Abstract
The demand for cybersecurity is growing to safeguard information flow and enhance data privacy. This essay suggests a novel authenticated public key elliptic curve based on a deep convolutional neural network (APK-EC-DCNN) for cybersecurity image encryption application. The public key elliptic curve discrete logarithmic problem (EC-DLP) is used for elliptic curve Diffie–Hellman key exchange (EC-DHKE) in order to generate a shared session key, which is used as the chaotic system’s beginning conditions and control parameters. In addition, the authenticity and confidentiality can be archived based on ECC to share the parameters between two parties by using the EC-DHKE algorithm. Moreover, the 3D Quantum Chaotic Logistic Map (3D QCLM) has an extremely chaotic behavior of the bifurcation diagram and high Lyapunov exponent, which can be used in high-level security. In addition, in order to achieve the authentication property, the secure hash function uses the output sequence of the DCNN and the output sequence of the 3D QCLM in the proposed authenticated expansion diffusion matrix (AEDM). Finally, partial frequency domain encryption (PFDE) technique is achieved by using the discrete wavelet transform in order to satisfy the robustness and fast encryption process. Simulation results and security analysis demonstrate that the proposed encryption algorithm achieved the performance of the state-of-the-art techniques in terms of quality, security, and robustness against noise- and signal-processing attacks.
1. Introduction
The security of the data, infrastructure, and applications used to store, process, and transmit information falls under the name of cybersecurity, which is the method used to respond, monitor, and protect transmitted data and information. Through a cybersecurity perspective, the focus is on the secure exchange of information. However, current encryption methods are not reliable for effective image encryption [1]. To achieve the security requirements, we use the sensitivity property of the initial condition and control parameters inherent in chaotic methods. Based on the propagation and confusion properties of Shannon’s diffusion, the security of the image ciphering algorithm is estimated. Chaotic maps are classified into two types: one-dimensional chaotic maps and higher-dimensional chaotic maps. One-dimensional chaotic maps with a single variable spanning discrete time steps include logistic maps, tent maps, and sine maps [2,3]. It is important to note that the chaotic maps have numerous flaws, including their small chaotic ranges and ease of conversion to the periodic map. We also point out that one of the flaws is the lack of sufficient control parameters [4,5,6,7]. On the other hand, chaotic maps with higher dimensions contain at least two variables. Their characteristics include chaotic orbits that are difficult to predict and improved performance [8,9], but due to their difficulty in implementation and high computing costs, they are not processed in real time [10,11].
The authors introduced a new one-dimensional chaotic system to overcome the limitations of one-dimensional chaotic maps. Based on the modular one principle, this system encodes images to increase the number of control parameters [11,12]. Yicong et al. [13] suggested a cascade chaotic system (CCS) as a general one-dimensional chaotic framework and used any two 1-D chaotic maps as seed maps to produce a new non-linear chaotic system. As for Zhongyun et.al, proposed dynamic parameters to control a chaotic system (DPCCS). DPCCS is a straightforward structure that dynamically adjusts the chaotic map’s other parameters using the control map’s output (seed map). Both CCS and DPCCS have an easy-to-implement hardware architecture, extremely chaotic behavior, and a basic structure. However, many weaknesses, such as time delays and hardware implementation difficulties, appear clearly when more initial maps are serialized [14].
The message hash or message digest is the fixed output, while the hash function is the encoding mechanism that converts the variable-length input message [15]. Hash functions are used by the majority of authentication systems, digital signatures, data integrity safeguards, and random number generators. In addition, we may determine the hash value by utilizing a contemporary cryptographic hash function. Because it is challenging to detect two different messages with the same hash value within the hash function, hash functions are frequently employed in popular security protocols (such as Transport Layer Security or Internet Protocol Security) (collision resistance). This characteristic enables the widespread usage of hash functions in widely used security protocols like Transport Layer Security and IP Security.
The Secure Hash Standard (SHA) was first released by NIST [16] in 1993. In 1995, SHA-1, an updated version of the SHA algorithm, was introduced in an attempt to address some of the original flaws. The SHA-2 hashing algorithm was proposed in 2001 [17]. Because it takes into consideration larger digest messages, it is more resistant to potential attacks and may be used with larger data inputs (up to 2128 bits in the case of SHA512) (DM). The size of the operands, initialization vectors, and final DM varies for the SHA224, SHA256, SHA384, and SHA512 hashing algorithms, but the SHA-2 hashing algorithm is the same for all of them [18]. One cipher alternative that is built using chaotic maps is the hash functions. Inputs of hash functions are of random size and outputs are of fixed length (message summary or hash value) divided into keyed and non-key variants. Hash functions have an important role in data look-up tables and message integrity checks. Message authentication can be added through the keyed variant of the hash functions. Uniform distribution is the form of distribution that is used to distribute hash functions, which are one-way functions and highly sensitive to any change in inputs. This sensitivity leads to obtaining a completely different hash value when making any slight change to the inputs. As it happens, the same characteristics are shared by chaotic maps. Therefore, to draw on these characteristics, many researchers have integrated chaotic maps in the hash functions [19,20,21,22,23,24,25,26].
For many years, there has been a famous encryption technique known as cryptography (asymmetric cryptography) [27]. For small devices, computationally strong public-key encryption is often too expensive if cryptographic hardware is not used to accelerate it. Effective public-key cryptosystems are frequently created using elliptic curves. Elliptic curve cryptography (ECC) is a well-liked technology with several benefits, including tiny storage requirements, quick computations, and low-power requirements [28]. The most well-known technique that used ECC, and also provided data security, is the Menezes Vanstone Elliptic Curve Cryptosystem (MV-ECC) [29]. This technology was used and made more convenient for image encryption and security. It is widely used for secure communication, since the elliptical curve, which is based on encryption systems, has excellent encryption properties. Applications for encrypting images with an asymmetric key method were introduced in [30]. The work that is being offered introduces a novel mechanism that transforms the image pixels into a set of points on elliptical curves over a finite field, GF (p). The collected points are then subjected to elliptic curve (EC) operations, which improve the security of the encryption system and result in higher performance. EC over the finite field GF (p) is the foundation of an image encryption technique proposed in [31]. Using the public key to encrypt the obtained points, the mapping table’s index value ranges from 0 to 255 while accounting for the image’s pixels and pixel positions.
To our knowledge, the proposed method is among the earliest publications to employ public key elliptic curve cryptography incorporations with deep CNN to achieve the authentication properties and integrity. Moreover, instead of using the privet hey for both block and stream cipher for designing the privet key generator, this work presents a new research direction for using the proposed APK-EC-DCNN to automatically realize private and public key generator and satisfy the authentication properties with a high-security level. The key contributions of the proposed method are summarized as follow:
- (i)
- The DCNN is used with the public key elliptic cryptosystem in order to generate authenticated public key.
- (ii)
- A new Quantum Chaotic authenticated PK-EC Deep CNN generator is introduced.
- (iii)
- A robust APK-EC-DCNN partial image encryption based on the frequency domain is suggested.
The rest of this paper is organized as follows: in Section 2, the preliminaries that contain the PK-Elliptic curve cryptosystem and 3D Quantum Chaotic Logistic Map are discussed. In Section 3, the proposed PK-ECC-DCNN partial image encryption is introduced and discussed in detail. The simulation results and security assessments are displayed in Section 4. The proposed study’s conclusion is then provided in Section 5.
2. Literature Review
2.1. Deep-Learning Networks
Since complex functions can be effectively expressed by using a multi-layer network structure, deep learning has emerged as a recent trend in scientific research and is used in a variety of applications (such as image processing, image classification [32,33], object detection [34,35], and image segmentation [36,37]). One of the subfields of deep learning is the Generative Adversarial Network (GAN) [38], which consists of the generator and the discriminator. The generator must keep track of the distribution of the sample data, while the discriminator must identify whether the input is real data or a manufactured sample. An alternative to the stream cypher generator is the deep-learning model, which has a large number of parameters, a complex network architecture, and a random training process.
In [39], a new algorithm based on a deep convolutional generated adversarial network (SCGANs) was introduced for chaotic block image encryption, and the Feistel network was improved. A new system combined with a deep and hyperchaotic convolutional adversarial network has also been proposed. The major goal was to deliver a key stream of random numbers that was more complex and unpredictable. A deep-learning-based streaming cypher generator and a stream cypher generator that produces the private key required to encrypt and decrypt medical images were also introduced by the researchers in [40]. Lately, work has been done to introduce the chaotic algorithm-based key generation and deep convolutional neural network-based picture encryption technique [41].
Recently, in the industry 5.0 technology, a new secure SIELNet encryption technique for color images has been introduced [42]. In order to encrypt color images in the first place, the authors provided a novel three-dimensional chaotic map, which produces cypher images that are related to the original images and this chaotic map has a good chaotic behavior. Second, the authors tackle the restricted super-resolution problem by reconstructing a lossy image from a compressed, encrypted image using a tailored residual dense spatial network.
2.2. PK–Elliptic Curve Cryptosystem
In image encryption algorithms, there are two commonly used cryptosystems: stream cipher and block cipher. Stream ciphers generally have a higher level of security than block ciphers like the Advanced Encryption Standard, International Data Encryption Algorithm, and Data Encryption Standard (AES), and they are also faster in terms of encryption and decryption speeds. They have low error propagation and better synchronization, and are cheaper to implement [43,44]. Linear feedback shift registers [45], nonlinear feedback shift registers [46], finite automation [47], linear congruence generators [48], and chaotic systems [49] are popular stream cypher generators. Public key encryption is more robust than the stream and block cipher. The elliptic curve discrete logarithm problem is the best algorithm now available for tackling the underlying mathematical problem of ECC, and it requires full exponential time. On the other hand, RSA and DSA rely on subexponentially-temporal techniques to solve the discrete logarithm and integer factorization problems [50]. This suggests that, compared to methods for integer factorization and discrete logarithm issues, techniques for addressing the elliptic curve discrete logarithm problem become infeasible considerably more quickly as the problem size increases. Due to the much-reduced key size, ECC provides security levels comparable to RSA and DSA [50].
In this section, an overview of the ECC in data security was presented in [51]. In [52], the concept of the Kobltiz technology, which encodes and decodes visual data to the points of an elliptical curve, was introduced. The approach in [53] alters the dimensions of the input images first by using the k parameter. In [54], a matrix-based image coding strategy was presented using a fast-mapping technique. Alphanumeric character values are converted into (x, y) coordinates for elliptic curves utilizing various matrix characteristics, an elliptical curve, and a non-singular matrix. The mapping technology employed in the plan ensures the confidentiality of the encrypted data, enhancing the encryption system’s security. ECC and its use in data security are surveyed by the authors in [54]. The authors compare the ECC-based encryption scheme to the current asymmetric key ciphering protocol and examine the ramifications of each. The ECC scheme’s security weaknesses are also described.
The author compared the ECC-based encryption system to other asymmetric key cryptography methods in use today, such as RSA, and evaluated its drawbacks. The authors demonstrated how the ECC system has security issues. The majority of systems have limited key spaces and lengthy execution times. With the cubic equation, an elliptic curve EC over a finite field Fp is defined [51]:
where is a large prime number and are two integers which are smaller than and satisfies the following condition:
In the above equations, each value of provides a different elliptic curve where , and are the parameters of the elliptic curve. The PK-EC Diffie–Hellman Key Exchange [40] can be discussed as: Le is a base point of an , and can be computed as [39]:
where , are the sender’s and receiver’s public keys, and , are the respective private keys. The transmitter and receiver calculate the shared key as and , respectively.
For a specific point on the of elliptic curve the private key is exponentially complex to solve, where =, G is a base point, while is a random integer. It is impossible to determine the discrete logarithm of with respect to a widely known base G. The elliptic curve discrete logarithmic problem (ECDLP) is significantly more secure than other encryption techniques that rely on the integer factorization problem for a certain key size [51].
2.3. 3D Quantum Chaotic Logistic Map
An excellent example of a complex chaotic map that results from nonlinear dynamical equations is the quantum logistic map, which is generated by the classical logistic system and is a quantized version of a classical chaotic system [55,56,57,58]. While chaotic maps in higher dimensions, such as the one used in the proposed scheme, can result in an expansion of the key space range, they are overly complex, highly random, and highly sensitive to initial conditions and control parameters, as opposed to classical chaotic maps, which have low control parameters and, as a result, a small chaotic range. Therefore, using the quantum logistic system as the seed system in an encryption method is appropriate [59]. A quantum chaotic map was presented in [55], which is defined as:
The main parameters used in the quantum chaotic map are the control parameter, the parameter, and the . respectively. The advantages of the quantum logistic map are its huge capacity, natural parallelism, and straightforward structure. Additionally, the chaotic patterns produced are more pseudorandom. For various control parameters, the quantum map’s bifurcation diagram and Lyapunov exponent are provided in [55]. When r ≥ 3.99 and β ≥ 6, the quantum chaotic map can exhibit better chaotic behavior, as shown in Figure 1 and Figure 2.
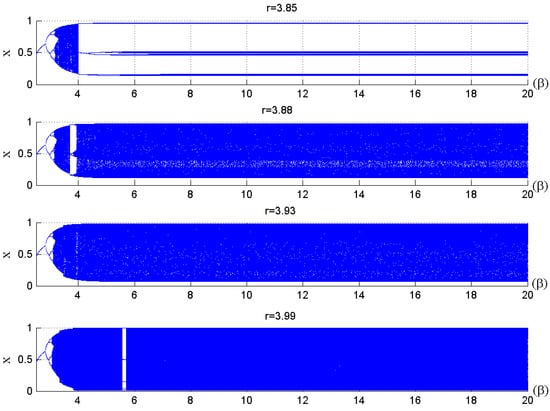
Figure 1.
Quantum map bifurcation diagram for various control parameters (r) [55].
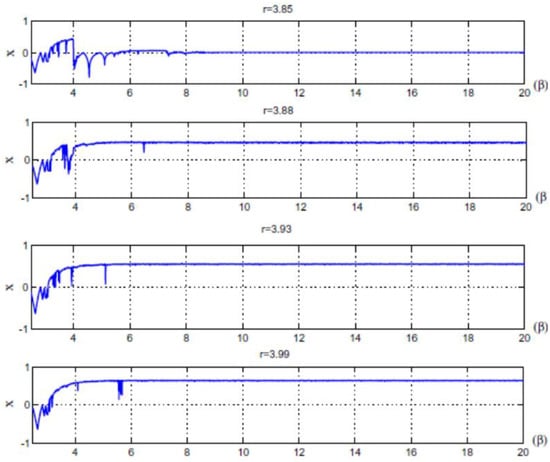
Figure 2.
Quantum map’s Lyapunov exponent for various control parameters (r) [55].
3. Proposed PK-ECC-DCNN Cryptosystem
In this section, the proposed PK-ECC-DCNN cryptosystem and its application in image encryption and authentication will be discussed. In the proposed image encryption cryptosystem, the PK-ECC Diffie–Hellman Key Exchange is used as a key exchange model based on the difficulty of the discrete logarithmic problem. The secret 3D quantum chaotic logistic map initial condition values and the control parameters will be extracted from the PK-ECC key exchange, which stuffy the authentication property. Based on the PK-ECC key exchange and the authentication property, the proposed authenticated chaotic DCNN key generator design is investigated. The outputs of the 3D quantum chaotic logistic map and the secure hash function are used to produce the proposed authenticated expansion diffusion matrix and the permutation confusion matrix. In the proposed cryptosystem, the partial image encryption can be achieved by using the discrete wavelet frequency domain transform.
3.1. Public Key Deep CNN Generator (PK-DCNNG)
In this section a public key is generated using Convolutional Neural Networks (CNNs). The pre-trained ResNet-18 convolutional neural network was used. This network is 18 layers deep [60], and it has been trained on more than 1-million images from the ImageNet database. This pre-trained network can categorize images into 1000 object categories, such as pencil, mouse, keyboard, and many more animal images. Thus, the network got acquainted with a lot of features for a large group of images. It is often much easier and faster to use transfer learning via pre-trained networks than to train a designed convolutional network from scratch. The proposed network model architecture is illustrated in Figure 3. The network contains 18 layers, 3 × 3 filters are used in convolutional layers, and the network is set up to ensure the number of filters is the same as the number of layers, if the output feature map is of the same size. However, when the output feature map is split in half, the filters are doubled in layers. By means of the convolutional layers by stride of 2, the down sampling is performed. The residual shortcut connections are inserted between layers throughout the network [61]. There are two types of connections. The first type is indicated by solid lines and is used when the input and output dimensions are the same. While the other type is used when increasing the dimensions, this type is referred to as the dotted lines. Identity mapping has been performed by this type of connection but with zeros padding with a stride of 2 for increased dimensions.
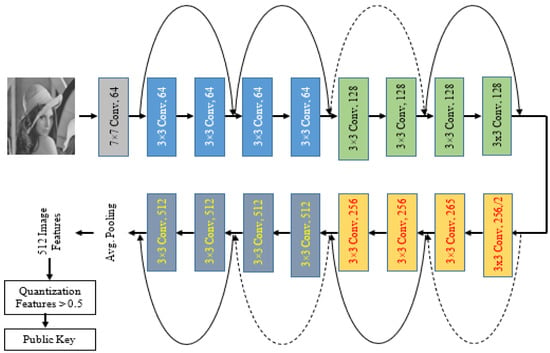
Figure 3.
Proposed ResNet-18 CNN for Public Key Generation.
The input photos are presented hierarchically by the network. Higher-level features that were acquired utilizing the lower-level features of the preceding layers are found in deeper layers. Through the use of activations on the global pooling layer, also known as “pool5,” we can acquire feature representations of training and test data at the conclusion of the network. In total, we obtain 512 features by aggregating the input features throughout all spatial areas by means of the global pooling layer. Through these image features, we obtain a value between 0 and 1. Finally, these values are converted to binary by comparing them with 0.5. If these values are less than 0.5, they will be 0. Otherwise, they will be 1.
3.2. Authenticated PK-Chaotic DCNN Key Generator
In this section, authenticated chaotic DCNN Key Generator (APK-C-DCNN-KG) has been investigated. Figure 4 and Figure 5 show a block diagram of the proposed chaotic DCNN-AKG. The proposed structure chaotic DCNN-AKG consists of the proposed chaotic map, the DCNN, secure hash function (SHA-1) with output length 8 × 32-bit words, and the authentication expansion diffusion Matrix (AEDM). The SHA-1 has two concatenated inputs. The first input is the output of the DCNN, and the second is the variable chaotic secret values and lengths obtained from the proposed chaotic map, which can be vary from 128 × 32-bit words to 512 × 32-bit words. The SHA-1 is used for key authentication for both DCNN output and the variable chaotic secret values and lengths. The AEDM inputs are the 8 32-bit words output of the SHA-1 and second output of the proposed chaotic map of length varies from 64 32-bit words to 256 × 32-bit words. Figure 4 depicts the proposed AEDM’s block diagram and the final output of the proposed AEDM is 2048 × 32-bit word. The proposed AEDM ultimate result can be converted to 256 × 256 × 8 bits, and then converted to 256 × 256 pixel as the size of the original image for the diffusion encryption step. The first and second variable chaotic secret lengths from the proposed chaotic map, which can be used as an input to the SHA-1 and the proposed AEDM, are provided from the PK-EC Diffie–Hellman Key Exchange and the proposed 3D QCLM. The expanded diffusion values to are provided by:
where “t” is the index parameter started from 17 to L; , , , are provided by:
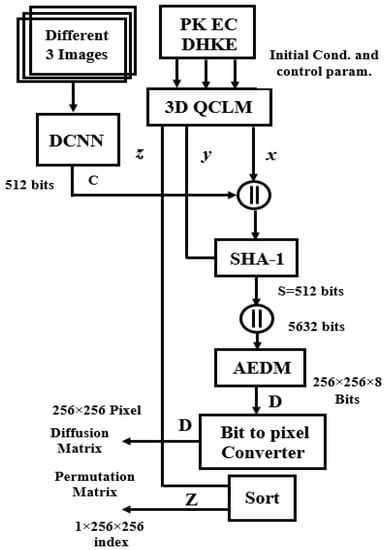
Figure 4.
Proposed Authenticated chaotic DCNN Key Generator (AC-DCNN-KG).
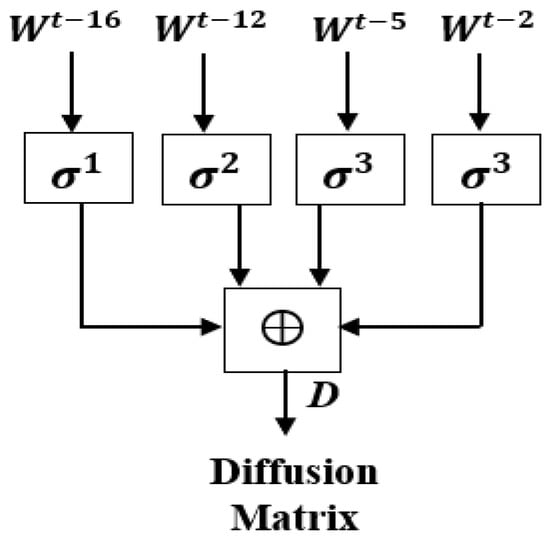
Figure 5.
The proposed Authenticated Expansion Diffusion Matrix (AECM).
In addition, the operations “+” is mod addition, is right shift by “n” bits, and “⊕” is the XOR operation.
The block diagram of the proposed authenticated public key generation is shown in Figure 4. Figure 4 shows that the proposed authenticated public key generator depends on the proposed deep convolutional neural network and the proposed authentication expansion diffusion Matrix in order to achieve the authentication strategy. The proposed Authenticated Expansion Diffusion Matrix (AECM) design is shown in Figure 5.
3.3. Proposed APK-EC-DCNN Partial Image Encryption
This study proposes a new scheme for partial image encryption. A new authenticated public key deep convolutional neural network was proposed in order to authenticate the public key generated by the Deep Convolutional Neural Network. In addition, the encrypted key exchanged scheme is based on the public key elliptic curve Diffie–Hellman key exchange protocol. This encrypted key exchange depends on how challenging the discrete logarithmic problem is to solve. The block diagram of Proposed PK-EC-APK-DCNN partial image encryption/decryption algorithm is shown in Figure 6.
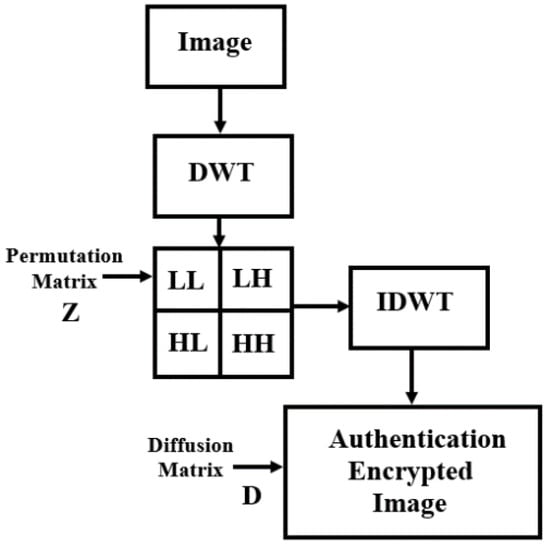
Figure 6.
The block diagram of the proposed authenticated encryption algorithm.
In addition, in order to achieve real-time processing, the partial encryption technique based on the discrete wavelet transforms where only a quarter part of all images will be encrypted so it can save computational time and cost. The two-dimensional (2D DWT) is used to achieve real-time processing. Each level of decomposition in 2D DWT yields four bands of data, one of which corresponds to the low pass band (LL), and the other three to the high pass bands (horizontal (HL), vertical (LH), and diagonal (HH)). Figure 7 shows the one-level wavelet decomposition of Lena and its corresponding wavelet decomposition sub-band mod. As illustrated in Figure 7, the 2-D DWT can be built utilizing two digital channel filters and a collection of down samplers. A Low-Pass Filter (LPF) and a High-Pass Filter (HPF) are the digital filters that are utilized. The image is subjected to a first-level (1-L) 2-D DWT to produce four distinct sub-images. In addition, in this paper, we used the Haar filter, which is a popular filter in the wavelet family.
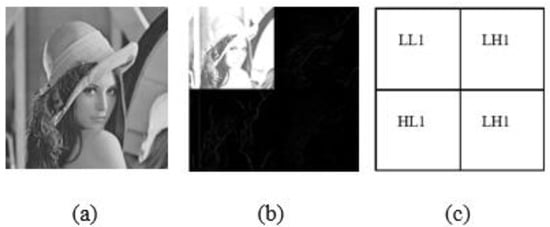
Figure 7.
DWT: (a) Lena image (b) schematic diagram of the two-layer wavelet decomposition of Lena; (c) wavelet decomposition sub-bands.
Authenticated Key Generation, confusion, and diffusion process are three steps used in the suggested partial encryption scheme. The Authenticated Key Generation is discussed in Section 3.2 in Algorithm 1. The confusion process is performed based on the third output of the 3D QCLM, in which a high degree of scrambling and randomization can be achieved. In addition, the diffusion process is used to change the image pixel values for cryptographic process. The authentication property can be achieved as follows:
- Authenticated public key elliptic curve based on deep convolutional neural network has been introduced in the paper.
- The public key elliptic curve cryptography incorporates with deep CNN is used to achieve authentication properties and integrity.
- Authenticated expansion diffusion matrix (AEDM) is designed in this paper based on the secure hash function (SHA), which uses the output sequence of the DCNN and the output sequence of the robust chaotic map in order to satisfy the authentication property.
| Algorithm 1. PK-Authenticated Key Generation | |
| 1.1 Deep CNN step | |
| Step 1 | Read the multi-image matrixes with the same size in Concatenated Structure A, B |
| Step 2 | Use the multi-image matrixes with the same size in concatenated structure as input to the DCNN to generate 512 output bits (C) |
| Step 3 | Extract the initial conditions and the control parameters from the PK-EC Diffie–Hellman Key Exchange (PK EC DHKE) for the 3D QCLM |
| Step 4 | Run the 3D QCLM and concatenate the 5120 bits from the ‘x’ (the first dimension) output with the output of DCNN 512 bits to get the 5632 bits (L) |
| 1.2 SHA-1 and AEDM | |
| Step 5 | Use the 5632 bits (L) as input to the SHA-1 to produce authenticated 256 bits (S) |
| Step 6 | Run the 3D QCLM and concatenate the 5120 bits from the ‘y’ (the second dimension) output and concatenated with the authenticated 256 bits (S) |
| Step 7 | The AEDM algorithm used the concatenated bit vector of 5632-bit length in order to produce the diffusion matrix “D” of length 256 × 256 × 8-bit vector by using Equations (12)–(16) |
| Step 8 | Convert the diffusion matrix “D” to 256 × 256 pixel (the original image size) |
| Step 9 | The chaotic sequences of the third dimension “z” output of the 3D QCLM output is obtained after a predetermined number of iterations is used to generate the permutation index matrix of length 128 × 128 sorted values based on the “z” output of the 3D QCLM as: Z = sort (z) (13) Here, the function sort (.) returns a random index vector with the ascending order |
3.3.1. Encryption Process
Step 1: Applying DWT to the image “I” yields the approximation matrices LL, diagonal HH, horizontal HL, and vertical LH.
Step 2: The permutation step is done in the frequency domain (the approximation LL’ matrix), by using the sort function indicated in Equation (13); this will cut down on calculation time and cost.
Step 3: Apply IDWT for all sub-bands (LL’, HH, HL, LH) to reconstruct the permuted images.
Step 4: Based on the authenticated diffusion matrix, the diffusion process can be achieved by using the exoring operation between the output of the IDWT step with the output of the authenticated encrypted diffusion matrix (D).
Step 5: The second user uses the same keys and secret same parameters to generate the authenticated encryption diffusion matrix and the permutation index matrix.
3.3.2. Decryption Process
Step 1: Based on the PK-EC Diffie–Hellman Key Exchange, the initial conditions and control parameters for the 3D QCLM can be generated.
Step 2: The second generates the same keys and the secret same parameters to generate the authenticated encryption diffusion matrix and the permutation index matrix.
Step 3: The first step in the decryption process is exoring operation the encrypted image with the output of the authenticated encrypted diffusion matrix (D).
Step 4: The second step in the decryption process started by applying DWT to the encrypted image yields the approximation matrices “LL,” diagonal “HH,” horizontal “HL,” and vertical “LH.”
Step 5: Applying the de-permutation on the (sub-band) approximation matrices “LL” to obtain the de-permutation sub-band “LL.’’
Step 6: Applying the IDWT to the all-sub-bands (“LL,’’ “HH,” “HL,” “LH”) to generate the decrypted image.
4. Simulation Results and Security Analysis
The parameters selected for EC in 64-bit in this study are p = 113, a = −1, b = 17, and G = (52,61). The proposed method will be used for grayscale images and Lena images for results comparison. By measuring the resistance of a cipher system to various attacks (such as statistical attack, known plaintext attack, differential attack, various brute force attack, and ciphertext attack), the robustness of the cipher system is evaluated. In order to evaluate the proposed scheme, a safety analysis was conducted on it by discussing entropy, histograms, correlation coefficient NPCR, UACI, MSE, and the NIST and randomness tests.
4.1. Randomness Test
The proposed AC-DCNN-KG randomization was tested using the 16 statistical tests that made up the NIST test suite. By means of these tests, it is possible to determine whether or not the generated sequence is random. Among these tests, the probability value (the p-value) is mainly relied upon. The boundary between the region of rejection or non-rejection is the comparison of the p-value to the level of significance. In Nest, the significant level is 0.01. When the value of P is less than 0.01, it means that the order is not arbitrary and, therefore, rejected. The order is reasonable and arbitrary when the p value is bigger than 0.01, though. The proposed authentication expansion diffusion matrix’s binary sequence of bits is tested using SP800-22 [62,63], and the results are shown in Table 1.

Table 1.
Proposed AEDM NIST Randomization tests.
4.2. Chi-Squared (Histogram) Analysis
We can spread the image’s pixel intensities by plotting the histogram. For effective encryption, the histogram of the encrypted image must be flat and homogeneous. As a result, there is no connection between the original image and the encrypted image, and no data that could be used to decode the original image. Figure 8 shows the histogram of satellite images sat1, sat2, and sat3. In addition, Figure 8d–f indicates the histogram of (a–c); (g–i) encrypted images of (a–c); (j–l) histograms of (g–i). Finally, as seen in Figure 8, the histogram of the encrypted image is regular and notably different from the histogram of the original image as a result of the diffusion and confusion used in the suggested approach. Thus, it is protected from statistical assaults.
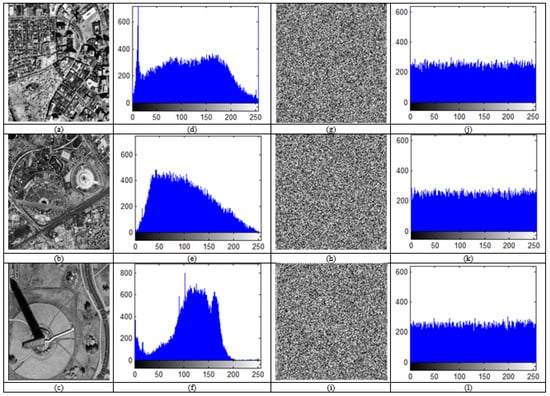
Figure 8.
Histogram of satellite images: (a–c), sat1; sat2; sat3 images; (d–f) Histogram of (a,c,d); (g–i) encrypted images of (a–c); (j–l) histograms of (g–i).
The chi-squared test (), created by renowned statistician Pearson is used to compare two frequencies: the expected frequency and the observed frequency from the experiment [64]. This test is crucial in determining how resilient an encryption is against statistical assault in image encryption. The histogram of an image’s distinctive pattern should be able to be changed by the encryption method into a straight line-like no-pattern known as a uniform distributed histogram. In a conventional image, each grey level has a different frequency, whereas in an encrypted image, each grey level must have the same frequency. Using Equation (14), the Chi-squared test calculated the difference in frequency between the plain image and the encrypted image [64].
In the above-mentioned Equation (14), where is the predicted frequency and represents the observed frequency of each grey level (0–255) for an original image, the difference between the two frequencies must be small in order for the test to be considered successful. When the Chi-square value is equal to α = 0.05, the critical Chi-square value = 293.2478.
In order to use the test, we prepere differents encrypted images by changing 1-bit of a pixel at a time different in original images. The Chi-square value score of different encrypted images is listed in Table 2, which proves that the proposed cryptosystem uniformly distributed the pixel values from 0 to 255. In Table 3, the Chi-square results test for 100 encrypted Lena images under α = 0:05 is studied and compared with recent researches.

Table 2.
Chi-square test results for 10 encrypted images of different sat. images.

Table 3.
Chi-square test results for 100 encrypted Lena images under α = 0:05.
4.3. Correlation Coefficient
Each pixel in the original image has a strong correlation with its surrounding pixels. There is no correlation between neighboring pixels in the vertical, horizontal, or diagonal directions thanks to the strong encrypted system, which minimizes this correlation to the lowest feasible value. The correlation between neighboring pixels of the satellite image is shown in Figure 9a–c, and its cypher image correlation is also obtained in Figure 9d–f in the horizontal, vertical, and diagonal directions. In an image, the correlation coefficient from Equation (15) is calculated between each pair of neighboring pixels. The correlation value should be close to zero [41]. The estimated correlation coefficients for each plain image and its associated cypher image are compared in Table 4 for each image.
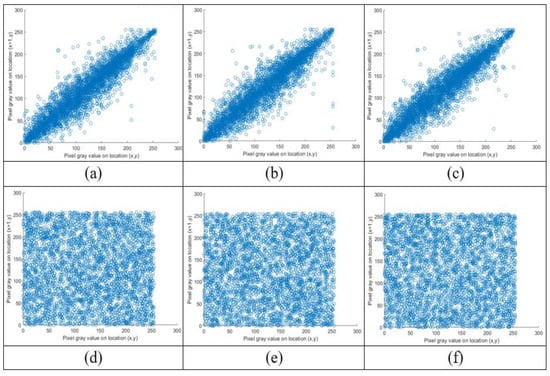
Figure 9.
Lena correlation analysis of ciphered image in three directions. (a,b) Horizontal correlation of the plain image and ciphered image. (c,d) Vertical correlation of the plain image and ciphered image. (e,f) Diagonal correlation of the plain image and ciphered image.

Table 4.
Correlation coefficient values for H, V, and D.
The correlation coefficients of the encrypted images, which were close to zero while the correlation coefficients of the original images were close to one, clearly show that the proposed technique is very robust to statistical attacks. The values of the ciphered images are very near to zero. As a result, the suggested encryption system has good confusion and diffusion properties and can withstand statistical attacks.
4.4. Information Entropy
Entropy, which indicates uncertainty in the cypher image, is used to calculate the unpredictability of the received image. Strong randomness and confidentiality are indicators of a high entropy for the encoded image [65,66,67]. According to one definition, the information system’s entropy is specified as:
where is the source of information, total number of bits represents the symbol , probability of symbol , the best value of the information entropy close to the value 8.
According to Table 5, which shows the information entropy of the ciphered image created by our algorithm to be close to 8, the suggested cryptosystem has a low probability that an attacker will be able to decode a cypher image.

Table 5.
Information entropy of cipher images by the proposed algorithm and references.
4.5. Key Space Analysis
The collection of all keys used in an image encryption system is known as key space. This key set should be sufficiently big to fend off a brute force attack and produce a successful strategy. This scheme can be evaluated by measuring the sensitivity of the key and the number of keys. In the proposed scheme, assuming that the double-precision binary floating-point IEEE 754 format is employed as , the 3D QCLM has different five secret parameters () with = . The SHA output is 256 bits, so it has a key space of . In addition, the keys will be exchanged by means of a 256-bit elliptic curve parameter using ECC. The raw parameters of the logistic map are derived to generate a 256-bit sequence using secretly shared elliptic curve point . The recipient receives the shared key as encrypted data . It is extremely hard to extract from , which necessitates knowing the private key . Note that has a little key size if compared with [30]. In addition, the 256-bit key is used to generate the key matrix. The total key space of the proposed cryptosystem is . It is known that the minimum key space necessary to resist brute-force attacks is , so the entire key space for the proposed cryptosystem is very large. Table 6 provides a comparison of key space with current designs.

Table 6.
Key Space Analysis.
4.6. Key Sensitivity Analysis
A robust encryption technique has high-key sensitivity across the board. As a result, a slight modification to the key results in the production of a completely different cypher image. Additionally, a small modification to the decryption key prevents the recovery of the original sound [28]. By encrypting the various images with the proper key as shown in Figure 10, the suggested approach tests the sensitivity of the key in different three satellite images (sat1, sat2, sat3) (a, b, c). The encrypted image in Figure 10g–l is decrypted using a working different key with a very small changes in the correct key. A slightly different key than the one used to encrypt the original image is used in Figure 10m–o. These significant discrepancies demonstrate that the suggested approach has a high raw key sensitivity and, as a result, a robust resistance against statistical attacks.
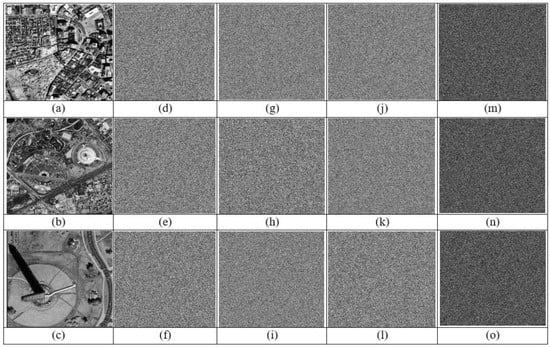
Figure 10.
The key sensitivity analysis for the three different selallite images. (a–c), sat1; sat2; sat3 are the original images; (d–f), (g–i), (j–l) the encrypted three images with modified different 3-bit key in each image. (m–o), illustrate the differences between the encrypted images.
4.7. Differential Attack Analysis
Diffusion performance is one metric used to gauge an image encryption system’s strength. That implies that the plain image’s pixels have a significant influence on the cypher image’s pixels. This time, the resistance to the differential attack can be assessed by altering the plain image by one bit and comparing the variations in the cypher images; as a result, a whole different cypher image must be provided. The image coding scheme is secured using two quantitative measures against differential attack, the two measures are the average intensity of uniform change and the rate of pixel change (NPCR) [66].
where M and N are the width and height of the plain image, respectively, and C1(i, j) and C2(i, j) are the values of the pixels in the position (i, j) of the two cypher pictures. The number of grey levels is 255; C1 and C2 are the plain image before and after changing one bit; and D (i, j) is specified as follows:
The conceptual values of 𝑁𝑃𝐶𝑅 = 99.61% and 𝑈𝐴𝐶𝐼 = 33.46. When the NPCR and UACI values are greater than or equal to these theoretical values, a better and more secure coding system is obtained. The value of one randomly chosen pixel was changed for the suggested technique, and the cypher images of the original image and the modified image, C1 and C2, were then calculated respectively, and NPCR and UACI were calculated for the different images. The result is shown in Table 7.

Table 7.
NPCR and UACI values for Lena Image.
4.8. Noise Attack Analysis
A data loss attack occurs when a potential intruder intentionally removes pixels from a specific area of an encrypted image or loses some of the image as it is being transmitted over the internet. If a cryptosystem recovers the crucial data from the encrypted image, which loses the data, it is flawless. Images often contain information, but during transmission, some noise contaminates the image [65,66]. The original information in the image can be missed if noise appears. (e.g., the sound of pepper and salt). This article examines the impact of our encryption system on the image of Lena, and different salt and pepper noise ratios serve as indicators of the intensity of the attack. Gaussian noise, salt and pepper, speckle noise, and the filtering attack are studied for the noise attack analysis [65,66]. In this section, we added the ciphertext image with the noise before decryption step. The PSNR is used to evaluate the degree to which the proposed technique obscures the image encrypted in order to show its efficacy. The lowest possible PSNR value is ideal for the highest level of encryption. Using the following mathematical formula, PSNR is determined [65,66]:
where I (i, j) is the pixel value in plane image at pixel point (i, j), and C (i, j) is the pixel value in cipher image at pixel point (i, j). Figure 10 displays the decrypted image with various noise levels. Table 8 shows the PSNR for different encrypted images, and it concluded that the PSNR possesses a very small value, which means that the proposed cryptosystem has a robust encryption algorithm.

Table 8.
Peak signal-to-noise ratio for different encrypted images.
Table 9 and Table 10 show the Gaussian noise, salt and pepper, speckle noise, and filtering attack effects on the decrypted Lena images and its PSNR values. These tables demonstrate that the proposed technique can withstand noise attacks by showing that when the noise reaches different level values, the decryption result can also be detected with the human eye.

Table 9.
PSNR for Lina image with Gaussian and salt and pepper noise.

Table 10.
PSNR for Lina image with speckle noise and filtering attack.
4.9. Computational Complexty
The relationship between complexity and cryptography is very important in encryption algorithm designs. The encryption algorithms consist of the key generation step and the image encryption step. In the key generation step, the time complexity of generation chaotic sequence with length is . In addition, the image encryption step, pixel permutation, and diffusion are both linear operations in which the time complexity of permutation is and the time complexity of diffusion is the time complexity of permutation. Finally, the total time complexity of the image encryption step is [67,68].
In the proposed cryptosystem, using DWT in the image encryption, only the approximation matrix LL is permuted in the frequency domain. Therefore, the time complexity of permutation can be obtained by . The diffusion process is applied after using the IDWT for to the four sub-bands (LL, HH, HL, LH). Then, the time complexity of the encryption process is . The total time complexity of the proposed cryptosystem can be computed as + . Finally, the proposed partial image cryptosystem is faster than the fully image cryptosystem. At an image with the size of (M = 256, N = 256), the time complexity of the full encryption process is equal to = 131,072. For the proposed partial encryption, the time complexity is equal to + . Therefore, the time complexity is 81920, and computational complexity saving is 37.5% compared with any full encryption scheme. For images with a size of where are (512 ) and (1024 ), the computational complexity saving will be increased.
5. Conclusions
A new elliptic curve with public key authentication based on deep convolutional neural network (APK-EC-DCNN) for cybersecurity image encryption application is suggested. The public key elliptic curve cryptography, incorporated with deep CNN, is used to achieve the authentication properties and integrity. In addition, an authenticated expansion diffusion matrix (AEDM) is designed in this paper based on the secure hash function, which uses the output sequence of the DCNN and the output sequence of the robust chaotic map in order to satisfy the authentication property. The experimental analysis shows that the proposed APK-EC-DCNN cryptosystem satisfies a very competitive encryption performance and can resist common attacks. In addition, the results indicate that the proposed cryptosystem has large key space, pseudo-randomness, one-time pad, and highly sensitive to change. In addition, the deep-learning mechanism is used in the encryption process, which considered a new direction of the encryption cryptosystems. The robustness of the encryption system is assessed by testing the resistance of the proposed system to numerous attacks. A safety analysis was done on the suggested method to evaluate it, and it included discussions of the histogram, entropy, correlation coefficient, NPCR, UACI, and NIST randomness tests.
This work contributes to the existing literature by further exploring the weaknesses of using the deep CNN as a feature extraction of an images as a secret key, which is used in recent works on image encryption. Moreover, the proposed cryptosystem introduces the use of public key elliptic curve cryptosystem in order to generate authenticated public key. In addition, an authenticated chaotic DCNN key generator is designed in order to achieved the authentication property. Moreover, the partial image encryption based on the frequency domain is used the discrete wavelet transform. The PK-EC Diffie–Hellman Key Exchange is used to share and extract the initial conditions and the control parameters for the 3D QCLM.
In future work, we will suggest a new deep CNN suitable for generating a digital signature in order to satisfy the identity property. In addition, the integration of the digital signature with the encryption can be designed as a digital deep CNN signcryption scheme. In addition, future research could focus on stream video encryption/decryption, watermarking, data hiding in encrypted images. Moreover, a compression–encryption system based on a new Deep Convolutional Neural Network will be suggested.
Author Contributions
Conceptualization, E.A.A.H., S.A., H.K. and T.M.H.; methodology, E.A.A.H. and T.M.H.; software, E.A.A.H. and T.M.H.; validation, E.A.A.H., S.A., H.K. and T.M.H.; formal analysis, E.A.A.H., S.A., H.K. and T.M.H.; writing—original draft preparation, E.A.A.H. and T.M.H.; writing—review and editing, E.A.A.H., S.A., H.K. and T.M.H.; visualization, E.A.A.H.; supervision, E.A.A.H. and T.M.H.; project administration, S.A. and H.K.; funding acquisition, S.A. All authors have read and agreed to the published version of the manuscript.
Funding
This research is funded by the King Saud University under project number RSP2023R260.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Acknowledgments
The authors would like to extend their gratitude to King Saud University (Riyadh, Saudi Arabia) for funding this research through Researchers Supporting Project number (RSP2023R260).
Conflicts of Interest
The authors declare no conflict of interest.
References
- Zhu, S.; Wang, G.; Zhu, C. A Secure and Fast Image Encryption Scheme based on Double Chaotic S-Boxes. Entropy 2019, 21, 790. [Google Scholar] [CrossRef] [PubMed]
- Parvaz, R.; Zarebnia, M. A combination chaotic system and application in color image encryption. Opt. Laser Technol. 2018, 101, 30–41. [Google Scholar] [CrossRef]
- Hua, Z.; Zhou, Y. One-Dimensional Nonlinear Model for Producing Chaos. IEEE Trans. Circuits Syst. 2018, 65, 235–246. [Google Scholar] [CrossRef]
- Zhou, Y.; Bao, L.; Chen, C.P. A New 1D Chaotic System for Image Encryption. Signal Process. 2014, 97, 172–182. [Google Scholar] [CrossRef]
- Liu, L.F.; Miao, S.X. A new image encryption algorithm based on logistic chaotic map with varying parameter. Springer-Plus 2016, 5, 289. [Google Scholar] [CrossRef]
- Liu, L.; Miao, S. A New Simple One-Dimensional Chaotic Map and Its Application for Image Encryption. Multimed. Tools Appl. 2018, 77, 21445–21462. [Google Scholar] [CrossRef]
- Lan, R.; He, J.; Wang, S.; Gu, T.; Luo, X. Integrated chaotic systems for image encryption. Signal Process. 2018, 147, 133–145. [Google Scholar] [CrossRef]
- Huang, H.; Yang, S.; Ye, R. Efficient symmetric image encryption by using a novel 2D chaotic system. IET Image Process. 2020, 14, 1157–1163. [Google Scholar] [CrossRef]
- Liu, L.; Wang, D.; Lei, Y. An Image Encryption Scheme Based on Hyper Chaotic System and DNA with Fixed Secret Keys. IEEE Access 2020, 8, 46400–46416. [Google Scholar] [CrossRef]
- Wu, Y.; Zhou, Y.; Bao, L. Discrete Wheel-Switching Chaotic System and Applications. IEEE Trans. Circuits Syst. 2014, 61, 3469–3477. [Google Scholar] [CrossRef]
- Chai, X.; Yang, K.; Gan, Z. A new chaos-based image encryption algorithm with dynamic key selection mechanisms. Multimed. Tools Appl. 2017, 76, 9907–9927. [Google Scholar] [CrossRef]
- Lin, R.M.; Ng, T.Y. Secure Image Encryption Based on an Ideal New Nonlinear Discrete Dynamical System. Math. Probl. Eng. 2018, 2018, 6797386. [Google Scholar] [CrossRef]
- Zhou, Y.; Hua, Z.; Pun, C.M.; Chen, C.L. Cascade Chaotic System with Applications. IEEE Trans. Cybern. 2015, 45, 2001–2012. [Google Scholar] [CrossRef]
- Hua, Z.; Zhou, Y. Dynamic Parameter Control Chaotic System. IEEE Trans. Cybern. 2016, 46, 3330–3341. [Google Scholar] [CrossRef]
- Abdoun, N.; El Assad, S.; D’eforges, O.; Assaf, R.; Khalil, M. Design and security analysis of two robust keyed hash functions based on chaotic neural networks. J. Ambient. Intell. Humaniz. Comput. 2019, 11, 2137–2161. [Google Scholar] [CrossRef]
- Abdoun, N.; Assad, S.E.; Hammoud, K.; Assaf, R.; Khalil, M.; Deforges, O. New keyed chaotic neural network hash function based on sponge construction. In Proceedings of the 2017 12th International Conference for Internet Technology and Secured Transactions (ICITST), Cambridge, UK, 11–14 December 2017. [Google Scholar] [CrossRef]
- Senthilkumar, C.; Thirumalaisamy, M.; Dhanaraj, R.K.; Nayyar, A. DNA Encoded Color Image Encryption Based on Chaotic Sequence from Neural Network. J. Sign. Process. Syst. 2023, 95, 459–474. [Google Scholar] [CrossRef]
- Parida, P.; Pradhan, C.; Alzubi, J.A.; Javadpour, A.; Gheisari, M.; Liu, Y.; Lee, C.C. Elliptic curve cryptographic image encryption using Henon map and Hopfield chaotic neural network. Multimed. Tools Appl. 2023, 1–26. [Google Scholar] [CrossRef]
- Ahmad, M.; Singh, S.; Khurana, S. Cryptographic one-way hash function generation using twelve-terms 4D nonlinear system. Int. J. Inf. Technol. 2018, 13, 2295–2303. [Google Scholar] [CrossRef]
- Chankasame, W.; San-Um, W. A chaos-based keyed hash function for secure protocol and message authentication in mobile ad hoc wireless networks. In Proceedings of the 2015 Science and Information Conference (SAI), London, UK, 28–30 July 2015; pp. 1357–1364. [Google Scholar] [CrossRef]
- Chenaghlu, M.A.; Jamali, S.; Khasmakhi, N.N. A novel keyed parallel hashing scheme based on a new chaotic system. Chaos Solitons Fractals 2016, 87, 216–225. [Google Scholar] [CrossRef]
- Li, Y.; Ge, G.; Xia, D. Chaotic hash function based on the dynamic S-Box with variable parameters. Nonlinear Dyn. 2016, 84, 2387–2402. [Google Scholar] [CrossRef]
- Al-Aali, Y.; Boussakta, S. Lightweight Hash Function Based on the New Mersenne Number Transform Family. In Proceedings of the 2022 7th International Conference on Frontiers of Signal Processing (ICFSP), Paris, France, 7–9 September 2022. [Google Scholar]
- Ambedkar, B.R.; Bharti, P.K.; Akhtar, H. Design and Analysis of Hash Algorithm Using Autonomous Initial Value Proposed Secure Hash Algorithm 64. In Proceedings of the 2021 IEEE 18th India Council International Conference (INDICON), Guwahati, India, 19–21 December 2021. [Google Scholar]
- Wang, Y.; Chen, L.; Wang, X.; Wu, G.; Yu, K.; Lu, T. The design of keyed hash function based on CNN-MD structure. Chaos Solitons Fractals 2021, 152, 111443. [Google Scholar] [CrossRef]
- Abdelfatah, R.I.; Baka, E.A.; Nasr, M.E. Keyed Parallel Hash Algorithm Based on Multiple Chaotic Maps (KPHA-MCM). IEEE Access 2021, 9, 130399–130409. [Google Scholar] [CrossRef]
- Xu, C.X. Modern Cryptography; Tsinghua University Press: Beijing, China, 2015. [Google Scholar]
- Kumar, D.; Joshi, A.B.; Singh, S.; Mishra, V.N. Digital color-image encryption scheme based on elliptic curve cryptography ElGamal encryption and 3D Lorenz map. AIP Conf. Proc. 2021, 2364, 20026. [Google Scholar]
- Ma, C.G. Modern Cryptography; Springer: Berlin/Heidelberg, Germany, 2022. [Google Scholar]
- Benssalah, M.; Rhaskali, Y.; Drouiche, K. An efficient image encryption scheme for TMIS based on elliptic curve integrated encryption and linear cryptography. Multimedia Tools Appl. 2020, 80, 2081–2107. [Google Scholar] [CrossRef]
- Azam, N.A.; Murtaza, G.; Hayat, U. A novel image encryption scheme based on elliptic curves and coupled map lattices. Optik 2023, 274, 170517. [Google Scholar] [CrossRef]
- Luo, W.; Li, J.; Yang, J.; Xu, W.; Zhang, J. Convolutional Sparse Autoencoders for Image Classification. IEEE Trans. Neural Netw. Learn. Syst. 2017, 29, 3289–3294. [Google Scholar] [CrossRef]
- Tang, P.; Wang, X.; Shi, B.; Bai, X.; Liu, W.; Tu, Z. Deep fishernet for image classification. IEEE Trans. Neural Netw. Learn. Syst. 2018, 30, 2244–2250. [Google Scholar] [CrossRef]
- Li, G.; Yu, Y. Contrast-Oriented Deep Neural Networks for Salient Object Detection. IEEE Trans. Neural Netw. Learn. Syst. 2018, 29, 6038–6051. [Google Scholar] [CrossRef]
- Ding, Y.; Luo, C.; Li, C.; Lan, T.; Qin, Z. High-order correlation detecting in features for diagnosis of Alzheimer’s disease and mild cognitive impairment. Biomed. Signal Process. Control 2019, 53, 101564. [Google Scholar] [CrossRef]
- Guo, W.; Aarabi, P. Hair Segmentation Using Heuristically-Trained Neural Networks. IEEE Trans. Neural Netw. Learn. Syst. 2016, 29, 25–36. [Google Scholar] [CrossRef]
- Chen, H.; Qin, Z.; Ding, Y.; Tian, L.; Qin, Z. Brain tumor segmentation with deep convolutional symmetric neural network. Neurocomputing 2020, 392, 305–313. [Google Scholar] [CrossRef]
- Goodfellow, I.; Pouget-Abadie, J.; Mirza, M.; Xu, B.; Warde-Farley, D.; Ozair, S.; Courville, A.; Bengio, Y. Generative adversarial nets. Adv. Neural Inf. Process. Syst. 2014, 27, 2672–2680. [Google Scholar]
- Fang, P.; Liu, H.; Wu, C. A Novel Chaotic Block Image Encryption Algorithm Based on Deep Convolutional Generative Adversarial Networks. IEEE Access 2020, 9, 18497–18517. [Google Scholar] [CrossRef]
- Ding, Y.; Tan, F.; Qin, Z.; Cao, M.; Choo, K.-K.R.; Qin, Z. DeepKeyGen: A Deep Learning-Based Stream Cipher Generator for Medical Image Encryption and Decryption. IEEE Trans. Neural Netw. Learn. Syst. 2021, 33, 4915–4929. [Google Scholar] [CrossRef]
- Erkan, U.; Toktas, A.; Enginoğlu, S.; Akbacak, E.; Thanh, D.N.H. An image encryption scheme based on chaotic logarithmic map and key generation using deep CNN. Multimedia Tools Appl. 2022, 81, 7365–7391. [Google Scholar] [CrossRef]
- Singh, K.N.; Baranwal, N.; Singh, O.P.; Singh, A.K. SIELNet: 3D Chaotic-map-based Secure Image Encryption using Customized Residual Dense Spatial Network. IEEE Trans. Consum. Electron. 2022, 1. [Google Scholar] [CrossRef]
- Canniere, C.D. Trivium: A stream cipher construction inspired by block cipher design principles. In Proceedings of the International Conference on Information Security, Samos, Greece, 30 August–2 September 2006. [Google Scholar]
- Mannai, O.; Becheikh, R.; Rhouma, R. A new stream cipher based on nonlinear dynamic system. In Proceedings of the 2018 26th European Signal Processing Conference (EUSIPCO), Rome, Italy, 3–7 September 2018; pp. 316–320. [Google Scholar]
- Ogasahara, Y.; Hori, Y.; Koike, H. Implementation of pseudo linear feedback shift register physical unclonable function on silicon. In Proceedings of the 2016 IEEE International Symposium on Circuits and Systems (ISCAS), Montreal, QC, Canada, 22–25 May 2016; pp. 758–761. [Google Scholar]
- Hemattil, M.; Ahmadi, A.; Makkil, S.V.; Ahmadi, M. Hardware design of chaotic pseudo-random number generator based on nonlinear feedback shift register. In Proceedings of the 2018 IEEE 61st International Midwest Symposium on Circuits and Systems (MWSCAS), Windsor, ON, Canada, 5–8 August 2018; pp. 980–983. [Google Scholar]
- Miroschnyk, M.; Pakhomov, Y.; German, E.; Shkil, A.; Kulak, E.; Kucherenko, D. Design automation of testable finite state machines. In Proceedings of the 2017 IEEE East-West Design & Test Symposium (EWDTS), Novi Sad, Serbia, 29 September–2 October 2017; pp. 1–6. [Google Scholar]
- Cao, G.; Wang, X. Image encryption based on the combination of roulette wheel selection with linear congruence pixel transformation. Multimedia Tools Appl. 2019, 78, 10625–10647. [Google Scholar] [CrossRef]
- Hua, Z.; Zhou, B.; Zhou, Y. Sine-Transform-Based Chaotic System with FPGA Implementation. IEEE Trans. Ind. Electron. 2017, 65, 2557–2566. [Google Scholar] [CrossRef]
- Shemanske, T.R. Modern Cryptography and Elliptic Curves; American Mathematical Society: Providence, RI, USA, 2017. [Google Scholar]
- Schneier, B. Applied Cryptography, 2nd ed.; John Wiley & Sons: New York, NY, USA, 1996. [Google Scholar]
- Abdel Haleem, S.H.; Abd-El-Hafiz, S.K.; Radwan, A.G. A generalized framework for elliptic curves based PRNG and its utilization in image encryption. Sci. Rep. 2022, 12, 13278. [Google Scholar] [CrossRef]
- El Kinani, E.H. Fast mapping method based on matrix approach for elliptic curve cryptography. Int. J. Inf. Netw. Secur. 2012, 1, 54–59. [Google Scholar] [CrossRef]
- Kolhekar, M.; Jadhav, A. Implementation of elliptic curve cryptography on text and image. Int. J. Enterprise Comput. Bus. Syst. 2011, 1, 1–13. [Google Scholar]
- Barani, M.J.; Valandar, M.Y.; Ayubi, P. A new digital image tamper detection algorithm based on integer wavelet transform and secured by encrypted authentication sequence with 3D quantum map. Opt.—Int. J. Light Electron. Opt. 2019, 187, 205–222. [Google Scholar] [CrossRef]
- Sinha, B.; Kumar, S.; Pradhan, C. Comparative analysis of color image encryption using 3D chaotic maps. In Proceedings of the International Conference on Communication and Signal Processing (ICCSP), Melmaruvathur, India, 6–8 April 2016; pp. 332–335. [Google Scholar]
- Liu, X.; Xiao, D.; Xiang, Y. Quantum Image Encryption Using Intra and Inter Bit Permutation Based on Logistic Map. IEEE Access 2019, 7, 6937–6946. [Google Scholar] [CrossRef]
- Ye, G.; Jiao, K.; Pan, C.; Huang, X. An Effective Framework for Chaotic Image Encryption Based on 3D Logistic Map. Secur. Commun. Netw. 2018, 5, 11. [Google Scholar] [CrossRef]
- Mohamed, N.A.E.-S.; Youssif, A.; El-Sayed, H.A.-G. Fast and Robust Image Encryption Scheme Based on Quantum Logistic Map and Hyperchaotic System. Complexity 2022, 2022, 3676265. [Google Scholar] [CrossRef]
- Ghassemi, S.; Magli, E. Convolutional Neural Networks for On-Board Cloud Screening. Remote Sens. 2019, 11, 1417. [Google Scholar] [CrossRef]
- Ramzan, F.; Khan, M.U.G.; Rehmat, A.; Iqbal, S.; Saba, T.; Rehman, A.; Mehmood, Z. A Deep Learning Approach for Automated Diagnosis and Multi-Class Classification of Alzheimer’s Disease Stages Using Resting-State fMRI and Residual Neural Networks. J. Med. Syst. 2020, 44, 37. [Google Scholar] [CrossRef]
- FIPS 140-2; Security Requirements for Cryptographic Modules. NIST: Gaithersburg, MA, USA, 2000.
- Rukhin, A.; Soto, J.; Nechvatal, J.; Smid, M.; Barker, E.; Leigh, S.; Levenson, M.; Vangel, M.; Banks, D.; Heckert, A.; et al. A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications; NIST Special Publication 800-22 with revisions; NIST: Gaithersburg, MA, USA, 2001. [Google Scholar]
- Firdous, A.; Rehman, A.U.; Missen, M.M.S. A Gray Image Encryption Technique Using the Concept of Water Waves, Chaos and Hash Function. IEEE Access 2021, 9, 11675–11693. [Google Scholar] [CrossRef]
- Jiang, X.; Jiang, G.; Wang, Q.; Shu, D. Image encryption algorithm based on 2D-CLICM chaotic system. IET Image Process. 2023, 17, 2127–2141. [Google Scholar] [CrossRef]
- Hagras, E.A.; El-Mahallawy, M.S.; Eldin, A.Z.; Fakhr, M.W. Robust secure and blind watermarking based on dwt dct partial multi map chaotic encryption. Int. J. Multimed. Its Appl. 2011, 3, 37. [Google Scholar] [CrossRef]
- Moya-Albor, E.; Romero-Arellano, A.; Brieva, J.; Gomez-Coronel, S.L. Color Image Encryption Algorithm Based on a Chaotic Model Using the Modular Discrete Derivative and Langton’s Ant. Mathematics 2023, 11, 2396. [Google Scholar] [CrossRef]
- Zhang, B.; Rahmatullah, B.; Wang, S.L.; Liu, Z. A plain-image correlative semi-selective medical image encryption algorithm using enhanced 2D-logistic map. Multimed. Tools Appl. 2023, 82, 15735–15762. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).







