Gaussian-Distributed Spread-Spectrum for Covert Communications
Abstract
1. Introduction
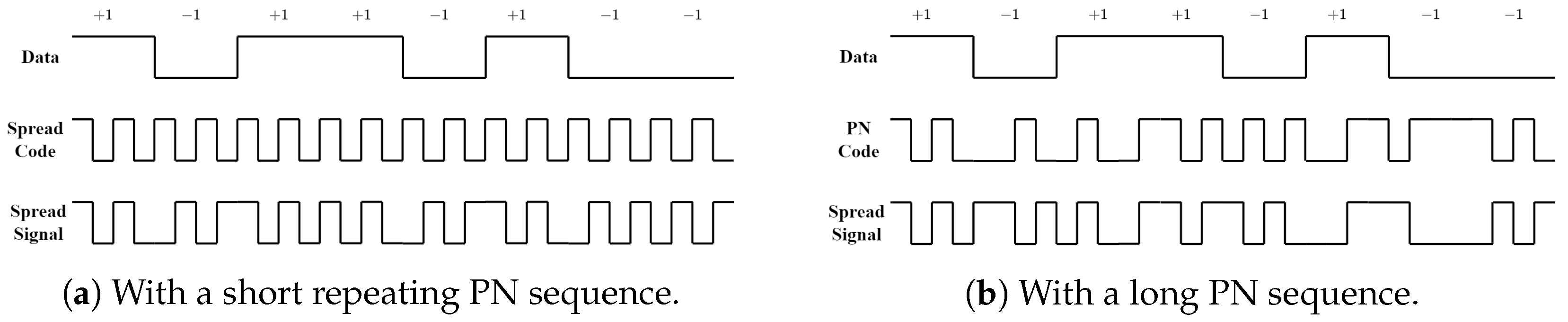
2. DSSS Modulation
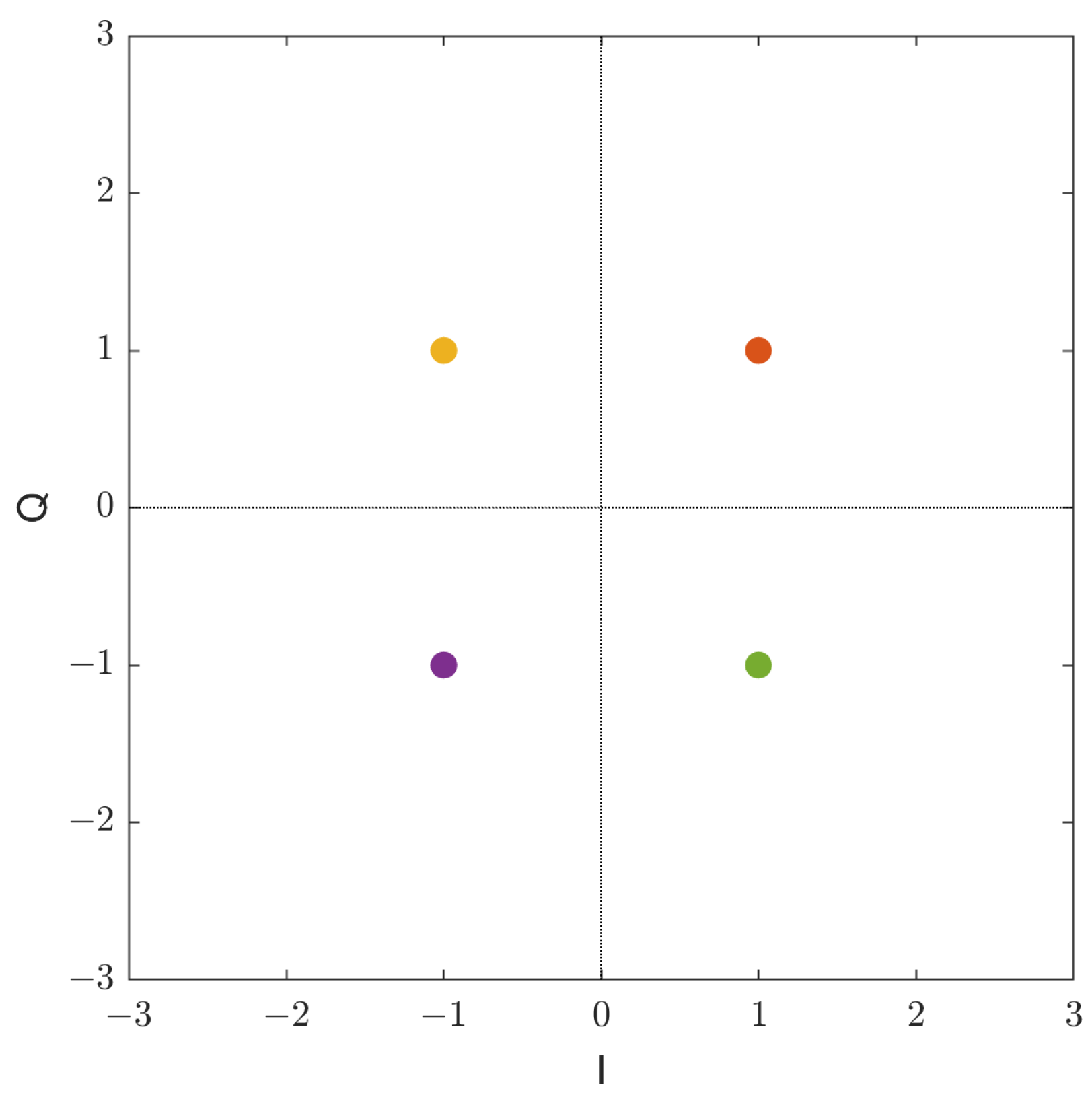
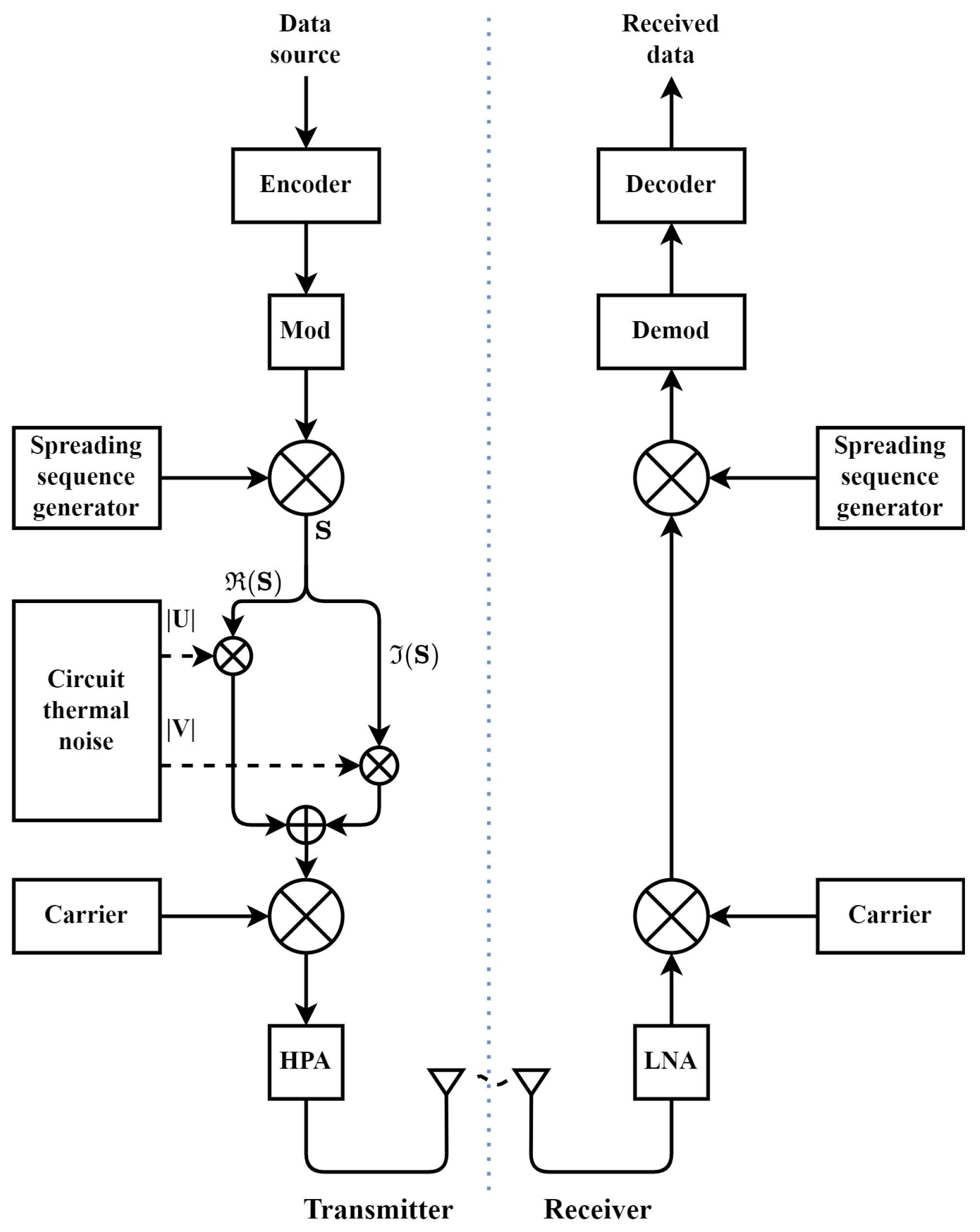
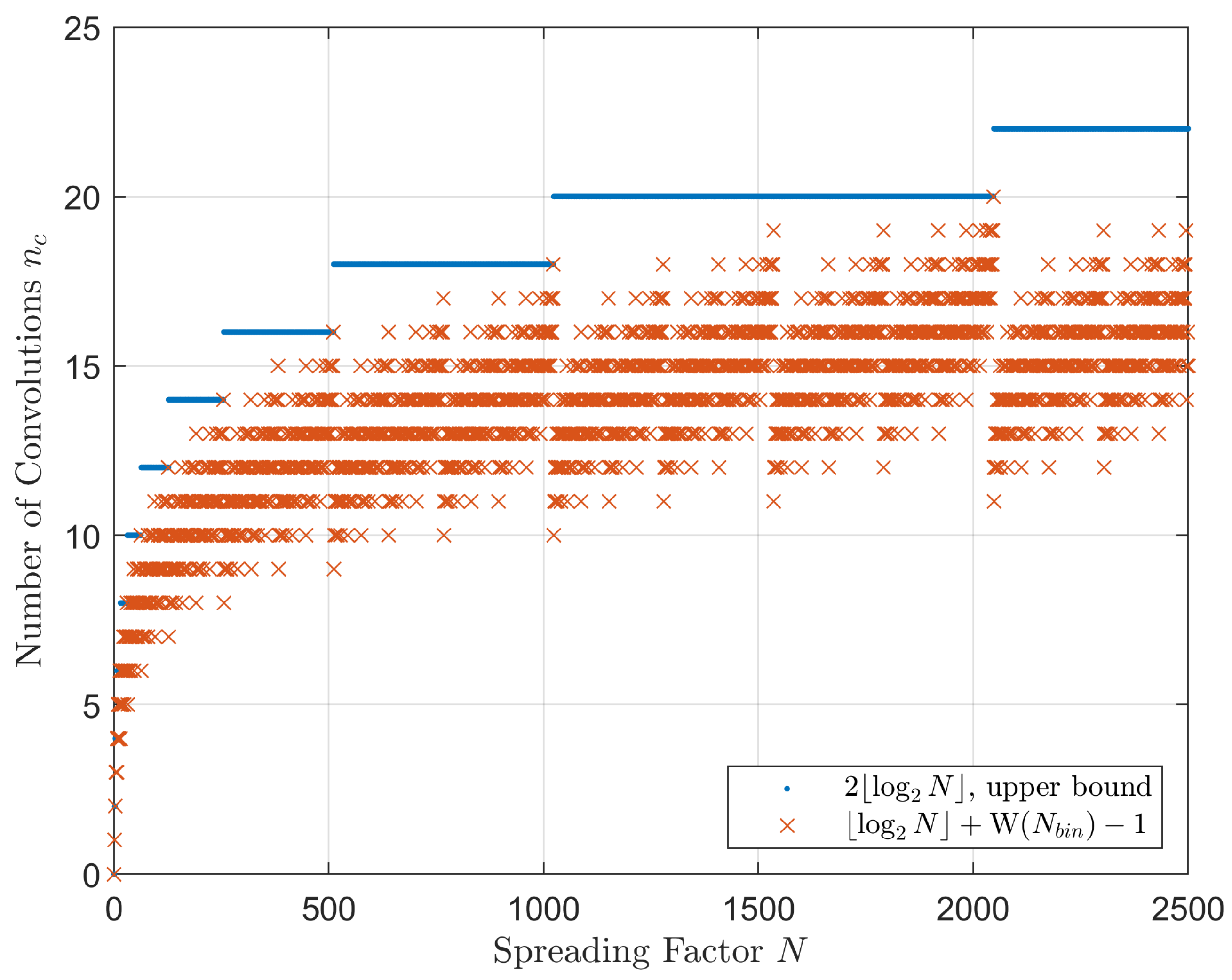
3. Proposed GDSS Scheme
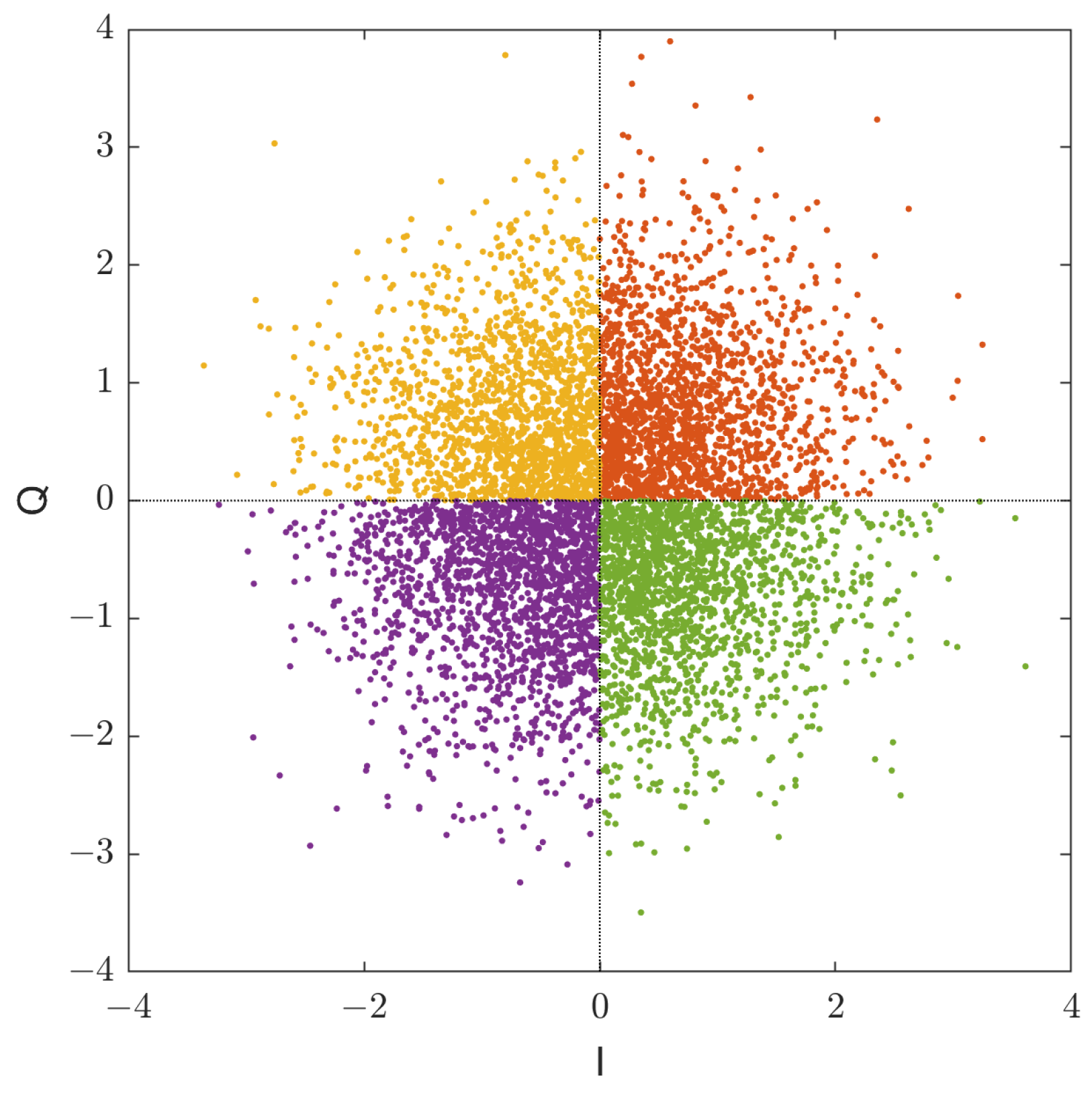
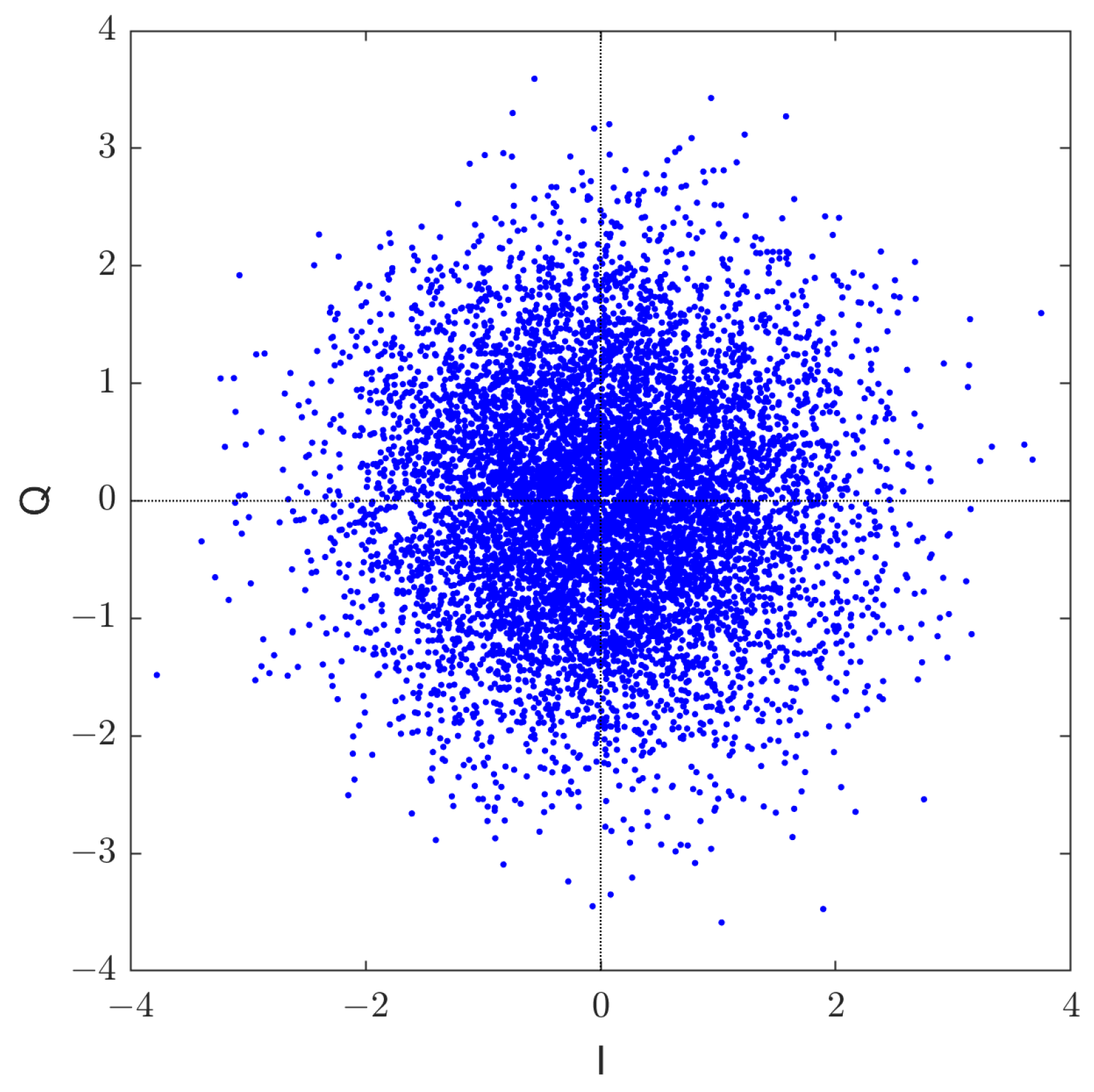
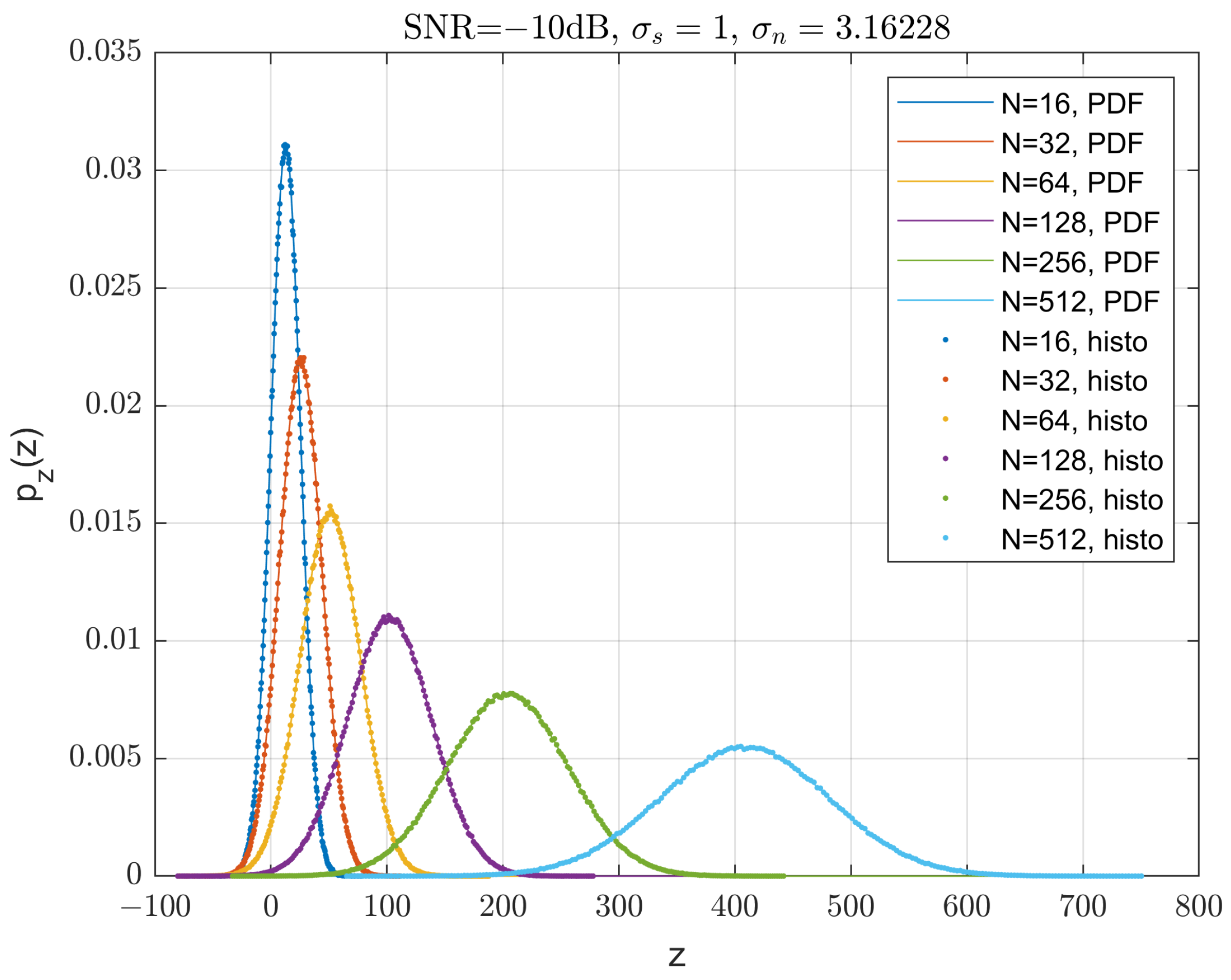
Gaussianity of GDSS Signals
4. Detectability of GDSS Signals
4.1. Detection Using High-Order Moments
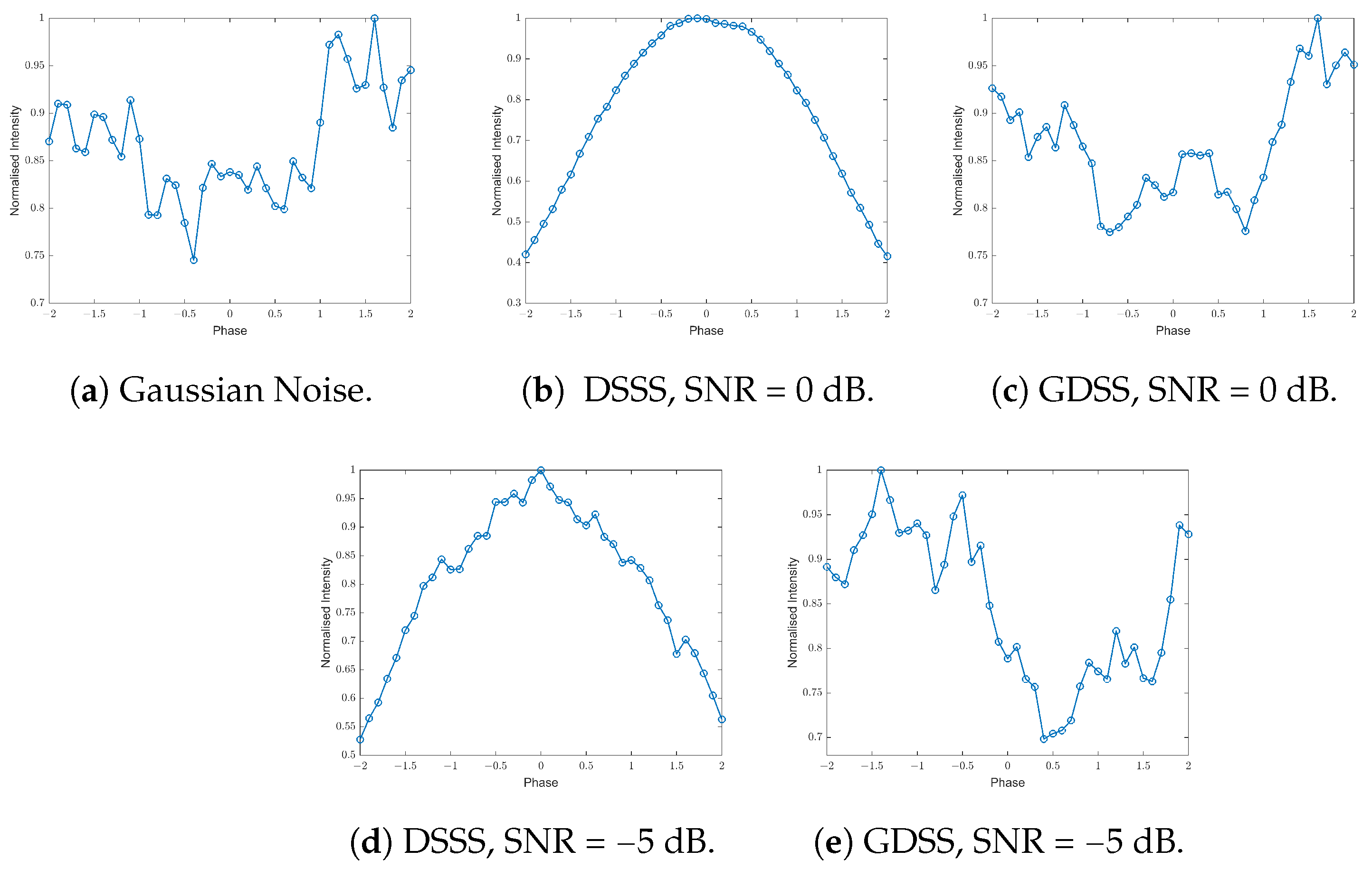
4.2. Detection Using Modulation Stripping
4.3. Energy Detector
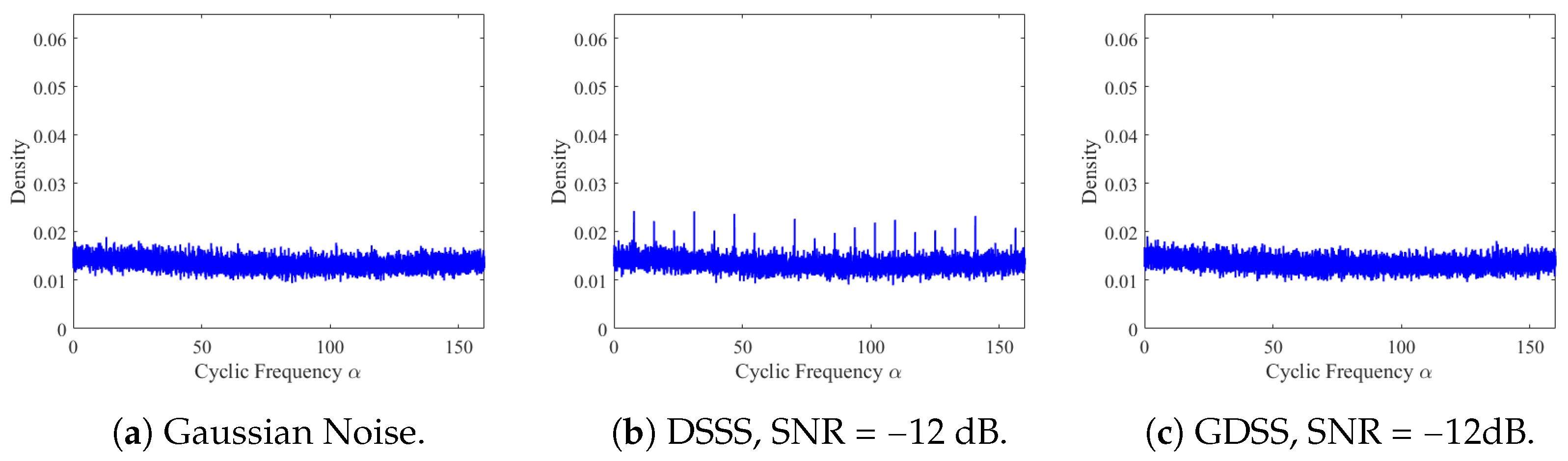
4.4. Cyclostationary Analysis
5. BER Performance
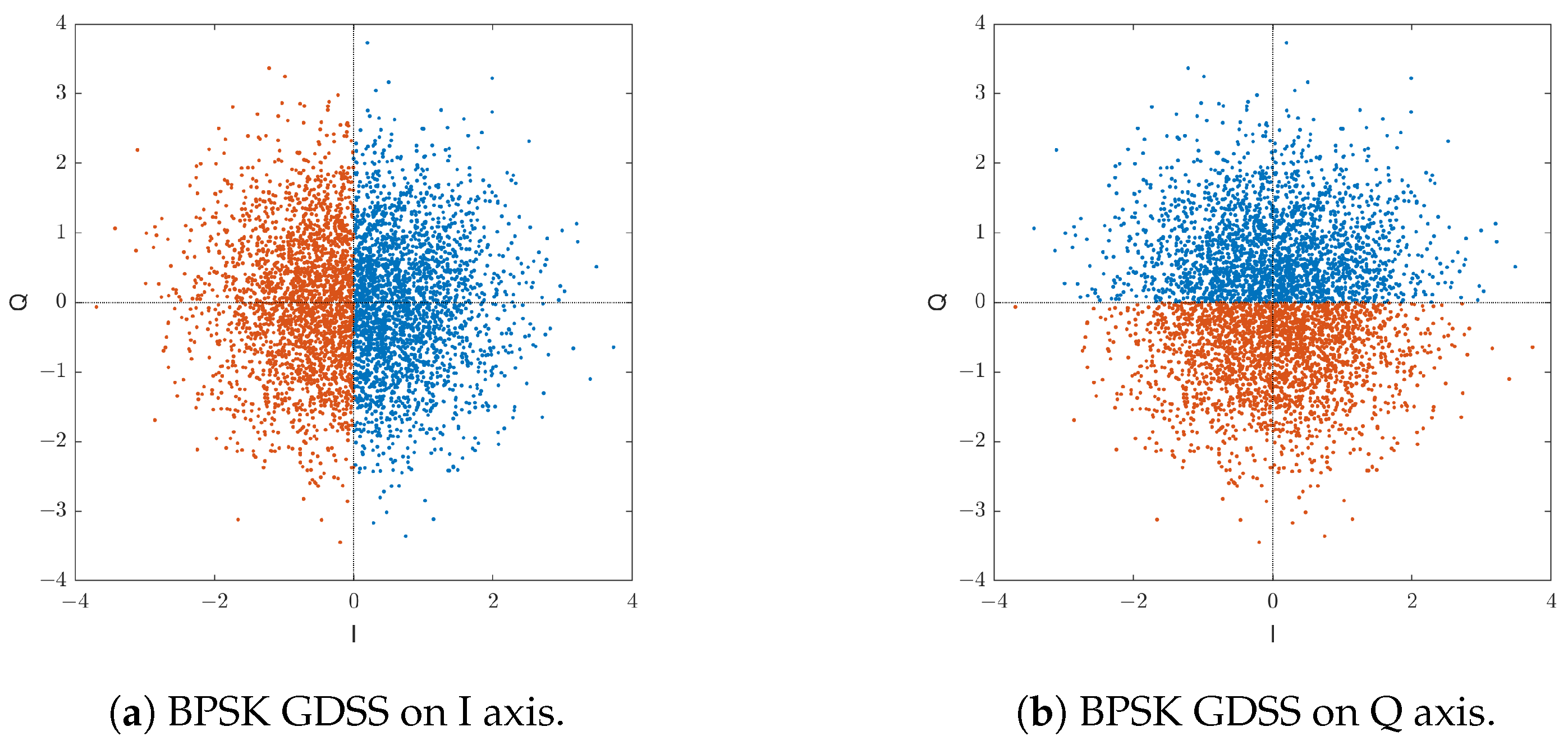
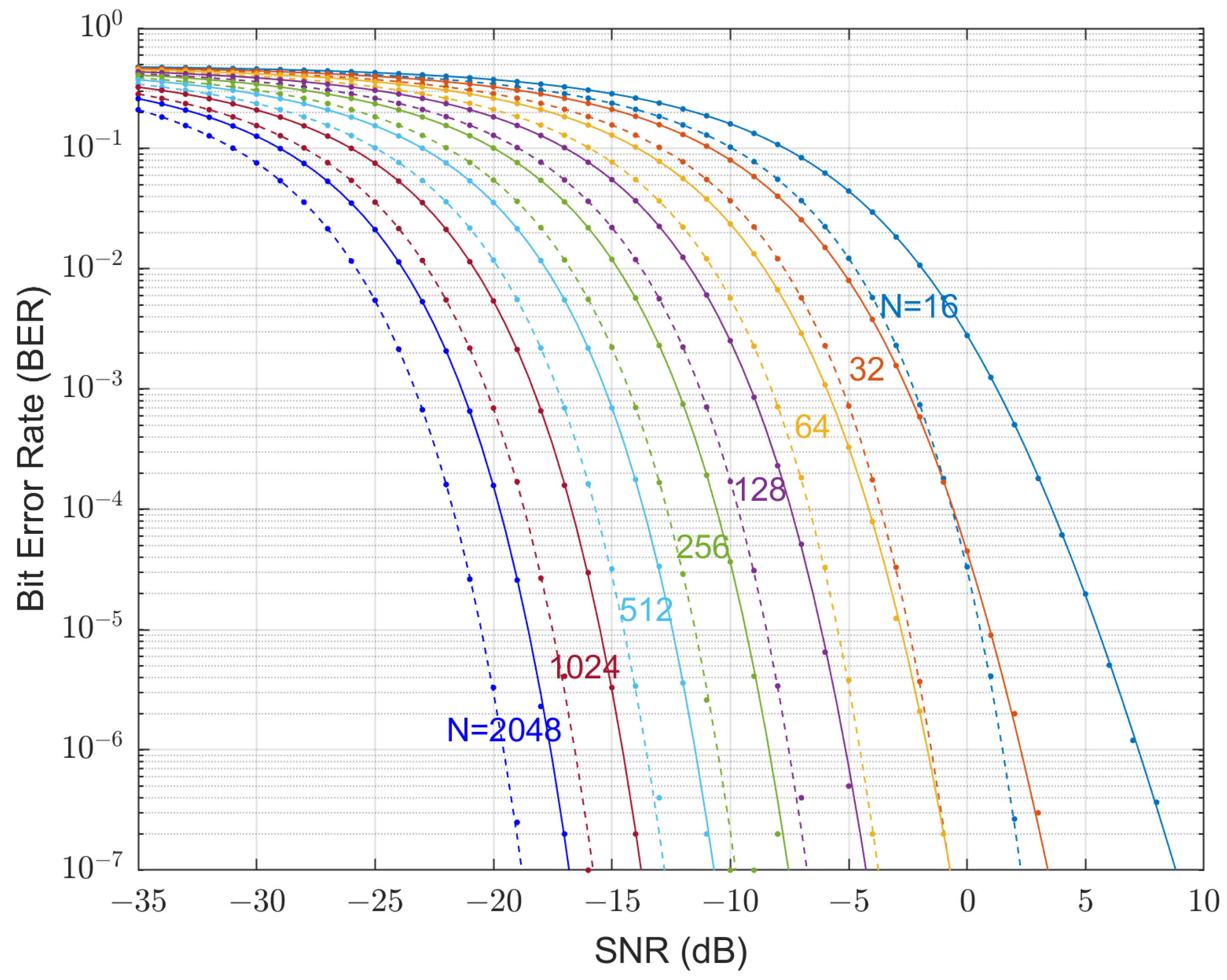
5.1. Uncoded BER Performance
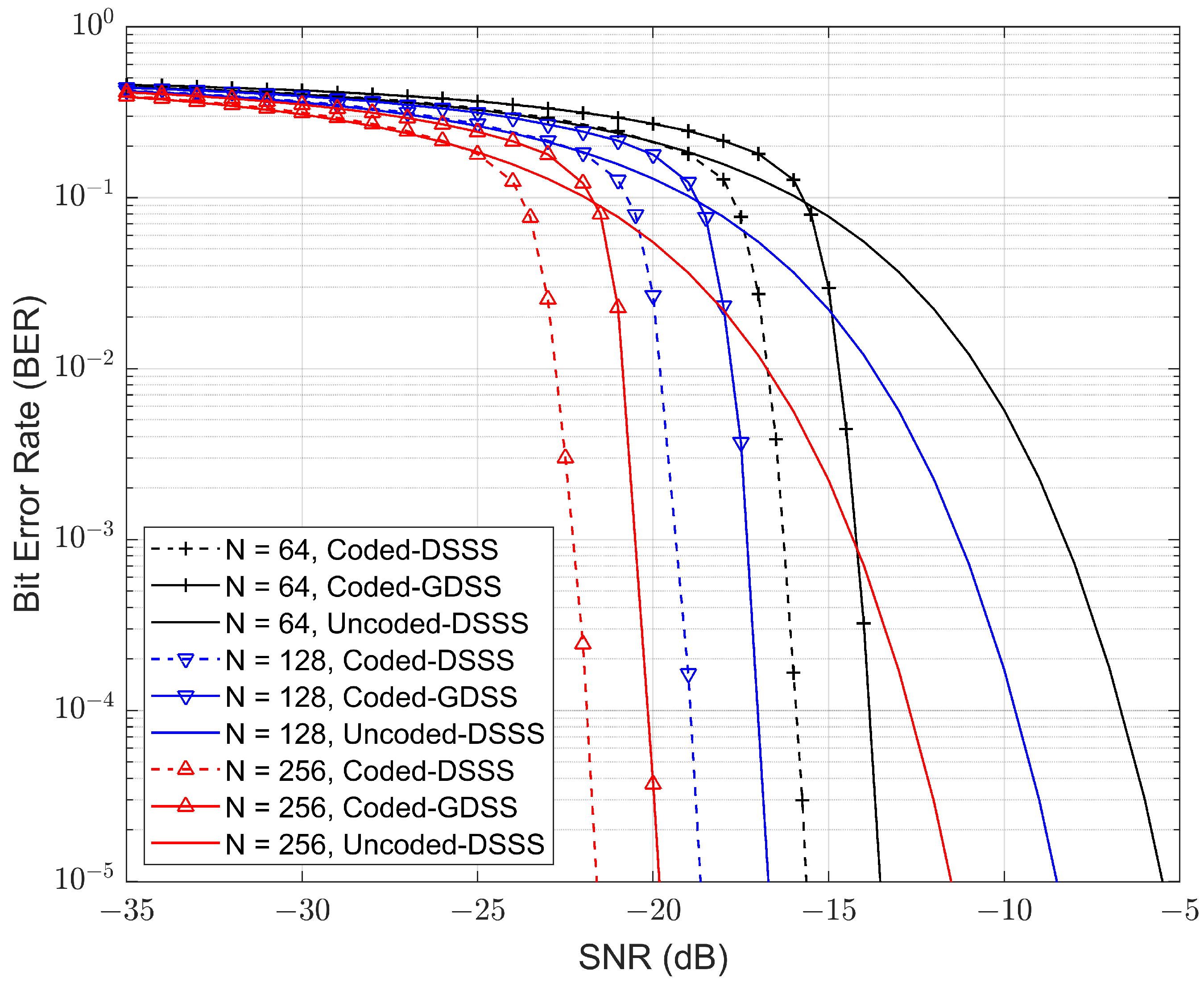
5.2. LDPC-Coded GDSS System
6. Conclusions
Author Contributions
Funding
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Varghese, F.; Sasikala, P. A Detailed Review Based on Secure Data Transmission Using Cryptography and Steganography. Springer Wirel. Pers. Commun. 2023, 129, 2291–2318. [Google Scholar] [CrossRef]
- Oladipupo, E.T.; Abikoye, O.C.; Imoize, A.L.; Awotunde, J.B.; Chang, T.Y.; Lee, C.C.; Do, D.T. An Efficient Authenticated Elliptic Curve Cryptography Scheme for Multicore Wireless Sensor Networks. IEEE Access 2023, 11, 1306–1323. [Google Scholar] [CrossRef]
- Li, M.; Liu, Y.; Tian, Z.; Shan, C. Privacy Protection Method Based on Multidimensional Feature Fusion Under 6G Networks. IEEE Trans. Netw. Sci. Eng. 2022, 1, 1–14. [Google Scholar] [CrossRef]
- Ambika; Virupakshappa; Veerashetty, S. Secure Communication over Wireless Sensor Network using Image Steganography with Generative Adversarial Networks. Meas. Sens. 2022, 24, 100452. [Google Scholar]
- Sharma, H.; Kumar, N.; Tekchandani, R. Physical Layer Security using Beamforming Techniques for 5G and Beyond Networks: A Systematic Review. Phys. Commun. 2022, 54, 101791. [Google Scholar]
- Glenn, A. Low Probability of Intercept. IEEE Commun. Mag. 1983, 21, 26–33. [Google Scholar] [CrossRef]
- Turner, L. The Evolution of Featureless Waveforms for LPI Communications. In Proceedings of the IEEE 1991 National Aerospace and Electronics Conference (NAECON), Dayton, OH, USA, 20–24 May 1991; pp. 1325–1331. [Google Scholar]
- Makhdoom, K.; Abolhasan, M.; Lipman, J. A Comprehensive Survey of Covert Communication Techniques, Limitations and Future Challenges. Comput. Secur. 2022, 120, 102784. [Google Scholar] [CrossRef]
- Anand, A.; Singh, A.K. A Comprehensive Study of Deep Learning-based Covert Communication. ACM Transactions on Multimedia Computing. Commun. Appl. 2022, 18, 1–19. [Google Scholar]
- Huang, K.W.; Wang, H.M.; Towsley, D.; Poor, H.V. LPD Communication: A Sequential Change-Point Detection Perspective. IEEE Trans. Commun. 2020, 68, 2474–2490. [Google Scholar] [CrossRef]
- Bash, B.A.; Goeckel, D.; Towsley, D.; Guha, S. Hiding Information in Noise: Fundamental Limits of Covert Wireless Communication. IEEE Commun. Mag. 2015, 53, 26–31. [Google Scholar]
- Yan, S.; Zhou, X.; Hu, J.; Hanly, S.V. Low Probability of Detection Communication: Opportunities and Challenges. IEEE Wirel. Commun. 2019, 26, 19–25. [Google Scholar] [CrossRef]
- Bash, B.A.; Goeckel, D.; Towsley, D. Limits of Reliable Communication with Low Probability of Detection on AWGN Channels. IEEE J. Sel. Areas Commun. 2013, 31, 1921–1930. [Google Scholar] [CrossRef]
- Ma, R.; Yang, W.; Tao, L.; Lu, X.; Xiang, Z.; Liu, J. Covert Communications with Randomly Distributed Wardens in the Finite Blocklength Regime. IEEE Trans. Veh. Technol. 2022, 71, 533–544. [Google Scholar] [CrossRef]
- Kaddoum, G. Wireless Chaos-based Communication Systems: A Comprehensive Survey. IEEE Access 2016, 4, 2621–2648. [Google Scholar] [CrossRef]
- Eisencraft, M.; Monteiro, L.H.; Soriano, D.C. White Gaussian Chaos. IEEE Commun. Lett. 2017, 8, 1719–1722. [Google Scholar] [CrossRef]
- Michaels, A.J.; Chester, D.B. Efficient and Flexible Chaotic Communication Waveform Family. In Proceedings of the 2010—Milcom 2010 Military Communications Conference, San Jose, CA, USA, 31 October 2010–3 November 2010. [Google Scholar]
- Shakeel, I. Machine Learning Based Featureless Signalling. In Proceedings of the MILCOM 2018— 2018 IEEE Military Communications Conference (MILCOM), Los Angeles, CA, USA, 29–31 October 2018. [Google Scholar]
- Norris, J.; Nieto, J. Application of Sub-Sample Dithering to Reduce Probability of Signal Detection. In Proceedings of the 2021 IEEE Military Communications Conference (MILCOM), San Diego, CA, USA, 29 November 2021–2 December 2021; pp. 916–920. [Google Scholar]
- Zhu, Z.A.; Nandi, A.K. Automatic Modulation Classification: Principles, Algorithms and Applications; Wiley: London, UK, 2015. [Google Scholar]
- Burel, G.; Bouder, C. Blind Estimation of the Pseudo-random Sequence of a Direct Sequence Spread Spectrum Signal. In Proceedings of the MILCOM 2000 Proceedings, 21st Century Military Communications. Architectures and Technologies for Information Superiority (Cat. No.00CH37155), Los Angeles, CA, USA, 22–25 October 2000. [Google Scholar]
- Gardner, W.A.; Spooner, C.M. Signal Interception Performance Advantages of Cyclic-feature Detectors. IEEE Trans. Commun. 1992, 40, 149–159. [Google Scholar] [CrossRef]
- Vlok, J.D.; Olivier, J.C. Blind Sequence-length Estimation of Low-SNR Cyclostationary Sequences. IET Commun. 2014, 8, 1578–1588. [Google Scholar] [CrossRef]
- Choi, J.; Ahn, J.; Choe, C.; Shin, Y.; Park, D.; Ahn, S. Practical LPI Communication with Noise-Shaped Signaling. In Proceedings of the 2019 International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Korea, 16-18 October 2019; pp. 332–337. [Google Scholar]
- Michaels, A.J.; Chester, D.B. Featureless Chaotic Spread Spectrum Modulation of Arbitrary Data Constellations. In Proceedings of the 2011 IEEE 12th International Workshop on Signal Processing Advances in Wireless Communications, San Francisco, CA, USA, 26–29 June 2011; pp. 36–40. [Google Scholar]
- Guo, S.; Fu, Y. A Time-Varying Chaotic Multitone Communication Method Based on OFDM for Low Detection Probability of Eavesdroppers. IEEE Access 2021, 9, 107566–107573. [Google Scholar] [CrossRef]
- Nguyen, L. Self-encoded Spread Spectrum and Multiple Access Communications. In Proceedings of the 2000 IEEE Sixth International Symposium on Spread Spectrum Techniques and Applications. ISSTA 2000. Proceedings (Cat. No.00TH8536), Parsippany, NJ, USA, 6–8 September 2000; pp. 394–398. [Google Scholar]
- Shahzad, K.; Zhou, X.; Yan, S. Covert Communication in Fading Channels under Channel Uncertainty. In Proceedings of the IEEE 85th Vehicular Technology Conference (VTC Spring), Sydney, NSW, Australia, 4–7 June 2017; pp. 1–5. [Google Scholar]
- He, B.; Yan, S.; Zhou, X.; Lau, V.K. On Covert Communication with Noise Uncertainty. IEEE Commun. Lett. 2017, 21, 941–944. [Google Scholar] [CrossRef]
- Bash, B.; Goeckel, D.; Towsley, D. Covert Communication Gains from Adversary’s Ignorance of Transmission Time. IEEE Trans. Wirel. Commun. 2016, 15, 8394–8405. [Google Scholar] [CrossRef]
- Sobers, T.; Bash, B.A.; Guha, S.; Towsley, D.; Goeckel, D. Covert Communication in the Presence of an Uninformed Jammer. IEEE Trans. Wirel. Commun. 2017, 16, 6193–6206. [Google Scholar] [CrossRef]
- Zhang, Y.; Li, Y.; Xiang, W.; Wang, J.; Xiao, S.; Li, X.; Tang, W. The Optimal Precoded Faster-Than-Nyquist Signaling for Covert Communications. IEEE Commun. Lett. 2022, 26, 1249–1253. [Google Scholar] [CrossRef]
- Kim, S.W.; Ta, H.Q. Covert Communication by Exploiting Node Multiplicity and Channel Variations. In Proceedings of the ICC 2020—2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar]
- Zheng, T.X.; Wang, H.M.; Ng, D.W.K.; Yuan, J. Multi-antenna Covert Communications in Random Wireless Networks. IEEE Trans. Wirel. Commun. 2019, 18, 1974–1987. [Google Scholar] [CrossRef]
- Lee, K.A.; Barry, J.R. Opportunistic Power Control for Low Probability of Detection Communication. In Proceedings of the IEEE Military Communications Conference, Rockville, MD, USA, 28 November 2022–2 December 2022; pp. 667–671. [Google Scholar]
- Soltani, R.; Goeckel, D.; Towsley, D.; Bash, B.A.; Guha, S. Covert Wireless Communication with Artificial Noise Generation. IEEE Trans. Wirel. Commun. 2018, 17, 7252–7267. [Google Scholar] [CrossRef]
- Jamali, M.V.; Mahdavifar, H. Covert Millimeter-Wave Communication: Design Strategies and Performance Analysis. IEEE Trans. Wirel. Commun. 2022, 21, 3691–3704. [Google Scholar] [CrossRef]
- Sudhakar, J.; Shaik, F.B.; Hari, J. FPGA Implementation of PN-sequence Generator with Binary Chaos Synchronization. In Proceedings of the 2014 International Conference on Electronics and Communication Systems (ICECS), Coimbatore, India, 13–14 February 2014; pp. 1–7. [Google Scholar]
- Popper, C.; Strasser, M.; Capkun, S. Anti-jamming Broadcast Communication using Uncoordinated Spread Spectrum Techniques. IEEE J. Sel. Areas Commun. 2010, 28, 703–715. [Google Scholar] [CrossRef]
- Bohm, G.; Zech, G. Introduction to Statistics and Data Analysis for Physicists; Verlag Deutsches Elektronen-Synchrotron: Berlin, Germany, 2010. [Google Scholar]
- Antoni, J.; Xin, G.; Hamzaoui, N. Fast Computation of the Spectral Correlation. Mech. Syst. Signal Process. 2017, 92, 248–277. [Google Scholar] [CrossRef]
- Half-Normal Distribution, from Wikipedia, the Free Encyclopedia. Available online: https://en.wikipedia.org/wiki/Half-normal_distribution (accessed on 30 March 2023).
- Weisstein, E.W. Half-Normal Distribution, From MathWorld—A Wolfram Web Resource. Available online: https://mathworld.wolfram.com/Half-NormalDistribution.html (accessed on 30 March 2023).
- Chung, S.Y.; Chung, S.Y.; Forney, G.D.; Richardson, T.J.; Urbanke, R. On the Design of Low-Density Parity-Check Codes within 0.0045 dB of the Shannon Limit. IEEE Commun. Lett. 2001, 5, 58–60. [Google Scholar] [CrossRef]



| Moment | SGD (Theory) | GDSS | DSSS |
|---|---|---|---|
| 2nd | 1 | 1 | 1 |
| 4th | 3 | 3 | 1 |
| 6th | 15 | 15 | 1 |
| 8th | 105 | 105 | 1 |
| 10th | 945 | 947 | 1 |
| 12th | 10,395 | 10,428 | 1 |
| 14th | 135,135 | 135,524 | 1 |
| 16th | 2,027,025 | 2,025,880 | 1 |
| 18th | 34,459,425 | 34,102,797 | 1 |
| 20th | 654,729,075 | 634,790,833 | 1 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shakeel, I.; Hilliard, J.; Zhang, W.; Rice, M. Gaussian-Distributed Spread-Spectrum for Covert Communications. Sensors 2023, 23, 4081. https://doi.org/10.3390/s23084081
Shakeel I, Hilliard J, Zhang W, Rice M. Gaussian-Distributed Spread-Spectrum for Covert Communications. Sensors. 2023; 23(8):4081. https://doi.org/10.3390/s23084081
Chicago/Turabian StyleShakeel, Ismail, Jack Hilliard, Weimin Zhang, and Mark Rice. 2023. "Gaussian-Distributed Spread-Spectrum for Covert Communications" Sensors 23, no. 8: 4081. https://doi.org/10.3390/s23084081
APA StyleShakeel, I., Hilliard, J., Zhang, W., & Rice, M. (2023). Gaussian-Distributed Spread-Spectrum for Covert Communications. Sensors, 23(8), 4081. https://doi.org/10.3390/s23084081





