Delayed Response and Random Backoff First for Low-Power Random Access of IoT Devices with Poor Channel Conditions
Abstract
:1. Introduction
- (1)
- In this paper, instead of using separate resources by group, multiple groups use shared resource to efficiently use a random access resource. Using the proposed techniques, even with the shared resource, the collision probability of bad-channel devices can be reduced without increasing the collision probability of other devices.
- (2)
- The proposed methods perform interference cancellation for bad-channel devices, but do not increase the transmission power of other devices. The interference cancellation is performed at the base station and does not sacrifice the transmission power of good-channel devices.
- (3)
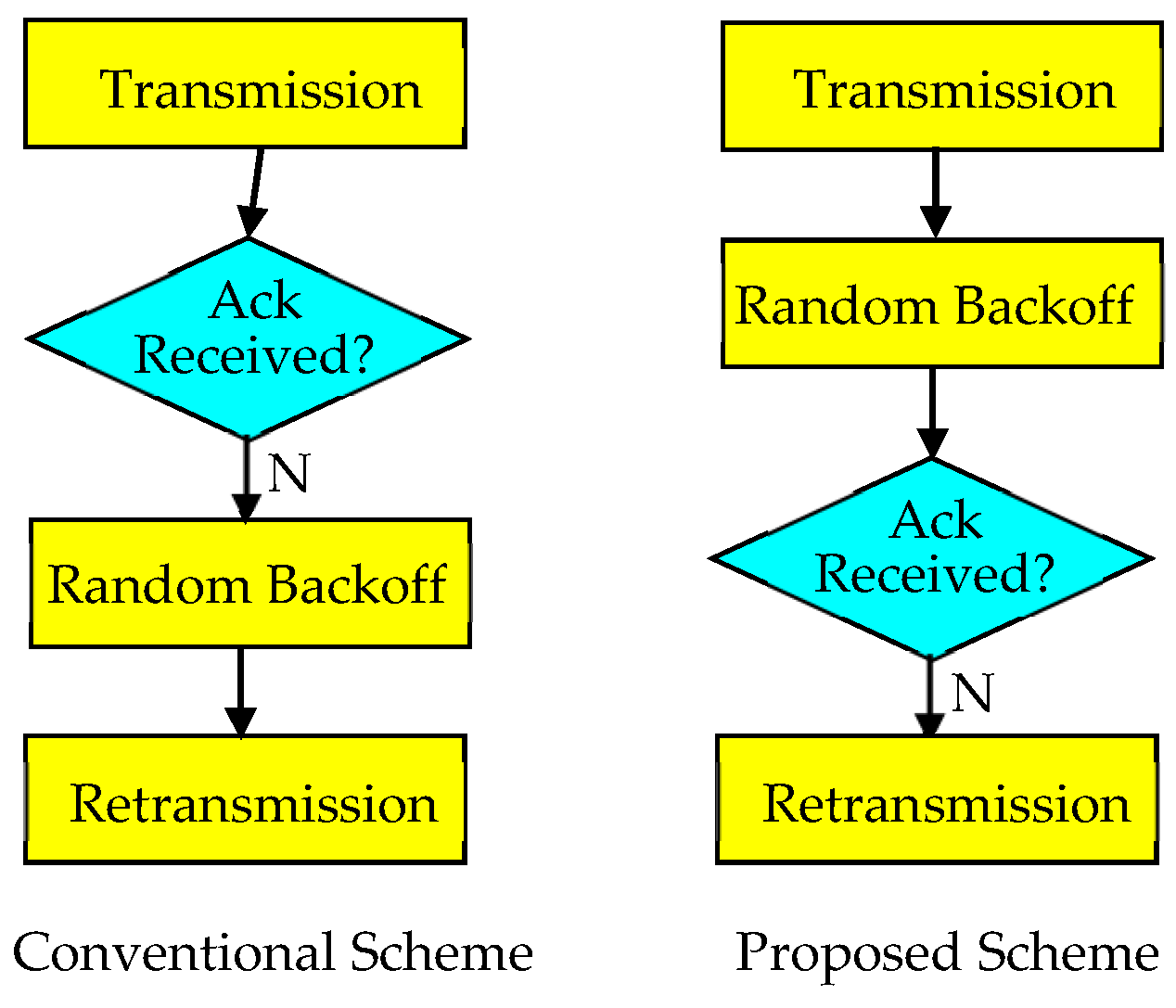
- There are two versions of the proposed schemes. The first method, called Delayed Response, delays the response of a packet to eliminate the interference to the packet in the meantime. The second method, called Random Backoff First, reverses the order of response checking and random backoff. A system can choose the appropriate method based on the system requirements or use a combination of both methods.
- (4)
- The proposed method does not sacrifice the performance of good-channel devices for the sake of bad-channel devices. The interference cancellation significantly reduces the collision probability of bad-channel devices while also reducing the collision probability of good-channel devices to some extent.
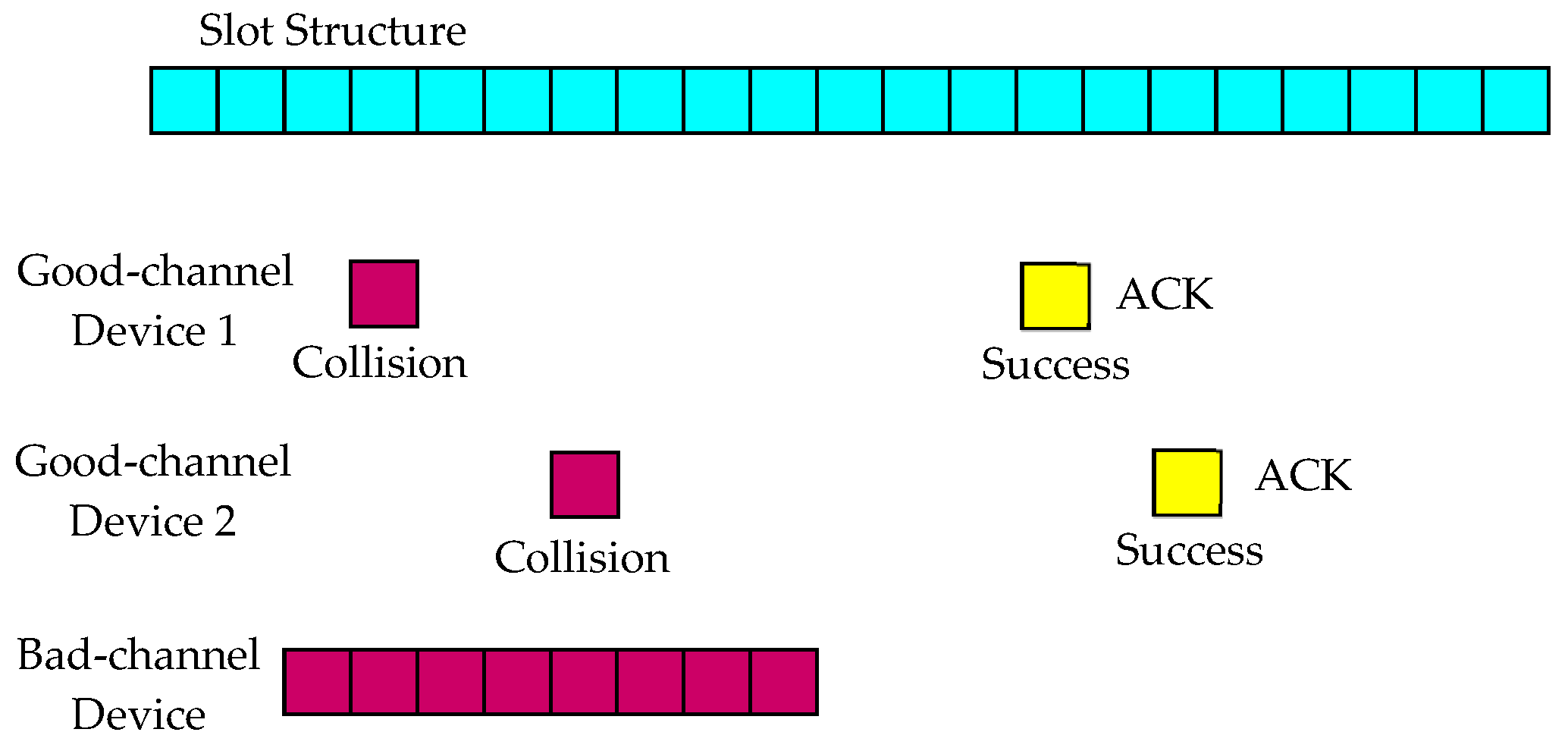
2. System Model
3. Proposed Random Access Schemes
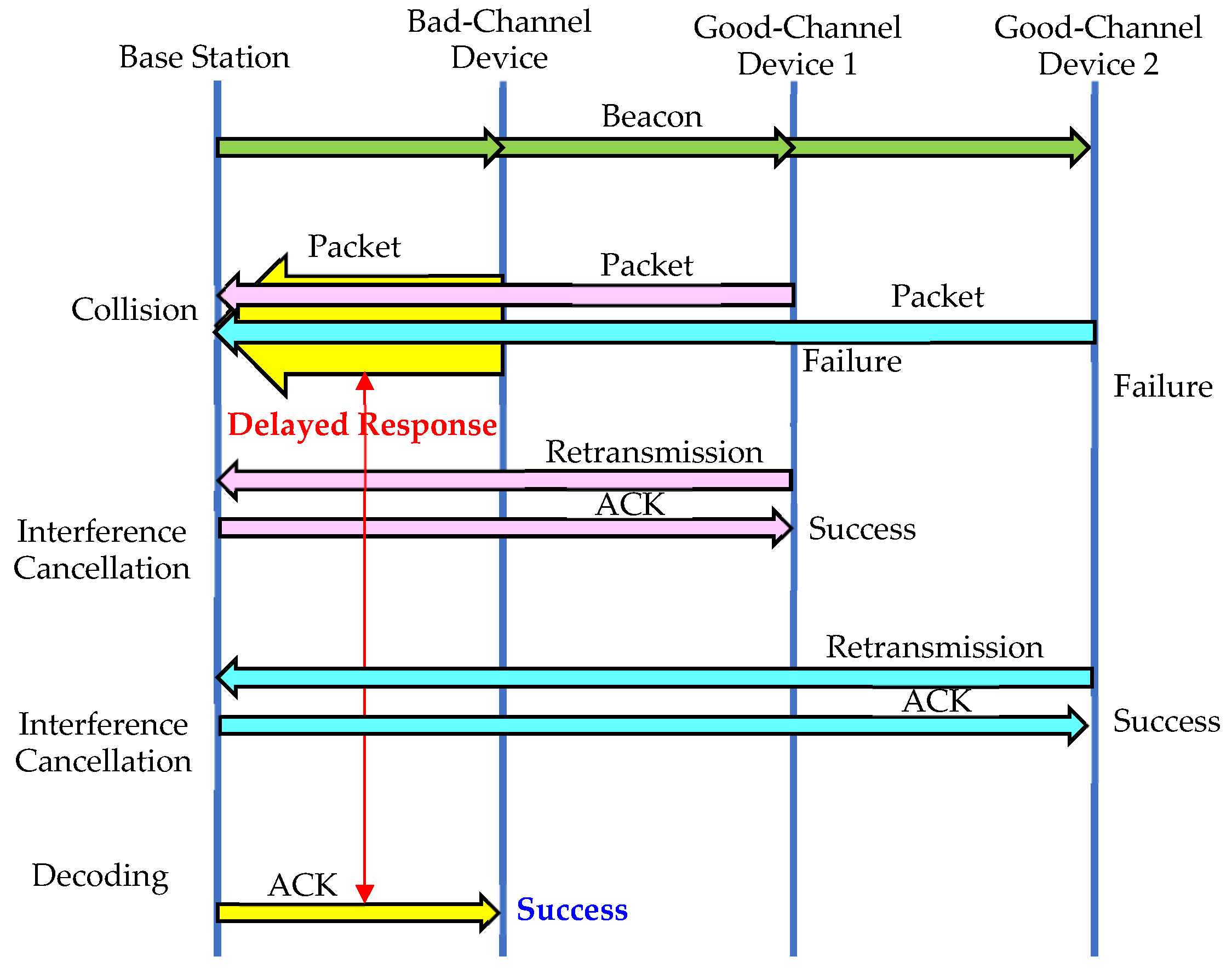
3.1. Delayed Response
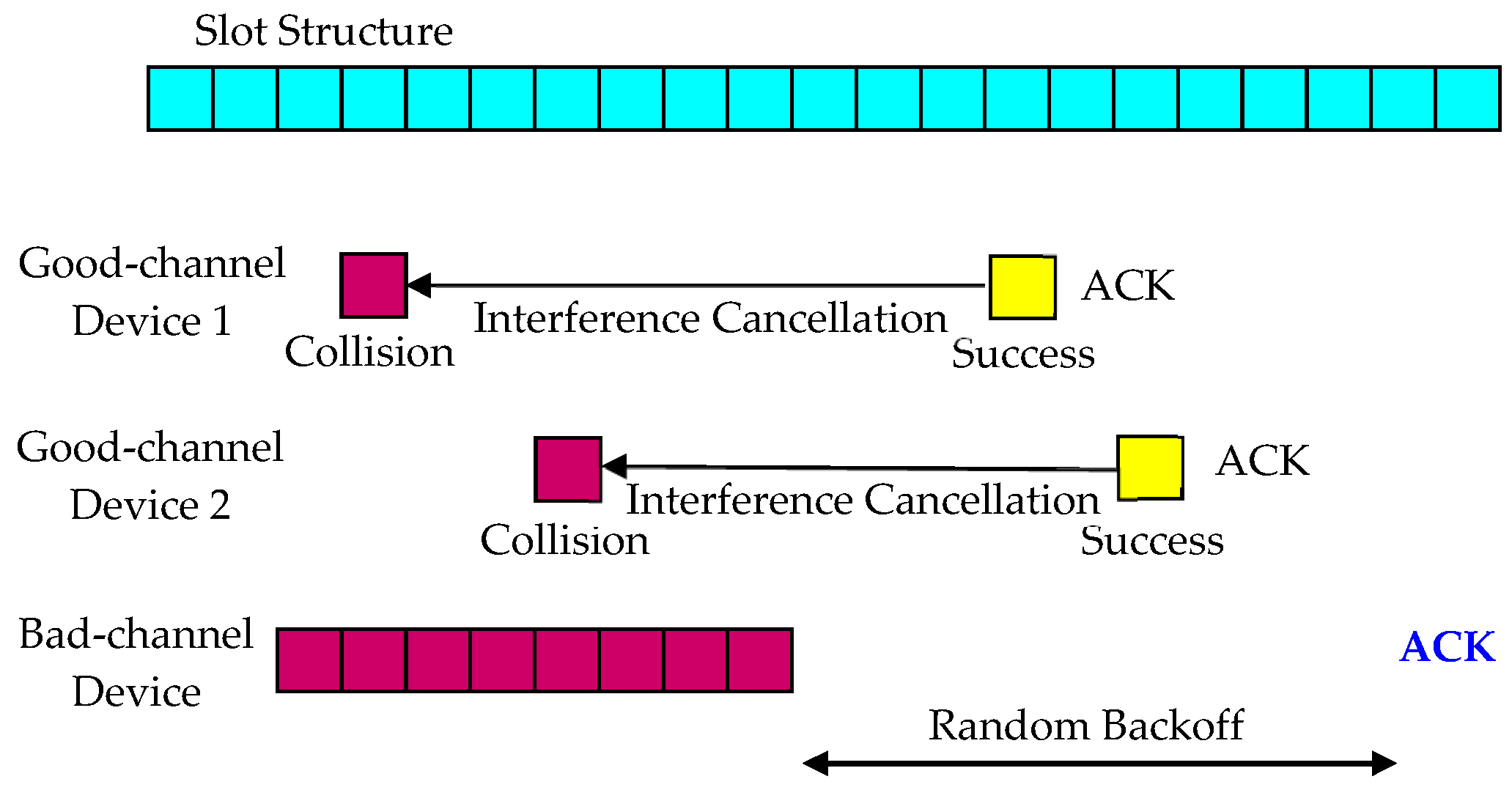
3.2. Random Backoff First
4. Interference Cancellation
5. Simulation Results
5.1. When a Good-Channel Device Does Not Perform Random Backoff
5.2. When a Good-Channel Device Performs Random Backoff
6. Conclusions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Zheng, K.; Ou, S.; Alonso-Zarate, J.; Dohler, M.; Liu, F.; Zhu, H. Challenges of Massive Access in Highly Dense LTE-Advanced Networks with Machine-to-Machine Communications. IEEE Wirel. Commun. 2014, 21, 12–18. [Google Scholar] [CrossRef]
- Ijaz, A.; Zhang, L.; Grau, M.; Mohamed, A.; Vural, S.; Quddus, A.U.; Imran, M.A.; Foh, C.H.; Tafazolli, R. Enabling Massive IoT in 5G and Beyond Systems: PHY Radio Frame Design Considerations. IEEE Access 2016, 4, 3322–3339. [Google Scholar] [CrossRef]
- Yang, Y.; Song, G.; Zhang, W.; Ge, X.; Wang, C. Neighbor-aware Multiple Access Protocol for 5G mMTC Applications. China Commun. 2016, 13 (Suppl. S2), 80–88. [Google Scholar] [CrossRef]
- Islam, M.T.; Haha, A.M.; Akl, S. A Survey of Access Management Techniques in Machine Type Communications. IEEE Commun. Mag. 2014, 52, 74–81. [Google Scholar] [CrossRef]
- Yang, F.; Bi, Q. On Novel Access and Scheduling Schemes for IoT Communications. Mob. Inf. Syst. 2016, 2016, 3973287. [Google Scholar]
- Hasan, M.; Hossain, E.; Niyato, D. Random Access for Machine-to-Machine Communication in LTE-Advanced Networks: Issues and Approaches. IEEE Commun. Mag. 2013, 51, 86–93. [Google Scholar] [CrossRef]
- Zanella, A.; Zorzi, M.; Santos, A.F.D.; Popovski, P.; Pratas, N.; Stefanovic, C.; Dekorsy, A.; Bockelmann, C.; Busropan, B.; Norp, T.A.H.J. M2M Massive Wireless Access: Challenges, Research Issues, and Ways Forward. In Globecom Workshops; IEEE: New York, NU, USA, 2013; pp. 151–156. [Google Scholar]
- Ding, J.; Nemati, M.; Ranaweera, C.; Choi, J. IoT Connectivity Technologies and Applications: A Survey. IEEE Access 2020, 8, 67646–67673. [Google Scholar] [CrossRef]
- Jang, H.; Jung, B.; Quek, T.Q.S.; Sung, D. Resource Hopping-Based Grant-Free Multiple Access for 6G-Enabled Massive IoT Networks. IEEE Internet Things J. 2021, 8, 15349–15360. [Google Scholar] [CrossRef]
- Kim, G.; Rim, M. Internet of Things in the 5G Mobile Communication System: The Optimal Number of Channels in Channel Hopping. Int. J. Networked Distrib. Comput. 2018, 6, 108–117. [Google Scholar] [CrossRef]
- Rim, M.; Chae, S.; Kang, C.G. MIMO Receivers considering Preamble Collisions for Grant-Free Random Access in Machine Type Communication Systems. Telecommun. Syst. 2019, 70, 185–191. [Google Scholar] [CrossRef]
- Vaezi, M.; Azari, A.; Khosravirad, S.R.; Shirvanimoghaddam, M.; Azari, M.M.; Chasaki, D. Cellular, Wide-Area, and Non-Terrestrial IoT: A Survey on 5G Advances and the Road Toward 6G. IEEE Commun. Surv. Tutor. 2022, 24, 1117–1174. [Google Scholar] [CrossRef]
- Bansal, V.; Pandey, N. Analytical Approach to Optimize Battery Life using Fog-IoT Paradigm. In Proceedings of the 2018 International Conference on Computational Techniques, Electronics and Mechanical Systems (CTEMS), Belgaum, India, 21–22 December 2018; pp. 140–144. [Google Scholar]
- George, A.M.; Kulkarni, S.Y. Characterization of Battery Life of an IoT based Wireless Networked Office Lighting System. In Proceedings of the 2020 IEEE International Conference on Electronics, Computing and Communication Technologies (CONECCT), Bangalore, India, 2–4 July 2020. [Google Scholar]
- Darabkh, K.A.; Kassab, W.K.; Khalifeh, A.F. Maximizing the Life Time of Wireless Sensor Networks over IoT Environment. In Proceedings of the 2020 Fifth International Conference on Fog and Mobile Edge Computing (FMEC), Paris, France, 20–23 April 2020; pp. 270–274. [Google Scholar]
- Kim, G.; Kang, J.; Rim, M. Dynamic Duty-Cycle MAC Protocol for IoT Environments and Wireless Sensor Networks. Energies 2019, 12, 4069. [Google Scholar] [CrossRef]
- Kim, G.; Rim, M. Duty-Cycle-Based Pre-Emption Protocol for Emergency Networks. Sensors 2021, 22, 30. [Google Scholar] [CrossRef] [PubMed]
- Hussain, K.; Gupta, R. Method to Minimize Radio Resource Wastage and Battery Consumption in NB-IoT. In Proceedings of the 2021 IEEE Wireless Communications and Networking Conference (WCNC), Nanjing, China, 29 March–1 April 2021. [Google Scholar]
- Chang, X.; Chen, K.; Xing, G.; Huang, J.; Chen, B. Optimizing NB-IoT Power Consumption via Adaptive Radio Access. IEEE Internet Things J. 2021, 9, 4693–4703. [Google Scholar] [CrossRef]
- Liu, Y.; Deng, Y.; Elkashlan, M.; Nallanathan, A. Random Access Performance for Three Coverage Enhancement Groups in NB-IoT Networs. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019. [Google Scholar]
- Harwahyu, R.; Cheng, R.; Liu, D.; Sari, R.F. Fair Configuration Scheme for Random Access in NB-IoT with Multiple Coverage Enhancement Levels. IEEE Trans. Mob. Comput. 2021, 20, 1408–1419. [Google Scholar] [CrossRef]
- Chafii, M.; Bader, F.; Palicot, J. Enhancing Coverage in Narrow Band IoT Using Machine Learning. In Proceedings of the 2018 IEEE Wireless Communications and Networking Conference (WCNC), Barcelona, Spain, 15–18 April 2018. [Google Scholar]
- Liu, Y.; Deng, Y.; Jiang, N.; Elkashlan, M.; Nallanathan, A. Analysis of Random Access in NB-IoT Networks with Three Coverage Enhancement Groups: A Stochastic Geometry Approach. IEEE Trans. Wirel. Commun. 2021, 20, 549–564. [Google Scholar] [CrossRef]
- Wang, W.; Leshem, A.; Niyato, D.; Han, Z. Decentralized Learning for Channel Allocation in IoT Networks Over Unlicensed Bandwidth as a Contextual Multi-Player Multi-Armed Bandit Game. IEEE Trans. Wirel. Commun. 2022, 21, 3162–3178. [Google Scholar] [CrossRef]
- Kerkouche, R.; Alami, R.; Feraud, R.; Varsier, N.; Maille, P. Node-based Optimization of LoRa Transmissions with Multi-Armed Bandit Algorithms. In Proceedings of the 2018 25th International Conference on Telecommunications (ICT), Saint-Malo, France, 26–28 June 2018; pp. 521–526. [Google Scholar]
- Mohammadkarimi, M.; Raza, M.A.; Dobre, O.A. Signature-Based Nonorthogonal Massive Multiple Access for Future Wireless Networks: Uplink Massive Connectivity for Machine-Type Communications. IEEE Veh. Technol. Mag. 2018, 13, 40–50. [Google Scholar] [CrossRef]
- Shirvanimoghaddam, M.; Condoluci, M.; Dohler, M.; Johnson, S.J. On the Fundamental Limits of Random Non-Orthogonal Multiple Access in Cellular Massive IoT. IEEE J. Sel. Areas Commun. 2017, 35, 2238–2252. [Google Scholar] [CrossRef]
- Kiani, A.; Ansari, N. Edge Computing Aware NOMA for 5G Networks. IEEE Internet Things J. 2018, 5, 1299–1306. [Google Scholar] [CrossRef]
- Dai, L.; Wang, B.; Yuan, Y.; Han, S.; Chih-lin, I.; Wang, Z. Non-Orthogonal Multiple Access for 5G: Solutions, Challenges, Opportunities, and Future Research Trends. IEEE Commun. Mag. 2015, 53, 74–81. [Google Scholar] [CrossRef]
- Zhang, N.; Wang, J.; Kang, G.; Liu, Y. Uplink Nonorthogonal Multiple Access in 5G Systems. IEEE Commun. Lett. 2016, 20, 458–461. [Google Scholar] [CrossRef]
- Chen, S.; Ren, B.; Gao, Q.; Kang, S.; Sun, S.; Niu, K. Pattern Division Multiple Access–A Novel Non-Orthogonal Multiple Access for 5G Radio Network. IEEE Trans. Veh. Technol. 2017, 66, 3185–3196. [Google Scholar] [CrossRef]
- Du, Y.; Dong, B.; Chen, Z.; Fang, J.; Gao, P.; Liu, Z. Low-Complexity Detector in Sparse Code Multiple Access Systems. IEEE Commun. Lett. 2016, 20, 1812–1815. [Google Scholar] [CrossRef]
- Tao, Y.; Liu, L.; Liu, S.; Zhang, Z. A Survey: Several Technologies of Non-Orthogonal Transmission for 5G. China Commun. 2015, 12, 1–15. [Google Scholar] [CrossRef]
- Chen, Y.; Schaepperle, J.; Wild, T. Comparing IDMA and NOMA with Superimposed Pilots Based Channel Estimation in Uplink. In Proceedings of the 2015 IEEE 26th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Hong Kong, China, 30 August–2 September 2015; pp. 89–94. [Google Scholar]
- Sergienko, A.B.; Klimentyev, V.P. SCMA Detection with Channel Estimation Error and Resource Block Diversity. In Proceedings of the 2016 International Siberian Conference on Control and Communications (SIBCON), Moscow, Russia, 12–14 May 2016; pp. 1–5. [Google Scholar]
- Du, Y.; Dong, B.; Zhu, W.; Gao, P.; Chen, Z.; Wang, X.; Fang, J. Joint Channel Estimation and Multiuser Detection for Uplink Grant-Free NOMA. IEEE Wirel. Commun. Lett. 2018, 7, 682–685. [Google Scholar] [CrossRef]
- Tegos, S.A.; Diamantoulakis, P.D.; Lioumpas, A.S.; Sarigiannidis, P.G.; Karaagiannidis, G.K. Slotted ALOHA With NOMA for the Next Generation IoT. IEEE Trans. Commun. 2020, 68, 6289–6301. [Google Scholar] [CrossRef]
- Gao, Y.; Xia, B.; Liu, Y.; Yao, Y.; Xiao, K.; Lu, G. Analysis of the Dynamic Ordered Decoding for Uplink NOMA Systems with Imperfect CSI. IEEE Trans. Veh. Technol. 2018, 67, 6647–6651. [Google Scholar] [CrossRef]
- Rim, M.; Kang, C.G. Uplink Non-Orthogonal Multiple Access with Channel Estimation Errors for Internet of Things Applications. Sensors 2019, 19, 912. [Google Scholar] [CrossRef]
- Rim, M.; Kang, C.G. Carrier Sensing for OFDMA-based D2D Group-casting Systems. IEEE Trans. Veh. Technol. 2017, 66, 2301–2310. [Google Scholar] [CrossRef]
- Clerckx, B.; Mao, Y.; Schober, R.; Jorswiek, E.A.; Love, D.J.; Yuan, J.; Hanzo, L.; Li, G.Y.; Larsson, E.G.; Caire, G. Is NOMA Efficient in Multi-Antenna Networks? A Critical Look at Next Generation Multiple Access Techniques. IEEE Open J. Commun. Soc. 2021, 2, 1310–1343. [Google Scholar] [CrossRef]
- Vaezi, M.; Schober, R.; Ding, Z.; Poor, H.V. NOMA: Common Myths and Critical Questions. IEEE Wirel. Commun. 2019, 26, 174–180. [Google Scholar] [CrossRef]
- Paolini, E.; Stefanovic, C.; Liva, G.; Popovski, P. Coded Random Access: Applying Codes on Graphs to Design Random Access Protocols. IEEE Commun. Mag. 2015, 53, 144–150. [Google Scholar] [CrossRef]
- Zhang, Z.; Xu, C.; Ping, L. Coded Random Access with Distributed Power Control and Multiple Packet Reception. IEEE Wirel. Commun. Lett. 2014, 4, 117–120. [Google Scholar] [CrossRef]
- Paolini, E.; Liva, G.; Chiani, M. Coded Slotted ALOHA: A Graph-Based Method for Uncoordinated Multiple Access. IEEE Trans. Inf. Theory 2015, 61, 6815–6832. [Google Scholar] [CrossRef]
- Stefanovic, C.; Popovski, P. ALOHA Random Access that Operates as a Rateless Code. EEE Trans. Commun. 2013, 64, 4653–4662. [Google Scholar] [CrossRef]
- Wunder, G.; Stefanovic, C.; Popovski, P.; Thiele, L. Compressive Coded Random Access for Massive MTC Traffic in 5G Systems. In Proceedings of the Asiloma Conference on Signals, Systems, and Computers, Pacific Grove, CA, USA, 8–11 November 2015; pp. 13–17. [Google Scholar]
- Purwita, A.A.; Anwar, K. Massive Multiway Relay Networks Applying Coded Random Access. IEEE Trans. Commun. 2016, 64, 4134–4146. [Google Scholar] [CrossRef]
- Rim, M.; Chae, S. Frame-Based Random Access with Interference Cancellation across Frames for Massive Machine Type Communications. Mob. Inf. Syst. 2017, 2017, 7954631. [Google Scholar] [CrossRef]














| Delayed Response | Random Backoff First |
|---|---|
| Delays response | Reverses the order of response checking and random backoff |
| Increases transmission latency | Does not increase transmission latency |
| Attempts to decode once just before the response time | Attempts to decode multiple times each time interference cancellation is performed |
| Performs sufficient interference cancellation if the delay value is large | May perform insufficient interference cancellation if a small backoff value is selected |
| Simulation Parameters | Values |
|---|---|
| Number of devices performing random access () | 1~120 for Figure 9, Figure 10, Figure 11 and Figure 12; 1~150 for Figure 13 and Figure 14; 1~120 for Figure 15, Figure 16 and Figure 17; 1~150 for Figure 18 and Figure 19 |
| Virtual frame size () | 8 |
| Packet length of a good-channel device | 1 |
| Transmission period | One packet per 512 slots |
| Packet length of a bad-channel device | 1, 2, 4, 8, 16 for Figure 9; 16 for Figure 10, Figure 11 and Figure 12; 1 (i.e., no bad-channel device) for Figure 13 and Figure 14; 1, 2, 4, 8, 16 for Figure 15; 16 for Figure 16 and Figure 17; 1 (i.e., no bad-channel device) for Figure 18 and Figure 19 |
| Eliminating interference caused by a good-channel device | 0 packets for Figure 9; Up to 7 previously transmitted packets for Figure 10, Figure 11, Figure 12, Figure 13 and Figure 14; 0 packets for Figure 15; Up to 7 previously transmitted packets for Figure 16, Figure 17, Figure 18 and Figure 19 |
| Random access schemes for a bad-channel device | Conventional for Figure 9; Delayed Response for Figure 10; Random Backoff First for Figure 11; Delayed Response + Random Backoff First for Figure 12; No bad-channel device for Figure 13 and Figure 14; Conventional for Figure 15; Delayed Response for Figure 16; Random Backoff First for Figure 17; No bad-channel device for Figure 18 and Figure 19 |
| Contention window size of a good-channel device | 1 for Figure 9, Figure 10, Figure 11, Figure 12, Figure 13 and Figure 14; 4 for Figure 15, Figure 16, Figure 17, Figure 18 and Figure 19 |
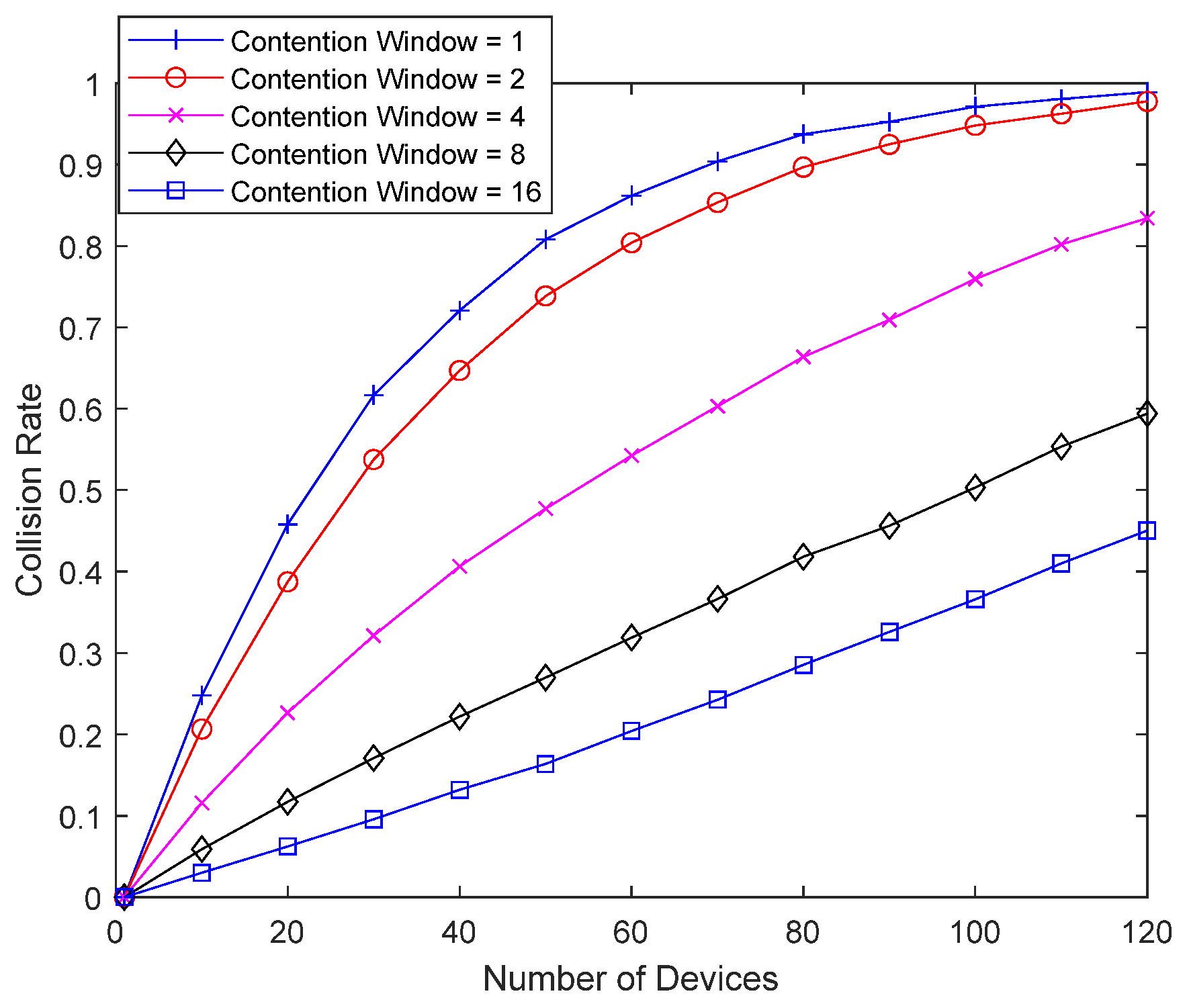
| Contention window size of a bad-channel device | 1, 2, 4, 8, 16 for Figure 11, Figure 12 and Figure 17 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rim, M. Delayed Response and Random Backoff First for Low-Power Random Access of IoT Devices with Poor Channel Conditions. Sensors 2023, 23, 9556. https://doi.org/10.3390/s23239556
Rim M. Delayed Response and Random Backoff First for Low-Power Random Access of IoT Devices with Poor Channel Conditions. Sensors. 2023; 23(23):9556. https://doi.org/10.3390/s23239556
Chicago/Turabian StyleRim, Minjoong. 2023. "Delayed Response and Random Backoff First for Low-Power Random Access of IoT Devices with Poor Channel Conditions" Sensors 23, no. 23: 9556. https://doi.org/10.3390/s23239556
APA StyleRim, M. (2023). Delayed Response and Random Backoff First for Low-Power Random Access of IoT Devices with Poor Channel Conditions. Sensors, 23(23), 9556. https://doi.org/10.3390/s23239556





