An Evidence Theoretic Approach for Traffic Signal Intrusion Detection
Abstract
1. Introduction
- We developed a theoretical model for our proposed IDS, leveraging the Dempster–Shafer (DS) decision theory. Our model incorporates real-time observations of vehicle flow rate, vehicle speed, and traffic signal change duration, as well as relevant historical data obtained from transportation authorities. By utilising this decision theory, we sought to enhance the performance of our proposed system, leading to a more efficient and effective traffic control system. Our approach enables the integration of both historical and real-time data, facilitating the system’s ability to make more precise and informed decisions.
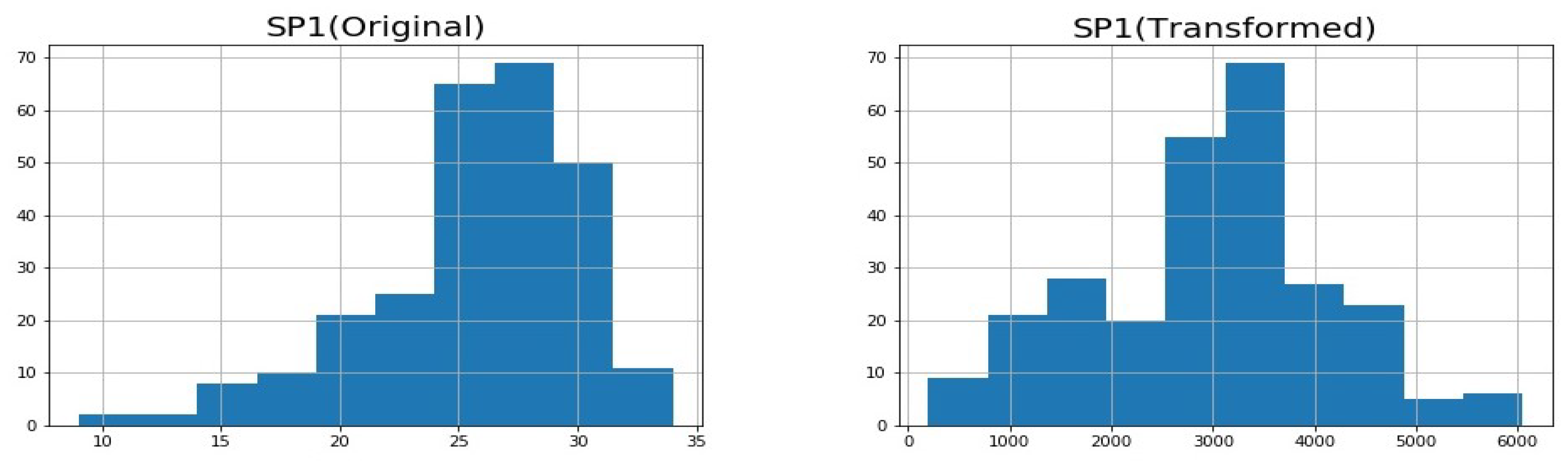
- The historical data associated with traffic flow and vehicle speed were transformed into normal distributions. A heuristic mass function was introduced by assigning higher probabilities to those phase time values that are most frequently observed and are closer to the most observed value.
- To assess the uncertainty associated with our observations, we utilised Shannon’s entropy. In order to verify and validate our proposed IDS, we developed a simulation model that is based on the SUMO traffic simulator [14]. Our simulation model incorporates real-world scenarios and utilises data collected by the Victorian Transportation Authority, Australia (VicRoads). The results of our simulations demonstrate that our proposed IDS is highly effective in detecting intrusions on traffic signals while reducing false alarms.
2. Related Works
2.1. Intrusion in Traffic Signals
2.2. Evaluating the Impact of an Attack on Traffic Signals
2.3. Detecting Intrusions in Traffic Signal
3. Proposed Intrusion Detection System
- Data collection: Traffic data are collected from the intelligent traffic system, including information on traffic flow rate, vehicle speed, and phase time.
- Baseline generation: A baseline is generated from the collected traffic data, which represents the normal traffic patterns and behaviour for the system.
- Anomaly detection: The traffic data are continuously monitored for any deviations from the baseline. Significant deviation from the baseline is flagged as potential anomalies and investigated further.
- Response: Once an anomaly is detected, the system sends an alarm to the traffic controller.
3.1. Overview of the Proposed IDS
3.2. Monitoring the Status of the Traffic Signal
3.3. Development of the Probability Mass Function
3.4. Data Conversion into Normal Distribution
3.5. Probabilities of Observed Evidence for Flow Rate and Vehicle Speed
3.6. Probability of Observed Evidence for Phase Time
4. Evaluating the Traffic Signal to Detect Intrusion
4.1. Simulation Environment
4.2. Performance Metrics
4.3. Results and Analysis
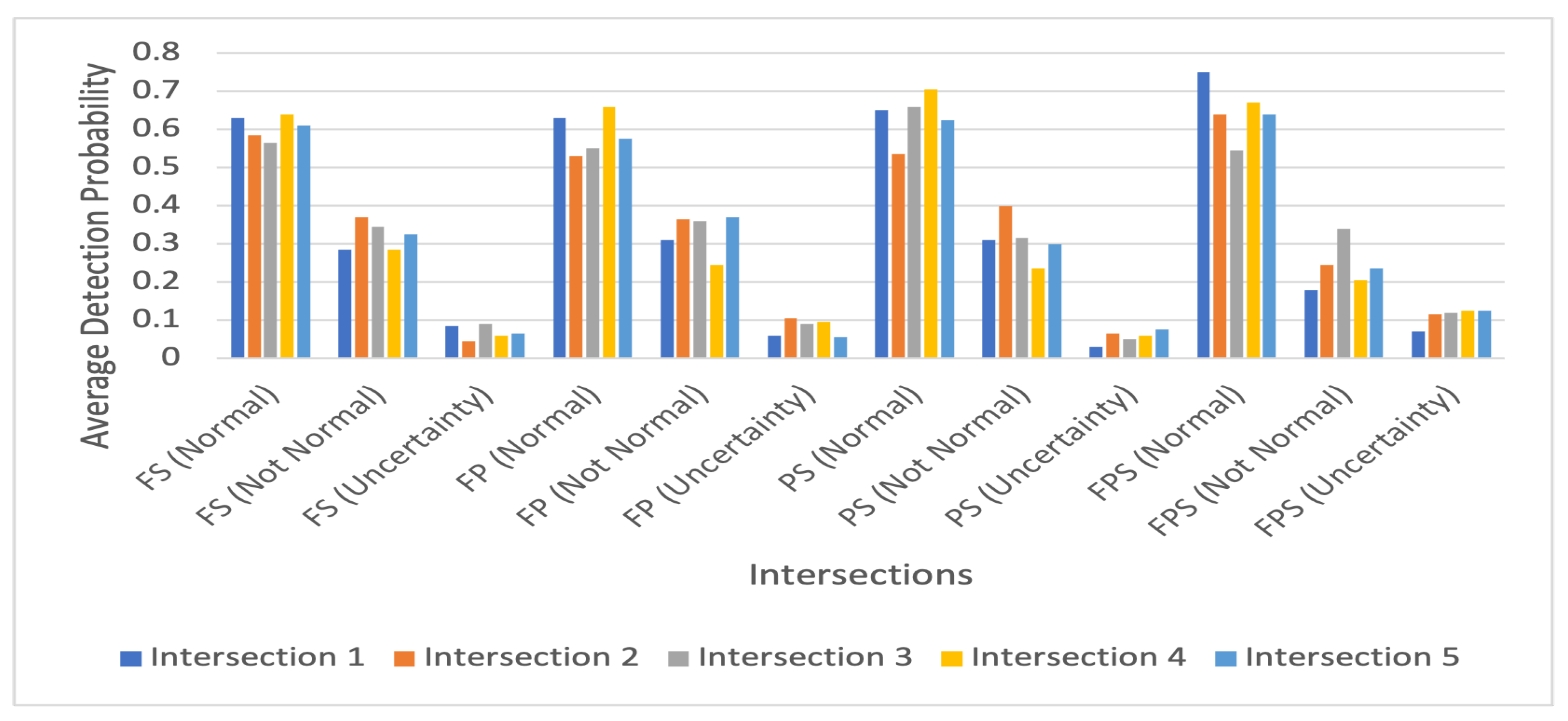
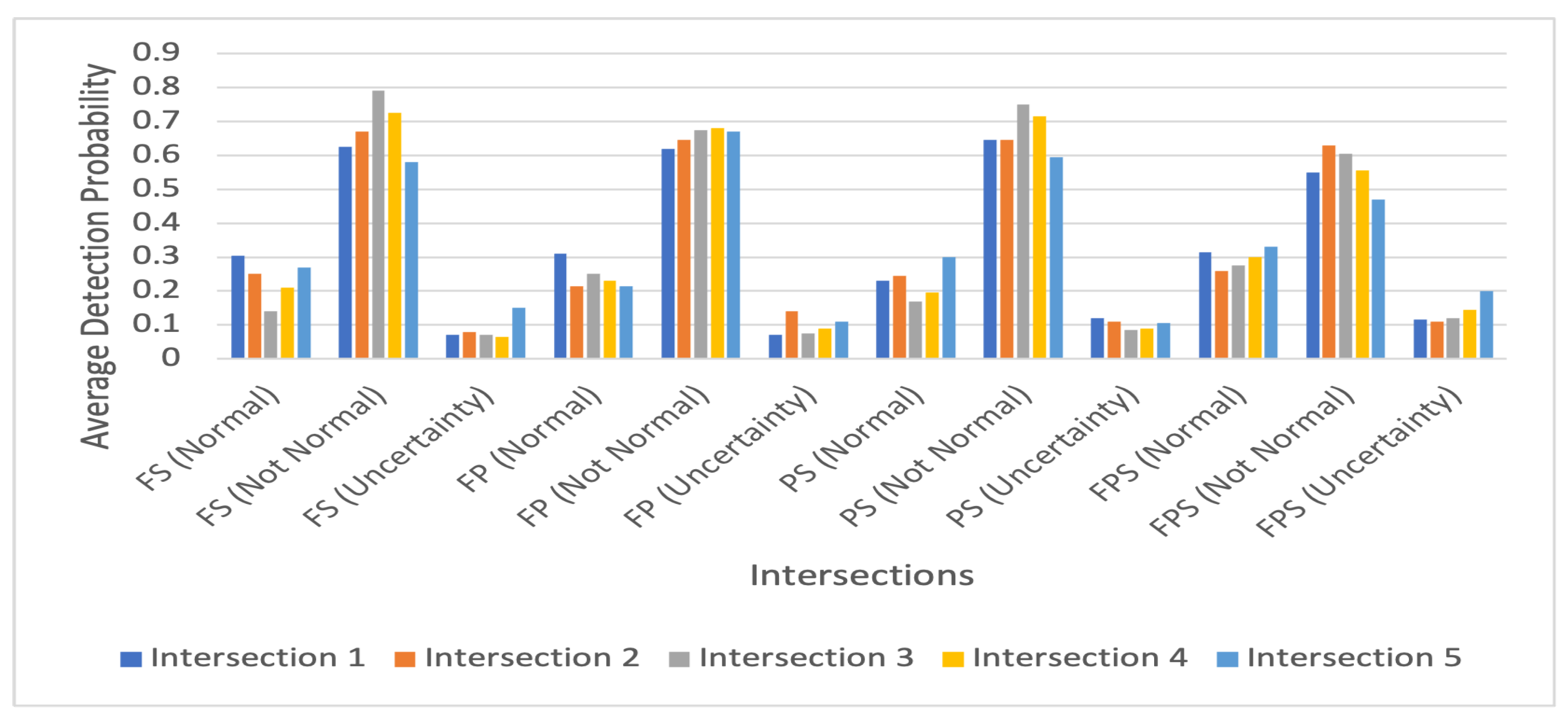
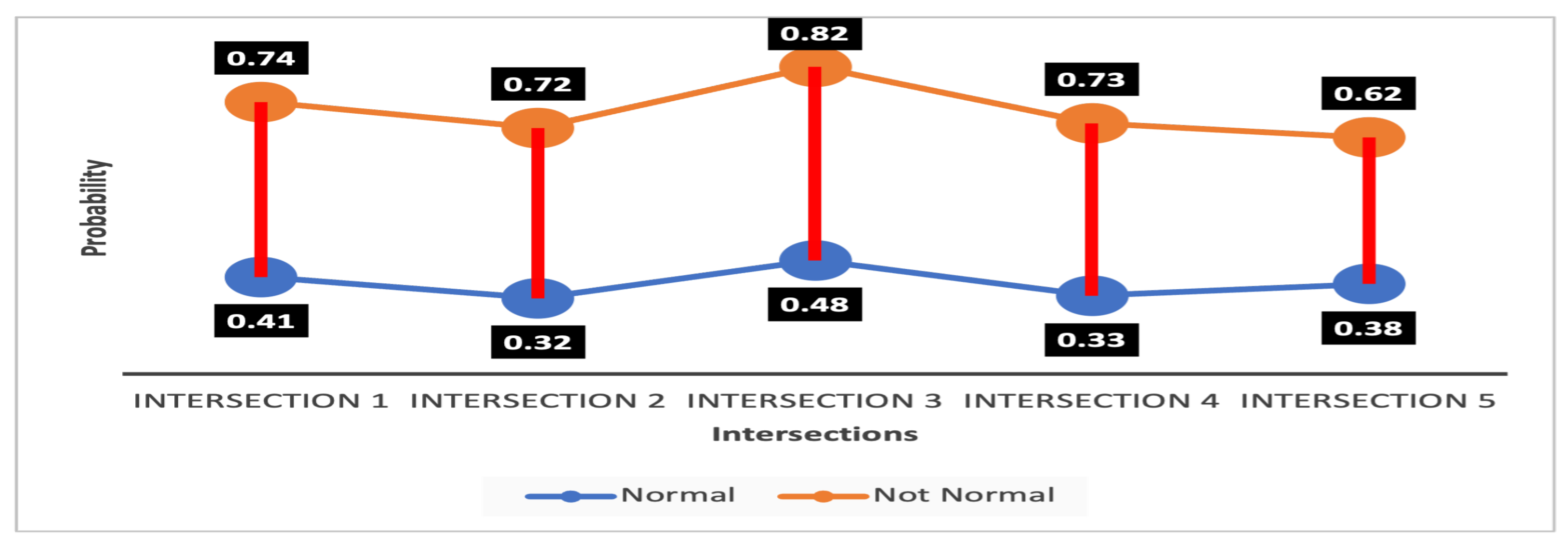
4.3.1. Detection Probability
4.3.2. Class Separability
4.3.3. Detection Performance
- Flow rate and phase time:The model utilising flow rate and phase time as features has sensitivity values ranging from 0.79 to 0.86, specificity values between 0.61 and 0.83, accuracy values varying from 0.77 to 0.85, and F1-Scores ranging from 0.70 to 0.84. This model seems to have a relatively good overall performance with varying levels of specificity.
- Phase time and vehicle speed:This model, based on phase time and vehicle speed, shows sensitivity values between 0.81 and 0.88, specificity values ranging from 0.72 to 0.78, accuracy values varying from 0.79 to 0.85, and F1-Scores ranging from 0.76 to 0.82. The performance of this model is consistent and generally good across all instances.
- Flow rate and vehicle speed:For the model using flow rate and vehicle speed as features, sensitivity values range from 0.81 to 0.87, specificity values are between 0.72 and 0.77, accuracy values vary from 0.79 to 0.83, and F1-Scores range from 0.77 to 0.81. This model demonstrates a fairly consistent and good performance across all instances, with a slightly lower specificity compared to the phase time and vehicle speed model.
- Flow rate, phase time, and vehicle speed:The model that includes all three features—flow rate, phase time, and vehicle speed—has sensitivity values ranging from 0.78 to 0.83, specificity values between 0.52 and 0.62, accuracy values varying from 0.73 to 0.78, and F1-Scores ranging from 0.63 to 0.71. This model shows a drop in performance, especially in specificity, when compared to the other models.The models with the best performance are those that utilise two features: phase time and vehicle speed or flow rate and vehicle speed. The phase time and vehicle speed model shows a slightly better performance than the flow rate and vehicle speed model, with higher specificity values. The model using all three features (flow rate, phase time, and vehicle speed) exhibits the lowest performance, especially in specificity. Based on these findings, it is recommended to use the phase time and vehicle speed model or the flow rate and vehicle speed model for further analysis or deployment.
5. Conclusions
Author Contributions
Funding
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Salih, K.O.M.; Rashid, T.A.; Radovanovic, D.; Bacanin, N. A comprehensive survey on the Internet of Things with the industrial marketplace. Sensors 2022, 22, 730. [Google Scholar] [CrossRef] [PubMed]
- Chowdhury, A. Priority based and secured traffic management system for emergency vehicle using IoT. In Proceedings of the 2016 International Conference on Engineering & MIS (ICEMIS), Agadir, Morocco, 22–24 September 2016; pp. 1–6. [Google Scholar]
- Cafiso, S.; Di Graziano, A.; Giuffrè, T.; Pappalardo, G.; Severino, A. Managed Lane as Strategy for Traffic Flow and Safety: A Case Study of Catania Ring Road. Sustainability 2022, 14, 2915. [Google Scholar] [CrossRef]
- Ning, Z.; Zhang, F.; Remias, S. Understanding the security of traffic signal infrastructure. In Proceedings of the International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, Gothenburg, Sweden, 19–20 June 2019; Springer: Berlin/Heidelberg, Germany, 2019; pp. 154–174. [Google Scholar]
- Li, Z.; Jin, D.; Hannon, C.; Shahidehpour, M.; Wang, J. Assessing and mitigating cybersecurity risks of traffic light systems in smart cities. IET Cyber-Phys. Syst. Theory Appl. 2016, 1, 60–69. [Google Scholar] [CrossRef]
- Feng, Y.; Huang, S.; Chen, Q.A.; Liu, H.X.; Mao, Z.M. Vulnerability of traffic control system under cyber attacks using falsified data. In Proceedings of the 97th Annual Meeting of the Transportation Research Board, Washington, DC, USA, 7–11 January 2018. [Google Scholar]
- Wei, Q.; Yang, B. Adaptable vehicle detection and speed estimation for changeable urban traffic with anisotropic magnetoresistive sensors. IEEE Sens. J. 2017, 17, 2021–2028. [Google Scholar] [CrossRef]
- Zhang, X.; Wang, D. Adaptive traffic signal control mechanism for intelligent transportation based on a consortium blockchain. IEEE Access 2019, 7, 97281–97295. [Google Scholar] [CrossRef]
- Perrine, K.A.; Levin, M.W.; Yahia, C.N.; Duell, M.; Boyles, S.D. Implications of traffic signal cybersecurity on potential deliberate traffic disruptions. Transp. Res. Part A Policy Pract. 2019, 120, 58–70. [Google Scholar] [CrossRef]
- Turner, G.; Chen, G.; Zhang, Y. A Visual Analytics Approach for Anomaly Detection from a Novel Traffic Light Data. Electron. Imaging 2021, 2021, 330–331. [Google Scholar] [CrossRef]
- Xiang, Y.; Niu, W.; Tong, E.; Li, Y.; Jia, B.; Wu, Y.; Liu, J.; Chang, L.; Li, G. Congestion attack detection in intelligent traffic signal system: Combining empirical and analytical methods. Secur. Commun. Netw. 2021, 2021, 1–17. [Google Scholar] [CrossRef]
- Li, Y.; Xiang, Y.; Tong, E.; Niu, W.; Jia, B.; Li, L.; Liu, J.; Han, Z. An empirical study on gan-based traffic congestion attack analysis: A visualized method. Wirel. Commun. Mob. Comput. 2020, 2020, 1–14. [Google Scholar] [CrossRef]
- Chowdhury, A.; Karmakar, G.; Kamruzzaman, J.; Saha, T. Detecting Intrusion in the Traffic Signals of an Intelligent Traffic System. In Proceedings of the International Conference on Information and Communications Security, Lille, France, 29–31 October 2018; Springer: Cham, Switzerland, 2018; pp. 696–707. [Google Scholar]
- Han, G.H.; Chen, X.R.; Yu, Y.; Li, Y.Q. A study of microscopic traffic simulation based on sumo platform. Comput. Eng. Sci. 2012, 34, 195–198. [Google Scholar]
- Zhu, L.; Yu, F.R.; Wang, Y.; Ning, B.; Tang, T. Big data analytics in intelligent transportation systems: A survey. IEEE Trans. Intell. Transp. Syst. 2018, 20, 383–398. [Google Scholar] [CrossRef]
- Gonçalves, F.; Ribeiro, B.; Gama, O.; Santos, A.; Costa, A.; Dias, B.; Macedo, J.; Nicolau, M.J. A systematic review on intelligent intrusion detection systems for VANETs. In Proceedings of the 2019 11th International Congress on Ultra Modern Telecommunications and Control Systems and Workshops (ICUMT), Dublin, Ireland, 28–30 October 2019; pp. 1–10. [Google Scholar]
- Gibbs, S. Ransomware Attack on San Francisco Public Transit Gives Everyone a Free Ride. 2016. Available online: https://www.theguardian.com/technology/2016/nov/28/passengers-free-ride-san-francisco-muni-ransomeware (accessed on 12 March 2023).
- Perallos, A.; Hernandez-Jayo, U.; Zuazola, I.J.G.; Onieva, E. Intelligent Transport Systems: Technologies and Applications; John Wiley & Sons: Hoboken, NJ, USA, 2015. [Google Scholar]
- Li, W.; Nejad, M.; Zhang, R. A blockchain-based architecture for traffic signal control systems. In Proceedings of the 2019 IEEE International Congress on Internet of Things (ICIOT), Milan, Italy, 8–13 July 2019; pp. 33–40. [Google Scholar]
- Chen, Q.A.; Yin, Y.; Feng, Y.; Mao, Z.M.; Liu, H.X. Exposing Congestion Attack on Emerging Connected Vehicle based Traffic Signal Control. In Proceedings of the NDSS, San Diego, CA, USA, 18–21 February 2018. [Google Scholar]
- Wang, X.; Xiang, Y.; Niu, W.; Tong, E.; Chen, Q.A.; Li, G.; Liu, J.; Li, L. Constructing Optimal Sparse Decision Tree for Analying I-SIG System Attack. In Proceedings of the 2020 IEEE Intl Conf on Parallel & Distributed Processing with Applications, Big Data & Cloud Computing, Sustainable Computing & Communications, Social Computing & Networking (ISPA/BDCloud/SocialCom/SustainCom), Exeter, UK, 17–19 December 2020; pp. 321–328. [Google Scholar]
- Pretorius, B.; van Niekerk, B. IIoT Security: Do I Really Need a Firewall for my Train? In Proceedings of the ICCWS 2019 14th International Conference on Cyber Warfare and Security: ICCWS 2019, Stellenbosch, South Africa, 28 February–1 March 2019; Academic Conferences and Publishing Limited: Montreal, QC, Canada, 2019; p. 338. [Google Scholar]
- Naveed, Q.N.; Alqahtani, H.; Khan, R.U.; Almakdi, S.; Alshehri, M.; Abdul Rasheed, M.A. An intelligent traffic surveillance system using integrated wireless sensor network and improved phase timing optimization. Sensors 2022, 22, 3333. [Google Scholar] [CrossRef] [PubMed]
- Xiang, Y.; Chen, T.; Li, Y.; Tian, Y.; Niu, W.; Tong, E.; Liu, J.; Jia, B.; Wu, Y.; Huang, X. Predicting Congestion Attack of Variable Spoofing Frequency for Reliable Traffic Signal System. In Proceedings of the Security and Privacy in New Computing Environments: 4th EAI International Conference, SPNCE 2021, Virtual Event, 10–11 December 2021; Springer: Berlin/Heidelberg, Germany, 2022; pp. 219–237. [Google Scholar]
- Jiang, N. Optimal signal design for mixed equilibrium networks with autonomous and regular vehicles. J. Adv. Transp. 2017, 2017, 5649823. [Google Scholar] [CrossRef]
- Bhatnagar, S.; Guo, R.; McCabe, K.; McCluskey, T.L.; Scala, E.; Vallati, M. Leveraging Artificial Intelligence for Simulating Traffic Signal Strategies. In Proceedings of the 2022 IEEE 25th International Conference on Intelligent Transportation Systems (ITSC), Macau, China, 8–12 October 2022; pp. 607–612. [Google Scholar]
- Wang, H.; Zhu, M.; Hong, W.; Wang, C.; Tao, G.; Wang, Y. Optimizing signal timing control for large urban traffic networks using an adaptive linear quadratic regulator control strategy. IEEE Trans. Intell. Transp. Syst. 2020, 23, 333–343. [Google Scholar] [CrossRef]
- Chowdhury, A.; Karmakar, G.; Kamruzzaman, J.; Jolfaei, A.; Das, R. Attacks on self-driving cars and their countermeasures: A survey. IEEE Access 2020, 8, 207308–207342. [Google Scholar] [CrossRef]
- Javaid, S.; Sufian, A.; Pervaiz, S.; Tanveer, M. Smart traffic management system using Internet of Things. In Proceedings of the 2018 20th International Conference on Advanced Communication Technology (ICACT), Chuncheon, Republic of Korea, 11–14 February 2018; pp. 393–398. [Google Scholar]
- VicRoads. VicRoads Traffic Data. 2019. Available online: https://discover.data.vic.gov.au/dataset/traffic-volume (accessed on 20 February 2023).
- Chowdhury, A.; Karmakar, G.; Kamruzzaman, J.; Islam, S. Trustworthiness of self-driving vehicles for intelligent transportation systems in industry applications. IEEE Trans. Ind. Inform. 2020, 17, 961–970. [Google Scholar] [CrossRef]
- Wu, Y.; Meng, F.; Wang, G.; Yi, P. A dempster-shafer theory based traffic information trust model in vehicular ad hoc networks. In Proceedings of the 2015 International Conference on Cyber Security of Smart Cities, Industrial Control System and Communications (SSIC), Shanghai, China, 5–7 August 2015; pp. 1–7. [Google Scholar]
- Rényi, A. On measures of entropy and information. In Proceedings of the Fourth Berkeley Symposium on Mathematical Statistics and Probability, Volume 1: Contributions to the Theory of Statistics; University of California Press: Berkeley, CA, USA, 1961; pp. 547–561. [Google Scholar]
- Atkinson, A.C.; Riani, M.; Corbellini, A. The Box–Cox Transformation: Review and Extensions. Stat. Sci. 2021, 36, 239–255. [Google Scholar] [CrossRef]
- Krajzewicz, D.; Erdmann, J.; Behrisch, M.; Bieker, L. Recent development and applications of SUMO-Simulation of Urban MObility. Int. J. Adv. Syst. Meas. 2012, 5, 128–138. [Google Scholar]
- Krauß, S. Microscopic Modeling of Traffic Flow: Investigation of Collision Free Vehicle Dynamics. Ph.D. Thesis, Forschungszentrum fuer Luft- und Raumfahrt (DLR), Köln, Germany, 1998. [Google Scholar]
- Song, J.; Wu, Y.; Xu, Z.; Lin, X. Research on car-following model based on SUMO. In Proceedings of the 7th IEEE/International Conference on Advanced Infocomm Technology, Fuzhou, China, 14–16 November 2014; pp. 47–55. [Google Scholar]
- VicRoads. Traffic Volume. 2023. Available online: https://vicroadsopendata-vicroadsmaps.opendata.arcgis.com/datasets/vicroadsmaps::traffic-volume/about (accessed on 12 March 2023).
- VicRoads. Traffic Lights. 2023. Available online: https://vicroadsopendata-vicroadsmaps.opendata.arcgis.com/datasets/vicroadsmaps::traffic-lights/about (accessed on 12 March 2023).
- VicRoads. Traffic Signal Volume Data. 2023. Available online: https://discover.data.vic.gov.au/dataset/traffic-signal-volume-data (accessed on 12 March 2023).



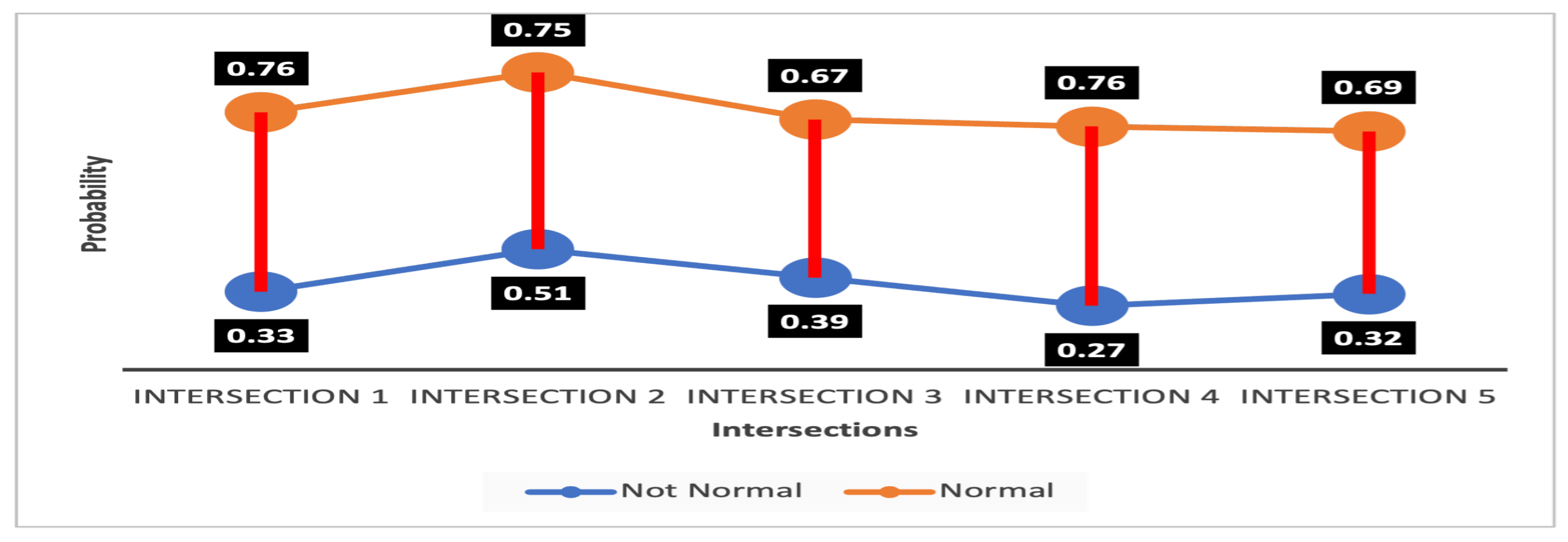
| Normal (N) | Not Normal (¬ N) | Uncertainty (N N) | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| FS | FP | PS | FPS | FS | FP | PS | FPS | FS | FP | PS | FPS | |
| 1 | 0.58 | 0.65 | 0.71 | 0.76 | 0.3 | 0.29 | 0.27 | 0.16 | 0.12 | 0.06 | 0.02 | 0.08 |
| 2 | 0.75 | 0.58 | 0.64 | 0.72 | 0.23 | 0.31 | 0.29 | 0.17 | 0.02 | 0.11 | 0.07 | 0.11 |
| 3 | 0.48 | 0.52 | 0.67 | 0.58 | 0.39 | 0.36 | 0.29 | 0.21 | 0.13 | 0.12 | 0.04 | 0.21 |
| 4 | 0.61 | 0.61 | 0.76 | 0.63 | 0.31 | 0.29 | 0.21 | 0.25 | 0.08 | 0.1 | 0.03 | 0.12 |
| 5 | 0.57 | 0.52 | 0.58 | 0.59 | 0.32 | 0.39 | 0.3 | 0.22 | 0.11 | 0.09 | 0.12 | 0.19 |
| Normal (N) | Not Normal (¬ N) | Uncertainty (N N) | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| FS | FP | PS | FPS | FS | FP | PS | FPS | FS | FP | PS | FPS | |
| 1 | 0.41 | 0.38 | 0.24 | 0.41 | 0.51 | 0.53 | 0.64 | 0.5 | 0.08 | 0.09 | 0.12 | 0.09 |
| 2 | 0.32 | 0.27 | 0.32 | 0.38 | 0.62 | 0.64 | 0.57 | 0.56 | 0.06 | 0.09 | 0.11 | 0.06 |
| 3 | 0.27 | 0.48 | 0.32 | 0.46 | 0.66 | 0.44 | 0.62 | 0.43 | 0.07 | 0.08 | 0.06 | 0.11 |
| 4 | 0.19 | 0.24 | 0.21 | 0.33 | 0.72 | 0.69 | 0.71 | 0.55 | 0.09 | 0.07 | 0.08 | 0.12 |
| 5 | 0.23 | 0.17 | 0.26 | 0.28 | 0.63 | 0.72 | 0.62 | 0.54 | 0.14 | 0.11 | 0.12 | 0.18 |
| Normal (N) | Not Normal (¬ N) | Uncertainty (N N) | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| FS | FP | PS | FPS | FS | FP | PS | FPS | FS | FP | PS | FPS | |
| 1 | 0.68 | 0.61 | 0.59 | 0.74 | 0.27 | 0.33 | 0.35 | 0.2 | 0.05 | 0.06 | 0.04 | 0.06 |
| 2 | 0.42 | 0.48 | 0.50 | 0.51 | 0.51 | 0.42 | 0.51 | 0.32 | 0.07 | 0.1 | 0.06 | 0.12 |
| 3 | 0.65 | 0.58 | 0.66 | 0.51 | 0.30 | 0.36 | 0.34 | 0.47 | 0.05 | 0.06 | 0.06 | 0.03 |
| 4 | 0.67 | 0.71 | 0.65 | 0.72 | 0.26 | 0.20 | 0.26 | 0.16 | 0.04 | 0.09 | 0.09 | 0.13 |
| 5 | 0.65 | 0.63 | 0.67 | 0.69 | 0.33 | 0.35 | 0.30 | 0.25 | 0.02 | 0.02 | 0.03 | 0.06 |
| Normal (N) | Not Normal (¬ N) | Uncertainty (N N) | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| FS | FP | PS | FPS | FS | FP | PS | FPS | FS | FP | PS | FPS | |
| 1 | 0.20 | 0.24 | 0.22 | 0.22 | 0.74 | 0.71 | 0.65 | 0.6 | 0.06 | 0.05 | 0.12 | 0.14 |
| 2 | 0.18 | 0.16 | 0.17 | 0.14 | 0.71 | 0.65 | 0.72 | 0.70 | 0.10 | 0.19 | 0.11 | 0.16 |
| 3 | 0.01 | 0.02 | 0.02 | 0.09 | 0.92 | 0.91 | 0.88 | 0.78 | 0.08 | 0.07 | 0.11 | 0.13 |
| 4 | 0.23 | 0.22 | 0.18 | 0.27 | 0.73 | 0.67 | 0.72 | 0.56 | 0.04 | 0.11 | 0.10 | 0.17 |
| 5 | 0.31 | 0.26 | 0.34 | 0.38 | 0.53 | 0.62 | 0.57 | 0.40 | 0.16 | 0.11 | 0.09 | 0.22 |
| Sen. | Spec. | Acc. | F1 | ||||||
|---|---|---|---|---|---|---|---|---|---|
| FP | 1 | 1960 | 678 | 122 | 536 | 0.79 | 0.85 | 0.80 | 0.82 |
| 2 | 2052 | 306 | 194 | 444 | 0.82 | 0.61 | 0.79 | 0.70 | |
| 3 | 2316 | 664 | 136 | 380 | 0.86 | 0.83 | 0.85 | 0.84 | |
| 4 | 2157 | 513 | 287 | 439 | 0.83 | 0.64 | 0.79 | 0.72 | |
| 5 | 2324 | 505 | 295 | 572 | 0.80 | 0.63 | 0.77 | 0.71 | |
| PS | 1 | 2352 | 619 | 181 | 414 | 0.85 | 0.77 | 0.83 | 0.81 |
| 2 | 2025 | 578 | 222 | 471 | 0.81 | 0.72 | 0.79 | 0.76 | |
| 3 | 2435 | 626 | 174 | 382 | 0.86 | 0.78 | 0.85 | 0.82 | |
| 4 | 2187 | 606 | 194 | 309 | 0.88 | 0.76 | 0.85 | 0.81 | |
| 5 | 2343 | 582 | 218 | 453 | 0.84 | 0.73 | 0.81 | 0.78 | |
| FS | 1 | 2074 | 577 | 223 | 322 | 0.87 | 0.72 | 0.83 | 0.79 |
| 2 | 2295 | 612 | 188 | 401 | 0.85 | 0.77 | 0.83 | 0.81 | |
| 3 | 2377 | 613 | 187 | 512 | 0.82 | 0.77 | 0.81 | 0.79 | |
| 4 | 1866 | 589 | 211 | 430 | 0.81 | 0.74 | 0.79 | 0.77 | |
| 5 | 2203 | 613 | 187 | 393 | 0.85 | 0.77 | 0.83 | 0.81 | |
| FPS | 1 | 2126 | 458 | 342 | 612 | 0.78 | 0.57 | 0.73 | 0.66 |
| 2 | 2052 | 473 | 327 | 444 | 0.82 | 0.59 | 0.77 | 0.69 | |
| 3 | 2352 | 466 | 334 | 472 | 0.83 | 0.58 | 0.78 | 0.69 | |
| 4 | 1826 | 413 | 387 | 417 | 0.81 | 0.52 | 0.74 | 0.63 | |
| 5 | 2192 | 496 | 304 | 452 | 0.83 | 0.62 | 0.78 | 0.71 | |
| Overall | 0.82 | 0.71 | 0.79 | 0.80 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chowdhury, A.; Karmakar, G.; Kamruzzaman, J.; Das, R.; Newaz, S.H.S. An Evidence Theoretic Approach for Traffic Signal Intrusion Detection. Sensors 2023, 23, 4646. https://doi.org/10.3390/s23104646
Chowdhury A, Karmakar G, Kamruzzaman J, Das R, Newaz SHS. An Evidence Theoretic Approach for Traffic Signal Intrusion Detection. Sensors. 2023; 23(10):4646. https://doi.org/10.3390/s23104646
Chicago/Turabian StyleChowdhury, Abdullahi, Gour Karmakar, Joarder Kamruzzaman, Rajkumar Das, and S. H. Shah Newaz. 2023. "An Evidence Theoretic Approach for Traffic Signal Intrusion Detection" Sensors 23, no. 10: 4646. https://doi.org/10.3390/s23104646
APA StyleChowdhury, A., Karmakar, G., Kamruzzaman, J., Das, R., & Newaz, S. H. S. (2023). An Evidence Theoretic Approach for Traffic Signal Intrusion Detection. Sensors, 23(10), 4646. https://doi.org/10.3390/s23104646









