Detection of Management-Frames-Based Denial-of-Service Attack in Wireless LAN Network Using Artificial Neural Network
Abstract
:1. Introduction
2. Related Works
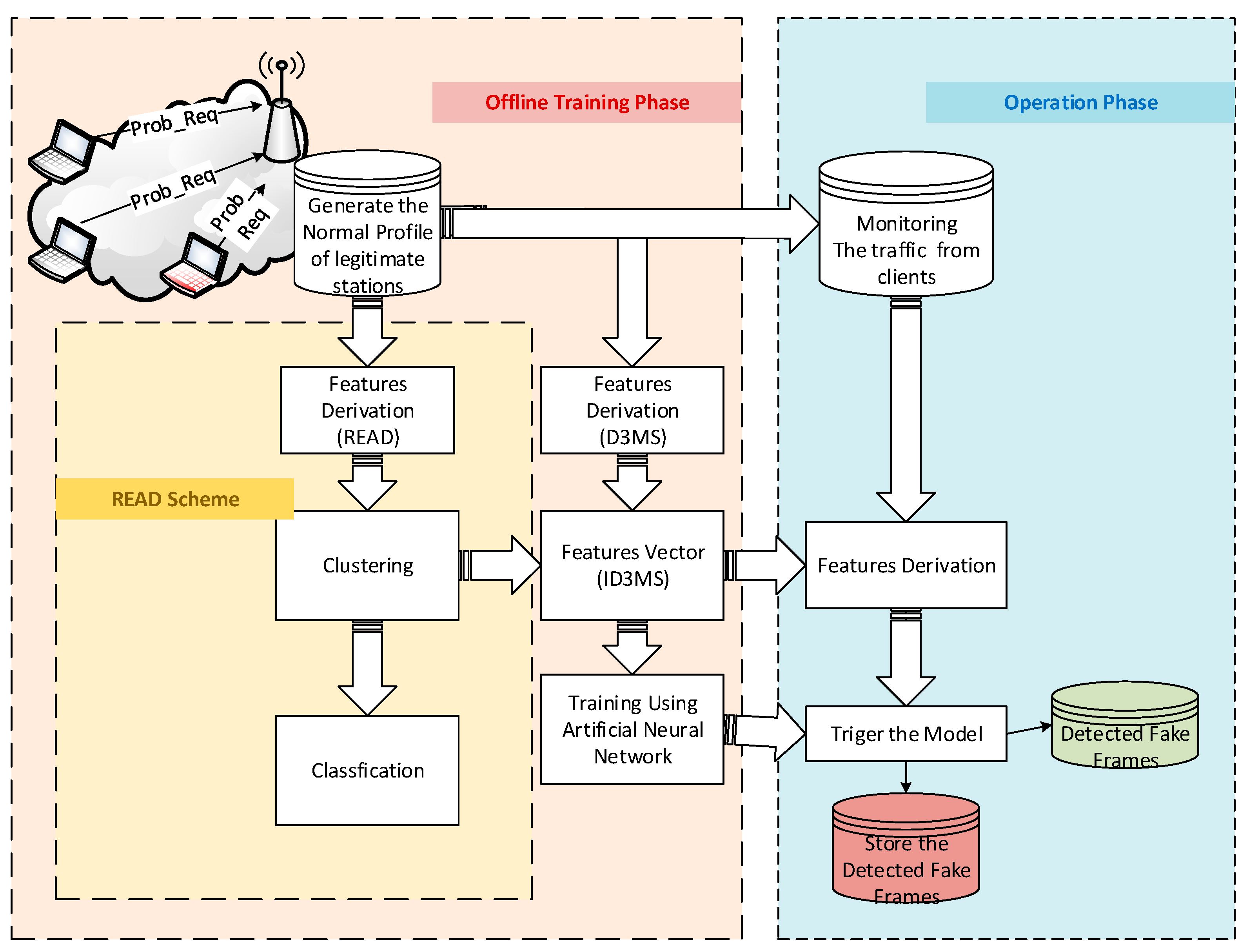
3. Proposed Scheme
4. Details of the Scheme
4.1. Offline Training Phase
4.1.1. Data Gathering
4.1.2. Derivation of Features
- Time of last Authentication/Association (TLA): TLA is the amount of time that passes between a request for de-authentication or disassociation and the answer to the most recent request for authentication or association.
- Time to last data packet received (TLD): TLD is the interval between the de-authentication/disassociation request and the preceding data packet.
- Data Rate at De-authentication/Disassociation Frames Request (D.R.): The D.R. is the typical station data rate computed from the most recent time frame prior to the re-receipt of the de-authentication/disassociation request.
- The signal strength of the de-authentication/disassociation request frame is represented by the RSSI value of the de-authentication/disassociation frame (RSSI).
- Sequence Jumping Distance (SJD): the distance between the most recent and preceding sequence numbers.
- Packet Spoofing Score (PSS): The distance between the message rank and the cluster centroid.
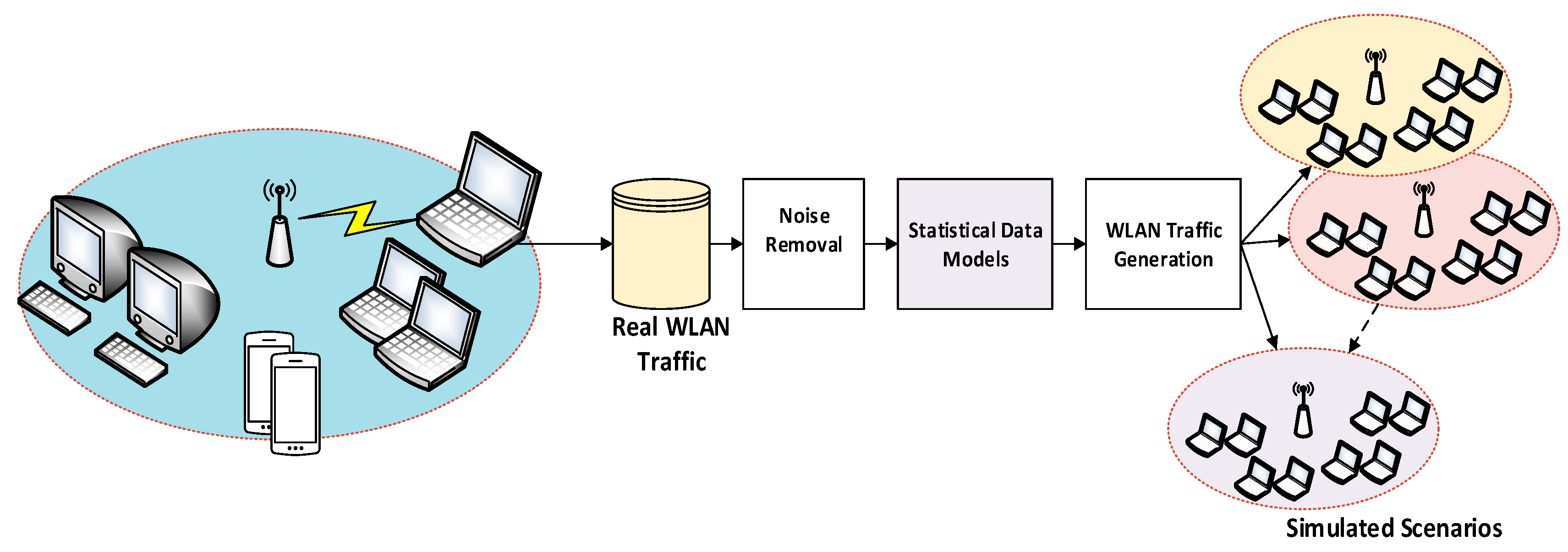
4.1.3. Dataset Replication and Attack Simulation
4.1.4. Model Construction
4.2. Online Operation
- The access point listens to the benign stations’ upcoming association and authentication requests. The stations could be stationary such as PCs, or mobile, such as laptops and smartphones.
- Upon receiving any association and authentication request from a client station, the access point executes a request and responds to the client through an authentication or association response.
- The access point monitors the traffic activities of every client. It keeps their details in a temporary buffer for a period of time that is determined when the access point receives a de-authentication or disassociation request from the client.
- Upon receiving any de-authentication or de-authentication/disassociation request from a client station, the access point derives the feature vector according to the procedure described in Section 3.
- The access point triggers the neural network classification model to classify the requesting station based on the derived vector. The classifier predicts the vector label and suggests the class.
- According to the class label, the access point chooses to execute or drop the request from the station.
5. Experimental Setup
5.1. The Traffic Capturing
5.2. DE-Authentication/Disassociation Attack Simulation
- By keeping an eye on the network traffic for a while, the attacker locates the victims among the clients connected to the AP.
- The attacker modifies its MAC address to precisely match the victim’s station.
- The perpetrator launches a phoney de-authentication/disassociation attack.
- The AP responds by executing the request from the MAC address of the request if it is not protected.
5.3. Performance Evaluation
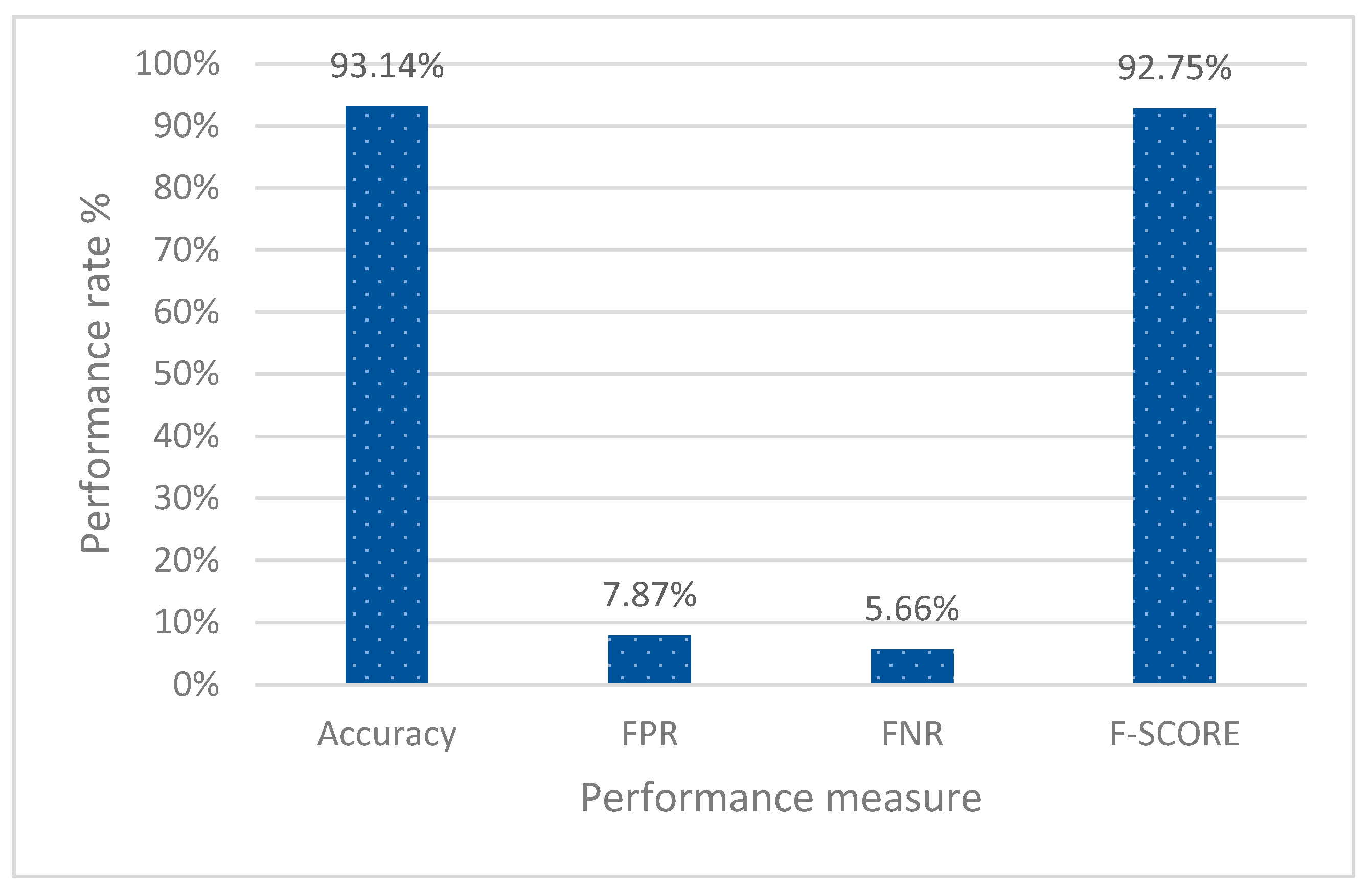
5.3.1. Analysis and Discussion of the Results
5.3.2. Comparison and Result Analysis
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Kaur, J.; Sondhi, P. Analysing Dupes-Algorithm to Detect and Prevent DOS Attack. J. Posit. Sch. Psychol. 2022, 6, 5937–5942. [Google Scholar]
- Bicakci, K.; Tavli, B. Denial-of-Service Attacks and Countermeasures in IEEE 802.11 Wireless Networks. Comput. Stand. Interfaces 2009, 31, 931–941. [Google Scholar] [CrossRef]
- Kamboj, A.K.; Jindal, P.; Verma, P. Physical Layer Security-Based Relay Selection for Wireless Cooperative Networks: A Reinforcement Learning Approach. In Intelligent Computing and Communication Systems. Algorithms for Intelligent Systems; Singh, B., Coello Coello, C.A., Jindal, P., Verma, P., Eds.; Springer: Singapore, 2021. [Google Scholar] [CrossRef]
- Haider, Z.; Saleem, M.; Jamal, T. Analysis of Interference in Wireless Networks. arXiv 2018, arXiv:1810.13164. [Google Scholar]
- Cheema, A.; Tariq, M.; Hafiz, A.; Khan, M.M.; Ahmad, F.; Anwar, M. Prevention Techniques against Distributed Denial of Service Attacks in Heterogeneous Networks: A Systematic Review. Secur. Commun. Netw. 2022, 2022, 8379532. [Google Scholar] [CrossRef]
- Alshammari, A.; Aldribi, A. Apply Machine Learning Techniques to Detect Malicious Network Traffic in Cloud Computing. J Big Data 2021, 8, 90. [Google Scholar] [CrossRef]
- Jamal, T.; Mendes, P. Relay Selection Approaches for Wireless Cooperative Networks. In Proceedings of the 2010 IEEE 6th International Conference on Wireless and Mobile Computing, Networking and Communications, Niagara Falls, ON, Canada, 11–13 October 2010; pp. 661–668. [Google Scholar]
- Jamal, T.; Mendes, P.; Zuquete, A. Opportunistic Relay Selection for Wireless Cooperative Network. In Proceedings of the 2012 5th International Conference on New Technologies, Mobility and Security (NTMS), Istanbul, Turkey, 7–10 May 2012; pp. 1–4. [Google Scholar]
- Jazzar, M.; Hamad, M. An Analysis Study of IoT and DoS Attack Perspective. In Proceedings of the International Conference on Intelligent Cyber-Physical Systems, West Bengal, India, 24–26 June 2021; pp. 127–142. [Google Scholar]
- Kaur, J. Mac Layer Management Frame Denial of Service Attacks. In Proceedings of the 2016 International Conference on Micro-Electronics and Telecommunication Engineering, ICMETE 2016, Ghaziabad, India, 22–23 September 2016; pp. 155–160. [Google Scholar]
- Baharudin, N.; Ali, F.H.M.; Darus, M.Y.; Awang, N. Wireless Intruder Detection System (WIDS) in Detecting De-Authentication and Disassociation Attacks in IEEE 802.11. In Proceedings of the 2015 5th International Conference on IT Convergence and Security (ICITCS), Kuala Lumpur, Malaysia, 24–27 August 2015; pp. 1–5. [Google Scholar]
- Elhigazi, A.; Razak, S.A.; Hamdan, M.; Mohammed, B.; Abaker, I.; Elsafi, A. Authentication Flooding DOS Attack Detection and Prevention in 802.11. In Proceedings of the 2020 IEEE Student Conference on Research and Development, SCOReD 2020, Batu Pahat, Malaysia, 27–29 September 2020; pp. 325–329. [Google Scholar]
- Schepers, D.; Ranganathan, A.; Vanhoef, M. On the Robustness of Wi-Fi Deauthentication Countermeasures. In Proceedings of the WiSec 2022—15th ACM Conference on Security and Privacy in Wireless and Mobile Networks, San Antonio, TX, USA, 16–19 May 2022; pp. 245–256. [Google Scholar]
- Abdallah, A.E.; Hamdan, M.; Abd Razak, S.; Ghalib, F.A.; Hamzah, M.; Khan, S.; Ali, S.A.B.; Khairi, M.H.H.; Salih, S. Resource Exhaustion Attack Detection and Mitigation Scheme using Artificial Neural Network. Comput. Mater. Contin. 2022, 74, 5607–5623. [Google Scholar] [CrossRef]
- Abdallah, A.E.; Razak, S.A.; Ghalib, F.A. Deauthentication and disassociation detection and mitigation scheme using artificial neural network. In Proceedings of the International Conference of Reliable Information and Communication Technology, Johor, Malaysia, 22–23 September 2019; pp. 857–886. [Google Scholar]
- Chen, Y.; Trappe, W.; Martin, R.P. Detecting and Localizing Wireless Spoofing Attacks. In Proceedings of the 2007 4th Annual IEEE Communications Society Conference on Sensor, Mesh and Ad Hoc Communications and Networks, San Diego, CA, USA, 18–21 June 2007; pp. 193–202. [Google Scholar]
- Wu, W.; Gu, X.; Dong, K.; Shi, X.; Yang, M. PRAPD: A Novel Received Signal Strength–Based Approach for Practical Rogue Access Point Detection. Int. J. Distrib. Sens. Netw. 2018, 14, 155014771879583. [Google Scholar] [CrossRef]
- Ratnayake, D.N.; Kazemian, H.B.; Yusuf, S.A. Identification of Probe Request Attacks in WLANs Using Neural Networks. Neural. Comput. Appl. 2014, 25, 1–14. [Google Scholar] [CrossRef]
- Sheng, Y.; Tan, K.; Chen, G.; Kotz, D.; Campbell, A. Detecting 802.11 MAC Layer Spoofing Using Received Signal Strength. In Proceedings of the IEEE INFOCOM 2008—The 27th Conference on Computer Communications, Phoenix, AZ, USA, 13–18 April 2008; pp. 1768–1776. [Google Scholar]
- Gonzales, H.; Bauer, K.; Lindqvist, J.; McCoy, D.; Sicker, D. Practical Defenses for Evil Twin Attacks in 802.11. In Proceedings of the 2010 IEEE Global Telecommunications Conference GLOBECOM 2010, Miami, FL, USA, 6–10 December 2010; pp. 1–6. [Google Scholar]
- Demirbas, M.; Song, Y. An RSSI-Based Scheme for Sybil Attack Detection in Wireless Sensor Networks. In Proceedings of the 2006 International Symposium on a World of Wireless, Mobile and Multimedia Networks (WoWMoM’06), Buffalo-Niagara Falls, NY, USA, 26–29 June 2006; pp. 564–570. [Google Scholar]
- Dey, K.; Kalita, K.; Chakraborty, S. Prediction performance analysis of neural network models for an electrical discharge turning process. Int. J. Interact. Des. Manuf. 2022, 1–19. [Google Scholar] [CrossRef]
- Ibrahim, A.O.; Shamsuddin, S.M.; Abraham, A.; Qasem, S.N. Adaptive memetic method of multi-objective genetic evolutionary algorithm for backpropagation neural network. Neural Comput. Appl. 2019, 31, 4945–4962. [Google Scholar] [CrossRef]

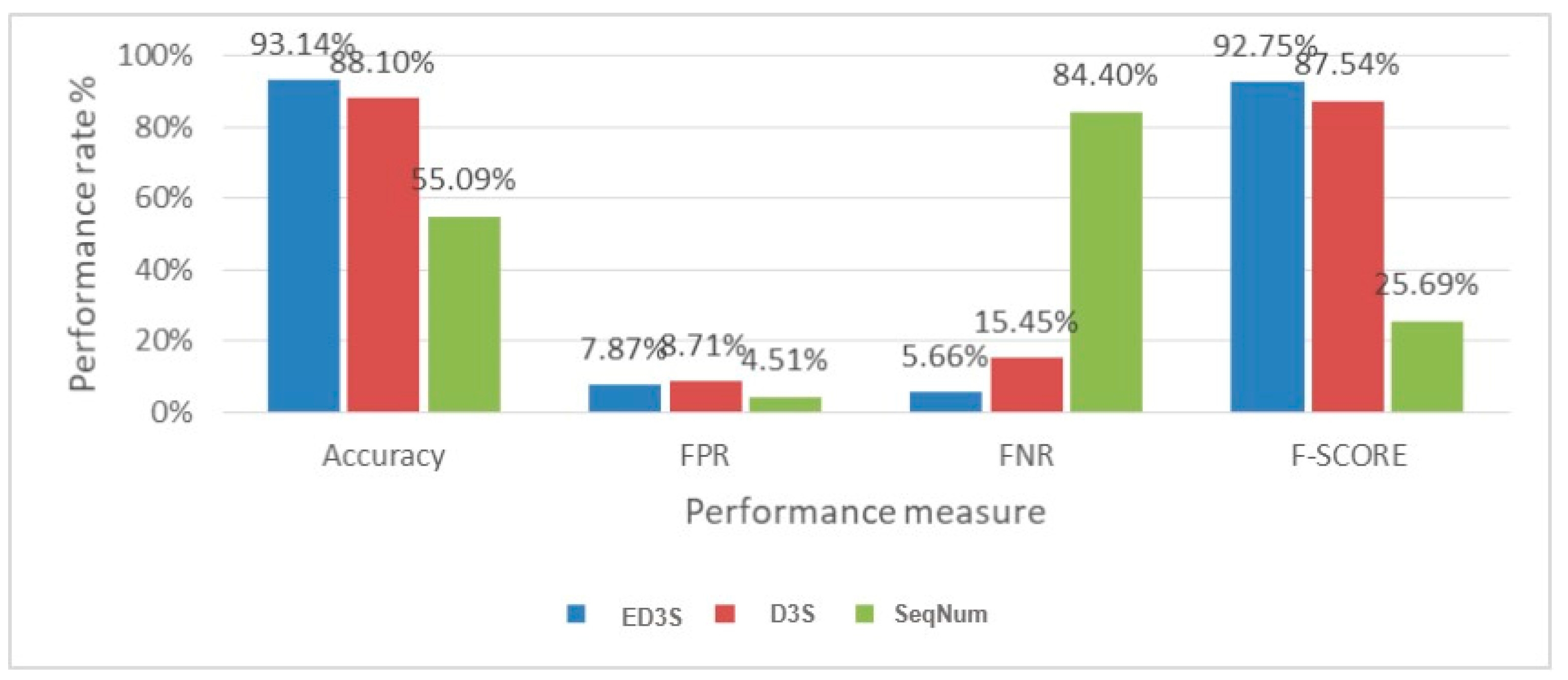
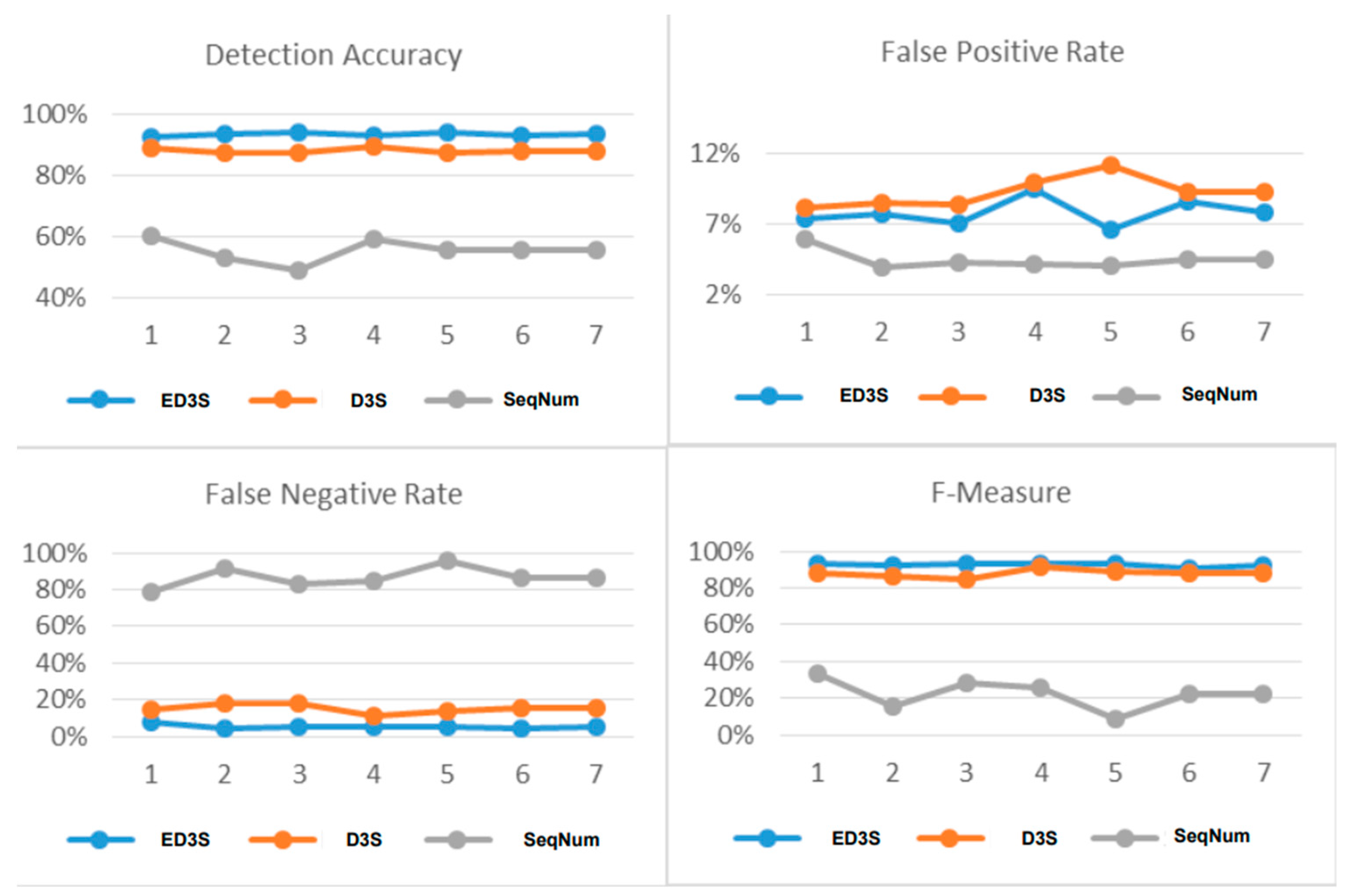
| Scheme | Scenarios | Accuracy | FPR | FNR | F-SCORE |
|---|---|---|---|---|---|
| ED3S Scheme (The Proposed) | 1 | 92.48% | 7.33% | 7.69% | 92.86% |
| 2 | 93.57% | 7.67% | 4.47% | 92.02% | |
| 3 | 93.78% | 7.03% | 5.14% | 92.95% | |
| 4 | 92.71% | 9.46% | 5.32% | 93.16% | |
| Average | 93.14% | 7.87% | 5.66% | 92.75% | |
| D3S Scheme | 1 | 88.87% | 8.11% | 14.43% | 88.02% |
| 2 | 86.96% | 8.45% | 17.81% | 86.07% | |
| 3 | 87.26% | 8.37% | 18.38% | 84.84% | |
| 4 | 89.30% | 9.91% | 11.17% | 91.25% | |
| Average | 88.10% | 8.71% | 15.45% | 87.54% | |
| SeqNum Based (Baseline Scheme) | 1 | 59.91% | 5.89% | 78.79% | 33.18% |
| 2 | 52.78% | 3.88% | 91.16% | 15.68% | |
| 3 | 48.80% | 4.20% | 83.31% | 27.93% | |
| 4 | 58.86% | 4.07% | 84.36% | 25.98% | |
| Average | 55.09% | 4.51% | 84.40% | 25.69% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Abdallah, A.E.; Hamdan, M.; Gismalla, M.S.M.; Ibrahim, A.O.; Aljurayban, N.S.; Nagmeldin, W.; Khairi, M.H.H. Detection of Management-Frames-Based Denial-of-Service Attack in Wireless LAN Network Using Artificial Neural Network. Sensors 2023, 23, 2663. https://doi.org/10.3390/s23052663
Abdallah AE, Hamdan M, Gismalla MSM, Ibrahim AO, Aljurayban NS, Nagmeldin W, Khairi MHH. Detection of Management-Frames-Based Denial-of-Service Attack in Wireless LAN Network Using Artificial Neural Network. Sensors. 2023; 23(5):2663. https://doi.org/10.3390/s23052663
Chicago/Turabian StyleAbdallah, Abdallah Elhigazi, Mosab Hamdan, Mohammed S. M. Gismalla, Ashraf Osman Ibrahim, Nouf Saleh Aljurayban, Wamda Nagmeldin, and Mutaz H. H. Khairi. 2023. "Detection of Management-Frames-Based Denial-of-Service Attack in Wireless LAN Network Using Artificial Neural Network" Sensors 23, no. 5: 2663. https://doi.org/10.3390/s23052663
APA StyleAbdallah, A. E., Hamdan, M., Gismalla, M. S. M., Ibrahim, A. O., Aljurayban, N. S., Nagmeldin, W., & Khairi, M. H. H. (2023). Detection of Management-Frames-Based Denial-of-Service Attack in Wireless LAN Network Using Artificial Neural Network. Sensors, 23(5), 2663. https://doi.org/10.3390/s23052663










