Detection and Mitigation of SYN Flooding Attacks through SYN/ACK Packets and Black/White Lists
Abstract
1. Introduction
- The method proposed in this paper reduces about half of the malicious traffic, improves detection accuracy by 2%, and reduces the usage of registers by half compared to existing methods.
- To detect and mitigate more malicious traffic compared with the TCP reset method, which only records IP addresses in a whitelist, our proposed method adds a blacklist and records MAC addresses instead to prevent attackers from changing IP addresses too often and being detected.
- The proposed method is implemented on bmv2 P4 software switch by combining revised cuckoo hashing, a detection module, a and mitigation module. The experimental results prove that it is more advantageous than the existing methods.
2. Related Works
2.1. SYN Flooding Attack
2.2. Attack to Encryption and Blockchain
3. Proposed Scheme
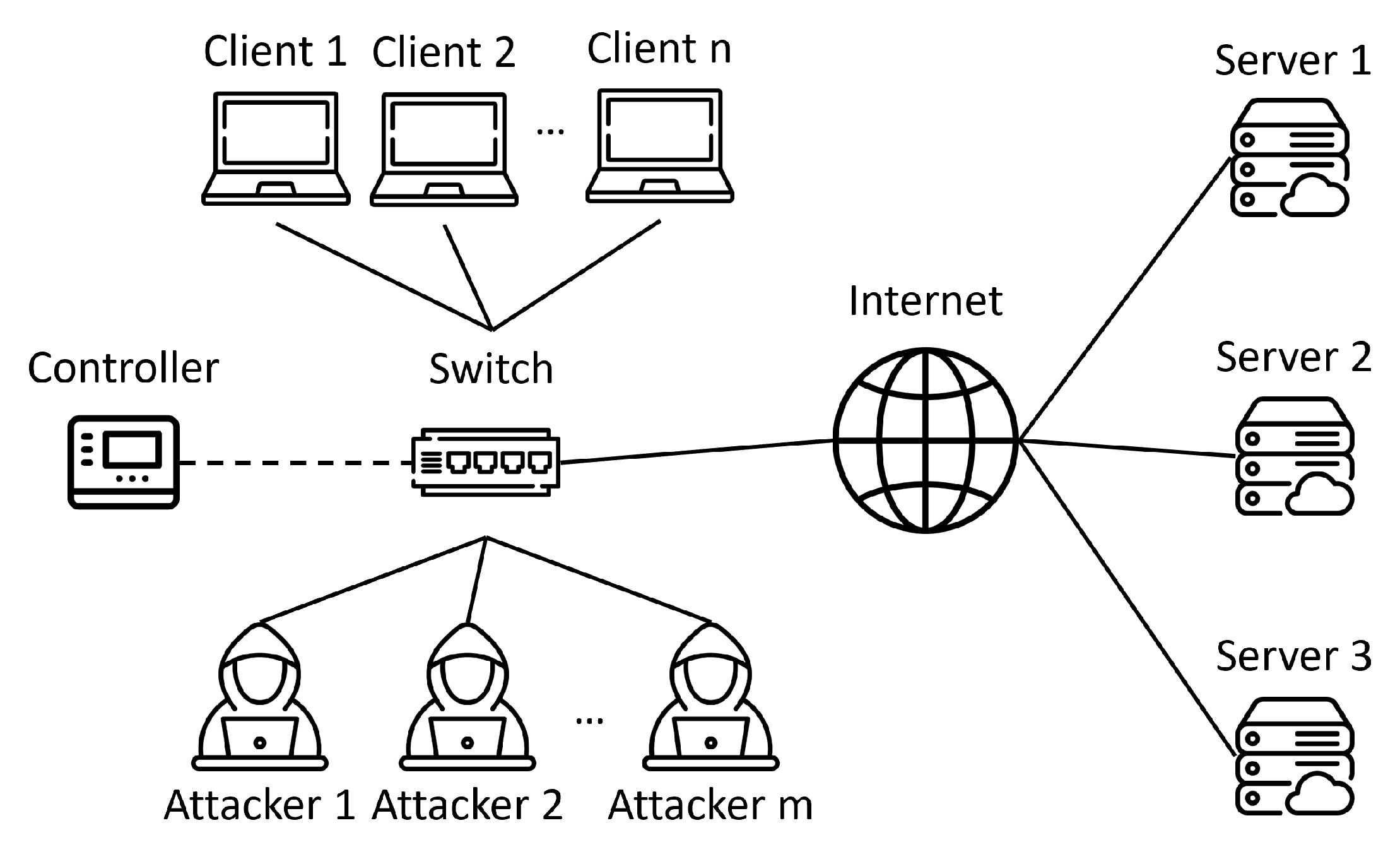
3.1. Framework of the Proposed Method
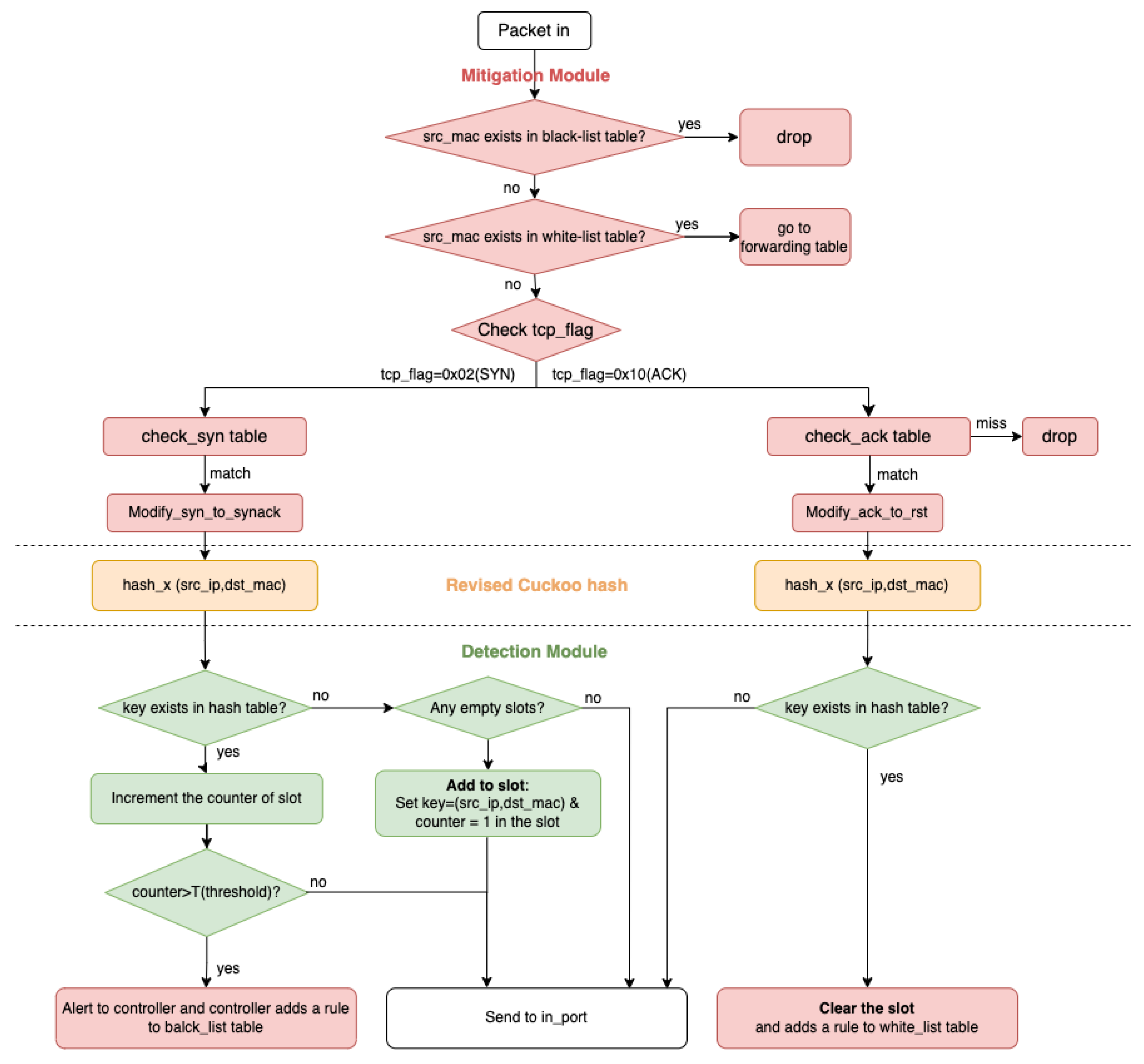
3.2. Revised Cuckoo Hashing
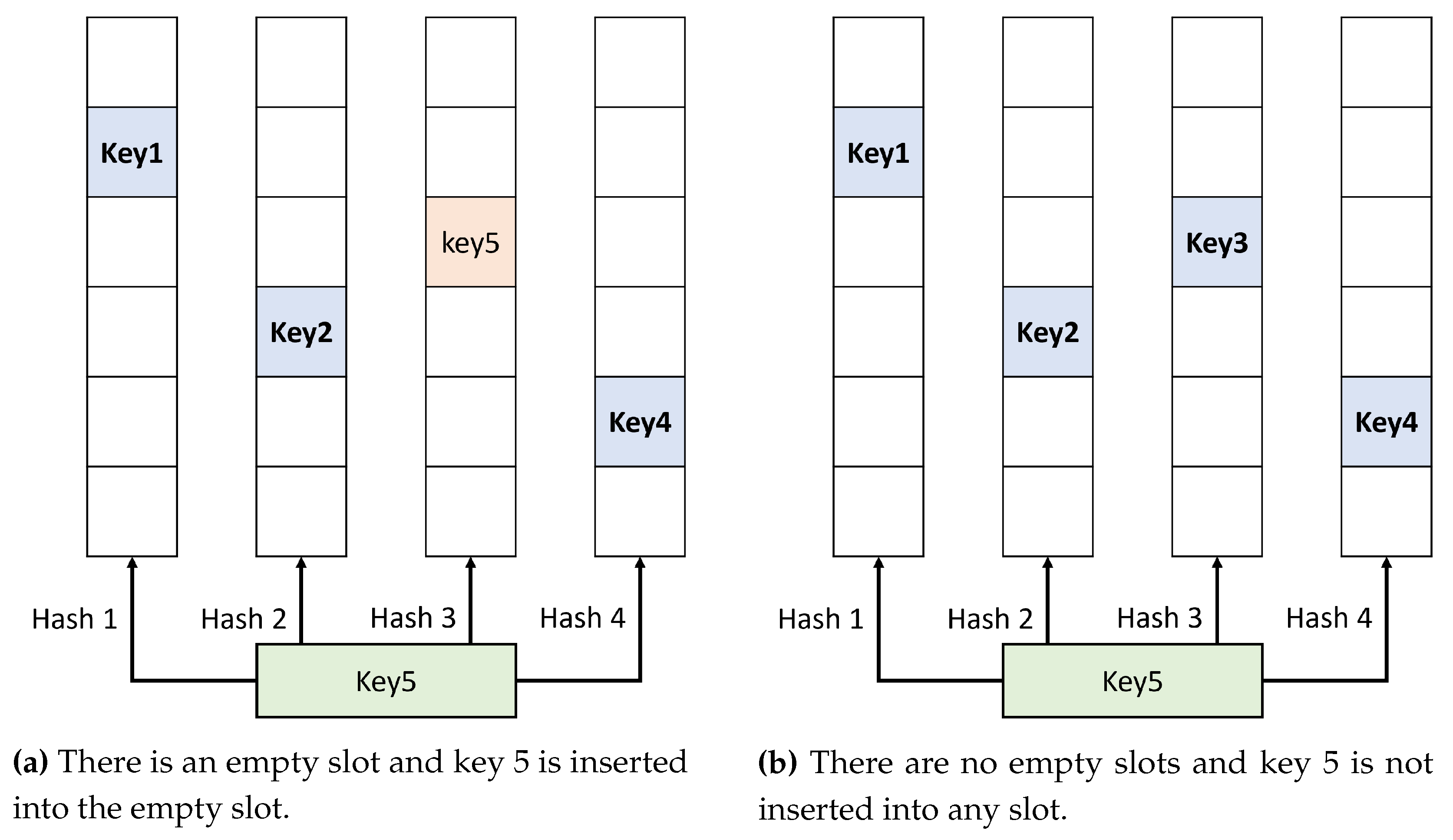
3.3. Detection Module
3.3.1. Add to a Slot
| Algorithm 1 Add to a slot |
| Require: a hash table with N slots, ; each slot contains three fields: , , ; an array with k random numbers, ; the length of a bucket, ; the threshold, T; |
| 1: procedure ADD-A-SLOT(, ) |
| 2: |
| 3: |
| 4: for to k do |
| 5: |
| 6: |
| 7: |
| 8: |
| 9: if and then |
| 10: |
| 11: |
| 12: else if and then |
| 13: |
| 14: if then |
| 15: |
| 16: |
| 17: end if |
| 18: |
| 19: |
| 20: end if |
| 21: end for |
| 22: if and then |
| 23: |
| 24: end if |
| 25: end procedure |
3.3.2. Clear the Slot
| Algorithm 2 Clear the slot |
| Require: a hash table with N slots, ; each slot contains three fields: , , ; an array with k random numbers, ; the length of a bucket, ; |
| 1: procedure CLEAR-SLOT(, ) |
| 2: |
| 3: |
| 4: for to k do |
| 5: |
| 6: |
| 7: |
| 8: |
| 9: if and then |
| 10: |
| 11: end if |
| 12: end for |
| 13: end procedure |
3.4. Mitigation Module
- blacklist table: Block the MAC address of the attacker.
- whitelist table: Check the source MAC address of the packet. If there is a matching entry, the packet will be forwarded. Otherwise, the SYN packet will be put into the check-syn table, the ACK packet will be put into the check-ack table, and the rest of the packet will be dropped.
- forwarding table: Forward the packets to the corresponding output port.
- check-syn table: If a packet matches one of the 256 entries, modify_syn_to_synack is executed and the attacker is detected.
- check-ack table: Verify the ACK number of the packet. If the ACK number is correct, then run modify_ack_to_rst and detect the attacker. Otherwise, the packet is discarded.
4. Performance Evaluation
4.1. Simulation Environment
4.2. Experiments
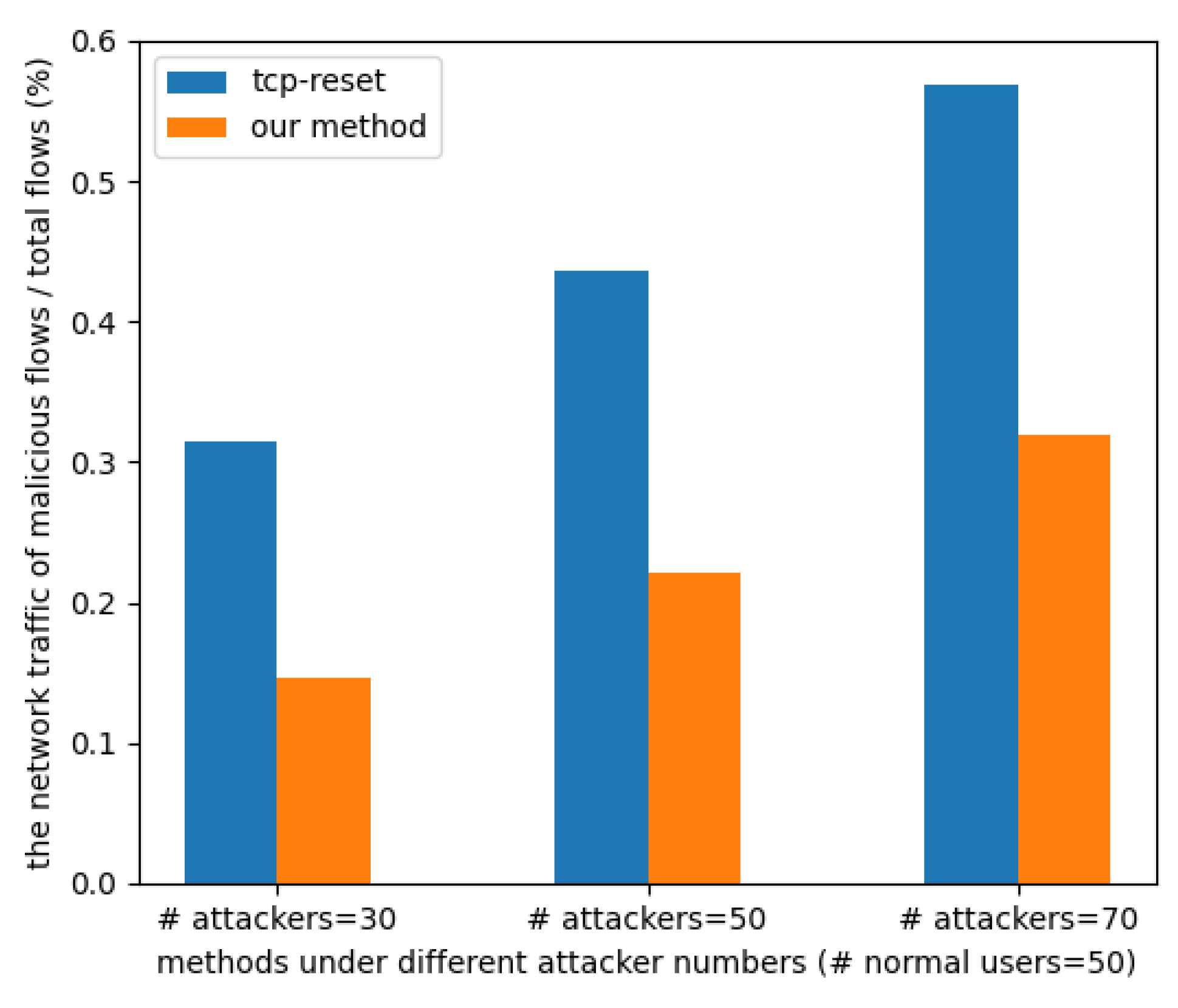
- Experiment 1: Compare the traffic amount of our method and TCP reset.
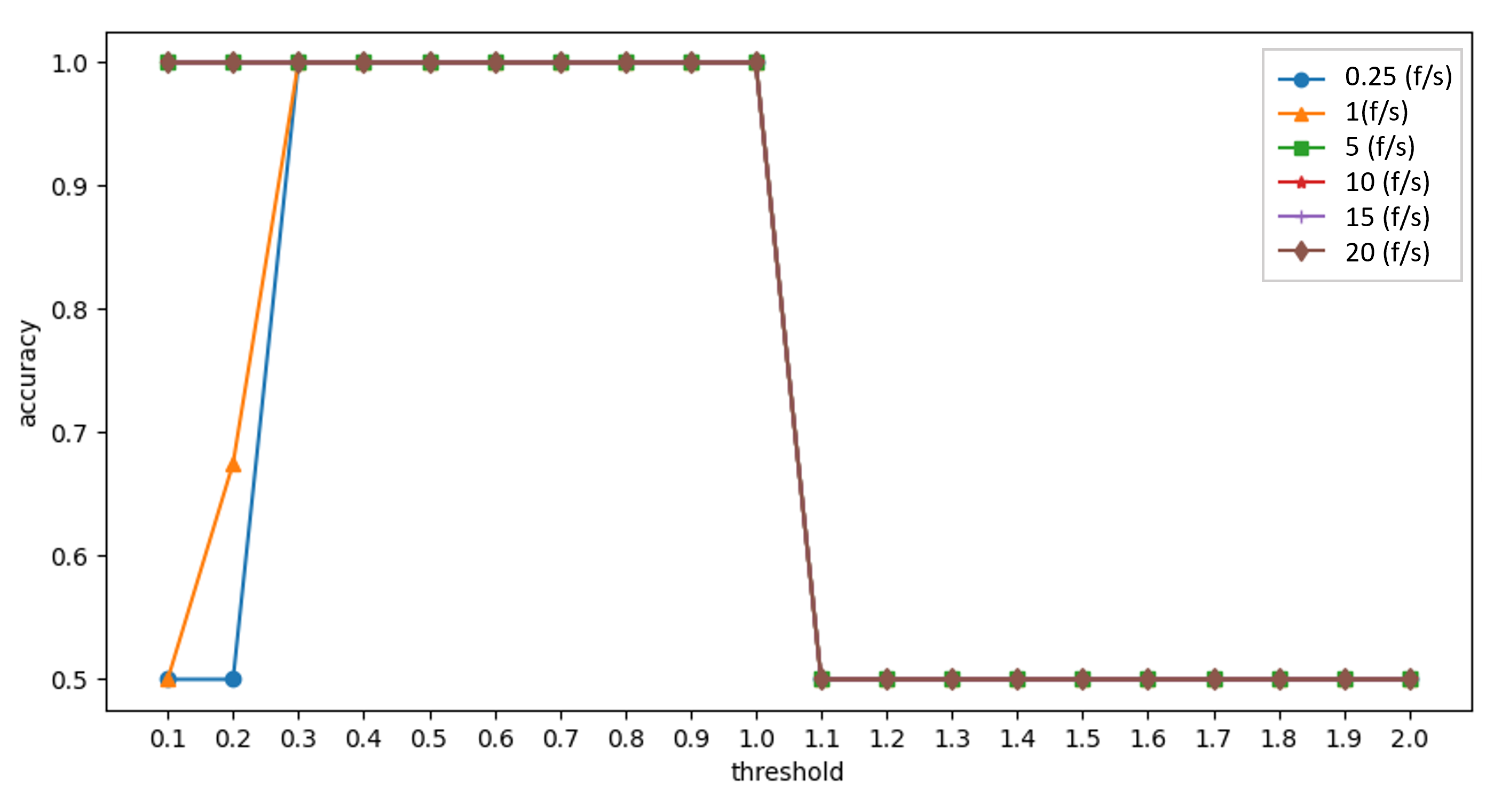
- Experiment 2: Set the thresholds for the Bloom filter method.
- Experiment 3 and 4: Compare the detection accuracy of our method and the Bloom filter method in the high/low-rate attack and normal user.
- Experiment 5: Compare the required register size of our method and the Bloom filter method in the same situation.
4.2.1. Experiment 1: Compare the Traffic Amount of Our Method and TCP Reset
4.2.2. Experiment 2: Set the Thresholds for the Bloom Filter Method
4.2.3. Experiments 3 and 4: Compare the Detection Accuracy of thE Proposed Method with the Bloom Filter Method for High- and Low-Rate Attacks
High-Rate Attack
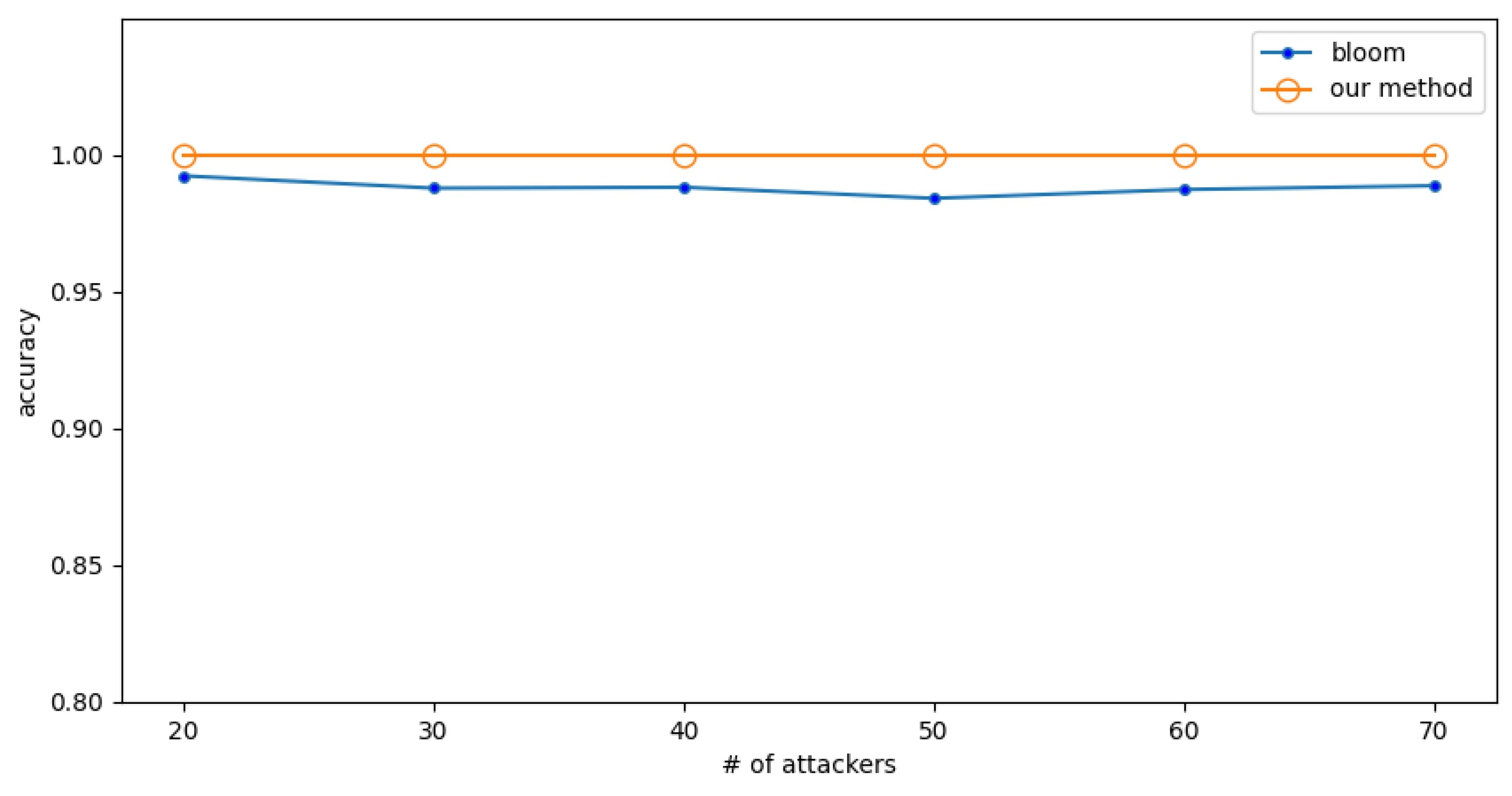

Low-Rate Attack


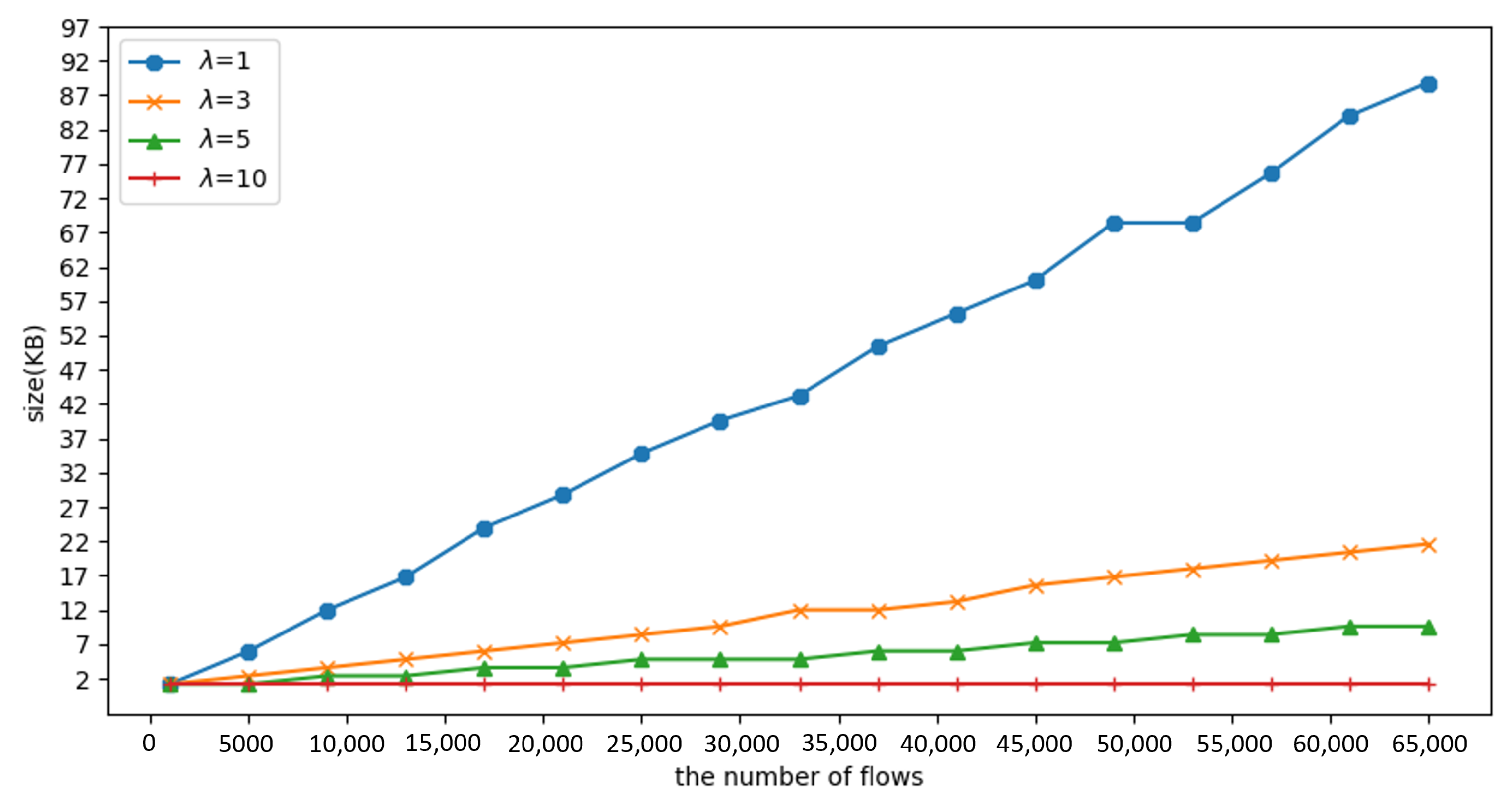
4.2.4. Experiment 5: Evaluate the Required Size of Register
5. Conclusions and Future Work
5.1. Conclusions
5.2. Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Kreutz, D.; Ramos, F.; Verı´ssimo, P.; Rothenberg, C.; Azodolmolky, S.; Uhlig, S. Software-Defined Networking: A Comprehensive Survey. Proc. IEEE 2014, 103, 14–76. [Google Scholar] [CrossRef]
- Bouyeddou, B.; Kadri, B.; Harrou, F.; Sun, Y. DDOS-attacks detection using an efficient measurement-based statistical mechanism. Eng. Sci. Technol. Int. J. 2020, 23, 870–878. [Google Scholar] [CrossRef]
- Hill, J.; Aloserij, M.; Grosso, P. Tracking Network Flows with P4. In Proceedings of the 2018 IEEE/ACM Innovating the Network for Data-Intensive Science (INDIS), Dallas, TX, USA, 11 November 2018. [Google Scholar]
- Lin, T.Y.; Wu, J.P.; Hung, P.H.; Shao, C.H.; Wang, Y.T.; Cai, Y.Z.; Tsai, M.H. Mitigating SYN flooding attack and ARP spoofing in SDN data plane. In Proceedings of the 2020 21st Asia-Pacific Network Operations and Management Symposium (APNOMS), Daegu, Republic of Korea, 22–25 September 2020; pp. 114–119. [Google Scholar]
- Bosshart, P.; Daly, D.; Gibb, G.; Izzard, M.; McKeown, N.; Rexford, J.; Schlesinger, C.; Talayco, D.; Vahdat, A.; Varghese, G.; et al. P4: Programming protocol-independent packet processors. ACM SIGCOMM Comput. Commun. Rev. 2014, 44, 87–95. [Google Scholar] [CrossRef]
- Pagh, R.; Rodler, F.F. Cuckoo hashing. J. Algorithms 2004, 51, 122–144. [Google Scholar] [CrossRef]
- Luo, L.; Guo, D.; Ma, R.T.B.; Rottenstreich, O.; Luo, X. Network anti-spoofing with SDN data plane. In Proceedings of the IEEE INFOCOM 2017—IEEE Conference on Computer Communications, Atlanta, GA, USA, 1–4 May 2017. [Google Scholar]
- Lin, T.Y.; Wang, C.Y.; Tuan, Y.P.; Tsai, M.H.; Chenz, Y.R. A Study on Traffic Asymmetry for Detecting DDoS Attack in P4-based SDN. J. Inf. Sci. Eng. 2022, 38, 1265–1283. [Google Scholar] [CrossRef]
- Almaiah, M.A.; Al-Zahrani, A.; Almomani, O.; Alhwaitat, A.K. Classification of cyber security threats on mobile devices and applications. In Artificial Intelligence and Blockchain for Future Cybersecurity Applications; Springer: Cham, Switzerland, 2021; pp. 107–123. [Google Scholar]
- Kumar, P.; Tripathi, M.; Nehra, A.; Conti, M.; Lal, C. SAFETY: Early Detection and Mitigation of TCP SYN Flood Utilizing Entropy in SDN. IEEE Trans. Netw. Serv. Manag. 2018, 15, 1545–1559. [Google Scholar] [CrossRef]
- Shannon, C.E. Prediction and Entropy of Printed English. Bell Syst. Tech. J. 1951, 30, 50–64. [Google Scholar] [CrossRef]
- Mohammadi, R.; Javidan, R.; Conti, M. SLICOTS: An SDN-Based Lightweight Countermeasure for TCP SYN Flooding Attacks. IEEE Trans. Netw. Serv. Manag. 2017, 14, 487–497. [Google Scholar] [CrossRef]
- Ahmed, M.N.; Abdullah, A.H.; Chizari, H.; Kaiwartya, O. F3TM: Flooding Factor based Trust Management Framework for secure data transmission in MANETs. J. King Saud Univ.-Comput. Inf. Sci. 2017, 29, 269–280. [Google Scholar] [CrossRef]
- Kumar, S.; Singh, K.; Kumar, S.; Kaiwartya, O.; Cao, Y.; Zhou, H. Delimitated anti jammer scheme for Internet of vehicle: Machine learning based security approach. IEEE Access 2019, 7, 113311–113323. [Google Scholar] [CrossRef]
- Paolucci, F.; Civerchia, F.; Sgambelluri, A.; Giorgetti, A.; Cugini, F.; Castoldi, P. P4 Edge node enabling stateful traffic engineering and cyber security. J. Opt. Commun. Netw. 2019, 11, A84–A95. [Google Scholar] [CrossRef]
- Friday, K.; Kfoury, E.; Bou-Harb, E.; Crichigno, J. Towards a Unified In-Network DDoS Detection and Mitigation Strategy. In Proceedings of the IEEE Conference on Network Softwarization (NetSoft), Ghent, Belgium, 29 June–3 July 2020. [Google Scholar]
- Luo, L.; Guo, D.; Ma, R.T.B.; Rottenstreich, O.; Luo, X. Optimizing Bloom Filter: Challenges, Solutions, and Comparisons. IEEE Commun. Surv. Tutor. 2018, 21, 1912–1949. [Google Scholar] [CrossRef]
- Almaiah, M.A.; Dawahdeh, Z.; Almomani, O.; Alsaaidah, A.; Al-Khasawneh, A.; Khawatreh, S. A new hybrid text encryption approach over mobile ad hoc network. Int. J. Electr. Comput. Eng. (IJECE) 2020, 10, 6461–6471. [Google Scholar] [CrossRef]
- Ali, A.; Almaiah, M.A.; Hajjej, F.; Pasha, M.F.; Fang, O.H.; Khan, R.; Teo, J.; Zakarya, M. An industrial IoT-based blockchain-enabled secure searchable encryption approach for healthcare systems using neural network. Sensors 2022, 22, 572. [Google Scholar] [CrossRef]
- Open Networking Foundation. Mininet. 2014. Available online: http://mininet.org/ (accessed on 6 April 2023).
- Open Networking Foundation. Bmv2. 2022. Available online: https://github.com/p4lang/behavioral-model (accessed on 6 April 2023).
- Cai, Y.Z.; Lai, C.H.; Wang, Y.T.; Tsai, M.H. Improving scanner data collection in p4-based sdn. In Proceedings of the 2020 21st Asia-Pacific Network Operations and Management Symposium (APNOMS), Daegu, Republic of Korea, 22–25 September 2020; pp. 126–131. [Google Scholar]
- Stenberg, D. Curl. 1996. Available online: https://curl.se/ (accessed on 6 April 2023).
- Sanfilippo, S. Hping3. 2006. Available online: http://wiki.hping.org/ (accessed on 6 April 2023).
- Zhijun, W.; Wenjing, L.; Liang, L.; Meng, Y. Low-Rate DoS Attacks, Detection, Defense, and Challenges: A Survey. IEEE Access 2020, 8, 43920–43943. [Google Scholar] [CrossRef]

Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yang, C.-H.; Wu, J.-P.; Lee, F.-Y.; Lin, T.-Y.; Tsai, M.-H. Detection and Mitigation of SYN Flooding Attacks through SYN/ACK Packets and Black/White Lists. Sensors 2023, 23, 3817. https://doi.org/10.3390/s23083817
Yang C-H, Wu J-P, Lee F-Y, Lin T-Y, Tsai M-H. Detection and Mitigation of SYN Flooding Attacks through SYN/ACK Packets and Black/White Lists. Sensors. 2023; 23(8):3817. https://doi.org/10.3390/s23083817
Chicago/Turabian StyleYang, Chun-Hao, Jhen-Ping Wu, Fang-Yi Lee, Ting-Yu Lin, and Meng-Hsun Tsai. 2023. "Detection and Mitigation of SYN Flooding Attacks through SYN/ACK Packets and Black/White Lists" Sensors 23, no. 8: 3817. https://doi.org/10.3390/s23083817
APA StyleYang, C.-H., Wu, J.-P., Lee, F.-Y., Lin, T.-Y., & Tsai, M.-H. (2023). Detection and Mitigation of SYN Flooding Attacks through SYN/ACK Packets and Black/White Lists. Sensors, 23(8), 3817. https://doi.org/10.3390/s23083817







