1. Introduction
In recent years, the Internet of Things (IoT) has been growing rapidly and all kinds of IoT devices are often present in our personal lives in the form of various applications, such as smart homes, smart transportation, and smart cities.
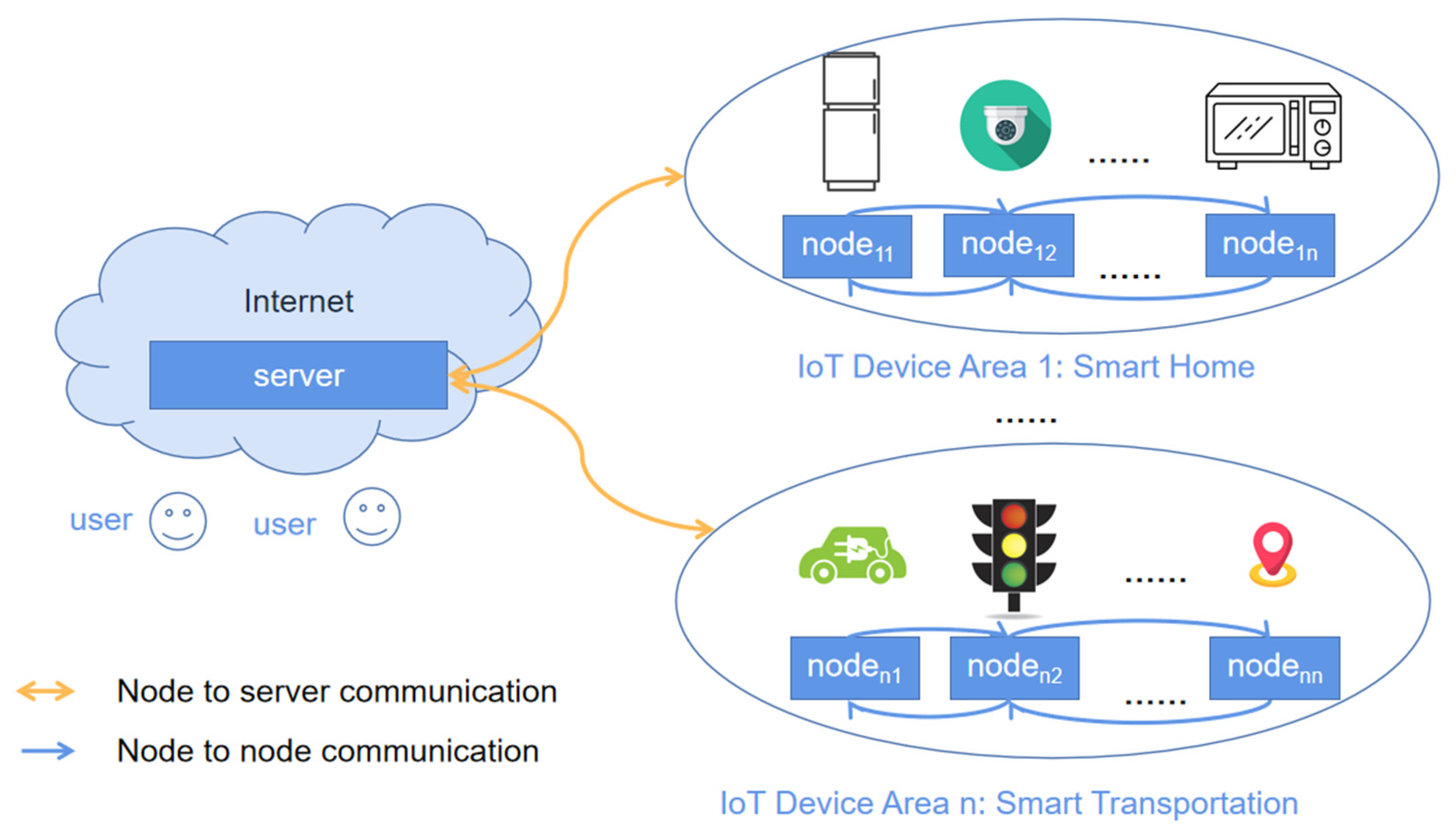
Figure 1 depicts the communication scenario between the IoT server and devices (nodes). However, security is one of the major challenges when IoT enters sensitive fields, e.g., a smart street light monitoring system. Unlike traditional networks, IoT consists of a large number of complex, heterogeneous, and interoperable IoT devices [
1]. Hence, under a hostile environment, IoT devices are often vulnerable to attacks and therefore require stronger security techniques to overcome their potential security weaknesses, such as counterfeit identity and sensitive data leakage. Authentication and key exchange protocols can provide the service of authentication and secret session key establishment between various IoT devices. Here, the session key is used to support confidential data transfer between IoT devices.
However, designing authentication and key exchange protocols is an intractable task for IoT applications. Firstly, there is a huge number of IoT devices, but their computing and storage resources are usually limited. Therefore, lightweight protocols are urgently needed to realize efficient interaction between devices without overloading their performance. Secondly, IoT devices are often deployed in complex, heterogeneous network environments and can be connected to and accessed by multiple unknown and untrusted devices, leading to extreme security challenges. Robust authentication and key exchange protocols should satisfy all strict requirements from IoT devices and their applications.
The physically unclonable function (PUF) [
2] can help build robust security protocols. PUF is regarded as a basic security primitive for resource-constrained IoT devices. PUF generates a unique digital fingerprint from micro-variations in physical devices. This fingerprint is unable to be cloned and is sensitive to being tampered with. PUF generates an unpredictable output (i.e., response) for corresponding input (i.e., challenge). The process is irreversible and is independent of storage memory. PUF is realized in various scenarios, such as field programmable gate array (FPGA) [
3], cloud storage, and IoT, to protect data from unauthorized access and attacks. The advantage of PUF is that resource-constrained devices do not require the maintenance of the secret key [
4]. Moreover, it reduces the risks associated with key transmission, storage, and management to a greater extent than other common cryptographic techniques. Therefore, PUF is as a promising alternative to designing lower-cost authentication and key exchange protocols.
On the one hand, PUF has advantages in efficiency and security compared with cryptographic algorithms. Hence, it is expected to design more practical authentication and key exchange protocols for IoT. On the other hand, PUF-based authentication and key exchange protocols are relatively new, compared with the protocols using purely cryptographic algorithms and/or smart cards. And there are still many security issues in its designs, which should be addressed. Hence, in this paper, we investigate the PUF-based authentication and key exchange protocol for IoT devices.
1.1. Related Work
Cryptographic algorithms are widely used in security protocols. According to the type of cryptographic algorithm, we divide PUF-based authentication and key exchange protocols into two categories as follows:
The PUF-based authentication and key exchange protocols using public key algorithms. The public key algorithms have high key management flexibility. This is because the communicating parties have two different keys, one of which is kept as a secret and the other is made public. There is no need to share the secret key as in symmetric key algorithms. The PUF-based protocols using public key algorithms inherit this feature. Yilmaz et al. [
5] applied the RSA algorithm in the lightweight PUF-based authentication protocol. Chatterjee et al. [
6] developed an authentication and key exchange protocol combining PUFs, identity-based encryption (IBE), and the keyed hash function. Chuang et al. [
7] designed a PUF-based authenticated key exchange protocol for IoT devices without verifiers and an explicit challenge–response pair (CRP). Using certificateless public key cryptography (CL-PKC), Li et al. [
8] proposed a PUF-based end-to-end mutual authentication and key exchange protocol for IoT devices. Chaterjee et al. [
9] proposed a private PUF-based anonymous authentication protocol. Siddiqui et al. [
10] proposed a PUF-based authentication protocol, which is dependent on two certificate authorities of the cloud IoT system. Harishma et al. [
11] proposed a PUF-based operationally asymmetric mutual authentication and key exchange protocol for secure communication. Qureshi and Munir [
12] introduced a lightweight CRP obfuscation mechanism using XOR and shuffle operations and further used it to design the PUF-based key exchange protocol.
The PUF-based authentication and key exchange protocols using symmetric key algorithms. The advantage of symmetric key algorithms is low computational cost. These algorithms are therefore well suited for authentication and key exchange protocols for resource-constrained IoT devices and help to reduce the computational burden of these IoT devices. In the PUF-based protocols using symmetric key algorithms, shared keys are generated by PUFs and hash functions are commonly used to authenticate messages. The researchers [
13,
14] proposed PUF-based mutual authentication protocols for IoT systems. Their protocols are presented for two scenarios, that is, device-to-device communication and device-to-server communication. Qureshi and Munir [
15] presented a PUF-based identity-preserving protocol. During the authentication run of their protocol, the server does not store, generate, transmit, or receive complete devices’ CRPs. Lounis and Zulkernine [
16] proposed PUF-based Thing-to-Thing (T2T) architectures, where devices autonomously authenticate each other without any human intervention involved. Nimmy et al. [
17] proposed a protocol that avoids explicit storage of CRPs for verification by using geometric threshold secret sharing. Zheng and Chang [
18] proposed a new lightweight PUF-based mutual authentication and key exchange protocol for two PUF-embedded IoT devices. Wang et al. [
19] leveraged PUFs to generate symmetric shared keys in the lightweight protocol. Ebrahimabadi et al. [
20] designed an authentication protocol to thwart modeling attacks for PUF-based IoT devices. Zerrouki et al. [
21] proposed a mutual authentication and session key establishment protocol for IoT devices based on PUFs. Sun and Tian [
22] further gave security analysis and improvements to this protocol and suggested the idea of a key compromise to evaluate other novel PUF protocol designs. Wang et al. [
23] introduced a supplementary sub-protocol to the PUF-based authentication protocol for the purpose of enhancing resistance to desynchronization attacks. Park and Park [
24] employed PUFs to realize an improved authentication and key agreement protocol for cloud-enabled IoT devices. To achieve decentralization and security, Aseeri et al. [
25] introduced a secure, lightweight, cost-efficient reinforcement machine learning framework (SLCR-MLF) with PUFs. In addition, some researchers [
26,
27,
28] proposed PUF-based two-factor authentication mechanisms.
1.2. Our Motivations and Contributions
In
IEEE Internet Things J. 2023, 10, 8547–8559, Roy et al. [
29] proposed a PUF-based authentication and key exchange protocol. Roy et al.’s protocol is interesting because it tries to leverage cryptographic XOR operation and hash function for traditional secure communication and PUF for preventing physical attacks. Moreover, this standalone protocol can perform device-to-device and device-to-server authentication, eradicating the need for disparate protocols. In addition, using the Scyther verifier tool, the security of Roy et al.’s protocol is evaluated by the formal method.
Due to their inherent vulnerability, IoT devices (nodes) are easily compromised by insider attackers. Therefore, in this paper, we carefully study the security of Roy et al.’s protocol under the assumption of an inside attack. Our results are summarized as follows:
- (1)
A legitimate but malicious IoT node can monitor the secure communication among the server and any other IoT nodes, because the malicious IoT node can reveal their secret session key. The only requirement of the malicious IoT node is to observe the transmitted messages over public channel during the authentication and key exchange phase of Roy et al.’s protocol.
- (2)
A legitimate but malicious IoT node is able to impersonate a target IoT node to cheat the server and any other IoT nodes during the authentication and key exchange phase of Roy et al.’s protocol. Finally, the malicious IoT node can establish a secret session key for the subsequent secure communication.
- (3)
A legitimate but malicious IoT node can masquerade as the server to cheat any other target IoT nodes during the authentication and key exchange phase of Roy et al.’s protocol. Here, the malicious IoT node is able to generate the valid session key for the target IoT nodes.
2. Basic Knowledge of PUF
PUFs make use of the intrinsic random variability in the physical microstructure of integrated circuits (ICs) to produce a unique
n-bit response
Ri to an
m-bit challenge
Ci for any
i∈
. We can write a PUF’s instance as follows.
where
Ci∈{0,1}
m and
Ri∈{0,1}
n.
PUF has the following safety features:
Uniqueness: PUFs cannot output the same response for different input challenges, while different PUFs output different responses for the same input challenge. For two different
Ci and
Cj, with
i,
j∈
, and any two different PUF instances
fAPUF and
fBPUF, the uniqueness expression is as follows.
Reliability: This feature measures the reproducibility of a PUF response under different operating conditions for a given challenge. The reliability expression of the PUF instance for different time periods
t1 and
t2 is:
In fact, the PUF response is sensitive to various noise elements, such as temperature, voltage, and other environmental changes. Under the same challenge, the noise can cause the PUF to give an erroneous response, which is different from the original one. To eliminate the effects of such noise, Roy et al. [
29] considered the use of lightweight error-correcting algorithms (ECAs) to stabilize the noisy PUF response and thus improved its reliability.
3. Review of Roy et al.’s Protocol
The one-time enrollment phase is responsible for enrolling the new IoT nodes in the server. The authentication and key exchange phase realizes mutual authentication between the server and the node(s). To maintain consistency, we employ the same notions of [
29] and write them in
Table 1.
3.1. One-Time Enrollment Phase
This phase is run in a secure environment without the attacker. After completing this phase, the IoT nodes can be deployed in the IoT network. When any A wants to enroll in the server, the server randomly generates an input CAi (i.e., challenge) for A’s PUF and collects its output RAi (i.e., response), where RAi = fAPUF(CAi). Then, the server stores A’s ID-CRP {idA, CAi, RAi} in its secure database. The server only maintains one ID-CRP record for each IoT device.
3.2. Authentication and Key Exchange Phase
This phase has two communication models, i.e., Node-to-Node (N2N) communication and Node-to-Server (N2S) communication. N2N communication aims to provide the mutual authentication and key establishment of any two IoT nodes. Meanwhile, N2S communication realizes the mutual authentication and key establishment between any one IoT node and the server.
3.2.1. N2N Communication
Assume that two nearby
A and
B nodes want to authenticate each other and establish their session key. As shown in
Figure 2,
A,
B, and the server perform the following steps.
Step 1. A sends a connection request {idA} to B. Upon receiving this request, B sends the N2N connection establishment request {idA, idB} to the server.
Step 2. The server fetches corresponding ID-CRPs {
idA,
CAi,
RAi} and {
idB,
CBi,
RBi} from its secure database and generates two random numbers
RN and
TAB. The server computes:
Then, the server sends the message {
CAi,
MA,
MB,
HA,
HB,
T’AB} to
A and the message {
CBi,
MA,
MB,
HA,
HB,
T’AB} to
B.
Step 3. Upon receiving the message {
CAi,
MA,
MB,
HA,
HB,
T’AB},
A first computes:
To authenticate the server,
A then checks whether
HA is equal to
H*A and
HB is equal to
H*B. If any verification fails,
A terminates the session. Otherwise,
A further calculates:
Finally,
A sends {
TB} to
B.
Step 4. Upon receiving the messages {
CBi,
MA,
MB,
HA,
HB,
T’AB} and {
TB},
B computes:
To authenticate the server,
B checks
HA and
HB using
H*A and
H*B just like
A. If any verification fails,
B also terminates the session. Moreover,
B evaluates:
Now,
B checks whether
RBi is equal to
R*Bi. If the verification is incorrect,
B terminates the session; otherwise,
B computes:
Finally,
B sends {
TA} to
A and {
MSB,
HSB} to the server.
Step 5. Upon receiving the message {
TA},
A computes:
A checks whether
RAi is equal to
R*Ai. If the verification is incorrect,
A terminates the session; otherwise,
A computes:
A then sends {
MSA,
HSA} to the server.
Step 6. Upon receiving the messages {
MSA,
HSA} and {
MSB,
HSB}, the server computes:
The server then checks whether
HSA is equal to
H*SA and
HSB is equal to
H*SB. If any verification is incorrect, the server terminates the session; otherwise, the server computes:
Now, the server updates {
idA,
CAi,
RAi} to {
idA,
C*A(i+1),
R*A(i+1)} and {
idB,
CBi,
RBi} to {
idB,
C*B(i+1),
R*B(i+1)} in its secure database.
After the successful completion of above steps, TAB is used as the secret session key for subsequent secure communication between A and B. Clearly, TAB gets updated in every new session.
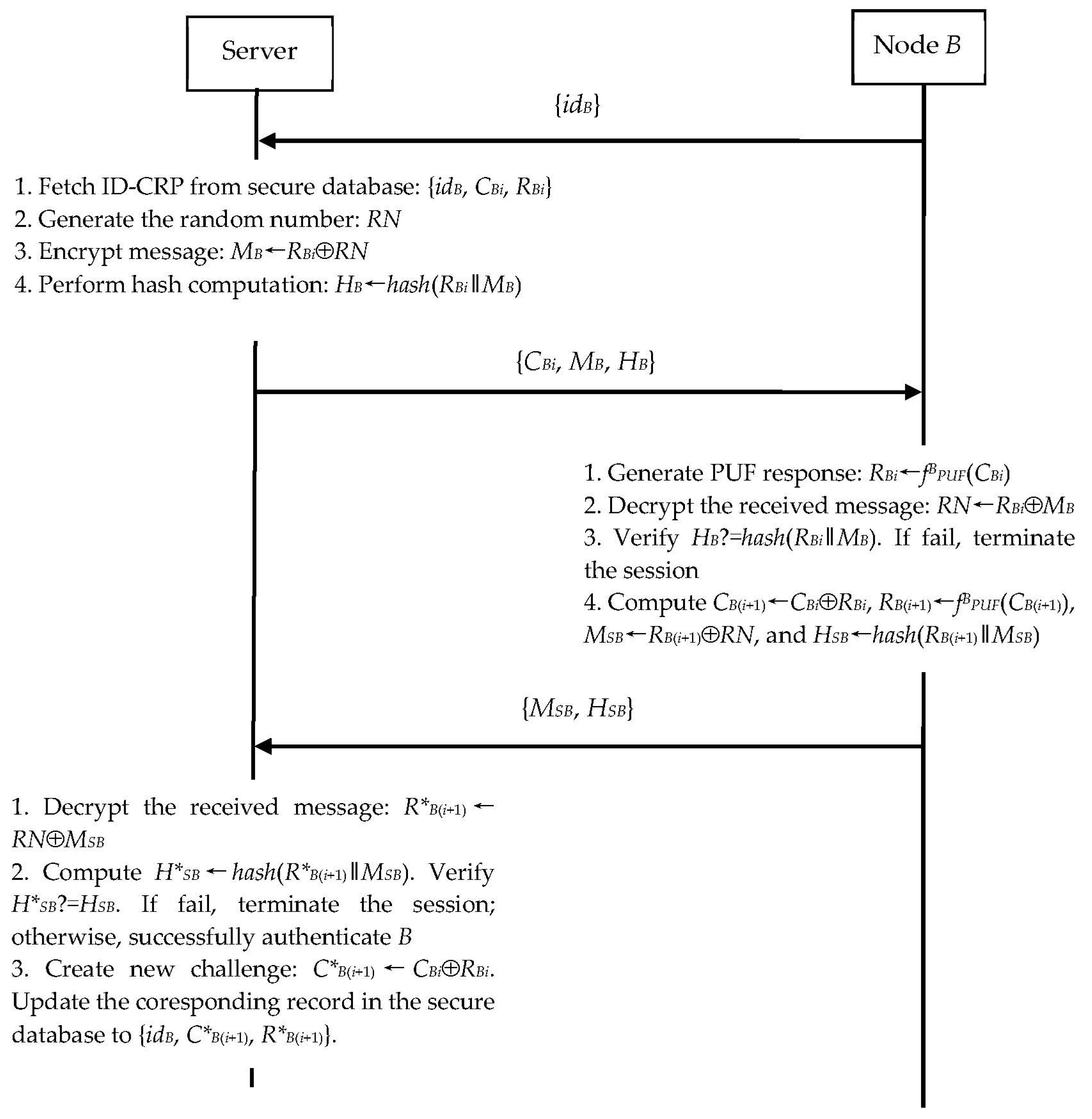
3.2.2. N2S Communication
Assume that
B wants to authenticate the proximity server and establish a session key with the server. As shown in
Figure 3,
B and the server perform the following steps.
Step 1. B sends the N2S connection establishment request {idB} to the server.
Step 2. The server fetches the corresponding ID-CRP {
idB,
CBi,
RBi} from its secure database and generates a random number
RN. The server computes:
The server then sends the message {
CBi,
MB,
HB} to
B.
Step 3. Upon receiving the message {
CBi,
MB,
HB},
B computes:
To authenticate the server,
B then checks whether
HB is equal to
H*B. If any verification fails,
B terminates the session. Otherwise,
B further computes:
Finally,
B sends {
MSB,
HSB} to the server.
Step 4. Upon receiving the message {
MSB,
HSB}, the server computes:
The server then checks whether
HSB is equal to
H*SB. If the verification is incorrect, the server terminates the session; otherwise, the server computes:
Now, the server updates {
idB,
CBi,
RBi} to {
idB,
C*B(i+1),
R*B(i+1)} in its secure database.
Once the above authentication procedure is completed, B and the server share RB(i+1) as their secret session key. This key is updated in every new session establishment.
4. Insider Attack on Roy et al.’s Protocol
Let
A be an insider attacker. It means that
A has a legitimate ID-CRP record {
idA,
CAi,
RAi} in the server’s secure database but attempts to sabotage the server and other IoT nodes. When both
A and
B run the N2N communication model with the server,
A executes the steps as described in
Figure 2. At the same time,
A as an insider further performs the following operations.
- (1)
A eavesdrops on B’s {idA, idB} during Step 1.
- (2)
A eavesdrops on the server’s {CBi, MA, MB, HA, HB, T’AB} during Step 2.
- (3)
In Step 4, A eavesdrops on B’s {MSB, HSB}.
Based on above, A can compute B’s CB(i+1) by evaluating CBi⊕RBi, because it knows RBi (see Equation (12)) during Step 3. And A can correctly recover B’s RB(i+1) by calculating MSB⊕RN. Here, we know that A also computes the correct RN (see Equation (11)) during Step 3. Finally, we conclude that A obtains B’s {idB, CBi, RBi} used in the next session, i.e., {idB, CB(i+1), RB(i+1)}.
4.1. Surveillance on IoT Nodes and Server
4.1.1. Surveillance Exploiting N2N Communication
To achieve authentication and establish the session key,
B runs the N2N communication model with any
C. As shown in
Figure 4,
A can eavesdrop on their session messages. And then,
A further discloses the secret session key
TCB between
C and
B. Hence,
A can monitor the subsequent secret channel using
TCB. For more detail, we describe
A’s behaviors on the session run of the N2N communication model between
C and
B.
- (1)
In Step 1, A eavesdrops on C’s {idc}.
- (2)
In Step 2, A eavesdrops on the server’s {CBi, MC, MB, HC, HB, T’CB}.
Now, A can obtain the RN by computing RBi⊕MB, where RBi is collected in A’s previous session with B. A then recovers TCB by computing T’CB⊕RN. Moreover, if A wants to monitor B’s next session, it can further perform as follows.
In Step 4, A eavesdrops on B’s {MSB, HSB}.
A can compute B’s CB(i+1) by evaluating CBi⊕RBi and then recover B’s RB(i+1) by calculating MSB⊕RN. In the end, A updates its {idB, CBi, RBi} to {idB, CB(i+1), RB(i+1)} for B’s next session. In addition, if A wants to monitor C’s next session, it further performs in the following.
- (1)
In Step 2, A eavesdrops on the server’s {CCi, MC, MB, HC, HB, T’CB}.
- (2)
In Step 5, A eavesdrops on C’s {MSC, HSC}.
In this situation, A computes RCi by using MC⊕RN and CC(i+1) by using CCi⊕RCi. A also recovers C’s RB(i+1) by calculating MSC⊕RN. Finally, A can record {idC, CC(i+1), RC(i+1)} for monitoring C’s next session.
Comments. According to above surveillance, in the initial stage, the insider attacker needs to collect information about the target IoT node (i.e., B) by running a session with the target IoT node. Afterwards, the insider attacker can expand their surveillance to other IoT nodes (e.g., C), which run the sessions with the target IoT node. Meanwhile, the insider attacker no longer needs to participate in those session runs and still obtains those secrets. This effectively hides the insider attacker and reduces the probability of the insider attacker being identified. Moreover, the insider attacker can establish a surveillance network of the selected IoT nodes based on our proposed attack.
4.1.2. Surveillance Exploiting N2S Communication
A is able to monitor the session run of the N2S communication model between
B and the server. As shown in
Figure 5,
A can perform the following operations to reveal the secret session key
RB(i+1) shared by
B and the server.
- (1)
In Step 2, A eavesdrops on the server’s {CBi, MB, HB}.
- (2)
In Step 3, A eavesdrops on B’s {MSB, HSB}.
Because A knows B’s RBi, A can obtain the RN by computing RBi⊕MB. Now, A further recovers the secret session key RB(i+1) by computing MSB⊕RN. A can therefore observe the following secure communication using RB(i+1). Moreover, if A wants to continuously monitor the session run of the N2S communication model between B and the server, A merely computes CB(i+1) = CBi⊕RBi and replaces the old {idB, CBi, RBi} with the new {idB, CB(i+1), RB(i+1)}.
4.2. Impersonating IoT Node
4.2.1. IoT Node Impersonation Exploiting N2N Communication
In N2N communication,
A can imitate
B run with any
C, when
A obtains a legal {
idB,
CBi,
RBi}. As shown in
Figure 6,
A replaces
B to perform
B’s following steps during the run of N2N communication.
- (1)
Upon receiving C’s request {idC} in Step 1, A sends the N2N connection establishment request {idC, idB} to the server.
- (2)
Upon receiving the messages {CBi, MC, MB, HC, HB, T’CB} and {TB} in Step 4, A computes RN←RBi⊕MB, RCi←MC⊕RN, TCB←T’CB⊕RN, TC←TCB⊕RCi, and CB(i+1)←CBi⊕RBi. Then, A generates RB(i+1) at random. Next, A evaluates MSB←RB(i+1)⊕RN and HSB←hash(RB(i+1)‖MSB). Finally, A sends {TC} to C and {MSB, HSB} to the server.
Herein, A randomly generates RB(i+1) instead of B’s RB(i+1) outputted by the valid PUF to evaluate MSB and HSB in Step 4. A can still pass the server’s authentication, because the server never checks the PUF validness of its receiving RB(i+1) in Step 6. If A wants to continuously impersonate B, A further uses the new {idB, CB(i+1), RB(i+1)} to replace the old {idB, CBi, RBi} for B’s next session. In addition, A can also employ a similar attack to impersonate initiator C, if A obtains C’s {idC, CCi, RCi}.
Comments. After A completes above impersonation, B will no longer be able to successfully run the authentication and key exchange phase with the server and other IoT nodes. In this situation, we know that the server updates its {idB, CBi, RBi} to {idB, CB(i+1), RB(i+1)}, where RB(i+1) is randomly generated by A. When B runs the authentication and key exchange phase, the server should use the random RBi to generate MB (see Equation (6)) and send it to B in Step 2. However, in Step 4, B retrieves its local RBi by invoking fBPUF(CBi) (see Equation (17)). Clearly, the server’s RBi and B’s RBi are always not equal because of the PUF’s safety feature. Hence, B should recover an incorrect RN using Equation (18) and fail the subsequent authentication and key exchange procedure with the server and the counterpart IoT node. Therefore, B suffers from a denial of service attack due to A’s impersonation.
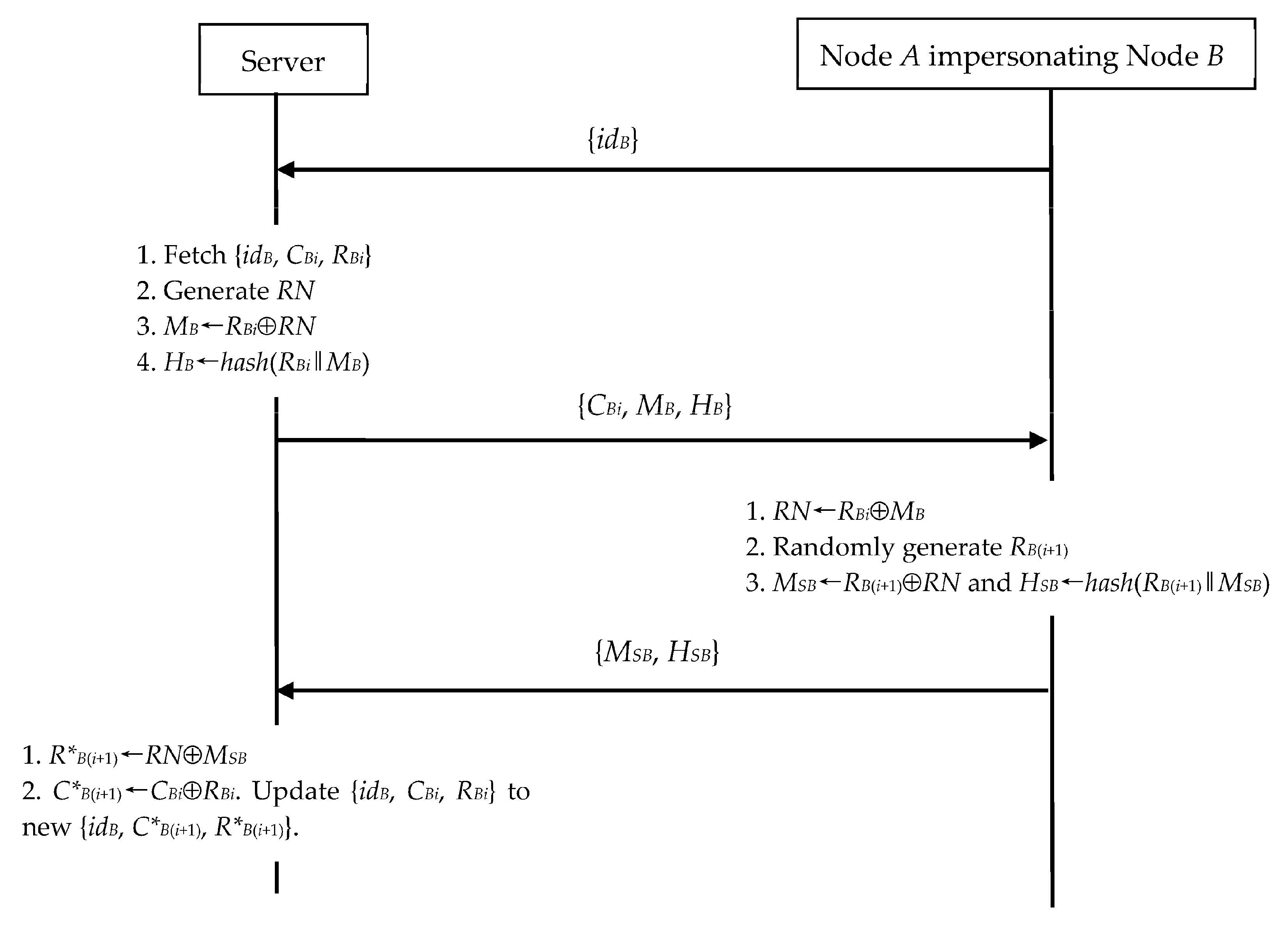
4.2.2. IoT Node Impersonation Exploiting N2S Communication
In N2S communication,
A can impersonate
B to cheat the server, when
A obtains
B’s {
idB,
CBi,
RBi}. As shown in
Figure 7, we demonstrate
A’s operations as follows.
- (1)
A sends the request {idB} to the server in Step 1.
- (2)
Upon receiving the message {CBi, MB, HB} in Step 3, A computes RN←RBi⊕MB. Then, A generates RB(i+1) at random. Next, A evaluates MSB←RB(i+1)⊕RN and HSB←hash(RB(i+1)‖MSB). Finally, A sends {MSB, HSB} to the server.
This node impersonation is similar to that of the impersonation discussed in
Section 4.2.1. Clearly, the server should confirm the validity of
A’s
HSB in Step 4, and therefore we omit this operation in
Figure 7 for simplicity. The slight difference is that, after session run,
A applies
RB(i+1) as the secret session key instead of
TCB as in
Section 4.2.1.
4.3. Impersonating Server
4.3.1. Server Impersonation Exploiting N2N Communication
A can impersonate the server to cheat both
C and
B in N2N communication, if
A obtains
C’s {
idC,
CCi,
RCi} and
B’s {
idB,
CBi,
RBi}.
Figure 8 shows the process of
A’s server impersonation.
A performs the following operations.
- (1)
In Step 2, A randomly generates RN and TCB. A further computes MC←RCi⊕RN, MB←RBi⊕RN, T’CB←TCB⊕RN, HC←hash(RCi‖MC), and HB←hash(RBi‖MB). Then, A sends the message {CCi, MC, MB, HC HB, T’CB} to C and the message {CBi, MC, MB, HC, HB, T’CB} to B.
- (2)
Upon receiving the messages {MSC, HSC} and {MSB, HSB} in Step 6, A omits them.
A finally shares the session key TCB with both C and B. Moreover, A still can reuse C’s {idC, CCi, RCi} and B’s {idB, CBi, RBi} to impersonate the server in the subsequent session, because C and B do not verify the freshness of CCi and CBi in each session run. Certainly, in Step 6, A can also compute R*C(i+1)←RN⊕MSC, R*B(i+1)←RN⊕MSB, C*C(i+1)←CCi⊕RCi, and C*B(i+1)←CBi⊕RBi. This means that A obtains new ID-CRPs for future attacks.
4.3.2. Server Impersonation Exploiting N2S Communication
When
B wants to run N2S communication,
A can make use of
B’s {
idB,
CBi,
RBi} to impersonate the server. As shown in
Figure 9,
A executes the following operations to achieve it.
- (1)
In Step 2, A generates the random number RN. A computes MB←RBi⊕RN and HB←hash(RBi‖MB). Then, A sends the message {CBi, MB, HB} to B.
- (2)
Upon receiving the message {MSB, HSB} in Step 4, A computes R*B(i+1)←RN⊕MSB and C*B(i+1)←CBi⊕RBi and further replaces its {idB, CBi, RBi} with {idB, C*B(i+1), R*B(i+1)}.
As a result,
A and
B establish the secret session key
R*B(i+1).
A can omit to replace its {
idB,
CBi,
RBi} with {
idB,
C*B(i+1),
R*B(i+1)} and still use {
idB,
CBi,
RBi} for the subsequent impersonation. The reason is the same as in our discussion in
Section 4.3.1.
4.4. Discussion of Insider Attacker
We discuss how an IoT node practically becomes a malicious IoT node, i.e., an insider attacker. In general, the IoT system contains plenty of IoT nodes. And some of them are possibly manufactured and provided by third parties. From a third-party perspective, these IoT nodes may not only want to work properly in the IoT system, but also engage in malicious behaviors such as surveillance and impersonation. Clearly, in this situation, the malicious IoT nodes can enter the IoT system during the one-time enrollment phase of Roy et al.’s protocol.
After the deployment of the IoT nodes, physical attacks are very common for the IoT system. They typically require physical proximity to the IoT system and can involve actions that limit the efficacy of the IoT nodes. In order to turn benign IoT nodes into malicious IoT nodes, the physical attack can further inject malicious codes into benign IoT nodes. These malicious codes include the logic that requires the IoT nodes to execute insider attacks in some cases. In addition, software attacks can be exploited to compromise the IoT nodes, that is, the attackers use the malware, such as viruses, worms, and Trojans, to manipulate the IoT nodes.
It is possible that malicious IoT nodes have limited resources and functionalities. This means that the malicious IoT nodes cannot handle and store the derived session keys for next session and for another IoT node, cannot intercept the transmitted messages over the public channel, cannot impersonate the server, and so on. To complete our insider attacks, the attacker can build a powerful auxiliary node to support malicious IoT nodes. Each malicious IoT node A merely outputs its {idA, CAi, RAi} to the auxiliary node. The auxiliary node can replace the malicious IoT node A to implement the insider attacks.
5. Experimental Verification of Proposed Insider Attacks
Scyther is a formal analysis tool for automatic verification of security protocols based on the security protocol description language (SPDL). Scyther can analyze protocols that contain multiple subjects, infinite session interaction, and the use of random numbers. We therefore use Scyther to confirm our insider attacks on Roy et al.’s protocol. We implement experimental verification on the 64-bit Windows 10 operating system, Graphviz v2.50, and Python v2.7 using the Compile-0.9.2 version of the Scyther tool.
When using the Scyther tool to verify Roy et al.’s protocol, we write secret PUF responses, XOR-encrypted messages, etc., into the SPDL script to model the protocol. The details of the Scyther tool parameter settings are shown in
Table 2. Here, the attacker can obtain the secret PUF responses and furthermore derive the session key and random numbers. This is consistent with the capabilities of the malicious IoT nodes assumed in
Section 4.
For Roy et al.’s protocol,
Figure 10 shows Scyther’s verification results for N2N communication (see
Figure 10a) and N2S communication (see
Figure 10b). The results show that both N2N communication and N2S communication do not meet Scyther’s automatic declaration requirements of Alive, Weakagree (weak agree), Nisynch (noninjective synchronization), and Niagree (noninjective agreement). Moreover, the results also indicate that the secret session key
TAB in the N2N communication and the secret session key
RB(i+1) in the N2S communication are both insecure. Hence, we conclude that the process of the authentication and key exchange in Roy et al.’s protocol is insecure and is subject to insider attacks on the IoT nodes and the server.
6. Suggestion for Preventing Insider Attacks
We know that A is required to recover B’s RBi (see Equation (12)) to verify B (see Equation (14)) in the N2N communication of Roy et al.’s protocol. Similarly, B needs to recovering A’s RAi (see Equation (19)) to verify A (see Equation (20)). However, we know that both RAi and RBi are the secrets of A and B, respectively. It means that A and B obtain each other secrets after Step 4 of the N2N communication, which incurs the secure breach. In fact, these verifications conducted by A and B are unnecessary because both A and B believe the server. Therefore, one suggestion is to cancel the verifications, that is, the server does not send MB and HB to A and MA and HA to B during Step 2 of the N2N communication.
Moreover, we find that both A and B share a random number RN in the N2N communication. RN is used to encrypt their all secrets. Because of sharing the RN, the malicious IoT node can decrypt other IoT node’s secrets. Hence, another suggestion is that the server must randomly select two random numbers instead of just one RN, that is, one random number for A and the other one for B.
The above two suggestions may defend against our proposed insider attacks. However, accurate security results for improvements require formal security models, security assumptions, security definitions, and reductions. We keep these for future work.
7. Conclusions
In the N2N communication of Roy et al.’s protocol, the IoT node requires the counterpart IoT node’s secret output of the PUF to verify it. More importantly, the malicious IoT node can derive the counterpart IoT node’s next output of the PUF if it eavesdrops on the message transmitted to the server. These defects have led to our insider attacks on Roy et al.’s protocol. Moreover, in the cases of the N2N communication and the N2S communication, we must point out that once the attacker stole the session keys, i.e., TAB or RB(i+1), he can always impersonate not only the IoT node to cheat other IoT nodes or the server but also the server to cheat the IoT nodes in the subsequent sessions. The secure communications between the server and the corresponding IoT nodes are also possibly under the attacker’s surveillance. This means that Roy et al.’s protocol fails to provide the known key security. Our security analysis results indicate that designing PUF-based authentication and key exchange protocols for IoT remains a challenging task.
Author Contributions
Conceptualization, D.-Z.S.; methodology, D.-Z.S.; validation, D.-Z.S. and Y.T.; formal analysis, D.-Z.S. and Y.-N.G.; investigation, D.-Z.S.; writing—original draft preparation, D.-Z.S. and Y.-N.G.; writing—review and editing, D.-Z.S. and Y.T.; supervision, D.-Z.S.; funding acquisition, D.-Z.S. All authors have read and agreed to the published version of the manuscript.
Funding
The work of Da-Zhi Sun was supported in part by the National Natural Science Foundation of China under Grant No. 61872264. The APC was funded by the National Natural Science Foundation of China under Grant No. 61872264.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
No new data was created or analyzed in this study. Data sharing is not applicable to this article.
Acknowledgments
The authors would like to thank the editors and the reviewers for their valuable suggestions and comments.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Idriss, T.; Idriss, H.; Bayoumi, M. A lightweight PUF-based authentication protocol using secret pattern recognition for constrained IoT devices. IEEE Access 2021, 9, 80546–80558. [Google Scholar] [CrossRef]
- Mukhopadhyay, D.; Chakraborty, R.S.; Nguyen, P.H.; Sahoo, D.P. Physically Unclonable Function: A Promising Security Primitive for Internet of Things. In Proceedings of the 2015 IEEE 28th International Conference on VLSI Design (VLSID), Bangalore, India, 3–7 January 2015; IEEE Computer Society: Los Alamitos, CA, USA, 2015; pp. 14–15. [Google Scholar]
- Goncu, E.; Yalcin, M.E. A design of cellular automata-based PUF and its implementation on FPGA. Int. J. Circuit Theory Appl. 2020, 48, 1244–1255. [Google Scholar] [CrossRef]
- Yoon, S.; Kim, B.; Kang, Y.; Choi, D. Security Enhancement for IoT Device Using Physical Unclonable Functions. In Proceedings of the 10th International Conference on Information and Communication Technology Convergence (ICTC)-ICT Convergence Leading the Autonomous Future, Jeju, Republic of Korea, 16–18 October 2019; IEEE: New York, NY, USA, 2019; pp. 1457–1459. [Google Scholar]
- Yilmaz, Y.; Gunn, S.R.; Halak, B. Lightweight PUF-Based Authentication Protocol for IoT Devices. In Proceedings of the 3rd IEEE International Verification and Security Workshop (IVSW), Catalonia, Spain, 2–4 July 2018; IEEE: New York, NY, USA, 2018; pp. 38–43. [Google Scholar]
- Chatterjee, U.; Govindan, V.; Sadhukhan, R.; Mukhopadhyay, D.; Chakraborty, R.S.; Mahata, D.; Prabhu, M.M. Building PUF based authentication and key exchange protocol for IoT without explicit CRPs in verifier database. IEEE Trans. Dependable Secur. Comput. 2019, 16, 16424–16437. [Google Scholar] [CrossRef]
- Chuang, Y.H.; Lei, C.L. PUF based authenticated key exchange protocol for IoT without verifiers and explicit CRPs. IEEE Access 2021, 9, 112733–112743. [Google Scholar] [CrossRef]
- Li, S.N.; Zhang, T.K.; Yu, B.; He, K. A provably secure and practical PUF-based end-to-end mutual authentication and key exchange protocol for IoT. Sensors 2021, 21, 5487–5501. [Google Scholar] [CrossRef]
- Chaterjee, U.; Mukhopadhyay, D.; Chakraborty, R.S. 3PAA: A private PUF protocol for anonymous authentication. IEEE Trans. Inf. Forensics Secur. 2021, 16, 756–769. [Google Scholar] [CrossRef]
- Siddiqui, Z.; Gao, J.C.; Khan, M.K. An improved lightweight PUF-PKI digital certificate authentication scheme for the internet of things. IEEE Internet Things J. 2022, 9, 19744–19756. [Google Scholar] [CrossRef]
- Harishma, B.; Mathew, P.; Patranabis, S.; Chatterjee, U.; Agarwal, U.; Maheshwari, M.; Dey, S.; Mukhopadhyay, D. Safe is the new smart: PUF-based authentication for load modification-resistant smart meters. IEEE Trans. Dependable Secur. Comput. 2022, 19, 663–680. [Google Scholar] [CrossRef]
- Qureshi, M.A.; Munir, A. PUF-RAKE: A PUF-based robust and lightweight authentication and key establishment protocol. IEEE Trans. Dependable Secur. Comput. 2022, 19, 2457–2475. [Google Scholar] [CrossRef]
- Aman, M.N.; Chua, K.C.; Sikdar, B. Mutual authentication in IoT systems using physical unclonable functions. IEEE Internet Things J. 2017, 4, 1327–1340. [Google Scholar] [CrossRef]
- Roy, S.; Das, D.; Mondal, A.; Mahalat, M.H.; Roy, S.; Sen, B. PUF Based Lightweight Authentication and Key Exchange Protocol for IoT. In Proceedings of the 18th International Conference on Security and Cryptography (SECRYPT), Online, 6–8 July 2021; pp. 698–703. [Google Scholar]
- Qureshi, M.A.; Munir, A. PUF-IPA: A PUF-Based Identity Preserving Protocol for Internet of Things Authentication. In Proceedings of the IEEE 17th Annual Consumer Communications and Networking Conference (CCNC), Las Vegas, NV, USA, 10–13 January 2020; pp. 1–7. [Google Scholar]
- Lounis, K.; Zulkernine, M. T2T-MAP: A PUF-based thing-to-thing mutual authentication protocol for IoT. IEEE Access 2021, 9, 137384–137405. [Google Scholar] [CrossRef]
- Nimmy, K.; Sankaran, S.; Achuthan, K. A novel lightweight PUF based authentication protocol for IoT without explicit CRPs in verifier database. J. Ambient Intell. Humaniz. Comput. 2023, 14, 6227–6242. [Google Scholar] [CrossRef]
- Zheng, Y.; Chang, C.H. Secure Mutual Authentication and Key-Exchange Protocol between PUF-Embedded IoT Endpoints. In Proceedings of the IEEE International Symposium on Circuits and Systems (ISCAS), Daegu, Republic of Korea, 22–28 May 2021; IEEE: New York, NY, USA, 2021; pp. 1–5. [Google Scholar]
- Wang, Z.Y.; Li, S.Q.; Guo, Y.; Zeng, J.P. A lightweight key sharing protocol for IoT devices based on PUF. J. Hunan Univ. Nat. Sci. 2022, 49, 103–110. [Google Scholar]
- Ebrahimabadi, M.; Younis, M.; Karimi, N. A PUF-based modeling-attack resilient authentication protocol for IoT devices. IEEE Internet Things J. 2022, 9, 3684–3703. [Google Scholar] [CrossRef]
- Zerrouki, F.; Ouchani, S.; Bouarfa, H. PUF-based mutual authentication and session key establishment protocol for IoT devices. J. Ambient Intell. Humaniz. Comput. 2022. early access. [Google Scholar] [CrossRef]
- Sun, D.Z.; Tian, Y. Security of a PUF mutual authentication and session key establishment protocol for IoT devices. Mathematics 2022, 10, 4310. [Google Scholar] [CrossRef]
- Wang, H.Y.; Meng, J.; Du, X.L.; Cao, T.F.; Xie, Y. Lightweight and anonymous mutual authentication protocol for edge IoT nodes with physical unclonable function. Secur. Commun. Netw. 2022, 2022, 1203691. [Google Scholar] [CrossRef]
- Park, K.; Park, Y. IAKA-CIOT: An improved authentication and key agreement scheme for cloud enabled internet of things using physical unclonable function. Sensors 2022, 22, 6264. [Google Scholar] [CrossRef]
- Aseeri, A.O.; Chauhdary, S.H.; Alkatheiri, M.S.; Alqarni, M.A.; Zhuang, Y. Application of physical unclonable function for lightweight authentication in internet of things. Comput. Mater. Contin. 2023, 75, 1901–1918. [Google Scholar] [CrossRef]
- Prosanta, G.; Biplab, S. Lightweight and privacy-preserving two-factor authentication scheme for IoT devices. IEEE Internet Things J. 2019, 6, 6580–6589. [Google Scholar]
- Mostafa, A.; Lee, S.J.; Peker, Y.K. Physical unclonable function and hashing are all you need to mutually authenticate IoT devices. Sensors 2020, 20, 4361. [Google Scholar] [CrossRef]
- Uysal, E.; Akgun, M. P/Key: PUF based second factor authentication. PLoS ONE 2023, 18, e0280181. [Google Scholar] [CrossRef]
- Roy, S.; Das, D.; Mondal, A.; Mahalat, M.H.; Sen, B.; Sikdar, B. PLAKE: PUF based secure lightweight authentication and key exchange protocol for IoT. IEEE Internet Things J. 2023, 10, 8547–8559. [Google Scholar] [CrossRef]
| Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).