A Smart Card-Based Two-Factor Mutual Authentication Scheme for Efficient Deployment of an IoT-Based Telecare Medical Information System
Abstract
1. Introduction
- We propose an efficient and provably secure two-factor authentication scheme based on hyperelliptic curve cryptography (HECC) with a smart card-based approach;
- We use the most advantageous property of HECC, a smaller key size, to make the proposed scheme as lightweight as possible;
- The proposed authentication scheme consists of two steps: validation and verification; on the reader side, the smart card performs the first phase of authentication while the server manages the second phase.
- The proposed scheme is resistant to a variety of attacks, as demonstrated by formal and informal analyses;
- Finally, after comparing the performance of the proposed scheme with that of the existing schemes, it was found that the proposed scheme is more cost-effective than the existing schemes in terms of computation and communication costs.
2. Literature Review
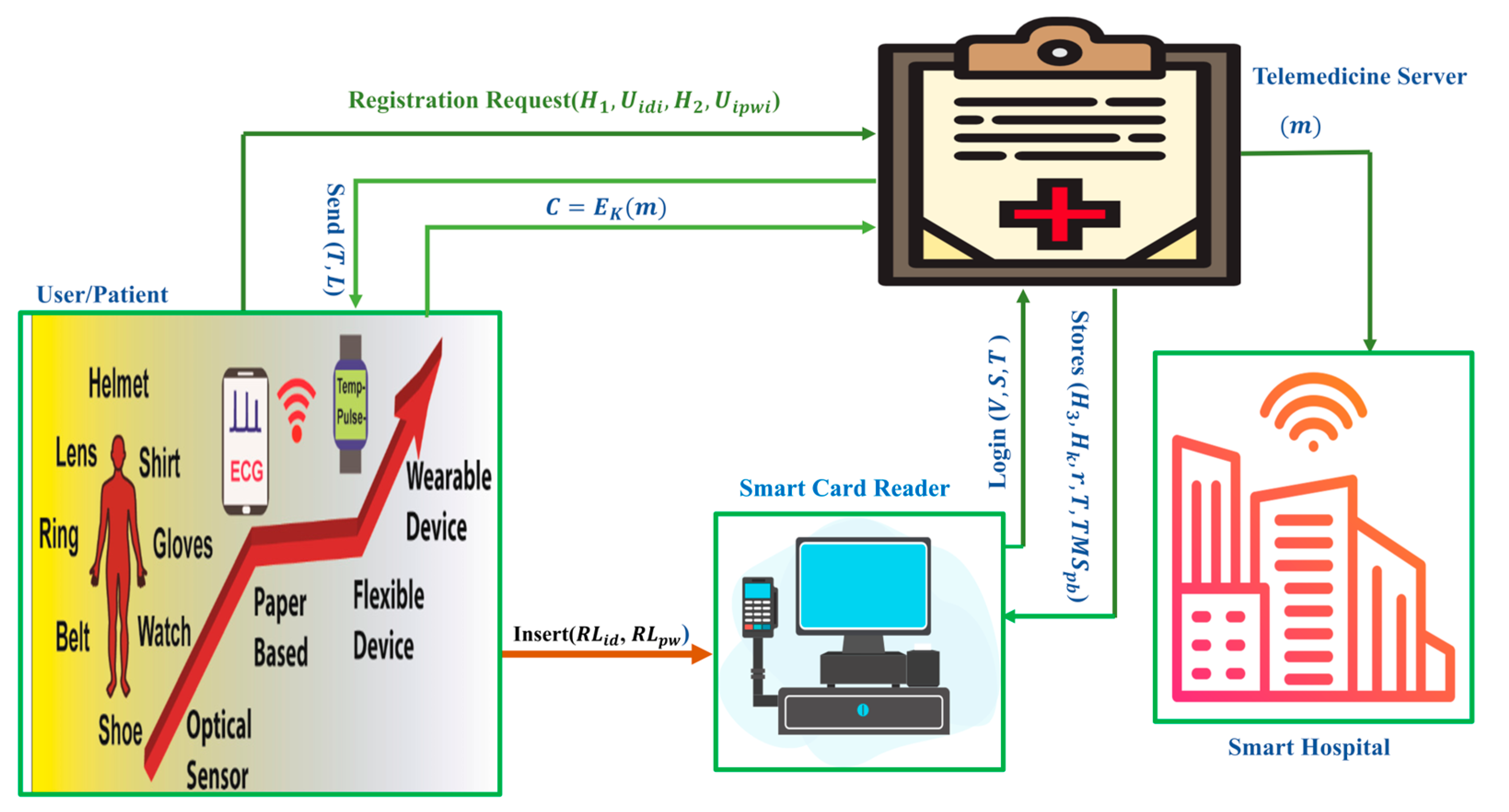
3. Network Architecture
4. Proposed Smart Card-Based Two-Factor Mutual Authentication Scheme
- Initialization: The telemedicine server (TMS) can select the hyperelliptic curve () with a genus equal to or less than 2 and a devisor () that contains 80 bits. Additionally, the finite field () has a size that is not greater than 80 bits. The TMS selects its private key from () and computes its master public key using the equation = . At the very end, it is possible for it to define some hash functions, such as (), from the SHA family.
- Key Generation: The user () selects his private key from () and computes his public key using the equation
- Registrations: With the real identity of () and password (), the user () can perform the following steps:
- Choose () from and compute ;
- Calculate , ;
- Calculate and send () to the TMS;
- When () is received by the TMS, it performs the following steps:
- It calculates and ;
- Then, the TMS stores the values () into the smart card of .
- Login: The user must insert their identity and secret password into the smart card reader during the login process. The smart card reader (SCR) performs the first level of authentication, as covered in the following steps.
- The SCR calculates and ;
- If is satisfied, then the login is accepted; otherwise, the login is denied;
- Calculates and chooses () from ;
- Calculates the equation = and =;
- Performs encryption for a random number as ;
- Generates a login request by using () and then send it to the TMS.
- Mutual Authentication: If the TMS receives the login request triples (), then it first checks the validity of the timestamp (); if it is valid, then the TMS decrypts . After this, the TMS calculates = and compares the value of equality, i.e., =; if it is satisfied, then the server calculates = and =, where is a chosen number. Then, it sends () to. When receives (), it checks the validity of and calculates =. Then, it passes the mutual authentication process and sets as a secret key for communication. After, the user encrypts as and sends to the TMS. When the TMS receives , it decrypts as .
- Password Update: This step is identical to the password update phase presented in [24].
5. Security Analysis
5.1. Formal Security Analysis
5.2. Informal Security Analysis
5.2.1. Confidentiality
5.2.2. Integrity
5.2.3. Forward Security
5.2.4. Anonymity and Untraceability
- Calculate and ;
- Verify if ) is satisfied; if yes, the login will be authorized; otherwise, the login will be denied;
- Calculate and choose () from ;
- Calculate the equation = and = ;
- Perform encryption for a random number as ;
- Generate a login request by using () and sends it to the TMS.
5.2.5. Resist against Replay Attack
- Calculates and ;
- Checks if is satisfied; if yes, then the login will be permitted; otherwise, it rejects the login;
- Computes and chooses () from ;
- Compute the equations = and = ;
- Does encryption for a random number as V = E(TMSpb)(X);
- Generates a login request by using () and sends it to the TMS.
5.2.6. Resistant against Denial-of-Service Attacks
5.2.7. Mutual Authentication
5.2.8. Key Agreement
6. Performance Analysis
6.1. Computational Cost
- The CPU architecture is 64 bits, and the processor is an Intel Core i5-10400 running at 2.90 GHz with six cores; there is also 16 GB of RAM;
- Operating System: Ubuntu 18.04 LTS;
- Library: MIRACL [26].
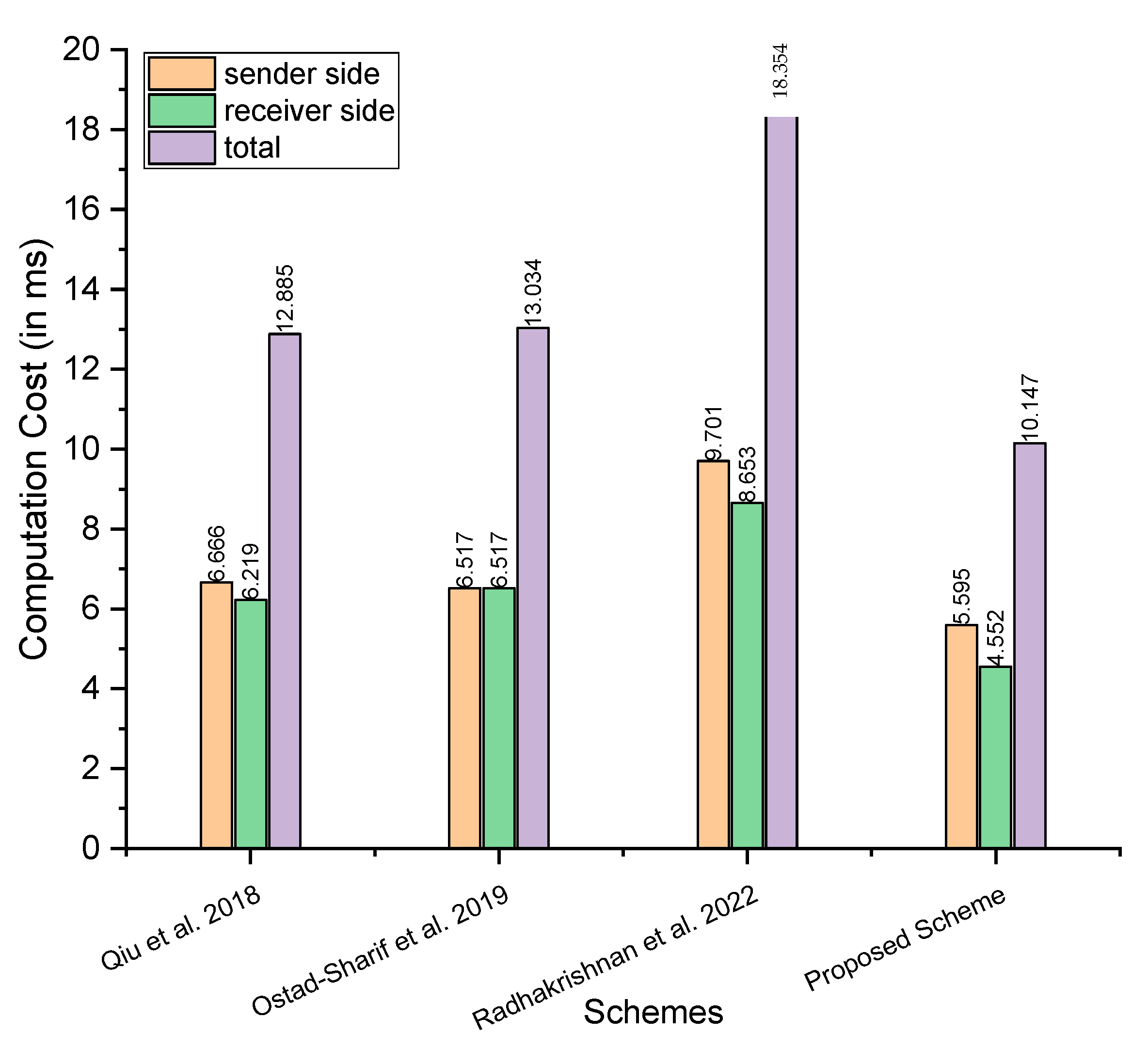
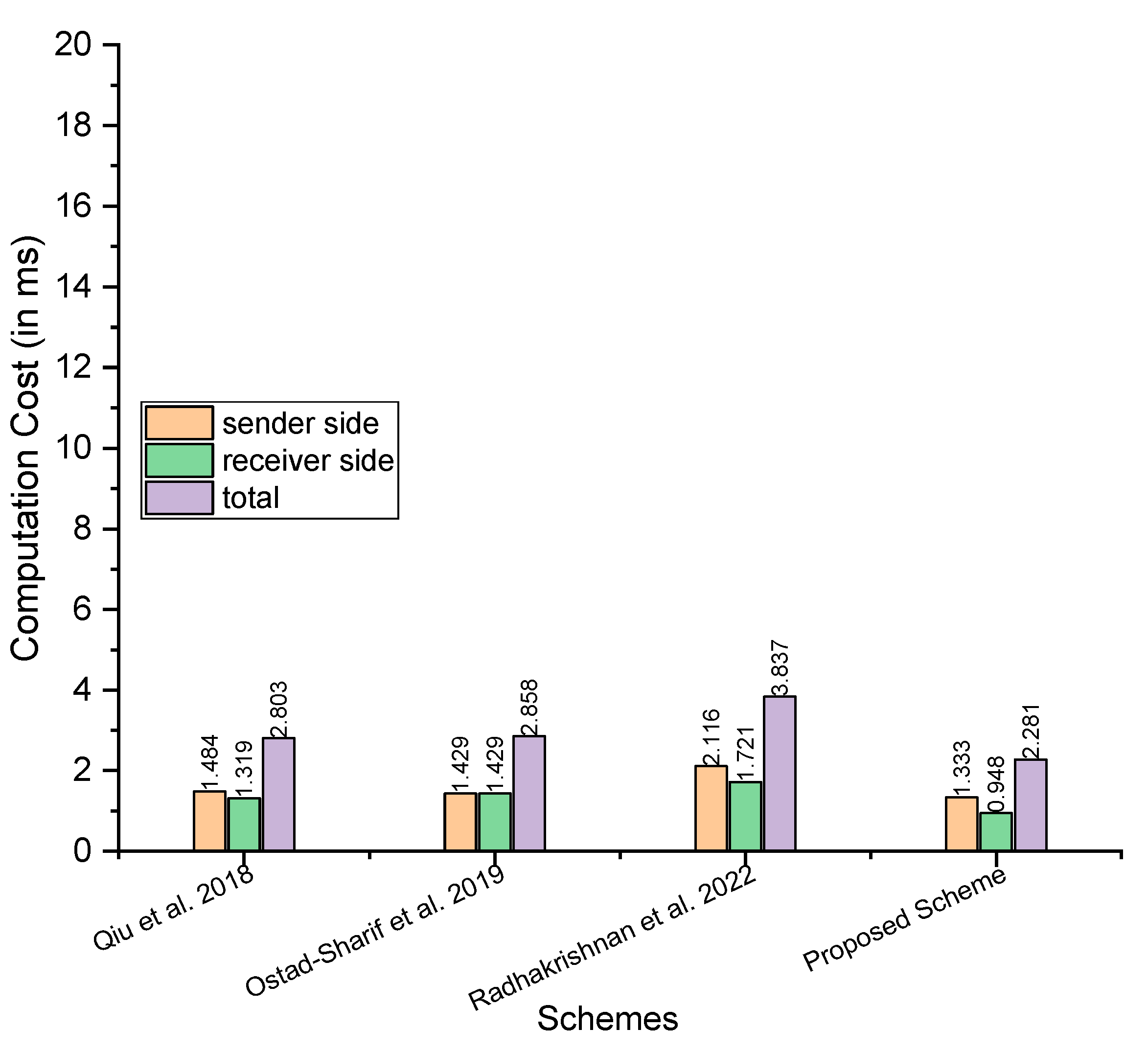
- Maximum time in milliseconds: considering the maximum time, Qiu et al. [21] need at sender side, at the receiver side, and the total is ; Ostad-Sharif et al. [22] need at sender side, at the receiver side, and the total is ; Radhakrishnan et al. [24] need at sender side, at the receiver side, and the total is ; and our proposed scheme needs at sender side, at the receiver side, and the total is
- Minimum time in milliseconds: for the minimum time in milliseconds, Qiu et al. [21] need at sender side, at the receiver side, and the total is Ostad-Sharif et al. [22] need at sender side, at the receiver side, and the total is ; Radhakrishnan et al. [24] need at sender side, at the receiver side, and the total is ; and our proposed scheme needs at sender side, at the receiver side, and the total is
- Average time in milliseconds: for the average time in milliseconds, Qiu et al. [21] need at sender side, at the receiver side, and the total is Ostad-Sharif et al. [22] need at sender side, at the receiver side, and the total is ; Radhakrishnan et al. [24] need at sender side, at the receiver side, and the total is ; and our proposed scheme needs at sender side, at the receiver side, and the total is
6.2. Communication Cost
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| BP | bilinear pairing |
| DOS | denial of service |
| ECC | elliptic curve cryptography |
| HECC | hyperelliptic curve cryptography |
| HECDLP | hyperelliptic curve discrete logarithm problem |
| IoT | Internet of things |
| KGC | key generation centre |
| MIRACL | multiprecision integer and rational arithmetic cryptographic |
| ROM | random oracle mode |
| ROR | real-or-random |
| RSA | Rivest-Shamir-Adleman |
| SHA | secure hashing algorithm |
| TMIS | telecare medicine information system |
| TMS | telemedicine server |
References
- Ullah, I.; Khan, M.A.; Abdullah, A.M.; Noor, F.; Innab, N.; Chen, C.-M. Enabling Secure Communication in Wireless Body Area Networks with Heterogeneous Authentication Scheme. Sensors 2023, 23, 1121. [Google Scholar] [CrossRef] [PubMed]
- Ullah, I.; Zeadally, S.; Amin, N.U.; Khan, M.A.; Khattak, H. Lightweight and provable secure cross-domain access control scheme for Internet of things (IoT) based wireless body area networks (WBAN). Microprocess. Microsyst. 2020, 81, 103477. [Google Scholar] [CrossRef]
- AlQahtani, S.A. An Evaluation of e-Health Service Performance through the Integration of 5G IoT, Fog, and Cloud Computing. Sensors 2023, 23, 5006. [Google Scholar] [CrossRef]
- Al-kahtani, M.S.; Khan, F.; Taekeun, W. Application of Internet of Things and Sensors in Healthcare. Sensors 2022, 22, 5738. [Google Scholar] [CrossRef] [PubMed]
- Gao, H.; Zhou, L.; Kim, J.Y.; Li, Y.; Huang, W. Applying probabilistic model checking to the behavior guidance and abnormality detection for A-MCI patients under wireless sensor network. ACM Trans. Sens. Netw. 2023, 19, 1–24. [Google Scholar] [CrossRef]
- Döschl, A.; Keller, M.-E.; Mandl, P. Performance evaluation of GPU- and cluster-computing for parallelization of compute-intensive tasks. Int. J. Web Inf. Syst. 2021, 17, 377–402. [Google Scholar] [CrossRef]
- Cardinale, Y.; Cornejo-Lupa, M.A.; Pinto-De la Gala, A.; Ticona-Herrera, R. Application of a methodological approach to compare ontologies. Int. J. Web Inf. Syst. 2021, 17, 333–376. [Google Scholar] [CrossRef]
- Khan, M.A.; Rehman, S.U.; Uddin, M.I.; Nisar, S.; Noor, F.; Alzahrani, A.; Ullah, I. An Online-Offline Certificateless Signature Scheme for Internet of Health Things. J. Health Eng. 2020, 2020, 6654063. [Google Scholar] [CrossRef]
- Chen, C.M.; Liu, S.; Chaudhry, S.A.; Chen, Y.C.; Khan, M.A. A Lightweight and Robust User Authentication Protocol with User Anonymity for IoT-Based Healthcare. CMES-Comput. Model. Eng. Sci. 2022, 131, 307–329. [Google Scholar] [CrossRef]
- Lamport, L. Password authentication with insecure communication. Commun. ACM 1981, 24, 770–772. [Google Scholar] [CrossRef]
- Ullah, I.; Alomari, A.; Ul Amin, N.; Khan, M.A.; Khattak, H. An Energy Efficient and Formally Secured Certificate-Based Signcryption for Wireless Body Area Networks with the Internet of Things. Electronics 2019, 8, 1171. [Google Scholar] [CrossRef]
- Khan, J.; Khan, G.A.; Li, J.P.; AlAjmi, M.F.; Haq, A.U.; Khan, S.; Ahmad, N.; Parveen, S.; Shahid, M.; Ahmad, S. Secure smart healthcare monitoring in industrial Internet of things (iiot) ecosystem with cosine function hybrid chaotic map encryption. Sci. Program. 2022, 2022, 8853448. [Google Scholar] [CrossRef]
- Khan, J.; Li, J.P.; Haq, A.U.; Khan, G.A.; Ahmad, S.; Abdullah Alghamdi, A.; Golilarz, N.A. Efficient secure surveillance on smart healthcare IoT system through cosine-transform encryption. J. Intell. Fuzzy Syst. 2021, 40, 1417–1442. [Google Scholar] [CrossRef]
- Chaudhry, S.A.; Irshad, A.; Khan, M.A.; Khan, S.A.; Nosheen, S.; AlZubi, A.A.; Zikria, Y.B. A Lightweight Authentication Scheme for 6G-IoT Enabled Maritime Transport System. IEEE Trans. Intell. Transp. Syst. 2021, 24, 2401–2410. [Google Scholar] [CrossRef]
- Wu, Z.Y.; Lee, Y.C.; Lai, F.; Lee, H.C.; Chung, Y. A secure authentication scheme for telecare medicine information systems. J. Med. Syst. 2010, 36, 1529–1535. [Google Scholar] [CrossRef]
- He, D.; Chen, J.; Zhang, R. A more secure authentication scheme for telecare medicine information systems. J. Med. Syst. 2012, 36, 1989–1995. [Google Scholar]
- Wei, J.; Hu, X.; Liu, W. An improved authentication scheme for telecare medicine information systems. J. Med. Syst. 2012, 36, 3597–3604. [Google Scholar] [CrossRef]
- Xu, X.; Zhu, P.; Wen, Q.; Jin, Z.; Zhang, H.; He, L. A secure and efficient authentication and key agreement scheme based on ECC for telecare medicine information systems. J. Med. Syst. 2014, 38, 9994. [Google Scholar] [CrossRef]
- Islam, S.H.; Khan, M.K. Cryptanalysis and Improvement of Authentication and Key Agreement Protocols for Telecare Medicine Information Systems. J. Med. Syst. 2014, 38, 135. [Google Scholar] [CrossRef]
- Chaudhry, S.A.; Naqvi, H.; Shon, T.; Sher, M.; Farash, M.S. Cryptanalysis and Improvement of an Improved Two Factor Authentication Protocol for Telecare Medical Information Systems. J. Med. Syst. 2015, 39, 66. [Google Scholar] [CrossRef]
- Qiu, S.; Xu, G.; Ahmad, H.; Wang, L. A Robust Mutual Authentication Scheme Based on Elliptic Curve Cryptography for Telecare Medical Information Systems. IEEE Access 2018, 6, 7452–7463. [Google Scholar] [CrossRef]
- Ostad-Sharif, A.; Abbasinezhad-Mood, D.; Nikooghadm, M. A robust and efficient ECC-based mutual authentication and session key generation scheme for healthcare applications. J. Med. Syst. 2019, 43, 10. [Google Scholar] [CrossRef] [PubMed]
- Kumari, S.; Chaudhary, P.; Chen, C.M.; Khan, M.K. Questioning key compromise attack on Ostad-Sharif et al.’s authentication and session key generation scheme for healthcare applications. IEEE Access 2019, 7, 39717–39720. [Google Scholar] [CrossRef]
- Radhakrishnan, N.; Muniyandi, A.P. Dependable and Provable Secure Two-Factor Mutual Authentication Scheme Using ECC for IoT-Based Telecare Medical Information System. J. Healthc. Eng. 2022, 2022, 9273662. [Google Scholar] [CrossRef]
- Xie, P.-S.; Pan, X.-J.; Wang, H.; Wang, J.L.; Feng, T.; Yan, Y. Conditional Privacy-Preserving Authentication Scheme for IoV Based on ECC. Int. J. Netw. Secur. 2022, 24, 501–510. [Google Scholar]
- Shamus Sofware Ltd. Miracl Library. Available online: http://github.com/miracl/MIRACL (accessed on 15 April 2023).
- Khan, M.A.; Shah, H.; Rehman, S.U.; Kumar, N.; Ghazali, R.; Shehzad, D.; Ullah, I. Securing Internet of drones with identity-based proxy signcryption. IEEE Access 2021, 9, 89133–89142. [Google Scholar] [CrossRef]
- Ullah, I.; Khan, M.A.; Khan, F.; Jan, M.A.; Srinivasan, R.; Mastorakis, S.; Hussain, S.; Khattak, H. An Efficient and Secure Multi-message and Multi-receiver Signcryption Scheme for Edge Enabled Internet of Vehicles. IEEE Internet Things J. 2021, 9, 2688–2697. [Google Scholar] [CrossRef]
| S. No | Symbol | Description |
|---|---|---|
| 1 | The hash function that belongs to the SHA family | |
| 2 | The private key of the TMS, which is selected from the finite field () | |
| 3 | () | The finite field of a hyperelliptic curve has a size that is not greater than 80 bits |
| 4 | () | The hyperelliptic curve with genus equal to or less than 2 |
| 5 | () | The devisor is on a hyperelliptic curve and has a size that is not greater than 80 bits |
| 6 | The real identity of the user | |
| 7 | () | The password for the user |
| 8 | The public key of the TMS which is the multiplication of the private key | |
| 9 | Encryption process by using the public key of the TMS | |
| 10 | Used to represent the encryption and decryption | |
| 11 | Decryption process by using the private key of the TMS | |
| 12 | It is used to represent the timestamp | |
| 13 | Three randomly generated numbers from () | |
| 14 | The secret key which is shared among the TMS and the user | |
| 15 | Encryption process by using the shared secret key of the TMS and the user | |
| 16 | Decryption process by using the shared secret key of the TMS and the user |
| Schemes | Communication Cost | Communication Cost in Bits |
|---|---|---|
| Qiu et al. [21] | ||
| Ostad-Sharif et al. [22] | ||
| Radhakrishnan et al. [24] | ||
| Proposed Scheme |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khan, M.A.; Alhakami, H.; Alhakami, W.; Shvetsov, A.V.; Ullah, I. A Smart Card-Based Two-Factor Mutual Authentication Scheme for Efficient Deployment of an IoT-Based Telecare Medical Information System. Sensors 2023, 23, 5419. https://doi.org/10.3390/s23125419
Khan MA, Alhakami H, Alhakami W, Shvetsov AV, Ullah I. A Smart Card-Based Two-Factor Mutual Authentication Scheme for Efficient Deployment of an IoT-Based Telecare Medical Information System. Sensors. 2023; 23(12):5419. https://doi.org/10.3390/s23125419
Chicago/Turabian StyleKhan, Muhammad Asghar, Hosam Alhakami, Wajdi Alhakami, Alexey V. Shvetsov, and Insaf Ullah. 2023. "A Smart Card-Based Two-Factor Mutual Authentication Scheme for Efficient Deployment of an IoT-Based Telecare Medical Information System" Sensors 23, no. 12: 5419. https://doi.org/10.3390/s23125419
APA StyleKhan, M. A., Alhakami, H., Alhakami, W., Shvetsov, A. V., & Ullah, I. (2023). A Smart Card-Based Two-Factor Mutual Authentication Scheme for Efficient Deployment of an IoT-Based Telecare Medical Information System. Sensors, 23(12), 5419. https://doi.org/10.3390/s23125419