An Adaptive Distributed Denial of Service Attack Prevention Technique in a Distributed Environment
Abstract
1. Introduction and Background
1.1. Introduction
1.2. Literature Review
2. Proposed Solution and Methodology (SFaDMT)
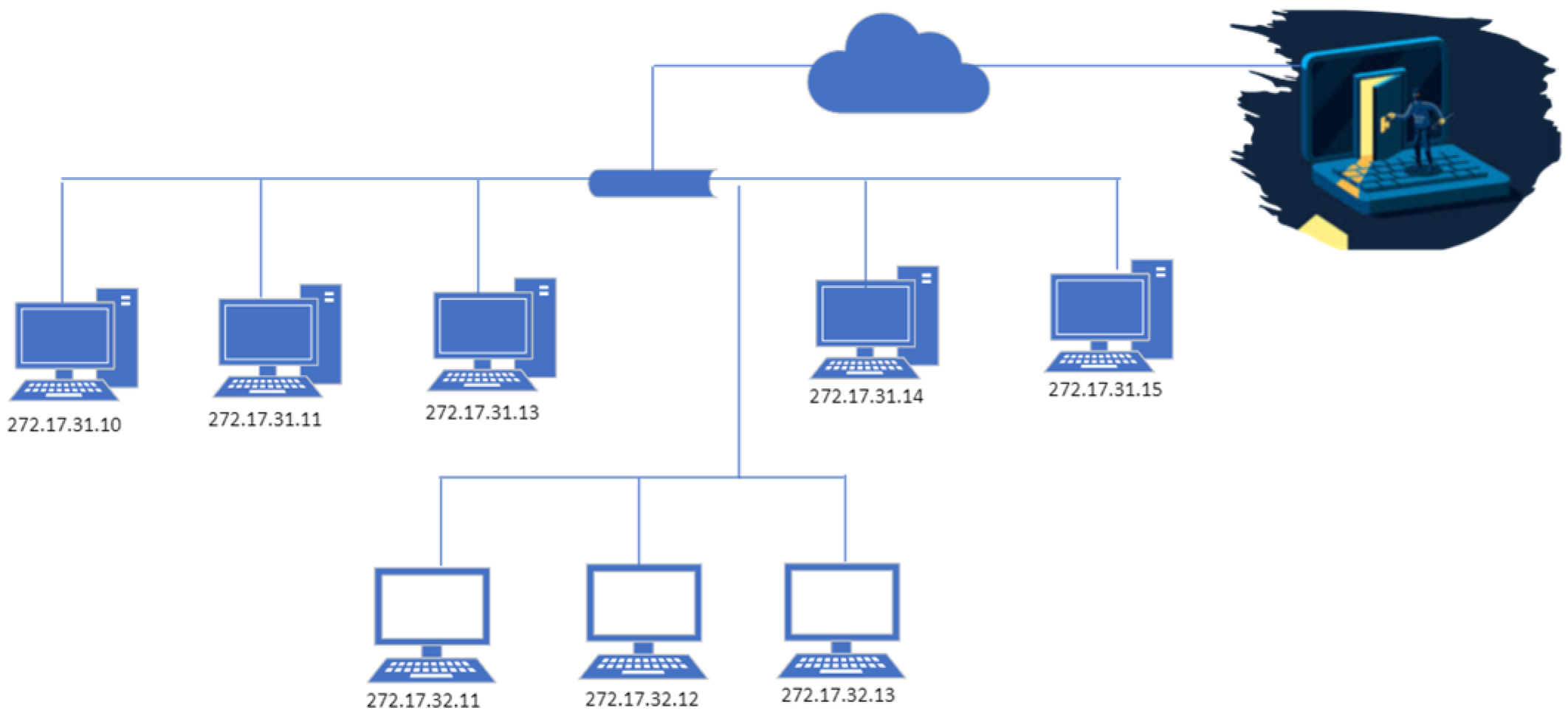
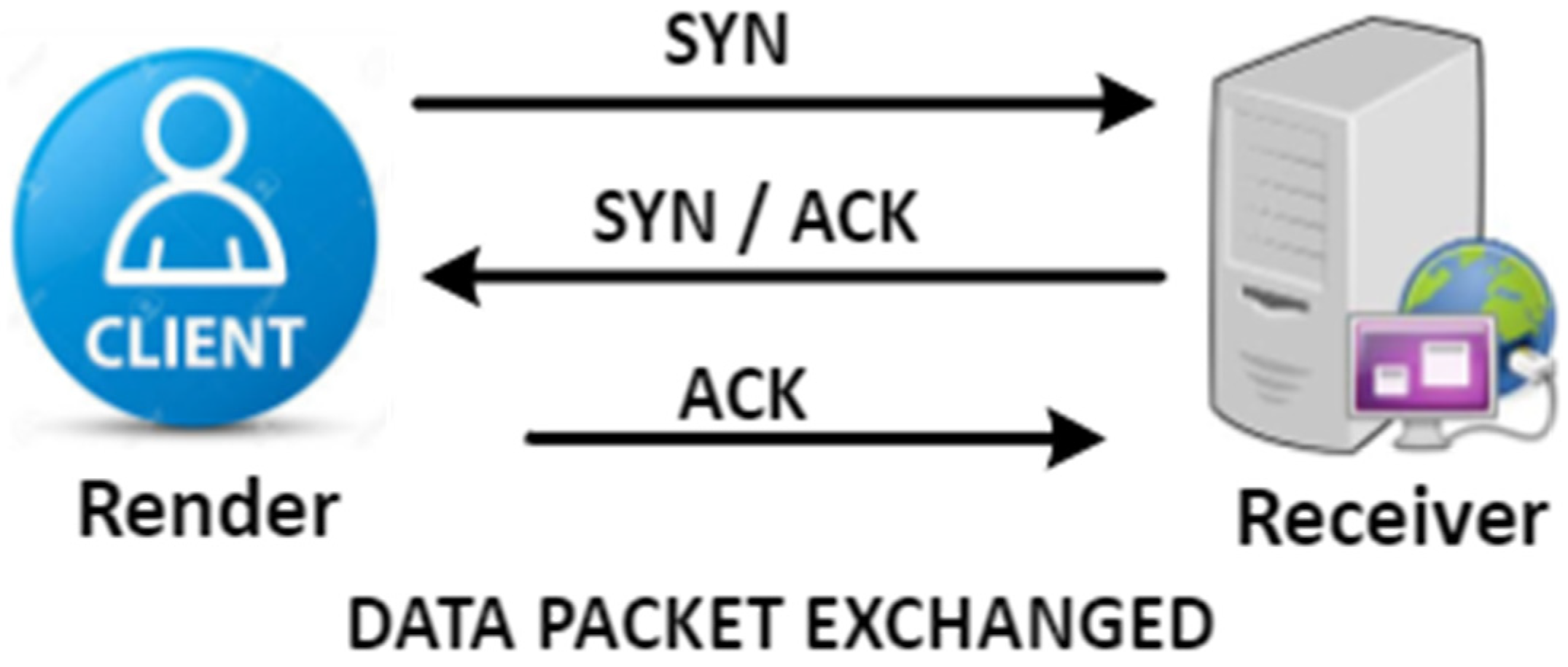
2.1. Establishment of TCP Connection—(Three-Sided Shake of TCP)
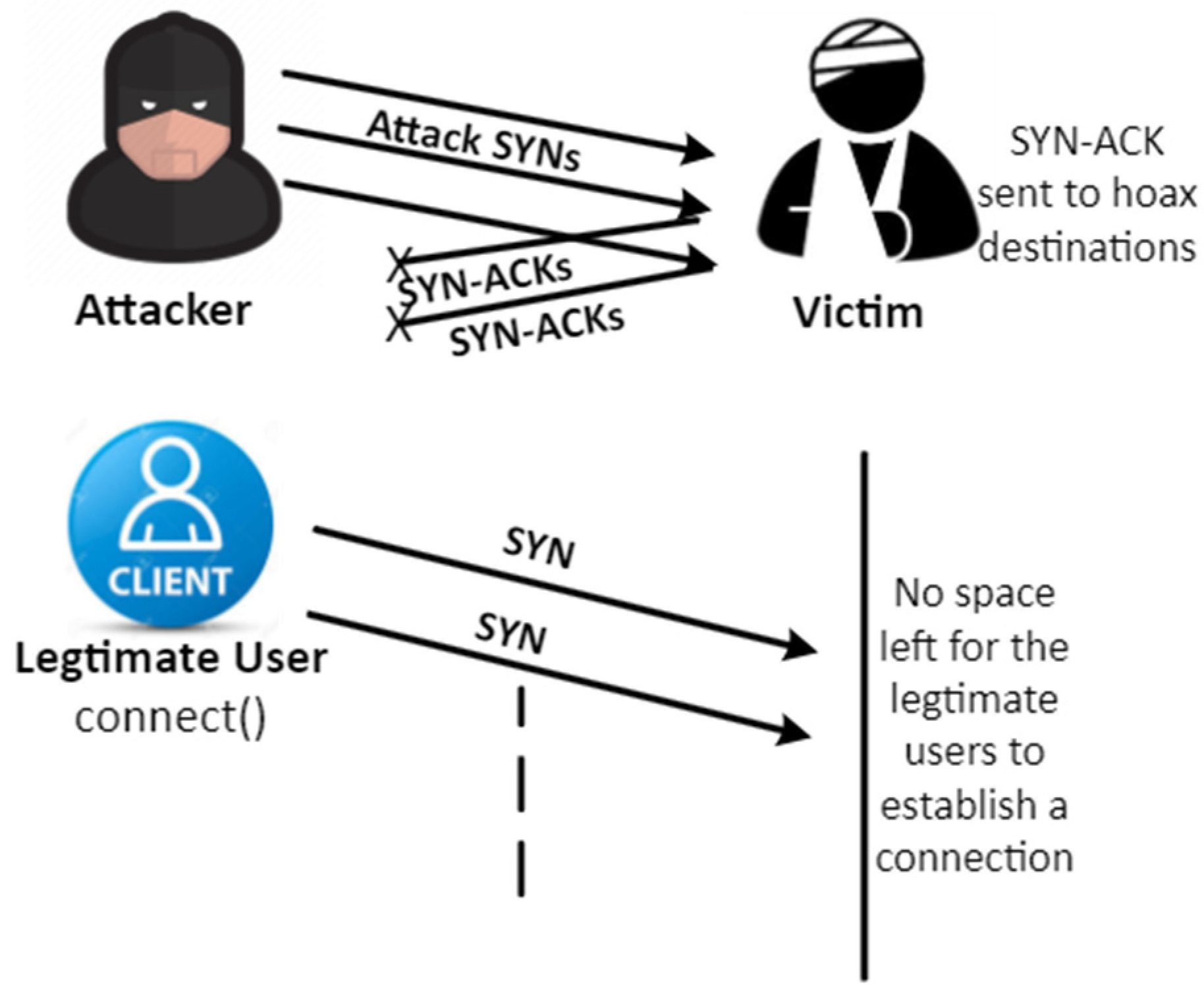
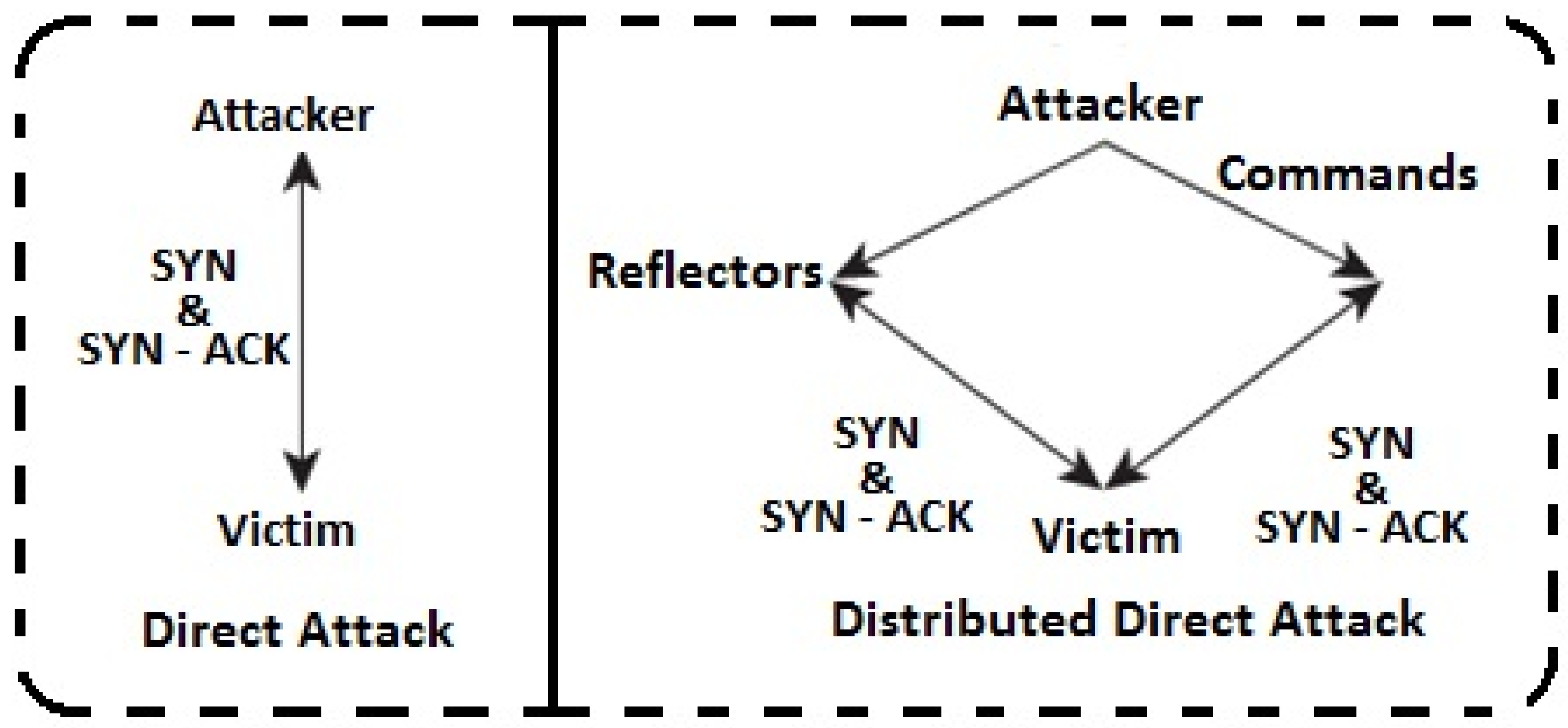
2.2. The Technique for DoS/DDoS Outbreak (TCP-SYN Flooding Intrusion)
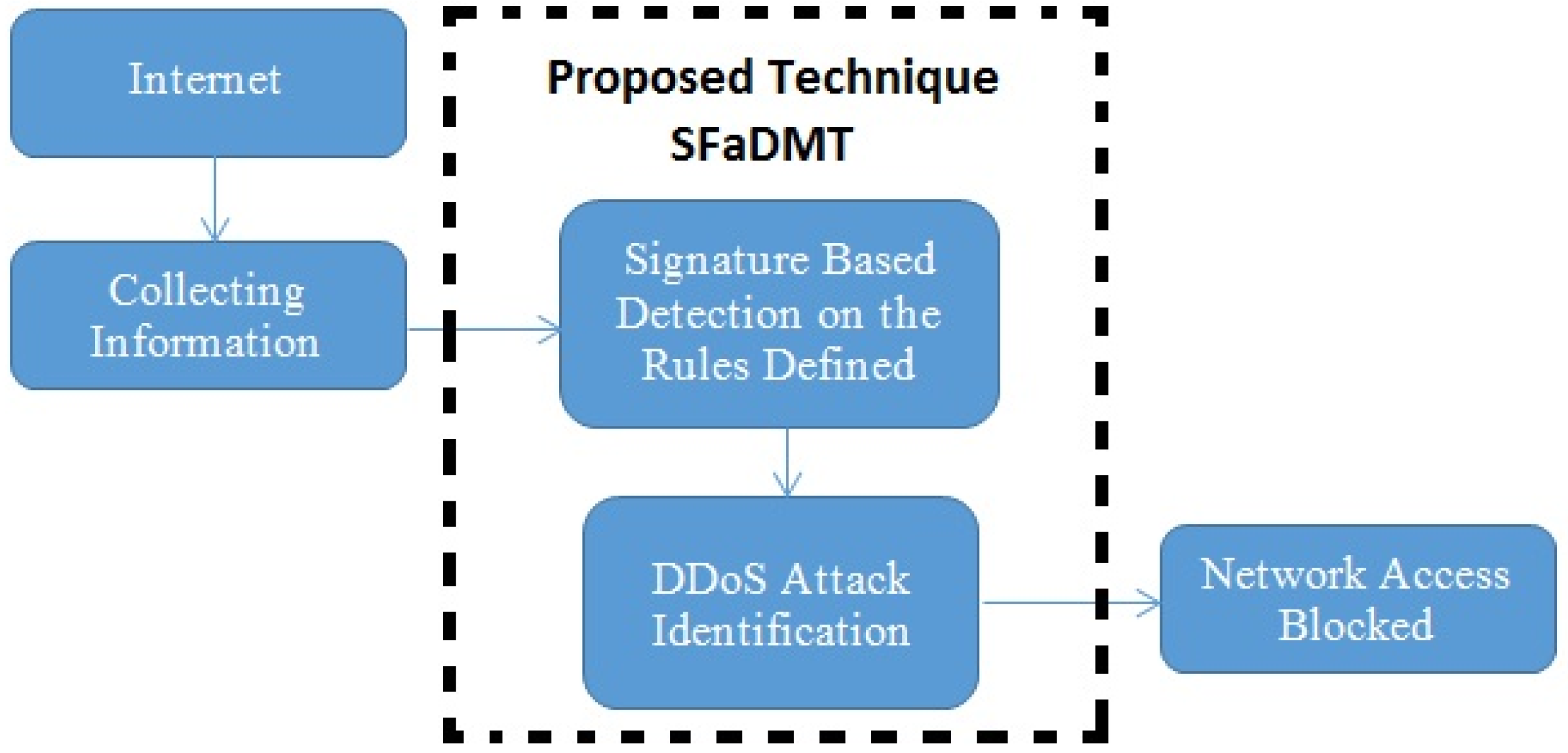
3. Proposed Technique (SFaDMT)
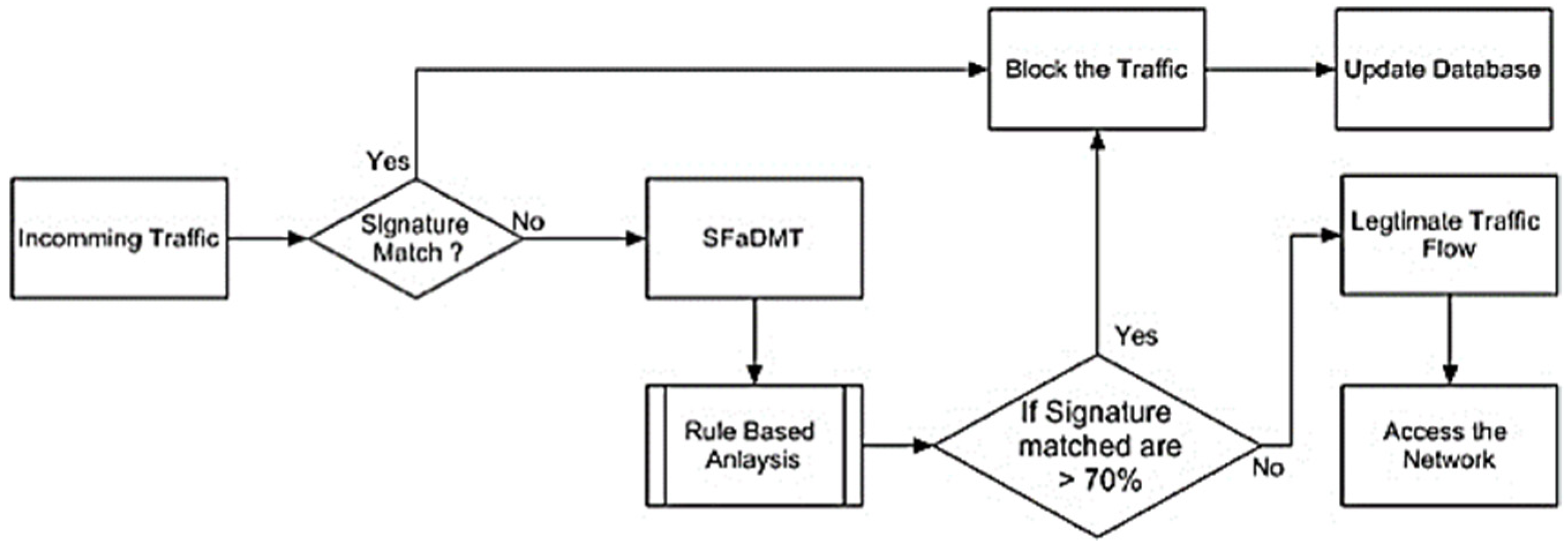
3.1. Flowchart
- (a)
- Application of a multi-deposit preceptor deposit in a centralized environment.
- (b)
- Pattern and signature-centred strategies are used to identify DDoS intrusion.
3.2. The Model of SFaDMT
3.3. Proposed Solution and Methodology
3.4. Guidelines for the Categorization of SYN Flood Malevolent Instructions/Apps
| Algorithm 1. Check for Half Open TCP Connection. |
| while |
| read present connection; |
| if (connection attempt is not successful || |
| TCP connection is not synchronized at both ends || |
| TCP connection is aborted || connection cannot be closed) |
| then |
| the TCP connection is malicious; |
| else |
| the TCP connection is legitimate; |
| end |
| end |
| Algorithm 2. The following algorithm implements the above rules and detects malicious traffic based on signatures from the already-saved attack signature database. |
| Input: Packet Pkt |
| Output: Generates logs when DDoS Attacks are performed |
| while (true) |
| if (a packet is not equal to null) do |
| if (TCP packet arrives) do |
| TCPCount++; |
| if (TCP Packets % threshold ≥ 70) do |
| Alarm “TCP Flow Attack has been detected!”; |
| else if (IP Packets % threshold ≥ 70 && source_ip == destination_ip) do |
| Alarm “IP Address Pattern has been detected!”; |
| else |
| Show “Error” |
| end if; |
| end if; |
| end if; |
| Algorithm 3. The following algorithm is the mitigation of attack traffic performed using SFaDMT. |
| Input: Data Traffic Dt |
| Output: Analyze Dt |
| while (true) |
| if (Dt arrives) do |
| Dt++; |
| if (Packet Header == Legitimate Dt) do |
| Display “Legitimate Traffic and can access the network”; |
| else if (Packet Header == Malicious Dt) do |
| Display “Malicious Traffic has been detected and mitigated”; |
| else if (Packet Header == Unknown Dt) do |
| Display “Deep Analysis needs to be performed on this packet”; |
| else if (Packet Analysis == Dt Attack Pattern Detected) do |
| Display “Restrict traffic from the network”; |
| else |
| Display “Legitimate traffic has been detected and mitigated”; |
3.5. Rules for the Filtration of SYN Flood Malicious Packets
4. Result and Analysis
4.1. Case I
4.2. Case II
4.3. Case III
4.4. Case IV
5. Evaluation Parameters
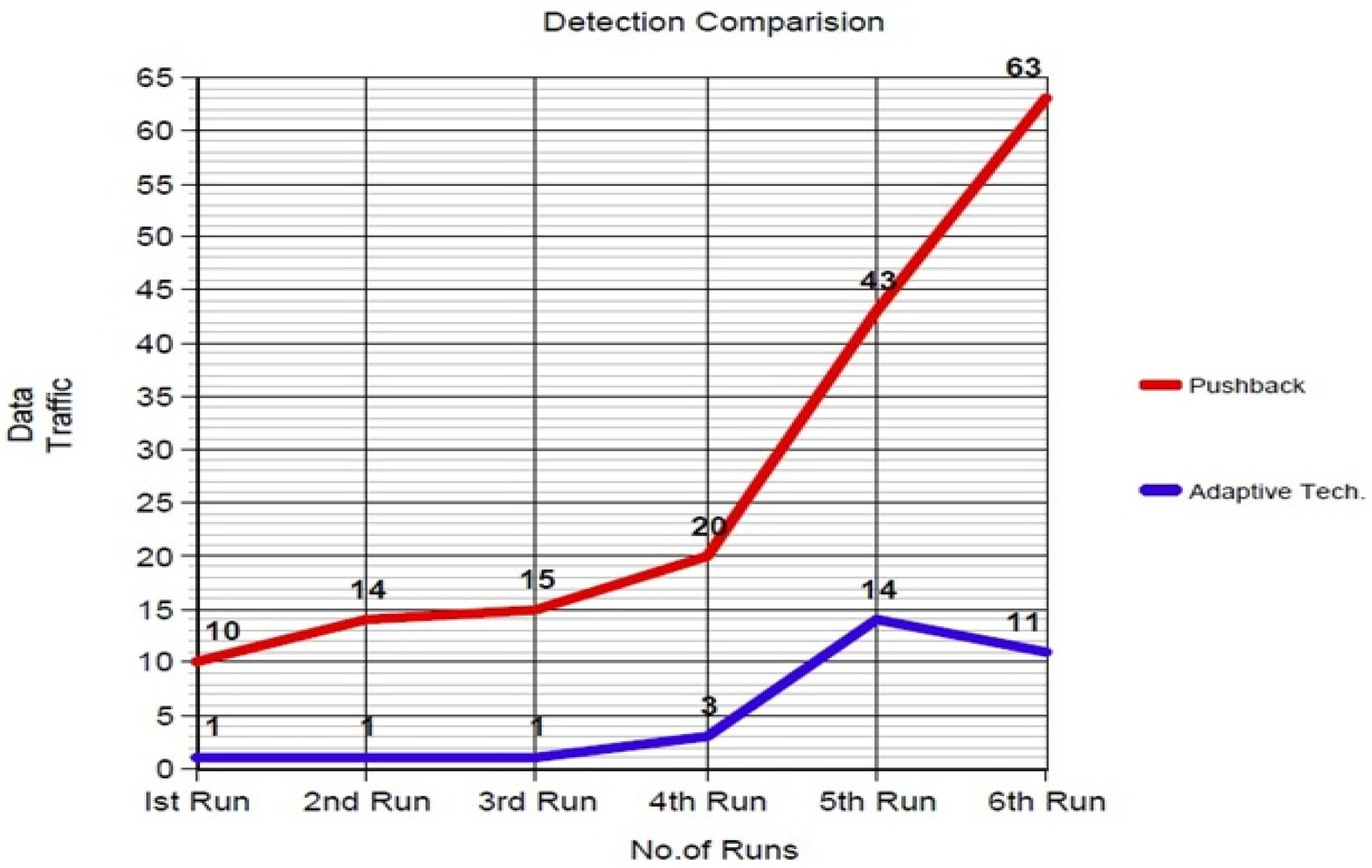
Analysis of the Adaptive Technique with the Previous Technique
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Hwang, R.H.; Peng, M.C.; Huang, C.W.; Lin, P.C.; Nguyen, V.L. An unsupervised deep learning model for early network traffic anomaly detection. IEEE Access 2020, 8, 30387–30399. [Google Scholar] [CrossRef]
- Novaes, M.P.; Carvalho, L.F.; Lloret, J.; Proença, M.L. Long short-term memory and fuzzy logic for anomaly detection and mitigation in software-defined network environment. IEEE Access 2020, 8, 83765–83781. [Google Scholar] [CrossRef]
- Lima Filho, F.S.D.; Silveira, F.A.; de Medeiros Brito Junior, A.; Vargas-Solar, G.; Silveira, L.F. Smart detection: An online approach for DoS/DDoS attack detection using machine learning. Secur. Commun. Netw. 2019, 2019, 1574749. [Google Scholar] [CrossRef]
- Li, Z.; Rios, A.L.G.; Xu, G.; Trajković, L. Machine learning techniques for classifying network anomalies and intrusions. In Proceedings of the 2019 IEEE International Symposium on Circuits and Systems (ISCAS), Sapporo, Japan, 26–29 May 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–5. [Google Scholar]
- Lin, P.; Ye, K.; Xu, C.Z. Dynamic network anomaly detection system by using deep learning techniques. In International Conference on Cloud Computing; Springer: Berlin, Germany, 2019; pp. 161–176. [Google Scholar]
- Jaafar, G.A.; Abdullah, S.M.; Ismail, S. Review of recent detection methods for HTTP DDoS attack. J. Comput. Netw. Commun. 2019, 2019, 1283472. [Google Scholar] [CrossRef]
- Nawir, M.; Amir, A.; Yaakob, N.; Lynn, O.B. Effective and efficient network anomaly detection system using machine learning algorithm. Bull. Electr. Eng. Inform. 2019, 8, 46–51. [Google Scholar] [CrossRef]
- Ghaffari, F.; Gharaee, H.; Arabsorkhi, A. Cloud security issues based on people, process and technology model: A survey. In Proceedings of the 2019 5th International Conference on Web Research (ICWR), Tehran, Iran, 24–25 April 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 196–202. [Google Scholar] [CrossRef]
- Kemp, C.; Calvert, C.; Khoshgoftaar, T. Utilizing netflow data to detect slow read attacks. In Proceedings of the 2018 IEEE International Conference on Information Reuse and Integration (IRI), Salt Lake City, UT, USA, 6–9 July 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 108–116. [Google Scholar]
- Hatef, M.A.; Shaker, V.; Jabbarpour, M.R.; Jung, J.; Zarrabi, H. HIDCC: A hybrid intrusion detection approach in cloud computing. Concurr. Comput. Pract. Exp. 2018, 30, e4171. [Google Scholar] [CrossRef]
- Aborujilah, A.; Musa, S. Cloud-based DDoS HTTP attack detection using a covariance matrix approach. J. Comput. Netw. Commun. 2017, 2017, 7674594. [Google Scholar] [CrossRef]
- Alzahrani, S.; Hong, L. A survey of cloud computing detection techniques against DDoS attacks. J. Inf. Secur. 2017, 9, 45–69. [Google Scholar] [CrossRef]
- Hong, K.; Kim, Y.; Choi, H.; Park, J. SDN-assisted slow HTTP DDoS attack defense method. IEEE Commun. Lett. 2017, 22, 688–691. [Google Scholar] [CrossRef]
- Kaur, P.; Kumar, M.; Bhandari, A. A review of detection approaches for distributed denial of service attacks. Syst. Sci. Control Eng. 2017, 5, 301–320. [Google Scholar] [CrossRef]
- Ramírez-Gallego, S.; Krawczyk, B.; García, S.; Woźniak, M.; Herrera, F. A survey on data preprocessing for data stream mining: Current status and future directions. Neurocomputing 2017, 239, 39–57. [Google Scholar] [CrossRef]
- Sahi, A.; Lai, D.; Li, Y.; Diykh, M. An efficient DDoS TCP flood attack detection and prevention system in a cloud environment. IEEE Access 2017, 5, 6036–6048. [Google Scholar] [CrossRef]
- Gomes, H.M.; Bifet, A.; Read, J.; Barddal, J.P.; Enembreck, F.; Pfharinger, B.; Holmes, G.; Abdessalem, T. Adaptive random forests for evolving data stream classification. Mach. Learn. 2017, 106, 1469–1495. [Google Scholar] [CrossRef]
- Liu, B.; Chen, J.; Hu, Y. Mode division-based anomaly detection against integrity and availability attacks in industrial cyber-physical systems. Comput. Ind. 2022, 137, 103609. [Google Scholar] [CrossRef]
- Falliere, N.; O’Murchu, L.; Chien, E. W32. Stuxnet Dossier (Version 1.4); Symantec: Tempe, AZ, USA, 2011. [Google Scholar]
- Zeller, M. Myth or reality—Does the Aurora vulnerability pose a risk to my generator? In Proceedings of the 2011 64th Annual Conference for Protective Relay Engineers, College Station, TX, USA, 11–14 April 2011; pp. 130–136. [Google Scholar]
- Khalid, A.; Kirisci, P.; Khan, Z.H.; Ghrairi, Z.; Thoben, K.-D.; Pannek, J. Security framework for industrial collaborative robotic cyber-physical systems. Comput. Ind. 2018, 97, 132–145. [Google Scholar] [CrossRef]
- Choi, J.; Choi, C.; Ko, B.; Kim, P. A method of DDoS attack detection using HTTP packet pattern and rule engine in cloud computing environment. Soft Comput. 2014, 18, 1697–1703. [Google Scholar] [CrossRef]
- Basheer Riskhan, R.M. Virtual Machine Performance Approaches in the Online Education System. In Proceedings of the International MultiConference of Engineers and Computer Scientists 2016 Vol I, IMECS 2016, Hong Kong, China, 16–18 March 2016. [Google Scholar]
- Modi, C.; Patel, D.; Borisaniya, B.; Patel, A.; Rajarajan, M. A survey on security issues and solutions at different layers of cloud computing. J. Supercomput. 2013, 63, 561–592. [Google Scholar] [CrossRef]
- Bakshi, A.; Dujodwala, Y.B. Securing cloud from DDoS attacks using intrusion detection system in virtual machine. In Proceedings of the 2010 Second International Conference on Communication Software and Networks, Singapore, 26–28 February 2010; pp. 260–264. [Google Scholar]
- Munz, G.; Carle, G. Distributed network analysis using TOPAS and wireshark. In Proceedings of the NOMS Workshops 2008-IEEE Network Operations and Management Symposium Workshops, Salvador, Brazil, 7–11 April 2008; IEEE: Piscataway, NJ, USA, 2008; pp. 161–164. [Google Scholar]
- Douligeris, C.; Mitrokotsa, A. DDoS attacks and defense mechanisms: Classification and state-of-the-art. Comput. Netw. 2004, 44, 643–666. [Google Scholar] [CrossRef]
- Riskhan, B.; Zhou, K.; Muhammad, R. Energy Management of the System: An Empirical Investigation of Virtualization Approaches in Static and Dynamic Modes. Inf. Technol. J. 2016, 16, 1–10. [Google Scholar] [CrossRef]





| Evaluation Parameters | |
|---|---|
| Nodes | 10–200 |
| N/W Type | Static |
| Traffic Burst | 1.0–2.2 Gb |
| Malicious Node | Unknown |
| No. of Run | 1–9 |
| Legitimate Traffic Analysis | ||
|---|---|---|
| No. of Runs | Data Traffic (Mb) | |
| Adaptive SFaDMT Technique | Pushback Technique | |
| 1st Run | 1.0 | 1.2 |
| 2nd Run | 1.3 | 1.8 |
| 3rd Run | 1.4 | 1.75 |
| 4th Run | 1.5 | 1.9 |
| 5th Run | 1.7 | 1.9 |
| 6th Run | 1.9 | 1.9 |
| 7th Run | 1.65 | 1.75 |
| 8th Run | 1.9 | 2.1 |
| 9th Run | 1.7 | 1.9 |
| Detection Comparison | ||
|---|---|---|
| No. of Runs | Data Traffic (Mb) | |
| Adaptive SFaDMT Technique | Pushback Technique | |
| 1st Run | 1.0 | 10.0 |
| 2nd Run | 1.0 | 14.0 |
| 3rd Run | 1.0 | 15.0 |
| 4th Run | 3.0 | 20.0 |
| 5th Run | 14.0 | 43.0 |
| 6th Run | 11.0 | 63.0 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Riskhan, B.; Safuan, H.A.J.; Hussain, K.; Elnour, A.A.H.; Abdelmaboud, A.; Khan, F.; Kundi, M. An Adaptive Distributed Denial of Service Attack Prevention Technique in a Distributed Environment. Sensors 2023, 23, 6574. https://doi.org/10.3390/s23146574
Riskhan B, Safuan HAJ, Hussain K, Elnour AAH, Abdelmaboud A, Khan F, Kundi M. An Adaptive Distributed Denial of Service Attack Prevention Technique in a Distributed Environment. Sensors. 2023; 23(14):6574. https://doi.org/10.3390/s23146574
Chicago/Turabian StyleRiskhan, Basheer, Halawati Abd Jalil Safuan, Khalid Hussain, Asma Abbas Hassan Elnour, Abdelzahir Abdelmaboud, Fazlullah Khan, and Mahwish Kundi. 2023. "An Adaptive Distributed Denial of Service Attack Prevention Technique in a Distributed Environment" Sensors 23, no. 14: 6574. https://doi.org/10.3390/s23146574
APA StyleRiskhan, B., Safuan, H. A. J., Hussain, K., Elnour, A. A. H., Abdelmaboud, A., Khan, F., & Kundi, M. (2023). An Adaptive Distributed Denial of Service Attack Prevention Technique in a Distributed Environment. Sensors, 23(14), 6574. https://doi.org/10.3390/s23146574






