Abstract
Multihop transmission is one of the important techniques to overcome the transmission coverage of each node in wireless sensor networks (WSNs). However, multihop transmission has a security issue due to the nature of a wireless medium. Additionally, the eavesdropper also attempts to interrupt the legitimate users’ transmission. Thus, in this paper, we study the secrecy performance of a multihop transmission under various eavesdropping attacks for WSNs. To improve the secrecy performance, we propose two node selection schemes in each cluster, namely, minimum node selection (MNS) and optimal node selection (ONS) schemes. To exploit the impact of the network parameters on the secrecy performance, we derive the closed-form expression of the secrecy outage probability (SOP) under different eavesdropping attacks. From the numerical results, the ONS scheme shows the most robust secrecy performance compared with the other schemes. However, the ONS scheme requires a lot of channel information to select the node in each cluster and transmit information. On the other side, the MNS scheme can reduce the amount of channel information compared with the ONS scheme, while the MNS scheme still provides secure transmission. In addition, the impact of the network parameters on the secrecy performance is also insightfully discussed in this paper. Moreover, we evaluate the trade-off of the proposed schemes between secrecy performance and computational complexity.
1. Introduction
The main focus of the next-generation network is on human-to-machine interactions and real-time communication by utilizing various tactile/haptic sensors and actuators that have a massive number with a small size but limited energy [1]. In 5G networks, the number of devices in a network can reach 1 million devices per square kilometer. Moreover, the connection density in 6G systems will reach devices/km [2]. However, a high density network is still prone to blockages when the destination is located in a far distance from the low-energy source, and there is no traffic distribution [3].
By using cooperative transmission, nodes in the network can be designated as relays that decode the received information from the source and retransmit the received information to the destination. Relay gives benefits to a communication network by extending its coverage, increasing the signal reception while reducing its energy consumption [4]. Due to these advantages, cooperative transmission has been implemented in various wireless systems [5,6,7]. Specifically, sensor nodes in wireless sensor networks (WSNs) collect confidential and sensitive information to a gateway or server through a cooperative multihop communication [8].
In practice, WSN with cooperative transmission is widely implemented in various industries, such as disaster mitigation, vehicular network, and battlefield. Security has become the main issue for the large-scale application of WSNs [9]. Due to the broadcast nature of wireless nodes, illegitimate users can easily wiretap data transmission. An eavesdropper can disconnect the transmission between sensor nodes or send a wrong message and cause an error. In multihop WSN where intermediate nodes directly access the message and retransmit it to the next hop, the end-to-end security for confidential messages is difficult to achieve if there is no countermeasure in the data transmission [10].
A higher number of nodes that relay confidential information can surely reach the destination in a more remote area, but it is also more susceptible to eavesdropping attack [11]. An illegitimate node that is located within the relays’ wireless range can overhear the broadcast messages [12]. The illegitimate node that only overhears the main channel transmission is known as a passive eavesdropper. On the other side, when the illegitimate node simultaneously transmits a jamming signal while overhearing the main channel transmission, it is known as an active eavesdropper and more advanced than a passive eavesdropper [13].
There are several considerable techniques to overcome an eavesdropper. The well-known technique is using data encryption in the network’s application layer. However, encryption needs careful key management and distribution in the source node and destination node. Encryption can also be deciphered by brute-force computing in an advanced eavesdropper node [14]. The new emerging technique for overcoming an eavesdropper is physical layer security (PLS), which exploits communications’ medium information to either enhance the main channel capacity, reduce the eavesdropper capacity, or both [15].
In this paper, we exploit the impact of secrecy performance on various eavesdropping attacks in multihop transmission. To enhance the secrecy performance, we propose two node selection schemes. The first node selection scheme can select the node in each cluster to minimize the eavesdropper channel. The second node selection scheme can select the node in each cluster to maximize the secrecy capacity. The main contributions of this paper can be summarized as follows:
- We exploit the impact of different eavesdropping attacks on the secure multihop transmission for WSNs. More specifically, in the passive eavesdropping attack, the eavesdropper only overhears legitimate users’ transmission. Different from the passive eavesdropping attack, the active eavesdropping attack can overhear each hop transmission and radiate the jamming signal to reduce the main channel condition at the same time. This scenario has not been studied in this literature.
- To enhance the secrecy performance, we propose two node selection schemes. The first scheme can select the node that minimizes the eavesdropper channel gains, called the minimal node selection (MNS) scheme. The second scheme, namely, the optimal node selection (ONS) scheme, can maximize the secrecy capacity of each cluster. We also consider the random node selection (RNS) scheme, which randomly selects the node in each cluster as a benchmark to compare the secrecy performance with the proposed schemes in a multicluster network.
- In order to find the relation between the system parameters and the secrecy performance, we derive a closed-form expression of the secrecy outage probability (SOP) with different eavesdropping attacks and the proposed node selection schemes. Specifically, we obtain the end-to-end SOP as the function of the number of clusters, number of nodes, target secrecy rate, main channel transmit SNR, and eavesdropper jamming SNR.
- From the numerical results, the active eavesdropper seriously affects secrecy performance compared with that of a passive eavesdropping attack. Additionally, ONS outperforms RNS and MNS secrecy performance in terms of SOP, while ONS requires a huge amount of channel information compared with that of other schemes.
The rest of this paper is organized as follows: Section 2 exploits previous works that motivate this research. Section 3 describes the system model of the proposed multihop relaying network, along with the passive and active scenarios of an eavesdropper attack and three node selection schemes. Section 4 analyzes the closed-form function of the system’s SOP for all cases as the combination of eavesdropper scenarios and node selection schemes. Section 5 presents the numerical results obtained from the derived analysis and simulations. Finally, Section 6 concludes the paper.
2. Related Works
Studies on PLS mostly focus on three main strategies: optimized resource allocation, secure beamforming/precoding, and antenna/node selection [16]. Duo et al. proposed joint UAV trajectory and power control optimization for securing UAV communications [17]. However, finding an optimal resource allocation in a wireless network is a complicated task that needs a strategic game to formulate the interactions between all nodes. Wang et al. obtained a Stackelberg equilibrium in multiantenna cellular networks through an iterative algorithm [18]. Luo and Yang in [19] formulated the cooperation between cellular user, D2D user, and active eavesdropper as a secrecy antijamming game. Moreover, Luo et al. in [20] considered a multitier Stackelberg game to model the complex interaction among the nodes.
Regarding secure beamforming in PLS, Lin et al. investigated three different hybrid beamforming architectures to maximize the joint secrecy performance and energy efficiency in satellite–terrestrial integrated networks (STIN) [21]. Furthermore, the authors in [22,23,24] considered joint beamforming and optimization for cooperative STIN transmission. However, since the optimization problem is mathematically intractable, the beamforming strategy needs an iterative algorithm.
In the field of precoding strategy in PLS, Liu et al. employed a source with multiantennas to transmit artificial noise (AN) and information signals as secure precoding in an unmanned aerial vehicle (UAV) network [25]. The authors in [26] sent AN via random and null-space precoders from a massive MIMO base station. Meanwhile, the authors in [27,28] applied cooperative jamming from a multiantenna relay and source to overcome an active eavesdropper. In addition, the authors in [29] used another user in z satellite–terrestrial network as a friendly jammer. However, cooperative jamming requires an additional antenna/node and precoders to transmit the jamming signal aside from the information signal.
In a high-density network, a node selection strategy becomes the common technique to secure the cooperative transmission. The authors in [30,31,32] implemented relay selection to overcome an active eavesdropper, but only in dual-hop transmissions. On the other hand, a multihop network with a larger number of nodes makes the node selection process more complex. Shim et al. studied node selection for a source cluster and relay cluster in [33], while in [34], the authors utilized node selection for a multihop relaying network with power beacons. However, these two studies only studied the secrecy performance under a passive eavesdropper attack, while an active eavesdropper is more destructive to the system performance than a passive eavesdropper.
The authors in [35] proposed a node selection scheme to improve the end-to-end throughput without an eavesdropping attack. The authors in [36] proposed a train-to-train multihop transmission and next relay selection scheme. However, this work did not consider an eavesdropping attack. In [37], the authors exploited the outage performance for short packet communication in a multihop transmission with wireless energy transfer. This work also did not consider an eavesdropping attack. As can be observed, in the multihop transmission context, the improvements of secrecy performance and system throughput are studied. However, the study of a secure multihop transmission under active eavesdropping using a node selection strategy has not been conducted yet.
Different from previous works in [34,35,36,37] that studied various strategies to improve multihop transmission performance without considering an active eavesdropper attack, we propose a cooperative multihop relaying network in confronting a passive and active eavesdropper using node selection schemes. Other works in [30,31,32] only studied the secrecy performance of a dual-hop transmission under active eavesdropping attacks, while with the higher number of node clusters, the end-to-end security is harder to be deployed in multicluster WSNs [10].
3. System Model
3.1. System Description
Let us consider a multihop transmission in WSN consisting of K clusters with N nodes in every cluster, as depicted in Figure 1. The desired source (i-th node) in the first cluster () transmits confidential information to a destination () through clusters of relay () as the main channel of cooperative transmission. We assume that all nodes in the main channel transmission have a single antenna. Meanwhile, the eavesdropper can overhear the legitimate users’ transmission. If the eavesdropper is operated on the passive mode, the eavesdropper only wiretaps the confidential message since the eavesdropper is equipped with a single antenna. However, when the eavesdropper is operated on the active mode, the eavesdropper wiretaps the confidential message and radiates the jamming signal by using two antennas at the same time. In this paper, we exploit the impact of two eavesdropping “scenarios”, called passive and active. Additionally, we propose node selection “schemes” to improve the system secrecy.
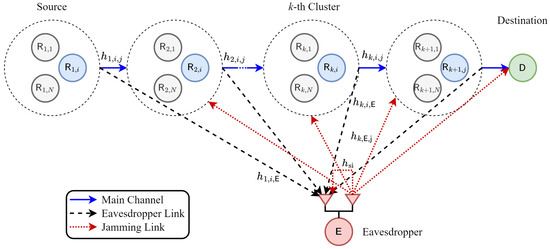
Figure 1.
The proposed system model of the multihop transmission.
3.2. Scenario 1—Passive Eavesdropper
The received signal from the i-th node in the k-th cluster () at the j-th node in the next cluster () with a passive eavesdropper can be described as
where and denote the transmit signal and power at the i-th node in the k-th cluster, respectively. denotes the channel coefficient of the link. The channel noise at is denoted by as an additive white Gaussian noise (AWGN) model with zero mean and variance . The signal-to-noise ratio (SNR) of the main channel at the k-th hop under a passive eavesdropper attack can be described as
The received signal at that only overhears the k-th hop data transmission can be expressed as
where indicates the channel coefficient of the link. indicates the channel noise at with an AWGN model and variance . The SNR of the eavesdropper link with a passive mode at the k-th hop can be expressed as
3.3. Scenario 2—Active Eavesdropper
In the active attack, the received signal at the k-th hop data transmission is interfered by the jamming signal from , which can be described as
where denotes the channel coefficient of the link. The jamming signal and power from are denoted by and , respectively. The signal-to-interference-plus-noise ratio (SINR) of the main channel at the k-th hop can be described as
At , the received signal is affected by the noise of the channel link and the self-interference (SI) from its jamming signal. The received signal at can be expressed as
where indicates the channel coefficient of the SI link. After different stages of mitigation, the residual SI (RSI) can be decreased to the noise level [38]. The observation with an RSI component at can be expressed as
The SINR of the active eavesdropper at the k-th hop transmission can be expressed as
3.4. The Proposed Node Selection Scheme
3.4.1. Random Node Selection (RNS) Scheme
In this scheme, RNS selects a relay node randomly in each cluster without considering the channel information in every node. The SNR of the k-th hop main channel transmission with RNS and a passive eavesdropper can be described as
Meanwhile, the SNR of the passive eavesdropper link at the k-th hop can be written as
The SINR of the k-th hop main channel transmission with RNS and an active eavesdropper can be described as
Meanwhile, the SINR of the active eavesdropper link at the k-th hop can be written as
We consider this scheme as a benchmark to compare the performance result with the following proposed schemes.
3.4.2. Minimum Node Selection (MNS) Scheme
We propose a minimum selection process to select a relay node in every cluster. The selection criteria of the node with the minimum eavesdropper’s channel gain can be expressed as
The SNR of the k-th hop main channel transmission with minimum selection in the presence of a passive eavesdropper can be expressed as
where denotes the selected node that has already chosen in the next hop. On the other side, the SNR of the passive eavesdropper link at the k-th hop becomes
The SINR of the k-th hop main channel transmission with minimum selection and an active eavesdropper can be expressed as
Meanwhile, the SINR of the active eavesdropper link at the k-th hop becomes
3.4.3. Optimal Node Selection (ONS) Scheme
In this selection process, we select the relay node in every cluster that can maximize the secrecy capacity of the system. The main and eavesdropper channels are both considered in an optimal selection process, which can be described by
The SNR of the k-th hop main channel transmission with ONS in the presence of a passive eavesdropper can be written as
In addition, the SNR of the passive eavesdropper link at the k-th hop can be expressed as
The SINR of the k-th hop main channel transmission with ONS in the presence of an active eavesdropper can be written as
Lastly, the SINR of the active eavesdropper link at the k-th hop can be expressed as
As can be seen, the SNR models with the proposed scheme and with passive eavesdropping are similar to the well-known selection scheme. However, as can be seen in (17), (18), (22) and (23), the SINR models with the proposed scheme and with an active eavesdropping attack are different since they have a jamming signal, which cause the derivation complexity that is very challenging. Thus, the proposed node selection schemes still have novel contributions.
4. Secrecy Outage Performance Analysis
The system’s secrecy outage probability (SOP) is defined as the probability in which the system secrecy capacity is less than the target secrecy rate (), which can be written as
where . The SOP of the system is associated with the probability that the system cannot securely decode the information [39]. In other words, part of the secret information can be decoded by an eavesdropper. The SOP analysis of the proposed schemes will be presented in six different cases as the combination of the selection scheme and eavesdropper scenario that is shown in Table 1.

Table 1.
Selection and scenario combinations.
We assume that all channels in the system undergo Rayleigh fading, in which the channel gain from to () follows an exponential distribution with mean . denotes the Euclidean distance between and , while represents the reference distance, and represents the path-loss exponent. For convenience, we define the channel gains as , , and . Without loss of generality, we assume = and . We can further suppose = and = .
4.1. Case I: Random Node Selection Scheme under Passive Eavesdropper
From (24), the SOP with case I can be further written as
where . By relying on the channel characteristic of each link with an RNS scheme, the SOP with case I can be rewritten as
In order to further calculate , (26) can be re-expressed as
in (27) can be rewritten as
Relying on the fact [40] (Equation 3.310), i.e., , and can be, respectively, re-expressed as
By plugging and into (28), can be further expressed as
By substituting (31) into (27) and after some mathematical steps, the closed-form expression for the SOP under case I can be obtained as
4.2. Case II: Random Node Selection Scheme under Active Eavesdropper
The SOP under case II can be further written as
From (12) and (13), the SOP of case II can be rewritten as
in (34) can be re-expressed as
in (35) can be rewritten as
In order to further calculate , we rely on the fact [40] (Equation 3.310). and in (36) can be, respectively, obtained as
Plugging and into , (36) can be rewritten as
By substituting into (35) and after some algebraic steps, can be further expressed as
In order to further express , we rely on the fact [40] (Equation 3.310) and [40] (Equation 3.352.4). and in (40) can be, respectively, obtained as
where , , and mean the exponential integral function [40] (Equation 8.211.1). Again, plugging and into (40), can be obtained as
After some algebraic steps, the closed-form expression for the SOP under case II () can be obtained as
4.3. Case III: Minimal Node Selection with Passive Eavesdropper
The SOP with case III can be further written as
From (15) and (16), the SOP under case III can be rewritten as
As can be seen, the events of the probability (46) are not mutually exclusive since it includes . Therefore, by conditioning = y, in (46) can be re-expressed as
The following lemmas will help to further calculate . First, Lemma 1 helps to obtain the probability of one relay node, which is selected inside a cluster.
Lemma 1.
The probability of one node selected among N nodes can be expressed as
Proof.
The probability of a node selected based on the criteria in (14) can be expressed as
By conditioning and assuming that nodes are independent, we can calculate the probability as
Using [40] (Equation 3.310), we can obtain the probability of a node selected as in (48). The proof of Lemma 1 is concluded. □
The statistical characteristic of the channel gain from the selected node to the next hop will be presented in the following lemma.
Lemma 2.
Given the selected node , the CDF and pdf of can be, respectively, expressed as
Proof.
Since the MNS scheme at every hop selects the node in a cluster that minimizes the eavesdropper’s channel gain, the statistical characteristic of will be presented in the following lemma.
Lemma 3.
Let ; the CDF and pdf of can be, respectively, expressed as
Proof.
By utilizing (48), (51), and (55), in (47) can be rewritten as
Using [40] (Equation 3.310), and can be further expressed as
After plugging (60) and (61) into (59), in (59) can be further expressed as
By substituting into (46) and after some mathematical calculation steps, the SOP with case III can be obtained as
4.4. Case IV: Minimal Node Selection with Active Eavesdropper
The SOP of the system with minimum selection in the presence of an active eavesdropper can be written as
As can be seen in (64), the events of the probability (64) are not mutually exclusive since they include . Thus, by conditioning = y, in (64) can be further expressed as
In order to further represent , can be expressed as
Relying on the fact [40] (Equation 3.310), and in (66) can be, respectively, obtained as
where . When plugging and into , (66) can be rewritten as
By substituting into (65) and after some algebraic steps, can be re-expressed as
Using the fact [40] (Equation 3.310), can be obtained as
In order to further expressed , we utilize the fact [40] (Equation 3.352.4). can be re-expressed as
where . After plugging and into (70), can be obtained as
By inserting into (64), we obtain the SOP of case IV as
4.5. Case V: Optimal Node Selection with Passive Eavesdropper
According to the definition of the SOP in (24), the SOP under case V can be further written as
After some algebraic operations, the SOP under case V can be expressed as
in (76) can be rewritten as
Relying on the fact [40] (Equation 3.310), and can be, respectively, obtained as
By plugging and into (77), can be further expressed as
By substituting (80) into (76) and using the binomial theorem [40] (Equation 1.111), we can obtain the closed-form expression for the SOP with case V, which can be expressed as
4.6. Case VI: Optimal Node Selection with Active Eavesdropper
From (24), the SOP with case 6 can be further written as
The SOP in (82) can be re-expressed as
in (83) can be given by
In order to further calculate (84), can be written as
Relying on the fact [40] (Equation 3.310), and in (85) can be, respectively, expressed as
where is defined as (68). Again, when plugging and into (85), can be rewritten as
By substituting into (84) and after some algebraic steps, can be re-expressed as
Using the fact [40] (Equation 3.310), can be obtained as
In order to further express , we utilize the fact [40] (Equation 3.352.4). can be re-expressed as
where . After plugging and into (89), can be obtained as
By plugging into (83) and using the binomial theorem [40] (Equation 1.111), we obtain the SOP of case VI as
5. Performance Evaluations
In this section, we exploit the impact of the active eavesdropping attack and the proposed node selection schemes on the secrecy performance. Unless otherwise stated, the simulation parameters are presented in Table 2.

Table 2.
Simulation parameters.
Figure 2 shows the effect of on the SOP. As can be seen, when the transmitted SNR increases, the SOP is decreased. It can be explained by the SNR of the main channel, which is improved, as well as that of the eavesdropper channel. However, the impact of the SNR of the main channel is more than that of the eavesdropper channel. Additionally, when the eavesdropper generates a jamming signal, i.e., active eavesdropping attack, the SOP is higher than the passive eavesdropping attack. The reason is that the jamming signal can degrade the SINR of the main channel, which leads to reducing the difference between the main channel and eavesdropper channel capacities. In order to counteract the eavesdropper attack, different from the other node selection schemes that select the node randomly or utilize only eavesdropper channel information, the proposed ONS scheme uses both main channel and eavesdropper channel information. Thus, the proposed ONS scheme shows the most robust secrecy performance compared with that of other node selection schemes. The comparison between simulation and analytical results is in good agreement, validating the correctness of our derivation approaches. Hence, the following results only provide the theoretical results.
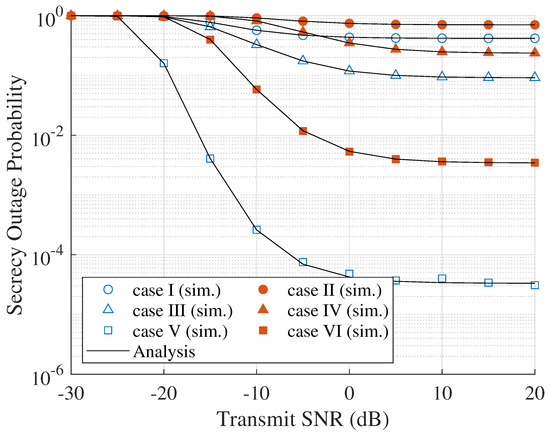
Figure 2.
SOP versus node transmit SNR ().
Figure 3 shows the effect of towards the SOP of a cooperative multihop relaying network. As can be seen, the SOP for passive eavesdropper scenarios is constant. It can be explained by the fact that the eavesdropper does not radiate a jamming signal, only overhearing the legitimate users’ transmission. In contrast, the active eavesdropper radiates the jamming signal. Thus, when the jamming SNR increases, the SOP with case II, case IV, and case VI is increased. It means that the difference between main channel and eavesdropper channel capacities is reduced. In Figure 3, ONS has the lowest SOP among all the node selection schemes because ONS selects a node in every cluster that gives the maximum secrecy rate. Therefore, the probability of the system secrecy being outage in an ONS scheme becomes minimum. On the contrary, RNS selects a node randomly, and MNS selects a node only based on the eavesdropper link that makes low system secrecy capacity and high SOP.
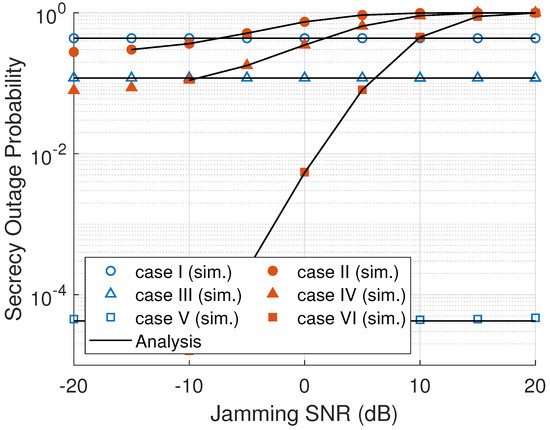
Figure 3.
SOP versus eavesdropper’s jamming SNR ().
Figure 4 shows the effect of on the SOP. As shown in Figure 4, with the higher target secrecy data rate, the SOP is increased. The reason is that a higher target secrecy rate correlates with a higher threshold level of the system secrecy being outage. Therefore, the probability of the outage event becomes higher. In Figure 4, a passive eavesdropper scenario produces a better SOP than an active scenario because the system secrecy in a passive attack is higher; then the probability of an outage event is lower. Once again, ONS has the most robust SOP between all node selection schemes in Figure 4 because ONS utilizes both main channel and eavesdropper channel information to select a node. Case V with an ONS scheme and passive eavesdropper scenario has the lowest SOP among all cases. One of the reasons is that ONS selects the best node in every cluster that maximizes the secrecy capacity rate. Furthermore, the passive mode of an eavesdropper allows a less significant attack to the main channel capacity.
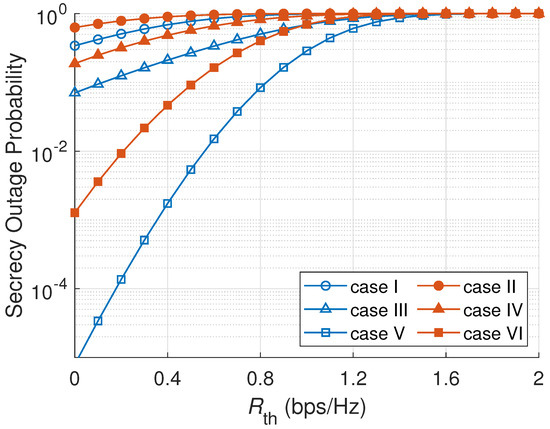
Figure 4.
SOP versus target secrecy data rate ().
Figure 5 illustrates the relation between the SOP and N. As can be seen, the number of nodes in a cluster does not have an impact on the SOP of an RNS scheme. An RNS scheme’s SOP in cases I and II is constant for all N values because RNS only selects one node randomly regardless of many nodes that can be chosen. ONS and MNS schemes, on the other side, have a lower SOP when the number of nodes per cluster increases because there are more nodes that can be selected to relay the confidential information. In a cluster with more nodes, ONS and MNS schemes have more possibility to choose a node that has better secrecy capacity; then the probability of the secrecy being outage declines. Additionally, an active eavesdropper scenario yields a higher SOP due to more attacks on the main channel capacity than a passive eavesdropper scenario. An active eavesdropper radiates a jamming signal aiming to harm the main channel transmission. Hence, an active eavesdropper is more destructive.
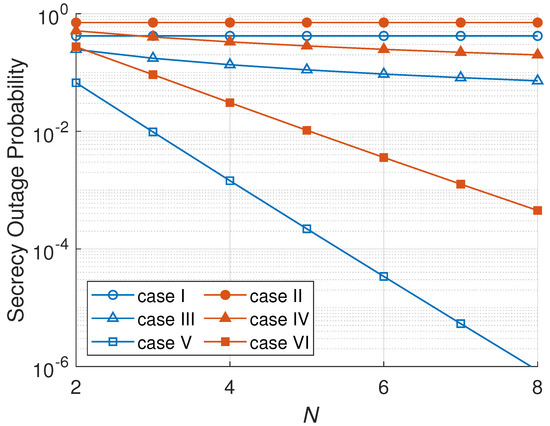
Figure 5.
SOP versus number of nodes per cluster (N).
Figure 6 illustrates the impact of K on the SOPs. The SOP is decreased when the number of hops increases because there are more hops that can be chosen as the minimum system secrecy capacity rate. This corresponds to (24), where the SOP is inversely proportional to the number of hops. As can be observed more from Figure 6, a passive eavesdropper scenario produces a lower SOP due to its harmless attack on the main channel capacity than an active mode. The passive eavesdropping scenarios do not radiate a jamming signal, different from the active eavesdropping scenario. In Figure 6, an ONS scheme has the lowest SOP among all the node selection schemes since ONS selects the best node in every cluster that gives the maximum secrecy capacity based on the main channel and eavesdropper channel information. On the other hand, RNS selects a node randomly and MNS selects a node only based on the minimum eavesdropper channel gain that cannot increase the secrecy capacity significantly.
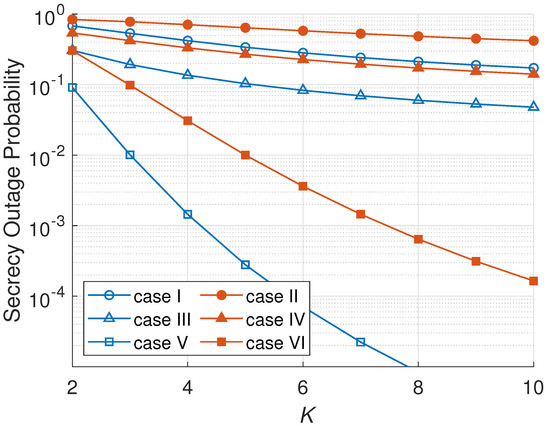
Figure 6.
SOP versus number of hops (K).
In order to further analyze the secrecy performance of the considered multihop transmission system, we calculate the system secrecy throughput, which is mathematically defined as [38]
Secrecy throughput is defined as the achievable secrecy rate of the system [41]. Figure 7 presents the system’s secrecy throughput as a function of . The increment of the node transmit SNR results in the increase in the system’s secrecy throughput. High SNR in the relay nodes increases the main channel capacity higher than the eavesdropper channel capacity because of the eavesdropping counteracting at the node selection process in every cluster. This eventually increases the overall system secrecy rate. The ONS scheme in Figure 7 has the highest secrecy throughput since ONS selects a node with the maximum secrecy capacity in every cluster. On the other hand, an RNS scheme has the lowest secrecy throughput because RNS selects a node randomly without considering the main channel and eavesdropper channel information. Active eavesdropping scenarios bring more destruction in the system secrecy throughput than passive eavesdropping scenarios due to the transmitted jamming signal that degrades the main channel capacity rate.
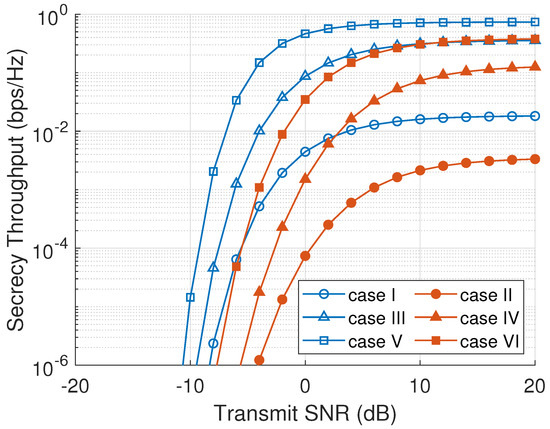
Figure 7.
Secrecy throughput versus node transmit SNR ().
Figure 8 presents the system’s secrecy throughput as a function of . As can be seen, a passive scenario of an eavesdropper in cases I, III, and V has a constant secrecy throughput because a passive eavesdropper only overhears the main channel information without transmitting any jamming signal. Cases II, IV, and VI under an active eavesdropper attack has a declination of secrecy throughput as a jamming SNR is increasing, since more jamming is interfering the main channel transmission, and eventually, the difference between main channel and eavesdropper channel capacities is decreasing. Case II with an RNS scheme has the lowest secrecy throughput because a node in every cluster is chosen randomly regardless of its channel information. However, the utilization of an ONS scheme can increase the secrecy throughput higher than RNS and MNS, since ONS selects the best node with the maximum secrecy capacity based on both main channel and eavesdropper channel information.
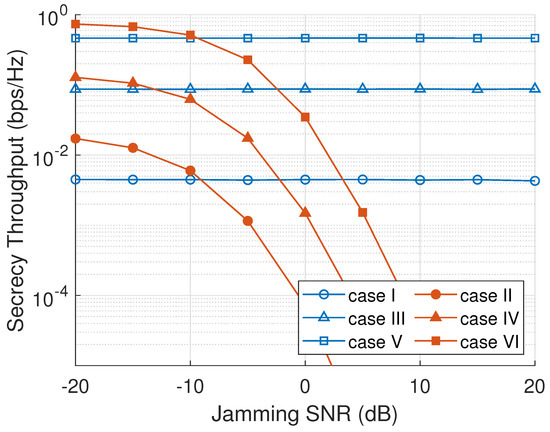
Figure 8.
Secrecy throughput versus eavesdropper jamming SNR ().
Finally, we turn our attention to the complexity order. The complexity order is defined as the amount of channel information to select the node and transmit a signal. Table 3 presents the complexity order for every case of a system. Since an RNS scheme selects the node randomly, the RNS scheme does not utilize the channel information at the node selection step. Thus, the RNS scheme shows the lowest complexity order among the considered schemes. An MNS scheme only utilizes the eavesdropper channel information to select the node in each cluster, so the complexity for the selection process grows as . An ONS scheme utilizes both main channel and eavesdropper channel information to select a node in every cluster. Thus, an ONS scheme requires the most channel information among the considered schemes.

Table 3.
Complexity order of the schemes.
Figure 9 visualizes the trade-off between the SOP and complexity as a function of K. As can be seen, when the number of hops increases, the complexity order of the proposed node selection schemes is increased, while the SOP is decreased. More specifically, the RNS scheme’s complexity order increases linearly, while the SOP is decreased. On the other hand, the ONS scheme’s complexity order increases when the number of hops increases, while the SOP is decreased significantly. Finally, the complexity order of the MNS scheme is slightly increased, while the SOP of the MNS scheme is decreased and still providing secure transmission. From these phenomena, complexity order and SOP have a trade-off. However, though the complexity order of an ONS scheme is increased, the secrecy performance is significantly improved. Thus, we can conclude that the ONS scheme has advantage against complexity order.
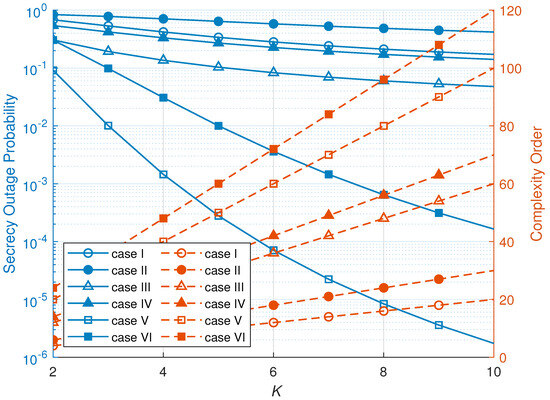
Figure 9.
Complexity versus number of hops (K).
6. Conclusions
This paper studied the impact of the eavesdropping attack on the multihop transmission system for sensor networks. More specifically, we exploited the active and passive eavesdropping attacks. The active eavesdropping attack can overhear the legitimate users’ transmission and radiate the jamming signal to degrade the main channel condition. The passive eavesdropping attack only overhears the legitimate users’ transmission. As a counteraction, in order to protect the confidential message against various eavesdropping attacks, we proposed the node selection schemes called MNS scheme and ONS scheme. Since the MNS scheme only required the eavesdropper channel information to select the node in each cluster, it had low complexity and slightly improved the secrecy performance. Meanwhile, the ONS scheme selected the node in each cluster to maximize the secrecy capacity. Thus, the ONS scheme showed high complexity and significantly improved the secrecy performance. We derived the closed-form expression for the SOP with a different eavesdropping attack and node selection scheme. Numerical results showed that an active eavesdropping attack is more destructive compared with a passive attack since an active eavesdropper generated the jamming signal. The ONS scheme utilized both the main channel and eavesdropper channel to select the node in each cluster, which brought the most robust secrecy performance compared with the other node selection schemes. Additionally, through various numerical results, the proposed node selection scheme and different eavesdropping attack on the secrecy performance were discussed. In order to expand this work, we try to develop the secure routing protocol that utilizes the physical layer security concept and blockchain to protect a confidential packet against a sniffing attack.
Author Contributions
Conceptualization, Y.T., R.H.Y.P., K.S. and B.A.; methodology, Y.T., K.S. and B.A.; software, Y.T., R.H.Y.P. and K.S.; validation, Y.T., R.H.Y.P., K.S. and B.A.; formal analysis, Y.T.; investigation, Y.T. and B.A.; resources, B.A.; writing—original draft preparation, Y.T.; writing—review and editing, R.H.Y.P., K.S. and B.A.; visualization, Y.T., K.S. and B.A.; supervision, B.A.; project administration, B.A.; funding acquisition, B.A. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by National Research Foundation of Korea (NRF) grant funded by the Korean government (MSIT) (NRF-2022R1A2B5B01001190).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Sharma, S.K.; Woungang, I.; Anpalagan, A.; Chatzinotas, S. Toward Tactile Internet in beyond 5G Era: Recent Advances, Current Issues, and Future Directions. IEEE Access 2020, 8, 56948–56991. [Google Scholar] [CrossRef]
- Tataria, H.; Shafi, M.; Molisch, A.F.; Dohler, M.; Sjoland, H.; Tufvesson, F. 6G Wireless Systems: Vision, Requirements, Challenges, Insights, and Opportunities. Proc. IEEE 2021, 109, 1166–1199. [Google Scholar] [CrossRef]
- Lee, Y.L.; Qin, D.; Wang, L.C.; Sim, G.H. 6G Massive Radio Access Networks: Key Applications, Requirements and Challenges. IEEE Open J. Veh. Technol. 2021, 2, 54–66. [Google Scholar] [CrossRef]
- Mao, Z.; Hu, F.; Sun, D.; Ma, S.; Liu, X. Fairness-Aware Intragroup Cooperative Transmission in Wireless Powered Communication Networks. IEEE Trans. Veh. Technol. 2020, 69, 6463–6472. [Google Scholar] [CrossRef]
- Tuan, N.T.; Kim, D.S.; Lee, J.M. On the performance of cooperative transmission schemes in industrial wireless sensor networks. IEEE Trans. Industr. Inform. 2018, 14, 4007–4018. [Google Scholar] [CrossRef]
- El-Banna, A.A.; Wu, K.; Elhalawany, B.M. Opportunistic Cooperative Transmission for Underwater Communication Based on the Water’s Key Physical Variables. IEEE Sens. J. 2020, 20, 2792–2802. [Google Scholar] [CrossRef]
- Ji, B.; Han, Y.; Wang, Y.; Cao, D.; Tao, F.; Fu, Z.; Li, P.; Wen, H. Relay Cooperative Transmission Algorithms for IoV under Aggregated Interference. IEEE Trans. Intell. Transp. Syst. 2022, 23, 9712–9725. [Google Scholar] [CrossRef]
- Adil, M.; Khan, R.; Almaiah, M.A.; Al-Zahrani, M.; Zakarya, M.; Amjad, M.S.; Ahmed, R. MAC-AODV Based Mutual Authentication Scheme for Constraint Oriented Networks. IEEE Access 2020, 8, 44459–44469. [Google Scholar] [CrossRef]
- Li, B.; Zou, Y.; Zhu, J.; Cao, W. Impact of hardware impairment and co-channel interference on security-reliability trade-off for wireless sensor networks. IEEE Trans. Wirel. Commun. 2021, 20, 7011–7025. [Google Scholar] [CrossRef]
- Mehmood, A.; Umar, M.M.; Song, H. ICMDS: Secure inter-cluster multiple-key distribution scheme for wireless sensor networks. Ad Hoc Netw. 2017, 55, 97–106. [Google Scholar] [CrossRef]
- Hieu, T.D.; Duy, T.T.; Kim, B.S. Performance Enhancement for Multihop Harvest-to-Transmit WSNs with Path-Selection Methods in Presence of Eavesdroppers and Hardware Noises. IEEE Sens. J. 2018, 18, 5173–5186. [Google Scholar] [CrossRef]
- Nguyen, V.L.; Lin, P.C.; Cheng, B.C.; Hwang, R.H.; Lin, Y.D. Security and Privacy for 6G: A Survey on Prospective Technologies and Challenges. IEEE Commun. Surv. Tutor. 2021, 23, 2384–2428. [Google Scholar] [CrossRef]
- Ari, N.; Thomos, N.; Musavian, L. Active Eavesdropping in Short Packet Communication: Average Secrecy Throughput Analysis. In Proceedings of the 2021 IEEE International Conference on Communications Workshops, Montreal, Canada, 14–23 June 2021; pp. 1–6. [Google Scholar]
- Wu, Y.; Khisti, A.; Xiao, C.; Caire, G.; Wong, K.K.; Gao, X. A Survey of Physical Layer Security Techniques for 5G Wireless Networks and Challenges Ahead. IEEE J. Sel. Areas Commun. 2018, 36, 679–695. [Google Scholar] [CrossRef]
- Hamamreh, J.M.; Furqan, H.M.; Arslan, H. Classifications and Applications of Physical Layer Security Techniques for Confidentiality: A Comprehensive Survey. IEEE Commun. Surv. Tutor. 2019, 21, 1773–1828. [Google Scholar] [CrossRef]
- Wang, D.; Bai, B.; Zhao, W.; Han, Z. A Survey of Optimization Approaches for Wireless Physical Layer Security. IEEE Commun. Surv. Tutor. 2019, 21, 1878–1911. [Google Scholar] [CrossRef]
- Duo, B.; Luo, J.; Li, Y.; Hu, H.; Wang, Z. Joint trajectory and power optimization for securing UAV communications against active eavesdropping. China Commun. 2021, 18, 88–99. [Google Scholar] [CrossRef]
- Wang, W.; Teh, K.C.; Li, K.H.; Luo, S. On the Impact of Adaptive Eavesdroppers in Multi-Antenna Cellular Networks. IEEE Trans. Inf. Forensics Secur. 2018, 13, 269–279. [Google Scholar] [CrossRef]
- Luo, Y.; Yang, Y. Secrecy Anti-jamming Game Learning in D2D Underlay Cellular Networks with an Active Eavesdropper. In Proceedings of the 2018 IEEE 18th International Conference on Communication Technology (ICCT), Chongqing, China, 8–11 October 2018; pp. 446–451. [Google Scholar]
- Luo, Y.; Feng, Z.; Jiang, H.; Yang, Y.; Huang, Y.; Yao, J. Game-theoretic learning approaches for secure D2D communications against full-duplex active eavesdropper. IEEE Access 2019, 7, 41324–41335. [Google Scholar] [CrossRef]
- Lin, Z.; Lin, M.; Champagne, B.; Zhu, W.P.; Al-Dhahir, N. Secrecy-Energy Efficient Hybrid Beamforming for Satellite-Terrestrial Integrated Networks. IEEE Trans. Commun. 2021, 69, 6345–6360. [Google Scholar] [CrossRef]
- Lin, Z.; Lin, M.; Wang, J.B.; Cola, T.D.; Wang, J. Joint Beamforming and Power Allocation for Satellite-Terrestrial Integrated Networks with Non-Orthogonal Multiple Access. IEEE J. Sel. Top. Signal Process. 2019, 13, 657–670. [Google Scholar] [CrossRef]
- Lin, Z.; Lin, M.; Cola, T.D.; Wang, J.B.; Zhu, W.P.; Cheng, J. Supporting IoT with Rate-Splitting Multiple Access in Satellite and Aerial-Integrated Networks. IEEE Internet Things J. 2021, 8, 11123–11134. [Google Scholar] [CrossRef]
- Lin, Z.; Niu, H.; An, K.; Wang, Y.; Zheng, G.; Chatzinotas, S.; Hu, Y. Refracting RIS-Aided Hybrid Satellite-Terrestrial Relay Networks: Joint Beamforming Design and Optimization. IEEE Trans. Aerosp. Electron. Syst. 2022, 58, 3717–3724. [Google Scholar] [CrossRef]
- Liu, C.; Lee, J.; Quek, T.Q. Safeguarding uav communications against full-duplex active eavesdropper. IEEE Trans. Wirel. Commun. 2019, 18, 2919–2931. [Google Scholar] [CrossRef]
- Kudathanthirige, D.; Timilsina, S.; Baduge, G.A.A. Secure Communication in Relay-Assisted Massive MIMO Downlink with Active Pilot Attacks. IEEE Trans. Inf. Forensics Secur. 2019, 14, 2819–2833. [Google Scholar] [CrossRef]
- Lu, X.; Yang, W.; Guan, X.; Cai, Y. DCE-Based Secure Transmission for Massive MIMO Relay System against Active Eavesdropper. IEEE Trans. Veh. Technol. 2020, 69, 13045–13059. [Google Scholar] [CrossRef]
- Abdullah, Z.; Chen, G.; Abdullah, M.A.; Chambers, J.A. Enhanced Secrecy Performance of Multihop IoT Networks with Cooperative Hybrid-Duplex Jamming. IEEE Trans. Inf. Forensics Secur. 2021, 16, 161–172. [Google Scholar] [CrossRef]
- Bouabdellah, M.; Bouanani, F.E. A PHY Layer Security of a Jamming-Based Underlay Cognitive Satellite-Terrestrial Network. IEEE Trans. Cogn. Commun. Netw. 2021, 7, 1266–1279. [Google Scholar] [CrossRef]
- Vahidian, S.; Hatamnia, S.; Champagne, B. On the Security Analysis of a Cooperative Incremental Relaying Protocol in the Presence of an Active Eavesdropper. IEEE Access 2019, 7, 181812–181828. [Google Scholar] [CrossRef]
- Zhou, H.; He, D.; Wang, H.; Yang, D. Optimal Relay Selection with a Full-duplex Active Eavesdropper in Cooperative Wireless Networks. In Proceedings of the 2019 IEEE 89th Vehicular Technology Conference (VTC2019-Spring), Kuala Lumpur, Malaysia, 28 April–1 May 2019; pp. 1–5. [Google Scholar]
- Liu, J.; Xu, X.; Han, S.; Zhang, Z.; Liu, C. Hybrid relay selection and cooperative jamming scheme for secure communication in healthcare-IoT. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), Nanjing, China, 29 March–1 April 2021; pp. 1–7. [Google Scholar]
- Shim, K.; Do, N.T.; An, B. Performance analysis of physical layer security of opportunistic scheduling in multiuser multirelay cooperative networks. Sensors 2017, 17, 377. [Google Scholar] [CrossRef]
- Shim, K.; Nguyen, T.V.; An, B. Exploiting opportunistic scheduling schemes and wpt-based multi-hop transmissions to improve physical layer security in wireless sensor networks. Sensors 2019, 19, 5456. [Google Scholar] [CrossRef]
- Nguyen, T.V.; Do, T.N.; Bao, V.N.Q.; Costa, D.B.d.; An, B. On the Performance of Multihop Cognitive Wireless Powered D2D Communications in WSNs. IEEE Trans. Veh. Technol. 2020, 69, 2684–2699. [Google Scholar] [CrossRef]
- Ma, S.; Li, M.; Yang, R.; Sun, Y.; Wang, Z.; Si, P. Next-Hop Relay Selection for Ad Hoc Network-Assisted Train-to-Train Communications in the CBTC System. Sensors 2023, 23, 5883. [Google Scholar] [CrossRef] [PubMed]
- Nguyen, T.V.; Nguyen, V.D.; da Costa, D.B.; Huynh-The, T.; Hu, R.Q.; An, B. Short-Packet Communications in Multihop Networks with WET: Performance Analysis and Deep Learning-Aided Optimization. IEEE Trans. Wirel. Commun. 2023, 22, 439–456. [Google Scholar] [CrossRef]
- Shim, K.; Do, T.N.; Nguyen, T.V.; Costa, D.B.D.; An, B. Enhancing PHY-Security of FD-Enabled NOMA Systems Using Jamming and User Selection: Performance Analysis and DNN Evaluation. IEEE Internet Things J. 2021, 8, 17476–17494. [Google Scholar] [CrossRef]
- Ai, Y.; Mathur, A.; Verma, G.D.; Kong, L.; Cheffena, M. Comprehensive Physical Layer Security Analysis of FSO Communications over Málaga Channels. IEEE Photon. J. 2020, 12, 7906617. [Google Scholar] [CrossRef]
- Gradshteyn, I.; Ryzhik, I. Table of Integrals, Series, and Products Seventh Edition; Elsevier Academic Press: Amsterdam, The Netherlands, 2007. [Google Scholar]
- Lyu, J.; Wang, H.M.; Huang, K.W. Physical Layer Security in D2D Underlay Cellular Networks with Poisson Cluster Process. IEEE Trans. Commun. 2020, 68, 7123–7139. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).