Bluetooth Low Energy Mesh: Applications, Considerations and Current State-of-the-Art
Abstract
:1. Introduction
- To the best of our knowledge, this is the first research work exploring the practical applicability, challenges, and opportunities of using BT Mesh for a diverse set of IoT scenarios.
- This work presents a review of BT Mesh experimental investigations from related work and insights from our test-bed, analysing real-world implications for latency, energy, scalability, and reliability based on BT Mesh parameters and behaviour.
2. Overview of Bluetooth Mesh
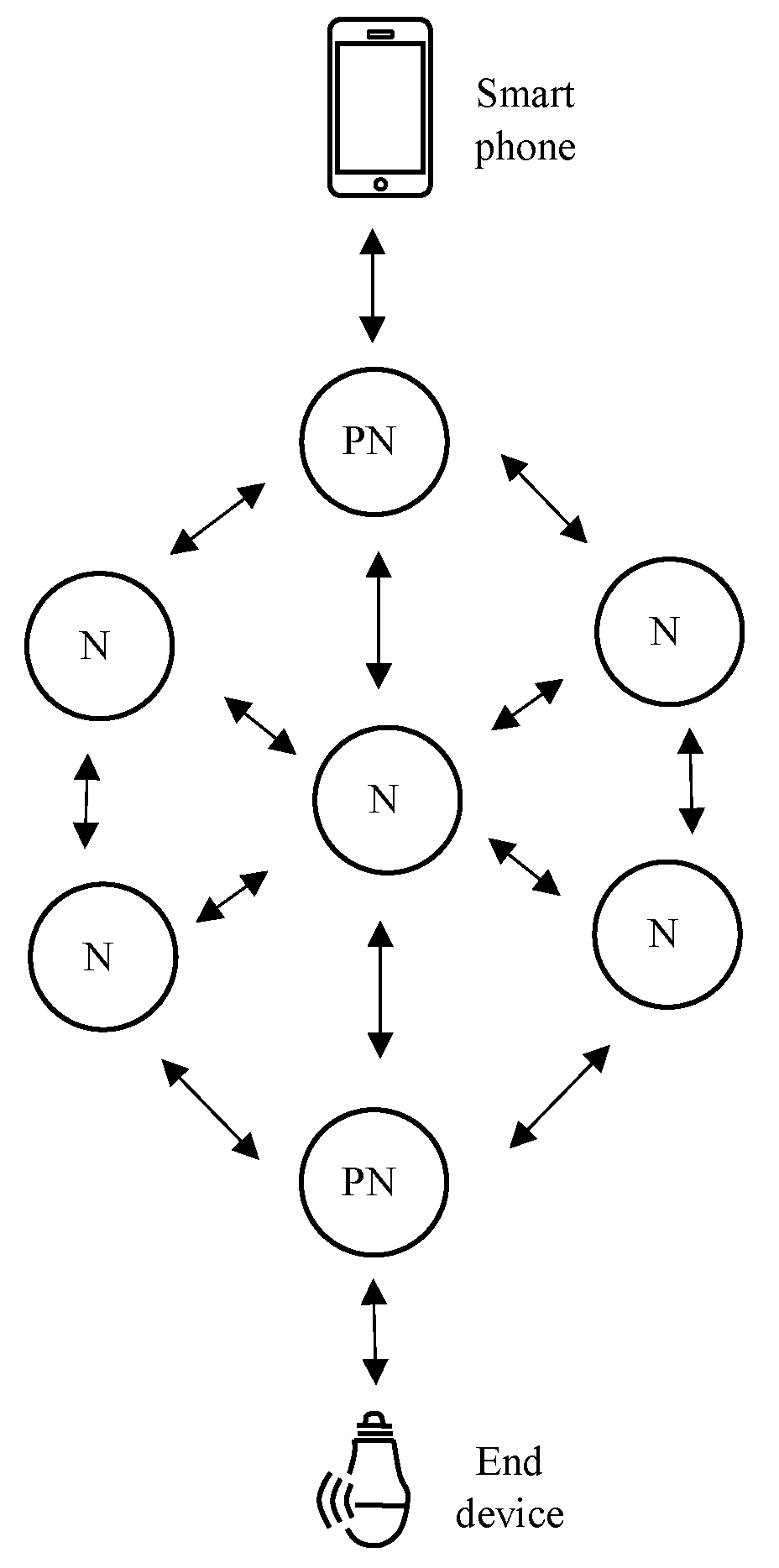
2.1. Different Node Types in BT Mesh
2.1.1. Relay Node
2.1.2. Low-Power Node (LPN)
2.1.3. Friend Node
2.1.4. Proxy Node
2.2. Addressing
- 1.
- Unicast addresses: The unicast address is assigned to each element of the node during the new node adding process to the mesh network. The unicast address cannot be changed during the lifetime of the node on the mesh network. The unicast addresses are assigned sequentially.
- 2.
- Group addresses: Group addresses are multicast addresses on the mesh network. They are used to communicate with multiple nodes at once. The nodes or elements are assigned to the group address during the node configuration process.
- 3.
- Virtual addresses: Users can generate virtual addresses, and they can be considered as a special kind of group address.
2.3. Privacy and Security of BT Mesh
2.3.1. Separation of Concerns
2.3.2. Area Isolation
2.3.3. Secure Device Provisioning
2.3.4. The Key Refresh Procedure
2.3.5. Message Obfuscation
3. Applications of Bluetooth Mesh
3.1. Selected IoT Application Implementations
3.1.1. Smart Buildings
3.1.2. Smart Lighting
3.1.3. Monitoring
3.1.4. Disaster Communication
3.1.5. Smart Factory
3.1.6. Smart Parking
3.2. How BT Mesh Can Support IoT Application Requirements
- 1.
- Scalability: Scalability refers to a system’s ability to handle growing amounts of work. IoT systems will need to be scalable in varying degrees, depending on the application context. For example, a wireless lighting system in an underground tunnel will need to cater to thousands of nodes, spread across a large geographical area, whereas the IoT devices in a smart home system will most likely consist of hundreds of nodes situated within a comparably smaller geographical area. BT Mesh can be used to cater to both extremes, due to the large number of nodes it can accommodate (32,000 nodes and 127 hops per packet at maximum, according to specs, although this will be lower in practice). Due to its mesh topology, BT Mesh can also cover an extended area. However, BT Mesh’s mechanism of controlled-flooding can cause the “broadcast storm” issue [6], where increased node saturation amounts to increased packet collisions, which poses a challenge for scaling up [24].
- 2.
- Flexible Configuration: For some IoT systems, it is essential to be able to support node configurations on the fly. There could be requirements to dynamically move nodes or to allocate nodes to different groups. Due to the mesh structure, BT Mesh networks can self-form and self-heal, which also provides fault-tolerance. BT Mesh standard supports dynamic assignment of the group and virtual addresses so that the physical network structure can be dynamically updated [7]. However, this method of dynamic group allocation using the publish–subscribe model also presents bottlenecks when a large number of nodes need to send acknowledgements of messages received to a single group owner [38]. For example, consider an IoT application for an underground mine where a controller node needs to send a mission-critical message (such as a notification to vacate an area due to a flammable gas leak) to hundreds of nodes. In this context, it is critical for the group owner to know whether the message has been received. However, because all of the hundreds of nodes in the group would be attempting to send their acknowledgements to the group owner at the same time, the network must manage high traffic, and there is a high probability of packet losses. A solution was experimentally implemented by Pierleoni et al. [38], where the acknowledgements are sent with a random delay to avoid simultaneous transmission, as suggested in the BT Mesh spec [39].
- 3.
- Robustness: Kitchenham et al. [40] defines robustness as “the degree to which a system or component can function correctly in the presence of invalid inputs or stressful environmental conditions”. In the context of IoT systems, considering the many heterogeneous devices interconnected together via various connection mediums, there is a high possibility of system errors occurring [41]. In some cases, failures in the system can be critical and even life-threatening, such as in autonomous vehicle control. BT Mesh provides fault-tolerance in the network due to its mesh topology that enables path diversity and its managed flooding [5]. However, although more fault-tolerant, the redundant transmissions mean that it is less efficient than single-path routing [5]. It is up to the developers to configure the degree of flooding according to the application context.
- 4.
- Responsiveness: IoT apps that involve human interactions require low latency so that the system can provide a quick reaction to fulfill human expectations. In particular, IETF RFC 5826 specifies interaction as real-time when the latency is below 500 ms [42]. BT Mesh can support this requirement, depending on the number of hops to reach the destination and if the nodes involve LPNs. Typically, in BT Mesh, each hop can take between 1 ms and 20 ms [5], unless the destination nodes are LPNs, in which case there can be additional delays, as LPNs can only receive data after polling its friend node/s. Developers can control latency by adjusting the BT Mesh parameters of advertising events and scanning events timing [6]; however, this needs to be balanced with implications for network robustness.
- 5.
- Integrated Functionality: IoT applications typically integrate multiple sensing, processing, connectivity, and actuating elements [43,44]. For example, integration of BLE beacons, mobile apps, wearables, and other IoT devices can provide localization, proximity detection, and activity sensing capabilities in numerous application areas, such as marketing, health monitoring, museum guiding, smart homes and offices, and warehouses [45]. Hence, it is particularly advantageous to use BT Mesh, which allows integrated functionality via its Models feature, which makes it easier to include custom features. For example, a BT Mesh lighting system can be embedded with other features, such as wireless lights also functioning as BLE beacons, or integrated with occupancy sensors [7]. A challenge is a limited payload available in messages used in BT Mesh models, which limits communication throughput. However, this may be alleviated to a considerable amount using pointers to other packets, i.e., packet chains [4].
- 6.
- Security: IoT architecture consists of components at the physical device layer, communication layer, and interfaces/services layer. This exposes IoT applications to attackers taking advantage of vulnerabilities in all these layers [46,47]. When considering security at the communication layer, BT Mesh has been designed with security as a first class citizen. Nodes in BT Mesh are provisioned using 256-bit elliptic curves and out-of-band authentication. To encrypt and authenticate the messages themselves, AES-CCM with 128-bit keys are used. Mesh operations and communications are secured via Network Key (to secure messages in nodes in the same network), Device Key (unique to each node, used to encrypt configuration messages), and Application Key (to encrypt and decrypt application data) [5,48]. According to the BT Mesh standard [39] the aforementioned security measures can provide protection against most threats against mesh networks. However, there are still vulnerabilities; device and application keys can be stolen/recovered by hardware exploitation and be susceptible to attacks such as simple power analysis, differential power analysis, and fault attack [49]. Other possible threats include malformation of the TTL value of packets [50] and exploiting “friend” nodes that lead to denial-of-service and impersonation attacks [51].
- 7.
- Energy Efficiency: Due to the limited battery power of hardware elements and the large number of devices involved in some cases, the need to conserve energy is important for IoT systems [52]. BT Mesh inherently supports this requirement via its BLE technology. The Upper Transport layer in BT Mesh protocol stack (See Figure 2) provides support for energy-constrained LPNs (see Section 2.1.2). LPNs are able to operate at reduced duty cycles with minimized usage of radio, with the help of nearby “friend nodes” (see Section 2.1.3). In addition, users can configure the TTLs to control the maximum hops per message, which acts as another energy conservation measure by ensuring messages are not relayed further than required [5,7]. Although flooding can be controlled via the TTL values, it is still more energy draining than routing, and the developers need to fine-tune the number of relay nodes and transmissions in a BT Mesh network to avoid unnecessary energy use. Moreover, LPNs are unable to act as relay nodes because relay nodes need to be in continuous scanning mode [4]. Hence, perhaps unsurprisingly, an experimental comparison of BT Mesh with 6BLEMesh has found 6BLEMesh to be more energy efficient for a given latency target [5] (see Section 5.1). To alleviate some of the aforementioned energy issues of flooding, the work in [53] proposed a simplified ContikiMAC mechanism [54], which lowers the receiving duty cycle, and by limiting the number of forwarded packets. In another study [55], the authors presented a strategy to reduce energy consumption in the friendship mechanism with burst transmissions and listen before transmit (BTLBT), showing a 19.81% improvement in a lifetime.
4. Comparing Bluetooth Mesh with Other Related Protocols
- As BT Mesh does not use a central hub for communication and uses a mesh networking, the connectivity is more reliable and can avoid single-point failure.
- BT Mesh technology can be easily extended to cover a larger area. This is possible as there is no single master device used in this technology such as the one used in BT Piconet.
- The low power consumption of BT Mesh makes it ideally suited for power demanding applications where a main power supply is not available.
- Due to the interoperability of BT Mesh between different manufacturers, it can be used in diverse contexts.
- BT Mesh is scalable and, as a result, it can be modified easily even after it is implemented.
- BT Mesh nodes are secure, as the system provides end to end security for messages exchange between devices.
5. Experiments in Related Work
5.1. BT Mesh versus 6BLEMesh
- Latency: To asses the latency, delays in packet transmission over multihop paths were measured. It was presented in [5] that in BT Mesh each hop contributes at least the time required to transmit a packet via the advertising channels. In 6BLEMesh, the time necessary to transfer a packet from one node to its next node is a uniformly distributed random variable.
- Energy consumption: In [5], current consumption is measured based on an nRF51 DK hardware platform and a battery capacity of 235 mA. As expected, for both BT Mesh and 6BLEMesh, the battery lifetimes were primarily based on the parameter values chosen. Form the data presented in [5], we can conclude that for a given latency goal, devices consume less energy in 6BLEMesh compared to BT Mesh.
- Message transmission count: From different network sizes, node densities, and protocol parameters, the total number of message transmissions are counted. One can see from the data provided in [5] that BT Mesh exhibited a higher number of data message transmissions compared to 6BLEMesh. This is due to the fact that BT Mesh and 6BLEMesh use managed-flooding and single-path routing, respectively.
- Link corruption robustness: Robustness of both technologies against radio signal fading or interference was assessed in [5]. Robustness was measured in terms of end-to-end packet delivery probability. It can be observed from [5] that BT Mesh achieved a higher packet delivery rate when there was diversity in the paths. On the other hand, 6BLEMesh showed excellent packet delivery performance when the maximum number of consecutive link-layer retries in a Link layer connection was set to a sufficiently large value.
5.2. Reliability, Delay, and Scalability Analysis
5.3. Evaluation of a Framework for Collecting Network Traffic Data
- Memory utilization: The additional memory used on nodes was measured when the framework was deployed compared to nodes without the framework. From the data presented in [8], we can see that more memory was used when the framework was deployed, as expected. From the information provided in [8], in terms of percentage, we can say that the extra memory usage was small. The analysis presented in [8] only took static use of the available memory and it did not take into account the stack and the heap (which are also stored in RAM).
- Effects on user traffic: To measure the network traffic, the packet delivery ratio (PDR) was used as the metric. From the experimental data in [8], one can see that PDR was reduced with the distance between transmissions. This can be expected as with increasing distance, the probability of packets colliding and interfering with each other reduces.A greater distance between transmissions reduced the probability of packets colliding and interfering with each other and, therefore, decreased the PDR. Further, from the experiment outcomes, we can observe that PDRs decreased with increasing message sizes.
- Latency: The experiments were primarily designed to measure the transmission delay against message sizes. From the presented data in [8], one can clearly see that delay linearly increased with the message size, as anticipated. From the experimental results, it is evident that the relaying process introduced uncertainty in the delay. This can be expected as relaying generates more traffic, which will increase the probability of collision.
5.4. Evaluation of the BT Mesh Protocol for Monitoring Applications
- Full-scale one-hop: The goal of this experiment was to assess the full potential of the BT Mesh network under different traffic conditions. In this experiment, relay nodes were not used. To evaluate the performance of the BT Mesh under a radio-frequency signal environment, experiments were conducted both during work hours and during off-hours. The PDR was primarily used to measure performance. From the experimental results, it can be seen that there is an approx. 10% reduction in overall packet reception ratio due to the interference from other radio technologies such as Wifi.
- Small-scale multi-hop: The primary aim of this experiment was to evaluate the processing and transmitting packet capacity of the relay nodes. From the experiments, authors calculated the maximum amount of packets relays can process. It can be noted from the experiments that relays became unreliable when they were overloaded.
- Full-scale multi-hop: In this experiment, the overall performance of the network was tested in multi-hop communication scenarios with an increasing number of nodes. From the experimental results, one can see that the PDRs significantly varied based on the location of the nodes. This is mainly caused by the inability of the relay nodes to process a larger amount of packets per second.
- Nomadic Node Experiments: In [56], patients with wireless sensors were referred to as nomadic nodes. These nodes were expected to move in the environment. For convenience, all nomadic nodes were attached to the same individual. The parameters are adjusted to make the nomadic node functional by reducing the stress on the relay nodes. However, adequate details of the experimentation results using nomadic Node were not provided in [56].
5.5. Performance Assessment of BT Mesh in Terms of Latency, Round Time Trip (RTT) Delays, and Energy Consumption
- Latency and RTT experiment: In this part of the experiment, several tests were conducted in [57]. Overall, the results show that the RTT increased with an increasing number of hops, as expected. Furthermore, it can be seen from the results presented in [57] that RTT increased in a non-linear manner with the number of nodes.
- Energy consumption: In this experiment, current consumption and battery lifetime of the devices were tested. The goal of the experiment was to generate a current consumption model for low-power devices. Details of the experimental setups are provided together with results in [57]. From the results, we can see that, compared to the normal expectancy of 10 years, the experiments and the related calculations show a lifetime of slightly less than 2 years. It should be noted that in [57], authors considered sleep-mode current consumption in the devices used. It can also be observed in [57] that there is a sensitivity of battery lifetime to parameters such as receive window size.
5.6. Evaluating the Latency Performance of BT Mesh
- Baseline Measurement: To have a reference level RTT that was measured with just two nodes;
- Multiple Neighbors Measurement: Measurements are made with more neighbours. As expected, RTT reduced with more neighbours;
- Multiple Hops Measurement: In this measurement, communication flows that span multiple hops in a BT Mesh were considered a network. It can be seen from the data that RTT almost linearly increased with a number of hops.
5.7. Energy Consumption with Flooding Protocols
- Tandem scenario: In this scenario, authors created a maximum range topology where nodes were separated by 1.5 m. The network was designed in such a way that all the nodes needed to be active to make the network functional. From the data presented in [58] we can see that the throughput of Tickle was comparable to Drypp. Further, the Tickle protocol had a higher percentage of packet transmissions than the Drypp protocol.
- Parallel scenario: In this scenario, the performance of Tickle and Drypp were compared when they were applied in a parallel topology [58]. The data clearly show that the throughput of Drypp and Trickle were converging with time and were relatively closer to each other. In the context of battery by time, the difference between the fall time of each node changed in a divergent manner.
6. Experiments in Group Messages
6.1. Experiment Setup
- Test 1: The nodes and the gateway device were set up in close proximity ( 1–5 cm between each other), and group messages were sent to the nodes.
- Test 2: The nodes and the gateway device were set up with approximately 10 m distance between each node and the gateway (in a star topology), and group messages were sent to the nodes.
- Test 3: The nodes and the gateway device were set up approximately 10 m between nodes and the gateway in a linear arrangement, and group messages were sent to the nodes.
6.2. Experimental Results
6.3. Discussion
7. Challenges Related to Bluetooth Mesh
- BT Mesh networks experience interference due to the presence of other signals such as Wi-Fi signals. Randomization of the timing parameters could alleviate some of the effects of this interference [60].
- Nodes such as relays/friends are expected to scan the network continuously. However, due to the limitations in firmware/hardware, scanning procedures do not occur continuously. As a result, the packets received within the non-scanning period are lost. However, in general, except in the case of acknowledgment messages, this is not a significant loss due to BT Mesh’s controlled flooding and redundant transmissions where each message is transmitted three times [5].
- BT Mesh networks do not support streaming high data rate applications such as audio streaming. For example, using BT Mesh networks, one cannot stream music to all the speakers in their home. This is because BT Mesh networks use BLE that is not designed for continuous wireless connections. As technology improves, including increased bandwidth in future BT Mesh versions, a wider range of software or firmware profiles might support a larger range of applications, including multimedia.
8. Conclusions and Future Directions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Baert, M.; Rossey, J.; Shahid, A.; Hoebeke, J. The bluetooth mesh standard: An overview and experimental evaluation. Sensors 2018, 18, 2409. [Google Scholar] [CrossRef] [PubMed]
- Yin, J.; Yang, Z.; Cao, H.; Liu, T.; Zhou, Z.; Wu, C. A survey on Bluetooth 5.0 and mesh: New milestones of IoT. ACM Trans. Sens. Netw. (TOSN) 2019, 15, 1–29. [Google Scholar] [CrossRef]
- Ghori, M.R.; Wan, T.C.; Sodhy, G.C. Bluetooth low energy mesh networks: Survey of communication and security protocols. Sensors 2020, 20, 3590. [Google Scholar] [CrossRef] [PubMed]
- Hernandez-Solana, A.; Perez-Diaz-De-Cerio, D.; García-Lozano, M.; Bardaji, A.V.; Valenzuela, J.L. Bluetooth Mesh Analysis, Issues, and Challenges. IEEE Access 2020, 8, 53784–53800. [Google Scholar] [CrossRef]
- Darroudi, S.M.; Gomez, C.; Crowcroft, J. Bluetooth low energy mesh networks: A standards perspective. IEEE Commun. Mag. 2020, 58, 95–101. [Google Scholar] [CrossRef]
- Rondón, R.; Mahmood, A.; Grimaldi, S.; Gidlund, M. Understanding the performance of bluetooth mesh: Reliability, delay, and scalability analysis. IEEE Internet Things J. 2020, 7, 2089–2101. [Google Scholar] [CrossRef]
- Woolley, M.; Schmidt, S. Bluetooth Mesh Networking: Paving the Way for Smart Lighting. 2017. Available online: https://www.bluetooth.com/bluetooth-resources/bluetooth-mesh-paving-the-way-for-smart-lighting/ (accessed on 27 October 2022).
- Karlsson, S. A Data Collection Framework for Bluetooth Mesh Networks. Master’s Thesis, Department of Computer and Information Science, Linköping University, Linköping, Sweden, 2019. [Google Scholar]
- Xia, N.; Chen, H.H.; Yang, C.S. Emerging technologies for machine-type communication networks. IEEE Netw. 2019, 34, 214–222. [Google Scholar] [CrossRef]
- Tekler, Z.D.; Low, R.; Gunay, B.; Andersen, R.K.; Blessing, L. A scalable Bluetooth Low Energy approach to identify occupancy patterns and profiles in office spaces. Build. Environ. 2020, 171, 106681. [Google Scholar] [CrossRef]
- Esrafilian-Najafabadi, M.; Haghighat, F. Occupancy-based HVAC control systems in buildings: A state-of-the-art review. Build. Environ. 2021, 197, 107810. [Google Scholar] [CrossRef]
- Jürgens, M.; Meis, D.; Möllers, D.; Nolte, F.; Stork, E.; Vossen, G.; Werner, C.; Winkelmann, H. Bluetooth Mesh Networks for Indoor Localization. In Proceedings of the 2019 20th IEEE International Conference on Mobile Data Management (MDM), Hong Kong, China, 10–13 June 2019; pp. 397–402. [Google Scholar] [CrossRef]
- Montecchiari, L.; Trotta, A.; Bononi, L.; Di Felice, M. Bluetooth Mesh Technology for the Joint Monitoring of Indoor Environments and Mobile Device Localization: A Performance Study. In Proceedings of the 2022 IEEE 19th Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 8–11 January 2022; pp. 193–199. [Google Scholar] [CrossRef]
- Tong, X.; Wang, L.; Cui, Y. Research on Indoor Positioning Based on Smart Home Bluetooth Networking. In Proceedings of the 2022 International Conference on Artificial Intelligence and Computer Information Technology (AICIT), Yichang, China, 16–18 September 2022; pp. 1–4. [Google Scholar] [CrossRef]
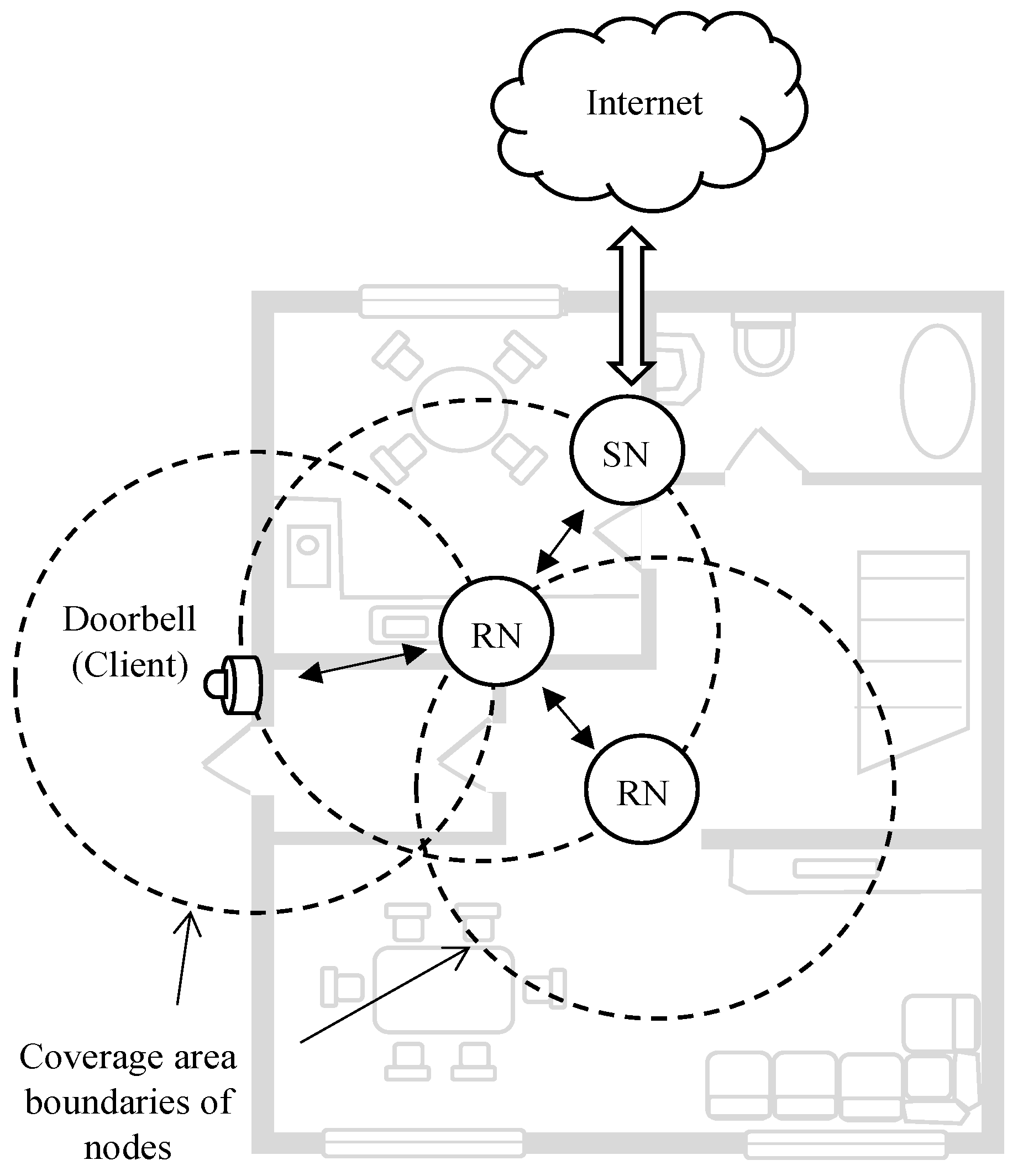
- Martínez, C.; Eras, L.; Domínguez, F. The Smart Doorbell: A proof-of-concept Implementation of a Bluetooth Mesh Network. In Proceedings of the 2018 IEEE Third Ecuador Technical Chapters Meeting (ETCM), Cuenca, Ecuador, 15–19 October 2018; pp. 1–5. [Google Scholar]
- Taştan, S.İ.; Dalkiliç, G. Smart Home System Using Internet of Things Devices and Mesh Topology. In Proceedings of the 2021 6th International Conference on Computer Science and Engineering (UBMK), Ankara, Turkey, 15–17 September 2021; pp. 407–412. [Google Scholar] [CrossRef]
- Tran, Q.T.; Tran, D.D.; Doan, D.; Nguyen, M.S. An Approach of BLE Mesh Network For Smart Home Application. In Proceedings of the 2020 International Conference on Advanced Computing and Applications (ACOMP), Quy Nhon, Vietnam, 25–27 November 2020; pp. 170–174. [Google Scholar] [CrossRef]
- Dvoynikov, V.M.; Smirnov, V.A.; Burilov, D.A. Comparative Analysis of Mesh and Thread Networks and their Application Possibility in the "Smart Home" Systems. In Proceedings of the 2021 IEEE Conference of Russian Young Researchers in Electrical and Electronic Engineering (ElConRus), St. Petersburg, Russia, 26–29 January 2021; pp. 8–11. [Google Scholar] [CrossRef]
- Sergi, I.; Montanaro, T.; Gammariello, M.C.; Patrono, L. The use of Bluetooth Mesh Networking in IoT-aware Applications. In Proceedings of the 2021 6th International Conference on Smart and Sustainable Technologies (SpliTech), Bol and Split, Croatia, 8–11 September 2021; pp. 01–06. [Google Scholar]
- Zheng, X.; Xue, S.; Cao, H.; Wang, F.; Zhang, M. A cost-efficient smart IoT device controlling system based on bluetooth mesh and cloud computing. In Proceedings of the 2020 Chinese Automation Congress (CAC), Shanghai, China, 6–8 November 2020; pp. 3374–3379. [Google Scholar]
- Lee, T.Y.; Truong, P.H.; Lee, C.K.; Jeong, G.M. Range extension of LED control systems using a Bluetooth mesh network. In Proceedings of the 2017 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 8–10 January 2017; pp. 166–167. [Google Scholar]
- Abboud, K.; Li, Y.; Bermudez, S. eSNAP: Enabling Sensor Network Automatic Positioning in IoT Lighting Systems. IEEE Internet Things J. 2020, 7, 10427–10436. [Google Scholar] [CrossRef]
- Veiga, A.A.; Abbas, C.J. Proposal and application of Bluetooth mesh profile for smart cities’ services. Smart Cities 2018, 2, 1–19. [Google Scholar] [CrossRef]
- De Leon, E.; Nabi, M. An experimental performance evaluation of bluetooth mesh technology for monitoring applications. In Proceedings of the 2020 IEEE Wireless Communications and Networking Conference (WCNC), Seoul, Republic of Korea, 25–28 May 2020; pp. 1–6. [Google Scholar]
- Dvoynikov, V.M.; Smirnov, V.A.; Burylov, D.A. Implementation of a Monitoring System for an Electrical Network Based on a Contactless Temperature Sensor and a Hall Effect Current Sensor. In Proceedings of the 2022 Conference of Russian Young Researchers in Electrical and Electronic Engineering (ElConRus), Saint Petersburg, Russia, 25–28 January 2022; pp. 604–607. [Google Scholar]
- Witham, O.; Johnston, L.N.; Xiao, M.; Feng, J.; Zhou, N.; Shaker, G. Batteryless wireless water leak detection system. In Proceedings of the 2019 International Conference on Smart Applications, Communications and Networking (SmartNets), Sharm El Sheikh, Egypt, 17–19 December 2019; pp. 1–4. [Google Scholar]
- Álvarez, F.; Almon, L.; Radtki, H.; Hollick, M. Bluemergency: Mediating Post-disaster Communication Systems using the Internet of Things and Bluetooth Mesh. In Proceedings of the 2019 IEEE Global Humanitarian Technology Conference (GHTC), Seattle, WA, USA, 17–20 October 2019; pp. 1–8. [Google Scholar]
- Yang Lam, T.C.; Ling Yew, S.S.; Keoh, S.L. Bluetooth Mesh Networking: An Enabler of Smart Factory Connectivity and Management. In Proceedings of the 2019 20th Asia-Pacific Network Operations and Management Symposium (APNOMS), Matsue, Japan, 18–20 September 2019; pp. 1–6. [Google Scholar]
- Garrido-Hidalgo, C.; Hortelano, D.; Roda-Sanchez, L.; Olivares, T.; Ruiz, M.C.; Lopez, V. IoT heterogeneous mesh network deployment for human-in-the-loop challenges towards a social and sustainable Industry 4.0. IEEE Access 2018, 6, 28417–28437. [Google Scholar] [CrossRef]
- Seymer, P.; Wijesekera, D.; Kan, C. Secure Outdoor Smart Parking Using Dual Mode Bluetooth Mesh Networks. In Proceedings of the 2019 IEEE 89th Vehicular Technology Conference (VTC2019-Spring), Kuala Lumpur, Malaysia, 28 April–1 May 2019; pp. 1–7. [Google Scholar]
- Seymer, P.; Wijesekera, D.; Kan, C.D. Smart Parking Zones Using Meshed Bluetooth Sensor Networks. In Proceedings of the International Conference on Smart Cities and Green ICT Systems, International Conference on Vehicle Technology and Intelligent Transport Systems; Springer: Cham, Switzerland, 2021; pp. 245–269. [Google Scholar]
- Al Dakheel, J.; Del Pero, C.; Aste, N.; Leonforte, F. Smart buildings features and key performance indicators: A review. Sustain. Cities Soc. 2020, 61, 102328. [Google Scholar] [CrossRef]
- Akkaya, K.; Guvenc, I.; Aygun, R.; Pala, N.; Kadri, A. IoT-based occupancy monitoring techniques for energy-efficient smart buildings. In Proceedings of the 2015 IEEE Wireless communications and networking conference workshops (WCNCW), New Orleans, LA, USA, 9–12 March 2015; pp. 58–63. [Google Scholar]
- Füchtenhans, M.; Grosse, E.H.; Glock, C.H. Smart lighting systems: State-of-the-art and potential applications in warehouse order picking. Int. J. Prod. Res. 2021, 59, 3817–3839. [Google Scholar] [CrossRef]
- Chew, I.; Karunatilaka, D.; Tan, C.P.; Kalavally, V. Smart lighting: The way forward? Reviewing the past to shape the future. Energy Build. 2017, 149, 180–191. [Google Scholar] [CrossRef]
- Ruuvi Innovations Ltd. Available online: https://ruuvi.com/ruuvitag-specs/ (accessed on 27 January 2023).
- Nordic Semiconductor Inc. nRF52840 Dongle Mannual. Available online: https://www.nordicsemi.com/-/media/Software-and-other-downloads/Product-Briefs/nRF52840-Dongle-product-brief.pdf (accessed on 20 January 2022).
- Pierleoni, P.; Gentili, A.; Mercuri, M.; Belli, A.; Garello, R.; Palma, L. Performance Improvement on Reception Confirmation Messages in Bluetooth Mesh Networks. IEEE Internet Things J. 2021, 9, 2056–2070. [Google Scholar] [CrossRef]
- Bluetooth SIG Inc. Mesh Profile 1.0.1. 2019. Available online: https://www.bluetooth.com/specifications/specs/mesh-profile-1-0-1/ (accessed on 27 October 2022).
- Kitchenham, B.; Brereton, O.P.; Budgen, D.; Turner, M.; Bailey, J.; Linkman, S. Systematic literature reviews in software engineering–a systematic literature review. Inf. Softw. Technol. 2009, 51, 7–15. [Google Scholar] [CrossRef]
- Xing, L. Reliability in Internet of Things: Current status and future perspectives. IEEE Internet Things J. 2020, 7, 6704–6721. [Google Scholar] [CrossRef]
- Brandt, A.; Buron, J.; Porcu, G. Home Automation Routing Requirements in Low-Power and Lossy Networks. 2010. Available online: https://www.rfc-editor.org/rfc/rfc5826 (accessed on 27 October 2022).
- Ibarra-Esquer, J.E.; González-Navarro, F.F.; Flores-Rios, B.L.; Burtseva, L.; Astorga-Vargas, M.A. Tracking the evolution of the internet of things concept across different application domains. Sensors 2017, 17, 1379. [Google Scholar] [CrossRef]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Jeon, K.E.; She, J.; Soonsawad, P.; Ng, P.C. BLE beacons for internet of things applications: Survey, challenges, and opportunities. IEEE Internet Things J. 2018, 5, 811–828. [Google Scholar] [CrossRef]
- Hassan, W.H. Current research on Internet of Things (IoT) security: A survey. Comput. Netw. 2019, 148, 283–294. [Google Scholar]
- Balliu, M.; Bastys, I.; Sabelfeld, A. Securing IoT Apps. IEEE Secur. Priv. 2019, 17, 22–29. [Google Scholar] [CrossRef]
- Lacava, A.; Zottola, V.; Bonaldo, A.; Cuomo, F.; Basagni, S. Securing Bluetooth Low Energy networking: An overview of security procedures and threats. Comput. Netw. 2022, 211, 108953. [Google Scholar] [CrossRef]
- Adomnicai, A.; Fournier, J.J.; Masson, L. Hardware security threats against Bluetooth mesh networks. In Proceedings of the IEEE Conference on Communications and Network Security (CNS), Beijing, China, 30 May–1 June 2018; pp. 1–9. [Google Scholar]
- Krzysztoń, M.; Marks, M. Simulation of watchdog placement for cooperative anomaly detection in bluetooth mesh intrusion detection system. Simul. Model. Pract. Theory 2020, 101, 102041. [Google Scholar] [CrossRef]
- Álvarez, F.; Almon, L.; Hahn, A.S.; Hollick, M. Toxic friends in your network: Breaking the bluetooth mesh friendship concept. In Proceedings of the 5th ACM Workshop on Security Standardisation Research Workshop, London, UK, 11 November 2019; pp. 1–12. [Google Scholar]
- Kaur, N.; Sood, S.K. An energy-efficient architecture for the Internet of Things (IoT). IEEE Syst. J. 2015, 11, 796–805. [Google Scholar] [CrossRef]
- Gotz, J.D.; Rayel, O.K.; Moritz, G.L. Improving Bluetooth Mesh Energy Efficiency Using Clustering. J. Commun. Inf. Syst. 2021, 36, 156–165. [Google Scholar] [CrossRef]
- Dunkels, A. The ContikiMAC Radio Duty Cycling Protocol, SICS Technical Report T2011:13 ISSN 1100-3154. Available online: http://www.dunkels.com/adam/dunkels11contikimac.pdf (accessed on 25 January 2022).
- Hortelano, D.; Olivares, T.; Ruiz, M.C. Reducing the energy consumption of the friendship mechanism in Bluetooth mesh. Comput. Netw. 2021, 195, 108172. [Google Scholar] [CrossRef]
- Romero, E.A.D.L. Experimental Performance Evaluation of the Bluetooth Mesh Protocol for Monitoring Applications. Master’s Thesis, Department of Electrical Engineering, Eindhoven University of Technology, Eindhoven, The Netherlands, 2019. [Google Scholar]
- Sánchez, R.C. Experimental Evaluation of Bluetooth Low Energy Mesh Networks. Master’s Thesis, Castelldefels School of Telecommunications and Aerospace Engineering, Barcelona, Spain, 2018. [Google Scholar]
- Brandão, A.S.; Lima, M.C.; Abbas, C.J.B.; Villalba, L.J.G. An Energy Balanced Flooding Algorithm for a BLE Mesh Network. IEEE Access 2020, 8, 97946–97958. [Google Scholar] [CrossRef]
- Ghamari, M.; Villeneuve, E.; Soltanpur, C.; Khangosstar, J.; Janko, B.; Sherratt, R.S.; Harwin, W. Detailed examination of a packet collision model for bluetooth low energy advertising mode. IEEE Access 2018, 6, 46066–46073. [Google Scholar] [CrossRef]
- Perez-Diaz-de Cerio, D.; Hernandez-Solana, A.; Garcia-Lozano, M.; Bardají, A.V.; Valenzuela, J.L. Speeding up bluetooth mesh. IEEE Access 2021, 9, 93267–93284. [Google Scholar] [CrossRef]






| Category | Use of BT Mesh |
|---|---|
| Smart Buildings | BT Mesh has been used to support a variety of features in smart buildings, including smart homes and commercial/office buildings. These include indoor localisation features [12,13,14], smart doorbells [15], and other smart home functions [16,17,18,19,20]. |
| Smart Lighting | Applications for wireless smart lighting can include various indoor and outdoor settings. Scenarios explored in the literature include smart homes [21], smart office spaces [22], and smart city traffic lights [23]. |
| Monitoring | Monitoring systems can include observing human behaviour and environmental conditions as well as keeping track of the health of critical equipment via sensors. Related work has investigated the feasibility of using BT Mesh to support such monitoring scenarios in [13,24,25,26] experimentally, emulating office and lab settings, where BT Mesh was used to deliver the sensor data packets. |
| Disaster Communication | BT Mesh based communication systems can be an alternative in cases of lack of Internet connectivity when communication infrastructure breaks down in disaster scenarios such as proposed in [27]. |
| Smart Factory | Industrial environments can use BT Mesh to support efficient human–machine and machine–machine communication as investigated in [28,29]. |
| Smart Parking | BT Mesh can be employed to implement infrastructure-less ticketing and management of parking lots, as proposed in [30,31], aided by BLE beacons. |
| Goal | Examples from Literature | Metrics in Literature | Findings from Literature |
|---|---|---|---|
| Extend the range of control/messaging | Smart doorbell | Package losses | Proposed mechanism exhibits no lower package loss when the distance is less than or equal to 10 m; when the distance is less than or equal to 24 m, the packet loss is less . |
| LED control system extension | Transfer rate | Transfer rate dramatically decreases after 24 m | |
| Smart factory | Average time taken, average message interval, message loss, message data rates, round trip time | When 500 messages are used, min. average time taken = 6569 ms, min. average message interval = 13 ms, max.message data rate = 76 msg/s, min. round trip time 109 ms, and there are no messages lost. | |
| Localisation using RSSI | Secure smart parking lot | Detection accuracy | Detection accuracy of approximately 70% |
| Enable communication in the absence of infrastructure | Post-disaster communication system | Response time, packet-loss-rate | In the smart office, response time (ms) and packet loss rate (%) are 1053.13 and 38.21, respectively. In the smart home, response time (ms) and packet loss rate (%) are 995.53 and 8.5, respectively. |
| Attributes | Technologies | ||||||||
|---|---|---|---|---|---|---|---|---|---|
| BT Mesh | Wi-Fi | Z-Wave | Zigbee | LTE-M | NB-IoT | Sigfox | LoRaWAN | BT Piconet | |
| Range | 100 m–1 km | 15 m–100 m | 30 m–50 m | 30 m–100 m | 1 km–10 km | 1 km–10 km | 3 km–50 km | 2 km–20 km | <10 m |
| Through-put | 125 kbps–2 Mbps | 54 Mbps–1.3 Gbps | 10 kbps–100 kbps | 20 kbps–250 kbps | ≤1 Mbps | ≤200 kbps | ≤100 bps | 10 kbps–50 kbps | 200–2100 kbps |
| Power consumption | Low | Medium | Low | Low | Medium | Low | Low | Low | Medium |
| Ongoing cost | One-time | One-time | One-time | One-time | Recurring | Recurring | Recurring | One-time | One-time |
| Topology | Mesh | Star, Mesh | Mesh | Mesh | Star | Star | Star | Star | Star |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Natgunanathan, I.; Fernando, N.; Loke, S.W.; Weerasuriya, C. Bluetooth Low Energy Mesh: Applications, Considerations and Current State-of-the-Art. Sensors 2023, 23, 1826. https://doi.org/10.3390/s23041826
Natgunanathan I, Fernando N, Loke SW, Weerasuriya C. Bluetooth Low Energy Mesh: Applications, Considerations and Current State-of-the-Art. Sensors. 2023; 23(4):1826. https://doi.org/10.3390/s23041826
Chicago/Turabian StyleNatgunanathan, Iynkaran, Niroshinie Fernando, Seng W. Loke, and Charitha Weerasuriya. 2023. "Bluetooth Low Energy Mesh: Applications, Considerations and Current State-of-the-Art" Sensors 23, no. 4: 1826. https://doi.org/10.3390/s23041826
APA StyleNatgunanathan, I., Fernando, N., Loke, S. W., & Weerasuriya, C. (2023). Bluetooth Low Energy Mesh: Applications, Considerations and Current State-of-the-Art. Sensors, 23(4), 1826. https://doi.org/10.3390/s23041826








