Steganography in IoT: Information Hiding with APDS-9960 Proximity and Gestures Sensor
Abstract
:1. Introduction
2. Materials and Methods
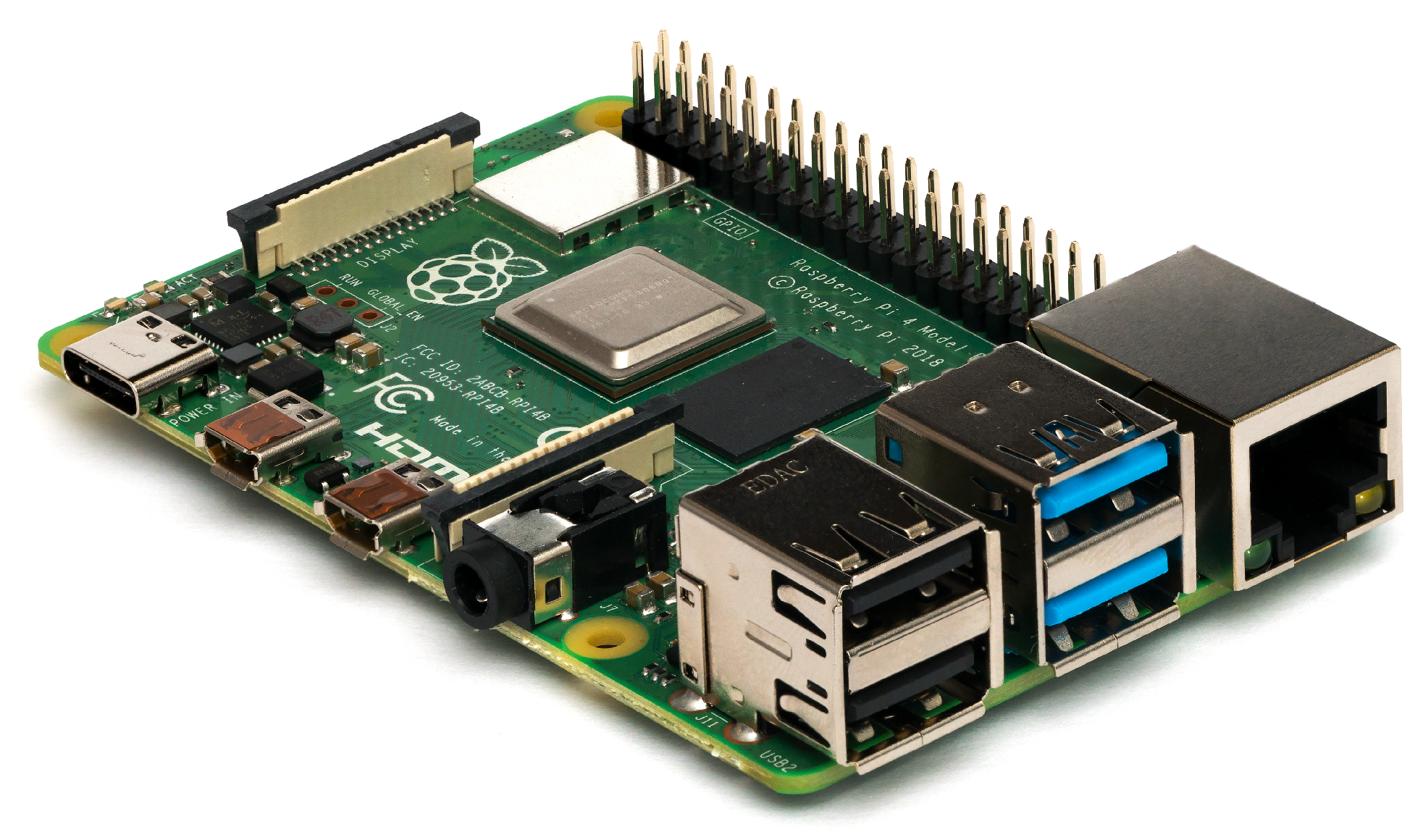
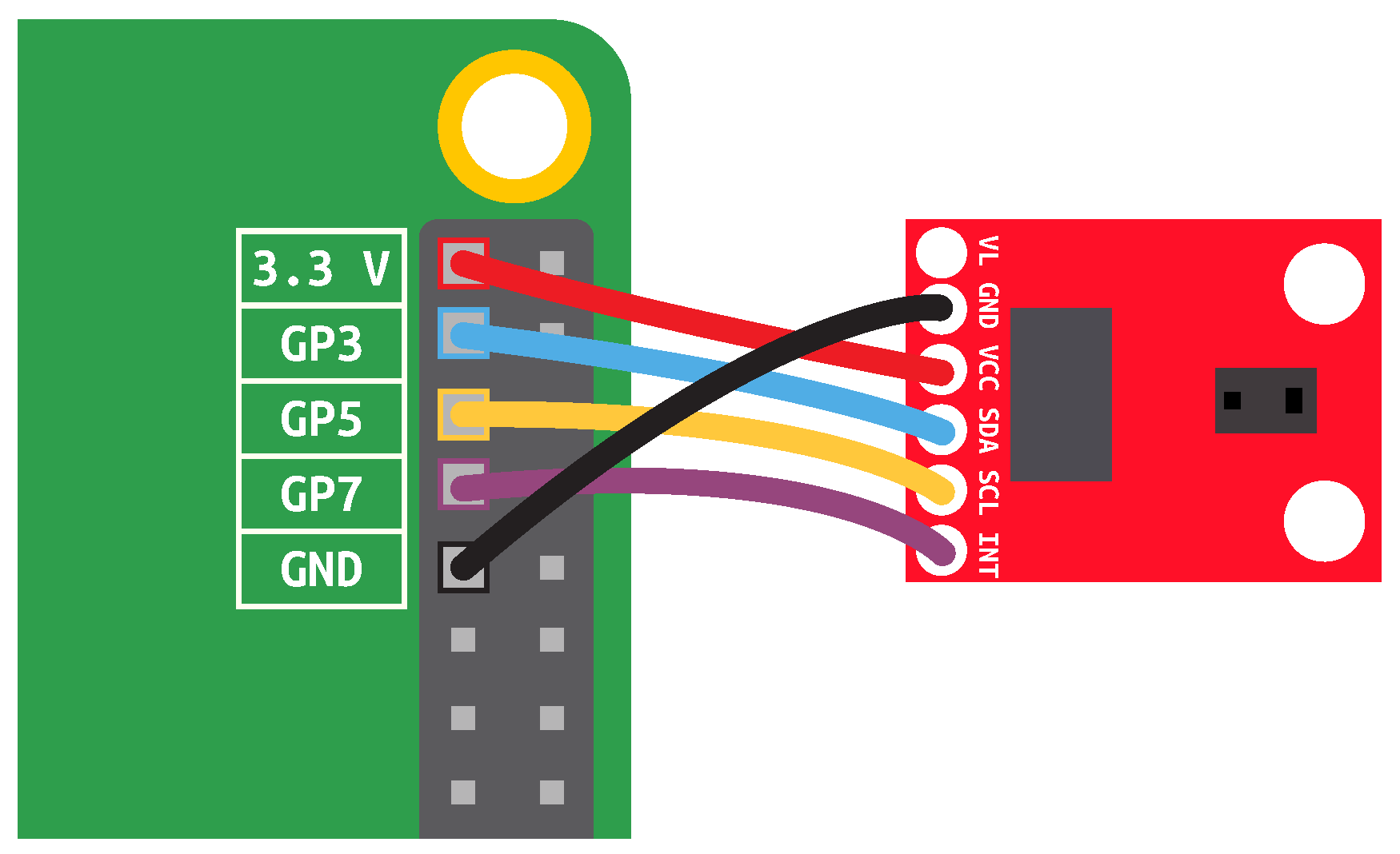
2.1. Hardware
2.2. Configuration
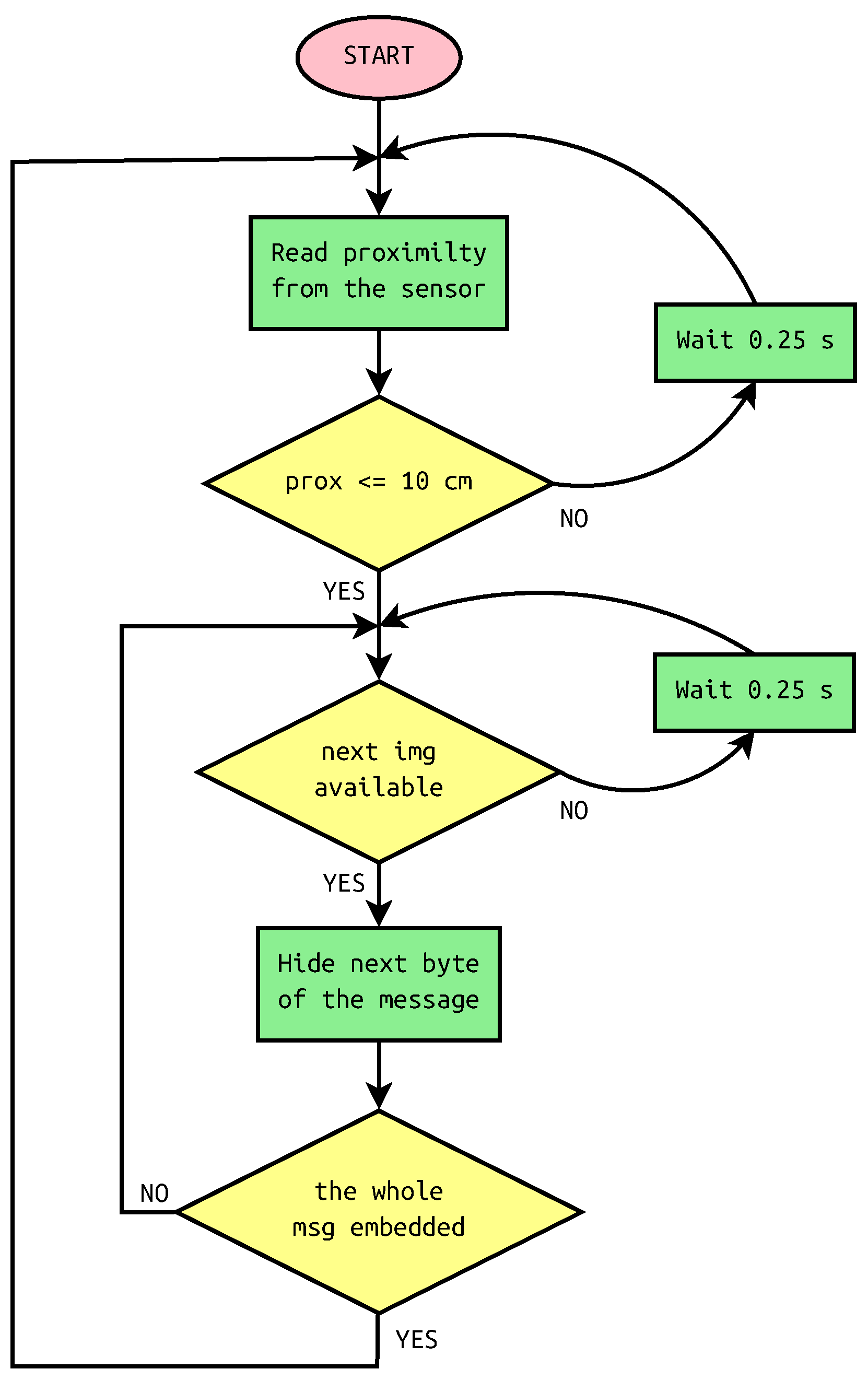
2.3. Methods
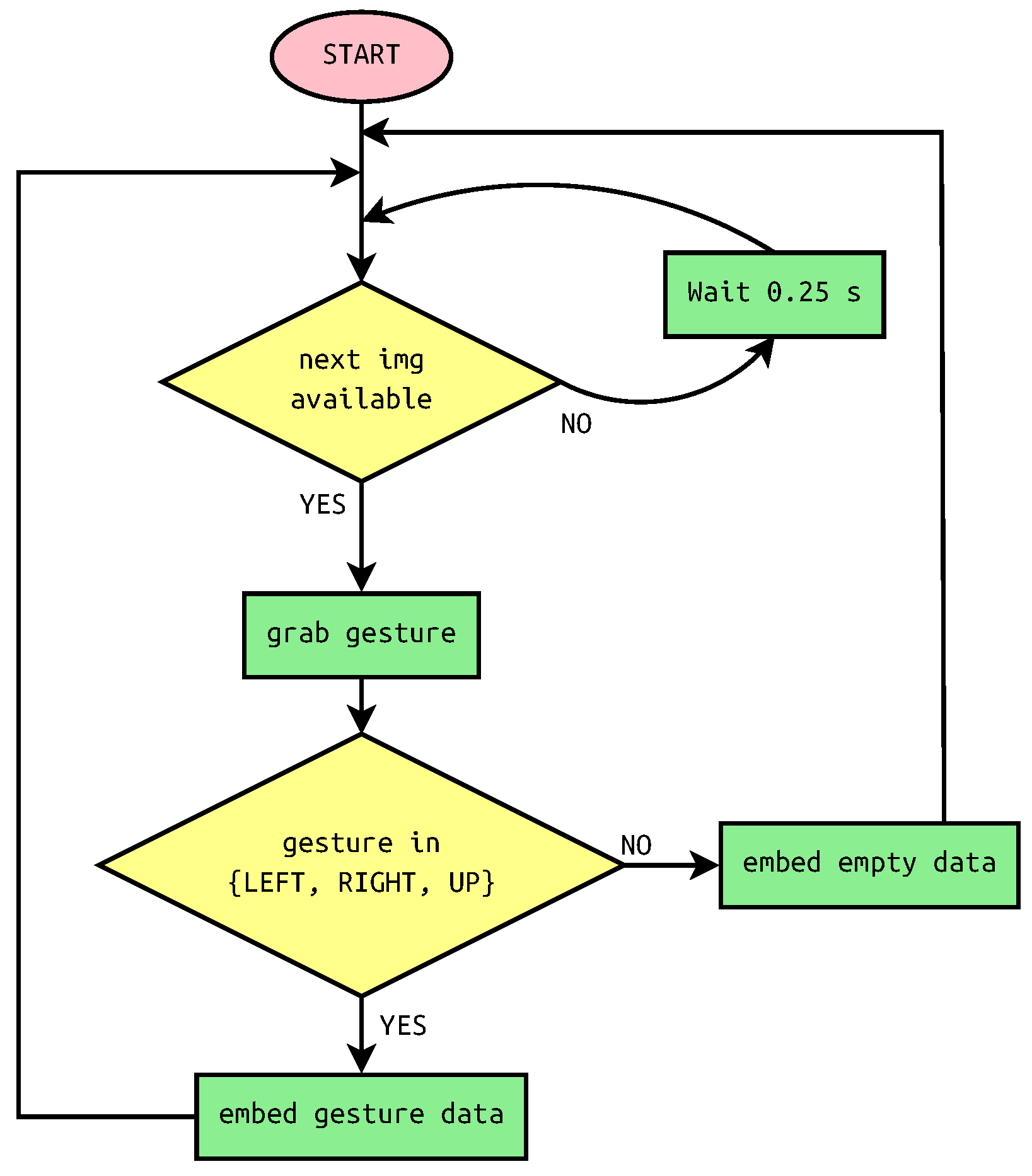
2.4. Gesture Detection
2.5. Implementation Details
| Algorithm 1: Embedding algorithm in trigger mode |
 |
| Algorithm 2: Extracting algorithm in trigger mode |
 |
| Algorithm 3: Embedding algorithm in data input mode |
 |
| Algorithm 4: Extracting algorithm in data input mode |
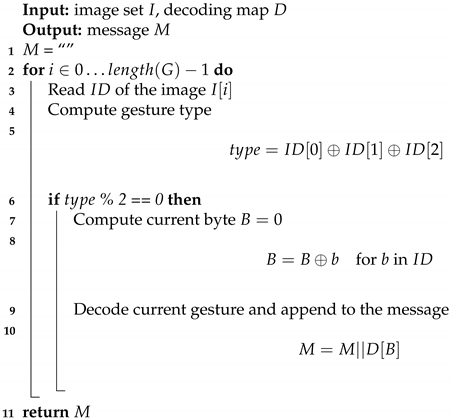 |
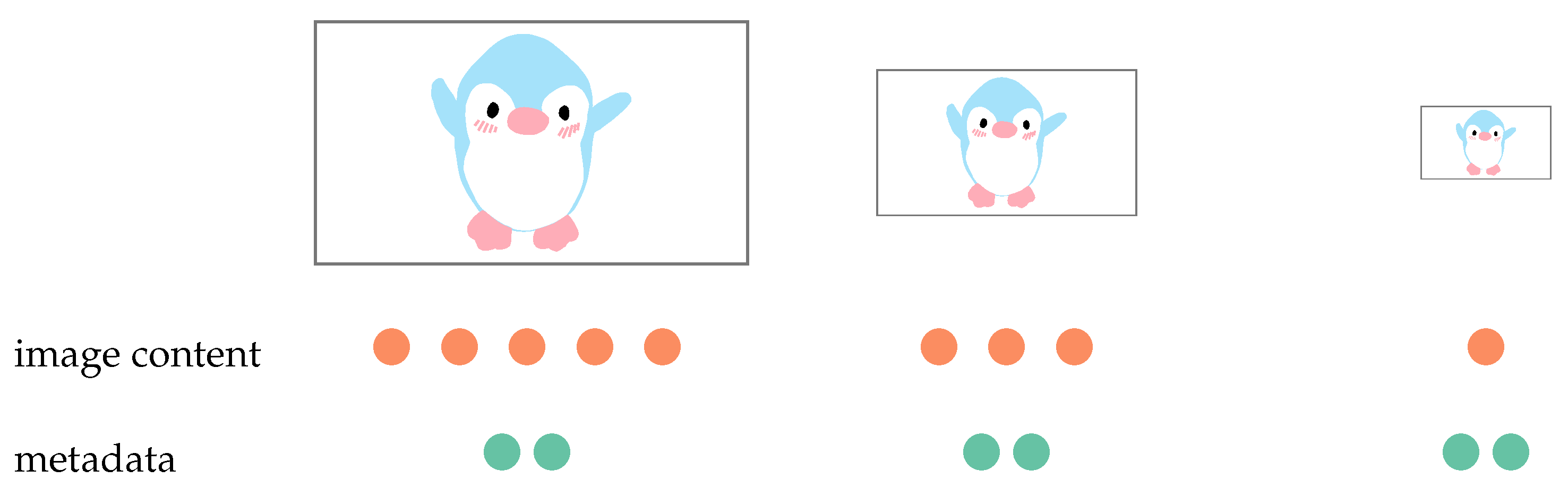
2.6. Datasets
3. Tests
4. Results
5. Discussion
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Wang, J.; Yang, Y.; Wang, T.; Sherratt, R.; Zhang, J. Big Data Service Architecture: A Survey. J. Internet Technol. 2020, 21, 393–405. [Google Scholar]
- Bayrakdar, M.E. Cost effective smart system for water pollution control with underwater wireless sensor networks: A simulation study. Comput. Syst. Sci. Eng. 2020, 35, 283–292. [Google Scholar] [CrossRef]
- Sivakumar, N.R. Stabilizing energy consumption in unequal clusters of wireless sensor networks. Comput. Mater. Contin. 2020, 64, 81–96. [Google Scholar] [CrossRef]
- Janarthanan, A.; Kumar, D. Localization based evolutionary routing (LOBER) for efficient aggregation in wireless multimedia sensor networks. Comput. Mater. Contin. 2019, 60, 895–912. [Google Scholar] [CrossRef] [Green Version]
- The OWASP IoT Security Team, OWASP Top Ten IoT. 2018. Available online: https://owasp.org/www-pdf-archive/OWASP-IoT-Top-10-2018-final.pdf (accessed on 21 March 2022).
- Rahman, S.; Masood, F.; Khan, W.U.; Ullah, N.; Khan, F.Q.; Tsaramirsis, G.; Jan, S.; Ashraf, M. A novel approach of image steganography for secure communication based on lsb substitution technique. Comput. Mater. Contin. 2020, 64, 31–61. [Google Scholar] [CrossRef]
- Das, R.; Baykara, M.; Tuna, G. A novel approach to steganography: Enhanced least significant bit substitution algorithm integrated with self-determining encryption feature. Comput. Syst. Sci. Eng. 2019, 34, 23–32. [Google Scholar] [CrossRef]
- Koptyra, K.; Ogiela, M.R. Lightweight and efficient approach for multi-secret steganography. Int. J. Embed. Syst. 2020, 20, 434–440. [Google Scholar] [CrossRef]
- Available online: https://www.raspberrypi.com/ (accessed on 21 March 2022).
- Avago Technologies. APDS-9960: Digital Proximity, Ambient Light, RGB and Gesture Sensor. Data Sheet. 2015. Available online: https://www.google.com.hk/url?sa=t&rct=j&q=&esrc=s&source=web&cd=&ved=2ahUKEwip0quSzOr2AhVmF6YKHY7CATkQFnoECAUQAQ&url=https%3A%2F%2Fwww.mouser.com%2Fdatasheet%2F2%2F678%2FV02-4191EN_DS_APDS-9960_2015-11-13-909346.pdf&usg=AOvVaw0GUoMvG4WEZMwmbRjvzr9r (accessed on 21 March 2022).
- Arducam. OV5647 Mini Camera Module for Raspberry Pi, Rev 3.0. Data Sheet. 2017. Available online: https://www.arducam.com/product/arducam-ov5647-standard-raspberry-pi-camera-b0033/ (accessed on 21 March 2022).
- Ogiela, M.R.; Koptyra, K. False and multi-secret steganography in digital images. Soft Comput. 2015, 19, 3331–3339. [Google Scholar] [CrossRef]
- Penna, G.D.; Orefice, S. Using spatial relations for qualitative specification of gestures. Comput. Syst. Sci. Eng. 2019, 34, 325–338. [Google Scholar] [CrossRef]
- Yin, J.H.J.; Fen, G.M.; Mughal, F.; Iranmanesh, V. Internet of Things: Securing Data using Image Steganography. In Proceedings of the 2015 Third International Conference on Artificial Intelligence, Modelling and Simulation, Kota Kinabalu, Malaysia, 2–4 December 2015. [Google Scholar] [CrossRef]
- Manik, C.; Prema, S. Instigating Improved Steganography Scheme for Internet of Things. Int. Adv. Res. J. Sci. Eng. Technol. 2018, 5, 83–87. [Google Scholar]
- Sangeetha, R.; Koteeswari, G.; Phil, M. Securing Data in IOT using Cryptography & Steganography Techniques. Int. J. Res. Eng. Sci. IJRES 2021, 9, 1–5. [Google Scholar]
- Subhedar, M.S.; Mankar, V.H. Current status and key issues in image steganography: A survey. Comput. Sci. Rev. 2014, 13–14, 95–113. [Google Scholar] [CrossRef]
- Westfeld, A. F5—A steganographic algorithm: High capacity despite better steganalysis. In Proceedings of the 4th International Workshop on Information Hiding, Pittsburgh, PA, USA, 25–27 April 2001; Springer: Berlin/Heidelberg, Germany, 2001; pp. 289–302. [Google Scholar]
- Castiglione, A.; De Santis, A.; Fiore, U.; Palmieri, F. E-mail-based covert channels for asynchronous message steganography. In Proceedings of the Fifth International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing (IMIS), Seoul, Korea, 30 June–2 July 2011; pp. 503–508. [Google Scholar]
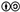 ).
).
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Koptyra, K.; Ogiela, M.R. Steganography in IoT: Information Hiding with APDS-9960 Proximity and Gestures Sensor. Sensors 2022, 22, 2612. https://doi.org/10.3390/s22072612
Koptyra K, Ogiela MR. Steganography in IoT: Information Hiding with APDS-9960 Proximity and Gestures Sensor. Sensors. 2022; 22(7):2612. https://doi.org/10.3390/s22072612
Chicago/Turabian StyleKoptyra, Katarzyna, and Marek R. Ogiela. 2022. "Steganography in IoT: Information Hiding with APDS-9960 Proximity and Gestures Sensor" Sensors 22, no. 7: 2612. https://doi.org/10.3390/s22072612
APA StyleKoptyra, K., & Ogiela, M. R. (2022). Steganography in IoT: Information Hiding with APDS-9960 Proximity and Gestures Sensor. Sensors, 22(7), 2612. https://doi.org/10.3390/s22072612






