CNN-CNN: Dual Convolutional Neural Network Approach for Feature Selection and Attack Detection on Internet of Things Networks
Abstract
1. Introduction
- Leveraging CNNs to select feature sets that help to detect IoT attacks. A CNN’s ability to discover and prioritize crucial features is essential for this attack detection. By applying CNNs to the feature selection process, we aim to enhance the accuracy and efficiency of IoT attack detection systems. Our research contributes to advancing IoT security by demonstrating the effectiveness of CNNs in identifying relevant features for robust attack detection, thereby improving the overall security posture of IoT environments.
- Design and implementation of a CNN-based detection model that utilizes the features selected by the first CNN model. The procedure comprises training the CNN on these features, which ultimately yields a reliable and robust detection system.
- Extensive testing and analysis to evaluate the effectiveness of the proposed approach’s CNN-based feature selection and detection model. This evaluation provides valuable insights into the strengths, limitations, and overall efficacy of the proposed approach in detecting IoT-based attacks.
2. Background
2.1. Internet of Things Security
2.2. Feature Selection
2.3. Convolutional Neural Networks
- Feature selection: CNNs can be utilized to select significant features from the dataset that help identify IoT-based attacks. By leveraging their ability to learn intricate patterns and representations from data, CNNs can analyze and prioritize features that are most relevant for detecting IoT attacks. This feature selection process enhances the accuracy and efficiency of IoT threat detection systems.
- Detection model construction: CNNs can be employed to build robust detection models specifically designed to accurately detect IoT-based attacks. These models leverage the learned representations and weights from the CNN layers to effectively analyze and classify IoT data instances as normal or malicious. By training the detection models with appropriate features, CNNs enhance the performance and reliability of IoT attack detection systems.
3. Related Works
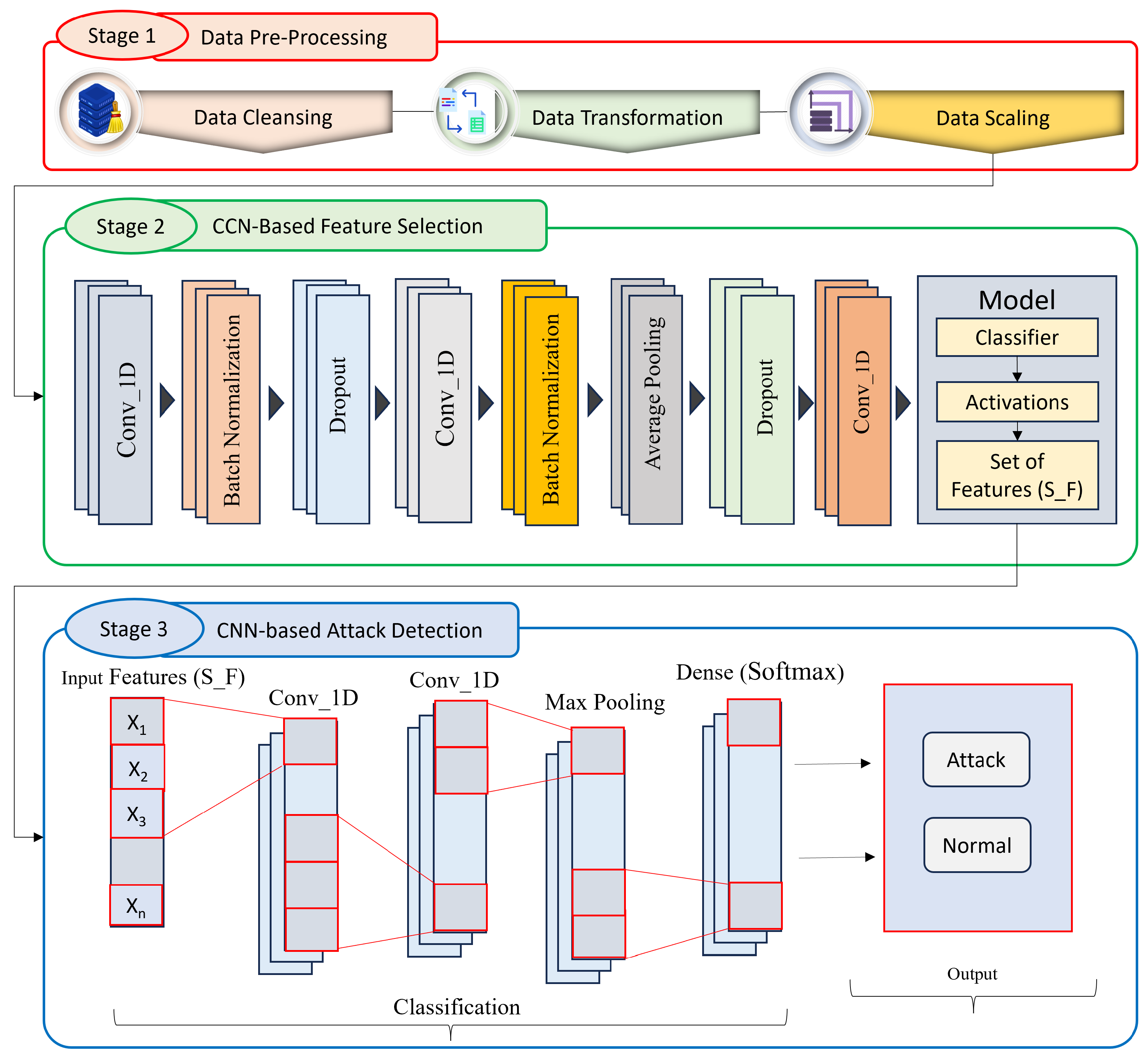
4. Proposed Approach
4.1. Data Preprocessing
4.2. CNN-Based Feature Selection Stage
| Algorithm 1 CNN-based Feature Selection. |
|
4.3. CNN-Based IoT Attacks Detection Stage
| Algorithm 2 CNN-based detection model. |
|
- Preprocessing: Preprocess the input data to prepare it for training the CNN. This may include normalization, scaling, and other data-cleaning techniques.
- Build a CNN model: Build a CNN model with multiple convolutional and pooling layers to extract features from the input data. The output of the last convolutional layer can be used as a set of feature maps.
- Train the CNN model: Train the CNN model using the input data to learn the filters that produce the most informative feature maps.
- Compute the mean activations for the last convolutional layer: Extract the feature maps from the testing data using the trained CNN model. Compute the mean activation of each feature map across all instances in the testing dataset.
- Select the most informative features: Identify the most informative feature maps by sorting the mean activations in descending order and selecting the top-k feature maps. These feature maps can be considered the most important features of the given dataset.
- Build a new model using the selected features: Build a new model that uses the selected feature maps as inputs. This new model is used for detecting IoT attacks.
5. Experimental Results and Discussion
5.1. Dataset
5.2. Evaluation Metrics
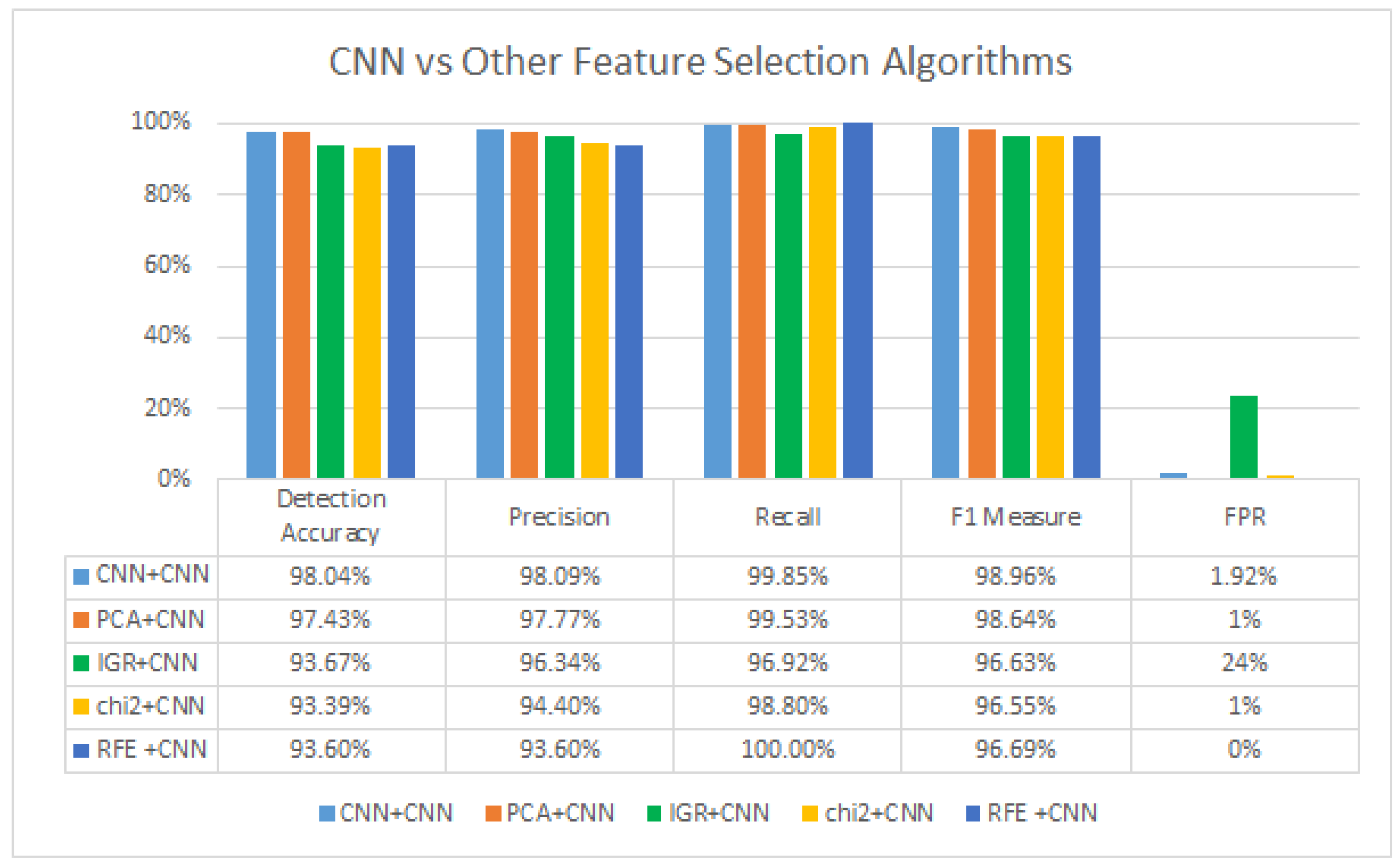
5.3. The Result of CNN-Based Feature Selection Stage
5.4. The Result of CNN-Based IoT Attacks Detection
5.5. Discussion
6. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Sarker, I.H.; Khan, A.I.; Abushark, Y.B.; Alsolami, F. Internet of things (iot) security intelligence: A comprehensive overview, machine learning solutions and research directions. Mob. Netw. Appl. 2022, 1–17. [Google Scholar] [CrossRef]
- Al-Shalabi, M.; Anbar, M.; Obeidat, A. Alternating sensing process to prolong the lifetime of wireless sensor networks. J. Theor. Appl. Inf. Technol. (JATIT) 2019, 97, 2132–2141. [Google Scholar]
- Al-Sarawi, S.; Anbar, M.; Abdullah, R.; Al Hawari, A.B. Internet of things market analysis forecasts, 2020–2030. In Proceedings of the 2020 Fourth World Conference on Smart Trends in Systems, Security and Sustainability (WorldS4), London, UK, 27–28 July 2020; pp. 449–453. [Google Scholar]
- Al-Amiedy, T.A.; Anbar, M.; Belaton, B.; Bahashwan, A.A.; Hasbullah, I.H.; Aladaileh, M.A.; Mukhaini, G.A. A systematic literature review on attacks defense mechanisms in RPL-based 6LoWPAN of Internet of Things. Internet Things 2023, 22, 100741. [Google Scholar] [CrossRef]
- Zhang, X.; Upton, O.; Beebe, N.L.; Choo, K.K.R. Iot botnet forensics: A comprehensive digital forensic case study on mirai botnet servers. Forensic Sci. Int. Digit. Investig. 2020, 32, 300926. [Google Scholar] [CrossRef]
- Herwig, S.; Harvey, K.; Hughey, G.; Roberts, R.; Levin, D. Measurement and analysis of Hajime, a peer-to-peer IoT botnet. In Proceedings of the Network and Distributed Systems Security (NDSS) Symposium, San Diego, CA, USA, 24–27 February 2019. [Google Scholar]
- Al-Amiedy, T.A.; Anbar, M.; Belaton, B.; Kabla, A.H.H.; Hasbullah, I.H.; Alashhab, Z.R. A systematic literature review on machine and deep learning approaches for detecting attacks in RPL-based 6LoWPAN of Internet of Things. Sensors 2022, 22, 3400. [Google Scholar] [CrossRef]
- Asgharzadeh, H.; Ghaffari, A.; Masdari, M.; Gharehchopogh, F.S. Anomaly-based intrusion detection system in the Internet of Things using a convolutional neural network and multi-objective enhanced Capuchin Search Algorithm. J. Parallel Distrib. Comput. 2023, 175, 1–21. [Google Scholar] [CrossRef]
- Krishnamurthi, R.; Kumar, A.; Gopinathan, D.; Nayyar, A.; Qureshi, B. An overview of IoT sensor data processing, fusion, and analysis techniques. Sensors 2020, 20, 6076. [Google Scholar] [CrossRef]
- Bahashwan, A.A.; Anbar, M.; Abdullah, N.; Al-Hadhrami, T.; Hanshi, S.M. Review on common IoT communication technologies for both long-range network (LPWAN) and short-range network. In Advances on Smart and Soft Computing, Proceedings of ICACIn 2020, Casablanca, Morocco, 12–13 April 2020; Springer: Singapore, 2021; pp. 341–353. [Google Scholar]
- Khan, A.R.; Kashif, M.; Jhaveri, R.H.; Raut, R.; Saba, T.; Bahaj, S.A. Deep learning for intrusion detection and security of Internet of things (IoT): Current analysis, challenges, and possible solutions. Secur. Commun. Netw. 2022, 2022, 4016073. [Google Scholar] [CrossRef]
- Shafiq, M.; Tian, Z.; Sun, Y.; Du, X.; Guizani, M. Selection of effective machine learning algorithm and Bot-IoT attacks traffic identification for internet of things in smart city. Future Gener. Comput. Syst. 2020, 107, 433–442. [Google Scholar] [CrossRef]
- Alamiedy, T.A.; Anbar, M.F.; Belaton, B.; Kabla, A.H.; Khudayer, B.H. Ensemble feature selection approach for detecting denial of service attacks in RPL networks. In Proceedings of the Advances in Cyber Security: Third International Conference, ACeS 2021, Penang, Malaysia, 24–25 August 2021; Revised Selected Papers 3. Springer: Berlin/Heidelberg, Germany, 2021; pp. 340–360. [Google Scholar]
- Ullah, S.; Ahmad, J.; Khan, M.A.; Alkhammash, E.H.; Hadjouni, M.; Ghadi, Y.Y.; Saeed, F.; Pitropakis, N. A new intrusion detection system for the internet of things via deep convolutional neural network and feature engineering. Sensors 2022, 22, 3607. [Google Scholar] [CrossRef]
- Maldonado, J.; Riff, M.C.; Neveu, B. A review of recent approaches on wrapper feature selection for intrusion detection. Expert Syst. Appl. 2022, 198, 116822. [Google Scholar] [CrossRef]
- Elhaik, E. Principal component analyses (PCA)-based findings in population genetic studies are highly biased and must be reevaluated. Sci. Rep. 2022, 12, 14683. [Google Scholar] [CrossRef]
- Kunang, Y.N.; Nurmaini, S.; Stiawan, D.; Zarkasi, A.; Firdaus; Jasmir. Automatic features extraction using autoencoder in intrusion detection system. In Proceedings of the 2018 International Conference on Electrical Engineering and Computer Science (ICECOS), Pangkal, Indonesia, 2–4 October 2018; pp. 219–224. [Google Scholar]
- Quinlan, J.R. Induction of decision trees. Mach. Learn. 1986, 1, 81–106. [Google Scholar] [CrossRef]
- Lancaster, H.O.; Seneta, E. Chi-square distribution. In Encyclopedia of Biostatistics; Wiley Online Library: Hoboken, NJ, USA, 2005; Volume 2. [Google Scholar]
- Chen, X.W.; Jeong, J.C. Enhanced recursive feature elimination. In Proceedings of the Sixth International Conference on Machine Learning and Applications (ICMLA 2007), Cincinnati, OH, USA, 13–15 December 2007; pp. 429–435. [Google Scholar]
- Gu, J.; Wang, Z.; Kuen, J.; Ma, L.; Shahroudy, A.; Shuai, B.; Liu, T.; Wang, X.; Wang, G.; Cai, J.; et al. Recent advances in convolutional neural networks. Pattern Recognit. 2018, 77, 354–377. [Google Scholar] [CrossRef]
- Li, Z.; Liu, F.; Yang, W.; Peng, S.; Zhou, J. A survey of convolutional neural networks: Analysis, applications, and prospects. IEEE Trans. Neural Netw. Learn. Syst. 2021, 33, 6999–7019. [Google Scholar] [CrossRef]
- R.M., S.P.; Maddikunta, P.K.R.; M., P.; Koppu, S.; Gadekallu, T.R.; Chowdhary, C.L.; Alazab, M. An effective feature engineering for DNN using hybrid PCA-GWO for intrusion detection in IoMT architecture. Comput. Commun. 2020, 160, 139–149. [Google Scholar] [CrossRef]
- Li, D.; Deng, L.; Lee, M.; Wang, H. IoT data feature extraction and intrusion detection system for smart cities based on deep migration learning. Int. J. Inf. Manag. 2019, 49, 533–545. [Google Scholar] [CrossRef]
- Roopak, M.; Tian, G.Y.; Chambers, J. An intrusion detection system against ddos attacks in iot networks. In Proceedings of the 2020 10th annual computing and communication workshop and conference (CCWC), Las Vegas, NV, USA, 6–8 January 2020; pp. 562–567. [Google Scholar]
- Hodo, E.; Bellekens, X.; Hamilton, A.; Dubouilh, P.L.; Iorkyase, E.; Tachtatzis, C.; Atkinson, R. Threat analysis of IoT networks using artificial neural network intrusion detection system. In Proceedings of the 2016 International Symposium on Networks, Computers and Communications (ISNCC), Yasmine Hammamet, Tunisia, 11–13 May 2016; pp. 1–6. [Google Scholar]
- Mohammed, S. A Machine Learning-Based Intrusion Detection of DDoS Attack on IoT Devices. Int. J. 2021, 10, 2278–3091. [Google Scholar]
- Alimi, K.O.A.; Ouahada, K.; Abu-Mahfouz, A.M.; Rimer, S.; Alimi, O.A. Refined LSTM Based Intrusion Detection for Denial-of-Service Attack in Internet of Things. J. Sens. Actuator Netw. 2022, 11, 32. [Google Scholar] [CrossRef]
- Ge, M.; Fu, X.; Syed, N.; Baig, Z.; Teo, G.; Robles-Kelly, A. Deep Learning-Based Intrusion Detection for IoT Networks. In Proceedings of the 2019 IEEE 24th Pacific Rim International Symposium on Dependable Computing (PRDC), Kyoto, Japan, 1–3 December 2019; pp. 256–25609. [Google Scholar] [CrossRef]
- Pecori, R.; Tayebi, A.; Vannucci, A.; Veltri, L. IoT Attack Detection with Deep Learning Analysis. In Proceedings of the 2020 International Joint Conference on Neural Networks (IJCNN), Glasgow, UK, 19–24 July 2020; pp. 1–8. [Google Scholar] [CrossRef]
- Susilo, B.; Sari, R.F. Intrusion Detection in IoT Networks Using Deep Learning Algorithm. Information 2020, 11, 279. [Google Scholar] [CrossRef]
- Kaur, G.; Habibi Lashkari, A.; Rahali, A. Intrusion Traffic Detection and Characterization using Deep Image Learning. In Proceedings of the 2020 IEEE Intl Conf on Dependable, Autonomic and Secure Computing, Intl Conf on Pervasive Intelligence and Computing, Intl Conf on Cloud and Big Data Computing, Intl Conf on Cyber Science and Technology Congress (DASC/PiCom/CBDCom/CyberSciTech), Calgary, AB, Canada, 17–22 August 2020; pp. 55–62. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Maglaras, L.; Moschoyiannis, S.; Janicke, H. Deep learning for cyber security intrusion detection: Approaches, datasets, and comparative study. J. Inf. Secur. Appl. 2020, 50, 102419. [Google Scholar] [CrossRef]
- Koroniotis, N.; Moustafa, N.; Sitnikova, E.; Turnbull, B. Towards the development of realistic botnet dataset in the Internet of Things for network forensic analytics: Bot-IoT dataset. Future Gener. Comput. Syst. 2019, 100, 779–796. [Google Scholar] [CrossRef]
- Sharafaldin, I.; Lashkari, A.H.; Ghorbani, A.A. Toward generating a new intrusion detection dataset and intrusion traffic characterization. ICISSp 2018, 1, 108–116. [Google Scholar]
- Odetola, T.A.; Oderhohwo, O.; Hasan, S.R. A scalable multilabel classification to deploy deep learning architectures for edge devices. arXiv 2019, arXiv:1911.02098. [Google Scholar]
- Alasadi, S.A.; Bhaya, W.S. Review of data preprocessing techniques in data mining. J. Eng. Appl. Sci. 2017, 12, 4102–4107. [Google Scholar]
- Ali, P.J.M.; Faraj, R.H.; Koya, E.; Ali, P.J.M.; Faraj, R.H. Data normalization and standardization: A technical report. Mach. Learn. Tech. Rep. 2014, 1, 1–6. [Google Scholar]
- Pallasdies, F.; Norton, P.; Schleimer, J.H.; Schreiber, S. Neural optimization: Understanding trade-offs with Pareto theory. Curr. Opin. Neurobiol. 2021, 71, 84–91. [Google Scholar] [CrossRef] [PubMed]
- Ahmad, Z.; Shahid Khan, A.; Nisar, K.; Haider, I.; Hassan, R.; Haque, M.R.; Tarmizi, S.; Rodrigues, J.J.P.C. Anomaly Detection Using Deep Neural Network for IoT Architecture. Appl. Sci. 2021, 11, 7050. [Google Scholar] [CrossRef]
- Snehi, M.; Bhandari, A. IoT-based DDoS on cyber physical systems: Research challenges, datasets and future prospects. In Proceedings of the 2022 IEEE International IOT, Electronics and Mechatronics Conference (IEMTRONICS), Toronto, ON, Canada, 1–4 June 2022; pp. 1–8. [Google Scholar]
- Al-Ani, A.K.; Anbar, M.; Al-Ani, A.; Ibrahim, D.R. Match-prevention technique against denial-of-service attack on address resolution and duplicate address detection processes in IPv6 link-local network. IEEE Access 2020, 8, 27122–27138. [Google Scholar] [CrossRef]
- Alalousi, A.; Razif, R.; AbuAlhaj, M.; Anbar, M.; Nizam, S. A preliminary performance evaluation of K-means, KNN and EM unsupervised machine learning methods for network flow classification. Int. J. Electr. Comput. Eng. 2016, 6, 778. [Google Scholar]
- Alieyan, K.; Kadhum, M.M.; Anbar, M.; Rehman, S.U.; Alajmi, N.K.A. An overview of DDoS attacks based on DNS. In Proceedings of the 2016 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Republic of Korea, 19–21 October 2016; pp. 276–280. [Google Scholar]
- Yazdinejad, A.; Kazemi, M.; Parizi, R.M.; Dehghantanha, A.; Karimipour, H. An ensemble deep learning model for cyber threat hunting in industrial internet of things. Digit. Commun. Netw. 2023, 9, 101–110. [Google Scholar] [CrossRef]
- Nanduri, A.; Sherry, L. Anomaly detection in aircraft data using Recurrent Neural Networks (RNN). In Proceedings of the 2016 Integrated Communications Navigation and Surveillance (ICNS), Herndon, VA, USA, 19–21 April 2016; pp. 5C2-1–5C2-8. [Google Scholar]
- Sattari, M.T.; Apaydin, H.; Shamshirband, S. Performance evaluation of deep learning-based gated recurrent units (GRUs) and tree-based models for estimating ETo by using limited meteorological variables. Mathematics 2020, 8, 972. [Google Scholar] [CrossRef]
- Elejla, O.E.; Anbar, M.; Hamouda, S.; Faisal, S.; Bahashwan, A.A.; Hasbullah, I.H. Deep-Learning-Based Approach to Detect ICMPv6 Flooding DDoS Attacks on IPv6 Networks. Appl. Sci. 2022, 12, 6150. [Google Scholar] [CrossRef]
| Layer (Type) | Output Shape | Number of Parameters | Layer/Technique Sequence |
|---|---|---|---|
| conv1d_4 (Conv1D) | (None, 79, 4) | 16 | 1 |
| batch_normalization_6 | (None, 79, 4) | 16 | 2 |
| dropout_6 | (None, 79, 4) | 0 | 3 |
| conv1d_5 (Conv1D) | (None, 75, 16) | 336 | 4 |
| batch_normalization_7 | (None, 75, 16) | 64 | 5 |
| average_pooling1d_2 | (None, 37, 16) | 0 | 6 |
| dropout_7 | (None, 37, 16) | 0 | 7 |
| cnov1 (Conv1D) | (None, 33, 120) | 9720 | 7 |
| batch_normalization_8 | (None, 33, 120) | 480 | 8 |
| dropout_8 | (None, 33, 120) | 0 | 9 |
| flatten_2 | (None, 3960) | 0 | 10 |
| dense_2 (Dense) | (None, 2) | 7922 | 11 |
| No. of normal category records | 40,073 |
| No. of attack category records | 585,710 |
| Total no. of records | 625,783 |
| No. of features | 85 |
| Evaluation Metric | Definition |
|---|---|
| Precision | The ratio of accurately predicted attacks to all samples predicted as attacks. Precision = TP/(TP + FP) |
| Recall or True Positive Rate (TPR) | The proportion of all attack samples correctly classified as attacks vs. all attack samples. Recall = TP/(TP + FN) |
| False Positive Rate (FPR) | The ratio of incorrectly predicted attack samples vs. all normal samples. False Alarm Rate = FP/(TN + FP) |
| Accuracy | The proportion of instances correctly classified vs. the total number of instances. Accuracy = (TP + TN)/(TP + TN + FP + FN) |
| F1 measure | The harmonic means of precision and recall. F1 Measure = 2 × (Precision × Recall)/(Precision + Recall) |
| AUC-ROC | The AUC-ROC is computed by plotting the TPR against the FPR at various classification thresholds and calculating the area under this curve. |
| Batch Size | Selected Features |
|---|---|
| 16 | Fwd_IAT_Min, Flow_IAT_Mean, TotLen_Bwd_Pkts, Bwd_Pkt_Len_Std, Fwd_IAT_Tot, Fwd_Pkt_Len_Max, Pkt_Size_Avg, Bwd_Pkts/s, Flow_Pkts/s, Bwd_IAT_Std |
| 32 | Flow_IAT_Max, Bwd_Header_Len, Flow_Pkts/s, Fwd_Pkts/s, Idle_Max, Bwd_Pkt_Len_Min, Pkt_Len_Std, SYN_Flag_Cnt, Bwd_IAT_Min, Active_Mean |
| 64 | Fwd_Seg_Size_Avg, RST_Flag_Cnt, Fwd_Seg_Size_Min, ECE_Flag_Cnt, ACK_Flag_Cnt, URG_Flag_Cnt, Fwd_Byts/b_Avg, Pkt_Size_Avg, Bwd_Header_Len, Fwd_IAT_Std |
| 128 | Fwd_URG_Flags, Bwd_Blk_Rate_Avg, Init_Bwd_Win_Byts, Flow_IAT_Std, Subflow_Bwd_Pkts, Down/Up_Ratio, Bwd_PSH_Flags, Fwd_Blk_Rate_Avg, Bwd_Pkt_Len_Min, Flow_Byts/s |
| 256 | Idle_Std, Flow_IAT_Min, RST_Flag_Cnt, Tot_Fwd_Pkts, URG_Flag_Cnt, Fwd_Seg_Size_Min, Subflow_Bwd_Byts, CWE_Flag_Count, Idle_Max, Flow_Duration |
| 512 | Fwd_Act_Data_Pkts, Idle_Std, Bwd_Pkt_Len_Min, CWE_Flag_Count, Bwd_Pkt_Len_Max, Fwd_Pkt_Len_Min, Pkt_Len_Min, Fwd_IAT_Min, Fwd_Blk_Rate_Avg, RST_Flag_Cnt |
| 1024 | Bwd_Pkts/b_Avg, Bwd_Seg_Size_Avg, Subflow_Fwd_Byts, Fwd_IAT_Min, Pkt_Len_Std, Bwd_Pkts/s, Fwd_IAT_Tot, Init_Bwd_Win_Byts, Idle_Std, URG_Flag_Cnt |
| Feature Set | Detection Accuracy | Precision | Recall Score | F1 Measure | FPR | AUC-ROC |
|---|---|---|---|---|---|---|
| Set1 | 95.20% | 95.33% | 99.76% | 97.49% | 4.69% | 64.15% |
| Set2 | 97.11% | 97.01% | 99.99% | 98.48% | 3.09% | 77.45% |
| Set3 | 95.00% | 95.41% | 99.45% | 97.39% | 4.68% | 64.75% |
| Set4 | 96.99% | 97.06% | 99.81% | 98.41% | 2.96% | 77.78% |
| Set5 | 97.39% | 97.54% | 99.73% | 98.62% | 2.46% | 81.48% |
| Set6 | 95.96% | 96.08% | 99.74% | 97.88% | 3.98% | 70.17% |
| Set7 | 98.04% | 98.09% | 99.85% | 98.96% | 1.93% | 85.73% |
| Model | Detection Accuracy | Precision | Recall Score | F1 Measure | FPR | AUC-ROC |
|---|---|---|---|---|---|---|
| CNN | 98.04% | 98.09% | 99.85% | 98.96% | 1.92% | 85.73% |
| RNN | 96.44% | 96.72% | 99.57% | 98.12% | 3.29% | 75.08% |
| LSTM | 96.54% | 96.68% | 99.73% | 98.18% | 3.32% | 74.87% |
| GRU | 96.60% | 96.92% | 99.53% | 98.21% | 3.07% | 76.68% |
| Algorithm | Selected Features |
|---|---|
| CNN | [‘Bwd_Pkts/b_Avg’, ‘Bwd_Seg_Size_Avg’, ‘Subflow_Fwd_Byts’, ‘Fwd_IAT_Min’, ‘Pkt_Len_Std’, ‘Bwd_Pkts/s’, ‘Fwd_IAT_Tot’, ‘Init_Bwd_Win_Byts’, ‘Idle_Std’, ‘URG_Flag_Cnt’] |
| PCA | [‘Flow_Duration’, ‘Tot_Fwd_Pkts’, ‘Tot_Bwd_Pkts’, ‘TotLen_Fwd_Pkts’, ‘TotLen_Bwd_Pkts’, ‘Fwd_Pkt_Len_Max’, ‘Fwd_Pkt_Len_Min’, ‘Fwd_Pkt_Len_Mean’, ‘Fwd_Pkt_Len_Std’, ‘Bwd_Pkt_Len_Max’] |
| AE | [‘Bwd_Pkt_Len_Max’, ‘Tot_Bwd_Pkts’, ‘Fwd_Pkt_Len_Mean’, ‘Fwd_Pkt_Len_Max’, ‘Tot_Fwd_Pkts’, ‘TotLen_Fwd_Pkts’, ‘TotLen_Bwd_Pkts’, ‘Fwd_Pkt_Len_Min’, ’Flow_Duration’, ‘Fwd_Pkt_Len_Std’] |
| IGR | [‘Flow_Duration’, ‘TotLen_Bwd_Pkts’, ‘Flow_Byts/s’, ‘Flow_IAT_Mean’, ‘Bwd_Header_Len’, ‘RST_Flag_Cnt’, ‘Subflow_Fwd_Byts’, ‘Subflow_Bwd_Byts’, ‘Active_Max’, ‘Idle_Mean’] |
| chi2 | [‘Fwd_Pkt_Len_Max’, ‘Fwd_Pkt_Len_Mean’, ‘Fwd_Pkt_Len_Std’, ‘Bwd_Pkt_Len_Min’, ‘Pkt_Len_Max’, ‘Pkt_Len_Mean’, ‘Pkt_Len_Var’, ‘RST_Flag_Cnt’, ‘Down/Up_Ratio’, ‘Subflow_Bwd_Byts’] |
| REF | [‘Flow_Duration’, ‘Fwd_Pkt_Len_Std’, ‘Flow_Byts/s’, ‘Flow_IAT_Mean’,‘Bwd_URG_Flags’, ‘Bwd_Header_Len’, ‘Bwd_Pkts/s’, ‘RST_Flag_Cnt’, ‘Subflow_Bwd_Byts’, ‘Idle_Mean’] |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alabsi, B.A.; Anbar, M.; Rihan, S.D.A. CNN-CNN: Dual Convolutional Neural Network Approach for Feature Selection and Attack Detection on Internet of Things Networks. Sensors 2023, 23, 6507. https://doi.org/10.3390/s23146507
Alabsi BA, Anbar M, Rihan SDA. CNN-CNN: Dual Convolutional Neural Network Approach for Feature Selection and Attack Detection on Internet of Things Networks. Sensors. 2023; 23(14):6507. https://doi.org/10.3390/s23146507
Chicago/Turabian StyleAlabsi, Basim Ahmad, Mohammed Anbar, and Shaza Dawood Ahmed Rihan. 2023. "CNN-CNN: Dual Convolutional Neural Network Approach for Feature Selection and Attack Detection on Internet of Things Networks" Sensors 23, no. 14: 6507. https://doi.org/10.3390/s23146507
APA StyleAlabsi, B. A., Anbar, M., & Rihan, S. D. A. (2023). CNN-CNN: Dual Convolutional Neural Network Approach for Feature Selection and Attack Detection on Internet of Things Networks. Sensors, 23(14), 6507. https://doi.org/10.3390/s23146507






