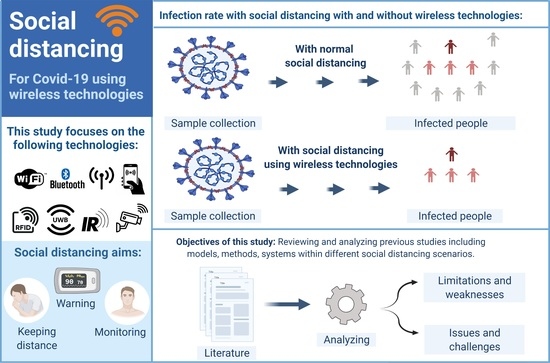
Wireless Technologies for Social Distancing in the Time of COVID-19: Literature Review, Open Issues, and Limitations
Abstract
:1. Introduction
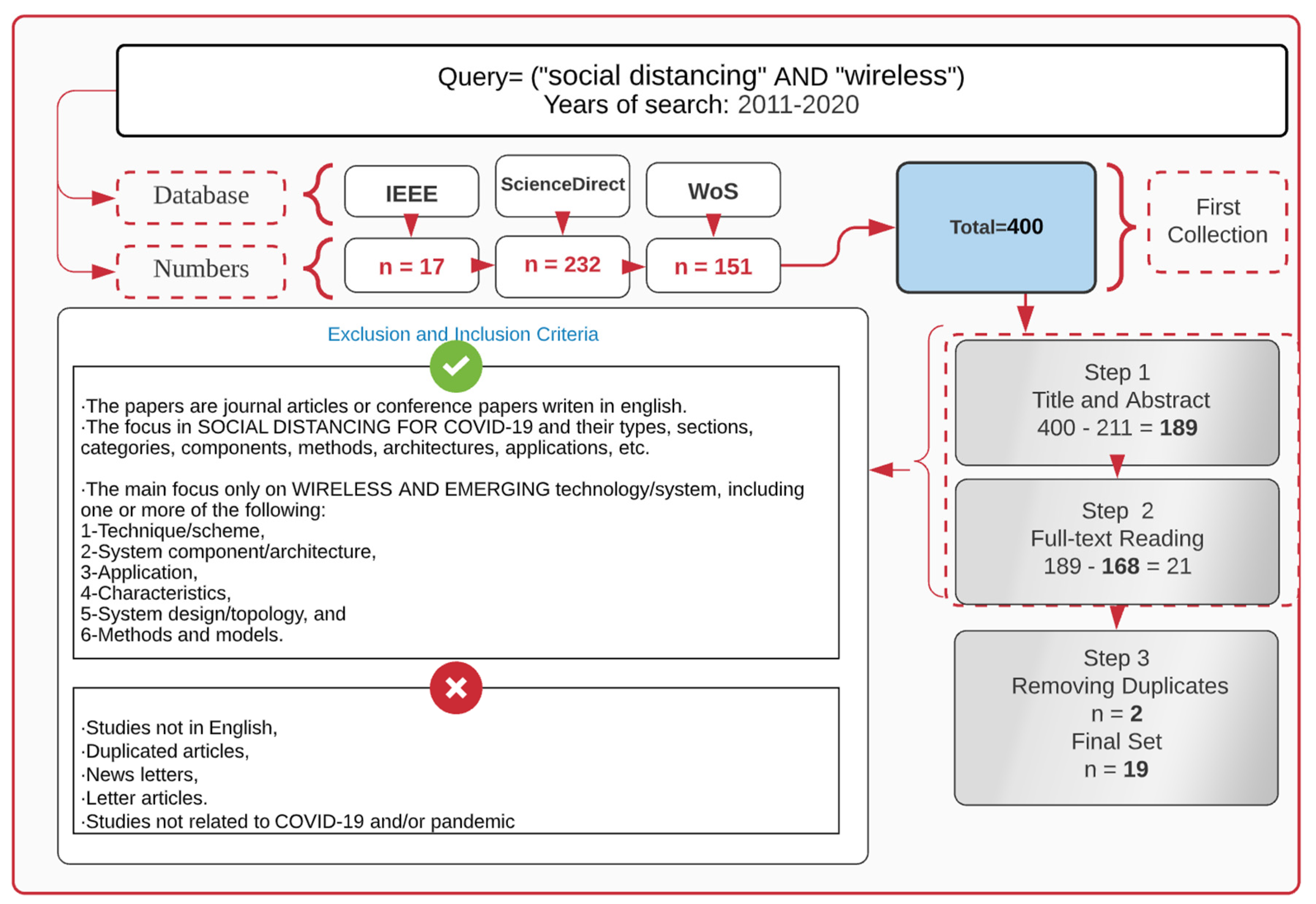
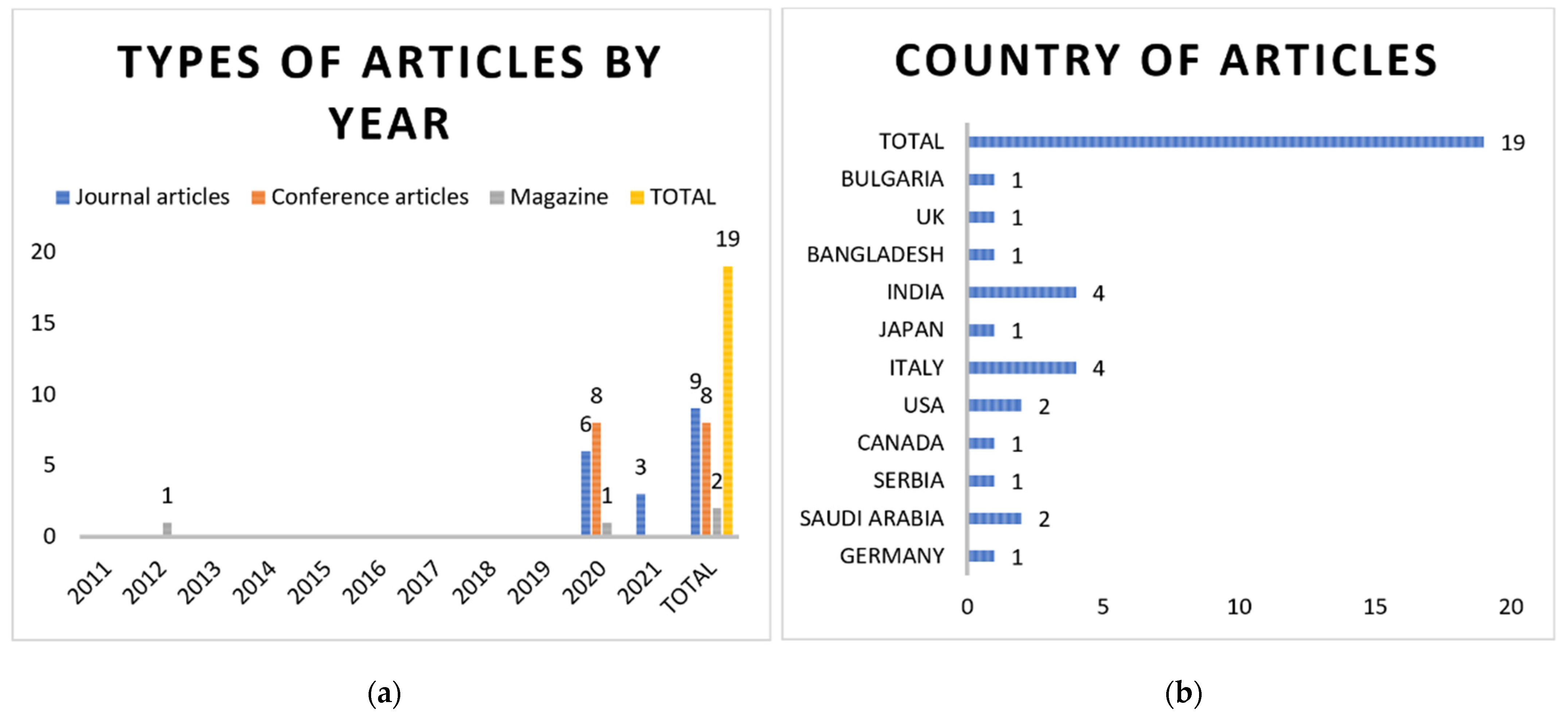
2. Methodology
Method, Study Selection, & Search Results
3. Wireless Technologies for Social Distancing
3.1. Background
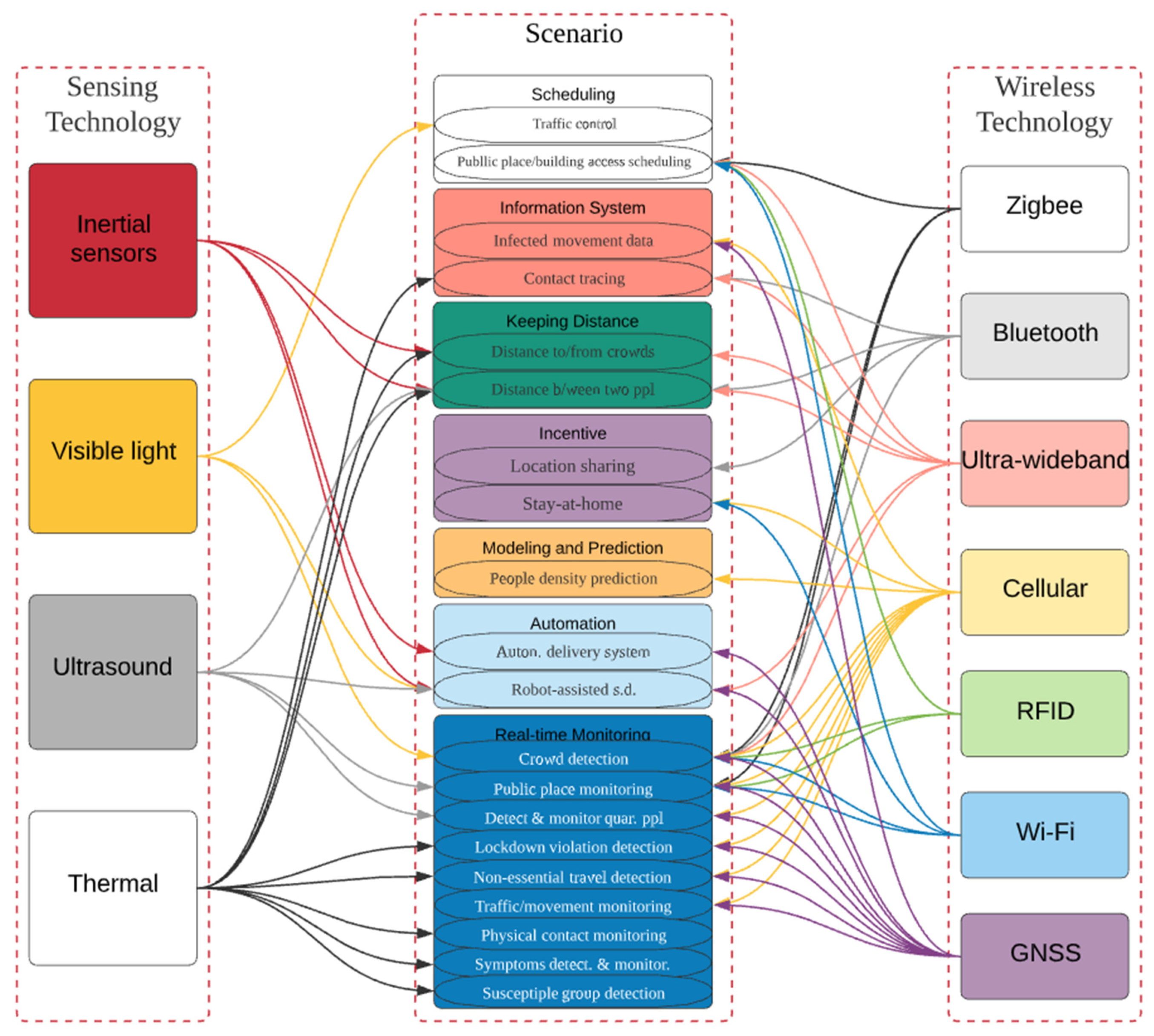
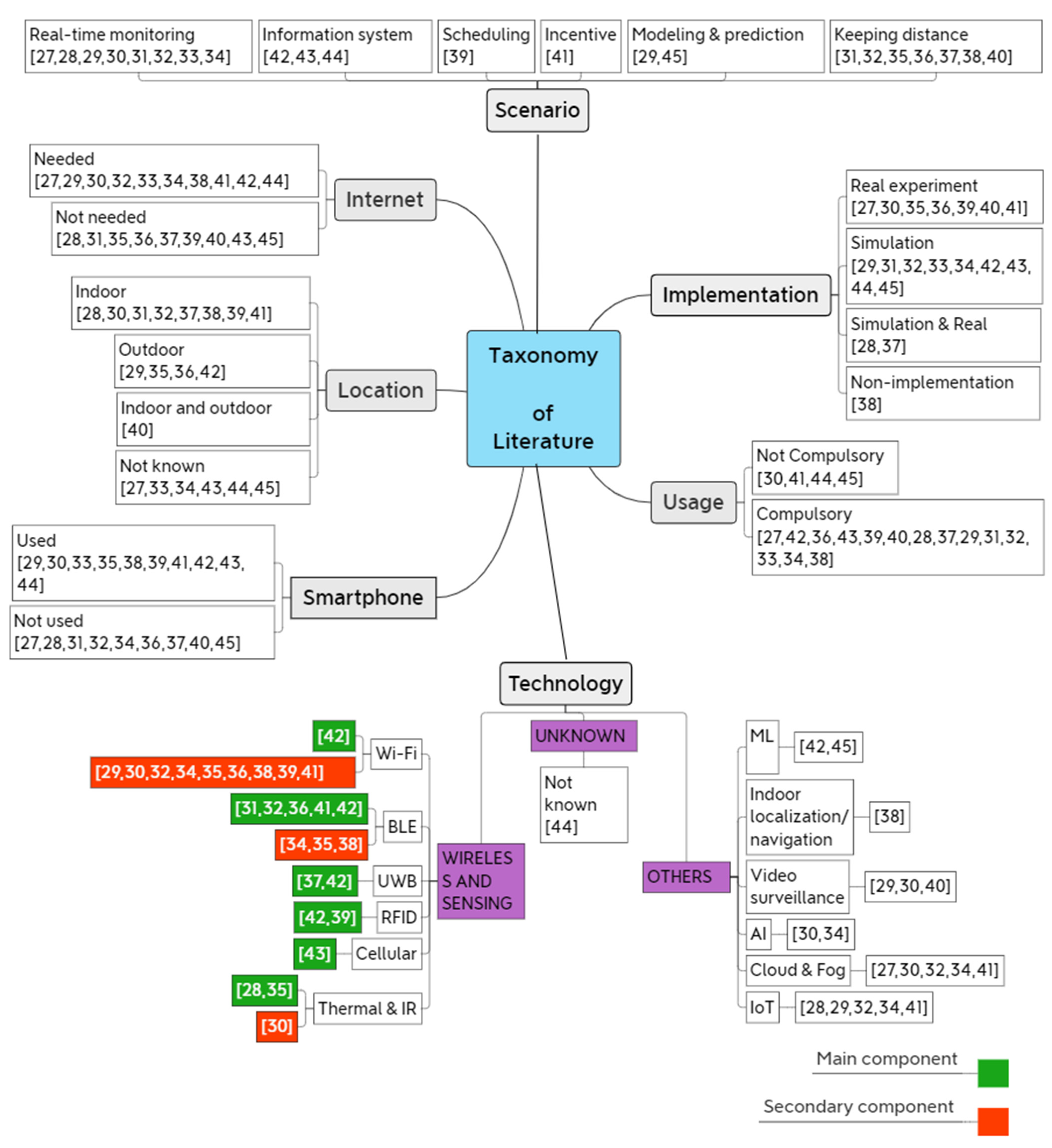
3.2. Taxonomy
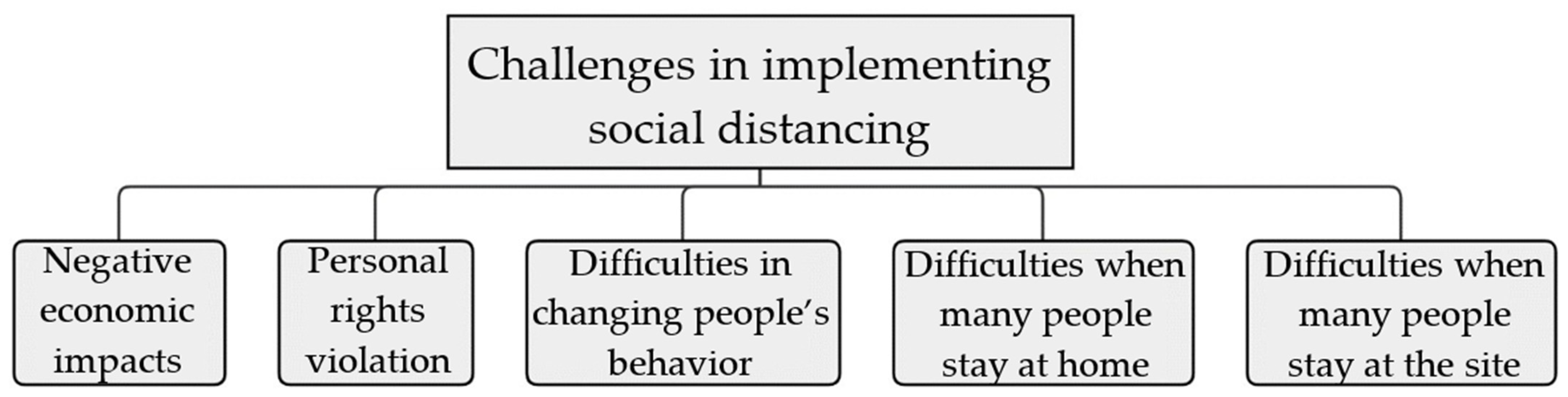
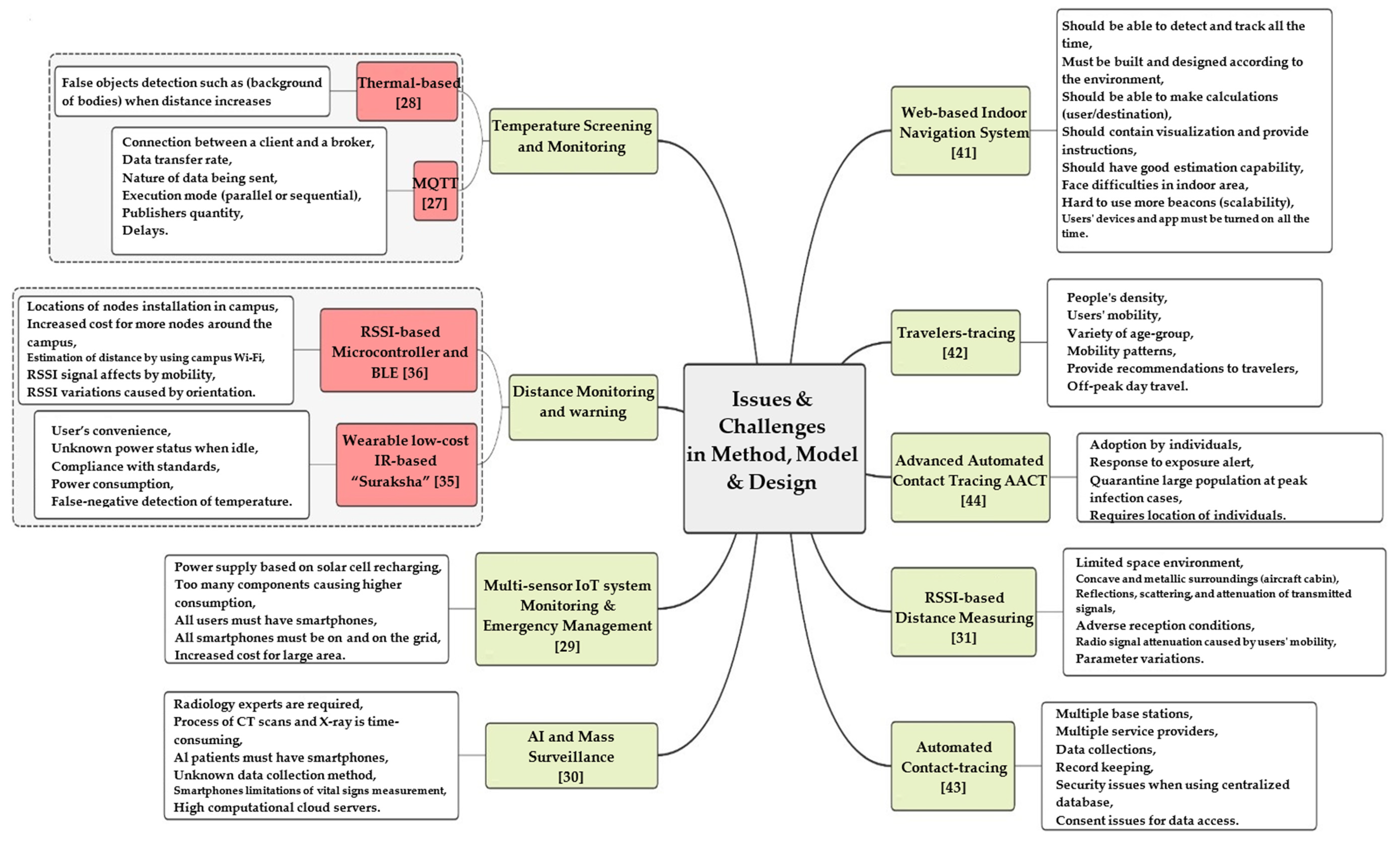
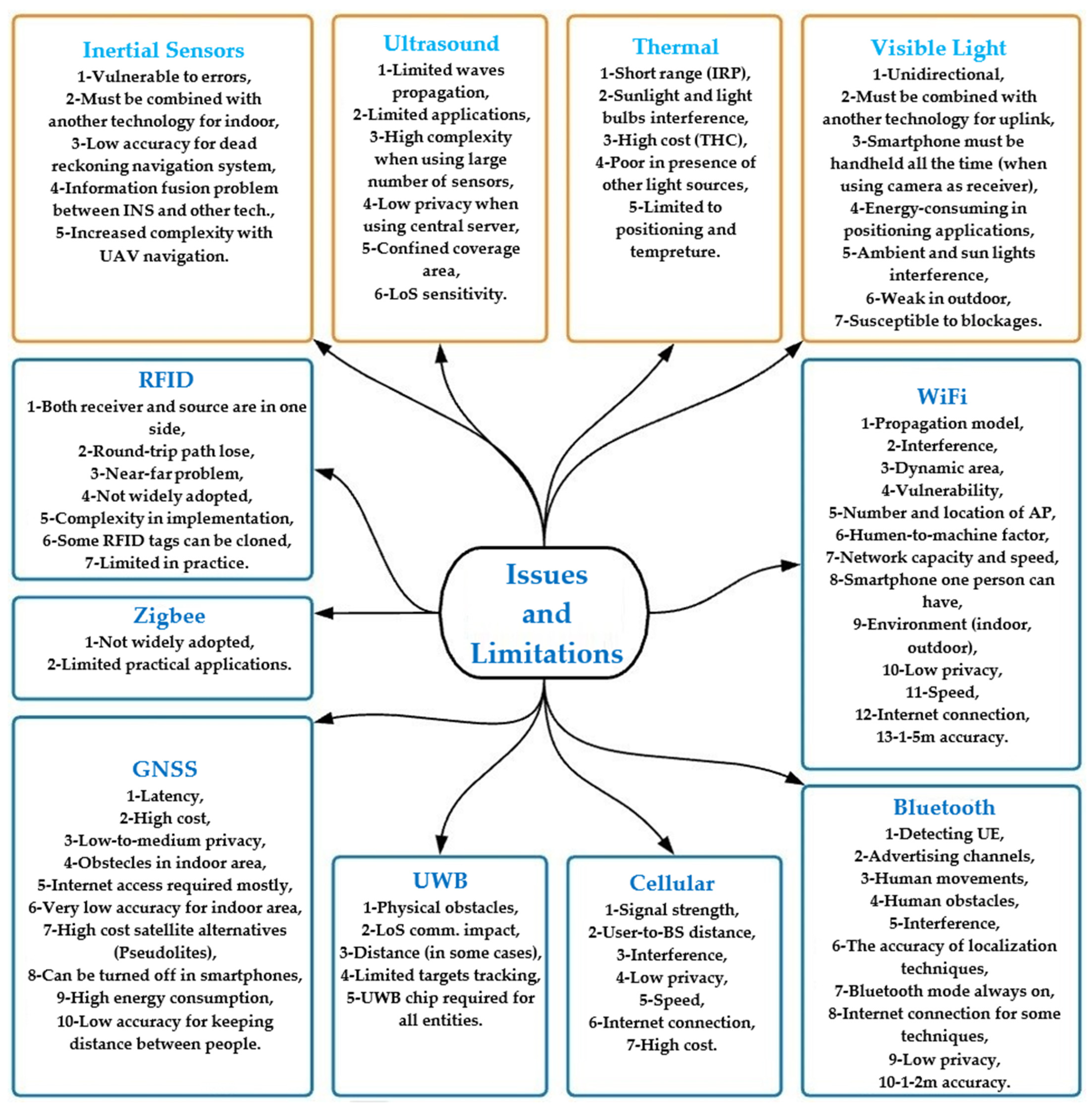
4. Issues and Challenges
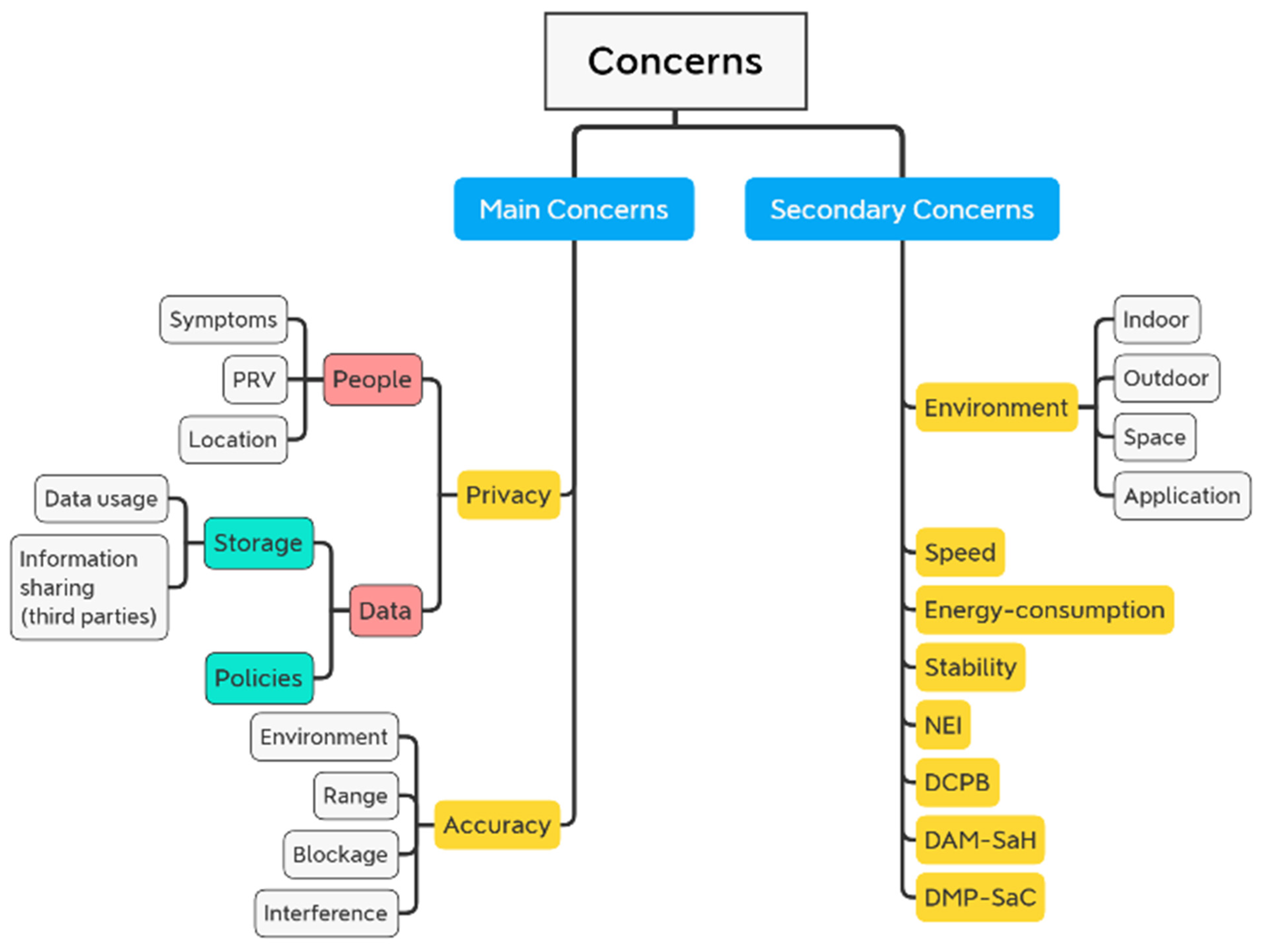
- Location: Users’ location is required by some systems and applications, such as wireless services and Global Positioning System (GPS) systems.
- Symptoms: Many suggested research would involve taking vital signs of persons and/or patients without their knowledge or agreement to gather data.
- PRV: Some systems may require people to respond to specific discoveries and/or decisions made by the systems they are using, such as denial of access, blocking, and the like.
4.1. General Issues & Challenges
4.2. Issues and Challenges in Method, Model, and Design
- (1)
- In order to do this, it should be able to detect and monitor the user’s location within the building,
- (2)
- It should also be aware of the surrounding environment,
- (3)
- The system should be able to determine the optimum route between the user and destination, taking into account the measure of interest (e.g., the shortest path, the most extensive way and/or passage, the lowest people density level, and so on), and
- (4)
- While viewing a map and offering spoken or iconographic instructions, it should guide the user to their desired destination.
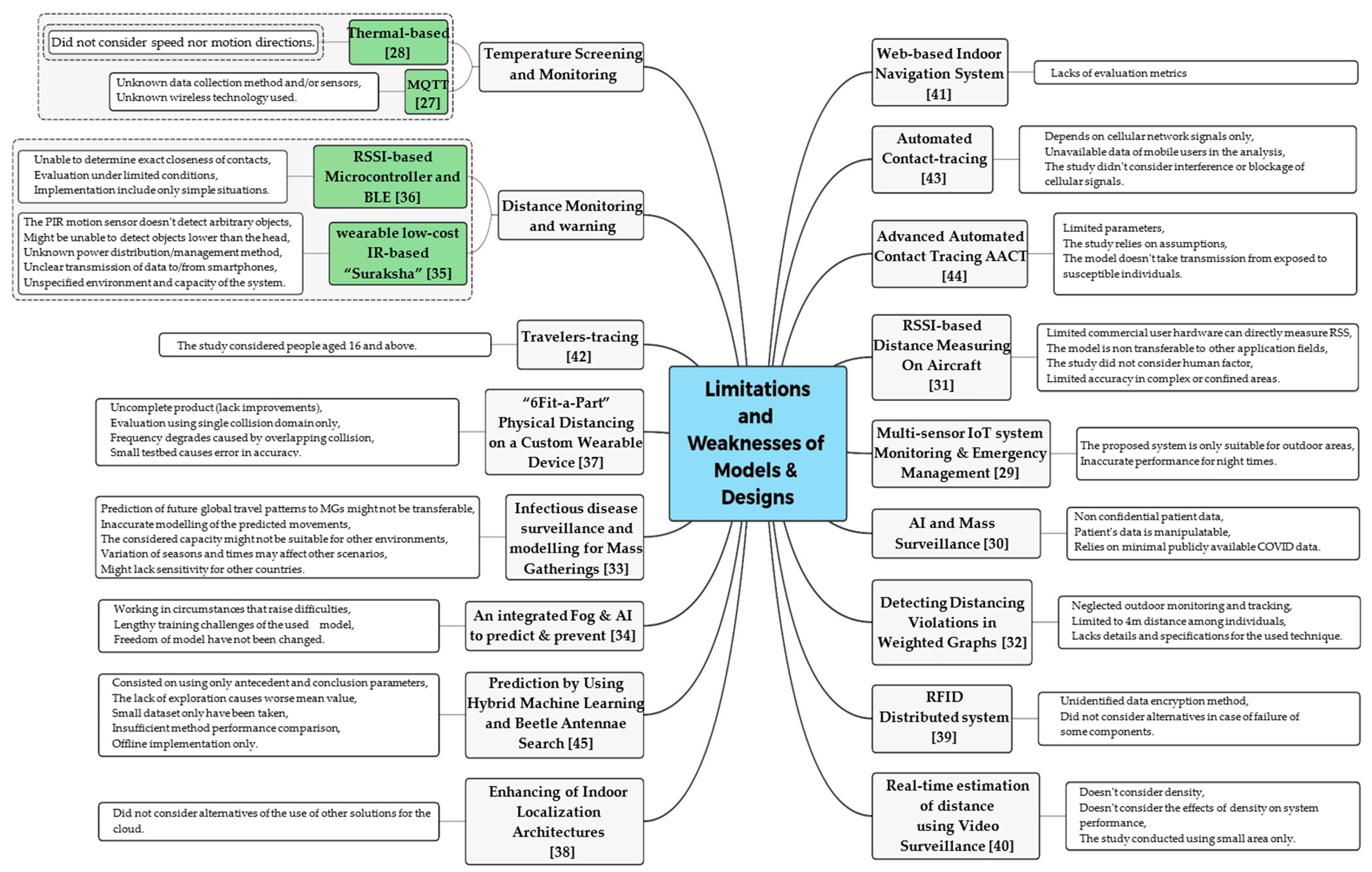
5. Limitations
5.1. General Limitations of Wireless Technologies for Social Distancing
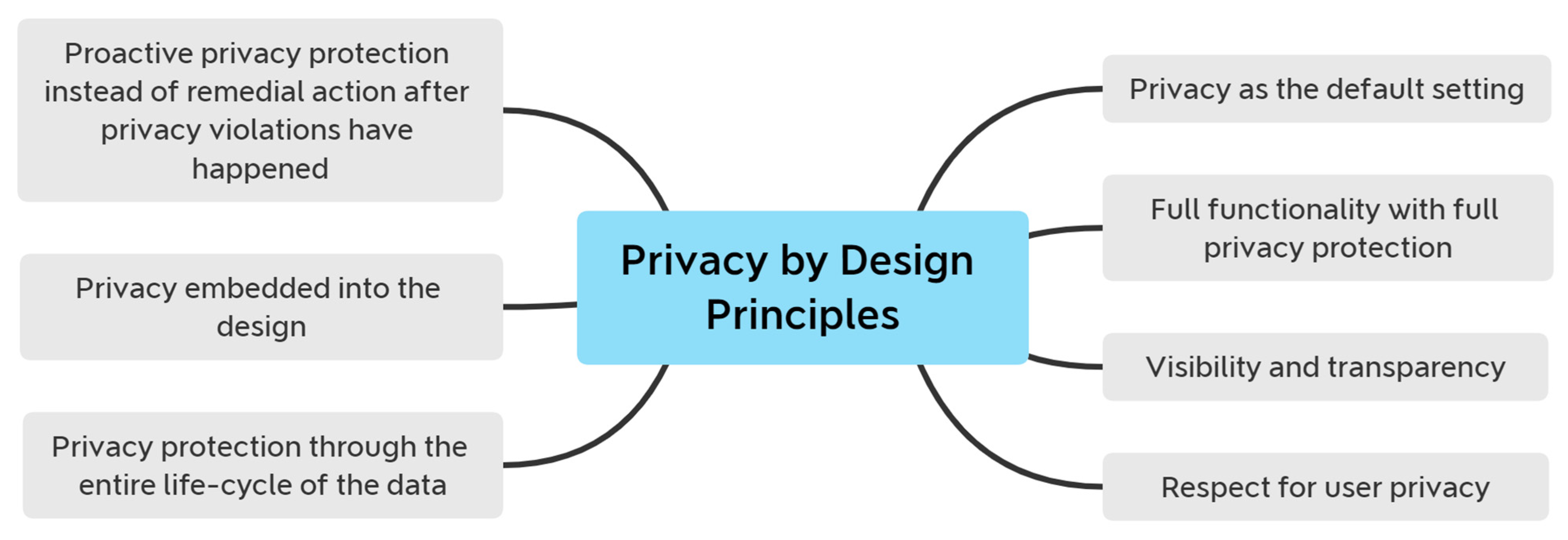
5.2. Limitations of the Method, Model and Design
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- World Health Organization. Timeline of WHO’s Response to COVID-19. 2020. Available online: https://www.who.int/newsroom/detail/29-06-2020-covidtimeline (accessed on 29 June 2020).
- World Health Organization. Coronavirus (COVID-19). 2020. Available online: https://covid19.who.int/ (accessed on 20 April 2020).
- Lempinen, E. COVID-19: Economic Impact, Human Solutions. Berkeley News. Available online: https://news.berkeley.edu/2020/04/10/covid-19-economic-impacthuman-solutions/ (accessed on 20 April 2020).
- Evans, P. Canada Lost More Than 1 Million Jobs Last Month as COVID-19 Struck. CBC News. 2020. Available online: https://www.cbc.ca/news/business/canada-jobs-march-covid-19-1.5527359 (accessed on 20 April 2020).
- Sullivan, K. Unemployment Rate Predicted to Reach 10 Per Cent Amid Coronavirus Pandemic, Pushing Australia Into Recession. ABC News. 2020. Available online: https://www.abc.net.au/news/2020-04-13/coronavirus-unemploy (accessed on 20 April 2020).
- Gopinath, G. International Monetary Fund Blog. The Great Lockdown: Worst Economic Downturn Since the Great Depression. 2020. Available online: https://blogs.imf.org/2020/04/14/the-great-lockdown-worst-economicdowntur (accessed on 20 April 2020).
- Pickert, R.; Qiu, Y.; McIntyre, A. Bloomberg. U.S Recession Model at 100% Confirms Downturn is Already Here. 2020. Available online: https://www.bloomberg.com/graphics/us-economic-recession-tracker/ (accessed on 20 April 2020).
- BBC News. Coronavirus: World Economy May Face Double Recession. 2020. Available online: https://www.bbc.com/news/business-52306001 (accessed on 20 April 2020).
- Ferguson, N.M.; Cummings, D.A.; Cauchemez, S.; Fraser, C.; Riley, S.; Meeyai, A.; Iamsirithaworn, S.; Burke, D.S. Strategies for containing an emerging influenza pandemic in Southeast Asia. Nature 2005, 437, 209–214. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Fraser, C.; Riley, S.; Anderson, R.M.; Ferguson, N.M. Factors that make an infectious disease outbreak controllable. Proc. Natl. Acad. Sci. USA 2004, 101, 6146–6151. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Ferguson, N.M.; Cummings, D.A.T.; Fraser, C.; Cajka, J.C.; Cooley, P.C.; Burke, D.S. Strategies for mitigating an influenza pandemic. Nature 2006, 442, 448–452. [Google Scholar] [CrossRef] [PubMed]
- Adlhoch, C. European centre for disease prevention and control. In Considerations Relating to Social Distancing Measures in Response to COVID-19_Second Update; ECDC: Stockholm, Sweden, 2020; Available online: https://www.ecdc. (accessed on 20 April 2020).
- Irfan, U. The Math Behind Why We Need Social Distancing, Starting Right Now. Vox. 2020. Available online: https://www.vox.com/2020/3/15/21180342/coronavirus-covid-19-us-social-distancing (accessed on 20 April 2020).
- Department of Health. Social Distancing for Coronavirus (COVID-19). 2020. Available online: https://www.health.gov.au/news/health-alerts/novelcoronavirus-2019-ncov-health-alert/how-to-protect-you (accessed on 20 April 2020).
- Centers for Disease Control and Prevention. Social Distancing, Quarantine, and Isolation. 2020. Available online: https://www.cdc.gov/coronavirus/2019-ncov/prevent-gettingsick/so (accessed on 20 April 2020).
- Public Health England. Guidance on Social Distancing for Everyone in the UK. 2020. Available online: https://www.gov.uk/government/publications/covid-19-guidanceon-social-distancing-and-for-vulnerable-people/guidanc (accessed on 20 April 2020).
- Our World in Data. Daily Con_rmed COVID-19 Cases, Rolling 3-Day Average. 2020. Available online: https://ourworldindata.org/grapher/daily-covid-cases-3-dayaverage?time=2020-02-21.&country=GBR+ESP+ITA+FRA+DEU (accessed on 20 April 2020).
- Our World in Data. Coronavirus Pandemic (COVID-19). 2020. Available online: https://ourworldindata.org/coronavirus (accessed on 7 July 2020).
- McFall-Johnsen, M. Countries in Asia are Facing New Waves of Coronavirus Infections After Lockdowns Lift. The Same Could Happen in the Rest of the World. Business Insider. 2020. Available online: https://www.businessins. (accessed on 20 April 2020).
- Jancowicz, M. At Least 6 Countries Reimposed Lockdown Measures as New Coronavirus Cases Flared Up Again. Here’s What they Looked Like. Business Insider. 2020. Available online: https://www.businessinsider.com/countriesi (accessed on 29 June 2020).
- Ali, Z. Coronavirus: Has a Second Wave of Infections Hit Iran? BBC. 2020. Available online: https://www.bbc.com/news/52959756 (accessed on 29 June 2020).
- Safer Together. TraceTogether. Available online: https://www.tracetogether.gov.sg/ (accessed on 20 April 2020).
- Williams, S. IT Brief. COVID-19: Zoom Downloads Explode as People Work from Home. 2020. Available online: https://itbrief.com.au/story/covid-19-zoomdownloads-explode-as-people-work-from-home (accessed on 20 April 2020).
- Giles, M. Microsoft Teams Has Seen a 775% Rise in Users in Italy Because of COVID-19. 2020. Available online: https://www.forbes.com/sites/martingiles/2020/03/30/microsoft-cloud-service-775-percentrise-covid- (accessed on 20 April 2020).
- Nguyen, C.T.; Saputra, Y.M.; Van Huynh, N.; Nguyen, N.-T.; Khoa, T.V.; Tuan, B.M.; Nguyen, D.N.; Hoang, D.T.; Vu, T.X.; Dutkiewicz, E.; et al. A comprehensive survey of enabling and emerging technologies for social distancing—Part I: Fundamentals and enabling technologies. IEEE Access 2020, 8, 153479–153507. [Google Scholar] [CrossRef] [PubMed]
- Nguyen, C.T.; Saputra, Y.M.; Van Huynh, N.; Nguyen, N.-T.; Khoa, T.V.; Tuan, B.M.; Nguyen, D.N.; Hoang, D.T.; Vu, T.X.; Dutkiewicz, E.; et al. A comprehensive survey of enabling and emerging technologies for social distancing—Part II: Emerging technologies and open issues. IEEE Access 2020, 8, 154209–154236. [Google Scholar] [CrossRef] [PubMed]
- Priyamvadaa, R. Temperature and saturation level monitoring system using MQTT for COVID-19. In Proceedings of the 2020 International Conference on Recent Trends on Electronics, Information, Communication & Technology (RTEICT), Bangalore, India, 12–13 November 2020; IEEE: Manhattan, NY, USA, 2020; pp. 17–20. [Google Scholar]
- Savazzi, S.; Rampa, V.; Costa, L.; Kianoush, S.; Tolochenko, D. Processing of body-induced thermal signatures for physical distancing and temperature screening. IEEE Sens. J. 2020, 21, 14168–14179. [Google Scholar] [CrossRef]
- Fedele, R.; Merenda, M. An IoT system for social distancing and emergency management in smart cities using multi-sensor data. Algorithms 2020, 13, 254. [Google Scholar] [CrossRef]
- Hossain, M.S.; Muhammad, G.; Guizani, N. Explainable AI and mass surveillance system-based healthcare framework to combat COVID-I9 like pandemics. IEEE Netw. 2020, 34, 126–132. [Google Scholar] [CrossRef]
- Schwarzbach, P.; Engelbrecht, J.; Michler, A.; Schultz, M.; Michler, O. Evaluation of technology-supported distance measuring to ensure safe aircraft boarding during COVID-19 pandemic. Sustainability 2020, 12, 8724. [Google Scholar] [CrossRef]
- Subahi, A.F. A model transformation approach for detecting distancing violations in weighted graphs. Comput. Syst. Sci. Eng. 2021, 36, 13–39. [Google Scholar] [CrossRef]
- Khan, K.; McNabb, S.J.N.; Memish, Z.A.; Eckhardt, R.; Hu, W.; Kossowsky, D.; Sears, J.; Arino, J.; Johansson, A.; Barbeschi, M.; et al. Infectious disease surveillance and modelling across geographic frontiers and scientifi c specialties. Lancet Infect. Dis. 2012, 12, 222–230. [Google Scholar] [CrossRef]
- Singh, P.; Kaur, R. An integrated fog and artificial intelligence smart health framework to predict and prevent COVID-19. Glob. Transit. 2020, 2, 283–292. [Google Scholar] [CrossRef] [PubMed]
- Raghav, S.; Vijay, G.; Harika, P.S.; Rao, A.V.; Gopinath, A.; Shibu, N.B.S.; Gayathri, G. Suraksha: Low cost device to maintain social distancing during COVID-19. In Proceedings of the 2020 4th International Conference on Electronics, Communication and Aerospace Technology (ICECA), Coimbatore, India, 5–7 November 2020; IEEE: Manhattan, NY, USA, 2020; pp. 1476–1480. [Google Scholar]
- Kobayashi, Y.; Taniguchi, Y.; Ochi, Y.; Iguchi, N. A system for monitoring social distancing using microcomputer modules on university campuses. In Proceedings of the 2020 IEEE International Conference on Consumer Electronics-Asia (ICCE-Asia), Seoul, Korea, 1–3 November 2020; IEEE: Manhattan, NY, USA, 2020; pp. 1–4. [Google Scholar]
- Cao, Y.; Dhekne, A.; Ammar, M. 6Fit-A-part: A protocol for physical distancing on a custom wearable device. In Proceedings of the 2020 IEEE 28th International Conference on Network Protocols (ICNP), Madrid, Spain, 13–16 October 2020; IEEE: Manhattan, NY, USA, 2020; pp. 1–12. [Google Scholar]
- Barsocchi, P.; Calabrò, A.; Crivello, A.; Daoudagh, S.; Furfari, F.; Girolami, M.; Marchetti, E. COVID-19 & privacy: Enhancing of indoor localization architectures towards effective social distancing. Array 2021, 9, 100051. [Google Scholar]
- Yadav, B.K.; Burman, A.; Mahato, A.; Choudhary, M.; Kundu, A. Smart cart: A distributed framework. In Proceedings of the 2020 IEEE 1st International Conference for Convergence in Engineering (ICCE), Kolkata, India, 5–6 September 2020; IEEE: Manhattan, NY, USA, 2020; pp. 210–213. [Google Scholar]
- Neshov, N.; Manolova, A.; Tonchev, K.; Poulkov, V. Real-time estimation of distance between people and/or objects in video surveillance. In Proceedings of the 2020 23rd International Symposium on Wireless Personal Multimedia Communications (WPMC), Okayama, Japan, 19–26 October 2020; IEEE: Manhattan, NY, USA, 2020; pp. 1–4. [Google Scholar]
- Fazio, M.; Buzachis, A.; Galletta, A.; Celesti, A.; Villari, M. A proximity-based indoor navigation system tackling the COVID-19 social distancing measures. In Proceedings of the 2020 IEEE Symposium on Computers and Communications (ISCC), Rennes, France, 7–10 July 2020; IEEE: Manhattan, NY, USA, 2020; pp. 1–6. [Google Scholar]
- Asad, S.M.; Dashtipour, K.; Hussain, S.; Abbasi, Q.H.; Imran, M.A. Travelers-tracing and mobility profiling using machine learning in railway systems. In Proceedings of the 2020 International Conference on UK-China Emerging Technologies (UCET), Glasgow, UK, 20–21 August 2020; IEEE: Manhattan, NY, USA, 2020; pp. 1–4. [Google Scholar]
- Rahman, T.; Khan, R.T.; Khandaker, M.R.A.; Sellathurai, M.; Salan, S.A. An automated contact tracing approach for controlling COVID-19 spread based on geolocation data from mobile cellular networks. IEEE Access 2020, 8, 213554–213565. [Google Scholar] [CrossRef]
- Nuzzo, A.; Tan, C.O.; Raskar, R.; De Simone, D.C.; Kapa, S.; Gupta, R. Universal shelter-in-place versus advanced automated contact tracing and targeted isolation. Mayo Clin. Proc. 2020, 95, 1898–1905. [Google Scholar] [CrossRef]
- Zivkovic, M.; Bacanin, N.; Venkatachalam, K.; Nayyar, A.; Djordjevic, A.; Strumberger, I.; Al-Turjman, F. COVID-19 cases prediction by using hybrid machine learning and beetle antennae search approach. Sustain. Cities Soc. 2021, 66, 102669. [Google Scholar] [CrossRef]
- O’Dea, S. Number of Smart Phone Users Worldwide|Statista. 2020. Available online: https://www.statista.com/statistics/330695/number-of-smartphone-users-w%orldwide/ (accessed on 20 June 2021).
- Abdulla, M.A.; Esmaeel, A.M. Providing information through smart platforms: An applied study on academic libraries in Saudi universities. J. Educ. Soc. Behav. Sci. 2019, 30, 1–24. [Google Scholar] [CrossRef]
- Kaptchuk, G.; Goldstein, D.G.; Hargittai, E.; Hofman, J.; Redmiles, E.M. How good is good enough for COVID19 apps? The influence of benefits, accuracy, and privacy on willingness to adopt. arXiv 2020, arXiv:2005.04343. [Google Scholar]
- Redmiles, E.M. User concerns & tradeoffs in technology-facilitated COVID-19 response. Digit. Gov. Res. Pract. 2021, 2, 1–12. [Google Scholar]
- de Montjoye, Y.; Houssiau, F.; Gadotti, A.; Guepin, F. Evaluating COVID-19 Contact Tracing Apps? Here Are 8 Privacy Questions We Think You Should Ask. Computational Privacy Group. 2020. Available online: https://cpg.doc.ic.ac.uk/blog/evaluating-contact-tracing-apps-here-are-8-privacy-questions-we-think-you-should-ask/ (accessed on 20 May 2021).
- Hua, J.; Shaw, R. Corona virus (COVID-19) ‘infodemic’ and emerging issues through a data lens: The case of china. Int. J. Environ. Res. Public Health 2020, 17, 2309. [Google Scholar] [CrossRef] [Green Version]
- Ko, H.; Leitner, J.; Kim, E.; Jeong, J. Structure and enforcement of data privacy law in South Korea. Int. Data Priv. Law 2017, 7, 100–114. [Google Scholar] [CrossRef] [Green Version]
- Khan, K.; Memish, Z.A.; Chabbra, A.; Liauw, J.; Hu, W.; Janes, D.A.; Sears, J.; Arino, J.; Macdonald, M.; Calderon, F.; et al. Global public health implications of a mass gathering in Mecca, Saudi Arabia during the midst of an influenza pandemic. J. Travel Med. 2010, 17, 75–81. [Google Scholar] [CrossRef] [PubMed]
- Khan, K.; Freifeld, C.C.; Wang, J.; Mekaru, S.R.; Kossowsky, D.; Sonricker, A.L.; Hu, W.; Sears, J.; Chan, A.; Brownstein, J.S. Preparing for infectious disease threats at mass gatherings: The case of the Vancouver 2010 olympic winter games. Can. Med. Assoc. J. 2010, 182, 579–583. [Google Scholar] [CrossRef] [Green Version]
- WHO. Revision of the International Health Regulations. 2005. Available online: http://www.who.int/csr/ihr/en/ (accessed on 15 June 2011).
- Grein, T. Rumors of disease in the global village: Outbreak verification. Emerg. Infect. Dis. 2000, 6, 97–102. [Google Scholar] [CrossRef] [PubMed]
- Heymann, D.L.; Rodier, G.R. Hot spots in a wired world: WHO surveillance of emerging and re-emerging infectious diseases. Lancet Infect. Dis. 2001, 1, 345–353. [Google Scholar] [CrossRef]
- Scarpino, S.V.; Petri, G. On the predictability of infectious disease outbreaks. Nat. Commun. 2019, 10, 898. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Zhan, Z.; Dong, W.; Lu, Y.; Yang, P.; Wang, Q.; Jia, P. Real-time forecasting of hand-foot-and-mouth disease outbreaks using the integrating compartment model and assimilation filtering. Sci. Rep. 2019, 9, 2661. [Google Scholar] [CrossRef]
- Rypdal, M.; Sugihara, G. Inter-outbreak stability reflects the size of the susceptible pool and forecasts magnitudes of seasonal epidemics. Nat. Commun. 2019, 10, 2374. [Google Scholar] [CrossRef] [Green Version]
- Exposure Notification—Bluetooth Specification; Technical Report; Bluetooth SIG Inc.: Washington, DC, USA, 2020; Available online: https://www.bluetooth.com/bluetooth-resources/ (accessed on 20 March 2021).
- Ahmed, N.; Michelin, R.A.; Xue, W.; Ruj, S.; Malaney, R.; Kanhere, S.S.; Seneviratne, A.; Hu, W.; Janicke, H.; Jha, S.K. A survey of COVID-19 contact tracing apps. IEEE Access 2020, 8, 134577–134601. [Google Scholar] [CrossRef]
- Mishra, P.K. Bluetooth security threats. Int. J. Comput. Sci. Eng. Technol. 2013, 4, 147–151. [Google Scholar]
- Naveed, M.; Zhou, X.; Demetriou, S.; Wang, X.; Gunter, C.A. Inside job: Understanding and mitigating the threat of external device mis-binding on android. In Proceedings of the 2014 Network and Distributed System Security (NDSS) Symposium, San Diego, CA, USA, 23–26 February 2014. [Google Scholar]
- Spill, D.; Bittau, A. BlueSniff: Eve meets alice and bluetooth. WOOT 2007, 7, 1–10. [Google Scholar]
- Bai, X.; Xing, L.; Zhang, N.; Wang, X.; Liao, X.; Li, T.; Hu, S.-M. Staying secure and unprepared: Understanding and mitigating the security risks of apple zeroconf. In Proceedings of the 2016 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–26 May 2016; pp. 655–674. [Google Scholar]
- Jeong, Y.; Yoon, K.; Joung, K. Probabilistic method to determine human subjects for low-resolution thermal imaging sensor. In Proceedings of the 2014 IEEE Sensors Applications Symposium (SAS), Queenstown, New Zealand, 18–20 February 2014; pp. 97–102. [Google Scholar]
- Dittmar, A.; Gehin, C.; Delhomme, G.; Boivin, D.; Dumont, G.; Mott, C. A non invasive wearable sensor for the measurement of brain temperature. In Proceedings of the 2006 International Conference of the IEEE Engineering in Medicine and Biology Society, New York, NY, USA, 30 August–3 September 2006; pp. 900–902. [Google Scholar]
- Chen, H.-Y.; Chen, A.; Chen, C. Investigation of the impact of infrared sensors on core body temperature monitoring by comparing measurement sites. Sensors 2020, 20, 2885. [Google Scholar] [CrossRef] [PubMed]
- Amendola, S.; Bovesecchi, G.; Palombi, A.; Coppa, P.; Marrocco, G. Design, calibration and experimentation of an epidermal RFID sensor for remote temperature monitoring. IEEE Sens. J. 2016, 16, 7250–7257. [Google Scholar] [CrossRef]
- Chaglla, E.J.S.; Celik, N.; Balachandran, W. Measurement of core body temperature using graphene-inked infrared thermopile sensor. Sensors 2018, 18, 3315. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Psikuta, A.; Niedermann, R.; Rossi, R.M. Effect of ambient temperature and attachment method on surface temperature measurements. Int. J. Biometeorol. 2014, 58, 877–885. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Güttler, J.; Georgoulas, C.; Bock, T. Contactless fever measurement based on thermal imagery analysis. In Proceedings of the 2016 IEEE Sensors Applications Symposium (SAS), Catania, Italy, 20–22 April 2016; pp. 1–6. [Google Scholar]
- Nguyen, A.V.; Cohen, N.J.; Lipman, H.; Brown, C.M.; Molinari, N.-A.; Jackson, W.L.; Kirking, H.; Szymanowski, P.; Wilson, T.W.; Salhi, B.; et al. Comparison of 3 infrared thermal detection systems and self-report for mass fever screening. Emerg. Infect. Dis. 2010, 16, 1710–1717. [Google Scholar] [CrossRef]
- Negishi, T.; Abe, S.; Matsui, T.; Liu, H.; Kurosawa, M.; Kirimoto, T.; Sun, G. Contactless vital signs measurement system using RGB-thermal image sensors and its clinical screening test on patients with seasonal influenza. Sensors 2020, 20, 2171. [Google Scholar] [CrossRef] [Green Version]
- Allam, Z.; Dey, G.; Jones, D.S. Artificial intelligence (AI) provided early detection of the coronavirus (COVID-19) in China and will influence future urban health policy internationally. AI 2020, 1, 156–165. [Google Scholar] [CrossRef] [Green Version]
- Shen, L.; Zhang, Q.; Pang, J.; Xu, H.; Li, P.; Xue, D. ANTspin: Efficient absolute localization method of RFID tags via spinning antenna. Sensors 2019, 19, 2194. [Google Scholar] [CrossRef] [Green Version]
- Zhang, D.; Yang, L.T.; Chen, M.; Zhao, S.; Guo, M.; Zhang, Y. Real-time locating systems using active RFID for internet of things. IEEE Syst. J. 2016, 10, 1226–1235. [Google Scholar] [CrossRef]
- Paolini, G.; Masotti, D.; Antoniazzi, F.; Cinotti, T.S.; Costanzo, A. Fall detection and 3-D indoor localization by a custom RFID reader embedded in a smart e-health platform. IEEE Trans. Microw. Theory Tech. 2019, 67, 5329–5339. [Google Scholar] [CrossRef]
- Faragher, R.; Harle, R. Location fingerprinting with bluetooth low energy beacons. IEEE J. Sel. Areas Commun. 2015, 33, 2418–2428. [Google Scholar] [CrossRef]
- Wu, K.; Xiao, J.; Yi, Y.; Gao, M.; Ni, L.M. FILA: Fine-grained indoor localization. In Proceedings of the 2012 Proceedings IEEE INFOCOM, Orlando, FL, USA, 25–30 March 2012; pp. 2210–2218. [Google Scholar]
- Rahman, M.A.; Hossain, M.S.; Alrajeh, N.A.; Guizani, N. B5G and explainable deep learning assisted healthcare vertical at the edge: COVID-I9 perspective. IEEE Netw. 2020, 34, 98–105. [Google Scholar] [CrossRef]
- Rappaport, T.S. Wireless Communications: Principles and Practice; Prentice Hall PTR: Hoboken, NJ, USA, 1996; Volume 2. [Google Scholar]
- Al-Qaness, M.A.A.; Ewees, A.A.; Fan, H.; El Aziz, M.A. Optimization method for forecasting confirmed cases of COVID-19 in China. J. Clin. Med. 2020, 9, 674. [Google Scholar] [CrossRef] [Green Version]
- Ma, C.; Yang, J.; Chen, J.; Tang, Y. Time synchronization requirement of global navigation satellite system augmentation system based on pseudolite. Meas. Control 2019, 52, 303–313. [Google Scholar] [CrossRef] [Green Version]
- Shao, M.; Sui, X. Study on differential GPS positioning methods. In Proceedings of the 2015 International Conference on Computer Science and Mechanical Automation (CSMA), Hangzhou, China, 23–25 October 2015; pp. 223–225. [Google Scholar]
- Al-Shaery, A.; Zhang, S.; Rizos, C. An enhanced calibration method of GLONASS inter-channel bias for GNSS RTK. GPS Solut. 2012, 17, 165–173. [Google Scholar] [CrossRef]
- Tu, R.; Liu, J.; Zhang, R.; Fan, L.; Zhang, P.; Han, J. Real-time kinematic positioning algorithm with GNSS and high-frequency accelerometer observations for broadband signals. Meas. Sci. Technol. 2019, 31, 035007. [Google Scholar] [CrossRef]
- Zigbee Alliance. Zigbee. Available online: https://zigbeealliance.org/ (accessed on 20 April 2020).
- Komine, T.; Nakagawa, M. Fundamental analysis for visible-light communication system using LED lights. IEEE Trans. Consum. Electron. 2004, 50, 100–107. [Google Scholar] [CrossRef]
- Pathak, P.H.; Feng, X.; Hu, P.; Mohapatra, P. Visible light communication, networking, and sensing: A survey, potential and challenges. IEEE Commun. Surv. Tutor. 2015, 17, 2047–2077. [Google Scholar] [CrossRef]
- Badeel, R.; Subramaniam, S.K.; Hanapi, Z.M.; Muhammed, A. A review on LiFi network research: Open issues, applications and future directions. Appl. Sci. 2021, 11, 11118. [Google Scholar] [CrossRef]
- Ho, H.J.; Zhang, Z.X.; Huang, Z.; Aung, A.H.; Lim, W.-Y.; Chow, A. Use of a real-time locating system for contact tracing of health care workers during the COVID-19 pandemic at an infectious disease center in Singapore: Validation study. J. Med. Internet Res. 2020, 22, e19437. [Google Scholar] [CrossRef] [PubMed]
- Murad, S.S.; Badeel, R.; Salih, N.; Alsandi, A.; Faraj, R.; Ahmed, A.R.; Muhammed, A.; Derahman, M.; Alsandi, N. Optimized Min-Min task scheduling algorithm for scientific workflows in a cloud environment. J. Theor. Appl. Inf. Technol. 2022, 100, 480–506. [Google Scholar]



| Ref. | [35] | [27] | [42] | [36] | [43] | [39] | [40] | [41] | [28] | [37] | [29] | [30] | [31] | [32] | [44] | [33] | [34] | [45] | [38] | ||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Internal Factors | General | Approach | MWP | VSM | TT | MWP | CT | TC | MWP | INS, ISh | PhD, VSM | PhD | MWP, CD | VSM | VSM | NK | SiP | MG | SmH | PD | IL |
| Environment | OT | BCE | RS | UniC | G | SM | G | LSM | P | IPP | SC | SHC | AC | IPP | GB | GB, LCL | HC | NK | IPP | ||
| Specific | Accuracy | L-M | M-H | M-H | L-M | M-H | H | M | L-M | M | L-M | M-H | L-M | L-M | M | M | M | M-H | L-M | M | |
| Speed | M | M-H | M | M-H | M | H | M | M | M | M-H | M-H | L-M | M | L-M | M | M | M-H | L | M-H | ||
| Privacy | Data: H; People: H | Data: L; People: L | Data: L; People: L | Data: L; People: L | Data: M; People: L | Data: M; People: NA | Data: L; People: L | Data: M; People: M | Data: H; People: H | Data: H; People: H | Data: L; People: L | Data: M; People: L | Data: M; People: L | Data: H; People: L | Data: L; People: L | Data: L; People: L | Data: M-H; People: L | NK | Data: H; People: L | ||
| Energy- consumption | M-H | L-M | L-M | H | H | L | L-M | M-H | L-M | M-H | L-M | H | L | NK | L | L-M | M-H | NK | L-H | ||
| Disconn. possibility | L | L | L | L-M | L-M | L | L | L-M | L | L | M | L | M-H | M-H | L | L-M | L | NK | L-M | ||
| Computation | L | M | M | L-M | L | L | M | L-M | M-H | M | L-M | H | L | M-H | L | L-M | M | H | L-M | ||
| External Factors | Implementation Challenges | NEI | NO | NO | YES | NO | NO | NO | NO | NO | NO | NO | L | L | H | M | YES | YES | NO | NO | YES |
| PRV | NO | YES | YES | NO | NO | NO | YES | NO | NO | NO | M | L | M-H | M | YES | YES | NO | NO | YES | ||
| DCPB | NO | NO | NO | YES | NO | NO | NO | YES | NO | NO | YES | YES | YES | NO | YES | YES | NO | NO | YES | ||
| DMP-SaH | NO | NO | NO | NO | NO | NO | NO | NO | NO | NO | NO | NO | NO | NO | NO | NO | NO | NK | NO | ||
| DMP-SaC | YES | NO | YES | YES | NO | NO | YES | YES | YES | YES | YES | NO | YES | YES | NO | YES | YES | NK | YES | ||
| Terms and definitions | Approach | MWP: monitor and warn people, VSM: vital sign monitoring, TT: travellers tracing, CT: contact tracing, TC: traffic control, INS: Indoor navigation system, ISh: Information sharing, PhD: physical distancing, CD: crowd density, SiP: shelter in place, MG: mass gathering, SmH: smart health, PD: people density, IL: indoor localization; | |||||||||||||||||||
| Environment | OT: outside travelling, BCE: bandwidth-constrained environment, RS: railway system, UniC: university campus, G: general, LSM: inside large smart buildings, P: public places, IPP: indoor public areas, SM: shopping markets, SC: smart cities, SHC: smart healthcare, AC: aircraft, GB: global, LCL: local, HC: healthcare; | ||||||||||||||||||||
| Specific | L: low, M: Medium, H: high, N: needed, Nt: not needed; | ||||||||||||||||||||
| External factors | NEI: negative economic impacts, PRV: personal rights violation, DCPB: difficulties changing people’s behaviour, DMP-SaH: difficulties when many people at home, DMP-SaC: difficulties when many people at the site; | ||||||||||||||||||||
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Murad, S.S.; Yussof, S.; Badeel, R. Wireless Technologies for Social Distancing in the Time of COVID-19: Literature Review, Open Issues, and Limitations. Sensors 2022, 22, 2313. https://doi.org/10.3390/s22062313
Murad SS, Yussof S, Badeel R. Wireless Technologies for Social Distancing in the Time of COVID-19: Literature Review, Open Issues, and Limitations. Sensors. 2022; 22(6):2313. https://doi.org/10.3390/s22062313
Chicago/Turabian StyleMurad, Sallar Salam, Salman Yussof, and Rozin Badeel. 2022. "Wireless Technologies for Social Distancing in the Time of COVID-19: Literature Review, Open Issues, and Limitations" Sensors 22, no. 6: 2313. https://doi.org/10.3390/s22062313
APA StyleMurad, S. S., Yussof, S., & Badeel, R. (2022). Wireless Technologies for Social Distancing in the Time of COVID-19: Literature Review, Open Issues, and Limitations. Sensors, 22(6), 2313. https://doi.org/10.3390/s22062313