Digital Transformation and Cybersecurity Challenges for Businesses Resilience: Issues and Recommendations
Abstract
1. Introduction
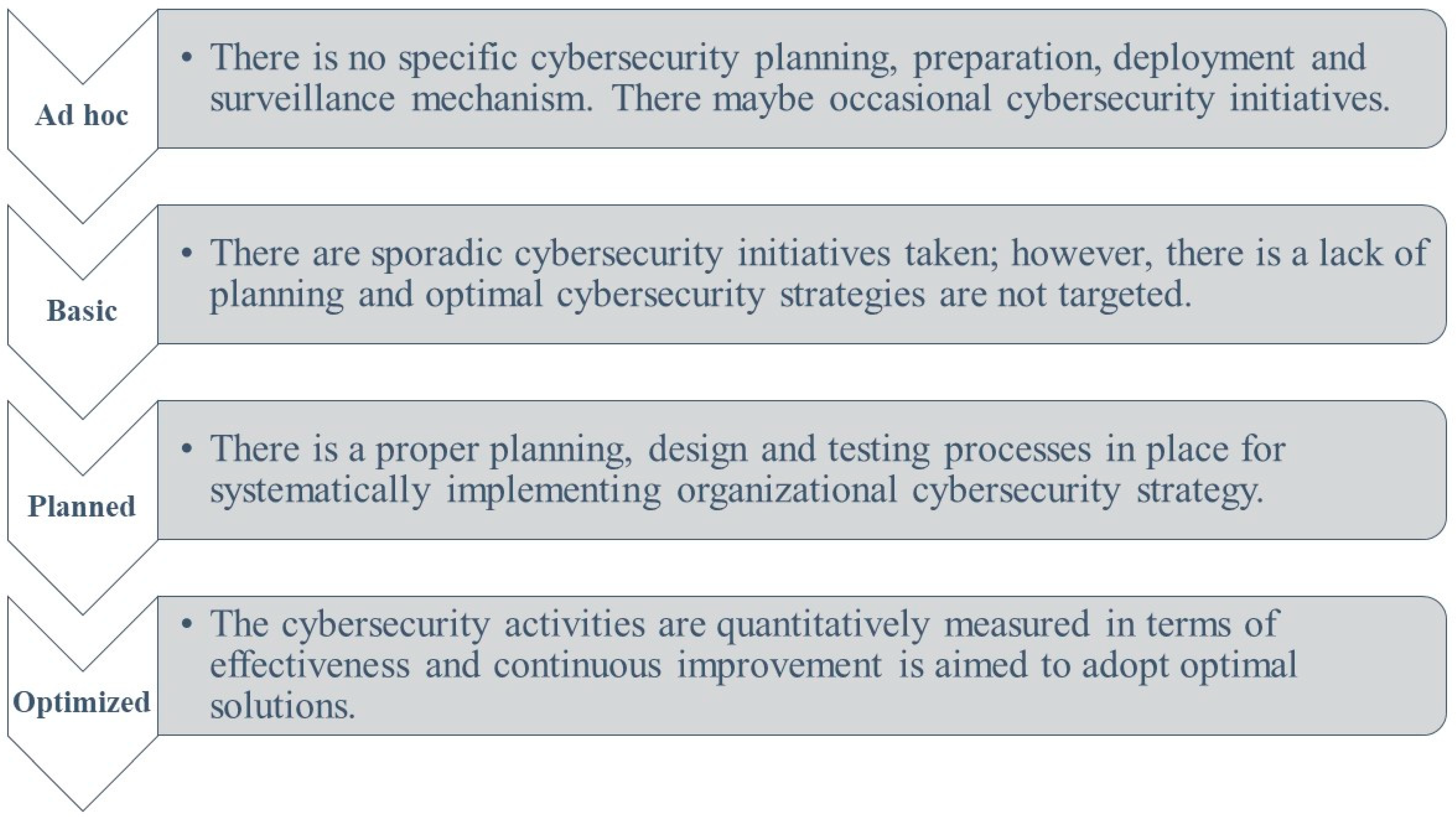
2. Materials and Methods
- The paper should be relevant to digital business and cybersecurity.
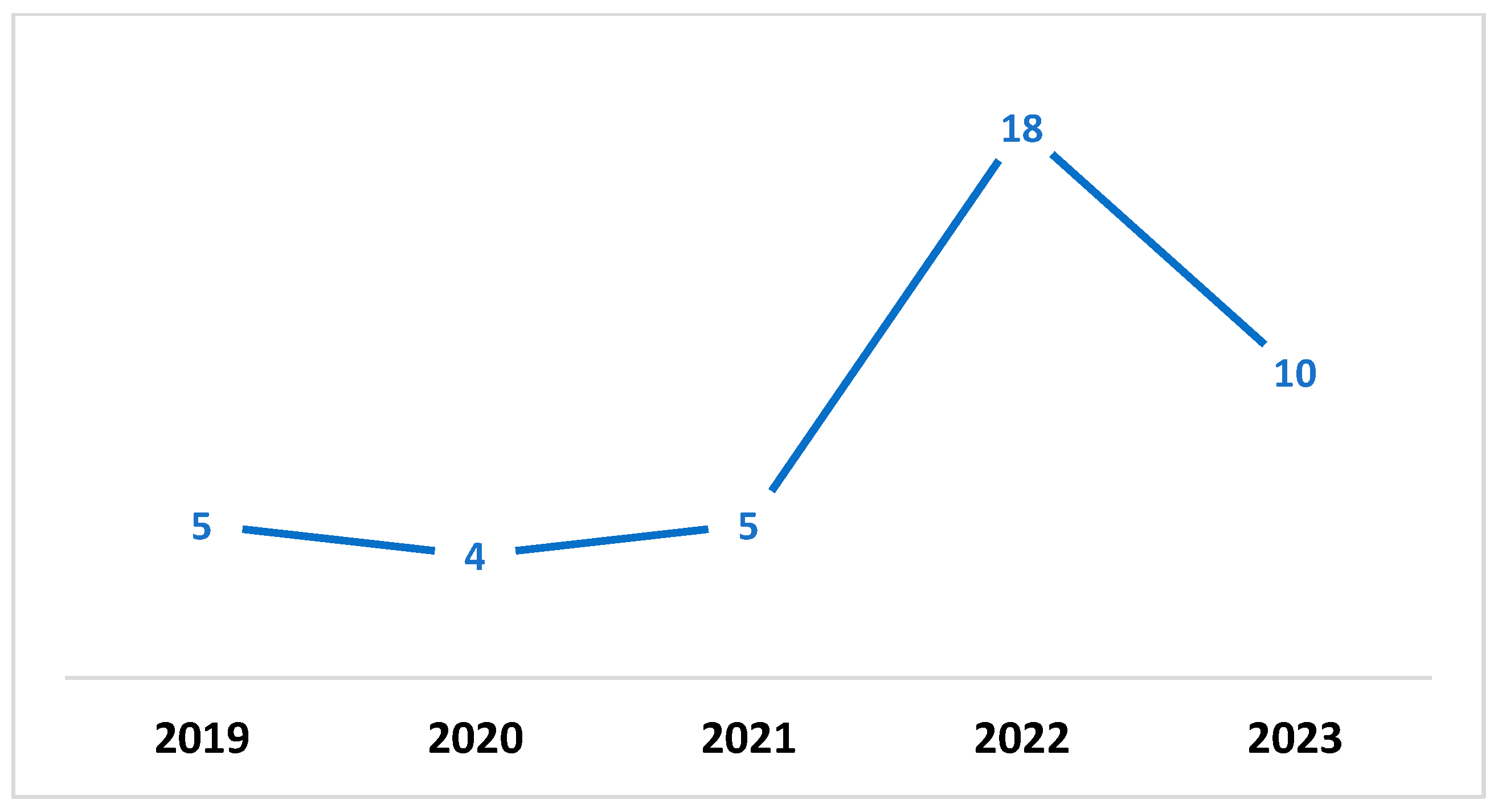
- The paper is published between 2019–2023.
- The papers are not written in the English language.
- The paper is not related to cybersecurity and digital transformation.
- The paper is a review paper.
3. Results
3.1. Financial Sector
3.2. Health Sector
3.3. Governmental Sector
3.4. Business Sector
3.5. Industrial Sector
3.6. Diverse Organizational Contexts
| Paper | Publication Year | Application Domain | Key Technologies/Theories | Key Findings |
|---|---|---|---|---|
| [22] | 2022 | Financial sector | Artificial intelligence, cognitive mapping, DEMATEL techniques | Provision of a decision-support model by combining the decision-making trial and evaluation laboratory (DEMATEL) method and cognitive mapping. |
| [23] | 2023 | Financial sector | Cognitive technologies | Provided directions to use cognitive technologies in the digital transformation of the Russian economy. |
| [24] | 2022 | Financial sector | Artificial intelligence, blockchain, voice-based technology, or natural language processing | Higher trust in Fintech by stakeholders in the financial sector. |
| [25] | 2019 | Public institutions, financial institutions, banking institutions, industry, transportation, and agriculture | Different technologies related to digitalization | Highlighting the need for information security in different application domains. |
| [34] | 2023 | Healthcare sector | No specific technology was mentioned | Sustainability of digital transformation in the healthcare sector requires cybersecurity skills, uncertainty management, and the healthcare sector’s interdependence. |
| [35] | 2023 | Healthcare sector | Electronic health records, remote patient monitoring, artificial intelligence, telemedicine, and federated learning | Privacy and security recommendations for the healthcare sector. |
| [36] | 2020 | Healthcare sector | Smartphone apps and wearable tech products enable data sharing | Need for data privacy of patients in healthcare applications. |
| [37] | 2021 | Healthcare sector | No specific technology was mentioned | Need for enhanced cybersecurity in post-COVID-19 digital transformation. |
| [41] | 2022 | Government sector | No specific technology was mentioned | Recommendation to use a secure network by the ministry in Palestine. |
| [42] | 2022 | Government sector | No specific technology was mentioned | Establishment of clear data exchange policies and clear job descriptions for IT employees. |
| [43] | 2023 | Government tax payments | Full-service mobile apps and e-payment channel | Need for actions to make the process transparent and legal in Danish tax payment. |
| [44] | 2023 | Governmental and other public services | AI and other leading technologies | Emphasizes cybersecurity governance. |
| [45] | 2021 | Government critical infrastructure | No specific technology was mentioned | Emphasizes cybersecurity of critical infrastructure. |
| [47] | 2022 | Business sector | No specific technology was mentioned. | Emphasizes state regulations for the transformation of economic clusters at the international level. |
| [48] | 2022 | Business sector | Advanced encryption and data analytics are essential for cybersecurity and AML efficiency | Analyzed digital transformation and cybersecurity situations across different countries. |
| [49] | 2022 | Business sector | Business sector advanced encryption and data analytics are essential for cybersecurity and AML efficiency | Digital transformation in Indonesia and six-ware cyber security framework. |
| [50] | 2023 | Business sector | IT security and data protection, cloud migration, cloud computing | Security concerns for cloud transformation of business. |
| [51] | 2021 | Business sector | Blockchain, IoTs, AI, and other emerging technologies | SWOT analysis of blockchain and other technologies. |
| [52] | 2022 | E-commerce | Trustworthiness, credit card usage concerns, consumer rating | User information security perception in Saudi Arabian E-commerce applications. |
| [5] | 2023 | E-commerce | Protection Motivation Theory | User information security perception of E-commerce in Pakistan. |
| [60] | 2023 | Industrial sector | No specific technology was mentioned | Security implication of small power plants. |
| [61] | 2022 | Industrial sector | Quantum computing, cryptography, optical fiber, and related technologies are discussed | Information security implications in quantum technologies. |
| [62] | 2019 | Industrial sector | Robotic Process Automation (RPA) | Information system security compliance and response implications. |
| [63] | 2019 | Service industry | IoTs, machine learning, AI, and digital transformation | Cybersecurity implications of IoTs, machine learning, and digital transformation. |
| [64] | 2022 | Networked organizational structure | Genetic algorithms | Factors affecting quality in manufacturing settings. |
| [65] | 2021 | Work environment | Cloud computing | Emphasizes the importance of secure software development in digital transformation. |
| [66] | 2020 | Enterprises | Mobile devices, cloud computing, social media platforms | Cybersecurity implications for the digital transformation of humanitarian organizations. |
| [67] | 2022 | Work environment | Firewalls, encryption software, intrusion detection systems | Emphasizes data security of employee data in organizations. |
| [68] | 2022 | Environment | No specific technology focused on | Digital transformation and environmental security in Russia. |
| [69] | 2022 | Environment | IoTs | Green IoTs and adaptive cybersecurity implications. |
| [70] | 2019 | Governance, economy, and social sectors | No specific technology was mentioned | Digital transformation and security in Russia. |
| [71] | 2020 | Economy | No specific technology was mentioned | Economic security and digital transformation in Russia. |
| [72] | 2022 | Digital agriculture | Smart sensors, Internet of Things, machine learning | Side-channel attacks in digital agriculture. |
| [73] | 2020 | Digital agriculture | Internet of Things, 5G networks | Privacy-preserving data aggregation scheme. |
| [74] | 2022 | Digital accounting | Robotics, enterprise resource planning, artificial intelligence, optical character recognition | Digital transformation and future of accounting. |
| [75] | 2022 | Digital accounting | AI, blockchain, cloud computing | Emphasis on benefits for accounting firms in digital transformation. |
| [76] | 2021 | Education | Artificial intelligence, Internet of Things, blockchain, 3D printing, cybersecurity, big data | Futuristic universities in the era of digital transformation. |
| [77] | 2022 | Education | No specific technology focused on | Emphasis on cybersecurity culture in universities. |
| [80] | 2019 | Power systems | IEEE RTS 96 | Emphasizes the impact of cybersecurity attacks on power systems. |
| [81] | 2023 | Power systems | Artificial neural networks, convolutional neural networks, and support vector machines | Meta-heuristic and deep learning algorithms for cybersecurity in power systems. |
| [82] | 2023 | Power systems | Graph Convolutional Long Short-Term Memory (GC-LSTM) and a deep convolutional network | Model for situational awareness in online cyber-attack. |
| [83] | 2022 | Maritime | No specific technology focused on | Cybersecurity implications for maritime industry. |
4. Discussion
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Hai, T.N.; Van, Q.N.; Thi Tuyet, M.N. Digital transformation: Opportunities and challenges for leaders in the emerging countries in response to COVID-19 pandemic. Emerg. Sci. J. 2021, 5, 21–36. [Google Scholar] [CrossRef]
- Möller, D. Cybersecurity in Digital Transformation: Scope and Applications; Springer: Berlin/Heidelberg, Germany, 2020. [Google Scholar]
- Matt, C.; Hess, T.; Benlian, A. Digital transformation strategies. Bus. Inf. Syst. Eng. 2015, 57, 339–343. [Google Scholar] [CrossRef]
- Saeed, S. Digital Workplaces and Information Security Behavior of Business Employees: An Empirical Study of Saudi Arabia. Sustainability 2023, 15, 6019. [Google Scholar] [CrossRef]
- Saeed, S. A Customer-Centric View of E-Commerce Security and Privacy. Appl. Sci. 2023, 13, 1020. [Google Scholar] [CrossRef]
- Sharif, M.H.U.; Mohammed, M.A. A literature review of financial losses statistics for cyber security and future trend. World J. Adv. Res. Rev. 2022, 15, 138–156. [Google Scholar] [CrossRef]
- Haislip, J.; Kolev, K.; Pinsker, R.; Steffen, T. The economic cost of cybersecurity breaches: A broad-based analysis. In Proceedings of the Workshop on the Economics of Information Security (WEIS), Boston, MA, USA, 3–4 June 2019; Volume 1, p. 37. [Google Scholar]
- Garg, V. Covenants without the Sword: Market Incentives for Cybersecurity Investment. In Proceedings of the TPRC49: The 49th Research Conference on Communication, Information and Internet Policy, Virtual, 22–24 September 2021. [Google Scholar]
- Lee, I. Cybersecurity: Risk management framework and investment cost analysis. Bus. Horiz. 2021, 64, 659–671. [Google Scholar] [CrossRef]
- Gordon, L.A.; Loeb, M.P.; Zhou, L. Integrating cost–benefit analysis into the NIST Cybersecurity Framework via the Gordon–Loeb Model. J. Cybersecur. 2020, 6, tyaa005. [Google Scholar] [CrossRef]
- Krutilla, K.; Alexeev, A.; Jardine, E.; Good, D. The benefits and costs of cybersecurity risk reduction: A dynamic extension of the Gordon and Loeb model. Risk Anal. 2021, 41, 1795–1808. [Google Scholar] [CrossRef]
- Simon, J.; Omar, A. Cybersecurity investments in the supply chain: Coordination and a strategic attacker. Eur. J. Oper. Res. 2020, 282, 161–171. [Google Scholar] [CrossRef]
- Uddin, M.H.; Ali, M.H.; Hassan, M.K. Cybersecurity hazards and financial system vulnerability: A synthesis of literature. Risk Manag. 2020, 22, 239–309. [Google Scholar] [CrossRef]
- Curti, F.; Ivanov, I.; Macchiavelli, M.; Zimmermann, T. City Hall Has Been Hacked! The Financial Costs of Lax Cybersecurity. The Financial Costs of Lax Cybersecurity. Available online: https://ssrn.com/abstract=4465071 (accessed on 15 June 2023).
- Page, M.J.; McKenzie, J.E.; Bossuyt, P.M.; Boutron, I.; Hoffmann, T.C.; Mulrow, C.D.; Shamseer, L.; Tetzlaff, J.M.; Akl, E.A.; Brennan, S.E.; et al. The PRISMA 2020 statement: An updated guideline for reporting systematic reviews. BMJ 2021, 372, n71. [Google Scholar] [CrossRef] [PubMed]
- Al-Alawi, A.I.; Al-Bassam MS, A. The significance of cybersecurity system in helping managing risk in banking and financial sector. J. Xidian Univ. 2020, 14, 1523–1536. [Google Scholar]
- Hasan, M.F.; Al-Ramadan, N.S. Cyber-attacks and Cyber Security Readiness: Iraqi Private Banks Case. Soc. Sci. Humanit. J. 2021, 5, 2312–2323. [Google Scholar]
- Joveda, N.; Khan, M.T.; Pathak, A.; Chattogram, B. Cyber laundering: A threat to banking industries in Bangladesh: In quest of effective legal framework and cyber security of financial information. Int. J. Econ. Financ. 2019, 11, 54–65. [Google Scholar] [CrossRef]
- Almudaires, F.; Almaiah, M. Data an overview of cybersecurity threats on credit card companies and credit card risk mitigation. In Proceedings of the 2021 International Conference on Information Technology (ICIT), Amman, Jordan, 14–15 July 2021; pp. 732–738. [Google Scholar]
- Smith, K.J.; Dhillon, G. Assessing blockchain potential for improving the cybersecurity of financial transactions. Manag. Financ. 2020, 46, 833–848. [Google Scholar] [CrossRef]
- Kuzmenko, O.; Kubálek, J.; Bozhenko, V.; Kushneryov, O.; Vida, I. An approach to managing innovation to protect financial sector against cybercrime. Pol. J. Manag. Stud. 2021, 24, 276–291. [Google Scholar] [CrossRef]
- Rodrigues, A.R.D.; Ferreira, F.A.; Teixeira, F.J.; Zopounidis, C. Artificial intelligence, digital transformation and cybersecurity in the banking sector: A multi-stakeholder cognition-driven framework. Res. Int. Bus. Financ. 2022, 60, 101616. [Google Scholar] [CrossRef]
- Fedorov, B.M.; Fedorova, S.V.; Zhang, H.; Mamedova, N.A. Using Cognitive Technologies to Ensure the Information Security of Banks in the Conditions of Digital Transformation and Development of Biometrical Identification. WSEAS Trans. Bus. Econ. 2023, 20, 382–387. [Google Scholar] [CrossRef]
- Patil, R.; Bharathi, S.V. A Study on the Business Transformation, Security issues and Investors Trust in Fintech Innovation. Cardiometry 2022, 24, 918–932. [Google Scholar]
- Rãƒdulescu, C.V.; Bodislav, D.A.; Negescu, M.D.O. The Risks of Digitization in the Context of Economic Development and of Ensuring Social and Informational Security. In Proceedings of the International Management Conference, Poznan, Poland, 27–29 June 2019; Faculty of Management, Academy of Economic Studies: Bucharest, Romania, 2019; Volume 13, pp. 1040–1050. [Google Scholar]
- Mijwil, M.; Aljanabi, M.; Ali, A.H. Chatgpt: Exploring the role of cybersecurity in the protection of medical information. Mesopotamian J. Cybersecur. 2023, 2023, 18–21. [Google Scholar] [CrossRef]
- Sethuraman, S.C.; Vijayakumar, V.; Walczak, S. Cyber attacks on healthcare devices using unmanned aerial vehicles. J. Med. Syst. 2020, 44, 29. [Google Scholar] [CrossRef]
- Buzdugan, A. Integration of cyber security in healthcare equipment. In Proceedings of the 4th International Conference on Nanotechnologies and Biomedical Engineering: Proceedings of ICNBME-2019, Chisinau, Moldova, 18–21 September 2019; Springer International Publishing: Berlin/Heidelberg, Germany, 2020; pp. 681–684. [Google Scholar]
- Thomasian, N.M.; Adashi, E.Y. Cybersecurity in the Internet of medical things. Health Policy Technol. 2021, 10, 100549. [Google Scholar] [CrossRef]
- Abie, H. Cognitive cybersecurity for CPS-IoT enabled healthcare ecosystems. In Proceedings of the 2019 13th International Symposium on Medical Information and Communication Technology (ISMICT), Oslo, Norway, 8–10 May 2019; pp. 1–6. [Google Scholar]
- Loi, M.; Christen, M.; Kleine, N.; Weber, K. Cybersecurity in health–disentangling value tensions. J. Inf. Commun. Ethics Soc. 2019, 17, 229–245. [Google Scholar] [CrossRef]
- Ali, K.A.; Alyounis, S. Cybersecurity in healthcare industry. In Proceedings of the 2021 International Conference on Information Technology (ICIT), Amman, Jordan, 14–15 July 2021; pp. 695–701. [Google Scholar]
- Abbas HS, M.; Qaisar, Z.H.; Ali, G.; Alturise, F.; Alkhalifah, T. Impact of cybersecurity measures on improving institutional governance and digitalization for sustainable healthcare. PLoS ONE 2022, 17, e0274550. [Google Scholar] [CrossRef] [PubMed]
- Garcia-Perez, A.; Cegarra-Navarro, J.G.; Sallos, M.P.; Martinez-Caro, E.; Chinnaswamy, A. Resilience in healthcare systems: Cyber security and digital transformation. Technovation 2023, 121, 102583. [Google Scholar] [CrossRef]
- Paul, M.; Maglaras, L.; Ferrag, M.A.; AlMomani, I. Digitization of Healthcare Sector: A Study on Privacy and Security Concerns. ICT Express 2023, in press. [Google Scholar] [CrossRef]
- Nwaiwu, F.; Mbelu, S. Digital Transformation in Healthcare and Surveillance Capitalism: Comparative Assessment of Data and Privacy Protection Compliance across the European Union (5 July 2020). Available online: https://ssrn.com/abstract=3643838 (accessed on 15 June 2023).
- Maleh, Y.; Mellal, B. Digital transformation and cybersecurity in the context of COVID-19 proliferation. IEEE Technol. Policy Ethics 2021, 6, 1–4. [Google Scholar] [CrossRef]
- Shaheen, K.; Zolait, A.H. The impacts of the cyber-trust program on the cybersecurity maturity of government entities in the Kingdom of Bahrain. Inf. Comput. Secur. 2023. ahead-of-print. [Google Scholar] [CrossRef]
- Montasari, R. Cyber Threats and the Security Risks They Pose to National Security: An Assessment of Cybersecurity Policy in the United Kingdom. In Countering Cyberterrorism: The Confluence of Artificial Intelligence, Cyber Forensics and Digital Policing in US and UK National Cybersecurity; Springer Nature: Berlin/Heidelberg, Germany, 2023; pp. 7–25. [Google Scholar]
- Alhalafi, N.; Veeraraghavan, P. Exploring the Challenges and Issues in Adopting Cybersecurity in Saudi Smart Cities: Conceptualization of the Cybersecurity-Based UTAUT Model. Smart Cities 2023, 6, 1523–1544. [Google Scholar] [CrossRef]
- Al Shobaki, M.J.; El Talla, S.A.; Al Najjar, M.T. Digital Transformation and Its Impact on the Application of Cyber Security in the Ministry of Interior and National Security in Palestine. 2022. Available online: http://www.moi.gov.ps (accessed on 15 June 2023).
- Al Najjar, M.T.; Al Shobaki, M.J.; El Talla, S.A. The Reality of Digital Transformation in the Palestinian Ministry of Interior and National Security. 2022. Available online: www.ijeais.org/ijamsr (accessed on 15 June 2023).
- Fjord, L.B.; Schmidt, P.K. The Digital Transformation of Tax Systems: Progress, Pitfalls and Protection in a Danish Context. 2022. Available online: https://ssrn.com/abstract=4252832 (accessed on 15 June 2023).
- Mijwil, M.; Filali, Y.; Aljanabi, M.; Bounabi, M.; Al-Shahwani, H. The Purpose of Cybersecurity Governance in the Digital Transformation of Public Services and Protecting the Digital Environment. Mesopotamian J. Cybersecur. 2023, 2023, 1–6. [Google Scholar]
- Maglaras, L.; Kantzavelou, I.; Ferrag, M.A. Digital Transformation and Cybersecurity of Critical Infrastructures. Appl. Sci. 2021, 11, 8357. [Google Scholar] [CrossRef]
- Bokhari, S.; Hamrioui, S.; Aider, M. Cybersecurity strategy under uncertainties for an IoE environment. J. Netw. Comput. Appl. 2022, 205, 103426. [Google Scholar] [CrossRef]
- Gonchar, V. The Transformation of Entrepreneurial Activity in the Conditions of the Development of the Digital Economy and a Methodology of Assessing Its Digital Security in Digital Technologies in the Contemporary Economy: Collective Monograph; Simanavičienė, Ž., Ed.; Mykolas Romeris University Research: Vilnius, Lithuania, 2022; ISBN 9786094880506. [Google Scholar]
- Kuzior, A.; Vasylieva, T.; Kuzmenko, O.; Koibichuk, V.; Brożek, P. Global Digital Convergence: Impact of Cybersecurity, Business Transparency, Economic Transformation, and AML Efficiency. J. Open Innov. Technol. Mark. Complex. 2022, 8, 195. [Google Scholar] [CrossRef]
- Putri MS, D.; Gultom, R.A.; Wadjdi, A.F. The Concept of an Electronic-Based Government System and the Six-Ware Cyber Security Framework in Supporting the Digitization of the Indonesian Government. Def. Secur. Stud. 2023, 4, 1–7. [Google Scholar]
- Shitta-Bey, A.M. Security Concerns of Cloud Migration and Its Implications on Cloud-Enabled Business Transformation Effect of Quality Education on Poverty Alleviation View Project. Master’s Thesis, Università della Svizzera Italiana, Lugano, Switzerland, 2023. Available online: https://www.researchgate.net/publication/369118961 (accessed on 15 June 2023).
- Trung, N.D.; Huy DT, N.; Van Thanh, T.; Thanh NT, P.; Dung, N.T.; Thanh Huong, L.T. Digital transformation, AI applications and IoTs in Blockchain managing commerce secrets: And cybersecurity risk solutions in the era of industry 4.0 and further. Webology 2021, 18, 10–14704. [Google Scholar] [CrossRef]
- Gull, H.; Saeed, S.; Iqbal, S.Z.; Bamarouf, Y.A.; Alqahtani, M.A.; Alabbad, D.A.; Alamer, A. An empirical study of mobile commerce and customers security perception in Saudi Arabia. Electronics 2022, 11, 293. [Google Scholar] [CrossRef]
- Anthi, E.; Williams, L.; Rhode, M.; Burnap, P.; Wedgbury, A. Adversarial attacks on machine learning cybersecurity defences in industrial control systems. J. Inf. Secur. Appl. 2021, 58, 102717. [Google Scholar] [CrossRef]
- Meeran, Y.A.; Shyry, S.P. Resilient Detection of Cyber Attacks in Industrial Devices. In Proceedings of the 2023 7th International Conference on Trends in Electronics and Informatics (ICOEI), Tirunelveli, India, 11–13 April 2023; pp. 564–569. [Google Scholar]
- Ameri, K.; Hempel, M.; Sharif, H.; Lopez Jr, J.; Perumalla, K. Design of a novel information system for semi-automated management of cybersecurity in industrial control systems. ACM Trans. Manag. Inf. Syst. 2023, 14, 1–35. [Google Scholar] [CrossRef]
- Buja, A.; Apostolova, M.; Luma, A. Enhancing Cyber Security in Industrial Internet of Things Systems: An Experimental Assessment. In Proceedings of the 2023 12th Mediterranean Conference on Embedded Computing (MECO), Budva, Montenegro, 14 June 2023; pp. 1–5. [Google Scholar]
- Ramirez, R.; Chang, C.K.; Liang, S.H. PLC Cybersecurity Test Platform Establishment and Cyberattack Practice. Electronics 2023, 12, 1195. [Google Scholar] [CrossRef]
- Zanasi, C.; Russo, S.; Colajanni, M. Flexible Zero Trust Architecture for the Cybersecurity of Industrial Iot Infrastructures. Available online: https://ssrn.com/abstract=4481853 (accessed on 15 June 2023).
- Jacopo, P.; Graziana, C.; Federica, P.; Giarrè, L. Using Digital Twin to Detect Cyber-Attacks in Industrial Control Systems. In Proceedings of the IEEE Proceedings of 2023 EUROCON, Torino, Italy, 6–8 July 2023. [Google Scholar]
- Osak, A.; Buzina, E. Flexibility and security of power systems, methods of analysis, and criteria for their evaluation in the conditions of digital transformation of the power industry. AIP Conf. Proc. 2023, 2552, 040008. [Google Scholar]
- Mayhuasca, J.; Sotelo, S. Quantum Technologies for Digital Transformation and Informatica Security. Int. J. Eng. Sci. 2022, 15, 43–50. [Google Scholar] [CrossRef]
- Raza, H.; Baptista, J.; Constantinides, P. Conceptualizing the Role of IS Security Compliance in Projects of Digital Transformation: Tensions and Shifts between Prevention and Response Modes; ICIS: Houston, TX, USA, 2019. [Google Scholar]
- Trung, N.D.; Huy DT, N.; Le, T.H. IoTs, machine learning (ML), AI and digital transformation affects various industries-principles and cybersecurity risks solutions. Management 2021, 18, 10–14704. [Google Scholar] [CrossRef]
- Di, Z.; Liu, Y.; Li, S. Networked Organizational Structure of Enterprise Information Security Management Based on Digital Transformation and Genetic Algorithm. Front. Public Health 2022, 10, 921632. [Google Scholar] [CrossRef]
- Alenezi, M. Software and Security Engineering in Digital Transformation. arXiv 2021, arXiv:2201.01359. [Google Scholar]
- Marelli, M. Hacking humanitarians: Defining the cyber perimeter and developing a cyber security strategy for international humanitarian organizations in digital transformation. Int. Rev. Red Cross 2020, 102, 367–387. [Google Scholar] [CrossRef]
- Dvojmoč, M.; Verboten, M.T. Cyber (In) security of Personal Data and Information in Times of Digitization. Med. Law Soc. 2022, 15, 287–304. [Google Scholar] [CrossRef]
- Zarapina, L.; Mukhlynina, M.; Adamenko, A.; Mukhlynin, D.; Belokopytova, N. Issues of Legal Support of Socio-economic Policy and Environmental Security of Russia in the Context of Digital Transformation. In Proceedings of the International Scientific-Practical Conference “Ensuring the Stability and Security of Socio-Economic Systems: Overcoming the Threats of the Crisis Space” (SES 2021), Kirov, Russia, 17–18 June 2021; Sciete Press: Kirov, Russia, 2021; pp. 336–340, ISBN 978-989-758-546-3. [Google Scholar] [CrossRef]
- Halabi, T.; Bellaiche, M.; Fung, B.C. Towards Adaptive Cybersecurity for Green IoT. In Proceedings of the 2022 IEEE International Conference on Internet of Things and Intelligence Systems (IoTaIS), Bali, Indonesia, 24–26 November 2022; pp. 64–69. [Google Scholar]
- Voskresenskaya, E.; Vorona-Slivinskaya, L.; Panov, S. Digital transformation of social sector as the factor of development and security of the country. In E3S Web of Conferences; EDP Sciences: Les Ulis, France, 2019; Volume 135, p. 03075. [Google Scholar]
- Kuchumov, A.; Pecherictsa, E.; Chaikovskaya, A.; Zhilyaeva, I. Digital transformation in the concept of economic security of Russia and its regions. In Proceedings of the 2nd International Scientific Conference on Innovations in Digital Economy, St. Petersburg, Russia, 22–23 October 2020; pp. 1–8. [Google Scholar]
- Alahmadi, A.N.; Rehman, S.U.; Alhazmi, H.S.; Glynn, D.G.; Shoaib, H.; Solé, P. Cyber-Security Threats and Side-Channel Attacks for Digital Agriculture. Sensors 2022, 22, 3520. [Google Scholar] [CrossRef]
- Song, J.; Zhong, Q.; Wang, W.; Su, C.; Tan, Z.; Liu, Y. FPDP: Flexible privacy-preserving data publishing scheme for smart agriculture. IEEE Sens. J. 2020, 21, 17430–17438. [Google Scholar] [CrossRef]
- Gonçalves, M.J.A.; da Silva, A.C.F.; Ferreira, C.G. The Future of Accounting: How Will Digital Transformation Impact the Sector? Informatics 2022, 9, 19. [Google Scholar] [CrossRef]
- Tiron-Tudor, A.; Donțu, A.N.; Bresfelean, V.P. Emerging Technologies’ Contribution to the Digital Transformation in Accountancy Firms. Electronics 2022, 11, 3818. [Google Scholar] [CrossRef]
- Rodríguez-Abitia, G.; Bribiesca-Correa, G. Assessing digital transformation in universities. Future Internet 2021, 13, 52. [Google Scholar] [CrossRef]
- Pavlova, E. Enhancing the organisational culture related to cyber security during the university digital transformation. Inf. Secur. 2020, 46, 239–249. [Google Scholar] [CrossRef]
- Ribas Monteiro, L.F.; Rodrigues, Y.R.; Zambroni de Souza, A.C. Cybersecurity in Cyber–Physical Power Systems. Energies 2023, 16, 4556. [Google Scholar] [CrossRef]
- Liang, J.; Zhu, H.; Zhang, B.; Liu, L.; Liu, X.; Lin, H.; Tian, J.; Chen, Q. Research and Prospect of Cyber-Attacks Prediction Technology for New Power Systems. In Proceedings of the 2023 IEEE 6th Information Technology, Networking, Electronic and Automation Control Conference (ITNEC), Chongqing, China, 24–26 February 2023; Volume 6, pp. 638–647. [Google Scholar]
- Dagoumas, A. Assessing the impact of cybersecurity attacks on power systems. Energies 2019, 12, 725. [Google Scholar] [CrossRef]
- Diaba, S.Y.; Shafie-Khah, M.; Elmusrati, M. Cyber Security in Power Systems Using Meta-Heuristic and Deep Learning Algorithms. IEEE Access 2023, 11, 18660–18672. [Google Scholar] [CrossRef]
- Presekal, A.; Ştefanov, A.; Rajkumar, V.S.; Palensky, P. Attack graph model for cyber-physical power systems using hybrid deep learning. IEEE Trans. Smart Grid 2023. Early Access. [Google Scholar] [CrossRef]
- Kechagias, E.P.; Chatzistelios, G.; Papadopoulos, G.A.; Apostolou, P. Digital transformation of the maritime industry: A cybersecurity systemic approach. Int. J. Crit. Infrastruct. Prot. 2022, 37, 100526. [Google Scholar] [CrossRef]
- Khashan, O.A.; Alamri, S.; Alomoush, W.; Alsmadi, M.K.; Atawneh, S.; Mir, U. Blockchain-Based Decentralized Authentication Model for IoT-Based E-Learning and Educational Environments. Comput. Mater. Contin. 2023, 75, 3133–3158. [Google Scholar] [CrossRef]
- Sufyan, A.; Khan, K.B.; Khashan, O.A.; Mir, T.; Mir, U. From 5G to beyond 5G: A Comprehensive Survey of Wireless Network Evolution, Challenges, and Promising Technologies. Electronics 2023, 12, 2200. [Google Scholar] [CrossRef]
- Al-Taleb, N.; Saqib, N.A. Towards a hybrid machine learning model for intelligent cyber threat identification in smart city environments. Appl. Sci. 2022, 12, 1863. [Google Scholar] [CrossRef]
- Sandhu, K. Advancing Cybersecurity for Digital Transformation: Opportunities and Challenges. In Handbook of Research on Advancing Cybersecurity for Digital Transformation; IGI Global: Hershey, PA, USA, 2021; pp. 1–17. [Google Scholar]
- Azizi, N.; Haass, O. Cybersecurity Issues and Challenges. In Handbook of Research on Cybersecurity Issues and Challenges for Business and FinTech Applications; IGI Global: Hershey, PA, USA, 2023; pp. 21–48. [Google Scholar] [CrossRef]
- Lesmana, D.; Afifuddin, M.; Adriyanto, A. Challenges and Cybersecurity Threats in Digital Economic Transformation. Int. J. Humanit. Educ. Soc. Sci. 2023, 2. [Google Scholar] [CrossRef]
- Maglaras, L.; Drivas, G.; Chouliaras, N.; Boiten, E.; Lambrinoudakis, C.; Ioannidis, S. Cybersecurity in the era of digital transformation: The case of Greece. In Proceedings of the 2020 International Conference on Internet of Things and Intelligent Applications (ITIA), Zhenjiang, China, 27–29 November 2020; pp. 1–5. [Google Scholar]
- Nobles, C. Stress, burnout, and security fatigue in cybersecurity: A human factors problem. HOLISTICA–J. Bus. Public Adm. 2022, 13, 49–72. [Google Scholar] [CrossRef]
- Metawa, N.; Elhoseny, M.; Mutawea, M. The role of information systems for digital transformation in the private sector: A review of Egyptian SMEs. Afr. J. Econ. Manag. Stud. 2022, 13, 468–479. [Google Scholar] [CrossRef]
- Özsungur, F. Business Management and Strategy in Cybersecurity for Digital Transformation. In Handbook of Research on Advancing Cybersecurity for Digital Transformation; IGI Global: Hershey, PA, USA, 2021; pp. 144–162. [Google Scholar]
- Nguyen Duc, A.; Chirumamilla, A. Identifying security risks of digital transformation-an engineering perspective. In Digital Transformation for a Sustainable Society in the 21st Century: 18th IFIP WG 6.11 Conference on e-Business, e-Services, and e-Society, I3E 2019, Trondheim, Norway, 18–20 September 2019; Springer International Publishing: Berlin/Heidelberg, Germany, 2019; pp. 677–688. [Google Scholar]
- Kour, R.; Patwardhan, A.; Thaduri, A.; Karim, R. A review on cybersecurity in railways. Proc. Inst. Mech. Eng. Part F J. Rail Rapid Transit 2023, 237, 3–20. [Google Scholar] [CrossRef]


Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Saeed, S.; Altamimi, S.A.; Alkayyal, N.A.; Alshehri, E.; Alabbad, D.A. Digital Transformation and Cybersecurity Challenges for Businesses Resilience: Issues and Recommendations. Sensors 2023, 23, 6666. https://doi.org/10.3390/s23156666
Saeed S, Altamimi SA, Alkayyal NA, Alshehri E, Alabbad DA. Digital Transformation and Cybersecurity Challenges for Businesses Resilience: Issues and Recommendations. Sensors. 2023; 23(15):6666. https://doi.org/10.3390/s23156666
Chicago/Turabian StyleSaeed, Saqib, Salha A. Altamimi, Norah A. Alkayyal, Ebtisam Alshehri, and Dina A. Alabbad. 2023. "Digital Transformation and Cybersecurity Challenges for Businesses Resilience: Issues and Recommendations" Sensors 23, no. 15: 6666. https://doi.org/10.3390/s23156666
APA StyleSaeed, S., Altamimi, S. A., Alkayyal, N. A., Alshehri, E., & Alabbad, D. A. (2023). Digital Transformation and Cybersecurity Challenges for Businesses Resilience: Issues and Recommendations. Sensors, 23(15), 6666. https://doi.org/10.3390/s23156666







