Steganography in IoT: Information Hiding with Joystick and Touch Sensors
Abstract
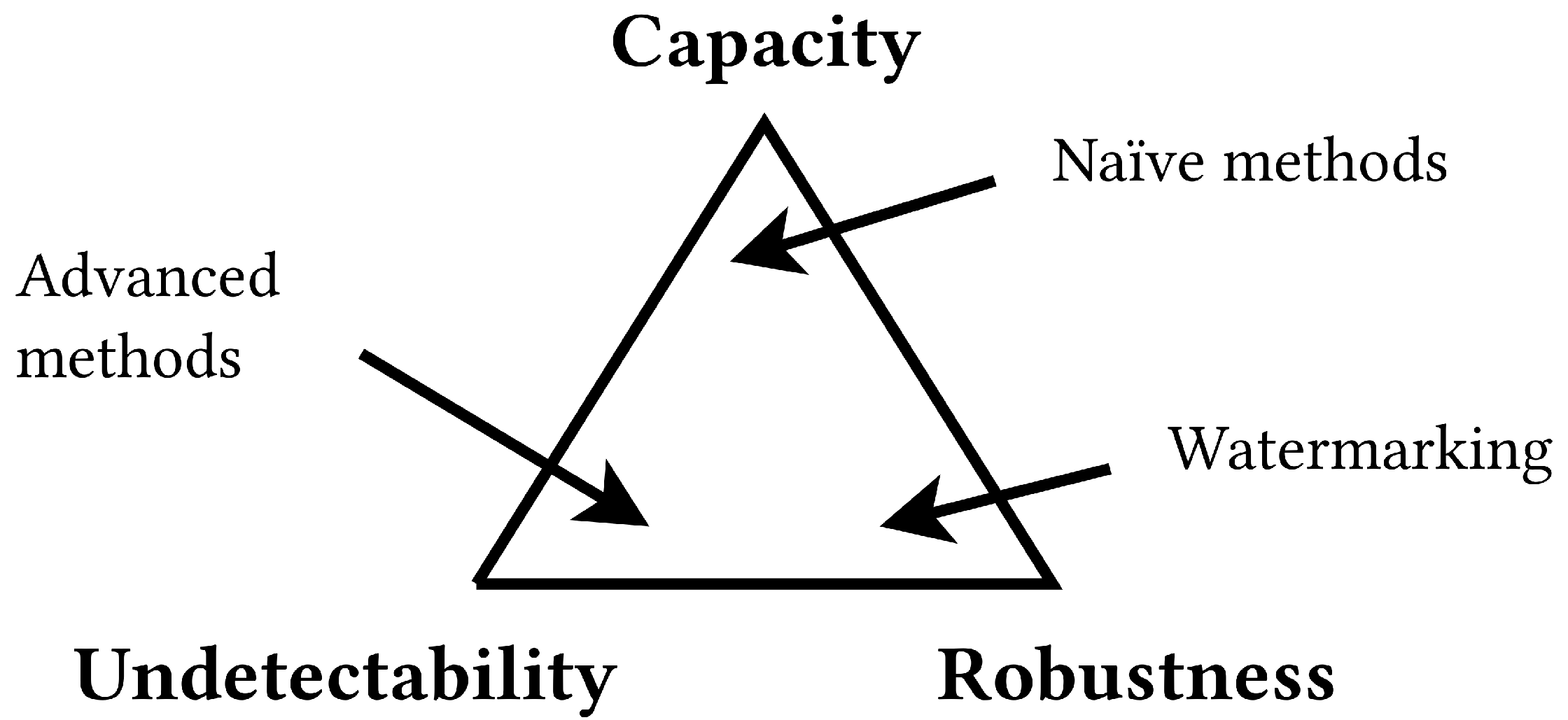
1. Introduction
2. Materials and Methods
2.1. Hardware
2.1.1. Platform
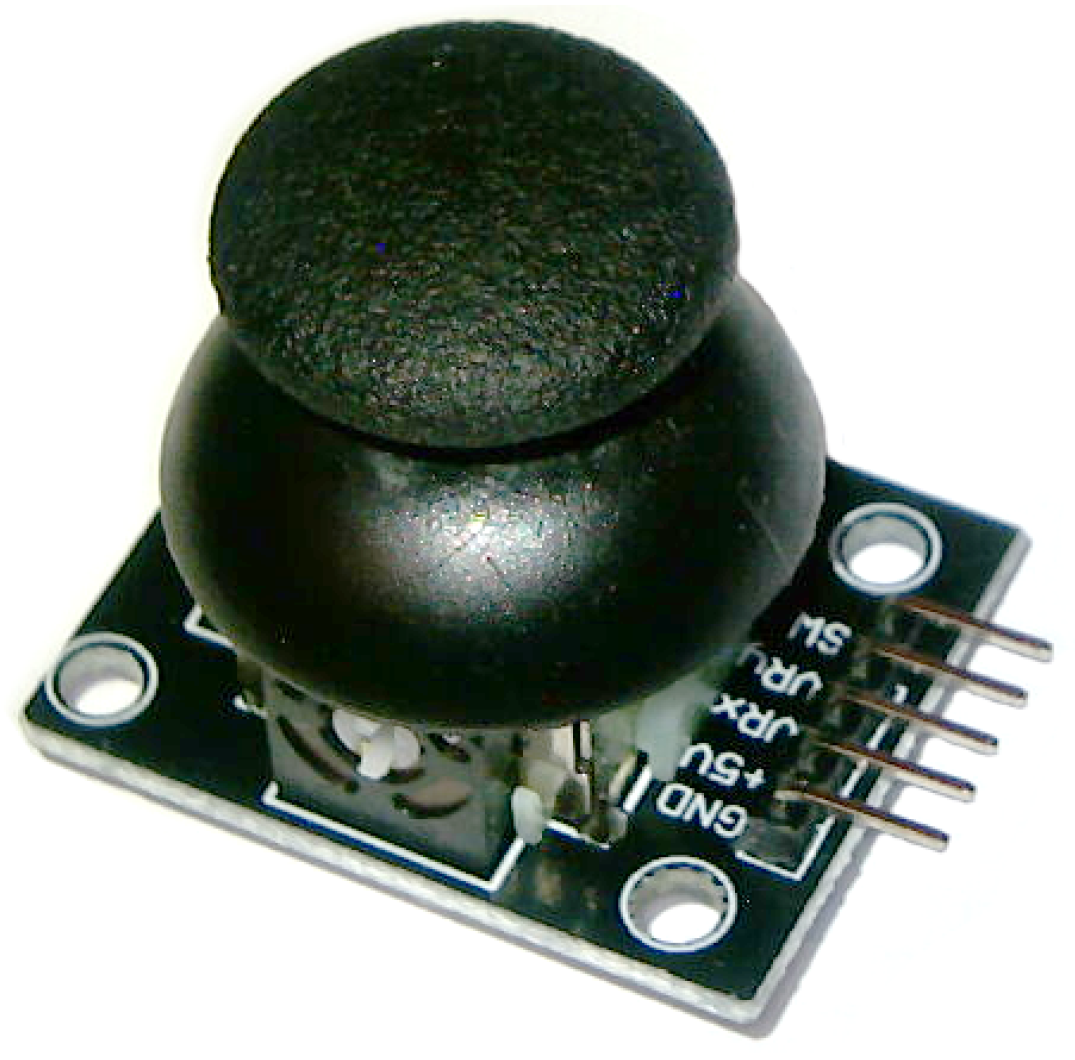
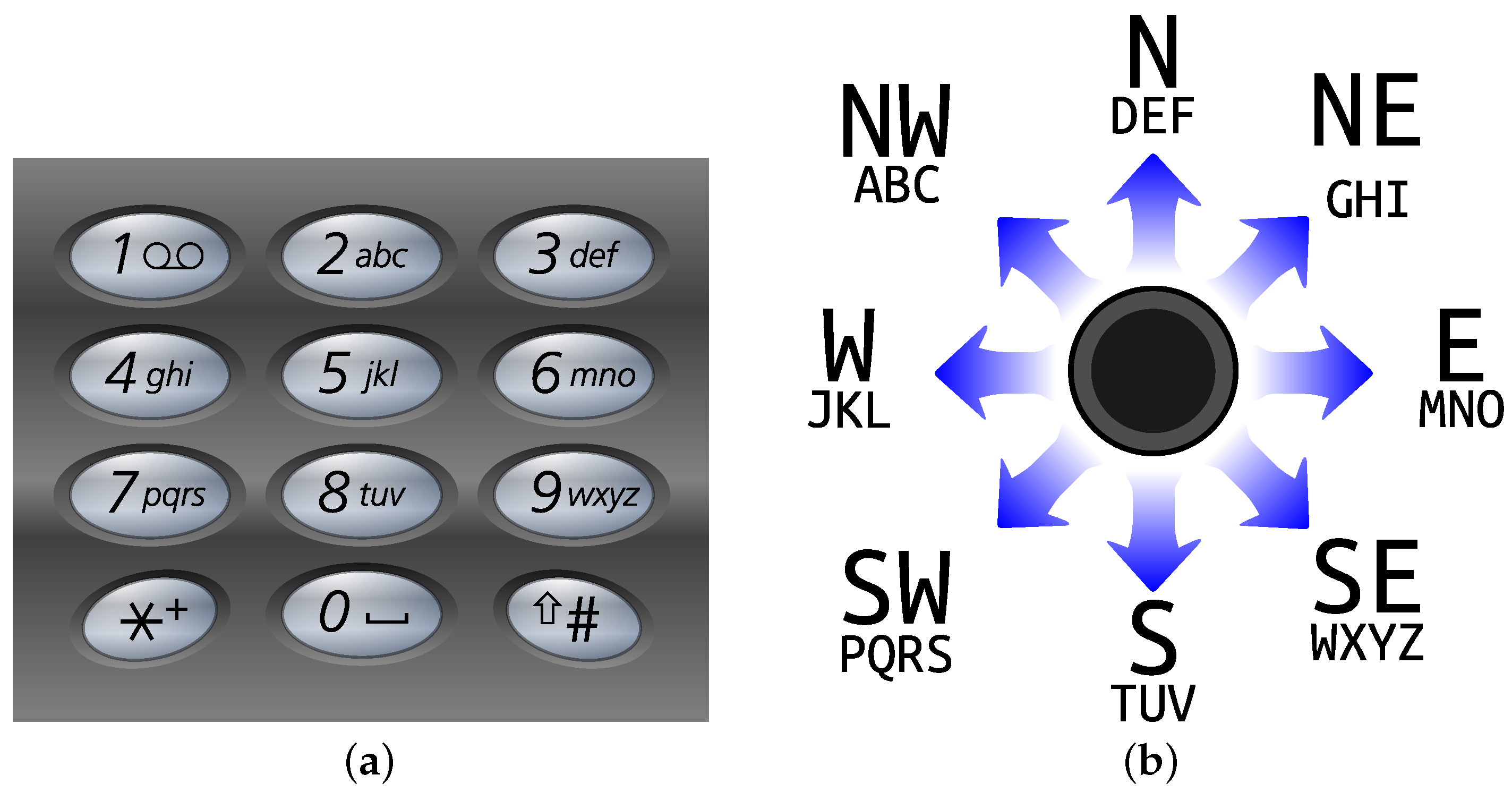
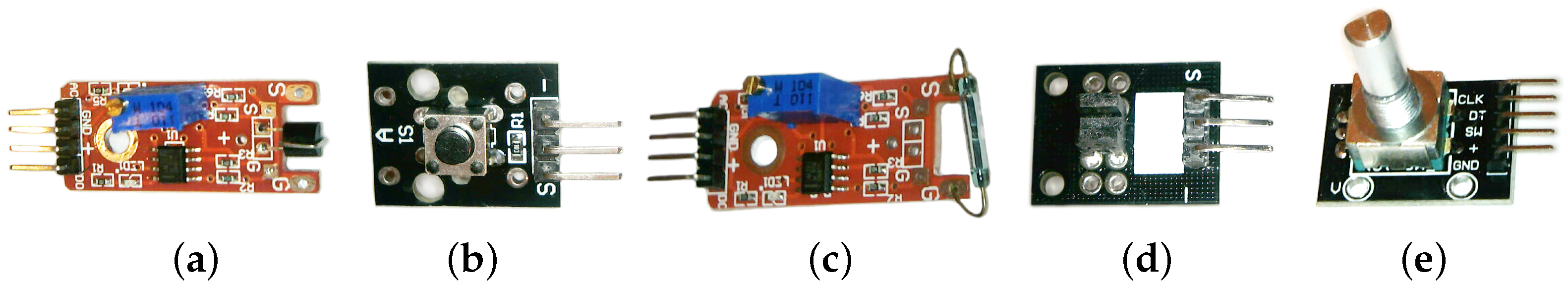
2.1.2. Thumb Joystick
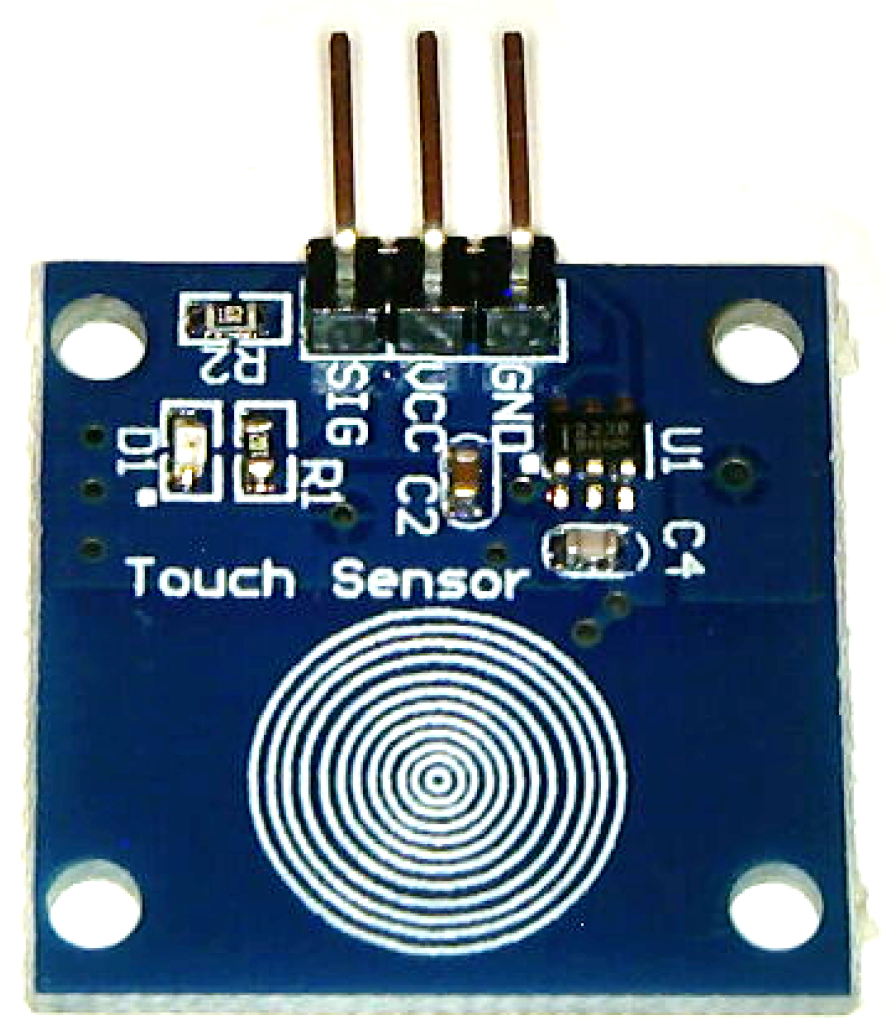
2.1.3. Touch Sensor
2.2. Software
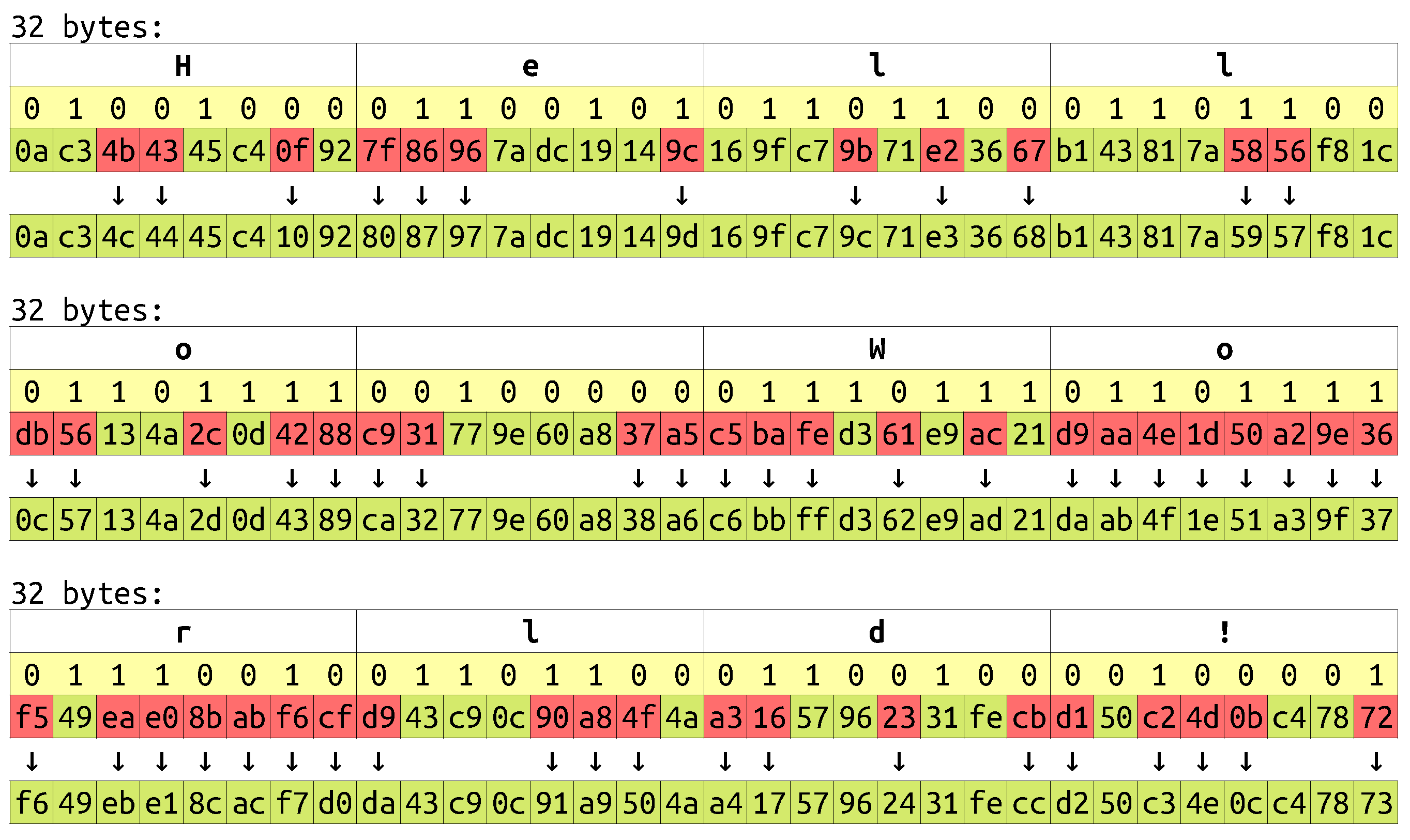
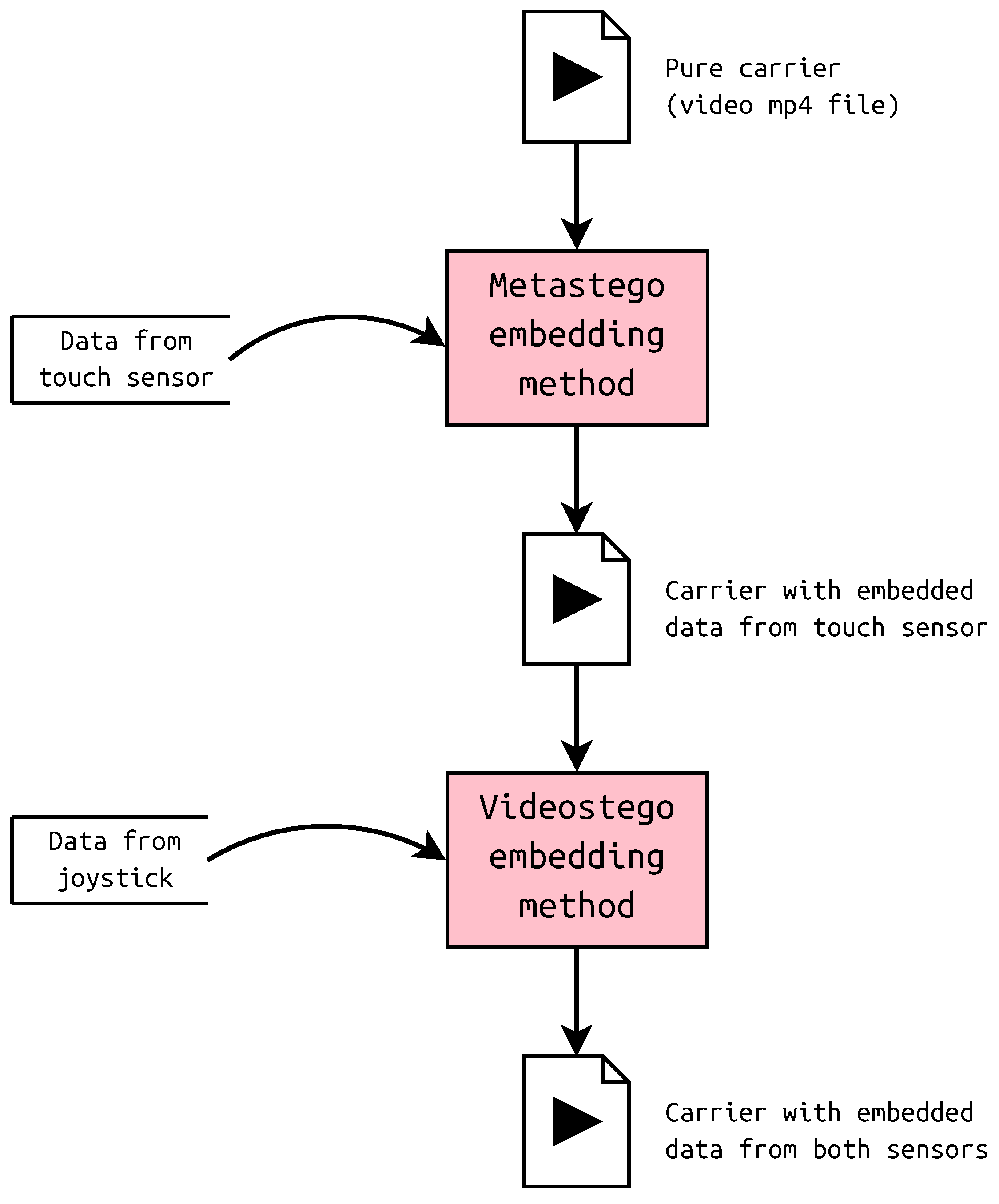
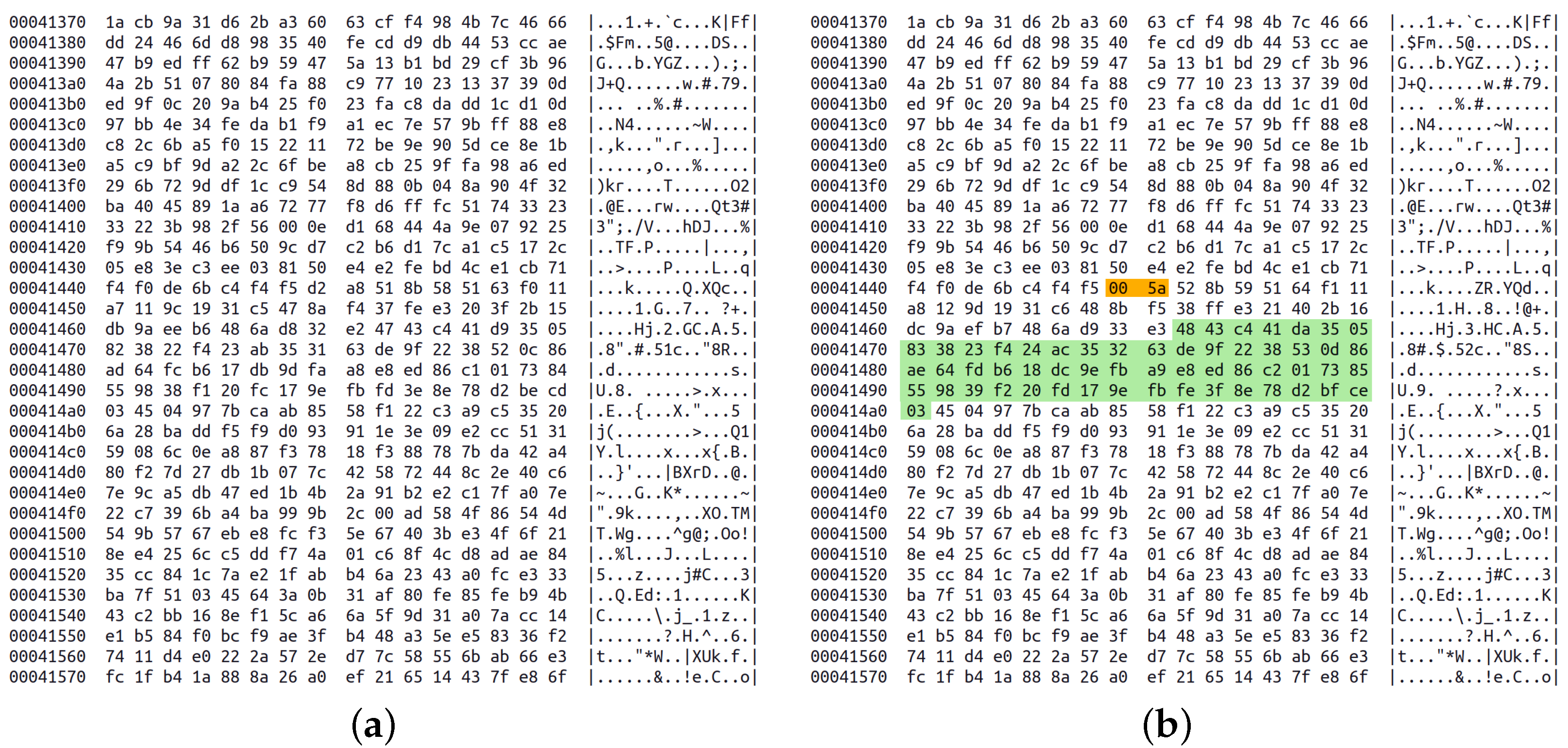
2.2.1. Videostego
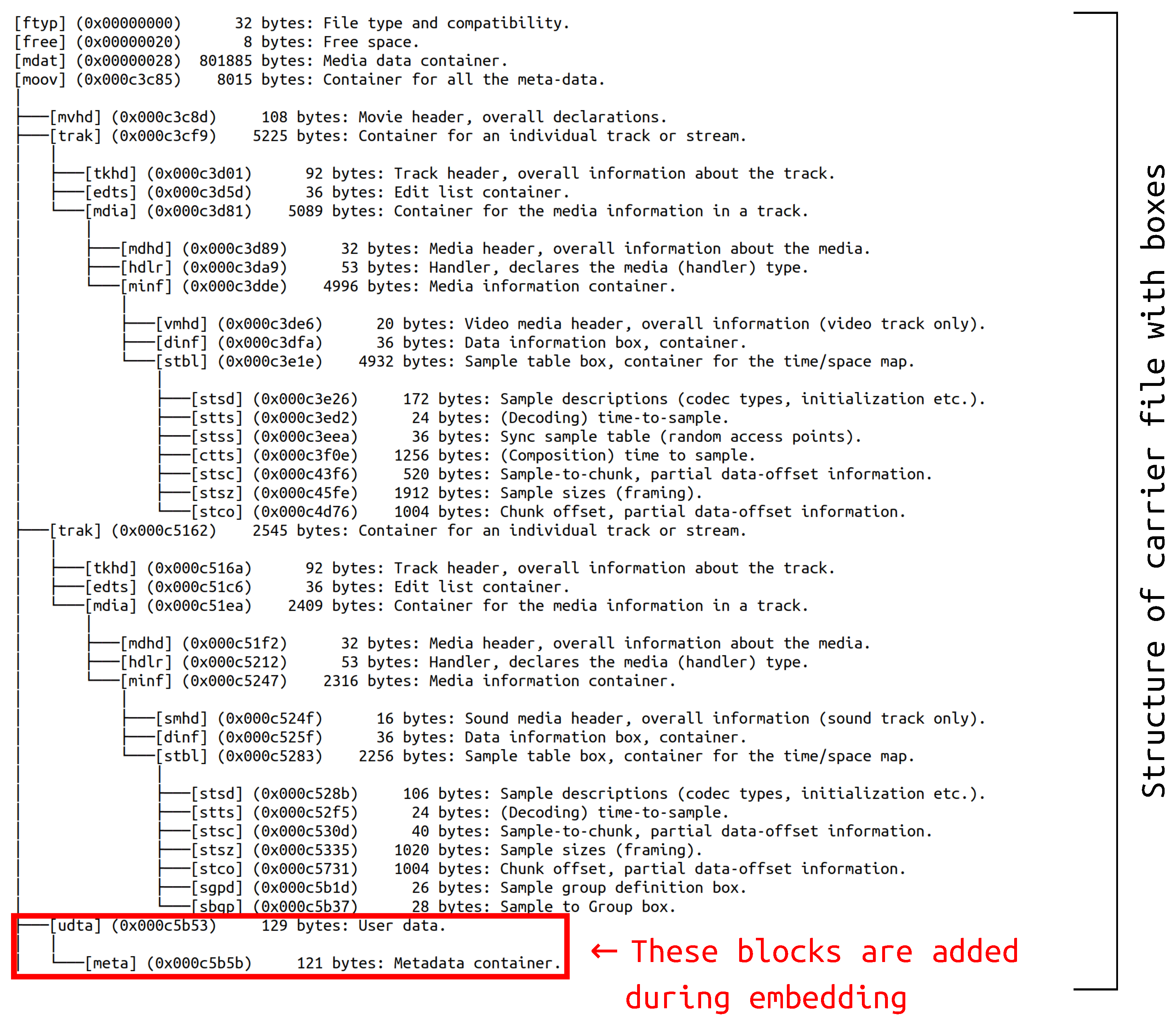
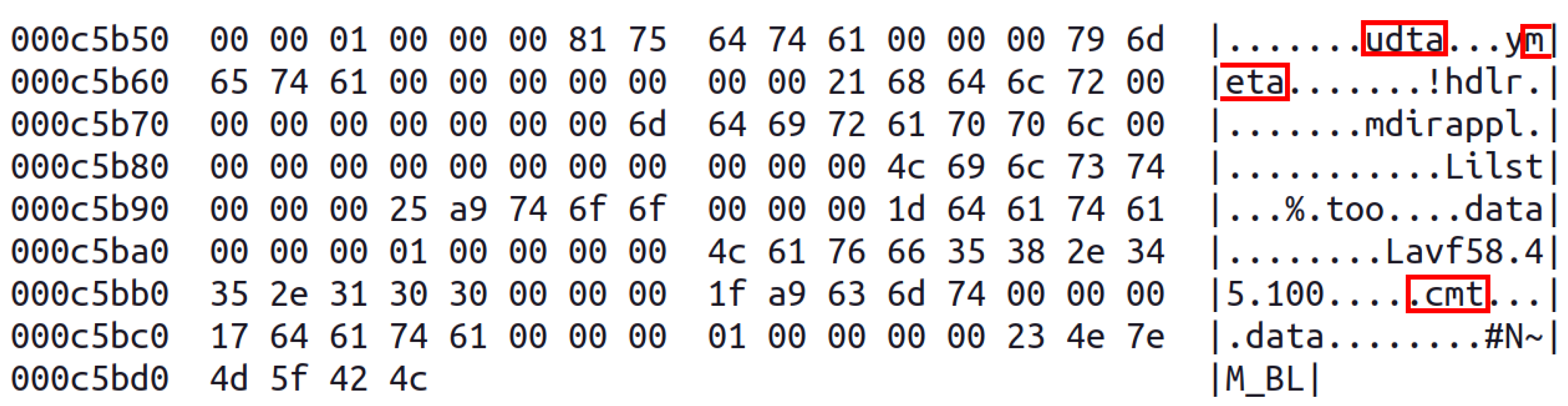
2.2.2. Metastego
3. Results
4. Discussion
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Liu, M.; Guo, Y.; Zhou, L. Text steganography based on online chat. In Proceedings of the Fifth International Conference on Intelligent Information Hiding and Multimedia Signal Processing, Kyoto, Japan, 12–14 September 2009; pp. 807–810. [Google Scholar]
- Wang, Z.-H.; Chang, C.-C.; Kieu, T.D.; Li, M.-C. Emoticon-based text steganography in chat. In Proceedings of the Asia-Pacific Conference on Computational Intelligence and Industrial Applications, Wuhan, China, 28–29 November 2009; Volume 2, pp. 457–460. [Google Scholar]
- Qazanfari, K.; Reza, S. A new steganography method which preserves histogram: Generalization of LSB++. Inf. Sci. 2014, 277, 90–101. [Google Scholar] [CrossRef]
- Westfeld, A. F5—A steganographic algorithm: High capacity despite better steganalysis. In Proceedings of the 4th International Workshop on Information Hiding, Pittsburgh, PA, USA, 25–27 April 2001; pp. 289–302. [Google Scholar]
- Provos, N. Defending against statistical steganalysis. In Proceedings of the 10th Conference on USENIX Security Symposium, Washington, DC, USA, 13–17 August 2001; Volume 10, p. 24. [Google Scholar]
- Saha, A.; Halder, S.; Kollya, S. Image steganography using 24-bit bitmap images. In Proceedings of the 14th International Conference on Computer and Information Technology, Dhaka, Bangladesh, 22–24 December 2011; pp. 56–60. [Google Scholar]
- Furuta, T.; Noda, H.; Niimi, M.; Kawaguchi, E. Bit-plane decomposition steganography using wavelet compressed video. In Proceedings of the Fourth International Conference on Information, Communications and Signal Processing and the Fourth Pacific Rim Conference on Multimedia, Singapore, 15–18 December 2003; Volume 2, pp. 970–974. [Google Scholar]
- Bin, H.; Li-Yi, Z.; Wei-Dong, Z. A novel steganography algorithm based on motion vector and matrix encoding. In Proceedings of the IEEE 3rd International Conference on Communication Software and Networks, Xi’an, China, 27–29 May 2011; pp. 406–409. [Google Scholar]
- Nair, A.S.; Kumar, A.; Sur, A.; Nandi, S. Length based network steganography using UDP protocol. In Proceedings of the IEEE 3rd International Conference on Communication Software and Networks, Xi’an, China, 27–29 May 2011; pp. 726–730. [Google Scholar]
- Savateev, E.O. Design of the steganography system based on the version 4 Internet protocol. In Proceedings of the Siberian Conference on Control and Communications, Tomsk, Russia, 21–22 October 2005; pp. 38–51. [Google Scholar]
- Murdoch, S.J.; Lewis, S. Embedding Covert Channels into TCP/IP; Springer: Berlin/Heidelberg, Germany, 2005; pp. 247–261. [Google Scholar]
- Kipper, G. Investigator’s Guide to Steganography; CRC Press LLC: Boca Raton, FL, USA, 2004. [Google Scholar]
- Castiglione, A.; De Santis, A.; Soriente, C. Taking advantages of a disadvantage: Digital forensics and steganography using document metadata. J. Syst. Softw. 2007, 80, 750–764. [Google Scholar] [CrossRef]
- Castiglione, A.; D’Alessio, B.; De Santis, A.; Palmieri, F. New steganographic techniques for the OOXML file format. In Proceedings of the IFIP WG 8.4/8.9 International Cross Domain Conference on Availability, Reliability and Security for Business, Enterprise and Health Information Systems, Vienna, Austria, 22–26 August 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 344–358. [Google Scholar]
- Li, Z.; Sun, X.; Wang, B.; Wang, X. A steganography scheme in P2P network. In Proceedings of the International Conference on Intelligent Information Hiding and Multimedia Signal Processing, Harbin, China, 15–17 August 2008; pp. 20–24. [Google Scholar]
- Shirali-Shahreza, M.; Shirali-Shahreza, S. Steganography in TEX documents. In Proceedings of the 3rd International Conference on Intelligent System and Knowledge Engineering, Xiamen, China, 17–19 November 2008; Volume 1, pp. 1363–1366. [Google Scholar]
- Ogiela, M.R.; Koptyra, K. False and multi-secret steganography in digital images. Soft Comput. 2015, 19, 3331–3339. [Google Scholar] [CrossRef]
- Koptyra, K.; Ogiela, M.R. Embedding Strategies in multi-secret steganography. In Advances on P2p, Parallel, Grid, Cloud and Internet Computing, Lecture Notes on Data Engineering and Communications Technologies; Springer International Publishing: Cham, Switzerland, 2017; 2p. [Google Scholar] [CrossRef]
- Zakaria, A.; Hussain, M.; Wahid, A.; Idris, M.; Abdullah, N.; Jung, K.H. High-Capacity Image Steganography with Minimum Modified Bits Based on Data Mapping and LSB Substitution. Appl. Sci. 2018, 8, 2199. [Google Scholar] [CrossRef]
- Mohamed, M.; Mohamed, L. High Capacity Image Steganography Technique based on LSB Substitution Method. Appl. Math. Inf. Sci. 2016, 10, 259–266. [Google Scholar] [CrossRef]
- Saghir, B.; Ahmed, E.; Zen Alabdeen Salh, G.; Mansour, A. A Spatial Domain Image Steganography Technique Based on Pseudorandom Permutation Substitution Method using Tree and Linked List. Int. J. Eng. Trends Technol. 2015, 23, 209–217. [Google Scholar] [CrossRef]
- Gulve, A.; Joshi, M. A High Capacity Secured Image Steganography Method with Five Pixel Pair Differencing and LSB Substitution. Int. J. Image Graph. Signal Process. 2015, 7, 66–74. [Google Scholar] [CrossRef]
- Kasapbaşı, M.C.; Elmasry, W. New LSB-based colour image steganography method to enhance the efficiency in payload capacity, security and integrity check. Sādhanā 2018, 43, 68. [Google Scholar] [CrossRef]
- Das, A.; Das, P.; Chakraborty, K.; Sinha, S. A New Image Steganography Method using Message Bits Shuffling. J. Mech. Contin. Math. Sci. 2018, 13, 1–15. [Google Scholar] [CrossRef]
- Shete, K.; Patil, M.; Chitode, J. Least Significant Bit and Discrete Wavelet Transform Algorithm Realization for Image Steganography Employing FPGA. Int. J. Image Graph. Signal Process. 2016, 8, 48–56. [Google Scholar] [CrossRef]
- Bergman, C.; Davidson, J. Unitary embedding for data hiding with the SVD. In Security, Steganography, and Watermarking of Multimedia Contents VII; International Society for Optics and Photonics: Bellingham, WA, USA, 2005; Volume 5681, pp. 619–630. [Google Scholar]
- Chung, K.L.; Yang, W.N.; Huang, Y.H.; Wu, S.T.; Hsu, Y.C. On SVD-based watermarking algorithm. Appl. Math. Comput. 2007, 188, 54–57. [Google Scholar] [CrossRef]
- Chang, C.C.; Lin, C.C.; Hu, Y.S. An SVD oriented watermark embedding scheme with high qualities for the restored images. Int. J. Innov. Comput. Inf. Control 2007, 3, 609–620. [Google Scholar]
- Chanu, Y.J.; Singh, K.M.; Tuithung, T. A Robust Steganographic Method based on Singular Value Decomposition. Int. J. Inf. Comput. Technol. 2014, 4, 717–726. [Google Scholar]
- Hachaj, T.; Koptyra, K.; Ogiela, M.R. Eigenfaces-Based Steganography. Entropy 2021, 23, 273. [Google Scholar] [CrossRef]
- Hingorani, C.; Bhatia, R.; Pathai, O.; Mirani, T. Face Detection and Steganography Algorithms for Passport Issuing System. Int. J. Eng. Res. Technol. 2014, 3, 1438–1441. [Google Scholar]
- Raju, K.; Srivatsa, S. Video Steganography for Face Recognition with Signcryption for Trusted and Secured Authentication by using PCASA. Int. J. Comput. Appl. 2012, 56, 1–5. [Google Scholar] [CrossRef]
- Kadry, S.; Nasr, S. New Generating Technique for Image Steganography. Innova Cienc. 2012, 4, 46. [Google Scholar] [CrossRef]
- Zhang, H.; Hu, J.; Wang, G.; Zhang, Y. A steganography scheme based on fractal images. In Proceedings of the 2011 Second International Conference on Networking and Distributed Computing (ICNDC), Beijing, China, 21–24 September 2011; pp. 28–31. [Google Scholar]
- Castiglione, A.; De Santis, A.; Fiore, U.; Palmieri, F. An asynchronous covert channel using spam. Comput. Math. Appl. 2012, 63, 437–447. [Google Scholar] [CrossRef]
- Saračević, M.; Adamović, S.; Miškovic, V.; Maček, N.; Šarac, M. A novel approach to steganography based on the properties of Catalan numbers and Dyck words. Future Gener. Comput. Syst. 2019, 100, 186–197. [Google Scholar] [CrossRef]
- McAteer, I.; Ibrahim, A.; Guanglou, Z.; Yang, W.; Valli, C. Integration of Biometrics and Steganography: A Comprehensive Review. Technologies 2019, 7, 34. [Google Scholar] [CrossRef]
- Hassan, R.; Pepíć, S.; Saračević, M.; Ahmad, K.; Tasic, M. A Novel Approach to Data Encryption Based on Matrix Computations. Comput. Mater. Contin. 2020, 66, 1139–1153. [Google Scholar] [CrossRef]
- Hamid, N.; Yahya, A.; Ahmad, R.B.; Al-Qershi, O.M. Image Steganography Techniques: An Overview. Int. J. Comput. Sci. Secur 2012, 6, 168–187. [Google Scholar]
- Surana, J.; Sonsale, A.; Joshi, B.; Sharma, D.; Choudhary, N. Steganography Techniques. Int. J. Eng. Dev. Res. 2017, 5, 989–992. [Google Scholar]
- Shelke, F.M.; Dongre, A.A.; Soni, P.D. Comparison of different techniques for Steganography in images. Int. J. Appl. Innov. Eng. Manag. 2014, 3, 171–176. [Google Scholar]
- Rejani, R.; Murugan, D.; Krishnan, D.V. Comparative Study of Spatial Domain Image Steganography Techniques. Int. J. Adv. Netw. Appl. 2015, 7, 2650–2657. [Google Scholar]
- Fridrich, J. Applications of data hiding in digital images. In Proceedings of the ISPACS Conference, Brisbane, QLD, Australia, 18–21 August 1998. [Google Scholar]
- Koptyra, K.; Ogiela, M.R. Lightweight and efficient approach for multi-secret steganography. Int. J. Embed. Syst. 2020, 20, 434–440. [Google Scholar] [CrossRef]
- The OWASP IoT Security Team. OWASP Top Ten IoT. 2018. Available online: https://owasp.org/www-pdf-archive/OWASP-IoT-Top-10-2018-final.pdf (accessed on 1 December 2022).
- Ma, S.; Pang, Y.; Ji, Q.; Zhao, X.; Li, Y.; Qin, Z.; Liu, Z.; Xu, Y. High-Temperature Sensing Based on GAWBS In Silica Single-Mode Fiber. Sensors 2023, 23, 1277. [Google Scholar] [CrossRef]
- Kim, K.; Ryu, J.; Lee, Y.; Won, D. An Improved Lightweight User Authentication Scheme for the Internet of Medical Things. Sensors 2023, 23, 1122. [Google Scholar] [CrossRef]
- Ito, T.; Yoneyama, H.; Akiyama, Y.; Hagiwara, T.; Ezawa, S. Sensing Algorithm to Estimate Slight Displacement and Posture Change of Target from Monocular Images. Sensors 2023, 23, 851. [Google Scholar] [CrossRef]
- Shylendra, S.P.; Wajrak, M.; Alameh, K.; Kang, J.J. Nafion Modified Titanium Nitride pH Sensor for Future Biomedical Applications. Sensors 2023, 23, 699. [Google Scholar] [CrossRef] [PubMed]
- Luna-Perejón, F.; Salvador-Domínguez, B.; Perez-Peña, F.; Corral, J.M.R.; Escobar-Linero, E.; Morgado-Estévez, A. Smart Shoe Insole Based on Polydimethylsiloxane Composite Capacitive Sensors. Sensors 2023, 23, 1298. [Google Scholar] [CrossRef]
- Saeed, U.; Lee, Y.-D.; Jan, S.U.; Koo, I. CAFD: Context-Aware Fault Diagnostic Scheme towards Sensor Faults Utilizing Machine Learning. Sensors 2021, 21, 617. [Google Scholar] [CrossRef]
- Patalas-Maliszewska, J.; Pajak, I.; Krutz, P.; Pajak, G.; Rehm, M.; Schlegel, H.; Dix, M. Inertial Sensor-Based Sport Activity Advisory System Using Machine Learning Algorithms. Sensors 2023, 23, 1137. [Google Scholar] [CrossRef] [PubMed]
- Park, S.-C.; Park, K.-H.; Chang, J.-H. Luminance-Degradation Compensation Based on Multistream Self-Attention to Address Thin-Film Transistor-Organic Light Emitting Diode Burn-In. Sensors 2021, 21, 3182. [Google Scholar] [CrossRef]
- Koptyra, K.; Ogiela, M.R. Steganography in IoT: Information Hiding with APDS-9960 Proximity and Gestures Sensor. Sensors 2022, 22, 2612. [Google Scholar] [CrossRef] [PubMed]
- Gómez, J.-D. Videostego. 2021. Available online: https://github.com/JavDomGom/videostego (accessed on 12 October 2022).
- Cimmaron Systems. Elements of the H.264 Video/AAC Audio MP4 Movie; 2014—Application Note: AN101. Available online: https://www.cimarronsystems.com/wp-content/uploads/2017/04/Elements-of-the-H.264-VideoAAC-Audio-MP4-Movie-v2_0.pdf (accessed on 12 October 2022).
- Longman Communication 3000. Available online: https://ia801908.us.archive.org/13/items/longman_3000_list/longman_3000_list.pdf (accessed on 6 December 2022).
- Patel, K.; Rora, K.K.; Singh, K.; Verma, S. Lazy wavelet transform based steganography in video. In Proceedings of the 2013 International Conference on Communication Systems and Network Technologies, Tiruchengode, India, 6–8 April 2013; pp. 497–500. [Google Scholar]
- Sahu, A.K.; Gutub, A. Improving grayscale steganography to protect personal information disclosure within hotel services. Multimed. Tools Appl. 2022, 81, 30663–30683. [Google Scholar] [CrossRef]
- Xu, C.; Ping, X.; Zhang, T. Steganography in compressed video stream. In Proceedings of the First International Conference on Innovative Computing, Information and Control, Beijing, China, 30 August–1 September 2006; pp. 269–272. [Google Scholar]
- Fang, D.Y.; Chang, L.W. Data hiding for digital video with phase of motion vector. In Proceedings of the IEEE International Symposium on Circuits and Systems, Kos, Greece, 21–24 May 2006; pp. 1422–1425. [Google Scholar]
- Aly, H. Data hiding in motion vectors of compressed video based on their associated prediction error. IEEE Trans. Inf. Forensics Secur. 2011, 6, 14–18. [Google Scholar] [CrossRef]
- Wang, K.; Zhao, H.; Wang, H. Video steganalysis against motion vector-based steganography by adding or subtracting one motion vector value. IEEE Trans. Inf. Forensics Secur. 2014, 9, 741–751. [Google Scholar] [CrossRef]
- Zhang, H.; Cao, Y.; Zhao, X. A Steganalytic Approach to Detect Motion Vector Modification Using Near-Perfect Estimation for Local Optimality. IEEE Trans. Inf. Forensics Secur. 2017, 12, 465–478. [Google Scholar] [CrossRef]
- Zhang, H.; You, W.; Zhao, X. A Video Steganalytic Approach Against Quantized Transform Coefficient-Based H.264 Steganography by Exploiting In-Loop Deblocking Filtering. IEEE Access 2020, 8, 186862–186878. [Google Scholar] [CrossRef]
- Dasgupta, K.; Mondal, J.K.; Dutta, P. Optimized video steganography using genetic algorithm (GA). Procedia Technol. 2013, 10, 131–137. [Google Scholar] [CrossRef]
- Gutub, A.A.A. Adopting counting-based secret-sharing for e-Video Watermarking allowing Fractional Invalidation. Multimed. Tools Appl. 2022, 81, 9527–9547. [Google Scholar] [CrossRef]
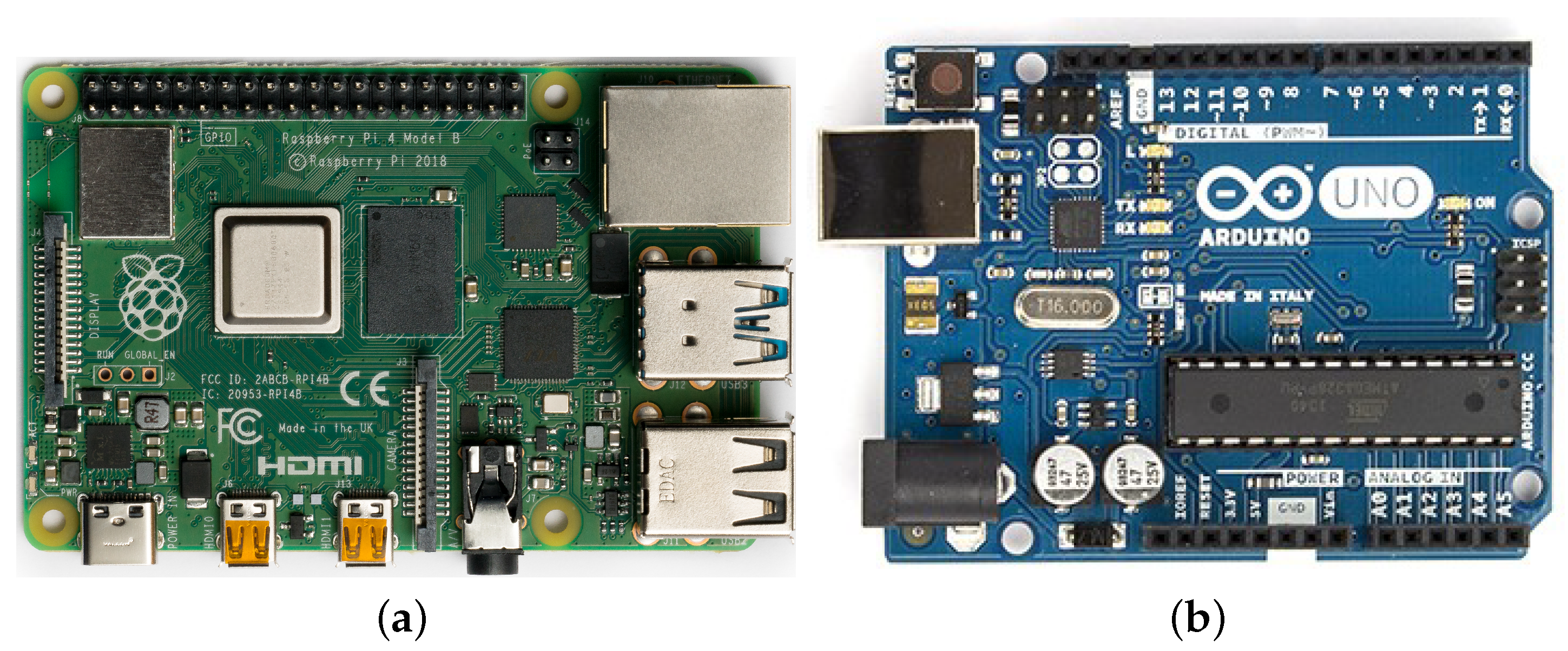
 ); (b) Arduino Uno (R.hampl/Wikimedia Commons/
); (b) Arduino Uno (R.hampl/Wikimedia Commons/ ).
).
 ); (b) Arduino Uno (R.hampl/Wikimedia Commons/
); (b) Arduino Uno (R.hampl/Wikimedia Commons/ ).
).

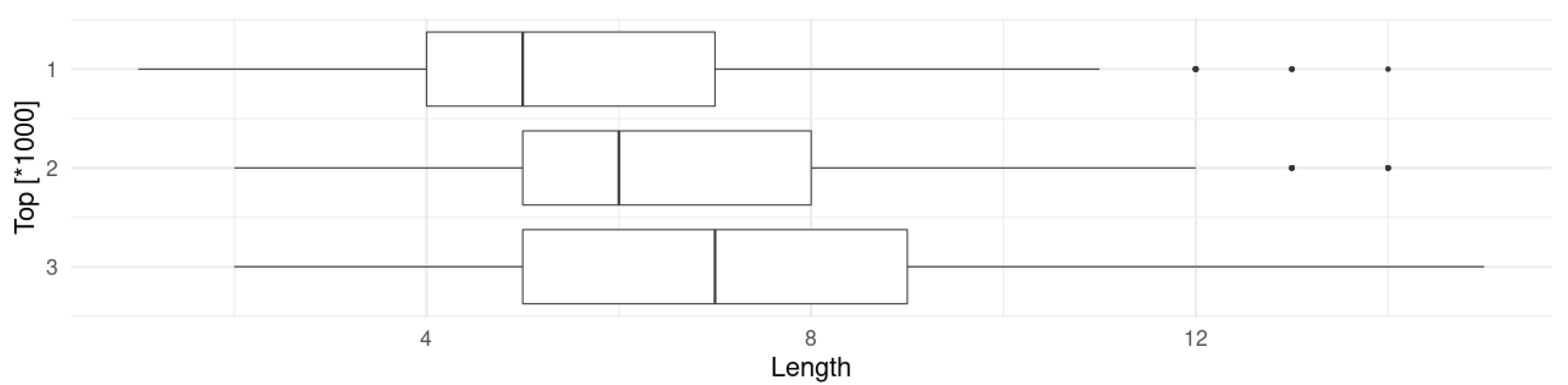
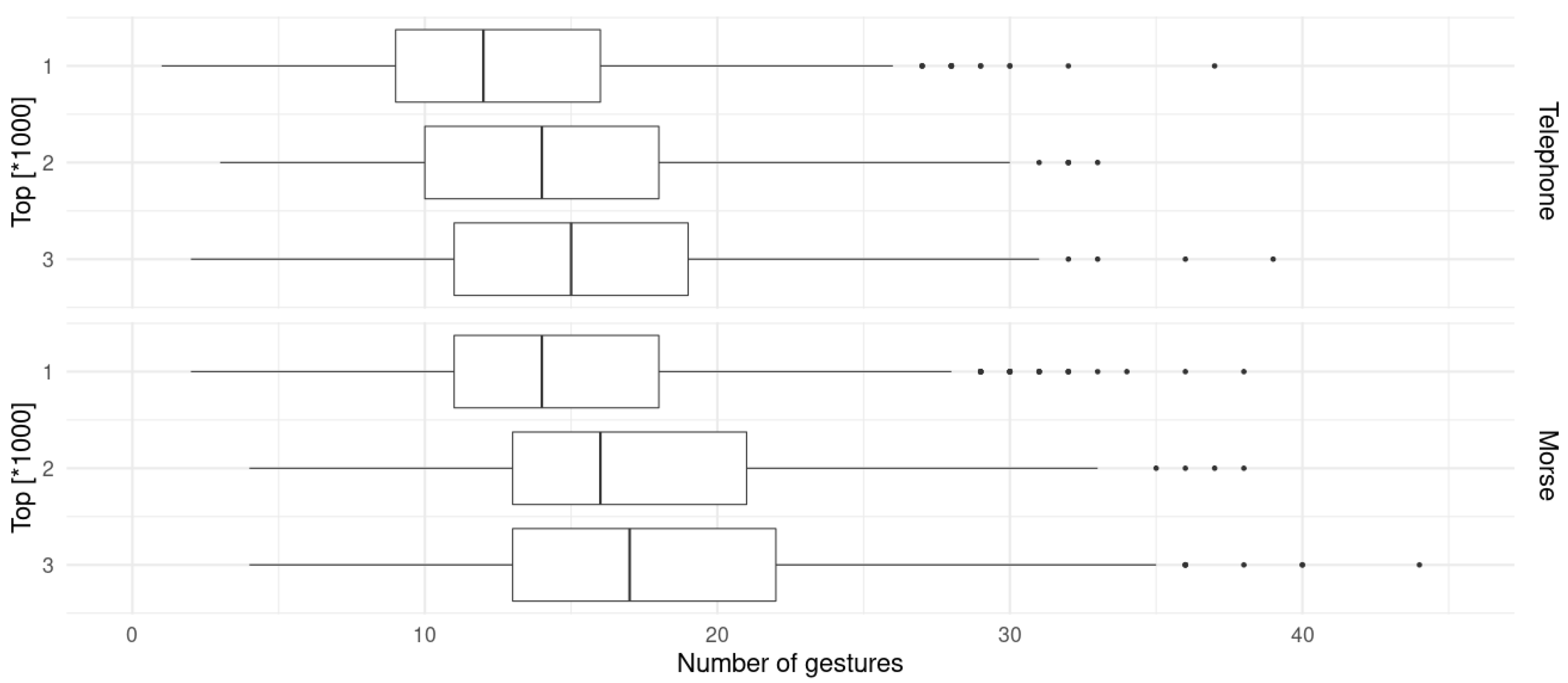
| Category | Min | Median | Mean | Max |
|---|---|---|---|---|
| Top1000 | 1 | 4 | 5.688 | 14 |
| Top2000 | 1 | 4 | 6.126 | 14 |
| Top3000 | 1 | 5 | 6.365 | 15 |
| Encoding | Category | Min | Median | Mean | Max |
|---|---|---|---|---|---|
| Telephone | Top1000 | 1 | 12 | 12.53 | 37 |
| Top2000 | 1 | 13 | 13.5 | 37 | |
| Top3000 | 1 | 13 | 14.06 | 39 | |
| Morse | Top1000 | 2 | 14 | 14.72 | 38 |
| Top2000 | 2 | 15 | 15.75 | 38 | |
| Top3000 | 2 | 15 | 16.36 | 44 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Koptyra, K.; Ogiela, M.R. Steganography in IoT: Information Hiding with Joystick and Touch Sensors. Sensors 2023, 23, 3288. https://doi.org/10.3390/s23063288
Koptyra K, Ogiela MR. Steganography in IoT: Information Hiding with Joystick and Touch Sensors. Sensors. 2023; 23(6):3288. https://doi.org/10.3390/s23063288
Chicago/Turabian StyleKoptyra, Katarzyna, and Marek R. Ogiela. 2023. "Steganography in IoT: Information Hiding with Joystick and Touch Sensors" Sensors 23, no. 6: 3288. https://doi.org/10.3390/s23063288
APA StyleKoptyra, K., & Ogiela, M. R. (2023). Steganography in IoT: Information Hiding with Joystick and Touch Sensors. Sensors, 23(6), 3288. https://doi.org/10.3390/s23063288







