, H.; Nadhif, M.F. DDoS Attack Early Detection and Mitigation System on SDN using Random Forest Algorithm and Ryu Framework. In Proceedings of the 2021 8th International Conference on Computer and Communication Engineering (ICCCE), Kuala Lumpur, Malaysia, 22–23 June 2021; pp. 178–183. [Google Scholar] [CrossRef]
- Oo, M.M.; Kamolphiwong, S.; Kamolphiwong, T.; Vasupongayya, S. Analysis of Features Dataset for DDoS Detection by using ASVM Method on Software Defined Networking. Int. J. Netw. Distrib. Comput. 2020, 8, 86–93. [Google Scholar] [CrossRef]
- Zhijun, W.; Qing, X.; Jingjie, W.; Meng, Y.; Liang, L. Low-Rate DDoS Attack Detection Based on Factorization Machine in Software Defined Network. IEEE Access 2020, 8, 17404–17418. [Google Scholar] [CrossRef]
- Myint Oo, M.; Kamolphiwong, S.; Kamolphiwong, T.; Vasupongayya, S. Advanced Support Vector Machine- (ASVM-) Based Detection for Distributed Denial of Service (DDoS) Attack on Software Defined Networking (SDN). J. Comput. Netw. Commun. 2019, 2019, 1–13. [Google Scholar] [CrossRef]
- RT, K.; Thamarai Selvi, S.; Govindarajan, K. DDoS detection and analysis in SDN-based environment using support vector machine classifier. In Proceedings of the 2014 Sixth International Conference on Advanced Computing (ICoAC), Chennai, India, 17–19 December 2014; pp. 205–210. [Google Scholar] [CrossRef]
- Wang, Y.; Hu, T.; Tang, G.; Xie, J.; Lu, J. SGS: Safe-Guard Scheme for Protecting Control Plane Against DDoS Attacks in Software-Defined Networking. IEEE Access 2019, 7, 34699–34710. [Google Scholar] [CrossRef]
- Xu, Y.; Sun, H.; Xiang, F.; Sun, Z. Efficient DDoS Detection Based on K-FKNN in Software Defined Networks. IEEE Access 2019, 7, 160536–160545. [Google Scholar] [CrossRef]
- Dong, S.; Sarem, M. DDoS Attack Detection Method Based on Improved KNN With the Degree of DDoS Attack in Software-Defined Networks. IEEE Access 2019, 8, 5039–5048. [Google Scholar] [CrossRef]
- Hannache, O.; Batouche, M. Neural Network-Based Approach for Detection and Mitigation of DDoS Attacks in SDN Environments. Int. J. Inf. Secur. Priv. (IJISP) 2020, 14, 50–71. [Google Scholar] [CrossRef]
- Yang, L.; Zhao, H. DDoS Attack Identification and Defense Using SDN Based on Machine Learning Method. In Proceedings of the 2018 15th International Symposium on Pervasive Systems, Algorithms and Networks (I-SPAN), Yichang, China, 16–18 October 2018; pp. 174–178. [Google Scholar] [CrossRef]
- Phan, T.V.; Bao, N.K.; Park, M. Distributed-SOM: A novel performance bottleneck handler for large-sized software-defined networks under flooding attacks. J. Netw. Comput. Appl. 2017, 91, 14–25. [Google Scholar] [CrossRef]
- Cui, Y.; Yan, L.; Li, S.; Xing, H.; Pan, W.; Zhu, J.; Zheng, X. SD-Anti-DDoS: Fast and efficient DDoS defense in software-defined networks. J. Netw. Comput. Appl. 2016, 68, 65–79. [Google Scholar] [CrossRef]
- Fatmah, A.; Kamal, J.; Fathy, E.; Maher, K.; Abdullah, B.; Khalid, A. Ensemble Deep Learning Models for Mitigating DDoS Attack in Software-Defined Network. Intell. Autom. Soft Comput. 2022, 33, 923–938. [Google Scholar] [CrossRef]
- Mbasuva, U.; Zodi, G.A.L. Designing Ensemble Deep Learning Intrusion Detection System for DDoS attacks in Software Defined Networks. In Proceedings of the 2022 16th International Conference on Ubiquitous Information Management and Communication (IMCOM), Seoul, Korea, 3–5 January 2022; pp. 1–8. [Google Scholar] [CrossRef]
- Haider, S.; Akhunzada, A.; Ahmed, G.; Raza, M. Deep Learning based Ensemble Convolutional Neural Network Solution for Distributed Denial of Service Detection in SDNs. In Proceedings of the 2019 UK/China Emerging Technologies (UCET), Glasgow, UK, 21–22 August 2019; pp. 1–4. [Google Scholar] [CrossRef]
- Abdallah, M.; An Le Khac, N.; Jahromi, H.; Delia Jurcut, A. A Hybrid CNN-LSTM Based Approach for Anomaly Detection Systems in SDNs. In Proceedings of the 16th International Conference on Availability, Reliability and Security, Vienna, Austria, 17–20 August 2021; pp. 1–7. [Google Scholar] [CrossRef]
- Haider, S.; Akhunzada, A.; Mustafa, I.; Patel, T.B.; Fernandez, A.; Choo, K.K.R.; Iqbal, J. A Deep CNN Ensemble Framework for Efficient DDoS Attack Detection in Software Defined Networks. IEEE Access 2020, 8, 53972–53983. [Google Scholar] [CrossRef]
- Nugraha, B.; Murthy, R.N. Deep Learning-based Slow DDoS Attack Detection in SDN-based Networks. In Proceedings of the 2020 IEEE Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN), Leganes, Spain, 10–12 November 2020; pp. 51–56. [Google Scholar] [CrossRef]
- Alshra’a, A.S.; Farhat, A.; Seitz, J. Deep learning algorithms for detecting denial of service attacks in software-defined networks. Procedia Comput. Sci. 2021, 191, 254–263. [Google Scholar] [CrossRef]
- Gadze, J.D.; Bamfo-Asante, A.A.; Agyemang, J.O.; Nunoo-Mensah, H.; Opare, K.A.B. An Investigation into the Application of Deep Learning in the Detection and Mitigation of DDOS Attack on SDN Controllers. Technologies 2021, 9, 14. [Google Scholar] [CrossRef]
- Elsayed, M.S.; Le-Khac, N.A.; Dev, S.; Jurcut, A.D. DDoSNet: A Deep-Learning Model for Detecting Network Attacks. In Proceedings of the 2020 IEEE 21st International Symposium on “A World of Wireless, Mobile and Multimedia Networks” (WoWMoM), Cork, Ireland, 31 August–3 September 2020; pp. 391–396. [Google Scholar] [CrossRef]
- Tang, T.A.; Mhamdi, L.; McLernon, D.; Zaidi, S.A.R.; Ghogho, M.; El Moussa, F. DeepIDS: Deep Learning Approach for Intrusion Detection in Software Defined Networking. Electronics 2020, 9, 1533. [Google Scholar] [CrossRef]
- Tang, T.A.; McLernon, D.; Mhamdi, L.; Zaidi, S.A.R.; Ghogho, M. Intrusion detection in sdn-based networks: Deep recurrent neural network approach. In Deep Learning Applications for Cyber Security; Springer: Berlin, Germany, 2019; pp. 175–195. [Google Scholar] [CrossRef]
- Li, C.; Wu, Y.; Yuan, X.; Sun, Z.; Wang, W.; Li, X.; Gong, L. Detection and defense of DDoS attack–based on deep learning in OpenFlow-based SDN. Int. J. Commun. Syst. 2018, 31, e3497. [Google Scholar] [CrossRef]
- Tang, T.A.; Mhamdi, L.; McLernon, D.; Zaidi, S.A.R.; Ghogho, M. Deep Recurrent Neural Network for Intrusion Detection in SDN-based Networks. In Proceedings of the 2018 4th IEEE Conference on Network Softwarization and Workshops (NetSoft), Montreal, QC, Canada, 25–29 June 2018; pp. 202–206. [Google Scholar] [CrossRef]
- Liu, Y.; Zhi, T.; Shen, M.; Wang, L.; Li, Y.; Wan, M. Software-defined DDoS detection with information entropy analysis and optimized deep learning. Future Gener. Comput. Syst. 2022, 129, 99–114. [Google Scholar] [CrossRef]
- Wang, H.; Li, W. DDosTC: A Transformer-Based Network Attack Detection Hybrid Mechanism in SDN. Sensors 2021, 21, 5047. [Google Scholar] [CrossRef] [PubMed]
- Janabi, A.H.; Kanakis, T.; Johnson, M. Convolutional Neural Network Based Algorithm for Early Warning Proactive System Security in Software Defined Networks. IEEE Access 2022, 10, 14301–14310. [Google Scholar] [CrossRef]
- Assis, M.V.; Carvalho, L.F.; Lloret, J.; Proença, M.L. A GRU deep learning system against attacks in software defined networks. J. Netw. Comput. Appl. 2021, 177, 102942. [Google Scholar] [CrossRef]
- Novaes, M.P.; Carvalho, L.F.; Lloret, J.; Proença, M.L. Adversarial Deep Learning approach detection and defense against DDoS attacks in SDN environments. Future Gener. Comput. Syst. 2021, 125, 156–167. [Google Scholar] [CrossRef]
- Ahuja, N.; Singal, G.; Mukhopadhyay, D. DLSDN: Deep Learning for DDOS attack detection in Software Defined Networking. In Proceedings of the 2021 11th International Conference on Cloud Computing, Data Science & Engineering (Confluence), Noida, India, 28–29 January 2021; pp. 683–688. [Google Scholar] [CrossRef]
- Elsayed, M.S.; Jahromi, H.Z.; Nazir, M.M.; Jurcut, A.D. The role of CNN for intrusion detection systems: An improved CNN learning approach for SDNs. In Proceedings of the International Conference on Future Access Enablers of Ubiquitous and Intelligent Infrastructures, Virtual Event, 6–7 May 2021; pp. 91–104. [Google Scholar] [CrossRef]
- Makuvaza, A.; Jat, D.S.; Gamundani, A.M. Deep neural network (DNN) solution for real-time detection of distributed denial of service (DDoS) attacks in software defined networks (SDNs). SN Comput. Sci. 2021, 2, 1–10. [Google Scholar] [CrossRef]
- Itagi, V.; Javali, M.; Madhukeshwar, H.; Shettar, P.; Somashekar, P.; Narayan, D. DDoS Attack Detection in SDN Environment using Bi-directional Recurrent Neural Network. In Proceedings of the 2021 IEEE International Conference on Distributed Computing, VLSI, Electrical Circuits and Robotics (DISCOVER), Nitte, India, 19–20 November 2021; pp. 123–128. [Google Scholar] [CrossRef]
- Liu, Y.; Dong, M.; Ota, K.; Li, J.; Wu, J. Deep Reinforcement Learning based Smart Mitigation of DDoS Flooding in Software-Defined Networks. In Proceedings of the 2018 IEEE 23rd International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), Barcelona, Spain, 17–19 September 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Arivudainambi, D.; KA, V.K.; Sibi Chakkaravarthy, S. LION IDS: A meta-heuristics approach to detect DDoS attacks against Software-Defined Networks. Neural Comput. Appl. 2019, 31, 1491–1501. [Google Scholar] [CrossRef]
- Niyaz, Q.; Sun, W.; Javaid, A.Y. A Deep Learning Based DDoS Detection System in Software-Defined Networking (SDN). ICST Trans. Secur. Saf. 2016, 4, 1–18. [Google Scholar] [CrossRef]
- Tang, T.A.; Mhamdi, L.; McLernon, D.; Zaidi, S.A.R.; Ghogho, M. Deep learning approach for Network Intrusion Detection in Software Defined Networking. In Proceedings of the 2016 International Conference on Wireless Networks and Mobile Communications (WINCOM), Fez, Morocco, 26–29 October 2016; pp. 258–263. [Google Scholar] [CrossRef]
- MohanaPriya, P.; Shalinie, S.M. Restricted Boltzmann Machine based detection system for DDoS attack in Software Defined Networks. In Proceedings of the 2017 Fourth International Conference on Signal Processing, Communication and Networking (ICSCN), Chennai, India, 16–18 March 2017; pp. 1–6. [Google Scholar] [CrossRef]
- ElSayed, M.S.; Le-Khac, N.A.; Albahar, M.A.; Jurcut, A. A novel hybrid model for intrusion detection systems in SDNs based on CNN and a new regularization technique. J. Netw. Comput. Appl. 2021, 191, 103160. [Google Scholar] [CrossRef]
- Yungaicela-Naula, N.M.; Vargas-Rosales, C.; Perez-Diaz, J.A. SDN-Based Architecture for Transport and Application Layer DDoS Attack Detection by Using Machine and Deep Learning. IEEE Access 2021, 9, 108495–108512. [Google Scholar] [CrossRef]
- Mhamdi, L.; McLernon, D.; El-Moussa, F.; Zaidi, S.A.R.; Ghogho, M.; Tang, T. A deep learning approach combining autoencoder with one-class SVM for DDoS attack detection in SDNs. In Proceedings of the 2020 IEEE Eighth International Conference on Communications and Networking (ComNet), Hammamet, Tunisia, 27–30 October 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Novaes, M.P.; Carvalho, L.F.; Lloret, J.; Proença, M.L. Long short-term memory and fuzzy logic for anomaly detection and mitigation in software-defined network environment. IEEE Access 2020, 8, 83765–83781. [Google Scholar] [CrossRef]
- Said Elsayed, M.; Le-Khac, N.A.; Dev, S.; Jurcut, A.D. Network Anomaly Detection Using LSTM Based Autoencoder; Association for Computing Machinery: New York, NY, USA, 2020; pp. 37–45. [Google Scholar] [CrossRef]
- Karan, B.; Narayan, D.; Hiremath, P. Detection of DDoS Attacks in Software Defined Networks. In Proceedings of the 2018 3rd International Conference on Computational Systems and Information Technology for Sustainable Solutions (CSITSS), Bengaluru, India, 20–22 December 2018; pp. 265–270. [Google Scholar] [CrossRef]
- Al-Amiedy, T.A.; Anbar, M.; Belaton, B.; Kabla, A.H.H.; Hasbullah, I.H.; Alashhab, Z.R. A Systematic Literature Review on Machine and Deep Learning Approaches for Detecting Attacks in RPL-Based 6LoWPAN of Internet of Things. Sensors 2022, 22, 3400. [Google Scholar] [CrossRef] [PubMed]
- Elsayed, M.S.; Le-Khac, N.A.; Jurcut, A.D. InSDN: A novel SDN intrusion dataset. IEEE Access 2020, 8, 165263–165284. [Google Scholar] [CrossRef]
- Ahuja, N.; Singal, G.; Mukhopadhyay, D. DDOS attack SDN Dataset. Mendeley Data 2020, 1, 17632. [Google Scholar] [CrossRef]
- Al-Garadi, M.A.; Mohamed, A.; Al-Ali, A.K.; Du, X.; Ali, I.; Guizani, M. A survey of machine and deep learning methods for internet of things (IoT) security. IEEE Commun. Surv. Tutor. 2020, 22, 1646–1685. [Google Scholar] [CrossRef]

| Publication Year & Ref. | SLR | Approaches | Architecture SDN | OpenFlow Forwarding | DDoS Attack in SDN | Number of Online Databases | Time Span (Coverage Years) | Concentrated on Specific SDN Datasets | ||
|---|---|---|---|---|---|---|---|---|---|---|
| ML | DL | Hybrid | ||||||||
| [8], 2020 | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | - | - | ✗ |
| [10], 2021 | ✓ | ✓ | ✗ | ✗ | ✓ | ✗ | ✓ | 4 | 2015–2021 | ✗ |
| [11], 2021 | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | 2 | 2019–2020 | ✗ |
| [12], 2022 | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | 8 | Till April–2022 | ✗ |
| [13], 2022 | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | 5 | 2013–2020 | ✗ |
| [14], 2023 | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | 5 | 2018–2022 | ✗ |
| This SLR, 2023 | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | 8 | 2014–2022 | ✓ |
| No. | This SLR Include Articles That Are: | This SLR Exclude Articles That Are: |
|---|---|---|
| 1 | From conferences, journals, and book chapters are written in the English language. | Written in other languages. |
| 2 | Listed at one of the database sources. | Not accessible full version. |
| 3 | Related to DDoS attacks detection and mitigation approach against SDN network. | Related to SDN DDoS attacks on IoT, cloud computing, 5G networks, mobile networks, wireless networks, and Ad hoc networks or DDoS attacks on conventional networks. |
| 4 | Empirical or experimental studies since the systematic reviews are generally concentrated on them. | Duplicated and unrelated (i.e., review/survey research papers, books, editorials, and not accessible) studies. |
| 5 | Published up to 2022. | Not within the search period. |
| 6 | Related to research questions. | Not related to research questions or score less than or equal to 3.5 in the quality assessment criteria. |
| No. | Online Database | Search Within | Links |
|---|---|---|---|
| 1 | IEEE Xplore. | Title, Abstract, Keywords | (https://ieeexplore.ieee.org, accessed on 1 January 2022). |
| 2 | Scopus-Elsevier. | Title, Abstract, Keywords | (https://www.scopus.com, accessed on 1 January 2022). |
| 3 | Taylor & Francis Online. | Title, Abstract, Keywords | (https://www.tandfonline.com, accessed on 1 January 2022). |
| 4 | Science Direct. | Title, Abstract, Keywords | (https://www.sciencedirect.com, accessed on 1 January 2022). |
| 5 | Web of Science (WoS). | Title, Abstract, Full Text | (https://www.webofknowledge.com, accessed on 1 January 2022). |
| 6 | Wiley Online Library. | Title, Abstract, Keywords | (https://onlinelibrary.wiley.com, accessed on 1 January 2022). |
| 7 | Springer Link. | Title, Abstract, Full Text | (https://link.springer.com, accessed on 1 January 2022). |
| 8 | ACM Digital Library. | Title, Abstract, Keywords | (https://dl.acm.org, accessed on 1 January 2022). |
| Checklist Questions | |
|---|---|
| Design | 1. Are the objectives expressed clearly? 2. Is the topic addressed in the paper associated with this SLR? 3. Are the studies capable of answering any one of the research questions? 4. Are the study evaluation metrics fully defined? |
| Conduct | 5. Is the dataset of the research paper clearly described? 6. Are the implementation methods sufficiently represented? |
| Analysis | 7. Are the analysis of the results sufficiently explained? 8. Are the analysis of the results compared with existing approaches? |
| Conclusion | 9. Are the research limitations stated? |
| No. | Data Extracted | Description |
|---|---|---|
| 1 | Study ID | Specific identity numbers for each study. |
| 2 | Bibliographic Info | Title, author, publication source, and the publication year (up to 31 Mar 2022). |
| 3 | Type of publication | Conference or journal paper. |
| 4 | Study objective(s) | Aim of the study. |
| 5 | Method used. | The method used by the study (i.e., ML, DL, and hybrid (both ML and DL)). |
| 6 | Datasets type. | The dataset used by the study (i.e., benchmark dataset and realistic or unrealistic datasets). |
| 7 | Evaluation Metrics. | (i.e., detection performance/efficiency metrics or computational performance metrics). |
| 8 | Study finding. | Results of the study. |
| 9 | Study limitations. | Limitations of the study. |
| 10 | Study experiment. | Network simulators, hacking tools, and experimental platforms. |
| Ref. | ML-Based Approaches | Realistic Dataset | Feature Selection Technique (f) | Deployment of Detection Approach | DDoS Attack Techniques | Rates of DDoS Attacks | Detection Accuracy | Limitation(s) | ||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Ẹ | Ḥ | Ṣ | In | Out | Ḍ | Ṃ | High | Low | High | Low | ||||
| [59] | ✓ | ✗ | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | The proposed approach was evaluated with unrealistic datasets, which did not reflect the characteristics of the SDN network. |
| [60] | ✓ | ✗ | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The proposed approach was evaluated with unrealistic datasets, which did not reflect the characteristics of the SDN network. |
| [61] | ✓ | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | Implementing the proposed model on a real SDN network is superior to testing its performance in detecting such attacks. |
| [62] | ✓ | ✗ | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✗ | ✓ | The proposed approach was evaluated with unrealistic datasets, which did not reflect the characteristics of the SDN network. The ensemble approach achieved low performance. |
| [63] | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The approach is limited to high DDoS attacks, which are manageable to predict with high accuracy due to high forged traffic |
| [64] | ✗ | ✓ | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The approach was trained and tested with an unrealistic dataset, which does not reflect the character of the SDN network environment. |
| [65] | ✗ | ✓ | ✗ | ✓ | ✓ | ✗ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The DAD is limited to SYN DDoS flood attacks on a data plan since the DDoS attacks against the SDN controller have a global impact. The proposed model was trained and tested using a small dataset. |
| [66] | ✗ | ✓ | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | The proposed model was tested and trained with unrealistic datasets, which do not reflect the characteristics of SDN networks |
| [67] | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | The proposed approach is limited to TCP-SYN flood attacks. The proposed method has been evaluated with a small dataset. |
| [68] | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | It needs to be tested on a real SDN testbed, which would be preferable. It is limited to high-rate DDoS attacks, which are easy to detect due to massive network traffic flow. |
| [69] | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | It was trained with the default settings because MLworks best when hyper-parameters or control parameters are tuned or optimized. |
| [70] | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | The approach does not compare the results with other approaches. The proposed system runs on the controller, which adds unnecessary load and overhead to the controller. |
| [71] | ✗ | ✓ | ✗ | ✗ | ✓ | - | - | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The remaining algorithms achieve low performance. The proposed method was evaluated using an unrealistic dataset, which does not reflect the characteristics of the SDN network environment. |
| [72] | ✗ | ✓ | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✗ | ✓ | The method achieves deficient performance; for example, an accuracy rate of 78% and 85% for DT and SVM, respectively. The proposed method was evaluated using an unrealistic dataset, which does not reflect the characteristics of the SDN network environment. |
| [73] | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The remaining ML classifiers achieve relatively low performance regarding detection accuracy. There is no information about the proposed approach’s false positive rate. |
| [74] | ✗ | ✓ | ✗ | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | The proposed approach achieves a low detection accuracy of 95%. The proposed model was evaluated using an unrealistic dataset that does not reflect the characteristics of the SDN network environment. |
| [75] | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | The framework is evaluated to detect high-rate DDoS attacks, which are easy to detect due to the massive amount of forged traffic. The proposed framework increases the controller’s workload. |
| [76] | ✗ | ✓ | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | The proposed system runs on the controller, which adds unnecessary load and overhead to the controller. The proposed approach suffers from high processing and communication overhead. |
| [77] | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | The proposed method implemented on the SDN controller adds an unnecessary burden in the case of DDoS attacks |
| [78] | ✗ | ✓ | ✗ | ✓ | ✗ | - | - | ✓ | ✗ | ✓ | ✗ | ✗ | ✓ | The proposed approach still achieves lower performance for detecting DDoS attacks, and needs to execute the approach on a real SDN network to test its performance in detecting such attacks. |
| [79] | ✗ | ✓ | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✗ | ✓ | The proposed approach reveals low performance and needs improvement. The proposed approach was evaluated with an unrealistic dataset that does not reflect the characteristics of the SDN network. |
| [80] | ✗ | ✓ | ✗ | ✓ | ✓ | - | - | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The proposed approach showed that the controller DDoS attack has the lowest classification results (for SVM and MLP, less than 90% accuracy rates) than flow-table and bandwidth attacks. There is no information about the proposed approach’s false positive rate. |
| [81] | ✗ | ✓ | ✗ | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | The defense system was evaluated, tested, and trained on an unrealistic dataset that does not reflect the characteristics of the SDN network environment. |
| [82] | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | The proposed model runs at the controller, adding unnecessary load and overhead. The defense system was evaluated, tested, and trained on an unrealistic dataset that does not reflect the characteristics of the SDN network environment. |
| [83] | ✗ | ✓ | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The proposed approach implemented at the SDN controller increases the controller overhead in case of DDoS attacks. |
| [84] | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | The proposed approach runs on the SDN controller as an application system, adding unnecessary load and overhead, particularly during DDoS attacks against the controller. |
| [85] | ✗ | ✗ | ✓ | ✓ | ✓ | - | - | ✓ | ✗ | ✓ | ✗ | ✗ | ✓ | The ASVM method achieves low performance for detecting DDoS attacks. |
| [86] | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✗ | ✓ | ✓ | ✓ | The proposed approach achieves a low detection accuracy of 95.80%. The method’s detection performance is worse under different attack rates. |
| [87] | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✗ | ✓ | The proposed approach implemented at the controller adds unnecessary load and overhead. It also needs to be improved in terms of detection accuracy. |
| [88] | ✗ | ✗ | ✓ | ✗ | ✗ | - | - | ✓ | ✗ | ✓ | ✗ | ✓ | ✓ | The performance of the proposed approach achieved low accuracy. Furthermore, the proposed approach was tested and trained using an unrealistic dataset that does not reflect the characteristics of the SDN network environment. |
| [89] | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The proposed approach on SDN switches makes the proposed method suffer from a scalability issue since the scheme must be implemented on every switch. |
| [90] | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | The proposed model suffers from processing and communication overhead at the SDN controller. The proposed method was evaluated and trained on an unrealistic NSL-KDD dataset that does not reflect the characteristics of the SDN network environment. |
| [91] | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The proposed model runs at the controller, which adds excessive load and overhead of the SDN controller in the event of DDoS attacks. There is a lack of information about the tested and training datasets. |
| [92] | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ | ✓ | The proposed approach shows a low detection accuracy of 96.13% because the proposed approach suffers from high false-positive and false-negative effects. |
| [93] | ✗ | ✗ | ✓ | ✗ | ✓ | ✗ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The proposed approach has been evaluated with an unrealistic dataset, which does not reflect the characteristics of the SDN network environment. The proposed approach needs to be evaluated in terms of false-positive rates or any other evaluation metrics. |
| [94] | ✗ | ✗ | ✓ | ✗ | ✓ | ✗ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The OpenFlow switches of the data layer have an attack-detection module that can analyze all packet flows that come through the switches, which takes more time to process and classify. |
| [95] | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | This approach still suffers from overhead in the case of high DDoS attack flows because the SDN controller collects all flows from the switches for detection purposes, which results in congestion and degradation of the response time. |
| Ref. | DL-Based Approaches | Realistic Dataset | Feature Selection Technique (f) | Deployment of Detection Approach | DDoS Attack Techniques | Rates of DDoS Attacks | Detection Accuracy | Limitation(s) | ||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Ẹ | Ḥ | Ṣ | In | Out | Ḍ | Ṃ | High | Low | High | Low | ||||
| [96] | ✓ | ✗ | ✗ | ✗ | ✗ | - | - | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The proposed method was evaluated using an unrealistic dataset, which does not reflect the characteristics of the SDN network environment. |
| [97] | ✓ | ✗ | ✗ | ✗ | ✓ | - | - | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The proposed approach was evaluated using an unrealistic dataset, which does not reflect the characteristics of the SDN network environment. |
| [98] | ✓ | ✗ | ✗ | ✗ | ✓ | - | - | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The proposed ensemble model was evaluated, tested, and trained on an unrealistic dataset that does not reflect the characteristics of the SDN network environment. |
| [99] | ✗ | ✓ | ✗ | ✓ | ✓ | - | - | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The hybrid approach achieved low accuracy but relatively high false-positive and false-negative rates. |
| [100] | ✗ | ✓ | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The approach is limited to detecting high-rate DDoS attacks. The proposed method was evaluated using an unrealistic dataset that does not reflect the characteristics of the SDN network environment. |
| [101] | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✗ | ✓ | ✓ | ✗ | The dataset was not presented clearly and lacked information about low-rate DDoS attacks. Implementing the hybrid model in an SDN system is preferable to test its performance in detecting such attacks. |
| [102] | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The proposed approach performs better when the model detects the entire dataset of attacks. The proposed model runs at the controller, which adds unnecessary load and overhead to the controller. |
| [103] | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✗ | ✓ | The proposed approach was evaluated using an unrealistic dataset and achieved low detection accuracy. The proposed model runs at the controller, which adds unnecessary load and overhead to the controller. |
| [104] | ✗ | ✓ | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The proposed approach was evaluated and trained using an unrealistic dataset, which does not reflect the characteristics of the SDN network environment. In addition, the proposed model runs at the controller, adding unnecessary load and overhead. |
| [105] | ✗ | ✓ | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✗ | ✓ | The proposed system was evaluated with NSL-KDD dataset and achieved low detection accuracy. |
| [106] | ✗ | ✓ | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | The proposed approach is trained, tested, and evaluated using an unrealistic dataset, which does not reflect the characteristics of the SDN network environment. The proposed approach achieved low detection accuracy of 89% for the NSL-KDD dataset. The proposed model runs at the controller, adding unnecessary load and overhead. |
| [107] | ✗ | ✓ | ✗ | ✗ | ✓ | ✗ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The proposed approach was evaluated and trained using an unrealistic dataset, which does not reflect the characteristic of the SDN network environment. |
| [108] | ✗ | ✓ | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | The detection rate of the proposed approach achieved a low detection accuracy. The proposed method was evaluated, tested, and trained using an unrealistic dataset that does not reflect the characteristics of the SDN network environment. |
| [109] | ✗ | ✓ | ✗ | ✓ | ✓ | ✗ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The proposed method achieved low performance, particularly in the two-level method and information entropy, because it does not consider adaptive parameters |
| [110] | ✗ | ✓ | ✗ | ✗ | ✓ | - | - | ✓ | ✗ | ✓ | ✗ | ✗ | ✓ | The proposed method was evaluated using an unrealistic Dataset, which does not reflect the characteristics of the SDN network environment. |
| [111] | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The proposed system is complicated since it must first convert the selected features into RGB images to rescale the data and then forward them to the CNN classifier model, and the proposed system runs at the SDN controller, adding unnecessary overhead during DDoS attacks. |
| [112] | ✗ | ✗ | ✓ | ✗ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | The proposed system was evaluated using unrealistic datasets, which do not reflect the characteristics of the SDN network environment. The proposed method suffers from computational overhead and needs to improve the mitigation results. |
| [113] | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | The proposed approach runs on the SDN controller, which adds unnecessary load and overhead, particularly during DDoS attacks against the controller. |
| [114] | ✗ | ✗ | ✓ | ✓ | ✓ | - | - | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | The proposed system needs to be tested in an SDN environment. The approach needs to be compared with the findings of other existing approaches. |
| [115] | ✗ | ✗ | ✓ | ✓ | ✓ | - | - | ✓ | ✗ | ✓ | ✗ | ✗ | ✓ | The proposed approach achieved a low detection accuracy. |
| [116] | ✗ | ✗ | ✓ | ✗ | ✓ | - | - | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The proposed method was evaluated using an unrealistic dataset, which does not reflect the characteristics of the SDN network environment. |
| [117] | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The proposed approach must be evaluated using other evaluation metrics (i.e., false-positive rates) and compared with other existing approaches. |
| [118] | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✓ | Around 85% of the regular traffic reaches the server when the mitigation agent starts against the flooding attacks. The mitigation agent may not perform as a stand-alone IDS for detecting such attacks. |
| [119] | ✗ | ✗ | ✓ | ✗ | ✓ | - | - | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The proposed system was tested and trained with an unrealistic dataset, which does not reflect the characteristics of the SDN network. |
| [120] | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✗ | ✓ | The proposed DL-based DDoS detection model has low detection accuracy. The approach runs on the SDN controller, which adds unnecessary load and overhead, particularly when detecting DDoS attacks against the controller. |
| [121] | ✗ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The proposed approach achieved a low detection accuracy. The proposed method was evaluated and trained using an unrealistic dataset that does not reflect the characteristics of the SDN network environment. |
| [122] | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✗ | ✓ | The proposed system’s performance needs to be improved. |
| Ref. | Hybrid- Based Approaches | Realistic Dataset | Feature Selection Technique (f) | Deployment of Detection Approach | DDoS Attack Techniques | Rates of DDoS Attacks | Detection Accuracy | Limitation(s) | ||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| In | Out | Ḍ | Ṃ | High | Low | High | Low | |||||
| [123] | ✓ | ✓ | ✓ | - | - | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | It needs to be implemented in an SDN environment to test its performance in detecting such attacks. |
| [124] | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The proposed approach runs at the controller, which adds unnecessary load and overhead to the controller and achieves low performance for application-layer DDoS attack. |
| [125] | ✓ | ✗ | ✓ | - | - | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | The proposed approach runs on the SDN controller, adding unnecessary load and overhead. The approach was trained and evaluated using an unrealistic dataset, which does not reflect the characteristics of the SDN network environment. |
| [126] | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | The proposed anomaly detection and mitigation approach achieved high performance for the first scenario, and satisfactory performance for the second scenario. The proposed approach runs on the SDN application plane, which adds unnecessary load and overhead to the controller in the event of DDoS attacks against the SDN controller. |
| [127] | ✓ | ✓ | ✓ | - | - | ✓ | ✗ | ✓ | ✗ | ✗ | ✓ | The proposed approach achieved a relatively low detection accuracy of 90.5%. Implementing the proposed model in a real SDN network is superior to testing its performance in detecting such attacks and extending the binary classification into multi-class classification problems to identify network attacks. |
| [128] | ✓ | ✗ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✗ | ✓ | The proposed approach achieved low detection accuracy of 74.3% and 92.3% for SVM and DNN, respectively. The proposed method was evaluated, tested, and trained on an unrealistic dataset that does not reflect the characteristics of the SDN network environment. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bahashwan, A.A.; Anbar, M.; Manickam, S.; Al-Amiedy, T.A.; Aladaileh, M.A.; Hasbullah, I.H. A Systematic Literature Review on Machine Learning and Deep Learning Approaches for Detecting DDoS Attacks in Software-Defined Networking. Sensors 2023, 23, 4441. https://doi.org/10.3390/s23094441
Bahashwan AA, Anbar M, Manickam S, Al-Amiedy TA, Aladaileh MA, Hasbullah IH. A Systematic Literature Review on Machine Learning and Deep Learning Approaches for Detecting DDoS Attacks in Software-Defined Networking. Sensors. 2023; 23(9):4441. https://doi.org/10.3390/s23094441
Chicago/Turabian StyleBahashwan, Abdullah Ahmed, Mohammed Anbar, Selvakumar Manickam, Taief Alaa Al-Amiedy, Mohammad Adnan Aladaileh, and Iznan H. Hasbullah. 2023. "A Systematic Literature Review on Machine Learning and Deep Learning Approaches for Detecting DDoS Attacks in Software-Defined Networking" Sensors 23, no. 9: 4441. https://doi.org/10.3390/s23094441
APA StyleBahashwan, A. A., Anbar, M., Manickam, S., Al-Amiedy, T. A., Aladaileh, M. A., & Hasbullah, I. H. (2023). A Systematic Literature Review on Machine Learning and Deep Learning Approaches for Detecting DDoS Attacks in Software-Defined Networking. Sensors, 23(9), 4441. https://doi.org/10.3390/s23094441








