Secrecy Performance Analysis of Backscatter Communications with Side Information
Abstract
:1. Introduction
1.1. Related Works
1.2. Motivations and Contributions
- By considering the non-causally known SI at the transmitter, we first derive the closed-form expressions of marginal distributions of the equivalent SNR at both a legitimate receiver and an eavesdropper under independent Rayleigh fading channels.
- Based on the derived probability density function (PDF) and cumulative distribution function (CDF) of the received SNR at the receiver and eavesdropper, we obtain the analytical expressions of the ASC and SOP to analyze the secrecy performance of the BC systems under the effect of non-causally known SI.
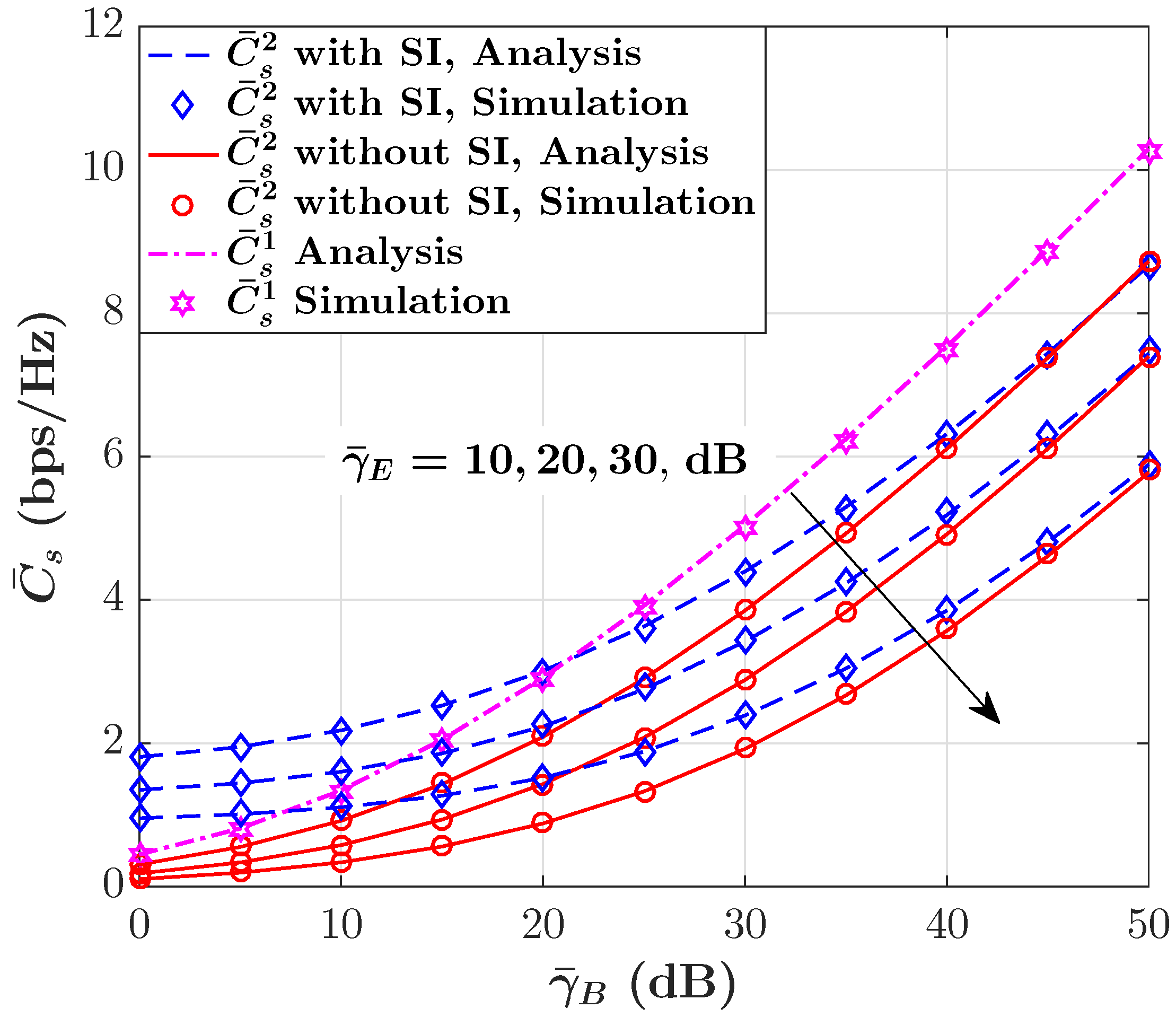
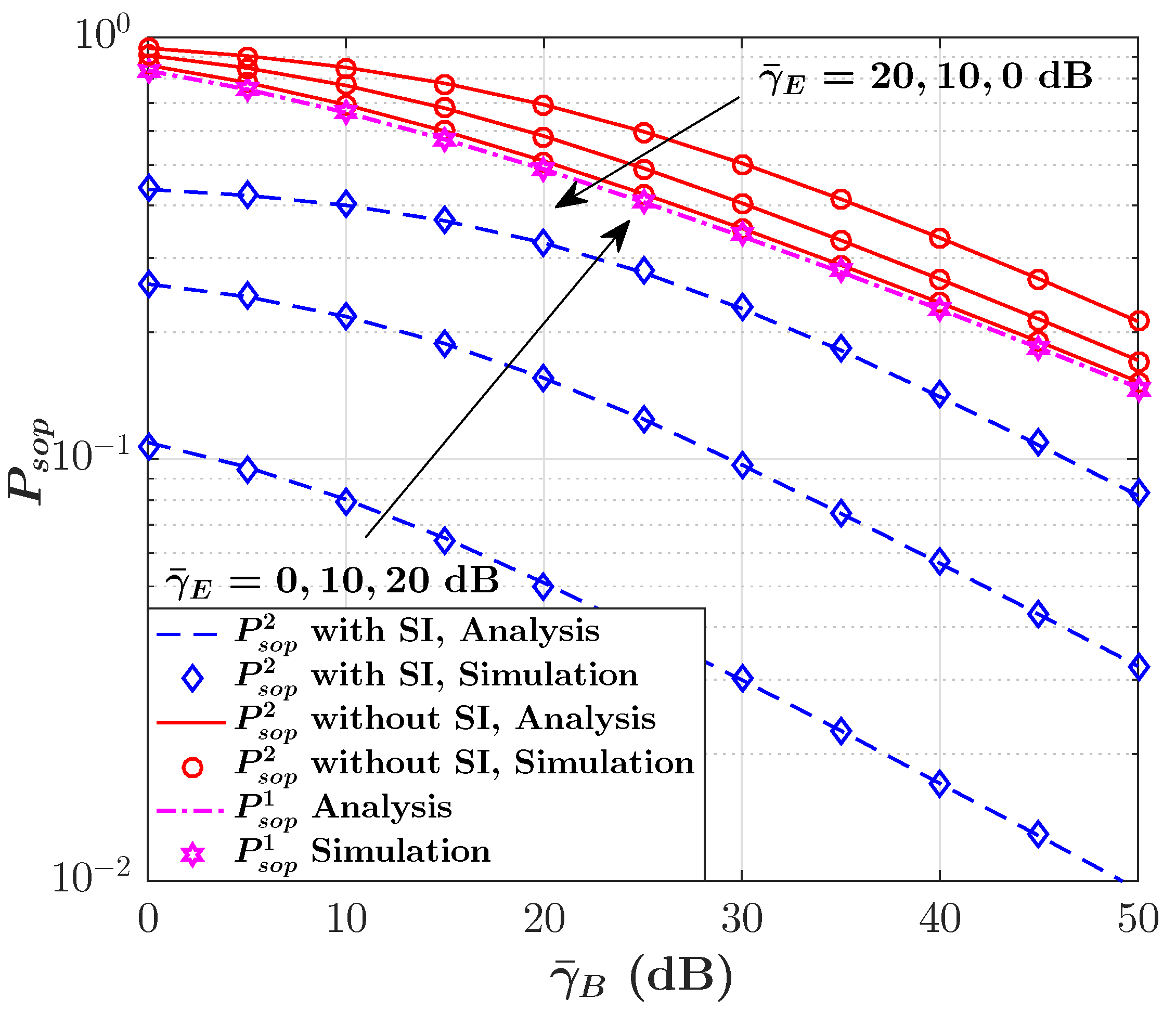
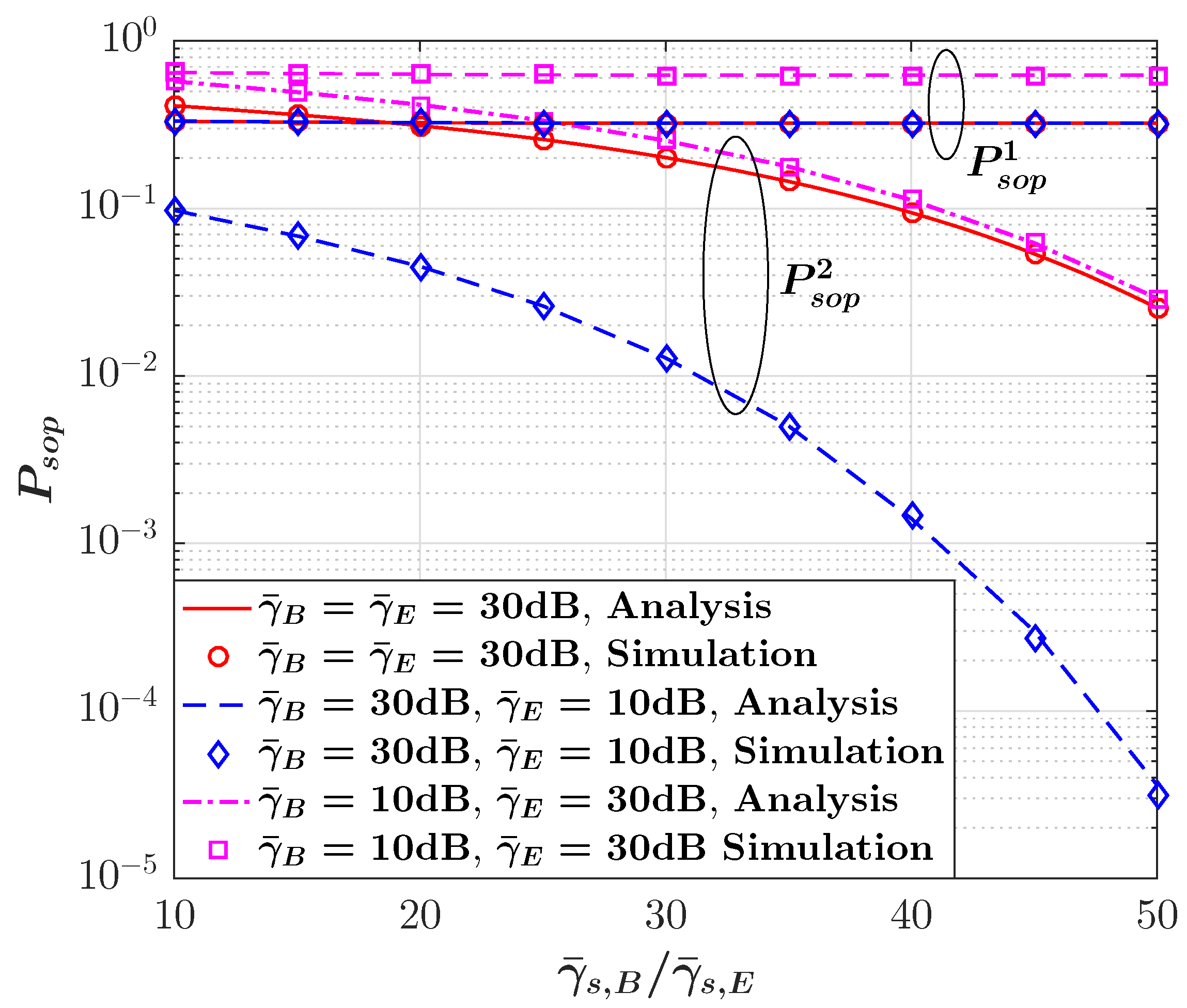
- Finally, we validate our analytical results through a Monte Carlo simulation. Our numerical results validate the analytical expressions and indicate that even considering a small amount of non-causally known SI at the transmitter can significantly enhance the performance of secure BC systems, namely, providing a higher ASC and a lower SOP compared with the blank BC scenarios (i.e., without SI).
1.3. Paper Organization
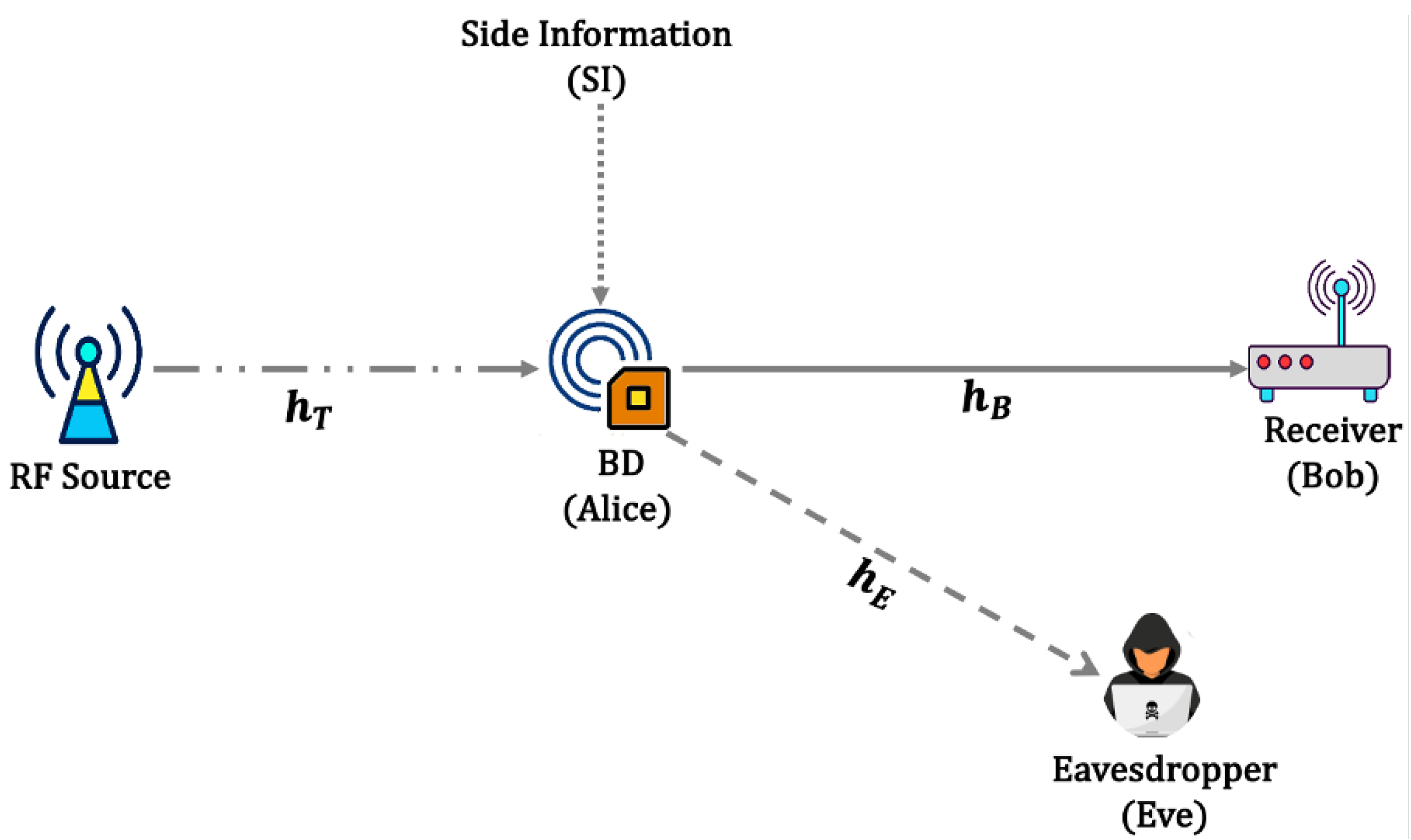
2. System Model
2.1. Channel Model
2.2. SNR Distribution
3. Secrecy Performance Analysis
3.1. ASC Analysis
3.2. SOP Analysis
4. Numerical Results
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| BC | Backscatter communication |
| IoT | Internet of things |
| SI | Side information |
| ASC | Average secrecy capacity |
| SOP | Secrecy outage probability |
| 6G | Sixth generation |
| PLS | Physical layer security |
| P2P | Point-to-point |
| CSI | Channel state information |
| SISO | Single-input single-output |
| MIMO | Multiple-input multiple-output |
| SNR | Signal-to-noise ratio |
| RF | Radio-frequency |
References
- Wu, W.; Wang, X.; Hawbani, A.; Yuan, L.; Gong, W. Survey on ambient backscatter communications: Principles, systems, applications, and challenges. Comput. Netw. 2022, 216, 109235. [Google Scholar] [CrossRef]
- Jameel, F.; Duan, R.; Chang, Z.; Liljemark, A.; Ristaniemi, T.; Jantti, R. Applications of backscatter communications for healthcare networks. IEEE Netw. 2019, 33, 50–57. [Google Scholar] [CrossRef]
- Xu, C.; Yang, L.; Zhang, P. Practical backscatter communication systems for battery-free Internet of Things: A tutorial and survey of recent research. IEEE Signal Process. Mag. 2018, 35, 16–27. [Google Scholar] [CrossRef]
- Yang, L.; Li, X.; Sun, M.; Sun, C. Hybrid policy-based reinforcement learning of adaptive energy management for the Energy transmission-constrained island group. IEEE Trans. Ind. Inform. 2023, 19, 10751–10762. [Google Scholar] [CrossRef]
- Duan, R.; Wang, X.; Yigitler, H.; Sheikh, M.U.; Jantti, R.; Han, Z. Ambient backscatter communications for future ultra-low-power machine type communications: Challenges, solutions, opportunities, and future research trends. IEEE Commun. Mag. 2020, 58, 42–47. [Google Scholar] [CrossRef]
- Wang, P.; Yan, Z.; Zeng, K. Bcauth: Physical layer enhanced authentication and attack tracing for backscatter communications. IEEE Trans. Inf. Forensics Secur. 2022, 17, 2818–2834. [Google Scholar] [CrossRef]
- Ghadi, F.R.; Martin-Vega, F.J.; Martínez, F.J.L. Capacity of backscatter communication under arbitrary fading dependence. IEEE Trans. Veh. Technol. 2022, 71, 5593–5598. [Google Scholar] [CrossRef]
- Cao, K.; Weng, J.; Li, K. Reliability-Driven End–End–Edge Collaboration for Energy Minimization in Large-Scale Cyber-Physical Systems. IEEE Trans. Reliab. 2023. early access. [Google Scholar] [CrossRef]
- Wang, P.; Wang, N.; Dabaghchian, M.; Zeng, K.; Yan, Z. Optimal Resource Allocation for Secure Multi-User Wireless Powered Backscatter Communication with Artificial Noise. In Proceedings of the IEEE INFOCOM 2019, Paris, France, 29 April–2 May 2019. [Google Scholar]
- Li, X.; Zheng, Y.; Khan, W.U.; Zeng, M.; Li, D.; Ragesh, G.K.; Li, L. Physical layer security of cognitive ambient backscatter communications for green Internet-of-Things. IEEE Trans. Green Commun. Netw. 2021, 5, 1066–1076. [Google Scholar] [CrossRef]
- Li, M.; Yang, X.; Khan, F.; Jan, M.A.; Chen, W.; Han, Z. Improving physical layer security in vehicles and pedestrians networks with ambient backscatter communication. IEEE Trans. Intell. Transp. Syst. 2022, 23, 9380–9390. [Google Scholar] [CrossRef]
- Tang, Z.; Hou, T.; Liu, Y.; Zhang, J.; Zhong, C. A novel design of RIS for enhancing the physical layer security for RIS-aided NOMA networks. IEEE Wirel. Commun. Lett. 2021, 10, 2398–2401. [Google Scholar] [CrossRef]
- Zhu, F.; Yao, M. Improving physical-layer security for CRNs using SINR-based cooperative beamforming. IEEE Trans. Veh. Technol. 2015, 65, 1835–1841. [Google Scholar] [CrossRef]
- Yang, Y.S.; Yan, Z.; Zeng, K.; Wang, P.; Li, J.J. Physical Layer Authentication in Backscatter Communication: A Review. IEEE Wirel. Commun. Mag. 2022, 17, 2818–2834. [Google Scholar]
- Wang, P.; Yan, Z.; Wang, N.; Zeng, K. Optimal Resource Allocation for Secure Multi-device Wirelessly Powered Backscatter Communications with Artificial Noise. IEEE Trans. Wirel. Commun. 2022, 21, 7794–7809. [Google Scholar] [CrossRef]
- Yang, Y.S.; Kaveh, M.; Li, J.J.; Zhang, Y.F.; Yan, Z.; Zeng, K. BatAu: A Batch Authentication Scheme for Backscatter Devices in a Smart Home Network. In Proceedings of the IEEE 2023 IEEE International Conference on Communications (ICC), Rome, Italy, 28 May–1 June 2023. [Google Scholar]
- Wang, P.; Jiao, L.; Zeng, K.; Yan, Z. Physical Layer Key Generation between Backscatter Devices over Ambient RF Signals. In Proceedings of the IEEE INFOCOM 2021, Virtual Conference, 10–13 May 2021. [Google Scholar]
- Shannon, C.E. Communication theory of secrecy systems. Bell Labs Tech. J. 1949, 28, 656–715. [Google Scholar] [CrossRef]
- Wyner, A.D. The wire-tap channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Shannon, C.E. Channels with side information at the transmitter. IBM J. Res. Dev. 1958, 2, 289–293. [Google Scholar] [CrossRef]
- Jafar, S. Capacity with causal and noncausal side information: A unified view. IEEE Trans. Inf. Theory 2006, 52, 5468–5474. [Google Scholar] [CrossRef]
- Mitrpant, C.; Vinck, A.J.H.; Luo, Y. An achievable region for the Gaussian wiretap channel with side information. IEEE Trans. Inf. Theory 2006, 52, 2181–2190. [Google Scholar] [CrossRef]
- Costa, M. Writing on dirty paper (corresp.). IEEE Trans. Inf. Theory 1983, 29, 439–441. [Google Scholar] [CrossRef]
- Chen, Y.; Vinck, A.H. Wiretap channel with side information. IEEE Trans. Inf. Theory 2008, 54, 395–402. [Google Scholar] [CrossRef]
- Saad, W.; Zhou, X.; Han, Z.; Poor, H.V. On the physical layer security of backscatter wireless systems. IEEE Trans. Wirel. Commun. 2014, 13, 3442–3451. [Google Scholar] [CrossRef]
- Zhang, Y.; Gao, F.; Fan, L.; Lei, X.; Karagiannidis, G.K. Secure communications for multi-tag backscatter systems. IEEE Wirel. Commun. Lett. 2019, 8, 1146–1149. [Google Scholar] [CrossRef]
- Liu, Y.; Ye, Y.; Hu, R.Q. Secrecy outage probability in backscatter communication systems with tag selection. IEEE Wirel. Commun. Lett. 2021, 10, 2190–2194. [Google Scholar] [CrossRef]
- Liu, Z.; Ye, Y.; Chu, X.; Sun, H. Secrecy performance of backscatter communications with multiple self-powered tags. IEEE Commun. Lett. 2022, 26, 2875–2879. [Google Scholar] [CrossRef]
- Muratkar, T.S.; Bhurane, A.; Sharma, P.K.; Kothari, A. Physical layer security analysis in ambient backscatter communication with node mobility and imperfect channel estimation. IEEE Commun. Lett. 2021, 26, 27–30. [Google Scholar] [CrossRef]
- Zheng, Y.; Li, X.; Zhang, H.; Alshehri, M.D.; Dang, S.; Huang, G.; Zhang, C. Overlay cognitive ABCom-NOMA-based ITS: An in-depth secrecy analysis. IEEE Trans. Intell. Transp. Syst. 2022, 24, 2217–2228. [Google Scholar] [CrossRef]
- Jia, S.; Wang, R.; Xu, Y.; Lou, Y.; Zhang, D.; Sato, T. Secrecy Analysis of ABCom-Based Intelligent Transportation Systems With Jamming. IEEE Trans. Intell. Transp. Syst. 2023. early access. [Google Scholar] [CrossRef]
- Sharma, H.K.; Kumbhani, B. Ergodic secrecy capacity of backscatter communication based automatic toll collection systems. Sādhanā 2023, 48, 83. [Google Scholar] [CrossRef]
- Zan, J.; Shi, L.; Lu, G.; Ye, Y. Wireless-powered backscatter communications for smart sustainable cities: A secrecy analysis. Sustain. Energy Technol. Assess. 2023, 56, 103036. [Google Scholar] [CrossRef]
- Wang, H.; Jiang, J.; Huang, G.; Wang, W.; Deng, D.; Elhalawany, B.M.; Li, X. Physical layer security of two-way ambient backscatter communication systems. Wirel. Commun. Mob. Comput. 2022, 2022, 5445676. [Google Scholar] [CrossRef]
- Bai, L.; Chen, Q.; Bai, T.; Wang, J. UAV-enabled secure multiuser backscatter communications with planar array. IEEE J. Sel. Areas Commun. 2022, 40, 2946–2961. [Google Scholar] [CrossRef]
- That, P.T.; Ha, D.H.; Nguyen, H.N. Secrecy capacity analysis of bi-static backscatter communication systems. Bull. Electr. Eng. Inform. 2022, 11, 3353–3360. [Google Scholar] [CrossRef]
- Li, X.; Zhao, M.; Liu, Y.; Li, L.; Ding, Z.; Nallanathan, A. Secrecy analysis of ambient backscatter NOMA systems under I/Q imbalance. IEEE Trans. Veh. Technol. 2020, 69, 12286–12290. [Google Scholar] [CrossRef]
- Gorbade, S.; Shrivastava, R.; Bhurane, A. Physical Layer Security Analysis in Ambient Backscatter Communication With Source and Reader Mobility. In Proceedings of the 2022 1st International Conference on the Paradigm Shifts in Communication, Embedded Systems, Machine Learning and Signal Processing (PCEMS), Nagpur, India, 6–7 May 2022; pp. 57–61. [Google Scholar]
- Kim, T.T.; Skoglund, M. On the expected rate of slowly fading channels with quantized side information. IEEE Trans. Commun. 2007, 55, 820–829. [Google Scholar] [CrossRef]
- Narula, A.; Lopez, M.J.; Trott, M.D.; Wornell, G.W. Efficient use of side information in multiple-antenna data transmission over fading channels. IEEE J. Sel. Areas Commun. 1998, 16, 1423–1436. [Google Scholar] [CrossRef]
- Sharif, M.; Hassibi, B. On the capacity of MIMO broadcast channels with partial side information. IEEE Trans. Inf. Theory 2005, 51, 506–522. [Google Scholar] [CrossRef]
- Ghadi, F.R.; Hodtani, G.A.; López-Martínez, F.J. The role of correlation in the doubly dirty fading MAC with side information at the transmitters. IEEE Wirel. Commun. Lett. 2021, 10, 2070–2074. [Google Scholar] [CrossRef]
- Ghadi, F.R.; Zhu, W.P. Performance Analysis Over Correlated/Independent Fisher-Snedecor F Fading Multiple Access Channels. IEEE Trans. Veh. Technol. 2022, 71, 7561–7571. [Google Scholar] [CrossRef]
- Ghadi, F.R.; López-Martínez, F.J. RIS-Aided Communications over Dirty MAC: Capacity Region and Outage Probability. IEEE Commun. Lett. 2023, 27, 2009–2013. [Google Scholar] [CrossRef]
- Ghadi, F.R.; López-Martínez, F.J.; Zhu, W.P.; Gorce, J.M. The impact of side information on physical layer security under correlated fading channels. IEEE Trans. Inf. Forensics Secur. 2022, 17, 3626–3636. [Google Scholar] [CrossRef]
- Walid, S.; Bennis, M.; Chen, M. A vision of 6G wireless systems: Applications, trends, technologies, and open research problems. IEEE Netw. 2019, 34, 134–142. [Google Scholar]
- Biswas, R.; Sheikh, M.U.; Yiğitler, H.; Lempiäinen, J.; Jäntti, R. Direct path interference suppression requirements for bistatic backscatter communication system. In Proceedings of the IEEE 93rd Vehicular Technology Conference, Helsinki, Finland, 25–28 April 2022; pp. 1–5. [Google Scholar]
- Zhang, M.; Zhao, J.; Chen, S.; Gong, W. Reliable backscatter with commodity BLE. In Proceedings of the IEEE Conference on Computer Communications (INFOCOM), Toronto, ON, Canada, 6–9 July 2022; pp. 1291–1299. [Google Scholar]
- Liao, J.; Wang, X.; Ruttik, K.; Jäntti, R.; Phan-Huy, D.T. In-band Ambient FSK Backscatter Communications Leveraging LTE Cell-Specific Reference Signals. IEEE J. Radio Freq. Identif. 2023, 7, 267–277. [Google Scholar] [CrossRef]
- Prudnikov, A.P. Integrals and Series: More Special Functions; CRC Press: Boca Raton, FL, USA, 1986; Volume 3. [Google Scholar]
- Mathai, A.M.; Saxena, R.K.; Haubold, H.J. The H-Function: Theory and Applications; Springer Science and Business Media: Berlin/Heidelberg, Germany, 2009. [Google Scholar]

Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kaveh, M.; Rostami Ghadi, F.; Jäntti, R.; Yan, Z. Secrecy Performance Analysis of Backscatter Communications with Side Information. Sensors 2023, 23, 8358. https://doi.org/10.3390/s23208358
Kaveh M, Rostami Ghadi F, Jäntti R, Yan Z. Secrecy Performance Analysis of Backscatter Communications with Side Information. Sensors. 2023; 23(20):8358. https://doi.org/10.3390/s23208358
Chicago/Turabian StyleKaveh, Masoud, Farshad Rostami Ghadi, Riku Jäntti, and Zheng Yan. 2023. "Secrecy Performance Analysis of Backscatter Communications with Side Information" Sensors 23, no. 20: 8358. https://doi.org/10.3390/s23208358
APA StyleKaveh, M., Rostami Ghadi, F., Jäntti, R., & Yan, Z. (2023). Secrecy Performance Analysis of Backscatter Communications with Side Information. Sensors, 23(20), 8358. https://doi.org/10.3390/s23208358






