Detection of False Data Injection Attacks in Smart Grids Based on Expectation Maximization
Abstract
:1. Introduction
- Since the error models of both measurement vectors and state variables with false data have the characteristics of the Gaussian mixture model (GMM), a false data injection attack detection method based on the k-means++ and expectation maximization (EM) algorithms is proposed.
- To address the fact that the k-means algorithm is sensitive to the initial clustering centers and affects the convergence efficiency, the k-means++ algorithm is proposed to determine the initial estimated parameters of the GMM in a faster iterative approach.
- The k-means++ algorithm is used to preprocess the data to solve the problem of EM algorithm being sensitive to initial values. It also decreases the calculation complexity of the EM algorithm, and finally detects and locates false data rapidly according to the classification results.
2. System Model
3. Attack Detection
3.1. Maximum Likelihood Estimation
3.2. K-Means++ Algorithm
3.3. EM Algorithm
4. Algorithm Implementation
| Algorithm 1 Joint k-means++ and EM algorithms for estimating parameters of GMM. | |
| Input: and . For each dataset with , . Initialize: Iteration index n = 0 for k-means++ algorithm; the EM algorithm’s iteration index = 0; convergence tolerance is ; and maximum iteration number is . K-means++ algorithm loop: (1) A sample point is randomly selected as the initial cluster center , and then the second cluster center is selected according to the roulette wheel selection. (2) Update according to Equation (15), and then reclassify the sample points. (3) Update Cluster Center according to Equation (16). (4) If the convergence condition is satisfied, the k-means++ algorithm is terminated. Otherwise, set and return to (2). Get the initial estimation parameters: (1) . (2) . (3) . EM algorithm loop: (1) Update according to Equation (18). (2) Parameters , , are updated according to Equations (25)–(27). (3) If the convergence condition or is satisfied, the EM algorithm is terminated. Otherwise, set and return to (1). Output: and . | |
5. Algorithm Analysis
5.1. Convergence Analysis
5.2. Complexity Analysis
- (1)
- : FLOPs required for addition.
- (2)
- : FLOPs required for subtraction.
- (3)
- : FLOPs required for multiplication.
- (4)
- : FLOPs required for division.
- (5)
- : FLOPs required for exponential.
- (6)
- : FLOPs required for square.
- (7)
- : FLOPs required for square root.
- (8)
- : FLOPs required for comparation.
- (9)
- : FLOPs required for assignment.
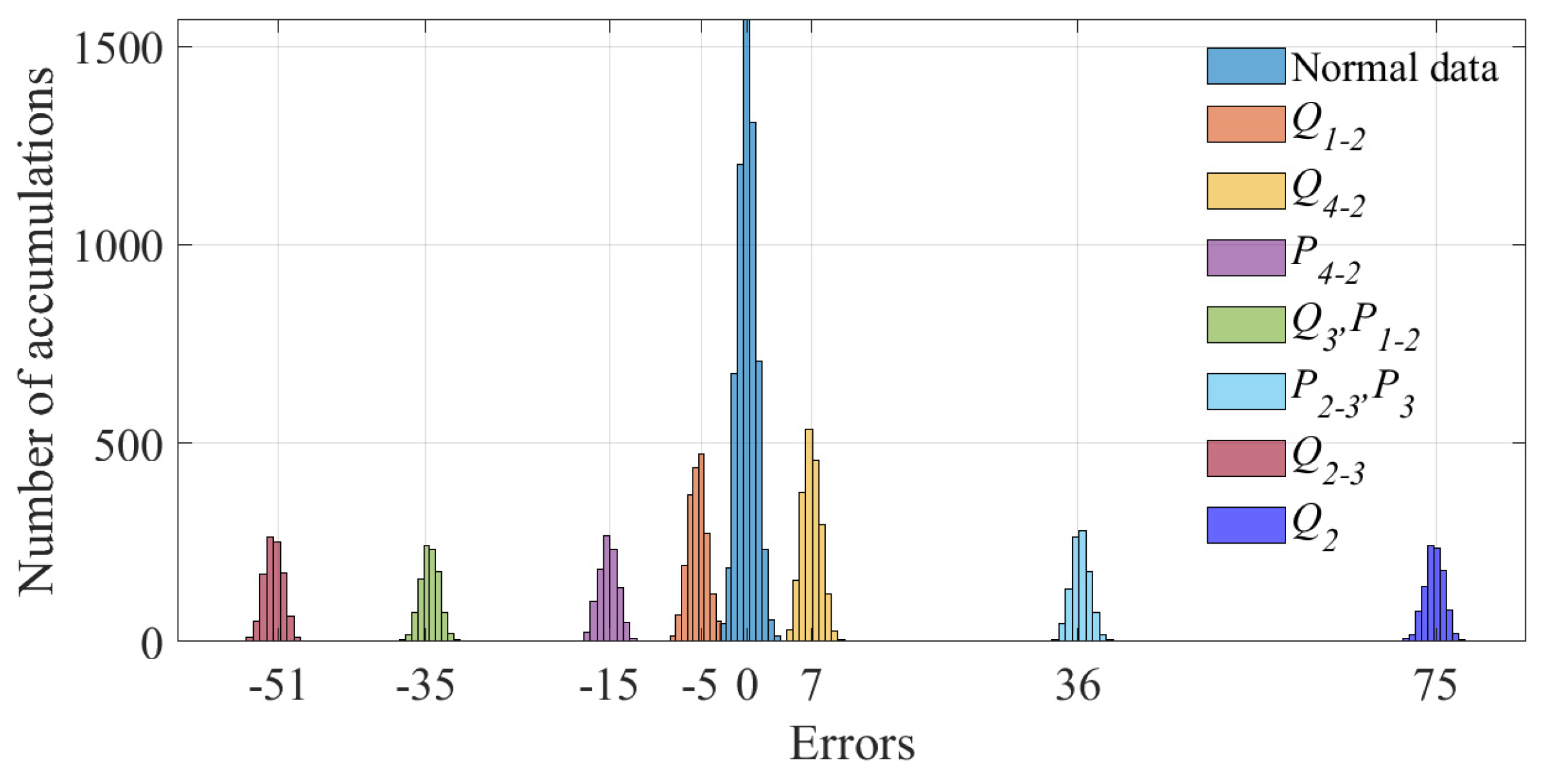
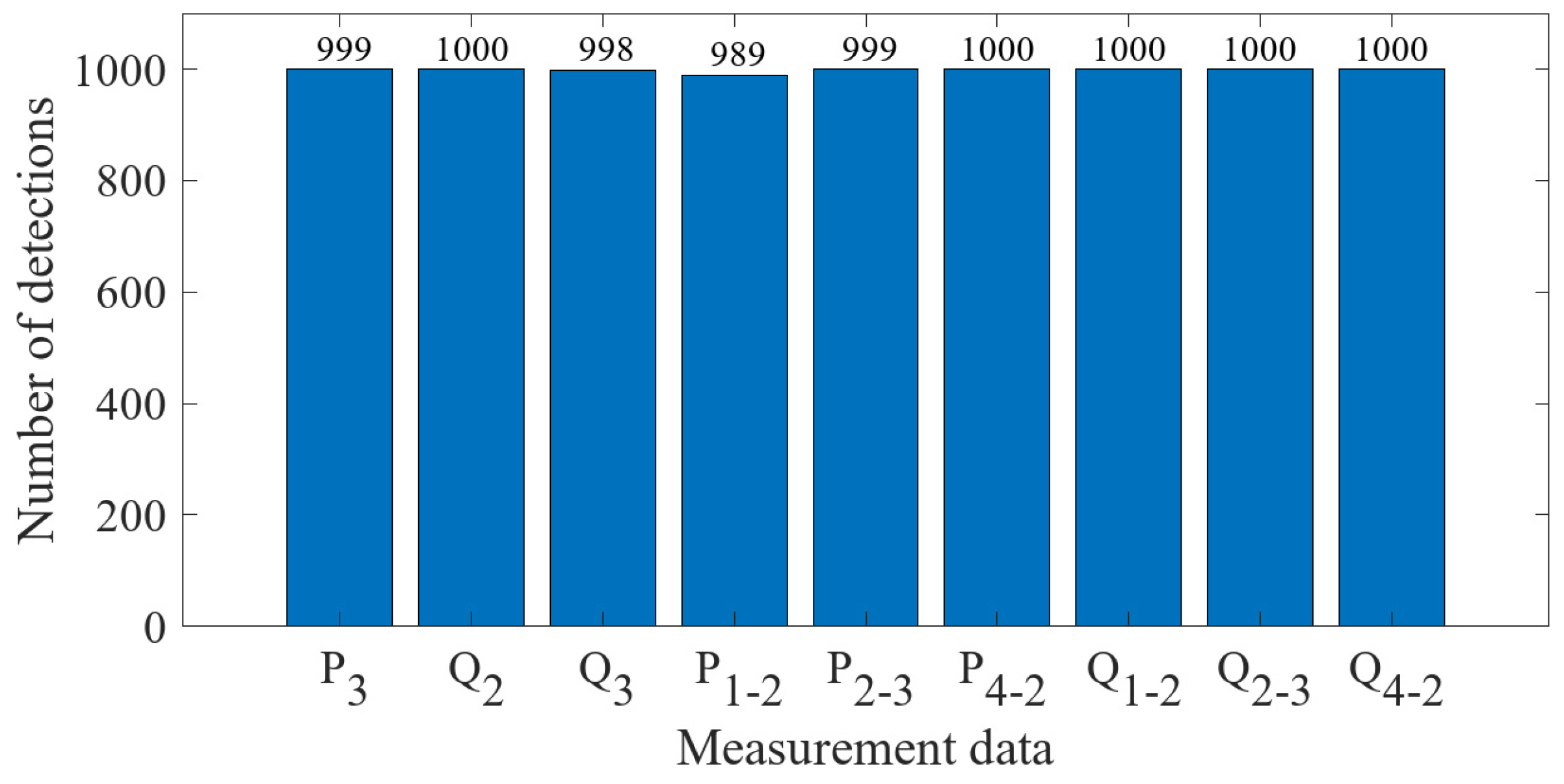
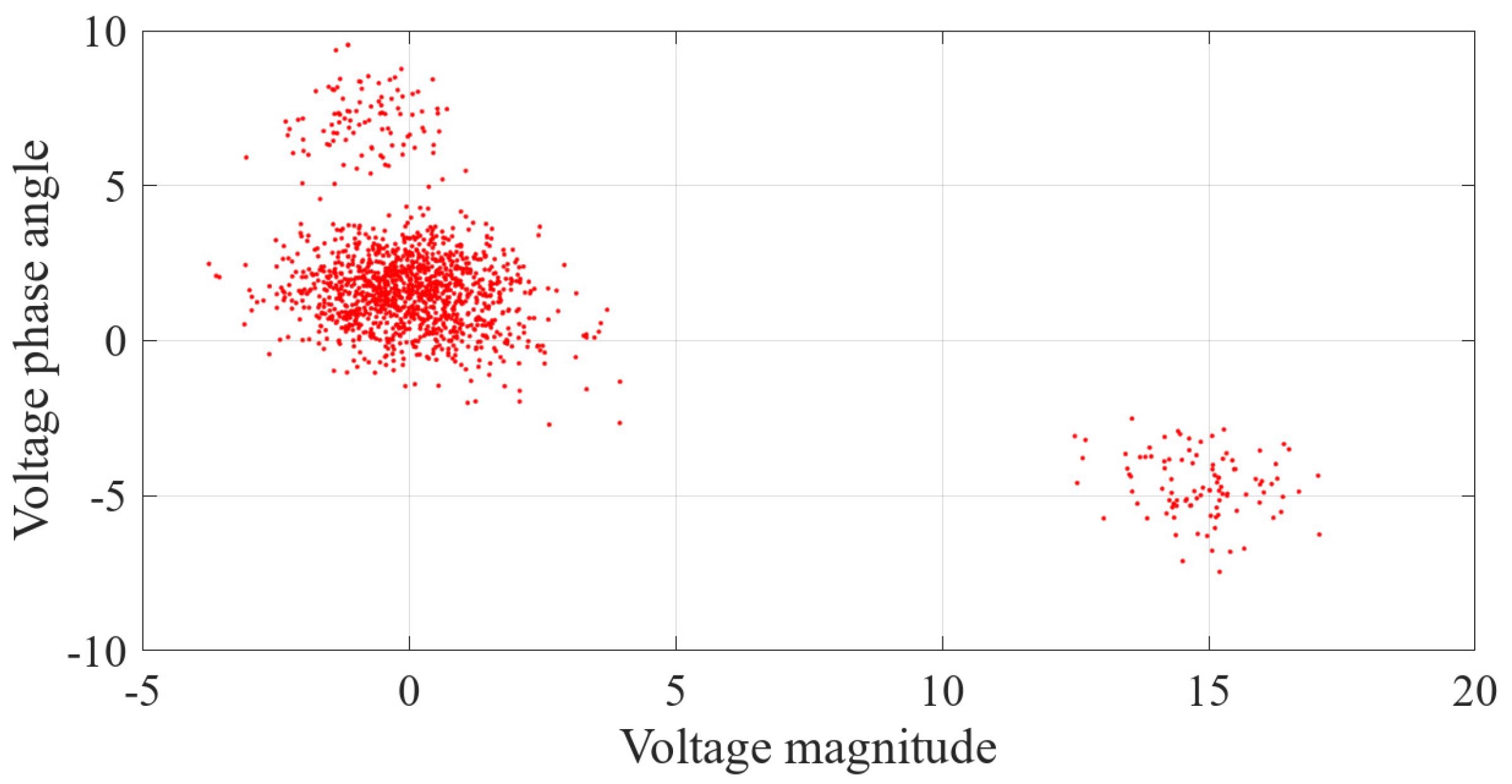
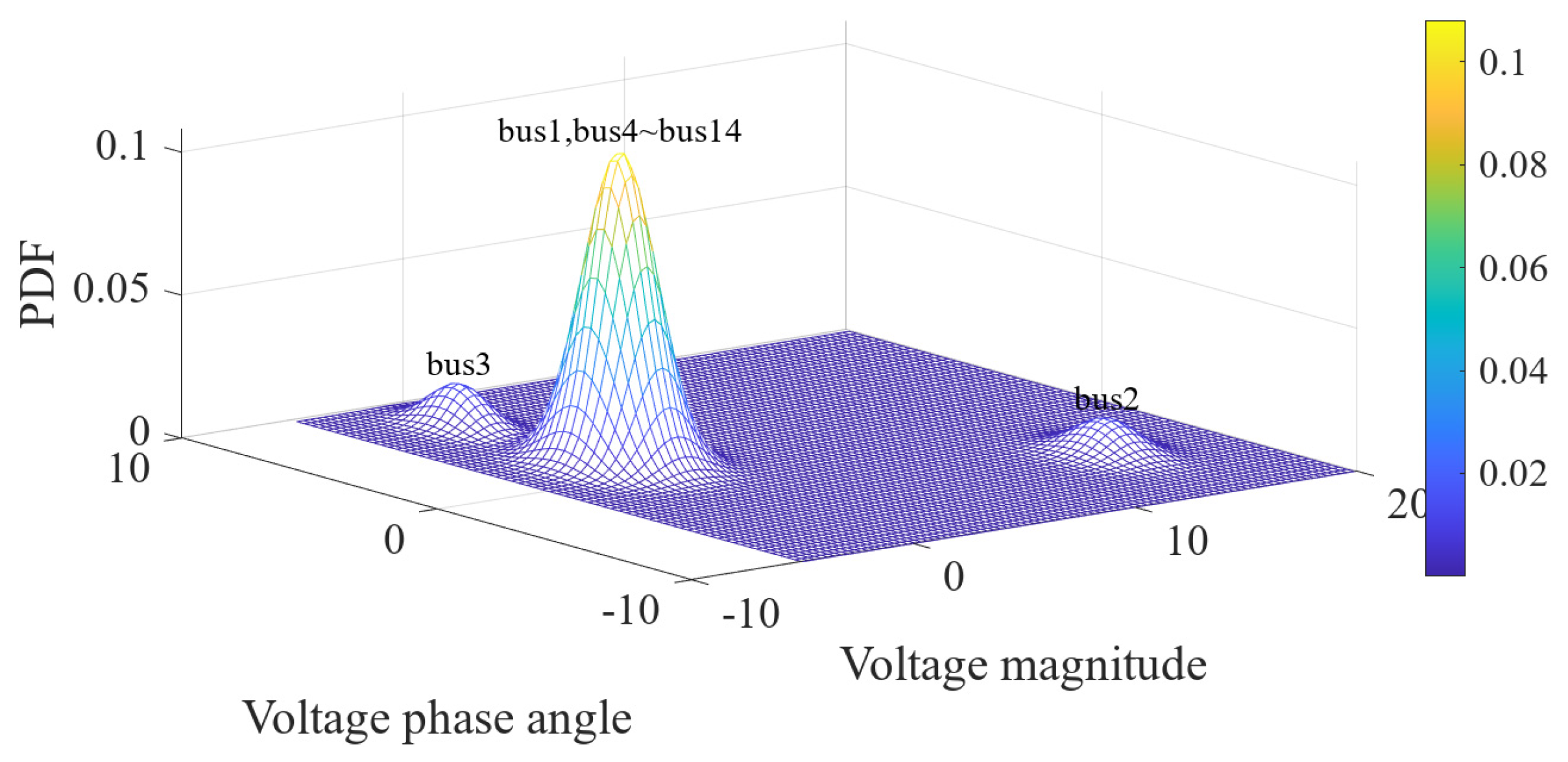
6. Simulation Analysis
6.1. Simulation Parameters
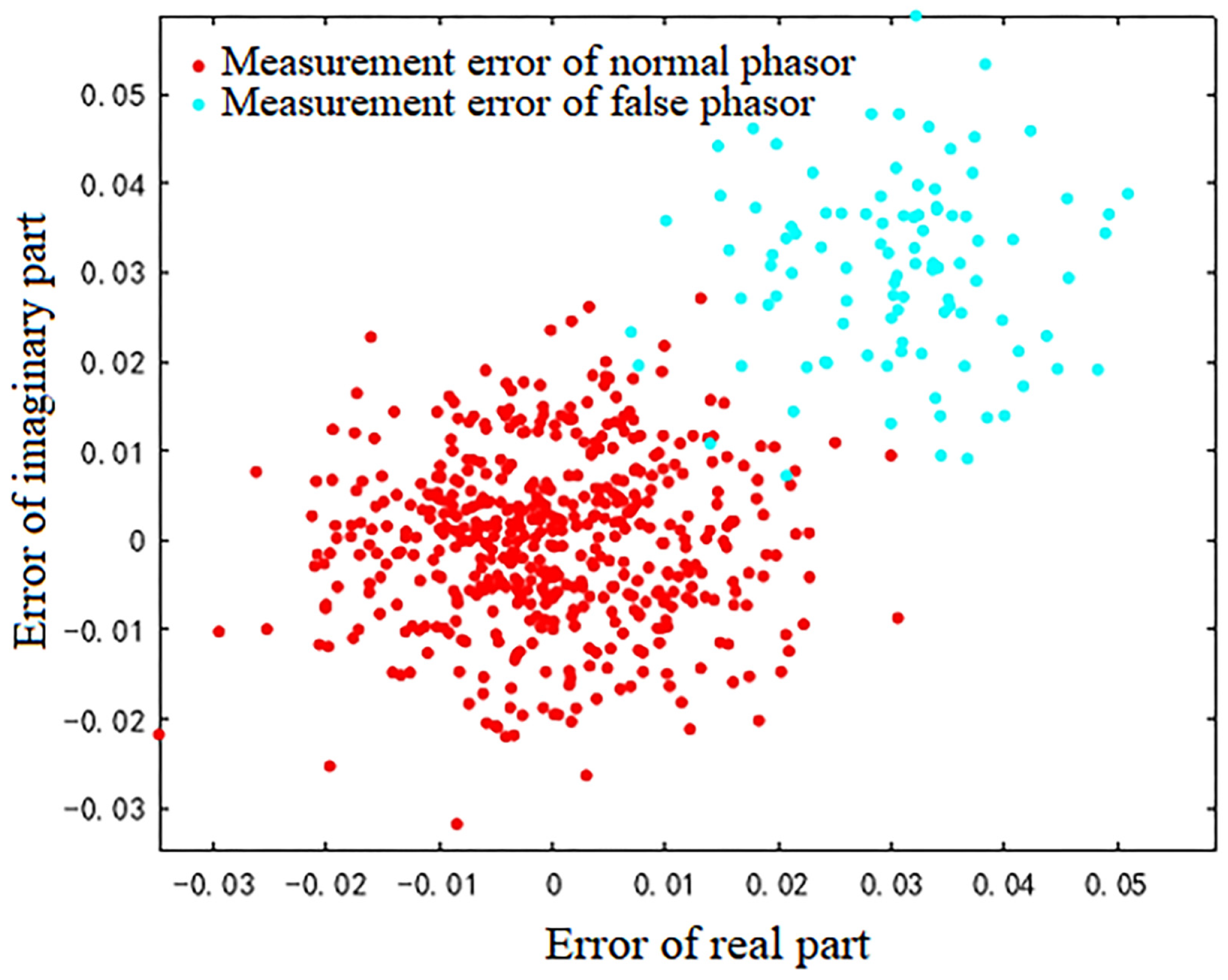
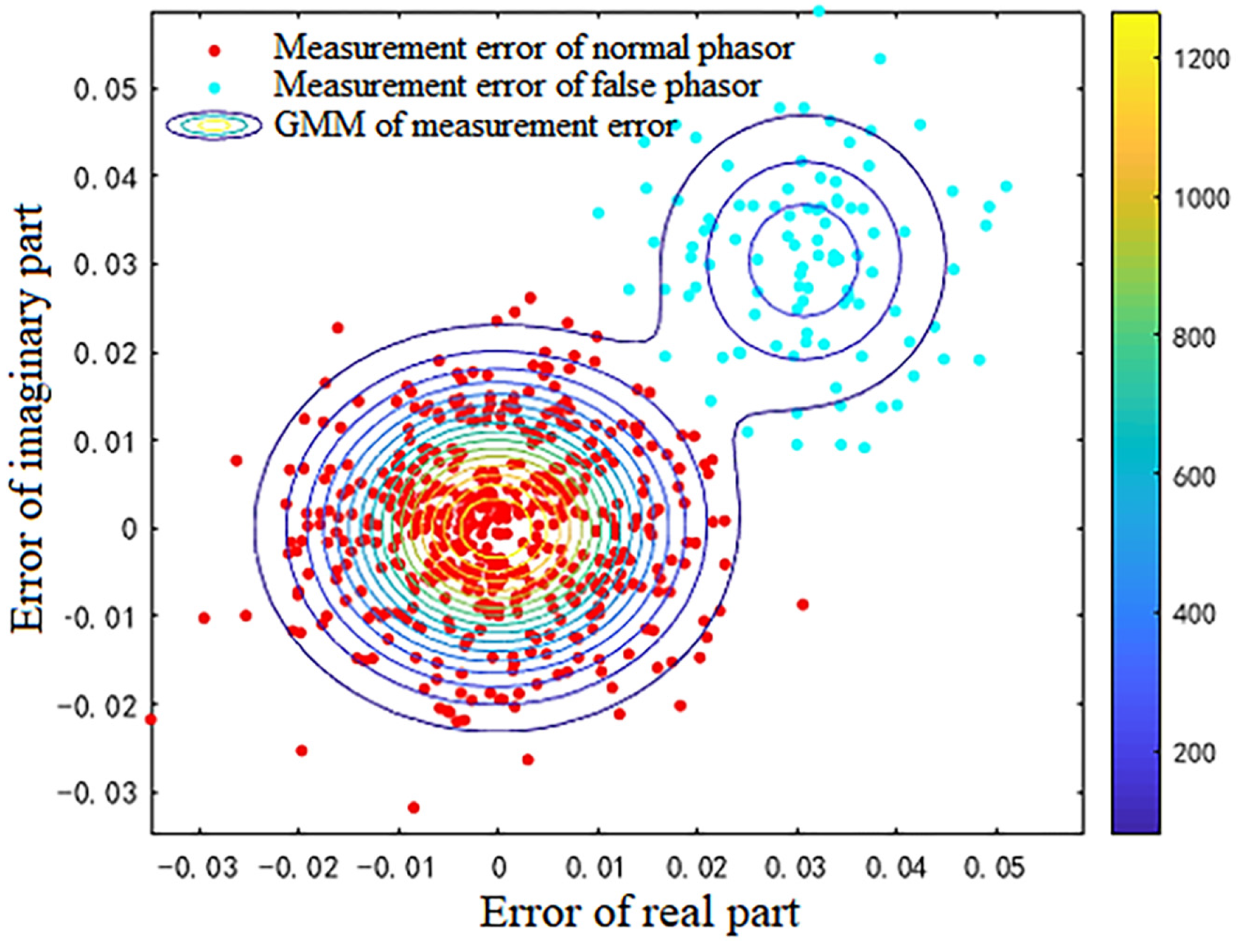
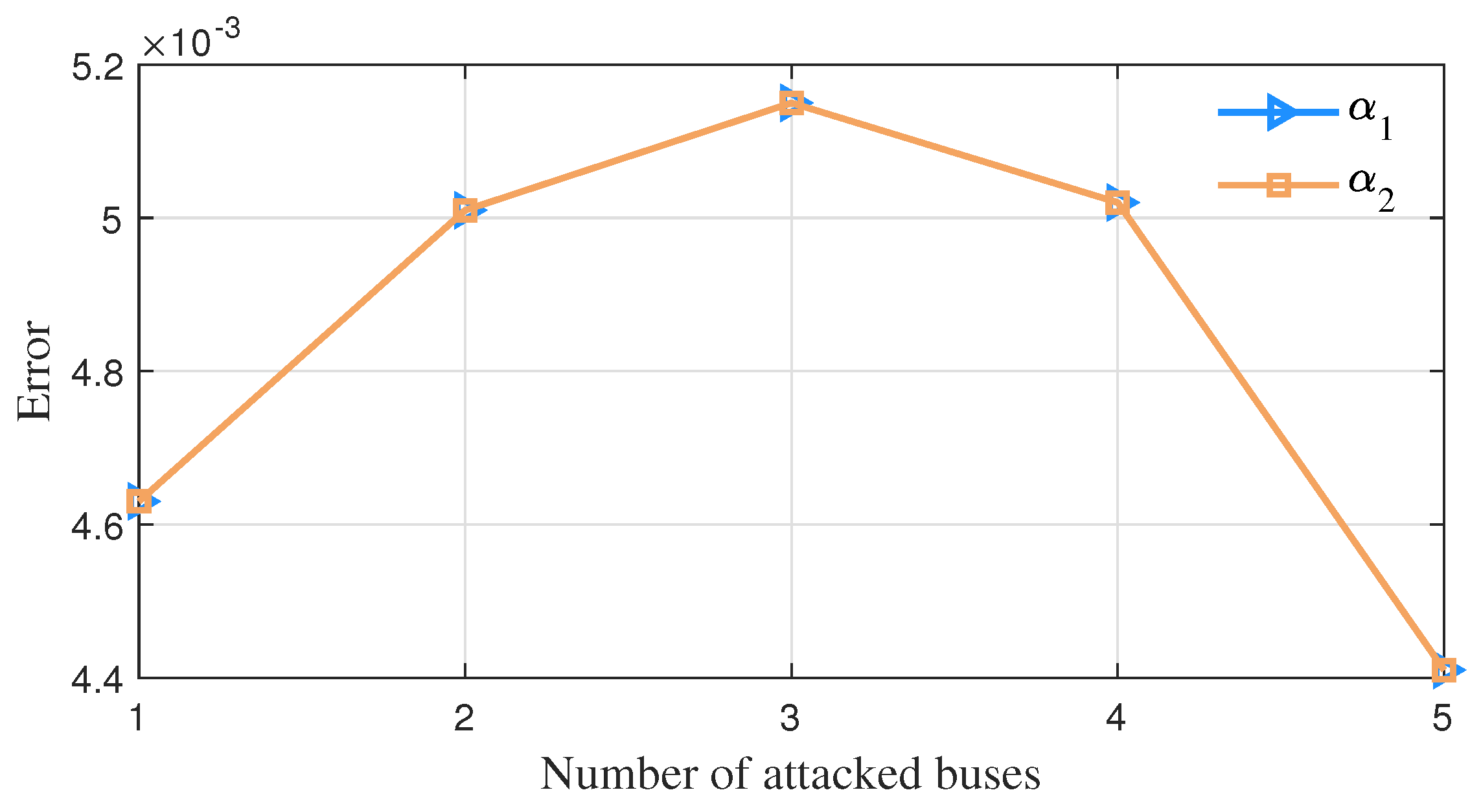
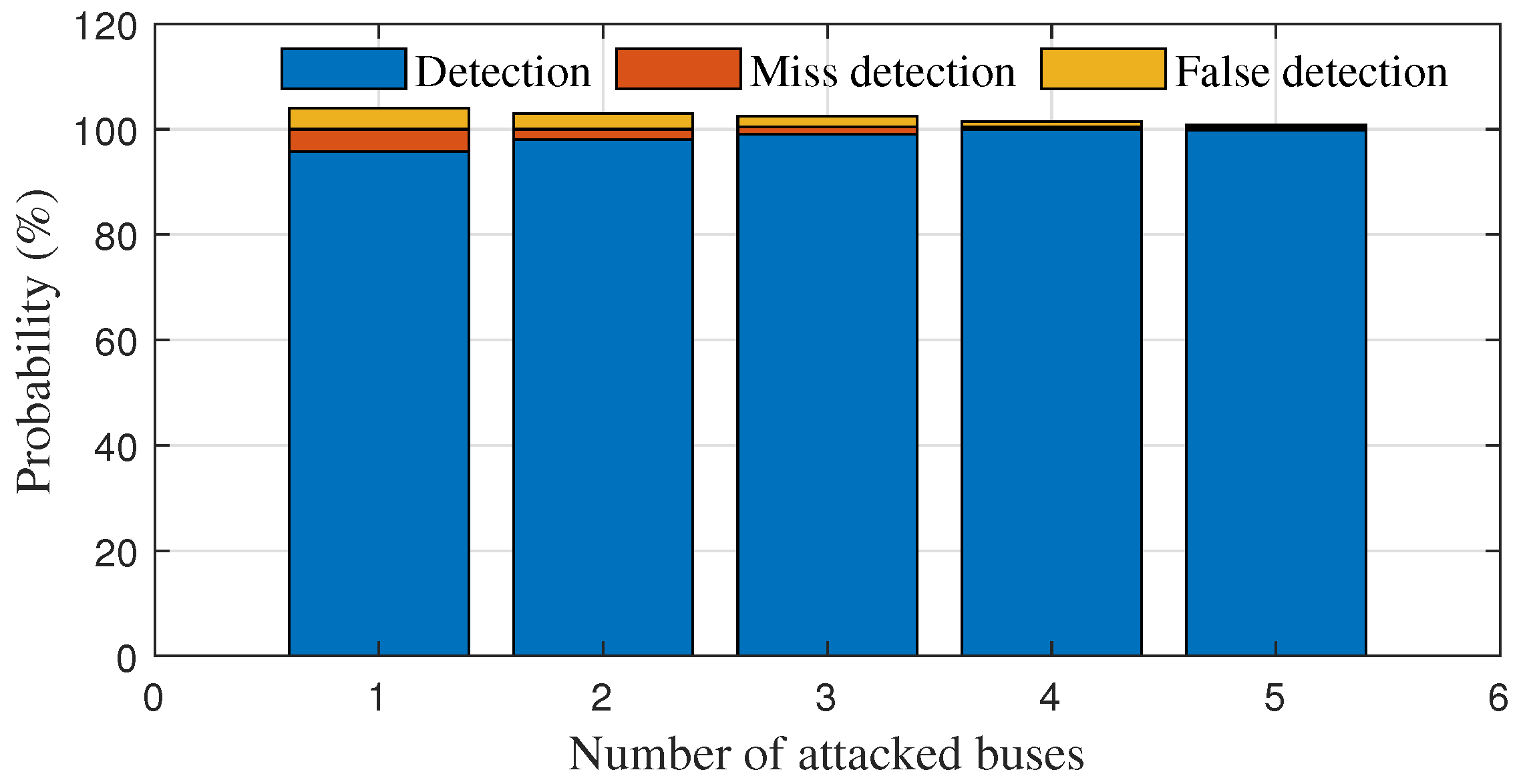
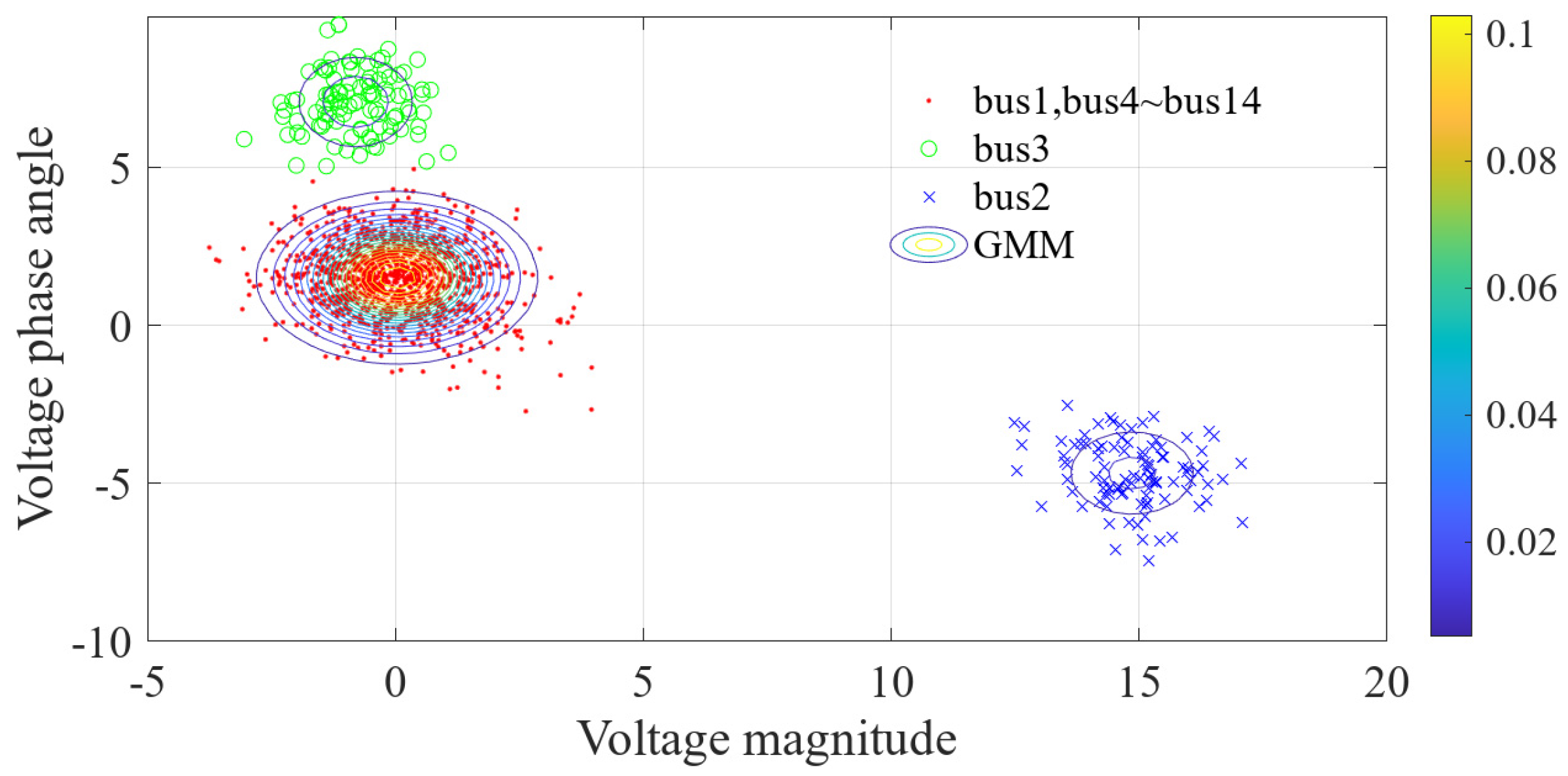
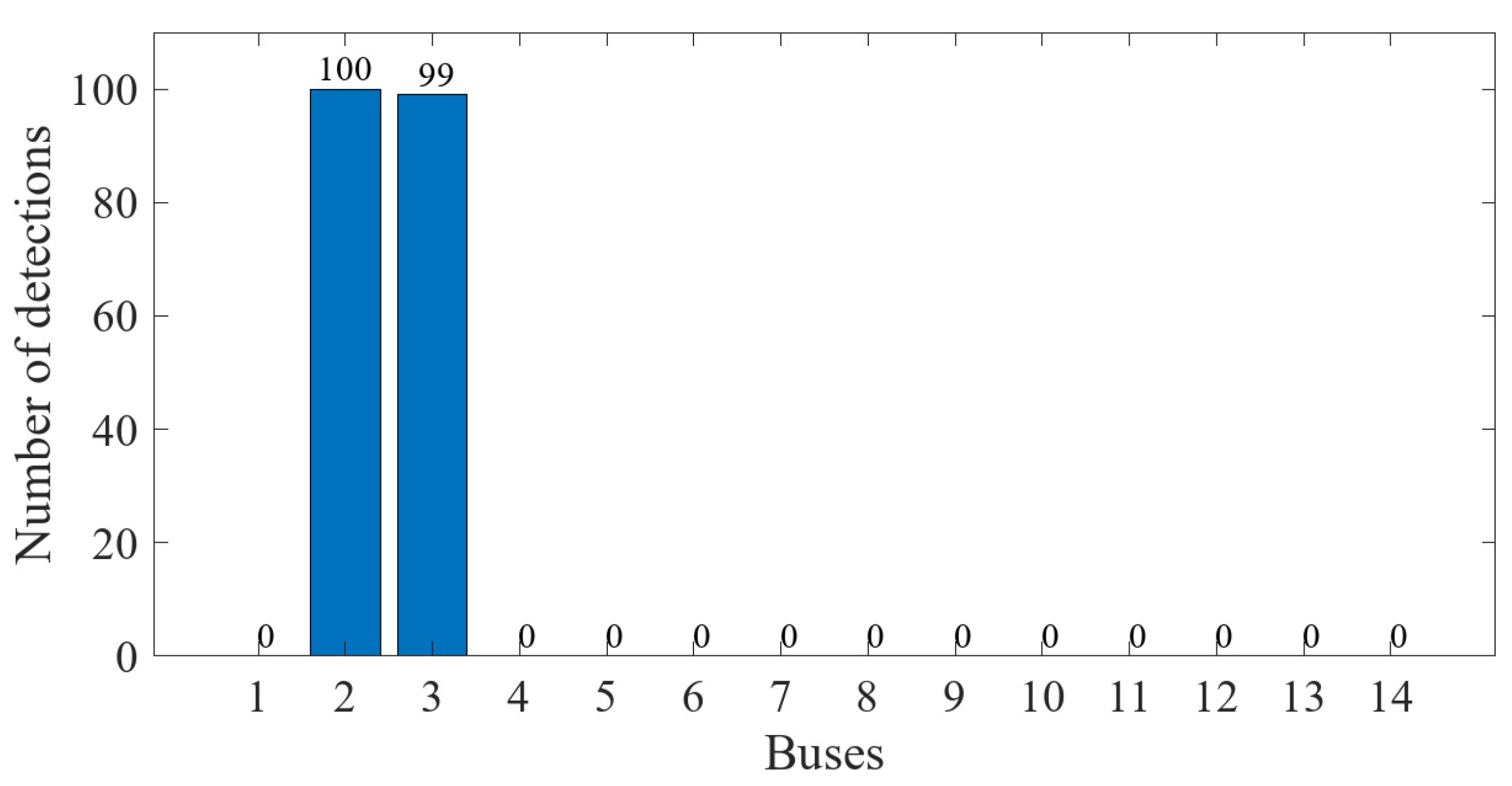
6.2. Simulation Results
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Abur, A.; Exposito, A.G. Power System State Estimation: Theory and Implementation; CRC Press: Boca Raton, FL, USA, 2004. [Google Scholar]
- Monticelli, A.; Wu, F.F.; Yen, M. Mutiple bad data identwication for state estimation by combinatorial oftimization. IEEE Trans. Power Deliv. 1986, 1, 361–369. [Google Scholar] [CrossRef]
- Granelli, G.P.; Montagna, M. Identification of interacting bad data in the framework of the weighted least square method. Electr. Power Syst. Res. 2008, 78, 806–814. [Google Scholar] [CrossRef]
- Harvey, M.; Long, D.; Reinhard, K. Visualizing nistir 7628, guidelines for smart grid cyber security. In Proceedings of the 2014 Power and Energy Conference at Illinois (PECI), Champaign, IL, USA, 28 February–1 March 2014; pp. 1–8. [Google Scholar] [CrossRef]
- Zanero, S. When cyber got real: Challenges in securing cyber-physical systems. In Proceedings of the 2018 IEEE Sensors, New Delhi, India, 28–31 October 2018; pp. 1–4. [Google Scholar] [CrossRef]
- Ten, C.W.; Liu, C.C.; Manimaran, G. Vulnerability assessment of cybersecurity for SCADA systems. IEEE Trans. Power Syst. 2008, 23, 1836–1846. [Google Scholar] [CrossRef]
- Khurana, H.; Hadley, M.; Lu, N.; Frincke, D.A. Smart-grid security issues. IEEE Secur. Priv. 2010, 8, 81–85. [Google Scholar] [CrossRef]
- Mo, Y.; Kim, H.J.; Brancik, K.; Dickinson, D.; Lee, H.; Perrig, A.; Sinopoli, B. Cyber–physical security of a smart grid infrastructure. Proc. IEEE 2012, 100, 195–209. [Google Scholar] [CrossRef]
- Teixeira, A.; Amin, S.; Sandberg, H.; Johansson, K.H.; Sastry, S.S. Cyber security analysis of state estimators in electric power systems. In Proceedings of the 49th IEEE Conference on Decision and Control (CDC), Atlanta, GA, USA, 15–17 December 2010; pp. 5991–5998. [Google Scholar] [CrossRef]
- Metke, A.R.; Ekl, R.L. Smart grid security technology. In Proceedings of the 2010 Innovative Smart Grid Technologies (ISGT), Gaithersburg, MD, USA, 19–21 January 2010; pp. 1–7. [Google Scholar] [CrossRef]
- Liu, Y.; Reiter, M.K.; Ning, P. False data injection attacks against state estimation in electric power grids. In Proceedings of the 2009 ACM Conference on Computer and Communications Security (CCS), Chicago, IL, USA, 9–13 November 2009; pp. 1–33. [Google Scholar]
- Xie, B.; Peng, C.; Zhang, H.; Yang, M. Power system state estimation based on network attack node credibility. Chin. J. Sci. Instrum. 2018, 39, 157–166. [Google Scholar] [CrossRef]
- Ahmadi, N.; Chakhchoukh, Y.; Ishii, H. Power systems decomposition for robustifying state estimation under cyber attacks. IEEE Trans. Power Syst. 2021, 36, 1922–1933. [Google Scholar] [CrossRef]
- Jia, L.; Thomas, R.J.; Tong, L. Impacts of malicious data on real-time price of electricity market operations. In Proceedings of the Hawaii International Conference on System Sciences, Maui, HI, USA, 4–7 January 2012; pp. 1907–1914. [Google Scholar] [CrossRef]
- Xie, L.; Mo, Y.; Sinopoli, B. Integrity data attacks in power market operations. IEEE Trans. Smart Grid 2011, 2, 659–666. [Google Scholar] [CrossRef]
- Choi, D.H.; Xie, L. Malicious ramp-induced temporal data attack in power market with look-ahead dispatch. In Proceedings of the 2012 IEEE Third International Conference on Smart Grid Communications (SmartGridComm), Tainan, Taiwan, 5–8 November 2012; pp. 330–335. [Google Scholar] [CrossRef]
- Yuan, Y.; Li, Z.; Ren, K. Modeling load redistribution attacks in power systems. IEEE Trans. Smart Grid 2011, 2, 382–390. [Google Scholar] [CrossRef]
- Du, M.; Pierrou, G.; Wang, X.; Kassouf, M. Targeted false data injection attacks against AC state estimation without network parameters. IEEE Trans. Smart Grid 2021, 12, 5349–5361. [Google Scholar] [CrossRef]
- Liu, C.; Liang, H.; Chen, T. Network parameter coordinated false data injection attacks against power system AC state estimation. IEEE Trans. Smart Grid 2021, 12, 1626–1639. [Google Scholar] [CrossRef]
- Liu, C.; He, W.; Deng, R.; Tian, Y.C.; Du, W. False data injection enabled network parameter modifications in power systems: Attack and detection. IEEE Trans. Ind. Inform. 2022, 19, 177–188. [Google Scholar] [CrossRef]
- Molzahn, D.K.; Wang, J. Detection and characterization of intrusions to network parameter data in electric power systems. IEEE Trans. Smart Grid 2019, 10, 3919–3928. [Google Scholar] [CrossRef]
- Chaojun, G.; Jirutitijaroen, P.; Motani, M. Detecting false data injection attacks in AC state estimation. IEEE Trans. Smart Grid 2015, 6, 2476–2483. [Google Scholar] [CrossRef]
- Singh, S.K.; Khanna, K.; Bose, R.; Panigrahi, B.K.; Joshi, A. Joint-transformation-based detection of false data injection attacks in smart grid. IEEE Trans. Ind. Inform. 2018, 14, 89–97. [Google Scholar] [CrossRef]
- Li, B.; Ding, T.; Huang, C.; Zhao, J.; Yang, Y.; Chen, Y. Detecting false data injection attacks against power system state estimation with fast go-decomposition approach. IEEE Trans. Ind. Inform. 2019, 15, 2892–2904. [Google Scholar] [CrossRef]
- Cheng, G.; Lin, Y.; Zhao, J.; Yan, J. A highly discriminative detector against false data injection attacks in AC state estimation. IEEE Trans. Smart Grid 2022, 13, 2318–2330. [Google Scholar] [CrossRef]
- Chen, Y.; Hayawi, K.; Zhao, Q.; Mou, J.; Yang, L.; Tang, J.; Li, Q.; Wen, H. Vector auto-regression-based false data injection attack detection method in edge computing environment. Sensors 2022, 22, 6789. [Google Scholar] [CrossRef]
- Almasabi, S.; Alsuwian, T.; Javed, E.; Irfan, M.; Jalalah, M.; Aljafari, B.; Harraz, F.A. A novel technique to detect false data injection attacks on phasor measurement units. Sensors 2021, 21, 5791. [Google Scholar] [CrossRef]
- Yu, J.Q.; Hou, Y.; Li, V. Online False Data Injection Attack Detection with Wavelet Transform and Deep Neural Networks. IEEE Trans. Ind. Inform. 2018, 14, 3271–3280. [Google Scholar] [CrossRef]
- Xue, D.; Jing, X.; Liu, H. Detection of False Data Injection Attacks in Smart Grid Utilizing ELM-Based OCON Framework. IEEE Access 2019, 7, 31762–31773. [Google Scholar] [CrossRef]
- Almasabi, S.; Alsuwian, T.; Awais, M.; Irfan, M.; Jalalah, M.; Aljafari, B.; Harraz, F.A. False Data Injection Detection for Phasor Measurement Units. Sensors 2022, 22, 3146. [Google Scholar] [CrossRef] [PubMed]
- An, P.; Wang, Z.; Zhang, C. Ensemble unsupervised autoencoders and Gaussian mixture model for cyberattack detection. Inf. Process. Manag. Libr. Inf. Retr. Syst. Commun. Netw. Int. J. 2022, 59, 102844. [Google Scholar] [CrossRef]
- Sheng, T.; Wu, W.; Sun, H.; Wang, Z.; Sun, Q.; Ma, J. A fully distributed topology identification approach for active distribution network based on multi-agent framework. In Proceedings of the 2018 IEEE Innovative Smart Grid Technologies-Asia (ISGT Asia), Singapore, 22–25 May 2018; pp. 435–440. [Google Scholar] [CrossRef]
- Chen, J.C.; Chung, H.M.; Wen, C.K.; Li, W.T.; Teng, J.H. State estimation in smart distribution system with low-precision measurements. IEEE Access 2017, 5, 22713–22723. [Google Scholar] [CrossRef]
- Jiang, J.; Qian, Y. Defense mechanisms against data injection attacks in smart grid networks. IEEE Commun. Mag. 2017, 55, 76–82. [Google Scholar] [CrossRef]
- Sheng, J.; Liu, D. An improved maximum likelihood approach to image reconstruction using ordered subsets and data subdivisions. IEEE Trans. Nucl. Sci. 2004, 51, 130–135. [Google Scholar] [CrossRef]
- Duan, X.; Sun, G.; Tao, Y. Moving target detection based on genetic k-means algorithm. In Proceedings of the 2011 IEEE 13th International Conference on Communication Technology, Jinan, China, 25–28 September 2011; pp. 819–822. [Google Scholar] [CrossRef]
- Watanabe, M.; Yamaguchi, K. The EM Algorithm and Related Statistical Models; CRC Press: Boca Raton, FL, USA, 2003. [Google Scholar] [CrossRef]
- Boyd, S.; Vandenberghe, L. Convex Optimization; Cambridge University Press: Cambridge, UK, 2004. [Google Scholar]







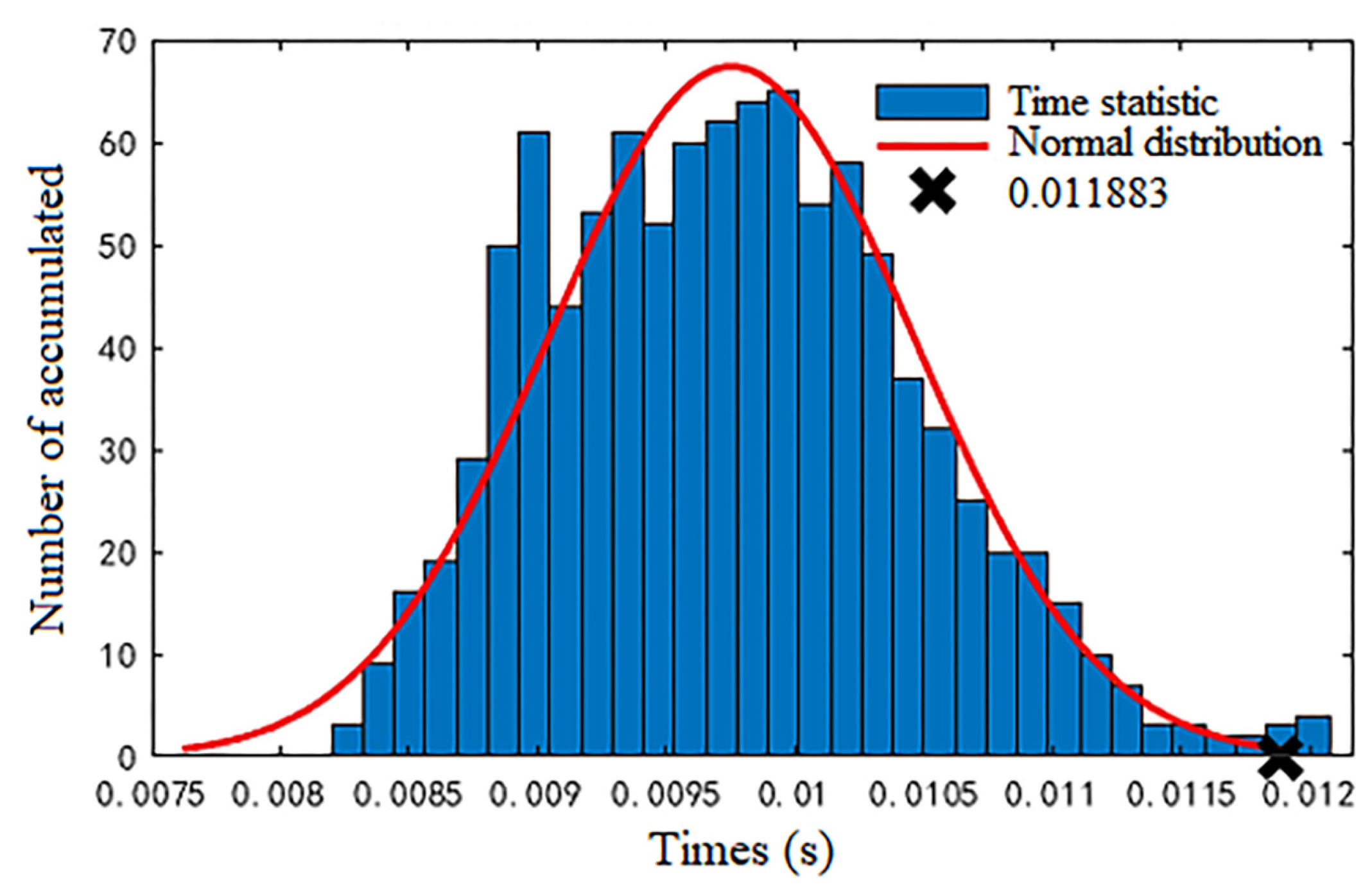
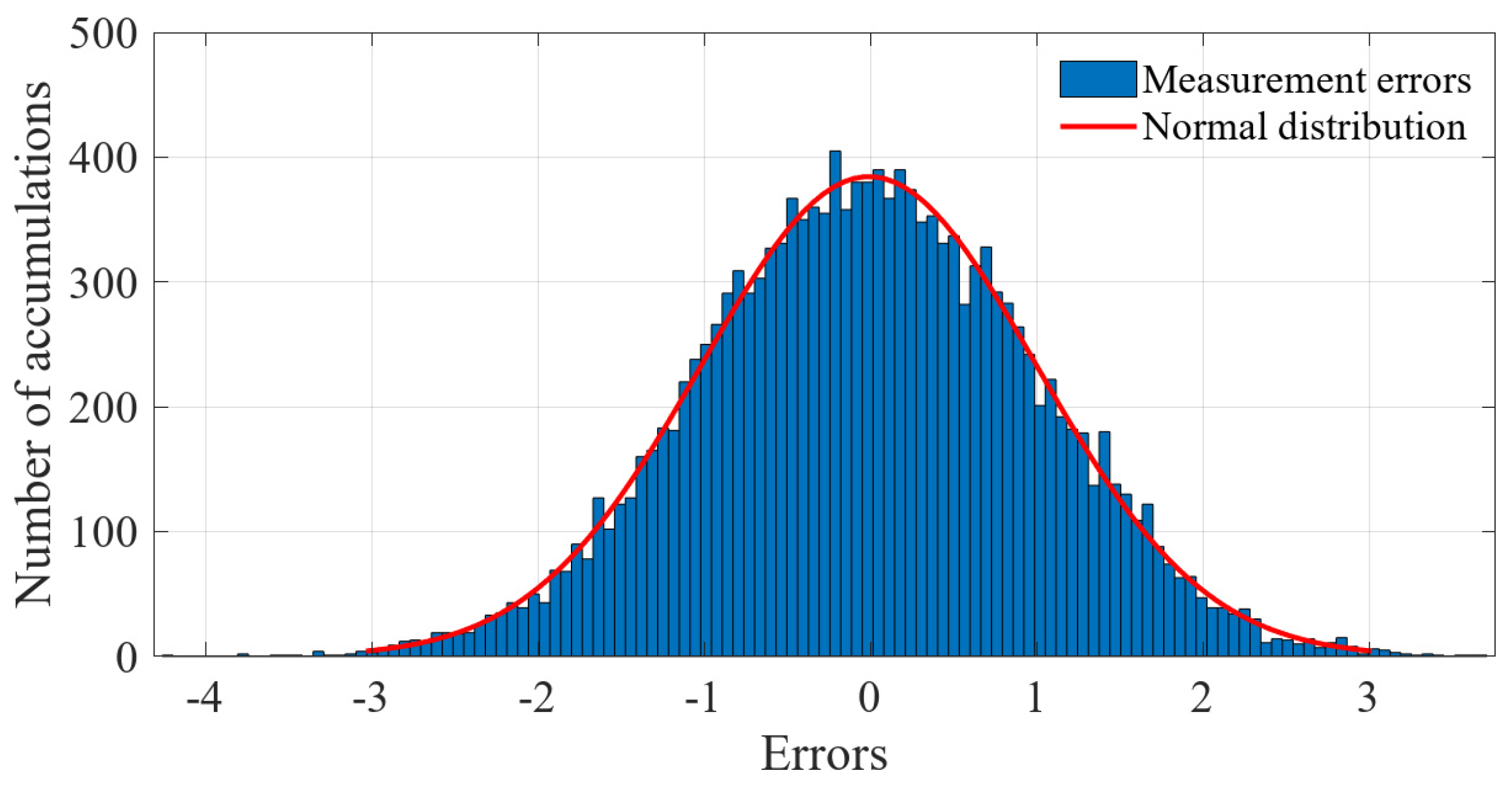

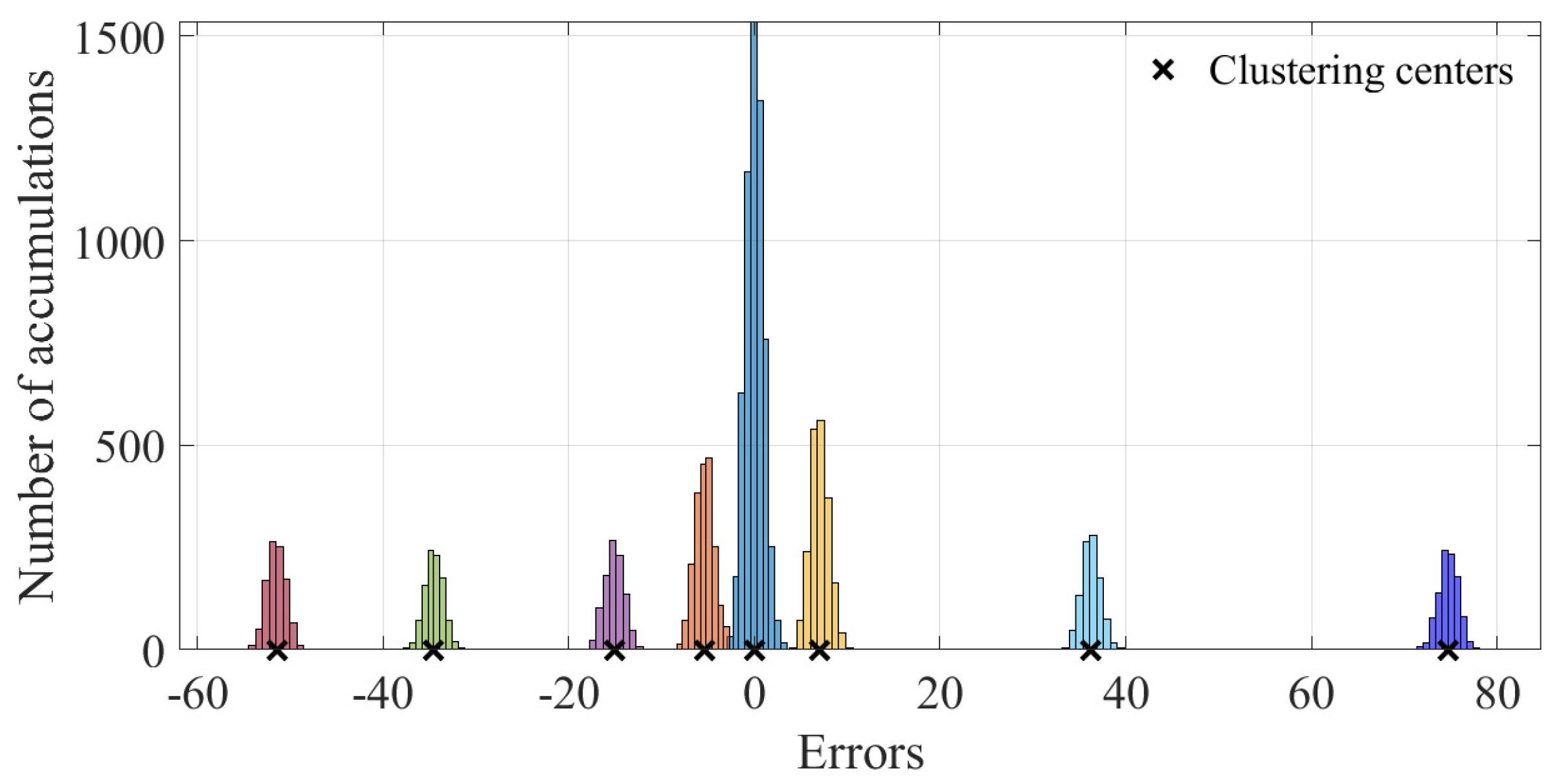
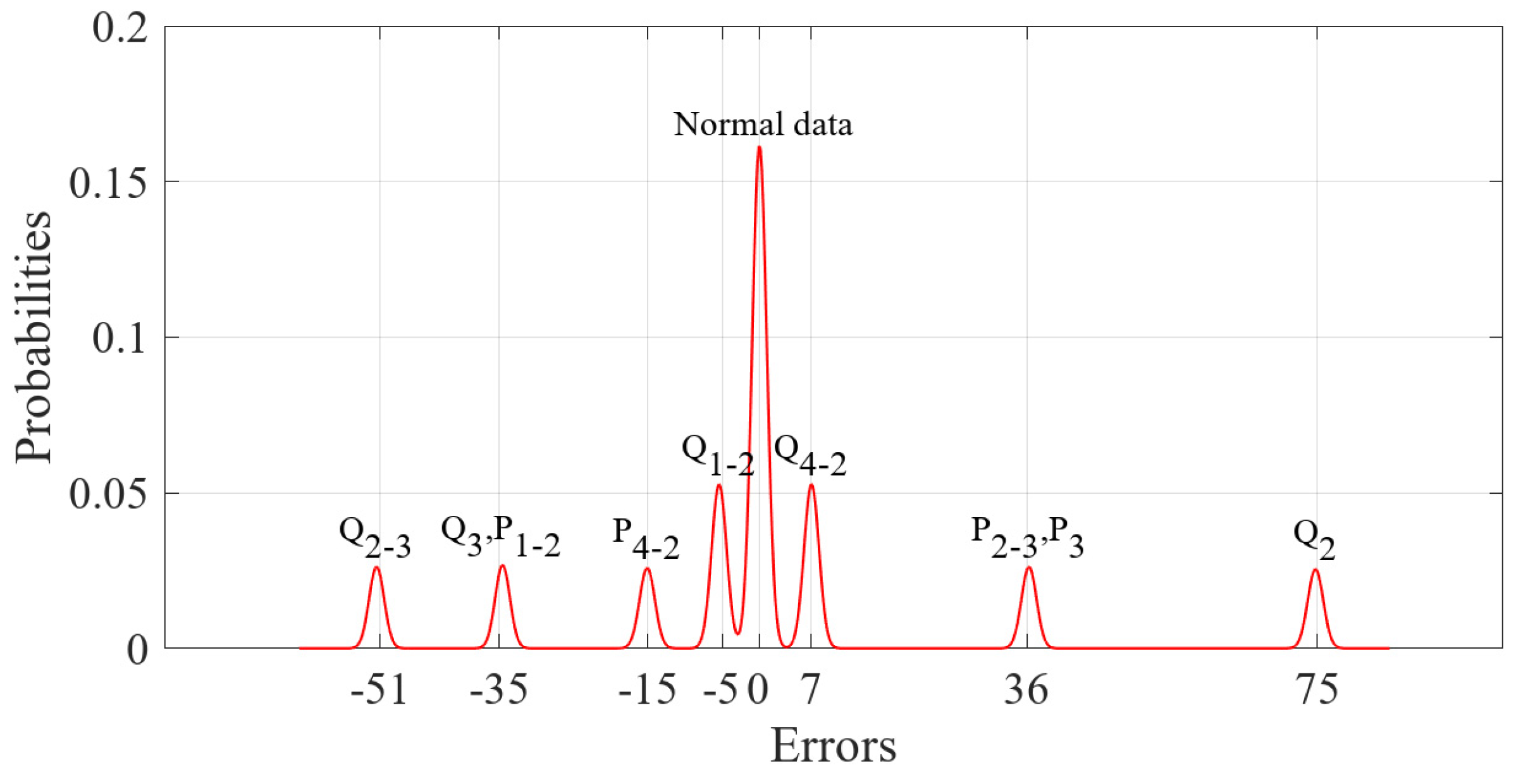

| Raw Data | Simulation Parameters | |
|---|---|---|
| Amplitude/p.u. | 2.5078 | 2.5369 |
| Phase angle/ | −1.8803 | −1.1809 |
| Parameter | Value |
|---|---|
| N | 6 |
| K | 100 |
| [0 0] | |
| [0.03 0.03] | |
| 0.01 | |
| 100 |
| Types of Measurements | Measurement Error before the Attack | Measurement Error after the Attack |
|---|---|---|
| 0.01 | 0.015 | |
| 0.01 | 0.015 | |
| 0.008 | 0.012 | |
| 0.008 | 0.012 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hu, P.; Gao, W.; Li, Y.; Wu, M.; Hua, F.; Qiao, L. Detection of False Data Injection Attacks in Smart Grids Based on Expectation Maximization. Sensors 2023, 23, 1683. https://doi.org/10.3390/s23031683
Hu P, Gao W, Li Y, Wu M, Hua F, Qiao L. Detection of False Data Injection Attacks in Smart Grids Based on Expectation Maximization. Sensors. 2023; 23(3):1683. https://doi.org/10.3390/s23031683
Chicago/Turabian StyleHu, Pengfei, Wengen Gao, Yunfei Li, Minghui Wu, Feng Hua, and Lina Qiao. 2023. "Detection of False Data Injection Attacks in Smart Grids Based on Expectation Maximization" Sensors 23, no. 3: 1683. https://doi.org/10.3390/s23031683
APA StyleHu, P., Gao, W., Li, Y., Wu, M., Hua, F., & Qiao, L. (2023). Detection of False Data Injection Attacks in Smart Grids Based on Expectation Maximization. Sensors, 23(3), 1683. https://doi.org/10.3390/s23031683






