1. Introduction
Cloud computing plays an important and interconnected role amongst today’s trending technologies related to the Internet of Things (IoT), machine learning (ML), deep learning (DL), and cyber-physical systems (CPS). All these major domains require cloud platforms as mandatory ones for the storage and processing of data from sensors and devices and to provide possible suggestions. All the massive applications related to smart cities, surveillance, or smart transports also depend on cloud platforms either for storing or retrieval of their data as it is more flexible and convenient to access the information anywhere around the globe instead of maintaining it in a local environment [
1,
2]. The interrelated preferences of such critical applications push the cloud to ensure the maximum level of security [
3]. The target of this paper is to identify the wide category of security violations targeting IoT data in rest and motion. The security framework is formulated for the identified attack categories by adopting effective methodologies and algorithms.
The year 2020 accelerated the prevalence of digital technology and the cloud due to the benefits of connecting all the needs in spite of several ongoing challenges. As connectivity seems to be increasingly necessary for individuals pursuing work from home during the COVID-19 pandemic, digital transformation and data transmitted by IoT devices have begun their rapid blooming phase. The data transmitted by IoT devices paved a critical role in order to optimize business processes, analyzing patterns, streamlining processes, and understanding everyday business routines [
4,
5]. The digital transformation routed us to today’s integrated platform of cloud and IoT. The combined solutions of cloud and IoT help in supporting data capture with real-time control and intelligence monitoring.
The applications of cloud-assisted IoT technologies range widely from:
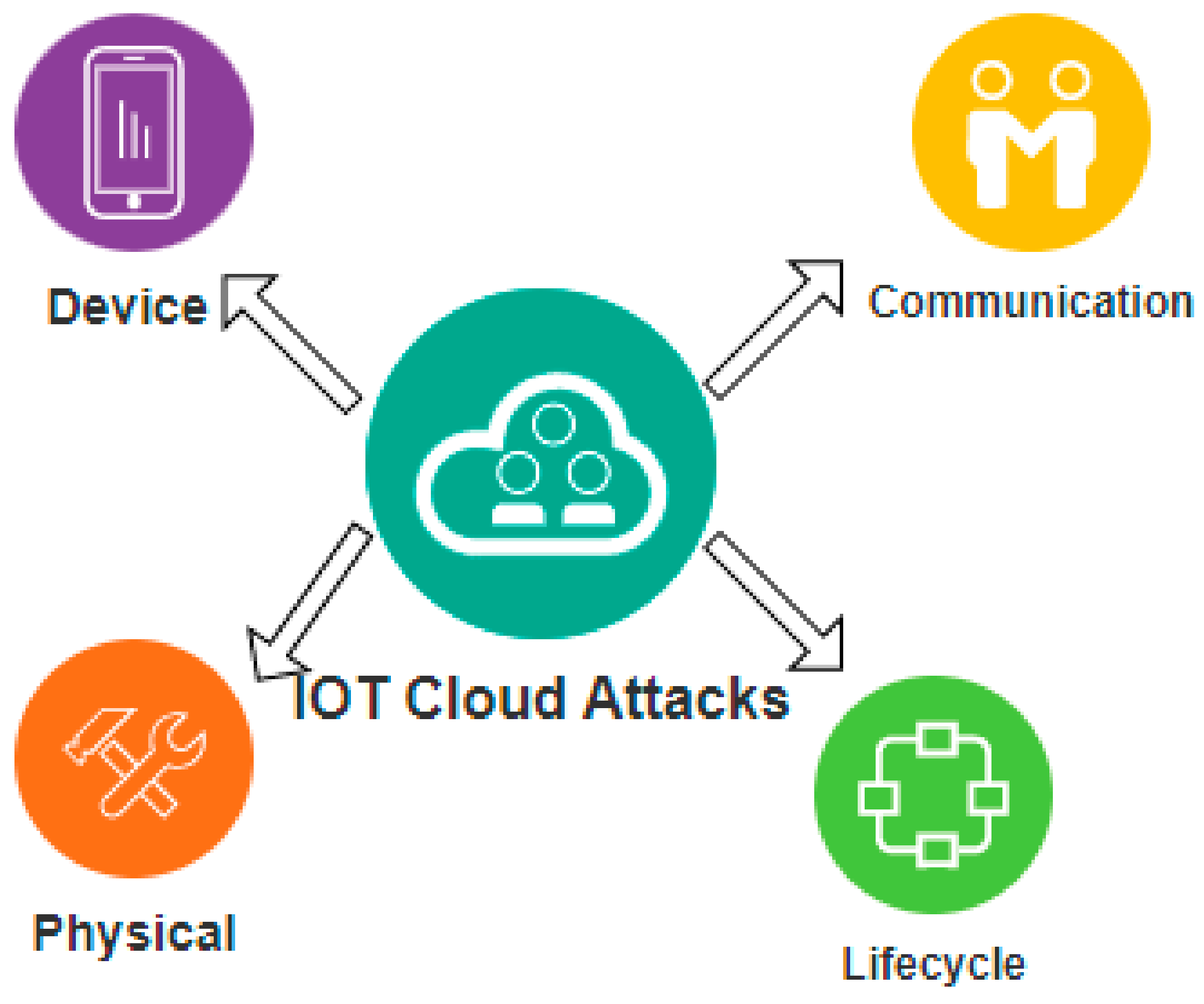
The growing nature and interconnectivity of the internet make the IoT platform more scalable and easily adaptable. IoT has put its marks in the fields of food production, the manufacturing industry, the finance sector, and the healthcare domain. Day by day, more automation techniques are getting merged into IoT platforms to enhance a high degree of comfort and convenience for internet users. More and more organizations are migrating towards IoT, which in turn, increases the count of IoT devices. Collection and monitoring such a volume of IoT devices prove challenging as it suffers from severe security violations. Hence the attack surfaces of IoT devices need to be focused on in order to analyze the existence of possible threats and vulnerabilities, among which the general IoT attack categories are depicted in
Figure 1, and major attack targets are depicted in
Figure 2.
Based on the current literature related to security violations among IoT devices, the aforementioned attacks in
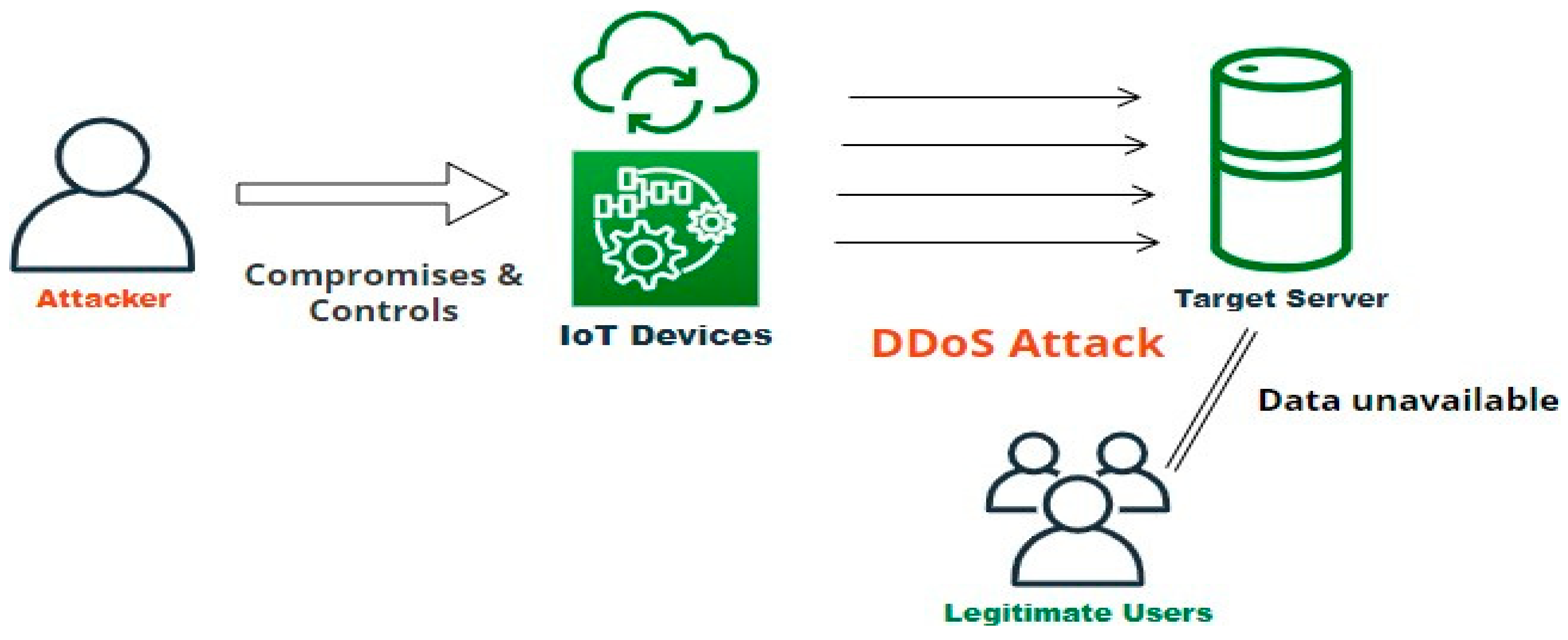
Figure 2 play a major role in weakening security and making the complete system unavailable to intended users. Distributed denial-of-service (DDoS), malware, and Man-in-The-Middle (MiTM) attacks focus on violating confidentiality and availability constraints and making IoT devices and communication channels vulnerable.
In addition to Man-in-the-Middle (MiTM) and distributed denial-of-service (DDoS) attacks, there are other types of attacks that can disrupt the normal functioning of IoT devices and their applications. These attacks include denial-of-service, jamming, Sybil, black hole, worm hole, and malware attacks. Among these attacks, DDoS attacks are considered the most vulnerable as they disrupt and corrupt the complete functioning of the entire system, causing more damage and taking more time to recover compared to the severity of other attack categories.
In this paper, we have focused on DDoS and false data sharing attacks as the major attack categories and proposed a comprehensive solution to mitigate these attacks by using various methods such as simple network management protocol (SNMP), Kullback–Leibler distance (KLD), access control rules (ACL), and moving target defense (MTD) techniques. The SNMP is used to closely monitor the abnormal patterns of incoming network traffic based on changes in the values of SNMP management information base (MIB) variables. DDoS detection is carried out by analyzing the incoming attack patterns and packet structure of attack requests and formulating ACL rules to block known DDoS patterns. The MTD techniques are applied to harden the attack target and reduce the attack probability. The proposed method has been validated by estimating attack probabilities and switching delays in an experimental testbed simulation on the Amazon Web Service (AWS) platform. Results have shown that the proposed method is effective in reducing the attack probability to a minimum of 0.2%.
Furthermore, the proposed solution is designed to be flexible and adaptable to different types of IoT environments and can be easily integrated with existing systems. It also provides a comprehensive and effective approach to detecting and mitigating DDoS and false data-sharing attacks in IoT environments.
2. Technical Background
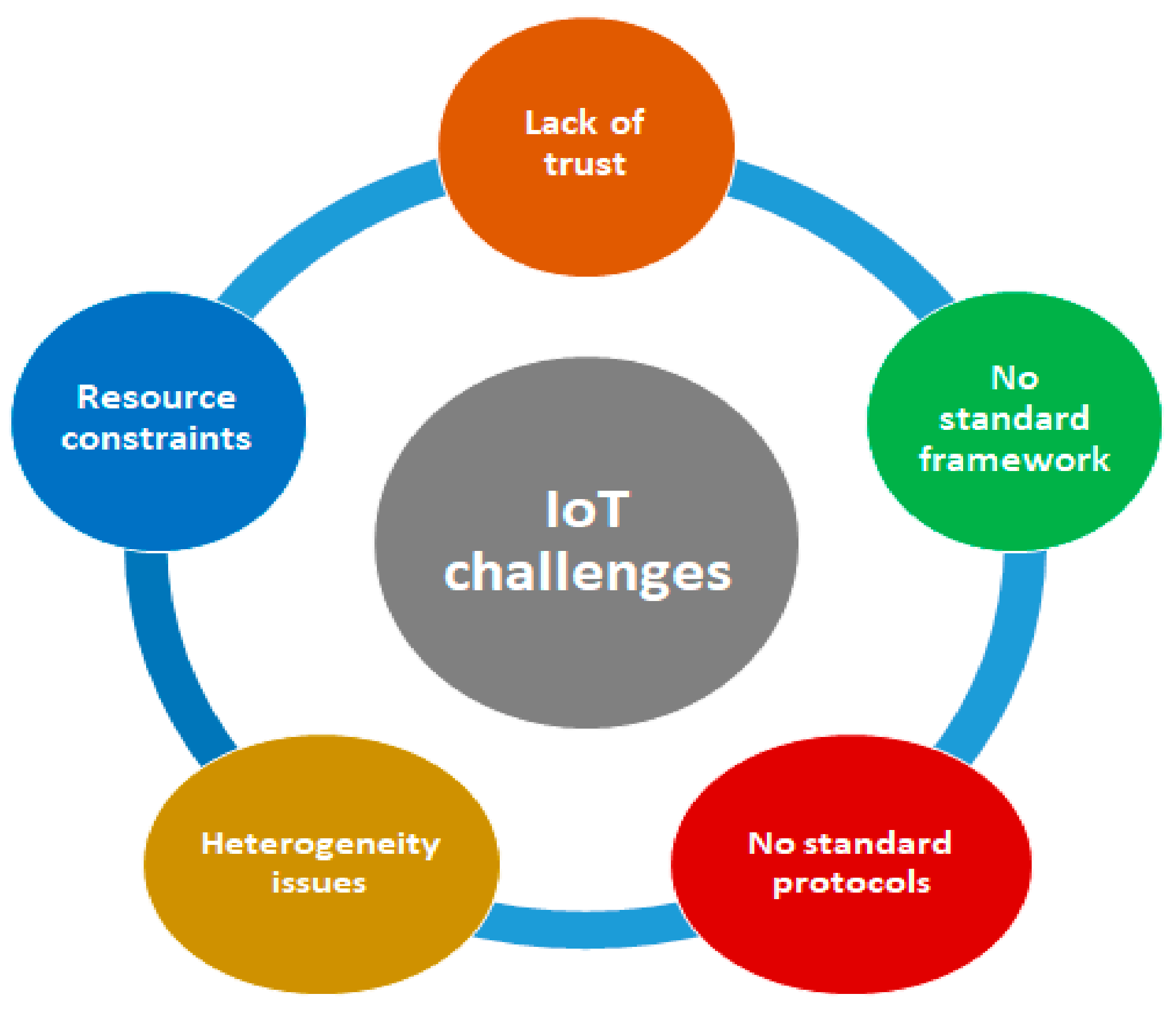
The key security concerns in the IoT environment [
6] are classified into implementation, privacy, network infrastructure, security threats, malware, authentication, and authorization-related challenges. Violation of IoT-related security focus merely related to the areas of privacy and confidentiality among heterogeneous management and network capacity constraints. Possible security issues include securing IoT architecture, active detection, and protection of DoS and DDoS, standards, methods, or tools for managing all user identity and objects. A few issues related to the private domain are personal information control, improvement of privacy technologies and related rules, protection of exchanged sensitive information over the communication medium, and confidentiality of stored messages. The widespread adoption of the cloud to effectively carry out the collection, storage, and analysis of IoT data paves the way for more associated open challenges [
7], which disrupt authorized access, retrieval, and extraction of information from the cloud.
The goal of this paper [
8] is to identify the security challenges and key issues that are likely to arise in the IoT environment in order to guide authentication techniques to achieve a secure IoT service. Denial-of-service (DoS) [
9] is considered to be the most dominant and devastating in the IoT environment. The attackers could be using flooding attacks in order to exhaust system resources such as CPU, memory, and bandwidth. With the adoption of numerous techniques, the attacker’s target is to flood the network with bogus packets [
10,
11,
12] and hence block legitimate or trusted users from utilizing the usual services.
Replay attack [
13] targets the authentication and key exchange-related protocols in order to capture or store either a whole session or a fragment of a session in legitimate traffic. On gaining trust over the public network, the attacker sends the captured message in order to indicate participation in the original session. A replay attack is mentioned as a security weakness or vulnerability in the authorization procedure for accessing stored data. To handle a replay attack, the current scenario uses three types of solutions, including timestamp, nonce, or challenge-response mechanisms. The freshness of a message is identified and tracked by using the concept of timestamp, where the purpose of the nonce is the generation of random digits and comparing the same for granting access. Challenge-response measures attempt to test the pre-shared secret values between the user and the target system or entity.
The password-guessing attack [
14,
15] occurs by overhearing the communication channel by exploring weaknesses in numerous authentication protocols. This type of attack could take place either in online or offline mode. The attacker will be able to guess all possible passwords in order to succeed in the authentication process. The main aim of a spoofing attack is to make the servers trust that the attacker is one of the authorized entities.
Various categories of distributed denial-of-service (DDoS) attacks, along with their impact on IoT devices, are discussed [
16], along with detailed mitigation models. It deliberately discusses the classification of different intrusion detection systems, anomaly detection techniques, different intrusion detection models related to datasets, various machine learning and deep learning methods for pre-processing data, and malware detection is carried out. Most of the security challenges are specific to the issues related to IoT devices and are listed below in
Figure 3.
There are many categories of DDoS attacks specific to IoT devices namely, TCP SYN flood, tear drop, Smurf, ping of death, and botnet attacks. The main classification of DDoS includes reflection and amplification attacks. The main difference between these two attack categories could be analyzed by observing the size of request and response packets. The size of the response is times bigger than the request size in an amplification attack, whereas the size of the response is equal to the request size in reflection-based attacks. Attackers will be utilizing common vulnerabilities for launching DDoS attacks:
Various anomaly detection techniques [
17,
18] used for detecting the presence of malware in IoT devices are signature-based detection and anomaly-based detection. The former detection pattern is not a successful one as the bots keep on changing their signature pattern, while the latter helps in tracking behavioral changes between the normal and botnet traffic. Other approaches related to community-based anomaly detection [
19,
20,
21] focus on identifying bots based on the communication graph. A bad neighborhood is one of the methods utilized in phishing and spam detection to identify the cluster of IP addresses that performs malicious activities over a period of time. The various authentication techniques for securing IoT devices are detailed in
Table 1.
3. Dimensions of Security Threats in IoT
The security threats and challenges associated with IoT are more prevailing as, according to a recent survey of IoT analytics, by 2025, there will be 30.9 billion [
22] connected devices in the world. The increasing security vulnerabilities and cyber-attacks block many users from utilizing IoT devices. IoT-related security problems are more prevalent in healthcare and logistic-related domains [
23]. The security challenges associated with IoT data while operating in a cloud environment could be generalized based on the analysis of common threats prevailing in the current scenario, which are listed below:
Software vulnerabilities;
Firmware vulnerabilities;
Insecure communication channel;
Data leaks from IoT systems;
Malware risks;
Cyber-attacks.
The possible causes for the occurrence of such threats in IoT-associated cloud environments are due to the following:
Lack of computational capacity;
Poor access control techniques;
Limited budget to carry out testing;
Limited budget to ensure firmware security;
Lack of regular patches;
Lack of periodic upgrades;
Technical limitations of IoT devices;
Unavailability of software updates for older IoT devices;
Ineffective protection from physical attacks.
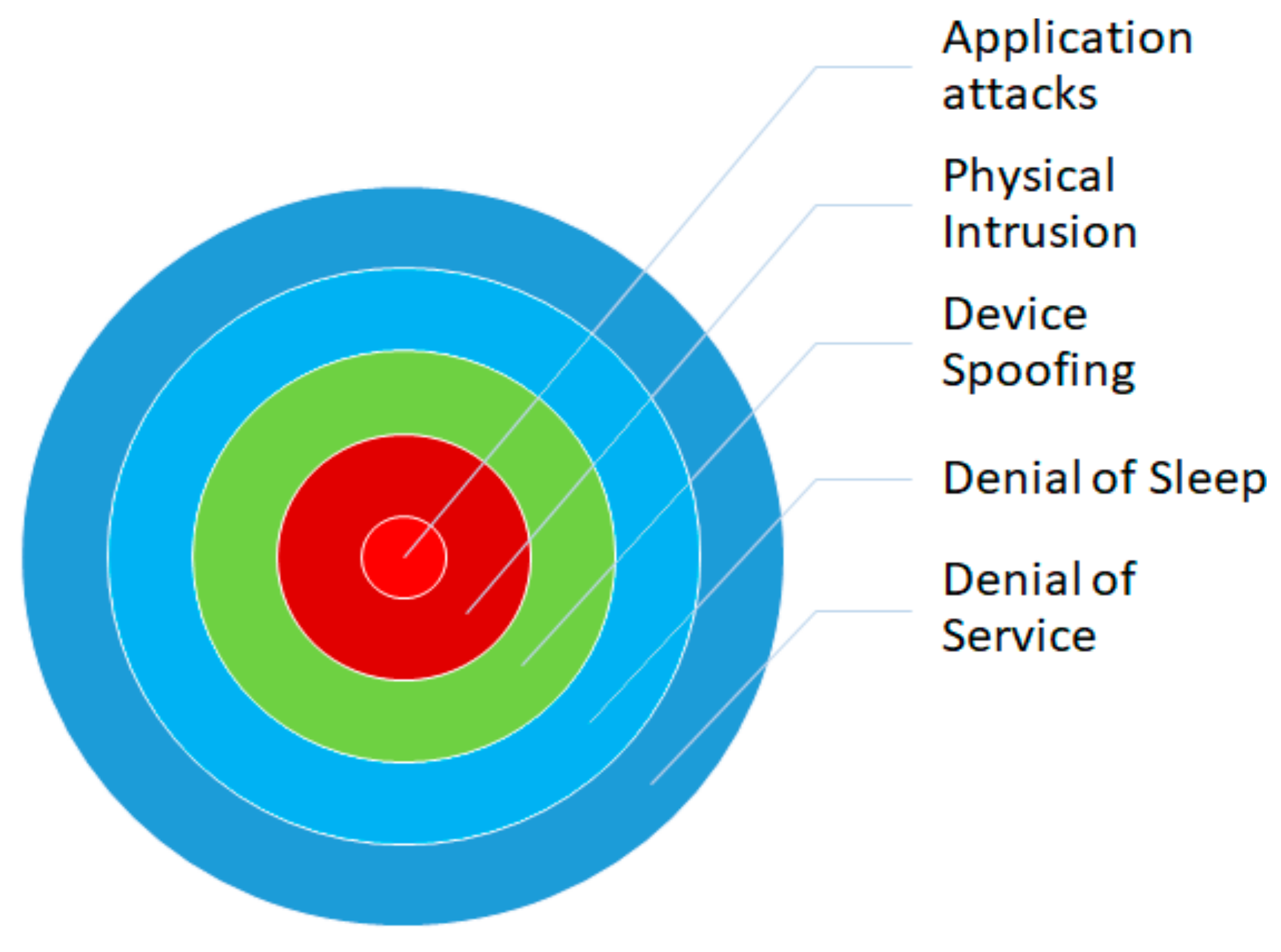
One of the most dangerous threats which happen due to an insecure communication medium is the Man-in-the-Middle (MiTM) attack. On installing malware or by changing the device’s functionality, MiTM is launched if the device does not use any encryption or authentication mechanisms. Man-in-the-Middle (MiTM) attacks are a significant threat to the security of IoT systems due to their reliance on insecure communication mediums. These attacks involve the attacker intercepting and altering communication between two parties without their knowledge or consent. This can be accomplished by installing malware on a device or altering its functionality. IoT systems are particularly vulnerable to MiTM attacks because they often lack robust encryption and authentication mechanisms. As a result, attackers can easily intercept and modify communication between devices, making it difficult for users to detect and prevent these attacks. IoT systems are prone to various cyber-attack categories, as depicted in
Figure 4. Application attacks target vulnerabilities in the software or firmware of an IoT device. This can include SQL injection, cross-site scripting, and command injection attacks. Physical intrusion involves physically accessing an IoT device to extract information, install malware, or disrupt its operation. An attacker may use tools like lock picking or physical access to the IoT device to perform these attacks.
Device spoofing involves tricking a device into connecting to a fake device or network, allowing the attacker to intercept or modify communication. This can be done through a technique known as “rogue access points” or “evil twin” attacks. Denial of sleep involves preventing IoT devices from entering a low-power state, which can cause them to consume more energy and potentially shorten their lifespan. Denial of service involves overwhelming a device or network with a flood of traffic, making it inaccessible to legitimate users. This can be done through a distributed denial-of-service (DDoS) attack, where multiple devices are used to flood the target.
These attacks are often interconnected, with one layer of security being compromised, providing an easy pathway for a DDoS attack to be launched.
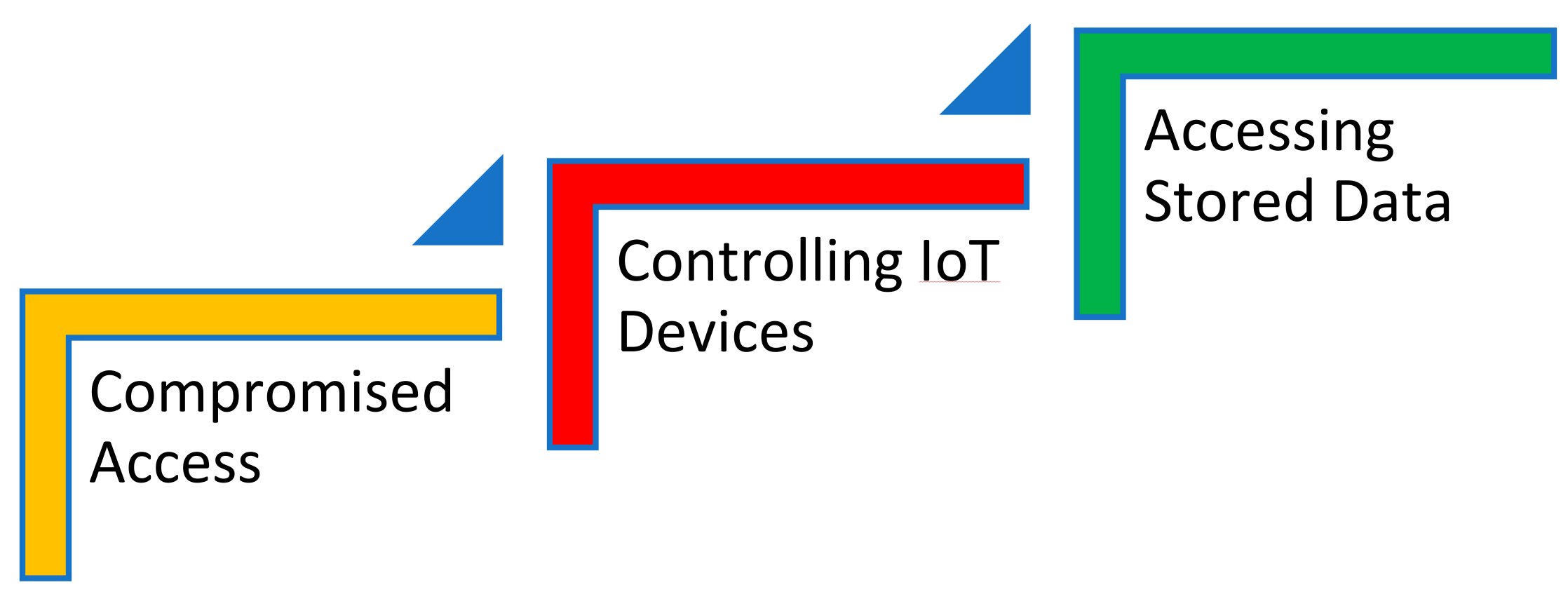
On careful analysis and deep inspection of existing cyber-attacks, general attacks, and device-specific threat categories of IoT in a cloud environment, the below structure, as depicted in
Figure 5, is formulated. Irrespective of the type of cyber-attack in the cloud-assisted IoT environment, the below steps remain the same.
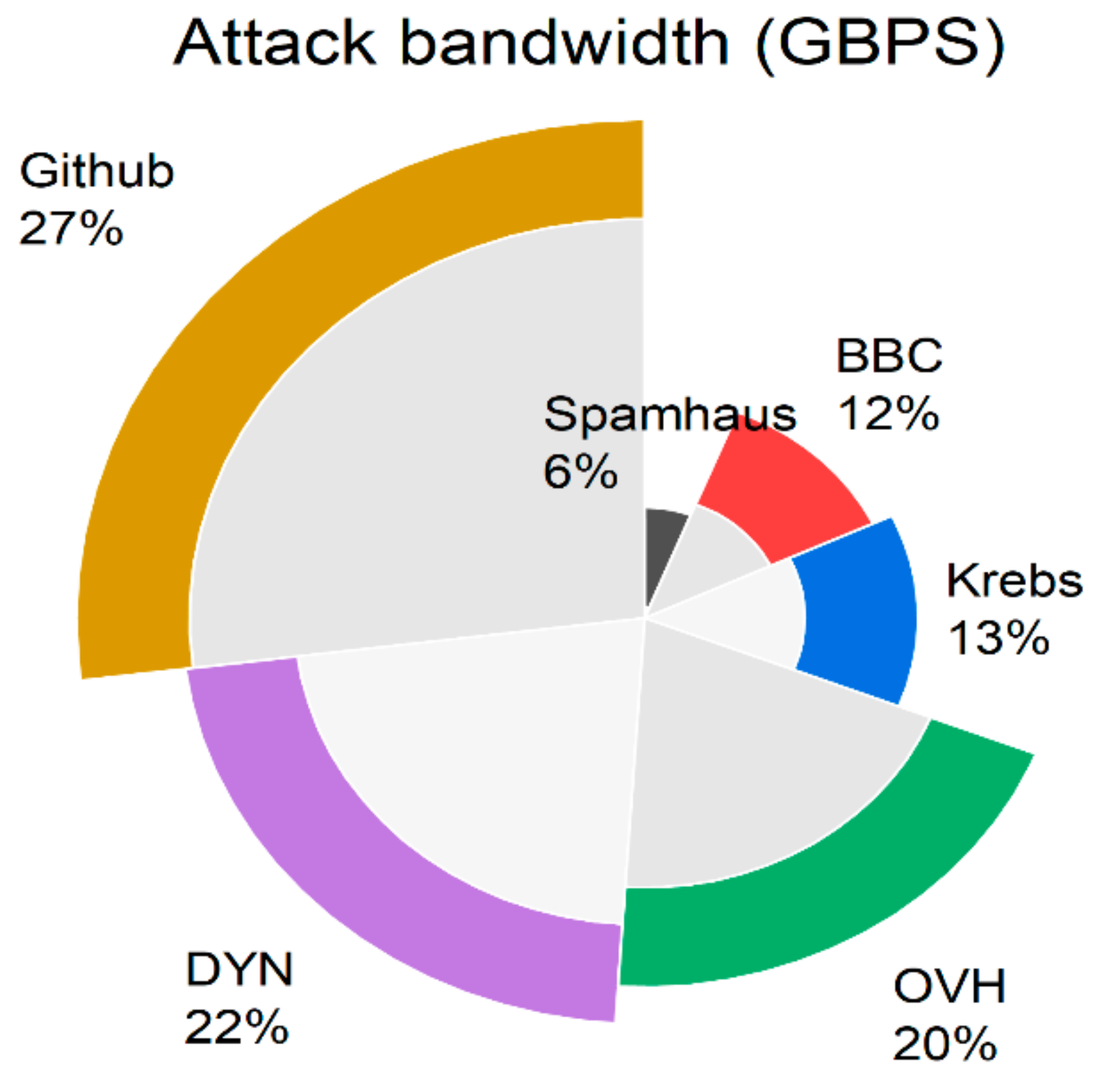
Among other attack categories in the IoT environment, DDoS seems to be more prevalent, which is evident from the below statistics depicted in
Figure 6. DDoS is more devastating as it makes the complete IoT devices inaccessible and unavailable for the legitimate user community. The prevalence of DDoS attacks in IoT platforms and their underlying structure are depicted in
Figure 6 and
Figure 7.
Figure 6 clearly illustrates the bandwidth affected in the IoT platform due to the launch of a DDoS attack. The ultimate reasons for DDoS attacks are the insecure communication medium and unsecured data in a cloud environment. The proposed works address both by formulating an efficient architecture.
Due to the prevalence of DDoS attacks in IoT environments, this paper suggests the application of moving target defense strategies to make the attack target harder and to decrease the attack probability by applying various MTD techniques, diversity, and migration.
4. IoT Attack Detection Procedure Using SNMP and Kullback–Leibler Distance (KLD)
The most devastating threat to IoT devices, namely DDoS and false data injection, is chosen to provide mitigation solutions in terms of access control list and moving target defense. Detection of DDoS targeting IoT devices is identified with the help of a simple network management protocol (SNMP) [
24,
25]. SNMP is an application layer protocol that is merely adopted to track the normal functioning of network devices. In the DDoS pattern analysis experiment, SNMP features are adopted by deploying SNMP agent and SNMP manager source codes in the experimental setup discussed in [
26]. Based on the changes in SNMP MIBs tcpActiveOpens, tcpPassiveOpens, and tcpAttemptFails, the incoming traffic is categorized as “normal” or “attack”, which is depicted in
Figure 8. Based on the observations from SNMP and further analysis of incoming request headers [
27], ACL rules are formulated, which work by blocking unknown, malformed headers and unknown reference links. On detecting DDoS attacks using SNMP MIBs, access control rules are formulated as a basic Level 1 prevention measure.
The detection of false data injection is done by estimating the Kullback–Leibler distance (KLD) between the original data (at the time of sending) and received data (after sending across the communication channel).
This method is proven to be most effective in the detection of abnormal traffic based on either the packet size or distribution statistics [
28,
29,
30,
31]. Probability distributions for data before sending in the network and after sending in the communication channel are carried out, and differences between them are analyzed using Equation (1). Information distance is represented as the divergence between two probability distributions. The information divergence between the probability distributions
and
where
;
of order
could be calculated as:
Detection of false data injection attacks on the data collected from IoT sensors could be identified with the help of Kullback–Leibler distance. Larger KLD reflects the variation in probability distributions of the measurements from historical data. It is a natural distance function from a true probability distribution to a target probability distribution . Based on the deviation in final equation values, it could be verified if any false data is added along with the original one or not.
5. IoT Attack Mitigation Procedure Using ACL and MTD in AWS
The complete setup is configured in the Amazon Web Service (AWS) console to represent various proxy and web server configurations. For mitigation against DDoS, two levels of control measures are enforced by adopting the access control list in Level 1 and moving target defense-based migration concepts in Level 2. All the initial parameters specific to legitimate user requests are analyzed in detail, based on which the specific functionalities are identified in pre-defined ACL rules.
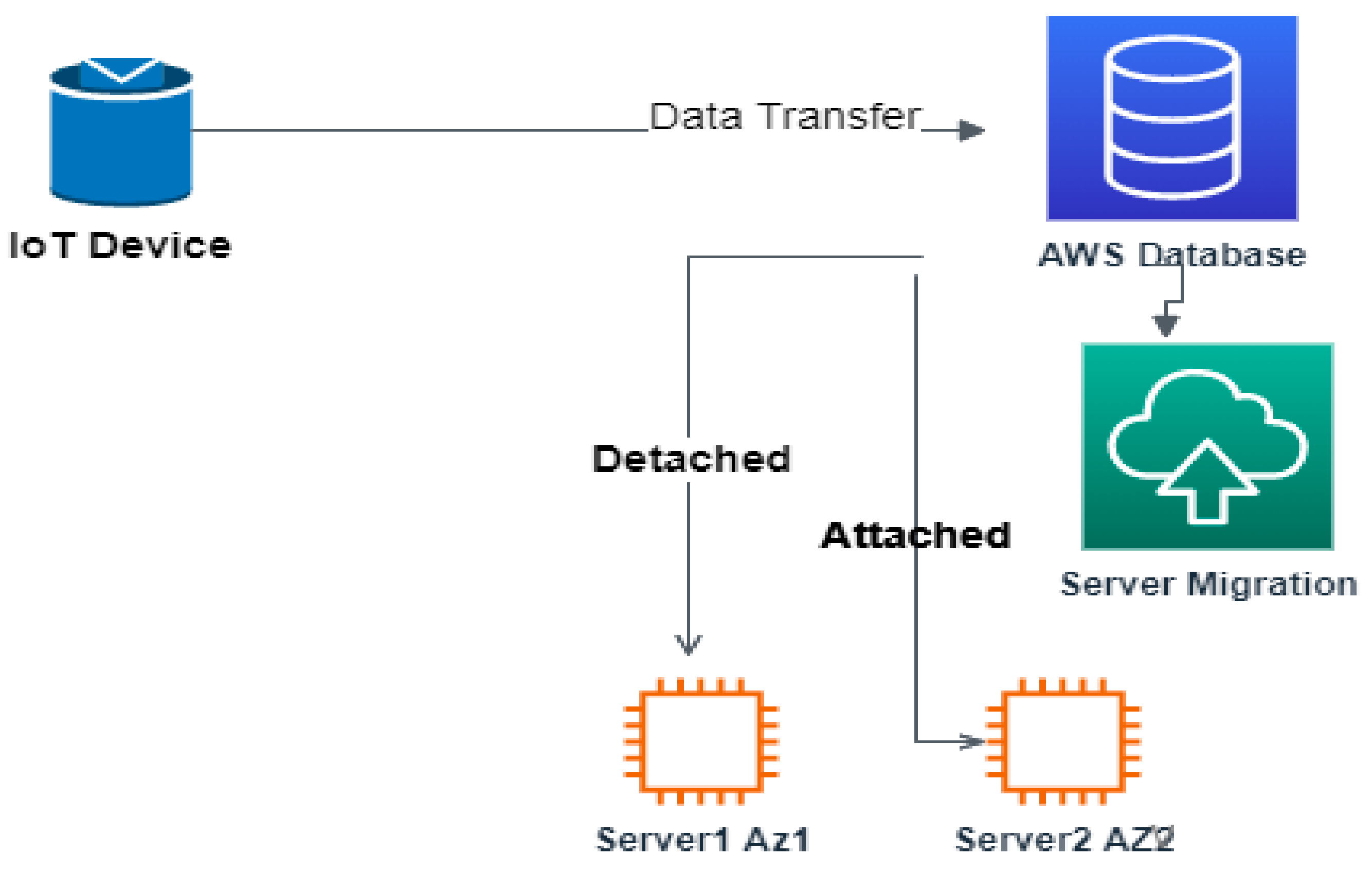
The main purpose of adding ACL rules in Level 1 is to filter DDoS attack traffic related to user-agent, header filed, request size, request count, and IP address. The requests which get validated and proven to be legitimate in Level 1 will be moved to Level 2. To secure the main or target server from crashing due to unwanted malicious incoming traffic, server hardening is carried out, which in turn decreases the DDoS attack probability by hiding the IP of the main server by maintaining servers in different availability zones and with the migration process. The target servers are made dynamic by applying the concept of MTD diversity. The location of the target server changes from time to time across various availability zones in order to withstand attacks by applying the concept of migration, which is depicted in
Figure 9.
The AWS server instance plays a crucial role in maintaining the data that is transferred from IoT devices. In order to ensure the confidentiality of this data, the concept of server migration is applied. This is done to prevent an attacker from compromising the data by gaining knowledge of the IP address and other protection mechanisms of the server using port scanning tools.
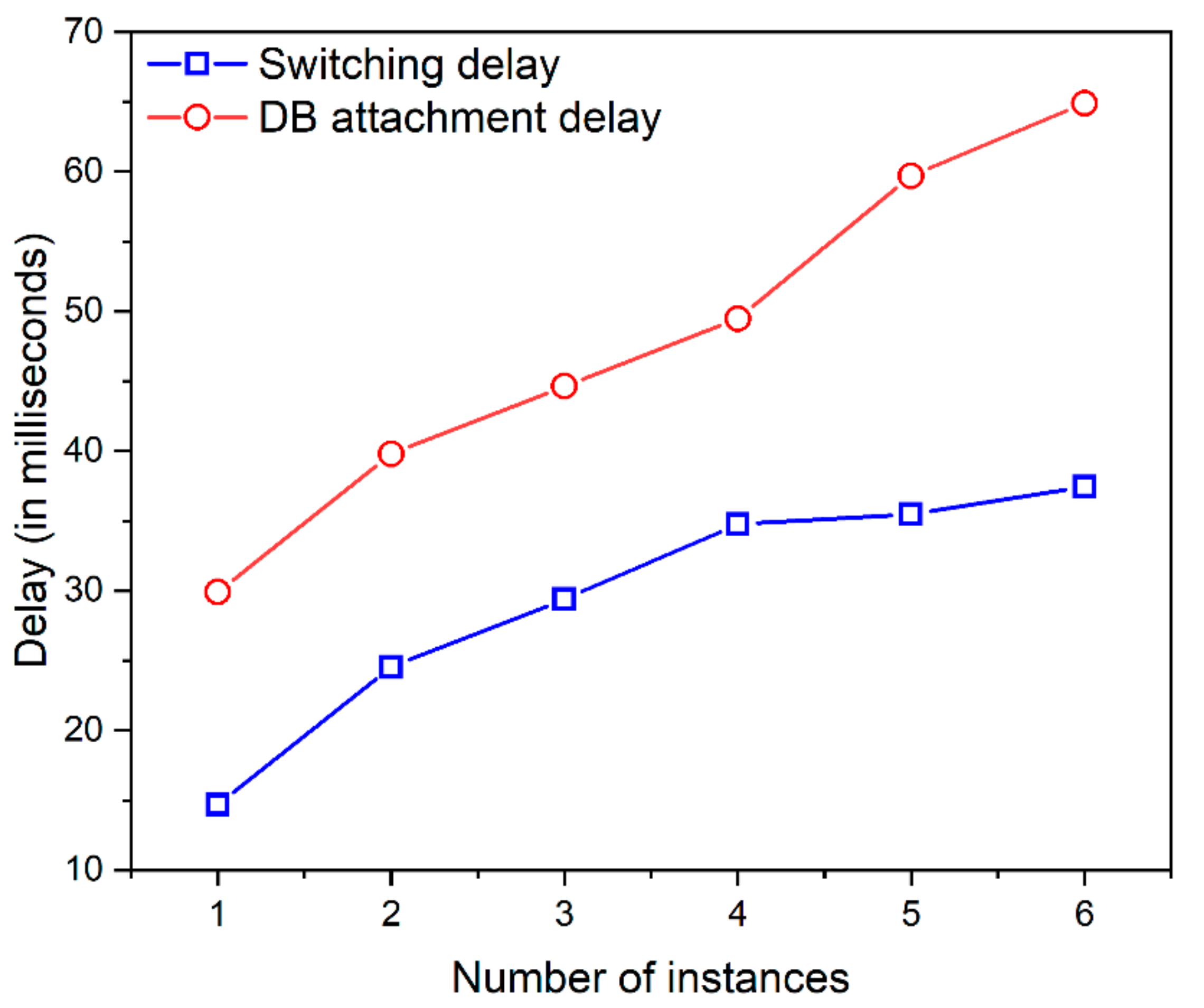
The moving target defense (MTD) technique is applied to achieve more security by migrating the server instance from time to time. The migration process does not cause any delay or connection issues whenever there is a legitimate attempt because the AWS server instance in different availability zones alone remains attached or detached from the database instance. This is validated by the graph depicted in
Figure 10 and
Figure 11.
In
Figure 10, the
x-axis represents the number of instances chosen in AWS, and the
y-axis represents the switching delay in milliseconds. The switching delay indicates the requests directed from one instance to another. The y-axis also represents the DB attachment delay in milliseconds which indicates the time taken to attach DB from one instance to another.
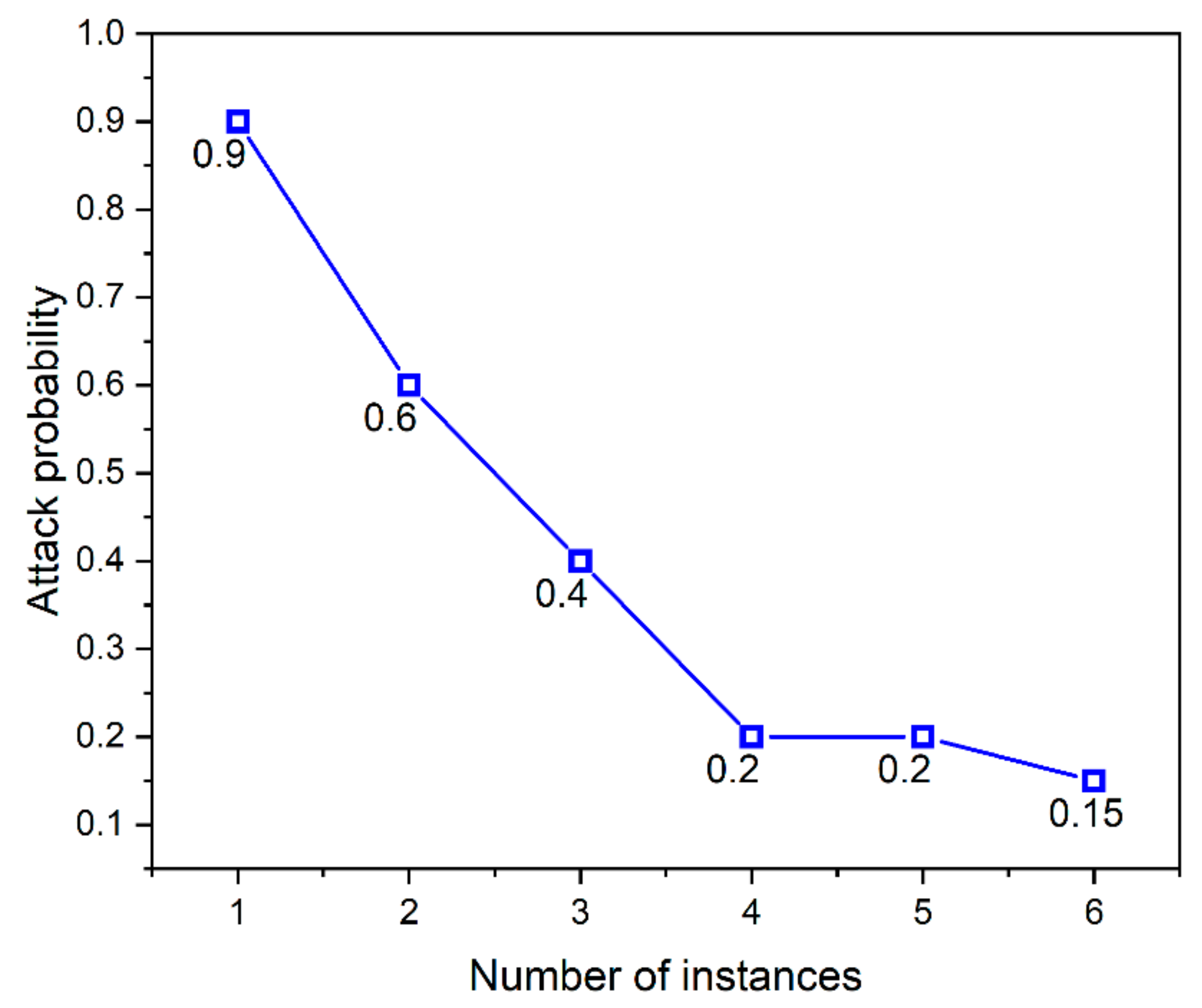
In
Figure 11, the
x-axis indicates the number of instances in AWS, and the
y-axis indicates the attack probability reduction with an increase in the number of instances. It is observed that on increasing the number of AWS instances and applying the concepts of MTD, the attack probability is reduced to a minimum of 0.15% as the probability of occurrence of an attack. The chosen MTD method outperforms the existing schemes [
22,
31] in reducing the attack probability from 0.5% to 0.15%, the switching delay reduced to 0.076 s from 1.2 s, and the DB attachment delay also decreased on comparing the existing literature from 1.4 s to 0.032 s.
Therefore, the methods applied in the proposed method are effective in mitigating the IoT-based DDoS and false data-sharing attacks with a considerable increase in performance metrics. The result shows that the MTD technique is effective in reducing the attack probability and improves the performance of the system by reducing the delay of switching and DB attachment.
6. Conclusions
IoT technology plays a vital role in today’s digital, interconnected scenario. Ensuring the confidentiality and security of data from IoT devices is crucial for the success of the entire IoT model. In this paper, we discussed the detection and mitigation of DDoS and false data injection attacks in IoT environments. The detection of these attacks was carried out using simple network management protocol (SNMP) and kernel learning detection (KLD), whereas the mitigation was done using access control lists (ACL) and moving target defense (MTD) techniques. The proposed techniques were found to be more accurate and efficient than existing security techniques.
The focus of future work should be extended to the proposed techniques to detect and mitigate other types of IoT attacks. The communication channel is secured by maintaining ACL lists and SNMP monitors, while the stored data in AWS instances is maintained using MTD techniques such as diversity and migration. Both these techniques help in maintaining the dynamic IP address of the server and provide an added layer of security by not giving any clue about the location of the data. The processing delay due to migration is negligible, as evident from the experimental results discussed in the paper.
In conclusion, the proposed techniques provide an efficient and effective solution for detecting and mitigating DDoS and false data injection attacks in IoT environments. The proposed techniques are not only accurate but also improve the performance of the system by reducing the delay of switching and DB attachment. As IoT technology continues to evolve and expand, it is essential to develop robust security mechanisms to protect against various types of attacks and ensure the confidentiality of data.
Author Contributions
Conceptualization, R.G., S.U., M.M., R.V. (Rajasekharan Vezhavendhan), R.V. (Rajiv Vincent), M.R. and M.E.; Methodology, R.G., S.U., R.V. (Rajasekharan Vezhavendhan) and R.V. (Rajiv Vincent); Software, M.M. and M.E.; Validation, R.G., S.U., R.V. (Rajasekharan Vezhavendhan), R.V. (Rajiv Vincent) and M.R.; Formal analysis, R.G., S.U., R.V. (Rajasekharan Vezhavendhan), R.V. (Rajiv Vincent) and M.R.; Investigation, R.G., S.U., R.V. (Rajasekharan Vezhavendhan), R.V. (Rajiv Vincent) and M.R.; Resources, M.M. and M.E.; Writing—original draft, R.G., S.U., R.V. (Rajasekharan Vezhavendhan), R.V. (Rajiv Vincent) and M.R.; Writing—review & editing, M.M. and M.E. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the project SP2023/74 Application of Machine and Process Control Advanced Methods supported by the Ministry of Education, Youth and Sports, Czech Republic.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Zhang, H.; Luo, G.; Li, J.; Wang, F.-Y. C2FDA: Coarse-to-fine domain adaptation for traffic object detection. IEEE Trans. Intell. Transp. Syst. 2022, 23, 12633–12647. [Google Scholar] [CrossRef]
- Cao, B.; Li, M.; Liu, X.; Zhao, J.; Cao, W.; Lv, Z. Many-objective deployment optimization for a drone-assisted camera network. IEEE Trans. Netw. Sci. Eng. 2021, 8, 2756–2764. [Google Scholar] [CrossRef]
- Lv, Z.; Chen, D.; Lou, R.; Song, H. Industrial security solution for virtual reality. IEEE Internet Things J. 2021, 8, 6273–6281. [Google Scholar] [CrossRef]
- Wang, S.; Sheng, H.; Yang, D.; Zhang, Y.; Wu, Y.; Wang, S. Extendable Multiple nodes recurrent tracking framework with RTU+. IEEE Trans. Image Process. 2022, 31, 5257–5271. [Google Scholar] [CrossRef]
- Zhou, X.; Zhang, L. SA-FPN: An effective feature pyramid network for crowded human detection. Appl. Intell. 2022, 52, 12556–12568. [Google Scholar] [CrossRef]
- Ghorbani, H.R.; Ahmadzadegan, M.H. Security challenges in internet of things: Survey. In Proceedings of the 2017 IEEE Conference on Wireless Sensors (ICWiSe), Miri, Malaysia, 13–14 November 2017. [Google Scholar]
- Kiruthika, J.; Khaddaj, S. Software quality issues and challenges of internet of things. In Proceedings of the 2015 14th International Symposium on Distributed Computing and Applications for Business Engineering and Science (DCABES), Guiyang, China, 18–24 August 2015. [Google Scholar]
- Azrour, M.; Mabrouki, J.; Guezzaz, A.; Kanwal, A. Internet of Things security: Challenges and key issues. Secur. Commun. Netw. 2021, 2021, 5533843. [Google Scholar] [CrossRef]
- Neshenko, N.; Bou-Harb, E.; Crichigno, J.; Kaddoum, G.; Ghani, N. Demystifying IoT security: An exhaustive survey on IoT vulnerabilities and a first empirical look on internet-scale IoT exploitations. IEEE Commun. Surv. Tutor. 2019, 21, 2702–2733. [Google Scholar] [CrossRef]
- Ahmed, A.; Latif, R.; Latif, S.; Abbas, H.; Khan, F.A. Malicious insiders attack in IoT based Multi-Cloud e-Healthcare environment: A Systematic Literature Review. Multimed. Tools Appl. 2018, 77, 21947–21965. [Google Scholar] [CrossRef]
- Archana, K.C.; Harini, N. Mitigation of spoofing attacks on IOT home networks. Int. J. Eng. Adv. Technol. 2019, 9, 240–245. [Google Scholar]
- Conti, M.; Dragoni, N.; Lesyk, V. A survey of man in the middle attacks. IEEE Commun. Surv. Tutor. 2016, 18, 2027–2051. [Google Scholar] [CrossRef]
- Feng, Y.; Wang, W.; Weng, Y.; Zhang, H. A replay-attack resistant authentication scheme for the internet of things. In Proceedings of the 2017 IEEE International Conference on Computational Science and Engineering (CSE) and IEEE International Conference on Embedded and Ubiquitous Computing (EUC), Guangzhou, China, 21–24 July 2017. [Google Scholar]
- Azrour, M.; Farhaoui, Y.; Ouanan, M. Cryptanalysis of Farash et al.’s SIP authentication protocol. Int. J. Dyn. Syst. Differ. Equ. 2018, 8, 77. [Google Scholar] [CrossRef]
- Ryu, J.; Lee, H.; Kim, H.; Won, D. Secure and Efficient Three-Factor Protocol for Wireless Sensor Networks. Sensors 2018, 18, 4481. [Google Scholar] [CrossRef]
- Mishra, N.; Pandya, S. Internet of things applications, security challenges, attacks, intrusion detection, and future visions: A systematic review. IEEE Access 2021, 9, 59353–59377. [Google Scholar] [CrossRef]
- Ghasemi, J.; Esmaily, J.; Moradinezhad, R. Intrusion detection system using an optimized kernel extreme learning machine and efficient features. Sadhana 2020, 45, 1–9. [Google Scholar] [CrossRef]
- Ibrahim, W.N.H.; Anuar, S.; Selamat, A.; Krejcar, O.; Gonzalez Crespo, R.; Herrera-Viedma, E.; Fujita, H. Multilayer framework for botnet detection using machine learning algorithms. IEEE Access 2021, 9, 48753–48768. [Google Scholar] [CrossRef]
- Wang, W.; Fang, B.; Zhang, Z.; Li, C. A novel approach to detect IRC-based botnets. In Proceedings of the 2009 International Conference on Networks Security, Wireless Communications and Trusted Computing, Wuhan, China, 25–26 April 2009. [Google Scholar]
- Zhao, D.; Traore, I.; Sayed, B.; Lu, W.; Saad, S.; Ghorbani, A.; Garant, D. Botnet detection based on traffic behavior analysis and flow intervals. Comput. Secur. 2013, 39, 2–16. [Google Scholar] [CrossRef]
- Moura, G.; Sadre, R.; Pras, A. Bad neighborhoods on the internet. IEEE Commun. Mag. 2014, 52, 132–139. [Google Scholar] [CrossRef]
- Wang, H.; Jia, Q.; Fleck, D.; Powell, W.; Li, F.; Stavrou, A. A moving target DDoS defense mechanism. Comput. Commun. 2014, 46, 10–21. [Google Scholar] [CrossRef]
- Yang, D.; Zhu, T.; Wang, S.; Wang, S.; Xiong, Z. LFRSNet: A robust light field semantic segmentation network combining contextual and geometric features. Front. Environ. Sci. 2022, 10, 1443. [Google Scholar] [CrossRef]
- Gayathri, R.; Vincent, R.; Rajesh, M.; Kumar Sivaraman, A.; Muralidhar, A. Web-acl based dos mitigation solution for cloud. Adv. Math. Sci. J. 2020, 9, 5105–5113. [Google Scholar] [CrossRef]
- Rajakumaran, G.; Venkataraman, N. Identification of regression function and distribution model for denial of service attack in Second Life online community using simple network management protocol. Int. J. Web Based Communities 2019, 15, 225. [Google Scholar]
- Rajakumaran, G.; Venkataraman, N.; Mukkamala, R.R. Denial of service attack prediction using gradient descent algorithm. SN Comput. Sci. 2020, 1, 1–8. [Google Scholar] [CrossRef]
- Rajakumaran, G.; Venkataraman, N. Performance assessment of hybrid MTD for DoS mitigation in public cloud. Int. J. Intell. Netw. 2021, 2, 140–147. [Google Scholar] [CrossRef]
- Yu, S.; Zhou, W. Entropy-based collaborative detection of DDOS attacks on community networks. In Proceedings of the 2008 Sixth Annual IEEE International Conference on Pervasive Computing and Communications (PerCom), Hong Kong, China, 17–21 March 2008. [Google Scholar]
- Yu, S.; Zhou, W.; Doss, R.; Jia, W. Traceback of DDoS attacks using entropy variations. IEEE Trans. Parallel Distrib. Syst. 2011, 22, 412–425. [Google Scholar] [CrossRef]
- Xiang, Y.; Li, K.; Zhou, W. Low-rate DDoS attacks detection and traceback by using new information metrics. IEEE Trans. Inf. Forensics Secur. 2011, 6, 426–437. [Google Scholar] [CrossRef]
- Zhou, Y.; Cheng, G.; Jiang, S.; Zhao, Y.; Chen, Z. Cost-effective moving target defense against DDoS attacks using trilateral game and multi-objective Markov decision processes. Comput. Secur. 2020, 97, 101976. [Google Scholar] [CrossRef]
| Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).